Poketree: A Dynamically Competitive Data Structure with Good Worst-Case Performance
|
|
|
- Gordon Leonard
- 5 years ago
- Views:
Transcription
1 Poketree: A Dynamically Competitive Data Structure with Good Worst-Case Performance Jussi Kujala and Tapio Elomaa Institute of Software Systems Tampere University of Technology P.O. Box 553, FI Tampere, Finland jussi.kujala@tut.fi, elomaa@cs.tut.fi Abstract. We introduce a new O(lg lg n)-competitive binary search tree data structure called poketree that has the advantage of attaining, under worst-case analysis, O(lg n) cost per operation, including updates. Previous O(lg lg n)-competitive binary search tree data structures have not achieved O(lg n) worst-case cost per operation. A standard data structure such as red-black tree or deterministic skip list can be augmented with the dynamic links of a poketree to make it O(lg lg n)-competitive. Our approach also uses less memory per node than previous competitive data structures supporting updates. 1 Introduction Among the most widely used data structures are different binary search trees (BSTs). They support a variety of operations, usually at least searching for a key as well as updating the set of stored items through insertions and deletions. A successful search for a key stored into the BST is called an access. BST data structures are mostly studied by analyzing the cost of serving an arbitrary sequence of operation requests. Moreover, the realistic online BST algorithms, which cannot see future requests, are often contrasted in competitive analysis against offline BST algorithms that have the unrealistic advantage of knowing future requests. Examples of BST algorithms include 2-3 trees, red-black trees [1], B-trees [2], splay trees [3], and an alternative to using the tree structure, skip lists [4,5]. In an attempt to make some progress in resolving the dynamic optimality conjecture of Sleator and Tarjan [3], Demaine et al. [6] recently introduced Tango, an online BST data structure effectively designed to reverse engineer Wilber s [7] first lower bound on the cost of optimal offline BST. Broadly taken the dynamic optimality conjecture proposes that some (self-adjusting) BST data structure working online, possibly splay tree, would be competitive up to a constant factor with the best offline algorithm for any access sequence. Tango does not quite attain constant competitiveness, but Demaine et al. showed an asymptotically small competitive ratio of O(lg lg n) for Tango in a static universe of n keys.
2 Table 1. Known asymptotic upper bounds on the performance of competitive BST algorithms. Memory is given in bits, where letter w is a shorthand for words. Tango MST Poketree Poketree(RB) Poketree(skip) Search, worst-case O(lg lg n lg n) O(lg 2 n) O(lg n) O(lg n) O(lg n) Search, amortized O(lg lg n lg n) O(lg n) O(lg n) O(lg n) O(lg n) insert/delete N/A O(lg 2 n) N/A O(lg n) O(lg 2 n) memory per node 4w+2lg w+2 7w+lg w+1 6w+1 6w+2 4w+lg lg w Prior to this result the best known competitive factor for an online BST data structure was the trivial O(lg n) achieved by any balanced BST. 1 Tango only stores a static set of keys, it does not support update operations on stored data items. It has O(lg n lg lg n) worst-case access cost and cannot guarantee better performance under amortized analysis for all access sequences. 2 Wang, Derryberry, and Sleator [8] put forward a somewhat more practical BST data structure, in the sense that it supports update operations as well, multisplay trees (MST) a hybrid of Tango and splay trees which also attains the double logarithmic competitive ratio O(lg lg n). The worst-case complexity of a MST is O(lg 2 n), but it achieves O(lg n) amortized access cost. The costs for update operations in a MST are similar. MSTs inherit some interesting properties from splay trees; it is, e.g., shown that the sequential access lemma [9] holds for MSTs. In this paper we introduce poketree, which is a generic scheme for attaining O(lg lg n)-competitive BST data structures with different static data structures underlying it. As static data structures we use red-black trees [1] and deterministic skip lists [5]. By using different static data structures we can balance between the amount of augmented information in the nodes and efficiency of operations. In contrast to Tango and MST, poketree has O(lg n) cost per operation under worst-case analysis. The O(lg 2 n) update cost with skip lists can be, in practice, lowered to O(lg n) cost per update [5]. See Table 1 for a summary of the characteristic costs of Tango, MST, and poketree. The contribution of this paper is a dynamically O(lg lg n)-optimal data structure that has the best combination of space and cost requirements with updates supported. Poketree is not a strict binary search tree, because nodes in it can have up to one additional pointer, but it supports the same set of operations. As a side result we give a lower bound to the cost of BST algorithms, proven in a similar manner to the bound of Demaine et al. [6], which has a small increase in the additive term from the previous best of n 2r [8] to n/2 r/2. The remainder of this paper is organized as follows. In Section 2 we explain the lower bound on the cost of offline BST algorithms that we use. It is slightly tighter than the one in [6] and formulated to support other than strict 2-trees. In Section 3 we demonstrate the idea behind poketree in case where the static 1 By lg n, for a positive integer n, we denote log 2 n and define lg 0 = lg 1 = 1. 2 Subsequent manuscripts available at the Internet mention that Tango can be modified to support O(lg n) worst-case access.
3 structure is a perfectly balanced BST with no update operations supported. In Sections 4 and 5 we generalize to other static structures, now supporting update operations. The concluding remarks of this paper are presented in Section 6. 2 Cost Model and the Interleave Bound Because we want to compare the costs of online and offline BST algorithms, we need a formal model of cost. Earlier work [3,7,6,8] has mostly used a model which charges one unit of cost for each node accessed and for each rotation. However, a simpler cost model was used by Demaine et al. [6] in proving a lower bound. They only counted the number of nodes touched in serving an access. A node is touched during an access if the data structure reads or writes information on the node. These two models, and several others, differ at most by a constant factor because a BST can be transformed to any other one containing the same set of keys using a number of rotations that is twice the number of nodes in the tree [10]. We adopt the latter model and take care that no computation is too costly when compared to the number of nodes accessed. Wilber [7] gave two lower bounds on the cost of dynamic BST algorithms; the first of these is also known as the interleave bound. It has been used to prove the O(lg lg n)-competitiveness of the recent online BST algorithms [6,8]. We will also use it to show the O(lg lg n)-competitiveness of poketree. Let us describe the interleave bound briefly. Let P be a static BST on the items that are accessed. The BST P is called a reference tree. It may be a proper BST, 2-3 tree, or any * tree. Using BSTs results in the tightest bound and, hence, they have been used previously. However, we do not necessarily need as tight results as possible, therefore, we give a slightly different version of the interleave bound. We are given an access sequence σ = σ 1,..., σ m that is served using P. For each item i in P define the preferred child of i as the child into whose subtree the most recent access to the subtree of i was directed. Let IB(σ, P, i) be the number of switches of preferred child of i in serving σ. The interleave bound IB(σ, P) is the sum of these over all the nodes of P: i P IB(σ, P, i). Let r be the number of rotations in P while serving σ. Theorem 1. Any dynamic binary search tree algorithm serving an access sequence σ has a cost of at least IB(σ, P)/2 + m n/2 r/2. This bound is slightly tighter than previously known best lower bound IB(σ, P)/2 +m n 2r by Wang, Derryberry, and Sleator [8]. The proof for the new bound is given is given in Appendix B. 3 Poketree A Dynamic Data Structure Let P t be the state of the reference tree P at time t. In addition to P, P t contains information on preferred children. Preferred paths follow preferred child pointers in P t. Both Tango and MST keep each preferred path of a reference
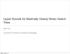
4 tree P t on a separate tree; these trees make up a tree of trees. When the interleave bound on P increases by k, then exactly k subtrees are touched. Moreover, the algorithms provide an efficient way to update the structure to correspond to the new reference tree P t+1. Thus the access cost is at most k lg(# of items on a path) k lg lg n when the data structure for subtrees is chosen suitably. We, rather, augment a standard balanced search structure with dynamic links to support a kind of binary search on preferred paths. The balanced search structure corresponds to the structure of the reference tree, which is used to provide a lower bound on the cost. In our approach we take advantage of the static links in searching for an item, whereas Tango and MST maintain the reference tree information but do not really use it in searching. This enables us to implement update operations using less space than MST. We first describe how our method, called poketree, works on a perfectly balanced tree. In the following sections we relax these assumptions and generalize it to handle trees with less balance and to support update operations insert and delete. Interpreted most strictly, poketree is not really a BST, because items are not necessarily searched through a search tree, but using dynamic links. However, this is rather a philosophical than a practical point, since the same operations are supported in any case. The nodes of a poketree are augmented with a dynamic link to make it dynamically competitive. The idea is to follow a dynamic link whenever possible, and descend via a static link otherwise. Dynamic links allow to efficiently find a desired location on a preferred path and they can be efficiently updated to match the new reference tree P t+1. We consider later the requirement of inserting (removing) an item to the head of a preferred path brought along by supporting insertion (deletion). Let us fix a preferred path a = a 1,..., a l and note that a l is always a leaf in the static tree but a 1 is not necessarily its root. If the dynamic links would implement a binary search on the path a, then it would be possible to travel from a 1 to any a i in lg l lg lg n time. However, this idea does not work as such, because updating dynamic links would be difficult and, even worse, since the preferred path a is a path in a BST, it is not necessarily ordered, making it impossible to carry out binary search on it. For now we just augment each node to contain the smallest and the largest item in the subtree rooted at the node (we later lift this requirement in Section 5). We still have to set the dynamic links to implement a kind of binary search including quick updates to the structure of the preferred paths in P. There are two types of nodes, of type SDD and S. Define a static successor of a node N to be the child in which the last search through N went. The dynamic link of a node of type SDD leads to the same node as following two dynamic links starting from its static successor. A node of type S, on the other hand, has its dynamic link pointing to its static successor. Note that the dynamic links always point lower in the tree, except in the special case of a leaf node. The key trick is to choose the type of a node. The rule for this is as follows. A node is of type SDD if the length of the dynamic link of its successor equals the
5 Fig.1. An example of dynamic links. Static links are omitted, they point always to the next item in the list. The round nodes are of type SDD and the square ones of type S. The node with label 0 is a leaf. length of the dynamic link of the dynamic link of the successor. Otherwise, the node is of type S or a leaf node, which does not have a dynamic link. Observe that to satisfy this requirement, links have to be set up from a leaf to the root. An example of the resulting structure is given in Figure 1. Intuitively, dynamic links let us recursively split a path into two parts and have one dynamic link arc over the first part and another one over the second part. The two Ds in SDD stand for these arcs. Now note that if these links are set from the last item to the first one, the distance that a dynamic link traverses is a function of its distance to the end of the preferred path. Every possible path starting from a particular node is of the same length because we have assumed that a poketree is perfectly balanced. These facts together make it possible to update dynamic links quickly when a preferred path in P changes direction. We describe next the search operation and how to update the structure corresponding to P t to correspond to P t+1. The search attempts at each node to use the dynamic link to potentially skip a number of static links. However, if following the dynamic link leads to a node that does not contain the searched item in the range of items in its subtree, we say that the dynamic link fails. If the dynamic link fails, then the search backtracks to the node where the dynamic link was used and resorts to using the appropriate static pointer. Using a dynamic link has a cost, because an additional node has to be visited. It is possible to augment the parent of a dynamic link with the range information of the dynamic link, but this costs more space. After the searched item has been found, we may have to update those nodes in which a static link was used, because the preferred path may have changed. Assume that we know whether a node is of type S or SDD, for example by reading a bit that contains this information. After performing a search, in going from the bottom to the top, the dynamic link in each node can be (re)set because the the links in the subtree rooted at the preferred child have already been set up. Let us start by stating the most obvious result. Theorem 2. The worst-case cost for any search in a poketree is O(lg n). Proof. Clearly, in the worst case all dynamic links fail because otherwise some static link can be skipped with no cost. Thus, the worst-case cost is bounded to be a constant factor away from the number of static links traversed. This bound is of the order O(lg n) because the static structure is balanced and a constant amount of work is done during each static link.
6 The following theorem states that dynamic links are fast enough. Theorem 3. No more than O(lg lg n) time is spent on a preferred path on the way to the accessed element. The proof is given in Appendix A. Each change in the preferred paths, and subsequently in dynamic links, corresponds to one switch in dynamic pointers. Poketree does at most a constant amount of work for each switch in the dynamic links. Thus, by Theorems 3 and 1, it follows: Theorem 4. Poketree is O(lg lg n)-competitive among the class of all binary search tree algorithms. 4 Insertions and Deletions: Poketree(RB) In previous section we assumed that each root-to-leaf path has the same length. In reality, a data structure must support insertions and deletions and, thus, we cannot rely on idealized perfect balance to make things easy for us. Nevertheless, it is possible to retain the use of dynamic links while supporting these important operations. Some data structures are in a sense always perfectly balanced. For example, in a red-black tree [1,11] every root-to-leaf path has the same number of black nodes and in balanced 2-3 tree implementations the nodes (each containing one or two items) are always in perfect balance. In order to argue competitiveness, we need a cost model that can handle updates. During updates the structure of the reference tree changes to correspond to the static structure of the poketree. An insertion causes a search and insertion to the location in the reference tree where the item should be, and a deletion causes a search to both the deleted item and its successor in the key space, after which the item is deleted as usual. The actual cost charged from an offline BST algorithm is the number of preferred child pointers that switch, more precisely a constant factor of that number. Wang et al. [8] implement updates and use a similar model, which however is not as tight, because in a deletion they search for both predecessor and successor as well as rotate the item in the offline BST to a leaf. We now describe how to support insertion and deletion by using a red-black tree as the static structure. A red-black tree can be viewed as a tree, where a node of the tree corresponds to a black node and its red children. We choose the reference tree P to be the tree of the red-black tree. In the red-black tree the dynamic links point only from black nodes to black nodes. First, note that in the tree view of a red-black tree, the tree increases height only from the top, and when splitting nodes the distance from nodes to leaves stays the same (in the tree). Second, during updates nodes in the red-black tree may switch nodes in the tree, because there might be repaints. Third, it is known that during an update to a red-black tree the amortized number of repaints and the worst-case number of rotations are both constants [12]. The resulting algorithm,
7 poketree(rb), has the same asymptotic competitiveness properties as a perfectly balanced poketree, but now with updates supported. Note that the competitive ratio is not exactly the same, because red nodes are without dynamic links and, thus, there is a constant factor overhead in the competitive ratio. On the other hand, less unnecessary work is done if the access sequence does not conform to a structure that allows a BST algorithm to serve it in less than Θ(m lg n) cost. To support update operations, we must be able to decide the type of a new root S or SDD assuming that the types in the subtree rooted at the root are set up correctly. If we are given such a node, then it is possible to count the number of consecutive SDD nodes its static successor and dynamic link of the static successor have. If these are equal, then the node is of type SDD, otherwise it is of type S. This holds, because the rule for choosing the type of a node depends on the fact that the length of the dynamic link in its successor and in the dynamic link of the successor are the same, which is true if the same number of SDD nodes have been chosen in a row in those two locations. Leaf nodes (tails in a preferred path) make an exception, because they do not have a dynamic link. In poketree each node carries information about the interval of keys in its subtree. In poketree(rb) these bounds are maintained in the form of strict lower and upper bounds, i.e., a lower bound cannot be the smallest key in the tree, but could be the predecessor to the smallest key. The reason is that these bounds can be efficiently handled during updates. To insert a key to a poketree(rb) we need to search for its predecessor and successor (note that there is no need to actually know their values), actually insert it and set the lower and upper bound in the corresponding node, update the dynamic links, and finally fix any violations to red-black invariants while taking care in each repaint of the nodes that the poketree invariant holds in the tree at the level of the current operation. In general a repaint from black to red deletes the dynamic link and a repaint from red to black sets the dynamic link according to the type of the node which can either be obtained from some other node or as described above in the case of a new root node. For completeness we describe what to do during the fixup of the red-black tree as it might not be obvious. These cases correspond to ones in [11, pp ]. Unfortunately, the page limit does not allow for a more complete presentation. Case 1: Swap memory locations of the A and C nodes and set static pointers and dynamic pointer in A. This ensures that dynamic links upper in the tree point to a correct node. Then set the type of D to be the type of C and remove dynamic link in C and set the dynamic link in D. This case represents a split of a node in the tree view. Case 2: Do nothing. Case 3: Swap memory locations of B and C and set the static pointers. Thus B obtains the dynamic link that was in C and dynamic links upper in the tree point to a correct node.
8 Finally, if the root was repainted from red to black, obtain a new type using the procedure described above and set the type info and dynamic link accordingly. Note that we may need to update information about lower and upper bounds on the nodes. The total time of insertion is O(lg n), because the type-procedure needs to be called at most once at the root. A deletion can be implemented using the same ideas as the insertion, but the details are slightly more complicated. In a deletion the following sequence of operations is executed: find the item to be deleted; find its successor by using dynamic links, bound information, and comparing the lower bound to the deleted item; set dynamic links; delete the item as usual; finally, call the RB-fixup to fix possible invariant violations. In fixup there are several cases to consider, but the general idea is that in the tree there might be an extra black with an associated memory address (because a node further up in the tree may point to it through a dynamic link), which floats upper in the tree, and the address might change, until it is assigned in another location. Things to consider during RB-fixup: Case 1: Swap memory locations of B and D items and set the static pointers. Case 2: (There is no dynamic link pointing to D). Delete dynamic information on D. Swap memory location and type of A with the extra black. This represents a merge of two nodes in the tree. Case 3: Swap memory locations of C and D items and set the static pointers. Case 4: Set static pointers, delete dynamic information on D, set type of E to type of D and set the dynamic pointer, swap memory location and type of A with extra black, set memory location and type of B to those of the extra black, set static pointers and update the dynamic pointer on B and A accordingly. If there is an extra black in the root, just delete it and set the type to be the type of a black child node before the update. Note that the lower bound must be set on the nodes along the dynamic links on the preferred path from the successor node to the location where the successor previously was. This ensures that the dynamic links pointing from above of the successor to its subtree do not make a mistake if the successor is later accessed. All operations done during updates have a cost of O(lg lg n) per switch of preferred child pointer in the reference tree. We conclude that poketree(rb) is O(lg lg n)-competitive, even when updates to the tree are taken into account. 5 Reducing Memory Consumption: Poketree(skip) So far we have augmented each node in a poketree with a lower bound and an upper bound on key values in its subtree. This constitutes a problem, since each node consumes two words of precious memory. It is no surprise that it is possible to fare better, as a part of the information about lower and upper bounds seems to be redundant between nodes. We suggest a poketree based on a variant of a deterministic skip list by Munro, Papadakis, and Sedgewick [5].
9 In a skip list items form a list. A node of this list is an array that contains a key, a pointer to the next item in the list, and a varying number of links that point progressively further in the list. More precisely, each additional link on an item points about twice as far as the previous link. The number of additional links on an item is referred to as its height. Approximately 1/2 h th part of the nodes have h additional links and links of same height are nearly uniformly distributed in the list. Thus, the search cost is logarithmic and the total space consumed is upper bound by n + n + n i=1 1/2i = 3n. What makes this structure desirable for us is that if we search for an item and can see only a node of the list, then it is easy to check whether the searched item is between the current node and a node pointed by a link of some particular height. Hence, we can lower the memory overhead of storing bounds for keys in subtrees, but have to fetch one additional node to see its key. A deterministic skip list corresponds to a perfectly balanced 2-3 tree [5]. Using this correspondence, it is possible to relate the performance of a skip list augmented with dynamic links to BST algorithms. More specifically, if there is a dynamic link for each additional static link, then it is possible to associate each dynamic link to a node in the 2-3 tree view. Items between an item and a particular static link on it correspond to a subtree rooted to a node in the 2-3 tree. The dynamic link associated with this static link corresponds to the dynamic link of that node in the 2-3 tree. We do not go into the details, because of lack of space. Insertion and deletion can be implemented similarly as in a poketree(rb). Unfortunately, an insertion takes O(lg 2 n)-time in a deterministic skip list, so we have a trade-off here. However, Munro et al. [5] argue that in practice the update operation can be implemented in O(lg n)-time if memory for nodes is allocated in powers of two. 6 Conclusions We have presented poketree algorithm, which is O(lg lg n)-competitive against the best dynamic offline BST algorithm and that is founded on same ideas as previous such algorithms, like Tango [6]. Our implementation supports update operations, like MST [8] does, and has better worst case performance. Acknowledgments This work was supported by Academy of Finland project INTENTS: Intelligent Online Data Structures. Moreover, the work of J. Kujala is financially supported by Tampere Graduate School in Information Science and Engineering (TISE). References 1. Bayer, R.: Symmetric binary B-trees: Data structure and maintenance algorithms. Acta Informatica 1 (1972)
10 2. Bayer, R., McCreight, E.M.: Organization and maintenance of large ordered indices. Acta Informatica 1 (1972) Sleator, D.D., Tarjan, R.E.: Self-adjusting binary search trees. Journal of the ACM 32(3) (1985) Pugh, W.: Skip lists: A probabilistic alternative to balanced trees. Communications of the ACM 33(6) (1990) Munro, I., Papadakis, T., Sedgewick, R.: Deterministic skip lists. In: Proceedings of the 3rd Annual ACM-SIAM Symposium on Discrete Algorithms, SIAM (1992) Demaine, E.D., Harmon, D., Iacono, J., Pǎtraşcu, M.: Dynamic optimality almost. In: Proceedings of the 45th Annual IEEE Symposium on Foundations of Computer Science, IEEE Computer Society Press (2004) Wilber, R.: Lower bounds for accessing binary search trees with rotations. SIAM Journal on Computing 18(1) (1989) Wang, C.C., Derryberry, J., Sleator, D.D.: O(log log n)-competitive dynamic binary search trees. In: Proceedings of the 17th Annual ACM-SIAM Symposium on Discrete Algorithms, ACM Press (2006) Tarjan, R.E.: Sequential access in splay trees takes linear time. Combinatorica 5(4) (1985) Culik II, K., Wood, D.: A note on some tree similarity measures. Information Processing Letters 15(1) (1982) Cormen, T.H., Leiserson, C.E., Rivest, R.L., Stein, C.: Introduction to Algorithms. Second edn. McGraw-Hill (2001) 12. Tarjan, R.E.: Data Structures and Network Algorithms. SIAM (1983) A Proof of Theorem 3 The definition of dynamic links gives the following recursive rule for the length L(m) of the dynamic link of the mth item counted from the tail of a preferred path. 0 m 1 L(m) = 1 + 2L(m 1) if L(m 1) = L(m 1 L(m 1)) 1 otherwise. Let b 1,...,b j be the items accessed on the preferred path when searching for b j, or the place where the search deviates from the path, and the first item on the path is b 1. Associate to each b i a the length of its dynamic link k i. We will prove that the sequence K = k 1,..., k j is of the form where it first increases and then decreases and, moreover, that no number appears more than twice in a row. Together with the fact that numbers k i are of form L(N) = {0, 1, 3, 7, 15, 31, 63,..., 2 i 1,...} and a maximal k i is at most a length of a root-to-leaf path l this implies that j can be at most 4 lg l 4 lg lg n, if l lg n. As a tool we use a more intuitive presentation of the sequence L(m): L(m) is the mth item in a sequence 0, S, where S is a infinite sequence. Let S 1:i be the prefix of S containing the first i numbers. The sequence S has been generated by repeatedly applying a rule to generate a longer prefix of S: S 1 1:2 = 1, 1 S k 1:2(i+1) = Sk 1 1:i, (i + 1), S k 1 1:i, (i + 1).
11 Here the superscript k counts how many times this rule has been used. Equivalence of these two presentations can be verified by simple induction on k. In induction step assume that numbers in S1:i k equal numbers given by the function L, i.e. S1:i k = L(2),..., L(i + 1). By inductive assumption S k = S k 1, L(i+1), S k 1, L(i+1) and by definition the first i numbers in S k+1 equal S k and S k+1 i+1 = 2L(i+1)+1 = L(i+2). Now, L(i+3) = 1 because L(i+2) must be larger than numbers in L(1),..., L(i+1), and L(i+3) = 1 because L(i+1) > 1 and L(i+2) = 1. In fact, L(2),...,L(i+2) = L(i+3),...,L(2i+3), because L(i+2) is larger than numbers in L(2),..., L(i+1) and thus it behaves like 0 in the definition of L until the number L(i + 2) itself is generated again, which is not until L(2i + 3). Thus L(i + 3),..., L(2i + 4) = S k, 2i + 1 and we can conclude that the correspondence between L and S holds. Let us denote by k M the maximal element in the sequence K. The prefix of K that is k 1,..., k i+1, k i+2,...,k M is a non-decreasing sequence with at most two repetitions of the same value because of the following structure in a subsequence of S: k M,...,k i+1 or k i+2, 1, 1,..., k }{{} i, }{{}..., k i, 2k i + 1. k i 1 items k i 1 items Now the subscript in the item marked by k = (k i+1 or k i+2 ) depends on which k i corresponds to the actual item that is visited during k i in K (we use k i as both an item in the sequence K and a numerical value). Due to the rule generating S, k must be either 0, which is impossible in our case, 2k i +1, or a larger value. On the other hand, k M,...,k i,...,k j is a non-increasing sequence with at most two repetitions of same value, because we can again write a subsequence S as:..., 1, 1,..., k }{{} i, 1, 1,..., k }{{} i, 2k i + 1,...,k M,.... k j is here or here Here the parts indicated by underbraces are of length k i 1. B Proof of Theorem 1 A BST algorithm serving σ = σ 1,..., σ m defines a sequence of trees T 0,...,T m and touches items during each access, let these be connected subtrees S 1,..., S m. In the spirit of Demaine et al. [6], we will play with marbles. Our argument is similar, but not quite the same as theirs. More precisely, for each change of a preferred child, we will place a marble on an item. They are placed so that at any time there is at most one marble on an item. Furthermore, no more than two marbles per item in S j σ j are discarded during σ j. Two can be discarded because after the first discard a new marble might be placed and then discarded. Thus, half of the number of the marbles discarded is a lower bound on the cost of the BST algorithm minus m. The number of marbles discarded can be at most that of marbles placed M placed and is at least M placed n, because there is
12 at most one marble on an item at any given time. So the total cost of any BST algorithm is at least M placed /2 n/2 + m. Note that in our argument the trees T i are BSTs, but P can have nodes with several items. As such, this is not an improvement to the results of Demaine et al., because if for example a 2-3 tree P is given as a BST it gives a tighter bound, but we are able to get a smaller additive term of n/2 to the bound. Let us now describe a method of placing marbles. On an access σ j we first discard marbles on S j σ j. Then for each switch in preferred children a marble is placed. It is placed to the least common ancestor (LCA) in T j of items in the subtree of formerly preferred child. Note that T j is the tree after an access σ j. After placing marbles, again discard marbles on S j σ j. Why are two marbles never on the same item? First, note that distinct subtrees rooted at items in P form continuous intervals in key values. Thus their LCAs must be distinct, because the LCA of a continuous interval belongs to that interval. This implies that marbles placed during the same time step do not mix; the previously preferred subtrees are distinct, so their LCAs are distinct too. Second, marbles placed at different time steps do not mix. To see why, assume that there is an item a that already has a marble when we try to place another on it. Preferred child pointer of a node v changes; it previously pointed to subtree P a of P containing a. Let s 1 be the access during which the first marble was placed and s 2 the access trying to place the second marble. There are two separate cases depending on where the first marble has been placed: above of v in P or on v or below it. In the first case we must either have touched a during the access to s 2, because a must have been an ancestor of s 2, or a must have been touched while it was rotated from being an ancestor to s 2. In the second case the first marble has been placed on v or in P a and a has been touched when an item in P a was last accessed, which must be after or during s 1 because the preferred child pointer of v points to P a and s 1 is in P a. In any case, a cannot hold the first marble anymore and the second marble can be safely inserted to a. Assume now that we may do rotations on BST P. What happens if we rotate an item a above of b? If before the rotation tree P was safe in the sense that an access to any item would not place two marbles on the same item, then by removing a marble from a certain item on P, we can guarantee that after the rotation the new tree P is safe as well. To find this item, note that preferred child pointers of a and b point to two subtrees and it is safe to switch the pointers to these subtrees and place a marble to the LCA of those subtrees. After the rotation, if the preferred child pointers are set to their natural places, at most one of these two pointers points to a different tree (this can be verified by going through all four eight, counting the mirror images possible cases). If we remove the marble on the LCA of the items in this tree, then P is safe. This implies a lower bound of (IB(σ, P) n r)/2 + m, where r is the number of rotations. This is the tightest known bound formulated using a reference tree P.
3 Competitive Dynamic BSTs (January 31 and February 2)
 3 Competitive Dynamic BSTs (January 31 and February ) In their original paper on splay trees [3], Danny Sleator and Bob Tarjan conjectured that the cost of sequence of searches in a splay tree is within
3 Competitive Dynamic BSTs (January 31 and February ) In their original paper on splay trees [3], Danny Sleator and Bob Tarjan conjectured that the cost of sequence of searches in a splay tree is within
Lecture 3 February 20, 2007
 6.897: Advanced Data Structures Spring 2007 Prof. Erik Demaine Lecture 3 February 20, 2007 Scribe: Hui Tang 1 Overview In the last lecture we discussed Binary Search Trees and the many bounds which achieve
6.897: Advanced Data Structures Spring 2007 Prof. Erik Demaine Lecture 3 February 20, 2007 Scribe: Hui Tang 1 Overview In the last lecture we discussed Binary Search Trees and the many bounds which achieve
Dynamic Optimality Almost
 Dynamic Optimality Almost Erik D. Demaine Dion Harmon John Iacono Mihai Pǎtraşcu Abstract We present an O(lg lg n)-competitive online binary search tree, improving upon the best previous (trivial) competitive
Dynamic Optimality Almost Erik D. Demaine Dion Harmon John Iacono Mihai Pǎtraşcu Abstract We present an O(lg lg n)-competitive online binary search tree, improving upon the best previous (trivial) competitive
Dynamic Optimality Almost
 ynamic Optimality Almost Erik. emaine ion Harmon John Iacono Mihai Pǎtraşcu Abstract We present an O(lg lg n)-competitive online binary search tree, improving upon the best previous (trivial) competitive
ynamic Optimality Almost Erik. emaine ion Harmon John Iacono Mihai Pǎtraşcu Abstract We present an O(lg lg n)-competitive online binary search tree, improving upon the best previous (trivial) competitive
Dynamic Optimality and Multi-Splay Trees 1
 Dynamic Optimality and Multi-Splay Trees 1 Daniel Dominic Sleator and Chengwen Chris Wang November 5, 2004 CMU-CS-04-171 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Abstract
Dynamic Optimality and Multi-Splay Trees 1 Daniel Dominic Sleator and Chengwen Chris Wang November 5, 2004 CMU-CS-04-171 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Abstract
A Distribution-Sensitive Dictionary with Low Space Overhead
 A Distribution-Sensitive Dictionary with Low Space Overhead Prosenjit Bose, John Howat, and Pat Morin School of Computer Science, Carleton University 1125 Colonel By Dr., Ottawa, Ontario, CANADA, K1S 5B6
A Distribution-Sensitive Dictionary with Low Space Overhead Prosenjit Bose, John Howat, and Pat Morin School of Computer Science, Carleton University 1125 Colonel By Dr., Ottawa, Ontario, CANADA, K1S 5B6
arxiv: v1 [cs.ds] 13 Jul 2009
![arxiv: v1 [cs.ds] 13 Jul 2009 arxiv: v1 [cs.ds] 13 Jul 2009](/thumbs/74/69732557.jpg) Layered Working-Set Trees Prosenjit Bose Karim Douïeb Vida Dujmović John Howat arxiv:0907.2071v1 [cs.ds] 13 Jul 2009 Abstract The working-set bound [Sleator and Tarjan, J. ACM, 1985] roughly states that
Layered Working-Set Trees Prosenjit Bose Karim Douïeb Vida Dujmović John Howat arxiv:0907.2071v1 [cs.ds] 13 Jul 2009 Abstract The working-set bound [Sleator and Tarjan, J. ACM, 1985] roughly states that
Lecture 2 February 4, 2010
 6.897: Advanced Data Structures Spring 010 Prof. Erik Demaine Lecture February 4, 010 1 Overview In the last lecture we discussed Binary Search Trees(BST) and introduced them as a model of computation.
6.897: Advanced Data Structures Spring 010 Prof. Erik Demaine Lecture February 4, 010 1 Overview In the last lecture we discussed Binary Search Trees(BST) and introduced them as a model of computation.
Upper Bounds for Maximally Greedy Binary Search Trees
 Upper Bounds for Maximally Greedy Binary Search Trees Kyle Fox -- University of Illinois at Urbana-Champaign Balanced Binary Search Trees Want data structures for dictionary, predecessor search, etc. Red-black
Upper Bounds for Maximally Greedy Binary Search Trees Kyle Fox -- University of Illinois at Urbana-Champaign Balanced Binary Search Trees Want data structures for dictionary, predecessor search, etc. Red-black
Treaps. 1 Binary Search Trees (BSTs) CSE341T/CSE549T 11/05/2014. Lecture 19
 CSE34T/CSE549T /05/04 Lecture 9 Treaps Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types
CSE34T/CSE549T /05/04 Lecture 9 Treaps Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types
Lecture 5. Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
 Lecture 5 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs Reading: Randomized Search Trees by Aragon & Seidel, Algorithmica 1996, http://sims.berkeley.edu/~aragon/pubs/rst96.pdf;
Lecture 5 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs Reading: Randomized Search Trees by Aragon & Seidel, Algorithmica 1996, http://sims.berkeley.edu/~aragon/pubs/rst96.pdf;
DYNAMIC OPTIMALITY ALMOST
 DYNAMIC OPTIMALITY ALMOST ERIK D. DEMAINE, DION HARMON, JOHN IACONO, AND MIHAI PǍTRAŞCU Abstract. We present an O(lg lg n)-competitive online binary search tree, improving upon the best previous (trivial)
DYNAMIC OPTIMALITY ALMOST ERIK D. DEMAINE, DION HARMON, JOHN IACONO, AND MIHAI PǍTRAŞCU Abstract. We present an O(lg lg n)-competitive online binary search tree, improving upon the best previous (trivial)
Deterministic Jumplists
 Nordic Journal of Computing Deterministic Jumplists Amr Elmasry Department of Computer Engineering and Systems Alexandria University, Egypt elmasry@alexeng.edu.eg Abstract. We give a deterministic version
Nordic Journal of Computing Deterministic Jumplists Amr Elmasry Department of Computer Engineering and Systems Alexandria University, Egypt elmasry@alexeng.edu.eg Abstract. We give a deterministic version
ICS 691: Advanced Data Structures Spring Lecture 3
 ICS 691: Advanced Data Structures Spring 2016 Prof. Nodari Sitchinava Lecture 3 Scribe: Ben Karsin 1 Overview In the last lecture we started looking at self-adjusting data structures, specifically, move-to-front
ICS 691: Advanced Data Structures Spring 2016 Prof. Nodari Sitchinava Lecture 3 Scribe: Ben Karsin 1 Overview In the last lecture we started looking at self-adjusting data structures, specifically, move-to-front
CSE100. Advanced Data Structures. Lecture 8. (Based on Paul Kube course materials)
 CSE100 Advanced Data Structures Lecture 8 (Based on Paul Kube course materials) CSE 100 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
CSE100 Advanced Data Structures Lecture 8 (Based on Paul Kube course materials) CSE 100 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
Lecture 4 Feb 21, 2007
 6.897: Advanced Data Structures Spring 2007 Prof. Erik Demaine Lecture 4 Feb 21, 2007 Scribe: Mashhood Ishaque 1 Overview In the last lecture we worked in a BST model. We discussed Wilber lower bounds
6.897: Advanced Data Structures Spring 2007 Prof. Erik Demaine Lecture 4 Feb 21, 2007 Scribe: Mashhood Ishaque 1 Overview In the last lecture we worked in a BST model. We discussed Wilber lower bounds
Search Trees. Undirected graph Directed graph Tree Binary search tree
 Search Trees Undirected graph Directed graph Tree Binary search tree 1 Binary Search Tree Binary search key property: Let x be a node in a binary search tree. If y is a node in the left subtree of x, then
Search Trees Undirected graph Directed graph Tree Binary search tree 1 Binary Search Tree Binary search key property: Let x be a node in a binary search tree. If y is a node in the left subtree of x, then
A Fast Algorithm for Optimal Alignment between Similar Ordered Trees
 Fundamenta Informaticae 56 (2003) 105 120 105 IOS Press A Fast Algorithm for Optimal Alignment between Similar Ordered Trees Jesper Jansson Department of Computer Science Lund University, Box 118 SE-221
Fundamenta Informaticae 56 (2003) 105 120 105 IOS Press A Fast Algorithm for Optimal Alignment between Similar Ordered Trees Jesper Jansson Department of Computer Science Lund University, Box 118 SE-221
Advanced Algorithms. Class Notes for Thursday, September 18, 2014 Bernard Moret
 Advanced Algorithms Class Notes for Thursday, September 18, 2014 Bernard Moret 1 Amortized Analysis (cont d) 1.1 Side note: regarding meldable heaps When we saw how to meld two leftist trees, we did not
Advanced Algorithms Class Notes for Thursday, September 18, 2014 Bernard Moret 1 Amortized Analysis (cont d) 1.1 Side note: regarding meldable heaps When we saw how to meld two leftist trees, we did not
Efficient Access to Non-Sequential Elements of a Search Tree
 Efficient Access to Non-Sequential Elements of a Search Tree Lubomir Stanchev Computer Science Department Indiana University - Purdue University Fort Wayne Fort Wayne, IN, USA stanchel@ipfw.edu Abstract
Efficient Access to Non-Sequential Elements of a Search Tree Lubomir Stanchev Computer Science Department Indiana University - Purdue University Fort Wayne Fort Wayne, IN, USA stanchel@ipfw.edu Abstract
Efficient Non-Sequential Access and More Ordering Choices in a Search Tree
 Efficient Non-Sequential Access and More Ordering Choices in a Search Tree Lubomir Stanchev Computer Science Department Indiana University - Purdue University Fort Wayne Fort Wayne, IN, USA stanchel@ipfw.edu
Efficient Non-Sequential Access and More Ordering Choices in a Search Tree Lubomir Stanchev Computer Science Department Indiana University - Purdue University Fort Wayne Fort Wayne, IN, USA stanchel@ipfw.edu
Abstract Relaxed balancing of search trees was introduced with the aim of speeding up the updates and allowing a high degree of concurrency. In a rela
 Chromatic Search Trees Revisited Institut fur Informatik Report 9 Sabine Hanke Institut fur Informatik, Universitat Freiburg Am Flughafen 7, 79 Freiburg, Germany Email: hanke@informatik.uni-freiburg.de.
Chromatic Search Trees Revisited Institut fur Informatik Report 9 Sabine Hanke Institut fur Informatik, Universitat Freiburg Am Flughafen 7, 79 Freiburg, Germany Email: hanke@informatik.uni-freiburg.de.
Efficient pebbling for list traversal synopses
 Efficient pebbling for list traversal synopses Yossi Matias Ely Porat Tel Aviv University Bar-Ilan University & Tel Aviv University Abstract 1 Introduction 1.1 Applications Consider a program P running
Efficient pebbling for list traversal synopses Yossi Matias Ely Porat Tel Aviv University Bar-Ilan University & Tel Aviv University Abstract 1 Introduction 1.1 Applications Consider a program P running
Randomized Splay Trees Final Project
 Randomized Splay Trees 6.856 Final Project Robi Bhattacharjee robibhat@mit.edu Ben Eysenbach bce@mit.edu May 17, 2016 Abstract We propose a randomization scheme for splay trees with the same time complexity
Randomized Splay Trees 6.856 Final Project Robi Bhattacharjee robibhat@mit.edu Ben Eysenbach bce@mit.edu May 17, 2016 Abstract We propose a randomization scheme for splay trees with the same time complexity
CS60020: Foundations of Algorithm Design and Machine Learning. Sourangshu Bhattacharya
 CS62: Foundations of Algorithm Design and Machine Learning Sourangshu Bhattacharya Binary Search Tree - Best Time All BST operations are O(d), where d is tree depth minimum d is d = ëlog for a binary tree
CS62: Foundations of Algorithm Design and Machine Learning Sourangshu Bhattacharya Binary Search Tree - Best Time All BST operations are O(d), where d is tree depth minimum d is d = ëlog for a binary tree
Binary Trees. BSTs. For example: Jargon: Data Structures & Algorithms. root node. level: internal node. edge.
 Binary Trees 1 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the root, which are disjoint from
Binary Trees 1 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the root, which are disjoint from
CS60020: Foundations of Algorithm Design and Machine Learning. Sourangshu Bhattacharya
 CS62: Foundations of Algorithm Design and Machine Learning Sourangshu Bhattacharya Balanced search trees Balanced search tree: A search-tree data structure for which a height of O(lg n) is guaranteed when
CS62: Foundations of Algorithm Design and Machine Learning Sourangshu Bhattacharya Balanced search trees Balanced search tree: A search-tree data structure for which a height of O(lg n) is guaranteed when
where is a constant, 0 < <. In other words, the ratio between the shortest and longest paths from a node to a leaf is at least. An BB-tree allows ecie
 Maintaining -balanced Trees by Partial Rebuilding Arne Andersson Department of Computer Science Lund University Box 8 S-22 00 Lund Sweden Abstract The balance criterion dening the class of -balanced trees
Maintaining -balanced Trees by Partial Rebuilding Arne Andersson Department of Computer Science Lund University Box 8 S-22 00 Lund Sweden Abstract The balance criterion dening the class of -balanced trees
Algorithms. AVL Tree
 Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
Lecture 8 13 March, 2012
 6.851: Advanced Data Structures Spring 2012 Prof. Erik Demaine Lecture 8 13 March, 2012 1 From Last Lectures... In the previous lecture, we discussed the External Memory and Cache Oblivious memory models.
6.851: Advanced Data Structures Spring 2012 Prof. Erik Demaine Lecture 8 13 March, 2012 1 From Last Lectures... In the previous lecture, we discussed the External Memory and Cache Oblivious memory models.
9/29/2016. Chapter 4 Trees. Introduction. Terminology. Terminology. Terminology. Terminology
 Introduction Chapter 4 Trees for large input, even linear access time may be prohibitive we need data structures that exhibit average running times closer to O(log N) binary search tree 2 Terminology recursive
Introduction Chapter 4 Trees for large input, even linear access time may be prohibitive we need data structures that exhibit average running times closer to O(log N) binary search tree 2 Terminology recursive
Red-black tree. Background and terminology. Uses and advantages
 Red-black tree A red-black tree is a type of self-balancing binary search tree, a data structure used in computer science, typically used to implement associative arrays. The original structure was invented
Red-black tree A red-black tree is a type of self-balancing binary search tree, a data structure used in computer science, typically used to implement associative arrays. The original structure was invented
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/27/17
 01.433/33 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/2/1.1 Introduction In this lecture we ll talk about a useful abstraction, priority queues, which are
01.433/33 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/2/1.1 Introduction In this lecture we ll talk about a useful abstraction, priority queues, which are
Quiz 1 Solutions. (a) f(n) = n g(n) = log n Circle all that apply: f = O(g) f = Θ(g) f = Ω(g)
 Introduction to Algorithms March 11, 2009 Massachusetts Institute of Technology 6.006 Spring 2009 Professors Sivan Toledo and Alan Edelman Quiz 1 Solutions Problem 1. Quiz 1 Solutions Asymptotic orders
Introduction to Algorithms March 11, 2009 Massachusetts Institute of Technology 6.006 Spring 2009 Professors Sivan Toledo and Alan Edelman Quiz 1 Solutions Problem 1. Quiz 1 Solutions Asymptotic orders
arxiv: v2 [cs.ds] 9 Apr 2009
![arxiv: v2 [cs.ds] 9 Apr 2009 arxiv: v2 [cs.ds] 9 Apr 2009](/thumbs/72/66843812.jpg) Pairing Heaps with Costless Meld arxiv:09034130v2 [csds] 9 Apr 2009 Amr Elmasry Max-Planck Institut für Informatik Saarbrücken, Germany elmasry@mpi-infmpgde Abstract Improving the structure and analysis
Pairing Heaps with Costless Meld arxiv:09034130v2 [csds] 9 Apr 2009 Amr Elmasry Max-Planck Institut für Informatik Saarbrücken, Germany elmasry@mpi-infmpgde Abstract Improving the structure and analysis
1 The range query problem
 CS268: Geometric Algorithms Handout #12 Design and Analysis Original Handout #12 Stanford University Thursday, 19 May 1994 Original Lecture #12: Thursday, May 19, 1994 Topics: Range Searching with Partition
CS268: Geometric Algorithms Handout #12 Design and Analysis Original Handout #12 Stanford University Thursday, 19 May 1994 Original Lecture #12: Thursday, May 19, 1994 Topics: Range Searching with Partition
V Advanced Data Structures
 V Advanced Data Structures B-Trees Fibonacci Heaps 18 B-Trees B-trees are similar to RBTs, but they are better at minimizing disk I/O operations Many database systems use B-trees, or variants of them,
V Advanced Data Structures B-Trees Fibonacci Heaps 18 B-Trees B-trees are similar to RBTs, but they are better at minimizing disk I/O operations Many database systems use B-trees, or variants of them,
Outline. Definition. 2 Height-Balance. 3 Searches. 4 Rotations. 5 Insertion. 6 Deletions. 7 Reference. 1 Every node is either red or black.
 Outline 1 Definition Computer Science 331 Red-Black rees Mike Jacobson Department of Computer Science University of Calgary Lectures #20-22 2 Height-Balance 3 Searches 4 Rotations 5 s: Main Case 6 Partial
Outline 1 Definition Computer Science 331 Red-Black rees Mike Jacobson Department of Computer Science University of Calgary Lectures #20-22 2 Height-Balance 3 Searches 4 Rotations 5 s: Main Case 6 Partial
Lecture 9 March 4, 2010
 6.851: Advanced Data Structures Spring 010 Dr. André Schulz Lecture 9 March 4, 010 1 Overview Last lecture we defined the Least Common Ancestor (LCA) and Range Min Query (RMQ) problems. Recall that an
6.851: Advanced Data Structures Spring 010 Dr. André Schulz Lecture 9 March 4, 010 1 Overview Last lecture we defined the Least Common Ancestor (LCA) and Range Min Query (RMQ) problems. Recall that an
Lecture 3 February 9, 2010
 6.851: Advanced Data Structures Spring 2010 Dr. André Schulz Lecture 3 February 9, 2010 Scribe: Jacob Steinhardt and Greg Brockman 1 Overview In the last lecture we continued to study binary search trees
6.851: Advanced Data Structures Spring 2010 Dr. André Schulz Lecture 3 February 9, 2010 Scribe: Jacob Steinhardt and Greg Brockman 1 Overview In the last lecture we continued to study binary search trees
arxiv: v3 [cs.ds] 18 Apr 2011
![arxiv: v3 [cs.ds] 18 Apr 2011 arxiv: v3 [cs.ds] 18 Apr 2011](/thumbs/84/89362283.jpg) A tight bound on the worst-case number of comparisons for Floyd s heap construction algorithm Ioannis K. Paparrizos School of Computer and Communication Sciences Ècole Polytechnique Fèdèrale de Lausanne
A tight bound on the worst-case number of comparisons for Floyd s heap construction algorithm Ioannis K. Paparrizos School of Computer and Communication Sciences Ècole Polytechnique Fèdèrale de Lausanne
Properties of red-black trees
 Red-Black Trees Introduction We have seen that a binary search tree is a useful tool. I.e., if its height is h, then we can implement any basic operation on it in O(h) units of time. The problem: given
Red-Black Trees Introduction We have seen that a binary search tree is a useful tool. I.e., if its height is h, then we can implement any basic operation on it in O(h) units of time. The problem: given
V Advanced Data Structures
 V Advanced Data Structures B-Trees Fibonacci Heaps 18 B-Trees B-trees are similar to RBTs, but they are better at minimizing disk I/O operations Many database systems use B-trees, or variants of them,
V Advanced Data Structures B-Trees Fibonacci Heaps 18 B-Trees B-trees are similar to RBTs, but they are better at minimizing disk I/O operations Many database systems use B-trees, or variants of them,
Algorithms. Red-Black Trees
 Algorithms Red-Black Trees Red-Black Trees Balanced binary search trees guarantee an O(log n) running time Red-black-tree Binary search tree with an additional attribute for its nodes: color which can
Algorithms Red-Black Trees Red-Black Trees Balanced binary search trees guarantee an O(log n) running time Red-black-tree Binary search tree with an additional attribute for its nodes: color which can
ADAPTIVE SORTING WITH AVL TREES
 ADAPTIVE SORTING WITH AVL TREES Amr Elmasry Computer Science Department Alexandria University Alexandria, Egypt elmasry@alexeng.edu.eg Abstract A new adaptive sorting algorithm is introduced. The new implementation
ADAPTIVE SORTING WITH AVL TREES Amr Elmasry Computer Science Department Alexandria University Alexandria, Egypt elmasry@alexeng.edu.eg Abstract A new adaptive sorting algorithm is introduced. The new implementation
We assume uniform hashing (UH):
 We assume uniform hashing (UH): the probe sequence of each key is equally likely to be any of the! permutations of 0,1,, 1 UH generalizes the notion of SUH that produces not just a single number, but a
We assume uniform hashing (UH): the probe sequence of each key is equally likely to be any of the! permutations of 0,1,, 1 UH generalizes the notion of SUH that produces not just a single number, but a
arxiv: v3 [cs.ds] 3 Apr 2018
![arxiv: v3 [cs.ds] 3 Apr 2018 arxiv: v3 [cs.ds] 3 Apr 2018](/thumbs/87/96355553.jpg) arxiv:1711.07746v3 [cs.ds] 3 Apr 2018 The Hidden Binary Search Tree: A Balanced Rotation-Free Search Tree in the AVL RAM Model Saulo Queiroz Email: sauloqueiroz@utfpr.edu.br Academic Department of Informatics
arxiv:1711.07746v3 [cs.ds] 3 Apr 2018 The Hidden Binary Search Tree: A Balanced Rotation-Free Search Tree in the AVL RAM Model Saulo Queiroz Email: sauloqueiroz@utfpr.edu.br Academic Department of Informatics
Problem Set 5 Solutions
 Introduction to Algorithms November 4, 2005 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik D. Demaine and Charles E. Leiserson Handout 21 Problem Set 5 Solutions Problem 5-1. Skip
Introduction to Algorithms November 4, 2005 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik D. Demaine and Charles E. Leiserson Handout 21 Problem Set 5 Solutions Problem 5-1. Skip
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1
![1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1](/thumbs/85/92778785.jpg) Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 2. O(n) 2. [1 pt] What is the solution to the recurrence T(n) = T(n/2) + n, T(1)
Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 2. O(n) 2. [1 pt] What is the solution to the recurrence T(n) = T(n/2) + n, T(1)
l So unlike the search trees, there are neither arbitrary find operations nor arbitrary delete operations possible.
 DDS-Heaps 1 Heaps - basics l Heaps an abstract structure where each object has a key value (the priority), and the operations are: insert an object, find the object of minimum key (find min), and delete
DDS-Heaps 1 Heaps - basics l Heaps an abstract structure where each object has a key value (the priority), and the operations are: insert an object, find the object of minimum key (find min), and delete
DDS Dynamic Search Trees
 DDS Dynamic Search Trees 1 Data structures l A data structure models some abstract object. It implements a number of operations on this object, which usually can be classified into l creation and deletion
DDS Dynamic Search Trees 1 Data structures l A data structure models some abstract object. It implements a number of operations on this object, which usually can be classified into l creation and deletion
8.1. Optimal Binary Search Trees:
 DATA STRUCTERS WITH C 10CS35 UNIT 8 : EFFICIENT BINARY SEARCH TREES 8.1. Optimal Binary Search Trees: An optimal binary search tree is a binary search tree for which the nodes are arranged on levels such
DATA STRUCTERS WITH C 10CS35 UNIT 8 : EFFICIENT BINARY SEARCH TREES 8.1. Optimal Binary Search Trees: An optimal binary search tree is a binary search tree for which the nodes are arranged on levels such
Algorithm 23 works. Instead of a spanning tree, one can use routing.
 Chapter 5 Shared Objects 5.1 Introduction Assume that there is a common resource (e.g. a common variable or data structure), which different nodes in a network need to access from time to time. If the
Chapter 5 Shared Objects 5.1 Introduction Assume that there is a common resource (e.g. a common variable or data structure), which different nodes in a network need to access from time to time. If the
Solutions. Suppose we insert all elements of U into the table, and let n(b) be the number of elements of U that hash to bucket b. Then.
 Assignment 3 1. Exercise [11.2-3 on p. 229] Modify hashing by chaining (i.e., bucketvector with BucketType = List) so that BucketType = OrderedList. How is the runtime of search, insert, and remove affected?
Assignment 3 1. Exercise [11.2-3 on p. 229] Modify hashing by chaining (i.e., bucketvector with BucketType = List) so that BucketType = OrderedList. How is the runtime of search, insert, and remove affected?
Introduction. for large input, even access time may be prohibitive we need data structures that exhibit times closer to O(log N) binary search tree
 Chapter 4 Trees 2 Introduction for large input, even access time may be prohibitive we need data structures that exhibit running times closer to O(log N) binary search tree 3 Terminology recursive definition
Chapter 4 Trees 2 Introduction for large input, even access time may be prohibitive we need data structures that exhibit running times closer to O(log N) binary search tree 3 Terminology recursive definition
Cuckoo Hashing for Undergraduates
 Cuckoo Hashing for Undergraduates Rasmus Pagh IT University of Copenhagen March 27, 2006 Abstract This lecture note presents and analyses two simple hashing algorithms: Hashing with Chaining, and Cuckoo
Cuckoo Hashing for Undergraduates Rasmus Pagh IT University of Copenhagen March 27, 2006 Abstract This lecture note presents and analyses two simple hashing algorithms: Hashing with Chaining, and Cuckoo
CS521 \ Notes for the Final Exam
 CS521 \ Notes for final exam 1 Ariel Stolerman Asymptotic Notations: CS521 \ Notes for the Final Exam Notation Definition Limit Big-O ( ) Small-o ( ) Big- ( ) Small- ( ) Big- ( ) Notes: ( ) ( ) ( ) ( )
CS521 \ Notes for final exam 1 Ariel Stolerman Asymptotic Notations: CS521 \ Notes for the Final Exam Notation Definition Limit Big-O ( ) Small-o ( ) Big- ( ) Small- ( ) Big- ( ) Notes: ( ) ( ) ( ) ( )
Red-Black Trees. Based on materials by Dennis Frey, Yun Peng, Jian Chen, and Daniel Hood
 Red-Black Trees Based on materials by Dennis Frey, Yun Peng, Jian Chen, and Daniel Hood Quick Review of Binary Search Trees n Given a node n... q All elements of n s left subtree are less than n.data q
Red-Black Trees Based on materials by Dennis Frey, Yun Peng, Jian Chen, and Daniel Hood Quick Review of Binary Search Trees n Given a node n... q All elements of n s left subtree are less than n.data q
Sorted Arrays. Operation Access Search Selection Predecessor Successor Output (print) Insert Delete Extract-Min
 Binary Search Trees FRIDAY ALGORITHMS Sorted Arrays Operation Access Search Selection Predecessor Successor Output (print) Insert Delete Extract-Min 6 10 11 17 2 0 6 Running Time O(1) O(lg n) O(1) O(1)
Binary Search Trees FRIDAY ALGORITHMS Sorted Arrays Operation Access Search Selection Predecessor Successor Output (print) Insert Delete Extract-Min 6 10 11 17 2 0 6 Running Time O(1) O(lg n) O(1) O(1)
l Heaps very popular abstract data structure, where each object has a key value (the priority), and the operations are:
 DDS-Heaps 1 Heaps - basics l Heaps very popular abstract data structure, where each object has a key value (the priority), and the operations are: l insert an object, find the object of minimum key (find
DDS-Heaps 1 Heaps - basics l Heaps very popular abstract data structure, where each object has a key value (the priority), and the operations are: l insert an object, find the object of minimum key (find
Multi-way Search Trees! M-Way Search! M-Way Search Trees Representation!
 Lecture 10: Multi-way Search Trees: intro to B-trees 2-3 trees 2-3-4 trees Multi-way Search Trees A node on an M-way search tree with M 1 distinct and ordered keys: k 1 < k 2 < k 3
Lecture 10: Multi-way Search Trees: intro to B-trees 2-3 trees 2-3-4 trees Multi-way Search Trees A node on an M-way search tree with M 1 distinct and ordered keys: k 1 < k 2 < k 3
Distributed minimum spanning tree problem
 Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
On k-dimensional Balanced Binary Trees*
 journal of computer and system sciences 52, 328348 (1996) article no. 0025 On k-dimensional Balanced Binary Trees* Vijay K. Vaishnavi Department of Computer Information Systems, Georgia State University,
journal of computer and system sciences 52, 328348 (1996) article no. 0025 On k-dimensional Balanced Binary Trees* Vijay K. Vaishnavi Department of Computer Information Systems, Georgia State University,
Ensures that no such path is more than twice as long as any other, so that the tree is approximately balanced
 13 Red-Black Trees A red-black tree (RBT) is a BST with one extra bit of storage per node: color, either RED or BLACK Constraining the node colors on any path from the root to a leaf Ensures that no such
13 Red-Black Trees A red-black tree (RBT) is a BST with one extra bit of storage per node: color, either RED or BLACK Constraining the node colors on any path from the root to a leaf Ensures that no such
9/24/ Hash functions
 11.3 Hash functions A good hash function satis es (approximately) the assumption of SUH: each key is equally likely to hash to any of the slots, independently of the other keys We typically have no way
11.3 Hash functions A good hash function satis es (approximately) the assumption of SUH: each key is equally likely to hash to any of the slots, independently of the other keys We typically have no way
Lecture 3: B-Trees. October Lecture 3: B-Trees
 October 2017 Remarks Search trees The dynamic set operations search, minimum, maximum, successor, predecessor, insert and del can be performed efficiently (in O(log n) time) if the search tree is balanced.
October 2017 Remarks Search trees The dynamic set operations search, minimum, maximum, successor, predecessor, insert and del can be performed efficiently (in O(log n) time) if the search tree is balanced.
CSE 502 Class 16. Jeremy Buhler Steve Cole. March A while back, we introduced the idea of collections to put hash tables in context.
 CSE 502 Class 16 Jeremy Buhler Steve Cole March 17 2015 Onwards to trees! 1 Collection Types Revisited A while back, we introduced the idea of collections to put hash tables in context. abstract data types
CSE 502 Class 16 Jeremy Buhler Steve Cole March 17 2015 Onwards to trees! 1 Collection Types Revisited A while back, we introduced the idea of collections to put hash tables in context. abstract data types
II (Sorting and) Order Statistics
 II (Sorting and) Order Statistics Heapsort Quicksort Sorting in Linear Time Medians and Order Statistics 8 Sorting in Linear Time The sorting algorithms introduced thus far are comparison sorts Any comparison
II (Sorting and) Order Statistics Heapsort Quicksort Sorting in Linear Time Medians and Order Statistics 8 Sorting in Linear Time The sorting algorithms introduced thus far are comparison sorts Any comparison
6 Distributed data management I Hashing
 6 Distributed data management I Hashing There are two major approaches for the management of data in distributed systems: hashing and caching. The hashing approach tries to minimize the use of communication
6 Distributed data management I Hashing There are two major approaches for the management of data in distributed systems: hashing and caching. The hashing approach tries to minimize the use of communication
Randomized Ternary Search Tries
 Randomized Ternary Search Tries icolai Diethelm bstract simple method for maintaining balance in ternary search tries is presented. The new kind of selfbalancing ternary search trie, called an r-trie,
Randomized Ternary Search Tries icolai Diethelm bstract simple method for maintaining balance in ternary search tries is presented. The new kind of selfbalancing ternary search trie, called an r-trie,
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Binary Search Trees CLRS 12.2, 12.3, 13.2, read problem 13-3 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Binary Search Trees CLRS 12.2, 12.3, 13.2, read problem 13-3 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures
Multi-Way Search Trees
 Multi-Way Search Trees Manolis Koubarakis 1 Multi-Way Search Trees Multi-way trees are trees such that each internal node can have many children. Let us assume that the entries we store in a search tree
Multi-Way Search Trees Manolis Koubarakis 1 Multi-Way Search Trees Multi-way trees are trees such that each internal node can have many children. Let us assume that the entries we store in a search tree
The Geometry of Binary Search Trees
 The Geometry of Binary Search Trees Erik Demaine MIT John Iacono Poly Inst. of NYU Dion Harmon NECSI Daniel Kane Harvard Mihai Pătraşcu IBM Almaden ASS Point set in the plane ASS = any nontrivial rectangle
The Geometry of Binary Search Trees Erik Demaine MIT John Iacono Poly Inst. of NYU Dion Harmon NECSI Daniel Kane Harvard Mihai Pătraşcu IBM Almaden ASS Point set in the plane ASS = any nontrivial rectangle
Quake Heaps: A Simple Alternative to Fibonacci Heaps
 Quake Heaps: A Simple Alternative to Fibonacci Heaps Timothy M. Chan Cheriton School of Computer Science, University of Waterloo, Waterloo, Ontario N2L G, Canada, tmchan@uwaterloo.ca Abstract. This note
Quake Heaps: A Simple Alternative to Fibonacci Heaps Timothy M. Chan Cheriton School of Computer Science, University of Waterloo, Waterloo, Ontario N2L G, Canada, tmchan@uwaterloo.ca Abstract. This note
1 Binary Search Trees (BSTs)
 Lecture 19-20 Binary Search Trees Parallel and Sequential Data Structures and Algorithms, 15-210 (Fall 2013) Lectured by Danny Sleator 31 Oct (Halloween!) and Nov 5 2013 Today: - Binary Search Trees (BST)
Lecture 19-20 Binary Search Trees Parallel and Sequential Data Structures and Algorithms, 15-210 (Fall 2013) Lectured by Danny Sleator 31 Oct (Halloween!) and Nov 5 2013 Today: - Binary Search Trees (BST)
Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of C
 Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of California, San Diego CA 92093{0114, USA Abstract. We
Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of California, San Diego CA 92093{0114, USA Abstract. We
Lecture 6: Analysis of Algorithms (CS )
 Lecture 6: Analysis of Algorithms (CS583-002) Amarda Shehu October 08, 2014 1 Outline of Today s Class 2 Traversals Querying Insertion and Deletion Sorting with BSTs 3 Red-black Trees Height of a Red-black
Lecture 6: Analysis of Algorithms (CS583-002) Amarda Shehu October 08, 2014 1 Outline of Today s Class 2 Traversals Querying Insertion and Deletion Sorting with BSTs 3 Red-black Trees Height of a Red-black
Binary search trees. Binary search trees are data structures based on binary trees that support operations on dynamic sets.
 COMP3600/6466 Algorithms 2018 Lecture 12 1 Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees are data structures based on binary trees that support operations on dynamic
COMP3600/6466 Algorithms 2018 Lecture 12 1 Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees are data structures based on binary trees that support operations on dynamic
Jana Kosecka. Red-Black Trees Graph Algorithms. Many slides here are based on E. Demaine, D. Luebke slides
 Jana Kosecka Red-Black Trees Graph Algorithms Many slides here are based on E. Demaine, D. Luebke slides Binary Search Trees (BSTs) are an important data structure for dynamic sets In addition to satellite
Jana Kosecka Red-Black Trees Graph Algorithms Many slides here are based on E. Demaine, D. Luebke slides Binary Search Trees (BSTs) are an important data structure for dynamic sets In addition to satellite
Binary search trees 3. Binary search trees. Binary search trees 2. Reading: Cormen et al, Sections 12.1 to 12.3
 Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees 3 Binary search trees are data structures based on binary trees that support operations on dynamic sets. Each element
Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees 3 Binary search trees are data structures based on binary trees that support operations on dynamic sets. Each element
Notes on Binary Dumbbell Trees
 Notes on Binary Dumbbell Trees Michiel Smid March 23, 2012 Abstract Dumbbell trees were introduced in [1]. A detailed description of non-binary dumbbell trees appears in Chapter 11 of [3]. These notes
Notes on Binary Dumbbell Trees Michiel Smid March 23, 2012 Abstract Dumbbell trees were introduced in [1]. A detailed description of non-binary dumbbell trees appears in Chapter 11 of [3]. These notes
Cache-Oblivious Traversals of an Array s Pairs
 Cache-Oblivious Traversals of an Array s Pairs Tobias Johnson May 7, 2007 Abstract Cache-obliviousness is a concept first introduced by Frigo et al. in [1]. We follow their model and develop a cache-oblivious
Cache-Oblivious Traversals of an Array s Pairs Tobias Johnson May 7, 2007 Abstract Cache-obliviousness is a concept first introduced by Frigo et al. in [1]. We follow their model and develop a cache-oblivious
Real-time integrated prefetching and caching
 Real-time integrated prefetching and caching Peter Sanders Johannes Singler Rob van Stee September 26, 2012 Abstract The high latencies for access to background memory like hard disks or flash memory can
Real-time integrated prefetching and caching Peter Sanders Johannes Singler Rob van Stee September 26, 2012 Abstract The high latencies for access to background memory like hard disks or flash memory can
Solutions to Exam Data structures (X and NV)
 Solutions to Exam Data structures X and NV 2005102. 1. a Insert the keys 9, 6, 2,, 97, 1 into a binary search tree BST. Draw the final tree. See Figure 1. b Add NIL nodes to the tree of 1a and color it
Solutions to Exam Data structures X and NV 2005102. 1. a Insert the keys 9, 6, 2,, 97, 1 into a binary search tree BST. Draw the final tree. See Figure 1. b Add NIL nodes to the tree of 1a and color it
Lecture 8: The Traveling Salesman Problem
 Lecture 8: The Traveling Salesman Problem Let G = (V, E) be an undirected graph. A Hamiltonian cycle of G is a cycle that visits every vertex v V exactly once. Instead of Hamiltonian cycle, we sometimes
Lecture 8: The Traveling Salesman Problem Let G = (V, E) be an undirected graph. A Hamiltonian cycle of G is a cycle that visits every vertex v V exactly once. Instead of Hamiltonian cycle, we sometimes
Part 2: Balanced Trees
 Part 2: Balanced Trees 1 AVL Trees We could dene a perfectly balanced binary search tree with N nodes to be a complete binary search tree, one in which every level except the last is completely full. A
Part 2: Balanced Trees 1 AVL Trees We could dene a perfectly balanced binary search tree with N nodes to be a complete binary search tree, one in which every level except the last is completely full. A
The PRAM model. A. V. Gerbessiotis CIS 485/Spring 1999 Handout 2 Week 2
 The PRAM model A. V. Gerbessiotis CIS 485/Spring 1999 Handout 2 Week 2 Introduction The Parallel Random Access Machine (PRAM) is one of the simplest ways to model a parallel computer. A PRAM consists of
The PRAM model A. V. Gerbessiotis CIS 485/Spring 1999 Handout 2 Week 2 Introduction The Parallel Random Access Machine (PRAM) is one of the simplest ways to model a parallel computer. A PRAM consists of
Search Trees. The term refers to a family of implementations, that may have different properties. We will discuss:
 Search Trees CSE 2320 Algorithms and Data Structures Alexandra Stefan Based on slides and notes from: Vassilis Athitsos and Bob Weems University of Texas at Arlington 1 Search Trees Preliminary note: "search
Search Trees CSE 2320 Algorithms and Data Structures Alexandra Stefan Based on slides and notes from: Vassilis Athitsos and Bob Weems University of Texas at Arlington 1 Search Trees Preliminary note: "search
Balanced Binary Search Trees. Victor Gao
 Balanced Binary Search Trees Victor Gao OUTLINE Binary Heap Revisited BST Revisited Balanced Binary Search Trees Rotation Treap Splay Tree BINARY HEAP: REVIEW A binary heap is a complete binary tree such
Balanced Binary Search Trees Victor Gao OUTLINE Binary Heap Revisited BST Revisited Balanced Binary Search Trees Rotation Treap Splay Tree BINARY HEAP: REVIEW A binary heap is a complete binary tree such
TREES. Trees - Introduction
 TREES Chapter 6 Trees - Introduction All previous data organizations we've studied are linear each element can have only one predecessor and successor Accessing all elements in a linear sequence is O(n)
TREES Chapter 6 Trees - Introduction All previous data organizations we've studied are linear each element can have only one predecessor and successor Accessing all elements in a linear sequence is O(n)
Analysis of Algorithms
 Analysis of Algorithms Concept Exam Code: 16 All questions are weighted equally. Assume worst case behavior and sufficiently large input sizes unless otherwise specified. Strong induction Consider this
Analysis of Algorithms Concept Exam Code: 16 All questions are weighted equally. Assume worst case behavior and sufficiently large input sizes unless otherwise specified. Strong induction Consider this
Multi-way Search Trees
 Multi-way Search Trees Kuan-Yu Chen ( 陳冠宇 ) 2018/10/24 @ TR-212, NTUST Review Red-Black Trees Splay Trees Huffman Trees 2 Multi-way Search Trees. Every node in a binary search tree contains one value and
Multi-way Search Trees Kuan-Yu Chen ( 陳冠宇 ) 2018/10/24 @ TR-212, NTUST Review Red-Black Trees Splay Trees Huffman Trees 2 Multi-way Search Trees. Every node in a binary search tree contains one value and
PAPER Constructing the Suffix Tree of a Tree with a Large Alphabet
 IEICE TRANS. FUNDAMENTALS, VOL.E8??, NO. JANUARY 999 PAPER Constructing the Suffix Tree of a Tree with a Large Alphabet Tetsuo SHIBUYA, SUMMARY The problem of constructing the suffix tree of a tree is
IEICE TRANS. FUNDAMENTALS, VOL.E8??, NO. JANUARY 999 PAPER Constructing the Suffix Tree of a Tree with a Large Alphabet Tetsuo SHIBUYA, SUMMARY The problem of constructing the suffix tree of a tree is
On the other hand, the main disadvantage of the amortized approach is that it cannot be applied in real-time programs, where the worst-case bound on t
 Randomized Meldable Priority Queues Anna Gambin and Adam Malinowski Instytut Informatyki, Uniwersytet Warszawski, Banacha 2, Warszawa 02-097, Poland, faniag,amalg@mimuw.edu.pl Abstract. We present a practical
Randomized Meldable Priority Queues Anna Gambin and Adam Malinowski Instytut Informatyki, Uniwersytet Warszawski, Banacha 2, Warszawa 02-097, Poland, faniag,amalg@mimuw.edu.pl Abstract. We present a practical
Representing Dynamic Binary Trees Succinctly
 Representing Dynamic Binary Trees Succinctly J. Inn Munro * Venkatesh Raman t Adam J. Storm* Abstract We introduce a new updatable representation of binary trees. The structure requires the information
Representing Dynamic Binary Trees Succinctly J. Inn Munro * Venkatesh Raman t Adam J. Storm* Abstract We introduce a new updatable representation of binary trees. The structure requires the information
Advanced Set Representation Methods
 Advanced Set Representation Methods AVL trees. 2-3(-4) Trees. Union-Find Set ADT DSA - lecture 4 - T.U.Cluj-Napoca - M. Joldos 1 Advanced Set Representation. AVL Trees Problem with BSTs: worst case operation
Advanced Set Representation Methods AVL trees. 2-3(-4) Trees. Union-Find Set ADT DSA - lecture 4 - T.U.Cluj-Napoca - M. Joldos 1 Advanced Set Representation. AVL Trees Problem with BSTs: worst case operation
(2,4) Trees. 2/22/2006 (2,4) Trees 1
 (2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
(2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
CMPS 2200 Fall 2017 Red-black trees Carola Wenk
 CMPS 2200 Fall 2017 Red-black trees Carola Wenk Slides courtesy of Charles Leiserson with changes by Carola Wenk 9/13/17 CMPS 2200 Intro. to Algorithms 1 Dynamic Set A dynamic set, or dictionary, is a
CMPS 2200 Fall 2017 Red-black trees Carola Wenk Slides courtesy of Charles Leiserson with changes by Carola Wenk 9/13/17 CMPS 2200 Intro. to Algorithms 1 Dynamic Set A dynamic set, or dictionary, is a
Hash Tables. CS 311 Data Structures and Algorithms Lecture Slides. Wednesday, April 22, Glenn G. Chappell
 Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
