Windows 10 Identity and Security
|
|
|
- Harold Ray
- 6 years ago
- Views:
Transcription
1 Windows 10 Identity and Security
2
3 CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $3.0 TRILLION $3.5 MILLION $500 MILLION Impact of lost productivity and growth Average cost of a data breach (15% YoY increase) Corporate liability coverage. CYBER THREATS ARE A MATERIAL RISK TO YOUR BUSINESS Source: McKinsey, Ponemon Institute, Verizon
4 EVOLUTION OF ATTACKS Mischief Fraud and Theft Damage and Disruption Script Kiddies Unsophisticated Organized Crime More sophisticated Nations, Terror Groups, Activists Very sophisticated and well resourced
5 RANSOMWARE
6 ANATOMY OF AN ATTACK Browser or Doc Exploit Delivery Malicious Attachment Delivery Phishing Attacks ENTER USER DEVICE ESTABLISH Internet Service Compromise Browser or Doc Exploit Execution Malicious Attachment Execution Stolen Credential Use Kernel Exploits Kernel-mode Malware Pass-the-Hash EXPAND NETWORK ENDGAME BUSINESS DISRUPTION LOST PRODUCTIVITY DATA THEFT ESPIONAGE, LOSS OF IP RANSOM
7 ANATOMY OF AN ATTACK: STRONTIUM PHISHING USER DEVICE Browser or Doc Exploit Execution PASS-THE-HASH NETWORK ENDGAME Theft of sensitive information, disruption of government.
8 ANATOMY OF AN ATTACK: STRONTIUM PHISHING USER DEVICE Browser or Doc Exploit Execution PASS-THE-HASH NETWORK ENDGAME Theft of sensitive information, disruption of government.
9 ANATOMY OF AN ATTACK: STRONTIUM Total Elapsed Time: 00:00.1 PHISHING USER DEVICE Browser or Doc Exploit Execution PASS-THE-HASH Exploit NETWORK runs Land on exploit page ENDGAME Redirected to legitimate page Theft of sensitive information, disruption of government.
10 THE WINDOWS 10 DEFENSE STACK PROTECT, DETECT & RESPOND PRE-BREACH POST-BREACH Device protection Threat resistance Identity protection Information protection Breach detection investigation & response Device integrity Health Device attestation control Device Guard Device Control Security policies SmartScreen Windows AppLocker Firewall Microsoft Device Guard Edge Windows Device Defender Guard Windows Network/Firewall Defender Windows Built-in Hello 2FA :) Account Credential lockdown Guard Credential Guard Microsoft Passport Windows Hello :) Device BitLocker protection and / Drive BitLocker encryption to Go Enterprise Windows Data Information Protection Protection Conditional access Windows Conditional Defender Access Windows ATP Defender ATP
11 C A P A B I L I T Y Threat Game change protection with over Windows time and Software as a Services Attackers take advantage of periods Disrupt and between out innovate releases our adversaries by design Protection Gap T I M E P R O D U C T R E L E A S E T H R E A T S O P H I S T I C A T I O N
12 Windows 7 Security features Device protection Threat resistance Identity protection Information protection Breach detection investigation & response PRE-BREACH POST-BREACH
13 Windows 10 Security on Legacy or Modern Devices (Upgraded from Windows 7 or 32-bit Windows 8) Device protection Threat resistance Identity protection Information protection Breach detection investigation & response PRE-BREACH POST-BREACH
14 Windows 10 Security on Modern Devices (Fresh Install or upgraded from 64-bit Windows 8 ) Device protection Threat resistance Identity protection Information protection Breach detection investigation & response PRE-BREACH POST-BREACH
15 THE WINDOWS 10 DEFENSE STACK PROTECT, DETECT & RESPOND PRE-BREACH POST-BREACH Device protection Threat resistance Identity protection Information protection Breach detection investigation & response Device integrity Health Device attestation control Device Guard Device Control Security policies SmartScreen Windows Firewall Microsoft Edge Device Guard Windows Defender Windows Hello :) Credential Guard BitLocker and BitLocker to Go Windows Information Protection Conditional Access Windows Defender ATP
16 DEV ICE PROTECTION SECURE ROOTS OF TRUST Device integrity Cryptographic processing Biometrics sensors Virtualization
17 TRADITIONAL PL ATFORM STACK Apps Windows Platform Services Kernel Device Hardware
18 Trustlet #1 Trustlet #2 Trustlet #3 VIRTUALIZATION BASED SECURITY WINDOWS 10 Apps Windows Platform Services Kernel Windows Operating System Kernel System Container Hyper-V Hyper-V Device Hardware Hypervisor
19 VIRTUALIZATION BASED SECURITY THE FUTURE Apps Windows Platform Services Windows Platform Services Critical System Processes Kernel AppContainer Kernel Windows Operating System Kernel SystemContainer Hyper-V Hyper-V Device Hardware Hypervisor
20 THE WINDOWS 10 DEFENSE STACK PROTECT, DETECT & RESPOND PRE-BREACH POST-BREACH Device protection Threat resistance Identity protection Information protection Breach detection investigation & response Device integrity Device control SmartScreen Windows Firewall Microsoft Edge Device Guard Windows Defender Windows Hello :) Credential Guard BitLocker and BitLocker to Go Windows Information Protection Conditional Access Windows Defender ATP
21 T RADIT IONAL APPROACH Type of threats to consider and mitigate Device Tampering Vulnerabilities Malware Phishing
22 COMPREHENSIVE THREAT RESISTENCE Office ATP SmartScreen Windows Firewall External Internal Microsoft Edge Windows Defender Device Guard
23 Windows 10 PROTECT FROM THE EDGE Protect devices before they encounter threats
24 PROACTIVE THREAT IDENTIFICATION AND PROTECTION Microsoft SmartScreen Phishing and malware filtering technology for Microsoft Edge and Internet Explorer 11 in Windows 10. Provides protection from drive-by attacks. Cloud service is continuously updated, nothing for you to deploy. Exchange Online Advanced Threat Protection Cloud-based filtering service helps protect against unknown malware and viruses. URL trace technology examines potentially harmful links.
25 Windows 10 PROTECT FROM WITHIN Operating system used defense in depth to address threats that get inside the perimeter
26 MICROSOFT EDGE: DESIGNED FOR SECUR E BR OWSING Microsoft Edge is the most secure browser Microsoft has ever shipped Tactics Objective Strategy Eliminate vulnerabilities before attackers can find them Keep our customers safe when browsing the web Make it difficult and costly for attackers to find and exploit vulnerabilities in Microsoft Edge Break exploitation techniques used by attackers Contain the damage when vulnerabilities are discovered Prevent navigation to known exploit sites
27 MICROSOFT EDGE: BUILDING A SAFER BROWSER Fundamentally improve security and enable users to confidently experience the web when using Windows 10 www DEFEND USERS New DEFEND THE BROWSER (SmartScreen) (Universal Windows Platform) (Microsoft Passport and Windows Hello) (Windows Address Space Layout Randomization on 64-bit systems) (MemGC) (Cert. Reputation, EdgeHTML, W3C Content Security Policy, HTTP Strict Transport Security) (Control Flow Guard)
28 MICROSOFT EDGE SECUR ITY IMPR OV EMENTS Microsoft Edge and Flash no longer have full access to win32k.sys API calls are filtered Only 40% of interfaces are available to Flash and Edge reducing attack surface Flash player moves into its own AppContainer Working directly with Adobe to harden Flash player to be resistant to vulnerability exploits Before Full access to Win32.sys Microsoft Edge Browser Windows Kernel Edge Content Process Win32k.sys Flash Host Process Today 60% less surface area of attack on a highly targeted library Microsoft Edge Browser Windows Kernel Edge Content Process Allowed Win32k.sys interfaces Flash Host Process Blocked Win32k.sys interfaces
29 MICROSOF T EDGE Hardware based isolation enables the most secure browsing experience Windows Defender Application Guard protects the device from advanced attacks launched against Microsoft Edge Malware and vulnerability exploits targeting the browser, including zero days, are unable to impact the operating system, apps, data and network Application Guard uses virtualization based security to hardware isolate to isolate Microsoft Edge and any browsing activity away from the rest of the system Closing Microsoft Edge wipes all traces of attacks that may been encountered while online
30 HARDWARE ISOLATION WITH WINDOWS DEFENDER APPLICATION GUARD Microsoft Edge Apps Windows Platform Services Windows Platform Services Critical System Processes Kernel Windows Defender Application Guard Container Kernel Windows Operating System Kernel System Container Hyper-V Hyper-V Device Hardware Hypervisor
31
32 TODAY S CHALLENGE: APPS
33 YOUR SECURITY DEPENDS ON A PL ATFORM WHERE: APPS MUST EARN TRUST BEFORE USE
34 Windows 10 NEXT GENERATION APP CONTROL Secure your devices with Device Guard
35 DEVICE GUARD Hardware Rooted App Control Windows desktop can be locked down to only run trusted apps, just like many mobile OS s (e.g.: Windows Phone) Untrusted apps and executables, such as malware, are unable to run Signed policy secures configuration from tampering Protects system core (kernel mode) and drivers from zero days and vulnerabilities Requires Windows 8 certified or greater hardware with VT-X and VT-D
36 DEVICE GUARD Trustlet #2 Trustlet #3 DEVICE GUARD IN VBS ENVIRONMENT DECISIVE MITIGATION Apps Windows Platform Services Kernel Windows Operating System Kernel SystemContainer Hyper-V Hyper-V Device Hardware Hypervisor
37
38 WINDOWS DEFENDER ANTI-VIRUS PROTECTION Protection that competes to win Scored 98.1% detection rating from AV Comparatives testing against top competitors (March 2016). Behavior and cloud-powered malware detection Can detect fast changing malware varietals using behavior monitoring and cloud-powered protection that expedites signature delivery Tamper Resistant Windows Trusted Boot and platform isolation protect Windows Defender from attacks and enable it to self-repair Built into Windows and Always Up-To-Date No additional deployment & Infrastructure. Continuously up-todate, lower costs Microsoft Protection Stars AVTest
39 THE WINDOWS 10 DEFENSE STACK PROTECT, DETECT & RESPOND PRE-BREACH POST-BREACH Device protection Threat resistance Identity protection Information protection Breach detection investigation & response Device integrity Device control SmartScreen Windows Firewall Microsoft Edge Device Guard Windows Defender Windows Hello :) Credential Guard BitLocker and BitLocker to Go Windows Information Protection Conditional Access Windows Defender ATP
40 WINDOWS 10 IDENTITY GOA LS Mainstream two-factor authentication Make credentials theft resistant and breach and phish proof Deliver solution to both consumer and business users Provide a solution that works in all scenarios and industries
41 Windows 10 USER IDENTITY & AUTHENTICATION
42 SHARED SECRETS Easily mishandled or lost (Hint: The user is the problem) shhh!
43 Complex, costly, and under attack PKI SOLUTIONS
44 ENTER PR ISE DEMANDS Reduce costs Simplify implementation
45 WINDOWS H ELLO FOR BUSINESS Device-Based Multi-Factor USER CREDENTIAL UTILIZE FAMILIAR DEVICES An asymmetrical key pair Provisioned via PKI or created locally via Windows 10 SECURED BY HARDWARE
46 Example board level members FIDO ALLIANCE
47 BIOMETRIC MODA LITIES Improved security Fingerprint and facial recognition Ease of use Impossible to forget VBS support
48 COMPA NION DEV ICE AUTHENTICATION WINDOWS HELLO COMPANION DEVICE FRAMEWORK Phone Band 2 USB RFID Phone Wearable USB Card
49 COMPANION DEVICE SCENARIOS Companion as second factor Credentials are mobile and remain on companion Increase convenience and improve security. Adds additional security by storing creds off of the device. Helps with compliance and convenience.
50
51 Windows 10 DERIVED CREDENTIALS & ACCESS TOKENS
52 PASS THE HASH ATTACKS Today s security challenge
53 TODAY S SECURITY CHALLENGE: PASS THE HASH AT TACKS Access to one device can lead to access to many 1. Single IT Pro s machine is compromised IT Pro manages kiosks/shared devices on network Attacker steals IT Pro s access token 2. Using IT Pros access token attacker looks for kiosk/shared devices and mines them for tokens 3. Repeat
54 Credential Guard Trustlet #2 Trustlet #3 TODAY S SOLUTION: CREDENTIAL GUARD Pass the Hash (PtH) attacks are the #1 go-to tool for hackers. Used in nearly every major breach and APT type of attack Apps Credential Guard uses VBS to isolate Windows authentication from Windows operating system Windows Platform Services Protects LSA Service (LSASS) and derived credentials (NTLM Hash) Fundamentally breaks derived credential theft using MimiKatz, Kernel Windows Operating System Hyper-V Hyper-V Kernel SystemContainer Device Hardware Hypervisor
55
56 THE WINDOWS 10 DEFENSE STACK PROTECT, DETECT & RESPOND PRE-BREACH POST-BREACH Device protection Threat resistance Identity protection Information protection Breach detection investigation & response Device integrity Device control SmartScreen Windows Firewall Microsoft Edge Device Guard Windows Defender Windows Hello :) Credential Guard BitLocker and BitLocker to Go Windows Information Protection Conditional Access Windows Defender ATP
57 YOUR INFORMATION PR OTECTION NEEDS DEVICE PROTECTION DATA SEPARATION LEAK PROTECTION SHARING PROTECTION BitLocker enhancements Protect system and in Windows data when 8.1 device is lost or stolen InstantGo 3 rd party adoption Containment Data separation Prevent unauthorized users and apps from accessing and leaking data Protect data when shared with others, or shared outside of organizational devices and control
58 INFORMATION PR OTECTION NEEDS DEVICE PROTECTION DATA SEPARATION LEAK PROTECTION SHARING PROTECTION BitLocker enhancements in Windows 8.1 InstantGo 3 rd party BitLocker adoption Windows Information Protection Azure Rights Management Office 365
59 Windows 10 DATA-AT-REST PROTECTION The threat of lost or stolen devices
60 DEVICE ENCRYPTION BitLocker Modern devices may be encrypted outof-box with BitLocker technology Increased global acceptance of TPM TPM pervasive on Windows devices by end 2015 Easiest deployment, leading security, reliability, and performance Single sign-on for modern devices and configurable Windows 7 hardware Enterprise grade management (MBAM) and compliance (FIPS)
61 INFORMATION PR OTECTION NEEDS DEVICE PROTECTION DATA SEPARATION LEAK PROTECTION SHARING PROTECTION Protect system and data when device is lost or stolen Containment Data separation Prevent unauthorized apps from accessing data
62 MA R KET SOLUTIONS FOR DATA LOSS PREVENTION Mobile Platforms Desktop Platforms Using Containers Limited Platform Integration Compromised user experience Better user experience Ease of deployment Difficult to deploy Lowest cost Higher cost
63 INTRODUCING WINDOWS INFOR MA TION PR OTECTION Integrated protection against accidental data leaks Protects data at rest locally and on removable storage. Ships in the Windows 10 Anniversary Update Common experience across all Windows 10 devices with copy and paste protection. Corporate vs personal data identifiable wherever it rests on the device and can be wiped. Seamless integration into the platform, No mode switching and use any app. Prevents unauthorized apps from accessing business data and users from leaking data via copy and paste protection.
64 WINDOWS INFORMAT ION PROT ECT ION LIFECYCLE
65 INFORMATION PR OTECTION NEEDS DEVICE PROTECTION DATA SEPARATION LEAK PROTECTION SHARING PROTECTION Containment BYOD separation Prevent unauthorized apps from accessing data Protect data when shared with others, or shared outside of organizational devices and control
66 SHARING PR OTECTION Rights Management Services Protect all file types, everywhere they go, cloud, , BYOD, Support for all commonly used devices and systems Windows, OSX, ios, Android Support for B2B and B2B via Azure AD Support for on premise and cloud based scenarios (e.g.: Office 365) Seamless, easy to provision and support for FIPS regulation and compliance
67
68 THE WINDOWS 10 DEFENSE STACK PROTECT, DETECT & RESPOND PRE-BREACH POST-BREACH Device protection Threat resistance Identity protection Information protection Breach detection investigation & response Device integrity Device control SmartScreen Windows Firewall Microsoft Edge Device Guard Windows Defender Windows Hello :) Credential Guard BitLocker and BitLocker to Go Windows Information Protection Conditional Access Windows Defender ATP
69 Windows 10 SECURE YOUR ENVIRONMENT WITH CONDITIONAL ACCESS Keep unhealthy devices out with Intune and Windows Device Health Attestation.
70 UNKNOWN PC HEALTH Important resources Today health is assumed 1 2
71 WINDOWS DEVICE HEALTH AT TESTATION ENABLES: MDMS to gate access based on device integrity and health Important resources 2 1
72 AT TACKS HAPPEN FAST AND ARE HARD TO STOP If an attacker sends an to 100 people in your company 23 people will open it 11 people will open the attachment and six will do it in the first hour.
73 WINDOWS DEFENDER ADVANCED THREAT PROTECTION DETECT ADVANCED ATTACKS AND REMEDIATE BREACHES Built into Windows No additional deployment & Infrastructure. Continuously up-to-date, lower costs. Behavior-based, cloud-powered breach detection Actionable, correlated alerts for known and unknown adversaries. Real-time and historical data. Rich timeline for investigation Easily understand scope of breach. Data pivoting across endpoints. Deep file and URL analysis. Unique threat intelligence knowledge base Unparalleled threat optics provide detailed actor profiles 1st and 3rd party threat intelligence data.
74
75 US DEPARTMENT OF DEFENSE MICROSOFT RECEIVES THE ULTIMATE WINDOWS 10 SECURITY PROOF POINT FROM US DEPARTMENT OF DEFENSE PENTAGON ORDERS WINDOWS 10 TO BE INSTALLED ON ALL 4 MILLION OF ITS PCS
76 ACTIVE TWO-FACTOR HARDWARE DATA THREAT LOSS ROOTED PREVENTION FOR PROTECTION EVERYONE TRUST Secure devices Secured identities Information protection Threat resistance
77 Resources: aka.ms/itinnovation Continue your learning Download the presentation, access online training and demos, try Windows 10 for free. aka.ms/itinnovationresources Build your IT Pro skills Attend the Microsoft Tech Summit.
78
79
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
Consultant since many years. Mainly working with defense and public sector. MCSE on Windows Server 2000 security ;-)
 About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
Enterprise Ransomware Mitigations
 打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
WINDOWS 10 ENTERPRISE New Security Features
 WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
Evolution of Cyber Security. Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa
 Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Pieter Wigleven Windows Technical Specialist
 Pieter Wigleven Windows Technical Specialist HOW DO BREACHES OCCUR? Malware and vulnerabilities are not the only thing to worry about 46% of compromised systems had no malware on them 99.9% of exploited
Pieter Wigleven Windows Technical Specialist HOW DO BREACHES OCCUR? Malware and vulnerabilities are not the only thing to worry about 46% of compromised systems had no malware on them 99.9% of exploited
Hardening the Modern Windows Client Let s NOT break it this time
 Hardening the Modern Windows Client Let s NOT break it this time Raymond P.L. Comvalius Raymond Comvalius IT Infra Architect/Trainer MVP Windows IT Pro Zelfstandig sinds 1998 Agenda History of Hardening
Hardening the Modern Windows Client Let s NOT break it this time Raymond P.L. Comvalius Raymond Comvalius IT Infra Architect/Trainer MVP Windows IT Pro Zelfstandig sinds 1998 Agenda History of Hardening
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Identity & Access Management
 Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
We need a browser that just works with modern web sites and services. I m worried about Internet security threats and the risk to my business
 WHAT WE HEARD FROM YOU We need a browser that just works with modern web sites and services I m worried about Internet security threats and the risk to my business My employees need to be productive when
WHAT WE HEARD FROM YOU We need a browser that just works with modern web sites and services I m worried about Internet security threats and the risk to my business My employees need to be productive when
BDPA Conference Windows 10
 BDPA Conference Windows 10 Tommy Patterson- Sr Technical Evangelist @tommy_patterson Do The you digital have economy what it takes to succeed? Are cybersecurity threats keeping you up at night? Your people
BDPA Conference Windows 10 Tommy Patterson- Sr Technical Evangelist @tommy_patterson Do The you digital have economy what it takes to succeed? Are cybersecurity threats keeping you up at night? Your people
Windows 10 Security & Audit
 Windows 10 Security & Audit John Tannahill, CA, CISM, CGEIT, CRISC, CSX-P jtannahi@rogers.com Windows 10 Editions Home Pro Enterprise Education Mobile IoT Editions 1 Windows 10 Builds Windows 10 (initial
Windows 10 Security & Audit John Tannahill, CA, CISM, CGEIT, CRISC, CSX-P jtannahi@rogers.com Windows 10 Editions Home Pro Enterprise Education Mobile IoT Editions 1 Windows 10 Builds Windows 10 (initial
Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering. Key Threats Internet was just growing Mail was on the verge
 Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Bromium: Virtualization-Based Security
 Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION BREACH & ATTACK SIMULATION
 BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
Protect Your Endpoint, Keep Your Business Safe. White Paper. Exosphere, Inc. getexosphere.com
 Protect Your Endpoint, Keep Your Business Safe. White Paper Exosphere, Inc. getexosphere.com White Paper Today s Threat Landscape Cyber attacks today are increasingly sophisticated and widespread, rendering
Protect Your Endpoint, Keep Your Business Safe. White Paper Exosphere, Inc. getexosphere.com White Paper Today s Threat Landscape Cyber attacks today are increasingly sophisticated and widespread, rendering
PLATFORM CONVERGENCE JOURNEY
 Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
Desktop features placemat
 Desktop features placemat Home Pro Enterprise Existing Differentiated Features in Win7 /Win8.1 Domain Join and Group Policy Management Existing Win7 / Win 8.1 Enterprise features Windows 10: Management
Desktop features placemat Home Pro Enterprise Existing Differentiated Features in Win7 /Win8.1 Domain Join and Group Policy Management Existing Win7 / Win 8.1 Enterprise features Windows 10: Management
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Make security part of your client systems refresh
 Make security part of your client systems refresh Safeguard your information with Dell Data Security Solutions while boosting productivity and reducing costs Your organization might have many reasons for
Make security part of your client systems refresh Safeguard your information with Dell Data Security Solutions while boosting productivity and reducing costs Your organization might have many reasons for
9 Years in Consulting. Broad experience in Microsoft Infrastructure solutions. Specialised in Windows 10 & Surface familly
 About 9 Years in Consulting Broad experience in Microsoft Infrastructure solutions Specialised in Windows 10 & Surface familly We know Windows XP Windows 7 wasn t easy It often took between 3-7 years!
About 9 Years in Consulting Broad experience in Microsoft Infrastructure solutions Specialised in Windows 10 & Surface familly We know Windows XP Windows 7 wasn t easy It often took between 3-7 years!
Using Biometric Authentication to Elevate Enterprise Security
 Using Biometric Authentication to Elevate Enterprise Security Biometric authentication in the enterprise? It s just a matter of time Mobile biometric authentication is officially here to stay. Most of
Using Biometric Authentication to Elevate Enterprise Security Biometric authentication in the enterprise? It s just a matter of time Mobile biometric authentication is officially here to stay. Most of
Windows Server Security Guide
 Windows Server Security Guide August 2017 Contents Windows Server 2016 Security Guide... 3 Why is Windows Server 2016 security important?... 3 How does Windows Server 2016 help prevent and detect compromise?...
Windows Server Security Guide August 2017 Contents Windows Server 2016 Security Guide... 3 Why is Windows Server 2016 security important?... 3 How does Windows Server 2016 help prevent and detect compromise?...
CloudSOC and Security.cloud for Microsoft Office 365
 Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
MD-101: Modern Desktop Administrator Part 2
 Days: 5 Description: This five-day course is for Desktop Administrators that deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. As desktops has
Days: 5 Description: This five-day course is for Desktop Administrators that deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. As desktops has
Windows 10 edition. Find out which. is right for you. Core features. Familar, and better than ever Home Pro Enterprise Education Mobile.
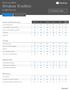 Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
WORKPLACE Data Leak Prevention: Keeping your sensitive out of the public domain. Frans Oudendorp Ronny de Jong
 Data Leak Prevention: Keeping your sensitive out of the public domain Frans Oudendorp Ronny de Jong Session objectives & takeaways Session objectives: Overview of information protection solutions How to
Data Leak Prevention: Keeping your sensitive out of the public domain Frans Oudendorp Ronny de Jong Session objectives & takeaways Session objectives: Overview of information protection solutions How to
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
One Ring to Rule them All
 One Ring to Rule them All A primer on virtualization enhanced security @SimonCrosby Co-founder & CTO Introduction We use micro-virtualization to secure endpoints We serve enterprises and government agencies
One Ring to Rule them All A primer on virtualization enhanced security @SimonCrosby Co-founder & CTO Introduction We use micro-virtualization to secure endpoints We serve enterprises and government agencies
SECURING DEVICES IN THE INTERNET OF THINGS
 SECURING DEVICES IN THE INTERNET OF THINGS WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including
SECURING DEVICES IN THE INTERNET OF THINGS WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including
THE EVOLUTION OF SIEM
 THE EVOLUTION OF SIEM Why it is critical to move beyond logs BUSINESS-DRIVEN SECURITY SOLUTIONS THE EVOLUTION OF SIEM Why it is critical to move beyond logs Despite increasing investments in security,
THE EVOLUTION OF SIEM Why it is critical to move beyond logs BUSINESS-DRIVEN SECURITY SOLUTIONS THE EVOLUTION OF SIEM Why it is critical to move beyond logs Despite increasing investments in security,
BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY
 SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
Windows IoT Security. Jackie Chang Sr. Program Manager
 Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
SECURING DEVICES IN THE INTERNET OF THINGS
 SECURING DEVICES IN THE INTERNET OF THINGS EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including steep financial losses, damage
SECURING DEVICES IN THE INTERNET OF THINGS EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including steep financial losses, damage
Mobile Field Worker Security Advocate Series: Customer Conversation Guide. Research by IDC, 2015
 Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Endpoint Protection : Last line of defense?
 Endpoint Protection : Last line of defense? First TC Noumea, New Caledonia 10 Sept 2018 Independent Information Security Advisor OVERVIEW UNDERSTANDING ENDPOINT SECURITY AND THE BIG PICTURE Rapid development
Endpoint Protection : Last line of defense? First TC Noumea, New Caledonia 10 Sept 2018 Independent Information Security Advisor OVERVIEW UNDERSTANDING ENDPOINT SECURITY AND THE BIG PICTURE Rapid development
Building Resilience in a Digital Enterprise
 Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
GSE/Belux Enterprise Systems Security Meeting
 MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
1
 Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
Symantec Endpoint Protection Family Feature Comparison
 Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Securing the SMB Cloud Generation
 Securing the SMB Cloud Generation Intelligent Protection Against the New Generation of Threats Colin Brackman, National Distribution Manager, Consumer Sales, Symantec Christopher Covert Principal Product
Securing the SMB Cloud Generation Intelligent Protection Against the New Generation of Threats Colin Brackman, National Distribution Manager, Consumer Sales, Symantec Christopher Covert Principal Product
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
Windows 10 Consumer Storybook v1.0_november update_partner-ready
 Windows 10 Consumer Storybook v1.0_november update_partner-ready 2 Empower every person and every organization to achieve more 1 billion Windows 10 devices in 2-3 years 500 million+ Windows 7/8 devices
Windows 10 Consumer Storybook v1.0_november update_partner-ready 2 Empower every person and every organization to achieve more 1 billion Windows 10 devices in 2-3 years 500 million+ Windows 7/8 devices
Securing Privileged Access and the SWIFT Customer Security Controls Framework (CSCF)
 Securing Privileged Access and the SWIFT Customer Security Controls Framework (CSCF) A Guide to Leveraging Privileged Account Security to Assist with SWIFT CSCF Compliance Table of Contents Executive Summary...
Securing Privileged Access and the SWIFT Customer Security Controls Framework (CSCF) A Guide to Leveraging Privileged Account Security to Assist with SWIFT CSCF Compliance Table of Contents Executive Summary...
Managing Microsoft 365 Identity and Access
 Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
PROTECTION SERVICE FOR BUSINESS. Datasheet
 PROTECTION SERVICE FOR BUSINESS Datasheet Protection Service For Business is one of the world s leading multi-endpoint security solutions. It is the only endpoint security solution on the market that combines
PROTECTION SERVICE FOR BUSINESS Datasheet Protection Service For Business is one of the world s leading multi-endpoint security solutions. It is the only endpoint security solution on the market that combines
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches
 Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches Introduction No matter how hard you work to educate your employees about the constant and evolving threats
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches Introduction No matter how hard you work to educate your employees about the constant and evolving threats
IT Security Training MS-500: Microsoft 365 Security Administration. Upcoming Dates. Course Description. Course Outline $2,
 IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
Service. Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution
 Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Windows 10 Pro device opportunity
 Windows 10 Pro device opportunity I m too limited in what I can do and what I can achieve on Chromebook. Corey Weathers, CEO Homegrown Trailers Work more securely Modern PCs can protect against botnets
Windows 10 Pro device opportunity I m too limited in what I can do and what I can achieve on Chromebook. Corey Weathers, CEO Homegrown Trailers Work more securely Modern PCs can protect against botnets
TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION
 INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
Easy Activation Effortless web-based administration that can be activated in as little as one business day - no integration or migration necessary.
 Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Towards Trustworthy Internet of Things for Mission-Critical Applications. Arjmand Samuel, Ph.D. Microsoft Azure - Internet of Things
 Towards Trustworthy Internet of Things for Mission-Critical Applications Arjmand Samuel, Ph.D. Microsoft Azure - Internet of Things Internet of Things is a game changer Organizations are benefiting from
Towards Trustworthy Internet of Things for Mission-Critical Applications Arjmand Samuel, Ph.D. Microsoft Azure - Internet of Things Internet of Things is a game changer Organizations are benefiting from
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Windows in the enterprise
 Windows in the enterprise Enabling flexible workstyles with Windows 8.1 Enterprise Terry Stein Territory Manager anywhere, anytime expectations BYOD goes mainstream enabling mobility critical for success
Windows in the enterprise Enabling flexible workstyles with Windows 8.1 Enterprise Terry Stein Territory Manager anywhere, anytime expectations BYOD goes mainstream enabling mobility critical for success
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
12/5/2013. work-life blur. more mobile. digital generation. multiple devices. tech. fast savvy
 1 work-life blur more mobile digital generation multiple devices CONSUMERIZATION tech fast savvy VIRTUALIZATION CLOUD paced 2 By Avanade Global Research Study 2013 2 3 Embracing the consumerization of
1 work-life blur more mobile digital generation multiple devices CONSUMERIZATION tech fast savvy VIRTUALIZATION CLOUD paced 2 By Avanade Global Research Study 2013 2 3 Embracing the consumerization of
ISO COMPLIANCE GUIDE. How Rapid7 Can Help You Achieve Compliance with ISO 27002
 ISO 27002 COMPLIANCE GUIDE How Rapid7 Can Help You Achieve Compliance with ISO 27002 A CONTENTS Introduction 2 Detailed Controls Mapping 3 About Rapid7 8 rapid7.com ISO 27002 Compliance Guide 1 INTRODUCTION
ISO 27002 COMPLIANCE GUIDE How Rapid7 Can Help You Achieve Compliance with ISO 27002 A CONTENTS Introduction 2 Detailed Controls Mapping 3 About Rapid7 8 rapid7.com ISO 27002 Compliance Guide 1 INTRODUCTION
Windows ierīces Enterprise infrastruktūrā. Aris Dzērvāns Microsoft
 Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
McAfee Advanced Threat Defense
 Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
A NEW MODEL FOR AUTHENTICATION
 All Rights Reserved. FIDO Alliance. Copyright 2016. A NEW MODEL FOR AUTHENTICATION ENABLING MORE EFFICIENT DIGITAL SERVICE DELIVERY Jeremy Grant jeremy.grant@chertoffgroup.com Confidential 5 The world
All Rights Reserved. FIDO Alliance. Copyright 2016. A NEW MODEL FOR AUTHENTICATION ENABLING MORE EFFICIENT DIGITAL SERVICE DELIVERY Jeremy Grant jeremy.grant@chertoffgroup.com Confidential 5 The world
Windows 10 Pro for Your Modern Workforce. Jared Bernatt Microsoft Windows
 Windows 10 Pro for Your Modern Workforce Jared Bernatt Microsoft Windows Agenda Windows 10 Pro means business The most comprehensive security for your business Best-in-class management that grows with
Windows 10 Pro for Your Modern Workforce Jared Bernatt Microsoft Windows Agenda Windows 10 Pro means business The most comprehensive security for your business Best-in-class management that grows with
Beginning your General Data Protection Regulation (GDPR) Journey. Accelerate GDPR compliance with Windows 10
 Beginning your General Data Protection Regulation (GDPR) Journey Accelerate GDPR compliance with Windows 10 Table of Contents Disclaimer... 2 Introduction... 3 The GDPR and Its Implications... 3 Personal
Beginning your General Data Protection Regulation (GDPR) Journey Accelerate GDPR compliance with Windows 10 Table of Contents Disclaimer... 2 Introduction... 3 The GDPR and Its Implications... 3 Personal
Secure access to your enterprise. Enforce risk-based conditional access in real time
 Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
How to Identify Advanced Persistent, Targeted Malware Threats with Multidimensional Analysis
 White paper How to Identify Advanced Persistent, Targeted Malware Threats with Multidimensional Analysis AhnLab, Inc. Table of Contents Introduction... 1 Multidimensional Analysis... 1 Cloud-based Analysis...
White paper How to Identify Advanced Persistent, Targeted Malware Threats with Multidimensional Analysis AhnLab, Inc. Table of Contents Introduction... 1 Multidimensional Analysis... 1 Cloud-based Analysis...
BUFFERZONE Advanced Endpoint Security
 BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
BUFFERZONE Advanced Endpoint Security
 BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
Designing an Adaptive Defense Security Architecture. George Chiorescu FireEye
 Designing an Adaptive Defense Security Architecture George Chiorescu FireEye Designing an Adaptive Security Architecture Key Challanges Existing blocking and prevention capabilities are insufficient to
Designing an Adaptive Defense Security Architecture George Chiorescu FireEye Designing an Adaptive Security Architecture Key Challanges Existing blocking and prevention capabilities are insufficient to
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM
 SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
10 FOCUS AREAS FOR BREACH PREVENTION
 10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
Securing Your Amazon Web Services Virtual Networks
 Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
HP Fortify Software Security Center
 HP Fortify Software Security Center Proactively Eliminate Risk in Software Trust Your Software 92% of exploitable vulnerabilities are in software National Institute for Standards and Technology (NIST)
HP Fortify Software Security Center Proactively Eliminate Risk in Software Trust Your Software 92% of exploitable vulnerabilities are in software National Institute for Standards and Technology (NIST)
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
Streaming Prevention in Cb Defense. Stop malware and non-malware attacks that bypass machine-learning AV and traditional AV
 Streaming Prevention in Cb Defense Stop malware and non-malware attacks that bypass machine-learning AV and traditional AV 2 STREAMING PREVENTION IN Cb DEFENSE OVERVIEW Over the past three years, cyberattackers
Streaming Prevention in Cb Defense Stop malware and non-malware attacks that bypass machine-learning AV and traditional AV 2 STREAMING PREVENTION IN Cb DEFENSE OVERVIEW Over the past three years, cyberattackers
Agenda. Why we need a new approach to endpoint security. Introducing Sophos Intercept X. Demonstration / Feature Walk Through. Deployment Options
 Agenda Why we need a new approach to endpoint security Introducing Sophos Intercept X Demonstration / Feature Walk Through Deployment Options Q & A 2 Endpoint Security has reached a Tipping Point Attacks
Agenda Why we need a new approach to endpoint security Introducing Sophos Intercept X Demonstration / Feature Walk Through Deployment Options Q & A 2 Endpoint Security has reached a Tipping Point Attacks
The Top 6 WAF Essentials to Achieve Application Security Efficacy
 The Top 6 WAF Essentials to Achieve Application Security Efficacy Introduction One of the biggest challenges IT and security leaders face today is reducing business risk while ensuring ease of use and
The Top 6 WAF Essentials to Achieve Application Security Efficacy Introduction One of the biggest challenges IT and security leaders face today is reducing business risk while ensuring ease of use and
Securing Your Microsoft Azure Virtual Networks
 Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
We b Ap p A t ac ks. U ser / Iden tity. P hysi ca l 11% Other (VPN, PoS,infra.)
 We b Ap p A t ac ks U ser / Iden tity 33% 53% Apps And Identities Initial Targets In 86% Of Breaches P hysi ca l 11% Other (VPN, PoS,infra.) 3% Fix vulnerabilities Stop web attacks Risk & compliance What
We b Ap p A t ac ks U ser / Iden tity 33% 53% Apps And Identities Initial Targets In 86% Of Breaches P hysi ca l 11% Other (VPN, PoS,infra.) 3% Fix vulnerabilities Stop web attacks Risk & compliance What
Windows 10 and the Enterprise. Craig A. Brown Prepared for: GMIS
 Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Securing Devices in the Internet of Things
 AN INTEL COMPANY Securing Devices in the Internet of Things WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe
AN INTEL COMPANY Securing Devices in the Internet of Things WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe
Securing Wireless Mobile Devices. Lamaris Davis. East Carolina University 11/15/2013
 Securing Wireless Mobile Devices Lamaris Davis East Carolina University 11/15/2013 Attract As more employees prefer to use mobile devices in the workplace, organizations are starting to adopt the Bring
Securing Wireless Mobile Devices Lamaris Davis East Carolina University 11/15/2013 Attract As more employees prefer to use mobile devices in the workplace, organizations are starting to adopt the Bring
The security challenge in a mobile world
 The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
Securing Your Most Sensitive Data
 Software-Defined Access Securing Your Most Sensitive Data Company Overview Digital Growth Means Digital Threats Digital technologies offer organizations unprecedented opportunities to innovate their way
Software-Defined Access Securing Your Most Sensitive Data Company Overview Digital Growth Means Digital Threats Digital technologies offer organizations unprecedented opportunities to innovate their way
Compliance series Building secure endpoints with Windows 10 and Defendpoint
 Compliance series Building secure endpoints with Windows 10 and Defendpoint avecto.com Introduction to Windows 10 Windows 10 heralds a new era in computing as Microsoft promise to renew focus on the enterprise
Compliance series Building secure endpoints with Windows 10 and Defendpoint avecto.com Introduction to Windows 10 Windows 10 heralds a new era in computing as Microsoft promise to renew focus on the enterprise
Transforming Security Part 2: From the Device to the Data Center
 SESSION ID: SP01-R11 Transforming Security Part 2: From the Device to the Data Center John Britton Director, EUC Security VMware @RandomDevice The datacenter as a hospital 3 4 5 Digital transformation
SESSION ID: SP01-R11 Transforming Security Part 2: From the Device to the Data Center John Britton Director, EUC Security VMware @RandomDevice The datacenter as a hospital 3 4 5 Digital transformation
PEOPLE CENTRIC SECURITY THE NEW
 PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft Finland. Microsoft in Finland is a strong millennial, born ,000+ partners generating 8 $ revenue per each $ by MSFT
 Microsoft Finland Microsoft in Finland is a strong millennial, born 1992 2+ million active users in Microsoft Office 365 cloud 2,000+ partners generating 8 $ revenue per each $ by MSFT Partner ecosystem
Microsoft Finland Microsoft in Finland is a strong millennial, born 1992 2+ million active users in Microsoft Office 365 cloud 2,000+ partners generating 8 $ revenue per each $ by MSFT Partner ecosystem
Managed Endpoint Defense
 DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
June 2 nd, 2016 Security Awareness
 June 2 nd, 2016 Security Awareness Security is the degree of resistance to, or protection from, harm. if security breaks down, technology breaks down Protecting People, Property and Business Assets Goal
June 2 nd, 2016 Security Awareness Security is the degree of resistance to, or protection from, harm. if security breaks down, technology breaks down Protecting People, Property and Business Assets Goal
Securing Dynamic Data Centers. Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan &
 Securing Dynamic Data Centers Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan & Afghanistan @WajahatRajab Modern Challenges By 2020, 60% of Digital Businesses will suffer Major Service
Securing Dynamic Data Centers Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan & Afghanistan @WajahatRajab Modern Challenges By 2020, 60% of Digital Businesses will suffer Major Service
Mobility Windows 10 Bootcamp
 Mobility Windows 10 Bootcamp Length: 8 days Format: Bootcamp Time: Day About This Course This boot camp is designed to provide students with the knowledge and skills required to install and configure Windows
Mobility Windows 10 Bootcamp Length: 8 days Format: Bootcamp Time: Day About This Course This boot camp is designed to provide students with the knowledge and skills required to install and configure Windows
MESSAGING SECURITY GATEWAY. Solution overview
 MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
Windows 10 IoT Core Azure Connectivity and Security
 Windows 10 IoT Core Azure Connectivity and Security Published July 27, 2016 Version 1.0 Table of Contents Introduction... 2 Device identities... 2 Building security into the platform... 3 Security as a
Windows 10 IoT Core Azure Connectivity and Security Published July 27, 2016 Version 1.0 Table of Contents Introduction... 2 Device identities... 2 Building security into the platform... 3 Security as a
SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP)
 SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP) Adaptive Cybersecurity at the Speed of Your Business Attackers Evolve. Risk is in Constant Fluctuation. Security is a Never-ending Cycle.
SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP) Adaptive Cybersecurity at the Speed of Your Business Attackers Evolve. Risk is in Constant Fluctuation. Security is a Never-ending Cycle.
The Mobile Risk Management Company. Overview of Fixmo and Mobile Risk Management (MRM) Solutions
 The Mobile Risk Management Company Overview of Fixmo and Mobile Risk Management (MRM) Solutions Company Proprietary Information Copyright Fixmo Inc., 2012 Introduction to Fixmo Founded on a simple idea:
The Mobile Risk Management Company Overview of Fixmo and Mobile Risk Management (MRM) Solutions Company Proprietary Information Copyright Fixmo Inc., 2012 Introduction to Fixmo Founded on a simple idea:
