Joomla! custom reports using TinyButStrong
|
|
|
- Katherine Turner
- 6 years ago
- Views:
Transcription
1 Joomla! custom reports using TinyButStrong Summary A get started guide: Part 2 staying secure Joomla! Administrators familiar with the database and with SQL can use TinyButStrong (TBS) to present information from the database in web pages without needing to create a module or component. The first article in this series looked at the creation of simple tables, delivering the required information in a simple layout. This article looks at the security issues around using TBS and suggests how TBS might be used most securely. The concepts developed here are presented as a practical example in part 3 of this series. Purpose The TBS plugin for Joomla! allows access to the Joomla! database and therefore has security implications. It has various security related options that can be used to balance convenience and security. Some of these options are discussed in this note. There are no references here to information on general website security or on Joomla! security as these would rapidly become outdated. For such information, current web searches are the best approach. The risks TBS allows direct access to the database containing all the information in a Joomla! web site. This essentially bypasses the normal security mechanisms. These are there to ensure that information designated as available only to specific groups is indeed only available to those groups. If you set up a way of accessing information using TBS, it is up to you to ensure that information does not become more widely available than it should be. In some jurisdictions, the information in the Joomla! database may be covered by data privacy legislation. Another class of information within the database is that defining the Joomla! site itself. Unauthorised access to this may allow others to hack your system. The design of TBS is such that simply installing it does not compromise the security of your site. The extent to which others can access the data is determined by paramters set by you, the administrator. TBS security mechanisms Plugin access The plugin can be configured as usable by all, by restricted & special users or by special users only. In some situations it may be possible to use the plugin access configuration as the primary security control. If so, administration and system design become much easier. In practice, it is likely that the data presentation facilities provided by TBS will be used for publicly available data as well as for restricted data. When this is the case, the data access security features and associated system design must be used to maintain security. Data access The TBS plugin for Joomla! can be operated in three different ways: 1 Jul 2011 Joomla! custom reports with TinyButStrong : Part 2 Page 1 of 5
2 Direct MergeBlocks External scripts Internal scripts Each has its use and its security implications. The security issues arise from access to the database, not from the presentation of data on the web site, hence [square bracket] sections related to TBS templates will not be discussed in this article. The approaches used have parameters that can be set in the TBS plugin. These are discussed in the following sections. In addition, the article number of every article using TBS must be specified in the plugin's parameters. This feature can be circumvented by specifying * as the article number. Setting the article number to * is not recommended if anyone other than the administrator has editor rights. Direct MergeBlocks Data is accessed using a TBS block of the form {tbs}mergeblock=blockname; sql=sql statements {/tbs} This would appear in a Joomla! article. It is a convenient way to get started with TBS as it keeps the data extraction and the presentation templates in the same place, thus simplifying the development process. The parameter Direct MergeBlock has the following possible settings: Forbidden Only SELECT queries (default) All query types and stored procedures Because any SELECT command can be issued from the Direct MergeBlock, anyone with the authority to change the article can change the SELECT command to access any data in the database. You therefore need to be very sure that no one with the ability to edit articles might have any reason to hunt through the database for information beyond their normal authority. If the plugin's Direct MergeBlock parameter is set to All query types and stored procedures, someone able to edit the article can easily gain access as a super-administrator to your site. This a serious security risk. The facility can be useful as a development tool on a private network behind a firewall. 1. It is most appropriate for a personal website where only one person maintains the site. 2. Never use Direct MergeBlocks with All query types and stored procedures on a publicly accessible web site. 3. Set the Direct MergeBlock parameter to Forbidden unless you are running a site with very few people authorised to edit articles and on which there is no information protected by data privacy laws (e.g. names and contact information). 1 Jul 2011 Joomla! custom reports with TinyButStrong : Part 2 Page 2 of 5
3 4. Set the Direct MergeBlock parameter to only SELECT queries if you want to use TBS but you don't want to use External Scripts. External Scripts Data is accessed using a TBS block of the form {tbs}script=myscript.php{/tbs} The file myscript.php is a PHP language file including TBS elements. If given as a simple file name, it should be stored in the directory given in the Script Location parameter of the plugin. The External Scripts parameter has the following possible settings: Forbidden Only from the Script location (default) All external scripts An external script can contain any valid PHP, hence there is no restriction on what can be done by the script. At first, this might seem to be a recipe for complete insecurity 1 but read on. The important feature of the External Scripts mechanism is the ability to specify the location in which the script files can be found. This is done using the Only from Script location parameter setting. By setting this to be a directory on your web server but outside the web root directory, you can ensure that only those with FTP access to your site are able to amend the script. Typically only the super-administrator group would have FTP access to files outside the web root, hence the superadministrator can create the scripts, ensuring that no sensitive information is available through them. Those with the the authority to edit documents can be shown the script files without compromising the database and they can use the data created by the script files in templates, only releasing the information deemed proper by the script's author. By contrast, setting the parameter to All external scripts hands anyone with the authority to edit articles the keys to your site. The open_basedir parameter of the php.ini can be used to limit the risk but if used in its normal form where scripts must lie within the web-site, it must be extended to permit the use of scripts in the TBS script directory. If you are not a PHP programmer, don't be put off: there is an example script file in the appendix. If you can manipulate SQL as required by TBS, you shouldn't have any problem with the trivial PHP required. 1. Create all script files in a directory outside the web root. If the open_basedir parameter is set in your php.ini file, you may need to amend it, e.g. open_basedir = /home/sites/[mysite]/public_html:/home/sites/ [mysite]/tbsscripts It is not in the scope of this article to explain the open_basedir parameter. 2. Nominate the directory in (1) above as the location for script files. 1 If you don't understand why, you probably shouldn't be administering a Joomla! site 1 Jul 2011 Joomla! custom reports with TinyButStrong : Part 2 Page 3 of 5
4 3. Keep the External Scripts parameter at its default value of Only from the Script location. 4. Ensure that no sensitive fields (e.g. password ) are accessible through External Scripts. Internal Scripts Within the HTML include two separate sections: {tbs}embedded{/tbs} which tells TBS to look for an internal script, and <!--TBS PHP code --> which contains PHP code with TBS elements. 1. Forbidden 2. Allowed Internal scripts provide all the security risks of external scripts with none of the safeguards. There may be circumstances where it is easier to develop a script using the Internal script approach before converting it to an external script. This should only be considered for a personal web server behind a firewall and never for a publicly accessible site. 1. Don't use them. 2. Set the Internal Scripts parameter to Forbidden. Conclusion For publicly accessible web sites, use only External Scripts and store these outside the web root. Set both the Direct MergeBlock and Internal Script parameters to Forbidden. Acknowledgement Without the author and maintainer of TBS, skrol29, none of this would be possible. It is clear that TBS is both very well designed and very well implemented. Thank you, skrol29 and your associates. CheshireCat 1 Jul Jul 2011 Joomla! custom reports with TinyButStrong : Part 2 Page 4 of 5
5 Appendix 1 Sample External Script At its simplest, the external script file will contain: <?php $TBS->MergeBlock('blockname','mysql','SQL code');?> where blockname is the name of the block as used in the template [square bracket] sections, mysql is the database type (it might be mysqli in some sites) and SQL code is the SQL you wish to run against the Joomla! Database. Note that although the examples use the same name for the block and for the PHP file, there is no necessity to make the names the same. The first example from article 1 used a Direct MergeBlock: {tbs}mergeblock=content;sql=select title, hits FROM jos_content ORDER BY hits DESC LIMIT 0, 10{/tbs} This could be replaced by: {tbs}script=content1.php{/tbs} where file content1.php contains the following: <?php $TBS->MergeBlock('content','mysql','SELECT title, hits FROM jos_content ORDER BY hits DESC LIMIT 0, 10');?> As noted in the main part of this article, the file content1.php should be in the directory nominated in the Script Location parameter and this directory should lie outside the web root. 1 Jul 2011 Joomla! custom reports with TinyButStrong : Part 2 Page 5 of 5
Joomla 3.X Global Settings Part III Server Settings
 Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Page 1 of 13. E-COMMERCE PROJECT HundW Consult MENA Instructor: Ahmad Hammad Phone:
 E-COMMERCE PROJECT HundW Consult MENA Instructor: Ahmad Hammad Email: AhmadNassr@gmail.com Phone: 0599042502 1. Rationale This is the major project for both (Open Source and.net teams) as an E-Commerce
E-COMMERCE PROJECT HundW Consult MENA Instructor: Ahmad Hammad Email: AhmadNassr@gmail.com Phone: 0599042502 1. Rationale This is the major project for both (Open Source and.net teams) as an E-Commerce
Publish Joomla! Article
 Enterprise Architect User Guide Series Publish Joomla! Article Author: Sparx Systems Date: 10/05/2018 Version: 1.0 CREATED WITH Table of Contents Publish Joomla! Article 3 Install Joomla! Locally 4 Set
Enterprise Architect User Guide Series Publish Joomla! Article Author: Sparx Systems Date: 10/05/2018 Version: 1.0 CREATED WITH Table of Contents Publish Joomla! Article 3 Install Joomla! Locally 4 Set
Publish Joomla! Article
 Enterprise Architect User Guide Series Publish Joomla! Article Sparx Systems Enterprise Architect supports publishing an entire model, or part of the model, in a local Joomla! Repository as Articles (HTML
Enterprise Architect User Guide Series Publish Joomla! Article Sparx Systems Enterprise Architect supports publishing an entire model, or part of the model, in a local Joomla! Repository as Articles (HTML
Birmingham Midshires - Terms and Conditions Mortgage Intermediaries On-line Terms of Use (June 2017)
 Birmingham Midshires - Terms and Conditions http://www.bmsolutions.co.uk/terms/ Mortgage Intermediaries On-line Terms of Use (June 2017) 1. General Which Terms Apply? - Directly Authorised Firms:If you
Birmingham Midshires - Terms and Conditions http://www.bmsolutions.co.uk/terms/ Mortgage Intermediaries On-line Terms of Use (June 2017) 1. General Which Terms Apply? - Directly Authorised Firms:If you
Content Management Systems. Week 14 LBSC 671 Creating Information Infrastructures
 Content Management Systems Week 14 LBSC 671 Creating Information Infrastructures Putting the Pieces Together Browser HTML CGI Web Server SQL Query Database HTML Results Why Database-Generated Pages? Remote
Content Management Systems Week 14 LBSC 671 Creating Information Infrastructures Putting the Pieces Together Browser HTML CGI Web Server SQL Query Database HTML Results Why Database-Generated Pages? Remote
HEXDATA DOCUMENTATION
 HEXDATA DOCUMENTATION Overview:- HexData is an import/export tool based on Joomla CMS. It provides you a very simple and flexible way to add/update data to your Website. It also allows you to keep a backup
HEXDATA DOCUMENTATION Overview:- HexData is an import/export tool based on Joomla CMS. It provides you a very simple and flexible way to add/update data to your Website. It also allows you to keep a backup
About the Tutorial. Audience. Prerequisites. Copyright & Disclaimer. Joomla
 About the Tutorial Joomla is an open source Content Management System (CMS), which is used to build websites and online applications. It is free and extendable which is separated into frontend templates
About the Tutorial Joomla is an open source Content Management System (CMS), which is used to build websites and online applications. It is free and extendable which is separated into frontend templates
Installing and Confi guring Joomla! 1.5 and Jobs! Pro 1.3.2
 Installing and Confi guring Joomla! 1.5 and Jobs! Pro 1.3.2 Joomla! has earned a reputation of being one of the most powerful CMS programs around, as its core team emerged from another popular open source
Installing and Confi guring Joomla! 1.5 and Jobs! Pro 1.3.2 Joomla! has earned a reputation of being one of the most powerful CMS programs around, as its core team emerged from another popular open source
Drupal Command Line Instructions Windows 7 List All >>>CLICK HERE<<<
 Drupal Command Line Instructions Windows 7 List All Drush is a command-line interface for Drupal that provides a wide set of utilities for administering and drush @pantheon.drupal-7-sandbox.dev status
Drupal Command Line Instructions Windows 7 List All Drush is a command-line interface for Drupal that provides a wide set of utilities for administering and drush @pantheon.drupal-7-sandbox.dev status
Locate your Advanced Tools and Applications
 MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
Accessing an Extremely Secure LAN Via Remote Access That Was Not Possible With Previous Technologies
 Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
Dreamweaver MX The Basics
 Chapter 1 Dreamweaver MX 2004 - The Basics COPYRIGHTED MATERIAL Welcome to Dreamweaver MX 2004! Dreamweaver is a powerful Web page creation program created by Macromedia. It s included in the Macromedia
Chapter 1 Dreamweaver MX 2004 - The Basics COPYRIGHTED MATERIAL Welcome to Dreamweaver MX 2004! Dreamweaver is a powerful Web page creation program created by Macromedia. It s included in the Macromedia
MySQL On Crux Part II The GUI Client
 DATABASE MANAGEMENT USING SQL (CIS 331) MYSL ON CRUX (Part 2) MySQL On Crux Part II The GUI Client MySQL is the Structured Query Language processor that we will be using for this class. MySQL has been
DATABASE MANAGEMENT USING SQL (CIS 331) MYSL ON CRUX (Part 2) MySQL On Crux Part II The GUI Client MySQL is the Structured Query Language processor that we will be using for this class. MySQL has been
Joomla 3.X User Manager
 Joomla 3.X User Manager Introduction Most Joomla websites have three levels of content available: 1. Content that can be accessed totally free by every one that visits the website 2. Content that requires
Joomla 3.X User Manager Introduction Most Joomla websites have three levels of content available: 1. Content that can be accessed totally free by every one that visits the website 2. Content that requires
Static Webpage Development
 Dear Student, Based upon your enquiry we are pleased to send you the course curriculum for PHP Given below is the brief description for the course you are looking for: - Static Webpage Development Introduction
Dear Student, Based upon your enquiry we are pleased to send you the course curriculum for PHP Given below is the brief description for the course you are looking for: - Static Webpage Development Introduction
Content Management Systems
 Content Management Systems By multiple authors, see citation for each section Overview This reading includes two documents that explain the concept behind content management (CMS) systems and why you would
Content Management Systems By multiple authors, see citation for each section Overview This reading includes two documents that explain the concept behind content management (CMS) systems and why you would
Developing Online Databases and Serving Biological Research Data
 Developing Online Databases and Serving Biological Research Data 1 Last Time PHP scripts can be used to create better web interfaces for specific database schemas If you want something more user friendly
Developing Online Databases and Serving Biological Research Data 1 Last Time PHP scripts can be used to create better web interfaces for specific database schemas If you want something more user friendly
Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE. s3security.com
 Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE s3security.com Security Professional Services S3 offers security services through its Security Professional Services (SPS) group, the security-consulting
Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE s3security.com Security Professional Services S3 offers security services through its Security Professional Services (SPS) group, the security-consulting
SETTING UP AND RUNNING A WEB SITE ON YOUR LENOVO STORAGE DEVICE WORKING WITH WEB SERVER TOOLS
 White Paper SETTING UP AND RUNNING A WEB SITE ON YOUR LENOVO STORAGE DEVICE WORKING WITH WEB SERVER TOOLS CONTENTS Introduction 1 Audience 1 Terminology 1 Enabling a custom home page 1 Adding webmysqlserver
White Paper SETTING UP AND RUNNING A WEB SITE ON YOUR LENOVO STORAGE DEVICE WORKING WITH WEB SERVER TOOLS CONTENTS Introduction 1 Audience 1 Terminology 1 Enabling a custom home page 1 Adding webmysqlserver
Website Designing for
 5 Website Designing for www.scap.com.pk Complete Proposal for website designing and associated web solutions of www.scap.com.pk. The web solutions included, Search Engine Optimization and web hosting.
5 Website Designing for www.scap.com.pk Complete Proposal for website designing and associated web solutions of www.scap.com.pk. The web solutions included, Search Engine Optimization and web hosting.
CONTENTS IN DETAIL INTRODUCTION 1 THE FAQS OF LIFE THE SCRIPTS EVERY PHP PROGRAMMER WANTS (OR NEEDS) TO KNOW 1 2 CONFIGURING PHP 19
 CONTENTS IN DETAIL INTRODUCTION xiii 1 THE FAQS OF LIFE THE SCRIPTS EVERY PHP PROGRAMMER WANTS (OR NEEDS) TO KNOW 1 #1: Including Another File as a Part of Your Script... 2 What Can Go Wrong?... 3 #2:
CONTENTS IN DETAIL INTRODUCTION xiii 1 THE FAQS OF LIFE THE SCRIPTS EVERY PHP PROGRAMMER WANTS (OR NEEDS) TO KNOW 1 #1: Including Another File as a Part of Your Script... 2 What Can Go Wrong?... 3 #2:
Introduction to PHP. Handling Html Form With Php. Decisions and loop. Function. String. Array
 Introduction to PHP Evaluation of Php Basic Syntax Defining variable and constant Php Data type Operator and Expression Handling Html Form With Php Capturing Form Data Dealing with Multi-value filed Generating
Introduction to PHP Evaluation of Php Basic Syntax Defining variable and constant Php Data type Operator and Expression Handling Html Form With Php Capturing Form Data Dealing with Multi-value filed Generating
TERMS & CONDITIONS PLEASE READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THE SITE
 TERMS & CONDITIONS PLEASE READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THE SITE 1. General The term PPS refers to: Professional Provident Society Holdings Trust, (The Holding Trust); Professional
TERMS & CONDITIONS PLEASE READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THE SITE 1. General The term PPS refers to: Professional Provident Society Holdings Trust, (The Holding Trust); Professional
Learning PHP & MySQL: Step-by-Step Guide To Creating Database-Driven Web Sites By Michele E. Davis, Jon A. Phillips
 Learning PHP & MySQL: Step-by-Step Guide To Creating Database-Driven Web Sites By Michele E. Davis, Jon A. Phillips If looking for a ebook Learning PHP & MySQL: Step-by-Step Guide to Creating Database-Driven
Learning PHP & MySQL: Step-by-Step Guide To Creating Database-Driven Web Sites By Michele E. Davis, Jon A. Phillips If looking for a ebook Learning PHP & MySQL: Step-by-Step Guide to Creating Database-Driven
Web Hosting Control Panel
 Web Hosting Control Panel cpanel Hosting refers to any web hosting plan that uses cpanel as its web hosting control panel. cpanel is the leading control panel interface in the web hosting industry today.
Web Hosting Control Panel cpanel Hosting refers to any web hosting plan that uses cpanel as its web hosting control panel. cpanel is the leading control panel interface in the web hosting industry today.
STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY
 STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY Introduction The college offer an extensive range of IT systems across campuses and online for course related activities and drop-in purposes. This policy applies
STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY Introduction The college offer an extensive range of IT systems across campuses and online for course related activities and drop-in purposes. This policy applies
WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN
 WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN Document Control Document Properties Title Author Document Type Filename File location
WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN Document Control Document Properties Title Author Document Type Filename File location
Joomla Basics Series: Joomla Overview
 Joomla Basics Series: Joomla Overview Presented By - Wilma Howell http://www.gktsolutions.com What is Joomla! Joomla! is a popular, free, award-winning Content Management System (CMS) written in PHP and
Joomla Basics Series: Joomla Overview Presented By - Wilma Howell http://www.gktsolutions.com What is Joomla! Joomla! is a popular, free, award-winning Content Management System (CMS) written in PHP and
2.1 Website means operated and owned by UCS Technology Services, including any page, part of element thereof;
 WEBSITE USAGE TERMS AND CONDITIONS Acceptable Usage Terms 1. Introduction 1.1 By accessing the UCS Technology Services website, web pages or any part thereof for any reason whatsoever, the User agrees
WEBSITE USAGE TERMS AND CONDITIONS Acceptable Usage Terms 1. Introduction 1.1 By accessing the UCS Technology Services website, web pages or any part thereof for any reason whatsoever, the User agrees
KEIL software. Index of contents INSTALLATION
 Index of contents 1. Important information 1.1. Requirements 1.2. Additional language files 1.3. Thumbnail creation and resizing 1.4. Data protection and shop security 2. Installation 2.1. FTP upload 2.2.
Index of contents 1. Important information 1.1. Requirements 1.2. Additional language files 1.3. Thumbnail creation and resizing 1.4. Data protection and shop security 2. Installation 2.1. FTP upload 2.2.
CITY SECURITY MAGAZINE
 DATA PRIVACY POLICY as 14 MARCH 2018 Policy Overview We take your privacy seriously and will only use your personal information to administer your subscription with us. We will not share or rent your personal
DATA PRIVACY POLICY as 14 MARCH 2018 Policy Overview We take your privacy seriously and will only use your personal information to administer your subscription with us. We will not share or rent your personal
Development Technologies. Agenda: phpmyadmin 2/20/2016. phpmyadmin MySQLi. Before you can put your data into a table, that table should exist.
 CIT 736: Internet and Web Development Technologies Lecture 10 Dr. Lupiana, DM FCIM, Institute of Finance Management Semester 1, 2016 Agenda: phpmyadmin MySQLi phpmyadmin Before you can put your data into
CIT 736: Internet and Web Development Technologies Lecture 10 Dr. Lupiana, DM FCIM, Institute of Finance Management Semester 1, 2016 Agenda: phpmyadmin MySQLi phpmyadmin Before you can put your data into
White Paper: Clustering of Servers in ABBYY FlexiCapture
 White Paper: Clustering of Servers in ABBYY FlexiCapture By: Jim Hill Published: May 2018 Introduction Configuring an ABBYY FlexiCapture Distributed system in a cluster using Microsoft Windows Server Clustering
White Paper: Clustering of Servers in ABBYY FlexiCapture By: Jim Hill Published: May 2018 Introduction Configuring an ABBYY FlexiCapture Distributed system in a cluster using Microsoft Windows Server Clustering
Controls Electronic messaging Information involved in electronic messaging shall be appropriately protected.
 I Use of computers This document is part of the UCISA Information Security Toolkit providing guidance on the policies and processes needed to implement an organisational information security policy. To
I Use of computers This document is part of the UCISA Information Security Toolkit providing guidance on the policies and processes needed to implement an organisational information security policy. To
Jacobs University userweb Guide January 2016
 Jacobs University userweb Guide January 2016 Every Jacobs member, students included, can create up to five LAMP hosts by themselves and access the file system by FTP to upload files, store data in a MySql
Jacobs University userweb Guide January 2016 Every Jacobs member, students included, can create up to five LAMP hosts by themselves and access the file system by FTP to upload files, store data in a MySql
Custom Fields With Virtuemart 2. Simple Custom Fields. Creating a Custom Field Type
 Customization in Virtuemart 2 Custom Fields With Virtuemart 2 Custom Plugin Fields in Virtuemart 2 Part 1. Installing and Using Custom Plugin Fields Custom Plugin Fields in Virtuemart 2 Part 2. Programming
Customization in Virtuemart 2 Custom Fields With Virtuemart 2 Custom Plugin Fields in Virtuemart 2 Part 1. Installing and Using Custom Plugin Fields Custom Plugin Fields in Virtuemart 2 Part 2. Programming
Improving Security in Wireless Networks
 Improving Security in Wireless Networks Introduction Wireless networking provides many advantages over conventional wired networks. For instance the ability to connect to your network resources without
Improving Security in Wireless Networks Introduction Wireless networking provides many advantages over conventional wired networks. For instance the ability to connect to your network resources without
Keeping your healthcare information secure: Simple security and privacy tips
 Keeping your healthcare information secure: Simple security and privacy tips This guide provides awareness of privacy settings that you can use to adjust your My Health Record to suit your own requirements.
Keeping your healthcare information secure: Simple security and privacy tips This guide provides awareness of privacy settings that you can use to adjust your My Health Record to suit your own requirements.
Joomla 1.6 Integration
 Joomla 1.6 Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 5.3 Setting
Joomla 1.6 Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 5.3 Setting
Token Sale Privacy Policy
 Token Sale Privacy Policy PRIVACY POLICY LAST UPDATED ON: [11 SEP 2018] A. OVERVIEW You must read the entirety of this Privacy Policy carefully before making any decision to purchase Tokens. You must also
Token Sale Privacy Policy PRIVACY POLICY LAST UPDATED ON: [11 SEP 2018] A. OVERVIEW You must read the entirety of this Privacy Policy carefully before making any decision to purchase Tokens. You must also
Privacy Policy. LAST UPDATED: 23 June March 2017
 Privacy Policy LAST UPDATED: 23 June 20156 March 2017 VERSION 3.0 2.0 Comment [A1]: The Privacy Policy has been updated because we now use Google Analytics, to help improve our services and our communications
Privacy Policy LAST UPDATED: 23 June 20156 March 2017 VERSION 3.0 2.0 Comment [A1]: The Privacy Policy has been updated because we now use Google Analytics, to help improve our services and our communications
Revision of HSBC Bank Malaysia Berhad ( HSBC Bank ) Universal Terms and Conditions
 Revision of HSBC Bank Malaysia Berhad ( HSBC Bank ) Universal Terms and Conditions Dear valued customers, We would like to inform that our Universal Terms and Conditions for HSBC Bank will be updated and
Revision of HSBC Bank Malaysia Berhad ( HSBC Bank ) Universal Terms and Conditions Dear valued customers, We would like to inform that our Universal Terms and Conditions for HSBC Bank will be updated and
PHP & PHP++ Curriculum
 PHP & PHP++ Curriculum CORE PHP How PHP Works The php.ini File Basic PHP Syntax PHP Tags PHP Statements and Whitespace Comments PHP Functions Variables Variable Types Variable Names (Identifiers) Type
PHP & PHP++ Curriculum CORE PHP How PHP Works The php.ini File Basic PHP Syntax PHP Tags PHP Statements and Whitespace Comments PHP Functions Variables Variable Types Variable Names (Identifiers) Type
"Charting the Course... Intermediate PHP & MySQL Course Summary
 Course Summary Description In this PHP training course, students will learn to create database-driven websites using PHP and MySQL or the database of their choice. The class also covers SQL basics. Objectives
Course Summary Description In this PHP training course, students will learn to create database-driven websites using PHP and MySQL or the database of their choice. The class also covers SQL basics. Objectives
Terms and Conditions 01 January 2016
 Terms and Conditions 01 January 2016 thehealthsource: Terms and Conditions Page 1 of 7 This Agreement (the Agreement ) is entered into by and between thehealthsource (Pty) Ltd and the entity agreeing to
Terms and Conditions 01 January 2016 thehealthsource: Terms and Conditions Page 1 of 7 This Agreement (the Agreement ) is entered into by and between thehealthsource (Pty) Ltd and the entity agreeing to
VxWorks Real-Time Kernel Connectivity
 Florida Gulf Coast University VxWorks Real-Time Kernel Connectivity An Internet Toolkit for Remote Device Testing Michael Lekon Instructor: Janusz Zalewski Fort Myers, Florida 12/4/2009 Table of Contents
Florida Gulf Coast University VxWorks Real-Time Kernel Connectivity An Internet Toolkit for Remote Device Testing Michael Lekon Instructor: Janusz Zalewski Fort Myers, Florida 12/4/2009 Table of Contents
Privacy policy. Privacy Policy
 Privacy policy Privacy Policy This privacy policy is for this website (www.stoll.org.uk) provided by Stoll (Sir Oswald Stoll Foundation) and governs the privacy of those people who choose to use it. The
Privacy policy Privacy Policy This privacy policy is for this website (www.stoll.org.uk) provided by Stoll (Sir Oswald Stoll Foundation) and governs the privacy of those people who choose to use it. The
SIMPLIFi Compliance Software User Manual
 SIMPLIFi Compliance Software User Manual Version 1.7 2013 Simplifi-Solutions Ltd, Environmental Center, Unit B5, The Gordon Manley Building, Lancaster University, LA1 4WA Telephone: 01524 510431 Email:
SIMPLIFi Compliance Software User Manual Version 1.7 2013 Simplifi-Solutions Ltd, Environmental Center, Unit B5, The Gordon Manley Building, Lancaster University, LA1 4WA Telephone: 01524 510431 Email:
Advanced Ethical Hacking & Penetration Testing. Ethical Hacking
 Summer Training Internship Program 2017 (STIP - 2017) is a practical oriented & industrial level training program for all students who have aspiration to work in the core technical industry domain. This
Summer Training Internship Program 2017 (STIP - 2017) is a practical oriented & industrial level training program for all students who have aspiration to work in the core technical industry domain. This
Coastal Babysitters Privacy Policy
 . Coastal Babysitters Privacy Policy Orly Isa Muscat trading as "Coastal Babysitters" (ABN 66 206 628 086) ("we", "us" or the "Company") is committed to privacy protection. At http://coastalbabysitters.com.au/
. Coastal Babysitters Privacy Policy Orly Isa Muscat trading as "Coastal Babysitters" (ABN 66 206 628 086) ("we", "us" or the "Company") is committed to privacy protection. At http://coastalbabysitters.com.au/
PF4 Google Calendar Synchronisation
 PF4 Google Calendar Synchronisation synchronise your ProjectFork tasks and milestones with Google Calendar. Kon Angelopoulos ABSTRACT PF4 Google Calendar Synchronisation is a Joomla 3.x package that provides
PF4 Google Calendar Synchronisation synchronise your ProjectFork tasks and milestones with Google Calendar. Kon Angelopoulos ABSTRACT PF4 Google Calendar Synchronisation is a Joomla 3.x package that provides
Using in Schools
 Using e-mail in Schools Education, Leisure & Lifelong Learning Baglan Information Technology Centre C O N T E N T S Page Background... 1 Teaching e-safety... 1 Using e-mail to enhance teaching and learning...
Using e-mail in Schools Education, Leisure & Lifelong Learning Baglan Information Technology Centre C O N T E N T S Page Background... 1 Teaching e-safety... 1 Using e-mail to enhance teaching and learning...
OS Property Ajax search module
 OS Property Ajax search module By Ossolution Version 1.0 [Updated: March 2013] Introduction This extension dramatically changes your concept about the search modules. Fancy design, real-time working and
OS Property Ajax search module By Ossolution Version 1.0 [Updated: March 2013] Introduction This extension dramatically changes your concept about the search modules. Fancy design, real-time working and
Privacy notice. Last updated: 25 May 2018
 Privacy notice Last updated: 25 May 2018 www.courtprice.co.uk ('Website') is provided by Courtprice Limited ('we'/'us'/'our'). In doing so, we may be in a position to receive and process personal information
Privacy notice Last updated: 25 May 2018 www.courtprice.co.uk ('Website') is provided by Courtprice Limited ('we'/'us'/'our'). In doing so, we may be in a position to receive and process personal information
Chapter 12 Databases and Database Management Systems
 Chapter 12 Databases and Database Management Systems permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. What Is a Database?
Chapter 12 Databases and Database Management Systems permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use. What Is a Database?
MASTERCARD PRICELESS SPECIALS INDIA PRIVACY POLICY
 Effective Date: 12 September 2017 MASTERCARD PRICELESS SPECIALS INDIA PRIVACY POLICY Mastercard respects your privacy. This Privacy Policy describes how we process personal data, the types of personal
Effective Date: 12 September 2017 MASTERCARD PRICELESS SPECIALS INDIA PRIVACY POLICY Mastercard respects your privacy. This Privacy Policy describes how we process personal data, the types of personal
Web Hosting Control Panel
 Web Hosting Control Panel 1 P a g e Our web hosting control panel has been created to provide you with all the tools you need to make the most of your website. This guide will provide you with an over
Web Hosting Control Panel 1 P a g e Our web hosting control panel has been created to provide you with all the tools you need to make the most of your website. This guide will provide you with an over
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
The Table Privacy Policy Last revised on August 22, 2012
 The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
ABOUT WEB TECHNOLOGY COURSE SCOPE:
 ABOUT WEB TECHNOLOGY COURSE SCOPE: The booming IT business across the globe, the web has become one in every of the foremost necessary suggests that of communication nowadays and websites are the lifelines
ABOUT WEB TECHNOLOGY COURSE SCOPE: The booming IT business across the globe, the web has become one in every of the foremost necessary suggests that of communication nowadays and websites are the lifelines
Table of Contents. 1. Introduction 1. 1 Overview Business Context Glossary...3
 Table of Contents 1. Introduction 1. 1 Overview......2 1. 2 Business Context.. 2 1. 3 Glossary...3 2. General Description 2. 1 Product/System Functions..4 2. 2 User Characteristics and Objectives 4 2.
Table of Contents 1. Introduction 1. 1 Overview......2 1. 2 Business Context.. 2 1. 3 Glossary...3 2. General Description 2. 1 Product/System Functions..4 2. 2 User Characteristics and Objectives 4 2.
Starflow Token Sale Privacy Policy
 Starflow Token Sale Privacy Policy Last Updated: 23 March 2018 Please read this Privacy Policy carefully. By registering your interest to participate in the sale of STAR tokens (the Token Sale ) through
Starflow Token Sale Privacy Policy Last Updated: 23 March 2018 Please read this Privacy Policy carefully. By registering your interest to participate in the sale of STAR tokens (the Token Sale ) through
TIA. Privacy Policy and Cookie Policy 5/25/18
 TIA Privacy Policy and Cookie Policy 5/25/18 Background: TIA understands that your privacy is important to you and that you care about how your information is used and shared online. We respect and value
TIA Privacy Policy and Cookie Policy 5/25/18 Background: TIA understands that your privacy is important to you and that you care about how your information is used and shared online. We respect and value
Attend Events. Version 0.9.x
 Attend Events Version 0.9.x Contents 1 Introduction 3 1.1 Features................................ 3 1.2 JEvents Integration.......................... 4 2 Installation and Set-Up 5 2.1 Installation..............................
Attend Events Version 0.9.x Contents 1 Introduction 3 1.1 Features................................ 3 1.2 JEvents Integration.......................... 4 2 Installation and Set-Up 5 2.1 Installation..............................
Providence Web Site Terms of Use and Privacy Policy
 Page 1 of 11 Providence Web Site Terms of Use and Privacy Policy Providence Health & Services (called Providence below) operates a system of hospitals, physician clinics, home care and other health care
Page 1 of 11 Providence Web Site Terms of Use and Privacy Policy Providence Health & Services (called Providence below) operates a system of hospitals, physician clinics, home care and other health care
Installing Joomla
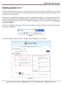 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Guidelines for work on the Genebank KB site
 Guidelines for work on the Genebank KB site (By Geert Claessens. For extra information email to geert.jef.claessens@gmail.com) These guidelines are written for users of the Crop Genebank Knowledge Base
Guidelines for work on the Genebank KB site (By Geert Claessens. For extra information email to geert.jef.claessens@gmail.com) These guidelines are written for users of the Crop Genebank Knowledge Base
Greyhead.net. How-to docs and tutorials. ChronoConnectivity How-to doc Static filters for your listing CHRONO. Connectivity
 How-to docs and tutorials ChronoConnectivity How-to doc Static filters for your listing How to select the records to be displayed in ChronoConnection listing. Using the WHERE SQL box to select records
How-to docs and tutorials ChronoConnectivity How-to doc Static filters for your listing How to select the records to be displayed in ChronoConnection listing. Using the WHERE SQL box to select records
Excerpts of Web Application Security focusing on Data Validation. adapted for F.I.S.T. 2004, Frankfurt
 Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Zend EXAM Zend Certified PHP Engineer. Buy Full Product.
 Zend EXAM - 200-550 Zend Certified PHP Engineer Buy Full Product http://www.examskey.com/200-550.html Examskey Zend 200-550 exam demo product is here for you to test the quality of the product. This Zend
Zend EXAM - 200-550 Zend Certified PHP Engineer Buy Full Product http://www.examskey.com/200-550.html Examskey Zend 200-550 exam demo product is here for you to test the quality of the product. This Zend
2. What is Personal Information and Non-Personally Identifiable Information?
 Privacy Notice Snipp Interactive, Inc. Last Updated: February 11, 2016 Contents: 1. Introduction 2. What is Personal Information? 3. Information we collect about you 4. Use of Your Information 5. Location
Privacy Notice Snipp Interactive, Inc. Last Updated: February 11, 2016 Contents: 1. Introduction 2. What is Personal Information? 3. Information we collect about you 4. Use of Your Information 5. Location
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 3 Protecting Systems
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
What is cloud computing? The enterprise is liable as data controller. Various forms of cloud computing. Data controller
 A guide to CLOUD COMPUTING 2014 Cloud computing Businesses that make use of cloud computing are legally liable, and must ensure that personal data is processed in accordance with the relevant legislation
A guide to CLOUD COMPUTING 2014 Cloud computing Businesses that make use of cloud computing are legally liable, and must ensure that personal data is processed in accordance with the relevant legislation
Transaction Safe Feature in MySQL Databases
 Transaction Safe Feature in MySQL Databases Index Understanding the MySQL 5.0 Storage Engines 1 The Tools 1 Some more stuff you must know 1 Let's work a little 2 More tools Using PHP 3 Not all can be undone
Transaction Safe Feature in MySQL Databases Index Understanding the MySQL 5.0 Storage Engines 1 The Tools 1 Some more stuff you must know 1 Let's work a little 2 More tools Using PHP 3 Not all can be undone
TERMS AND CONDITIONS
 TERMS AND CONDITIONS Welcome to www.westcornwallpasty.co.uk. If you continue to browse and use this website, you are agreeing to comply with and be bound by the following terms and conditions of use, which
TERMS AND CONDITIONS Welcome to www.westcornwallpasty.co.uk. If you continue to browse and use this website, you are agreeing to comply with and be bound by the following terms and conditions of use, which
SMS SERVICE PROVISION
 SMS SERVICE PROVISION Terms and Conditions and Privacy Policy Version 2.05 Jan 2017 Page 1 Contents TERMS & CONDITIONS... 3 Registration... 3 Your Personal Information... 3 Our Obligations to SMS Service
SMS SERVICE PROVISION Terms and Conditions and Privacy Policy Version 2.05 Jan 2017 Page 1 Contents TERMS & CONDITIONS... 3 Registration... 3 Your Personal Information... 3 Our Obligations to SMS Service
Install Apache, PHP And MySQL On CentOS 7 (LAMP)
 Install Apache, PHP And MySQL On CentOS 7 (LAMP) Version 1.0 Authors: Till Brehm , Falko Timme Updates: Srijan Kishore Follow Howtoforge
Install Apache, PHP And MySQL On CentOS 7 (LAMP) Version 1.0 Authors: Till Brehm , Falko Timme Updates: Srijan Kishore Follow Howtoforge
SCADA Expert Vijeo Citect 2015 Programming with Cicode Study Guide
 SCADA Expert Vijeo Citect 2015 Programming with Cicode Study Guide 2015 Schneider-Electric Pty (Australia) Ltd 78 Waterloo Road Macquarie Park NSW 2113 Australia DISCLAIMER Schneider Electric makes no
SCADA Expert Vijeo Citect 2015 Programming with Cicode Study Guide 2015 Schneider-Electric Pty (Australia) Ltd 78 Waterloo Road Macquarie Park NSW 2113 Australia DISCLAIMER Schneider Electric makes no
National Unit Specification: general information. The Internet (Higher) NUMBER DM4F 12. Information Systems (Higher)
 National Unit Specification: general information NUMBER DM4F 12 COURSE Information Systems (Higher) SUMMARY This Unit is designed to develop knowledge and understanding of the operating principles of the
National Unit Specification: general information NUMBER DM4F 12 COURSE Information Systems (Higher) SUMMARY This Unit is designed to develop knowledge and understanding of the operating principles of the
Step 1: Accessing the account
 Quick guide Step 1: Accessing the account Step 2: Download RSFiles! Step 3: Installing RSFiles! Step 4: RSFiles! settings 4.1 Add the license code in the General tab 4.2 File settings 4.3 Frontend settings
Quick guide Step 1: Accessing the account Step 2: Download RSFiles! Step 3: Installing RSFiles! Step 4: RSFiles! settings 4.1 Add the license code in the General tab 4.2 File settings 4.3 Frontend settings
JobRouter Product description Version 3.0
 JobRouter Product description Version 3.0 Index Philosophy... 03 Workflow with JobRouter Basics... 04 Defining the term workflow... 04. Displaying processes... 04 Forms of process management... 05 Sequential...
JobRouter Product description Version 3.0 Index Philosophy... 03 Workflow with JobRouter Basics... 04 Defining the term workflow... 04. Displaying processes... 04 Forms of process management... 05 Sequential...
COMMON ISSUES AFFECTING SECURITY USABILITY
 Evaluating the usability impacts of security interface adjustments in Word 2007 M. Helala 1, S.M.Furnell 1,2 and M.Papadaki 1 1 Centre for Information Security & Network Research, University of Plymouth,
Evaluating the usability impacts of security interface adjustments in Word 2007 M. Helala 1, S.M.Furnell 1,2 and M.Papadaki 1 1 Centre for Information Security & Network Research, University of Plymouth,
Setting up Omeka on IU s Webserve
 Setting up Omeka on IU s Webserve Request Webserve Account Consult the "Getting Started" document before you request a Webserve account. The following steps are required: 1. Request a Group Account 1.
Setting up Omeka on IU s Webserve Request Webserve Account Consult the "Getting Started" document before you request a Webserve account. The following steps are required: 1. Request a Group Account 1.
JINC THE ADMINISTRATION GUIDE
 JINC THE ADMINISTRATION GUIDE Author Lhacky Date 06 September 2010 Version 1.0 Software Version JINC 0.7 1 SUMMARY About this document...3 Intended audience...3 JINC Capabilities...4 JINC Installation...6
JINC THE ADMINISTRATION GUIDE Author Lhacky Date 06 September 2010 Version 1.0 Software Version JINC 0.7 1 SUMMARY About this document...3 Intended audience...3 JINC Capabilities...4 JINC Installation...6
Learning Management System - Privacy Policy
 We recognize that visitors to our Learning Management System (LMS) may be concerned about what happens to information they provide when they make use of the system. We also recognize that education and
We recognize that visitors to our Learning Management System (LMS) may be concerned about what happens to information they provide when they make use of the system. We also recognize that education and
Cyberlogic Knowledge Base
 Cyberlogic Knowledge Base KB2010-07: OPC SERVER TUTORIAL The OPC server is the hidden part of an OPC-based system. It sits behind the scenes, where it passes data between your PLCs and the operator interface
Cyberlogic Knowledge Base KB2010-07: OPC SERVER TUTORIAL The OPC server is the hidden part of an OPC-based system. It sits behind the scenes, where it passes data between your PLCs and the operator interface
Installing and Configuring Worldox/Web Mobile
 Installing and Configuring Worldox/Web Mobile SETUP GUIDE v 1.1 Revised 6/16/2009 REVISION HISTORY Version Date Author Description 1.0 10/20/2008 Michael Devito Revised and expanded original draft document.
Installing and Configuring Worldox/Web Mobile SETUP GUIDE v 1.1 Revised 6/16/2009 REVISION HISTORY Version Date Author Description 1.0 10/20/2008 Michael Devito Revised and expanded original draft document.
Note about compatibility: This module requires that PHP is enabled on the server. You should verify that your host offers PHP prior to installation.
 http://www.vikingcoders.com Soft Goods This module provides a means for selling downloadable products. The Concept... This module provides an interface for you to deliver downloadable products, such as
http://www.vikingcoders.com Soft Goods This module provides a means for selling downloadable products. The Concept... This module provides an interface for you to deliver downloadable products, such as
Let's have a look at the normal Joomla! URLs:
 Joomla! v 1.5 Search Engine Friendly URLs (SEF URLs) A. What are SEF URLs? SEF means search engine friendly. Websites are considered search engine friendly if the pages can easily be found by search engines.
Joomla! v 1.5 Search Engine Friendly URLs (SEF URLs) A. What are SEF URLs? SEF means search engine friendly. Websites are considered search engine friendly if the pages can easily be found by search engines.
Joomla 2.5 User Change Password Frontend
 Joomla 2.5 User Change Password Frontend Add User Frontend makes it possible to add users to Joomla from the frontend. It will even Autogenerate username and password - Add users to Attention: Description
Joomla 2.5 User Change Password Frontend Add User Frontend makes it possible to add users to Joomla from the frontend. It will even Autogenerate username and password - Add users to Attention: Description
BHIG - Mobile Devices Policy Version 1.0
 Version 1.0 Authorised by: CEO Endorsed By: Chief Operations Officer 1 Document Control Version Date Amended by Changes Made 0.1 20/01/2017 Lars Cortsen Initial document 0.2 29/03/2017 Simon Hahnel Incorporate
Version 1.0 Authorised by: CEO Endorsed By: Chief Operations Officer 1 Document Control Version Date Amended by Changes Made 0.1 20/01/2017 Lars Cortsen Initial document 0.2 29/03/2017 Simon Hahnel Incorporate
PHP for PL/SQL Developers. Lewis Cunningham JP Morgan Chase
 PHP for PL/SQL Developers Lewis Cunningham JP Morgan Chase 1 What is PHP? PHP is a HTML pre-processor PHP allows you to generate HTML dynamically PHP is a scripting language usable on the web, the server
PHP for PL/SQL Developers Lewis Cunningham JP Morgan Chase 1 What is PHP? PHP is a HTML pre-processor PHP allows you to generate HTML dynamically PHP is a scripting language usable on the web, the server
Polemic is a business involved in the collection of personal data in the course of its business activities and on behalf of its clients.
 Privacy policy 1 Background This document sets out the policy of Polemic Forensic ABN 60 392 752 759 ( Polemic ) relating to the protection of the privacy of personal information. Polemic is a business
Privacy policy 1 Background This document sets out the policy of Polemic Forensic ABN 60 392 752 759 ( Polemic ) relating to the protection of the privacy of personal information. Polemic is a business
Web development using PHP & MySQL with HTML5, CSS, JavaScript
 Web development using PHP & MySQL with HTML5, CSS, JavaScript Static Webpage Development Introduction to web Browser Website Webpage Content of webpage Static vs dynamic webpage Technologies to create
Web development using PHP & MySQL with HTML5, CSS, JavaScript Static Webpage Development Introduction to web Browser Website Webpage Content of webpage Static vs dynamic webpage Technologies to create
Architecture. Steven M. Bellovin October 31,
 Architecture Steven M. Bellovin October 31, 2016 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
Architecture Steven M. Bellovin October 31, 2016 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
INFORMATION TECHNOLOGY SECURITY POLICY
 INFORMATION TECHNOLOGY SECURITY POLICY Author Responsible Director Approved By Data Approved September 15 Date for Review November 17 Version 2.3 Replaces version 2.2 Mike Dench, IT Security Manager Robin
INFORMATION TECHNOLOGY SECURITY POLICY Author Responsible Director Approved By Data Approved September 15 Date for Review November 17 Version 2.3 Replaces version 2.2 Mike Dench, IT Security Manager Robin
Terms and Conditions for External accounts Service
 Terms and Conditions for External accounts Service You must read these Terms and Conditions before using External accounts service. IMPORTANT INFORMATION External accounts service is an account aggregation
Terms and Conditions for External accounts Service You must read these Terms and Conditions before using External accounts service. IMPORTANT INFORMATION External accounts service is an account aggregation
Webnodes Developers Quick Guide
 Webnodes Webnodes Developers Quick Guide Want to get started right away? Ole Gulbrandsen 1/1/2010 Webnodes Developers Quick Guide Want to get started right away? This guide is for C# developers and will
Webnodes Webnodes Developers Quick Guide Want to get started right away? Ole Gulbrandsen 1/1/2010 Webnodes Developers Quick Guide Want to get started right away? This guide is for C# developers and will
Working with Databases
 Working with Databases TM Control Panel User Guide Working with Databases 1 CP offers you to use databases for storing, querying and retrieving information. CP for Windows currently supports MS SQL, PostgreSQL
Working with Databases TM Control Panel User Guide Working with Databases 1 CP offers you to use databases for storing, querying and retrieving information. CP for Windows currently supports MS SQL, PostgreSQL
