Global Information Security Survey. A life sciences perspective
|
|
|
- Lindsay Baker
- 5 years ago
- Views:
Transcription
1 Global Information Security Survey A life sciences perspective
2 Introduction Welcome to the life sciences perspective on the results from Creating trust in the digital world: EY s Global Information Security Survey 2015, an investigation of the most important cybersecurity issues facing businesses today. A mixed picture for life sciences cybersecurity Following the completion of our latest survey, we decided to take a closer look at the data for the life sciences sector a sector that is undergoing big disruptive and transformational changes as a result of advances in digital technology. What we found is a mixture of good news and bad. On the positive side, life sciences companies clearly have many of the right ideas about developing their cybersecurity. And they are making genuine progress in how they respond to today s cyber threats and attacks. In particular, their security operations centers (SOCs), which monitor and respond to threats, have a high level of maturity in information technology (IT) terms. But this focus on IT is actually the flaw in many life sciences organizations cybersecurity. With SOCs still firmly located within IT, cybersecurity will most likely be too concerned with technology and have too little understanding of, and alignment with, the needs of the business as a whole. Only by getting closer to the business will life sciences cybersecurity be in a position to enable the big digital changes going on within the sector, such as the move to payment by outcomes. To help life sciences companies understand how we believe they need to refashion their cybersecurity function, we have created two options. One details the ideal approach, which allows cybersecurity to break free of IT. The other provides a way for the information security function to get a little closer to the business, without the need for a more fundamental reorganization. About this study This study features inputs from 36 life sciences companies from across the globe. It draws insights from the main Global Information Security Survey (GISS) report, which featured responses from 1,755 organizations across 25 industry sectors. We believe that this study is a useful tool for those seeking to understand the state of cybersecurity in the sector. And we hope that it will serve as a starting point for discussions within life sciences organizations, helping them to better understand the nature and scope of the changes they should be making. For further details about how to build the active cybersecurity your business needs, please refer to the full text of Creating trust in the digital world. Or, of course, you could get in touch with us here at EY. Trapped in IT: the failings in life sciences cybersecurity Most life sciences cybersecurity functions remain firmly embedded in IT, which is understandable given that this is where cybersecurity has its origins. But over the last decade, the rapid rise of digital connections between businesses, customers, suppliers and other stakeholders has meant that cybersecurity must now be understood as a priority for the whole organization. Being isolated within IT leaves cybersecurity facing a number of serious shortcomings. A lack of understanding Cybersecurity functions located within IT will most likely be too focused on the needs of IT rather than on those of the business as a whole. They will lack sufficient alignment with the organization s business strategy and risk strategy. And as a result, resources will not be focused on protecting what is most valuable to the business or on enabling the business to succeed with its most important initiatives. Being located within IT also makes it more difficult for the cybersecurity function to truly understand the needs of the business. This reduces the ability of the function to prepare for new developments within the business and to accurately assess, and then address, the organization s vulnerabilities. In our survey, most of the life sciences respondents say that their cybersecurity strategy aligns with the organization s IT strategy than with their organization s business strategy. This is a serious shortcoming, and cybersecurity s alignment with the business is an area in which life sciences lags behind other sectors. None of the life sciences respondents to our survey believe that their cybersecurity fully meets their organization s needs. Seventy-five percent of life sciences respondents say that their cybersecurity strategy aligns with the organization s IT strategy. Only 39% say that their cybersecurity strategy is aligned with the organization s business strategy. 2 3
3 The SOC should be the first to know about any incidents, but 65% of life sciences organizations report that they had a significant cyber incident that was not first picked up by their security operations center. The Internet of Things (IoT) which is crucial to payment by outcomes will create a huge increase in the number of access points to a life sciences company s systems. But 72% of the life sciences organizations we surveyed do not yet recognize that this presents a serious cybersecurity challenge. A lack of influence In organizations where cybersecurity expertise is kept within IT, there will be few representatives able to go out to support the business in its new digital initiatives. This will limit the influence of the cybersecurity function on how those initiatives are executed and will, as a result, increase the level of unnecessary risk new initiatives create. Ultimately, the aim should be for cybersecurity to act as a digital enabler it should be a function that helps the organization to experiment and innovate safely and securely. But for this to happen, the cybersecurity function needs to be close to the business and be visible in helping the business. Otherwise, other functions will simply bypass cybersecurity when pursuing their digital agendas, leaving their initiatives far more vulnerable to possible attack. A lack of awareness Apart from presenting only risks to new or unknown activities, cybersecurity s isolation in IT damages its current effectiveness. Located within IT, cybersecurity will tend to place too much emphasis on technology and will miss the other dimensions of today s sophisticated cyber attacks: people and processes. If a sophisticated multichannel attack is only detected once it has an impact on the organization s technology rather than when unexplained variations are seen in day-to-day business processes or when employees have noted suspicious incidents then the cybersecurity function will have less time to respond to the attack or to avert it. And the result will be more damage done to the organization. The digital future of life sciences payment by outcomes Digital can help life sciences companies improve their services and maximize their revenues. One way it can do this is by allowing them to move to payment by outcomes, a more patient-centric approach that focuses on increasing the value of treatments rather than on simply providing pills. To adopt this approach, life sciences companies will need to broaden their services and better connect with payers, providers and, in particular, patients/consumers in order to monitor and influence their lifestyles and to maximize the benefit of treatments. And to achieve this will require an increased focus on digital channels, data and analytics, and exploiting intellectual property (IP). How cybersecurity can help build digital channels To improve interactions with patients/consumers, payers and providers, life sciences companies need to build better digital channels, such as connected monitors, apps and web portals. And, at each stage of the design and development of new channels, cybersecurity requirements must be met. Digital channels are there to help companies build relationships and access people s data. So they need to be secure from the start to maintain trust. This means that cybersecurity cannot only be called in to check projects once they are complete. Rather, from initial concept to launch, cybersecurity needs to be built in. But for this to happen, the cybersecurity function must be close enough to the business to understand and enable what it is the business is trying to achieve. How cybersecurity can help the business handle its data For each life sciences company, the success of payment by outcomes will largely be determined by how well the company gathers and analyzes the data it generates from patients/ consumers, payers and providers. But with the rise of health monitoring devices, social media and other digital channels, the risk is that this data will become an unmanageable flood. To stop this from happening, organizations must have a data security strategy. They must make sure that incoming data is classified as to its value and sensitivity, and then dealt with appropriately and cost-effectively whether that involves obfuscating personal data or using the full strength of the organization s cybersecurity resources to secure data crucial to the future of the business. But for data classification and data management to be carried out successfully, the cybersecurity function must be close enough to the business to understand its strategy and to recognize the value of different data to that strategy. How cybersecurity can help companies keep their competitive advantage IP data that is processed, the insights generated from it and the advances those insights help produce are all at the heart of most life sciences companies and are only going to become more important for them in the future. Unfortunately, however, digital technology has made IP easier to steal than ever before. In order to secure the future of the business, cybersecurity must protect the most important IP the crown jewels of the organization. But to do this, the cybersecurity function must be close enough to the business to know what that IP data is and where it is stored crucial knowledge that many businesses lack. Every new technology carries its own risks, but 61% of life sciences organizations still do not have a cybersecurity role or department that focuses on emerging technology. Only 6% of life sciences organizations report that the SOC regularly meets with the heads of business operations units to understand their concerns and risks. 4 5
4 Option 1 Relocate the cybersecurity function outside of IT. Three-quarters of life sciences companies we surveyed are either currently using big data or have plans to use it. Amend the governance structure and reporting lines, so that the chief information security officer reports to a board member. Identify cybersecurity key performance indicators (KPIs) for regular board reporting. Align the cybersecurity strategy with the business strategy. Extend the focus of the SOC to cover people and processes. Moving toward a closer alignment To survive, life sciences companies must innovate. So cybersecurity must become a business enabler a function that, instead of saying no to new activities, says yes, and this is how you can do it securely. To achieve this, however, the cybersecurity function needs to get far closer to the business. Establish regular meetings between cybersecurity leadership and business representatives, to help the cybersecurity function understand the needs of the business. Only 19% of life sciences cybersecurity functions report to their organization s top governing structure on the alignment between the business and cybersecurity. In the next page, we have provided two options to help organizations build that connection between cybersecurity and the business. The first is the ideal approach, which is the one that we would recommend. But for those organizations that are not yet prepared to make such big changes, we have created a second option one that increases cybersecurity s connections with the business while leaving the cybersecurity function itself still within IT. Forty-two percent of the life sciences organizations we surveyed said Option 2 The next-best thing: Cybersecurity remains in IT, but builds stronger ties with the business. Keep existing reporting lines, but introduce a dotted line to a board member. Identify suitable representatives in the business to act as key interfaces. Align the cybersecurity strategy with the business strategy. Create cybersecurity initiatives to meet the needs of the business. Establish regular meetings between cybersecurity leadership and business representatives, to help the cybersecurity function understand the needs of the business. that cyber attacks to steal intellectual property or data had been a factor with a high or very high impact on increasing their risk exposure in the last 12 months. 6 7
5 How the biggest life sciences companies lead the rest of the sector Our sample of life sciences companies included some of the largest businesses in the sector. And we discovered that those very large businesses are far more mature in their cybersecurity and their response to cyber threats than the other businesses in the sector. How the very largest life sciences companies lead the sector as a whole All the largest life sciences companies have a threat intelligence program, which helps them to understand, and adapt to, the changing threat landscape. Only 47% of the organizations in the sector sample have such a program. All of the largest life sciences companies have a vulnerability identification program, which helps them to spot vulnerabilities before the cybercriminals do. Only 36% of the organizations in the life sciences sector sample as a whole have one. All of the largest life sciences companies have an incident response program to help them identify when an attack has occurred and how to coordinate their response. Only 25% of all the life sciences organizations we surveyed have one. All of the largest life sciences companies have a breach detection program because breaches of security are inevitable, and early detection is crucial in limiting their impact. This compares with just 19% for the life sciences sector sample as a whole. All of the largest life sciences companies have an identity and access management program to make sure that only the right users have access to the information they need. Only 24% of the life sciences organizations we surveyed have such a program. All of the largest life sciences companies have a focus on privacy by design, making sure that privacy issues are considered from the very start of new initiatives. This compares with 17% among the life sciences sector sample as a whole. How life sciences cybersecurity can become an enabler of innovation To achieve future growth, life sciences organizations must innovate. New digital technologies such as mobile, social media, the cloud and the IoT can enable life sciences organizations to greatly increase their connections with patients/consumers, payers, providers, suppliers and employees. However, while greater connectivity offers huge opportunities, it also creates new risks. To address these risks will demand a broadening of the scope of cybersecurity beyond its traditional IT focus to include the organization s people, processes and all of its many activities. To obtain this broader cybersecurity, life sciences organizations must bring the cybersecurity function closer to the business. Only by achieving this will they be able to close the gap between their need to innovate and their ability to make innovations secure. With the emergence of new digital technologies and the growing sophistication of cybercriminals, this gap will only increase for organizations that do not enhance their cybersecurity. Embedding cybersecurity into the business is an area in which life sciences organizations can learn a great deal from the largest organizations in their sector and from organizations in other sectors. Changes to the role of the cybersecurity function are crucial, but there is also much that those in cybersecurity can do to get closer to the business. They need to build connections with people in the business so that when a new product or process is being developed, those involved know exactly who can guide them on the right cybersecurity steps to take. And the cybersecurity function also needs to find sponsors in the business so that the voice of cybersecurity can be heard at the highest levels. By making these changes and by working together more closely, life sciences organizations and their cybersecurity functions will be able to start building the more active and effective cybersecurity they need cybersecurity that can enable the organization to experiment and innovate in the digital world, successfully and securely. Every new technology carries its own risks, but 61% of life sciences organizations still do not have a cybersecurity role or department that focuses on emerging technology. 8 9
6
7 Want to learn more? Global Information Security Survey ey.com/giss Cybersecurity and the Internet of Things ey.com/iot Cyber threat intelligence how to get ahead of cybercrime ey.com/cti EY Assurance Tax Transactions Advisory About EY EY is a global leader in assurance, tax, transaction and advisory services. The insights and quality services we deliver help build trust and confidence in the capital markets and in economies the world over. We develop outstanding leaders who team to deliver on our promises to all of our stakeholders. In so doing, we play a critical role in building a better working world for our people, for our clients and for our communities. EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients. For more information about our organization, please visit ey.com. How EY s Global Life Sciences Sector can help your business Life sciences companies from emerging start-ups to multinational enterprises face new challenges in a rapidly changing health care ecosystem. Payers and regulators are increasing scrutiny and accelerating the transition to value and outcomes. Big data and patient-empowering technologies are driving new approaches and enabling transparency and consumerism. Players from other sectors are entering health care, making collaborations increasingly complex. These trends challenge every aspect of the life sciences business model, from R&D to marketing. Our Global Life Sciences Sector brings together a worldwide network more than 7,000 sector-focused assurance, tax, transaction and advisory professionals to anticipate trends, identify their implications and develop points of view on responding to critical issues. We can help you navigate your way forward and achieve success in the new ecosystem EYGM Limited. All Rights Reserved. EYG no. FN0251 BMC Agency GA 0000_04183 ED None In line with EY s commitment to minimize its impact on the environment, this document has been printed on paper with a high recycled content. This material has been prepared for general informational purposes only and is not intended to be relied upon as accounting, tax, or other professional advice. Please refer to your advisors for specific advice. The views of third parties set out in this publication are not necessarily the views of the global EY organization or its member firms. Moreover, they should be seen in the context of the time they were made. ey.com/giss
Canada Highlights. Cybersecurity: Do you know which protective measures will make your company cyber resilient?
 Canada Highlights Cybersecurity: Do you know which protective measures will make your company cyber resilient? 21 st Global Information Security Survey 2018 2019 1 Canada highlights According to the EY
Canada Highlights Cybersecurity: Do you know which protective measures will make your company cyber resilient? 21 st Global Information Security Survey 2018 2019 1 Canada highlights According to the EY
EY s data privacy service offering
 EY s data privacy service offering How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world Introduction Data privacy encompasses the rights and obligations
EY s data privacy service offering How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world Introduction Data privacy encompasses the rights and obligations
Danish Cloud Maturity Survey 2018
 Danish Cloud Maturity Survey 2018 Current and planned adoption of cloud services Danish Cloud Maturity Survey 2018 1 Early days for cloud adoption with concerns for security and expertise, and complexity
Danish Cloud Maturity Survey 2018 Current and planned adoption of cloud services Danish Cloud Maturity Survey 2018 1 Early days for cloud adoption with concerns for security and expertise, and complexity
Does someone else own your company s reputation? EY Global Information Security Survey 2018
 Does someone else own your company s reputation? EY Global Information Security Survey 2018 Perspectives for technology, media and entertainment, and telco companies Risking cyber reputations Are TMT companies
Does someone else own your company s reputation? EY Global Information Security Survey 2018 Perspectives for technology, media and entertainment, and telco companies Risking cyber reputations Are TMT companies
Introduction. When it comes to GDPR compliance, is OK for now enough? Minds made for protecting financial services
 When it comes to GDPR compliance, is OK for now enough? EY CertifyPoint s GDPR certification process will help you achieve and demonstrate compliance. Minds made for protecting financial services Introduction
When it comes to GDPR compliance, is OK for now enough? EY CertifyPoint s GDPR certification process will help you achieve and demonstrate compliance. Minds made for protecting financial services Introduction
Demonstrating data privacy for GDPR and beyond
 Demonstrating data privacy for GDPR and beyond EY data privacy assurance services Introduction The General Data Protection Regulation (GDPR) is ushering in a new era of data privacy in Europe. Organizations
Demonstrating data privacy for GDPR and beyond EY data privacy assurance services Introduction The General Data Protection Regulation (GDPR) is ushering in a new era of data privacy in Europe. Organizations
EY Norwegian Cloud Maturity Survey 2018
 EY Norwegian Cloud Maturity Survey 2018 Current and planned adoption of cloud services EY Norwegian Cloud Maturity Survey 2018 1 It is still early days for cloud adoption in Norway, and the complexity
EY Norwegian Cloud Maturity Survey 2018 Current and planned adoption of cloud services EY Norwegian Cloud Maturity Survey 2018 1 It is still early days for cloud adoption in Norway, and the complexity
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Big data privacy in Australia
 Five-article series Big data privacy in Australia Three actions you can take towards compliance Article 5 Big data and privacy Three actions you can take towards compliance There are three actions that
Five-article series Big data privacy in Australia Three actions you can take towards compliance Article 5 Big data and privacy Three actions you can take towards compliance There are three actions that
Digital trends in real estate, hospitality and construction. Building blocks for future growth. Brochure title RR. Brochure subtitle RR
 Digital trends in real estate, hospitality and construction Building blocks for future growth Brochure title RR Brochure subtitle RR 2 Digital trends in real estate, hospitality and construction: building
Digital trends in real estate, hospitality and construction Building blocks for future growth Brochure title RR Brochure subtitle RR 2 Digital trends in real estate, hospitality and construction: building
What s new in EY Atlas. November 2018
 November 2018 EY tlas is regularly evolving and being enhanced to make your experience with the tool even better. This document highlights the new features and enhancements made since EY tlas was launched
November 2018 EY tlas is regularly evolving and being enhanced to make your experience with the tool even better. This document highlights the new features and enhancements made since EY tlas was launched
Cybersecurity. Securely enabling transformation and change
 Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
SOLUTION BRIEF RSA ARCHER IT & SECURITY RISK MANAGEMENT
 RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
Security in India: Enabling a New Connected Era
 White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
Step 1: Open browser to navigate to the data science challenge home page
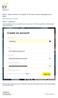 Step 1: Open browser to navigate to the data science challenge home page https://datascience.ey.com/ Step 2: Logging in You will need to create an account if you are a new user. Click the sign up button
Step 1: Open browser to navigate to the data science challenge home page https://datascience.ey.com/ Step 2: Logging in You will need to create an account if you are a new user. Click the sign up button
EY Norwegian Cloud Maturity Survey Current and planned adoption of cloud services
 EY Norwegian Cloud Maturity Survey 2019 Current and planned adoption of cloud services Contents 01 Cloud maturity 4 02 Drivers and challenges 6 03 Current usage 10 04 Future plans 16 05 About the survey
EY Norwegian Cloud Maturity Survey 2019 Current and planned adoption of cloud services Contents 01 Cloud maturity 4 02 Drivers and challenges 6 03 Current usage 10 04 Future plans 16 05 About the survey
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Tax News Update: Global Edition (GTNU) User Guide
 Tax News Update: Global Edition (GTNU) User Guide Agenda GTNU introduction Highlights How to access GTNU How to set up email preferences Browsing for content Refinement panel Searching for content Page
Tax News Update: Global Edition (GTNU) User Guide Agenda GTNU introduction Highlights How to access GTNU How to set up email preferences Browsing for content Refinement panel Searching for content Page
If you were under cyber attack would you ever know?
 If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
MITIGATE CYBER ATTACK RISK
 SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
The New Healthcare Economy is rising up
 The New Healthcare Economy is rising up February 2017 The ever-rising costs of healthcare are fostering innovative solutions and disruptive business models Cybersecurity concerns come to medical technology
The New Healthcare Economy is rising up February 2017 The ever-rising costs of healthcare are fostering innovative solutions and disruptive business models Cybersecurity concerns come to medical technology
Data Management and Security in the GDPR Era
 Data Management and Security in the GDPR Era Franck Hourdin; Vice President, EMEA Security Russ Lowenthal; Director, Database Security Product Management Mike Turner; Chief Operating Officer, Capgemini
Data Management and Security in the GDPR Era Franck Hourdin; Vice President, EMEA Security Russ Lowenthal; Director, Database Security Product Management Mike Turner; Chief Operating Officer, Capgemini
Digital innovation? Cyber secure? Digital security: a Financial Services perspective
 innovation? Cyber secure? security: a Financial Services perspective Contents // Protecting your digital strategy in an evolving cyber environment 1 // What s included in a comprehensive digital risk approach?
innovation? Cyber secure? security: a Financial Services perspective Contents // Protecting your digital strategy in an evolving cyber environment 1 // What s included in a comprehensive digital risk approach?
The State of Cybersecurity and Digital Trust 2016
 The State of Cybersecurity and Digital Trust 2016 Identifying Cybersecurity Gaps to Rethink State of the Art Executive Summary Executive Summary While the advent of digital technology has fueled new business
The State of Cybersecurity and Digital Trust 2016 Identifying Cybersecurity Gaps to Rethink State of the Art Executive Summary Executive Summary While the advent of digital technology has fueled new business
THALES DATA THREAT REPORT
 2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security U.S. FEDERAL EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Federal agency data is under siege. Over half of all agency IT security
2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security U.S. FEDERAL EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Federal agency data is under siege. Over half of all agency IT security
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
Cyber Threat Landscape April 2013
 www.pwc.co.uk Cyber Threat Landscape April 2013 Cyber Threats: Influences of the global business ecosystem Economic Industry/ Competitors Technology-led innovation has enabled business models to evolve
www.pwc.co.uk Cyber Threat Landscape April 2013 Cyber Threats: Influences of the global business ecosystem Economic Industry/ Competitors Technology-led innovation has enabled business models to evolve
RIMS Perk Session Protecting the Crown Jewels A Risk Manager's guide to cyber security March 18, 2015
 www.pwc.com RIMS Perk Session 2015 - Protecting the Crown Jewels A Risk Manager's guide to cyber security March 18, 2015 Los Angeles RIMS Agenda Introductions What is Cybersecurity? Crown jewels The bad
www.pwc.com RIMS Perk Session 2015 - Protecting the Crown Jewels A Risk Manager's guide to cyber security March 18, 2015 Los Angeles RIMS Agenda Introductions What is Cybersecurity? Crown jewels The bad
ISACA Cincinnati Chapter March Meeting
 ISACA Cincinnati Chapter March Meeting Recent and Proposed Changes to SOC Reports Impacting Service and User Organizations. March 3, 2015 Presenters: Sayontan Basu-Mallick Lori Johnson Agenda SOCR Overview
ISACA Cincinnati Chapter March Meeting Recent and Proposed Changes to SOC Reports Impacting Service and User Organizations. March 3, 2015 Presenters: Sayontan Basu-Mallick Lori Johnson Agenda SOCR Overview
Modern Database Architectures Demand Modern Data Security Measures
 Forrester Opportunity Snapshot: A Custom Study Commissioned By Imperva January 2018 Modern Database Architectures Demand Modern Data Security Measures GET STARTED Introduction The fast-paced, ever-changing
Forrester Opportunity Snapshot: A Custom Study Commissioned By Imperva January 2018 Modern Database Architectures Demand Modern Data Security Measures GET STARTED Introduction The fast-paced, ever-changing
IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES
 IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES Introductions Agenda Overall data risk and benefit landscape / shifting risk and opportunity landscape and market expectations Looking at data
IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES Introductions Agenda Overall data risk and benefit landscape / shifting risk and opportunity landscape and market expectations Looking at data
RSA Solution Brief. Managing Risk Within Advanced Security Operations. RSA Solution Brief
 RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
IBM Security Systems. IBM X-Force 2012 & CISO Survey. Cyber Security Threat Landscape IBM Corporation IBM Corporation
 IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
FOR FINANCIAL SERVICES ORGANIZATIONS
 RSA BUSINESS-DRIVEN SECURITYTM FOR FINANCIAL SERVICES ORGANIZATIONS MANAGING THE NEXUS OF RISK & SECURITY A CHANGING LANDSCAPE AND A NEW APPROACH Today s financial services technology landscape is increasingly
RSA BUSINESS-DRIVEN SECURITYTM FOR FINANCIAL SERVICES ORGANIZATIONS MANAGING THE NEXUS OF RISK & SECURITY A CHANGING LANDSCAPE AND A NEW APPROACH Today s financial services technology landscape is increasingly
THALES DATA THREAT REPORT
 2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security INDIA EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Rising risks for sensitive data in India In India, as in the rest of the
2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security INDIA EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Rising risks for sensitive data in India In India, as in the rest of the
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
Modernizing Healthcare IT for the Data-driven Cognitive Era Storage and Software-Defined Infrastructure
 Modernizing Healthcare IT for the Data-driven Cognitive Era Storage and Software-Defined Infrastructure An IDC InfoBrief, Sponsored by IBM April 2018 Executive Summary Today s healthcare organizations
Modernizing Healthcare IT for the Data-driven Cognitive Era Storage and Software-Defined Infrastructure An IDC InfoBrief, Sponsored by IBM April 2018 Executive Summary Today s healthcare organizations
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
EY Consulting. Is your strategy planning for the future or creating it? #TransformativeAge
 2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
Securing Digital Transformation
 September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Angela McKay Director, Government Security Policy and Strategy Microsoft
 Angela McKay Director, Government Security Policy and Strategy Microsoft Demographic Trends: Internet Users in 2005.ru.ca.is.uk.nl.be.no.de.pl.ua.us.fr.es.ch.it.eg.il.sa.jo.tr.qa.ae.kz.cn.tw.kr.jp.mx.co.br.pk.th.ph.ng.in.sg.my.ar.id.au
Angela McKay Director, Government Security Policy and Strategy Microsoft Demographic Trends: Internet Users in 2005.ru.ca.is.uk.nl.be.no.de.pl.ua.us.fr.es.ch.it.eg.il.sa.jo.tr.qa.ae.kz.cn.tw.kr.jp.mx.co.br.pk.th.ph.ng.in.sg.my.ar.id.au
Data Protection. Practical Strategies for Getting it Right. Jamie Ross Data Security Day June 8, 2016
 Data Protection Practical Strategies for Getting it Right Jamie Ross Data Security Day June 8, 2016 Agenda 1) Data protection key drivers and the need for an integrated approach 2) Common challenges data
Data Protection Practical Strategies for Getting it Right Jamie Ross Data Security Day June 8, 2016 Agenda 1) Data protection key drivers and the need for an integrated approach 2) Common challenges data
Get ahead of cybercrime. EY s 2014 Global Information Security Survey
 Get ahead of cybercrime EY s 2014 Global Information Security Survey Agenda Introduction The cyber threat landscape The journey to cybersecurity maturity Activate Adapt Anticipate Summary Page 2 EY s Global
Get ahead of cybercrime EY s 2014 Global Information Security Survey Agenda Introduction The cyber threat landscape The journey to cybersecurity maturity Activate Adapt Anticipate Summary Page 2 EY s Global
Developing your GDPR response for competitive advantage. EU General Data Protection Regulation (GDPR)
 Developing your GDPR response for competitive advantage EU General Data Protection Regulation (GDPR) Introduction In May 2018, the EU s new GDPR ushers in unprecedented levels of data protection for EU
Developing your GDPR response for competitive advantage EU General Data Protection Regulation (GDPR) Introduction In May 2018, the EU s new GDPR ushers in unprecedented levels of data protection for EU
THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION BREACH & ATTACK SIMULATION
 BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
The Deloitte-NASCIO Cybersecurity Study Insights from
 The Deloitte-NASCIO Cybersecurity Study Insights from 2010-2016 August 21, 2018 Srini Subramanian State Government Sector Leader Deloitte Erik Avakian CISO Pennsylvania Michael Roling CISO Missouri Meredith
The Deloitte-NASCIO Cybersecurity Study Insights from 2010-2016 August 21, 2018 Srini Subramanian State Government Sector Leader Deloitte Erik Avakian CISO Pennsylvania Michael Roling CISO Missouri Meredith
SOLUTION BRIEF RSA NETWITNESS EVOLVED SIEM
 RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
Building a Resilient Security Posture for Effective Breach Prevention
 SESSION ID: GPS-F03B Building a Resilient Security Posture for Effective Breach Prevention Avinash Prasad Head Managed Security Services, Tata Communications Agenda for discussion 1. Security Posture 2.
SESSION ID: GPS-F03B Building a Resilient Security Posture for Effective Breach Prevention Avinash Prasad Head Managed Security Services, Tata Communications Agenda for discussion 1. Security Posture 2.
SELLING YOUR ORGANIZATION ON APPLICATION SECURITY. Navigating a new era of cyberthreats
 SELLING YOUR ORGANIZATION ON APPLICATION SECURITY Navigating a new era of cyberthreats Selling Your Organization on Application Security 01 It's no secret that cyberattacks place organizations large and
SELLING YOUR ORGANIZATION ON APPLICATION SECURITY Navigating a new era of cyberthreats Selling Your Organization on Application Security 01 It's no secret that cyberattacks place organizations large and
IBM Cloud Internet Services: Optimizing security to protect your web applications
 WHITE PAPER IBM Cloud Internet Services: Optimizing security to protect your web applications Secure Internet applications and APIs against denialof-service attacks, customer data compromise, and abusive
WHITE PAPER IBM Cloud Internet Services: Optimizing security to protect your web applications Secure Internet applications and APIs against denialof-service attacks, customer data compromise, and abusive
Real estate predictions 2017 What changes lie ahead?
 Real estate predictions 2017 What changes lie ahead? Cyber Risk 2017. For information, contact Deloitte Consultores, S.A. Real Estate Predictions 2017 2 Cyber Risk Rising cyber risk in real estate through
Real estate predictions 2017 What changes lie ahead? Cyber Risk 2017. For information, contact Deloitte Consultores, S.A. Real Estate Predictions 2017 2 Cyber Risk Rising cyber risk in real estate through
ALIGNING CYBERSECURITY AND MISSION PLANNING WITH ADVANCED ANALYTICS AND HUMAN INSIGHT
 THOUGHT PIECE ALIGNING CYBERSECURITY AND MISSION PLANNING WITH ADVANCED ANALYTICS AND HUMAN INSIGHT Brad Stone Vice President Stone_Brad@bah.com Brian Hogbin Distinguished Technologist Hogbin_Brian@bah.com
THOUGHT PIECE ALIGNING CYBERSECURITY AND MISSION PLANNING WITH ADVANCED ANALYTICS AND HUMAN INSIGHT Brad Stone Vice President Stone_Brad@bah.com Brian Hogbin Distinguished Technologist Hogbin_Brian@bah.com
Cyber Security and Cyber Fraud
 Cyber Security and Cyber Fraud Remarks by Andrew Ross Director, Payments and Cyber Security Canadian Bankers Association for Senate Standing Committee on Banking, Trade, and Commerce October 26, 2017 Ottawa
Cyber Security and Cyber Fraud Remarks by Andrew Ross Director, Payments and Cyber Security Canadian Bankers Association for Senate Standing Committee on Banking, Trade, and Commerce October 26, 2017 Ottawa
Cybersecurity: balancing risks and controls for finance professionals
 Cybersecurity: balancing risks and controls for finance professionals Protecting your corporate brand June 2015 A recent discussion hosted by EY for nearly 250 finance professionals, outlined that organisations
Cybersecurity: balancing risks and controls for finance professionals Protecting your corporate brand June 2015 A recent discussion hosted by EY for nearly 250 finance professionals, outlined that organisations
Safeguarding unclassified controlled technical information (UCTI)
 Safeguarding unclassified controlled technical information (UCTI) An overview Government Contract Services Bulletin Safeguarding UCTI An overview On November 18, 2013, the Department of Defense (DoD) issued
Safeguarding unclassified controlled technical information (UCTI) An overview Government Contract Services Bulletin Safeguarding UCTI An overview On November 18, 2013, the Department of Defense (DoD) issued
Implementing ITIL v3 Service Lifecycle
 Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Cisco Connected Factory Accelerator Bundles
 Data Sheet Cisco Connected Factory Accelerator Bundles Many manufacturers are pursuing the immense business benefits available from digitizing and connecting their factories. Major gains in overall equipment
Data Sheet Cisco Connected Factory Accelerator Bundles Many manufacturers are pursuing the immense business benefits available from digitizing and connecting their factories. Major gains in overall equipment
Engaging Executives and Boards in Cybersecurity Session 303, Feb 20, 2017 Sanjeev Sah, CISO, Texas Children s Hospital Jimmy Joseph, Senior Manager,
 Engaging Executives and Boards in Cybersecurity Session 303, Feb 20, 2017 Sanjeev Sah, CISO, Texas Children s Hospital Jimmy Joseph, Senior Manager, Deloitte & Touche LLP 1 Speaker Introduction Sanjeev
Engaging Executives and Boards in Cybersecurity Session 303, Feb 20, 2017 Sanjeev Sah, CISO, Texas Children s Hospital Jimmy Joseph, Senior Manager, Deloitte & Touche LLP 1 Speaker Introduction Sanjeev
Embedded SIM Study. September 2015 update
 Embedded SIM Study September 2015 update Executive summary Following a first white paper drawing upon interviews with mobile network operators in 3Q 2014, EY decided to perform a second round of interviews
Embedded SIM Study September 2015 update Executive summary Following a first white paper drawing upon interviews with mobile network operators in 3Q 2014, EY decided to perform a second round of interviews
Emerging Technologies The risks they pose to your organisations
 Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
Vulnerability Management. June Risk Advisory
 June 2018 Risk Advisory Contents A Better Way To Manage Vulnerabilities 4 Business Challenge 6 Vulnerability Management as a Service 7 Robust Service Architecture 8 Our Differentiators 9 Vulnerability
June 2018 Risk Advisory Contents A Better Way To Manage Vulnerabilities 4 Business Challenge 6 Vulnerability Management as a Service 7 Robust Service Architecture 8 Our Differentiators 9 Vulnerability
Cyber Security Incident Response Fighting Fire with Fire
 Cyber Security Incident Response Fighting Fire with Fire Arun Perinkolam, Senior Manager Deloitte & Touche LLP Professional Techniques T21 CRISC CGEIT CISM CISA AGENDA Companies like yours What is the
Cyber Security Incident Response Fighting Fire with Fire Arun Perinkolam, Senior Manager Deloitte & Touche LLP Professional Techniques T21 CRISC CGEIT CISM CISA AGENDA Companies like yours What is the
EY Training. Project Management Professional PMP. Exam preparatory course. 30 September 4 October 2018
 EY Training Project Management Professional PMP Exam preparatory course 30 September 4 October 2018 Contents Introduction 04 Membership and examination 05 Key information 06 Registration form 07 Introduction
EY Training Project Management Professional PMP Exam preparatory course 30 September 4 October 2018 Contents Introduction 04 Membership and examination 05 Key information 06 Registration form 07 Introduction
Using Threat Analytics to Protect Privileged Access and Prevent Breaches
 Using Threat Analytics to Protect Privileged Access and Prevent Breaches Under Attack Protecting privileged access and preventing breaches remains an urgent concern for companies of all sizes. Attackers
Using Threat Analytics to Protect Privileged Access and Prevent Breaches Under Attack Protecting privileged access and preventing breaches remains an urgent concern for companies of all sizes. Attackers
THE POWER OF TECH-SAVVY BOARDS:
 THE POWER OF TECH-SAVVY BOARDS: LEADERSHIP S ROLE IN CULTIVATING CYBERSECURITY TALENT SHANNON DONAHUE DIRECTOR, INFORMATION SECURITY PRACTICES 1 IT S A RISK-BASED WORLD: THE 10 MOST CRITICAL UNCERTAINTIES
THE POWER OF TECH-SAVVY BOARDS: LEADERSHIP S ROLE IN CULTIVATING CYBERSECURITY TALENT SHANNON DONAHUE DIRECTOR, INFORMATION SECURITY PRACTICES 1 IT S A RISK-BASED WORLD: THE 10 MOST CRITICAL UNCERTAINTIES
CLOSING THE DOOR TO CYBER ATTACKS HOW ENTERPRISES CAN IMPLEMENT COMPREHENSIVE INFORMATION SECURITY
 CLOSING THE DOOR TO CYBER ATTACKS HOW ENTERPRISES CAN IMPLEMENT COMPREHENSIVE INFORMATION SECURITY CLOSING THE DOOR TO CYBER ATTACKS Cybersecurity and information security have become key challenges for
CLOSING THE DOOR TO CYBER ATTACKS HOW ENTERPRISES CAN IMPLEMENT COMPREHENSIVE INFORMATION SECURITY CLOSING THE DOOR TO CYBER ATTACKS Cybersecurity and information security have become key challenges for
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
Six Weeks to Security Operations The AMP Story. Mike Byrne Cyber Security AMP
 Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
STOPS CYBER ATTACKS BEFORE THEY STOP YOU. Prepare, recognize, and respond to today s attacks earlier with Verizon Security Solutions.
 Intelligence-driven security STOPS CYBER ATTACKS BEFORE THEY STOP YOU. Prepare, recognize, and respond to today s attacks earlier with Verizon Security Solutions. BETTER INTELLIGENCE. BETTER DEFENSE. The
Intelligence-driven security STOPS CYBER ATTACKS BEFORE THEY STOP YOU. Prepare, recognize, and respond to today s attacks earlier with Verizon Security Solutions. BETTER INTELLIGENCE. BETTER DEFENSE. The
Eliminating the Blind Spot: Rapidly Detect and Respond to the Advanced and Evasive Threat
 WHITE PAPER Eliminating the Blind Spot: Rapidly Detect and Respond to the Advanced and Evasive Threat Executive Summary Unfortunately, it s a foregone conclusion that no organisation is 100 percent safe
WHITE PAPER Eliminating the Blind Spot: Rapidly Detect and Respond to the Advanced and Evasive Threat Executive Summary Unfortunately, it s a foregone conclusion that no organisation is 100 percent safe
GOVERNMENT IT: FOCUSING ON 5 TECHNOLOGY PRIORITIES
 GOVERNMENT IT: FOCUSING ON 5 TECHNOLOGY PRIORITIES INSIGHTS FROM PUBLIC SECTOR IT LEADERS DISCOVER NEW POSSIBILITIES. New network technology is breaking down barriers in government offices, allowing for
GOVERNMENT IT: FOCUSING ON 5 TECHNOLOGY PRIORITIES INSIGHTS FROM PUBLIC SECTOR IT LEADERS DISCOVER NEW POSSIBILITIES. New network technology is breaking down barriers in government offices, allowing for
BHConsulting. Your trusted cybersecurity partner
 Your trusted cybersecurity partner BH Consulting Securing your business BH Consulting is an award-winning, independent provider of cybersecurity consulting and information security advisory services. Recognised
Your trusted cybersecurity partner BH Consulting Securing your business BH Consulting is an award-winning, independent provider of cybersecurity consulting and information security advisory services. Recognised
Presented by Ingrid Fredeen and Pamela Passman. Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0
 Cyber Security and Inside Threats: Turning Policies into Practices Presented by Ingrid Fredeen and Pamela Passman Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0 Presented By Ingrid Fredeen, J.D.
Cyber Security and Inside Threats: Turning Policies into Practices Presented by Ingrid Fredeen and Pamela Passman Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0 Presented By Ingrid Fredeen, J.D.
Cyber Security: It s all about TRUST
 www.pwc.com/vn Cyber Security: It s all about TRUST 29 th March 2017 Robert Tran Cybersecurity leader, Vietnam Content s Digital IQ Survey 1 Current state of Cybersecurity in Vietnam 2 2 Our global team
www.pwc.com/vn Cyber Security: It s all about TRUST 29 th March 2017 Robert Tran Cybersecurity leader, Vietnam Content s Digital IQ Survey 1 Current state of Cybersecurity in Vietnam 2 2 Our global team
AUSTRALIA Building Digital Trust with Australian Healthcare Consumers
 AUSTRALIA Building Digital Trust with Australian Healthcare Consumers Accenture 2017 Consumer Survey on Healthcare Cybersecurity and Digital Trust 2 Consumers in Australia trust healthcare organisations
AUSTRALIA Building Digital Trust with Australian Healthcare Consumers Accenture 2017 Consumer Survey on Healthcare Cybersecurity and Digital Trust 2 Consumers in Australia trust healthcare organisations
Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL
 Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL Shifting budgets and responsibilities require IT and physical security teams to consider fundamental change in day-to-day
Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL Shifting budgets and responsibilities require IT and physical security teams to consider fundamental change in day-to-day
Incentives for IoT Security. White Paper. May Author: Dr. Cédric LEVY-BENCHETON, CEO
 White Paper Incentives for IoT Security May 2018 Author: Dr. Cédric LEVY-BENCHETON, CEO Table of Content Defining the IoT 5 Insecurity by design... 5 But why are IoT systems so vulnerable?... 5 Integrating
White Paper Incentives for IoT Security May 2018 Author: Dr. Cédric LEVY-BENCHETON, CEO Table of Content Defining the IoT 5 Insecurity by design... 5 But why are IoT systems so vulnerable?... 5 Integrating
Mapping Your Requirements to the NIST Cybersecurity Framework. Industry Perspective
 Mapping Your Requirements to the NIST Cybersecurity Framework Industry Perspective 1 Quest has the solutions and services to help your organization identify, protect, detect, respond and recover, better
Mapping Your Requirements to the NIST Cybersecurity Framework Industry Perspective 1 Quest has the solutions and services to help your organization identify, protect, detect, respond and recover, better
Cyber Security in Real Estate
 Cyber Security in Real Estate Protecting against a very real risk Mark Brown Executive Director, Cyber Security & Resilience The question is not if your company will be breached, or even when. It has already
Cyber Security in Real Estate Protecting against a very real risk Mark Brown Executive Director, Cyber Security & Resilience The question is not if your company will be breached, or even when. It has already
Robert Hayes Senior Director Microsoft Global Cyber Security & Data Protection Group
 Robert Hayes Senior Director Microsoft Global Cyber Security & Data Protection Group Presentation Objectives Introductions Cyber security context Cyber security in the maritime sector Developing cybersecurity
Robert Hayes Senior Director Microsoft Global Cyber Security & Data Protection Group Presentation Objectives Introductions Cyber security context Cyber security in the maritime sector Developing cybersecurity
Express Monitoring 2019
 Express Monitoring 2019 WHY CHOOSE PT EXPRESS MONITORING PT Express Monitoring provides a quick evaluation of the current signaling network protection level. This service helps to discover critical vulnerabilities
Express Monitoring 2019 WHY CHOOSE PT EXPRESS MONITORING PT Express Monitoring provides a quick evaluation of the current signaling network protection level. This service helps to discover critical vulnerabilities
Cyber Security Technologies
 1 / Cyber Security Technologies International Seminar on Cyber Security: An Action to Establish the National Cyber Security Center Lisbon, 12 th September 2013 23 / Key highlights - Thales Group Thales
1 / Cyber Security Technologies International Seminar on Cyber Security: An Action to Establish the National Cyber Security Center Lisbon, 12 th September 2013 23 / Key highlights - Thales Group Thales
EY GlobalOne Individual Portal
 EY GlobalOne Individual Portal User guide LOG IN EY GlobalOne Individual Portal ( GlobalOne ) allows clients and EY to securely exchange information to support the delivery of global Immigration and Tax
EY GlobalOne Individual Portal User guide LOG IN EY GlobalOne Individual Portal ( GlobalOne ) allows clients and EY to securely exchange information to support the delivery of global Immigration and Tax
The value of visibility. Cybersecurity risk management examination
 The value of visibility Cybersecurity risk management examination Welcome to the "new normal" Cyberattacks are inevitable. In fact, it s no longer a question of if a breach will occur but when. Cybercriminals
The value of visibility Cybersecurity risk management examination Welcome to the "new normal" Cyberattacks are inevitable. In fact, it s no longer a question of if a breach will occur but when. Cybercriminals
A new approach to Cyber Security
 A new approach to Cyber Security Feel Free kpmg.ch We believe cyber security should be about what you can do not what you can t. DRIVEN BY BUSINESS ASPIRATIONS We work with you to move your business forward.
A new approach to Cyber Security Feel Free kpmg.ch We believe cyber security should be about what you can do not what you can t. DRIVEN BY BUSINESS ASPIRATIONS We work with you to move your business forward.
SDI, Containers and DevOps - Cloud Adoption Trends Driving IT Transformation
 SDI, Containers and DevOps - Cloud Adoption Trends Driving IT Transformation Research Report August 2017 suse.com Executive Summary As we approach 2020, businesses face a maelstrom of increasing customer
SDI, Containers and DevOps - Cloud Adoption Trends Driving IT Transformation Research Report August 2017 suse.com Executive Summary As we approach 2020, businesses face a maelstrom of increasing customer
Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture
 February 2019 Challenging State of Vulnerability Management Today: Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture In the last two years, businesses and governments have seen data breaches
February 2019 Challenging State of Vulnerability Management Today: Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture In the last two years, businesses and governments have seen data breaches
CYBER INSURANCE: MANAGING THE RISK
 CYBER INSURANCE: MANAGING THE RISK LEON FOUCHE PARTNER & NATIONAL CYBERSECURITY LEAD BDO AUSTRALIA MEMBER OF THE GLOBAL CYBERSECURITY LEADERSHIP GROUP ii CYBER INSURANCE: MANAGING THE RISK There s no doubt
CYBER INSURANCE: MANAGING THE RISK LEON FOUCHE PARTNER & NATIONAL CYBERSECURITY LEAD BDO AUSTRALIA MEMBER OF THE GLOBAL CYBERSECURITY LEADERSHIP GROUP ii CYBER INSURANCE: MANAGING THE RISK There s no doubt
General Framework for Secure IoT Systems
 General Framework for Secure IoT Systems National center of Incident readiness and Strategy for Cybersecurity (NISC) Government of Japan August 26, 2016 1. General Framework Objective Internet of Things
General Framework for Secure IoT Systems National center of Incident readiness and Strategy for Cybersecurity (NISC) Government of Japan August 26, 2016 1. General Framework Objective Internet of Things
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cyber Risk for Maritime
 Cyber Risk for Maritime Enabling a step-change in risk management for the maritime industry kpmg.no kongsberg.com/kdi 0 Cyber Risk for Maritime The international shipping industry is responsible for the
Cyber Risk for Maritime Enabling a step-change in risk management for the maritime industry kpmg.no kongsberg.com/kdi 0 Cyber Risk for Maritime The international shipping industry is responsible for the
TRANSFORMING WEST MIDLANDS POLICE A BOLD NEW MODEL FOR POLICING
 TRANSFORMING WEST MIDLANDS POLICE A BOLD NEW MODEL FOR POLICING In 2014, West Midlands Police (WMP) committed to a striking transformation programme that would help the force meet current and future policing
TRANSFORMING WEST MIDLANDS POLICE A BOLD NEW MODEL FOR POLICING In 2014, West Midlands Police (WMP) committed to a striking transformation programme that would help the force meet current and future policing
Combating Cyber Risk in the Supply Chain
 SESSION ID: CIN-W10 Combating Cyber Risk in the Supply Chain Ashok Sankar Senior Director Cyber Strategy Raytheon Websense @ashoksankar Introduction The velocity of data breaches is accelerating at an
SESSION ID: CIN-W10 Combating Cyber Risk in the Supply Chain Ashok Sankar Senior Director Cyber Strategy Raytheon Websense @ashoksankar Introduction The velocity of data breaches is accelerating at an
Run the business. Not the risks.
 Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
EY s Data Privacy Services. January 2019
 EY s Data Privacy Services January 2019 Introduction Data privacy encompasses the rights and obligations of individuals and organizations with respect to the collection, use, disclosure, and retention
EY s Data Privacy Services January 2019 Introduction Data privacy encompasses the rights and obligations of individuals and organizations with respect to the collection, use, disclosure, and retention
Securing the Internet of Things (IoT) at the U.S. Department of Veterans Affairs
 Securing the Internet of Things (IoT) at the U.S. Department of Veterans Affairs Dominic Cussatt Acting Deputy Assistant Secretary / Chief Information Security Officer (CISO) February 20, 2017 The Cyber
Securing the Internet of Things (IoT) at the U.S. Department of Veterans Affairs Dominic Cussatt Acting Deputy Assistant Secretary / Chief Information Security Officer (CISO) February 20, 2017 The Cyber
