LifeGuard for Android FREQUENTLY ASKED QUESTIONS TABLE OF CONTENTS
|
|
|
- Justina Griffin
- 5 years ago
- Views:
Transcription
1 TABLE OF CONTENTS 1. What is LifeGuard TM for Android TM (LG)? Why LG now? What is the potential impact of mobile attacks to enterprise customers? Are mobile vulnerabilities on the rise? What are OS security updates? What is the difference between LifeGuard and Mx? Under LG, how long will Zebra provide security updates? Can end of sale dates shift? Are all Zebra Android products covered under LG (see matrix)? Does Zebra guarantee my device is secure if I am up to date? What is a CVE? What types of attacks are we working to prevent? What is an Android Security Bulletin? What is a patch level? How long does Google provide Security support for Android? How does LG OTP help customers maintain security during an OS transition? Does LG support change during product/os life cycle? (L1, L2, L3) How much does LG Cost? Can I add support to a pre-existing portfolio not already covered under a service plan? Can I extend LG support? How much does it cost? How do I procure? Can I purchase a one (1) year extension at any time? What do consumer companies offer for security updates? Where do I find security updates? How are security patches installed on a device? Local? EMM OTA? How large are typical security updates?... 8 FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 1
2 26. Can I reverse/rollback a patch? How do I tell what security updates have been loaded on my device? Are security updates always separate from other Maintenance Releases? Are security updates cumulative? Do security updates come with release notes? Can I be notified when a patch is available for my platform? Do I have to be on the latest maintenance release to install an update? How long will it take Zebra to release a security update after a security bulletin? Does Zebra advise customers to install all updates? Are Zebra updates ever covertly pushed to devices? Does Zebra provide security patches for GMS? What about Zero day attacks? After Google ends support, how does Zebra determine what to patch? After Google ends support for an OS release, does Zebra guarantee that all vulnerabilities are patched? Do I need LifeGuard for PCI compliance? What is the life cycle of GMS Updates? What is the life cycle for EMM Updates? Does LifeGuard provide security updates for GMS? Can customers still obtail a locked-down image via a custom products request? What if a customer detects a vulnerability? What is the Zebra URL to access the LifeGuard Security updates?.11 FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 2
3 This FAQ is designed for Zebra partners and end-customers. It is designed to provide end-customers an overview of Zebra s. Please note that Lifeguard for Android security updates are classified by Zebra as restricted software. As such, they are governed by Zebra s restricted software End User License Agreement (EULA) which means the security software updates can only be downloaded to entitled Zebra devices. Entitled Zebra devices include those devices which are still within the first 90 days (warranty entitlement) or protected by a Zebra OneCareTM Support Services agreement. For additional information, contact your local Zebra representative. 1. WHAT IS LIFEGUARD FOR ANDROID (LG)? LG represents an Operating System (OS) security support model for Zebra Android products. LG provides Zebra customers three security value propositions; 1) Extended availability of OS security updates/patches 2) Security support during OS transitions (referred to as an OS Transition Period ) 3) Periodic security patches as frequent as every 30 days. Note that one-year security support extensions are available at an additional fee. Life Guard is unique in that it caters specifically to enterprise customers. Extending the security life, extends the device service life, which ultimately reduces TCO (Total Cost of Ownership). Consumer device manufacturers are working diligently to do the exact opposite, i.e. keep support windows short to increase refresh rates and sell more devices. 2. WHY LG NOW? In 2016 Android & IOS comprised over 99% of the Worldwide mobile OS market share. Though such large-scale adoption brings many benefits, it also creates lucrative targets for hackers. Thus, now more than ever enterprise customers must be more prescriptive and diligent with respect to security maintenance of their mobile operating system. As highlighted in a recent Homeland Security (April 2017) report ( Study on Mobile Security ) on enterprise security best practices: 1). The most important defense against mobile device security threats is to ensure devices are patched against the publicly known security vulnerabilities 2). When making procurement decisions, enterprises should seek clear commitment from device vendors or mobile carriers that security updates will be provided in a timely manner 3). When a device model is no longer supported with updates, enterprises should decommission those devices FINAL.pdf 3. WHAT IS THE POTENTIAL IMPACT OF MOBILE ATTACKS TO ENTERPRISE CUSTOMERS? It s hard to put an exact dollar amount on mobile attacks, but in general customers should be concerned with; Disruption of Business, Loss of Productivity, Loss of Privacy, Theft of Information, Legal Liability, Brand/Reputation Damage. It is critical that customers understand the scope of these attacks. A 2016 attack called DressCode enabled a compromised mobile device to be used as a gateway to corporate back-end servers. Thus, even if customers are not storing significant sensitive data on the mobile device, they should still be diligent with security updates. FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 3
4 4. ARE MOBILE VULNERABILITIES ON THE RISE? Yes, vulnerabilities have risen with increased mobile device functionality, connectivity, and software supply chain contributors. CVE details ( estimates that Android vulnerabilities in 2016 rose over 400% year-over-year. Recognize that a vulnerability is not the same as an attack. Many headline vulnerabilities (e.g. Stage fright) were never actually detected on any devices outside of a research lab. 5. WHAT ARE OS SECURITY UPDATES? The terms Security Updates & Security patches are used synonymously. These are software updates specifically to fortify the underlying Android OS and device specifics from known vulnerabilities. 6. WHAT IS THE DIFFERENCE BETWEEN LIFEGUARD AND MX? Mx (Mobile extensions) represents Zebra extensions made to standard Android to enhance management and security. These extensions are made available to EMMs, developers (via Zebra EMDK), and Zebra utilities (e.g. StageNow). Some of the Mx features enable disabling or locking down unused device features which mitigates or blocks threats. In contrast, LifeGuard is relegated to security life cycle management and security updates. The updates in LG remediate threats. That is, it patches vulnerabilities in the core operating system. 7. UNDER LG, HOW LONG WILL ZEBRA PROVIDE SECURITY UPDATES? Security updates under LG is based on the device life cycle. Under LG, security patches are made available for 2 years past the device end-of-sale (EoS). Note that past OS releases for a given product are generally not supported except as defined under an OS Transition Policy (OTP), which is covered later in this FAQ. 8. CAN END OF SALE DATES SHIFT? Yes. Zebra typically targets products as available for sale as either 3, 4, or 5 years depending on the type of product. End-of-sale dates may fluctuate based on market conditions and component availability. Zebra works diligently during component selection to align with the planned life cycle, but we cannot make any guarantees. 9. ARE ALL ZEBRA ANDROID PRODUCTS COVERED UNDER LG? No. In general, recently introduced products include LG support. LG for TC20/TC25 products will be slightly delayed from initial launch, starting in March Legacy products may either have LG support or some lesser security support profile. Please contact your Zebra representative for the exact level of support for the product of interest. 10. DOES ZEBRA GUARANTEE MY DEVICE IS SECURE IF I AM UP TO DATE? No. It is often said that security is a journey with no end destination. Security updates are one element in a defense in depth security model. That is, a model that provides multiple levels of protection. Customers should install the latest security updates, and leverage standard Android & Zebra Mx features for added protection. FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 4
5 11. WHAT IS A CVE? CVE s ( Common Vulnerability Exposure ) represent security vulnerabilities. All CVE instances have a unique identifier. A database of CVE s can be found at: Customers can obtain details of a specific CVE through a simple database search. 12. WHAT TYPE OF ATTACKS ARE WE WORKING TO PREVENT? There are many types of attacks. Some common attacks include; remote code execution, application privilege escalation (permitting application access to resources it should not), disclosure of information on the device, and denial of service attacks. Note that most recent attacks have not been by exploiting OS vulnerabilities, but rather social networking (e.g. phishing). 13. WHAT IS AN ANDROID SECURITY BULLETIN? Each month (generally early in the month) Google publishes an Android Security Bulletin. Bulletins are labeled by the month in which they were released (January, February ). Google OEM device suppliers (e.g. Zebra) are provided access to the bulletins 30 days prior to the public release. With this notification Google includes patch samples which then must be integrated accordingly into each respective platform. Bulletins include a list of recently discovered Android CVE s along with their respective severity level (e.g. Low to Critical). In 2016 Google addressed a total 655 vulnerabilities (an average of over 50 per month). 133 of these vulnerabilities were ranked as severe (~11/month on average). Note that not all CVE s are relevant to all Android products (some are dependent on specific hardware vendors/components). A description of what constitutes a specific CVE severity rating can be found at: Published Android Security Bulletins can be found at: WHAT IS A PATCH LEVEL? Applying the updates associated with each bulletin will set the Patch Level as indicated in the Bulletin. This same information is in an individual product s release notes. The Patch Level provides two dates. The first date is your device s most recent full security update. The second date is date your device last received Critical Only updates. EXAMPLE: Patch Level Critical The example illustrates that the device was last fully patched in May of 2016 and started receiving critical patches. The last date that Critical patches were applied was December 1, You can find the patch level on a device by going into Settings >> About Phone 15. HOW LONG DOES GOOGLE PROVIDE SECURITY SUPPORT FOR ANDROID? Google does not have a standard security support policy, but typical security support has been for 36 months after an OS release has gone open source. For example; Lollipop 5.0 (API 21) went open source in Dec 2014 and Google Security support will end on Nov FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 5
6 16. HOW DOES LG OTP HELP CUSTOMERS MAINTAIN SECURITY DURING AN OS TRANSITION? Under LG, when Zebra releases a new OS version (desert release) for a product, we continue to support the earlier version for a period of 12 months. This is referred to as an OS Transition Period (OTP). During OTP, customers receive quarterly (exact cadence may fluctuate slightly) updates with a minimum coverage for all critical severity CVE s. 17. DOES LG SUPPORT CHANGE DURING PRODUCT/OS LIFE CYCLE (L1, L2, L3)? LG has three support levels; L1, L2, L3. Except where explicitly stated, the scope of all support levels is the Google Android Security bulletins. L1 is the highest level of support and is provided for the latest OS release for a product during the period in which Google is providing security support. L2 has slightly less support and is provided for an older OS during an OS Transition Period, and for the latest OS during the period after Google stops security support and prior to Zebra end of support (EoS + 2 yrs). L1 - during L1 Zebra provides updates approximately every 30 days. Updates are comprehensive, in that all relevant Android Security Bulletin CVE s regardless of severity level are addressed. L1 support is provided for the latest current OS release on a product during the period in which Google is providing security support updates. L2 - during L2 Zebra provides quarterly updates minimally covering all Android Security Bulletin CVE s posted as critical. L2 support is provided during two periods. The first is during an OS Transition Period (OTP). The second is the period after Google has terminated security support and prior to Zebra s end of security support. L3 - Products not in either L1 or L2 fall into a Zebra discretionary support window (L3), during which Zebra will make a best effort to address major security vulnerabilities. 18. HOW MUCH DOES LG COST? LG is zero cost for customers covered under any of the following Zebra agreements; 1) Zebra Initial Purchase Software Warranty 2) Zebra OneCare Essential 3) Zebra OneCare Select 4) Zebra OneCare TSS (Technical and software support excludes break-fix repair) One-year OS security support extensions are available at additional cost. Descriptions of the OneCare options can be found at: CAN I ADD SUPPORT TO A PRE-EXISTING PORTFOLIO NOT ALREADY COVERED UNDER A SERVICE PLAN? Yes, you can purchase a OneCare service contract inclusive of LG. However, there may be an added service charge depending on the specific device/os platform(s) that you are looking to cover. Please contact your local Zebra representative for additional information. FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 6
7 20. CAN I EXTEND LG SUPPORT? HOW MUCH DOES IT COST? HOW DO I PROCURE? Yes. Zebra offers 1 year OS security support extensions. This allows customers to extend either the end security support date or the OS Transition Period (OTP). For example; under standard LG security support for a 3/3 product is 5 years from first product ship (3+2). By purchasing a one-year extension, a customer can then extend the 5 years by one additional year. Similarly a customer can extend the standard LG OS Transition Period (OTP). Extending an OTP allows the customers added time (i.e. more than 12 months) to transition between OS releases while still getting security updates. The scope of the one-year extension is to a specific product model on a specific OS release (identified within the purchase agreement). Support during the extension period is L2 (Quarterly updates /Critical severity). The agreement only covers security support and does not entitle the customer to general bug fixes or maintenance releases. In some instances, a security patch may be contingent on a bug fix/mr, in which case Zebra will make the necessary bug fix/mr available to the customer. In many instances these security updates may fall outside of the Google Support window. Though an exception condition, certain security vulnerabilities may be systemic; requiring significant changes that would impact the stability and interoperability of the platform of an earlier OS release. In such cases, Zebra cannot guarantee that it will directly remediate every such vulnerability. Therefore, Zebra will provide remediation recommendations, but may not provide a code patch/update for such vulnerabilities. Under the one-year extension agreement, Zebra will provide limited phone support. Often referred to as Level 1 escalation this will be relegated to basic question & answers. Contact your Zebra representative for pricing information. 21. CAN I PURCHASE A ONE (1) YEAR EXTENSION AT ANY TIME? No. A customer can only purchase an extension if the product/os is under existing security support. The extension must be purchased no less than 90 days prior to the end of the customer s existing support contract. Please fill out the LifeGuard OS Extended Service request form available at: WHAT DO CONSUMER COMPANIES OFFER FOR SECURITY UPDATES? Many consumer device providers do not offer a formal security update policy. Google does for their Nexus & Pixel devices. Nexus & Pixel are generally considered the gold standard for consumer grade support. Google provides security support for the later of either 36 months from first ship or 18 months past end-of-sale. In general consumer device life cycles are less than 18 months, so typical support is relegated to the 36 months from first ship. In comparison, a Zebra 5/5 product offers 84 months of support. FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 7
8 23. WHERE DO I FIND SECURITY UPDATES? Security updates can be found at: HOW ARE SECURITY PATCHES INSTALLED ON A DEVICE? LOCAL? EMM OTA? Security patches can generally be installed either over USB via ADB, using an external SD card (if supported), or over-the-air (OTA) via an EMM (consult Zebra for validated EMMs). 25. HOW LARGE ARE TYPICAL SECURITY UPDATES? Sizes can vary significantly. Security updates bundled with bug fixes and maintenance releases will be larger in size. Typical updates will be 40-50MB. 26. CAN I REVERSE/ROLLBACK A PATCH? Yes. In the atypical situation where you have to reverse a patch, you can do so by either installing an earlier patch level or issuing a factory reset. 27. HOW DO I TELL WHAT SECURITY UPDATES HAVE BEEN LOADED ON MY DEVICE? The Patch Level provides the date the last monthly and quarterly critical only updates. 28. ARE SECURITY UPDATES ALWAYS SEPARATE FROM OTHER MAINTENANCE RELEASES? No. Security updates may be either separate or bundled with bug fixes and maintenance releases 29. ARE SECURITY UPDATES CUMULATIVE? Yes. If you opted to forego loading some earlier update, loading a newer update will load the previous and current updates. 30. DO SECURITY UPDATES COME WITH RELEASE NOTES? Yes. Release notes are posted with the security update. 31. CAN I BE NOTIFIED WHEN A PATCH IS AVAILABLE FOR MY PLATFORM? Yes. You can subscribe for notifications at: DO I HAVE TO BE ON THE LATEST MAINTENANCE RELASE TO INSTALL AN UPDATE***? Yes. Zebra cannot validate security on all incremental maintenance releases, therefore, you must be on the latest maintenance release prior to loading the security update. FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 8
9 33. HOW LONG WILL IT TAKE ZEBRA TO RELEASE A SECURITY UPDATE AFTER A SECURITY BULLETIN? Zebra s goal is to be within 2-3 days of the public Android security bulletin. However, many updates vary in complexity and scope, and have dependencies on third party code that must be obtained by Zebra. Thus, security updates may vary depending on the region, product model, and third-party software suppliers. Additionally, releases for WAN (cellular) devices may lag other release due to additional testing and/or carrier certification. Carrier certifications can vary from 2 wks to 6 wks depending on the specific carrier and the extent of required testing. Note also that an update may be a combination of a maintenance release and a security update. Finally, because of the lag time in carrier certification it is possible that a carrier certified update may actually have a security patch level earlier than a prior release. Thus, when loading a new, major, carrier certified update, customers should check the patch level and if necessary load the necessary patches. 34. DOES ZEBRA ADVISE CUSTOMERS TO INSTALL ALL UPDATES? Zebra does advise customers to install all updates in a timely manner. However, we appreciate that all software updates carry some degree of functional risk. Customers operating in a peak season (and a potential code lockdown) may want to assess the individual CVE s being addressed in a release. Customers may already be using techniques that mitigate many these CVEs (e.g. application white listing, enterprise home screen, lock task mode). Though updates will provide an added level of defense (defense in depth) customers should make an informed decision. 35. ARE ZEBRA UPDATES EVER COVERTLY PUSHED TO DEVICES? No. In contrast to other platforms (e.g. IOS), Zebra does not push updates either overtly (e.g. user receives a message asking to accept update) or covertly directly to devices. 36. DOES ZEBRA PROVIDE SECURITY PATCHES FOR GMS? No. Zebra devices are either AOSP or GMS. Technically Google Mobile Services (GMS) sits above AOSP. In contrast to AOSP which is open source, GMS is closed binary, owned by Google. GMS updates (including security enhancements) are provided by Google. GMS updates come from the Google Play Store and typically requires a Google account (Managed Account or Google Account) be present on the device (note: Google has the right to push an update without an account). 37. WHAT ABOUT ZERO-DAY ATTACKS? Occasionally a major attack instantly surfaces. These attacks cannot be predicted and it is difficult to predict a response time. Zebra does however monitor for such attacks and has responded in real time in the past. 38. AFTER GOOGLE ENDS SUPPORT, HOW DOES ZEBRA DETERMINE WHAT TO PUSH? The principal source for Zebra updates are the Android security bulletins. This is true both during Google support for an OS release and after Google ends support. Thus, post Google support, Zebra assess each vulnerability and determines how to backport relevant patches (if possible). FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 9
10 Note that during this period, certain security vulnerabilities may be systemic; requiring significant changes that would impact the stability and interoperability of the platform of an earlier OS release. In such cases, Zebra cannot guarantee that it will directly remediate every such vulnerability. Therefore, Zebra will provide remediation recommendations, but may not provide a code patch/update for such vulnerabilities. 39. AFTER GOOGLE ENDS SUPPORT FOR AN OS RELEASE, DOES ZEBRA GUARANTEE THAT ALL VULNERABILITIES ARE PATCHED? We do our best, but we cannot guarantee that all vulnerabilities will be patched. After Google has ended security support for an OS release (e.g. a desert OS), Zebra continues to monitor the newer Google monthly updates. We analyze each vulnerability in the update to determine if it is applicable to the older (unsupported by Google) OS release. If it is, we take the patch and backport (the process of taking a newer patch and adapting it to an older OS). We can only backport updates in cases where the functionality previously existed and/or the update does not impact the integrity of the platform. 40. DO I NEED LIFEGUARD FOR PCI COMPLIANCE? Zebra is not a PCI Qualified Security Assessor (QSA), with whom we suggest you consult. PCI DSS 3.2 does not appear to have this as a hard dependency. However, PCI DSS 3.2 Section (Change control procedures) Guidelines, states; if not properly managed, the impact of system changes such as hardware or software updates and installation of security patches might not be full realized and could have unintended consequences. 41. WHAT IS THE LIFECYCLE FOR GMS UPDATES? As stated earlier, Google owns and maintains GMS. Though Google has no public policy, in Nov 2016 Google announced that the latest GMS would not support GB This equates to a period of over 5 years. Obsoleted devices will continue to operate but will not receive any updates (including security updates). 42. WHAT IS THE LIFECYCLE FOR EMM UPDATES? Zebra does not control EMM life cycle. Our experience has been that EMM s support legacy Operating Systems for ~5-6 years. Console operation will generally continue beyond this window, but new features and security support will no longer be available. Consult your EMM for any updates. 43. DOES LIFEGUARD PROVIDE SECURITY UPDATES FOR GMS? Zebra Android GMS devices actually consist of two major software components; Android Open Source Project (AOSP) and Google Mobile Services (GMS). AOSP is open source while GMS libraries are closed binaries licensed and provided by Google. The GMS libraries are typically updated by Google from the Android Play Store (access to the play store is required). The only exception will be when Zebra provides a complete image update, in which case the GMS libraries will be provided as part of that update. Note that the GMS version in the Zebra provided update may not be the latest. Customers with applications leveraging GMS services should enable a connection to the Play Store enabling a GMS update. FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 10
11 44. CAN CUSTOMERS STILL OBTAIN A LOCKED DOWN IMAGE VIA A CUSTOM PRODUCT REQUEST? Yes, however we have had customers inquiring about a semi-locked image that would include security updates with no maintenance updates. This is still under consideration. 45. WHAT IF A CUSTOMER DETECTS A VULNERABILITY? Customers that detect a vulnerability can securely report that vulnerability by going to: WHAT IS THE ZEBRA URL TO ACCESS THE LIFEGUARD SECURITY UPDATES? FAQ, Customer Release March 2018 ZEBRA TECHNOLOGIES 11
10 Considerations for a Cloud Procurement. March 2017
 10 Considerations for a Cloud Procurement March 2017 2017, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents
10 Considerations for a Cloud Procurement March 2017 2017, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents
Protect Your End-of-Life Windows Server 2003 Operating System
 Protect Your End-of-Life Windows Server 2003 Operating System Your guide to mitigating risks in your Windows Server 2003 Systems after the end of support End of Support is Not the End of Business When
Protect Your End-of-Life Windows Server 2003 Operating System Your guide to mitigating risks in your Windows Server 2003 Systems after the end of support End of Support is Not the End of Business When
Protect Your End-of-Life Windows Server 2003 Operating System
 Protect Your End-of-Life Windows Server 2003 Operating System Your guide to mitigating risks in your Windows Server 2003 Systems after the end of support End of Support is Not the End of Business When
Protect Your End-of-Life Windows Server 2003 Operating System Your guide to mitigating risks in your Windows Server 2003 Systems after the end of support End of Support is Not the End of Business When
Statement of Work IBM Support Services IBM Essential Care Service - Acquired from an IBM Business Partner -
 IBM Switzerland Ltd Statement of Work IBM Support Services IBM Essential Care Service - Acquired from an IBM Business Partner - Edition: December 2015 1. Subject The subject of the Service is the provision
IBM Switzerland Ltd Statement of Work IBM Support Services IBM Essential Care Service - Acquired from an IBM Business Partner - Edition: December 2015 1. Subject The subject of the Service is the provision
SWIFT Customer Security Controls Framework and self-attestation via The KYC Registry Security Attestation Application FAQ
 SWIFT Customer Security Controls Framework and self-attestation via The KYC Registry Security Attestation Application FAQ 1 SWIFT Customer Security Controls Framework Why has SWIFT launched new security
SWIFT Customer Security Controls Framework and self-attestation via The KYC Registry Security Attestation Application FAQ 1 SWIFT Customer Security Controls Framework Why has SWIFT launched new security
University of Pittsburgh Security Assessment Questionnaire (v1.7)
 Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.7) Directions and Instructions for completing this assessment The answers provided
Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.7) Directions and Instructions for completing this assessment The answers provided
Schedule document N4MDM. PUBLIC Node4 limited 31/11/2018. Node4 Limited Millennium Way Pride Park Derby DE24 8HZ
 Schedule document N4MDM PUBLIC Node4 limited 31/11/2018 Schedule document N4MDM This Schedule contains additional terms, Service Description & Service Level Agreement applicable to the N4 End Point Management
Schedule document N4MDM PUBLIC Node4 limited 31/11/2018 Schedule document N4MDM This Schedule contains additional terms, Service Description & Service Level Agreement applicable to the N4 End Point Management
SCHEDULE DOCUMENT N4MDM PUBLIC NODE4 LIMITED 13/07/2017. Node4 Limited Millennium Way Pride Park Derby DE24 8HZ
 SCHEDULE DOCUMENT N4MDM PUBLIC NODE4 LIMITED 13/07/2017 SCHEDULE This Schedule contains additional terms, Service Description & Service Level Agreement applicable to the N4 End Point Management Service
SCHEDULE DOCUMENT N4MDM PUBLIC NODE4 LIMITED 13/07/2017 SCHEDULE This Schedule contains additional terms, Service Description & Service Level Agreement applicable to the N4 End Point Management Service
Product Versioning and Back Support Policy
 Effective March 18, 2016 to Feb 1, 2017 Product Versioning and Back Support Policy Definitions Semantic Versioning Date Based Versioning Standard Support Extended Support End of Life Support Critical Security
Effective March 18, 2016 to Feb 1, 2017 Product Versioning and Back Support Policy Definitions Semantic Versioning Date Based Versioning Standard Support Extended Support End of Life Support Critical Security
Meeting PCI DSS 3.2 Compliance with RiskSense Solutions
 Meeting PCI DSS 3.2 Compliance with Solutions Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 2018, Inc. What s Changing with PCI DSS? Summary of PCI Business
Meeting PCI DSS 3.2 Compliance with Solutions Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 2018, Inc. What s Changing with PCI DSS? Summary of PCI Business
IBM Resilient Incident Response Platform On Cloud
 Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
Mobiliti. Certified Device List. Last Updated - 8/23/13- ASP Version
 Certified Device List Last Updated - - ASP Version 2011-2013, Inc. or its affiliates. All rights reserved. This work is confidential and its use is strictly limited. Use is permitted only in accordance
Certified Device List Last Updated - - ASP Version 2011-2013, Inc. or its affiliates. All rights reserved. This work is confidential and its use is strictly limited. Use is permitted only in accordance
Brocade Fabric OS DATA CENTER. Target Path Selection Guide October 17, 2017
 October 17, 2017 DATA CENTER Brocade Fabric OS Target Path Selection Guide Brocade Fabric OS (Brocade FOS) Target Path releases are recommended code levels for Brocade Fibre Channel switch platforms. Use
October 17, 2017 DATA CENTER Brocade Fabric OS Target Path Selection Guide Brocade Fabric OS (Brocade FOS) Target Path releases are recommended code levels for Brocade Fibre Channel switch platforms. Use
MemSQL Partner Program Guide
 MemSQL Partner Program Guide April 2018 Introduction As the world changes and it s changing faster than ever you need to be adapting to it. You need to be anticipating problems before they occur. You need
MemSQL Partner Program Guide April 2018 Introduction As the world changes and it s changing faster than ever you need to be adapting to it. You need to be anticipating problems before they occur. You need
Service Description VMware Workspace ONE
 VMware Workspace ONE Last Updated: 05 April 2018 The product described in this Service Description is protected by U.S. and international copyright and intellectual property laws. The product described
VMware Workspace ONE Last Updated: 05 April 2018 The product described in this Service Description is protected by U.S. and international copyright and intellectual property laws. The product described
Frequently Asked Questions Customers
 Important Updates on Maintenance Plans Frequently Asked Questions Customers This document answers frequently asked questions about maintenance plan changes as we move to one business model. Updated: May
Important Updates on Maintenance Plans Frequently Asked Questions Customers This document answers frequently asked questions about maintenance plan changes as we move to one business model. Updated: May
IoT & SCADA Cyber Security Services
 RIOT SOLUTIONS PTY LTD P.O. Box 10087 Adelaide St Brisbane QLD 4000 BRISBANE HEAD OFFICE Level 22, 144 Edward St Brisbane, QLD 4000 T: 1300 744 028 Email: sales@riotsolutions.com.au www.riotsolutions.com.au
RIOT SOLUTIONS PTY LTD P.O. Box 10087 Adelaide St Brisbane QLD 4000 BRISBANE HEAD OFFICE Level 22, 144 Edward St Brisbane, QLD 4000 T: 1300 744 028 Email: sales@riotsolutions.com.au www.riotsolutions.com.au
PCI DSS. Compliance and Validation Guide VERSION PCI DSS. Compliance and Validation Guide
 PCI DSS VERSION 1.1 1 PCI DSS Table of contents 1. Understanding the Payment Card Industry Data Security Standard... 3 1.1. What is PCI DSS?... 3 2. Merchant Levels and Validation Requirements... 3 2.1.
PCI DSS VERSION 1.1 1 PCI DSS Table of contents 1. Understanding the Payment Card Industry Data Security Standard... 3 1.1. What is PCI DSS?... 3 2. Merchant Levels and Validation Requirements... 3 2.1.
MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations
 MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations Mobile Operating System Transition Insights and Considerations www.honeywellaidc.com 1 Introduction A shift in the mobile operating system
MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations Mobile Operating System Transition Insights and Considerations www.honeywellaidc.com 1 Introduction A shift in the mobile operating system
eguide: Designing a Continuous Response Architecture 5 Steps to Reduce the Complexity of PCI Security Assessments
 eguide: Designing a Continuous Response Architecture 5 Steps to Reduce the Complexity of PCI Security Assessments Today s PCI compliance landscape is one of continuing change and scrutiny. Given the number
eguide: Designing a Continuous Response Architecture 5 Steps to Reduce the Complexity of PCI Security Assessments Today s PCI compliance landscape is one of continuing change and scrutiny. Given the number
STRENGTHENING THE CYBERSECURITY OF FEDERAL NETWORKS AND CRITICAL INFRASTRUCTURE
 STRENGTHENING THE CYBERSECURITY OF FEDERAL NETWORKS AND CRITICAL INFRASTRUCTURE By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby
STRENGTHENING THE CYBERSECURITY OF FEDERAL NETWORKS AND CRITICAL INFRASTRUCTURE By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby
Oracle Utilities Opower Rates Engagement Cloud Service
 Oracle Utilities Opower Rates Engagement Cloud Service Product Overview E87463-01 Last Updated: June 22, 2018 Oracle Utilities Rates Engagement Cloud Service Product Overview E87463-01 Copyright 2017,
Oracle Utilities Opower Rates Engagement Cloud Service Product Overview E87463-01 Last Updated: June 22, 2018 Oracle Utilities Rates Engagement Cloud Service Product Overview E87463-01 Copyright 2017,
HOSTING SERVICES AGREEMENT
 HOSTING SERVICES AGREEMENT 1 Introduction 1.1 Usage. This Schedule is an addition to and forms an integral part of the General Terms and Conditions, hereafter referred as the "Main Agreement". This Schedule
HOSTING SERVICES AGREEMENT 1 Introduction 1.1 Usage. This Schedule is an addition to and forms an integral part of the General Terms and Conditions, hereafter referred as the "Main Agreement". This Schedule
Updated: April, 2018 (see what s new) Table of Contents. Overview Switching from Maintenance to Subscription Pricing for Switching...
 Important Updates on Maintenance Plans Frequently Asked Questions Customers This document answers frequently asked questions about maintenance plan changes as we move to one business model. Updated: April,
Important Updates on Maintenance Plans Frequently Asked Questions Customers This document answers frequently asked questions about maintenance plan changes as we move to one business model. Updated: April,
McAfee Corporate Products End of Life Policy
 McAfee Corporate Products End of Life Policy Effective January 2018 Scope To ensure delivery of innovative and cost-effective products, McAfee may periodically discontinue specific products or versions
McAfee Corporate Products End of Life Policy Effective January 2018 Scope To ensure delivery of innovative and cost-effective products, McAfee may periodically discontinue specific products or versions
What is Penetration Testing?
 What is Penetration Testing? March 2016 Table of Contents What is Penetration Testing?... 3 Why Perform Penetration Testing?... 4 How Often Should You Perform Penetration Testing?... 4 How Can You Benefit
What is Penetration Testing? March 2016 Table of Contents What is Penetration Testing?... 3 Why Perform Penetration Testing?... 4 How Often Should You Perform Penetration Testing?... 4 How Can You Benefit
Release Notes - Zebra TC8000 Android L GMS Update 07 Release
 Release Notes - Zebra TC8000 Android L GMS Update 07 Release Contents Description Device Compatibility Component Contents Installation Requirements Installation Instructions Downloadable Software included
Release Notes - Zebra TC8000 Android L GMS Update 07 Release Contents Description Device Compatibility Component Contents Installation Requirements Installation Instructions Downloadable Software included
Twilio cloud communications SECURITY
 WHITEPAPER Twilio cloud communications SECURITY From the world s largest public companies to early-stage startups, people rely on Twilio s cloud communications platform to exchange millions of calls and
WHITEPAPER Twilio cloud communications SECURITY From the world s largest public companies to early-stage startups, people rely on Twilio s cloud communications platform to exchange millions of calls and
2018 Data Security Incident Response Report Building Cyber Resilience: Compromise Response Intelligence in Action
 2018 Data Security Incident Response Report Building Cyber Resilience: Compromise Response Intelligence in Action April 11, 2018 Contact Information Casie D. Collignon Partner Denver 303.764.4037 ccollignon@bakerlaw.com
2018 Data Security Incident Response Report Building Cyber Resilience: Compromise Response Intelligence in Action April 11, 2018 Contact Information Casie D. Collignon Partner Denver 303.764.4037 ccollignon@bakerlaw.com
The Business Value of including Cybersecurity and Vendor Risk in ERM
 The Business Value of including Cybersecurity and Vendor Risk in ERM Yo Delmar, Vice President, Customer Engagement, MetricStream RMA GCOR XI April 4 5, 2017 Hyatt Regency, Cambridge, MA Tuesday 2:30 pm
The Business Value of including Cybersecurity and Vendor Risk in ERM Yo Delmar, Vice President, Customer Engagement, MetricStream RMA GCOR XI April 4 5, 2017 Hyatt Regency, Cambridge, MA Tuesday 2:30 pm
Nov 20, 2017 Page 1. Tripwire, Inc. Product Support and Discontinuation Policy November 2017
 Nov 20, 2017 Page 1 Tripwire, Inc. Product Support and Discontinuation Policy November 2017 Support Policy for Tripwire Products Tripwire, Inc. provides Full Support for the Current Release (CR) of all
Nov 20, 2017 Page 1 Tripwire, Inc. Product Support and Discontinuation Policy November 2017 Support Policy for Tripwire Products Tripwire, Inc. provides Full Support for the Current Release (CR) of all
Hours of Operation Technical assistance will be provided by telephone or , Monday through Friday, 08:00 AM to 18:00 PM EST (GMT -5).
 ADLIB SOFTWARE MAINTENANCE POLICY The Adlib Software Maintenance Policy describes the features of the Adlib Software Maintenance offering and the terms under which it is provided. Terms of the Adlib Software
ADLIB SOFTWARE MAINTENANCE POLICY The Adlib Software Maintenance Policy describes the features of the Adlib Software Maintenance offering and the terms under which it is provided. Terms of the Adlib Software
Vulnerability Assessments and Penetration Testing
 CYBERSECURITY Vulnerability Assessments and Penetration Testing A guide to understanding vulnerability assessments and penetration tests. OVERVIEW When organizations begin developing a strategy to analyze
CYBERSECURITY Vulnerability Assessments and Penetration Testing A guide to understanding vulnerability assessments and penetration tests. OVERVIEW When organizations begin developing a strategy to analyze
Continuously Discover and Eliminate Security Risk in Production Apps
 White Paper Security Continuously Discover and Eliminate Security Risk in Production Apps Table of Contents page Continuously Discover and Eliminate Security Risk in Production Apps... 1 Continuous Application
White Paper Security Continuously Discover and Eliminate Security Risk in Production Apps Table of Contents page Continuously Discover and Eliminate Security Risk in Production Apps... 1 Continuous Application
TRACKVIA SECURITY OVERVIEW
 TRACKVIA SECURITY OVERVIEW TrackVia s customers rely on our service for many mission-critical applications, as well as for applications that have various compliance and regulatory obligations. At all times
TRACKVIA SECURITY OVERVIEW TrackVia s customers rely on our service for many mission-critical applications, as well as for applications that have various compliance and regulatory obligations. At all times
IBM Resilient Incident Response Platform On Cloud
 Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
INFORMATION SUPPLEMENT. Use of SSL/Early TLS for POS POI Terminal Connections. Date: June 2018 Author: PCI Security Standards Council
 Use of SSL/Early TLS for POS POI Terminal Connections Date: Author: PCI Security Standards Council Table of Contents Introduction...1 Executive Summary...1 What is the risk?...1 What is meant by Early
Use of SSL/Early TLS for POS POI Terminal Connections Date: Author: PCI Security Standards Council Table of Contents Introduction...1 Executive Summary...1 What is the risk?...1 What is meant by Early
IBM Resilient Incident Response Platform On Cloud
 Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and
Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
June 2012 First Data PCI RAPID COMPLY SM Solution
 June 2012 First Data PCI RAPID COMPLY SM Solution You don t have to be a security expert to be compliant. Developer: 06 Rev: 05/03/2012 V: 1.0 Agenda Research Background Product Overview Steps to becoming
June 2012 First Data PCI RAPID COMPLY SM Solution You don t have to be a security expert to be compliant. Developer: 06 Rev: 05/03/2012 V: 1.0 Agenda Research Background Product Overview Steps to becoming
YourStore A GUIDE TO
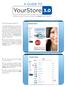 A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
IBM Managed Security Services - Vulnerability Scanning
 Service Description IBM Managed Security Services - Vulnerability Scanning This Service Description describes the Service IBM provides to Client. 1.1 Service IBM Managed Security Services - Vulnerability
Service Description IBM Managed Security Services - Vulnerability Scanning This Service Description describes the Service IBM provides to Client. 1.1 Service IBM Managed Security Services - Vulnerability
IBM App Connect Enterprise on IBM Cloud
 Service Description IBM App Connect Enterprise on IBM Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and
Service Description IBM App Connect Enterprise on IBM Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and
What's New in Database Cloud Service. On Oracle Cloud. April Oracle Cloud. What's New for Oracle Database Cloud Service
 Oracle Cloud What's New for Oracle Database Cloud Service E68400-29 April 2018 What's New in Database Cloud Service This document describes what's new in Oracle Database Cloud Service on all platforms
Oracle Cloud What's New for Oracle Database Cloud Service E68400-29 April 2018 What's New in Database Cloud Service This document describes what's new in Oracle Database Cloud Service on all platforms
PCI Compliance Updates
 PCI Compliance Updates PCI Mobile Payment Acceptance Security Guidelines Adam Goslin, Chief Operations Officer AGoslin@HighBitSecurity.com Direct: 248.388.4328 PCI Guidance February, 2013 - PCI Mobile
PCI Compliance Updates PCI Mobile Payment Acceptance Security Guidelines Adam Goslin, Chief Operations Officer AGoslin@HighBitSecurity.com Direct: 248.388.4328 PCI Guidance February, 2013 - PCI Mobile
QuickBooks Online Security White Paper July 2017
 QuickBooks Online Security White Paper July 2017 Page 1 of 6 Introduction At Intuit QuickBooks Online (QBO), we consider the security of your information as well as your customers and employees data a
QuickBooks Online Security White Paper July 2017 Page 1 of 6 Introduction At Intuit QuickBooks Online (QBO), we consider the security of your information as well as your customers and employees data a
Isaca EXAM - CISM. Certified Information Security Manager. Buy Full Product.
 Isaca EXAM - CISM Certified Information Security Manager Buy Full Product http://www.examskey.com/cism.html Examskey Isaca CISM exam demo product is here for you to test the quality of the product. This
Isaca EXAM - CISM Certified Information Security Manager Buy Full Product http://www.examskey.com/cism.html Examskey Isaca CISM exam demo product is here for you to test the quality of the product. This
HP Fortify Software Security Center
 HP Fortify Software Security Center Proactively Eliminate Risk in Software Trust Your Software 92% of exploitable vulnerabilities are in software National Institute for Standards and Technology (NIST)
HP Fortify Software Security Center Proactively Eliminate Risk in Software Trust Your Software 92% of exploitable vulnerabilities are in software National Institute for Standards and Technology (NIST)
SECURITY & PRIVACY DOCUMENTATION
 Okta s Commitment to Security & Privacy SECURITY & PRIVACY DOCUMENTATION (last updated September 15, 2017) Okta is committed to achieving and preserving the trust of our customers, by providing a comprehensive
Okta s Commitment to Security & Privacy SECURITY & PRIVACY DOCUMENTATION (last updated September 15, 2017) Okta is committed to achieving and preserving the trust of our customers, by providing a comprehensive
Micro Focus Partner Program. For Resellers
 Micro Focus Partner Program For Resellers Contents Micro Focus Today About Micro Focus Our solutions for digital transformation Products and Solutions Program Membership Tiers Become a Portfolio Expert
Micro Focus Partner Program For Resellers Contents Micro Focus Today About Micro Focus Our solutions for digital transformation Products and Solutions Program Membership Tiers Become a Portfolio Expert
IBM IoT Connected Vehicle Insights
 Service Description IBM IoT Connected Vehicle Insights This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients
Service Description IBM IoT Connected Vehicle Insights This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients
What's New in Database Cloud Service. On Oracle Cloud. Oracle Cloud. What's New for Oracle Database Cloud Service
 Oracle Cloud What's New for Oracle Database Cloud Service E68400-38 December 2018 What's New in Database Cloud Service This document describes what's new in Oracle Database Cloud Service on all platforms
Oracle Cloud What's New for Oracle Database Cloud Service E68400-38 December 2018 What's New in Database Cloud Service This document describes what's new in Oracle Database Cloud Service on all platforms
Compliance of Panda Products with General Data Protection Regulation (GDPR) Panda Security
 Panda Security Compliance of Panda Products with General Data Protection Regulation (GDPR) 1 Contents 1.1. SCOPE OF THIS DOCUMENT... 3 1.2. GENERAL DATA PROTECTION REGULATION: OBJECTIVES... 3 1.3. STORED
Panda Security Compliance of Panda Products with General Data Protection Regulation (GDPR) 1 Contents 1.1. SCOPE OF THIS DOCUMENT... 3 1.2. GENERAL DATA PROTECTION REGULATION: OBJECTIVES... 3 1.3. STORED
Release Notes Zebra TC51, TC51-HC, and TC56 Android N LifeGuard Update 07 for GMS
 Release Notes Zebra TC51, TC51-HC, and TC56 LifeGuard Update 07 for GMS Introduction Description Device Compatibility Component Contents Installation Requirements Installation Instructions Downloadable
Release Notes Zebra TC51, TC51-HC, and TC56 LifeGuard Update 07 for GMS Introduction Description Device Compatibility Component Contents Installation Requirements Installation Instructions Downloadable
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
ForeScout ControlFabric TM Architecture
 ForeScout ControlFabric TM Architecture IMPROVE MULTI-VENDOR SOLUTION EFFECTIVENESS, RESPONSE AND WORKFLOW AUTOMATION THROUGH COLLABORATION WITH INDUSTRY-LEADING TECHNOLOGY PARTNERS. The Challenge 50%
ForeScout ControlFabric TM Architecture IMPROVE MULTI-VENDOR SOLUTION EFFECTIVENESS, RESPONSE AND WORKFLOW AUTOMATION THROUGH COLLABORATION WITH INDUSTRY-LEADING TECHNOLOGY PARTNERS. The Challenge 50%
IBM IoT Connection Service
 Service Description IBM IoT Connection Service This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients of
Service Description IBM IoT Connection Service This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients of
SOFTWARE MAINTENANCE PROGRAM for exo Platform
 SOFTWARE MAINTENANCE PROGRAM for exo Platform Last update : march 30th, 2018 Overview Customers who have subscribed to an eligible Subscription Plan benefit from the exo Platform Software Maintenance Program.
SOFTWARE MAINTENANCE PROGRAM for exo Platform Last update : march 30th, 2018 Overview Customers who have subscribed to an eligible Subscription Plan benefit from the exo Platform Software Maintenance Program.
RiskSense Attack Surface Validation for IoT Systems
 RiskSense Attack Surface Validation for IoT Systems 2018 RiskSense, Inc. Surfacing Double Exposure Risks Changing Times and Assessment Focus Our view of security assessments has changed. There is diminishing
RiskSense Attack Surface Validation for IoT Systems 2018 RiskSense, Inc. Surfacing Double Exposure Risks Changing Times and Assessment Focus Our view of security assessments has changed. There is diminishing
CCISO Blueprint v1. EC-Council
 CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
OPTIMIZATION MAXIMIZING TELECOM AND NETWORK. The current state of enterprise optimization, best practices and considerations for improvement
 MAXIMIZING TELECOM AND NETWORK OPTIMIZATION The current state of enterprise optimization, best practices and considerations for improvement AOTMP.com The Next Evolution of Telecom Management OVERVIEW As
MAXIMIZING TELECOM AND NETWORK OPTIMIZATION The current state of enterprise optimization, best practices and considerations for improvement AOTMP.com The Next Evolution of Telecom Management OVERVIEW As
Teradata and Protegrity High-Value Protection for High-Value Data
 Teradata and Protegrity High-Value Protection for High-Value Data 12.16 EB7178 DATA SECURITY Table of Contents 2 Data Centric Security: Providing High-Value Protection for High-Value Data 3 Visibility:
Teradata and Protegrity High-Value Protection for High-Value Data 12.16 EB7178 DATA SECURITY Table of Contents 2 Data Centric Security: Providing High-Value Protection for High-Value Data 3 Visibility:
locuz.com SOC Services
 locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
Release Notes Zebra TC51, TC51-HC, TC70x, TC56 and TC75x Android N - LifeGuard Update 04 for NGMS
 Release Notes Zebra TC51, TC51-HC, TC70x, TC56 and TC75x - LifeGuard Update 04 for NGMS Introduction Description Device Compatibility Component Contents Installation Requirements Installation Instructions
Release Notes Zebra TC51, TC51-HC, TC70x, TC56 and TC75x - LifeGuard Update 04 for NGMS Introduction Description Device Compatibility Component Contents Installation Requirements Installation Instructions
TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION
 INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
exo Product Maintenance Program
 exo Product Maintenance Program Overview exo s subscription customers benefit from the exo product maintenance program, according to the coverage specified in their subscription contract. The program provides
exo Product Maintenance Program Overview exo s subscription customers benefit from the exo product maintenance program, according to the coverage specified in their subscription contract. The program provides
Verizon Software Defined Perimeter (SDP).
 Verizon Software Defined Perimeter (). 1 Introduction. For the past decade, perimeter security was built on a foundation of Firewall, network access control (NAC) and virtual private network (VPN) appliances.
Verizon Software Defined Perimeter (). 1 Introduction. For the past decade, perimeter security was built on a foundation of Firewall, network access control (NAC) and virtual private network (VPN) appliances.
Windows IoT Security. Jackie Chang Sr. Program Manager
 Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
90% of data breaches are caused by software vulnerabilities.
 90% of data breaches are caused by software vulnerabilities. Get the skills you need to build secure software applications Secure Software Development (SSD) www.ce.ucf.edu/ssd Offered in partnership with
90% of data breaches are caused by software vulnerabilities. Get the skills you need to build secure software applications Secure Software Development (SSD) www.ce.ucf.edu/ssd Offered in partnership with
JBoss Enterprise Middleware
 JBoss Enterprise Middleware Making software from the open source community ready for the enterprise DLT Solutions 2411 Dulles Corner Park, Suite 800 Herndon, VA 20171 Web: www.dlt.com Phone: 703-709-7172
JBoss Enterprise Middleware Making software from the open source community ready for the enterprise DLT Solutions 2411 Dulles Corner Park, Suite 800 Herndon, VA 20171 Web: www.dlt.com Phone: 703-709-7172
(Office 365) Service Level Expectation
 Email SLE Service Overview... 2 Service Features... 2 Service Warranty... 3 Support Model... 3 Support Hours and Initial Response Times... 4 Support Request Resolution Targets... 5 Service Request Fulfillment
Email SLE Service Overview... 2 Service Features... 2 Service Warranty... 3 Support Model... 3 Support Hours and Initial Response Times... 4 Support Request Resolution Targets... 5 Service Request Fulfillment
PRODUCT DESCRIPTIONS AND METRICS
 PRODUCT DESCRIPTIONS AND METRICS Adobe PDM Adobe Campaign Managed Services (2014v3) The Products and Services described in this PDM are subject to the applicable Sales Order, the terms of this PDM, the
PRODUCT DESCRIPTIONS AND METRICS Adobe PDM Adobe Campaign Managed Services (2014v3) The Products and Services described in this PDM are subject to the applicable Sales Order, the terms of this PDM, the
RHM Presentation. Maas 360 Mobile device management
 RHM Presentation Maas 360 Mobile device management Strong adoption in the enterprise Manufacturing Financial Consumer Healthcare Public Others 2 Trusted by over 9,000 customers Recognized Industry Leadership
RHM Presentation Maas 360 Mobile device management Strong adoption in the enterprise Manufacturing Financial Consumer Healthcare Public Others 2 Trusted by over 9,000 customers Recognized Industry Leadership
Synology Security Whitepaper
 Synology Security Whitepaper 1 Table of Contents Introduction 3 Security Policy 4 DiskStation Manager Life Cycle Severity Ratings Standards Security Program 10 Product Security Incident Response Team Bounty
Synology Security Whitepaper 1 Table of Contents Introduction 3 Security Policy 4 DiskStation Manager Life Cycle Severity Ratings Standards Security Program 10 Product Security Incident Response Team Bounty
QuickSpecs. HPE SAS Hard Drives
 Overview Serial Attached SCSI (SAS) provides a superior storage solution. With some storage requirements escalating and others becoming more complex, factors such as flexibility, performance, increased
Overview Serial Attached SCSI (SAS) provides a superior storage solution. With some storage requirements escalating and others becoming more complex, factors such as flexibility, performance, increased
Reinvent Your 2013 Security Management Strategy
 Reinvent Your 2013 Security Management Strategy Laurent Boutet 18 septembre 2013 Phone:+33 6 25 34 12 01 Email:laurent.boutet@skyboxsecurity.com www.skyboxsecurity.com What are Your Key Objectives for
Reinvent Your 2013 Security Management Strategy Laurent Boutet 18 septembre 2013 Phone:+33 6 25 34 12 01 Email:laurent.boutet@skyboxsecurity.com www.skyboxsecurity.com What are Your Key Objectives for
Computer Hardware and Software Standards for OSU Extension
 Computer Hardware and Software Standards for OSU Extension Sections 1. Executive Summary 2. Criteria for Establishing Standards 3. Computers a. Primary Choices for Highest Level of Support b. Secondary
Computer Hardware and Software Standards for OSU Extension Sections 1. Executive Summary 2. Criteria for Establishing Standards 3. Computers a. Primary Choices for Highest Level of Support b. Secondary
NORTH AMERICAN SECURITIES ADMINISTRATORS ASSOCIATION Cybersecurity Checklist for Investment Advisers
 Identify Protect Detect Respond Recover Identify: Risk Assessments & Management 1. Risk assessments are conducted frequently (e.g. annually, quarterly). 2. Cybersecurity is included in the risk assessment.
Identify Protect Detect Respond Recover Identify: Risk Assessments & Management 1. Risk assessments are conducted frequently (e.g. annually, quarterly). 2. Cybersecurity is included in the risk assessment.
Exam4Tests. Latest exam questions & answers help you to pass IT exam test easily
 Exam4Tests http://www.exam4tests.com Latest exam questions & answers help you to pass IT exam test easily Exam : CISM Title : Certified Information Security Manager Vendor : ISACA Version : DEMO 1 / 10
Exam4Tests http://www.exam4tests.com Latest exam questions & answers help you to pass IT exam test easily Exam : CISM Title : Certified Information Security Manager Vendor : ISACA Version : DEMO 1 / 10
Introduction to the PCI DSS: What Merchants Need to Know
 Introduction to the PCI DSS: What Merchants Need to Know Successfully managing a business in today s environment is, in its own right, a challenging feat. Uncertain economics, increasing regulatory pressures,
Introduction to the PCI DSS: What Merchants Need to Know Successfully managing a business in today s environment is, in its own right, a challenging feat. Uncertain economics, increasing regulatory pressures,
ICBA Summary of FFIEC Cybersecurity Assessment Tool (May 2017 Update)
 ICBA Summary of FFIEC Cybersecurity Assessment Tool (May 2017 Update) June 2017 INSERT YEAR HERE Contact Information: Jeremy Dalpiaz AVP, Cyber and Data Security Policy Jeremy.Dalpiaz@icba.org ICBA Summary
ICBA Summary of FFIEC Cybersecurity Assessment Tool (May 2017 Update) June 2017 INSERT YEAR HERE Contact Information: Jeremy Dalpiaz AVP, Cyber and Data Security Policy Jeremy.Dalpiaz@icba.org ICBA Summary
Bring Your Own Device
 Bring Your Own Device Individual Liable User Contents Introduction 3 Policy Document Objectives & Legal Disclaimer 3 Eligibility Considerations 4 Reimbursement Considerations 4 Security Considerations
Bring Your Own Device Individual Liable User Contents Introduction 3 Policy Document Objectives & Legal Disclaimer 3 Eligibility Considerations 4 Reimbursement Considerations 4 Security Considerations
Information Infrastructure and Security. The value of smart manufacturing begins with a secure and reliable infrastructure
 Information Infrastructure and Security The value of smart manufacturing begins with a secure and reliable infrastructure The Case for Connection To be competitive, you must be connected. That is why industrial
Information Infrastructure and Security The value of smart manufacturing begins with a secure and reliable infrastructure The Case for Connection To be competitive, you must be connected. That is why industrial
Mobiliti. Certified Device List MR6 Release. Last Updated June, ASP Version
 Certified Device List MR6 Release Last Updated June, 2015 - ASP Version 2011-2014, Inc. or its affiliates. All rights reserved. This work is confidential and its use is strictly limited. Use is permitted
Certified Device List MR6 Release Last Updated June, 2015 - ASP Version 2011-2014, Inc. or its affiliates. All rights reserved. This work is confidential and its use is strictly limited. Use is permitted
PCI COMPLIANCE IS NO LONGER OPTIONAL
 PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
Magento GDPR Frequently Asked Questions
 Magento GDPR Frequently Asked Questions Whom does GDPR impact? Does this only impact European Union (EU) based companies? The new regulation provides rules that govern how companies may collect and handle
Magento GDPR Frequently Asked Questions Whom does GDPR impact? Does this only impact European Union (EU) based companies? The new regulation provides rules that govern how companies may collect and handle
OUR CUSTOMER TERMS CLOUD SERVICES - INFRASTRUCTURE
 CONTENTS 1 ABOUT THIS PART... 2 2 GENERAL... 2 3 CLOUD INFRASTRUCTURE (FORMERLY UTILITY HOSTING)... 2 4 TAILORED INFRASTRUCTURE (FORMERLY DEDICATED HOSTING)... 3 5 COMPUTE... 3 6 BACKUP & RECOVERY... 8
CONTENTS 1 ABOUT THIS PART... 2 2 GENERAL... 2 3 CLOUD INFRASTRUCTURE (FORMERLY UTILITY HOSTING)... 2 4 TAILORED INFRASTRUCTURE (FORMERLY DEDICATED HOSTING)... 3 5 COMPUTE... 3 6 BACKUP & RECOVERY... 8
Vulnerability Management
 Vulnerability Management Service Definition Table of Contents 1 INTRODUCTION... 2 2 SERVICE OFFERINGS VULNERABILITY MANAGEMENT... 2 3 SOLUTION PURPOSE... 3 4 HOW IT WORKS... 3 5 WHAT S INCLUDED... 4 6
Vulnerability Management Service Definition Table of Contents 1 INTRODUCTION... 2 2 SERVICE OFFERINGS VULNERABILITY MANAGEMENT... 2 3 SOLUTION PURPOSE... 3 4 HOW IT WORKS... 3 5 WHAT S INCLUDED... 4 6
FedRAMP: Understanding Agency and Cloud Provider Responsibilities
 May 2013 Walter E. Washington Convention Center Washington, DC FedRAMP: Understanding Agency and Cloud Provider Responsibilities Matthew Goodrich, JD FedRAMP Program Manager US General Services Administration
May 2013 Walter E. Washington Convention Center Washington, DC FedRAMP: Understanding Agency and Cloud Provider Responsibilities Matthew Goodrich, JD FedRAMP Program Manager US General Services Administration
Managing Privacy Risk & Compliance in Financial Services. Brett Hamilton Advisory Solutions Consultant ServiceNow
 Managing Privacy Risk & Compliance in Financial Services Brett Hamilton Advisory Solutions Consultant ServiceNow 1 Speaker Introduction INSERT PHOTO Name: Brett Hamilton Title: Advisory Solutions Consultant
Managing Privacy Risk & Compliance in Financial Services Brett Hamilton Advisory Solutions Consultant ServiceNow 1 Speaker Introduction INSERT PHOTO Name: Brett Hamilton Title: Advisory Solutions Consultant
10 FOCUS AREAS FOR BREACH PREVENTION
 10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
Data Protection and GDPR
 Data Protection and GDPR At DPDgroup UK Ltd (DPD & DPD Local) we take data protection seriously and have updated all our relevant policies and documents to ensure we meet the requirements of GDPR. We have
Data Protection and GDPR At DPDgroup UK Ltd (DPD & DPD Local) we take data protection seriously and have updated all our relevant policies and documents to ensure we meet the requirements of GDPR. We have
IBM Sterling B2B Services File Transfer Service
 Service Description IBM Sterling B2B Services File Transfer Service This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
Service Description IBM Sterling B2B Services File Transfer Service This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
BRING YOUR OWN DEVICE: POLICY CONSIDERATIONS
 WHITE PAPER BRING YOUR OWN DEVICE: POLICY CONSIDERATIONS INTRODUCTION As more companies embrace the broad usage of individual liable mobile devices or BYOD for access to corporate applications and data,
WHITE PAPER BRING YOUR OWN DEVICE: POLICY CONSIDERATIONS INTRODUCTION As more companies embrace the broad usage of individual liable mobile devices or BYOD for access to corporate applications and data,
ABB Process Automation, September 2014
 ABB Process Automation, September 2014 ABB Process Automation Services Services that add life to your products, systems and processes September 26, 2014 Slide 1 1 ABB Process Automation Services A proven
ABB Process Automation, September 2014 ABB Process Automation Services Services that add life to your products, systems and processes September 26, 2014 Slide 1 1 ABB Process Automation Services A proven
Autodesk and Spatial Business Systems Strategic Alliance Frequently Asked Questions for Customers
 Autodesk and Spatial Business Systems Strategic Alliance Frequently Asked Questions for Customers Table of Contents OVERVIEW... 1 1.1 WHAT IS CHANGING?... 2 1.2 WHY IS AUTODESK MAKING THIS CHANGE?... 2
Autodesk and Spatial Business Systems Strategic Alliance Frequently Asked Questions for Customers Table of Contents OVERVIEW... 1 1.1 WHAT IS CHANGING?... 2 1.2 WHY IS AUTODESK MAKING THIS CHANGE?... 2
ONC Health IT Certification Program
 ONC Health IT Certification Program Certification Requirements Update March 17, 2016 ICSA Labs Health IT Program Agenda Introduction Mandatory Product Disclosures and Transparency Requirements Certified
ONC Health IT Certification Program Certification Requirements Update March 17, 2016 ICSA Labs Health IT Program Agenda Introduction Mandatory Product Disclosures and Transparency Requirements Certified
Managed Security Services - Endpoint Managed Security on Cloud
 Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
XO SITE SECURITY SERVICES
 XO SITE SECURITY SERVICES 1.0 Product and Services 1.1 Product Description. XO Site Security (the "Service") is a managed security service which uses Premises-based, multi-threat sensing Customer Premises
XO SITE SECURITY SERVICES 1.0 Product and Services 1.1 Product Description. XO Site Security (the "Service") is a managed security service which uses Premises-based, multi-threat sensing Customer Premises
ASD CERTIFICATION REPORT
 ASD CERTIFICATION REPORT Amazon Web Services Elastic Compute Cloud (EC2), Virtual Private Cloud (VPC), Elastic Block Store (EBS) and Simple Storage Service (S3) Certification Decision ASD certifies Amazon
ASD CERTIFICATION REPORT Amazon Web Services Elastic Compute Cloud (EC2), Virtual Private Cloud (VPC), Elastic Block Store (EBS) and Simple Storage Service (S3) Certification Decision ASD certifies Amazon
