Phishing Activity Trends Report. 4 th Quarter Committed to Wiping Out Internet Scams and Fraud
|
|
|
- Gwen Gordon
- 6 years ago
- Views:
Transcription
1 4 th Quarter 2009 Committed to Wiping Out Internet Scams and Fraud October December 2009
2 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its Global Research Partners, through the organization s website at and by submissions to reportphishing@antiphishing.org. APWG also measures the evolution, proliferation and propagation of crimeware drawing from the research of our member companies. In the last half of this report you will find tabulations of crimeware statistics and related analyses. Phishing Defined Phishing is a criminal mechanism employing both social engineering and technical subterfuge to steal consumers personal identity data and financial account credentials. Social engineering schemes use spoofed e mails purporting to be from legitimate businesses and agencies to lead consumers to counterfeit websites designed to trick recipients into divulging financial data such as usernames and passwords. Technical subterfuge schemes plant crimeware onto PCs to steal credentials directly, often using systems to intercept consumers online account user names and passwords and to corrupt local navigational infrastructures to misdirect consumers to counterfeit websites (or authentic websites through phisher controlled proxies used to monitor and intercept consumers keystrokes). Table of Contents Statistical Highlights for 4 th Quarter, Phishing Reports and Phishing Site Trends 4 Brand-Domain Pairs Measurement 5 Most Used Ports Hosting Phishing Data Collection Servers in 4 th Quarter Brands & Legitimate Entities Hijacked by Phishing Attacks 6 Most Targeted Industry Sectors 7 Countries Hosting Phishing Sites 7 Measurement of Detected Crimeware 8 Rogue Anti-Malware Programs 9 Phishing-based Trojans & Downloader s Host Countries 2 (by IP address) 9 Desktop Crimeware Infections 10 APWG Trends Contributors: Report 4Websense, th Quarter MarkMonitor, / 2009 & Panda Security 11 More Brands Under Attack Than Ever Before, Hitting Record High in Q The fourth quarter of 2009 saw a rise in the number of hijacked brands to a record 356 in October, up nearly 4.4 per cent from the previous record of 341 in August [See page 6 for details.] 4 th Quarter 09 Phishing Activity Trends Summary The number of unique phishing reports submitted to APWG in Q4, 2009 saw a decrease of nearly 29 percent from the all time high of 40,621 in August, dropping to 28,897 reports in December. [p. 4] Member reports to APWG and research reviews reveal a substantial increase in phishing focused on high value targets such as personnel with treasury authority. [p. 4] October s high of 46,522 unique phishing websites detected by the APWG was down 18 percent from the August, 2009 record high of 56,362. [p. 4] The number of unique brand domain pairs rose to a quarter high of 23,380 in October, still down 4 percent from the all time high of 24,438 in August, [p. 5] The United States continued its position as the top country hosting phishing sites in Q4, [p. 7] There was an increase in rogueware variations of 36 percent in Q4 (252,025), up from Q3 (158,980). [p. 9] The total number of infected computers dropped to 10,305,805 in Q4, representing more than 47.8% percent of the total sample of scanned computers, the lowest infection rate recorded in [p. 10] Similar to Q3, Financial Services remained the top of most targeted industry sectors in Q4 [p. 7]
3 Methodology APWG continues to refine and develop its tracking and reporting methodology and to incorporate new data sources into our reports. APWG has re instated the tracking and reporting of unique phishing reports ( campaigns) in addition to unique phishing sites. An campaign is a unique sent out to multiple users, directing them to a specific phishing web site (multiple campaigns may point to the same web site). APWG counts unique phishing report s as those in a given month with the same subject line in the . APWG also tracks the number of unique phishing websites. This is now determined by the unique base URLs of the phishing sites. APWG additionally tracks crimeware instances (unique software applications as determined by MD5 hash of the crimeware sample) as well as unique sites that are distributing crimeware (typically via browser driveby exploits). REPORT DEVELOPMENT NOTE: A new metric was added to the previous 1 st half 2009 Phishing Activity Trends Report and we will continue using this statistic moving forward. Using data contributed from APWG member Websense, measuring proliferation of malevolent software, this metric measures proportions of three genera of malevolent code detected: Crimeware (data stealing malicious code designed specifically to be used to victimize financial institutions customers and to co opt those institutions identities); Data Stealing and Generic Trojans (code designed to send information from the infected machine, control it, and open backdoors on it); Other (the remainder of malicious code commonly encountered in the field such as auto replicating worms, dialers for telephone chargeback scams, etc.) This metric replaced the monthly counts of ʺpassword stealing malicious code URLsʺ and ʺpassword stealing malicious code unique applicationsʺ which, due to multiplicity of counting methods and incongruent sources has proven systematically unreliable. The Measure of Detected Crimeware, APWG believes, provides a more precisely descriptive measure of malevolent code trends. [See page 8] Statistical Highlights for 4 th Quarter, 2009 October November December Number of unique phishing reports received by APWG from consumers 33,254 30,490 28,897 Number of unique phishing web sites detected 46,522 44,907 46,190 Number of brands hijacked by phishing campaigns Country hosting the most phishing websites USA USA USA Contain some form of target name in URL 67.49% 40.09% 42.14% No hostname; just IP address 0.34%.38% 1.65% Percentage of sites not using port % 0.05% 0.15% 3
4 Phishing Reports and Phishing Site Trends 4 th Quarter 2009 The number of unique phishing reports submitted to APWG in the Q4, 2009 saw a substantial drop off after reaching an all time high of 40,621 in August, dropping to 28,897 reports in December, a decline of nearly 29 percent from that record high. Member reports to APWG and research reviews in Q3 and Q4, however, reveal a substantial increase in phishing focused on high value targets such as personnel with treasury authority. APWG Chairman Dave Jevans said, Spear phishing and whale phishing, where targeted individuals inside of corporations, or of high net worth, appears to be increasing. Phishers and malware attackers are sending s to individuals in a highly targeted fashion, attempting to gain access to corporate online banking systems, corporate VPN networks, and other online resources. These attacks do not contribute significantly to the overall number of unique phishing s that are sent, as they are not using broad based spam. Rather, the attackers customize their messages to target individual users, Jevans said. The number of unique phishing websites detected during the fourth quarter of 2009 remained steady, fluctuating by less than 1,300 between October and December. The quarter ended with 46,190 phishing sites detected in December, down some 18 percent from the record high of 56,362 unique phishing websites detected by the APWG in August,
5 Brand-Domain Pairs Measurement 4 th Quarter 2009 The following chart combines statistics based on brands phished, unique domains, unique domain/brand pairs, and unique URLs. Brand/domain pairs count the unique instances of a domain being used to target a specific brand. Example: if several URLs are targeting a brand but are hosted on the same domain this brand/domain pair would be counted as one instead of several. The number of unique brand domain pairs recorded in October at 23,380 was the highest in the quarter but still represented a decline of more than four percent from the all time high of 24,438 recorded in August of last year. Ihab Shraim, chief security officer and vice president, network and system engineering at MarkMonitor and Trends Report contributing analyst said, While phish attacks in Q4 2009, in general, continued at roughly the same rate as the previous quarter, the total number of phish attacks dropped slightly when compared with the previous period. The pattern of attacks per brand is particularly noteworthy. While the number of targeted brands declined in each month of the fourth quarter, the total number of brands targeted in phishing attacks actually increased from the previous quarter. Forensic utility of this metric: If the number of unique URLs is greater than the number of brand/domain pairs, it indicates many URLs are being hosted on the same domain to target the same brand. Knowing how many URLs occur with each domain indicates the approximate number of attacking domains a brand holding victim needs to locate and neutralize. Since Phishing prevention technologies (like browser and blocking) require the full URL, it is useful to understand the general number of unique URLs that occur per domain. October November December Number of Unique Phishing Web Sites Detected 46,522 44,907 46,190 Unique Domains 12,234 12,791 12,601 Unique Brand Domain Pairs 23,380 17,408 14,729 Unique Brands URLs Per Brand
6 Most Used Ports Hosting Phishing Data Collection Servers 4 th Quarter 2009 The fourth quarter of 2009 saw a continuation of HTTP port 80 being the most popular port used of all phishing sites reported, a trend that has been consistent since APWG began tracking and reporting. October November December Port % Port % Port % Port % Port % Port % Port % Port % Port 21.04% Port % Port % Port 78.01% Port % Port % Port % Port % Port % Port 29.01% Port % Port % Brands and Legitimate Entities Hijacked by Phishing Attacks 4 th Quarter 2009 The fourth quarter of 2009 saw a rise in the number of hijacked brands to a record 356 in October, up nearly 4.4 percent from the previous record of 341 in August Phishers continue to expand their target base to attach new brands. [See MarkMonitor commentary on page 5 of this report for additional interpretation.] 6
7 Most Targeted Industry Sectors 4 th Quarter 2009 Similar to Q3, Financial Services remained the top of most targeted industry sectors in Q4. It should be noted however that earlier in the year, the Payment Services category was ranked as the most targeted industry in Q1 and Q2 of Those two quarters presented the first instances in which the Financial Services category lost the top position since APWG began tracking the proportions of phishing attacks directed at each industry sector. Countries Hosting Phishing Sites 4 th Quarter 2009 The United States continued its position as the country hosting the most phishing sites during the fourth quarter of During the APWG H report, Sweden reached the top spot in June but has not appeared in the top 10 after July. Patrik Runald, Senior Manager, Security Research for Websense and APWG Phishing Trends Report contributing analyst said, ʺUnited States continues to be the top country when it comes to hosting phishing sites although China temporarily took over the number one spot in November. We believe that China will disappear from the top 10 list due to the new paperwork requirements that CNNIC [China Internet Network Information Center, registry for the.cn Top Level Domain] introduced in December. During the first quarter of 2010 we will see the effect of this with China being replaced by other countries.ʺ October November December USA 91.51% USA 90.14% USA 72.92% Hong Kong 3.76% Hong Kong 3.22% China 5.24% China 0.96% China 1.73% Canada 3.65% Brazil 0.89% Russia 1.01% Germany 2.12% Rep. Korea 0.47% Rep. Korea 0.55% Hong Kong 1.65% Germany 0.40% Germany 0.53% Rep. Korea 1.47% UK 0.29% UK 0.28% Russia 1.46% Russia 0.20% Canada 0.28% UK 1.44% France 0.18% France 0.26% Netherlands 1.23% Canada 0.17% Netherlands 0.17% France 1.07% 7
8 Crimeware Taxonomy and Samples According to Classification The APWG s Crimeware statistics categorize crimeware attacks as follows, though the taxonomy will grow as variations in attack code are spawned: Definition: Crimeware code which is designed with the intent of collecting information on the end user in order to steal those usersʹ credentials. Unlike most generic keyloggers, phishing based keyloggers have tracking components which attempt to monitor specific actions (and specific organizations, most importantly financial institutions, online retailers, and e commerce merchants) in order to target specific information. The most common types of information are: access to financial based websites, ecommerce sites, and web based mail sites. Measurement of Detected Crimeware 4 th Quarter 2009 The following metric has been added to the with this issue using data contributed from APWG member Websense, measuring proliferation of malevolent software. [See page 3 for more details on this metric.] Over the quarter, the proportion of crimeware specific (malicious code designed specifically against financial institutions customers) malware remained consistent, while data stealing malware grew to 34 percent in November and settled back to the same proportion that it described at the quarter s start with 31 percent. 8 Patrik Runald, Senior Manager, Security Research for Websense and Trends Report Contributing analyst said, ʺData stealing code continues to be an issue with over 35% of all attacks being aimed at stealing information from the user. This is due to the high success rate that hackers obtain when unleashing attacks with data stealing code. These types of attacks will most likely continue at this pace, and possibly increase as attack techniques evolve.ʺ
9 Rogue Anti-Malware Programs 4 th Quarter 2009 According to Luis Corrons, PandaLabs Technical Director and Trends Report contributing analyst, there was a huge increase in the creation of rogueware variations in Q4 (252,025) compared to Q3 (158,980), a increase from quarter to quarter of 36 percent. The high for the quarter, in December with 122,335 variations recorded, is still down nearly 13 percent from the previous record high of 152,197 in June, This is mainly caused by a few rogueware families: in October, 40 percent of all the samples created belonged to the family TotalSecurity2009; and in December, a 66.85% belong to 2 different families: MSAntiSpyware2009 and Antivirus2009. In fact, out of the 252,025 new samples in Q4, 233,965 (92.83%) belong to only four families: Adware/Antivirus2008 Adware/MSAntiSpyware2009 Adware/TotalSecurity2009 Adware/SystemGuard2009 Phishing-based Trojans and Downloader s Hosting Countries (by IP address) This chart represents a breakdown of the websites which were classified during the fourth quarter 2009 as hosting malicious code in the form of either a phishing based keylogger or a Trojan downloader which downloads a keylogger. Similar to last quarter, in which China moved ahead of the United States during August September, this quarter, China jumped to first place in this category during November. 9 October November December USA 28.18% China 29.97% USA 37.08% China 26.65% USA 28.19% China 18.22% Russia 11.17% Netherlands 7.78% Russia 4.90% Germany 5.77% Russia 5.78% Spain 4.19% Brazil 3.39% Brazil 4.77% Netherlands 4.18% Sweden 2.97% Germany 4.36% Germany 3.06% Netherlands 2.67% Rep. Korea 2.70% Brazil 3.01% Rep. Korea 2.42% Spain 1.97% Jamaica 2.19% Turkey 1.55% Canada 1.56% Luxembourg 2.02% Canada 1.51% France 1.33% Rep. Korea 1.90%
10 Desktop Crimeware Infections 4 th Quarter 2009 Scanning and Sampling Methodology: Panda Labs gathers data from millions of computers worldwide through its scanning service to give a statistically valid view of the security situation at the desktop. The scanned computers belong to both corporate and consumer users in more than 100 countries. Though the scanning system checks for many different kinds of potentially unwanted software, for this report, Panda Labs has segmented out Downloaders and Banking Trojans/Password Stealers as they are most often associated with financial crimes such as automated phishing schemes. In Q4, the proportion of infected computers has decreased from percent in Q3 to percent in Q4, the latter the lowest in In the same way, the proportion of banking Trojans has decreased from a percent in Q3 to percent in Q4. However, the proportion of downloaders has increased to 8.47 percent from 8.39 percent in Q3. Q4: Scanned Computers 21,528,736 Infected Computers 10,305, % Non Infected Computers 11,222, % Banking Trojans / Password 3,354, % Downloaders 1,823, % 10
11 APWG Contributors MarkMonitor, the global leader in enterprise brand protection, offers comprehensive solutions and services that safeguard brands, reputation and revenue from online risks. Panda Security s mission is to keep our customersʹ information and IT assets safe from security threats, providing the most effective protection with minimum resource consumption. Websense, Inc. is a global leader in secure Web gateway, data loss prevention and security solutions, protecting more than 43 million employees at organizations worldwide. The APWG is published by the APWG, an industry, government and law enforcement association focused on eliminating the identity theft and frauds that result from the growing problem of phishing, crimeware, and spoofing. For further information about the APWG, please contact APWG Deputy Secretary General Foy Shiver at or fshiver@antiphishing.org. For media inquiries related to the content of this report please contact APWG Secretary General Peter Cassidy at or Te Smith at MarkMonitor at or Te.Smith@markmonitor.com or Luis Corrons at Panda at lcorrons@pandasoftware.es or, for Websense, please contact publicrelations@websense.com. APWG thanks its contributing members, above, for the data and analyses in this report. About the APWG The APWG, founded as the Anti Phishing Working Group in 2003, is an industry association focused on eliminating the identity theft and fraud that result from the growing problem of phishing, crimeware and spoofing. The organization provides a forum to discuss phishing issues, define the scope of the phishing problem in terms of hard and soft costs and consequences, and to share information and best practices for eliminating the problem. Membership is open to qualified financial institutions, online retailers, ISPs, the law enforcement community, and solutions providers. There are more than 1,800 companies and government agencies participating in the APWG and more than 3,500 members. Note that because phishing attacks and fraud are sensitive subjects for many organizations that do business online, the APWG has a policy of maintaining the confidentiality of member organizations. The website of the APWG is It serves as a resource for information about the problem of phishing and electronic frauds perpetrated against personal computers and their users. The APWG, a 501c6 tax exempted corporation, was founded by Tumbleweed Communications, financial services institutions and e commerce providers. APWG s first meeting was in November 2003 in San Francisco and in June 2004 was incorporated as an independent corporation controlled by its steering committee, its board of directors, and its executives. 11 Report data consolidation and editing completed by Ronnie Manning, Mynt Public Relations, since 2005.
Phishing Activity Trends Report. 3 rd Quarter Committed to Wiping Out Internet Scams and Fraud
 3 rd Quarter 2009 Committed to Wiping Out Internet Scams and Fraud July September 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its
3 rd Quarter 2009 Committed to Wiping Out Internet Scams and Fraud July September 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report. 4 th Quarter Unifying the. Global Response To Cybercrime. October December 2012
 4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies,
4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies,
Phishing Activity Trends Report. 3 rd Quarter Unifying the. Global Response To Cybercrime. July September 2012
 3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report March, 2005
 Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report November, 2004
 Phishing Activity Trends Report November, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report November, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
4 th Quarter Phishing Activity Trends Report. Unifying the Global Response To Cybercrime. Activity October December 2017.
 4 th Quarter 2017 Unifying the Global Response To Cybercrime Table of Contents Statistical Highlights for 2nd Quarter 2017 3 Phishing E-mail Reports and Phishing Site Trends 4 Brand-Domain Pairs Measurement
4 th Quarter 2017 Unifying the Global Response To Cybercrime Table of Contents Statistical Highlights for 2nd Quarter 2017 3 Phishing E-mail Reports and Phishing Site Trends 4 Brand-Domain Pairs Measurement
Anti-Phishing Working Group
 Phishing Attack Trends Report April, 2004 Phishing attacks use spoofed e-mails and fraudulent websites designed to fool recipients into divulging personal financial data such as credit card numbers, account
Phishing Attack Trends Report April, 2004 Phishing attacks use spoofed e-mails and fraudulent websites designed to fool recipients into divulging personal financial data such as credit card numbers, account
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY
 RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
October 2009 Report #24
 October 2009 Report #24 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
October 2009 Report #24 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
CE Advanced Network Security Phishing I
 CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
Korea Phishing Activity Trends Report
 Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
The Cost of Denial-of-Services Attacks
 The Cost of Denial-of-Services Attacks Sponsored by Akamai Technologies Independently conducted by Ponemon Institute LLC Publication Date: March 2015 Ponemon Institute Research Report The Cost of Denial-of-Service
The Cost of Denial-of-Services Attacks Sponsored by Akamai Technologies Independently conducted by Ponemon Institute LLC Publication Date: March 2015 Ponemon Institute Research Report The Cost of Denial-of-Service
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
August 2009 Report #22
 August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
Second International Barometer of Security in SMBs
 1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
December 2009 Report #26
 December 2009 Report #26 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This
December 2009 Report #26 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
New Zealand National Cyber Security Centre Incident Summary
 New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Anti-Phishing Working Group
 Anti-Phishing Working Group www.antiphishing.org DNS Policy Sub-Committee Overview Rod Rasmussen Rod.Rasmussen@InternetIdentity.com Anti-Phishing Working Group Launched in 2003 2600+ members 1600+ companies
Anti-Phishing Working Group www.antiphishing.org DNS Policy Sub-Committee Overview Rod Rasmussen Rod.Rasmussen@InternetIdentity.com Anti-Phishing Working Group Launched in 2003 2600+ members 1600+ companies
Spam Evolution Report: October 2009
 Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
The Cost of Phishing. Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015
 The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
NHS South Commissioning Support Unit
 NHS South Commissioning Support Unit ICT Anti-virus Policy This document can be made available in a range of languages and formats on request to the policy author. Version: Ratified by: V.2.1 Alliance
NHS South Commissioning Support Unit ICT Anti-virus Policy This document can be made available in a range of languages and formats on request to the policy author. Version: Ratified by: V.2.1 Alliance
3.5 SECURITY. How can you reduce the risk of getting a virus?
 3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
2014 INTERNET COMMERCE CASE STUDY. The Battle Against Phishing and Fraudulent s. 100 S. Ellsworth Ave 4th Floor San Mateo, CA
 2014 INTERNET COMMERCE CASE STUDY The Battle Against Phishing and Fraudulent Emails 100 S. Ellsworth Ave 4th Floor San Mateo, CA 94401 650.627.7667 ABOUT AGARI Agari analizes big data from the world s
2014 INTERNET COMMERCE CASE STUDY The Battle Against Phishing and Fraudulent Emails 100 S. Ellsworth Ave 4th Floor San Mateo, CA 94401 650.627.7667 ABOUT AGARI Agari analizes big data from the world s
Prolexic Attack Report Q4 2011
 Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
How Enterprise Tackles Phishing. Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong
 How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
Top 10 Global Threat Rank by Source
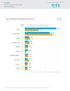 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Whitepaper on AuthShield Two Factor Authentication with SAP
 Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
REPORT. proofpoint.com
 REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
BRING SPEAR PHISHING PROTECTION TO THE MASSES
 E-Guide BRING SPEAR PHISHING PROTECTION TO THE MASSES SearchSecurity phishing. I n this expert tip, David Sherry describes how a combination of technical controls and user awareness training can help put
E-Guide BRING SPEAR PHISHING PROTECTION TO THE MASSES SearchSecurity phishing. I n this expert tip, David Sherry describes how a combination of technical controls and user awareness training can help put
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
U.S. State of Cybercrime
 EXCLUSIVE RESEARCH FROM EXECUTIVE SUMMARY 2017 U.S. State of Cybercrime IDG Communications, Inc. 2017 U.S. State of Cybercrime TODAY S CYBERCRIMES ARE BECOMING MORE TARGETED AND BUILT FOR MAXIMUM IMPACT,
EXCLUSIVE RESEARCH FROM EXECUTIVE SUMMARY 2017 U.S. State of Cybercrime IDG Communications, Inc. 2017 U.S. State of Cybercrime TODAY S CYBERCRIMES ARE BECOMING MORE TARGETED AND BUILT FOR MAXIMUM IMPACT,
WHITEPAPER. Protecting Against Account Takeover Based Attacks
 WHITEPAPER Protecting Against Account Takeover Based Email Attacks Executive Summary The onslaught of targeted email attacks such as business email compromise, spear phishing, and ransomware continues
WHITEPAPER Protecting Against Account Takeover Based Email Attacks Executive Summary The onslaught of targeted email attacks such as business email compromise, spear phishing, and ransomware continues
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
ADVANCED THREAT PREVENTION FOR ENDPOINT DEVICES 5 th GENERATION OF CYBER SECURITY
 ADVANCED THREAT PREVENTION FOR ENDPOINT DEVICES 5 th GENERATION OF CYBER SECURITY OUTLINE Advanced Threat Landscape (genv) Why is endpoint protection essential? Types of attacks and how to prevent them
ADVANCED THREAT PREVENTION FOR ENDPOINT DEVICES 5 th GENERATION OF CYBER SECURITY OUTLINE Advanced Threat Landscape (genv) Why is endpoint protection essential? Types of attacks and how to prevent them
MARKET NEWSLETTER No 69 February 2013
 Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
MRG Effitas Online Banking Browser Security Assessment Project Q Q1 2014
 MRG Effitas Online Banking Browser Security Assessment Project Q3 2013 - Q1 2014 1 Contents Introduction... 3 The Purpose of this Report... 3 Tests Employed... 3 Security Applications Tested... 4 Methodology
MRG Effitas Online Banking Browser Security Assessment Project Q3 2013 - Q1 2014 1 Contents Introduction... 3 The Purpose of this Report... 3 Tests Employed... 3 Security Applications Tested... 4 Methodology
CHAPTER 8 SECURING INFORMATION SYSTEMS
 CHAPTER 8 SECURING INFORMATION SYSTEMS BY: S. SABRAZ NAWAZ SENIOR LECTURER IN MANAGEMENT & IT SEUSL Learning Objectives Why are information systems vulnerable to destruction, error, and abuse? What is
CHAPTER 8 SECURING INFORMATION SYSTEMS BY: S. SABRAZ NAWAZ SENIOR LECTURER IN MANAGEMENT & IT SEUSL Learning Objectives Why are information systems vulnerable to destruction, error, and abuse? What is
DMARC Continuing to enable trust between brand owners and receivers
 DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
McAfee Labs Threat Report
 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
Mapping the Frontiers of the Electronic Crime Threat From Consumers' Desktops to National Equities Markets
 Mapping the Frontiers of the Electronic Crime Threat From Consumers' Desktops to National Equities Markets Peter Cassidy Secretary General www.antiphishing.org pcassidy@antiphishing.org Director of Research
Mapping the Frontiers of the Electronic Crime Threat From Consumers' Desktops to National Equities Markets Peter Cassidy Secretary General www.antiphishing.org pcassidy@antiphishing.org Director of Research
Conducted by Vanson Bourne Research
 Conducted by Vanson Bourne Research N o v e m b e r 2 0 1 3 1 3200 INTERVIEWS ALTOGETHER, 1600 IT & 1600 BUSINESS DECISION- MAKERS 100 & 100 IT BUSINESS DECISION- DECISION- MAKERS MAKERS COUNTRIES USA
Conducted by Vanson Bourne Research N o v e m b e r 2 0 1 3 1 3200 INTERVIEWS ALTOGETHER, 1600 IT & 1600 BUSINESS DECISION- MAKERS 100 & 100 IT BUSINESS DECISION- DECISION- MAKERS MAKERS COUNTRIES USA
The Challenge of Spam An Internet Society Public Policy Briefing
 The Challenge of Spam An Internet Society Public Policy Briefing 30 October 2015 Introduction Spam email, those unsolicited email messages we find cluttering our inboxes, are a challenge for Internet users,
The Challenge of Spam An Internet Society Public Policy Briefing 30 October 2015 Introduction Spam email, those unsolicited email messages we find cluttering our inboxes, are a challenge for Internet users,
Third Annual Green IT & Sustainability Survey: U.S. Results and Services Implications
 Third Annual Green IT & Sustainability Survey: U.S. Results and Services Implications Gard Little Research Manager Worldwide Services, Global Services Markets & Trends 2009 IDC 1 Agenda Overview of the
Third Annual Green IT & Sustainability Survey: U.S. Results and Services Implications Gard Little Research Manager Worldwide Services, Global Services Markets & Trends 2009 IDC 1 Agenda Overview of the
Webomania Solutions Pvt. Ltd. 2017
 The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
Custom Plugin A Solution to Phishing and Pharming Attacks
 Custom Plugin A Solution to Phishing and Pharming Attacks Omer Mahmood School of Information Technology Charles Darwin University Darwin, NT, Australia Abstract - This paper proposes a new method to detect,
Custom Plugin A Solution to Phishing and Pharming Attacks Omer Mahmood School of Information Technology Charles Darwin University Darwin, NT, Australia Abstract - This paper proposes a new method to detect,
Bank of america report phishing
 Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
The State of Spam A Monthly Report August Generated by Symantec Messaging and Web Security
 The State of Spam A Monthly Report August 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape While overall spam activity remained steady in July 2007, the tactics being used are
The State of Spam A Monthly Report August 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape While overall spam activity remained steady in July 2007, the tactics being used are
Updates on Sharing Threat Data, Security Awareness and Policy Efforts to Fight Cybercrime
 Updates on Sharing Threat Data, Security Awareness and Policy Efforts to Fight Cybercrime Foy Shiver Deputy Secretary General Agenda Who We Are Current Events Tracking Trends and Malicious Activities Education
Updates on Sharing Threat Data, Security Awareness and Policy Efforts to Fight Cybercrime Foy Shiver Deputy Secretary General Agenda Who We Are Current Events Tracking Trends and Malicious Activities Education
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
The Rise of Phishing. Dave Brunswick Tumbleweed Communications Anti-Phishing Working Group
 The Rise of Phishing Dave Brunswick Tumbleweed Communications Anti-Phishing Working Group 2 The Anti-Phishing Working Group Industry association focused on eliminating identity theft and fraud from the
The Rise of Phishing Dave Brunswick Tumbleweed Communications Anti-Phishing Working Group 2 The Anti-Phishing Working Group Industry association focused on eliminating identity theft and fraud from the
Perimeter Defenses T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN
 T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
Chapter 6 Network and Internet Security and Privacy
 Chapter 6 Network and Internet Security and Privacy Learning Objectives LO6.1: Explain network and Internet security concerns LO6.2: Identify online threats LO6.3: Describe cyberstalking and other personal
Chapter 6 Network and Internet Security and Privacy Learning Objectives LO6.1: Explain network and Internet security concerns LO6.2: Identify online threats LO6.3: Describe cyberstalking and other personal
Risk Outlook Anti money Laundering and Cybercrime. Steve Wilmott and George Hawkins
 Risk Outlook Anti money Laundering and Cybercrime Steve Wilmott and George Hawkins Introductions Steve Wilmott, Director of Intelligence and Investigations George Hawkins, Senior Technical Advisor, Risk
Risk Outlook Anti money Laundering and Cybercrime Steve Wilmott and George Hawkins Introductions Steve Wilmott, Director of Intelligence and Investigations George Hawkins, Senior Technical Advisor, Risk
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
NOT PROTECTIVELY MARKED PHISHING. July 2016
 - PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
- PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
Trend Micro Reports Record First Quarter Revenue & Operating Profit
 Trend Micro Reports Record First Quarter Revenue & Operating Profit Continued strong growth in U.S and Asia highlight quarter Tokyo, Japan April 25, 2006 Trend Micro, Incorporated (TSE: 4704, NASDAQ: TMIC),
Trend Micro Reports Record First Quarter Revenue & Operating Profit Continued strong growth in U.S and Asia highlight quarter Tokyo, Japan April 25, 2006 Trend Micro, Incorporated (TSE: 4704, NASDAQ: TMIC),
Kaspersky Security Network
 The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
Protecting Against Online Fraud. F5 EMEA Webinar August 2014
 Protecting Against Online Fraud F5 EMEA Webinar August 2014 Agenda Fraud threat trends and business challenges Web fraud protection Mobile fraud protection Security operations center Example architecture
Protecting Against Online Fraud F5 EMEA Webinar August 2014 Agenda Fraud threat trends and business challenges Web fraud protection Mobile fraud protection Security operations center Example architecture
YEAR-END 201O BROADBAND AND IPTV REPORT HIGHLIGHTS: GLOBAL BROADBAND PENETRATION IS THE CRITICAL DRIVER BEHIND BROADBAND FORUM s IPv6 SOLUTIONS
 YEAR-END 201O BROADBAND AND IPTV REPORT HIGHLIGHTS: GLOBAL BROADBAND PENETRATION IS THE CRITICAL DRIVER BEHIND BROADBAND FORUM s IPv6 SOLUTIONS 23 March 2011, London Global IPTV subscription had a record
YEAR-END 201O BROADBAND AND IPTV REPORT HIGHLIGHTS: GLOBAL BROADBAND PENETRATION IS THE CRITICAL DRIVER BEHIND BROADBAND FORUM s IPv6 SOLUTIONS 23 March 2011, London Global IPTV subscription had a record
TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION
 INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
How technology changed fraud investigations. Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011
 How technology changed fraud investigations Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011 The Changing Cyberfraud Landscape Underground Economy Malware Authors Organized
How technology changed fraud investigations Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011 The Changing Cyberfraud Landscape Underground Economy Malware Authors Organized
The Scenes of Cyber Crime
 Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
State of Mobile Commerce. Q
 State of Mobile Commerce. Q4 2014. JANUARY 2015 Executive Summary. Mobile commerce adoption is far ahead of expectations. Globally, mobile now accounts for 30% of ecommerce transactions. It is expected
State of Mobile Commerce. Q4 2014. JANUARY 2015 Executive Summary. Mobile commerce adoption is far ahead of expectations. Globally, mobile now accounts for 30% of ecommerce transactions. It is expected
A Layered Approach to Fraud Mitigation. Nick White Product Manager, FIS Payments Integrated Financial Services
 A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
IPS Securex s revenue rose 36.5% to S$2.3 million in 1Q2018
 IPS Securex Holdings Limited Company Registration Number: 201327639H Incorporated in the Republic of Singapore 213 Henderson Road, #04-09, Henderson Industrial Park Singapore 159553 www.ips-securex.com
IPS Securex Holdings Limited Company Registration Number: 201327639H Incorporated in the Republic of Singapore 213 Henderson Road, #04-09, Henderson Industrial Park Singapore 159553 www.ips-securex.com
The Business of Malware IT Security Presentation
 The Business of Malware IT Security Presentation Secure South West Plymouth University Thursday 20 th September 2012 Presented by: Alan Thake Head of Sales ESET UK Today s Topics The Business of malware
The Business of Malware IT Security Presentation Secure South West Plymouth University Thursday 20 th September 2012 Presented by: Alan Thake Head of Sales ESET UK Today s Topics The Business of malware
Observation by the Internet Fixed-Point Monitoring System (TALOT2) for November 2011
 Observation by the Internet Fixed-Point Monitoring System (TALOT2) for November 2011 Attachment 3 1. To General Internet Users According to the Internet Fixed-Point Monitoring System (TALOT2), 86,568 unwanted
Observation by the Internet Fixed-Point Monitoring System (TALOT2) for November 2011 Attachment 3 1. To General Internet Users According to the Internet Fixed-Point Monitoring System (TALOT2), 86,568 unwanted
Latest View on the Threat of Information Security and Risk Management Trends
 Latest View on the Threat of Information Security and Risk Management Trends Rob K Lamb, Vice-President, Worldwide Sales - Security, IBM Corporation lambr@us.ibm.com 2009 IBM Corporation Topics IBM security
Latest View on the Threat of Information Security and Risk Management Trends Rob K Lamb, Vice-President, Worldwide Sales - Security, IBM Corporation lambr@us.ibm.com 2009 IBM Corporation Topics IBM security
FORGING A TRUE GLOBAL CONNECTION - BROADBAND PASSES 500 MILLION SUBSCRIBERS. One in every five of the world s households now has broadband
 FORGING A TRUE GLOBAL CONNECTION - BROADBAND PASSES 500 MILLION SUBSCRIBERS One in every five of the world s households now has broadband 20 September 2010, Hong Kong Broadband has taken a significant
FORGING A TRUE GLOBAL CONNECTION - BROADBAND PASSES 500 MILLION SUBSCRIBERS One in every five of the world s households now has broadband 20 September 2010, Hong Kong Broadband has taken a significant
GTIC Monthly Threat Report June 2017
 GTIC Monthly Threat Report June 2017 Trickbot mac1 Phishing Campaign Name GTIC Monthly Threat Report June 2017 Owner Classification Status NTT Security GTIC TICT Aaron Perkins UNCLASSIFIED-EXTERNAL APPROVED
GTIC Monthly Threat Report June 2017 Trickbot mac1 Phishing Campaign Name GTIC Monthly Threat Report June 2017 Owner Classification Status NTT Security GTIC TICT Aaron Perkins UNCLASSIFIED-EXTERNAL APPROVED
TABLE OF CONTENTS Introduction: IS A TOP THREAT VECTOR... 3 THE PROBLEM: ATTACKS ARE EVOLVING FASTER THAN DEFENSES...
 The Guide TABLE OF CONTENTS Introduction: EMAIL IS A TOP THREAT VECTOR... 3 THE PROBLEM: ATTACKS ARE EVOLVING FASTER THAN EMAIL DEFENSES... 4 Today s Top Email Fraud Tactics...5 Advanced Malware...8 Outbound
The Guide TABLE OF CONTENTS Introduction: EMAIL IS A TOP THREAT VECTOR... 3 THE PROBLEM: ATTACKS ARE EVOLVING FASTER THAN EMAIL DEFENSES... 4 Today s Top Email Fraud Tactics...5 Advanced Malware...8 Outbound
Automated Context and Incident Response
 Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
ELECTRONIC BANKING & ONLINE AUTHENTICATION
 ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE
 CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE The Customer: Top 10 Airline CREDENTIAL STUFFING KILLCHAIN A Top 10 Global Airline that earns over $15 Billion in annual revenue and serves
CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE The Customer: Top 10 Airline CREDENTIAL STUFFING KILLCHAIN A Top 10 Global Airline that earns over $15 Billion in annual revenue and serves
Unique Phishing Attacks (2008 vs in thousands)
 The process of attempting to acquire sensitive information, such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. In the 2 nd half
The process of attempting to acquire sensitive information, such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. In the 2 nd half
Managed Enterprise Phishing Protection. Comprehensive protection delivered 24/7 by anti-phishing experts
 Managed Enterprise Phishing Protection Comprehensive protection delivered 24/7 by anti-phishing experts MANAGED ENTERPRISE PHISHING PROTECTION 24/7 expert protection against phishing attacks that get past
Managed Enterprise Phishing Protection Comprehensive protection delivered 24/7 by anti-phishing experts MANAGED ENTERPRISE PHISHING PROTECTION 24/7 expert protection against phishing attacks that get past
Electronic Identity Theft and Basic Security
 Electronic Identity Theft and Basic Security Prepared for DACS By Philip Chen CCSP, NSA infosec Professional 10-2-2007 Pchen@hi-link.com Agenda Introduction Examples Effective Security Defenses for Enterprises
Electronic Identity Theft and Basic Security Prepared for DACS By Philip Chen CCSP, NSA infosec Professional 10-2-2007 Pchen@hi-link.com Agenda Introduction Examples Effective Security Defenses for Enterprises
Site Data Protection (SDP) Program Update
 Advanced Payments October 9, 2006 Site Data Protection (SDP) Program Update Agenda Security Landscape PCI Security Standards Council SDP Program October 9, 2006 SDP Program Update 2 Security Landscape
Advanced Payments October 9, 2006 Site Data Protection (SDP) Program Update Agenda Security Landscape PCI Security Standards Council SDP Program October 9, 2006 SDP Program Update 2 Security Landscape
Symantec Intelligence Quarterly: Best Practices and Methodologies October - December, 2009
 Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Learning from a breach
 WHITEPAPER Learning from a breach How security breaches happen and how to stop them in their tracks. Breaches are on the rise Today, many IT and business leaders cannot confidently claim their organizations
WHITEPAPER Learning from a breach How security breaches happen and how to stop them in their tracks. Breaches are on the rise Today, many IT and business leaders cannot confidently claim their organizations
Evaluating DMARC Effectiveness for the Financial Services Industry
 Evaluating DMARC Effectiveness for the Financial Services Industry by Robert Holmes General Manager, Email Fraud Protection Return Path Executive Summary Email spoofing steadily increases annually. DMARC
Evaluating DMARC Effectiveness for the Financial Services Industry by Robert Holmes General Manager, Email Fraud Protection Return Path Executive Summary Email spoofing steadily increases annually. DMARC
Fraud Mobility: Exploitation Patterns and Insights
 WHITEPAPER Fraud Mobility: Exploitation Patterns and Insights September 2015 2 Table of Contents Introduction 3 Study Methodology 4 Once a SSN has been Compromised, it Remains at Risk 4 Victims Remain
WHITEPAPER Fraud Mobility: Exploitation Patterns and Insights September 2015 2 Table of Contents Introduction 3 Study Methodology 4 Once a SSN has been Compromised, it Remains at Risk 4 Victims Remain
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Automating Security Response based on Internet Reputation
 Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
