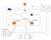
Deploy ERSPAN with the ExtraHop Discover Appliance and Brocade 5600 vrouter in AWS
|
|
|
- Emory Glenn
- 5 years ago
- Views:
Transcription
1 Deploy ERSPAN with the ExtraHop Discover Appliance and Brocade 5600 vrouter in AWS Published: This guide explains how to install and con#gure an example environment within Amazon Web Services (AWS) through built#in ERSPAN capabilities on the ExtraHop Discover appliance and the Brocade 5600 vrouter. Encapsulated Remote Switched Port Analyzer (ERSPAN) enables you to monitor traffic on multiple network interfaces or VLANs and send the monitored traffic to one or more destinations, including ExtraHop appliances. Configuring ERSPAN on the Brocade 5600 vrouter with the ExtraHop Discover appliance enables additional mission-critical traffic analytics, monitoring, and visibility across AWS and other cloud platforms. Additional references The document assumes a certain level of familiarity with networking. Completing the steps in this guide requires an AWS account. If you are new to ExtraHop, Brocade, or Amazon Web Services, see the following links for additional information: Deploy the ExtraHop Discover Appliance in AWS Using the Brocade 5600 vrouter 5600 in AWS Con#gure an AWS Virtual Private Cloud network In this section, you will con#gure a new virtual private cloud (VPC), an Internet gateway, subnets, and routing services. Create a VPC Sign into the AWS console. In the Networking section, click VPC. In the Virtual Private Cloud section, click Your VPCs and then click Create VPC In the Name tag field, type a name for the VPC. In the CIDR block field, type a block of IP addresses for the network, such as /16. In the Tenancy field, leave the option set to Default. Click Yes, Create. Note: Make note of the VPC ID (vpc-nnnnnnnn), which is needed for the next procedure. Create an Internet Gateway In the navigation pane, click Internet Gateways, and then click Create Internet Gateway. In the Name tag field, type a name to identify the Internet gateway. This setting allows public traffic in and out of your virtual private cloud ExtraHop Networks, Inc. All rights reserved.
2 Click Yes, Create. Make note of the gateway ID (igw-nnnnnnnn). Click Attach to VPC. From the drop-down list, select the VPC you created and then click Yes, Attach. Set routes Before traffic is allowed in or out of the new VPC, routing and traffic security rules must be con#gured. By default, all outbound traffic is allowed, but inbound traffic is more restrictive. In the navigation pane, click Route Tables From the table, select the checkbox next to the route that is associated with the VPC you created. Click the Routes tab, and then click Edit. Click Add another route. In the Destination field, type /0. In the Target field, type the name tag you entered for the Internet gateway. Click Save. Create a subnet This example network has a public and private subnet within the CIDR block you configured earlier. You will con#gure /24 as the public subnet and 10.0/24 as the private subnet. 6. In the navigation pane, click Subnets, and then click Create Subnet. In the Name tag field, type a name for the subnet. From the VPC drop-down list, select the VPC created earlier. Optional: From the Availability Zone drop-down list, select the Amazon availability zone where the subnet will reside. In the CIDR block field, type the public CIDR block of /2 Click Yes, Create. 2
3 7. Repeat steps 1-6 to create a private subnet with the 10.0/24 CIDR block. Associate the route table with the subnet In the navigation pane, click Route Tables. Verify that the route table selected is the table with the Internet gateway you created earlier. Click the Subnet Associations tab. Click Edit and select the public subnet of /24, and then click Save. 3
4 Click Create Route Table to create a new route table for the private subnet 10.0/2 In the Name tag field, type a name for the route table and select the VPC you created earlier, and then click Yes, Create. Select the route table created for the private subnet 10.0/2 Select the Subnet Associations tab. Click Edit and select the private subnet 10.0/24 and then click Save. Make note of this route table, in a subsequent step an association is made to the private interface of the Brocade vrouter with a route. Add inbound rules to the security group In the navigation pane, select your new VPC from the Filter by VPC pulldown. In the navigation pane, click Security Groups. The security group has rules allowing traffic into the VPC. The initial setup allows all traffic from itself, all ICMP (so you can test ping of interface) and SSH on port 2 Select the default security group for your new VPC. Click the Inbound Rules tab and then click Edit. Click Add another rule. Select All ICMP from the dropdown list and type /0 in the Source field. Click Add another rule. Select SSH (22) from the dropdown list and type /0 in the Source field. Click Save. 4
5 Note: This is a non-production con#guration; you would not typically allow all IP addresses to access your instance. Summary In this section you created a virtual public cloud, a private subnet for the 10.0/24 network and a public subnet for the /24 network. In addition, you created routing tables for routing traffic within the VPC subnets and externally through an Internet Gateway. Security groups allow traffic in or out of the VPC and you con#gured inbound rules to allow ICMP and SSH traffic. Configure the Brocade 5600v router In this section you will con#gure a new Brocade 5600v router within the public subnet created previously, and assign an Elastic IP to con#gure and test the setup through SSH. Click the Console Home icon in the upper left corner to return to the AWS Management Console page. In the Compute section, click EC In the navigation pane, click Instances. Click Launch Instance to start the Amazon Machine Image (AMI) wizard. Click AWS Marketplace and type 5600 or Brocade vrouter in the Search AWS Marketplace Products field and then press ENTER. 6. Click the Select button next to Brocade 5600 Virtual Router/Firewall/VPN. 7. For this example, select the mlarge instance type and then click Next: Configure Instance Details. 8. On the Configure Instance Details page, complete the following steps: a) Type 1 in the Number of instances field. b) From the Network dropdown list, select the VPC you created in the first section of this guide. c) From the Subnet dropdown list, select the public subnet, /2 d) In the Network interfaces section at the bottom of the page, type in the Primary IP field. 9. Click Next: Add Storage. Keep the default storage settings and then click Next: Tag Instance. 10. Type any name in the Value field for the Name key to identify the instance. Add any additional tags to identify this instance in the environment and then click Next: Con#gure Security Group. 1 Choose Select an existing security group and the select the default Security Group ID for your VPC. 5
6 Ensure the rules created earlier have been applied. For example, SSH and ICMP are still listed and their source addresses are /0. Optionally, a new security group could be created specifically for this instance. Click Review and Launch to launch and install the Brocade vrouter. Review the selections and entries, especially the subnet and IP addresses. If costs are a concern, ensure the instance has stayed within the confines of the free trial. Click Launch to launch the instance and register the Brocade vrouter. In the key pair dialog box, select Create a new key pair from the dropdown menu, type a friendly name and click the Download Key Pair button to download the key pair. Ensure you make note of the download location. Click Launch Instances to finish the install process. Click View Instances at the bottom of the Launch Status screen or select Instances from navigation pane. The instance, depending on the selections, might take a several minutes to be fully online. After the instance has fully launched and the Status Checks are complete, click the Description tab at the bottom of the page. In the Network interfaces section, click eth0. Verify that the IP address is (or the IP address configured earlier). Click the link associated with the Interface ID. In this example, the ID is eni-f554a48d. 19. With the private interface of the Brocade vrouter selected, click on the Actions dropdown menu and select Change Source/Dest. Check. 20. Select the Disabled radio button and then click Save. 2 Create the private subnet interface for the Brocade vrouter by clicking Create Network Interface. 2 In the Create Network Interface dialog box, complete the following fields: Description Type a name to identify the private interface. Subnet From the dropdown list, select the subnet for 10.0/2 Private IP Type Security groups Select the default VPS security group. 2 Click Yes, Create to create the new interface. 6
7 2 Select the private interface and then click on the Actions dropdown menu and select Change Source/Dest. Check. 2 Select the Disabled radio button and then click Save. Record or make note of the network interface ID. 26. With the private interface still selected, click Attach. 27. Select your instance from the Instance ID dropdown list and then click Attach. 28. Return to the VPC Dashboard. 29. In the navigation pane, select Route Tables. 30. Select the route table associated with the private subnet 10.0/2 3 Click the Routes tab and then click Edit. 3 Click Add another route. In the Destination field, type /0 and in the target field, type the interface ID noted in step 23 and then click Save. This route table should be associated with the private Interface ID of the Brocade vrouter and associated with the private subnet 10.0/2 3 Allocate an Amazon Elastic IP, a dynamically allocated publicly routed IP, by selecting Elastic IPs from the navigation pane. Click Allocate New Address, and then click Yes, Allocate. 3 From the Actions drop-down menu, select Associate Address and set the following fields: Associate with Network Interface Network Interface Select the public interface ID of the Brocade vrouter. In this example, the ID is enif554a48d. Private IP address Select the public subnet assigned IP address. In this example, it is Click Yes, Associate. Connect to your Brocade vrouter instance through SSH Note: The following procedures were performed in a Mac OS terminal application. Your commands might vary based on your choice of client. Open a terminal client and run the following commands: a) Change to the directory where you downloaded your private key file. For example: remote$ cd ~/Downloads b) Change the permissions of the key file so that it is not publically viewable: remote$ chmod 400 *.pem c) Establish the connection: remote$ ssh -i <vrouter_private_key.pm> vyatta@<elastic_ip> For example: ssh -i brocadevrouter5600.pem vyatta@ If the SSH connection is successful, output similar to the following appears: Welcome to Brocade vrouter Welcome to Brocade Vyatta Network OS Version: 1R2B Description: Brocade Vyatta Network OS 1 R2 7
8 Built on: Fri Dec 18 07:10:38 UTC 2015 Note: If the connection fails, add -vvv to the ssh command to collect debug output, check the security group rules to ensure SSH is allowed, verify the elastic IP is associated with the public interface, and verify ping to the public elastic IP returns a response. Display a list of configured interfaces by running the following command: show interfaces Output similar to the following appears: Codes: S - State, L - Link, u - Up, D - Down, A Admin Down Interface IP Address S/L Description dp0s /24 u/u dp0s /24 -A/D Note: If only one interface appears, reboot the Brocade vrouter by running the reboot command. Two interfaces should be visible. One interface is not configured and an IP address does not appear. To con#gure the interface run the following commands: a) Enter configure mode: configure b) Con#gure the private interface with the previously assigned private IP. In this example, was assigned in the instance in AWS on the private interface. set interfaces dataplane dp0s1 address 10.10/24 c) Set the number of gratuitous Address Resolution Protocol (ARP) requests to send: set interfaces dataplane dp0s1 ip gratuitous-arp-count 1 d) Enable reverse-path filter with no source validation: set interfaces dataplane dp0s1 ip rpf-check disable e) Set the number of NS packets to transmit: set interfaces dataplane dp0s1 ipv6 dup-addr-detect-transmits 1 f) Sets the size of the MTU for the data plane interface: set interfaces dataplane dp0s1 mtu 1500 g) Set the EtherType for VLAN frames: set interfaces dataplane dp0s1 vlan-protocol 0x8100 Run the show interfaces command to view the con#gured interfaces. Output similar to the following appears: interfaces { dataplane dp0s0 { address dhcp ip { gratuitous-arp-count 1 rpf-check disable 8
9 ipv6 { dup-addr-detect-transmits 1 mtu 1500 vlan-protocol 0x8100 dataplane dp0s1 { address 10.10/24 ip { gratuitous-arp-count 1 rpf-check disable ipv6 { dup-addr-detect-transmits 1 mtu 1500 vlan-protocol 0x8100 loopback lo Note: The plus () sign indicates unsaved changes Type commit and then press ENTER. Type save and then press ENTER to save the changes. Optional: Set the SSH service port to 22 to ensure ports are assigned properly on the Brocade vrouter in the con#guration #le: set service ssh port Type commit and then press ENTER. Type save and then press ENTER to save the changes. Type exit to leave configure mode. Run the show interfaces command. Both interfaces should be up and administratively up, similar to the following output: Codes: S - State, L - Link, u - Up, D - Down, A Admin Down Interface IP Address S/L Description dp0s /24 u/u dp0s /24 u/u Note: Leave the vrouter shell open to run additional commands later in this procedure. Summary In this section, you con#gured the Brocade vrouter to be accessible and con#gurable from a remote machine. You also added the appropriate interfaces for creation of additional subnets. (Optional) Con#gure Linux client for traffic generation In this section and the next, you will con#gure a new Linux AMI in order to verify the Brocade vrouter and ExtraHop Discover configuration. If other sources of traffic are available, then these sections can be skipped. Note: A Linux client is selected in the following example. 9
10 6. 7. Click the Console Home icon in the upper left corner to return to the AWS Management Console page. In the Compute section, click EC In the navigation pane, click Instances. Click Launch Instance to start the Amazon Machine Image (AMI) wizard. Locate an Ubuntu Server image in the list and then click Select. Select the tmicro instance type and then click Next: Configure Instance Details. On the Configure Instance Details page, complete the following steps: a) Type 1 in the Number of instances field. b) From the Network dropdown list, select the VPC you created in the first section of this guide. c) From the Subnet dropdown list, select the 10.0/24 subnet. A static IP is not necessary for this step, but make note of the IP address assigned to the instance. In this example, the IP is d) The remaining settings can be left at their default values. 8. Click Next: Add Storage. No changes are necessary. 9. Click Next: Tag Instance. No changes are necessary. 10. Click Next: Configure Security Group. 1 On the Configure Security Group page, complete the following steps: a) b) c) d) e) f) g) h) i) j) Select Create a new security group. In the Security group name field, type a descriptive name. For example, Ubuntu Linux. In the Description field, type a description for this security group. Click Add Rule. Select All ICMP from the dropdown list. In the Source column, select Anywhere from the dropdown list and type /0 in the field. If SSH is not listed, click Add Rule. In the Source column, select Anywhere from the dropdown list and type /0 in the field. Click Review and Launch. Acknowledge that your security group is open to the world, and then click Launch. k) Note: This is a non-production con#guration. Typically, traffic should not be configured open to the world. In the key pair dialog box, select Create a new key pair from the dropdown list. Type a name in the Key pair name field and click Download Key Pair. Make note of the download location and then click Launch Instances to #nish the install process. (Optional) Configure NAT on the vrouter for the Linux client To reach the Linux client on the internal private subnet, both inbound and outbound for traffic generation, NAT must be con#gured on the vrouter. Return to the previously opened vrouter shell prompt. Open a port and masquerade outbound traffic by running the following commands. a) Enter con#gure mode: configure b) Set the destination port. This is an arbitrary port and 445 is specified in this example. set service nat destination rule 10 destination port 445 c) Set the inbound interface: set service nat destination rule 10 inbound-interface dp0s0 10
11 d) Set the protocol: set service nat destination rule 10 protocol tcp e) Set the translation address, where <client_instance_ip> is the IP address of the Linux client: set service nat destination rule 10 translation address <client_ip_address> For example: set service nat destination rule 10 translation address f) Set the translation port: set service nat destination rule 10 translation port 22 g) h) i) Type commit and then press ENTER. Type save and then press ENTER to save the changes. Con#gure outbound traffic on the vrouter to mask the internal addresses: set service nat source rule 100 outbound-interface dp0s0 set service nat source rule 100 translation address masquerade j) k) Type commit and then press ENTER Type save and then press ENTER to save the changes. Note: The rule numbers are arbitrary; however, allow enough space between ranges in case you need to add related rules in the future. Verify that the con#guration is updated with the rules just created by running the following command: show service Output similar to the following appears. Make note of the destination port, the translation port and address to the Linux instance created. Additionally, make sure the interface on both rules are the external interface of the vrouter. nat { destination { rule 10 { destination { port 445 inbound-interface dp0s0 protocol tcp translation { address port 22 source { rule 100 { outbound-interface dp0s0 translation { address masquerade 11
12 ssh { authentication-retries 3 disable-password-authentication port 22 timeout 120 Return to the AWS console to create an inbound rule on the default security group to test NAT rules. a) In the navigation pane, click Instances. b) Select the vrouter in the list of instances. c) In the Description tab area, next to Security groups, click default. d) On the security group page, click the Inbound tab. e) Click Edit. f) Click Add Rule. g) In the Type drop-down list, select Custom TCP Rule. h) In the Port Range field, type 44 i) In the Source field, type /0. (Optional) Test the Linux client configuration On your client computer, open a new terminal window. Connect to the AWS Linux or Windows client with the appropriate keypair and username. ssh i <client.pem> <username>@<elastic_ip> -p 445 For example: ssh -i ubuntulinux.pem ubuntu@ p 445 Note: In the AWS console, with the instance selected, click Connect to learn how to connect to your particular instance. Usernames and connectivity are unique to the AMI selected. After you have successfully connected to the client, ping the public and private IP addresses that you configured earlier and make sure you can reach the specified IPs. For example: ubuntu@ip :~$ ping ubuntu@ip :~$ ping Open a new terminal window and connect to the Brocade vrouter with the appropriate username and keypair. Ping the Linux client IP address. For example: ping Display the route map by running the following command: show ip route Output similar to the following appears: Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area > - selected route, * - FIB route, p - stale info IP Route Table for VRF "default" 12
13 Gateway of last resort is to network K C C C 7. *> *> *> *> /0 via , /24 is directly 10.0/24 is directly /8 is directly dp0s0 connected, dp0s0 connected, dp0s1 connected, lo Display the ARP table by running the following command: show arp Output similar to the following appears: IP Address HW address 02:22:ef:75:6b:79 02:22:ef:75:6b:79 02:1f:68:6c:5c:81 02:f2:d9:aa:fe:c5 Dataplane VALID VALID VALID VALID Controller VALID VALID VALID Device dp0s0 dp0s0 dp0s1 dp0s1 Display the interfaces by running the following command: show interface Output similar to the following appears: Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down Interface IP Address S/L Description dp0s /24 u/u dp0s /24 u/u Summary In this section, you installed and con#gured a Linux instance for generating test packet traffic. Configure ExtraHop Discover appliance 1000v In this section, you will con#gure a new ExtraHop Discover appliance 1000v. 6. Click the Console Home icon in the upper left corner to return to the AWS Management Console page. In the Compute section, click EC In the navigation pane, click Instances. Click Launch Instance to start the Amazon Machine Image (AMI) wizard. Click Community AMIs. Type ExtraHop in the Search community AMIs field and locate the ExtraHop Discover Appliance 1000v x.x.x AMI and click Select. 7. Select the tmedium instance type and then click Next: Configure Instance Details. 8. In the Configure Instance Details page, complete the following steps: a) Type 1 in the Number of instances field. b) In the Network drop-down list, select the VPC created in the first portion of this guide. c) In the Subnet drop-down list, select the private subnet 10.0/2 d) In the Network interfaces section type in the Primary IP field and then click Next: Add Storage. 9. Leave the default storage size at the default setting. Click Next: Tag Instance. 10. Tag the instance with a name to identify the instance. Add any additional tags for identifying this instance in the environment and then click Next: Con#gure Security Group. 13
14 1 On the Configure Security Group page, complete the following steps: a) Select Create a new security group. b) In the Security group name field, type a descriptive name. For example, EDA 1000v. c) In the Description field, type a description for this security group. d) Click Add Rule 6 times and configure each protocol type as follows: Type Protocol Port Range Source SSH TCP 22 Anywhere /0 HTTP TCP 80 Anywhere /0 HTTPS TCP 443 Anywhere /0 Custom TCP Rule TCP 2003 Anywhere /0 Custom UDP Rule UDP 2003 Anywhere /0 All Traffic ALL Custom IP /16 All ICMP ICMP Anywhere /0 1 Click Review and Launch. Note: If a Boot from General Purpose (SSD) dialog appears, select the first option and then click Next. 1 Review the instance selection and then click Launch. 1 In the Select an existing key pair page dialog box, select Proceed without a key pair from the dropdown list. Most of the Discover configuration is completed through the Discover Admin UI, so a key pair is not necessary. Select the I acknowledge checkbox and then click Launch Instances. 1 Go to your Instances list in AWS. Confirm that the status checks have passed and note the instance IP. Configure NAT on the vrouter to access the ExtraHop Discover Web UI To access the ExtraHop Discover Web UI, NAT must be con#gured on the vrouter. Return to the previously opened vrouter shell prompt. Open a port and masquerade outbound traffic by running the following commands. a) Enter con#gure mode: configure b) Set the destination port. This is an arbitrary port and 8443 is specified in this example. set service nat destination rule 20 destination port 8443 c) Set the inbound interface: set service nat destination rule 20 inbound-interface dp0s0 d) Set the protocol: set service nat destination rule 20 protocol tcp e) Set the translation address, where <extrahop_instance_ip> is the IP address of the Linux client: set service nat destination rule 20 translation address <extrahop_ip_address> 14
15 For example: set service nat destination rule 20 translation address f) Set the translation port: set service nat destination rule 20 translation port 443 g) Con#gure outbound traffic on the vrouter to mask the internal addresses (if not done already): set service nat source rule 100 outbound-interface dp0s0 set service nat source rule 100 translation address masquerade h) i) Type commit and then press ENTER. Type save and then press ENTER to save the changes. Note: The rule numbers are arbitrary; however, allow enough space between ranges in case you need to add related rules in the future. Verify that the con#guration is updated with the rules just created by running the following command: show service Return to the AWS console to create an inbound rule on the default security group to test NAT rules. a) In the navigation pane, click Instances. b) Select the vrouter in the list of instances. c) In the Description tab area, next to Security groups, click default. d) On the security group page, click the Inbound tab. e) Click Edit. f) Click Add Rule. g) In the Type drop-down list, select Custom TCP Rule. h) In the Port Range field, type 844 i) In the Source field, type /0. In your browser, type the IP address of the ExtraHop appliance: 6. On the Licensing page, read the ExtraHop general terms and conditions, select I Agree, and then click Submit. 7. On the login screen, type setup for the user name and the instance ID for the password. You can find the Instance ID on the Instances page. Type the characters that follow i- (but not i- itself), and then click Log In. 8. On the Discover Admin page, in the System Settings section, click License. 9. Click Manage License and then click Register. 10. Type the product key obtained from ExtraHop in the Product Key field and then click Register. Note: If license registration fails, ensure the AWS security rules allow outbound HTTP and HTTPS traffic Click Done. Return to the Admin page. In the Network Settings section, click Connectivity. In the Interfaces section verify that Interface 1 is set to Management Port RPCAP/ERSPAN Target. 15
16 (Optional) Create a new volume for packet capture storage Create a new volume for the ExtraHop Discover Appliance 1000v to store trigger-enabled packet capture data In the navigation pane in AWS, click Volumes. Click Create Volume. In the Create Volume dialog box, make sure that the Availability Zone selected is the same zone as the Discover instance and then click Create. Select the new volume in the Volumes list and then select Attach Volume from the Actions dropdown menu. In the Instance field, select your Discover instance and then click Attach. In the navigation pane, click Instances. Select the Discover instance in the list and then click Actions > Instance State > Reboot. When the Discover instance returns to a running state, log into the Discover Admin UI. In the System Settings section, click Disk and verify that the new packet capture disk appears in the list of direct connected disks. Click Enable on the Packet Capture disk to enable. Summary In this section, you con#gured the ExtraHop Discover appliance to receive network packets and traffic from the ERSPAN interface. Optionally, an additional disk was con#gured to allow trigger-enabled packet captures. Configure ERSPAN and portmonitoring on the Brocade vrouter In this section you will con#gure the ERSPAN and portmonitoring features on the Brocade vrouter to send ERSPAN traffic to the ExtraHop Discover appliance. From a remote machine, SSH to the vrouter. ssh -i <vrouter_private_key.pm> vyatta@<elastic_ip> Con#gure the ERSPAN by running the following commands: a) Enter configuration mode: configure b) Set the local IP address for the ERSPAN interface: set interfaces erspan erspan1 local-ip c) Set the remote IP address for the ERSPAN interface: set interfaces erspan erspan1 remote-ip d) Set the following additional configuration: set interfaces erspan erspan1 ip tos inherit set interfaces erspan erspan1 ip ttl 255 set interfaces erspan erspan1 mtu 1500 e) Display the configuration changes: show interfaces f) g) Type commit and then press ENTER. Type save and then press ENTER to save the changes. 16
17 Con#gure the Port Monitor and ERSPAN source by running the following commands: Note: In this example, the source of the monitor is the internal interface of the Brocade vrouter. Additionally, the session and identi#er numbers are arbitrary, but should not overlap other session IDs. a) Set the portmonitor session type: set service portmonitor session 25 type erspan-source b) Set the source interface for portmonitoring: set service portmonitor session 25 source dp0s1 c) Set the destination interface for portmonitoring: set service portmonitor session 25 destination erspan1 d) Set the session identifier: set service portmonitor session 25 erspan identifier 200 e) Set the ERSPAN header type: set service portmonitor session 25 erspan header type-ii f) Set the ERSPAN direction: set service portmonitor session 25 source dp0s1 direction both g) h) i) j) Type commit and then press ENTER. Type save and then press ENTER to save the changes. Port monitoring for the session is immediately enabled if the type, source, destination, ERSPAN identi#er, and ERSPAN header type parameters are con#gured correctly. Type exit to leave configuration mode. Type show configuration to display the new configuration. Output similar to the following appears (truncated for clarity): erspan erspan1 { ip { tos inherit ttl 255 local-ip mtu 1500 remote-ip portmonitor { session 25 { destination erspan1 erspan { header type-ii identifier 200 source dp0s1 { direction both type erspan-source 17
18 Log into the Discover web UI and verify that the ExtraHop is receiving ERSPAN traffic from the vrouter from the Dashboards interface. Summary In this section you have con#gured the Brocade vrouter to send ERSPAN traffic to the ExtraHop appliance allowing analysis of traffic within the Amazon Web Services virtual private cloud without installing any RPCAPD clients. Sample Brocade vrouter con#guration show configuration interfaces { dataplane dp0s0 { address dhcp ip { gratuitous-arp-count 1 rpf-check disable ipv6 { dup-addr-detect-transmits 1 mtu 1500 vlan-protocol 0x8100 dataplane dp0s1 { address 10.10/24 ip { gratuitous-arp-count 1 rpf-check disable 18
19 ipv6 { dup-addr-detect-transmits 1 mtu 1500 vlan-protocol 0x8100 erspan erspan1 { ip { tos inherit ttl 255 local-ip mtu 1500 remote-ip loopback lo protocols { ecmp { mode hrw pim { register-suppression-timer 60 pim6 { register-suppression-timer 60 security { firewall { all-ping enable broadcast-ping disable config-trap disable syn-cookies enable service { nat { destination { rule 10 { destination { port 445 inbound-interface dp0s0 protocol tcp translation { address port 22 rule 20 { destination { port 8443 inbound-interface dp0s0 protocol tcp translation { address port 443 source { rule 100 { 19
20 outbound-interface dp0s0 translation { address masquerade portmonitor { session 25 { destination erspan1 erspan { header type-ii identifier 200 source dp0s1 { direction both type erspan-source ssh { authentication-retries 3 disable-password-authentication port 22 timeout 120 system { acm { create-default deny delete-default deny enable exec-default allow operational-ruleset { rule 9977 { command /show/tech-support/save rule 9978 { action deny command "/show/tech-support/save/*" rule 9979 { command /show/tech-support/save-uncompressed rule 9980 { action deny command "/show/tech-support/saveuncompressed/*" rule 9981 { command /show/tech-support/brief/save rule 9982 { action deny command "/show/tech-support/brief/save/*" 20
21 rule 9983 { command /show/tech-support/brief/saveuncompressed rule 9984 { action deny command "/show/tech-support/brief/saveuncompressed/*" rule 9985 { command /show/tech-support/brief/ rule 9986 { action deny command /show/tech-support/brief rule 9987 { action deny command /show/tech-support rule 9988 { action deny command /show/configuration rule 9989 { command "/clear/*" rule 9990 { command "/show/*" rule 9991 { command "/monitor/*" rule 9992 { command "/ping/*" rule 9993 { command "/reset/*" rule 9994 { command "/release/*" rule 9995 { 21
22 command "/renew/*" rule 9996 { command "/telnet/*" rule 9997 { command "/traceroute/*" rule 9998 { command "/update/*" rule 9999 { action deny command "*" read-default allow ruleset { rule 9999 { group vyattacfg operation "*" path "*" update-default deny config-management { commit-revisions 20 console { device ttys0 { speed 9600 host-name vyatta login { session-timeout 0 user vyatta { authentication { encrypted-password "********" public-keys TestBrocade { key xxx type ssh-rsa level admin syslog { global { archive { files 5 size
23 facility all { level warning time-zone GMT 23
EdgeConnect for Amazon Web Services (AWS)
 Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Deploy the Firepower Management Center Virtual On the AWS Cloud
 Deploy the Firepower Management Center Virtual On the AWS Cloud Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you define.
Deploy the Firepower Management Center Virtual On the AWS Cloud Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you define.
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud
 How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Amazon Web Services Hands- On VPC
 Amazon Web Services Hands- On VPC Copyright 2011-2015, Amazon Web Services, All Rights Reserved Page 1 Table of Contents Overview... 3 Create a VPC... 3 VPC Object Walkthrough... 6 Your VPCs... 6 Subnets...
Amazon Web Services Hands- On VPC Copyright 2011-2015, Amazon Web Services, All Rights Reserved Page 1 Table of Contents Overview... 3 Create a VPC... 3 VPC Object Walkthrough... 6 Your VPCs... 6 Subnets...
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Amazon Virtual Private Cloud. Getting Started Guide
 Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Deploying the Cisco CSR 1000v on Amazon Web Services
 Deploying the Cisco CSR 1000v on Amazon Web Services This section contains the following topics: Prerequisites, page 1 Information About Launching Cisco CSR 1000v on AWS, page 1 Launching the Cisco CSR
Deploying the Cisco CSR 1000v on Amazon Web Services This section contains the following topics: Prerequisites, page 1 Information About Launching Cisco CSR 1000v on AWS, page 1 Launching the Cisco CSR
FortiMail AWS Deployment Guide
 FortiMail AWS Deployment Guide FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT https://support.fortinet.com
FortiMail AWS Deployment Guide FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT https://support.fortinet.com
F5 BIG-IQ Centralized Management and Amazon Web Services: Setup. Version 5.4
 F5 BIG-IQ Centralized Management and Amazon Web Services: Setup Version 5.4 Table of Contents Table of Contents Getting Started with BIG-IQ Virtual Edition...5 What is BIG-IQ Virtual Edition?...5 About
F5 BIG-IQ Centralized Management and Amazon Web Services: Setup Version 5.4 Table of Contents Table of Contents Getting Started with BIG-IQ Virtual Edition...5 What is BIG-IQ Virtual Edition?...5 About
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
How to Install Forcepoint NGFW in Amazon AWS TECHNICAL DOCUMENT
 How to Install Forcepoint NGFW in Amazon AWS TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS... 1 TEST NETWORK DIAGRAM... 2 PREPARING YOUR VPC... 3 IP addressing... 3 Virtual Private Cloud (VPC)...
How to Install Forcepoint NGFW in Amazon AWS TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS... 1 TEST NETWORK DIAGRAM... 2 PREPARING YOUR VPC... 3 IP addressing... 3 Virtual Private Cloud (VPC)...
Silver Peak EC-V and Microsoft Azure Deployment Guide
 Silver Peak EC-V and Microsoft Azure Deployment Guide How to deploy an EC-V in Microsoft Azure 201422-001 Rev. A September 2018 2 Table of Contents Table of Contents 3 Copyright and Trademarks 5 Support
Silver Peak EC-V and Microsoft Azure Deployment Guide How to deploy an EC-V in Microsoft Azure 201422-001 Rev. A September 2018 2 Table of Contents Table of Contents 3 Copyright and Trademarks 5 Support
Immersion Day. Getting Started with Linux on Amazon EC2
 January 2017 Table of Contents Overview... 3 Create a new Key Pair... 4 Launch a Web Server Instance... 6 Browse the Web Server... 13 Appendix Additional EC2 Concepts... 14 Change the Instance Type...
January 2017 Table of Contents Overview... 3 Create a new Key Pair... 4 Launch a Web Server Instance... 6 Browse the Web Server... 13 Appendix Additional EC2 Concepts... 14 Change the Instance Type...
Configuring AWS for Zerto Virtual Replication
 Configuring AWS for Zerto Virtual Replication VERSION 1 MARCH 2018 Table of Contents 1. Prerequisites... 2 1.1. AWS Prerequisites... 2 1.2. Additional AWS Resources... 3 2. AWS Workflow... 3 3. Setting
Configuring AWS for Zerto Virtual Replication VERSION 1 MARCH 2018 Table of Contents 1. Prerequisites... 2 1.1. AWS Prerequisites... 2 1.2. Additional AWS Resources... 3 2. AWS Workflow... 3 3. Setting
Amazon AppStream 2.0: SOLIDWORKS Deployment Guide
 2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
PCoIP Connection Manager for Amazon WorkSpaces
 PCoIP Connection Manager for Amazon WorkSpaces Version 1.0.7 Administrators' Guide TER1408002-1.0.7 Introduction Amazon WorkSpaces is a fully managed cloud-based desktop service that enables end users
PCoIP Connection Manager for Amazon WorkSpaces Version 1.0.7 Administrators' Guide TER1408002-1.0.7 Introduction Amazon WorkSpaces is a fully managed cloud-based desktop service that enables end users
Scenario: V114 Configuration on Vyatta
 Scenario: V114 Configuration on Vyatta This section steps you through initial system configuration tasks. These are tasks that are required for almost any scenario in which you might use the V114 on the
Scenario: V114 Configuration on Vyatta This section steps you through initial system configuration tasks. These are tasks that are required for almost any scenario in which you might use the V114 on the
Immersion Day. Getting Started with Linux on Amazon EC2
 July 2018 Table of Contents Overview... 3 Create a new EC2 IAM Role... 4 Create a new Key Pair... 5 Launch a Web Server Instance... 8 Connect to the server... 14 Using PuTTY on Windows... 15 Configure
July 2018 Table of Contents Overview... 3 Create a new EC2 IAM Role... 4 Create a new Key Pair... 5 Launch a Web Server Instance... 8 Connect to the server... 14 Using PuTTY on Windows... 15 Configure
CloudEdge Deployment Guide
 Hillstone Networks, Inc. CloudEdge Deployment Guide Version 5.5R3P1 Copyright 2016Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice. The software
Hillstone Networks, Inc. CloudEdge Deployment Guide Version 5.5R3P1 Copyright 2016Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice. The software
MyIGW Main. Oregon. MyVPC /16. MySecurityGroup / us-west-2b. Type Port Source SSH /0 HTTP
 MyIGW Main Oregon MyVPC 10.0.0.0/16 10.0.1.0/24 10.0.1.0 -- us-west-2a MySecurityGroup 10.0.2.0/24 10.0.2.0 -- us-west-2b MyWebServer1 MyDBServer DMZ MyInternetRouteTable 0.0.0.0/0 IGW Type Port Source
MyIGW Main Oregon MyVPC 10.0.0.0/16 10.0.1.0/24 10.0.1.0 -- us-west-2a MySecurityGroup 10.0.2.0/24 10.0.2.0 -- us-west-2b MyWebServer1 MyDBServer DMZ MyInternetRouteTable 0.0.0.0/0 IGW Type Port Source
PCoIP Connection Manager for Amazon WorkSpaces
 PCoIP Connection Manager for Amazon WorkSpaces Version 1.0 Administrators' TER1408002-1.0 Contents Who Should Read This 3 What's New 4 Introduction 5 Before You Begin 5 Additional Documentation 6 Network
PCoIP Connection Manager for Amazon WorkSpaces Version 1.0 Administrators' TER1408002-1.0 Contents Who Should Read This 3 What's New 4 Introduction 5 Before You Begin 5 Additional Documentation 6 Network
SAM 8.0 SP2 Deployment at AWS. Version 1.0
 SAM 8.0 SP2 Deployment at AWS Version 1.0 Publication Date July 2011 Copyright 2011 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and
SAM 8.0 SP2 Deployment at AWS Version 1.0 Publication Date July 2011 Copyright 2011 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and
CloudEdge SG6000-VM Installation Guide
 Hillstone Networks, Inc. CloudEdge SG6000-VM Installation Guide Version 5.5R1 Copyright 2015Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice.
Hillstone Networks, Inc. CloudEdge SG6000-VM Installation Guide Version 5.5R1 Copyright 2015Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice.
Ross Whetten, North Carolina State University
 Your First EC2 Cloud Computing Session Jan 2013 Ross Whetten, North Carolina State University BIT815 notes 1. After you set up your AWS account, and you receive the confirmation email from Amazon Web Services
Your First EC2 Cloud Computing Session Jan 2013 Ross Whetten, North Carolina State University BIT815 notes 1. After you set up your AWS account, and you receive the confirmation email from Amazon Web Services
Amazon Virtual Private Cloud. User Guide API Version
 Amazon Virtual Private Cloud User Guide Amazon Web Services Amazon Virtual Private Cloud: User Guide Amazon Web Services Copyright 2012 Amazon Web Services LLC or its affiliates. All rights reserved. The
Amazon Virtual Private Cloud User Guide Amazon Web Services Amazon Virtual Private Cloud: User Guide Amazon Web Services Copyright 2012 Amazon Web Services LLC or its affiliates. All rights reserved. The
Eucalyptus User Console Guide
 Eucalyptus 3.4.1 User Console Guide 2013-12-11 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...5 Install the Eucalyptus User Console...6 Install on Centos / RHEL 6.3...6 Configure
Eucalyptus 3.4.1 User Console Guide 2013-12-11 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...5 Install the Eucalyptus User Console...6 Install on Centos / RHEL 6.3...6 Configure
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
VX 9000 Virtualized Controller INSTALLATION GUIDE
 VX 9000 Virtualized Controller INSTALLATION GUIDE 2 VX 9000 Virtualized Controller Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
VX 9000 Virtualized Controller INSTALLATION GUIDE 2 VX 9000 Virtualized Controller Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
SonicWALL / Toshiba General Installation Guide
 SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
Deploy the ExtraHop Discover Appliance with VMware
 Deploy the ExtraHop Discover Appliance with VMware Published: 2018-07-17 The ExtraHop virtual appliance can help you to monitor the performance of your applications across internal networks, the public
Deploy the ExtraHop Discover Appliance with VMware Published: 2018-07-17 The ExtraHop virtual appliance can help you to monitor the performance of your applications across internal networks, the public
AWS VPC Cloud Environment Setup
 AWS VPC Cloud Environment Setup Table of Contents Introduction 3 Requirements 5 Step 1: VPC Deployment Setup 10 Step 2: Launching a VNS3 Controller 15 Instance VNS3 Configuration Document Links 19 2 Introduction
AWS VPC Cloud Environment Setup Table of Contents Introduction 3 Requirements 5 Step 1: VPC Deployment Setup 10 Step 2: Launching a VNS3 Controller 15 Instance VNS3 Configuration Document Links 19 2 Introduction
Firebox Cloud. Deployment Guide. Firebox Cloud for AWS and Microsoft Azure
 Firebox Cloud Deployment Guide Firebox Cloud for AWS and Microsoft Azure About This Guide The Firebox Cloud Deployment Guide is a guide for deployment of a WatchGuard Firebox Cloud virtual security appliance.
Firebox Cloud Deployment Guide Firebox Cloud for AWS and Microsoft Azure About This Guide The Firebox Cloud Deployment Guide is a guide for deployment of a WatchGuard Firebox Cloud virtual security appliance.
Launch and Configure SafeNet ProtectV in AWS Marketplace
 ProtectV TECHNICAL INSTRUCTIONS Launch and Configure SafeNet ProtectV in AWS Marketplace Contents Overview... 2 Prerequisites... 2 Configure KeySecure... 3 Configure the Firewall (for Linux Clients Only)...
ProtectV TECHNICAL INSTRUCTIONS Launch and Configure SafeNet ProtectV in AWS Marketplace Contents Overview... 2 Prerequisites... 2 Configure KeySecure... 3 Configure the Firewall (for Linux Clients Only)...
PVS Deployment in the Cloud. Last Updated: June 17, 2016
 PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
From there, navigate to the Policies option and select the Create Policy button at the top:
 Information on the Palo Alto AWS AMI and the HA configuration steps. This will help avoid future pitfalls when deploying this. Policy Configuration: When deploying HA in AWS, before you do anything else
Information on the Palo Alto AWS AMI and the HA configuration steps. This will help avoid future pitfalls when deploying this. Policy Configuration: When deploying HA in AWS, before you do anything else
Sputnik Installation and Configuration Guide
 Sputnik Installation and Configuration Guide Contents Introduction... 2 Installing Sputnik (Local Linux Machine)... 2 Sputnik Operation... 2 Creating an Amazon EC2 instance for Sputnik... 3 Configuring
Sputnik Installation and Configuration Guide Contents Introduction... 2 Installing Sputnik (Local Linux Machine)... 2 Sputnik Operation... 2 Creating an Amazon EC2 instance for Sputnik... 3 Configuring
VX 9000E WiNG Express Manager INSTALLATION GUIDE
 VX 9000E WiNG Express Manager INSTALLATION GUIDE 2 VX 9000E WiNG Express Manager Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
VX 9000E WiNG Express Manager INSTALLATION GUIDE 2 VX 9000E WiNG Express Manager Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name
 firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
Deploy and Secure an Internet Facing Application with the Barracuda Web Application Firewall in Amazon Web Services
 Deploy and Secure an Internet Facing Application with the in Amazon Web In this lab, you will deploy an unsecure web application into Amazon Web (AWS), and then secure the application using the. To create
Deploy and Secure an Internet Facing Application with the in Amazon Web In this lab, you will deploy an unsecure web application into Amazon Web (AWS), and then secure the application using the. To create
AppGate for AWS Step-by-Step Setup Guide. Last revised April 28, 2017
 AppGate for AWS Step-by-Step Setup Guide Last revised April 28, 2017 Contents Welcome & Overview... 2 Getting Started... 3 Pre-Requisites... 4 But what about Security Groups?... 5 Browser Compatibility:...
AppGate for AWS Step-by-Step Setup Guide Last revised April 28, 2017 Contents Welcome & Overview... 2 Getting Started... 3 Pre-Requisites... 4 But what about Security Groups?... 5 Browser Compatibility:...
UDP Director Virtual Edition
 UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
Reset the Admin Password with the ExtraHop Rescue CD
 Reset the Admin Password with the ExtraHop Rescue CD Published: 2018-01-19 This guide explains how to reset the administration password on physical and virtual ExtraHop appliances with the ExtraHop Rescue
Reset the Admin Password with the ExtraHop Rescue CD Published: 2018-01-19 This guide explains how to reset the administration password on physical and virtual ExtraHop appliances with the ExtraHop Rescue
SelectSurvey.NET AWS (Amazon Web Service) Integration
 SelectSurvey.NET AWS (Amazon Web Service) Integration Written for V4.146.000 10/2015 Page 1 of 24 SelectSurvey.NET AWS Integration This document is a guide to deploy SelectSurvey.NET into AWS Amazon Web
SelectSurvey.NET AWS (Amazon Web Service) Integration Written for V4.146.000 10/2015 Page 1 of 24 SelectSurvey.NET AWS Integration This document is a guide to deploy SelectSurvey.NET into AWS Amazon Web
Sangoma VM SBC AMI at AWS (Amazon Web Services)
 Sangoma VM SBC AMI at AWS (Amazon Web Services) SBC in a Cloud Based UC/VoIP Service. One of the interesting use cases for Sangoma SBC is to provide VoIP Edge connectivity between Softswitches or IPPBX's
Sangoma VM SBC AMI at AWS (Amazon Web Services) SBC in a Cloud Based UC/VoIP Service. One of the interesting use cases for Sangoma SBC is to provide VoIP Edge connectivity between Softswitches or IPPBX's
SonicOS Release Notes
 SonicOS Contents Platform Compatibility... 1 Known Issues... 2 Resolved Issues... 4 Upgrading SonicOS Enhanced Image Procedures... 5 Related Technical Documentation... 10 Platform Compatibility The SonicOS
SonicOS Contents Platform Compatibility... 1 Known Issues... 2 Resolved Issues... 4 Upgrading SonicOS Enhanced Image Procedures... 5 Related Technical Documentation... 10 Platform Compatibility The SonicOS
VPN Definition SonicWall:
 VPN Definition SonicWall: Note: If you have only DHCP-WAN IP at the EdgeMAX side, unfortunatly you must input the WAN-IP as Peer IKE ID. If you have also a DHCP-WAN IP at the SonicWall side, you can input
VPN Definition SonicWall: Note: If you have only DHCP-WAN IP at the EdgeMAX side, unfortunatly you must input the WAN-IP as Peer IKE ID. If you have also a DHCP-WAN IP at the SonicWall side, you can input
ExtraHop Command-line Reference
 ExtraHop Command-line Reference Published: 2018-12-15 You can manage many administrative tasks on your ExtraHop system through a command-line interface (CLI). You will typically manage your ExtraHop appliance
ExtraHop Command-line Reference Published: 2018-12-15 You can manage many administrative tasks on your ExtraHop system through a command-line interface (CLI). You will typically manage your ExtraHop appliance
ForeScout CounterACT. (AWS) Plugin. Configuration Guide. Version 1.3
 ForeScout CounterACT Hybrid Cloud Module: Amazon Web Services (AWS) Plugin Version 1.3 Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic
ForeScout CounterACT Hybrid Cloud Module: Amazon Web Services (AWS) Plugin Version 1.3 Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
ACE Live on RSP: Installation Instructions
 ACE Live on RSP ACE Live on RSP: Installation Instructions These installation instructions apply to OPNET ACE Live on RSP Release 7.1.3. You can find the latest version of this document at the OPNET Support
ACE Live on RSP ACE Live on RSP: Installation Instructions These installation instructions apply to OPNET ACE Live on RSP Release 7.1.3. You can find the latest version of this document at the OPNET Support
Inspection of Inter-Subnet traffic in AWS VPC using CloudGuard
 Inspection of Inter-Subnet traffic in AWS VPC using CloudGuard I've been asked an interesting and, seemingly, trivial question: "How would you protect the hosts in AWS VPC located in a different subnets
Inspection of Inter-Subnet traffic in AWS VPC using CloudGuard I've been asked an interesting and, seemingly, trivial question: "How would you protect the hosts in AWS VPC located in a different subnets
Tutorial 1. Account Registration
 Tutorial 1 /******************************************************** * Author : Kai Chen * Last Modified : 2015-09-23 * Email : ck015@ie.cuhk.edu.hk ********************************************************/
Tutorial 1 /******************************************************** * Author : Kai Chen * Last Modified : 2015-09-23 * Email : ck015@ie.cuhk.edu.hk ********************************************************/
NetApp Cloud Volumes Service for AWS
 NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
SUREedge Migrator Installation Guide for Amazon AWS
 SUREedge Migrator Installation Guide for Amazon AWS Contents 1. Introduction... 3 1.1 SUREedge Migrator Deployment Scenarios... 3 1.2 Installation Overview... 4 2. Obtaining Software and Documentation...
SUREedge Migrator Installation Guide for Amazon AWS Contents 1. Introduction... 3 1.1 SUREedge Migrator Deployment Scenarios... 3 1.2 Installation Overview... 4 2. Obtaining Software and Documentation...
Figure 1 0: AMI Instances
 Title: Configuring Control-M installation in Cloud environment. Last Update: July 4 th, 2018 Cause: Cloud Services Background Cloud Services is a collection of remote computing services that together make
Title: Configuring Control-M installation in Cloud environment. Last Update: July 4 th, 2018 Cause: Cloud Services Background Cloud Services is a collection of remote computing services that together make
Lenovo ThinkAgile XClarity Integrator for Nutanix Installation and User's Guide
 Lenovo ThinkAgile XClarity Integrator for Nutanix Installation and User's Guide Version 1.0 Note Before using this information and the product it supports, read the information in Appendix A Notices on
Lenovo ThinkAgile XClarity Integrator for Nutanix Installation and User's Guide Version 1.0 Note Before using this information and the product it supports, read the information in Appendix A Notices on
Packet Forwarding with RPCAP
 Packet Forwarding with RPCAP Published: 2018-07-17 The ExtraHop Discover appliance generates metrics about your network and applications through a wire data feed, which is typically mirrored from a switch.
Packet Forwarding with RPCAP Published: 2018-07-17 The ExtraHop Discover appliance generates metrics about your network and applications through a wire data feed, which is typically mirrored from a switch.
Configuring the SMA 500v Virtual Appliance
 Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
ITCorporation HOW DO I INSTALL A FRESH INSTANCE OF ANALYZER? DESCRIPTION RESOLUTION. Knowledge Database KNOWLEDGE DATABASE
 KNOWLEDGE DATABASE HOW DO I INSTALL A FRESH INSTANCE OF ANALYZER? 3. Click on GMS/Analyzer - Virtual Appliance or GMS/Analyzer - Virtual Appliance 950GB under GMS - Virtual Appliance. Note: It is not recommended
KNOWLEDGE DATABASE HOW DO I INSTALL A FRESH INSTANCE OF ANALYZER? 3. Click on GMS/Analyzer - Virtual Appliance or GMS/Analyzer - Virtual Appliance 950GB under GMS - Virtual Appliance. Note: It is not recommended
Create a Dual Stack Virtual Private Cloud (VPC) in AWS
 Create a Dual Stack Virtual Private Cloud (VPC) in AWS Lawrence E. Hughes 5 November 2017 This recipe assumes you already have an AWS account. If you don t there is a lot of information online (including
Create a Dual Stack Virtual Private Cloud (VPC) in AWS Lawrence E. Hughes 5 November 2017 This recipe assumes you already have an AWS account. If you don t there is a lot of information online (including
FusionHub. SpeedFusion Virtual Appliance. Installation Guide Version Peplink
 FusionHub SpeedFusion Virtual Appliance Installation Guide Version 1.1.0-5 2015 Peplink FusionHub Installation Guide Table of Contents 1. Purpose... 2 2. FusionHub License Generation... 2 3. FusionHub
FusionHub SpeedFusion Virtual Appliance Installation Guide Version 1.1.0-5 2015 Peplink FusionHub Installation Guide Table of Contents 1. Purpose... 2 2. FusionHub License Generation... 2 3. FusionHub
AltaVault Cloud Integrated Storage Installation and Service Guide for Cloud Appliances
 AltaVault Cloud Integrated Storage 4.4.1 Installation and Service Guide for Cloud Appliances March 2018 215-13006_A0 doccomments@netapp.com Table of Contents 3 Contents Introduction to AltaVault cloud-based
AltaVault Cloud Integrated Storage 4.4.1 Installation and Service Guide for Cloud Appliances March 2018 215-13006_A0 doccomments@netapp.com Table of Contents 3 Contents Introduction to AltaVault cloud-based
Infoblox Trinzic V-x25 Series Appliances for AWS
 DEPLOYMENT GUIDE Infoblox Trinzic V-x25 Series Appliances for AWS NIOS version 8.2 Oct. 2017 2017 Infoblox Inc. All rights reserved. Infoblox Trinzic TE-Vx25 Deployment Guide October 2017 Page 1 of 29
DEPLOYMENT GUIDE Infoblox Trinzic V-x25 Series Appliances for AWS NIOS version 8.2 Oct. 2017 2017 Infoblox Inc. All rights reserved. Infoblox Trinzic TE-Vx25 Deployment Guide October 2017 Page 1 of 29
Virtual Private Cloud. User Guide. Issue 03 Date
 Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0)
 UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
DWS-4000 Series DWL-3600AP DWL-6600AP
 Unified Wired & Wireless Access System Configuration Guide Product Model: Release 1.0 DWS-4000 Series DWL-8600AP DWL-6600AP DWL-3600AP Page 1 Table of Contents 1. Scenario 1 - Basic L2 Edge Setup: 1 Unified
Unified Wired & Wireless Access System Configuration Guide Product Model: Release 1.0 DWS-4000 Series DWL-8600AP DWL-6600AP DWL-3600AP Page 1 Table of Contents 1. Scenario 1 - Basic L2 Edge Setup: 1 Unified
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
Immersion Day. Getting Started with Windows Server on Amazon EC2. June Rev
 Getting Started with Windows Server on Amazon EC2 June 2017 Rev 2015-09-19 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance...
Getting Started with Windows Server on Amazon EC2 June 2017 Rev 2015-09-19 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance...
Access Rules. Controlling Network Access
 This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
Horizon DaaS Platform 6.1 Service Provider Installation - vcloud
 Horizon DaaS Platform 6.1 Service Provider Installation - vcloud This guide provides information on how to install and configure the DaaS platform Service Provider appliances using vcloud discovery of
Horizon DaaS Platform 6.1 Service Provider Installation - vcloud This guide provides information on how to install and configure the DaaS platform Service Provider appliances using vcloud discovery of
Pexip Infinity and Google Cloud Platform Deployment Guide
 Pexip Infinity and Google Cloud Platform Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring your Google VPC network 4 Obtaining and preparing disk images for GCE Virtual Machines
Pexip Infinity and Google Cloud Platform Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring your Google VPC network 4 Obtaining and preparing disk images for GCE Virtual Machines
CPM. Quick Start Guide V2.4.0
 CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
LevelOne FBR User s Manual. 1W, 4L 10/100 Mbps ADSL Router. Ver
 LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
NSX-T Data Center Migration Coordinator Guide. 5 APR 2019 VMware NSX-T Data Center 2.4
 NSX-T Data Center Migration Coordinator Guide 5 APR 2019 VMware NSX-T Data Center 2.4 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
NSX-T Data Center Migration Coordinator Guide 5 APR 2019 VMware NSX-T Data Center 2.4 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Load Balancing FreePBX / Asterisk in AWS
 Load Balancing FreePBX / Asterisk in AWS Quick Reference Guide V1.0.1 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance FreePBX / Asterisk servers using the Enterprise
Load Balancing FreePBX / Asterisk in AWS Quick Reference Guide V1.0.1 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance FreePBX / Asterisk servers using the Enterprise
Packet Forwarding with RPCAP
 Packet Forwarding with RPCAP Published: 2019-02-09 The ExtraHop Discover appliance generates metrics about your network and applications through a wire data feed, which is typically mirrored from a switch.
Packet Forwarding with RPCAP Published: 2019-02-09 The ExtraHop Discover appliance generates metrics about your network and applications through a wire data feed, which is typically mirrored from a switch.
Eucalyptus User Console Guide
 Eucalyptus 4.0.2 User Console Guide 2014-11-05 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...5 Install the Eucalyptus User Console...6 Install on Centos / RHEL 6.3...6 Configure
Eucalyptus 4.0.2 User Console Guide 2014-11-05 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...5 Install the Eucalyptus User Console...6 Install on Centos / RHEL 6.3...6 Configure
Deploy the ExtraHop Discover Appliance with Hyper-V
 Deploy the ExtraHop Discover Appliance with Hyper-V Published: 2018-07-16 The following procedures explain how to deploy the ExtraHop Discover EDA 1000v and EDA 2000v virtual appliance on the Microsoft
Deploy the ExtraHop Discover Appliance with Hyper-V Published: 2018-07-16 The following procedures explain how to deploy the ExtraHop Discover EDA 1000v and EDA 2000v virtual appliance on the Microsoft
LB Cache Quick Start Guide v1.0
 LB Cache Quick Start Guide v1.0 Rev. 1.1.0 Copyright 2002 2017 Loadbalancer.org, Inc Table of Contents Introduction...3 About LBCache...3 Amazon Terminology...3 Getting Started...3 Deployment Concepts...4
LB Cache Quick Start Guide v1.0 Rev. 1.1.0 Copyright 2002 2017 Loadbalancer.org, Inc Table of Contents Introduction...3 About LBCache...3 Amazon Terminology...3 Getting Started...3 Deployment Concepts...4
Create a pfsense router for your private lab network template
 Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
AWS Quick Start Guide. Launch a Linux Virtual Machine Version
 AWS Quick Start Guide Launch a Linux Virtual Machine AWS Quick Start Guide: Launch a Linux Virtual Machine Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's
AWS Quick Start Guide Launch a Linux Virtual Machine AWS Quick Start Guide: Launch a Linux Virtual Machine Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's
Deploy the ExtraHop Discover Appliance 1100
 Deploy the ExtraHop Discover Appliance 1100 Published: 2018-07-17 The following procedures explain how to deploy an ExtraHop Discover appliance 1100. System requirements Your environment must meet the
Deploy the ExtraHop Discover Appliance 1100 Published: 2018-07-17 The following procedures explain how to deploy an ExtraHop Discover appliance 1100. System requirements Your environment must meet the
IBM Security Guardium Cloud Deployment Guide AWS EC2
 IBM Security Guardium Cloud Deployment Guide AWS EC2 Getting the Public Guardium Images The official Guardium version 10.1.3 AMIs are listed publicly and are accessible to all other AWS accounts. To get
IBM Security Guardium Cloud Deployment Guide AWS EC2 Getting the Public Guardium Images The official Guardium version 10.1.3 AMIs are listed publicly and are accessible to all other AWS accounts. To get
Deploy the ExtraHop Trace 6150 Appliance
 Deploy the ExtraHop Trace 6150 Appliance Published: 2018-04-20 This guide explains how to install the rack-mounted ETA 6150 ExtraHop Trace appliances. System requirements This guide explains how to install
Deploy the ExtraHop Trace 6150 Appliance Published: 2018-04-20 This guide explains how to install the rack-mounted ETA 6150 ExtraHop Trace appliances. System requirements This guide explains how to install
F5 WANJet 200. Quick Start Guide. Quick Start Overview
 F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
Launch and Configure SafeNet ProtectV in AWS Marketplace
 ProtectV TECHNICAL INSTRUCTIONS Launch and Configure SafeNet ProtectV in AWS Marketplace Contents Overview... 2 Prerequisites... 2 Configure KeySecure... 3 Configure the Firewall (for Linux Clients Only)...
ProtectV TECHNICAL INSTRUCTIONS Launch and Configure SafeNet ProtectV in AWS Marketplace Contents Overview... 2 Prerequisites... 2 Configure KeySecure... 3 Configure the Firewall (for Linux Clients Only)...
Creating Application Containers
 This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 3 About Application Container Templates, page 5 Creating
This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 3 About Application Container Templates, page 5 Creating
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
How to Setup Total Application Security
 How to Setup Total Application Security TABLE OF CONTENTS Access Total Application Security on AWS Marketplace... 2 Configuring Total Application Security... 12 Total Application Security Portal Access...
How to Setup Total Application Security TABLE OF CONTENTS Access Total Application Security on AWS Marketplace... 2 Configuring Total Application Security... 12 Total Application Security Portal Access...
Chapter 4 Software-Based IP Access Control Lists (ACLs)
 Chapter 4 Software-Based IP Access Control Lists (ACLs) This chapter describes software-based ACLs, which are ACLs that processed traffic in software or CPU. (This type of ACL was also referred to as flow-based
Chapter 4 Software-Based IP Access Control Lists (ACLs) This chapter describes software-based ACLs, which are ACLs that processed traffic in software or CPU. (This type of ACL was also referred to as flow-based
Provisioning Lumeta SPECTRE via AWS Sign in to the Amazon Web Services console at
 Thank you for choosing Lumeta SPECTRE! This document provides the essentials you ll need to make sense of your network in real time from the Amazon Web Services (AWS) cloud, including: 1) How to instantiate
Thank you for choosing Lumeta SPECTRE! This document provides the essentials you ll need to make sense of your network in real time from the Amazon Web Services (AWS) cloud, including: 1) How to instantiate
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
Installation of Informatica Services on Amazon EC2
 Installation of Informatica Services on Amazon EC2 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Installation of Informatica Services on Amazon EC2 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Immersion Day. Getting Started with Windows Server on. Amazon EC2. Rev
 Getting Started with Windows Server on Amazon EC2 Rev 2015-01-15 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance... 13
Getting Started with Windows Server on Amazon EC2 Rev 2015-01-15 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance... 13
