Combining cellular automata and local binary patterns for copy-move forgery detection. Dijana Tralic, Sonja Grgic, Xianfang Sun & Paul L.
|
|
|
- John Ford
- 5 years ago
- Views:
Transcription
1 Combining cellular automata and local binary patterns for copy-move forgery detection Dijana Tralic, Sonja Grgic, Xianfang Sun Paul L. Rosin Multimedia Tools and Applications An International Journal ISSN DOI /s
2 Your article is protected by copyright and all rights are held exclusively by Springer Science +Business Media New York. This e-offprint is for personal use only and shall not be selfarchived in electronic repositories. If you wish to self-archive your article, please use the accepted manuscript version for posting on your own website. You may further deposit the accepted manuscript version in any repository, provided it is only made publicly available 12 months after official publication or later and provided acknowledgement is given to the original source of publication and a link is inserted to the published article on Springer's website. The link must be accompanied by the following text: "The final publication is available at link.springer.com. 1 23
3 DOI /s Combining cellular automata and local binary patterns for copy-move forgery detection Dijana Tralic 1 Sonja Grgic 1 Xianfang Sun 2 Paul L. Rosin 2 Received: 17 April 2015 / Revised: 22 July 2015 / Accepted: 18 September 2015 # Springer Science+Business Media New York 2015 Abstract Detection of duplicated regions in digital images has been a highly investigated field in recent years since the editing of digital images has been notably simplified by the development of advanced image processing tools. In this paper, we present a new method that combines Cellular Automata (CA) and Local Binary Patterns (LBP) to extract feature vectors for the purpose of detection of duplicated regions. The combination of CA and LBP allows a simple and reduced description of texture in the form of CA rules that represents local changes in pixel luminance values. The importance of CA lies in the fact that a very simple set of rules can be used to describe complex textures, while LBP, applied locally, allows efficient binary representation. CA rules are formed on a circular neighborhood, resulting in insensitivity to rotation of duplicated regions. Additionally, a new search method is applied to select the nearest neighbors and determine duplicated blocks. In comparison with similar methods, the proposed method showed good performance in the case of plain/multiple copy-move forgeries and rotation/scaling of duplicated regions, as well as robustness to post-processing methods such as blurring, addition of noise and JPEG compression. An important advantage of the proposed method is its low computational complexity and simplicity of its feature vector representation. Keywords Copy-move forgery. Duplicated regions. Cellular automata. Local binary pattern * Dijana Tralic dijana.tralic@fer.hr 1 2 Faculty of Electrical Engineering and Computing, University of Zagreb, Unska 3/XII, HR Zagreb, Croatia School of Computer Science and Informatics, Cardiff University, Cardiff CF24 3AA, UK
4 1 Introduction Digital images are nowadays commonly used thanks to the simplicity of their acquisition, sharing, storing and editing. Many advanced processing tools allow editing of digital image without any visible traces, leading to the fact that digital images cannot be trusted any more [8]. Copy-move forgery (CMF) is one type of digital image forgerymethodsinwhichpartofanimageisselected,copiedandmovedtoanew location in the same image [7] with the aim of adding or hiding an object. Digital image forensic [17], whose goal is to distinguish edited images from original images and discover any changes of image content, has two common approaches in the field of CMF detection. Active methods require the embedding of some information in the digital image in the process of its creation, such as digital signatures or watermarks [4]. Passive methods, on the other hand, do not require any additional data since they are based on analyzing properties of the image [10] such as sensor noise, illumination, statistical properties, etc. Many different passive approaches were proposed for CMF detection based on defining feature sets of small, overlapping blocks of the image [2, 3, 6, 9, 11 13, 16, 19, 22, 26] orkeypoints[1, 5, 20]. A detection method based on Local Binary Patterns (LBP) [15] was introduced by Li et al. [11]. This approach was extended with Multi-resolution LBP (MLBP) [22]. The method showed good performance in the case of rotation, scaling, JPEG compression, blurring and noise addition. However, use of MLBP for feature set generation leads to large feature sets. To reduce the complexity of feature sets, 1D Cellular Automata (CA) [18] are used to generate feature sets as a binary array representing CA rules [23, 24]. 1D CA implies using pixels from one row of an image to learn the pixel s value in the next row of the image. However, the method was sensitive to rotation of duplicated regions due to the use of 1D neighborhoods and showed weak robustness to post-processing methods due to the applied search method based on lexicographic sorting. This paper presents a new idea of combining LBP with CA for the purpose of CMF detection based on circular neighborhoods. Prior to the detection process, an image is divided into small, overlapping blocks. A circular neighborhood is formed for each block by defining circles of different radii around the block s central pixel and by sampling points on those circles using bilinear interpolation. The sampled points are used to form small neighborhoods in such a way that points from one angle are used to learn point value on the next angle. However, use of point values as an input to CA leads to a combinatorial explosion in the number of possible rules. To cope with that, a reduced description of point values based on LBP is applied locally on every neighborhood in each block. The feature vector is defined as a binary array where each element describes the use of a specific binary pattern. Furthermore, the Fast Library for Approximate Nearest Neighbors (FLANN) [14] is used to select nearest neighbors for every feature vector allowing better performance of the postprocessing methods. A new search method based on analysis of spatial relationships between detected blocks is applied to identify true duplicated block pairs. The rest of the paper is organized as follows. In Section 2, the brief background about CA and LBP is given. Section 3 presents a new approach with explanation of feature vector and detection method. Testing setup is given in Section 4 and experimental results are presented in Section 5. The conclusion is provided in Section 6.
5 2Background In this section, a brief introduction to cellular automata and local binary patterns is given to illustrate their role in texture description for the purpose of CMF detection. 2.1 Cellular automata A cellular automaton [18] is a discrete system containing a regular grid of cells whose states can be in only one finite-state set. The use of CA for image processing is interesting because of its property that very simple CA rules can result in very complex behavior, so it can be used for texture description. ACAcanbepresentedbyaquadruple<C, S, N, f> wherec is a d-dimensional cellular space that consists of c cells, S is an s-value state space, N is an n-cell CA neighborhood, and f:s n S is a cell-state transition function [21]. Each observed cell c o is in one finite state s o determined by the states of a surrounding neighborhood of cells N(c o ), usually spatially close to the cell c o. The state of each cell in the next time step is defined using a transition function f, which can be represented by a set of rules. Each rule defines the next state of the observed cell c o corresponding to a specific combination of the neighborhood cells values, called neighborhood pattern, and is represented as if Nc ð o Þ ¼ fs 1 ; s 2 ; ; s n g then c o ¼ s o ð1þ Application of CA to digital images is possible using the following hypothesis: Set C is a 2-dimensional image that consists of X Y pixels (each pixel p i is one cell c i so cell c will be marked with p), Set S contains all possible pixel values (s=256 for 8-bit images or s=2 for binary images); Set N(p o ) is an arbitrarily selected group of n pixels spatially close to the observed pixel p o, Function f is defined by a set of rules in a way that it represents the connection of a pattern in the selected neighborhood N(p o ) and the value of the observed pixel p o. For example, rule 0 means that all combinations of neighboring elements (s n possible patterns) result in value of the observed pixel p o equal to 0 (more details in Subsection 3.1). By analyzing an image or region, it is possible to select a subset of s n possible patterns (combinations of neighboring elements) that describes local changes of pixels luminance values, e.g., it is possible to define a rule that can be used to generate a specific texture. Detection of duplicated regions is based on the fact that similar areas in an image should produce similar rules. 2.2 Local binary pattern Local Binary Pattern (LBP) [15] is a simple texture descriptor that transforms an image into a set of labels that describe the appearance of the image luminance values. A very important property of LBP, which is based on a local pattern and texture, is gray-scale invariance. The LBP of a neighborhood P with radius r is obtained by using the value of the central pixel p c of P as the threshold to define the values of the m neighborhood pixels located within radius r
6 around the central pixel p c. The binary values of the neighborhood pixels are then weighted by powers of two and summed to form a decimal number stored on the location of the central pixel p c,whichisdenotedbylbp(p, r). LBPðP; rþ ¼ Xm 1 i¼0 fðp c p i Þ2 i ; where fðþ¼ x 1; x 0 0; x < 0 Applying a CA on a gray-scale image implies using a whole range of image intensities as cell states (s=2 8 =256) leading to a large number of possible patterns (s n =256 n ) and even larger number of possible rules. For illustration, use of a CA neighborhood of n=7 pixels results in possible patterns. A proper binary representation ensures that only two values (0 and 1) are used as cell states (s=2), leading to a reduction of the possible patterns to 2 7 for a neighborhood of n=7 pixels. Although LBP treats regions locally, the representation still has 2 P LBP values so it is inappropriate as an image representation for CA. However, the main idea of local thresholding of image values according to a central pixel is mapped to the task of dealing with values of CA s neighborhood pixels as described in Subsection 3.1. ð2þ 3 Proposed method The proposed method combines CA and LBP for description of image texture, i.e., it focuses on local changes in pixel luminance values. The CA rules (feature vectors) are formed by analyzing binary patterns on a circular neighborhood which are used as a reduced texture description. Binary values are generated using LBP locally on every CA neighborhood (note that the CA neighborhood differs from the circular neighborhood as described in more detail in Subsection 3.1). Detection of duplicated image regions using the proposed method is done through the following steps: Pre-processing - Conversion of the image to gray-scale space is performed to adjust the image for the detection process. As an alternative to that, detection can be done for every color channel separately. Image subdivision - The image is divided into overlapping blocks of size b b pixels. Due to the fact that sliding by one pixel is used, dividing an X Y image with a b b block gives Z blocks in total. Z ¼ ðx b þ 1ÞðY b þ 1Þ ð3þ Feature vector formation - A description of every block, based on local changes of luminance, is accomplished by combining CA and LBP (see Subsection 3.1). A feature vector fv i of size s n for each block iϵ{1,, Z} is calculated and stored in a matrix F defined by fv i ¼ ffv i ð1þ; fv i ð2þ; ; fv i ðs n Þg F ¼ ffv 1 ; fv 2 ; ; fv Z g Duplication Detection - Feature vectors fv i from matrix F are analyzed to detect duplicated blocks (see Subsection 3.2). ð4þ
7 Result generation - Detected pairs of blocks are marked as duplicated regions and mathematical morphology is applied to remove small regions using opening and smooth detected areas using closing. 3.1 Forming feature vector After image pre-processing and subdivision, every defined block is analyzed separately with the goal to describe local changes in pixel luminance values using a reduced set of patterns. Those patterns actually represent the relationship between spatially close pixels that form its neighborhood. The main idea is to determine the frequencies of particular pattern occurrences and represent them in as simple a manner as possible (in the form of a short feature vector). Automation of this process, i.e., generating the feature vector, is possible using pixel values as input to the CA, which results in a description of generated patterns by CA rules. CA rules are formed for each overlapping block and used as feature vectors in the proposed method as described below D CA rules We first use a 1D CA to illustrate the main idea of CA rules as feature vectors and highlight the main disadvantage. In the case of 1D CA, CA rules and neighborhood patterns are formed using pixels from two neighboring rows of an image. The 1D neighborhood of n pixels from one row of the image is used to define the pattern, which together with a single pixel from the next row of the image (at half the length of the neighborhood) is used to form a CA rule. The detailed rule learning process for 1D CA is presented in [23, 24] and is omitted from this paper because it is not relevant for understanding the main concept. Table 1 represents a few 1D CA rules R for all possible combinations of CA neighborhood patterns N(p o ) on a binary image. In the presented example, a neighborhood of n=3 pixels above the observed pixel p o are selected and s=2 for a binary image so there are s n =2 3 =8 binary neighborhood patterns N(p o ). Moreover, there are s 8 =2 8 =256 possible rules R with values from 0 to 255. A rule s value defines the value of the observed pixel p o for all possible neighborhood patters N(p o ) (Table 1) and is used as a reduced feature vector fv i.notethata higher number of neighborhood pixels (n) results in more neighborhood patterns and more rules. However, the main issue in describing a block s texture by 1D CA is its sensitivity to rotation of a duplicated region due to its one dimensional neighborhood Introducing a circular neighborhood To ensure robustness to rotation, we introduced a circular neighborhood on each overlapping block using the following steps: j circles of radius r j with the origin at the block s central pixel p c are formed. Asetofm rj points is selected on each circle, located on radius r j with angles α i =i 360 / m rj, iϵ{1,2,,m rj }. The number of selected points differs for each circle, i.e., on circles with smaller radius a smaller number of points is defined. The set of points sampled on all the defined circles in one overlapping block is called a circular neighborhood (note that CA cells c are represented by points in this case so term m will be used instead of c).
8 Table 1 Examples of a few CA rules R for all possible neighborhood patterns N(p o ) on a binary image with neighborhood of n=3 pixels Rule R=0 (binary: ) Neighborhood pattern N(p o ) Observed pixel p o Rule R=60 (binary: ) Neighborhood pattern N(p o ) Observed pixel p o Rule R=124 (binary: ) Neighborhood pattern N(p o ) Observed pixel p o Rule R=255 (binary: ) Neighborhood pattern N(p o ) Observed pixel p o The value of rule R transformed into binary indicates the value of the observed pixel p o for all possible binary combination of neighborhood patterns. For example, rule R=0 means that the value of the observed pixel p o is equal to 0 for all possible combinations of neighborhood patterns N(p o ) Bilinear interpolation is used to sample each of the points using values of the closest four pixels surrounding the sampled point. The value of a sampled point is equal to a weighted average of those 4 pixels. Linear interpolation is used to extend a set of points sampled from each circle to get the same number of points on every circle. The number of points at each circle is expanded to equal the number of points at the largest circle. The selected set of points from each of the circles is transformed in such a way that points sampled at one circle form one column. Therefore, we can define that each row of a transformed set of points contains points located on different radii r j with the same angle α i. The concept of circular neighborhood forming and learning process is illustrated in Fig Forming CA neighborhood and CA rules Points sampled on circular neighborhoods (and transformed into columns) are used to define CA rules (feature vector in the proposed method) that describe luminance changes in a block. To determine CA rules, the CA neighborhood is defined for each observed point separately: CA neighborhood N(m o ) is defined for observed point m o as a set of n points from the row above the point m o. One point straight above m o and an equal number of neighboring points from both sides of that point is selected as the neighborhood according to Eq. (5), where we use m x,y to represent the point m o at position (x, y) in the transformed set of points. Nm ð o Þ ¼ N m x;y ¼ mxþi;y 1 i ¼ n 1 2 ; ; n 1 2 ð5þ Therefore, the value for observed point m o in row i, i.e., on radius with the angle α i,is defined using neighborhood N(m o )fromrowi-1, i.e., on radius with the angle α i-1.inthe example at Fig. 1, n=5 points from the first row, on radii with the angle α 1,are used as neighborhood N(m o ) for the observed point m o (at half the length of the neighborhood) from the second row, at radii with the angle α 2.
9 Fig. 1 Texture description using circular Cellular Automata for one block in an image: j circles are formed with radius r j ; m rj points are sampled on every circle by bilinearly interpolating the closest four pixels; the set of points at each circle is extended using linear interpolation and transformed into columns; rule learning is done using points from one row (at angle α i-1 in the circular neighborhood) to form neighborhood N(m o ) for an observed point m o in the next row (at angle α i in the circular neighborhood). For example, 5 points from the first row (at angle α 1 ) are used as neighborhood N(m o ) for the observed point m o (at half the length of the neighborhood) from the second row (at angle α 2 ) Note that a circular neighborhood contains a set of points sampled on j circles in one block of an image, while a CA neighborhood is defined for each sampled point separately and include n points from all possible points. Therefore, each CA neighborhood can be observed as a subset of a circular neighborhood (more precisely, a CA neighborhood is a subset of extended set of point from a circular neighborhood). For every CA neighborhood, the mean value is calculated using the value of the point m o and the values of all pixels from the CA neighborhood N(m o ). Hereafter, we will use m o / m i to represent both the value of the point m o /m i and the point itself without confusion. Thresholding based on the LBP method is applied locally to each CA neighborhood to obtain a binary representation by assigning every point m i a binary value b i. b i ¼ 1; m i meanfnm ð o Þ fm o gg; m i fnm ð o Þ fm o gg 0; otherwise ð6þ After defining binary values, the fast rule identification method proposed by Sun et al. [21] is applied to generate a pattern that describes the relation between each point b o and its binary CA neighborhood N(b o ). The main idea proposed in [21] isto determine frequencies of specific (binary neighborhood) pattern occurrence in cases when the observed point b o =1 and b o =0, as presented below. As described in Subsection 2.1, selection of n neighboring points for binary CA neighborhood results in 2 n possible patterns, so two vectors of size 2 n are generated: v 1 to store the number of patterns for b o =1 and v 0 to store the number of patterns for
10 b o =0. The number of specific pattern is stored at location l={0, 1,, 2 n -1} in vectors v 1 and v 0 that is determined as the decimal value of binary CA neighborhood N(b o ) of the observed point b o. v 1 ðþ¼jnb l ð o Þj bo¼1 v 0 ðþ¼jnb l ð o Þj bo ¼0 l ¼ n 2 k 1 N bo ðkþ where N bo ¼ Nb ð o Þ k¼1 ð7þ For CA neighborhood of n=5 points, vectors v 1 and v 0 have total of 2 5 =32 elements, where locations l ={0, 1,, 2 n -1} represent number of patterns N(b o )={ 00000, 00001,, }. For example, vector v 1 (0) contains number of patterns N(b o )= when b o =1, and vector v 0 (0) contains number of patterns N(b o )= when b o =0. Finally, a feature vector fv i is formed by comparing the number of specific pattern N(b o )in cases when the observed point b o =1 and b o =0, i.e., by comparing values from vectors v 1 and v 0 at each location l: fv i ðþ¼ l 1; v 1ðÞ v l 0 ðþ l 0; otherwise : ð8þ Figure 2 illustrates the process of forming a feature vector fv i with a neighborhood of n=5 elements. The feature vector fv i contains 2 n =2 5 =32 values defined as described above. For example, for binary pattern N(b o )= 00000, the values of vectors v 1 and v 0 are determined and stored at location l=0 that corresponds to the selected binary pattern. If v 1 (0)<v 0 (0), then feature vector fv i (l)=fv i (0)=0. In contrast to that, values of vectors v 1 and v 0 for binary pattern N(b o )= are stored at location l= 20. In this case, v 1 (20)>v 0 (20) so feature vector fv i (l)=fv i (20)=1. Each value in the feature vector is defined in the same way and is set to: 1 if most times when the pattern N(b o ) appears, the value of point b o is 1, 0 if most times when the pattern N(b o ) appears, the value of point b o is 0. Fig. 2 Example of forming a feature vector (for one block in an image): number of each binary pattern N(b o )is determined in the case when b o =1 and b o =0; determined values are stored in vectors v 1 and v 0 at location l; location l is determined by conversion of binary pattern N(b o ) to its decimal number; feature vector fv at location l issetto1ifv 1 (0)>v 0 (0)orto0isv 1 (0)<v 0 (0). In this example, binary pattern b o =00000 at location l=0 appears more often in the case when b o =0 (v 1 <v 0 ), therefore fv(0)=0. Elements at other locations in feature vector fv are determined in the same way
11 All generated feature vectors are stored in matrix F in such a way that the i-th row contains 2 n values of feature vector fv i. Therefore, matrix F contains Z feature vectors for each overlapping block defined in the analyzed image. 3.2 Detection process Identifying k nearest neighbors Having in mind the large number of overlapping blocks (for an image of size pixels, and block of size b=13, the number of overlapping blocks is Z= ), brute force searching for duplicated blocks would be highly time consuming, and therefore inefficient. Brute force searching means that each overlapping block of an image is selected in turn, and all the other blocks are compared with it. In case of a CMF, brute force is not effective because the search area is the whole matrix F of Z elements, e.g., every block has to be compared with Z-1 blocks. To improve the efficiency of the detection process, a sorting algorithm can be applied to matrix F to group similar feature vectors and search can then be done on a subset of the data. The described feature vectors have an important property - each element shows use of a particular binary pattern and therefore has the same level of importance for the description of texture. Use of a sorting algorithm which gives higher importance to some elements in a feature vector (e.g., lexicographic sorting which gives higher importance to first elements in feature vectors) is not suitable for this problem, so selection of similar feature vectors is done using a kd-tree. Due to the fact that feature vectors contain only binary values, FLANN [14] isusedtofindthek most similar feature vectors for all the feature vectors (i.e., k most similar blocks for everydefinedblockinanimage). FLANN hierarchically decomposes the search space (matrix of all feature vectors F) by clustering the input set and constructing trees. The tree building process divides feature vectors into K clusters by selecting K feature vectors at random as the cluster centers and assigning the rest of the feature vectors to the closest center. The algorithm is recursively repeated until the number of feature vectors in each leaf is below a certain threshold (called the maximum leaf size ls max ). At the end, every cluster contains one non-leaf node (cluster center) and leaf nodes with input feature vectors to be matched. The process of searching multiple clustering trees in parallel starts with a single traverse of each of the trees. The algorithm selects the feature vector closest to the query feature vector and recursively explores it, while adding the unexplored feature vectors to a priority queue. After each of the trees has been explored once, the search is continued by extracting from the priority queue the closest node to the query feature vector and resuming the tree traversal from there. The search ends when the number of examined feature vectors exceeds a maximum limit, i.e., the degree of approximation d aprox. A higher value of d aprox results in the more exact neighbors, but it also leads to more expensive search. Thanks to the hierarchical clustering trees, FLANN accomplishes significant speedups over linear search ranging between one and two orders of magnitude for search precisions in the range % [14]. Application of FLANN to the matrix F gives k nearest feature vectors for each feature vector fv i, i.e., it results in a matrix of Z k possible duplicated feature vectors P, where row i defines k nearest feature vectors for i-th feature vector fv i.
12 3.2.2 Identifying duplicated blocks To identify true duplicated blocks, matrix P is further analyzed using following steps: For each row i Euclidean distance v ij between values of feature vector fv i and its k nearest feature vectors fv j =P(i, j), j={1, 2,, k} fromi-th row is calculated using (9), and stored in matrix V. vffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffi ux 2n v ij ¼ t 2 fv i ðþ fv l j ðþ l ð9þ l¼1 Value v ij represents similarity of two feature vectors, i.e., similarity of two generated CA rules, so its analysis assures removal of blocks that differ in more binary patterns than allowed (defined by similarity threshold T s ). Then, matrix P is analyzed by calculating the Euclidean distance d ij between blocks coordinates (x i, y i ) of feature vector fv i (corresponding to i-th row of matrix P) and coordinates (x j, y j )ofitsk nearest feature vectors fv j =P(i, j), j={1, 2,, k} fromi-th row using (10), and stored in matrix D. rffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffi 2 2 d ij ¼ x j x i þ y j y i ð10þ Value d ij represents the spatial distance between two blocks so its analysis allows removal of spatially close blocks (especially partly overlapping blocks) which usually have very similar texture, and produce very similar feature vectors. Its analysis assures removal of blocks that are spatially closer then allowed (defined by distance threshold T d ). Elements P(i, j) from matrix P are removed from further analysis if distance v ij from matrix V is higher than threshold T s or distance d ij from matrix D is smaller than distance threshold T d. After this step every row in matrix P contains between 0 and k elements. Matrix P is used to form matrix I that contains identified pairs of feature vectors in a way that every remaining element in matrix P from i-th row is assigned to corresponding feature vector fv i. Therefore, a two-column matrix I is created using indexes i, j ϵ {1, 2,, Z} of identified pairs of feature vectors fv i, fv j. Finally, set I is analyzed using the shift vector between blocks so that block pair fv i, fv j is marked as truly duplicated if at least n s spatial neighbors of block fv i arecopiedtoanyn s spatial neighbors of block fv j. Spatial neighborhood N s (fv i ) for feature vector fv i is determined using feature vector index i from matrix I: N s ðfv i Þ ¼ ffv i ZX 2; fv i ZX 1; fv i ZX ; fv i 1 ; fv iþ1 ; fv iþzx ; fv iþzx þ1; fv iþzx þ2g ð11þ Z X ¼ X b; where X is the size of an image in the horizontal direction, and b is the size of overlapping blocks. Note that spatial neighborhood N s (fv i ) represents Moore neighborhood. All pairs of blocks fv i, fv j that do not meet this condition are removed from matrix I.
13 After this process, the detection result is generated by marking true duplicated blocks using coordinates of remaining feature vectors in matrix I and applying post-processing. 4 Testing setup To analyze the performance of the proposed method 80 plain CMF examples and 80 rotation CMF examples from a recent benchmark database called CoMoFoD is used [25]. All images are post-processed by applying JPEG compression, noise and blurring, making total of 1360 images. Every forgery example consists of an original image (without any forgery), a forged image (with a forgery) and two masks (colored and black/white) that indicate the forgery. Images in the CoMoFoD database are pixels, and all forgeries are generated using a Photoshop tool. The advantage of this dataset is that it contains examples of forgeries with different sizes of duplicated regions, homogenous/heterogeneous areas and cases of multiple forgeries. Thanks to its small image size, the database is adequate for fast and efficient testing of different detection approaches. Parameters used for implementation of the proposed method are given in Table 2. Alarger block size b makes it impossible to detect duplicated regions smaller than (b+1) b pixels. However, a smaller block size results in a larger number of overlapping blocks. Therefore block size is selected having in mind different sizes of duplicated regions and the computational complexity of a proposed method. Values of threshold T d, number of circles j, radiir j, number of points m rj and size of a disk element for morphological operations r morp are selected according to block size (Table 2). Note that circles are formed with radii r j to increase the number of circles in block b b and to ensure a sufficient number of samples for a better description of the block pattern. Similarity threshold T s is experimentally determined by selecting blocks of size b b from 10 images. On each block, transformations (scaling with different factors and rotation with different angles) and post-processing operations (blurring, addition of noise and JPEG compression) are applied. CA rules are obtained for all variations of each block by the process described in Subsection 3.1. Results showed that most rules for the same block differ in less Table 2 Parameters used for implementation of the proposed method Parameter Symbol Value Block size b 13 Similarity threshold T s 7 Distance threshold T d =floor(sqrt(2b 2 )) 18 Number of nearest neighbors k 4 Number of spatial neighbors n s 2 Number of circles j=(b-1) 12 Radii of circles r j =1/2,1,3/2,, (b-1)/2 1/2,1,3/2,, 6 Number of points on each circle m r1 =8, m rj =2m rj-1 8, 16,, Radius of disk element for morphology r morp 3 Number of clusters in FLANN K 8 Maximum leaf size in FLANN ls max 64 Degree of approximation in FLANN d aprox 0.9
14 than 7 elements so threshold T s is set to 7. The same experiment showed that in the case of post-processing and transformations, spatially close blocks have more similar rules than true duplicated blocks. Therefore we set k=4 to select four blocks with similar rules for further analysis. The number of spatial neighbors n s defines that at least two neighbor blocks have to be grouped to form duplicated areas. Values for FLANN (K, ls max, d aprox ) are used as proposed in [14] forbinarysetofdata. To evaluate the performance of the proposed method, precision P, recall R and F-measure F are calculated at the pixel level for every image: P ¼ T P ; R ¼ T P ; F ¼ 2PR T P þ F P T P þ F n P þ R where F p is the number of false positive pixels (mistakenly detected as copied), F n is the number of the false negative pixels (mistakenly detected as not copied), and T p is the number of the true positive pixels (correctly detected as copied). ð12þ 5 Detection results The accuracy of CMF detection is tested for plain CMF, multiple CMF, rotation of duplicated regions and three common types of post-processing: blurring, addition of noise and JPEG compression. Plain CMF refers to forgery where a part of an image is copied and translated to a new location in the same image without changing any properties. Multiple CMF refers to a case when one or more regions are copied to different locations in the same image. The authors in [7] evaluated 13 block-based and two keypoint-based methods for CMFD. Among all tested methods, the DCT [9], PCA [16], Zernike [19] and SURF [5, 20] methods gained the best results in most tested scenarios so the proposed method is compared with those four methods. 5.1 Plain CMF Figure 3 shows the detection results for plain CMF. The accuracy is quite high for all presented cases (F>0.92) showing that the method is capable of detecting duplicated regions of different sizes and shapes. Figure 3a and c illustrate that the proposed method can deal with repetitive image content. Figure 4 contains examples of multiple CMFD when one region is copied to different locations (Fig. 4a and b) and different regions are copied to different locations (Fig. 4c and d). Detection is satisfactorily accurate for all images leading to the conclusion Fig. 3 Detection of plain CMF for different sizes of copied regions
15 Fig. 4 Detection of multiple CMF: one region on two locations (a, b), two regions on different locations (c, d) that the proposed method can deal with multiple CMF. Additionally, Fig. 4a presents successful detection of duplicated homogeneous regions (F=0.9847). The lowest F-measure (among all tested images) is achieved in the case when the copied region is very small with respect to the whole image (e.g., the signs stands in Fig. 4c). Results for 40 examples of plain CMF are shown in Fig. 5. Results for original images are omitted because all methods correctly detect all 40 images (F 1 in all cases). For almost all images, the proposed method showed better performance than the other tested methods (the highest average F-measure). The F-measure is higher than 0.7 for all images showing that detection is very accurate. Furthermore, detection is successful for different sizes of copied areas the smallest successful detected area is around 0.13 % of the image size (360 pixels, Fig. 3a), and the largest is around 14 % of the image size. The Zernike method produces many false positives in homogeneous regions, while the PCA method failed to detect some small copied regions. The SURF method is unable to discriminate repetitive image content from true duplicated regions and falsely detects homogeneous duplicated regions. 5.2 Rotation of duplicated regions Figure 6 shows detection result for cases when a copied region is rotated by 90 (Fig. 6a), 7 (Fig. 6b) and 180 (Fig. 6c), and one case of multiple CMF where the region is rotated by 2 Fig. 5 Value of F-measure for 40 plain CMF images from CoMoFoD dataset with average F-measure: F proposed =0.9428, F DCT =0.9272, F PCA =0.7715, F Zernike =0.9036, F SURF =0.7181
16 Fig. 6 Examples of detection results for rotation of the copied region for different angle α and 3 (Fig. 6d). In all cases the copied regions are correctly detected demonstrating that the proposed circular neighborhood can deal with different angles of rotation. Note that there are no falsely detected areas in any of the presented cases. Also, detection is quite successful for complex textures (Fig. 6a, F =0.7384), as well as for homogeneous regions (Fig. 6d, F= ). Results for 80 images and all tested methods are shown in Fig. 7. Testing is done on images with rotation angles α={1, 2, 5, 7, 10, 40, 90, 180 }. The DCT method successfully detects rotation by small angles (α<5 ). The Zernike method showed good performance for almost all angles, while the PCA method was completely unable to handle higher rotation angles (α>3 ). The SURF method exhibits the most stable F-measure but it is significantly lower than the Zernike and the proposed method. The proposed method showed high F- measures for α<10 as well as for α=90 and α=180. For other tested cases detection was less accurate but it was still possible to partly detect copied regions for most rotation angles. 5.3 Scaling Figure 8 shows detection results for cases when a copied region is scaled by the scaling factor f. Note that factor f has the same value in all directions, e.g., scaling is uniform. Scaling with Fig. 7 Average F-measure for 80 images and different rotation angles (note that testing is done only for the highlighted angle values)
17 Fig. 8 Examples of detection results for scaling of the copied region for different factor f factor f=109 % (the copied region is 9 % larger than the original region) is illustrated in Fig. 8a. Detection is only partly possible (F 0.5), but no falsely detected regions are introduced, leading to easy identification of duplicated objects. An example of scaling a large region with scaling factor f=91 % (the copied region is 9 % smaller than the original region) is presented in Fig. 8b. Detection is also only partly possible, but it clearly indicates duplicated regions. Figure 8d contains an example of multiple CMF when the duplicated region is scaled with factor f 1 =76%andwithfactorf 2 =111 %. The F-measure is satisfactory high (F=0.6131) indicating that detection is quite successful even in a case of higher scaling factors. Also, both copied regions are successfully detected with no falsely detected areas. Average F-measures for 40 images and different scaling factors are given in Fig. 9. Testing is done for scaling factors f={91 % %} with a step of 2 and for f={50 %, 80 %, 120 %, 200 %}. The proposed method demonstrated good capabilities to handle a moderate amount of scaling with high F-measure for 91 %<f<109 %. For the higher amounts of scaling, detection accuracy rapidly decreases. Other block-based methods, namely Zernike, PCA and DCT, showed similar behavior but for most scaling factors they gained a lower average F-measure. Opposite to that, the SURF method remained stable across the whole scaling range leading to the conclusion that keypoint-based methods perform better for scaling factors higher than 9 %. Fig. 9 Average F-measure for 80 images and different scaling factors (note that testing is done only for the highlighted values of scaling factor)
18 5.4 Blurring CMFD on blurred images is done for two cases: an averaging filter of size 3 3 and 5 5, as shown in Fig. 10. In the first case (Fig. 10a and c), detection is almost perfect even after blurring. However, in the second case, filtering with an averaging filter of size 3 3 results in successful detection of forged regions but also introduces an additional falsely detected area (Fig. 10b). Note that the falsely detected area is very similar to the duplicated areas (letter Bo^). Applying a 5 5 filter to the same image reduces the size of detected regions and introduces some other falsely detected blocks (Fig. 10d). Those blocks can be removed by increasing the threshold T d. Detection results for all the methods are shown in Fig. 11 which illustrates the average F-measure for 80 original and forged images and both testing cases. The proposed method gained the highest F-measure for both cases, meaning that it can correctly detect most blurred images. Other tested methods were also successful in detection of blurred images but they introduced more falsely detected areas than the proposed method. Also, the Zernike method over-detected homogeneous regions, while the SURF method showed over sensitivity on low contrast regions after image blurring. 5.5 Addition of noise Addition of noise randomly changes properties of duplicated image regions so in that case it is not sufficient to search for two blocks with the same properties. Therefore, filtering the image with an averaging filter of size 3 3 is applied prior to the detection. Figure 12 contains an example of detection on a noisy image which contains added Gaussian noise with zero mean and different values of variance. Note that image intensities were normalized to the range [0, 1] prior to the addition of noise. Detection is partly possible even when a large amount of noise is added (Fig. 12a). However, note that even a large amount of noise does not introduce any falsely detected areas, which is a very important feature for digital image forensics. Figure 13 contains results for 80 images when Gaussian noise of zero mean and different values of variance is added ( , with multiplier step equal to 10). For a smaller amount of noise, the Zernike method was slightly more successful in detection of duplicated areas, but for larger amounts of noise the proposed method achieved the best performance in comparison to the other tested methods. Fig. 10 Examples of detection results on blurred images with different averaging filter
19 Fig. 11 Average F-measure for 80 images and different size of averaging filter 5.6 JPEG compression Detection of duplicated images after JPEG compression presents a serious problem for most detection algorithms because of its specific compression process where every 8 8 block of the image is treated separately. The consequence is that the same blocks have completely different binary representations, and so different sets of rules are generated. Also, JPEG blocks are smaller than the overlapping blocks defined in the proposed method (b=13).however,as in the case of added noise, dealing with JPEG compression is possible by pre-processing the image using an averaging filter. Figure 14 presents detection results for a forgery example with different JPEG quality factors. Accuracy of detection of duplicated areas rapidly decreases for higher levels of JPEG compression. However, even for images with high JPEG compression, detection is partly possible, and there are no falsely detected areas (Fig. 14a). Results for all tested methods are presented in Fig. 15, where the average F-measure for 80 test images is given. The proposed method was equally successful in detection of JPEG images as the DCT method for higher quality factors, while for lower JPEG quality the DCT method showed slightly better performance. The SURF method was most stable but it also gained a lower F-measure for most JPEG compression factors in comparison with the proposed method. Fig. 12 Example of detection results on a noisy image for different values of variance σ 2
20 Fig. 13 Average F-measure for 80 images and different values of variance Additionally, the proposed method outperformed other tested methods for all amounts of JPEG compression. 5.7 Feature vector complexity An important part of every CMF detection algorithm is the description of features using reduced and robust feature vectors. Table 3 shows the size of the calculated feature vectors for all tested methods. The size of feature vectors for the DCT and PCA methods (as well as computational complexity) depends on block size and image content, respectively. The size of the Zernike feature vector is defined by Zernike moment order o, and it is equal to 12 for o=5 [19], however it is computationally demanding. The size of SURF feature vectors (64 values) does not depend on any method specific parameters. Although SURF produces large feature vectors, it contains a smaller number of feature vectors than any block-based method. In the proposed method, the size of feature vector depends on the size of the CA neighborhood (2 n ). However, each feature vector contains only binary values so it can be represented as a single decimal number. In comparison with other methods, this property allows a significantly simplified description of texture. Computational complexity depends on the number of sampling points and the size of neighborhood but it is not more demanding than other block-based methods. Fig. 14 Examples of detection results on a JPEG image with different values of quality factor q
21 Fig. 15 Average F-measure for 80 images and different values of JPEG compression factor 6 Conclusion Detection of duplicated image regions has been widely researched in the past few years due to the fact that digital image content can be easily manipulated. Therefore we presented a new block-based method for detection of duplicated image regions that combines LBP with CA to accomplish a powerful pattern description. Identification of duplicated regions is accomplished by analyzing local changes of pixel luminance values in a circular neighborhood. Pixel values are transformed to binary values using LBP to form a reduced representation of a block and the binary values are used as an input to CA. The produced feature vector indicates the use of a specific set of patterns in the block texture, so similar image areas should produce similar feature vectors. FLANN is applied to the feature vectors set to find the k nearest neighbors for every element and a new search method is applied to select the duplicated blocks. Testing results showed excellent performance in the case of plain CMF and multiple CMF, where the proposed method outperformed the DCT, PCA, Zernike and SURF methods. While the DCT method gained similar F-measures as the proposed method, the PCA method was unable to detect small duplicated regions. Furthermore, the Zernike method generated a lot of falsely detected areas on homogeneous regions (e.g., sky) and the SURF method falsely marked a large amount of repetitive image content due to background similarities. Detection of rotated regions was quite successful for most rotation angles in which the proposed method Table 3 Properties of generated feature vectors for all tested methods Group Method Size of feature vector Dependence of parameter Block-based Proposed 128 (b) =1 (d) Neighborhood size n* DCT [9] 256 (d) Blocks size b PCA [16] / Image content Zernike [19] 12 (d) Zernike moment order o Keypoint-based SURF [5, 20] 64 (d) / * influence only on size of the feature vector in binary form
22 gained similar accuracy as the Zernike method. The SURF method showed most stable detection but with lower average F-measure, and the PCA and DCT methods successfully detected only at small rotation angles. In detection of scaling, the proposed method showed similar behavior to other block-based methods, but with a slightly higher average F-measure thanks to better robustness to homogeneous regions and repetitive image content. The keypoint-based method showed the lowest change in detection accuracy, but it also achieve the lowest average F-measure for almost all scaling factors. Furthermore, the proposed method showed good robustness to blurring, addition of noise and JPEG compression. It gained the best average F-measure for blurred images and images with added Gaussian noise, and it showed similar accuracy as the DCT method for JPEG compression. An important advantage of the proposed method is its binary coded feature vectors that can be represented as a single number, in contrast to all previous proposed methods. A simple descriptor of local luminance changes is applicable to classification tasks thanks to its low computational complexity and possibility for fast and efficient analysis. The strength of the proposed method lies in the description of local changes of pixel luminance values so it is not significantly affected by image post-processing. Additionally, the circular neighborhood assures insensitivity to rotation of the duplicated region. Use of a new search method allows better analysis of similarities between calculated feature vectors. The proposed method has low computational complexity and low memory requirements, and it produces a significantly more reduced description of image texture than all previously proposed methods. References 1. Amerini I, Ballan L, Caldelli R, Del Bimbo A, Giuseppe S (2011) A SIFT-based forensic method for copymove attack detection and transformation recovery. IEEE Trans Inf Forensics Secur 6(3): Bashar M, Noda K, Ohnishi N, Mori K (2010) Exploring duplicated regions in natural images. IEEE Trans Image Process. Accepted for publication 3. Bayram S, Sencar H, Memon N (2009) An efficient and robust method for detecting copy-move forgery. IEEE Int Conf Acoust Speech Signals Process: Bhatnagar G, Wu QMJ, Raman B (2011) A new aspect in robust digital watermarking. Multimedia Tools Appl 66(2): Bo X, Junwen W, Guangjie L, Yuewei D (2010) Image copy-move forgery detection based on SURF. Multimedia Inf Netw Secur: Bravo-Solorio S, Nandi AK (2011) Exposing duplicated regions affected by reflection, rotation and scaling. Int Conf Acoust Speech Signal Process: Christlein V, Riess C, Jordan J, Riess C, Angelopoulou E (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans Inf Forensics Secur 7(6): Farid H (2009) Image forgery detection: a survey. IEEE Signal Process Mag 26(2): Fridrich J, Soukal D, Lukas J (2003) Detection of copy move forgery in digital images. Proc. Digital Forensic Research Workshop 10. Hou X, Zhang T, Xiong G, Zhang Y, Ping X (2014) Image resampling detection based on texture classification. Multimedia Tools Appl 72(2): Li L, Li S, Zhu H, Chu S, Roddick J, Pan J (2013) An efficient scheme for detecting copy-move forged images by local binary patterns. J Inf Hiding Multimedia Signal Process 4(1): Lin H, Wang C, Kao Y (2009) Fast copy-move forgery detection. WSEAS Trans Signal Process 5(5): Luo W, Huang J, Qiu G (2006) Robust detection of region-duplication forgery in digital images. IEEE Inf Forensics Secur 4: Muja, M, Lowe, DG (2012) Fast matching of binary features. Comput Robot Vision (CRV), pp Ojala T, Pietikainen M, Maeenpaa T (2002) Multiresolution gray- scale and rotation invariant texture classification with local binary patterns. IEEE Trans Pattern Anal Mach Intell 24(7):
23 16. Popescu A, Farid H (2004) Exposing digital forgeries by detecting duplicated image regions, tech. rep. tr Dartmouth College 17. Redi JA, Taktak W, Dugelay J-L (2011) Digital image forensics: a booklet for beginners. Multimedia Tools Appl 51(1): Rosin PL (2007) Training cellular automata for image processing. IEEE Trans Image Process 15(7): Ryu S, Lee M, Lee H (2010) Detection of copy-rotate-move forgery using Zernike moments. Inf Hiding Conf: Shivakumar BL, Baboo S (2011) Detection of region duplication forgery in digital images using SURF. Int J Comput Sci Issues 8(4): Sun X, Rosin PL, Martin RR (2011) Fast rule identification and neighborhood selection for cellular automata. IEEE Trans Syst Man Cybern B 41(3): Swaminathan A, Min W, Liu K (2013) Copy-move forgery detection using multiresolution local binary patterns. Forensic Sci Int 231(1 3): Tralic D, Rosin PL, Sun X, Grgic S (2014) Detection of duplicated image regions using cellular automata. Proceed Int Conf Syst Signals Image Process: Tralic D, Rosin PL, Sun X, Grgic S (2014) Copy-move forgery detection using cellular automata. In: Rosin P L, Adamatzky A, Sun X (eds) Cellular Automata in Image Processing and Geometry. Springer, pp Tralic D, Zupancic I, Grgic S, Grgic M (2013) CoMoFoD - new database for copy-move forgery detection. In: Proc. 55th International Symposium ELMAR pp Wang J, Liu G, Zhang Z, Dai Y, Wang Z (2009) Fast and robust forensics for image region-duplication forgery. Acta Autom Sin 35(12): Dijana Tralic is a PhD Student and a Research Assistant at University of Zagreb, Faculty of Electrical Engineering and Computing, Croatia. In 2013 and 2014, she spent 6 months at Cardiff University as visiting researcher working in a computer vision group. She is a member of organization committees of ELMAR and IWSSIP-2014 conferences, and active IEEE member. Her research interests include signal and image processing, shape analysis, pattern recognition and digital image forensics.
24 Sonja Grgic received the B.Sc., M.Sc. and PhD degrees in electrical engineering from University of Zagreb, Faculty of Electrical Engineering and Computing, Croatia, in 1989, 1992 and 1996, respectively, where she is currently a Professor. She is the recipient of the silver medal BJosip Loncar^ from the Faculty of Electrical Engineering and Computing for an outstanding PhD thesis and annual award BRikard Podhorsky^ from Croatian Academy of Engineering (HATZ) for year She has participated in 11 domestic and international scientific projects, and was the principal investigator of the project BPicture Quality Management in Digital Video Broadcasting^ financed by the Ministry of Science, Education and Sports of the Republic of Croatia ( ). She is active member of IEEE, SMPTE, KoREMA, Elmar and HATZ. Her research interests include image quality evaluation methods, television signal transmission, wavelet image compression and video communication technologies. Xianfang Sun received the PhD degree in control theory and its applications from the Institute of Automation, Chinese Academy of Sciences. He is a lecturer at Cardiff University. His research interests include computer vision and graphics, pattern recognition and artificial intelligence, and system identification and control. He is on the Editorial Board of Acta Aeronautica et Astronautica Sinica.
25 Paul L. Rosin received a BSc in Computer Science and Microprocessor Systems in 1984 from Strathclyde University, and a PhD in Information Engineering from City University in This was followed by posts as: research fellow on the Alvey project BModel-Based Interpretation of Radiological Images^ at Guy s Hospital, London, lecturer at Curtin University of Technology, Perth, Australia, and research scientist at the Institute for Remote Sensing Applications, Joint Research Centre, Ispra, Italy. Returning to the UK he was lecturer at the Department of Information Systems and Computing, Brunel University before joining the School of Computer Science Informatics at Cardiff University. His research interests are wide, and include: low level image processing, performance evaluation, shape analysis, facial analysis, medical image analysis, 3D mesh processing, cellular automata and non-photorealistic rendering. Much of this work has been performed in multidisciplinary collaborations such as: the perception of trustworthiness from smiles, segmentation of 3D OCT scans of retinas, determining the effectiveness of surgery from facial morphology and temporal dynamics, analysing the effects of alcohol on crowd dynamics and violence and digitally unrolling of fragile parchments from 3D X-ray scans.
Copy Move Forgery using Hu s Invariant Moments and Log-Polar Transformations
 Copy Move Forgery using Hu s Invariant Moments and Log-Polar Transformations Tejas K, Swathi C, Rajesh Kumar M, Senior member, IEEE School of Electronics Engineering Vellore Institute of Technology Vellore,
Copy Move Forgery using Hu s Invariant Moments and Log-Polar Transformations Tejas K, Swathi C, Rajesh Kumar M, Senior member, IEEE School of Electronics Engineering Vellore Institute of Technology Vellore,
Advanced Digital Image Forgery Detection by Using SIFT
 RESEARCH ARTICLE OPEN ACCESS Advanced Digital Image Forgery Detection by Using SIFT Priyanka G. Gomase, Nisha R. Wankhade Department of Information Technology, Yeshwantrao Chavan College of Engineering
RESEARCH ARTICLE OPEN ACCESS Advanced Digital Image Forgery Detection by Using SIFT Priyanka G. Gomase, Nisha R. Wankhade Department of Information Technology, Yeshwantrao Chavan College of Engineering
Copy-Move Forgery Detection using DCT and SIFT
 Copy-Move Forgery Detection using DCT and SIFT Amanpreet Kaur Department of Computer Science and Engineering, Lovely Professional University, Punjab, India. Richa Sharma Department of Computer Science
Copy-Move Forgery Detection using DCT and SIFT Amanpreet Kaur Department of Computer Science and Engineering, Lovely Professional University, Punjab, India. Richa Sharma Department of Computer Science
DYADIC WAVELETS AND DCT BASED BLIND COPY-MOVE IMAGE FORGERY DETECTION
 DYADIC WAVELETS AND DCT BASED BLIND COPY-MOVE IMAGE FORGERY DETECTION Ghulam Muhammad*,1, Muhammad Hussain 2, Anwar M. Mirza 1, and George Bebis 3 1 Department of Computer Engineering, 2 Department of
DYADIC WAVELETS AND DCT BASED BLIND COPY-MOVE IMAGE FORGERY DETECTION Ghulam Muhammad*,1, Muhammad Hussain 2, Anwar M. Mirza 1, and George Bebis 3 1 Department of Computer Engineering, 2 Department of
A Study of Copy-Move Forgery Detection Scheme Based on Segmentation
 IJCSNS International Journal of Computer Science and Network Security, VOL.18 No.7, July 2018 27 A Study of Copy-Move Forgery Detection Scheme Based on Segmentation Mohammed Ikhlayel, Mochamad Hariadi
IJCSNS International Journal of Computer Science and Network Security, VOL.18 No.7, July 2018 27 A Study of Copy-Move Forgery Detection Scheme Based on Segmentation Mohammed Ikhlayel, Mochamad Hariadi
Cloning Localization Based On Feature Extraction and K-Means Clustering
 Cloning Localization Based On Feature Extraction and K-Means Clustering Areej S. Alfraih, Johann A. Briffa, and Stephan Wesemeyer Department of Computing, University of Surrey, Guildford GU2 7XH, UK a.alfraih@surrey.ac.uk
Cloning Localization Based On Feature Extraction and K-Means Clustering Areej S. Alfraih, Johann A. Briffa, and Stephan Wesemeyer Department of Computing, University of Surrey, Guildford GU2 7XH, UK a.alfraih@surrey.ac.uk
Copy-Move Forgery Detection Scheme using SURF Algorithm
 Copy-Move Forgery Detection Scheme using SURF Algorithm Ezhilvallarasi V. 1, Gayathri A. 2 and Dharani Devi P. 3 1 Student, Dept of ECE, IFET College of Engineering, Villupuram 2 Student, Dept of ECE,
Copy-Move Forgery Detection Scheme using SURF Algorithm Ezhilvallarasi V. 1, Gayathri A. 2 and Dharani Devi P. 3 1 Student, Dept of ECE, IFET College of Engineering, Villupuram 2 Student, Dept of ECE,
Copy-Move Image Forgery Detection Based on Center-Symmetric Local Binary Pattern
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 17, Issue 4, Ver. I (July Aug. 2015), PP 66-70 www.iosrjournals.org Copy-Move Image Forgery Detection Based on
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 17, Issue 4, Ver. I (July Aug. 2015), PP 66-70 www.iosrjournals.org Copy-Move Image Forgery Detection Based on
Improved LBP and K-Nearest Neighbors Algorithm
 Image-Splicing Forgery Detection Based On Improved LBP and K-Nearest Neighbors Algorithm Fahime Hakimi, Department of Electrical and Computer engineering. Zanjan branch, Islamic Azad University. Zanjan,
Image-Splicing Forgery Detection Based On Improved LBP and K-Nearest Neighbors Algorithm Fahime Hakimi, Department of Electrical and Computer engineering. Zanjan branch, Islamic Azad University. Zanjan,
Simulative Comparison of Copy- Move Forgery Detection Methods for Digital Images
 Simulative Comparison of Copy- Move Forgery Detection Methods for Digital Images Harpreet Kaur 1, Jyoti Saxena 2 and Sukhjinder Singh 3 1 Research Scholar, 2 Professor and 3 Assistant Professor 1,2,3 Department
Simulative Comparison of Copy- Move Forgery Detection Methods for Digital Images Harpreet Kaur 1, Jyoti Saxena 2 and Sukhjinder Singh 3 1 Research Scholar, 2 Professor and 3 Assistant Professor 1,2,3 Department
SURF-based Detection of Copy-Move Forgery in Flat Region
 SURF-based Detection of Copy-Move Forgery in Flat Region 1 Guang-qun Zhang, *2 Hang-jun Wang 1,First Author,* 2Corresponding Author School of Information Engineering, Zhejiang A&F University, 311300, Lin
SURF-based Detection of Copy-Move Forgery in Flat Region 1 Guang-qun Zhang, *2 Hang-jun Wang 1,First Author,* 2Corresponding Author School of Information Engineering, Zhejiang A&F University, 311300, Lin
COPY-MOVE FORGERY DETECTION USING DYADIC WAVELET TRANSFORM. College of Computer and Information Sciences, Prince Norah Bint Abdul Rahman University
 2011 Eighth International Conference Computer Graphics, Imaging and Visualization COPY-MOVE FORGERY DETECTION USING DYADIC WAVELET TRANSFORM Najah Muhammad 1, Muhammad Hussain 2, Ghulam Muhammad 2, and
2011 Eighth International Conference Computer Graphics, Imaging and Visualization COPY-MOVE FORGERY DETECTION USING DYADIC WAVELET TRANSFORM Najah Muhammad 1, Muhammad Hussain 2, Ghulam Muhammad 2, and
ON ROTATION INVARIANCE IN COPY-MOVE FORGERY DETECTION. Vincent Christlein, Christian Riess and Elli Angelopoulou
 ON ROTATION INVARIANCE IN COPY-MOVE FORGERY DETECTION Vincent Christlein, Christian Riess and Elli Angelopoulou Pattern Recognition Lab University of Erlangen-Nuremberg sivichri@stud.informatik.uni-erlangen.de,
ON ROTATION INVARIANCE IN COPY-MOVE FORGERY DETECTION Vincent Christlein, Christian Riess and Elli Angelopoulou Pattern Recognition Lab University of Erlangen-Nuremberg sivichri@stud.informatik.uni-erlangen.de,
An Improved SIFT-Based Copy-Move Forgery Detection Method Using T-Linkage and Multi-Scale Analysis
 Journal of Information Hiding and Multimedia Signal Processing c 2016 ISSN 2073-4212 Ubiquitous International Volume 7, Number 2, March 2016 An Improved SIFT-Based Copy-Move Forgery Detection Method Using
Journal of Information Hiding and Multimedia Signal Processing c 2016 ISSN 2073-4212 Ubiquitous International Volume 7, Number 2, March 2016 An Improved SIFT-Based Copy-Move Forgery Detection Method Using
Improved DSIFT Descriptor based Copy-Rotate-Move Forgery Detection
 Improved DSIFT Descriptor based Copy-Rotate-Move Forgery Detection Ali Retha Hasoon Khayeat 1,2, Xianfang Sun 1, Paul L. Rosin 1 1 School of Computer Science & Informatices, Cardi University, UK KhayeatAR@Cardiff.ac.uk,
Improved DSIFT Descriptor based Copy-Rotate-Move Forgery Detection Ali Retha Hasoon Khayeat 1,2, Xianfang Sun 1, Paul L. Rosin 1 1 School of Computer Science & Informatices, Cardi University, UK KhayeatAR@Cardiff.ac.uk,
Texture. Frequency Descriptors. Frequency Descriptors. Frequency Descriptors. Frequency Descriptors. Frequency Descriptors
 Texture The most fundamental question is: How can we measure texture, i.e., how can we quantitatively distinguish between different textures? Of course it is not enough to look at the intensity of individual
Texture The most fundamental question is: How can we measure texture, i.e., how can we quantitatively distinguish between different textures? Of course it is not enough to look at the intensity of individual
Object detection using non-redundant local Binary Patterns
 University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2010 Object detection using non-redundant local Binary Patterns Duc Thanh
University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2010 Object detection using non-redundant local Binary Patterns Duc Thanh
THE goal of blind image forensics is to determine the. An Evaluation of Popular Copy-Move Forgery Detection Approaches
 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY 1 An Evaluation of Popular Copy-Move Forgery Detection Approaches Vincent Christlein, Student Member, IEEE, Christian Riess, Student Member, IEEE,
IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY 1 An Evaluation of Popular Copy-Move Forgery Detection Approaches Vincent Christlein, Student Member, IEEE, Christian Riess, Student Member, IEEE,
Reduced Time Complexity for Detection of Copy-Move Forgery Using Discrete Wavelet Transform
 Reduced Time Complexity for of Copy-Move Forgery Using Discrete Wavelet Transform Saiqa Khan Computer Engineering Dept., M.H Saboo Siddik College Of Engg., Mumbai, India Arun Kulkarni Information Technology
Reduced Time Complexity for of Copy-Move Forgery Using Discrete Wavelet Transform Saiqa Khan Computer Engineering Dept., M.H Saboo Siddik College Of Engg., Mumbai, India Arun Kulkarni Information Technology
Thinking Beyond the Block Block Matching for Copy Move Forgery Detection Revisited
 Thinking Beyond the Block Block Matching for Copy Move Forgery Detection Revisited Matthias Kirchner Pascal Schöttle Christian Riess Binghamton University University of Münster Stanford University IS&T/SPIE
Thinking Beyond the Block Block Matching for Copy Move Forgery Detection Revisited Matthias Kirchner Pascal Schöttle Christian Riess Binghamton University University of Münster Stanford University IS&T/SPIE
Anushree U. Tembe 1, Supriya S. Thombre 2 ABSTRACT I. INTRODUCTION. Department of Computer Science & Engineering, YCCE, Nagpur, Maharashtra, India
 ABSTRACT 2017 IJSRSET Volume 3 Issue 2 Print ISSN: 2395-1990 Online ISSN : 2394-4099 Themed Section: Engineering and Technology Copy-Paste Forgery Detection in Digital Image Forensic Anushree U. Tembe
ABSTRACT 2017 IJSRSET Volume 3 Issue 2 Print ISSN: 2395-1990 Online ISSN : 2394-4099 Themed Section: Engineering and Technology Copy-Paste Forgery Detection in Digital Image Forensic Anushree U. Tembe
Improving the Detection and Localization of Duplicated Regions in Copy-Move Image Forgery
 Improving the Detection and Localization of Duplicated Regions in Copy-Move Image Forgery Maryam Jaberi, George Bebis Computer Science and Eng. Dept. University of Nevada, Reno Reno, USA (mjaberi,bebis)@cse.unr.edu
Improving the Detection and Localization of Duplicated Regions in Copy-Move Image Forgery Maryam Jaberi, George Bebis Computer Science and Eng. Dept. University of Nevada, Reno Reno, USA (mjaberi,bebis)@cse.unr.edu
Gabor Filter HOG Based Copy Move Forgery Detection
 IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-issn: 2278-2834,p-ISSN: 2278-8735 PP 41-45 www.iosrjournals.org Gabor Filter HOG Based Copy Move Forgery Detection Monisha Mohan
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-issn: 2278-2834,p-ISSN: 2278-8735 PP 41-45 www.iosrjournals.org Gabor Filter HOG Based Copy Move Forgery Detection Monisha Mohan
Chapter 3 Image Registration. Chapter 3 Image Registration
 Chapter 3 Image Registration Distributed Algorithms for Introduction (1) Definition: Image Registration Input: 2 images of the same scene but taken from different perspectives Goal: Identify transformation
Chapter 3 Image Registration Distributed Algorithms for Introduction (1) Definition: Image Registration Input: 2 images of the same scene but taken from different perspectives Goal: Identify transformation
Countermeasure for the Protection of Face Recognition Systems Against Mask Attacks
 Countermeasure for the Protection of Face Recognition Systems Against Mask Attacks Neslihan Kose, Jean-Luc Dugelay Multimedia Department EURECOM Sophia-Antipolis, France {neslihan.kose, jean-luc.dugelay}@eurecom.fr
Countermeasure for the Protection of Face Recognition Systems Against Mask Attacks Neslihan Kose, Jean-Luc Dugelay Multimedia Department EURECOM Sophia-Antipolis, France {neslihan.kose, jean-luc.dugelay}@eurecom.fr
ScienceDirect. Pixel based Image Forensic Technique for copy-move forgery detection using Auto Color Correlogram.
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 79 (2016 ) 383 390 7th International Conference on Communication, Computing and Virtualization 2016 Pixel based Image Forensic
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 79 (2016 ) 383 390 7th International Conference on Communication, Computing and Virtualization 2016 Pixel based Image Forensic
Feature Descriptors. CS 510 Lecture #21 April 29 th, 2013
 Feature Descriptors CS 510 Lecture #21 April 29 th, 2013 Programming Assignment #4 Due two weeks from today Any questions? How is it going? Where are we? We have two umbrella schemes for object recognition
Feature Descriptors CS 510 Lecture #21 April 29 th, 2013 Programming Assignment #4 Due two weeks from today Any questions? How is it going? Where are we? We have two umbrella schemes for object recognition
An Adaptive Threshold LBP Algorithm for Face Recognition
 An Adaptive Threshold LBP Algorithm for Face Recognition Xiaoping Jiang 1, Chuyu Guo 1,*, Hua Zhang 1, and Chenghua Li 1 1 College of Electronics and Information Engineering, Hubei Key Laboratory of Intelligent
An Adaptive Threshold LBP Algorithm for Face Recognition Xiaoping Jiang 1, Chuyu Guo 1,*, Hua Zhang 1, and Chenghua Li 1 1 College of Electronics and Information Engineering, Hubei Key Laboratory of Intelligent
Texture Classification by Combining Local Binary Pattern Features and a Self-Organizing Map
 Texture Classification by Combining Local Binary Pattern Features and a Self-Organizing Map Markus Turtinen, Topi Mäenpää, and Matti Pietikäinen Machine Vision Group, P.O.Box 4500, FIN-90014 University
Texture Classification by Combining Local Binary Pattern Features and a Self-Organizing Map Markus Turtinen, Topi Mäenpää, and Matti Pietikäinen Machine Vision Group, P.O.Box 4500, FIN-90014 University
Face and Nose Detection in Digital Images using Local Binary Patterns
 Face and Nose Detection in Digital Images using Local Binary Patterns Stanko Kružić Post-graduate student University of Split, Faculty of Electrical Engineering, Mechanical Engineering and Naval Architecture
Face and Nose Detection in Digital Images using Local Binary Patterns Stanko Kružić Post-graduate student University of Split, Faculty of Electrical Engineering, Mechanical Engineering and Naval Architecture
A Key-Point Based Robust Algorithm for Detecting Cloning Forgery
 Research Article International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347-5161 2014 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Mariam
Research Article International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347-5161 2014 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Mariam
Chapter 11 Representation & Description
 Chain Codes Chain codes are used to represent a boundary by a connected sequence of straight-line segments of specified length and direction. The direction of each segment is coded by using a numbering
Chain Codes Chain codes are used to represent a boundary by a connected sequence of straight-line segments of specified length and direction. The direction of each segment is coded by using a numbering
LOCAL AND GLOBAL DESCRIPTORS FOR PLACE RECOGNITION IN ROBOTICS
 8th International DAAAM Baltic Conference "INDUSTRIAL ENGINEERING - 19-21 April 2012, Tallinn, Estonia LOCAL AND GLOBAL DESCRIPTORS FOR PLACE RECOGNITION IN ROBOTICS Shvarts, D. & Tamre, M. Abstract: The
8th International DAAAM Baltic Conference "INDUSTRIAL ENGINEERING - 19-21 April 2012, Tallinn, Estonia LOCAL AND GLOBAL DESCRIPTORS FOR PLACE RECOGNITION IN ROBOTICS Shvarts, D. & Tamre, M. Abstract: The
A new predictive image compression scheme using histogram analysis and pattern matching
 University of Wollongong Research Online University of Wollongong in Dubai - Papers University of Wollongong in Dubai 00 A new predictive image compression scheme using histogram analysis and pattern matching
University of Wollongong Research Online University of Wollongong in Dubai - Papers University of Wollongong in Dubai 00 A new predictive image compression scheme using histogram analysis and pattern matching
Copy-move Forgery Detection in the Presence of Similar but Genuine Objects
 Copy-move Forgery Detection in the Presence of Similar but Genuine Objects Ye Zhu 1, 2, Tian-Tsong Ng 2, Bihan Wen 3, Xuanjing Shen 1, Bin Li 4 1 College of Computer Science and Technology, Jilin University,
Copy-move Forgery Detection in the Presence of Similar but Genuine Objects Ye Zhu 1, 2, Tian-Tsong Ng 2, Bihan Wen 3, Xuanjing Shen 1, Bin Li 4 1 College of Computer Science and Technology, Jilin University,
Content Based Image Retrieval Using Color Quantizes, EDBTC and LBP Features
 Content Based Image Retrieval Using Color Quantizes, EDBTC and LBP Features 1 Kum Sharanamma, 2 Krishnapriya Sharma 1,2 SIR MVIT Abstract- To describe the image features the Local binary pattern (LBP)
Content Based Image Retrieval Using Color Quantizes, EDBTC and LBP Features 1 Kum Sharanamma, 2 Krishnapriya Sharma 1,2 SIR MVIT Abstract- To describe the image features the Local binary pattern (LBP)
CS4733 Class Notes, Computer Vision
 CS4733 Class Notes, Computer Vision Sources for online computer vision tutorials and demos - http://www.dai.ed.ac.uk/hipr and Computer Vision resources online - http://www.dai.ed.ac.uk/cvonline Vision
CS4733 Class Notes, Computer Vision Sources for online computer vision tutorials and demos - http://www.dai.ed.ac.uk/hipr and Computer Vision resources online - http://www.dai.ed.ac.uk/cvonline Vision
ON THE EFFECTIVENESS OF LOCAL WARPING AGAINST SIFT-BASED COPY-MOVE DETECTION
 ON THE EFFECTIVENESS OF LOCAL WARPING AGAINST SIFT-BASED COPY-MOVE DETECTION R. Caldelli, I. Amerini, L. Ballan, G. Serra Media Integration and Communication Center University of Florence Viale Morgagni,
ON THE EFFECTIVENESS OF LOCAL WARPING AGAINST SIFT-BASED COPY-MOVE DETECTION R. Caldelli, I. Amerini, L. Ballan, G. Serra Media Integration and Communication Center University of Florence Viale Morgagni,
MULTI ORIENTATION PERFORMANCE OF FEATURE EXTRACTION FOR HUMAN HEAD RECOGNITION
 MULTI ORIENTATION PERFORMANCE OF FEATURE EXTRACTION FOR HUMAN HEAD RECOGNITION Panca Mudjirahardjo, Rahmadwati, Nanang Sulistiyanto and R. Arief Setyawan Department of Electrical Engineering, Faculty of
MULTI ORIENTATION PERFORMANCE OF FEATURE EXTRACTION FOR HUMAN HEAD RECOGNITION Panca Mudjirahardjo, Rahmadwati, Nanang Sulistiyanto and R. Arief Setyawan Department of Electrical Engineering, Faculty of
EE368 Project Report CD Cover Recognition Using Modified SIFT Algorithm
 EE368 Project Report CD Cover Recognition Using Modified SIFT Algorithm Group 1: Mina A. Makar Stanford University mamakar@stanford.edu Abstract In this report, we investigate the application of the Scale-Invariant
EE368 Project Report CD Cover Recognition Using Modified SIFT Algorithm Group 1: Mina A. Makar Stanford University mamakar@stanford.edu Abstract In this report, we investigate the application of the Scale-Invariant
RGB Digital Image Forgery Detection Using Singular Value Decomposition and One Dimensional Cellular Automata
 RGB Digital Image Forgery Detection Using Singular Value Decomposition and One Dimensional Cellular Automata Ahmad Pahlavan Tafti Mohammad V. Malakooti Department of Computer Engineering IAU, UAE Branch
RGB Digital Image Forgery Detection Using Singular Value Decomposition and One Dimensional Cellular Automata Ahmad Pahlavan Tafti Mohammad V. Malakooti Department of Computer Engineering IAU, UAE Branch
Locating 1-D Bar Codes in DCT-Domain
 Edith Cowan University Research Online ECU Publications Pre. 2011 2006 Locating 1-D Bar Codes in DCT-Domain Alexander Tropf Edith Cowan University Douglas Chai Edith Cowan University 10.1109/ICASSP.2006.1660449
Edith Cowan University Research Online ECU Publications Pre. 2011 2006 Locating 1-D Bar Codes in DCT-Domain Alexander Tropf Edith Cowan University Douglas Chai Edith Cowan University 10.1109/ICASSP.2006.1660449
Weighted Multi-scale Local Binary Pattern Histograms for Face Recognition
 Weighted Multi-scale Local Binary Pattern Histograms for Face Recognition Olegs Nikisins Institute of Electronics and Computer Science 14 Dzerbenes Str., Riga, LV1006, Latvia Email: Olegs.Nikisins@edi.lv
Weighted Multi-scale Local Binary Pattern Histograms for Face Recognition Olegs Nikisins Institute of Electronics and Computer Science 14 Dzerbenes Str., Riga, LV1006, Latvia Email: Olegs.Nikisins@edi.lv
Detecting Printed and Handwritten Partial Copies of Line Drawings Embedded in Complex Backgrounds
 9 1th International Conference on Document Analysis and Recognition Detecting Printed and Handwritten Partial Copies of Line Drawings Embedded in Complex Backgrounds Weihan Sun, Koichi Kise Graduate School
9 1th International Conference on Document Analysis and Recognition Detecting Printed and Handwritten Partial Copies of Line Drawings Embedded in Complex Backgrounds Weihan Sun, Koichi Kise Graduate School
On the Function of Graphic Language in Poster Design
 doi:10.21311/001.39.9.30 On the Function of Graphic Language in Poster Design Hong Zhao Anhui Institute of Information Engineering, Wuhu Anhui, 241000, China Abstract Graphic language in this paper refers
doi:10.21311/001.39.9.30 On the Function of Graphic Language in Poster Design Hong Zhao Anhui Institute of Information Engineering, Wuhu Anhui, 241000, China Abstract Graphic language in this paper refers
Detecting Forgery in Duplicated Region using Keypoint Matching
 International Journal of Scientific and Research Publications, Volume 2, Issue 11, November 2012 1 Detecting Forgery in Duplicated Region using Keypoint Matching N. Suganthi*, N. Saranya**, M. Agila***
International Journal of Scientific and Research Publications, Volume 2, Issue 11, November 2012 1 Detecting Forgery in Duplicated Region using Keypoint Matching N. Suganthi*, N. Saranya**, M. Agila***
Feature descriptors. Alain Pagani Prof. Didier Stricker. Computer Vision: Object and People Tracking
 Feature descriptors Alain Pagani Prof. Didier Stricker Computer Vision: Object and People Tracking 1 Overview Previous lectures: Feature extraction Today: Gradiant/edge Points (Kanade-Tomasi + Harris)
Feature descriptors Alain Pagani Prof. Didier Stricker Computer Vision: Object and People Tracking 1 Overview Previous lectures: Feature extraction Today: Gradiant/edge Points (Kanade-Tomasi + Harris)
SIFT - scale-invariant feature transform Konrad Schindler
 SIFT - scale-invariant feature transform Konrad Schindler Institute of Geodesy and Photogrammetry Invariant interest points Goal match points between images with very different scale, orientation, projective
SIFT - scale-invariant feature transform Konrad Schindler Institute of Geodesy and Photogrammetry Invariant interest points Goal match points between images with very different scale, orientation, projective
Lecture 2 Image Processing and Filtering
 Lecture 2 Image Processing and Filtering UW CSE vision faculty What s on our plate today? Image formation Image sampling and quantization Image interpolation Domain transformations Affine image transformations
Lecture 2 Image Processing and Filtering UW CSE vision faculty What s on our plate today? Image formation Image sampling and quantization Image interpolation Domain transformations Affine image transformations
CS 4495 Computer Vision A. Bobick. CS 4495 Computer Vision. Features 2 SIFT descriptor. Aaron Bobick School of Interactive Computing
 CS 4495 Computer Vision Features 2 SIFT descriptor Aaron Bobick School of Interactive Computing Administrivia PS 3: Out due Oct 6 th. Features recap: Goal is to find corresponding locations in two images.
CS 4495 Computer Vision Features 2 SIFT descriptor Aaron Bobick School of Interactive Computing Administrivia PS 3: Out due Oct 6 th. Features recap: Goal is to find corresponding locations in two images.
2D Image Processing Feature Descriptors
 2D Image Processing Feature Descriptors Prof. Didier Stricker Kaiserlautern University http://ags.cs.uni-kl.de/ DFKI Deutsches Forschungszentrum für Künstliche Intelligenz http://av.dfki.de 1 Overview
2D Image Processing Feature Descriptors Prof. Didier Stricker Kaiserlautern University http://ags.cs.uni-kl.de/ DFKI Deutsches Forschungszentrum für Künstliche Intelligenz http://av.dfki.de 1 Overview
TEXTURE CLASSIFICATION METHODS: A REVIEW
 TEXTURE CLASSIFICATION METHODS: A REVIEW Ms. Sonal B. Bhandare Prof. Dr. S. M. Kamalapur M.E. Student Associate Professor Deparment of Computer Engineering, Deparment of Computer Engineering, K. K. Wagh
TEXTURE CLASSIFICATION METHODS: A REVIEW Ms. Sonal B. Bhandare Prof. Dr. S. M. Kamalapur M.E. Student Associate Professor Deparment of Computer Engineering, Deparment of Computer Engineering, K. K. Wagh
SIFT: SCALE INVARIANT FEATURE TRANSFORM SURF: SPEEDED UP ROBUST FEATURES BASHAR ALSADIK EOS DEPT. TOPMAP M13 3D GEOINFORMATION FROM IMAGES 2014
 SIFT: SCALE INVARIANT FEATURE TRANSFORM SURF: SPEEDED UP ROBUST FEATURES BASHAR ALSADIK EOS DEPT. TOPMAP M13 3D GEOINFORMATION FROM IMAGES 2014 SIFT SIFT: Scale Invariant Feature Transform; transform image
SIFT: SCALE INVARIANT FEATURE TRANSFORM SURF: SPEEDED UP ROBUST FEATURES BASHAR ALSADIK EOS DEPT. TOPMAP M13 3D GEOINFORMATION FROM IMAGES 2014 SIFT SIFT: Scale Invariant Feature Transform; transform image
IMPROVED RHOMBUS INTERPOLATION FOR REVERSIBLE WATERMARKING BY DIFFERENCE EXPANSION. Catalin Dragoi, Dinu Coltuc
 0th European Signal Processing Conference (EUSIPCO 01) Bucharest, Romania, August 7-31, 01 IMPROVED RHOMBUS INTERPOLATION FOR REVERSIBLE WATERMARKING BY DIFFERENCE EXPANSION Catalin Dragoi, Dinu Coltuc
0th European Signal Processing Conference (EUSIPCO 01) Bucharest, Romania, August 7-31, 01 IMPROVED RHOMBUS INTERPOLATION FOR REVERSIBLE WATERMARKING BY DIFFERENCE EXPANSION Catalin Dragoi, Dinu Coltuc
Analysis of Image and Video Using Color, Texture and Shape Features for Object Identification
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 16, Issue 6, Ver. VI (Nov Dec. 2014), PP 29-33 Analysis of Image and Video Using Color, Texture and Shape Features
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 16, Issue 6, Ver. VI (Nov Dec. 2014), PP 29-33 Analysis of Image and Video Using Color, Texture and Shape Features
An Acceleration Scheme to The Local Directional Pattern
 An Acceleration Scheme to The Local Directional Pattern Y.M. Ayami Durban University of Technology Department of Information Technology, Ritson Campus, Durban, South Africa ayamlearning@gmail.com A. Shabat
An Acceleration Scheme to The Local Directional Pattern Y.M. Ayami Durban University of Technology Department of Information Technology, Ritson Campus, Durban, South Africa ayamlearning@gmail.com A. Shabat
Texture. Texture is a description of the spatial arrangement of color or intensities in an image or a selected region of an image.
 Texture Texture is a description of the spatial arrangement of color or intensities in an image or a selected region of an image. Structural approach: a set of texels in some regular or repeated pattern
Texture Texture is a description of the spatial arrangement of color or intensities in an image or a selected region of an image. Structural approach: a set of texels in some regular or repeated pattern
A FRAMEWORK FOR ANALYZING TEXTURE DESCRIPTORS
 A FRAMEWORK FOR ANALYZING TEXTURE DESCRIPTORS Timo Ahonen and Matti Pietikäinen Machine Vision Group, University of Oulu, PL 4500, FI-90014 Oulun yliopisto, Finland tahonen@ee.oulu.fi, mkp@ee.oulu.fi Keywords:
A FRAMEWORK FOR ANALYZING TEXTURE DESCRIPTORS Timo Ahonen and Matti Pietikäinen Machine Vision Group, University of Oulu, PL 4500, FI-90014 Oulun yliopisto, Finland tahonen@ee.oulu.fi, mkp@ee.oulu.fi Keywords:
A Robust Method for Circle / Ellipse Extraction Based Canny Edge Detection
 International Journal of Research Studies in Science, Engineering and Technology Volume 2, Issue 5, May 2015, PP 49-57 ISSN 2349-4751 (Print) & ISSN 2349-476X (Online) A Robust Method for Circle / Ellipse
International Journal of Research Studies in Science, Engineering and Technology Volume 2, Issue 5, May 2015, PP 49-57 ISSN 2349-4751 (Print) & ISSN 2349-476X (Online) A Robust Method for Circle / Ellipse
Comparison of Digital Image Watermarking Algorithms. Xu Zhou Colorado School of Mines December 1, 2014
 Comparison of Digital Image Watermarking Algorithms Xu Zhou Colorado School of Mines December 1, 2014 Outlier Introduction Background on digital image watermarking Comparison of several algorithms Experimental
Comparison of Digital Image Watermarking Algorithms Xu Zhou Colorado School of Mines December 1, 2014 Outlier Introduction Background on digital image watermarking Comparison of several algorithms Experimental
Broad field that includes low-level operations as well as complex high-level algorithms
 Image processing About Broad field that includes low-level operations as well as complex high-level algorithms Low-level image processing Computer vision Computational photography Several procedures and
Image processing About Broad field that includes low-level operations as well as complex high-level algorithms Low-level image processing Computer vision Computational photography Several procedures and
Improving Latent Fingerprint Matching Performance by Orientation Field Estimation using Localized Dictionaries
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 11, November 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 11, November 2014,
Texture Feature Extraction Using Improved Completed Robust Local Binary Pattern for Batik Image Retrieval
 Texture Feature Extraction Using Improved Completed Robust Local Binary Pattern for Batik Image Retrieval 1 Arrie Kurniawardhani, 2 Nanik Suciati, 3 Isye Arieshanti 1, Institut Teknologi Sepuluh Nopember,
Texture Feature Extraction Using Improved Completed Robust Local Binary Pattern for Batik Image Retrieval 1 Arrie Kurniawardhani, 2 Nanik Suciati, 3 Isye Arieshanti 1, Institut Teknologi Sepuluh Nopember,
Detecting Multiple Copies of Copy-Move Forgery Based on SURF
 ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Secial Issue 3, March 2014 2014 International Conference
ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Secial Issue 3, March 2014 2014 International Conference
Filtering and Enhancing Images
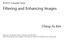 KECE471 Computer Vision Filtering and Enhancing Images Chang-Su Kim Chapter 5, Computer Vision by Shapiro and Stockman Note: Some figures and contents in the lecture notes of Dr. Stockman are used partly.
KECE471 Computer Vision Filtering and Enhancing Images Chang-Su Kim Chapter 5, Computer Vision by Shapiro and Stockman Note: Some figures and contents in the lecture notes of Dr. Stockman are used partly.
Learning based face hallucination techniques: A survey
 Vol. 3 (2014-15) pp. 37-45. : A survey Premitha Premnath K Department of Computer Science & Engineering Vidya Academy of Science & Technology Thrissur - 680501, Kerala, India (email: premithakpnath@gmail.com)
Vol. 3 (2014-15) pp. 37-45. : A survey Premitha Premnath K Department of Computer Science & Engineering Vidya Academy of Science & Technology Thrissur - 680501, Kerala, India (email: premithakpnath@gmail.com)
Color Local Texture Features Based Face Recognition
 Color Local Texture Features Based Face Recognition Priyanka V. Bankar Department of Electronics and Communication Engineering SKN Sinhgad College of Engineering, Korti, Pandharpur, Maharashtra, India
Color Local Texture Features Based Face Recognition Priyanka V. Bankar Department of Electronics and Communication Engineering SKN Sinhgad College of Engineering, Korti, Pandharpur, Maharashtra, India
An Introduction to Content Based Image Retrieval
 CHAPTER -1 An Introduction to Content Based Image Retrieval 1.1 Introduction With the advancement in internet and multimedia technologies, a huge amount of multimedia data in the form of audio, video and
CHAPTER -1 An Introduction to Content Based Image Retrieval 1.1 Introduction With the advancement in internet and multimedia technologies, a huge amount of multimedia data in the form of audio, video and
Fast Image Matching Using Multi-level Texture Descriptor
 Fast Image Matching Using Multi-level Texture Descriptor Hui-Fuang Ng *, Chih-Yang Lin #, and Tatenda Muindisi * Department of Computer Science, Universiti Tunku Abdul Rahman, Malaysia. E-mail: nghf@utar.edu.my
Fast Image Matching Using Multi-level Texture Descriptor Hui-Fuang Ng *, Chih-Yang Lin #, and Tatenda Muindisi * Department of Computer Science, Universiti Tunku Abdul Rahman, Malaysia. E-mail: nghf@utar.edu.my
Local Features: Detection, Description & Matching
 Local Features: Detection, Description & Matching Lecture 08 Computer Vision Material Citations Dr George Stockman Professor Emeritus, Michigan State University Dr David Lowe Professor, University of British
Local Features: Detection, Description & Matching Lecture 08 Computer Vision Material Citations Dr George Stockman Professor Emeritus, Michigan State University Dr David Lowe Professor, University of British
Digital Image Processing (CS/ECE 545) Lecture 5: Edge Detection (Part 2) & Corner Detection
 Digital Image Processing (CS/ECE 545) Lecture 5: Edge Detection (Part 2) & Corner Detection Prof Emmanuel Agu Computer Science Dept. Worcester Polytechnic Institute (WPI) Recall: Edge Detection Image processing
Digital Image Processing (CS/ECE 545) Lecture 5: Edge Detection (Part 2) & Corner Detection Prof Emmanuel Agu Computer Science Dept. Worcester Polytechnic Institute (WPI) Recall: Edge Detection Image processing
Digital Image Forgery Detection Based on GLCM and HOG Features
 Digital Image Forgery Detection Based on GLCM and HOG Features Liya Baby 1, Ann Jose 2 Department of Electronics and Communication, Ilahia College of Engineering and Technology, Muvattupuzha, Ernakulam,
Digital Image Forgery Detection Based on GLCM and HOG Features Liya Baby 1, Ann Jose 2 Department of Electronics and Communication, Ilahia College of Engineering and Technology, Muvattupuzha, Ernakulam,
Textural Features for Image Database Retrieval
 Textural Features for Image Database Retrieval Selim Aksoy and Robert M. Haralick Intelligent Systems Laboratory Department of Electrical Engineering University of Washington Seattle, WA 98195-2500 {aksoy,haralick}@@isl.ee.washington.edu
Textural Features for Image Database Retrieval Selim Aksoy and Robert M. Haralick Intelligent Systems Laboratory Department of Electrical Engineering University of Washington Seattle, WA 98195-2500 {aksoy,haralick}@@isl.ee.washington.edu
Controlling the spread of dynamic self-organising maps
 Neural Comput & Applic (2004) 13: 168 174 DOI 10.1007/s00521-004-0419-y ORIGINAL ARTICLE L. D. Alahakoon Controlling the spread of dynamic self-organising maps Received: 7 April 2004 / Accepted: 20 April
Neural Comput & Applic (2004) 13: 168 174 DOI 10.1007/s00521-004-0419-y ORIGINAL ARTICLE L. D. Alahakoon Controlling the spread of dynamic self-organising maps Received: 7 April 2004 / Accepted: 20 April
A Robust Visual Identifier Using the Trace Transform
 A Robust Visual Identifier Using the Trace Transform P. Brasnett*, M.Z. Bober* *Mitsubishi Electric ITE VIL, Guildford, UK. paul.brasnett@vil.ite.mee.com, miroslaw.bober@vil.ite.mee.com Keywords: image
A Robust Visual Identifier Using the Trace Transform P. Brasnett*, M.Z. Bober* *Mitsubishi Electric ITE VIL, Guildford, UK. paul.brasnett@vil.ite.mee.com, miroslaw.bober@vil.ite.mee.com Keywords: image
CHAPTER 2 TEXTURE CLASSIFICATION METHODS GRAY LEVEL CO-OCCURRENCE MATRIX AND TEXTURE UNIT
 CHAPTER 2 TEXTURE CLASSIFICATION METHODS GRAY LEVEL CO-OCCURRENCE MATRIX AND TEXTURE UNIT 2.1 BRIEF OUTLINE The classification of digital imagery is to extract useful thematic information which is one
CHAPTER 2 TEXTURE CLASSIFICATION METHODS GRAY LEVEL CO-OCCURRENCE MATRIX AND TEXTURE UNIT 2.1 BRIEF OUTLINE The classification of digital imagery is to extract useful thematic information which is one
CHAPTER 5 PALMPRINT RECOGNITION WITH ENHANCEMENT
 145 CHAPTER 5 PALMPRINT RECOGNITION WITH ENHANCEMENT 5.1 INTRODUCTION This chapter discusses the application of enhancement technique in palmprint recognition system. Section 5.2 describes image sharpening
145 CHAPTER 5 PALMPRINT RECOGNITION WITH ENHANCEMENT 5.1 INTRODUCTION This chapter discusses the application of enhancement technique in palmprint recognition system. Section 5.2 describes image sharpening
Digital Image Processing Chapter 11: Image Description and Representation
 Digital Image Processing Chapter 11: Image Description and Representation Image Representation and Description? Objective: To represent and describe information embedded in an image in other forms that
Digital Image Processing Chapter 11: Image Description and Representation Image Representation and Description? Objective: To represent and describe information embedded in an image in other forms that
Learning to Recognize Faces in Realistic Conditions
 000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
QUERY REGION DETERMINATION BASED ON REGION IMPORTANCE INDEX AND RELATIVE POSITION FOR REGION-BASED IMAGE RETRIEVAL
 International Journal of Technology (2016) 4: 654-662 ISSN 2086-9614 IJTech 2016 QUERY REGION DETERMINATION BASED ON REGION IMPORTANCE INDEX AND RELATIVE POSITION FOR REGION-BASED IMAGE RETRIEVAL Pasnur
International Journal of Technology (2016) 4: 654-662 ISSN 2086-9614 IJTech 2016 QUERY REGION DETERMINATION BASED ON REGION IMPORTANCE INDEX AND RELATIVE POSITION FOR REGION-BASED IMAGE RETRIEVAL Pasnur
Evaluation of Image Forgery Detection Using Multi-scale Weber Local Descriptors
 Evaluation of Image Forgery Detection Using Multi-scale Weber Local Descriptors Sahar Q. Saleh 1, Muhammad Hussain 1, Ghulam Muhammad 1, and George Bebis 2 1 College of Computer and Information Sciences,
Evaluation of Image Forgery Detection Using Multi-scale Weber Local Descriptors Sahar Q. Saleh 1, Muhammad Hussain 1, Ghulam Muhammad 1, and George Bebis 2 1 College of Computer and Information Sciences,
Robotics Programming Laboratory
 Chair of Software Engineering Robotics Programming Laboratory Bertrand Meyer Jiwon Shin Lecture 8: Robot Perception Perception http://pascallin.ecs.soton.ac.uk/challenges/voc/databases.html#caltech car
Chair of Software Engineering Robotics Programming Laboratory Bertrand Meyer Jiwon Shin Lecture 8: Robot Perception Perception http://pascallin.ecs.soton.ac.uk/challenges/voc/databases.html#caltech car
Invariant Recognition of Hand-Drawn Pictograms Using HMMs with a Rotating Feature Extraction
 Invariant Recognition of Hand-Drawn Pictograms Using HMMs with a Rotating Feature Extraction Stefan Müller, Gerhard Rigoll, Andreas Kosmala and Denis Mazurenok Department of Computer Science, Faculty of
Invariant Recognition of Hand-Drawn Pictograms Using HMMs with a Rotating Feature Extraction Stefan Müller, Gerhard Rigoll, Andreas Kosmala and Denis Mazurenok Department of Computer Science, Faculty of
CoE4TN4 Image Processing
 CoE4TN4 Image Processing Chapter 11 Image Representation & Description Image Representation & Description After an image is segmented into regions, the regions are represented and described in a form suitable
CoE4TN4 Image Processing Chapter 11 Image Representation & Description Image Representation & Description After an image is segmented into regions, the regions are represented and described in a form suitable
Filtering Images. Contents
 Image Processing and Data Visualization with MATLAB Filtering Images Hansrudi Noser June 8-9, 010 UZH, Multimedia and Robotics Summer School Noise Smoothing Filters Sigmoid Filters Gradient Filters Contents
Image Processing and Data Visualization with MATLAB Filtering Images Hansrudi Noser June 8-9, 010 UZH, Multimedia and Robotics Summer School Noise Smoothing Filters Sigmoid Filters Gradient Filters Contents
Rotation Invariant Finger Vein Recognition *
 Rotation Invariant Finger Vein Recognition * Shaohua Pang, Yilong Yin **, Gongping Yang, and Yanan Li School of Computer Science and Technology, Shandong University, Jinan, China pangshaohua11271987@126.com,
Rotation Invariant Finger Vein Recognition * Shaohua Pang, Yilong Yin **, Gongping Yang, and Yanan Li School of Computer Science and Technology, Shandong University, Jinan, China pangshaohua11271987@126.com,
A New Feature Local Binary Patterns (FLBP) Method
 A New Feature Local Binary Patterns (FLBP) Method Jiayu Gu and Chengjun Liu The Department of Computer Science, New Jersey Institute of Technology, Newark, NJ 07102, USA Abstract - This paper presents
A New Feature Local Binary Patterns (FLBP) Method Jiayu Gu and Chengjun Liu The Department of Computer Science, New Jersey Institute of Technology, Newark, NJ 07102, USA Abstract - This paper presents
Region-based Segmentation
 Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
SUMMARY: DISTINCTIVE IMAGE FEATURES FROM SCALE- INVARIANT KEYPOINTS
 SUMMARY: DISTINCTIVE IMAGE FEATURES FROM SCALE- INVARIANT KEYPOINTS Cognitive Robotics Original: David G. Lowe, 004 Summary: Coen van Leeuwen, s1460919 Abstract: This article presents a method to extract
SUMMARY: DISTINCTIVE IMAGE FEATURES FROM SCALE- INVARIANT KEYPOINTS Cognitive Robotics Original: David G. Lowe, 004 Summary: Coen van Leeuwen, s1460919 Abstract: This article presents a method to extract
Outline 7/2/201011/6/
 Outline Pattern recognition in computer vision Background on the development of SIFT SIFT algorithm and some of its variations Computational considerations (SURF) Potential improvement Summary 01 2 Pattern
Outline Pattern recognition in computer vision Background on the development of SIFT SIFT algorithm and some of its variations Computational considerations (SURF) Potential improvement Summary 01 2 Pattern
Evaluation of texture features for image segmentation
 RIT Scholar Works Articles 9-14-2001 Evaluation of texture features for image segmentation Navid Serrano Jiebo Luo Andreas Savakis Follow this and additional works at: http://scholarworks.rit.edu/article
RIT Scholar Works Articles 9-14-2001 Evaluation of texture features for image segmentation Navid Serrano Jiebo Luo Andreas Savakis Follow this and additional works at: http://scholarworks.rit.edu/article
A Comparison of SIFT, PCA-SIFT and SURF
 A Comparison of SIFT, PCA-SIFT and SURF Luo Juan Computer Graphics Lab, Chonbuk National University, Jeonju 561-756, South Korea qiuhehappy@hotmail.com Oubong Gwun Computer Graphics Lab, Chonbuk National
A Comparison of SIFT, PCA-SIFT and SURF Luo Juan Computer Graphics Lab, Chonbuk National University, Jeonju 561-756, South Korea qiuhehappy@hotmail.com Oubong Gwun Computer Graphics Lab, Chonbuk National
Algorithm for the Digital Forgery Catching Technique for Image Processing Application
 Algorithm for the Digital Forgery Catching Technique for Image Processing Application Manish Jain 1, Vinod Rampure 2 ¹Department of Computer Science and Engineering, Modern Institute of Technology and
Algorithm for the Digital Forgery Catching Technique for Image Processing Application Manish Jain 1, Vinod Rampure 2 ¹Department of Computer Science and Engineering, Modern Institute of Technology and
Computer Vision for HCI. Topics of This Lecture
 Computer Vision for HCI Interest Points Topics of This Lecture Local Invariant Features Motivation Requirements, Invariances Keypoint Localization Features from Accelerated Segment Test (FAST) Harris Shi-Tomasi
Computer Vision for HCI Interest Points Topics of This Lecture Local Invariant Features Motivation Requirements, Invariances Keypoint Localization Features from Accelerated Segment Test (FAST) Harris Shi-Tomasi
Video Inter-frame Forgery Identification Based on Optical Flow Consistency
 Sensors & Transducers 24 by IFSA Publishing, S. L. http://www.sensorsportal.com Video Inter-frame Forgery Identification Based on Optical Flow Consistency Qi Wang, Zhaohong Li, Zhenzhen Zhang, Qinglong
Sensors & Transducers 24 by IFSA Publishing, S. L. http://www.sensorsportal.com Video Inter-frame Forgery Identification Based on Optical Flow Consistency Qi Wang, Zhaohong Li, Zhenzhen Zhang, Qinglong
Improved Non-Local Means Algorithm Based on Dimensionality Reduction
 Improved Non-Local Means Algorithm Based on Dimensionality Reduction Golam M. Maruf and Mahmoud R. El-Sakka (&) Department of Computer Science, University of Western Ontario, London, Ontario, Canada {gmaruf,melsakka}@uwo.ca
Improved Non-Local Means Algorithm Based on Dimensionality Reduction Golam M. Maruf and Mahmoud R. El-Sakka (&) Department of Computer Science, University of Western Ontario, London, Ontario, Canada {gmaruf,melsakka}@uwo.ca
A Miniature-Based Image Retrieval System
 A Miniature-Based Image Retrieval System Md. Saiful Islam 1 and Md. Haider Ali 2 Institute of Information Technology 1, Dept. of Computer Science and Engineering 2, University of Dhaka 1, 2, Dhaka-1000,
A Miniature-Based Image Retrieval System Md. Saiful Islam 1 and Md. Haider Ali 2 Institute of Information Technology 1, Dept. of Computer Science and Engineering 2, University of Dhaka 1, 2, Dhaka-1000,
BRIEF Features for Texture Segmentation
 BRIEF Features for Texture Segmentation Suraya Mohammad 1, Tim Morris 2 1 Communication Technology Section, Universiti Kuala Lumpur - British Malaysian Institute, Gombak, Selangor, Malaysia 2 School of
BRIEF Features for Texture Segmentation Suraya Mohammad 1, Tim Morris 2 1 Communication Technology Section, Universiti Kuala Lumpur - British Malaysian Institute, Gombak, Selangor, Malaysia 2 School of
SOME stereo image-matching methods require a user-selected
 IEEE GEOSCIENCE AND REMOTE SENSING LETTERS, VOL. 3, NO. 2, APRIL 2006 207 Seed Point Selection Method for Triangle Constrained Image Matching Propagation Qing Zhu, Bo Wu, and Zhi-Xiang Xu Abstract In order
IEEE GEOSCIENCE AND REMOTE SENSING LETTERS, VOL. 3, NO. 2, APRIL 2006 207 Seed Point Selection Method for Triangle Constrained Image Matching Propagation Qing Zhu, Bo Wu, and Zhi-Xiang Xu Abstract In order
Copyright Detection System for Videos Using TIRI-DCT Algorithm
 Research Journal of Applied Sciences, Engineering and Technology 4(24): 5391-5396, 2012 ISSN: 2040-7467 Maxwell Scientific Organization, 2012 Submitted: March 18, 2012 Accepted: June 15, 2012 Published:
Research Journal of Applied Sciences, Engineering and Technology 4(24): 5391-5396, 2012 ISSN: 2040-7467 Maxwell Scientific Organization, 2012 Submitted: March 18, 2012 Accepted: June 15, 2012 Published:
