Update on new Microsoft Cloud Technology
|
|
|
- Antonia Elliott
- 5 years ago
- Views:
Transcription
1 Update on new Microsoft Cloud Technology
2 Advanced Threat Protection Thomas Collier Technical Pre-Sales
3
4 OFFICE 365 PHISH PROTECTION STACK Protect during Mail Flow Protect Post Delivery Detect & Respond Sender Authentication Checks AV Engine Scan ATP Machine Learning Models ATP Safe links Time of click Protection Client Tips for Suspicious Mails Implicit Intra Org Domain Spoof Detection URL Reputation Scan Phish Content Analysis Heuristics/Rules ATP Heuristic Clustering & Detonation ATP Link content Detonation ATP ZAP Safe links for Office Clients Multi factor Authentication for Office 365 Tenant Block URL for Safe links Monitor for risky user/app activity Search/Remediate mails in Threat Explorer
5 ROADMAP OFFICE 365 PHISH PROTECTION STACK Mail Flow Protection Post Delivery Protection Detect & Respond Sender Authentication Checks Implicit Intra Org Domain Implicit Spoof Intra Detection Org Domain Spoof Detection Soon: ATP Implicit External Soon: Domain ATP Spoof Implicit Detection External Domain Spoof Detection Soon: Soon: ATP ATP User User Intelligence mailbox Intelligence Soon: ATP User Soon: ATP User Impersonation Detection Impersonation Detection Soon: ATP Domain Impersonation Soon: ATP Domain Detection Impersonation Detection AV Engine Scan URL Reputation Scan URL Reputation Scan Phish Content Analysis Phish Heuristics/Rules Content Analysis Heuristics/Rules New: Windows 10 based New: Windows Rep Scan 10 based Rep Scan ATP Machine Learning Models ATP Heuristic Clustering New: ATP block of attachments with bad URLs New: ATP Attachment Detonation for phishing ATP Safe link Time of click Protection ATP ZAP New: Safe link for Internal Mail Multi factor Authentication for Office 365 Enhanced: Safe link for Office Clients Enhanced: Client Tips for Suspicious Mails Tenant Block URL for Safe links Monitor for risky user/app activity Enhanced:Threat Explorer New: Rich Reports & Insights New: Explore malicious submissions in Threat Explorer
6 Apply heuristics Leverage signals Collaboration signals anonymous links companywide sharing explicit sharing guest user activity file activity In Teams Threat feeds malware in + SPO Windows Defender Windows Defender ATP suspicious logins risky IP addresses Files in SharePoint Online, OneDrive for Business, Microsoft Teams 1 st and 3 rd party reputation Multiple AV engines Sandboxing Improves your security against zero-day attacks by directly integrating into OneDrive for Business, SharePoint Online, and Teams Protect your users from malicious links within shared documents in OneDrive for Business, SharePoint Online, and Teams Safeguard your environment by blocking malicious content identified by ATP Activity watch lists users IPs On-demand patterns (e.g. WannaCry, Petra)
7 ATTACK LURES/PAYLOADS Scams Brand Phising IT+SaaS Phising Spear Fishing Text Lures Domain Spoof Phishing Attachments Credential Phishing Links User Impersonation Domain Impersonation Link to fake SaaS Apps
8 PROTECT MAIL FLOW Edge block Authentication Implicit intra-org DMARC AV Engines Block before allowing in Standards SPF, DMARC, DKIM DKIM default signing Messages from one of your domains to one of your domains Acts like DMARC, based on Intelligence Multiple engines scan mail for known malicious content
9 Detonation Chambers Safe Attachment detonation Link Content detonation in Safe links Heuristic clustering Reputation data File hash and URLs from detonation URL feeds from 1 st and 3 rd parties Linked Content Detonation Heuristic Clustering Safe Attachments URL Reputations 1 st and 3 rd party Reputation Blocking
10 PROTECT POST DELIVERY Safe links provides Time of click protection Client Agnostic Location agnostic Integrated directly into Office clients Zero hour Auto purge (ZAP) Zero-Hour Auto-purge Safe Links for Office Clients Safe Links
11 Manage your users report on their phish experience with a plugin Integrate with Cloud App Security for IP Blocking REPORT FISH ATTEMPTS
12 URL SAFE LINKS EXAMPLE
13 INTELLIGENT CLIENT TIPS
14 BLOCK LIST
15 NEW: ATTACK SIMULATOR
16 Integration with Windows 10 Edge SmartScreen Mail flow and Safe links Enhanced ATP Detonation Phish in attachments URLs in attachments Safe link support for internal messages Implicit DMARC for external domains Domain impersonation Your domains and your partners Ćóntoso.com = Contoso.com Contoso Account <contoso.com> user@fabrikam.com = contoso.com User impersonation List of names to protect User level intelligence Intelligence built around who you communicate with Understanding relationship strengths Detection of new contacts/impersonation of existing contact NEW FUNCTIONALITY (ROADMAP)
How Enterprise Tackles Phishing. Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong
 How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
Competitive Matrix - IRONSCALES vs Alternatives
 Competitive Matrix - IRONSCALES vs Alternatives Traditional Awareness and Training Features IRONSCALES SEG PhishMe Wombat Knowbe4 Sans Institute Simulation & Training Compliance PCI/DSS, HIPAA, GLBA to
Competitive Matrix - IRONSCALES vs Alternatives Traditional Awareness and Training Features IRONSCALES SEG PhishMe Wombat Knowbe4 Sans Institute Simulation & Training Compliance PCI/DSS, HIPAA, GLBA to
Enterprise Ransomware Mitigations
 打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
CloudSOC and Security.cloud for Microsoft Office 365
 Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Phishing Discussion. Pete Scheidt Lead Information Security Analyst California ISO
 Phishing Discussion Pete Scheidt Lead Information Security Analyst California ISO 2 Phish What is Phishing Types of Phish 3 Phish What is Phishing Attackers (Phishers) would email (cast their nets) far
Phishing Discussion Pete Scheidt Lead Information Security Analyst California ISO 2 Phish What is Phishing Types of Phish 3 Phish What is Phishing Attackers (Phishers) would email (cast their nets) far
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches
 Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches Introduction No matter how hard you work to educate your employees about the constant and evolving threats
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches Introduction No matter how hard you work to educate your employees about the constant and evolving threats
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
Symantec Ransomware Protection
 Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
6 Ways Office 365 Keeps Your and Business Secure
 6 Ways Office 365 Keeps Your Email and Business Secure Acora House, Albert Drive, Burgess Hill, West Sussex, RH15 9TN T: +44 (0) 844 264 2222 W: acora.com E: sales@acora.com Introduction Microsoft have
6 Ways Office 365 Keeps Your Email and Business Secure Acora House, Albert Drive, Burgess Hill, West Sussex, RH15 9TN T: +44 (0) 844 264 2222 W: acora.com E: sales@acora.com Introduction Microsoft have
Proteggere Office365 e Cloud file sharing in meno di un minuto Tiberio Molino Sr.Sales Engineer Trend Micro
 Proteggere Office365 e Cloud file sharing in meno di un minuto Tiberio Molino Sr.Sales Engineer Trend Micro 2 Customer Challenges 3 Most Attacks Include Phishing Emails 5 Advanced Malware Difficult to
Proteggere Office365 e Cloud file sharing in meno di un minuto Tiberio Molino Sr.Sales Engineer Trend Micro 2 Customer Challenges 3 Most Attacks Include Phishing Emails 5 Advanced Malware Difficult to
DMARC Continuing to enable trust between brand owners and receivers
 DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
CAS Quick Deployment Guide January 2018
 CAS January 2018 Page 2 of 18 Trend Micro CAS January 2018 This document is to guide TrendMicro SE and Solution Architect team run a successful Cloud App Security POC with prospective customers. It is
CAS January 2018 Page 2 of 18 Trend Micro CAS January 2018 This document is to guide TrendMicro SE and Solution Architect team run a successful Cloud App Security POC with prospective customers. It is
On the Surface. Security Datasheet. Security Datasheet
 Email Security Datasheet Email Security Datasheet On the Surface No additional hardware or software required to achieve 99.9%+ spam and malware filtering effectiveness Initiate service by changing MX Record
Email Security Datasheet Email Security Datasheet On the Surface No additional hardware or software required to achieve 99.9%+ spam and malware filtering effectiveness Initiate service by changing MX Record
2018 Edition. Security and Compliance for Office 365
 2018 Edition Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world,
2018 Edition Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world,
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
WELCOME! Using Microsoft Office 365 for a Robust Mail and Conferencing System
 WELCOME! Using Microsoft Office 365 for a Robust Mail and Conferencing System Collect Learn Today Cards What do you hope to learn today? Please take a moment to fill out the yellow cards. Our presenters
WELCOME! Using Microsoft Office 365 for a Robust Mail and Conferencing System Collect Learn Today Cards What do you hope to learn today? Please take a moment to fill out the yellow cards. Our presenters
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Security Gaps from the Field
 Security Gaps from the Field Reconnaissance, Theft, and Looking Them in the Eye Helping you grow your business with scalable IT services & solutions Bruce Ward, CISM, Vice President for today s challenges
Security Gaps from the Field Reconnaissance, Theft, and Looking Them in the Eye Helping you grow your business with scalable IT services & solutions Bruce Ward, CISM, Vice President for today s challenges
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
Evolution of Cyber Security. Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa
 Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Office 365: Modern Workplace
 Office 365: Modern Workplace November 8, 2018 Bruce Ward, VP of Business Strategy Helping you grow your business with scalable IT services & solutions for today s challenges & tomorrow s vision. 2018 Peters
Office 365: Modern Workplace November 8, 2018 Bruce Ward, VP of Business Strategy Helping you grow your business with scalable IT services & solutions for today s challenges & tomorrow s vision. 2018 Peters
Cloud Security & Advance Threat Protection. Cloud Security & Advance Threat Protection
 Cloud Email Security & Advance Threat Protection Cloud Email Security & Advance Threat Protection Overview Over the years Cyber criminals have become more inventive in their attack methods to infiltrate
Cloud Email Security & Advance Threat Protection Cloud Email Security & Advance Threat Protection Overview Over the years Cyber criminals have become more inventive in their attack methods to infiltrate
EU GENERAL DATA PROTECTION: TIME TO ACT. Laurent Vanderschrick Channel Manager Belgium & Luxembourg Stefaan Van Hoornick Technical Manager BeNeLux
 EU GENERAL DATA PROTECTION: TIME TO ACT Laurent Vanderschrick Channel Manager Belgium & Luxembourg Stefaan Van Hoornick Technical Manager BeNeLux Is this the WAY you handle GDPR today 2 3 area s to consider
EU GENERAL DATA PROTECTION: TIME TO ACT Laurent Vanderschrick Channel Manager Belgium & Luxembourg Stefaan Van Hoornick Technical Manager BeNeLux Is this the WAY you handle GDPR today 2 3 area s to consider
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Phishing in the Age of SaaS
 Phishing in the Age of SaaS AN ESSENTIAL GUIDE FOR BUSINESSES AND USERS The Cloud Security Platform Q3 2017 intro Phishing attacks have become the primary hacking method used against organizations. In
Phishing in the Age of SaaS AN ESSENTIAL GUIDE FOR BUSINESSES AND USERS The Cloud Security Platform Q3 2017 intro Phishing attacks have become the primary hacking method used against organizations. In
ybersecurity for the Modern Era Three Steps to Stopping malware, Credential Phishing, Fraud and More
 ybersecurity for the Modern Era Three Steps to Stopping malware, Credential Phishing, Email Fraud and More www.proofpoint.com EBOOK Cybersecurity in the modern era 2 ONLY AMATEURS ATTACK MACHINES. PROFESSIONALS
ybersecurity for the Modern Era Three Steps to Stopping malware, Credential Phishing, Email Fraud and More www.proofpoint.com EBOOK Cybersecurity in the modern era 2 ONLY AMATEURS ATTACK MACHINES. PROFESSIONALS
Security for the Cloud Era
 Security for the Cloud Era Make the Most Out of Your Cloud Journey Fadhly Hassim Sales Engineer South East Asia & Korea Barracuda Networks Current Weather Situation Customer Provisions & Manage On-Premises
Security for the Cloud Era Make the Most Out of Your Cloud Journey Fadhly Hassim Sales Engineer South East Asia & Korea Barracuda Networks Current Weather Situation Customer Provisions & Manage On-Premises
IT Security Training MS-500: Microsoft 365 Security Administration. Upcoming Dates. Course Description. Course Outline $2,
 IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
Managing Microsoft 365 Identity and Access
 Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
Turning the Tide: Fending off Cyber Threats
 SESSION ID: SPO1-W05A Turning the Tide: Fending off Cyber Threats Authenticate / Protect / Respond Roy Murdoch SE Manager NEMEA Proofpoint Who s in the Actors Sights? Attacks Increasingly Target Individuals,
SESSION ID: SPO1-W05A Turning the Tide: Fending off Cyber Threats Authenticate / Protect / Respond Roy Murdoch SE Manager NEMEA Proofpoint Who s in the Actors Sights? Attacks Increasingly Target Individuals,
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
Welcome. Security: First Line of Defense. Chris Riley Director x4331
 Welcome Email Security: First Line of Defense Chris Riley Director criley@syssrc.com 410-771-5544 x4331 We Hope You are Enjoying Your Pizza!! If it hasn t arrived by 12:15 Please double check with your
Welcome Email Security: First Line of Defense Chris Riley Director criley@syssrc.com 410-771-5544 x4331 We Hope You are Enjoying Your Pizza!! If it hasn t arrived by 12:15 Please double check with your
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Symantec Advanced Threat Protection App for Splunk
 Symantec Advanced Threat Protection App for Splunk Administrator Guide Date Published: 27 th Mar 2017 Document Version: 1.0.5 Table of Contents Installing and setting up the ATP app 3 About the Symantec
Symantec Advanced Threat Protection App for Splunk Administrator Guide Date Published: 27 th Mar 2017 Document Version: 1.0.5 Table of Contents Installing and setting up the ATP app 3 About the Symantec
Easy Activation Effortless web-based administration that can be activated in as little as one business day - no integration or migration necessary.
 Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Deep Sea Phishing: Examples & Countermeasures
 Deep Sea Phishing: Examples & Countermeasures Phishing is impersonation of a person or brand. Our focus is email-based phishing. Phishing is not malware, spam, or xss, although these often coincide. Current
Deep Sea Phishing: Examples & Countermeasures Phishing is impersonation of a person or brand. Our focus is email-based phishing. Phishing is not malware, spam, or xss, although these often coincide. Current
 http://ignite.office.com Spam Protect communications Enforce policy Streamlined management On Premise Corporate Network EOP O365 Exchange Online Every Office 365 customer is an EOP customer Easy transition
http://ignite.office.com Spam Protect communications Enforce policy Streamlined management On Premise Corporate Network EOP O365 Exchange Online Every Office 365 customer is an EOP customer Easy transition
The Next Generation Security Platform. Domenico Stranieri Pre- Sales Engineer Palo Alto Networks EMEA Italy
 The Next Generation Security Platform Domenico Stranieri Pre- Sales Engineer Palo Alto Networks EMEA Italy The Next Generation Enterprise Security Platform Core Value Proposition An Enterprise Security
The Next Generation Security Platform Domenico Stranieri Pre- Sales Engineer Palo Alto Networks EMEA Italy The Next Generation Enterprise Security Platform Core Value Proposition An Enterprise Security
Cyber Resilience for TECHNICAL DEEP DIVE
 Cyber Resilience for Email TECHNICAL DEEP DIVE Email. It s the number-one business application used by organizations. It s also the number-one method used to execute cyberattacks, enabling malware delivery,
Cyber Resilience for Email TECHNICAL DEEP DIVE Email. It s the number-one business application used by organizations. It s also the number-one method used to execute cyberattacks, enabling malware delivery,
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Sophos Central Partner. help
 help Contents About help...1 About...2 Dashboard... 3 Alerts...4 Logs... 5 Audit Logs...5 Sophos Central...7 Sophos Central customers...7 Sophos Central Licenses... 7 Managed Customer Usage... 9 Trial
help Contents About help...1 About...2 Dashboard... 3 Alerts...4 Logs... 5 Audit Logs...5 Sophos Central...7 Sophos Central customers...7 Sophos Central Licenses... 7 Managed Customer Usage... 9 Trial
Avanan for G Suite. Technical Overview. Copyright 2017 Avanan. All rights reserved.
 Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Hybrid Identity de paraplu in de cloud
 EXPERTS LIVE SUMMER NIGHT Hybrid Identity de paraplu in de cloud Robbert van der Zwan TSP EM+S Netherlands EXPERTS LIVE SUMMER NIGHT Robbert van der Zwan Robbert works as an Enterprise Mobility and Security
EXPERTS LIVE SUMMER NIGHT Hybrid Identity de paraplu in de cloud Robbert van der Zwan TSP EM+S Netherlands EXPERTS LIVE SUMMER NIGHT Robbert van der Zwan Robbert works as an Enterprise Mobility and Security
DMARC ADOPTION AMONG. SaaS 1000 Q Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok
 DMARC ADOPTION AMONG SaaS 1000 Q1 2018 Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok TABLE OF CONTENTS Introduction... 03 Research Overview... 04 SaaS 1000... 05 DMARC Adoption Among SaaS
DMARC ADOPTION AMONG SaaS 1000 Q1 2018 Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok TABLE OF CONTENTS Introduction... 03 Research Overview... 04 SaaS 1000... 05 DMARC Adoption Among SaaS
How to Conquer Targeted Threats: SANS Review of Agari Enterprise Protect
 How to Conquer Targeted Email Threats: SANS Review of Agari Enterprise Protect A SANS Product Review Written by Dave Shackleford May 2017 Sponsored by Agari 2017 SANS Institute Introduction: Email Is a
How to Conquer Targeted Email Threats: SANS Review of Agari Enterprise Protect A SANS Product Review Written by Dave Shackleford May 2017 Sponsored by Agari 2017 SANS Institute Introduction: Email Is a
M 3 AAWG DMARC Training Series. Mike Adkins, Paul Midgen DMARC.org October 22, 2012
 M 3 AAWG DMARC Training Series Mike Adkins, Paul Midgen DMARC.org October 22, 2012 M3AAWG DMARC Training Videos (2.5 hours of training) This is Segment 1 of 6 The complete series of DMARC training videos
M 3 AAWG DMARC Training Series Mike Adkins, Paul Midgen DMARC.org October 22, 2012 M3AAWG DMARC Training Videos (2.5 hours of training) This is Segment 1 of 6 The complete series of DMARC training videos
Security and Compliance for Office 365
 Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world, you may be
Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world, you may be
A Buyer s Guide to DMARC
 0800 133 7127 support@lawyerchecker.co.uk A Buyer s Guide to DMARC Meet the cyber security protocol that reduces phishing attacks and improves email deliverability 1971 First email sent 1982 SMTP established
0800 133 7127 support@lawyerchecker.co.uk A Buyer s Guide to DMARC Meet the cyber security protocol that reduces phishing attacks and improves email deliverability 1971 First email sent 1982 SMTP established
Measuring cloud-based anti-malware protection for Office 365 user accounts
 Measuring cloud-based anti-malware protection for Office 365 user accounts Ferenc Leitold Veszprog fleitold@veszprog.hu Anthony Arrott CheckVir aarrott@checkvir.com William Kam Trend Micro william_kam@trendmicro.com
Measuring cloud-based anti-malware protection for Office 365 user accounts Ferenc Leitold Veszprog fleitold@veszprog.hu Anthony Arrott CheckVir aarrott@checkvir.com William Kam Trend Micro william_kam@trendmicro.com
HIPAA Compliance. with O365 Manager Plus.
 HIPAA Compliance with O365 Manager Plus www.o365managerplus.com About HIPAA HIPAA, the Health Insurance Portability and Accountability Act, sets the standard for protecting sensitive patient data. Any
HIPAA Compliance with O365 Manager Plus www.o365managerplus.com About HIPAA HIPAA, the Health Insurance Portability and Accountability Act, sets the standard for protecting sensitive patient data. Any
DMARC ADOPTION AMONG. SaaS 1000 Q Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok
 DMARC ADOPTION AMONG SaaS 1000 Q1 2018 Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok TABLE OF CONTENTS Introduction... 03 Research Overview... 04 SaaS 1000... 05 DMARC Adoption Among SaaS
DMARC ADOPTION AMONG SaaS 1000 Q1 2018 Featuring Matthew Vernhout (CIPP/C) Director of Privacy, 250ok TABLE OF CONTENTS Introduction... 03 Research Overview... 04 SaaS 1000... 05 DMARC Adoption Among SaaS
But it Was Such a Little Phish February 2016 Webinar
 But it Was Such a Little Phish February 2016 Webinar Firestorm Insights February 2016 1000 Holcomb Woods Parkway Suite 130 Roswell, GA 30076 770-643-1114 Fax: 1-800-418-9088 www.firestorm.com Page Intentionally
But it Was Such a Little Phish February 2016 Webinar Firestorm Insights February 2016 1000 Holcomb Woods Parkway Suite 130 Roswell, GA 30076 770-643-1114 Fax: 1-800-418-9088 www.firestorm.com Page Intentionally
Secure solutions for advanced threats
 Secure solutions for advanced email threats Threat-centric email security Cosmina Calin Virtual System Engineer November 2016 Get ahead of attackers with threat-centric security solutions In our live Security
Secure solutions for advanced email threats Threat-centric email security Cosmina Calin Virtual System Engineer November 2016 Get ahead of attackers with threat-centric security solutions In our live Security
One Phish, Two Phish, Three! Building an Active Threat Management Framework for Malicious
 One Phish, Two Phish, Three! Building an Active Threat Management Framework for Malicious Email - Ron Weiss, Incident Response Team lead Disclaimer: The information in this presentation is based on lessons
One Phish, Two Phish, Three! Building an Active Threat Management Framework for Malicious Email - Ron Weiss, Incident Response Team lead Disclaimer: The information in this presentation is based on lessons
SolarWinds Mail Assure
 TECHNICAL PRODUCT DATASHEET SolarWinds Mail Assure Email Protection & Email Archive SolarWinds Mail Assure provides best-in-class protection against email-based threats, such as spam, viruses, phishing,
TECHNICAL PRODUCT DATASHEET SolarWinds Mail Assure Email Protection & Email Archive SolarWinds Mail Assure provides best-in-class protection against email-based threats, such as spam, viruses, phishing,
GLBA Compliance. with O365 Manager Plus.
 GLBA Compliance with O365 Manager Plus www.o365managerplus.com About GLBA The Gramm-Leach-Bliley Act (GLB Act or GLBA) is also known as the Financial Modernization Act of 1999. It is a United States federal
GLBA Compliance with O365 Manager Plus www.o365managerplus.com About GLBA The Gramm-Leach-Bliley Act (GLB Act or GLBA) is also known as the Financial Modernization Act of 1999. It is a United States federal
Censornet. CensorNet Unified Security Service (USS) FREEDOM. VISIBILITY. PROTECTION. Lars Gotlieb Regional Manager DACH
 Censornet CensorNet Unified Security Service (USS) FREEDOM. VISIBILITY. PROTECTION. Lars Gotlieb Regional Manager DACH Censornet???? Former SMS passcode. One of the leading vendors in Multi factor authentifaction!
Censornet CensorNet Unified Security Service (USS) FREEDOM. VISIBILITY. PROTECTION. Lars Gotlieb Regional Manager DACH Censornet???? Former SMS passcode. One of the leading vendors in Multi factor authentifaction!
1
 Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
THE CLOUD SECURITY CHALLENGE:
 THE CLOUD EMAIL SECURITY CHALLENGE: CLOSING THE CYBERSECURITY SKILLS GAP THROUGH AUTOMATION THE EMAIL SECURITY CHALLENGE Email remains at the heart of the business communications landscape. While nobody
THE CLOUD EMAIL SECURITY CHALLENGE: CLOSING THE CYBERSECURITY SKILLS GAP THROUGH AUTOMATION THE EMAIL SECURITY CHALLENGE Email remains at the heart of the business communications landscape. While nobody
Technical Brochure F-SECURE THREAT SHIELD
 Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Trustwave SEG Cloud BEC Fraud Detection Basics
 .trust Trustwave SEG Cloud BEC Fraud Detection Basics Table of Contents About This Document 1 1 Background 2 2 Configuring Trustwave SEG Cloud for BEC Fraud Detection 5 2.1 Enable the Block Business Email
.trust Trustwave SEG Cloud BEC Fraud Detection Basics Table of Contents About This Document 1 1 Background 2 2 Configuring Trustwave SEG Cloud for BEC Fraud Detection 5 2.1 Enable the Block Business Email
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats Digital Transformation on a Massive Scale 15B Devices Today Attack Surface 500B Devices In 2030 Threat Actors $19T Opportunity Next 10 Years
Cisco Firepower NGFW Anticipate, block, and respond to threats Digital Transformation on a Massive Scale 15B Devices Today Attack Surface 500B Devices In 2030 Threat Actors $19T Opportunity Next 10 Years
Security Protection
 Email Security Protection Loay Alayadhi Abstract: Email is the most important business communication tool. Security has been an issue in mail from ancient times. Therefore, email security protection has
Email Security Protection Loay Alayadhi Abstract: Email is the most important business communication tool. Security has been an issue in mail from ancient times. Therefore, email security protection has
Agenda. Why we need a new approach to endpoint security. Introducing Sophos Intercept X. Demonstration / Feature Walk Through. Deployment Options
 Agenda Why we need a new approach to endpoint security Introducing Sophos Intercept X Demonstration / Feature Walk Through Deployment Options Q & A 2 Endpoint Security has reached a Tipping Point Attacks
Agenda Why we need a new approach to endpoint security Introducing Sophos Intercept X Demonstration / Feature Walk Through Deployment Options Q & A 2 Endpoint Security has reached a Tipping Point Attacks
Hardening the Modern Windows Client Let s NOT break it this time
 Hardening the Modern Windows Client Let s NOT break it this time Raymond P.L. Comvalius Raymond Comvalius IT Infra Architect/Trainer MVP Windows IT Pro Zelfstandig sinds 1998 Agenda History of Hardening
Hardening the Modern Windows Client Let s NOT break it this time Raymond P.L. Comvalius Raymond Comvalius IT Infra Architect/Trainer MVP Windows IT Pro Zelfstandig sinds 1998 Agenda History of Hardening
GSX 365 Usage Reports & Security Audit
 GSX 365 Usage Reports & Security Audit With you, everywhere, for more than 20 years Founded in 1996, Headquartered in Switzerland London Geneva Offices in USA, UK, France, Switzerland, Singapore and Bangalore
GSX 365 Usage Reports & Security Audit With you, everywhere, for more than 20 years Founded in 1996, Headquartered in Switzerland London Geneva Offices in USA, UK, France, Switzerland, Singapore and Bangalore
Microsoft Security Management
 Microsoft Security Management MICROSOFT SECURITY MANAGEMENT SECURITY MANAGEMENT CHALLENGES Some large financial services organizations have as many as 40 or more different security vendors inside their
Microsoft Security Management MICROSOFT SECURITY MANAGEMENT SECURITY MANAGEMENT CHALLENGES Some large financial services organizations have as many as 40 or more different security vendors inside their
TrendMicro Hosted Security. Best Practice Guide
 TrendMicro Hosted Email Security Best Practice Guide 1 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. The names of companies,
TrendMicro Hosted Email Security Best Practice Guide 1 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. The names of companies,
Symantec & Blue Coat Technical Update Webinar 29. Juni 2017
 Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Securing Office 365 with Symantec
 February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
Top 10 Global Threat Rank by Source
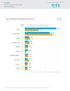 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Longline Phishing: -borne Threats, Cloud Computing, Big Data, and the Rise of Industrial Phishing Attacks. A Proofpoint White Paper WHITE PAPER
 Longline Phishing: Email-borne Threats, Cloud Computing, Big Data, and the Rise of Industrial Phishing Attacks A Proofpoint White Paper threat protection compliance archiving & governance secure communication
Longline Phishing: Email-borne Threats, Cloud Computing, Big Data, and the Rise of Industrial Phishing Attacks A Proofpoint White Paper threat protection compliance archiving & governance secure communication
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
Cirius Secure Messaging Enterprise Dedicated Cloud
 Secure messaging and message control that is flexible to data jurisdiction, integrates rapidly into Office 365 and Outlook, and supports regulatory compliance. Enterprise organizations are recognizing
Secure messaging and message control that is flexible to data jurisdiction, integrates rapidly into Office 365 and Outlook, and supports regulatory compliance. Enterprise organizations are recognizing
Synchronized Security
 Synchronized Security 2 Endpoint Firewall Synchronized Security Platform and Strategy Admin Manage All Sophos Products Self Service User Customizable Alerts Partner Management of Customer Installations
Synchronized Security 2 Endpoint Firewall Synchronized Security Platform and Strategy Admin Manage All Sophos Products Self Service User Customizable Alerts Partner Management of Customer Installations
Late Addition #1 EXECUTIVE DOCUMENT SUMMARY
 EXECUTIVE DOCUMENT SUMMARY Department: Information Technology Contact Person: Ron Plamondon Telephone No.: Source Selection Method Bid Other: Submittal Dates Executive Board: 01/15/2019 Regular Session:
EXECUTIVE DOCUMENT SUMMARY Department: Information Technology Contact Person: Ron Plamondon Telephone No.: Source Selection Method Bid Other: Submittal Dates Executive Board: 01/15/2019 Regular Session:
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY
 RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
PEOPLE CENTRIC SECURITY THE NEW
 PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
TABLE OF CONTENTS Introduction: IS A TOP THREAT VECTOR... 3 THE PROBLEM: ATTACKS ARE EVOLVING FASTER THAN DEFENSES...
 The Guide TABLE OF CONTENTS Introduction: EMAIL IS A TOP THREAT VECTOR... 3 THE PROBLEM: ATTACKS ARE EVOLVING FASTER THAN EMAIL DEFENSES... 4 Today s Top Email Fraud Tactics...5 Advanced Malware...8 Outbound
The Guide TABLE OF CONTENTS Introduction: EMAIL IS A TOP THREAT VECTOR... 3 THE PROBLEM: ATTACKS ARE EVOLVING FASTER THAN EMAIL DEFENSES... 4 Today s Top Email Fraud Tactics...5 Advanced Malware...8 Outbound
Phishing. A simplified walkthrough on how phishing campaigns are often orchestrated, and possible defences. Copyright March 2018
 Phishing A simplified walkthrough on how phishing campaigns are often orchestrated, and possible defences. Copyright March 2018 Netscylla Cyber Security Ltd GB 10571639 Address: Telecom House, 125-135
Phishing A simplified walkthrough on how phishing campaigns are often orchestrated, and possible defences. Copyright March 2018 Netscylla Cyber Security Ltd GB 10571639 Address: Telecom House, 125-135
Copyright 2018 Trend Micro Incorporated. All rights reserved.
 Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent
Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent
Chain 365 Cyber Threat Intelligence Enterprise & Cyber Security. August 2017
 Chain 365 Cyber Threat Intelligence Enterprise & Cyber Security August 2017 Fujitsu Cyber Threat Intelligence Office 365 Supply Chain Compromise Global Impact Executive Summary... 2 Chain 365... 3 Potential
Chain 365 Cyber Threat Intelligence Enterprise & Cyber Security August 2017 Fujitsu Cyber Threat Intelligence Office 365 Supply Chain Compromise Global Impact Executive Summary... 2 Chain 365... 3 Potential
Office 365 Integration Guide Software Version 6.7
 rat Office 365 Integration Guide Software Version 6.7 Guide Version 6.7.061418 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction...3 1.1 Email Flow Explanation...3
rat Office 365 Integration Guide Software Version 6.7 Guide Version 6.7.061418 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction...3 1.1 Email Flow Explanation...3
MigrationWiz Security Overview
 MigrationWiz Security Overview Table of Contents Introduction... 2 Overview... 2 Shared Security Approach... 2 Customer Best Practices... 2 Application Security... 4 Data Security and Handling... 4 Database
MigrationWiz Security Overview Table of Contents Introduction... 2 Overview... 2 Shared Security Approach... 2 Customer Best Practices... 2 Application Security... 4 Data Security and Handling... 4 Database
SECURING OFFICE 365 WITH ISOLATION
 SECURING OFFICE 365 EMAIL WITH ISOLATION WHITE PAPER OVERVIEW Introduction Microsoft Office 365 is one of the fastest-growing cloud-based applications today. While many organizations were at first reluctant
SECURING OFFICE 365 EMAIL WITH ISOLATION WHITE PAPER OVERVIEW Introduction Microsoft Office 365 is one of the fastest-growing cloud-based applications today. While many organizations were at first reluctant
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS
 KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
An Executive s FAQ About Authentication
 An Executive s FAQ About Email Authentication Understanding how email authentication helps your organization protect itself from phishing with an approach that s radically different from other security
An Executive s FAQ About Email Authentication Understanding how email authentication helps your organization protect itself from phishing with an approach that s radically different from other security
Barracuda Advanced Threat Protection. Bringing a New Layer of Security for . White Paper
 Barracuda Advanced Threat Protection Bringing a New Layer of Security for Email White Paper Evolving Needs for Protection Against Advanced Threats IT security threats are constantly evolving and improving,
Barracuda Advanced Threat Protection Bringing a New Layer of Security for Email White Paper Evolving Needs for Protection Against Advanced Threats IT security threats are constantly evolving and improving,
How to recognize phishing s
 Phishing email messages, websites, and phone calls are designed to steal money, steal data and/or destroy information. Cybercriminals can do this by installing malicious software on your computer or stealing
Phishing email messages, websites, and phone calls are designed to steal money, steal data and/or destroy information. Cybercriminals can do this by installing malicious software on your computer or stealing
Detecting Credential Spearphishing Attacks in Enterprise Settings
 Detecting Credential Spearphishing Attacks in Enterprise Settings Grant Ho UC Berkeley Aashish Sharma, Mobin Javed, Vern Paxson, David Wagner 1 Spear Phishing Targeted email that tricks victim into giving
Detecting Credential Spearphishing Attacks in Enterprise Settings Grant Ho UC Berkeley Aashish Sharma, Mobin Javed, Vern Paxson, David Wagner 1 Spear Phishing Targeted email that tricks victim into giving
Step 1 - Set Up Essentials for Office 365
 For each Barracuda Cloud Control account, you can have either a linked Barracuda Email Security Gateway appliance or a Barracuda Email Security Service subscription. You cannot use a single Barracuda Cloud
For each Barracuda Cloud Control account, you can have either a linked Barracuda Email Security Gateway appliance or a Barracuda Email Security Service subscription. You cannot use a single Barracuda Cloud
News and Updates June 1, 2017
 Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Introduction. Logging in. WebMail User Guide
 Introduction modusmail s WebMail allows you to access and manage your email, quarantine contents and your mailbox settings through the Internet. This user guide will walk you through each of the tasks
Introduction modusmail s WebMail allows you to access and manage your email, quarantine contents and your mailbox settings through the Internet. This user guide will walk you through each of the tasks
CipherPost Pro Enterprise Dedicated Cloud
 Feature Sheet CipherPost Pro Enterprise Dedicated Cloud Secure messaging and message control that is flexible to data jurisdiction, integrates rapidly into Office 365 and Outlook and supports regulatory
Feature Sheet CipherPost Pro Enterprise Dedicated Cloud Secure messaging and message control that is flexible to data jurisdiction, integrates rapidly into Office 365 and Outlook and supports regulatory
ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS
 PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
Identity & Access Management
 Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Secure access to your enterprise. Enforce risk-based conditional access in real time
 Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
Securing and File Sharing in the Cloud
 Securing Email and File Sharing in the Cloud Your Presenter Erick Simpson Vice President & CIO, SPC International Online A strategic IT business transformation specialist experienced in improving top and
Securing Email and File Sharing in the Cloud Your Presenter Erick Simpson Vice President & CIO, SPC International Online A strategic IT business transformation specialist experienced in improving top and
Microsoft 365. A complete, intelligent, secure solution to empower employees. Integrated for simplicity. Built for teamwork. Unlocks creativity
 2x 50% 5x Microsoft 365 A complete, intelligent, secure solution to empower employees Unlocks creativity Built for teamwork Integrated for simplicity Intelligent security Inner Loop Files Sites Content
2x 50% 5x Microsoft 365 A complete, intelligent, secure solution to empower employees Unlocks creativity Built for teamwork Integrated for simplicity Intelligent security Inner Loop Files Sites Content
Delivering Integrated Cyber Defense for the Cloud Generation Darren Thomson
 Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
