How do we get from what we know (score of data given a tree) to what we want (score of the tree, given the data)?
|
|
|
- Bethanie Lawson
- 5 years ago
- Views:
Transcription
1 Lecture 8 Contents 1 Probability of a tree o 1.1 Marginalizing 2 Designing an Algorithm o 2.1 Remember Fibonacci! o 2.2 Efficient computation 3 Greedy Algorithm for trying trees o 3.1 Branch Lengths Probability of a tree How do we get from what we know (score of data given a tree) to what we want (score of the tree, given the data)? From last time, one of the assumptions that we made is that without knowing anything about the data, two trees (T1 and T2) are equally likely. Note: when we propose a tree, we'll also find the branch lengths that work best for that tree. We'll treat that as part of the topology. Expression for the joint probability of all data: P(D T) = P(A,C,C,C,G,x,y,z,w T) T = topology of the tree (includes t1,t2... all the branch lengths) We're going to refer to x,y,z,w as "nuisance parameters" We don't care what their values ARE, we're just going to try ALL of them, and just integrate through. Join probability of the data can be separated into each of the independent events (mutations), and the probability of each event is exactly what the J-C formula gives us the way to calculate!
2 P(A,C,C,C,G,x,y,z,w T) = P * P * P * P x y z w P(x) = P x P(y x,t ) * P(A y,t ) * P(C y,t ) = P y P(z x,t ) * P(C z,t ) = P 8 3 z P(w z,t ) * P(C w,t ) * P(G w,t ) = P w Now that we have an expression for the joint probability, we can sum over the nuisance paramaters. For each possible set of values for the nuisance parameters, the joint probability distribution will take on a particular value. We then ADD these because we don't care what the nuisance parameters' values are, they can be one set of values, OR another set of values, OR another set of values... (each sum is over the 4 possibilites ACGT) P x * P y * P z * P w x y z w Marginalizing In order to calculate P x * P y * P z * P w x y z w Now consider that: 1. P_x doesn't depend on y or z or w, 2. P_y doesn't depend on z or w, 3. P_z doesn't depend on w, 4. but P_w depends on x and z. You can pull terms in front of the sum if they don't depend on the variable you're summing over.
3 16 possible trees for parent=a When you're considering the likelihood at a partcular node (P x for example) you have to look at 64 possibilities (4 at parent, 4 at each child) For p in ACGT: For q in ACGT: For r in ACGT: P = P(q) * P(r) * P(q p,t pq) * P(r p,t pr ) L[p] +=P Note: P is probability p is the state of the parent node (ACGT) Designing an Algorithm Remember Fibonacci! remember Fib: 1. return kth number 2. return series the series was the smart way to do it- the other one explodes computationally
4 Efficient computation In the Sankoff algorithm presented in class, we did this by simply calling this whole function again (64 times)- this will work, but it could be VERY expensive for anything but the smallest trees. Fortunately, there is a better way... The problem is that we included the recursion in a loop, so it is called many times for each node: def sankoff(tree,nodeseq): #this function returns the score for a particular state at the root min = inf #initialization if tree is a leaf: #stop condition if tree['data'] == nodeseq: return 0 return inf for leftseq in [A,C,G,T]: #now we're at a node with two children for rightseq in [A,C,G,T]: #we have to try all 16 possibilities here sum= cost(nodeseq,leftseq,rightseq) #cost is some function that looks up the cost in the table sum += sankoff(tree['left'],leftseq) #we have to remember to pass the cost along! sum += sankoff(tree['right'],rightseq) if (sum < min): min = sum return min...but we can move the recursion out of the loop if we return the costs for each possible nucleotide at each node def sankoff(tree): #this function returns a dictionary of scores for all possible states at the root for parentseq in [A,C,G,T]: #initialization scores[parentseq] = inf #infinity if tree is a leaf: #stop condition if tree['data'] == nodeseq: scores[tree['data']] = 0 #every state except the observed is set to infinity return scores leftscores = sankoff(tree['left']) #recursion moved outside of loop rightscores = sankoff(tree['right']) forparentseq in [A,C,G,T]: #try all seqs at the current node for leftseq in [A,C,G,T]: #now we're at a node with two children for rightseq in [A,C,G,T]: #we have to try all 16 possibilities here sum = cost(nodeseq,leftseq,rightseq) #cost is some function that looks up the cost in the table sum += leftscores[leftseq] #we have to remember to pass the cost along! sum += rightscores[rightseq] if (sum < scores[parentseq]): scores[parentseq] = sum return scores #return the dictionary
5 Note that this is exactly what we did with the fibonacci function to prevent unnecessary recursion - we returned a list of values instead of a single case. This is the dynamic programming approach: efficiently break a problem up into independent (and nonredunant) subproblems. OK... now to apply these lessons to a maximum likelihood computation: We want to define a function outside our main loop, and we want it to grab the probabilities P(q) for all q in ACGT P(r) for all r in ACGT where q is state at the left subtree, and r is state at the right. To do this we'll need a function that returns the probabilities for all possible states. For example: def ml(tree,pos): (insert code here) return {'A':0.1,'C':0.2,'G':0.1,'T':0.1} #values are just as an example! This is the trick we really want to see you implement in HW5; this is where dynamic programming comes in. We're not going to compute these probabilities 64 times. Recall how we pulled terms out of the sum... we can take advantage of that to break up the problem in an intelligent way: 1. Separate computation of P_w which doesn't depend on x,y,z 2. Separate computation of P_z which doesn't depend on x,y 3....etc... Some additional hints: in Sankoff, we took the min of the scores, but here we want to ADD all of the possible probabilities for each possible state of the internal nodes. Also, our cost function here is a function of time(distance), so we wont just look it up in a tablew. We have a separate function to calculate the probability under the Jukes-Cantor model of evolution. Greedy Algorithm for trying trees A heuristic (contrast with dynamic programming) We give up and say we're not going to find an exact solution, but we're going to find an okay solution
6 searching for a good tree Calculate P(D T) For some trees: compute L report best L 1. build 3-leaf tree 2. add a leaf 3. try all possibilities keep the best one 4. repeat until all leaves added 5. change leaf order and repeat Branch Lengths What are we going to do about branch lengths?
7 There's no proof of this, but what we're going to do is look at one branch length at a time keeping all other branch lengths equal, let's find the length of t_o that maximizes the tree. Usually you get something that looks like: inverted parabola with big right shoulder (y-axis = L, x-axis = t_o) Branch lengths not very difficult to optimize. So it is a heuristic solution, but it is pretty good.
Greedy Algorithms CHAPTER 16
 CHAPTER 16 Greedy Algorithms In dynamic programming, the optimal solution is described in a recursive manner, and then is computed ``bottom up''. Dynamic programming is a powerful technique, but it often
CHAPTER 16 Greedy Algorithms In dynamic programming, the optimal solution is described in a recursive manner, and then is computed ``bottom up''. Dynamic programming is a powerful technique, but it often
Algorithms and Data Structures
 Algorithms and Data Structures Priority Queues Ulf Leser Special Scenarios for Searching Up to now, we assumed that all elements of a list are equally important and that any of them could be searched next
Algorithms and Data Structures Priority Queues Ulf Leser Special Scenarios for Searching Up to now, we assumed that all elements of a list are equally important and that any of them could be searched next
Parsimony-Based Approaches to Inferring Phylogenetic Trees
 Parsimony-Based Approaches to Inferring Phylogenetic Trees BMI/CS 576 www.biostat.wisc.edu/bmi576.html Mark Craven craven@biostat.wisc.edu Fall 0 Phylogenetic tree approaches! three general types! distance:
Parsimony-Based Approaches to Inferring Phylogenetic Trees BMI/CS 576 www.biostat.wisc.edu/bmi576.html Mark Craven craven@biostat.wisc.edu Fall 0 Phylogenetic tree approaches! three general types! distance:
CSE 549: Computational Biology
 CSE 549: Computational Biology Phylogenomics 1 slides marked with * by Carl Kingsford Tree of Life 2 * H5N1 Influenza Strains Salzberg, Kingsford, et al., 2007 3 * H5N1 Influenza Strains The 2007 outbreak
CSE 549: Computational Biology Phylogenomics 1 slides marked with * by Carl Kingsford Tree of Life 2 * H5N1 Influenza Strains Salzberg, Kingsford, et al., 2007 3 * H5N1 Influenza Strains The 2007 outbreak
CS 581. Tandy Warnow
 CS 581 Tandy Warnow This week Maximum parsimony: solving it on small datasets Maximum Likelihood optimization problem Felsenstein s pruning algorithm Bayesian MCMC methods Research opportunities Maximum
CS 581 Tandy Warnow This week Maximum parsimony: solving it on small datasets Maximum Likelihood optimization problem Felsenstein s pruning algorithm Bayesian MCMC methods Research opportunities Maximum
Trees (Part 1, Theoretical) CSE 2320 Algorithms and Data Structures University of Texas at Arlington
 Trees (Part 1, Theoretical) CSE 2320 Algorithms and Data Structures University of Texas at Arlington 1 Trees Trees are a natural data structure for representing specific data. Family trees. Organizational
Trees (Part 1, Theoretical) CSE 2320 Algorithms and Data Structures University of Texas at Arlington 1 Trees Trees are a natural data structure for representing specific data. Family trees. Organizational
This lesson is part 5 of 5 in a series. You can go to Invoice, Part 1: Free Shipping if you'd like to start from the beginning.
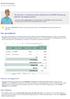 Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
Phylogenetics. Introduction to Bioinformatics Dortmund, Lectures: Sven Rahmann. Exercises: Udo Feldkamp, Michael Wurst
 Phylogenetics Introduction to Bioinformatics Dortmund, 16.-20.07.2007 Lectures: Sven Rahmann Exercises: Udo Feldkamp, Michael Wurst 1 Phylogenetics phylum = tree phylogenetics: reconstruction of evolutionary
Phylogenetics Introduction to Bioinformatics Dortmund, 16.-20.07.2007 Lectures: Sven Rahmann Exercises: Udo Feldkamp, Michael Wurst 1 Phylogenetics phylum = tree phylogenetics: reconstruction of evolutionary
Heap sort. Carlos Moreno uwaterloo.ca EIT
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 http://xkcd.com/835/ https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Last time, on ECE-250... Talked
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 http://xkcd.com/835/ https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Last time, on ECE-250... Talked
Binary heaps (chapters ) Leftist heaps
 Binary heaps (chapters 20.3 20.5) Leftist heaps Binary heaps are arrays! A binary heap is really implemented using an array! 8 18 29 20 28 39 66 Possible because of completeness property 37 26 76 32 74
Binary heaps (chapters 20.3 20.5) Leftist heaps Binary heaps are arrays! A binary heap is really implemented using an array! 8 18 29 20 28 39 66 Possible because of completeness property 37 26 76 32 74
Heap sort. Carlos Moreno uwaterloo.ca EIT
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 http://xkcd.com/835/ https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Last time, on ECE-250... Talked
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 http://xkcd.com/835/ https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Last time, on ECE-250... Talked
Geometric data structures:
 Geometric data structures: Machine Learning for Big Data CSE547/STAT548, University of Washington Sham Kakade Sham Kakade 2017 1 Announcements: HW3 posted Today: Review: LSH for Euclidean distance Other
Geometric data structures: Machine Learning for Big Data CSE547/STAT548, University of Washington Sham Kakade Sham Kakade 2017 1 Announcements: HW3 posted Today: Review: LSH for Euclidean distance Other
The Normal Distribution & z-scores
 & z-scores Distributions: Who needs them? Why are we interested in distributions? Important link between distributions and probabilities of events If we know the distribution of a set of events, then we
& z-scores Distributions: Who needs them? Why are we interested in distributions? Important link between distributions and probabilities of events If we know the distribution of a set of events, then we
CS 231 Data Structures and Algorithms Fall Recursion and Binary Trees Lecture 21 October 24, Prof. Zadia Codabux
 CS 231 Data Structures and Algorithms Fall 2018 Recursion and Binary Trees Lecture 21 October 24, 2018 Prof. Zadia Codabux 1 Agenda ArrayQueue.java Recursion Binary Tree Terminologies Traversal 2 Administrative
CS 231 Data Structures and Algorithms Fall 2018 Recursion and Binary Trees Lecture 21 October 24, 2018 Prof. Zadia Codabux 1 Agenda ArrayQueue.java Recursion Binary Tree Terminologies Traversal 2 Administrative
Balanced Trees Part Two
 Balanced Trees Part Two Outline for Today Recap from Last Time Review of B-trees, 2-3-4 trees, and red/black trees. Order Statistic Trees BSTs with indexing. Augmented Binary Search Trees Building new
Balanced Trees Part Two Outline for Today Recap from Last Time Review of B-trees, 2-3-4 trees, and red/black trees. Order Statistic Trees BSTs with indexing. Augmented Binary Search Trees Building new
Lecture 3 February 9, 2010
 6.851: Advanced Data Structures Spring 2010 Dr. André Schulz Lecture 3 February 9, 2010 Scribe: Jacob Steinhardt and Greg Brockman 1 Overview In the last lecture we continued to study binary search trees
6.851: Advanced Data Structures Spring 2010 Dr. André Schulz Lecture 3 February 9, 2010 Scribe: Jacob Steinhardt and Greg Brockman 1 Overview In the last lecture we continued to study binary search trees
The Normal Distribution & z-scores
 & z-scores Distributions: Who needs them? Why are we interested in distributions? Important link between distributions and probabilities of events If we know the distribution of a set of events, then we
& z-scores Distributions: Who needs them? Why are we interested in distributions? Important link between distributions and probabilities of events If we know the distribution of a set of events, then we
Sequence clustering. Introduction. Clustering basics. Hierarchical clustering
 Sequence clustering Introduction Data clustering is one of the key tools used in various incarnations of data-mining - trying to make sense of large datasets. It is, thus, natural to ask whether clustering
Sequence clustering Introduction Data clustering is one of the key tools used in various incarnations of data-mining - trying to make sense of large datasets. It is, thus, natural to ask whether clustering
MITOCW watch?v=w_-sx4vr53m
 MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
An undirected graph is a tree if and only of there is a unique simple path between any 2 of its vertices.
 Trees Trees form the most widely used subclasses of graphs. In CS, we make extensive use of trees. Trees are useful in organizing and relating data in databases, file systems and other applications. Formal
Trees Trees form the most widely used subclasses of graphs. In CS, we make extensive use of trees. Trees are useful in organizing and relating data in databases, file systems and other applications. Formal
Halting Measures and Termination Arguments
 Halting Measures and Termination Arguments CS 5010 Program Design Paradigms Bootcamp Lesson 8.2 Mitchell Wand, 2012-2015 This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International
Halting Measures and Termination Arguments CS 5010 Program Design Paradigms Bootcamp Lesson 8.2 Mitchell Wand, 2012-2015 This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
STAT 598L Probabilistic Graphical Models. Instructor: Sergey Kirshner. Exact Inference
 STAT 598L Probabilistic Graphical Models Instructor: Sergey Kirshner Exact Inference What To Do With Bayesian/Markov Network? Compact representation of a complex model, but Goal: efficient extraction of
STAT 598L Probabilistic Graphical Models Instructor: Sergey Kirshner Exact Inference What To Do With Bayesian/Markov Network? Compact representation of a complex model, but Goal: efficient extraction of
TREES AND ORDERS OF GROWTH 7
 TREES AND ORDERS OF GROWTH 7 COMPUTER SCIENCE 61A October 17, 2013 1 Trees In computer science, trees are recursive data structures that are widely used in various settings. This is a diagram of a simple
TREES AND ORDERS OF GROWTH 7 COMPUTER SCIENCE 61A October 17, 2013 1 Trees In computer science, trees are recursive data structures that are widely used in various settings. This is a diagram of a simple
Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5 [talking head] This lecture we study theory design and implementation. Programmers have two roles to play here. In one role, they
Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5 [talking head] This lecture we study theory design and implementation. Programmers have two roles to play here. In one role, they
The Normal Distribution & z-scores
 & z-scores Distributions: Who needs them? Why are we interested in distributions? Important link between distributions and probabilities of events If we know the distribution of a set of events, then we
& z-scores Distributions: Who needs them? Why are we interested in distributions? Important link between distributions and probabilities of events If we know the distribution of a set of events, then we
6. Finding Efficient Compressions; Huffman and Hu-Tucker
 6. Finding Efficient Compressions; Huffman and Hu-Tucker We now address the question: how do we find a code that uses the frequency information about k length patterns efficiently to shorten our message?
6. Finding Efficient Compressions; Huffman and Hu-Tucker We now address the question: how do we find a code that uses the frequency information about k length patterns efficiently to shorten our message?
CPSC 436D Video Game Programming
 CPSC 436D Video Game Programming Strategy & Adversarial Strategy Strategy Given current state, determine BEST next move Short term: best among immediate options Long term: what brings something closest
CPSC 436D Video Game Programming Strategy & Adversarial Strategy Strategy Given current state, determine BEST next move Short term: best among immediate options Long term: what brings something closest
CS 231: Algorithmic Problem Solving
 CS 231: Algorithmic Problem Solving Naomi Nishimura Module 7 Date of this version: January 28, 2019 WARNING: Drafts of slides are made available prior to lecture for your convenience. After lecture, slides
CS 231: Algorithmic Problem Solving Naomi Nishimura Module 7 Date of this version: January 28, 2019 WARNING: Drafts of slides are made available prior to lecture for your convenience. After lecture, slides
INF2220: algorithms and data structures Series 1
 Universitetet i Oslo Institutt for Informatikk A. Maus, R.K. Runde, I. Yu INF2220: algorithms and data structures Series 1 Topic Trees & estimation of running time (Exercises with hints for solution) Issued:
Universitetet i Oslo Institutt for Informatikk A. Maus, R.K. Runde, I. Yu INF2220: algorithms and data structures Series 1 Topic Trees & estimation of running time (Exercises with hints for solution) Issued:
Algorithms. AVL Tree
 Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
We will show that the height of a RB tree on n vertices is approximately 2*log n. In class I presented a simple structural proof of this claim:
 We have seen that the insert operation on a RB takes an amount of time proportional to the number of the levels of the tree (since the additional operations required to do any rebalancing require constant
We have seen that the insert operation on a RB takes an amount of time proportional to the number of the levels of the tree (since the additional operations required to do any rebalancing require constant
Dynamic Programming: Widget Layout
 Dynamic Programming: Widget Layout Setup There are two types of widgets. A leaf widget is a visible widget that someone may see or use, such as a button or an image. Every leaf widget has a list of possible
Dynamic Programming: Widget Layout Setup There are two types of widgets. A leaf widget is a visible widget that someone may see or use, such as a button or an image. Every leaf widget has a list of possible
Lecture 5. Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
 Lecture 5 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs Reading: Randomized Search Trees by Aragon & Seidel, Algorithmica 1996, http://sims.berkeley.edu/~aragon/pubs/rst96.pdf;
Lecture 5 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs Reading: Randomized Search Trees by Aragon & Seidel, Algorithmica 1996, http://sims.berkeley.edu/~aragon/pubs/rst96.pdf;
Exact Inference: Elimination and Sum Product (and hidden Markov models)
 Exact Inference: Elimination and Sum Product (and hidden Markov models) David M. Blei Columbia University October 13, 2015 The first sections of these lecture notes follow the ideas in Chapters 3 and 4
Exact Inference: Elimination and Sum Product (and hidden Markov models) David M. Blei Columbia University October 13, 2015 The first sections of these lecture notes follow the ideas in Chapters 3 and 4
Evolutionary tree reconstruction (Chapter 10)
 Evolutionary tree reconstruction (Chapter 10) Early Evolutionary Studies Anatomical features were the dominant criteria used to derive evolutionary relationships between species since Darwin till early
Evolutionary tree reconstruction (Chapter 10) Early Evolutionary Studies Anatomical features were the dominant criteria used to derive evolutionary relationships between species since Darwin till early
Getting to places from my house...
 Reductions, Self-Similarity, and Recursion Relations between problems Notes for CSC 100 - The Beauty and Joy of Computing The University of North Carolina at Greensboro Getting to places from my house...
Reductions, Self-Similarity, and Recursion Relations between problems Notes for CSC 100 - The Beauty and Joy of Computing The University of North Carolina at Greensboro Getting to places from my house...
Analysis of Algorithms - Greedy algorithms -
 Analysis of Algorithms - Greedy algorithms - Andreas Ermedahl MRTC (Mälardalens Real-Time Reseach Center) andreas.ermedahl@mdh.se Autumn 2003 Greedy Algorithms Another paradigm for designing algorithms
Analysis of Algorithms - Greedy algorithms - Andreas Ermedahl MRTC (Mälardalens Real-Time Reseach Center) andreas.ermedahl@mdh.se Autumn 2003 Greedy Algorithms Another paradigm for designing algorithms
Balanced Search Trees
 Balanced Search Trees Computer Science E-22 Harvard Extension School David G. Sullivan, Ph.D. Review: Balanced Trees A tree is balanced if, for each node, the node s subtrees have the same height or have
Balanced Search Trees Computer Science E-22 Harvard Extension School David G. Sullivan, Ph.D. Review: Balanced Trees A tree is balanced if, for each node, the node s subtrees have the same height or have
Name: Lirong TAN 1. (15 pts) (a) Define what is a shortest s-t path in a weighted, connected graph G.
 1. (15 pts) (a) Define what is a shortest s-t path in a weighted, connected graph G. A shortest s-t path is a path from vertex to vertex, whose sum of edge weights is minimized. (b) Give the pseudocode
1. (15 pts) (a) Define what is a shortest s-t path in a weighted, connected graph G. A shortest s-t path is a path from vertex to vertex, whose sum of edge weights is minimized. (b) Give the pseudocode
Outline for Today. How can we speed up operations that work on integer data? A simple data structure for ordered dictionaries.
 van Emde Boas Trees Outline for Today Data Structures on Integers How can we speed up operations that work on integer data? Tiered Bitvectors A simple data structure for ordered dictionaries. van Emde
van Emde Boas Trees Outline for Today Data Structures on Integers How can we speed up operations that work on integer data? Tiered Bitvectors A simple data structure for ordered dictionaries. van Emde
B-Trees. CS321 Spring 2014 Steve Cutchin
 B-Trees CS321 Spring 2014 Steve Cutchin Topics for Today HW #2 Once Over B Trees Questions PA #3 Expression Trees Balance Factor AVL Heights Data Structure Animations Graphs 2 B-Tree Motivation When data
B-Trees CS321 Spring 2014 Steve Cutchin Topics for Today HW #2 Once Over B Trees Questions PA #3 Expression Trees Balance Factor AVL Heights Data Structure Animations Graphs 2 B-Tree Motivation When data
6.001 Notes: Section 15.1
 6.001 Notes: Section 15.1 Slide 15.1.1 Our goal over the next few lectures is to build an interpreter, which in a very basic sense is the ultimate in programming, since doing so will allow us to define
6.001 Notes: Section 15.1 Slide 15.1.1 Our goal over the next few lectures is to build an interpreter, which in a very basic sense is the ultimate in programming, since doing so will allow us to define
Computer Vision Group Prof. Daniel Cremers. 4a. Inference in Graphical Models
 Group Prof. Daniel Cremers 4a. Inference in Graphical Models Inference on a Chain (Rep.) The first values of µ α and µ β are: The partition function can be computed at any node: Overall, we have O(NK 2
Group Prof. Daniel Cremers 4a. Inference in Graphical Models Inference on a Chain (Rep.) The first values of µ α and µ β are: The partition function can be computed at any node: Overall, we have O(NK 2
Data Structures. Oliver-Matis Lill. June 6, 2017
 June 6, 2017 Session Structure First I will hold a short lecture on the subject Rest of the time is spent on problem solving Try to nish the standard problems at home if necessary Topics Session subjects
June 6, 2017 Session Structure First I will hold a short lecture on the subject Rest of the time is spent on problem solving Try to nish the standard problems at home if necessary Topics Session subjects
Math 15 - Spring Homework 5.2 Solutions
 Math 15 - Spring 2017 - Homework 5.2 Solutions 1. (5.2 # 14 (not assigned)) Use Prim s algorithm to construct a minimal spanning tree for the following network. Draw the minimal tree and compute its total
Math 15 - Spring 2017 - Homework 5.2 Solutions 1. (5.2 # 14 (not assigned)) Use Prim s algorithm to construct a minimal spanning tree for the following network. Draw the minimal tree and compute its total
Algorithm classification
 Types of Algorithms Algorithm classification Algorithms that use a similar problem-solving approach can be grouped together We ll talk about a classification scheme for algorithms This classification scheme
Types of Algorithms Algorithm classification Algorithms that use a similar problem-solving approach can be grouped together We ll talk about a classification scheme for algorithms This classification scheme
So on the survey, someone mentioned they wanted to work on heaps, and someone else mentioned they wanted to work on balanced binary search trees.
 So on the survey, someone mentioned they wanted to work on heaps, and someone else mentioned they wanted to work on balanced binary search trees. According to the 161 schedule, heaps were last week, hashing
So on the survey, someone mentioned they wanted to work on heaps, and someone else mentioned they wanted to work on balanced binary search trees. According to the 161 schedule, heaps were last week, hashing
Part II. C. M. Bishop PATTERN RECOGNITION AND MACHINE LEARNING CHAPTER 8: GRAPHICAL MODELS
 Part II C. M. Bishop PATTERN RECOGNITION AND MACHINE LEARNING CHAPTER 8: GRAPHICAL MODELS Converting Directed to Undirected Graphs (1) Converting Directed to Undirected Graphs (2) Add extra links between
Part II C. M. Bishop PATTERN RECOGNITION AND MACHINE LEARNING CHAPTER 8: GRAPHICAL MODELS Converting Directed to Undirected Graphs (1) Converting Directed to Undirected Graphs (2) Add extra links between
CS61B Lecture #21: Tree Searching. Last modified: Wed Oct 12 19:23: CS61B: Lecture #21 1
 CS61B Lecture #21: Tree Searching Last modified: Wed Oct 12 19:23:14 2016 CS61B: Lecture #21 1 Divide and Conquer Much (most?) computation is devoted to finding things in response to various forms of query.
CS61B Lecture #21: Tree Searching Last modified: Wed Oct 12 19:23:14 2016 CS61B: Lecture #21 1 Divide and Conquer Much (most?) computation is devoted to finding things in response to various forms of query.
CAD Algorithms. Categorizing Algorithms
 CAD Algorithms Categorizing Algorithms Mohammad Tehranipoor ECE Department 2 September 2008 1 Categorizing Algorithms Greedy Algorithms Prim s Algorithm (Minimum Spanning Tree) A subgraph that is a tree
CAD Algorithms Categorizing Algorithms Mohammad Tehranipoor ECE Department 2 September 2008 1 Categorizing Algorithms Greedy Algorithms Prim s Algorithm (Minimum Spanning Tree) A subgraph that is a tree
Algorithm Theory, Winter Term 2015/16 Problem Set 5 - Sample Solution
 Albert-Ludwigs-Universität, Inst. für Informatik Prof. Dr. Fabian Kuhn M. Ahmadi, O. Saukh, A. R. Molla November, 20 Algorithm Theory, Winter Term 20/6 Problem Set - Sample Solution Exercise : Amortized
Albert-Ludwigs-Universität, Inst. für Informatik Prof. Dr. Fabian Kuhn M. Ahmadi, O. Saukh, A. R. Molla November, 20 Algorithm Theory, Winter Term 20/6 Problem Set - Sample Solution Exercise : Amortized
Binary Heaps in Dynamic Arrays
 Yufei Tao ITEE University of Queensland We have already learned that the binary heap serves as an efficient implementation of a priority queue. Our previous discussion was based on pointers (for getting
Yufei Tao ITEE University of Queensland We have already learned that the binary heap serves as an efficient implementation of a priority queue. Our previous discussion was based on pointers (for getting
Greedy Algorithms. Previous Examples: Huffman coding, Minimum Spanning Tree Algorithms
 Greedy Algorithms A greedy algorithm is one where you take the step that seems the best at the time while executing the algorithm. Previous Examples: Huffman coding, Minimum Spanning Tree Algorithms Coin
Greedy Algorithms A greedy algorithm is one where you take the step that seems the best at the time while executing the algorithm. Previous Examples: Huffman coding, Minimum Spanning Tree Algorithms Coin
Hi everyone. I hope everyone had a good Fourth of July. Today we're going to be covering graph search. Now, whenever we bring up graph algorithms, we
 Hi everyone. I hope everyone had a good Fourth of July. Today we're going to be covering graph search. Now, whenever we bring up graph algorithms, we have to talk about the way in which we represent the
Hi everyone. I hope everyone had a good Fourth of July. Today we're going to be covering graph search. Now, whenever we bring up graph algorithms, we have to talk about the way in which we represent the
Math 4242 Fibonacci, Memoization lecture 13
 Math 4242 Fibonacci, Memoization lecture 13 Today we talk about a problem that sometimes occurs when using recursion, and a common way to fix it. Recall the Fibonacci sequence (F 1, F 2,...) that occurs
Math 4242 Fibonacci, Memoization lecture 13 Today we talk about a problem that sometimes occurs when using recursion, and a common way to fix it. Recall the Fibonacci sequence (F 1, F 2,...) that occurs
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/27/17
 01.433/33 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/2/1.1 Introduction In this lecture we ll talk about a useful abstraction, priority queues, which are
01.433/33 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/2/1.1 Introduction In this lecture we ll talk about a useful abstraction, priority queues, which are
Computational Optimization ISE 407. Lecture 16. Dr. Ted Ralphs
 Computational Optimization ISE 407 Lecture 16 Dr. Ted Ralphs ISE 407 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms in
Computational Optimization ISE 407 Lecture 16 Dr. Ted Ralphs ISE 407 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms in
CS 380/480 Foundations of Artificial Intelligence Winter 2007 Assignment 2 Solutions to Selected Problems
 CS 380/480 Foundations of Artificial Intelligence Winter 2007 Assignment 2 Solutions to Selected Problems 1. Search trees for the state-space graph given below: We only show the search trees corresponding
CS 380/480 Foundations of Artificial Intelligence Winter 2007 Assignment 2 Solutions to Selected Problems 1. Search trees for the state-space graph given below: We only show the search trees corresponding
Best-First Search! Minimizing Space or Time!! RBFS! Save space, take more time!
 Best-First Search! Minimizing Space or Time!! RBFS! Save space, take more time! RBFS-1 RBFS general properties! Similar to A* algorithm developed for heuristic search! RBFS-2 RBFS general properties 2!
Best-First Search! Minimizing Space or Time!! RBFS! Save space, take more time! RBFS-1 RBFS general properties! Similar to A* algorithm developed for heuristic search! RBFS-2 RBFS general properties 2!
Graphing and Equations
 Graphing and Equations Plotting Functions (Graphing) Let's see how to plot the graphs of functions. If we want to graph the function f(x) on the interval [a,b] then we type in: plot(f(x), x=a..b) That
Graphing and Equations Plotting Functions (Graphing) Let's see how to plot the graphs of functions. If we want to graph the function f(x) on the interval [a,b] then we type in: plot(f(x), x=a..b) That
Minimum spanning trees
 Carlos Moreno cmoreno @ uwaterloo.ca EI-3 https://ece.uwaterloo.ca/~cmoreno/ece5 Standard reminder to set phones to silent/vibrate mode, please! During today's lesson: Introduce the notion of spanning
Carlos Moreno cmoreno @ uwaterloo.ca EI-3 https://ece.uwaterloo.ca/~cmoreno/ece5 Standard reminder to set phones to silent/vibrate mode, please! During today's lesson: Introduce the notion of spanning
D-Separation. b) the arrows meet head-to-head at the node, and neither the node, nor any of its descendants, are in the set C.
 D-Separation Say: A, B, and C are non-intersecting subsets of nodes in a directed graph. A path from A to B is blocked by C if it contains a node such that either a) the arrows on the path meet either
D-Separation Say: A, B, and C are non-intersecting subsets of nodes in a directed graph. A path from A to B is blocked by C if it contains a node such that either a) the arrows on the path meet either
CSE100. Advanced Data Structures. Lecture 8. (Based on Paul Kube course materials)
 CSE100 Advanced Data Structures Lecture 8 (Based on Paul Kube course materials) CSE 100 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
CSE100 Advanced Data Structures Lecture 8 (Based on Paul Kube course materials) CSE 100 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
Last week. Another example. More recursive examples. How about these functions? Recursive programs. CSC148 Intro. to Computer Science
 CSC48 Intro. to Computer Science Lecture 7: Recursive Functions/Structures Trees mir H. Chinaei, Summer 206 Office Hours: R 0-2 B4222 ahchinaei@cs.toronto.edu http://www.cs.toronto.edu/~ahchinaei/ Course
CSC48 Intro. to Computer Science Lecture 7: Recursive Functions/Structures Trees mir H. Chinaei, Summer 206 Office Hours: R 0-2 B4222 ahchinaei@cs.toronto.edu http://www.cs.toronto.edu/~ahchinaei/ Course
13.4 Deletion in red-black trees
 Deletion in a red-black tree is similar to insertion. Apply the deletion algorithm for binary search trees. Apply node color changes and left/right rotations to fix the violations of RBT tree properties.
Deletion in a red-black tree is similar to insertion. Apply the deletion algorithm for binary search trees. Apply node color changes and left/right rotations to fix the violations of RBT tree properties.
CSE 417 Branch & Bound (pt 4) Branch & Bound
 CSE 417 Branch & Bound (pt 4) Branch & Bound Reminders > HW8 due today > HW9 will be posted tomorrow start early program will be slow, so debugging will be slow... Review of previous lectures > Complexity
CSE 417 Branch & Bound (pt 4) Branch & Bound Reminders > HW8 due today > HW9 will be posted tomorrow start early program will be slow, so debugging will be slow... Review of previous lectures > Complexity
6.001 Notes: Section 31.1
 6.001 Notes: Section 31.1 Slide 31.1.1 In previous lectures we have seen a number of important themes, which relate to designing code for complex systems. One was the idea of proof by induction, meaning
6.001 Notes: Section 31.1 Slide 31.1.1 In previous lectures we have seen a number of important themes, which relate to designing code for complex systems. One was the idea of proof by induction, meaning
LECTURE NOTES OF ALGORITHMS: DESIGN TECHNIQUES AND ANALYSIS
 Department of Computer Science University of Babylon LECTURE NOTES OF ALGORITHMS: DESIGN TECHNIQUES AND ANALYSIS By Faculty of Science for Women( SCIW), University of Babylon, Iraq Samaher@uobabylon.edu.iq
Department of Computer Science University of Babylon LECTURE NOTES OF ALGORITHMS: DESIGN TECHNIQUES AND ANALYSIS By Faculty of Science for Women( SCIW), University of Babylon, Iraq Samaher@uobabylon.edu.iq
Solutions. (a) Claim: A d-ary tree of height h has at most 1 + d +...
 Design and Analysis of Algorithms nd August, 016 Problem Sheet 1 Solutions Sushant Agarwal Solutions 1. A d-ary tree is a rooted tree in which each node has at most d children. Show that any d-ary tree
Design and Analysis of Algorithms nd August, 016 Problem Sheet 1 Solutions Sushant Agarwal Solutions 1. A d-ary tree is a rooted tree in which each node has at most d children. Show that any d-ary tree
Notes 4 : Approximating Maximum Parsimony
 Notes 4 : Approximating Maximum Parsimony MATH 833 - Fall 2012 Lecturer: Sebastien Roch References: [SS03, Chapters 2, 5], [DPV06, Chapters 5, 9] 1 Coping with NP-completeness Local search heuristics.
Notes 4 : Approximating Maximum Parsimony MATH 833 - Fall 2012 Lecturer: Sebastien Roch References: [SS03, Chapters 2, 5], [DPV06, Chapters 5, 9] 1 Coping with NP-completeness Local search heuristics.
(Refer Slide Time: 05:25)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering IIT Delhi Lecture 30 Applications of DFS in Directed Graphs Today we are going to look at more applications
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering IIT Delhi Lecture 30 Applications of DFS in Directed Graphs Today we are going to look at more applications
Last week: Breadth-First Search
 1 Last week: Breadth-First Search Set L i = [] for i=1,,n L 0 = {w}, where w is the start node For i = 0,, n-1: For u in L i : For each v which is a neighbor of u: If v isn t yet visited: - mark v as visited,
1 Last week: Breadth-First Search Set L i = [] for i=1,,n L 0 = {w}, where w is the start node For i = 0,, n-1: For u in L i : For each v which is a neighbor of u: If v isn t yet visited: - mark v as visited,
Lecture 6. Binary Search Trees and Red-Black Trees
 Lecture Binary Search Trees and Red-Black Trees Sorting out the past couple of weeks: We ve seen a bunch of sorting algorithms InsertionSort - Θ n 2 MergeSort - Θ n log n QuickSort - Θ n log n expected;
Lecture Binary Search Trees and Red-Black Trees Sorting out the past couple of weeks: We ve seen a bunch of sorting algorithms InsertionSort - Θ n 2 MergeSort - Θ n log n QuickSort - Θ n log n expected;
Machine Learning
 Machine Learning 10-601 Tom M. Mitchell Machine Learning Department Carnegie Mellon University April 1, 2019 Today: Inference in graphical models Learning graphical models Readings: Bishop chapter 8 Bayesian
Machine Learning 10-601 Tom M. Mitchell Machine Learning Department Carnegie Mellon University April 1, 2019 Today: Inference in graphical models Learning graphical models Readings: Bishop chapter 8 Bayesian
PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between
 MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
13.4 Deletion in red-black trees
 The operation of Deletion in a red-black tree is similar to the operation of Insertion on the tree. That is, apply the deletion algorithm for binary search trees to delete a node z; apply node color changes
The operation of Deletion in a red-black tree is similar to the operation of Insertion on the tree. That is, apply the deletion algorithm for binary search trees to delete a node z; apply node color changes
Module 9: Binary trees
 Module 9: Binary trees Readings: HtDP, Section 14 We will cover the ideas in the text using different examples and different terminology. The readings are still important as an additional source of examples.
Module 9: Binary trees Readings: HtDP, Section 14 We will cover the ideas in the text using different examples and different terminology. The readings are still important as an additional source of examples.
Algorithms and Data Structures
 Algorithms and Data Structures Optimal Search Trees; Tries Marius Kloft Static Key Sets Sometimes, the set of keys is fixed Streets of a city, cities in a country, keywords of a prog. lang., Softer: Searches
Algorithms and Data Structures Optimal Search Trees; Tries Marius Kloft Static Key Sets Sometimes, the set of keys is fixed Streets of a city, cities in a country, keywords of a prog. lang., Softer: Searches
Algorithms in Systems Engineering ISE 172. Lecture 16. Dr. Ted Ralphs
 Algorithms in Systems Engineering ISE 172 Lecture 16 Dr. Ted Ralphs ISE 172 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms
Algorithms in Systems Engineering ISE 172 Lecture 16 Dr. Ted Ralphs ISE 172 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms
Improving Depth-first PN-Search: 1 + ε Trick
 Improving Depth-first PN-Search: 1 + ε Trick Jakub Pawlewicz, Łukasz Lew {pan,lew}@mimuw.edu.pl Institute of Informatics, Warsaw University Banacha 2, 02-097 Warsaw, Poland Abstract. Various efficient
Improving Depth-first PN-Search: 1 + ε Trick Jakub Pawlewicz, Łukasz Lew {pan,lew}@mimuw.edu.pl Institute of Informatics, Warsaw University Banacha 2, 02-097 Warsaw, Poland Abstract. Various efficient
Greedy Algorithms. Alexandra Stefan
 Greedy Algorithms Alexandra Stefan 1 Greedy Method for Optimization Problems Greedy: take the action that is best now (out of the current options) it may cause you to miss the optimal solution You build
Greedy Algorithms Alexandra Stefan 1 Greedy Method for Optimization Problems Greedy: take the action that is best now (out of the current options) it may cause you to miss the optimal solution You build
1. Meshes. D7013E Lecture 14
 D7013E Lecture 14 Quadtrees Mesh Generation 1. Meshes Input: Components in the form of disjoint polygonal objects Integer coordinates, 0, 45, 90, or 135 angles Output: A triangular mesh Conforming: A triangle
D7013E Lecture 14 Quadtrees Mesh Generation 1. Meshes Input: Components in the form of disjoint polygonal objects Integer coordinates, 0, 45, 90, or 135 angles Output: A triangular mesh Conforming: A triangle
6.001 Notes: Section 4.1
 6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
Dynamic Programming for Phylogenetic Estimation
 1 / 45 Dynamic Programming for Phylogenetic Estimation CS598AGB Pranjal Vachaspati University of Illinois at Urbana-Champaign 2 / 45 Coalescent-based Species Tree Estimation Find evolutionary tree for
1 / 45 Dynamic Programming for Phylogenetic Estimation CS598AGB Pranjal Vachaspati University of Illinois at Urbana-Champaign 2 / 45 Coalescent-based Species Tree Estimation Find evolutionary tree for
1 Dynamic Programming
 Recitation 13 Dynamic Programming Parallel and Sequential Data Structures and Algorithms, 15-210 (Fall 2013) November 20, 2013 1 Dynamic Programming Dynamic programming is a technique to avoid needless
Recitation 13 Dynamic Programming Parallel and Sequential Data Structures and Algorithms, 15-210 (Fall 2013) November 20, 2013 1 Dynamic Programming Dynamic programming is a technique to avoid needless
Binary Search Trees, etc.
 Chapter 12 Binary Search Trees, etc. Binary Search trees are data structures that support a variety of dynamic set operations, e.g., Search, Minimum, Maximum, Predecessors, Successors, Insert, and Delete.
Chapter 12 Binary Search Trees, etc. Binary Search trees are data structures that support a variety of dynamic set operations, e.g., Search, Minimum, Maximum, Predecessors, Successors, Insert, and Delete.
CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators)
 Name: Email address: Quiz Section: CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
Name: Email address: Quiz Section: CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
CSE 431/531: Analysis of Algorithms. Greedy Algorithms. Lecturer: Shi Li. Department of Computer Science and Engineering University at Buffalo
 CSE 431/531: Analysis of Algorithms Greedy Algorithms Lecturer: Shi Li Department of Computer Science and Engineering University at Buffalo Main Goal of Algorithm Design Design fast algorithms to solve
CSE 431/531: Analysis of Algorithms Greedy Algorithms Lecturer: Shi Li Department of Computer Science and Engineering University at Buffalo Main Goal of Algorithm Design Design fast algorithms to solve
CS 3114 Data Structures and Algorithms READ THIS NOW!
 READ THIS NOW! Print your name in the space provided below. There are 7 short-answer questions, priced as marked. The maximum score is 100. This examination is closed book and closed notes, aside from
READ THIS NOW! Print your name in the space provided below. There are 7 short-answer questions, priced as marked. The maximum score is 100. This examination is closed book and closed notes, aside from
Horn Formulae. CS124 Course Notes 8 Spring 2018
 CS124 Course Notes 8 Spring 2018 In today s lecture we will be looking a bit more closely at the Greedy approach to designing algorithms. As we will see, sometimes it works, and sometimes even when it
CS124 Course Notes 8 Spring 2018 In today s lecture we will be looking a bit more closely at the Greedy approach to designing algorithms. As we will see, sometimes it works, and sometimes even when it
15-110: Principles of Computing, Spring 2018
 15-110: Principles of Computing, Spring 2018 Programming Assignment 11 (PA11) Due: Tuesday, May 1 by 9PM IMPORTANT ANNOUNCEMENT You cant drop this assignment even if it is your lowest PA score. Failure
15-110: Principles of Computing, Spring 2018 Programming Assignment 11 (PA11) Due: Tuesday, May 1 by 9PM IMPORTANT ANNOUNCEMENT You cant drop this assignment even if it is your lowest PA score. Failure
1 Format. 2 Topics Covered. 2.1 Minimal Spanning Trees. 2.2 Union Find. 2.3 Greedy. CS 124 Quiz 2 Review 3/25/18
 CS 124 Quiz 2 Review 3/25/18 1 Format You will have 83 minutes to complete the exam. The exam may have true/false questions, multiple choice, example/counterexample problems, run-this-algorithm problems,
CS 124 Quiz 2 Review 3/25/18 1 Format You will have 83 minutes to complete the exam. The exam may have true/false questions, multiple choice, example/counterexample problems, run-this-algorithm problems,
Module 05: Types of recursion
 Module 05: Types of recursion Topics: Review of purely structural recursion Accumulative recursion Generative recursion Readings:ThinkP 5.8-5.10, 6.5-6.7 1 Review: Structural Recursion Template for code
Module 05: Types of recursion Topics: Review of purely structural recursion Accumulative recursion Generative recursion Readings:ThinkP 5.8-5.10, 6.5-6.7 1 Review: Structural Recursion Template for code
2017 ACM ICPC ASIA, INDIA REGIONAL ONLINE CONTEST
 Official Problem Set 017 ACM ICPC ASIA, INDIA REGIONAL ONLINE CONTEST 1 Problem code: EQUALMOD Problem name: Modulo Equality You have two arrays A and B, each containing N integers. Elements of array B
Official Problem Set 017 ACM ICPC ASIA, INDIA REGIONAL ONLINE CONTEST 1 Problem code: EQUALMOD Problem name: Modulo Equality You have two arrays A and B, each containing N integers. Elements of array B
One report (in pdf format) addressing each of following questions.
 MSCBIO 2070/02-710: Computational Genomics, Spring 2016 HW1: Sequence alignment and Evolution Due: 24:00 EST, Feb 15, 2016 by autolab Your goals in this assignment are to 1. Complete a genome assembler
MSCBIO 2070/02-710: Computational Genomics, Spring 2016 HW1: Sequence alignment and Evolution Due: 24:00 EST, Feb 15, 2016 by autolab Your goals in this assignment are to 1. Complete a genome assembler
CSE 326: Data Structures Lecture #11 B-Trees
 CSE 326: Data Structures Lecture #11 B-Trees Alon Halevy Spring Quarter 2001 B-Tree Properties Properties maximum branching factor of M the root has between 2 and M children other internal nodes have between!m/2"
CSE 326: Data Structures Lecture #11 B-Trees Alon Halevy Spring Quarter 2001 B-Tree Properties Properties maximum branching factor of M the root has between 2 and M children other internal nodes have between!m/2"
1.1 - Functions, Domain, and Range
 1.1 - Functions, Domain, and Range Lesson Outline Section 1: Difference between relations and functions Section 2: Use the vertical line test to check if it is a relation or a function Section 3: Domain
1.1 - Functions, Domain, and Range Lesson Outline Section 1: Difference between relations and functions Section 2: Use the vertical line test to check if it is a relation or a function Section 3: Domain
Here is a recursive algorithm that solves this problem, given a pointer to the root of T : MaxWtSubtree [r]
![Here is a recursive algorithm that solves this problem, given a pointer to the root of T : MaxWtSubtree [r] Here is a recursive algorithm that solves this problem, given a pointer to the root of T : MaxWtSubtree [r]](/thumbs/79/79323586.jpg) CSE 101 Final Exam Topics: Order, Recurrence Relations, Analyzing Programs, Divide-and-Conquer, Back-tracking, Dynamic Programming, Greedy Algorithms and Correctness Proofs, Data Structures (Heap, Binary
CSE 101 Final Exam Topics: Order, Recurrence Relations, Analyzing Programs, Divide-and-Conquer, Back-tracking, Dynamic Programming, Greedy Algorithms and Correctness Proofs, Data Structures (Heap, Binary
Algorithm Design Techniques (III)
 Algorithm Design Techniques (III) Minimax. Alpha-Beta Pruning. Search Tree Strategies (backtracking revisited, branch and bound). Local Search. DSA - lecture 10 - T.U.Cluj-Napoca - M. Joldos 1 Tic-Tac-Toe
Algorithm Design Techniques (III) Minimax. Alpha-Beta Pruning. Search Tree Strategies (backtracking revisited, branch and bound). Local Search. DSA - lecture 10 - T.U.Cluj-Napoca - M. Joldos 1 Tic-Tac-Toe
