Phishing Activity Trends Report. 4 th Quarter Unifying the. Global Response To Cybercrime. October December 2012
|
|
|
- Opal Houston
- 6 years ago
- Views:
Transcription
1 4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013
2 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies, its Global Research Partners, through the organization s website at and by e- mail submissions to reportphishing@antiphishing.org. APWG also measures the evolution, proliferation, and propagation of crimeware by drawing from the research of our member companies. Phishers Shift to Target Online Game Players Phishing Defined Phishing is a criminal mechanism employing both social engineering and technical subterfuge to steal consumers personal identity data and financial account credentials. Social engineering schemes use spoofed e- mails purporting to be from legitimate businesses and agencies, designed to lead consumers to counterfeit websites that trick recipients into divulging financial data such as usernames and passwords. Technical subterfuge schemes plant crimeware onto PCs to steal credentials directly, often using systems to intercept consumers online account user names and passwords - - and to corrupt local navigational infrastructures to misdirect consumers to counterfeit websites (or authentic websites through phisher- controlled proxies used to monitor and intercept consumers keystrokes). Table of Contents Statistical Highlights for 4th Quarter Phishing Reports and Phishing Site Trends 4 Brand-Domain Pairs Measurement 5 Brands & Legitimate Entities Hijacked by Phishing Attacks 6 Most Targeted Industry Sectors 7 Countries Hosting Phishing Sites 7 Top Malware Infected Countries 8 Measurement of Detected Crimeware 9 Hosting of Phishing-based Trojans and Downloaders by Country 10 Phishing by Top-Level Domain 10 APWG Phishing Trends Report Contributors 11 2 Phishing attacks against online game players saw a massive increase, from 2.7 percent of all phishing attacks in Q3 to 14.7 percent in Q4. Financial services continued to be the most- targeted industry sector in the fourth quarter of 2012 with payment services close behind. [p. 7] 4th Quarter '12 Phishing Activity Trends Summary During Q4, about 30 percent of personal computers worldwide were infected with malware. More than 57 percent of PCs in China may have been infected, while PCs in European nations were infected least- often. [p. 8] Except for October 2012, the number of phishing sites declined every month from April 2012 through December April 2012 saw 63,253 unique phishing sites detected, falling to 45,628 in December [p. 4] The APWG received reports of 28,195 unique phishing sites in December. December'ʹs total was 31 percent lower than the high of 40,621 reports in August [p. 4] Use of crimeware dipped slightly in this quarter from the previous, as did the use of data- stealing malware. The use of other malware has increased by a statistically significant amount from the previous quarter. [p. 9]
3 Methodology and Instrumented Data Sets The APWG continues to refine its tracking and reporting methodology and to incorporate new data sources into our reports. APWG has re- instated the tracking and reporting of unique phishing reports (e- mail campaigns) in addition to unique phishing sites. An e- mail campaign is a unique e- mail sent out to multiple users, directing them to a specific phishing web site (multiple campaigns may point to the same web site). APWG counts unique phishing report e- mails as those in a given month with the same subject line in the e- mail. The APWG also tracks the number of unique phishing websites. This is now determined by the unique base URLs of the phishing sites. APWG additionally tracks crimeware instances (unique software applications as determined by MD5 hash of the crimeware sample), as well as unique sites that are distributing crimeware (typically via browser drive- by exploits). The APWG also includes statistics on rogue anti- virus software, desktop infection rates, and related topics. Statistical Highlights for October November December Number of unique phishing e- mail reports (campaigns) received by APWG from consumers 23,365 24,563 28,195 Number of unique phishing websites detected 51,232 46,002 45,628 Number of brands targeted by phishing campaigns Country hosting the most phishing websites USA USA USA Contain some form of target name in URL 60.31% 54.23% 53.59% No hostname; just IP address 1.63% 1.87% 1.93% Percentage of sites not using port % 0.24% 1.04% 3
4 Phishing Reports and Phishing Site Trends 4th Quarter 2012 Except for October 2012, the number of phishing sites declined every month from April 2012 through December April 2012 saw 63,253 unique phishing sites detected, falling to 45,628 in December The drop from October to December was 11 percent, and the decline from the 2 nd quarter through the fourth quarter was 28 percent. The decline continues to be mainly in phishing against the retail and financial services sectors. The number of unique phishing reports submitted to APWG each month saw a gradual increase during the quarter. The quarter s high was 28,195 reports in December. December'ʹs high was 31 percent lower than the all- time high of 40,621 reports, recorded in August
5 Brand-Domain Pairs Measurement 4th Quarter 2012 The following chart combines statistics based on brands phished, unique domains, unique domain/brand pairs, and unique URLs. Brand/domain pairs count the unique instances of a domain being used to target a specific brand. Example: if several URLs are targeting a brand but are hosted on the same domain this brand/domain pair would be counted as one instead of several. The number of unique brand- domain pairs saw a massive drop during the fourth quarter of The high for the three- month period was 19,140 brand- domain pairs in October, dropping down nearly 5,000 to 14,637 in December. The total number of phishing attacks detected in Q dropped compared to the all- time high in Q2, but the total number of brands targeted by phishers increased in Q4 when compared to Q3 of 2012, said Ihab Shraim, chief information security officer and vice president, anti- fraud engineering and operations, MarkMonitor. These shifts are due to fraudsters using more advanced phishing techniques, such as geo- IP blocking, and malware. They are also taking advantage of the availability of non- traditional platforms such as social media and mobile to launch newer types of targeted phishing attacks. Forensic utility of this metric: If the number of unique URLs is greater than the number of brand/domain pairs, it indicates many URLs are being hosted on the same domain to target the same brand. Knowing how many URLs occur with each domain indicates the approximate number of attacking domains a brand- holding victim needs to locate and neutralize. Since phishing- prevention technologies (like browser and e- mail blocking) require the full URL, it is useful to understand the general number of unique URLs that occur per domain. October November December Number of Unique Phishing Web Sites Detected 51,232 46,002 45,628 Unique Domains 15,899 13,351 12,728 Unique Brand- Domain Pairs 19,140 15,579 14,637 Unique Brands URLs Per Brand
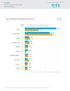
6 Brands and Legitimate Entities Targeted by Phishing Attacks 4th Quarter 2012 November 2012 saw 430 brands targeted by phishers. This was an all- time high, surpassing the 428 observed in April and July APWG members report that sophisticated targeted content continues to make a highly effective attack vector for phishing, malware, and spam. 6
7 Most-Targeted Industry Sectors 4th Quarter 2012 Financial services continued to be the most- targeted industry sector in the fourth quarter of 2012 with payment services close behind. Attacks against online gaming sites such as Battle.net saw a massive increase, from 2.7% in Q3 to 14.7% in Q4. Online gaming credentials are valuable to certain criminals, who sell them on the black market. In- game items held in those accounts can also be sold by phishers for real- world cash. Victims can even have their real- life identities stolen. Attacks against social media doubled to 6%, up from 3% in the third quarter. Countries Hosting Phishing Sites 4th Quarter 2012 Most phishing occurs on hacked or compromised Web servers. The United States continued to be the top country hosting phishing sites during the fourth quarter of This is mainly due to the fact that a large percentage of the world s Web sites and domain names are hosted in the United States. October November December USA 73.93% USA 73.87% USA 63.85% UK 4.52% China 5.65% China 6.22% Germany 2.20% Russia 2.33% UK 3.12% Canada 1.91% Thailand 1.76% Germany 2.84% China 1.70% Australia 1.59% Canada 2.68% Netherlands 1.21% Netherlands 1.39% Rep. of Korea 2.60% Australia 1.13% Germany 1.37% Russia 1.32% Ireland 0.97% Canada 1.33% Br. Virgin Isl. 1.17% France 0.94% UK 1.19% Netherlands 1.04% 7 Br. Virgin Isl. 0.92% Czech Rep. 1.19% Hungary 1.04%
8 Crimeware Taxonomy and Samples According to Classification The APWG s Crimeware statistics categorize crimeware attacks as follows; the taxonomy will grow as variations in attack code are spawned. Definition: Crimeware is code designed with the intent of collecting information on the end- user in order to steal the user s credentials. Unlike most generic keyloggers, phishing- based keyloggers have tracking components, which attempt to monitor specific actions (and specific organizations, such as financial institutions, retailers, and e- commerce merchants) in order to target specific information. The most common types of information are access to financial- based websites, ecommerce sites, and web- based mail sites. Malware Infected Countries 4th Quarter 2012 In the fourth quarter of 2012, 7 million new malware samples were detected by PandaLabs. The categorization was a follows: Type of Malware Identified % of malware samples Trojans 73.69% Virus 14.60% Worms 10.32% Rogueware 1.17% Other.21% Malware Infections by Type % of malware samples Trojans 77.06% Virus 8.95% Worms 6.21% Rogueware 4.67% Other 3.11% According to Luis Corrons, PandaLabs Technical Director and APWG Trends Report contributing analyst, the percentage of Trojans grew slightly, from percent in the 3rd quarter to percent in the 4th quarter of 2012, and Trojans continue to account for most of the new threats. Virus infections increased, from 6.56 percent in Q3 to 8.95 percent in Q Which countries were most infected? Which countries were best protected? The average number of infected PCs across the globe stood at percent percent, similar to Q3. China, as usual, is leading the way (57.62 percent of infected PCs), followed by Honduras (42.86 percent) and Turkey (41.60 percent). Depending upon the malware used, infected PCs can then be used to attack other computers or send spam to other computers around the world. As the table shows, there are high- infection countries in almost every part of the world: Asia, Europe, and South America. However, if we take a look at the least- infected countries, all of them are European with the only exception of South Africa. The country with the fewest infections is Finland (18.20 percent of infected PCs), followed by Switzerland (20.13 percent). Sweden takes the third spot (20.75 percent), maintaining its presence as one of the countries least affected by malware infections over the last few years. 8 Ranking Country Infection Rate 1 China 57.62% 2 Honduras 42.86% 3 Turkey 41.60% 4 Bolivia 41.46% 5 Poland 36.33% 6 Taiwan 36.20% 7 Peru 34.33% 8 Argentina 33.46% 9 Czech Republic 33.00% 10 El Salvador 32.63% Ranking Country Infection ratio 35 Denmark 23.31% 36 Austria 23.31% 37 United Kingdom 23.17% 38 South Africa 22.01% 39 Netherlands 21.91% 40 Germany 21.65% 41 Norway 21.61% 42 Sweden 20.75% 43 Switzerland 20.13% 44 Finland 18.20%
9 Measurement of Detected Crimeware 4th Quarter 2012 Using data contributed from APWG founding member Websense regarding the proliferation of malevolent software, this metric measures proportions of three genera of malevolent code: Crimeware (data- stealing malicious code designed specifically to be used to victimize financial institutions customers and to co- opt those institutions identities); Data Stealing and Generic Trojans (code designed to send information from the infected machine, control it, and open backdoors on it); and Other (the remainder of malicious code commonly encountered in the field such as auto- replicating worms, dialers for telephone charge- back scams, etc.) Carl Leonard of Websense Security Labs said: "ʺContinuing with the data collected for the last quarter of 2012, use of crimeware dipped slightly in the fourth quarter from the previous, as has data- stealing malware. The use of other malware has increased by a statistically significant amount from the previous quarter. 9
10 Hosting of Phishing-based Trojans and Downloaders by Country (by IP address) During the three- month period, USA and China still ranked as the top two countries for hosting phishing sites respectively, with the Netherlands making a second place appearance in November. The following chart represents a breakdown of the websites that were classified as hosting malicious code in the form of either a phishing- based keylogger or a Trojan downloader that downloads a keylogger. October November December USA 65.79% USA 67.96% USA 50.32% China 10.43% Netherlands 5.92% China 15.75% Netherlands 5.34% China 5.29% UK 5.45% France 2.67% Lithuania 3.92% Netherlands 4.65% Germany 2.13% Germany 2.39% France 3.97% Rep. of Korea 2.12% Rep. of Korea 2.13% Germany 2.46% Russia 1.80% Russia 1.80% Canada 1.58% Brazil 0.97% France 1.38% Russia 1.58% UK 0.77% UK 0.99% Rep of Korea 1.54% Br. Virgin Isl. 0.64% Brazil 0.91% Brazil 1.30% Phishing by Top-Level Domain APWG member Internet Identity records the top- level domains (TLDs) used to host phishing. Forty- six percent of phishing attacks were on.com names, and.com represents approximately 42 percent of domain names registered worldwide. The TLD of Brazil (.BR) had 4 percent of phishing worldwide, but only 1 percent of the total global domain name market. 10
11 APWG Contributors Illumintel Inc. provides advising and security services to top- level- domain registry operators and other Internet companies. Internet Identity (IID) is a US- based provider of technology and services that help organizations secure their Internet presence. MarkMonitor, the global leader in enterprise brand protection, offers comprehensive solutions and services that safeguard brands, reputation and revenue from online risks. Panda Security s mission is to keep our customers'ʹ information and IT assets safe from security threats, providing the most effective protection with minimum resource consumption. Websense, Inc. is a global leader in secure Web gateway, data loss prevention, and e- mail security solutions, protecting more than 43 million employees at organizations worldwide. The APWG is published by the APWG. For further information about the APWG, please contact APWG Deputy Secretary General Foy Shiver at or foy@apwg.org. For media inquiries related to the content of this report, please contact APWG Secretary General Peter Cassidy at ; Te Smith of MarkMonitor at or Te.Smith@markmonitor.com; Luis Corrons of Panda at lcorrons@pandasoftware.es; or Websense at publicrelations@websense.com. About the APWG Founded in 2003, the Anti- Phishing Working Group (APWG) is a not- for- profit industry association focused on eliminating the identity theft and frauds that result from the growing problem of phishing, crimeware, and e- mail spoofing. Membership is open to qualified financial institutions, retailers, ISPs, solutions providers, the law enforcement community, government agencies, multi- lateral treaty organizations, and NGOs. There are more than 2,000 enterprises worldwide participating in the APWG. Because electronic crime is a sensitive subject, APWG maintains a policy of confidentiality of member organizations. Websites of APWG public- service enterprises include its public website, < the Website of public awareness program, STOP. THINK. CONNECT. Messaging Convention < and the APWG s research website < These serve as resources about the problem of phishing and electronic frauds perpetrated against personal computers and their users and resources for countering these threats. The APWG, a 501c6 tax- exempted corporation, was founded by Tumbleweed Communications, financial services institutions and e- commerce providers. APWG s first meeting was in November 2003 in San Francisco and in June 2004 was incorporated as an independent corporation controlled by its board of directors, its executives and its steering committee. 11 Analysis by Greg Aaron, Illumintel; Trends Report editing by Ronnie Manning, Mynt Public Relations.
Phishing Activity Trends Report. 3 rd Quarter Unifying the. Global Response To Cybercrime. July September 2012
 3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report. 3 rd Quarter Committed to Wiping Out Internet Scams and Fraud
 3 rd Quarter 2009 Committed to Wiping Out Internet Scams and Fraud July September 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its
3 rd Quarter 2009 Committed to Wiping Out Internet Scams and Fraud July September 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its
Phishing Activity Trends Report. 4 th Quarter Committed to Wiping Out Internet Scams and Fraud
 4 th Quarter 2009 Committed to Wiping Out Internet Scams and Fraud October December 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies,
4 th Quarter 2009 Committed to Wiping Out Internet Scams and Fraud October December 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies,
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
4 th Quarter Phishing Activity Trends Report. Unifying the Global Response To Cybercrime. Activity October December 2017.
 4 th Quarter 2017 Unifying the Global Response To Cybercrime Table of Contents Statistical Highlights for 2nd Quarter 2017 3 Phishing E-mail Reports and Phishing Site Trends 4 Brand-Domain Pairs Measurement
4 th Quarter 2017 Unifying the Global Response To Cybercrime Table of Contents Statistical Highlights for 2nd Quarter 2017 3 Phishing E-mail Reports and Phishing Site Trends 4 Brand-Domain Pairs Measurement
Phishing Activity Trends Report March, 2005
 Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report November, 2004
 Phishing Activity Trends Report November, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report November, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Anti-Phishing Working Group
 Phishing Attack Trends Report April, 2004 Phishing attacks use spoofed e-mails and fraudulent websites designed to fool recipients into divulging personal financial data such as credit card numbers, account
Phishing Attack Trends Report April, 2004 Phishing attacks use spoofed e-mails and fraudulent websites designed to fool recipients into divulging personal financial data such as credit card numbers, account
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
October 2009 Report #24
 October 2009 Report #24 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
October 2009 Report #24 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
CE Advanced Network Security Phishing I
 CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
August 2009 Report #22
 August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Korea Phishing Activity Trends Report
 Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY
 RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
Anti-Phishing Working Group
 Anti-Phishing Working Group www.antiphishing.org DNS Policy Sub-Committee Overview Rod Rasmussen Rod.Rasmussen@InternetIdentity.com Anti-Phishing Working Group Launched in 2003 2600+ members 1600+ companies
Anti-Phishing Working Group www.antiphishing.org DNS Policy Sub-Committee Overview Rod Rasmussen Rod.Rasmussen@InternetIdentity.com Anti-Phishing Working Group Launched in 2003 2600+ members 1600+ companies
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
December 2009 Report #26
 December 2009 Report #26 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This
December 2009 Report #26 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This
Second International Barometer of Security in SMBs
 1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
The Cost of Phishing. Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015
 The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
Mapping the Frontiers of the Electronic Crime Threat From Consumers' Desktops to National Equities Markets
 Mapping the Frontiers of the Electronic Crime Threat From Consumers' Desktops to National Equities Markets Peter Cassidy Secretary General www.antiphishing.org pcassidy@antiphishing.org Director of Research
Mapping the Frontiers of the Electronic Crime Threat From Consumers' Desktops to National Equities Markets Peter Cassidy Secretary General www.antiphishing.org pcassidy@antiphishing.org Director of Research
Updates on Sharing Threat Data, Security Awareness and Policy Efforts to Fight Cybercrime
 Updates on Sharing Threat Data, Security Awareness and Policy Efforts to Fight Cybercrime Foy Shiver Deputy Secretary General Agenda Who We Are Current Events Tracking Trends and Malicious Activities Education
Updates on Sharing Threat Data, Security Awareness and Policy Efforts to Fight Cybercrime Foy Shiver Deputy Secretary General Agenda Who We Are Current Events Tracking Trends and Malicious Activities Education
Step 1: New Portal User User ID Created Using IdentityIQ (IIQ)
 Rockwell Automation PartnerNetwork Portal Single Sign-on (SSO) Login to Rockwell Automation PartnerNewtork Portal for Commercial Programs Participants Scope: This job aid provides instructions on how to
Rockwell Automation PartnerNetwork Portal Single Sign-on (SSO) Login to Rockwell Automation PartnerNewtork Portal for Commercial Programs Participants Scope: This job aid provides instructions on how to
Top 10 Global Threat Rank by Source
 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
The Cost of Denial-of-Services Attacks
 The Cost of Denial-of-Services Attacks Sponsored by Akamai Technologies Independently conducted by Ponemon Institute LLC Publication Date: March 2015 Ponemon Institute Research Report The Cost of Denial-of-Service
The Cost of Denial-of-Services Attacks Sponsored by Akamai Technologies Independently conducted by Ponemon Institute LLC Publication Date: March 2015 Ponemon Institute Research Report The Cost of Denial-of-Service
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
New Zealand National Cyber Security Centre Incident Summary
 New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
How technology changed fraud investigations. Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011
 How technology changed fraud investigations Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011 The Changing Cyberfraud Landscape Underground Economy Malware Authors Organized
How technology changed fraud investigations Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011 The Changing Cyberfraud Landscape Underground Economy Malware Authors Organized
Convergence Myth to Reality Jericho Forum
 Convergence Myth to Reality Jericho Forum David Ting Founder and CTO Imprivata, Inc. dting@imprivata.com What s Happening Out There? Data Protection Regs/Mandates Y2K without an end date! Scandinavia Canada
Convergence Myth to Reality Jericho Forum David Ting Founder and CTO Imprivata, Inc. dting@imprivata.com What s Happening Out There? Data Protection Regs/Mandates Y2K without an end date! Scandinavia Canada
Digital Opportunity Index. Michael Minges Telecommunications Management Group, Inc.
 Digital Opportunity Index Michael Minges Telecommunications Management Group, Inc. Digital Opportunity Index (DOI) Why How Preliminary results Conclusions WSIS Plan of Action E. Follow-up and evaluation
Digital Opportunity Index Michael Minges Telecommunications Management Group, Inc. Digital Opportunity Index (DOI) Why How Preliminary results Conclusions WSIS Plan of Action E. Follow-up and evaluation
2014 INTERNET COMMERCE CASE STUDY. The Battle Against Phishing and Fraudulent s. 100 S. Ellsworth Ave 4th Floor San Mateo, CA
 2014 INTERNET COMMERCE CASE STUDY The Battle Against Phishing and Fraudulent Emails 100 S. Ellsworth Ave 4th Floor San Mateo, CA 94401 650.627.7667 ABOUT AGARI Agari analizes big data from the world s
2014 INTERNET COMMERCE CASE STUDY The Battle Against Phishing and Fraudulent Emails 100 S. Ellsworth Ave 4th Floor San Mateo, CA 94401 650.627.7667 ABOUT AGARI Agari analizes big data from the world s
Cisco Aironet In-Building Wireless Solutions International Power Compliance Chart
 Cisco Aironet In-Building Wireless Solutions International Power Compliance Chart ADDITIONAL INFORMATION It is important to Cisco Systems that its resellers comply with and recognize all applicable regulations
Cisco Aironet In-Building Wireless Solutions International Power Compliance Chart ADDITIONAL INFORMATION It is important to Cisco Systems that its resellers comply with and recognize all applicable regulations
Account Takeover: Why Payment Fraud Protection is Not Enough
 Cybercrime Protection Account Takeover: Why Payment Fraud Protection is Not Enough Mustafa Rassiwala, ThreatMetrix, Inc. April 2014 1 Agenda 1. Customer Accounts Blessing or Curse? 2. Passwords Weakest
Cybercrime Protection Account Takeover: Why Payment Fraud Protection is Not Enough Mustafa Rassiwala, ThreatMetrix, Inc. April 2014 1 Agenda 1. Customer Accounts Blessing or Curse? 2. Passwords Weakest
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
GLOBAL MOBILE PAYMENT METHODS: FIRST HALF 2016
 PUBLICATION DATE: OCTOBER 2016 PAGE 2 GENERAL INFORMATION I PAGE 3 KEY FINDINGS I PAGE 4-8 TABLE OF CONTENTS I PAGE 9 REPORT-SPECIFIC SAMPLE CHARTS I PAGE 10 METHODOLOGY I PAGE 11 RELATED REPORTS I PAGE
PUBLICATION DATE: OCTOBER 2016 PAGE 2 GENERAL INFORMATION I PAGE 3 KEY FINDINGS I PAGE 4-8 TABLE OF CONTENTS I PAGE 9 REPORT-SPECIFIC SAMPLE CHARTS I PAGE 10 METHODOLOGY I PAGE 11 RELATED REPORTS I PAGE
Bank of america report phishing
 Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Innovative Fastening Technologies
 Innovative Fastening Technologies Corporate Overview 2011 Update Infastech is one of the world s largest producers of engineered mechanical fasteners with revenues exceeding USD500 million and an industry
Innovative Fastening Technologies Corporate Overview 2011 Update Infastech is one of the world s largest producers of engineered mechanical fasteners with revenues exceeding USD500 million and an industry
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Microsoft Dynamics 365 for Finance and Operations. Table of contents
 Microsoft Dynamics 365 for Finance and Operations Product localization and translation availability guide April 2018 update 1 Dynamics 365 for Finance and Operations Product localization and translation
Microsoft Dynamics 365 for Finance and Operations Product localization and translation availability guide April 2018 update 1 Dynamics 365 for Finance and Operations Product localization and translation
Digital EAGLEs. Outlook and perspectives
 2016 Digital EAGLEs Outlook and perspectives Fixed and Mobile broadband adoption rates in the next decade Changes in Fixed-Broadband penetration 2014-25 Changes in Mobile-Broadband penetration 2014-25
2016 Digital EAGLEs Outlook and perspectives Fixed and Mobile broadband adoption rates in the next decade Changes in Fixed-Broadband penetration 2014-25 Changes in Mobile-Broadband penetration 2014-25
Global Mobile Phone Insurance and Extended Warranties: A Worldwide Review
 Global Mobile Phone Insurance and Extended Warranties: A Worldwide Review Report Prospectus June 2016 Finaccord, 2016 Web: www.finaccord.com. E-mail: info@finaccord.com 1 Prospectus contents Page What
Global Mobile Phone Insurance and Extended Warranties: A Worldwide Review Report Prospectus June 2016 Finaccord, 2016 Web: www.finaccord.com. E-mail: info@finaccord.com 1 Prospectus contents Page What
Spam Evolution Report: October 2009
 Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
NEVIS Smart Solutions against sophisticated attackers
 NEVIS Smart Solutions against sophisticated attackers Stephan Schweizer NEVIS Product Manager March 2016 1 AdNovum at a Glance Enterprise-scale software and security solutions Founded in 1988, privately
NEVIS Smart Solutions against sophisticated attackers Stephan Schweizer NEVIS Product Manager March 2016 1 AdNovum at a Glance Enterprise-scale software and security solutions Founded in 1988, privately
Carrier Services. Intelligent telephony. for over COUNTRIES DID NUMBERS. All IP
 Carrier Services All IP Intelligent telephony In current times, being connected to the telephone network just isn t enough anymore; one needs to be INTERconnected with it, as it all has become IP. Along
Carrier Services All IP Intelligent telephony In current times, being connected to the telephone network just isn t enough anymore; one needs to be INTERconnected with it, as it all has become IP. Along
Microsoft Dynamics 365 for Finance and Operations, Enterprise edition. Table of contents
 Microsoft Dynamics 365 for Finance and Operations, Enterprise edition Product availability, localization, and translation guide July 2017 Update 1 Dynamics 365 for Finance and Operations, Enterprise edition
Microsoft Dynamics 365 for Finance and Operations, Enterprise edition Product availability, localization, and translation guide July 2017 Update 1 Dynamics 365 for Finance and Operations, Enterprise edition
Prolexic Attack Report Q4 2011
 Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Service withdrawal: Selected IBM ServicePac offerings
 Announcement ZS09-0086, dated April 21, 2009 Service withdrawal: Selected IBM offerings Table of contents 1 Overview 9 Announcement countries 8 Withdrawal date Overview Effective April 21, 2009, IBM will
Announcement ZS09-0086, dated April 21, 2009 Service withdrawal: Selected IBM offerings Table of contents 1 Overview 9 Announcement countries 8 Withdrawal date Overview Effective April 21, 2009, IBM will
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
MARKET NEWSLETTER No 69 February 2013
 Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
Perimeter Defenses T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN
 T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
VOICE/DATA SIMCARD USA UNLIMITED
 VOICE/DATA SIMCARD USA UNLIMITED Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
VOICE/DATA SIMCARD USA UNLIMITED Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
Global entertainment and media outlook Explore the content and tools
 www.pwc.com/outlook Global entertainment and media outlook Explore the content and tools A comprehensive online source of global analysis for consumer/ end-user and advertising spending 5-year forecasts
www.pwc.com/outlook Global entertainment and media outlook Explore the content and tools A comprehensive online source of global analysis for consumer/ end-user and advertising spending 5-year forecasts
The Business of Cybercrime
 Luis Corrons PandaLabs Technical Director 1 Agenda 1. Malware figures 2. Who is behind this? 3. Web Attack Toolkits 4. A Real Case 5. Underground Shopping Cart 6. Where to buy? 2 Malware figures 3 Malware
Luis Corrons PandaLabs Technical Director 1 Agenda 1. Malware figures 2. Who is behind this? 3. Web Attack Toolkits 4. A Real Case 5. Underground Shopping Cart 6. Where to buy? 2 Malware figures 3 Malware
THE POWER OF A STRONG PARTNERSHIP.
 THE POWER OF A STRONG PARTNERSHIP. Now you can harness a network of resources. Connections, knowledge, and expertise. All focused on your success. The Cisco Channel Partner Program. BE CONNECTED. Great
THE POWER OF A STRONG PARTNERSHIP. Now you can harness a network of resources. Connections, knowledge, and expertise. All focused on your success. The Cisco Channel Partner Program. BE CONNECTED. Great
The State of Spam A Monthly Report June Generated by Symantec Messaging and Web Security
 The State of Spam A Monthly Report June 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape Spam activity in May 2007 was overall consistent with trends observed in previous months.
The State of Spam A Monthly Report June 2007 Generated by Symantec Messaging and Web Security Monthly Spam Landscape Spam activity in May 2007 was overall consistent with trends observed in previous months.
OnAudience.com I Report 2017 Ad blocking in the Internet
 OnAudience.com I Report 2017 Ad blocking in the Internet Table of contents Introduction 1 Ad blocked page views 2 Impact on display advertising 8 Impact on e-commerce 11 About 13 Introduction 1 This report
OnAudience.com I Report 2017 Ad blocking in the Internet Table of contents Introduction 1 Ad blocked page views 2 Impact on display advertising 8 Impact on e-commerce 11 About 13 Introduction 1 This report
Interim report January September 2011
 Interim report January September 2011 Ray Mauritsson, CEO & President Fredrik Sjöstrand, CFO This is Axis > Founded in 1984 > IT company driving the network video market > Focused on Network Video Solutions
Interim report January September 2011 Ray Mauritsson, CEO & President Fredrik Sjöstrand, CFO This is Axis > Founded in 1984 > IT company driving the network video market > Focused on Network Video Solutions
WHAT IS CORPORATE ACCOUNT TAKEOVER? HOW DOES IT HAPPEN?
 WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
BRING SPEAR PHISHING PROTECTION TO THE MASSES
 E-Guide BRING SPEAR PHISHING PROTECTION TO THE MASSES SearchSecurity phishing. I n this expert tip, David Sherry describes how a combination of technical controls and user awareness training can help put
E-Guide BRING SPEAR PHISHING PROTECTION TO THE MASSES SearchSecurity phishing. I n this expert tip, David Sherry describes how a combination of technical controls and user awareness training can help put
Stealing digital information
 Stealing digital information Financial and personal perspective SUMMER SCHOOL 2014 Stealing information on the Internet is on the rise It might have negative effects on many aspects of our everyday life
Stealing digital information Financial and personal perspective SUMMER SCHOOL 2014 Stealing information on the Internet is on the rise It might have negative effects on many aspects of our everyday life
U85026A Detector 40 to 60 GHz
 Operating and Service Manual U85026A Detector 40 to 60 GHz Serial Numbers This manual applies directly to U85026A detectors with serial numbers 100 and above. For additional information on serial numbers,
Operating and Service Manual U85026A Detector 40 to 60 GHz Serial Numbers This manual applies directly to U85026A detectors with serial numbers 100 and above. For additional information on serial numbers,
Strategic IT Plan Improves NYCHA Resident Services While Reducing Costs US$150 Million
 C U S T O M E R C A S E S T U D Y Strategic IT Plan Improves NYCHA Resident Services While Reducing Costs US$150 Million Executive Summary CUSTOMER NAME New York City Housing Authority (NYCHA) INDUSTRY
C U S T O M E R C A S E S T U D Y Strategic IT Plan Improves NYCHA Resident Services While Reducing Costs US$150 Million Executive Summary CUSTOMER NAME New York City Housing Authority (NYCHA) INDUSTRY
Assessing Broadband in America. By Phil Heidenreich
 Assessing Broadband in America By Phil Heidenreich In the American Recovery and Reinvestment Act passed by Congress and signed into law by President Obama earlier this year, a provision was made for a
Assessing Broadband in America By Phil Heidenreich In the American Recovery and Reinvestment Act passed by Congress and signed into law by President Obama earlier this year, a provision was made for a
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
CISCO IP PHONE 7970G NEW! CISCO IP PHONE 7905G AND 7912G XML
 Q & A CISCO IP PHONE 7970G NEW! CISCO IP PHONE 7905G AND 7912G XML GENERAL QUESTIONS Q. What is the Cisco IP Phone 7970G? A. The 7970G is our latest state-of-the-art IP phone, which includes a large color,
Q & A CISCO IP PHONE 7970G NEW! CISCO IP PHONE 7905G AND 7912G XML GENERAL QUESTIONS Q. What is the Cisco IP Phone 7970G? A. The 7970G is our latest state-of-the-art IP phone, which includes a large color,
Overcoming the Compliance Challenges of VAT Remittance. 12 April :55 to 16:30 (CEST)
 Overcoming the Compliance Challenges of VAT Remittance 12 April 2016 15:55 to 16:30 (CEST) Presenters Nicole Jupin Vertex Inc. Senior Solutions Manager David Rossing Vertex Inc. Senior Tax Solutions Engineer,
Overcoming the Compliance Challenges of VAT Remittance 12 April 2016 15:55 to 16:30 (CEST) Presenters Nicole Jupin Vertex Inc. Senior Solutions Manager David Rossing Vertex Inc. Senior Tax Solutions Engineer,
MANUAL VOICE/DATA SIMCARD CANADA
 MANUAL VOICE/DATA SIMCARD CANADA Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
MANUAL VOICE/DATA SIMCARD CANADA Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
Traffic Offload. Cisco 7200/Cisco 7500 APPLICATION NOTE
 APPLICATION NOTE Cisco 700/Cisco 700 Traffic offload allows exchange carriers to offload their telephony traffic to a packet network from the Public Switched Telephone Network (PSTN). By doing so, carriers
APPLICATION NOTE Cisco 700/Cisco 700 Traffic offload allows exchange carriers to offload their telephony traffic to a packet network from the Public Switched Telephone Network (PSTN). By doing so, carriers
Purchasing. Operations 3% Marketing 3% HR. Production 1%
 Agenda Item DOC ID IAF CMC (11) 75 For Information For discussion For decision For comments to the author IAF End User Survey results (October 211) This report summarises the total responses to the IAF
Agenda Item DOC ID IAF CMC (11) 75 For Information For discussion For decision For comments to the author IAF End User Survey results (October 211) This report summarises the total responses to the IAF
Whitepaper on AuthShield Two Factor Authentication with SAP
 Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS
 KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
Samu Konttinen, CEO, F-Secure WE ARE F-SECURE. 1 F-Secure
 Samu Konttinen, CEO, F-Secure WE ARE F-SECURE 1 F-SECURE A FRONT RUNNER IN CYBER SECURITY We are the largest European single source of cyber security services and detection and response solutions for companies,
Samu Konttinen, CEO, F-Secure WE ARE F-SECURE 1 F-SECURE A FRONT RUNNER IN CYBER SECURITY We are the largest European single source of cyber security services and detection and response solutions for companies,
The Rise of Phishing. Dave Brunswick Tumbleweed Communications Anti-Phishing Working Group
 The Rise of Phishing Dave Brunswick Tumbleweed Communications Anti-Phishing Working Group 2 The Anti-Phishing Working Group Industry association focused on eliminating identity theft and fraud from the
The Rise of Phishing Dave Brunswick Tumbleweed Communications Anti-Phishing Working Group 2 The Anti-Phishing Working Group Industry association focused on eliminating identity theft and fraud from the
Trend Micro Reports Record First Quarter Revenue & Operating Profit
 Trend Micro Reports Record First Quarter Revenue & Operating Profit Continued strong growth in U.S and Asia highlight quarter Tokyo, Japan April 25, 2006 Trend Micro, Incorporated (TSE: 4704, NASDAQ: TMIC),
Trend Micro Reports Record First Quarter Revenue & Operating Profit Continued strong growth in U.S and Asia highlight quarter Tokyo, Japan April 25, 2006 Trend Micro, Incorporated (TSE: 4704, NASDAQ: TMIC),
McAfee Labs Threat Report
 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
Vodafone Usage Manager R2.0
 Vodafone Global Enterprise Vodafone Usage Manager R2.0 User Guide for Android Power to you Copyright Vodafone Global Enterprise, Vodafone Group Plc, Vodafone House, The Connection 19 April 2017Newbury,
Vodafone Global Enterprise Vodafone Usage Manager R2.0 User Guide for Android Power to you Copyright Vodafone Global Enterprise, Vodafone Group Plc, Vodafone House, The Connection 19 April 2017Newbury,
Programming Note. Agilent Technologies Quick Reference Guide For the 8757D/E Scalar Network Analyzer
 Programming Note Agilent Technologies Quick Reference Guide For the 8757D/E Scalar Network Analyzer Manufacturing Part Number: 08757-90130 Printed in USA Print Date: July 1992 Agilent Technologies, Inc.
Programming Note Agilent Technologies Quick Reference Guide For the 8757D/E Scalar Network Analyzer Manufacturing Part Number: 08757-90130 Printed in USA Print Date: July 1992 Agilent Technologies, Inc.
Automating Security Response based on Internet Reputation
 Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Telecommunication Regulatory Reform and the WTO Process
 Telecommunication Regulatory Reform and the WTO Process Dr Tim Kelly, ITU Session 1: Course on Telecom Policy, Regulation and Management, University of Witwatersrand, 6-7 May, 1999 * The views expressed
Telecommunication Regulatory Reform and the WTO Process Dr Tim Kelly, ITU Session 1: Course on Telecom Policy, Regulation and Management, University of Witwatersrand, 6-7 May, 1999 * The views expressed
The Business of Malware IT Security Presentation
 The Business of Malware IT Security Presentation Secure South West Plymouth University Thursday 20 th September 2012 Presented by: Alan Thake Head of Sales ESET UK Today s Topics The Business of malware
The Business of Malware IT Security Presentation Secure South West Plymouth University Thursday 20 th September 2012 Presented by: Alan Thake Head of Sales ESET UK Today s Topics The Business of malware
MRG Effitas Online Banking Browser Security Assessment Project Q Q1 2014
 MRG Effitas Online Banking Browser Security Assessment Project Q3 2013 - Q1 2014 1 Contents Introduction... 3 The Purpose of this Report... 3 Tests Employed... 3 Security Applications Tested... 4 Methodology
MRG Effitas Online Banking Browser Security Assessment Project Q3 2013 - Q1 2014 1 Contents Introduction... 3 The Purpose of this Report... 3 Tests Employed... 3 Security Applications Tested... 4 Methodology
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
Third Annual Green IT & Sustainability Survey: U.S. Results and Services Implications
 Third Annual Green IT & Sustainability Survey: U.S. Results and Services Implications Gard Little Research Manager Worldwide Services, Global Services Markets & Trends 2009 IDC 1 Agenda Overview of the
Third Annual Green IT & Sustainability Survey: U.S. Results and Services Implications Gard Little Research Manager Worldwide Services, Global Services Markets & Trends 2009 IDC 1 Agenda Overview of the
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
The Challenge of Spam An Internet Society Public Policy Briefing
 The Challenge of Spam An Internet Society Public Policy Briefing 30 October 2015 Introduction Spam email, those unsolicited email messages we find cluttering our inboxes, are a challenge for Internet users,
The Challenge of Spam An Internet Society Public Policy Briefing 30 October 2015 Introduction Spam email, those unsolicited email messages we find cluttering our inboxes, are a challenge for Internet users,
OWASP Global AppSec Conference Sponsorship
 OWASP Global AppSec Conference Sponsorship Open Web Application Security Project (OWASP) is a global open source application security project composed of corporations, educational organizations, and individuals
OWASP Global AppSec Conference Sponsorship Open Web Application Security Project (OWASP) is a global open source application security project composed of corporations, educational organizations, and individuals
The Scenes of Cyber Crime
 Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
REPORT. proofpoint.com
 REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
REPORT proofpoint.com Email fraud, also known as business email compromise (BEC), is one of today s greatest cyber threats. These socially engineered attacks seek to exploit people rather than technology.
Wick Hill Group, River Court, Albert Drive, Woking, Surrey, GU21 5RP
 2009, 2014 & 2015- Winner Finalist 2010, 2011, 2013 & 2016 2007, 2008, 2009, 2010 & 2015 WINNER 2007, 2008, 2009, 2010 2011, 2013, 2014, 2015 & 2016 2010, 2011, 2012, 2013, 2014 & 2015 Wick Hill Group,
2009, 2014 & 2015- Winner Finalist 2010, 2011, 2013 & 2016 2007, 2008, 2009, 2010 & 2015 WINNER 2007, 2008, 2009, 2010 2011, 2013, 2014, 2015 & 2016 2010, 2011, 2012, 2013, 2014 & 2015 Wick Hill Group,
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Global Economic Indicators: Global Leading Indicators
 Global Economic Indicators: Global Leading Indicators January 30, 2018 Dr. Edward Yardeni 516-2-7683 eyardeni@ Debbie Johnson 480-664-1333 djohnson@ Mali Quintana 480-664-1333 aquintana@ Please visit our
Global Economic Indicators: Global Leading Indicators January 30, 2018 Dr. Edward Yardeni 516-2-7683 eyardeni@ Debbie Johnson 480-664-1333 djohnson@ Mali Quintana 480-664-1333 aquintana@ Please visit our
