CHECK POINT TOTAL SECURITY APPLIANCES. Flexible Deployment. Centralized Management.
|
|
|
- Jeffry Park
- 6 years ago
- Views:
Transcription
1 CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to address virtually any security need. All Check Point appliances are built around a unified security architecture, enabling organizations to perform all aspects of security management via a single, unified console. The new Check Point Software Blade architecture adds new levels of flexibility, simplicity, and extensibility to Check Point appliances. This enables organizations of all sizes to tailor their network security infrastructure to meet their functional and performance needs with centralized management, simple deployment, and full extensibility. April 2009
2 UTM-1 Appliances All inclusive. All secured. UTM-1 appliances offer the ideal combination of proven security technologies and easy-to-use deployment and management features. With a full line of hardware-based solutions, Check Point UTM-1 appliances consolidate key security applications such as firewall, VPN, intrusion prevention, and antivirus and more into a single, easy-to-manage solution. UTM-1 Appliances are based on the Check Point Software Blade architecture that enables flexible and fast deployment of additional security capabilities, such as VoIP protections, without the addition of new hardware. UTM-1 appliances deliver a comprehensive set of security features including firewall, intrusion prevention, antivirus, anti-spyware, anti-spam, Web filtering, Web application security as well as secure site-to-site and remote access connectivity. UTM-1 Edge appliances deliver integrated firewall, intrusion prevention, VPN, and antivirus for branch offices of up to 100 users, ensuring small offices stay as secure as the corporate office. Benefits n Industry-leading application- and network-layer firewall n Site-to-site and remote-access VPNs n Gateway antivirus and anti-spyware n Intrusion prevention with type-based protections and security updates n Web security with URL filtering and integrated security for Web applications n security and anti-spam, including the Check Point six dimensions of comprehensive messaging security n Software Blade architecture for fast and flexible deployment of new security services UTM-1 Edge UTM UTM-1 appliances come in six models and UTM-1 Edge appliances come in four models that let organizations choose the right solution to meet price and performance requirements. UTM For more information:
3 Power-1 Appliances Security for high-performance environments Check Point Power-1 appliances enable organizations to maximize security in high-performance environments such as large campuses or data centers. They combine integrated firewall, IPSec VPN, and intrusion prevention with advanced acceleration technologies, delivering a high-performance security platform for multi-gbps environments. The Check Point Software Blade architecture enables flexible and fast deployment of additional security capabilities, such as VoIP protections and UTM functionality, on Power-1 appliances. Benefits n Ensures availability of business-critical applications with up to 25 Gbps throughput and intrusion prevention throughput up to 15 Gbps n Streamlines deployment of enterprise security for large offices and data centers n Provides comprehensive security that is extensible on demand to include SSL VPNs, Web security, URL filtering, antivirus, anti-spyware, and anti-spam n Simplifies administration with a single management console for all sites n Protects against emerging threats with optional blades for security services n Software Blade architecture for fast and flexible deployment of new security services Power-1 appliances come in five models Power , Power , Power , Power , and Power that let organizations choose the proper levels of performance and port density for their environments. Power Power Power For more information:
4 Check Point IP Appliances Flexible networking and performance options Proven for years in complex networking and performancedemanding environments, Check Point IP Appliances formerly Nokia appliances offer customers turnkey security functionality such as firewall, VPN, and intrusion prevention across a wide range of models. Optimized for Check Point Security Gateway software, the IP Appliances offer unsurpassed scalability, high performance, manageability, and best-in-class port density that reduces operational costs in complex, mission-critical security environments. Benefits n Security appliance combining hardware and software from Check Point n Scalable, modular, and configurable security architecture with multiple acceleration (ADP service modules) and interface options insures investment protection n Achieve high performance across a broad spectrum of traffic types n Enterprise-class high availability, scalability, and fault tolerance to insure network resiliency and business continuity n Carrier-grade serviceability and redundancy n Streamlined IT efficiency with advanced management tools for installation, configuration, and maintenance IP Appliances come in seven models that deliver security solutions from small offices to carrier-class enterprises. IP290 IP690 IP2450 Accelerated Data Path (ADP) for IP Appliances For more information:
5 VSX-1 Appliances Virtualized security The VSX-1 appliances are virtualized security gateways that enable the creation of hundreds of security systems on a single hardware platform, delivering deep cost savings and infrastructure consolidation. Based on the proven security of VPN-1 Power, VSX provides best-in-class firewall, VPN, URL filtering, and intrusion-prevention technology to multiple networks, securely connecting them to each other and shared resources such as the Internet and DMZs. All security systems, virtual and real, are centrally managed through Check Point SmartCenter or Provider-1 management consoles. Ideal for MSPs, VSX-1 becomes the ideal platform for new subscription revenue opportunities by delivering new security services easily and efficiently. Benefits n Unique and comprehensive virtualized security solution with firewall, VPN, IPS, and URL filtering n Consolidates from five to hundreds of security gateways on a single device, increasing device utilization and reducing power, space, and cooling n Linear scalability with performance up to 27 Gbps n Flexible deployment options including software and a full line of turnkey appliances n Single proven security management architecture VSX-1 appliances come in three models that allow organizations to choose the right solution for their performance and scalability needs. VSX VSX VSX For more information:
6 Check Point Integrated Appliance Solutions Integrated software and hardware from Check Point and IBM Check Point Integrated Appliance Solutions (IAS) provide organizations with the ultimate choice in appliances integrated software and hardware bundles customized to their exact specifications. These customized platforms enable them to provision security services based on exact corporate needs. Organizations can choose from Check Point Software Blades such as firewall, IPSec VPN, and intrusion prevention, and additional blades including UTM functionality. They can also chose to deploy Check Point s virtualized security gateway, VPN-1 Power VSX, as well as Provider-1 for management of large deployments with separate security domains. Check Point integrates the selected software onto an IBM System x server or IBM BladeCenter to provide a comprehensive solution that includes direct technical support from Check Point. Benefits n Provides a software/hardware combination trusted by the largest organizations in the world n Reduces complexity by ensuring compatibility of the latest certified components and servers n Increases flexibility for security services provisioning by allowing customers to choose from multiple Check Point solutions n Delivers scalable performance and port density based on customer needs n Protects against emerging threats with service-based Check Point Software Blades including IPS, Antivirus, Anti-Malware, and URL Filtering M series Integrated Appliance Solutions are predefined models that can be customized to meet specific needs. The M2 model delivers UTM functionality. The M6 and M8 models both provide maximum security for high-performance environments with integrated firewall, VPN, and intrusion prevention. IAS M8 For more information:
7 Appliance Specifications UTM-1 Edge UTM UTM UTM UTM UTM UTM Models Software Edition UTM-1 Edge X, UTM-1 Edge W, UTM-1 Edge X ADSL, UTM-1 Edge W ADSL Embedded NGX UTM UTM UTM UTM UTM UTM UTM UTM UTM UTM UTM UTM R65, R70 R65, R70 R65, R70 R65, R70 R65, R70 R65, R70 10/100 Ports /100/1000 Ports Firewall Throughput 190 Mbps 400 Mbps 600 Mbps 1.1 Gbps 2 Gbps 3 Gbps 4.5 Gbps VPN Throughput 35 Mbps 100 Mbps 100 Mbps 250 Mbps 250 Mbps 280 Mbps 1.1 Gbps Concurrent Sessions 8, , , , million 1.1 million 1.1 million IPS Throughput Mbps Mbps Mbps Mbps 1 1 Gbps 1 4 Gbps 1 Licensed Users 8/16/32/U Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited VLANs UTM Out of the Box Yes Yes Yes Yes Yes Yes Yes Security Acceleration No No No No No No Yes Multisite Management No Standalone Yes Yes Yes Yes Yes Storage - 80 GB 160 GB 160 GB 160 GB 160 GB 160 GB Enclosure Desktop Desktop 1U 1U 1U 1U 1U Dimensions (standard) 1.2 x 8 x 4.8 in x 5.7 x 1.6 in x 10 x 1.73 in x 10 x 1.73 in x 10 x 1.73 in x 15 x 1.73 in x 15 x 1.73 in. Dimensions (metric) 30 x 203 x 122mm 270 x 145 x 40mm 429 x x x x x 381 Weight 0.7kg (1.6 lbs) 1.6 kg (3.52 lbs) 3.7kg (8.1 lbs) 3.7kg (8.1 lbs) 3.7kg (8.1 lbs) 6.5kg (14.3 lbs) 6.5kg (14.3 lbs) Operating Environment Temperature: 5 to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m 3 Power Input Power Supply Spec (Max) 100/240V, 50/60Hz 18W 60W 65W 65W 65W 250W 250W 1 Test based on real-world traffic blend using the default profile 2 Maximum of 256 VLANs per interface 3 UTM-1 Edge operating environment: Temperature: 0º to 40º C, Humidity: 10% 90% non-condensing, Altitude: 4500m (15,000ft )
8 Appliance Specifications Power Power Power Series IAS 1 M2 IAS 1 M6 IAS 1 M8 Software Edition R65, R70 R65, R70 R70 R70 R70 R65, R70 R65, R70 R65, R70 10/100/1000 Ports 10/14 14/18 14/18 14/18 14/18 4/10 10/10 14/18 Firewall Throughput 2 9 Gbps 16 Gbps 15 Gbps 20 Gbps 25 Gbps 4.5 Gbps 8 Gbps 12 Gbps VPN Throughput Gbps 3.7 Gbps 3.7 Gbps 4 Gbps 4.5 Gbps 1.1 Gbps 2.4 Gbps 3.5 Gbps Concurrent Sessions 1.2 million 1.2 million 1.2 million 1.2 million 1.2 million 1.1 million 1.2 million 1.2 million IPS Throughput Gbps 3 10 Gbps 3 10 Gbps 3 12 Gbps 3 15 Gbps 3 4 Gbps Gbps Gbps 3 Licensed Users Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited VLANs UTM Out of the Box Optional Optional Optional Optional Optional Yes Optional Optional Security Acceleration Yes Yes Yes Yes Yes Optional Yes Yes Integrated Multigateway Management Optional Optional Optional Storage 160 GB 2 x 160 GB 2 x 250 GB 2 x 250 GB 2 x 250 GB 2 x 73 GB 2 x 73 GB 2 x 73 GB Enclosure 2U 2U 2U 2U 2U 1U 1U 2U Dimensions (standard) Dimensions (metric) Weight 17 x x kg (31.9 lbs) 17 x x kg (36.3 lbs) 17 x x kg (51.6 lbs) 17 x x kg (51.6 lbs) 17 x x kg (51.6 lbs) 17.3 x 27.5 x 1.75 in. 440 x kg (35.5 lbs) 17.3 x 27.5 x 1.75 in. 443 x kg (35.5 lbs) Operating Environment Temperature: 5 to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m Power Input 100/240V, 50/60Hz x 27.5 x 3.36 in. 444 x 698 x 84.8mm 26.1kg (57.5 lbs) Power Supply Spec (Max) 250W 400W 500W 500W 500W 350W 350W 835W 1 IAS = Integrated Appliance Solutions 2 Performance data represents the maximum capabilities of the systems as measured under optimal testing conditions. Deployment and policy considerations may impact performance results. 3 Test based on real-world traffic blend using the default profile 4 Maximum of 256 VLANs per interface 5 Redundant power supply
9 Appliance Specifications IP150 IP290 IP390 IP560 IP690 IP1280 IP /100/1000 Ports 4 6/8 4/8 4/12 4/16 4/28 4/32 10 GbE Ports / / /23.6 Firewall Throughput 550 Mbps 1.5 Gbps 3.0 Gbps 6.3/9.5 Gbps 2 Gbps 2 Gbps 2 Gbps 2 VPN Throughput 76 Mbps 1.0 Gbps 677 Mbps 1.7/3.3 Gbps 2 1.4/ 3.3 Gbps 2 1.9/8.3 Gbps 2 1.9/8.3 Gbps 2 Concurrent Sessions 360, million 1.1 million 1.1 million 1.1 million 1.1 million 1.1 million VLANs ADP Module Optional Optional Optional Optional VPN Acceleration Optional Optional Included Included Included Included Included Storage 40 GB 40 GB 80 GB 80 GB 80 GB 80 GB 80 GB Disk-Based or Flash Disk Disk or Flash Disk or Flash Disk or Flash Disk or Flash Disk or Flash Disk or Flash Enclosure 1U 1U/half rack 1U 1U 1U 2U 2U Dimensions (standard) Dimensions (metric) Weight 16.8 x 10 x 1.69 in. 43 x 254 x 43mm 4.76kg (10.5 lbs) 8.52 x 18 x 1.71 in. 216 x kg (11.25 lbs) 17 x 16 x 1.71 in. 432 x kg (17.0 lbs) x 22 x 1.71 in. 438 x kg (26.1 lbs) x 24 x 1.71 in. 438 x kg (27.3 lbs) x x kg (43.2 lbs) Operating Environment Temperature: 5 to 40 C 4, Humidity: 10% 85% non-condensing, Altitude: 2,500m x x kg (45.35 lbs) Power Input Power Supply Spec (Max) 100/240V, 50/60Hz 180W 133W 150W 225W 250W 700W 700W DC Power Supply Optional Optional Compliance Safety: UL , First Edition: 2003, CAN/CSAC22.2, No 60950:2000, IEC : 2001, EN :2001+A11 with Japanese National Deviations; Emission Compliance: FCC Part 15, Subpart B, Class A, EN50024,EN55022A: 1998, CISPR 22 Class A: 1985, EN , EN ; Immunity: EN55024: Optional 2 Performance without ADP/with ADP 3 Maximum of 256 VLANs per interface 4 IP390 can go to 50 C
10 Appliance Specifications VSX VSX VSX Software Edition VSX NGX R65 VSX NGX R65 VSX NGX R65 10/100/1000 Ports 10 14/18 28/36 Firewall Throughput 4.5 Gbps 13.5 Gpbs 27 Gpbs VPN Throughput 1.1 Gbps 3.5 Gbps 7 Gpbs Concurrent Sessions 1 million 1.1 million 1.8 million Licensed Users Unlimited Unlimited Unlimited VLANs Virtual Systems (included/capacity) 5/10 10/150 10/150 UTM Out of the Box Optional Optional Optional Security Acceleration Yes Yes Yes Multisite Management Optional 1 Optional 1 Optional 1 Storage 160 GB 2 x 160 GB 4 x 160 GB Enclosure 1U 2U 4U Dimensions (standard) 17.4 x 15 x 1.73 in. 17 x x 20 x 7 in. Dimensions (metric) 443 x x x 509.5x 176mm Weight 6.5kg (14.3 lbs) 16.5 kg (36.3 lbs) 33 kg (72.6 lbs) Operating Environment Temperature: 5 to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m Power Input 100/240V, 50/60Hz Power Supply Spec (Max) 65W 250W 500W 1 Management server resides on separate server
11 Contact Check Point now to discuss your Total Security appliances: By phone in the US: option 5 or contact check point Worldwide Headquarters 5 Ha Solelim Street, Tel Aviv 67897, Israel Tel: Fax: info@checkpoint.com U.S. Headquarters 800 Bridge Parkway, Redwood City, CA Tel: ; Fax: Check Point Software Technologies Ltd. All rights reserved. Check Point, AlertAdvisor, Application Intelligence, Check Point Endpoint Security, Check Point Endpoint Security On Demand, Check Point Express, Check Point Express CI, the Check Point logo, ClusterXL, Confidence Indexing, ConnectControl, Connectra, Connectra Accelerator Card, Cooperative Enforcement, Cooperative Security Alliance, CoreXL, CoSa, DefenseNet, Dynamic Shielding Architecture, Eventia, Eventia Analyzer, Eventia Reporter, Eventia Suite, FireWall-1, FireWall-1 GX, FireWall-1 SecureServer, FloodGate-1, Full Disk Encryption, Hacker ID, Hybrid Detection Engine, IMsecure, INSPECT, INSPECT XL, Integrity, Integrity Clientless Security, Integrity SecureClient, InterSpect, IPS-1, IQ Engine, MailSafe, NG, NGX, Open Security Extension, OPSEC, OSFirewall, Pointsec, Pointsec Mobile, Pointsec PC, Pointsec Protector, Policy Lifecycle Management,Power-1, Provider-1, PureAdvantage, PURE Security, the puresecurity logo, Safe@Home, Safe@Office, SecureClient, SecureClient Mobile, SecureKnowledge, SecurePlatform, SecurePlatform Pro, SecuRemote, SecureServer, SecureUpdate, SecureXL, SecureXL Turbocard, Security Management Portal, Sentivist, SiteManager-1, Smart-1, SmartCenter, SmartCenter Express, SmartCenter Power, SmartCenter Pro, SmartCenter UTM, SmartConsole, SmartDashboard, SmartDefense, SmartDefense Advisor, Smarter Security, SmartLSM, SmartMap, SmartPortal, SmartProvisioning, SmartUpdate, SmartView, SmartView Monitor, SmartView Reporter, SmartView Status, SmartView Tracker, SMP, SMP On-Demand, SofaWare, SSL Network Extender, Stateful Clustering, Total Security, the totalsecurity logo, TrueVector, Turbocard, UAM, UserAuthority, User-to-Address Mapping, UTM-1, UTM-1 Edge, UTM-1 Edge Industrial, UTM-1 Total Security, VPN-1, VPN-1 Accelerator Card, VPN-1 Edge, VPN-1 Express, VPN-1 Express CI, VPN-1 Power, VPN-1 Power Multi-core, VPN-1 Power VSX, VPN-1 Pro, VPN-1 SecureClient, VPN-1 SecuRemote, VPN-1 SecureServer, VPN-1 UTM, VPN-1 UTM Edge, VPN-1 VSX, VSX-1, Web Intelligence, ZoneAlarm, ZoneAlarm Anti-Spyware, ZoneAlarm Antivirus, ZoneAlarm ForceField, ZoneAlarm Internet Security Suite, ZoneAlarm Pro, ZoneAlarm Secure Wireless Router, Zone Labs, and the Zone Labs logo are trademarks or registered trademarks of Check Point Software Technologies Ltd. or its affiliates. ZoneAlarm is a Check Point Software Technologies, Inc. Company. All other product names mentioned herein are trademarks or registered trademarks of their respective owners. The products described in this document are protected by U.S. Patent No. 5,606,668, 5,835,726, 5,987,611, 6,496,935, 6,873,988, 6,850,943, and 7,165,076 and may be protected by other U.S. Patents, foreign patents, or pending applications. April 21, 2009
OpenChoice Flexible Deployment. Centralized Management.
 CHECK POINT APPLIANCE ECOSYSTEM OpenChoice Flexible Deployment. Centralized Management. Check Point provides customers with the greatest choice for deploying our award-winning security solutions. Customers
CHECK POINT APPLIANCE ECOSYSTEM OpenChoice Flexible Deployment. Centralized Management. Check Point provides customers with the greatest choice for deploying our award-winning security solutions. Customers
Solution Brief. Integrated IP Appliances (formerly Nokia): Top Reasons to Migrate
 Solution Brief Integrated IP Appliances (formerly Nokia): Top Reasons to Migrate Executive summary As the next phase in the Check Point acquisition of the Nokia security appliance business, Check Point
Solution Brief Integrated IP Appliances (formerly Nokia): Top Reasons to Migrate Executive summary As the next phase in the Check Point acquisition of the Nokia security appliance business, Check Point
Appliance Comparison Chart
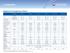 Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
CHECK POINT SECURITY APPLIANCES
 CHECK POINT SECURITY APPLIANCES Table of Contents Introduction 1 UTM-1 Appliances 2 Series 80 Appliance 3 Power-1 Appliances 4 IP Appliances 5 VSX-1 Appliances 6 DLP-1 Appliances 7 Smart-1 8 Smart-1 SmartEvent
CHECK POINT SECURITY APPLIANCES Table of Contents Introduction 1 UTM-1 Appliances 2 Series 80 Appliance 3 Power-1 Appliances 4 IP Appliances 5 VSX-1 Appliances 6 DLP-1 Appliances 7 Smart-1 8 Smart-1 SmartEvent
The New Face of Intrusion Prevention. Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price
 The New Face of Intrusion Prevention Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price Contents Better than the Best of Both Worlds 3 Best Protection
The New Face of Intrusion Prevention Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price Contents Better than the Best of Both Worlds 3 Best Protection
The New Face of Intrusion Prevention. Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price
 Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price Contents Better than the Best of Both Worlds 3 Best Protection 3 Best Total Threat Control 3 Reduced
Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price Contents Better than the Best of Both Worlds 3 Best Protection 3 Best Total Threat Control 3 Reduced
SECURITY APPLIANCES
 CHECK POINT SECURITY APPLIANCES www.checkpoint.com Table of Contents Introduction 1 Check Point GAiA The New Unified Security Operating System 2 About SecurityPower 3 Power-1 Appliances 4 IP Appliances
CHECK POINT SECURITY APPLIANCES www.checkpoint.com Table of Contents Introduction 1 Check Point GAiA The New Unified Security Operating System 2 About SecurityPower 3 Power-1 Appliances 4 IP Appliances
T: +44 (0) F: +44 (0) E: W:
 T: +44 (0) 1483-227600 F: +44 (0) 1483-227700 E: info@wickhill.co.uk W: www.wickhill.com Wick Hill Ltd. River Court, Albert Drive, Woking, Surrey, GU21 5RP Data Sheet Edge Wireless Secure wireless connectivity
T: +44 (0) 1483-227600 F: +44 (0) 1483-227700 E: info@wickhill.co.uk W: www.wickhill.com Wick Hill Ltd. River Court, Albert Drive, Woking, Surrey, GU21 5RP Data Sheet Edge Wireless Secure wireless connectivity
Endpoint Security. Administrator Guide Version NGX 7.0 GA
 Endpoint Security Administrator Guide Version NGX 7.0 GA January 9, 2008 2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Endpoint Security Administrator Guide Version NGX 7.0 GA January 9, 2008 2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Endpoint Security. Gateway Integration Guide R72
 Endpoint Security Gateway Integration Guide R72 July 21, 2009 2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
Endpoint Security Gateway Integration Guide R72 July 21, 2009 2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
VPN-1 Power VSX. Administration Guide NGX Scalability Pack
 VPN-1 Power VSX Administration Guide NGX Scalability Pack 701171 December 21, 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
VPN-1 Power VSX Administration Guide NGX Scalability Pack 701171 December 21, 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Unified Threat Management from Check Point
 puresecurity Unified Threat Management from Check Point The security you need. The simplicity you want. Unified Threat Management from Check Point Contents Introduction 3 Complexity of the security problem
puresecurity Unified Threat Management from Check Point The security you need. The simplicity you want. Unified Threat Management from Check Point Contents Introduction 3 Complexity of the security problem
Defending Small and Medium Sized Businesses with Cloud-Managed Security
 Defending Small and Medium Sized Businesses with Cloud-Managed Security Contents Introduction 3 Social Networking Could Mean Compromised Networks 4 Blended Threats More Blended than Ever 5 The Cloud Revolution
Defending Small and Medium Sized Businesses with Cloud-Managed Security Contents Introduction 3 Social Networking Could Mean Compromised Networks 4 Blended Threats More Blended than Ever 5 The Cloud Revolution
Provider-1/SiteManager-1. Version NGX R62
 Provider-1/SiteManager-1 Version NGX R62 December 27, 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
Provider-1/SiteManager-1 Version NGX R62 December 27, 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
SmartCenter. Version NGX R61
 SmartCenter Version NGX R61 701676 March 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under
SmartCenter Version NGX R61 701676 March 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under
Software Blades R7x. CC Evaluated Configuration Administration Guide
 Software Blades R7x CC Evaluated Configuration Administration Guide March 2012 2003-2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Software Blades R7x CC Evaluated Configuration Administration Guide March 2012 2003-2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Installation and Administration Guide
 Integrity Document Library Installation and Administration Guide Installing and using Integrity Agent for Linux 1-0277-0650-2006-03-09 Smarter Securi- Editor's Notes: 2006 Check Point Software Technologies
Integrity Document Library Installation and Administration Guide Installing and using Integrity Agent for Linux 1-0277-0650-2006-03-09 Smarter Securi- Editor's Notes: 2006 Check Point Software Technologies
IPS-1 Robust and accurate intrusion prevention
 Security Check Point security solutions are the marketleading choice for securing the infrastructure. IPS-1 Robust and accurate intrusion prevention Today s s operate in an environment that is ever changing,
Security Check Point security solutions are the marketleading choice for securing the infrastructure. IPS-1 Robust and accurate intrusion prevention Today s s operate in an environment that is ever changing,
Virtualized Network Security with
 White Paper Virtualized Network Security with A VPN-1 better approach Power to securing VSX networks Check Point protects every part of your network perimeter, internal, Web to keep your information resources
White Paper Virtualized Network Security with A VPN-1 better approach Power to securing VSX networks Check Point protects every part of your network perimeter, internal, Web to keep your information resources
Eventia Analyzer. Administration Guide Version NGX R63. December 2006
 Eventia Analyzer TM Administration Guide Version NGX R63 December 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Eventia Analyzer TM Administration Guide Version NGX R63 December 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Securing Browsers to Protect Endpoints and Enterprises from Web-based Attacks
 Securing Browsers to Protect Endpoints and Enterprises from Web-based Attacks Contents Introduction 3 Problem Statement: Web Usage Brings Huge Risks 3 Hackers Now Seek Profits, Not Glory 4 Why Traditional
Securing Browsers to Protect Endpoints and Enterprises from Web-based Attacks Contents Introduction 3 Problem Statement: Web Usage Brings Huge Risks 3 Hackers Now Seek Profits, Not Glory 4 Why Traditional
Pointsec Protector. Administrator s Guide
 Pointsec Protector Administrator s Guide Version 4.91, C May 2009 2003-2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Pointsec Protector Administrator s Guide Version 4.91, C May 2009 2003-2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point Appliance
 Datasheet: Check Point 12600 Appliance 12600 Datacenter-grade security appliance (1861 SPU/30Gbps) for superior multi Software Blades performance Check Point 12600 Appliance Today the enterprise gateway
Datasheet: Check Point 12600 Appliance 12600 Datacenter-grade security appliance (1861 SPU/30Gbps) for superior multi Software Blades performance Check Point 12600 Appliance Today the enterprise gateway
Check Point softwareblades Secure. Flexible. Simple
 Check Point softwareblades Secure. Flexible. Simple Ari Tarvainen Country Manager Baltic & Finland Agenda Who are we? The security challenge Introducing Software Blades Software Blades Offering Summary
Check Point softwareblades Secure. Flexible. Simple Ari Tarvainen Country Manager Baltic & Finland Agenda Who are we? The security challenge Introducing Software Blades Software Blades Offering Summary
CHECK POINT AND SECURITY SYSTEMS
 CHECK POINT 41000 AND 61000 SECURITY SYSTEMS SCALABLE PERFORMANCE FOR ADVANCED SECURITY Key features Scalable security solution from 3,200 up to 33,000 SecurityPower Units High raw firewall performance
CHECK POINT 41000 AND 61000 SECURITY SYSTEMS SCALABLE PERFORMANCE FOR ADVANCED SECURITY Key features Scalable security solution from 3,200 up to 33,000 SecurityPower Units High raw firewall performance
Check Point 1100 Appliances Frequently Asked Questions
 CHECK POINT SOFTWARE TECHNOLOGIES Check Point 1100 Appliances Frequently Asked Questions Table of Contents Overview:... 2 Ordering Information:... 3 Technology:... 4 Hardware:... 6 Performance:... 6 Updated
CHECK POINT SOFTWARE TECHNOLOGIES Check Point 1100 Appliances Frequently Asked Questions Table of Contents Overview:... 2 Ordering Information:... 3 Technology:... 4 Hardware:... 6 Performance:... 6 Updated
Cisco SR 520-T1 Secure Router
 Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Check Point Appliance
 Datasheet: Check Point 12200 Appliance 12200 Datacenter-grade security appliance (738 SPU/15Gbps) with optional redundancy Check Point 12200 Appliance Today the enterprise gateway is more than a firewall.
Datasheet: Check Point 12200 Appliance 12200 Datacenter-grade security appliance (738 SPU/15Gbps) with optional redundancy Check Point 12200 Appliance Today the enterprise gateway is more than a firewall.
Cisco NAC Network Module for Integrated Services Routers
 Cisco NAC Network Module for Integrated Services Routers The Cisco NAC Network Module for Integrated Services Routers (NME-NAC-K9) brings the feature-rich Cisco NAC Appliance Server capabilities to Cisco
Cisco NAC Network Module for Integrated Services Routers The Cisco NAC Network Module for Integrated Services Routers (NME-NAC-K9) brings the feature-rich Cisco NAC Appliance Server capabilities to Cisco
Check Point 4400 Appliance
 Datasheet: Check Point 4400 Appliance 4400 Enterprise-grade security appliance Check Point 4400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 4400 Appliance 4400 Enterprise-grade security appliance Check Point 4400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Cisco ASA 5500 Series IPS Solution
 Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
Security Quick Sales Guide
 Security Quick Sales Guide Security Quick Finder Product/Segment Model 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 50 ~ 75 PC Users USG 300 Unified Security Gateway 25 ~ 50 PC Users USG 200
Security Quick Sales Guide Security Quick Finder Product/Segment Model 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 50 ~ 75 PC Users USG 300 Unified Security Gateway 25 ~ 50 PC Users USG 200
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
The Cisco ASA 5500 Series Adaptive Security Appliances
 Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Check Point Virtual Systems & Identity Awareness
 Check Point Virtual Systems & Identity Awareness Jason Card, Senior Security Consultant, CISSP card@avantec.ch Agenda Check Point Virtual Systems Private Cloud Simplify Security Overview Identity Awareness
Check Point Virtual Systems & Identity Awareness Jason Card, Senior Security Consultant, CISSP card@avantec.ch Agenda Check Point Virtual Systems Private Cloud Simplify Security Overview Identity Awareness
Appliance Comparison Chart
 Security Gateway Appliances 300 300 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 340 45 600 950 750 400 Firewall (Gbps)..
Security Gateway Appliances 300 300 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 340 45 600 950 750 400 Firewall (Gbps)..
Check Point Appliance
 Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance (2900 SPU/0 Gbps ) with high port density, low latency and acceleration options Check Point 2400 Appliance Today s firewall
Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance (2900 SPU/0 Gbps ) with high port density, low latency and acceleration options Check Point 2400 Appliance Today s firewall
The SonicWALL PRO Series
 The SonicWALL PRO Series NETWORK SECURITY Dynamic Multi-function Network Security Appliances Powerful re-assembly free deep packet inspection engine Real-time gateway anti-virus, anti-spyware, anti-spam
The SonicWALL PRO Series NETWORK SECURITY Dynamic Multi-function Network Security Appliances Powerful re-assembly free deep packet inspection engine Real-time gateway anti-virus, anti-spyware, anti-spam
Future-ready security for small and mid-size enterprises
 First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
Appliance Comparison Chart
 Security Gateway Appliances 00 00 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 40 45 600 950 750 400 Firewall (Gbps)..
Security Gateway Appliances 00 00 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 40 45 600 950 750 400 Firewall (Gbps)..
Cisco ASA 5500 Series Adaptive Security Appliances
 Data Sheet Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, market-leading security services for small
Data Sheet Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, market-leading security services for small
Cisco ACE30 Application Control Engine Module
 Data Sheet Cisco ACE30 Application Control Engine Module Product Overview The Cisco ACE30 Application Control Engine Module (Figure 1) belongs to the Cisco ACE family of application switches, which deliver
Data Sheet Cisco ACE30 Application Control Engine Module Product Overview The Cisco ACE30 Application Control Engine Module (Figure 1) belongs to the Cisco ACE family of application switches, which deliver
Check Point Appliance
 Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Check Point licensing models. A few words about myself. Agenda. or oops, they did it again
 Check Point licensing models or oops, they did it again A few words about myself Dimension Data Switzerland, Senior Security Consultant CCMA 0019 Before that: 8 years with Check Point Israel Last 2 years
Check Point licensing models or oops, they did it again A few words about myself Dimension Data Switzerland, Senior Security Consultant CCMA 0019 Before that: 8 years with Check Point Israel Last 2 years
Cisco 3900 Series Router Datasheet
 Cisco 3900 Series Router Datasheet CONTENT Overview... 2 Appearance... 2 Key Features and Benefits... 3 Modularity Features and Benefits... 5 Product Specifications... 7 Basic Ordering Information... 12
Cisco 3900 Series Router Datasheet CONTENT Overview... 2 Appearance... 2 Key Features and Benefits... 3 Modularity Features and Benefits... 5 Product Specifications... 7 Basic Ordering Information... 12
ASA5525-FPWR-K9 Datasheet. Overview. Check its price: Click Here. Quick Specs
 ASA5525-FPWR-K9 Datasheet Check its price: Click Here Overview Cisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-
ASA5525-FPWR-K9 Datasheet Check its price: Click Here Overview Cisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-
Security Gateway Virtual Edition
 Security Gateway Virtual Edition R71 Release Notes 9 February 2012 Classification: [Restricted] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are
Security Gateway Virtual Edition R71 Release Notes 9 February 2012 Classification: [Restricted] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are
Check Point Appliance
 Datasheet: Check Point 2700 Appliance 2700 Datacenter-grade security appliance Check Point 2700 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Datasheet: Check Point 2700 Appliance 2700 Datacenter-grade security appliance Check Point 2700 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Seqrite TERMINATOR (UTM) Unified Threat Management Solution.
 Unified Threat Management Solution TERMINATOR Introduction Seqrite TERMINATOR is a high-performance, easy-to-use Unified Threat Management solution for small and mid-size enterprises. It is a robust solution
Unified Threat Management Solution TERMINATOR Introduction Seqrite TERMINATOR is a high-performance, easy-to-use Unified Threat Management solution for small and mid-size enterprises. It is a robust solution
Appliance Comparison Chart
 Security Gateway Appliances 3200 5200 5400 5600 5800 Branch Office Small Enterprise Mid-Size Enterprise Production Performance (Real-World Traffic Blend) Security 250 425 600 950 750 Firewall (Gbps) 2.
Security Gateway Appliances 3200 5200 5400 5600 5800 Branch Office Small Enterprise Mid-Size Enterprise Production Performance (Real-World Traffic Blend) Security 250 425 600 950 750 Firewall (Gbps) 2.
CHECK POINT NEXT GENERATION SECURITY GATEWAY FOR THE DATACENTER
 CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY FOR THE DATACENTER CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY Data center grade security, performance and reliability Product Benefits High performance
CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY FOR THE DATACENTER CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY Data center grade security, performance and reliability Product Benefits High performance
R75.40VS. Release Notes. 20 January Protected
 R75.40VS Release Notes 20 January 2014 Protected 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under
R75.40VS Release Notes 20 January 2014 Protected 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under
SECURITY FOR SMALL BUSINESSES
 SECURITY FOR SMALL BUSINESSES 2017 UNCOMPROMISING PERFORMANCE A common problem with firewalls used by small businesses has to do with hardware performance. Most often, vendor-stated bandwidth claims fall
SECURITY FOR SMALL BUSINESSES 2017 UNCOMPROMISING PERFORMANCE A common problem with firewalls used by small businesses has to do with hardware performance. Most often, vendor-stated bandwidth claims fall
Connectra Virtual Appliance Evaluation Guide
 Connectra Virtual Appliance Evaluation Guide This document is intended for users who are new to Check Point products and would like to evaluate and review Connectra Virtual Appliance. We recommend reading
Connectra Virtual Appliance Evaluation Guide This document is intended for users who are new to Check Point products and would like to evaluate and review Connectra Virtual Appliance. We recommend reading
Check Point for Nokia IPSO Getting Started Guide. Check Point NGX R62 Nokia IPSO 3.9, 4.1 and 4.2
 Check Point for Nokia IPSO Getting Started Guide Check Point NGX R62 Nokia IPSO 3.9, 4.1 and 4.2 Part No. N450000362 Rev 001 Published January 2007 COPYRIGHT 2007 Nokia. All rights reserved. Rights reserved
Check Point for Nokia IPSO Getting Started Guide Check Point NGX R62 Nokia IPSO 3.9, 4.1 and 4.2 Part No. N450000362 Rev 001 Published January 2007 COPYRIGHT 2007 Nokia. All rights reserved. Rights reserved
N-Dimension n-platform 340S Unified Threat Management System
 N-Dimension n-platform 340S Unified Threat Management System Firewall Router Site-to-Site VPN Remote-Access VPN Serial SCADA VPN Proxy Anti-virus SCADA IDS Port Scanner Vulnerability Scanner System & Service
N-Dimension n-platform 340S Unified Threat Management System Firewall Router Site-to-Site VPN Remote-Access VPN Serial SCADA VPN Proxy Anti-virus SCADA IDS Port Scanner Vulnerability Scanner System & Service
Symantec Network Security 7100 Series
 Symantec Network Security 7100 Series Proactive intrusion prevention device protects against known and unknown attacks to secure critical networks transition can be accomplished transparent to any network
Symantec Network Security 7100 Series Proactive intrusion prevention device protects against known and unknown attacks to secure critical networks transition can be accomplished transparent to any network
NGX R65 Operational Changes
 Chapter 1 NGX R65 Operational Changes Solutions in this chapter: New SmartPortal Features New FireWall-1/VPN-1 Features Edge Support for CLM Integrity Advanced Server New VPN Features ClusterXL Summary
Chapter 1 NGX R65 Operational Changes Solutions in this chapter: New SmartPortal Features New FireWall-1/VPN-1 Features Edge Support for CLM Integrity Advanced Server New VPN Features ClusterXL Summary
VPN-1 Power VSX NGX R65 Upgrade Guide
 VPN-1 Power VSX NGX R65 Upgrade Guide March 03 2008 In This Document Upgrade Overview page 2 Upgrading the Management Server to R65 page 4 Installing the GUI Clients page 6 Activating the VSX Plug-in in
VPN-1 Power VSX NGX R65 Upgrade Guide March 03 2008 In This Document Upgrade Overview page 2 Upgrading the Management Server to R65 page 4 Installing the GUI Clients page 6 Activating the VSX Plug-in in
UNIFIED THREAT MANAGEMENT SOLUTIONS AND NEXT-GENERATION FIREWALLS NETWORK SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY
 UNIFIED THREAT MANAGEMENT SOLUTIONS AND NEXT-GENERATION FIREWALLS NETWORK SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY OUR MISSION Provide cybersecurity and data protection for organizations,
UNIFIED THREAT MANAGEMENT SOLUTIONS AND NEXT-GENERATION FIREWALLS NETWORK SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY OUR MISSION Provide cybersecurity and data protection for organizations,
Security Platform. Security. Availability. Manageability. Scalability.
 Security Platform Security. Availability. Manageability. Scalability. security and heavy throughput environments in mind. StoneGate is unique in that it is designed from the ground up, with the demands
Security Platform Security. Availability. Manageability. Scalability. security and heavy throughput environments in mind. StoneGate is unique in that it is designed from the ground up, with the demands
Kerio Control. Unified Threat Management without Complexity. Presenters name. Presented by
 Kerio Control Unified Threat Management without Complexity Presented by Presenters name June 14, 2016 Agenda About Kerio About Kerio Control Kerio Control Benefits Kerio Control Licensing Summary About
Kerio Control Unified Threat Management without Complexity Presented by Presenters name June 14, 2016 Agenda About Kerio About Kerio Control Kerio Control Benefits Kerio Control Licensing Summary About
Next-Generation Firewall Series Datasheet
 RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
Cisco Integrated Services Routers 1941 Series Datasheet
 Cisco Integrated Services Routers 1941 Series Datasheet CONTENT Overview... 2 Appearance... 2 Key Features and Benefits... 3 Product Specifications... 4 Basic Ordering Information... 8 Sources... 8 Contact
Cisco Integrated Services Routers 1941 Series Datasheet CONTENT Overview... 2 Appearance... 2 Key Features and Benefits... 3 Product Specifications... 4 Basic Ordering Information... 8 Sources... 8 Contact
Selling the Total Converged Solution Module #1: Nortel Enterprise Networking Overview of the 4 Pillars and Why Nortel Tom Price Nortel HQ Sales
 Selling the Total Converged Solution Module #1: Nortel Enterprise Networking Overview of the 4 Pillars and Why Nortel Tom Price Nortel HQ Sales Engineer 1 Nortel Value Proposition >Nortel has an End-to-End
Selling the Total Converged Solution Module #1: Nortel Enterprise Networking Overview of the 4 Pillars and Why Nortel Tom Price Nortel HQ Sales Engineer 1 Nortel Value Proposition >Nortel has an End-to-End
R71. Release Notes. 12 August Classification: [Public]
![R71. Release Notes. 12 August Classification: [Public] R71. Release Notes. 12 August Classification: [Public]](/thumbs/76/73001449.jpg) R71 Release Notes 12 August 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
R71 Release Notes 12 August 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
CHECK POINT APPLIANCES
 CHECK POINT APPLIANCES 205 02 table of contents introduction 03 Table of ContentS 03 IntroductioN 04 Check Point GAiA a Unified Secure Operating System 05 About SecurityPower 06 Security Solutions 07 600
CHECK POINT APPLIANCES 205 02 table of contents introduction 03 Table of ContentS 03 IntroductioN 04 Check Point GAiA a Unified Secure Operating System 05 About SecurityPower 06 Security Solutions 07 600
Product Brief Nortel Switched Firewall 6000 Series
 Product Brief Nortel Switched Firewall 6000 Series Accelerated VPN-Firewall High-performance stateful firewall appliance for perimeter deployment Dual component switch-based appliance for highcapacity,
Product Brief Nortel Switched Firewall 6000 Series Accelerated VPN-Firewall High-performance stateful firewall appliance for perimeter deployment Dual component switch-based appliance for highcapacity,
Cisco ASA with FirePOWER Services
 Data Sheet with FirePOWER Meet the industry s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco ASA with FirePOWER delivers
Data Sheet with FirePOWER Meet the industry s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco ASA with FirePOWER delivers
Cisco Network Admission Control (NAC) Solution
 Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Remote Access Clients for Windows 32/64-bit
 Remote Access Clients for Windows 32/64-bit E80.41 Release Notes 16 January 2013 Classification: [Protected] 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Remote Access Clients for Windows 32/64-bit E80.41 Release Notes 16 January 2013 Classification: [Protected] 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Quick Sales Guide. Security
 Quick Sales Guide Security Security Quick Finder Product/Segment Model Unified Security Gateway USG 100/USG 100-PLUS USG 20/20W ZyWALL 1100 VPN Firewall ZyWALL 310 ZyWALL 110 ZyWALL OTPv2/OTP-MOBI Security
Quick Sales Guide Security Security Quick Finder Product/Segment Model Unified Security Gateway USG 100/USG 100-PLUS USG 20/20W ZyWALL 1100 VPN Firewall ZyWALL 310 ZyWALL 110 ZyWALL OTPv2/OTP-MOBI Security
SecurePlatform 2.6 for NGX R65 Release Notes
 SecurePlatform 2.6 for NGX R65 Release Notes Revised: March 26, 2008 This Release Notes document provides essential operating requirements and describes known issues for SecurePlatform 2.6 for NGX R65.
SecurePlatform 2.6 for NGX R65 Release Notes Revised: March 26, 2008 This Release Notes document provides essential operating requirements and describes known issues for SecurePlatform 2.6 for NGX R65.
Alcatel-Lucent OmniAccess 4x50 Series Mobility Controllers Service Multi-tenant Network Management
 Alcatel-Lucent OmniAccess 4x50 Series Mobility Controllers Service Multi-tenant Network Management The Alcatel-Lucent OmniAccess 4x50 Series Mobility Controller is a next generation networking platform
Alcatel-Lucent OmniAccess 4x50 Series Mobility Controllers Service Multi-tenant Network Management The Alcatel-Lucent OmniAccess 4x50 Series Mobility Controller is a next generation networking platform
Cisco SCE 2020 Service Control Engine
 Data Sheet Cisco SCE 2000 Series Service Control Engine The Cisco SCE 2000 Series Service Control Engine is a network element specifically designed for carrier-grade deployments requiring high-capacity
Data Sheet Cisco SCE 2000 Series Service Control Engine The Cisco SCE 2000 Series Service Control Engine is a network element specifically designed for carrier-grade deployments requiring high-capacity
NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD
 PRODUCT SPEC SHEET NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD CENTRALIZED SERVICE DELIVERY AND MANAGEMENT PLATFORM
PRODUCT SPEC SHEET NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD CENTRALIZED SERVICE DELIVERY AND MANAGEMENT PLATFORM
NG with Application Intelligence (R55)
 The Upgrade Guide NG with Application Intelligence (R55) IMPORTANT Check Point recommends that customers stay up-to-date with the latest service packs and versions of security products, as they contain
The Upgrade Guide NG with Application Intelligence (R55) IMPORTANT Check Point recommends that customers stay up-to-date with the latest service packs and versions of security products, as they contain
IBM Proventia Network Multi-Function Security MX0804 and MX1004
 One appliance, six security features designed to preemptively stop Internet threats IBM Proventia Network Multi-Function Security MX0804 and one is safe Single layered security such as a firewall or antivirus
One appliance, six security features designed to preemptively stop Internet threats IBM Proventia Network Multi-Function Security MX0804 and one is safe Single layered security such as a firewall or antivirus
Check Point VPN-1 Pro NGX IPv6Pack for Nokia Getting Started Guide. Check Point VPN-1 Pro NGX IPv6Pack Nokia IPSO 3.9 or 4.0
 Check Point VPN-1 Pro NGX IPv6Pack for Nokia Getting Started Guide Check Point VPN-1 Pro NGX IPv6Pack Nokia IPSO 3.9 or 4.0 Part No. N450000141 Rev 001 Published March 2006 COPYRIGHT 2006 Nokia. All rights
Check Point VPN-1 Pro NGX IPv6Pack for Nokia Getting Started Guide Check Point VPN-1 Pro NGX IPv6Pack Nokia IPSO 3.9 or 4.0 Part No. N450000141 Rev 001 Published March 2006 COPYRIGHT 2006 Nokia. All rights
SSL VPN and Web Security Server
 Connectra Server SSL VPN and Web Security Server IMPORTANT Check Point recommends that customers stay up-to-date with the latest service packs and versions of security products, as they contain security
Connectra Server SSL VPN and Web Security Server IMPORTANT Check Point recommends that customers stay up-to-date with the latest service packs and versions of security products, as they contain security
Preconfigured Audio/Video Bridging System
 Preconfigured Audio/Video Bridging System RSB-KIT Gateway Security Appliance (Router) with Rack Mount Bracket and VLAN switch The popularity and affordability of IP networking has driven audio/video and
Preconfigured Audio/Video Bridging System RSB-KIT Gateway Security Appliance (Router) with Rack Mount Bracket and VLAN switch The popularity and affordability of IP networking has driven audio/video and
Clean wireless. High-performance clean wireless solutions
 Clean wireless High-performance clean wireless solutions The demands on organizations wireless networks such as increased connection counts, bandwidth consumption, need for seamless roaming and extended
Clean wireless High-performance clean wireless solutions The demands on organizations wireless networks such as increased connection counts, bandwidth consumption, need for seamless roaming and extended
SEVONE DATA APPLIANCE FOR EUE
 Insight for the Connected World Data Appliance for EUE [ DataSheet ] SEVONE DATA APPLIANCE FOR EUE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Insight for the Connected World Data Appliance for EUE [ DataSheet ] SEVONE DATA APPLIANCE FOR EUE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Product Description. Product Overview. Architecture and Key Components of the MAG Series Junos Pulse Gateways
 DATASHEET MAG Series Junos Pulse Gateways Product Overview The challenge for today s technology leader is to build an infrastructure that provides easy, secure access to the corporate network for all workers
DATASHEET MAG Series Junos Pulse Gateways Product Overview The challenge for today s technology leader is to build an infrastructure that provides easy, secure access to the corporate network for all workers
Unified Threat Management
 Datasheet EN6200 Q 15 Unified Threat Management USB Port 3G/4G VGA Power Input Combo LAN/WAN LAN Modern Day UTM For Every Office In today s world, Cyber threats are same for all types of modern business.
Datasheet EN6200 Q 15 Unified Threat Management USB Port 3G/4G VGA Power Input Combo LAN/WAN LAN Modern Day UTM For Every Office In today s world, Cyber threats are same for all types of modern business.
Cisco 2900 Series Router Datasheet
 Cisco 2900 Series Router Datasheet CONTENT Overview... 2 Appearance... 2 Key Features and Benefits... 3 Modularity Features and Benefits... 4 Product Specifications... 7 Basic Ordering Information... 13
Cisco 2900 Series Router Datasheet CONTENT Overview... 2 Appearance... 2 Key Features and Benefits... 3 Modularity Features and Benefits... 4 Product Specifications... 7 Basic Ordering Information... 13
Course Modules for CCSE R77 (Check Point Certified Security Expert) Training Online
 Course Modules for CCSE R77 (Check Point Certified Security Expert) Training Online 1 Introduction to Check Point Technology A) Check Point Security Management Architecture(SMART) Smart Console Security
Course Modules for CCSE R77 (Check Point Certified Security Expert) Training Online 1 Introduction to Check Point Technology A) Check Point Security Management Architecture(SMART) Smart Console Security
USG310/210/110. Benefits. Always online. Protection and optimization. Next Generation Firewall (NGFW) for small and medium-sized businesses
 Next Generation Firewall (NGFW) for small and medium-sized businesses with firewall, anti-virus, antispam, content filtering, IDP, next-generation application intelligence and SSL inspection connectivity
Next Generation Firewall (NGFW) for small and medium-sized businesses with firewall, anti-virus, antispam, content filtering, IDP, next-generation application intelligence and SSL inspection connectivity
NSG100 Nebula Cloud Managed Security Gateway
 Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
Flexible and scalable five enterprise-grade Smart-1 dedicated management appliances. Full Threat Visibility
 SMART-1 SECURITY MANAGEMENT PLATFORM All-in-one security management solution, with policy management, integrated threat visibility, workflow and orchestration, empowering Check Point Infinity Architecture
SMART-1 SECURITY MANAGEMENT PLATFORM All-in-one security management solution, with policy management, integrated threat visibility, workflow and orchestration, empowering Check Point Infinity Architecture
NETWORK SECURITY STORMSHIELD. Unified Threat Management Solutions and Next- Generation Firewalls
 NETWORK SECURITY STORMSHIELD NETWORK SECURITY Unified Threat Management Solutions and Next- Generation Firewalls Our Mission Make the digital world a sustainable and trustworthy environment while ensuring
NETWORK SECURITY STORMSHIELD NETWORK SECURITY Unified Threat Management Solutions and Next- Generation Firewalls Our Mission Make the digital world a sustainable and trustworthy environment while ensuring
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
Cisco UCS B230 M2 Blade Server
 Data Sheet Cisco UCS B230 M2 Blade Server Product Overview The Cisco UCS B230 M2 Blade Server is one of the industry s highest-density two-socket blade server platforms. It is a critical new building block
Data Sheet Cisco UCS B230 M2 Blade Server Product Overview The Cisco UCS B230 M2 Blade Server is one of the industry s highest-density two-socket blade server platforms. It is a critical new building block
Integrity XML Policy File Reference
 Integrity XML Policy File Reference A Reference to XML Policy Elements and Attributes Preface This document describes the elements and attributes contained in the Check Point Integrity client XML Policy
Integrity XML Policy File Reference A Reference to XML Policy Elements and Attributes Preface This document describes the elements and attributes contained in the Check Point Integrity client XML Policy
Aruba 7000 Series Mobility Controller Data Sheet
 Aruba 7000 Series Mobility Controller Data Sheet CONTENT Overview...2 Key Models...2 Specifications...4 Ordering information...7 Where to Buy...9 Sources...9 Contact Us Tel: +1-626-239-8066 (USA) / +852-3050-1066
Aruba 7000 Series Mobility Controller Data Sheet CONTENT Overview...2 Key Models...2 Specifications...4 Ordering information...7 Where to Buy...9 Sources...9 Contact Us Tel: +1-626-239-8066 (USA) / +852-3050-1066
Acme Packet Net-Net 14000
 Acme Packet Overview The is Acme Packet s high-end platform for service providers who require the highest levels of performance and capacity, and the operational benefits of ATCA-compliant chassis-based
Acme Packet Overview The is Acme Packet s high-end platform for service providers who require the highest levels of performance and capacity, and the operational benefits of ATCA-compliant chassis-based
ASA5508-FTD-K9. ASA 5508-X with Firepower Threat Defense. 8GE. AC. 450 Mbps. 250 Mbps. 1 Gbps. 500 Mbps. 100 Mbps. Unlimited
 ASA5508-FTD-K9 Datasheet Overview The ASA5508-FTD-K9 is the ASA 5508-X with Firepower Threat Defense. 8GE. AC. Quick Spec Figure 1 shows the appearance of ASA5508-FTD-K9. Table 1 shows the quick spec.
ASA5508-FTD-K9 Datasheet Overview The ASA5508-FTD-K9 is the ASA 5508-X with Firepower Threat Defense. 8GE. AC. Quick Spec Figure 1 shows the appearance of ASA5508-FTD-K9. Table 1 shows the quick spec.
5 STEPS TO BUILDING ADVANCED SECURITY IN SOFTWARE- DEFINED DATA CENTERS
 5 STEPS TO BUILDING ADVANCED SECURITY IN SOFTWARE- DEFINED DATA CENTERS INTRODUCTION The modern data center is rapidly evolving. Virtualization is paving the way to the private cloud, enabling applications
5 STEPS TO BUILDING ADVANCED SECURITY IN SOFTWARE- DEFINED DATA CENTERS INTRODUCTION The modern data center is rapidly evolving. Virtualization is paving the way to the private cloud, enabling applications
Next Generation Firewalls For Your Network Security
 Our On-Premises Managed Firewall services go beyond perimeter protection; providing a new Web and Unified Threat Management (UTM) security feature. The solution combines the best-of-breed technologies.
Our On-Premises Managed Firewall services go beyond perimeter protection; providing a new Web and Unified Threat Management (UTM) security feature. The solution combines the best-of-breed technologies.
Security Management Server. Administration Guide Version R70
 Security Management Server Administration Guide Version R70 701676 March 8, 2009 2003-2009 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Security Management Server Administration Guide Version R70 701676 March 8, 2009 2003-2009 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
