Format String Dangers. Shachar Shemesh Security Consultant
|
|
|
- Raymond Gibson
- 6 years ago
- Views:
Transcription
1 Format String Dangers Shachar Shemesh Security Consultant
2 Schedule Reintroduction to printf (as if you don t already know ). Some reflection about common uses of printf. Dangers of letting attackers supply format strings. Step by step demonstration of exploit.
3 Printf manual PRINTF(3) Linux Programmer's Manual PRINTF(3) NAME printf, fprintf, sprintf, snprintf, vprintf, vfprintf, vsprintf, vsnprintf - formatted output conversion SYNOPSIS #include <stdio.h> int printf(const char *format,...); int fprintf(file *stream, const char *format,...); int sprintf(char *str, const char *format,...); int snprintf(char *str, size_t size, const char *format,...);
4 The Format String Most characters are simply echoed. A % indicates a special field (unless followed by another % ). It is up to the programmer to make sure the parameters number and type match the format string. Some compilers will verify this for static format strings.
5 Format String Functions (v)printf (v)sprintf (v)snprintf (v)fprintf syslog (v)wprintf (v)fwprintf (v)swprintf (v)dprintf (v)asprintf
6 Caveat Emptor sysinfo hasn t got the telltale printf word in it. It is all too easy to mistake it for accepting a plain string. Accepting a format string is all too common with error functions. An error is usually a situation triggerable by an attacker. Projects usually have similar, private, functions.
7 How Format Strings Work printf("hello %s, it s been %d days since your last login\n", username, days); Hello sun, it s been 25 since your last login username days days username format string ptr printf return addr.
8 When Format String and Parameters Mismatch printf( buffer ); What if buffer is %x%x%x%x%x%x%x%x? return address When the pointer is here the attacker controls both frame pointer parameter and interpretation %x%x%x%x%x%x %x%x%x%x%x%x format string ptr printf return addr.
9 What Can be Done? Query parameters from the stack %x, %d etc. Query data from anywhere in the program %s when the pointer is inside the buffer to get info from anywhere. Passwords, private keys... Crash the program %s from non-readable memory. %f wich requires to devide by zero.
10 Walk Ratio The ratio between the pointer advance and the characters it take. Determines how far up from our buffer we can peek. %x gives 1:2 %f gives 1:4, but risks devide by zero. what does printf("%3$d %2$d %1$d",5,6,7); print?
11 Who said it was read only? A user supply format string gives the attacker a read only debugger access into the application!
12 %n The Little Option Noobody Knows %n writes into the int pointed to by the respective argument the number of characters printed so far. An attacker can choose to write (%n), where to write (supply a pointer). By playing with field length, can also control what to write. Bare shortcuts, that may require printing an average of 2GB of data.
13 Some of the Shortcuts Write four times to addresses increasing by 1 each time. Will only work on platform that don t enforce integral boundries (e.g. - Intel). Use %hn to write to short. Now only requires printing 64K. Use %hhn to write to byte. Only prints 256 bytes.
14 A Few Bad Habits or you won t believe what people do! The following code samples represent errors found (not necessarily by me) in shipping code (some commercial, some free). The exact code was modified to protect paying customers the innocent.
15 A Few Bad Habits #define ASSERT(cond, err) \ if(!(cond)) { \ printf(err); exit(100); } What will the following imagenary code do? ASSERT(progress>10, Couldn t pass 10% mark );
16 Pointless use /* Initialize title */ sprintf( title, About to copy files ); sprintf scans the format string for fields. Unofficial benchmark shows 50% performance of sprintf(buff, data) over sprintf(buff, %s, data). Using strcpy or strncpy would be much better in this case.
17 Dangerous Pitfall int logerr( char *fmt,... ) { va_list args; char buff[1024]; va_start(args, fmt); vsnprintf(buff, sizeof(buff), fmt, args ); va_end(args); } return fprintf(errlog, buff);
18 Famous Example #include <stdio.h> main( ) { printf( Hello, printf( %s, world\n ); } Hello, world\n ); } The C Programming Language, Second Edition Brian W. Kernighan Dennis M. Ritchie Prentice Hall Software Series, 1988
CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output
 CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 Secure Coding String management Pointer Subterfuge
CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 Secure Coding String management Pointer Subterfuge
2/9/18. CYSE 411/AIT681 Secure Software Engineering. Readings. Secure Coding. This lecture: String management Pointer Subterfuge
 CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 String management Pointer Subterfuge Secure
CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 String management Pointer Subterfuge Secure
Security TR Editor's Report
 Security TR Editor's Report December 1, 2004 Randy Meyers 1. Introduction Let me apologize for the latest draft of the Security TR (N1088) being a week and a half late. I developed a nasty respiratory
Security TR Editor's Report December 1, 2004 Randy Meyers 1. Introduction Let me apologize for the latest draft of the Security TR (N1088) being a week and a half late. I developed a nasty respiratory
Format string vulnerabilities
 Format string vulnerabilities Goal Take control of the program (as usual) How? Write4 (write 4 bytes to an arbitrary location) Inject shellcode (or other exploits) into the process What should we overwrite?
Format string vulnerabilities Goal Take control of the program (as usual) How? Write4 (write 4 bytes to an arbitrary location) Inject shellcode (or other exploits) into the process What should we overwrite?
CSCE 548 Building Secure Software Integers & Integer-related Attacks & Format String Attacks. Professor Lisa Luo Spring 2018
 CSCE 548 Building Secure Software Integers & Integer-related Attacks & Format String Attacks Professor Lisa Luo Spring 2018 Previous Class Buffer overflows can be devastating It occurs when the access
CSCE 548 Building Secure Software Integers & Integer-related Attacks & Format String Attacks Professor Lisa Luo Spring 2018 Previous Class Buffer overflows can be devastating It occurs when the access
Software Vulnerabilities. Jeff Foster University of Maryland, College Park
 Software Vulnerabilities Jeff Foster University of Maryland, College Park When is a Program Secure? When it does exactly what it should! But what is it supposed to do? - Someone tells us (do we trust them?)
Software Vulnerabilities Jeff Foster University of Maryland, College Park When is a Program Secure? When it does exactly what it should! But what is it supposed to do? - Someone tells us (do we trust them?)
CSE / / 60567: Computer Security. Software Security 4
 CSE 40567 / 44567 / 60567: Computer Security Software Security 4 91 Homework #5 Due: Tonight at 11:59PM Eastern Time (ND) / Pacific Time (SV) See Assignments Page on the course website for details 92 Notes
CSE 40567 / 44567 / 60567: Computer Security Software Security 4 91 Homework #5 Due: Tonight at 11:59PM Eastern Time (ND) / Pacific Time (SV) See Assignments Page on the course website for details 92 Notes
System Security Class Notes 09/23/2013
 System Security Class Notes 09/23/2013 1 Format String Exploits a Format String bugs The printf family consists of functions with variable arguments i printf (char* format, ) ii sprint (char* dest, char*
System Security Class Notes 09/23/2013 1 Format String Exploits a Format String bugs The printf family consists of functions with variable arguments i printf (char* format, ) ii sprint (char* dest, char*
Pointers, Arrays, and Strings. CS449 Spring 2016
 Pointers, Arrays, and Strings CS449 Spring 2016 Pointers Pointers are important. Pointers are fun! Pointers Every variable in your program has a memory location. This location can be accessed using & operator.
Pointers, Arrays, and Strings CS449 Spring 2016 Pointers Pointers are important. Pointers are fun! Pointers Every variable in your program has a memory location. This location can be accessed using & operator.
CS 261 Fall C Introduction. Variables, Memory Model, Pointers, and Debugging. Mike Lam, Professor
 CS 261 Fall 2017 Mike Lam, Professor C Introduction Variables, Memory Model, Pointers, and Debugging The C Language Systems language originally developed for Unix Imperative, compiled language with static
CS 261 Fall 2017 Mike Lam, Professor C Introduction Variables, Memory Model, Pointers, and Debugging The C Language Systems language originally developed for Unix Imperative, compiled language with static
C Introduction. Comparison w/ Java, Memory Model, and Pointers
 CS 261 Fall 2018 Mike Lam, Professor C Introduction Comparison w/ Java, Memory Model, and Pointers Please go to socrative.com on your phone or laptop, choose student login and join room LAMJMU The C Language
CS 261 Fall 2018 Mike Lam, Professor C Introduction Comparison w/ Java, Memory Model, and Pointers Please go to socrative.com on your phone or laptop, choose student login and join room LAMJMU The C Language
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 15: Software Security II Department of Computer Science and Engineering University at Buffalo 1 Software Vulnerabilities Buffer overflow vulnerabilities account
CSE 565 Computer Security Fall 2018 Lecture 15: Software Security II Department of Computer Science and Engineering University at Buffalo 1 Software Vulnerabilities Buffer overflow vulnerabilities account
Module: Safe Programming. Professor Trent Jaeger. CSE543 - Introduction to Computer and Network Security
 CSE543 - Introduction to Computer and Network Security Module: Safe Programming Professor Trent Jaeger 1 1 Avoiding Vulnerabilities How do we write programs to avoid mistakes that lead to vulnerabilities?
CSE543 - Introduction to Computer and Network Security Module: Safe Programming Professor Trent Jaeger 1 1 Avoiding Vulnerabilities How do we write programs to avoid mistakes that lead to vulnerabilities?
This code has a bug that allows a hacker to take control of its execution and run evilfunc().
 Malicious Code Insertion Example This code has a bug that allows a hacker to take control of its execution and run evilfunc(). #include // obviously it is compiler dependent // but on my system
Malicious Code Insertion Example This code has a bug that allows a hacker to take control of its execution and run evilfunc(). #include // obviously it is compiler dependent // but on my system
Program Security and Vulnerabilities Class 2
 Program Security and Vulnerabilities Class 2 CEN-5079: 28.August.2017 1 Secure Programs Programs Operating System Device Drivers Network Software (TCP stack, web servers ) Database Management Systems Integrity
Program Security and Vulnerabilities Class 2 CEN-5079: 28.August.2017 1 Secure Programs Programs Operating System Device Drivers Network Software (TCP stack, web servers ) Database Management Systems Integrity
C Characters and Strings
 CS 2060 Character handling The C Standard Library provides many functions for testing characters in ctype.h. int isdigit(int c); // is c a digit (0-9)? int isalpha(int c); // is c a letter? int isalnum(int
CS 2060 Character handling The C Standard Library provides many functions for testing characters in ctype.h. int isdigit(int c); // is c a digit (0-9)? int isalpha(int c); // is c a letter? int isalnum(int
CSCE 548 Building Secure Software Buffer Overflow. Professor Lisa Luo Spring 2018
 CSCE 548 Building Secure Software Buffer Overflow Professor Lisa Luo Spring 2018 Previous Class Virus vs. Worm vs. Trojan & Drive-by download Botnet & Rootkit Malware detection Scanner Polymorphic malware
CSCE 548 Building Secure Software Buffer Overflow Professor Lisa Luo Spring 2018 Previous Class Virus vs. Worm vs. Trojan & Drive-by download Botnet & Rootkit Malware detection Scanner Polymorphic malware
Memory Corruption 101 From Primitives to Exploit
 Memory Corruption 101 From Primitives to Exploit Created by Nick Walker @ MWR Infosecurity / @tel0seh What is it? A result of Undefined Behaviour Undefined Behaviour A result of executing computer code
Memory Corruption 101 From Primitives to Exploit Created by Nick Walker @ MWR Infosecurity / @tel0seh What is it? A result of Undefined Behaviour Undefined Behaviour A result of executing computer code
Secure Software Programming and Vulnerability Analysis
 Secure Software Programming and Vulnerability Analysis Christopher Kruegel chris@auto.tuwien.ac.at http://www.auto.tuwien.ac.at/~chris Heap Buffer Overflows and Format String Vulnerabilities Secure Software
Secure Software Programming and Vulnerability Analysis Christopher Kruegel chris@auto.tuwien.ac.at http://www.auto.tuwien.ac.at/~chris Heap Buffer Overflows and Format String Vulnerabilities Secure Software
CS 645: Lecture 3 Software Vulnerabilities. Rachel Greenstadt July 3, 2013
 CS 645: Lecture 3 Software Vulnerabilities Rachel Greenstadt July 3, 2013 Project 1: Software exploits Individual project - done in virtual machine environment This assignment is hard. Don t leave it until
CS 645: Lecture 3 Software Vulnerabilities Rachel Greenstadt July 3, 2013 Project 1: Software exploits Individual project - done in virtual machine environment This assignment is hard. Don t leave it until
Introduction to N1031. Components of N1031. Guiding Principles. Walk through, issues, and rationale
 Introduction to N1031 Walk through, issues, and rationale Components of N1031 New functions that protect against buffer overflow and always produce null terminated strings New reentrant versions of old
Introduction to N1031 Walk through, issues, and rationale Components of N1031 New functions that protect against buffer overflow and always produce null terminated strings New reentrant versions of old
1. We have a code sequence that is potentially executed twice.
 Long Jump Long Jump Local Jumps In the following example: 1. We have a code sequence that is potentially executed twice. 2. A flag is used to determine whether the sequence is being executed the first
Long Jump Long Jump Local Jumps In the following example: 1. We have a code sequence that is potentially executed twice. 2. A flag is used to determine whether the sequence is being executed the first
C Language Part 1 Digital Computer Concept and Practice Copyright 2012 by Jaejin Lee
 C Language Part 1 (Minor modifications by the instructor) References C for Python Programmers, by Carl Burch, 2011. http://www.toves.org/books/cpy/ The C Programming Language. 2nd ed., Kernighan, Brian,
C Language Part 1 (Minor modifications by the instructor) References C for Python Programmers, by Carl Burch, 2011. http://www.toves.org/books/cpy/ The C Programming Language. 2nd ed., Kernighan, Brian,
Secure Programming. Buffer Overflows Learning objectives. Type. 3 Buffer Overflows. 4 An Important Vulnerability. 5 Example Overflow
 Secure Programming Buffer Overflows 2 Learning objectives Understand the definition of a buffer overflow Learn the importance of buffer overflows Know how buffer overflows happen Know how to handle strings
Secure Programming Buffer Overflows 2 Learning objectives Understand the definition of a buffer overflow Learn the importance of buffer overflows Know how buffer overflows happen Know how to handle strings
CS113: Lecture 7. Topics: The C Preprocessor. I/O, Streams, Files
 CS113: Lecture 7 Topics: The C Preprocessor I/O, Streams, Files 1 Remember the name: Pre-processor Most commonly used features: #include, #define. Think of the preprocessor as processing the file so as
CS113: Lecture 7 Topics: The C Preprocessor I/O, Streams, Files 1 Remember the name: Pre-processor Most commonly used features: #include, #define. Think of the preprocessor as processing the file so as
Required reading: StackGuard: Simple Stack Smash Protection for GCC
 Continuing with Software Security Writing & testing for Secure Code Required reading: StackGuard: Simple Stack Smash Protection for GCC Optional reading: Basic Integer Overflows Exploiting Format String
Continuing with Software Security Writing & testing for Secure Code Required reading: StackGuard: Simple Stack Smash Protection for GCC Optional reading: Basic Integer Overflows Exploiting Format String
Control Hijacking Attacks
 Control Hijacking Attacks Note: project 1 is out Section this Friday 4:15pm (Gates B03) Control hijacking attacks Attacker s goal: Take over target machine (e.g. web server) Execute arbitrary code on target
Control Hijacking Attacks Note: project 1 is out Section this Friday 4:15pm (Gates B03) Control hijacking attacks Attacker s goal: Take over target machine (e.g. web server) Execute arbitrary code on target
Secure Programming I. Steven M. Bellovin September 28,
 Secure Programming I Steven M. Bellovin September 28, 2014 1 If our software is buggy, what does that say about its security? Robert H. Morris Steven M. Bellovin September 28, 2014 2 The Heart of the Problem
Secure Programming I Steven M. Bellovin September 28, 2014 1 If our software is buggy, what does that say about its security? Robert H. Morris Steven M. Bellovin September 28, 2014 2 The Heart of the Problem
CIS 551 / TCOM 401 Computer and Network Security. Spring 2007 Lecture 2
 CIS 551 / TCOM 401 Computer and Network Security Spring 2007 Lecture 2 Announcements First project is on the web Due: Feb. 1st at midnight Form groups of 2 or 3 people If you need help finding a group,
CIS 551 / TCOM 401 Computer and Network Security Spring 2007 Lecture 2 Announcements First project is on the web Due: Feb. 1st at midnight Form groups of 2 or 3 people If you need help finding a group,
Foundations of Network and Computer Security
 Foundations of Network and Computer Security John Black Lecture #20 Nov 4 th 2004 CSCI 6268/TLEN 5831, Fall 2004 Announcements Quiz #3 Today Need to know what big-endian is Remind me to mention it if I
Foundations of Network and Computer Security John Black Lecture #20 Nov 4 th 2004 CSCI 6268/TLEN 5831, Fall 2004 Announcements Quiz #3 Today Need to know what big-endian is Remind me to mention it if I
Fundamentals of Computer Security
 Fundamentals of Computer Security Spring 2015 Radu Sion Software Errors Buffer Overflow TOCTTOU 2005-15 Portions copyright by Bogdan Carbunar and Wikipedia. Used with permission Why Security Vulnerabilities?
Fundamentals of Computer Security Spring 2015 Radu Sion Software Errors Buffer Overflow TOCTTOU 2005-15 Portions copyright by Bogdan Carbunar and Wikipedia. Used with permission Why Security Vulnerabilities?
CSE 303 Lecture 15. C File Input/Output (I/O) reading: Programming in C Ch. 16; Appendix B pp
 CSE 303 Lecture 15 C File Input/Output (I/O) reading: Programming in C Ch. 16; Appendix B pp. 473-478 slides created by Marty Stepp http://www.cs.washington.edu/303/ 1 Console I/O review #include
CSE 303 Lecture 15 C File Input/Output (I/O) reading: Programming in C Ch. 16; Appendix B pp. 473-478 slides created by Marty Stepp http://www.cs.washington.edu/303/ 1 Console I/O review #include
CS 241 Data Organization Pointers and Arrays
 CS 241 Data Organization Pointers and Arrays Brooke Chenoweth University of New Mexico Fall 2017 Read Kernighan & Richie 6 Structures Pointers A pointer is a variable that contains the address of another
CS 241 Data Organization Pointers and Arrays Brooke Chenoweth University of New Mexico Fall 2017 Read Kernighan & Richie 6 Structures Pointers A pointer is a variable that contains the address of another
This lists all known errors in The C Programming Language, Second Edition, by Brian Kernighan and Dennis Ritchie (Prentice-Hall, 1988).
 Errata for The C Programming Language, Second Edition This lists all known errors in The C Programming Language, Second Edition, by Brian Kernighan and Dennis Ritchie (Prentice-Hall, 1988). The pagination
Errata for The C Programming Language, Second Edition This lists all known errors in The C Programming Language, Second Edition, by Brian Kernighan and Dennis Ritchie (Prentice-Hall, 1988). The pagination
Vulnerabilities. Code Injection - Buffer overflows. Some Commonly Exploitable Flaws
 Vulnerabilities Lecture 2: Exploiting Vulnerabilities: Buffer Overflow, Format string, Timing Attacks, and Logic Attacks ECE1776 David Lie We define a vulnerability as: A program flaw (or bug) that when
Vulnerabilities Lecture 2: Exploiting Vulnerabilities: Buffer Overflow, Format string, Timing Attacks, and Logic Attacks ECE1776 David Lie We define a vulnerability as: A program flaw (or bug) that when
CMPT 102 Introduction to Scientific Computer Programming. Input and Output. Your first program
 CMPT 102 Introduction to Scientific Computer Programming Input and Output Janice Regan, CMPT 102, Sept. 2006 0 Your first program /* My first C program */ /* make the computer print the string Hello world
CMPT 102 Introduction to Scientific Computer Programming Input and Output Janice Regan, CMPT 102, Sept. 2006 0 Your first program /* My first C program */ /* make the computer print the string Hello world
gcc hello.c a.out Hello, world gcc -o hello hello.c hello Hello, world
 alun@debian:~$ gcc hello.c alun@debian:~$ a.out Hello, world alun@debian:~$ gcc -o hello hello.c alun@debian:~$ hello Hello, world alun@debian:~$ 1 A Quick guide to C for Networks and Operating Systems
alun@debian:~$ gcc hello.c alun@debian:~$ a.out Hello, world alun@debian:~$ gcc -o hello hello.c alun@debian:~$ hello Hello, world alun@debian:~$ 1 A Quick guide to C for Networks and Operating Systems
Control Hijacking Attacks
 Control Hijacking Attacks Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides from Chris Kruegel) Attacker s mindset Take control of the victim s machine Hijack the execution flow of a running
Control Hijacking Attacks Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides from Chris Kruegel) Attacker s mindset Take control of the victim s machine Hijack the execution flow of a running
Standard C Library Functions
 Demo lecture slides Although I will not usually give slides for demo lectures, the first two demo lectures involve practice with things which you should really know from G51PRG Since I covered much of
Demo lecture slides Although I will not usually give slides for demo lectures, the first two demo lectures involve practice with things which you should really know from G51PRG Since I covered much of
C Programming Language Review and Dissection III
 C Programming Language Review and Dissection III Lecture 5 Embedded Systems 5-1 Today Pointers Strings Formatted Text Output Reading Assignment: Patt & Patel Pointers and Arrays Chapter 16 in 2 nd edition
C Programming Language Review and Dissection III Lecture 5 Embedded Systems 5-1 Today Pointers Strings Formatted Text Output Reading Assignment: Patt & Patel Pointers and Arrays Chapter 16 in 2 nd edition
Memory Analysis tools
 Memory Analysis tools PURIFY The Necessity TOOL Application behaviour: Crashes intermittently Uses too much memory Runs too slowly Isn t well tested Is about to ship You need something See what your code
Memory Analysis tools PURIFY The Necessity TOOL Application behaviour: Crashes intermittently Uses too much memory Runs too slowly Isn t well tested Is about to ship You need something See what your code
Chapter 5, Standard I/O. Not UNIX... C standard (library) Why? UNIX programmed in C stdio is very UNIX based
 Chapter 5, Standard I/O Not UNIX... C standard (library) Why? UNIX programmed in C stdio is very UNIX based #include FILE *f; Standard files (FILE *varname) variable: stdin File Number: STDIN_FILENO
Chapter 5, Standard I/O Not UNIX... C standard (library) Why? UNIX programmed in C stdio is very UNIX based #include FILE *f; Standard files (FILE *varname) variable: stdin File Number: STDIN_FILENO
CSE 220: Systems Programming
 CSE 220: Systems Programming Pointers and Data Representation Ethan Blanton Department of Computer Science and Engineering University at Buffalo More on void Pointers Void pointers are powerful for raw
CSE 220: Systems Programming Pointers and Data Representation Ethan Blanton Department of Computer Science and Engineering University at Buffalo More on void Pointers Void pointers are powerful for raw
ECS 153 Discussion Section. April 6, 2015
 ECS 153 Discussion Section April 6, 2015 1 What We ll Cover Goal: To discuss buffer overflows in detail Stack- based buffer overflows Smashing the stack : execution from the stack ARC (or return- to- libc)
ECS 153 Discussion Section April 6, 2015 1 What We ll Cover Goal: To discuss buffer overflows in detail Stack- based buffer overflows Smashing the stack : execution from the stack ARC (or return- to- libc)
Hands-on Ethical Hacking: Preventing & Writing Buffer Overflow Exploits
 Hands-on Ethical Hacking: Preventing & Writing Buffer Overflow Exploits OWASP AppSec 2013 Rochester OWASP Chapter Lead Ralph Durkee - Durkee Consulting, Inc. info@rd1.net Hands-on Ethical Hacking: Preventing
Hands-on Ethical Hacking: Preventing & Writing Buffer Overflow Exploits OWASP AppSec 2013 Rochester OWASP Chapter Lead Ralph Durkee - Durkee Consulting, Inc. info@rd1.net Hands-on Ethical Hacking: Preventing
Input/Output and the Operating Systems
 Input/Output and the Operating Systems Fall 2015 Jinkyu Jeong (jinkyu@skku.edu) 1 I/O Functions Formatted I/O printf( ) and scanf( ) fprintf( ) and fscanf( ) sprintf( ) and sscanf( ) int printf(const char*
Input/Output and the Operating Systems Fall 2015 Jinkyu Jeong (jinkyu@skku.edu) 1 I/O Functions Formatted I/O printf( ) and scanf( ) fprintf( ) and fscanf( ) sprintf( ) and sscanf( ) int printf(const char*
CS201 Lecture 2 GDB, The C Library
 CS201 Lecture 2 GDB, The C Library RAOUL RIVAS PORTLAND STATE UNIVERSITY Announcements 2 Multidimensional Dynamically Allocated Arrays Direct access support. Same as Multidimensional Static Arrays No direct
CS201 Lecture 2 GDB, The C Library RAOUL RIVAS PORTLAND STATE UNIVERSITY Announcements 2 Multidimensional Dynamically Allocated Arrays Direct access support. Same as Multidimensional Static Arrays No direct
Introduction to Programming. Lecture 2: Introduction to C
 Introduction to Programming Lecture 2: Introduction to C Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Review Lecture 1 Introduction to the course General information Syllabus Course organization General rules
Introduction to Programming Lecture 2: Introduction to C Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Review Lecture 1 Introduction to the course General information Syllabus Course organization General rules
C Input/Output. Before we discuss I/O in C, let's review how C++ I/O works. int i; double x;
 C Input/Output Before we discuss I/O in C, let's review how C++ I/O works. int i; double x; cin >> i; cin >> x; cout
C Input/Output Before we discuss I/O in C, let's review how C++ I/O works. int i; double x; cin >> i; cin >> x; cout
C - Basics, Bitwise Operator. Zhaoguo Wang
 C - Basics, Bitwise Operator Zhaoguo Wang Java is the best language!!! NO! C is the best!!!! Languages C Java Python 1972 1995 2000 (2.0) Procedure Object oriented Procedure & object oriented Compiled
C - Basics, Bitwise Operator Zhaoguo Wang Java is the best language!!! NO! C is the best!!!! Languages C Java Python 1972 1995 2000 (2.0) Procedure Object oriented Procedure & object oriented Compiled
Copyright (2004) Purdue Research Foundation. All rights reserved.
 CS390S, Week 3: Buffer Overflows, Part 1 Pascal Meunier, Ph.D., M.Sc., CISSP January 23, 2008 Developed thanks to support and contributions from Symantec Corporation, support from the NSF SFS Capacity
CS390S, Week 3: Buffer Overflows, Part 1 Pascal Meunier, Ph.D., M.Sc., CISSP January 23, 2008 Developed thanks to support and contributions from Symantec Corporation, support from the NSF SFS Capacity
Source level debugging. October 18, 2016
 Source level debugging October 18, 2016 Source level debugging Source debugging is a nice tool for debugging execution problems; it can be particularly useful when working with crashed programs that leave
Source level debugging October 18, 2016 Source level debugging Source debugging is a nice tool for debugging execution problems; it can be particularly useful when working with crashed programs that leave
Physics 2660: Fundamentals of Scientific Computing. Lecture 3 Instructor: Prof. Chris Neu
 Physics 2660: Fundamentals of Scientific Computing Lecture 3 Instructor: Prof. Chris Neu (chris.neu@virginia.edu) Announcements Weekly readings will be assigned and available through the class wiki home
Physics 2660: Fundamentals of Scientific Computing Lecture 3 Instructor: Prof. Chris Neu (chris.neu@virginia.edu) Announcements Weekly readings will be assigned and available through the class wiki home
Software Security Buffer Overflows more countermeasures. Erik Poll. Digital Security Radboud University Nijmegen
 Software Security Buffer Overflows more countermeasures Erik Poll Digital Security Radboud University Nijmegen Recap last week Recurring security problems in C(++) code buffer overflows bugs with pointers
Software Security Buffer Overflows more countermeasures Erik Poll Digital Security Radboud University Nijmegen Recap last week Recurring security problems in C(++) code buffer overflows bugs with pointers
CSE 303: Concepts and Tools for Software Development
 CSE 303: Concepts and Tools for Software Development Hal Perkins Winter 2009 Lecture 7 Introduction to C: The C-Level of Abstraction CSE 303 Winter 2009, Lecture 7 1 Welcome to C Compared to Java, in rough
CSE 303: Concepts and Tools for Software Development Hal Perkins Winter 2009 Lecture 7 Introduction to C: The C-Level of Abstraction CSE 303 Winter 2009, Lecture 7 1 Welcome to C Compared to Java, in rough
Getting Started. Project 1
 Getting Started Project 1 Project 1 Implement a shell interface that behaves similarly to a stripped down bash shell Due in 3 weeks September 21, 2015, 11:59:59pm Specification, grading sheet, and test
Getting Started Project 1 Project 1 Implement a shell interface that behaves similarly to a stripped down bash shell Due in 3 weeks September 21, 2015, 11:59:59pm Specification, grading sheet, and test
Introduction to C An overview of the programming language C, syntax, data types and input/output
 Introduction to C An overview of the programming language C, syntax, data types and input/output Teil I. a first C program TU Bergakademie Freiberg INMO M. Brändel 2018-10-23 1 PROGRAMMING LANGUAGE C is
Introduction to C An overview of the programming language C, syntax, data types and input/output Teil I. a first C program TU Bergakademie Freiberg INMO M. Brändel 2018-10-23 1 PROGRAMMING LANGUAGE C is
Structure of this course. C and C++ Past Exam Questions. Text books
 Structure of this course C and C++ 1. Types Variables Expressions & Statements Alastair R. Beresford University of Cambridge Lent Term 2008 Programming in C: types, variables, expressions & statements
Structure of this course C and C++ 1. Types Variables Expressions & Statements Alastair R. Beresford University of Cambridge Lent Term 2008 Programming in C: types, variables, expressions & statements
Welcome to... CS113: Introduction to C
 Welcome to... CS113: Introduction to C Instructor: Erik Sherwood E-mail: wes28@cs.cornell.edu Course Website: http://www.cs.cornell.edu/courses/cs113/2005fa/ The website is linked to from the courses page
Welcome to... CS113: Introduction to C Instructor: Erik Sherwood E-mail: wes28@cs.cornell.edu Course Website: http://www.cs.cornell.edu/courses/cs113/2005fa/ The website is linked to from the courses page
EURECOM 6/2/2012 SYSTEM SECURITY Σ
 EURECOM 6/2/2012 Name SYSTEM SECURITY 5 5 5 5 5 5 5 5 5 5 50 1 2 3 4 5 6 7 8 9 10 Σ Course material is not allowed during the exam. Try to keep your answers precise and short. You will not get extra points
EURECOM 6/2/2012 Name SYSTEM SECURITY 5 5 5 5 5 5 5 5 5 5 50 1 2 3 4 5 6 7 8 9 10 Σ Course material is not allowed during the exam. Try to keep your answers precise and short. You will not get extra points
Course Information and Introduction
 August 22, 2017 Course Information 1 Instructors : Email : arash.rafiey@indstate.edu Office : Root Hall A-127 Office Hours : Tuesdays 11:30 pm 12:30 pm. Root Hall, A127. 2 Course Home Page : http://cs.indstate.edu/~arash/cs256.html
August 22, 2017 Course Information 1 Instructors : Email : arash.rafiey@indstate.edu Office : Root Hall A-127 Office Hours : Tuesdays 11:30 pm 12:30 pm. Root Hall, A127. 2 Course Home Page : http://cs.indstate.edu/~arash/cs256.html
Lecture 9 Assertions and Error Handling CS240
 Lecture 9 Assertions and Error Handling CS240 The C preprocessor The C compiler performs Macro expansion and directive handling Preprocessing directive lines, including file inclusion and conditional compilation,
Lecture 9 Assertions and Error Handling CS240 The C preprocessor The C compiler performs Macro expansion and directive handling Preprocessing directive lines, including file inclusion and conditional compilation,
CS 211 Programming I for Engineers
 CS 211 Programming I for Engineers Instructor: Tom Bartenstein Course Web Page: http://www.cs.binghamton.edu/~tbartens/cs211_fall_2018/ 1 Catalog Description Introduction to computer programming with engineering
CS 211 Programming I for Engineers Instructor: Tom Bartenstein Course Web Page: http://www.cs.binghamton.edu/~tbartens/cs211_fall_2018/ 1 Catalog Description Introduction to computer programming with engineering
Topic 8: I/O. Reading: Chapter 7 in Kernighan & Ritchie more details in Appendix B (optional) even more details in GNU C Library manual (optional)
 Topic 8: I/O Reading: Chapter 7 in Kernighan & Ritchie more details in Appendix B (optional) even more details in GNU C Library manual (optional) No C language primitives for I/O; all done via function
Topic 8: I/O Reading: Chapter 7 in Kernighan & Ritchie more details in Appendix B (optional) even more details in GNU C Library manual (optional) No C language primitives for I/O; all done via function
String constants. /* Demo: string constant */ #include <stdio.h> int main() {
 Strings 1 String constants 2 /* Demo: string constant */ #include s1.c int main() { printf("hi\n"); } String constants are in double quotes A backslash \ is used to include 'special' characters,
Strings 1 String constants 2 /* Demo: string constant */ #include s1.c int main() { printf("hi\n"); } String constants are in double quotes A backslash \ is used to include 'special' characters,
System Programming. Standard Input/Output Library (Cont d)
 Content : by Dr. B. Boufama School of Computer Science University of Windsor Instructor: Dr. A. Habed adlane@cs.uwindsor.ca http://cs.uwindsor.ca/ adlane/60-256 Content Content 1 Binary I/O 2 3 4 5 Binary
Content : by Dr. B. Boufama School of Computer Science University of Windsor Instructor: Dr. A. Habed adlane@cs.uwindsor.ca http://cs.uwindsor.ca/ adlane/60-256 Content Content 1 Binary I/O 2 3 4 5 Binary
Buffer Overflows. A brief Introduction to the detection and prevention of buffer overflows for intermediate programmers.
 Buffer Overflows A brief Introduction to the detection and prevention of buffer overflows for intermediate programmers. By: Brian Roberts What is a buffer overflow? In languages that deal with data structures
Buffer Overflows A brief Introduction to the detection and prevention of buffer overflows for intermediate programmers. By: Brian Roberts What is a buffer overflow? In languages that deal with data structures
Software and Web Security 1. Root Cause Analysis. Abstractions Assumptions Trust. sws1 1
 Software and Web Security 1 Reflections on using C(++) Root Cause Analysis Abstractions Assumptions Trust sws1 1 There are only two kinds of programming languages: the ones people complain about and the
Software and Web Security 1 Reflections on using C(++) Root Cause Analysis Abstractions Assumptions Trust sws1 1 There are only two kinds of programming languages: the ones people complain about and the
Programming in C. What is C?... What is C?
 C Programming in C UVic SEng 265 Developed by Brian Kernighan and Dennis Ritchie of Bell Labs Earlier, in 1969, Ritchie and Thompson developed the Unix operating system We will be focusing on a version
C Programming in C UVic SEng 265 Developed by Brian Kernighan and Dennis Ritchie of Bell Labs Earlier, in 1969, Ritchie and Thompson developed the Unix operating system We will be focusing on a version
Introduction to C Programming
 Introduction to C Programming Digital Design and Computer Architecture David Money Harris and Sarah L. Harris 2- C Chapter :: Topics Introduction to C Why C? Example Program Compiling and running a
Introduction to C Programming Digital Design and Computer Architecture David Money Harris and Sarah L. Harris 2- C Chapter :: Topics Introduction to C Why C? Example Program Compiling and running a
Programming in C UVic SEng 265
 Programming in C UVic SEng 265 Daniel M. German Department of Computer Science University of Victoria 1 SEng 265 dmgerman@uvic.ca C Developed by Brian Kernighan and Dennis Ritchie of Bell Labs Earlier,
Programming in C UVic SEng 265 Daniel M. German Department of Computer Science University of Victoria 1 SEng 265 dmgerman@uvic.ca C Developed by Brian Kernighan and Dennis Ritchie of Bell Labs Earlier,
Programming languages, their environments and system software interfaces
 ISO/IEC JTC1 SC22 WG14 N1146 Date: 2005-10-25 Reference number of document: ISO/IEC TR 24731 Committee identification: ISO/IEC JTC1 SC22 WG14 SC22 Secretariat: ANSI Information Technology Programming languages,
ISO/IEC JTC1 SC22 WG14 N1146 Date: 2005-10-25 Reference number of document: ISO/IEC TR 24731 Committee identification: ISO/IEC JTC1 SC22 WG14 SC22 Secretariat: ANSI Information Technology Programming languages,
COSC Software Engineering. Lecture 16: Managing Memory Managers
 COSC345 2013 Software Engineering Lecture 16: Managing Memory Managers Outline Typical problems (from previous lectures) Memory leaks aren t just for (Objective) C Tracking malloc() calls Catching calls
COSC345 2013 Software Engineering Lecture 16: Managing Memory Managers Outline Typical problems (from previous lectures) Memory leaks aren t just for (Objective) C Tracking malloc() calls Catching calls
CSCE150A. Introduction. Basics. String Library. Substrings. Line Scanning. Sorting. Command Line Arguments. Misc CSCE150A. Introduction.
 Chapter 9 Scanning Computer Science & Engineering 150A Problem Solving Using Computers Lecture 07 - Strings Stephen Scott (Adapted from Christopher M. Bourke) Scanning 9.1 String 9.2 Functions: Assignment
Chapter 9 Scanning Computer Science & Engineering 150A Problem Solving Using Computers Lecture 07 - Strings Stephen Scott (Adapted from Christopher M. Bourke) Scanning 9.1 String 9.2 Functions: Assignment
CSE 333 Midterm Exam 5/10/13
 Name There are 5 questions worth a total of 100 points. Please budget your time so you get to all of the questions. Keep your answers brief and to the point. The exam is closed book, closed notes, closed
Name There are 5 questions worth a total of 100 points. Please budget your time so you get to all of the questions. Keep your answers brief and to the point. The exam is closed book, closed notes, closed
Should you know scanf and printf?
 C-LANGUAGE INPUT & OUTPUT C-Language Output with printf Input with scanf and gets_s and Defensive Programming Copyright 2016 Dan McElroy Should you know scanf and printf? scanf is only useful in the C-language,
C-LANGUAGE INPUT & OUTPUT C-Language Output with printf Input with scanf and gets_s and Defensive Programming Copyright 2016 Dan McElroy Should you know scanf and printf? scanf is only useful in the C-language,
Buffer Overflow Vulnerability
 Buffer Overflow Vulnerability 1 Buffer Overflow Vulnerability Copyright c 2006 2014 Wenliang Du, Syracuse University. The development of this document is/was funded by three grants from the US National
Buffer Overflow Vulnerability 1 Buffer Overflow Vulnerability Copyright c 2006 2014 Wenliang Du, Syracuse University. The development of this document is/was funded by three grants from the US National
Computer Science & Engineering 150A Problem Solving Using Computers. Chapter 9. Strings. Notes. Notes. Notes. Lecture 07 - Strings
 Computer Science & Engineering 150A Problem Solving Using Computers Lecture 07 - Strings Scanning Stephen Scott (Adapted from Christopher M. Bourke) 1 / 51 Fall 2009 cbourke@cse.unl.edu Chapter 9 Scanning
Computer Science & Engineering 150A Problem Solving Using Computers Lecture 07 - Strings Scanning Stephen Scott (Adapted from Christopher M. Bourke) 1 / 51 Fall 2009 cbourke@cse.unl.edu Chapter 9 Scanning
Programming in C. What is C?... What is C?
 Programming in C UVic SEng 265 C Developed by Brian Kernighan and Dennis Ritchie of Bell Labs Earlier, in 1969, Ritchie and Thompson developed the Unix operating system We will be focusing on a version
Programming in C UVic SEng 265 C Developed by Brian Kernighan and Dennis Ritchie of Bell Labs Earlier, in 1969, Ritchie and Thompson developed the Unix operating system We will be focusing on a version
CSE 509: Computer Security
 CSE 509: Computer Security Date: 2.16.2009 BUFFER OVERFLOWS: input data Server running a daemon Attacker Code The attacker sends data to the daemon process running at the server side and could thus trigger
CSE 509: Computer Security Date: 2.16.2009 BUFFER OVERFLOWS: input data Server running a daemon Attacker Code The attacker sends data to the daemon process running at the server side and could thus trigger
Room 3P16 Telephone: extension ~irjohnson/uqc146s1.html
 UQC146S1 Introductory Image Processing in C Ian Johnson Room 3P16 Telephone: extension 3167 Email: Ian.Johnson@uwe.ac.uk http://www.csm.uwe.ac.uk/ ~irjohnson/uqc146s1.html Ian Johnson 1 UQC146S1 What is
UQC146S1 Introductory Image Processing in C Ian Johnson Room 3P16 Telephone: extension 3167 Email: Ian.Johnson@uwe.ac.uk http://www.csm.uwe.ac.uk/ ~irjohnson/uqc146s1.html Ian Johnson 1 UQC146S1 What is
CSC209H Lecture 3. Dan Zingaro. January 21, 2015
 CSC209H Lecture 3 Dan Zingaro January 21, 2015 Streams (King 22.1) Stream: source of input or destination for output We access a stream through a file pointer (FILE *) Three streams are available without
CSC209H Lecture 3 Dan Zingaro January 21, 2015 Streams (King 22.1) Stream: source of input or destination for output We access a stream through a file pointer (FILE *) Three streams are available without
Content. Input Output Devices File access Function of File I/O Redirection Command-line arguments
 File I/O Content Input Output Devices File access Function of File I/O Redirection Command-line arguments UNIX and C language C is a general-purpose, high-level language that was originally developed by
File I/O Content Input Output Devices File access Function of File I/O Redirection Command-line arguments UNIX and C language C is a general-purpose, high-level language that was originally developed by
Work relative to other classes
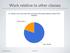 Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Computer Science & Engineering 150A Problem Solving Using Computers
 Computer Science & Engineering 150A Problem Solving Using Computers Lecture 07 - Strings Stephen Scott (Adapted from Christopher M. Bourke) 1 / 51 Fall 2009 Chapter 9 9.1 String 9.2 Functions: Assignment
Computer Science & Engineering 150A Problem Solving Using Computers Lecture 07 - Strings Stephen Scott (Adapted from Christopher M. Bourke) 1 / 51 Fall 2009 Chapter 9 9.1 String 9.2 Functions: Assignment
Ethical Hacking: Preventing & Writing Buffer Overflow Exploits
 Ethical Hacking: Preventing & Writing Buffer Overflow Exploits Rochester Security Summit 2014 Rochester OWASP Chapter Lead Ralph Durkee - Durkee Consulting, Inc. info@rd1.net Ralph Durkee Background Founder
Ethical Hacking: Preventing & Writing Buffer Overflow Exploits Rochester Security Summit 2014 Rochester OWASP Chapter Lead Ralph Durkee - Durkee Consulting, Inc. info@rd1.net Ralph Durkee Background Founder
Introduction to C Programming Ray Lauff Temple University Computer Science v2.0
 Introduction to C Programming Ray Lauff Temple University Computer Science v2.0 NOTE: Not all the material covered in class is included in this slide deck. These slides are not meant to be used as a stand-alone
Introduction to C Programming Ray Lauff Temple University Computer Science v2.0 NOTE: Not all the material covered in class is included in this slide deck. These slides are not meant to be used as a stand-alone
Dynamic memory allocation
 Dynamic memory allocation outline Memory allocation functions Array allocation Matrix allocation Examples Memory allocation functions (#include ) malloc() Allocates a specified number of bytes
Dynamic memory allocation outline Memory allocation functions Array allocation Matrix allocation Examples Memory allocation functions (#include ) malloc() Allocates a specified number of bytes
Software Security: Buffer Overflow Attacks (continued)
 CSE 484 / CSE M 584: Computer Security and Privacy Software Security: Buffer Overflow Attacks (continued) Spring 2015 Franziska (Franzi) Roesner franzi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann,
CSE 484 / CSE M 584: Computer Security and Privacy Software Security: Buffer Overflow Attacks (continued) Spring 2015 Franziska (Franzi) Roesner franzi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann,
Computer Security. Robust and secure programming in C. Marius Minea. 12 October 2017
 Computer Security Robust and secure programming in C Marius Minea marius@cs.upt.ro 12 October 2017 In this lecture Write correct code minimizing risks with proper error handling avoiding security pitfalls
Computer Security Robust and secure programming in C Marius Minea marius@cs.upt.ro 12 October 2017 In this lecture Write correct code minimizing risks with proper error handling avoiding security pitfalls
This time. Defenses and other memory safety vulnerabilities. Everything you ve always wanted to know about gdb but were too afraid to ask
 This time We will continue Buffer overflows By looking at Overflow Defenses and other memory safety vulnerabilities Everything you ve always wanted to know about gdb but were too afraid to ask Overflow
This time We will continue Buffer overflows By looking at Overflow Defenses and other memory safety vulnerabilities Everything you ve always wanted to know about gdb but were too afraid to ask Overflow
Slide Set 3. for ENCM 339 Fall Steve Norman, PhD, PEng. Electrical & Computer Engineering Schulich School of Engineering University of Calgary
 Slide Set 3 for ENCM 339 Fall 2016 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary September 2016 ENCM 339 Fall 2016 Slide Set 3 slide 2/46
Slide Set 3 for ENCM 339 Fall 2016 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary September 2016 ENCM 339 Fall 2016 Slide Set 3 slide 2/46
(heavily based on last year s notes (Andrew Moore) with thanks to Alastair R. Beresford. 1. Types Variables Expressions & Statements 2/23
 Structure of this course Programming in C: types, variables, expressions & statements functions, compilation, pre-processor pointers, structures extended examples, tick hints n tips Programming in C++:
Structure of this course Programming in C: types, variables, expressions & statements functions, compilation, pre-processor pointers, structures extended examples, tick hints n tips Programming in C++:
This time. Defenses and other memory safety vulnerabilities. Everything you ve always wanted to know about gdb but were too afraid to ask
 This time We will continue Buffer overflows By looking at Overflow Defenses and other memory safety vulnerabilities Everything you ve always wanted to know about gdb but were too afraid to ask Overflow
This time We will continue Buffer overflows By looking at Overflow Defenses and other memory safety vulnerabilities Everything you ve always wanted to know about gdb but were too afraid to ask Overflow
ECE 435 Network Engineering Lecture 5
 ECE 435 Network Engineering Lecture 5 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 18 September 2018 HW#2 was posted. Announcements 1 HW#1 Review Sockets Code Need to clear
ECE 435 Network Engineering Lecture 5 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 18 September 2018 HW#2 was posted. Announcements 1 HW#1 Review Sockets Code Need to clear
CSci 4061 Introduction to Operating Systems. Programs in C/Unix
 CSci 4061 Introduction to Operating Systems Programs in C/Unix Today Basic C programming Follow on to recitation Structure of a C program A C program consists of a collection of C functions, structs, arrays,
CSci 4061 Introduction to Operating Systems Programs in C/Unix Today Basic C programming Follow on to recitation Structure of a C program A C program consists of a collection of C functions, structs, arrays,
Other array problems. Integer overflow. Outline. Integer overflow example. Signed and unsigned
 Other array problems CSci 5271 Introduction to Computer Security Day 4: Low-level attacks Stephen McCamant University of Minnesota, Computer Science & Engineering Missing/wrong bounds check One unsigned
Other array problems CSci 5271 Introduction to Computer Security Day 4: Low-level attacks Stephen McCamant University of Minnesota, Computer Science & Engineering Missing/wrong bounds check One unsigned
Betriebssysteme und Sicherheit Sicherheit. Buffer Overflows
 Betriebssysteme und Sicherheit Sicherheit Buffer Overflows Software Vulnerabilities Implementation error Input validation Attacker-supplied input can lead to Corruption Code execution... Even remote exploitation
Betriebssysteme und Sicherheit Sicherheit Buffer Overflows Software Vulnerabilities Implementation error Input validation Attacker-supplied input can lead to Corruption Code execution... Even remote exploitation
UMSSIA LECTURE I: SOFTWARE SECURITY
 UMSSIA LECTURE I: SOFTWARE SECURITY THINKING LIKE AN ADVERSARY SECURITY ASSESSMENT Confidentiality? Availability? Dependability? Security by Obscurity: a system that is only secure if the adversary doesn
UMSSIA LECTURE I: SOFTWARE SECURITY THINKING LIKE AN ADVERSARY SECURITY ASSESSMENT Confidentiality? Availability? Dependability? Security by Obscurity: a system that is only secure if the adversary doesn
6.S096 Lecture 1 Introduction to C
 6.S096 Lecture 1 Introduction to C Welcome to the Memory Jungle Andre Kessler January 8, 2014 Andre Kessler 6.S096 Lecture 1 Introduction to C January 8, 2014 1 / 26 Outline 1 Motivation 2 Class Logistics
6.S096 Lecture 1 Introduction to C Welcome to the Memory Jungle Andre Kessler January 8, 2014 Andre Kessler 6.S096 Lecture 1 Introduction to C January 8, 2014 1 / 26 Outline 1 Motivation 2 Class Logistics
