Scanning-Less Scanning. Installation Guide
|
|
|
- Samuel Booker
- 5 years ago
- Views:
Transcription
1 Scanning-Less Scanning Installation Guide Last update: 9 February 2017
2 Table of Contents Scanning-Less Scanning Description A Traditional Approach Outpost24 s Unique Approach... 3 Enabling Scanning-Less Scanning Ad-hoc Scanning-Less Scanning... 5 Automatic Notifications Outpost24 SLS Setup Guide
3 This administration guide will assist you when installing and configuring Scanning-Less Scanning (SLS) available for Outpost24 products, ensuring you benefit from all features. Scanning-Less Scanning Description 1. A Traditional Approach Traditionally, organizations use vulnerability management tools to scan their network at regular intervals. This includes weekly, bi-weekly, and monthly intervals. If a new vulnerability is discovered in between those scans, the system is unknowingly susceptible to an attack during that time period. 2. Outpost24 s Unique Approach Traditional vulnerability management tools provide organizations with a false sense of security between regularly scheduled scans. The organization may feel safe, but new vulnerabilities during the time period between scans can be exploited to cause significant losses. In striving to offer a more proactive approach to vulnerability management, Outpost24 has incorporated a unique tool feature called SLS, which decreases the overall exposure window for attacks and eliminates risk. When a new vulnerability is discovered, Outpost24 s products are immediately updated. The tools then compare information gathered during the last scan and alert the user about any systems that could be affected by this new vulnerability. SLS is included in OUTSCAN, an on-demand Software-as-a-Service, and HIAB, a plug and play appliance, both of which allow organizations to easily detect vulnerabilities and manage remediation to prevent hackers from penetrating the network. 3 Outpost24 SLS Setup Guide
4 Enabling Scanning-Less Scanning In order to enable the SLS feature on your scans you should go to the specific schedule (under Menu (Outpost24 logo), Target Scanning, Scan Scheduling ) and right click on the schedule name, choose the option Edit from within the context menu that appears. This will bring up the Maintaining Scan Schedule window. As you can see above, in the Scan Settings tab, there is an option called Daily updates. This is the Scanning-Less Scanning feature, which allows the report to be updated on a daily basis (at the same time of day that is defined in the Next Scan field) with any new vulnerability that may affect the specific system. NOTE: The fingerprint database for a system will only be retained for a maximum of one month. After that period, the fingerprint database will be considered outdated and no longer used. 4 Outpost24 SLS Setup Guide
5 3. Ad-hoc Scanning-Less Scanning It is also possible to perform manual Scanning-Less Scans at whatever time you want. In the Manage Report section it is possible to right click on a schedule and select Update scan results. This will initiate a Scanning-Less Scan against the target and compare new vulnerabilities with the fingerprint stored for this scan. Any new vulnerability will then be available in the same report but with a different date in the column Date Added, which can be added to the report grid. If the report doesn t have a valid fingerprint database stored, this option won t be available in the above menu. 5 Outpost24 SLS Setup Guide
6 Automatic Notifications In order to be alerted upon new vulnerabilities you are required to define for which targets, who should be notified and for which criticality. This is done in the built-in Event Notification system, which is located under Menu, Settings. NOTE: This should be defined after an initial scan has been executed. Otherwise it will alert for each finding in the first report on the defined risk level. In the above example an alert will be send to on all new High risks that are detected on all targets included in the group High. The above step should be repeated for each criticality, which requires to be monitored according to the company policy. Multiple entries with different targets and recipients can of course be defined within the system. 6 Outpost24 SLS Setup Guide
Event Notifications Quick Start Guide
 Event Notifications Quick Start Guide Last update: 9 February 2017 Table of Contents 1. Executive Summary... 3 2. Event Notifications in Graphical User Interface... 4 2.1. Default Event Notification Settings...
Event Notifications Quick Start Guide Last update: 9 February 2017 Table of Contents 1. Executive Summary... 3 2. Event Notifications in Graphical User Interface... 4 2.1. Default Event Notification Settings...
Inspector Software Appliance User Guide
 User Guide 2017 RapidFire Tools, Inc. All rights reserved 20170804 Ver 3V Contents Overview... 3 Components of the... 3... 3 Inspector Diagnostic Tool... 3 Network Detective Application... 3 Features...
User Guide 2017 RapidFire Tools, Inc. All rights reserved 20170804 Ver 3V Contents Overview... 3 Components of the... 3... 3 Inspector Diagnostic Tool... 3 Network Detective Application... 3 Features...
User Interface. An Introductory Guide
 User Interface An Introductory Guide Last update: 18 May 2017 Index Introduction 3 Vulnerability Database 4 Overview 5 Targets 6 Findings 7 Vulnerability Details 8 Risk Acceptance 9 Network Interface Configuration
User Interface An Introductory Guide Last update: 18 May 2017 Index Introduction 3 Vulnerability Database 4 Overview 5 Targets 6 Findings 7 Vulnerability Details 8 Risk Acceptance 9 Network Interface Configuration
Reporter User Guide RapidFire Tools, Inc. All rights reserved Ver 4T
 Reporter User Guide 2017 RapidFire Tools, Inc. All rights reserved 20171102 Ver 4T Contents Overview... 3 Components of the Reporter... 3 Reporter Appliance... 3 Network Detective Application... 3 Diagnostic
Reporter User Guide 2017 RapidFire Tools, Inc. All rights reserved 20171102 Ver 4T Contents Overview... 3 Components of the Reporter... 3 Reporter Appliance... 3 Network Detective Application... 3 Diagnostic
Scheduling and E mailing Reports
 Scheduling and E mailing Reports Reports can be scheduled to run at specific times, run periodically, and increment date parameters. Report outputs can be e mailed to specific EAS users so that they can
Scheduling and E mailing Reports Reports can be scheduled to run at specific times, run periodically, and increment date parameters. Report outputs can be e mailed to specific EAS users so that they can
Auto-Notify Setup - Begin from Contacts (for Contacts/Searches Copied from Tempo/Fusion)
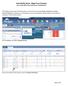 NOTE: Before going through the following steps, you should step through the Paragon Preferences and Client Connect Preferences to update your e-mail signature as well as choose default settings related
NOTE: Before going through the following steps, you should step through the Paragon Preferences and Client Connect Preferences to update your e-mail signature as well as choose default settings related
Setting up the Collaboration Center for a Client
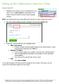 Setting up the Collaboration Center for a Client Save Search 1. Starting on the search you just completed for your client, click on Save Search located above the search criteria to open the Save Search
Setting up the Collaboration Center for a Client Save Search 1. Starting on the search you just completed for your client, click on Save Search located above the search criteria to open the Save Search
Meeting PCI DSS 3.2 Compliance with RiskSense Solutions
 Meeting PCI DSS 3.2 Compliance with Solutions Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 2018, Inc. What s Changing with PCI DSS? Summary of PCI Business
Meeting PCI DSS 3.2 Compliance with Solutions Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 2018, Inc. What s Changing with PCI DSS? Summary of PCI Business
User Guide. Version R95. English
 Software Management User Guide Version R95 English September 22, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Software Management User Guide Version R95 English September 22, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Continuously Discover and Eliminate Security Risk in Production Apps
 White Paper Security Continuously Discover and Eliminate Security Risk in Production Apps Table of Contents page Continuously Discover and Eliminate Security Risk in Production Apps... 1 Continuous Application
White Paper Security Continuously Discover and Eliminate Security Risk in Production Apps Table of Contents page Continuously Discover and Eliminate Security Risk in Production Apps... 1 Continuous Application
THE CRITICAL COMMUNICATIONS COMPANY CYBER SECURITY AS A SERVICE
 THE CRITICAL COMMUNICATIONS COMPANY CYBER SECURITY AS A SERVICE International Maritime Organization Regulations IMO has given shipowners and managers until 2021 to incorporate cyber risk management into
THE CRITICAL COMMUNICATIONS COMPANY CYBER SECURITY AS A SERVICE International Maritime Organization Regulations IMO has given shipowners and managers until 2021 to incorporate cyber risk management into
my energy. my usage. mymeter. Take control of your energy use with tools made just for you.
 my energy. my usage. mymeter. Take control of your energy use with tools made just for you. 1. New Users: Create your MyMeter Account Your prior user id and password from the Power of One Portal will not
my energy. my usage. mymeter. Take control of your energy use with tools made just for you. 1. New Users: Create your MyMeter Account Your prior user id and password from the Power of One Portal will not
Detector Service Delivery System (SDS) Version 3.0
 Detector Service Delivery System (SDS) Version 3.0 Detecting and Responding to IT Security Policy Violations Quick Start Guide 2018 RapidFire Tools, Inc. All rights reserved. V20180112 Contents Overview
Detector Service Delivery System (SDS) Version 3.0 Detecting and Responding to IT Security Policy Violations Quick Start Guide 2018 RapidFire Tools, Inc. All rights reserved. V20180112 Contents Overview
A Measurement Companion to the CIS Critical Security Controls (Version 6) October
 A Measurement Companion to the CIS Critical Security Controls (Version 6) October 2015 1 A Measurement Companion to the CIS Critical Security Controls (Version 6) Introduction... 3 Description... 4 CIS
A Measurement Companion to the CIS Critical Security Controls (Version 6) October 2015 1 A Measurement Companion to the CIS Critical Security Controls (Version 6) Introduction... 3 Description... 4 CIS
CASE STUDY. How 16 Penetration Tests Missed A Vulnerability Which Could ve Cost One Company Over $103 Million In PCI Fines
 CASE STUDY How 16 Penetration Tests Missed A Vulnerability Which Could ve Cost One Company Over $103 Million In PCI Fines IN A RECENT ENHANCED RED TEAM/ADVANCED PENETRATION TEST, OUR TEAM OF TESTERS UNCOVERED
CASE STUDY How 16 Penetration Tests Missed A Vulnerability Which Could ve Cost One Company Over $103 Million In PCI Fines IN A RECENT ENHANCED RED TEAM/ADVANCED PENETRATION TEST, OUR TEAM OF TESTERS UNCOVERED
Task Scheduling. Introduction to Task Scheduling. Configuring a Recurring Task
 The following topics explain how to schedule tasks: Introduction to, on page 1 Configuring a Recurring Task, on page 1 Scheduled Task Review, on page 17 Introduction to You can schedule many different
The following topics explain how to schedule tasks: Introduction to, on page 1 Configuring a Recurring Task, on page 1 Scheduled Task Review, on page 17 Introduction to You can schedule many different
VULNERABILITY ASSESSMENT: SYSTEM AND NETWORK PENETRATION TESTING. Presented by: John O. Adeika Student ID:
 VULNERABILITY ASSESSMENT: SYSTEM AND NETWORK PENETRATION TESTING. Presented by: John O. Adeika Student ID: 000205600 What is Penetration A penetration test, is a method of evaluating the security of a
VULNERABILITY ASSESSMENT: SYSTEM AND NETWORK PENETRATION TESTING. Presented by: John O. Adeika Student ID: 000205600 What is Penetration A penetration test, is a method of evaluating the security of a
Transforming Security from Defense in Depth to Comprehensive Security Assurance
 Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Case Study: The Evolution of EMC s Product Security Office. Dan Reddy, CISSP, CSSLP EMC Product Security Office
 Case Study: The Evolution of EMC s Product Security Office Dan Reddy, CISSP, CSSLP EMC Product Security Office 1 The Evolution of EMC Product Security 2000-2004 2005-2009 2010-Beyond External Drivers Hackers
Case Study: The Evolution of EMC s Product Security Office Dan Reddy, CISSP, CSSLP EMC Product Security Office 1 The Evolution of EMC Product Security 2000-2004 2005-2009 2010-Beyond External Drivers Hackers
Migrating Call Intelligence Settings for New CTC Clients
 Information Bulletin CDK Global, LLC. 1950 Hassell Road Hoffman Estates, IL 60169-6308 Migrating Call Intelligence Settings for New CTC Clients Converting to a New Phone System... 2 Overview of Important
Information Bulletin CDK Global, LLC. 1950 Hassell Road Hoffman Estates, IL 60169-6308 Migrating Call Intelligence Settings for New CTC Clients Converting to a New Phone System... 2 Overview of Important
Cyber Hygiene: Uncool but necessary. Automate Endpoint Patching to Mitigate Security Risks
 Cyber Hygiene: Uncool but necessary Automate Endpoint Patching to Mitigate Security Risks 1 Overview If you analyze any of the recent published attacks, two patterns emerge, 1. 80-90% of the attacks exploit
Cyber Hygiene: Uncool but necessary Automate Endpoint Patching to Mitigate Security Risks 1 Overview If you analyze any of the recent published attacks, two patterns emerge, 1. 80-90% of the attacks exploit
vcenter Support Assistant User's Guide
 vcenter Support Assistant 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
vcenter Support Assistant 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
IBM Proventia Management SiteProtector Sample Reports
 IBM Proventia Management SiteProtector Page Contents IBM Proventia Management SiteProtector Reporting Functionality Sample Report Index 2-25 Reports 26 Available SiteProtector Reports IBM Proventia Management
IBM Proventia Management SiteProtector Page Contents IBM Proventia Management SiteProtector Reporting Functionality Sample Report Index 2-25 Reports 26 Available SiteProtector Reports IBM Proventia Management
Standard: Vulnerability Management & Standard
 October 24, 2016 Page 1 Contents Revision History... 3 Executive Summary... 3 Introduction and Purpose... 4 Scope... 4 Standard... 4 Management of Technical Vulnerabilities... 4 Patching Application...
October 24, 2016 Page 1 Contents Revision History... 3 Executive Summary... 3 Introduction and Purpose... 4 Scope... 4 Standard... 4 Management of Technical Vulnerabilities... 4 Patching Application...
Security and Compliance Powered by the Cloud. Ben Friedman / Strategic Accounts Director /
 Security and Compliance Powered by the Cloud Ben Friedman / Strategic Accounts Director / bf@alertlogic.com Founded: 2002 Headquarters: Ownership: Houston, TX Privately Held Customers: 1,200 + Employees:
Security and Compliance Powered by the Cloud Ben Friedman / Strategic Accounts Director / bf@alertlogic.com Founded: 2002 Headquarters: Ownership: Houston, TX Privately Held Customers: 1,200 + Employees:
GDPR: Get Prepared! A Checklist for Implementing a Security and Event Management Tool. Contact. Ashley House, Ashley Road London N17 9LZ
 GDPR: Get Prepared! A Checklist for Implementing a Security and Event Management Tool Contact Ashley House, Ashley Road London N17 9LZ 0333 234 4288 info@networkiq.co.uk The General Data Privacy Regulation
GDPR: Get Prepared! A Checklist for Implementing a Security and Event Management Tool Contact Ashley House, Ashley Road London N17 9LZ 0333 234 4288 info@networkiq.co.uk The General Data Privacy Regulation
Application Security Use Cases. RASP, WAF, NGWAF, What The Hell is The Difference.
 Application Security Use Cases RASP, WAF, NGWAF, What The Hell is The Difference. Acronym Soup July 29, 2016 2 July 29, 2016 3 Definition of Terms WAF Web Application Firewall / waf / noun 1. An appliance,
Application Security Use Cases RASP, WAF, NGWAF, What The Hell is The Difference. Acronym Soup July 29, 2016 2 July 29, 2016 3 Definition of Terms WAF Web Application Firewall / waf / noun 1. An appliance,
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
EFFECTIVELY TARGETING ADVANCED THREATS. Terry Sangha Sales Engineer at Trustwave
 EFFECTIVELY TARGETING ADVANCED THREATS Terry Sangha Sales Engineer at Trustwave THE CHALLENGE PROTECTING YOUR ENVIRONMENT IS NOT GETTING EASIER ENDPOINT POINT OF SALE MOBILE VULNERABILITY MANAGEMENT CYBER
EFFECTIVELY TARGETING ADVANCED THREATS Terry Sangha Sales Engineer at Trustwave THE CHALLENGE PROTECTING YOUR ENVIRONMENT IS NOT GETTING EASIER ENDPOINT POINT OF SALE MOBILE VULNERABILITY MANAGEMENT CYBER
OPS Webportal User Guide - Reporting v.2.1
 OPS Webportal User Guide - Reporting v.2.1 Contents OPS Reporting... 3 OPS Web Portal... 4 Running Reports... 5 Report Navigation... 5 Group (Client) Selection... 6 Reporting Period... 7 Downloading the
OPS Webportal User Guide - Reporting v.2.1 Contents OPS Reporting... 3 OPS Web Portal... 4 Running Reports... 5 Report Navigation... 5 Group (Client) Selection... 6 Reporting Period... 7 Downloading the
vcenter Support Assistant User's Guide
 vcenter Support Assistant 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
vcenter Support Assistant 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
What is Penetration Testing?
 What is Penetration Testing? March 2016 Table of Contents What is Penetration Testing?... 3 Why Perform Penetration Testing?... 4 How Often Should You Perform Penetration Testing?... 4 How Can You Benefit
What is Penetration Testing? March 2016 Table of Contents What is Penetration Testing?... 3 Why Perform Penetration Testing?... 4 How Often Should You Perform Penetration Testing?... 4 How Can You Benefit
Managed Security Services - Automated Analysis, Threat Analyst Monitoring and Notification
 Service Description Managed Security Services - Automated Analysis, Threat Analyst Monitoring and Notification The services described herein are governed by the terms and conditions of the agreement specified
Service Description Managed Security Services - Automated Analysis, Threat Analyst Monitoring and Notification The services described herein are governed by the terms and conditions of the agreement specified
Quick Heal Mobile Security. Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
My Eddy Home App EDDY IQ
 My Eddy Home App The following steps show how to set-up and use your My Eddy Home App! EDDY IQ Quick and Easy Set-up 1. App Set-up Email. Once your Eddy installation is complete, you will receive an email
My Eddy Home App The following steps show how to set-up and use your My Eddy Home App! EDDY IQ Quick and Easy Set-up 1. App Set-up Email. Once your Eddy installation is complete, you will receive an email
HOW TO BUILD A SUCCESSFUL VULNERABILITY MANAGEMENT PROGRAM FOR MEDICAL DEVICES. Sarah Kennedy Robert Sloan
 HOW TO BUILD A SUCCESSFUL VULNERABILITY MANAGEMENT PROGRAM FOR MEDICAL DEVICES Sarah Kennedy Robert Sloan WHO WE ARE Sarah B.S. in Telecommunications Systems Management M.S. in Information Security CISSP
HOW TO BUILD A SUCCESSFUL VULNERABILITY MANAGEMENT PROGRAM FOR MEDICAL DEVICES Sarah Kennedy Robert Sloan WHO WE ARE Sarah B.S. in Telecommunications Systems Management M.S. in Information Security CISSP
CONTINUOUS VIGILANCE POLICY
 CONTINUOUS VIGILANCE POLICY Policy: Policy Owner: Continuous Vigilance CIO Change Management Original Implementation Date: 8/30/2017 Effectie Date: 8/30/2017 Reision Date: Approed By: NIST Cyber Security
CONTINUOUS VIGILANCE POLICY Policy: Policy Owner: Continuous Vigilance CIO Change Management Original Implementation Date: 8/30/2017 Effectie Date: 8/30/2017 Reision Date: Approed By: NIST Cyber Security
Tenable SecurityCenter Data Feeds for RSA Archer IT Security Vulnerability Program
 RSA ARCHER GRC Platform Implementation Guide Tenable SecurityCenter Data Feeds for RSA Archer IT Security Vulnerability Program Wesley Loeffler, RSA Engineering Last Modified:
RSA ARCHER GRC Platform Implementation Guide Tenable SecurityCenter Data Feeds for RSA Archer IT Security Vulnerability Program Wesley Loeffler, RSA Engineering Last Modified:
Nonprofit Donations Products
 Nonprofit Donations Products Fundraisers Guide Helping you get started with Fundraisers 01 02 03 04 05 06 Creating a Fundraiser Finding fundraisers for your organization How to access reports Accessing
Nonprofit Donations Products Fundraisers Guide Helping you get started with Fundraisers 01 02 03 04 05 06 Creating a Fundraiser Finding fundraisers for your organization How to access reports Accessing
Order Lifecycle Visibility (OLV) Supplier Alerts
 Order Lifecycle Visibility (OLV) Supplier Email Alerts November 2009 Summary of Getting Started Tasks 2 After you have Completed registration process for OLV via Trading Grid Assigned a Company Administrator
Order Lifecycle Visibility (OLV) Supplier Email Alerts November 2009 Summary of Getting Started Tasks 2 After you have Completed registration process for OLV via Trading Grid Assigned a Company Administrator
PCI Time-Based Requirements as a Starting Point for Business-As-Usual Process Monitoring
 PCI Time-Based Requirements as a Starting Point for Business-As-Usual Process Monitoring By Chip Ross February 1, 2018 In the Verizon Payment Security Report published August 31, 2017, there was an alarming
PCI Time-Based Requirements as a Starting Point for Business-As-Usual Process Monitoring By Chip Ross February 1, 2018 In the Verizon Payment Security Report published August 31, 2017, there was an alarming
ISO COMPLIANCE GUIDE. How Rapid7 Can Help You Achieve Compliance with ISO 27002
 ISO 27002 COMPLIANCE GUIDE How Rapid7 Can Help You Achieve Compliance with ISO 27002 A CONTENTS Introduction 2 Detailed Controls Mapping 3 About Rapid7 8 rapid7.com ISO 27002 Compliance Guide 1 INTRODUCTION
ISO 27002 COMPLIANCE GUIDE How Rapid7 Can Help You Achieve Compliance with ISO 27002 A CONTENTS Introduction 2 Detailed Controls Mapping 3 About Rapid7 8 rapid7.com ISO 27002 Compliance Guide 1 INTRODUCTION
FedRAMP Training - Continuous Monitoring (ConMon) Overview
 FedRAMP Training - Continuous Monitoring (ConMon) Overview 1. FedRAMP_Training_ConMon_v3_508 1.1 FedRAMP Continuous Monitoring Online Training Splash Screen Transcript Title of FedRAMP logo. Text
FedRAMP Training - Continuous Monitoring (ConMon) Overview 1. FedRAMP_Training_ConMon_v3_508 1.1 FedRAMP Continuous Monitoring Online Training Splash Screen Transcript Title of FedRAMP logo. Text
FedRAMP Plan of Action and Milestones (POA&M) Template Completion Guide. Version 1.2
 FedRAMP Plan of Action and Milestones (POA&M) Template Completion Guide Version 1.2 October 21, 2016 FedRAMP POA&M Template Completion Guide v1.1 September 1, 2015 Document Revision History Date Description
FedRAMP Plan of Action and Milestones (POA&M) Template Completion Guide Version 1.2 October 21, 2016 FedRAMP POA&M Template Completion Guide v1.1 September 1, 2015 Document Revision History Date Description
Concur Messaging: Reports
 Concur Messaging: Reports User Guide Proprietary Statement This document and any attached materials (including videos or other media) contain Concur Technologies, Inc. ( Concur ) proprietary information
Concur Messaging: Reports User Guide Proprietary Statement This document and any attached materials (including videos or other media) contain Concur Technologies, Inc. ( Concur ) proprietary information
Magento Extension User Guide BACKUP TO DROPBOX for Magento 2
 Magento Extension User Guide BACKUP TO DROPBOX for Magento 2 Table of contents 1. Key Features 1.1. Keeps Your Store Information Double Safe and Available 1.2. Manage Backup Frequency and Start Time 1.3.
Magento Extension User Guide BACKUP TO DROPBOX for Magento 2 Table of contents 1. Key Features 1.1. Keeps Your Store Information Double Safe and Available 1.2. Manage Backup Frequency and Start Time 1.3.
Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture
 February 2019 Challenging State of Vulnerability Management Today: Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture In the last two years, businesses and governments have seen data breaches
February 2019 Challenging State of Vulnerability Management Today: Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture In the last two years, businesses and governments have seen data breaches
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
ForeScout Extended Module for Qualys VM
 ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
Vulnerability Scanning Help Desk Ticket System
 Vulnerability Scanning Help Desk Ticket System - Ticket Management Ticket Management is a new subsystem designed to manage the process of solution of vulnerabilities. It allows a user to create new tickets
Vulnerability Scanning Help Desk Ticket System - Ticket Management Ticket Management is a new subsystem designed to manage the process of solution of vulnerabilities. It allows a user to create new tickets
Insurance Industry - PCI DSS
 Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services. Vanguard is the industry leader in z/os Mainframe Software to ensure enterprise compliance with the
Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services. Vanguard is the industry leader in z/os Mainframe Software to ensure enterprise compliance with the
VANGUARD WHITE PAPER VANGUARD INSURANCE INDUSTRY WHITEPAPER
 VANGUARD INSURANCE INDUSTRY WHITEPAPER Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to
VANGUARD INSURANCE INDUSTRY WHITEPAPER Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to
WHITE PAPERS. INSURANCE INDUSTRY (White Paper)
 (White Paper) Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to ensure enterprise compliance
(White Paper) Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to ensure enterprise compliance
Juniper Vendor Security Requirements
 Juniper Vendor Security Requirements INTRODUCTION This document describes measures and processes that the Vendor shall, at a minimum, implement and maintain in order to protect Juniper Data against risks
Juniper Vendor Security Requirements INTRODUCTION This document describes measures and processes that the Vendor shall, at a minimum, implement and maintain in order to protect Juniper Data against risks
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Machine-Based Penetration Testing
 Always in Control CyBot Suite Machine-Based Penetration Testing www.cronus-cyber.com - April 2016 CyBot PRODUCT SUITE Unique, patented Machine-based Penetration Testing Software with Global Attack Path
Always in Control CyBot Suite Machine-Based Penetration Testing www.cronus-cyber.com - April 2016 CyBot PRODUCT SUITE Unique, patented Machine-based Penetration Testing Software with Global Attack Path
IT SECURITY FOR NONPROFITS
 IT SECURITY FOR NONPROFITS COMMUNITY IT INNOVATORS PLAYBOOK April 2016 Community IT Innovators 1101 14th Street NW, Suite 830 Washington, DC 20005 The challenge for a nonprofit organization is to develop
IT SECURITY FOR NONPROFITS COMMUNITY IT INNOVATORS PLAYBOOK April 2016 Community IT Innovators 1101 14th Street NW, Suite 830 Washington, DC 20005 The challenge for a nonprofit organization is to develop
My Eddy Home App. The following steps show how to easily set up your My Eddy Home App!
 My Eddy Home App The following steps show how to easily set up your My Eddy Home App! 1 1. App Set-up Email. Once your Eddy installation is ready, you will receive an email from us with your login and
My Eddy Home App The following steps show how to easily set up your My Eddy Home App! 1 1. App Set-up Email. Once your Eddy installation is ready, you will receive an email from us with your login and
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
IBM Vulnerability Management Service
 Service Description 1. Service Overview IBM Vulnerability Management Service IBM Vulnerability Management Service (called VMS or Service ) is designed to provide a comprehensive, Web-driven vulnerability
Service Description 1. Service Overview IBM Vulnerability Management Service IBM Vulnerability Management Service (called VMS or Service ) is designed to provide a comprehensive, Web-driven vulnerability
Manage Contact Center, Agent Settings, and Scheduled Reports
 Manage Contact Center, Agent Settings, and Scheduled Reports As an administrator for the AT&T Collaborate service, you can create and manage company-wide settings for contact centers and their agents.
Manage Contact Center, Agent Settings, and Scheduled Reports As an administrator for the AT&T Collaborate service, you can create and manage company-wide settings for contact centers and their agents.
SAFETICA IMPLEMENTATION Quick Guide
 1 SAFETICA IMPLEMENTATION Quick Guide 2 INTRODUCTION... 3 DOWNLOADING SAFETICA... 3 CONFIGURATION PROCESS... 3 FIRST SAFETICA CONFIGURATION... 4 AUDITOR... 5 Functions settings... 5 Other tabs... 5 SUPERVISOR...
1 SAFETICA IMPLEMENTATION Quick Guide 2 INTRODUCTION... 3 DOWNLOADING SAFETICA... 3 CONFIGURATION PROCESS... 3 FIRST SAFETICA CONFIGURATION... 4 AUDITOR... 5 Functions settings... 5 Other tabs... 5 SUPERVISOR...
Express Monitoring 2019
 Express Monitoring 2019 WHY CHOOSE PT EXPRESS MONITORING PT Express Monitoring provides a quick evaluation of the current signaling network protection level. This service helps to discover critical vulnerabilities
Express Monitoring 2019 WHY CHOOSE PT EXPRESS MONITORING PT Express Monitoring provides a quick evaluation of the current signaling network protection level. This service helps to discover critical vulnerabilities
ORACLE MANAGED CLOUD SECURITY SERVICES - SERVICE DESCRIPTIONS. December 1, 2017
 ORACLE MANAGED CLOUD SECURITY SERVICES - SERVICE DESCRIPTIONS December 1, 2017 Table of Contents Oracle Managed Security Database Encryption Service for Oracle IaaS... 3 Oracle Managed Security Database
ORACLE MANAGED CLOUD SECURITY SERVICES - SERVICE DESCRIPTIONS December 1, 2017 Table of Contents Oracle Managed Security Database Encryption Service for Oracle IaaS... 3 Oracle Managed Security Database
The security challenge in a mobile world
 The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
Endpoint Security. powered by HEAT Software. Patch and Remediation Best Practice Guide. Version 8.5 Update 2
 Endpoint Security powered by HEAT Software Patch and Remediation Best Practice Guide Version 8.5 Update 2 Contents Introduction 3 Prepare Patch Infrastructure 5 Discover Assets 7 Install Agents 10 Create
Endpoint Security powered by HEAT Software Patch and Remediation Best Practice Guide Version 8.5 Update 2 Contents Introduction 3 Prepare Patch Infrastructure 5 Discover Assets 7 Install Agents 10 Create
SIEMLESS THREAT DETECTION FOR AWS
 SOLUTION OVERVIEW: ALERT LOGIC FOR AMAZON WEB SERVICES (AWS) SIEMLESS THREAT DETECTION FOR AWS Few things are as important to your business as maintaining the security of your sensitive data. Protecting
SOLUTION OVERVIEW: ALERT LOGIC FOR AMAZON WEB SERVICES (AWS) SIEMLESS THREAT DETECTION FOR AWS Few things are as important to your business as maintaining the security of your sensitive data. Protecting
Novell ZENworks 10 Patch Management SP3
 Reference AUTHORIZED DOCUMENTATION Novell ZENworks 10 Patch Management SP3 10.3 August 26, 2010 www.novell.com ZENworks 10 Patch Management Reference Legal Notices Novell, Inc. makes no representations
Reference AUTHORIZED DOCUMENTATION Novell ZENworks 10 Patch Management SP3 10.3 August 26, 2010 www.novell.com ZENworks 10 Patch Management Reference Legal Notices Novell, Inc. makes no representations
Machine-Based Penetration Testing
 Always in Control CyBot Suite Machine-Based Penetration Testing CyBot PRODUCT SUITE Unique, patented Machine-based Penetration Testing Software with Global Attack Path Scenarios (APS) product suite: CyBot
Always in Control CyBot Suite Machine-Based Penetration Testing CyBot PRODUCT SUITE Unique, patented Machine-based Penetration Testing Software with Global Attack Path Scenarios (APS) product suite: CyBot
Terms, Methodology, Preparation, Obstacles, and Pitfalls. Vulnerability Assessment Course
 Terms, Methodology, Preparation, Obstacles, and Pitfalls Vulnerability Assessment Course All materials are licensed under a Creative Commons Share Alike license. http://creativecommons.org/licenses/by-sa/3.0/
Terms, Methodology, Preparation, Obstacles, and Pitfalls Vulnerability Assessment Course All materials are licensed under a Creative Commons Share Alike license. http://creativecommons.org/licenses/by-sa/3.0/
Introduction. How Does it Work with Autodesk Vault? What is Microsoft Data Protection Manager (DPM)? autodesk vault
 Introduction What is Microsoft Data Protection Manager (DPM)? The Microsoft Data Protection Manager is a member of the Microsoft System Center family of management products. DPM provides continuous data
Introduction What is Microsoft Data Protection Manager (DPM)? The Microsoft Data Protection Manager is a member of the Microsoft System Center family of management products. DPM provides continuous data
VULNERABILITIES IN 2017 CODE ANALYSIS WEB APPLICATION AUTOMATED
 AUTOMATED CODE ANALYSIS WEB APPLICATION VULNERABILITIES IN 2017 CONTENTS Introduction...3 Testing methods and classification...3 1. Executive summary...4 2. How PT AI works...4 2.1. Verifying vulnerabilities...5
AUTOMATED CODE ANALYSIS WEB APPLICATION VULNERABILITIES IN 2017 CONTENTS Introduction...3 Testing methods and classification...3 1. Executive summary...4 2. How PT AI works...4 2.1. Verifying vulnerabilities...5
Dropout Detective - Advisor Alerts. Activating an Advisor Alert
 Dropout Detective automatically analyzes key performance indicators like grades, missing assignments, course participation, and other behaviors that take place in the online classroom. Advisor Alerts provides
Dropout Detective automatically analyzes key performance indicators like grades, missing assignments, course participation, and other behaviors that take place in the online classroom. Advisor Alerts provides
TRUE SECURITY-AS-A-SERVICE
 TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
Set Up & Navigate Your MUS Online Account
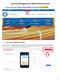 Set Up & Navigate Your MUS Online Account 1. Log on to the main website: www.musfiber.net and click on MY ACCOUNT 2. Click red box CREATE ACCOUNT 1 3. The system will offer several options to validate
Set Up & Navigate Your MUS Online Account 1. Log on to the main website: www.musfiber.net and click on MY ACCOUNT 2. Click red box CREATE ACCOUNT 1 3. The system will offer several options to validate
Threat Hunting in Modern Networks. David Biser
 Threat Hunting in Modern Networks David Biser What is Threat Hunting? The act of aggressively pursuing and eliminating cyber adversaries as early as possible in the Cyber Kill Chain. Why Perform Threat
Threat Hunting in Modern Networks David Biser What is Threat Hunting? The act of aggressively pursuing and eliminating cyber adversaries as early as possible in the Cyber Kill Chain. Why Perform Threat
n Explain penetration testing concepts n Explain vulnerability scanning concepts n Reconnaissance is the first step of performing a pen test
 Chapter Objectives n Explain penetration testing concepts n Explain vulnerability scanning concepts Chapter #4: Threats, Attacks, and Vulnerabilities Vulnerability Scanning and Penetration Testing 2 Penetration
Chapter Objectives n Explain penetration testing concepts n Explain vulnerability scanning concepts Chapter #4: Threats, Attacks, and Vulnerabilities Vulnerability Scanning and Penetration Testing 2 Penetration
FireMon Security manager
 FireMon Security manager Regain control of firewalls with comprehensive firewall management The enterprise network is a complex machine. New network segments, new hosts and zero-day vulnerabilities are
FireMon Security manager Regain control of firewalls with comprehensive firewall management The enterprise network is a complex machine. New network segments, new hosts and zero-day vulnerabilities are
Survey Results: Virtual Insecurity
 Best Practices SURVEY Survey Results: Virtual Insecurity May 2013 Executive Summary: Virtual Assets Could Bring Real Risk Virtualization technologies have reshaped how IT offers and delivers their services
Best Practices SURVEY Survey Results: Virtual Insecurity May 2013 Executive Summary: Virtual Assets Could Bring Real Risk Virtualization technologies have reshaped how IT offers and delivers their services
RBS OpenEMR Multisite Setup Improper Access Restriction Remote Code Execution of 5
 RBS-2017-001 OpenEMR Multisite Setup Improper Access Restriction Remote Code Execution 2018-03-22 1 of 5 Vendor / Product Information OpenEMR is a Free and Open Source electronic health records and medical
RBS-2017-001 OpenEMR Multisite Setup Improper Access Restriction Remote Code Execution 2018-03-22 1 of 5 Vendor / Product Information OpenEMR is a Free and Open Source electronic health records and medical
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
HIPAA RISK ADVISOR SAMPLE REPORT
 HIPAA RISK ADVISOR SAMPLE REPORT HIPAA Security Analysis Report The most tangible part of any annual security risk assessment is the final report of findings and recommendations. It s important to have
HIPAA RISK ADVISOR SAMPLE REPORT HIPAA Security Analysis Report The most tangible part of any annual security risk assessment is the final report of findings and recommendations. It s important to have
Ryan KS office thesee
 SERVERR and WORKSTATION REMOTE MANAGEMENT SERVICES Ryan Dental Systems Dental Computer Systems Support and Sales 303 2 nd Street, PO Box 194, Inland NE 68954 5506 SW 31stPh: 402-461-5575 Terrace Topeka
SERVERR and WORKSTATION REMOTE MANAGEMENT SERVICES Ryan Dental Systems Dental Computer Systems Support and Sales 303 2 nd Street, PO Box 194, Inland NE 68954 5506 SW 31stPh: 402-461-5575 Terrace Topeka
Continuous Security. Improve Web Application Security by using Continuous Security Scans
 Continuous Security Improve Web Application Security by using Continuous Security Scans 1 The world of software development has changed. Nowadays around 65% of software projects use agile development 1.
Continuous Security Improve Web Application Security by using Continuous Security Scans 1 The world of software development has changed. Nowadays around 65% of software projects use agile development 1.
SIEMLESS THREAT MANAGEMENT
 SOLUTION BRIEF: SIEMLESS THREAT MANAGEMENT SECURITY AND COMPLIANCE COVERAGE FOR APPLICATIONS IN ANY ENVIRONMENT Evolving threats, expanding compliance risks, and resource constraints require a new approach.
SOLUTION BRIEF: SIEMLESS THREAT MANAGEMENT SECURITY AND COMPLIANCE COVERAGE FOR APPLICATIONS IN ANY ENVIRONMENT Evolving threats, expanding compliance risks, and resource constraints require a new approach.
ForeScout ControlFabric TM Architecture
 ForeScout ControlFabric TM Architecture IMPROVE MULTI-VENDOR SOLUTION EFFECTIVENESS, RESPONSE AND WORKFLOW AUTOMATION THROUGH COLLABORATION WITH INDUSTRY-LEADING TECHNOLOGY PARTNERS. The Challenge 50%
ForeScout ControlFabric TM Architecture IMPROVE MULTI-VENDOR SOLUTION EFFECTIVENESS, RESPONSE AND WORKFLOW AUTOMATION THROUGH COLLABORATION WITH INDUSTRY-LEADING TECHNOLOGY PARTNERS. The Challenge 50%
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE
 ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
Data Breach Risk Scanning and Reporting
 Data Breach Risk Scanning and Reporting 2017. SolarWinds. All rights reserved. All product and company names herein may be trademarks of their respective owners. The information and content in this document
Data Breach Risk Scanning and Reporting 2017. SolarWinds. All rights reserved. All product and company names herein may be trademarks of their respective owners. The information and content in this document
IPLocks Vulnerability Assessment: A Database Assessment Solution
 IPLOCKS WHITE PAPER September 2005 IPLocks Vulnerability Assessment: A Database Assessment Solution 2665 North First Street, Suite 110 San Jose, CA 95134 Telephone: 408.383.7500 www.iplocks.com TABLE OF
IPLOCKS WHITE PAPER September 2005 IPLocks Vulnerability Assessment: A Database Assessment Solution 2665 North First Street, Suite 110 San Jose, CA 95134 Telephone: 408.383.7500 www.iplocks.com TABLE OF
FedRAMP JAB P-ATO Process TIMELINESS AND ACCURACY OF TESTING REQUIREMENTS. VERSION 1.0 October 20, 2016
 FedRAMP JAB P-ATO Process TIMELINESS AND ACCURACY OF TESTING REQUIREMENTS VERSION 1.0 October 20, 2016 MONTH 2015 Table of Contents 1. PURPOSE 3 2. BACKGROUND 3 3. TIMELINESS AND ACCURACY OF TESTING OVERVIEW
FedRAMP JAB P-ATO Process TIMELINESS AND ACCURACY OF TESTING REQUIREMENTS VERSION 1.0 October 20, 2016 MONTH 2015 Table of Contents 1. PURPOSE 3 2. BACKGROUND 3 3. TIMELINESS AND ACCURACY OF TESTING OVERVIEW
Security. ITM Platform
 Security ITM Platform Contents Contents... 0 1. SaaS and On-Demand Environments... 1 1.1. ITM Platform configuration modes... 1 1.2. Server... 1 1.3. Application and Database... 2 1.4. Domain... 3 1.5.
Security ITM Platform Contents Contents... 0 1. SaaS and On-Demand Environments... 1 1.1. ITM Platform configuration modes... 1 1.2. Server... 1 1.3. Application and Database... 2 1.4. Domain... 3 1.5.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
SECURITY PRACTICES OVERVIEW
 SECURITY PRACTICES OVERVIEW 2018 Helcim Inc. Copyright 2006-2018 Helcim Inc. All Rights Reserved. The Helcim name and logo are trademarks of Helcim Inc. P a g e 1 Our Security at a Glance About Helcim
SECURITY PRACTICES OVERVIEW 2018 Helcim Inc. Copyright 2006-2018 Helcim Inc. All Rights Reserved. The Helcim name and logo are trademarks of Helcim Inc. P a g e 1 Our Security at a Glance About Helcim
Admin Login Log. User Guide. Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9. Official Extension Page: Admin Login Log. User Guide: Admin Login Log Page 1
 Admin Login Log User Guide Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9 Official Extension Page: Admin Login Log User Guide: Admin Login Log Page 1 Table of contents: 1. Introduction.3 2.Extension Configuration..5
Admin Login Log User Guide Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9 Official Extension Page: Admin Login Log User Guide: Admin Login Log Page 1 Table of contents: 1. Introduction.3 2.Extension Configuration..5
Scheduled Reports Guide
 Scheduled Reports Guide Clarity Group Healthcare SafetyZone Portal Training Guide Copyright Clarity Group, Inc. 2019 Allow Users to Create and Manage Scheduled Reports Location: Administration User Maintenance
Scheduled Reports Guide Clarity Group Healthcare SafetyZone Portal Training Guide Copyright Clarity Group, Inc. 2019 Allow Users to Create and Manage Scheduled Reports Location: Administration User Maintenance
Intrusion prevention systems are an important part of protecting any organisation from constantly developing threats.
 Network IPS Overview Intrusion prevention systems are an important part of protecting any organisation from constantly developing threats. By using protocol recognition, identification, and traffic analysis
Network IPS Overview Intrusion prevention systems are an important part of protecting any organisation from constantly developing threats. By using protocol recognition, identification, and traffic analysis
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
SCOUT SUSPENSE TRACKER Version 10.0
 SCOUT SUSPENSE TRACKER Version 10.0 USER S MANUAL For Civilian Personnel Management Service (CPMS) HPC-COM LLC Help Desk 800-795-1902 Updated: February 2011 Table of Contents SCOUT Suspense Tracker V10.0
SCOUT SUSPENSE TRACKER Version 10.0 USER S MANUAL For Civilian Personnel Management Service (CPMS) HPC-COM LLC Help Desk 800-795-1902 Updated: February 2011 Table of Contents SCOUT Suspense Tracker V10.0
LOGmanager and PCI Data Security Standard v3.2 compliance
 LOGmanager and PCI Data Security Standard v3.2 compliance Whitepaper how deploying LOGmanager helps to maintain PCI DSS regulation requirements Many organizations struggle to understand what and where
LOGmanager and PCI Data Security Standard v3.2 compliance Whitepaper how deploying LOGmanager helps to maintain PCI DSS regulation requirements Many organizations struggle to understand what and where
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
