What a VPN Does and Does Not Do
|
|
|
- Hector Boyd
- 5 years ago
- Views:
Transcription
1 How to Set Up and Use a VPN There's more to setting up a virtual private network than just signing up and activating the service. Our guide can help you get the most from this critical privacy and security tool. ByMax Eddy May 9, :40AM EST Everyone should be using a virtual private network or VPN, whether you're connecting to the Internet on your computer or your smartphone. That may sound paranoid, but there are real threats out there, and they're only getting worse. On Wi-Fi networks, unscrupulous individuals can attempt to intercept your information. And whenever you connect to the internet, your Internet Service Provider (ISP) has access to everything you send and has been given the green light from Congress to sell your anonymized information to advertisers, too. Out on the wide open internet, advertisers and spies can track your movements between websites and discern your location by peeking at your IP address. It's scary out there. The fact is the internet was not designed to protect your privacy. It was created for easy information exchange, not user privacy, anonymization, or encrypted communication. While HTTPS goes a long way toward protecting your information, it doesn't guard against ISP snooping or local network attacks a major problem if you ever use a connection that isn't yours, such as one at a hotel or a coffee shop. So until a new, more private internet comes together (probably never), using a VPN is the easiest way to make sure that you're sharing as little information as possible. Make no mistake: You need a VPN. What a VPN Does and Does Not Do As with any security tool, it's important to understand the limitations of a VPN. After all, you wouldn't expect a kevlar vest to save you from falling out of an airplane or a parachute to stop a bullet. When you switch on a VPN, your traffic is routed through an encrypted tunnel to a server operated by the VPN company. That means that your ISP and anything (or anyone) connected to your router won't be able to see your web traffic. From the VPN server, your traffic exits onto the public internet. Unless you're headed to a site that uses HTTPS, your traffic is no longer encrypted. Because your traffic appears to come from the VPN's server, your actual IP address is effectively hidden. That's important, because IP addresses are distributed geographically and can be used to infer someone's location. If someone checks your IP address, they'll see the IP address of the VPN server. This can come in handy if you want to spoof your location. By connecting to a VPN server in London, you can make it appear as if you are accessing the internet from the UK. What a VPN won't do is completely anonymize your traffic. To do that, you'll want to use a service such as Tor. This excellent anonymization service is easily accessed through a special version of the Firefox browser. Instead of just piping your data through a single intermediary (that is, a VPN server) Tor bounces your data through several different
2 volunteer computers. This makes it much harder for someone trying to track your activities to see what you're up to. Additionally, websites can track your movements through cookies, browser fingerprinting, online trackers, and other tricky tools. Using an ad-blocker such as Privacy Badger helps suppress these ever watchful nasties and can make it much harder for advertisers to follow your movements across the web. Finally, just because you have a VPN doesn't mean you can forget about the security basics. While some VPN services claim they can block malware, we recommend standalone antivirus software for your computer, because these tools are designed specifically to protect your computer from malicious software. You should also use a password manager, because recycled passwords are a major point of failure. Another precaution is to use common sense when clicking on links or opening attachments. Phishing attacks when an attacker uses a bogus website that mimics a familiar one to trick you into entering your login credentials are so common as to almost be mundane, so stay alert. How to Choose a VPN When we review VPNs, there are a few key metrics we look for. One is that the VPN service should allow you to connect at least five devices at a time. Another is whether or not the VPN service allows BitTorrent traffic on their servers. Some do, some do not, and you don't want to run afoul of the company you're paying a monthly fee to. Speaking of fees, the average cost of a VPN service is $10.53 per month. A VPN service that is charging more per month isn't necessarily ripping you off, but it should offer something significant, such as a great interface or lots of server locations to sweeten the deal. You can usually get a discount if you buy longer-term contracts, but we recommend avoiding those until you're certain that you're happy with the service. Before you sign up with a VPN, be sure to read its terms of service. This document will outline what information the VPN collects and what it does with that information. Most companies say that they don't log traffic, which is great. Others go further, saying that they do not monitor user activity at all. This is important,because a VPN has access to all the information you're trying to protect from others. The best terms of service make all these issues clear, while the worst are opaque on the details and written in legalese. If reading one of these documents feels like you're trying to translate the Dead Sea Scrolls, consider trying another service. TunnelBear, for example, clearly outlines its operation in easy-to-understand language. It's also useful to see where the VPN company is based. Keep in mind that this isn't always the physical location of the business, but a legal distinction that outlines what jurisdiction the company operates under. NordVPN, for example, is in Panama, while ProtonVPN is in Switzerland. That means that these companies are not beholden to data retention laws, which would require them to hold on to certain information that could be obtained by law enforcement. Hide My Ass VPN, on the other hand, is based in the UK, which has more intrusive laws. The most important thing about a VPN is trust. If the location, pricing, or terms of service don't fill you with confidence, try another service.
3 Free or Paid VPNs? We at PCMag recently conducted a survey of 1,000 people, asking questions about VPN use. According to our results, 62.9 percent said they didn't want to pay more than $5, and 47.1 percent said they want to use a free VPN. Unfortunately, most VPNs are a far cry from free. Or even from $5. But you don't need to break the bank to get protected. If after trying out a service for a month or two, you can save more by purchasing longer-term contracts. Private Internet Access is an excellent and affordable service that costs just $6.95 per month for an albeit no-frills experience. Many VPN services offer a free trial, but usually for a limited time. Others, like TunnelBear and AnchorFree Hotspot Shield Elite, have totally free versions but may limit some features to paid users. TunnelBear, for example, has a data allowance for free users. Hotspot Shield, on the other hand, has an ad-supported free version. ProtonVPN, from the creators of the secure service ProtonMail, has a limited free version of its VPN, too. The browser Opera has a free VPN baked in,and charges nothing for its use. Opera separately offers excellent VPN apps for Android and ios, also completely free, extending protection to wherever you go. Getting Started Once you've settled on a service, the first thing to do is to download the company's app. There's usually a downloads page for this on the VPN service's website. Go ahead and download the apps for your mobile devices as well; you'll want to protect as many of your devices as you can. Generally, you pay one subscription fee for a certain number of licenses (usually five) and then you can use the service on any device for which it provides apps. We have found that when releasing VPNs for Mac, companies occasionally have different versions available in the Mac App Store and on the company website. This appears to be in order to comply with Apple's restrictions. Figuring out which will work for you can be tricky, but we've broken down the differences in our reviews. Once you've installed the apps, you're prompted to enter your login information. In most cases, this is the username and password you created when you signed up for the service. Some companies, such as Private Internet Access assign you a username that's different from your billing credentials, in order to provide customers with more privacy. Once you're logged in, your VPN app usually connects to the VPN server closest to your current location. That's done to provide better speeds with a VPN, as latency and speed reductions increase the farther the VPN server is from your actual location. That's it: Your information is now being securely tunneled to the VPN server. Note that you do not have to install the VPN company's app. Instead, you can configure your device's network settings to connect directly to the VPN service. If you're concerned about the potential for surveillance within app ecosystems, this might be a good option for you. Most VPN services will have documentation on how to configure your device.
4 Choosing a Server Sometimes you might not want to be connected to the server the VPN app recommends. Perhaps you want to spoof your location, use BitTorrent via VPN, or you want to take advantage of some of the custom servers your VPN company has provided. Many VPN companies include an interactive map as part of their app. NordVPN, for example, lets you click on countries to connect to those servers. It's a useful way to understand where your information is going, but there's probably a list of servers you can select from. Choosing a server depends entirely on what you want to accomplish. For security and speed, you should choose a server that's close by. To access region-locked content, you'll want a server that's local to content you want to watch. If you're trying to watch the BBC, you'll want to tunnel to the UK. Some VPN companies, such as KeepSolid VPN Unlimited and NordVPN, have specialized servers for streaming video. These specialized servers are useful because streaming services such as Netflix block VPNs. At issue are the licensing deals Netflix secures with studios. For example, Netflix has the rights to provide Star Trek: Discovery outside the US, but within the US you need to pay for CBS's All Access service. It's also a good idea to check and see whether your VPN service allows BitTorrent traffic on any server, or just specific ones. NordVPN clearly marks the servers cleared for torrenting, and others do the same. TorGuard, on the other hand, is all about torrenting and allows its use on all the company's servers. Other services like NordVPN and ProtonVPN have enhanced security options, such as access to Tor or multihop VPNs. Tor, as mentioned above, is a way to better protect your privacy, and lets you access hidden websites on the so-called Dark Web. Multihop VPN is similar: Instead of just routing your traffic through a single VPN server, a multihop connection tunnels you to one server and then another. Both of these offerings trade speed for enhanced privacy. If you've opted to ignore first-party apps and configure your network settings manually, you will probably have to enter the information for each VPN server individually. Advanced Settings The set of features in each VPN varies from service to service, so we can only generalize about what you may see when you open the Settings pane. But we encourage you to read through the documentation and try clicking some buttons. The best way to learn how to use a tool is to try, after all. Most VPN services include some kind of Kill-Switch feature. Once engaged, this option prevents your computer from transmitting or receiving information over the internet unless the VPN is engaged. It's useful for when your computer disconnects from the VPN, and it can prevent little bits of data sneaking through unencrypted.
5 Most services offer an option to select a VPN protocol. This can be intimidating, since they have weird names and companies rarely provide information about what these are, and what changing the protocol will do. In general, this is something you can leave alone. But if you're interested, the protocol we recommend is OpenVPN. It's open-source, so it has been picked over by many eyes for any potential vulnerabilities. IKEv2 is also a good, secure option if OpenVPN is not available. Note that on some platforms, such as macos and iphone, OpenVPN is not always available, because of additional restrictions placed on developers. The best VPNS for iphone give you access to the latest and greatest protocols available on that platform. When Should I Use a VPN? For the best security, you should use a VPN as often as possible and, ideally, all the time. But that's an ideal, and it's not always achievable. At minimum, you should use a VPN whenever you're using a network that's not one you control, and especially if it's a public Wi-Fi network. But in general we recommend that users set the default on their VPN apps to be connected as much as possible. You can always disconnect if it's causing a problem. VPNs for Android and other mobile devices are a little trickier, particularly if you frequently move in and out of cellphone coverage. Each time you lose and regain data connectivity, the VPN has to reconnect, which adds a frustrating wait. It's also just less likely that your cell traffic can be intercepted, but we've seen researchers prove that it can be done. And considering that law enforcement and intelligence agencies have effectively unfettered access to telecom data, it's a good idea to use a VPN even over cellular connections. Also, most mobile devices can automatically connect to any familiar looking Wi-Fi network. At minimum, you should use a VPN when connecting via Wi-Fi, especially because it's trivially simple to impersonate a Wi-Fi network. Many VPNs have settings for how and under what circumstances they should reconnect if they become disrupted. We honestly cannot think of a reason you wouldn't want your VPN to try reconnecting and encourage everyone to make sure their settings reflect this. If you're concerned about VPNs slowing your connections or blocking important traffic, you should take a look at split-tunneling options. Again, different companies give this feature different names, but the gist is that you can decide which apps will use the VPN for their traffic and which apps can transmit without the VPN. TunnelBear, for example, includes an option to not tunnel any Apple apps to ensure they function properly on a Mac. Frequent video streamers and gamers in need of a VPN may want to look into this as an option. How to Use a VPN For Streaming With Chromecast or AirPlay Chromecast and AirPlay let you share music and video from your computer or mobile device to speakers, TVs, and streaming boxes. But all of them require Wi-Fi, which can be a problem when you're using a VPN. When a VPN is engaged, your traffic is moving through an encrypted tunnel, which prevents the devices from finding each other on the same Wi-Fi network. That's as it should be, since you don't want someone snooping around a network to see what you're
6 up to. Sadly, it also means that Chromecast and AirPlay won't work when you have a VPN active. The simplest solution is to switch off your VPN, but that's not your only option. You can use split-tunneling, as mentioned above, to route only the traffic you want secured through the VPN. You can use a VPN browser plugin, which only encrypts your browser traffic and nothing else. Alternatively, you can install a VPN on your router. Doing so means that all the devices connected to your router from your phone to your smart juicer will have their traffic encrypted. That's a great option for a heavily wired smart home. VPNs Aren't Rocket Science Too many of you aren't using a VPN, and maybe that's because they seem like arcane security tools. But many companies have worked hard to make them friendly and easy to use. Most are now set-and-forget security tools, as it should be. And though opening your wallet to guard against potential threats is always annoying, buying a VPN is one of the best and easiest ways to guard your web traffic from, well, just about everyone.
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
WiFi Security User Guide
 WiFi Security User Guide Copyright Copyright 2018 Webroot. All rights reserved. Webroot WiFi Security User Guide Information in this document is subject to change without notice. The software described
WiFi Security User Guide Copyright Copyright 2018 Webroot. All rights reserved. Webroot WiFi Security User Guide Information in this document is subject to change without notice. The software described
Workshop #10 Wifi & WhatsApp
 Workshop #10 Wifi & WhatsApp What is Wi-Fi exactly, what s the big deal & how do I connect to it? WhatsApp Messenger explained Terms you will hear today What is WhatsApp? How do I send a message on WhatsApp
Workshop #10 Wifi & WhatsApp What is Wi-Fi exactly, what s the big deal & how do I connect to it? WhatsApp Messenger explained Terms you will hear today What is WhatsApp? How do I send a message on WhatsApp
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
Main area: Security Additional areas: Digital Access, Information Literacy, Privacy and Reputation
 Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
FAQ IN PARTNERSHIP WITH
 FAQ IN IN PARTNERSHIP WITH 1. What is the offer? Subscribers will get to enjoy special price as below: - (a) RM9.90/month for Varnam Pack subscribers (b) RM14.90/month for non-varnam Pack subscribers 2.
FAQ IN IN PARTNERSHIP WITH 1. What is the offer? Subscribers will get to enjoy special price as below: - (a) RM9.90/month for Varnam Pack subscribers (b) RM14.90/month for non-varnam Pack subscribers 2.
T Mobile Manual Contract Phone Deals Not Working
 T Mobile Manual Contract Phone Deals Not Working Trapped by contracts and phone payment plans? Say goodbye to old wireless Join us and see why 1.6 million people have already broken free from their old
T Mobile Manual Contract Phone Deals Not Working Trapped by contracts and phone payment plans? Say goodbye to old wireless Join us and see why 1.6 million people have already broken free from their old
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
Before You Lose Your iphone
 iphones are lost and stolen every day, but luckily Apple has robust tools built into ios that will keep your data safe and your device unusable if it's misplaced or snatched by a thief. With Find My iphone,
iphones are lost and stolen every day, but luckily Apple has robust tools built into ios that will keep your data safe and your device unusable if it's misplaced or snatched by a thief. With Find My iphone,
Samsung Smart Tv Connected To Internet But Doesn't Work
 Samsung Smart Tv Connected To Internet But Doesn't Work The Samsung software is unable to connect to the internet. My smart TV can talk to local network but anything outside is no. control, or hundreds
Samsung Smart Tv Connected To Internet But Doesn't Work The Samsung software is unable to connect to the internet. My smart TV can talk to local network but anything outside is no. control, or hundreds
INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING,
 INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING, DOWNLOAD EBOOK : INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE
INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING, DOWNLOAD EBOOK : INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE
Your security on click Jobs
 Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures.
 From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures. This is another tutorial which, in about 6 months, will probably be irrelevant. But until
From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures. This is another tutorial which, in about 6 months, will probably be irrelevant. But until
itunes What Is It Good For? 2018 Becky Diamond 1
 itunes What Is It Good For? 2018 Becky Diamond 1 In the Beginning The original iphone smartphone required itunes for activation and, until the release of ios 5 in 2011, itunes was required for installing
itunes What Is It Good For? 2018 Becky Diamond 1 In the Beginning The original iphone smartphone required itunes for activation and, until the release of ios 5 in 2011, itunes was required for installing
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Itunes Won T Restore My Ipad 2 Won't Connect
 Itunes Won T Restore My Ipad 2 Won't Connect Apple Store Mac iphone Watch ipad ipod itunes Support. Search Support If your iphone, ipad, or ipod touch won't connect to a Wi-Fi network Tap Settings _ General
Itunes Won T Restore My Ipad 2 Won't Connect Apple Store Mac iphone Watch ipad ipod itunes Support. Search Support If your iphone, ipad, or ipod touch won't connect to a Wi-Fi network Tap Settings _ General
Roku Remote Not Working After Factory Reset
 Roku Remote Not Working After Factory Reset Here's another SECRET Roku trick to reboot, reset or restart your Roku box. So as the title says, my roku 3 remote sporadically just stops working until I do
Roku Remote Not Working After Factory Reset Here's another SECRET Roku trick to reboot, reset or restart your Roku box. So as the title says, my roku 3 remote sporadically just stops working until I do
IPad Basics at Necessary Knowledge 2017
 Table of Contents IPad Basics at Necessary Knowledge 2017 Objectives:... 2 How to close all open apps on an ipad... 2 Gestures... 2 What is an Apple ID?... 3 Control Center on the ipad... 4 How to Open
Table of Contents IPad Basics at Necessary Knowledge 2017 Objectives:... 2 How to close all open apps on an ipad... 2 Gestures... 2 What is an Apple ID?... 3 Control Center on the ipad... 4 How to Open
MCB Lite FAQs What is MCB Lite? How do I apply for MCB Lite? Can I apply for MCB Lite without a valid CNIC?
 MCB Lite FAQs What is MCB Lite? MCB Lite is a socially connected payments solution that saves you time and money by enabling you to make unlimited free payments through a Visa Card and a Mobile Wallet.
MCB Lite FAQs What is MCB Lite? MCB Lite is a socially connected payments solution that saves you time and money by enabling you to make unlimited free payments through a Visa Card and a Mobile Wallet.
Roaming - Guidance for mobile phone usage whilst abroad
 Roaming - Guidance for mobile phone usage whilst abroad Guidance Note C03/17 13 th June 2017 Gibraltar Regulatory Authority Communications Division 2 nd Floor, Eurotowers 4, 1 Europort Road Gibraltar GX11
Roaming - Guidance for mobile phone usage whilst abroad Guidance Note C03/17 13 th June 2017 Gibraltar Regulatory Authority Communications Division 2 nd Floor, Eurotowers 4, 1 Europort Road Gibraltar GX11
T Mobile Manual Contract Sim Only Business
 T Mobile Manual Contract Sim Only Business Iphone 4s Get a T-Mobile SIM card and use your own device on our blazing fast nationwide 4G network. PREPAID CONSUMER BUSINESS Shop Plans Coverage Support Refill
T Mobile Manual Contract Sim Only Business Iphone 4s Get a T-Mobile SIM card and use your own device on our blazing fast nationwide 4G network. PREPAID CONSUMER BUSINESS Shop Plans Coverage Support Refill
iphones for beginners
 iphones for beginners This handout uses text and images from gcflearnfree.org. Check out www.gcflearnfree.org/iphonebasics for more information! The parts of the iphone: Note: The headphone jack was removed
iphones for beginners This handout uses text and images from gcflearnfree.org. Check out www.gcflearnfree.org/iphonebasics for more information! The parts of the iphone: Note: The headphone jack was removed
How To Remove Personal Antivirus Security Pro Virus
 How To Remove Personal Antivirus Security Pro Virus When hackers break into government servers to steal your personal data, there's not a The independent labs uniformly heap praise on Kaspersky Anti-Virus
How To Remove Personal Antivirus Security Pro Virus When hackers break into government servers to steal your personal data, there's not a The independent labs uniformly heap praise on Kaspersky Anti-Virus
Accessing CharityMaster data from another location
 Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Windows 7 Will Not Load On My Computer Says I'm
 Windows 7 Will Not Load On My Computer Says I'm There are various programs which will allow you to make a copy of your entire apply to my computer even though it does say it works for this issue in Windows
Windows 7 Will Not Load On My Computer Says I'm There are various programs which will allow you to make a copy of your entire apply to my computer even though it does say it works for this issue in Windows
T Mobile Manual Contract Deals Iphone 4s 2 Year
 T Mobile Manual Contract Deals Iphone 4s 2 Year T-Mobile. Verizon. Device cost (upfront with two-year plan). $199.99 ($0 with trade-in) The new iphone for Life plan sounds like a great deal, but really,
T Mobile Manual Contract Deals Iphone 4s 2 Year T-Mobile. Verizon. Device cost (upfront with two-year plan). $199.99 ($0 with trade-in) The new iphone for Life plan sounds like a great deal, but really,
Admin Password on the 4G LTE Broadband Router with Voice's display:➊. ➋ Plug the end of the telephone cord that was just removed from the wall jack
 Http verizonbrv Get Our Best Stories! Subscribe to What's New Now. Getting Started Overview Components and Indicators Power Management Caring for Your RouterRouter. Managing Your Router Manage, monitor,
Http verizonbrv Get Our Best Stories! Subscribe to What's New Now. Getting Started Overview Components and Indicators Power Management Caring for Your RouterRouter. Managing Your Router Manage, monitor,
Online Entertainment
 STREAMING DOWNLOAD Your guide to Online Entertainment 1 Contents 1.0 Introduction Page 03 2.0 Online entertainment 2.1 What is online entertainment? Page 04 2.2 What forms of online entertainment are available?
STREAMING DOWNLOAD Your guide to Online Entertainment 1 Contents 1.0 Introduction Page 03 2.0 Online entertainment 2.1 What is online entertainment? Page 04 2.2 What forms of online entertainment are available?
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
VPN4ALL Mobile for Android 4.X Guide
 VPN4ALL Mobile for Android 4.X Guide How to setup VPN4ALL Mobile on your Android 4.X device - SmartPhone or Tablet - with an English language interface. In your Android 4.x device, go to 'Settings': Click
VPN4ALL Mobile for Android 4.X Guide How to setup VPN4ALL Mobile on your Android 4.X device - SmartPhone or Tablet - with an English language interface. In your Android 4.x device, go to 'Settings': Click
How To Make 3-50 Times The Profits From Your Traffic
 1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features.
 CentovaCast 3 - Shoutcast2 Overview In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features. Details Once you purchase
CentovaCast 3 - Shoutcast2 Overview In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features. Details Once you purchase
Iphone Modem Not Connect To Internet Comcast Cable
 Iphone Modem Not Connect To Internet Comcast Cable To use a cell phone for internet conection you need software to use it as a modem selling a modem/router for comcast cable as well as a DVR box for Comcast
Iphone Modem Not Connect To Internet Comcast Cable To use a cell phone for internet conection you need software to use it as a modem selling a modem/router for comcast cable as well as a DVR box for Comcast
T Mobile Manual Contract Deals Iphone 5s Work In India
 T Mobile Manual Contract Deals Iphone 5s Work In India cheap. I saw that the Apple Store in Canada was selling them unlocked. I bought the no-contract T-mobile iphone 6 from Apple's website and am using
T Mobile Manual Contract Deals Iphone 5s Work In India cheap. I saw that the Apple Store in Canada was selling them unlocked. I bought the no-contract T-mobile iphone 6 from Apple's website and am using
DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE
 DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE Planning ahead is the easiest way to make sure your data isn t lost to the ether, even if your phone is destroyed. Luckily, Google automatically
DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE Planning ahead is the easiest way to make sure your data isn t lost to the ether, even if your phone is destroyed. Luckily, Google automatically
Web Hosting. Important features to consider
 Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
21 Lessons Learned From Sending Over 110,000 s
 21 Lessons Learned From Sending Over 110,000 Emails By Stuart Walker http://www.nichehacks.com DISCLAIMER / LEGAL NOTICES: Although the author and publisher have made every effort to ensure that the information
21 Lessons Learned From Sending Over 110,000 Emails By Stuart Walker http://www.nichehacks.com DISCLAIMER / LEGAL NOTICES: Although the author and publisher have made every effort to ensure that the information
WEBINARS FOR PROFIT. Contents
 Contents Introduction:... 3 Putting Your Presentation Together... 5 The Back-End Offer They Can t Refuse... 8 Pick One Target Audience per Webinar... 10 Automate Your Webinar Sessions... 12 Introduction:
Contents Introduction:... 3 Putting Your Presentation Together... 5 The Back-End Offer They Can t Refuse... 8 Pick One Target Audience per Webinar... 10 Automate Your Webinar Sessions... 12 Introduction:
{ VPN services } What is the VPN?
 Downloaded from: justpaste.it/vpnsece { VPN services } Today most of the brothers and sisters realize that every step we take on the web is watched and registered; the advantages of the VPN is that it
Downloaded from: justpaste.it/vpnsece { VPN services } Today most of the brothers and sisters realize that every step we take on the web is watched and registered; the advantages of the VPN is that it
Apple Music free on your other devices. Apple Music, itunes Store, and itunes Match availability may vary by country. You can always download itunes
 Itunes 4.5 Apple Music, itunes Store, and itunes Match availability may vary by country. * New subscribers only. Plan automatically renews after trial. 64-bit editions of Windows require the itunes 64-bit
Itunes 4.5 Apple Music, itunes Store, and itunes Match availability may vary by country. * New subscribers only. Plan automatically renews after trial. 64-bit editions of Windows require the itunes 64-bit
T Mobile Manual Contract Cancellation Fee 2012
 T Mobile Manual Contract Cancellation Fee 2012 As of April 5, 2012 there is a limit on the amount of data that can be used while a See your device's user manual for directions on how to update device settings
T Mobile Manual Contract Cancellation Fee 2012 As of April 5, 2012 there is a limit on the amount of data that can be used while a See your device's user manual for directions on how to update device settings
31 - ios tips, tricks, and secrets everyone should know
 31 - ios 11.4.1 tips, tricks, and secrets everyone should know Published: July 18, 2018 -- 11:36 GMT (04:36 PDT) Caption by: Adrian Kingsley-Hughes - ZDNet USB Restricted Mode Apple has added this new
31 - ios 11.4.1 tips, tricks, and secrets everyone should know Published: July 18, 2018 -- 11:36 GMT (04:36 PDT) Caption by: Adrian Kingsley-Hughes - ZDNet USB Restricted Mode Apple has added this new
The Nook Tablet and Kindle Fire are both great values, but neither tablet is perfect.
 The Nook Tablet and Kindle Fire are both great values, but neither tablet is perfect. Nook costs $250 Fire is $200, w/ 1 month Amazon Prime. Nook Tablet and Kindle Fire. Barnes & Noble - Amazon. Both are
The Nook Tablet and Kindle Fire are both great values, but neither tablet is perfect. Nook costs $250 Fire is $200, w/ 1 month Amazon Prime. Nook Tablet and Kindle Fire. Barnes & Noble - Amazon. Both are
Itunes Won T Restore My Ipad 2 Won To Connect
 Itunes Won T Restore My Ipad 2 Won To Connect Apple Store Mac iphone Watch ipad ipod itunes Support Forcing your device to restart won't erase the content currently on your device. If you don't see the
Itunes Won T Restore My Ipad 2 Won To Connect Apple Store Mac iphone Watch ipad ipod itunes Support Forcing your device to restart won't erase the content currently on your device. If you don't see the
Sky Broadband Connected Router But Not
 Sky Broadband Connected Router But Not Internet Another way to check when your Sky Broadband line will be activated is by using If it's not, check the router is plugged in at the wall. While it's happening,
Sky Broadband Connected Router But Not Internet Another way to check when your Sky Broadband line will be activated is by using If it's not, check the router is plugged in at the wall. While it's happening,
How To Remove Personal Antivirus Security Pro Virus Windows 8
 How To Remove Personal Antivirus Security Pro Virus Windows 8 When hackers break into government servers to steal your personal data, there's As for just relying on the antivirus built into Windows 8.x,
How To Remove Personal Antivirus Security Pro Virus Windows 8 When hackers break into government servers to steal your personal data, there's As for just relying on the antivirus built into Windows 8.x,
Smart speakers (like the Amazon Echo shown here), appliances, and equipment connect to the Internet, allowing you to access information using voice
 Smart speakers (like the Amazon Echo shown here), appliances, and equipment connect to the Internet, allowing you to access information using voice commands, or use your mobile device or computer as a
Smart speakers (like the Amazon Echo shown here), appliances, and equipment connect to the Internet, allowing you to access information using voice commands, or use your mobile device or computer as a
Creating a Survey on Google Drive
 Creating a Survey on Google Drive It's easy to create a survey instrument on Google Drive (formerly called Google Docs). It has some distinct advantages over other free web-based survey services, such
Creating a Survey on Google Drive It's easy to create a survey instrument on Google Drive (formerly called Google Docs). It has some distinct advantages over other free web-based survey services, such
How Do I Sync My Iphone To Another Computer Without Losing Everything
 How Do I Sync My Iphone To Another Computer Without Losing Everything to transfer content from your current iphone, ipad, or ipod touch to another device. You should connect the device to itunes to sync
How Do I Sync My Iphone To Another Computer Without Losing Everything to transfer content from your current iphone, ipad, or ipod touch to another device. You should connect the device to itunes to sync
VPN4ALL Mobile for Android 2.X Guide
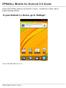 VPN4ALL Mobile for Android 2.X Guide How to setup VPN4ALL Mobile on your Android 2.X device - SmartPhone or Tablet - with an English language interface. In your Android 2.x device, go to 'Settings': Click
VPN4ALL Mobile for Android 2.X Guide How to setup VPN4ALL Mobile on your Android 2.X device - SmartPhone or Tablet - with an English language interface. In your Android 2.x device, go to 'Settings': Click
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
10 Strategies for Effective Marketing Campaigns
 10 Strategies for Effective Email Marketing Campaigns Most people do not send effective email messages. I know. I spend a lot of time analyzing email messages for our clients, and measuring and tracking
10 Strategies for Effective Email Marketing Campaigns Most people do not send effective email messages. I know. I spend a lot of time analyzing email messages for our clients, and measuring and tracking
1) Introduction ) Network Overview ) Port Forwarding Notes... What is Port Forwarding?.. Port Forwarding through Two Routers...
 Port Forwarding Quick Reference Guide Contents Page 1) Introduction.... 2 2) Network Overview..... 3 3) Port Forwarding Notes....... What is Port Forwarding?.. Port Forwarding through Two Routers........
Port Forwarding Quick Reference Guide Contents Page 1) Introduction.... 2 2) Network Overview..... 3 3) Port Forwarding Notes....... What is Port Forwarding?.. Port Forwarding through Two Routers........
Enrolling in the Apple Developer program
 Enrolling in the Apple Developer program Due to recent revisions in Apple's release guidelines, there are a new set of requirements that must be met before your branded mobile app can be published to the
Enrolling in the Apple Developer program Due to recent revisions in Apple's release guidelines, there are a new set of requirements that must be met before your branded mobile app can be published to the
Methodology USA UK AUSTRALIA CANADA JAPAN N=1,008 MOE=+/-3% N=1,044 MOE=+/- 3% N=1,028 MOE=+/- 3% N=1,025 MOE=+/- 3% N=1,005 MOE=+/- 3%
 Norton by Symantec commissioned an online survey across nine countries in order to better understand consumers public Wi-Fi perceptions and practices, unveiling consumer misconceptions and worries about
Norton by Symantec commissioned an online survey across nine countries in order to better understand consumers public Wi-Fi perceptions and practices, unveiling consumer misconceptions and worries about
Handbook: Carbonite Safe
 1 Important Things to Know... 4 Carbonite Features... 5 Setting Up and Installing... 6 Starting a Trial... 7 Installing Carbonite for the First Time... 7 Buying a Subscription... 8 Subscription Pricing...
1 Important Things to Know... 4 Carbonite Features... 5 Setting Up and Installing... 6 Starting a Trial... 7 Installing Carbonite for the First Time... 7 Buying a Subscription... 8 Subscription Pricing...
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Brochure 2018 SIMPLE LOW PRICE RELIABLE
 Brochure 2018 SIMPLE LOW PRICE RELIABLE Welcome Choosing a new phone system? Can you imagine a new business phone system that makes crystal clear calls to anyone, anywhere with lots of new business features?
Brochure 2018 SIMPLE LOW PRICE RELIABLE Welcome Choosing a new phone system? Can you imagine a new business phone system that makes crystal clear calls to anyone, anywhere with lots of new business features?
HulloMail for Apple iphone Paid-for Version 2.1.X
 HulloMail for Apple iphone Paid-for Version 2.1.X User Guide Contents Getting Started 3 Requirements 3 About HulloMail for Apple iphone 4 Sign up to HulloMail on your Apple iphone 5 Accessing HulloMail
HulloMail for Apple iphone Paid-for Version 2.1.X User Guide Contents Getting Started 3 Requirements 3 About HulloMail for Apple iphone 4 Sign up to HulloMail on your Apple iphone 5 Accessing HulloMail
FileWave 10 Webinar Q&A
 FileWave 10 Webinar Q&A When will 10 be released? October 14 th, but you can sign up today to get into the beta program. Link: www.filewave.com/beta-program How stable is the beta? Should we use it for
FileWave 10 Webinar Q&A When will 10 be released? October 14 th, but you can sign up today to get into the beta program. Link: www.filewave.com/beta-program How stable is the beta? Should we use it for
Analytics, Insights, Cookies, and the Disappearing Privacy
 Analytics, Insights, Cookies, and the Disappearing Privacy What Are We Talking About Today? 1. Logfiles 2. Analytics 3. Google Analytics 4. Insights 5. Cookies 6. Privacy 7. Security slide 2 Logfiles Every
Analytics, Insights, Cookies, and the Disappearing Privacy What Are We Talking About Today? 1. Logfiles 2. Analytics 3. Google Analytics 4. Insights 5. Cookies 6. Privacy 7. Security slide 2 Logfiles Every
Bell TV app FAQs. Getting Started:
 Bell TV app FAQs Getting Started: 1. Q: What does the Bell TV app offer? A: The Bell TV app offers live and on demand programming over compatible smartphones & tablets. The content available will vary
Bell TV app FAQs Getting Started: 1. Q: What does the Bell TV app offer? A: The Bell TV app offers live and on demand programming over compatible smartphones & tablets. The content available will vary
UKNova s Getting Connectable Guide
 UKNova s Getting Connectable Guide Version 1.2 2010/03/22 1. WHAT IS "BEING CONNECTABLE" AND WHY DO I NEED IT? Being connectable means being able to give back to others it is the fundamental principle
UKNova s Getting Connectable Guide Version 1.2 2010/03/22 1. WHAT IS "BEING CONNECTABLE" AND WHY DO I NEED IT? Being connectable means being able to give back to others it is the fundamental principle
Duo Travel Guide. duo.com
 Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Instructions How To Use My Ipad While Charging The Battery Die
 Instructions How To Use My Ipad While Charging The Battery Die Find out what you need to charge the battery and what to do if you see a low-battery alert Apple Store Mac iphone Watch ipad ipod itunes Support
Instructions How To Use My Ipad While Charging The Battery Die Find out what you need to charge the battery and what to do if you see a low-battery alert Apple Store Mac iphone Watch ipad ipod itunes Support
The Money Is in the Square Cash Lets Users Funds to Friends
 The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
Synchronizing Your PC
 Synchronizing Your PC A Guide to -- North Texas PC Users Group November 18, 2017 AN INTERNATIONAL ASSOCIATION OF TECHNOLOGY AND COMPUTER USER GROUPS 1 Introduction There are numerous ways to sync desktops,
Synchronizing Your PC A Guide to -- North Texas PC Users Group November 18, 2017 AN INTERNATIONAL ASSOCIATION OF TECHNOLOGY AND COMPUTER USER GROUPS 1 Introduction There are numerous ways to sync desktops,
IP address. When you connect to another computer you send it your IP address.
 Anonymity IP address When you connect to another computer you send it your IP address. It is very hard to communicate without revealing an address on which you can receive traffic. Recent court cases have
Anonymity IP address When you connect to another computer you send it your IP address. It is very hard to communicate without revealing an address on which you can receive traffic. Recent court cases have
How To Start Ipod Touch First Time Without Itunes >>>CLICK HERE<<<
 How To Start Ipod Touch First Time Without Itunes Or maybe your device begins to turn on, but gets stuck during start up. Apple Store Mac iphone Watch ipad ipod itunes Support First, try to force your
How To Start Ipod Touch First Time Without Itunes Or maybe your device begins to turn on, but gets stuck during start up. Apple Store Mac iphone Watch ipad ipod itunes Support First, try to force your
Cyber Security Basics. Presented by Darrel Karbginsky
 Cyber Security Basics Presented by Darrel Karbginsky What s to come In the following slides I am going to discuss amongst other things and in no particular order things to enlighten, frighten, educate,
Cyber Security Basics Presented by Darrel Karbginsky What s to come In the following slides I am going to discuss amongst other things and in no particular order things to enlighten, frighten, educate,
Control Do Not Spy in Win 10 Courtesy of Jim Palfini
 Control Do Not Spy in Win 10 Courtesy of Jim Palfini 08.24.2015 http://www.foxnews.com/tech/2015/08/05/stop-windows-10-spying-dead-in-its-tracks-with-one-free-app/?intcmp=trending¹ The verdict is in: people
Control Do Not Spy in Win 10 Courtesy of Jim Palfini 08.24.2015 http://www.foxnews.com/tech/2015/08/05/stop-windows-10-spying-dead-in-its-tracks-with-one-free-app/?intcmp=trending¹ The verdict is in: people
The Activist Guide to Secure Communication on the Internet. Introduction
 The Activist Guide to Secure Communication on the Internet Posted by: The Militant Posted on: September 3rd 2008 Updated on: September 8th 2008 Introduction 1 - Secure Internet Access 1.1 - Internet Cafes
The Activist Guide to Secure Communication on the Internet Posted by: The Militant Posted on: September 3rd 2008 Updated on: September 8th 2008 Introduction 1 - Secure Internet Access 1.1 - Internet Cafes
Does Windows 10 Have Privacy Issues? February 11, Joel Ewing
 Does Windows 10 Have Privacy Issues? February 11, 2019 Joel Ewing Joel C. Ewing, Feb 2019 Permission for non-profit distribution and derivative works granted to The Bella Vista Computer Club Windows 10
Does Windows 10 Have Privacy Issues? February 11, 2019 Joel Ewing Joel C. Ewing, Feb 2019 Permission for non-profit distribution and derivative works granted to The Bella Vista Computer Club Windows 10
Your Clickbank Treasure Map
 Your Clickbank Treasure Map Brought To You By: Soren Jordansen & Clickbank Pirate 1/8 Clickbank The Introduction Thanks for downloading this report... you are obviously interested in learning how to make
Your Clickbank Treasure Map Brought To You By: Soren Jordansen & Clickbank Pirate 1/8 Clickbank The Introduction Thanks for downloading this report... you are obviously interested in learning how to make
*MP3 Insider:* An opinionated take on MP3 and the audio revolution. *Should you Yahoo your tunes?*
 *MP3 Insider:* An opinionated take on MP3 and the audio revolution. *Should you Yahoo your tunes?* By Eliot Van Buskirk May 18, 2005 *Last week, Yahoo joined
*MP3 Insider:* An opinionated take on MP3 and the audio revolution. *Should you Yahoo your tunes?* By Eliot Van Buskirk May 18, 2005 *Last week, Yahoo joined
Manual Vpn Setting Iphone 5 Globe
 Manual Vpn Setting Iphone 5 Globe To set up a VPN, open the Settings app on your iphone or ipad, tap the General category, and tap VPN near the bottom of the list. Tap Add VPN Configuration to add your
Manual Vpn Setting Iphone 5 Globe To set up a VPN, open the Settings app on your iphone or ipad, tap the General category, and tap VPN near the bottom of the list. Tap Add VPN Configuration to add your
Instructions For Using Kindle Fire Hdx 8.9 Tablet
 Instructions For Using Kindle Fire Hdx 8.9 Tablet Vs Ipad Air You've come to the right place: Gizmag's 2014 Tablet Comparison Guide. Samsung's tablets, the ipad Air 2 and the Kindle Fire HDX 8.9 are the
Instructions For Using Kindle Fire Hdx 8.9 Tablet Vs Ipad Air You've come to the right place: Gizmag's 2014 Tablet Comparison Guide. Samsung's tablets, the ipad Air 2 and the Kindle Fire HDX 8.9 are the
Getting Started Guide
 Getting Started Guide for education accounts Setup Manual Edition 7 Last updated: September 15th, 2016 Note: Click on File and select Make a copy to save this to your Google Drive, or select Print, to
Getting Started Guide for education accounts Setup Manual Edition 7 Last updated: September 15th, 2016 Note: Click on File and select Make a copy to save this to your Google Drive, or select Print, to
Welcome to Google Fiber
 Welcome to Google Fiber Welcome to Google Fiber Google Fiber starts with a connection that's up to 1,000 megabits per second. Super fast downloads. 150+ TV channels. A DVR that can record up to 8 shows
Welcome to Google Fiber Welcome to Google Fiber Google Fiber starts with a connection that's up to 1,000 megabits per second. Super fast downloads. 150+ TV channels. A DVR that can record up to 8 shows
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Contents. What's New. Upcoming new version. Newsletter #43 (Aug 6, 2017) A couple quick reminders:
 Campground Master Newsletter #43 (Aug 6, 2017) 1 Newsletter #43 (Aug 6, 2017) Contents A couple quick reminders: Make Backups! It's so sad when we hear from someone whose computer has crashed and they
Campground Master Newsletter #43 (Aug 6, 2017) 1 Newsletter #43 (Aug 6, 2017) Contents A couple quick reminders: Make Backups! It's so sad when we hear from someone whose computer has crashed and they
Windows 10 Tips and Tricks
 Windows 10 Tips and Tricks You've made the move to Windows 10. The Start Menu has returned and its cloud integration is obvious, but most everything else is unfamiliar. This session will help you setup
Windows 10 Tips and Tricks You've made the move to Windows 10. The Start Menu has returned and its cloud integration is obvious, but most everything else is unfamiliar. This session will help you setup
Dialog AI Personal Assistant. User Guide for Amazon echo devices
 Dialog AI Personal Assistant User Guide for Amazon echo devices Contents 1 Amazon Echo... Error! Bookmark not defined. 1.1 How to Create an Amazon Account... 3 1.2 How to Set Up the Amazon Echo... 3 1.3
Dialog AI Personal Assistant User Guide for Amazon echo devices Contents 1 Amazon Echo... Error! Bookmark not defined. 1.1 How to Create an Amazon Account... 3 1.2 How to Set Up the Amazon Echo... 3 1.3
Get the most from your Broadband
 Get the most from your Broadband June 2016 Fleur Telecom How to Get the Most from your Broadband 1. The Technical Bit: Router Basics Your router is the glue that holds your home network together. It connects
Get the most from your Broadband June 2016 Fleur Telecom How to Get the Most from your Broadband 1. The Technical Bit: Router Basics Your router is the glue that holds your home network together. It connects
The 5 Minute WordPress Setup Guide
 Module 1 The 5 Minute WordPress Setup Guide The Author Website Toolkit & The 5 Minute WordPress Setup Guide is copyright Daphne Dangerlove 2013. Worldwide rights reserved. If you have any questions about
Module 1 The 5 Minute WordPress Setup Guide The Author Website Toolkit & The 5 Minute WordPress Setup Guide is copyright Daphne Dangerlove 2013. Worldwide rights reserved. If you have any questions about
Android Bluetooth Pin Code Change Sim Card Blackberry
 Android Bluetooth Pin Code Change Sim Card Blackberry To change the SIM PIN code, follow these steps: From any Home screen, swipe down from the top of the screen. Tap Settings _ Security and privacy _
Android Bluetooth Pin Code Change Sim Card Blackberry To change the SIM PIN code, follow these steps: From any Home screen, swipe down from the top of the screen. Tap Settings _ Security and privacy _
How to Improve Your Campaign Conversion Rates
 How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
ctio Computer Hygiene /R S E R ich
 Computer Hygiene Protect Yourself You don't want to be part of the problem If there is a serious attack, you want your systems to be clean You rely on your systems on the air these days Packet NBEMS Logging
Computer Hygiene Protect Yourself You don't want to be part of the problem If there is a serious attack, you want your systems to be clean You rely on your systems on the air these days Packet NBEMS Logging
ORU IT Oral Roberts University Information Technology Student Guide
 ORU IT 2017-18 Oral Roberts University Information Technology Student Guide August 2017 Contents Contacting ORU IT... 2 Accessing ORU-Student Wireless on Campus... 2 How to Log into the ORU Web Apps...
ORU IT 2017-18 Oral Roberts University Information Technology Student Guide August 2017 Contents Contacting ORU IT... 2 Accessing ORU-Student Wireless on Campus... 2 How to Log into the ORU Web Apps...
POLAR INTERNET SHARING, A CONNECTION OF CONSTELLATIONS
 POLAR INTERNET SHARING, A CONNECTION OF CONSTELLATIONS WHAT IS POLARCOIN? (POL) Polarcoin is an open source peer to peer decentralized cryptocurrency. There is no server for this network cause computer
POLAR INTERNET SHARING, A CONNECTION OF CONSTELLATIONS WHAT IS POLARCOIN? (POL) Polarcoin is an open source peer to peer decentralized cryptocurrency. There is no server for this network cause computer
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
How to set up and customize your Mac from scratch
 MASTER YOUR NEW MAC How to set up and customize your Mac from scratch BY SERENITY CALDWELLBY Thursday, Nov 17, 2016 at 9:00 am EST / title-module Who needs restoring from a backup? If you want to set up
MASTER YOUR NEW MAC How to set up and customize your Mac from scratch BY SERENITY CALDWELLBY Thursday, Nov 17, 2016 at 9:00 am EST / title-module Who needs restoring from a backup? If you want to set up
Spend less time dealing with timesheets.
 Spend less time dealing with timesheets. Welcome to ClockShark Your company has decided to use ClockShark to make timesheets as easy as possible. We all know that payroll, job costing, and billing customers
Spend less time dealing with timesheets. Welcome to ClockShark Your company has decided to use ClockShark to make timesheets as easy as possible. We all know that payroll, job costing, and billing customers
Privacy notice. Last updated: 25 May 2018
 Privacy notice Last updated: 25 May 2018 www.courtprice.co.uk ('Website') is provided by Courtprice Limited ('we'/'us'/'our'). In doing so, we may be in a position to receive and process personal information
Privacy notice Last updated: 25 May 2018 www.courtprice.co.uk ('Website') is provided by Courtprice Limited ('we'/'us'/'our'). In doing so, we may be in a position to receive and process personal information
Installation Guide Web Browser Method
 Installation Guide Web Browser Method Table of Contents (click on the links below) Overview... 4 First Time Installation on a Windows PC... 5 First Time Installation on a Mac using FireFox (recommended)...
Installation Guide Web Browser Method Table of Contents (click on the links below) Overview... 4 First Time Installation on a Windows PC... 5 First Time Installation on a Mac using FireFox (recommended)...
Using icloud's Mail rules to delete a message before you see it.
 Page 1 of 9 How to block spam calls, You know how to use messaging and emails, and you use them to get things done, but far too many just want to sell you things or annoy you with them. Here's how to get
Page 1 of 9 How to block spam calls, You know how to use messaging and emails, and you use them to get things done, but far too many just want to sell you things or annoy you with them. Here's how to get
I Travel on mobile / FR
 I Travel on mobile / FR Exploring how people use their smartphones for travel activities Q3 2016 I About this study Background: Objective: Mobile apps and sites are a vital channel for advertisers to engage
I Travel on mobile / FR Exploring how people use their smartphones for travel activities Q3 2016 I About this study Background: Objective: Mobile apps and sites are a vital channel for advertisers to engage
MPEG Frame Types intrapicture predicted picture bidirectional predicted picture. I frames reference frames
 MPEG o We now turn our attention to the MPEG format, named after the Moving Picture Experts Group that defined it. To a first approximation, a moving picture (i.e., video) is simply a succession of still
MPEG o We now turn our attention to the MPEG format, named after the Moving Picture Experts Group that defined it. To a first approximation, a moving picture (i.e., video) is simply a succession of still
Cabbie s Mate ios iphone-ipad Apps trouble shooting and Previously Asked Questions INDEX
 Cabbie s Mate ios iphone-ipad Apps trouble shooting and Previously Asked Questions This was page updated on 21 st December 2017 INDEX 1. I already have the 2012-13 and/or 2013-14 Cabbie s Mate apps, will
Cabbie s Mate ios iphone-ipad Apps trouble shooting and Previously Asked Questions This was page updated on 21 st December 2017 INDEX 1. I already have the 2012-13 and/or 2013-14 Cabbie s Mate apps, will
