CTF. I-Bank. Logical Flaws in a PHP banking application. FluxReiners
|
|
|
- Asher Maxwell
- 6 years ago
- Views:
Transcription
1 Logical Flaws in a PHP banking application FluxReiners
2 Final CTF phase: Exploitation 2/38
3 Setup: one bank per team with the same banking app 3 bank accounts per bank SSH access to own bank server (incl. PHP src) 4 donation accounts: Anonymous LulzSec Offshore of Potato Fund for French Fries Welfare 3/38
4 Goal: Protect own bank accounts (patch Logical Flaws) Own other bank accounts and transfer money to the donation accounts from them Timeline (theoretically): 4h create patches/exploits 1h orga check Penalty points for defects 1h attack phase 4/38
5 application 5/38
6 mysql> select * from users; id login password... recovery_password user_type otp_type N basic smart_token Ib5frg... Y contractor card gJgff... N contractor no mysql> select * from accounts; id user_id number sum /38
7 Preparation: Captcha Breaking 7/38
8 8/38
9 <img src="image.php?code=pufet3pxre4="> login=&password=&code=48380&_code=pufet3pxre4= Copy/paste to exploits Automatic login 9/38
10 User Enumeration 10/38
11 Attack 1: Weak Password Recovery Key 11/38
12 mysql> select * from users; id login password... recovery_password user_type otp_type N basic smart_token Ib5frg... Y contractor card gJgff... N contractor no mysql> select * from recovery; Empty set (0.10 sec) 12/38
13 Request reset key: user = $_POST["login"] Check, if recovery_password = 'Y' Check, if no reset key already requested (DB) Mail reset key to user insert into recovery (login, key) 13/38
14 mysql> select * from recovery; login key de01d74a564f45c7189a5e6c251bf36c /38
15 Insert reset key user = $_POST["login"], key = $_POST["key"] Check, if user+key combination in recovery table generate new password and change password for user Print new password 7 chars 15/38
16 mysql> select * from recovery; login key de01d74a564f45c7189a5e6c251bf36c $key = md5( $login. rand(1, 250) ); 16/38
17 mysql> select * from users; id login password... recovery_password user_type otp_type N basic smart_token Ib5frg... Y contractor card gJgff... N contractor no /38
18 Supplied OTP is checked against the database (status = clear used) OTP statically generated for known user id 18/38
19 Attack 2: Weak Session Token 19/38
20 mysql> select * from users; id login password... recovery_password user_type otp_type N basic smart_token Ib5frg... Y contractor card gJgff... N contractor no mysql> select * from sessions; user_id salt expire y82lr ju6t rows in set (0.00 sec) 20/38
21 salt contains 5 random alphanumerical chars [a-z0-9] 21/38
22 numerical CRC32 checksum of length 10 Is shortened to length 4 22/38
23 Less than 10 4 = possibilities 23/38
24 Cookie: auth= Bruteforce Transactions can be done without OTP check (otp_type=no) 24/38
25 Attack 3: Weak Passwords + Helpdesk Authentication Bypass 25/38
26 mysql> select * from users; id login password... recovery_password user_type otp_type N basic smart_token Ib5frg... Y contractor card gJgff... N contractor no mysql> select * from accounts; id user_id number sum /38
27 Helpdesk 27/38
28 mysql> select * from helpdesk_users; Empty set (0.00 sec) mysql> insert into helpdesk_users values( 0, 'admin', sha1('foobar'), 'admin@ibank.ru', 'foo', 'bar'); Query OK, 1 row affected (0.04 sec) mysql> select * from helpdesk_users; id login password first_name last_name admin 356a19... admin@bank.ru foo bar row in set (0.00 sec) 28/38
29 29/38
30 30/38
31 Todo: OTP Bypass 31/38
32 numerical random OTP of length 5, 10 5 = , bruteforce 32/38
33 Transfer- Formular Account- Check OTP- Check Transaction Jump from step2 to step4, bypass OTP check in step3 (also works for TransactionB of user , otp_type=card) 33/38
34 Summary 34/38
35 login User properties password recovery user type otp type weak passwd password recovery attacks weak session otp bypass N basic smart x x Y contractor card x x x x N contractor no x x - 35/38
36 login User properties password recovery user type otp type weak passwd password recovery attacks weak session otp bypass N basic smart Y contractor card - 3/12-3/ N contractor no - 0/12 PPP (4.) Tachikoma (9.) 0daysober (2.) 36/38
37 Timeline (practically): Organizers are going to attack However we found no foreign attacks in our logs 20 RUB / account, RUB / bank Account reset after 15min (new money) Attack phase ended after 30min FluxFingers was the only team stealing money however 40 / = negl No attack points for us, no minus points for others =( 37/38
38 Thank you for your attention Thank you GDATA for making our trip to Moscow possible 38/38
How to Integrate. REVE Secure 2FA App. with Dashboard.
 How to Integrate REVE Secure 2FA App with Dashboard REVE Secure Software Token supports widely deployed mobile platforms like ios, Android, Windows, etc. and uses time-based algorithm to support 2FA. This
How to Integrate REVE Secure 2FA App with Dashboard REVE Secure Software Token supports widely deployed mobile platforms like ios, Android, Windows, etc. and uses time-based algorithm to support 2FA. This
CN Assignment I. 1. With an example explain how cookies are used in e-commerce application to improve the performance.
 CN Assignment I 1. With an example explain how cookies are used in e-commerce application to improve the performance. In an e-commerce application, when the user sends a login form to the server, the server
CN Assignment I 1. With an example explain how cookies are used in e-commerce application to improve the performance. In an e-commerce application, when the user sends a login form to the server, the server
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
Application vulnerabilities and defences
 Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Advanced Web Technology 10) XSS, CSRF and SQL Injection
 Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 1 Table of Contents Cross Site Request Forgery - CSRF Presentation
Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 1 Table of Contents Cross Site Request Forgery - CSRF Presentation
Guide to your CGIAR Network account Self Service tool
 Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Why bother? Causes of data breaches OWASP. Top ten attacks. Now what? Do it yourself Questions?
 Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
Tale of a mobile application ruining the security of global solution because of a broken API design. SIGS Geneva 21/09/2016 Jérémy MATOS
 Tale of a mobile application ruining the security of global solution because of a broken API design SIGS Geneva 21/09/2016 Jérémy MATOS whois securingapps Developer background Spent last 10 years working
Tale of a mobile application ruining the security of global solution because of a broken API design SIGS Geneva 21/09/2016 Jérémy MATOS whois securingapps Developer background Spent last 10 years working
unsuccessful attempts.
 Step by Step Procedure for Resetting Transaction Password by the User. when the user has been disabled after 3 unsuccessful attempts. The following module helps the Customers in Resetting Transaction password
Step by Step Procedure for Resetting Transaction Password by the User. when the user has been disabled after 3 unsuccessful attempts. The following module helps the Customers in Resetting Transaction password
TWO-FACTOR AUTHENTICATION Version 1.1.0
 TWO-FACTOR AUTHENTICATION Version 1.1.0 User Guide for Magento 1.9 Table of Contents 1..................... The MIT License 2.................... About JetRails 2FA 4................. Installing JetRails
TWO-FACTOR AUTHENTICATION Version 1.1.0 User Guide for Magento 1.9 Table of Contents 1..................... The MIT License 2.................... About JetRails 2FA 4................. Installing JetRails
CMS-i First Time Activation User Guide
 Download Soft Token Application (ios Application) Download Soft Token Application (Android Application) First Time Activation Soft Token Registration Version : 4.0 Last updated : 22 nd February 2019 alrajhicashbiz24seven
Download Soft Token Application (ios Application) Download Soft Token Application (Android Application) First Time Activation Soft Token Registration Version : 4.0 Last updated : 22 nd February 2019 alrajhicashbiz24seven
Arseniy Reutov Timur Yunusov Dmitriy Nagibin
 Arseniy Reutov Timur Yunusov Dmitriy Nagibin Timeline of PHP problems with random numbers 2008: mt_srand and not so random numbers by Stefan Esser Early 2010: Abusing weak PRNGs in PHP applications by
Arseniy Reutov Timur Yunusov Dmitriy Nagibin Timeline of PHP problems with random numbers 2008: mt_srand and not so random numbers by Stefan Esser Early 2010: Abusing weak PRNGs in PHP applications by
Breaking FIDO Yubico. Are Exploits in There?
 Breaking FIDO Are Exploits in There? FIDO U2F (Universal 2nd Factor) Analyzing FIDO U2F Attack and Countermeasures Implementation Considerations Resources 2 User Experience 1. Enter username/pwd 2. Insert
Breaking FIDO Are Exploits in There? FIDO U2F (Universal 2nd Factor) Analyzing FIDO U2F Attack and Countermeasures Implementation Considerations Resources 2 User Experience 1. Enter username/pwd 2. Insert
When providing a native mobile app ruins the security of your existing web solution. CyberSec Conference /11/2015 Jérémy MATOS
 When providing a native mobile app ruins the security of your existing web solution CyberSec Conference 2015 05/11/2015 Jérémy MATOS whois securingapps Developer background Spent last 10 years working
When providing a native mobile app ruins the security of your existing web solution CyberSec Conference 2015 05/11/2015 Jérémy MATOS whois securingapps Developer background Spent last 10 years working
Databases (MariaDB/MySQL) CS401, Fall 2015
 Databases (MariaDB/MySQL) CS401, Fall 2015 Database Basics Relational Database Method of structuring data as tables associated to each other by shared attributes. Tables (kind of like a Java class) have
Databases (MariaDB/MySQL) CS401, Fall 2015 Database Basics Relational Database Method of structuring data as tables associated to each other by shared attributes. Tables (kind of like a Java class) have
Autopopulation; Session & Cookies
 ; Session & Cookies CGT 356 Web Programming, Development, & Database Integration Lecture 5 Session array Use the Session array to store data that needs to be recalled on later pages $_SESSION[ foo ] Use
; Session & Cookies CGT 356 Web Programming, Development, & Database Integration Lecture 5 Session array Use the Session array to store data that needs to be recalled on later pages $_SESSION[ foo ] Use
Side-channel attacks (and blind SQL injections)
 Side-channel attacks (and blind SQL injections) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction It is often the case that applications have
Side-channel attacks (and blind SQL injections) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction It is often the case that applications have
CNIT 129S: Securing Web Applications. Ch 4: Mapping the Application
 CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
The Way of the Bounty. by David Sopas
 The Way of the Bounty by David Sopas (@dsopas) ./whoami Security Consultant for Checkmarx Security Team Leader for Char49 Disclosed more than 50 security advisories Founder of WebSegura.net Love to hack
The Way of the Bounty by David Sopas (@dsopas) ./whoami Security Consultant for Checkmarx Security Team Leader for Char49 Disclosed more than 50 security advisories Founder of WebSegura.net Love to hack
Attacks Against Websites 3 The OWASP Top 10. Tom Chothia Computer Security, Lecture 14
 Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
IERG 4210 Tutorial 07. Securing web page (I): login page and admin user authentication Shizhan Zhu
 IERG 4210 Tutorial 07 Securing web page (I): login page and admin user authentication Shizhan Zhu Content for today Phase 4 preview From now please pay attention to the security issue of your website This
IERG 4210 Tutorial 07 Securing web page (I): login page and admin user authentication Shizhan Zhu Content for today Phase 4 preview From now please pay attention to the security issue of your website This
Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any
 OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
Excerpts of Web Application Security focusing on Data Validation. adapted for F.I.S.T. 2004, Frankfurt
 Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM)
 Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in
 1 This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in terms of prevalence (how much the vulnerability is widespread),
1 This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in terms of prevalence (how much the vulnerability is widespread),
service code Code: 2013 Language
 service code Code: 2013 Language 1. Service menu code 1. Service menu code Control times can only be altered in the service menu. The code for this is 2013 2. Service level A range of queries can be run
service code Code: 2013 Language 1. Service menu code 1. Service menu code Control times can only be altered in the service menu. The code for this is 2013 2. Service level A range of queries can be run
Web Security, Summer Term 2012
 IIG University of Freiburg Web Security, Summer Term 2012 Web Application: Testing Security Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 10) Web Application: Testing Security 1 Table of
IIG University of Freiburg Web Security, Summer Term 2012 Web Application: Testing Security Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 10) Web Application: Testing Security 1 Table of
User Guide for CA Integration
 User Guide for CA Integration Finacle E-Banking Solution SBI Bank, India INFOSYS LTD. Bangalore, India DOCUMENT SUMMARY Project Name SBI Phase Implementation Document Name SBI CA Integration Document Description
User Guide for CA Integration Finacle E-Banking Solution SBI Bank, India INFOSYS LTD. Bangalore, India DOCUMENT SUMMARY Project Name SBI Phase Implementation Document Name SBI CA Integration Document Description
REST Admin API. Note: Version 9.X or higher is required for the support of REST API. Version /17
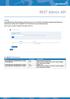 REST Admin API Setup Each application that will communicate to the SecurAccess server via the REST API interface will require authorisation as a trusted source, located under Config/REST API from the SecurEnvoy
REST Admin API Setup Each application that will communicate to the SecurAccess server via the REST API interface will require authorisation as a trusted source, located under Config/REST API from the SecurEnvoy
AUTHENTICATION. Do You Know Who You're Dealing With? How Authentication Affects Prevention, Detection, and Response
 AUTHENTICATION Do You Know Who You're Dealing With? How Authentication Affects Prevention, Detection, and Response Who we are Eric Scales Mandiant Director IR, Red Team, Strategic Services Scott Koller
AUTHENTICATION Do You Know Who You're Dealing With? How Authentication Affects Prevention, Detection, and Response Who we are Eric Scales Mandiant Director IR, Red Team, Strategic Services Scott Koller
Featuring. and. Göteborg. Ulf Larson Thursday, October 24, 13
 Featuring and Göteborg OWASP top ten 2013 Based on risk data from eight firms that specialize in application security, This data spans over 500,000 vulnerabilities across hundreds of organizations and
Featuring and Göteborg OWASP top ten 2013 Based on risk data from eight firms that specialize in application security, This data spans over 500,000 vulnerabilities across hundreds of organizations and
Why bother? Default configurations Buffer overflows Authentication mechanisms Reverse engineering Questions?
 Jeroen van Beek 1 Why bother? Default configurations Buffer overflows Authentication mechanisms Reverse engineering Questions? 2 Inadequate OS and application security: Data abuse Stolen information Bandwidth
Jeroen van Beek 1 Why bother? Default configurations Buffer overflows Authentication mechanisms Reverse engineering Questions? 2 Inadequate OS and application security: Data abuse Stolen information Bandwidth
OTP Issuance/Use Manual
 For B2B Administrators of Samsung Electronics Online Customer DB OTP Issuance/Use Manual (Windows Type) Contents 3 1. OVERVIEW OF OTP ISSUANCE/INSTALLATION 4 4 5 6 7 9 12 12 2. OTP ISSUANCE/INSTALLATION
For B2B Administrators of Samsung Electronics Online Customer DB OTP Issuance/Use Manual (Windows Type) Contents 3 1. OVERVIEW OF OTP ISSUANCE/INSTALLATION 4 4 5 6 7 9 12 12 2. OTP ISSUANCE/INSTALLATION
Security. CSC309 TA: Sukwon Oh
 Security CSC309 TA: Sukwon Oh Outline SQL Injection NoSQL Injection (MongoDB) Same Origin Policy XSSI XSS CSRF (XSRF) SQL Injection What is SQLI? Malicious user input is injected into SQL statements and
Security CSC309 TA: Sukwon Oh Outline SQL Injection NoSQL Injection (MongoDB) Same Origin Policy XSSI XSS CSRF (XSRF) SQL Injection What is SQLI? Malicious user input is injected into SQL statements and
Login Procedures. Access Treasury Gateway by entering the site address in your web browser navigation box: https://securentrycorp.calbanktrust.
 Treasury Gateway Getting Started Guide Treasury Gateway is a premier single sign-on and security portal which allows you access to multiple services simultaneously through the same session, provides convenient
Treasury Gateway Getting Started Guide Treasury Gateway is a premier single sign-on and security portal which allows you access to multiple services simultaneously through the same session, provides convenient
Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary Attack
 P3 - Explain the security risks and protection mechanisms involved in website performance Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary
P3 - Explain the security risks and protection mechanisms involved in website performance Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary
13241 Woodland Park Road, Suite 400 Herndon, VA USA A U T H O R : E X O S T A R D ATE: M A R C H V E R S I O N : 3.
 SECURE ACCESS MAN AG E R FIRST TIME LOGIN GUIDE A U T H O R : E X O S T A R D ATE: M A R C H 2 0 1 5 V E R S I O N : 3.0 1 S E C U R E A CCESS M A N A G E R SECURE ACCESS MANAGER OVERVIEW... 3 SUMMARY...
SECURE ACCESS MAN AG E R FIRST TIME LOGIN GUIDE A U T H O R : E X O S T A R D ATE: M A R C H 2 0 1 5 V E R S I O N : 3.0 1 S E C U R E A CCESS M A N A G E R SECURE ACCESS MANAGER OVERVIEW... 3 SUMMARY...
Lecture 13: MySQL and PHP. Monday, March 26, 2018
 Lecture 13: MySQL and PHP Monday, March 26, 2018 MySQL The Old Way In older versions of PHP, we typically used functions that started with mysql_ that did not belong to a class For example: o o o o mysql_connect()
Lecture 13: MySQL and PHP Monday, March 26, 2018 MySQL The Old Way In older versions of PHP, we typically used functions that started with mysql_ that did not belong to a class For example: o o o o mysql_connect()
10 Active Directory Misconfigurations That Lead to Total Compromise Austin, TX 201 W 5th St.
 10 Active Directory Misconfigurations That Lead to Total Compromise hello@javelin-networks.com +1-888-867-5179 Austin, TX 201 W 5th St. 1. Group Policy Preferences Visible Passwords Group Policy Preferences
10 Active Directory Misconfigurations That Lead to Total Compromise hello@javelin-networks.com +1-888-867-5179 Austin, TX 201 W 5th St. 1. Group Policy Preferences Visible Passwords Group Policy Preferences
Secure Access Manager User Guide September 2017
 Secure Access Manager User Guide September 2017 1 1 INTRODUCTION... 3 1.1 SUMMARY... 3 2 BASIC FUNCTIONS... 3 2.1 LOGIN TO YOUR SAM ACCOUNT... 3 2.1.1 How to Activate your Account... 3 2.1.2 How to Login
Secure Access Manager User Guide September 2017 1 1 INTRODUCTION... 3 1.1 SUMMARY... 3 2 BASIC FUNCTIONS... 3 2.1 LOGIN TO YOUR SAM ACCOUNT... 3 2.1.1 How to Activate your Account... 3 2.1.2 How to Login
One-Time PIN. User Guide
 One-Time PIN User Guide Table of Contents Online Banking Setting up One-Time PIN Registering your device Logging in with One-Time PIN Changing One-Time PIN Delivery Method Mobile Banking Setting up One-Time
One-Time PIN User Guide Table of Contents Online Banking Setting up One-Time PIN Registering your device Logging in with One-Time PIN Changing One-Time PIN Delivery Method Mobile Banking Setting up One-Time
Authentication Security
 Authentication Security Hui Zhu Copyright 2005 www.ebizsec.com Agenda Authentication Components Authentication Hacking Consideration for Authentication Security Principle for Authentication Security Case
Authentication Security Hui Zhu Copyright 2005 www.ebizsec.com Agenda Authentication Components Authentication Hacking Consideration for Authentication Security Principle for Authentication Security Case
Robust Defenses for Cross-Site Request Forgery Review
 Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Login Manager Windows Form Sample
 Login Manager Windows Form Sample Contents Introduction... 2 Login Management Framework... 2 Windows Form Application Sample... 2 Start Form... 2 Login Form... 6 UI... 6 User table... 6 Add Login Manager
Login Manager Windows Form Sample Contents Introduction... 2 Login Management Framework... 2 Windows Form Application Sample... 2 Start Form... 2 Login Form... 6 UI... 6 User table... 6 Add Login Manager
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
<Partner Name> <Partner Product> RSA SECURID ACCESS. NetMove SaAT Secure Starter. Standard Agent Client Implementation Guide
 RSA SECURID ACCESS Standard Agent Client Implementation Guide NetMove Daniel R. Pintal, RSA Partner Engineering Last Modified: April 4, 2018 Solution Summary Secure Starter
RSA SECURID ACCESS Standard Agent Client Implementation Guide NetMove Daniel R. Pintal, RSA Partner Engineering Last Modified: April 4, 2018 Solution Summary Secure Starter
Payment Services Group
 Payment Services Group Welcome to the Bank of Punjab Mobile Banking App The BOP Mobile Banking app lets you take control of your personal accounts. This guide helps you set up, register and use the BOP
Payment Services Group Welcome to the Bank of Punjab Mobile Banking App The BOP Mobile Banking app lets you take control of your personal accounts. This guide helps you set up, register and use the BOP
Web and e-registration Vendor Help Manual
 Web and e-registration Vendor Help Manual Table of Contents Contact Us... 2 Web Registration Process... 2 DSC Serial No. Updation Process... 4 Empanelment (E REGISTRATION) Process... 9 Contact Us: For
Web and e-registration Vendor Help Manual Table of Contents Contact Us... 2 Web Registration Process... 2 DSC Serial No. Updation Process... 4 Empanelment (E REGISTRATION) Process... 9 Contact Us: For
The Art Of HACKING. ORGANIZED by ENCIPHERS WEB HACKING BASIC LEVEL. September 29th, 2018
 The Art Of HACKING ORGANIZED by ENCIPHERS September 29th, 2018 WEB HACKING BASIC LEVEL The Art Of Hacking A series of training focused on teaching practical penetration testing on Web and Mobile applications.
The Art Of HACKING ORGANIZED by ENCIPHERS September 29th, 2018 WEB HACKING BASIC LEVEL The Art Of Hacking A series of training focused on teaching practical penetration testing on Web and Mobile applications.
Secure Access Manager (SAM) Administrator Guide December 2017
 Secure Access Manager (SAM) Administrator Guide December 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 SECURE ACCESS MANAGER (SAM) OVERVIEW... 4 ADMINISTRATIVE ROLES OVERVIEW... 4 SAM NAVIGATIONAL
Secure Access Manager (SAM) Administrator Guide December 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 SECURE ACCESS MANAGER (SAM) OVERVIEW... 4 ADMINISTRATIVE ROLES OVERVIEW... 4 SAM NAVIGATIONAL
Administrator's Guide SecureLogin for JIRA
 Administrator's Guide SecureLogin for JIRA Add-on Installation Before you begin To install the Secure Login Plugin, you must log-in with JIRA Admin permissions Installing Secure Login via the UPM 1. Click
Administrator's Guide SecureLogin for JIRA Add-on Installation Before you begin To install the Secure Login Plugin, you must log-in with JIRA Admin permissions Installing Secure Login via the UPM 1. Click
SECURITY TRENDS & VULNERABILITIES REVIEW FINANCIAL SYSTEMS
 SECURITY TRENDS & VULNERABILITIES REVIEW FINANCIAL SYSTEMS 2017 CONTENTS Introduction...3 Executive summary...3 1. Research data...5 2. Protection flaws...6 2.1. Overall statistics...6 2.2. Comparison
SECURITY TRENDS & VULNERABILITIES REVIEW FINANCIAL SYSTEMS 2017 CONTENTS Introduction...3 Executive summary...3 1. Research data...5 2. Protection flaws...6 2.1. Overall statistics...6 2.2. Comparison
1 About Web Security. What is application security? So what can happen? see [?]
![1 About Web Security. What is application security? So what can happen? see [?] 1 About Web Security. What is application security? So what can happen? see [?]](/thumbs/85/92997588.jpg) 1 About Web Security What is application security? see [?] So what can happen? 1 taken from [?] first half of 2013 Let s focus on application security risks Risk = vulnerability + impact New App: http://www-03.ibm.com/security/xforce/xfisi
1 About Web Security What is application security? see [?] So what can happen? 1 taken from [?] first half of 2013 Let s focus on application security risks Risk = vulnerability + impact New App: http://www-03.ibm.com/security/xforce/xfisi
Application Layer Security
 Application Layer Security General overview Ma. Angel Marquez Andrade Benefits of web Applications: No need to distribute separate client software Changes to the interface take effect immediately Client-side
Application Layer Security General overview Ma. Angel Marquez Andrade Benefits of web Applications: No need to distribute separate client software Changes to the interface take effect immediately Client-side
Server - The Tigo platform and urls associated with the api Client - Third party user with api access to the Tigo platform and/or Tigo api.
 Tigo REST API V3 Introduction This api is used to work with the Tigo Energy platform to automate the retrieval and creation of elements. It will attempt to adhere to standard REST calls found in most REST
Tigo REST API V3 Introduction This api is used to work with the Tigo Energy platform to automate the retrieval and creation of elements. It will attempt to adhere to standard REST calls found in most REST
Yubico with Centrify for Mac - Deployment Guide
 CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
OWASP TOP 10. By: Ilia
 OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
Administrator's Guide SecureLogin for Confluence
 Administrator's Guide SecureLogin for Confluence Add-on Installation Before you begin To install the Secure Login Plugin, you must log-in with Confluence Admin permissions Installing Secure Login via the
Administrator's Guide SecureLogin for Confluence Add-on Installation Before you begin To install the Secure Login Plugin, you must log-in with Confluence Admin permissions Installing Secure Login via the
VMware Identity Manager Administration
 VMware Identity Manager Administration VMware AirWatch 9.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
VMware Identity Manager Administration VMware AirWatch 9.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Application Security Introduction. Tara Gu IBM Product Security Incident Response Team
 Application Security Introduction Tara Gu IBM Product Security Incident Response Team About Me - Tara Gu - tara.weiqing@gmail.com - Duke B.S.E Biomedical Engineering - Duke M.Eng Computer Engineering -
Application Security Introduction Tara Gu IBM Product Security Incident Response Team About Me - Tara Gu - tara.weiqing@gmail.com - Duke B.S.E Biomedical Engineering - Duke M.Eng Computer Engineering -
WatchGuard AP - Remote Code Execution
 WatchGuard AP - Remote Code Execution Security Advisory Date 1/05/2018 Version: 1.0 Table of Contents 1. Document Control... 2 1.1. Document Information... 2 1.2. Revision Control... 2 2. Background...
WatchGuard AP - Remote Code Execution Security Advisory Date 1/05/2018 Version: 1.0 Table of Contents 1. Document Control... 2 1.1. Document Information... 2 1.2. Revision Control... 2 2. Background...
isupplier Portal: Multi-Factor Authentication and One-Time- Passcodes Last Updated: 4-Jun-18 Level 4 - Public INFRASTRUCTURE MINING & METALS
 INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS isupplier Portal: Multi-Factor Authentication and One-Time- Passcodes Last Updated: 4-Jun-18 Level 4 - Public Table
INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS isupplier Portal: Multi-Factor Authentication and One-Time- Passcodes Last Updated: 4-Jun-18 Level 4 - Public Table
Table of Contents. Single Sign On 1
 Table of Contents Table of Contents Single Sign On SAML Authentication Using SAML SSO Authentication Setting up SAML SSO Authentication Configuring OneLogin as an Identity Provider LDAP Authentication
Table of Contents Table of Contents Single Sign On SAML Authentication Using SAML SSO Authentication Setting up SAML SSO Authentication Configuring OneLogin as an Identity Provider LDAP Authentication
John Coggeshall Copyright 2006, Zend Technologies Inc.
 PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
Advanced ASP.NET Identity. Brock Allen
 Advanced ASP.NET Identity Brock Allen brockallen@gmail.com http://brockallen.com @BrockLAllen Advanced The complicated bits of ASP.NET Identity Brock Allen brockallen@gmail.com http://brockallen.com @BrockLAllen
Advanced ASP.NET Identity Brock Allen brockallen@gmail.com http://brockallen.com @BrockLAllen Advanced The complicated bits of ASP.NET Identity Brock Allen brockallen@gmail.com http://brockallen.com @BrockLAllen
RESTful API SecurAccess RESTful API Guide
 RESTful API SecurAccess SecurAccess RESTful API Guide Contents 1.1 SOLUTION SUMMARY... 3 1.2 GUIDE USAGE... 3 1.3 PREREQUISITES... 3 1.4 SETUP... 4 1.5 AVAILABLE RESOURCES... 4 1.41 GET USERS... 5 1.42
RESTful API SecurAccess SecurAccess RESTful API Guide Contents 1.1 SOLUTION SUMMARY... 3 1.2 GUIDE USAGE... 3 1.3 PREREQUISITES... 3 1.4 SETUP... 4 1.5 AVAILABLE RESOURCES... 4 1.41 GET USERS... 5 1.42
Web Application Security. Philippe Bogaerts
 Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
CMS-i First Time Activation User Guide
 Download Soft Token Application (ios Application) Download Soft Token Application (Android Application) First Time Activation Soft Token Registration Version : 1.0 Last updated : 25 th July 2018 alrajhicashbiz24seven
Download Soft Token Application (ios Application) Download Soft Token Application (Android Application) First Time Activation Soft Token Registration Version : 1.0 Last updated : 25 th July 2018 alrajhicashbiz24seven
Internet Banking. Support Pack. Call or visit delphibank.com.au
 Internet Banking Support Pack Call 1300 665 062 or visit delphibank.com.au Delphi Bank A Division of Bendigo and Adelaide Bank Limited, ABN 11 068 049 178 AFSL / Australian Credit Licence 237879. Step
Internet Banking Support Pack Call 1300 665 062 or visit delphibank.com.au Delphi Bank A Division of Bendigo and Adelaide Bank Limited, ABN 11 068 049 178 AFSL / Australian Credit Licence 237879. Step
Web Security. Attacks on Servers 11/6/2017 1
 Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
NOT SO RANDOM NUMBERS. TAKE TWO
 NOT SO RANDOM NUMBERS. TAKE TWO ARSENY REUTOV TIMUR YUNUSOV DMITRY NAGIBIN George Argyros and Aggelos Kiayias have published recently an awesome research concerning attacks on pseudo random generator in
NOT SO RANDOM NUMBERS. TAKE TWO ARSENY REUTOV TIMUR YUNUSOV DMITRY NAGIBIN George Argyros and Aggelos Kiayias have published recently an awesome research concerning attacks on pseudo random generator in
Web Security EITF05 Department of Electrical and Information Technology Lund University
 Final exam in Web Security EITF05 Department of Electrical and Information Technology Lund University October 31 st, 2014, 8.0013.00 You may answer in either Swedish or English. If any data is lacking,
Final exam in Web Security EITF05 Department of Electrical and Information Technology Lund University October 31 st, 2014, 8.0013.00 You may answer in either Swedish or English. If any data is lacking,
Managing User Account Passwords
 Managing User Account Passwords August 2013 Image 9: Confirming Security Preference Updates Selecting Yes will direct the user to the User Settings editor where preferences can be set (see Image 10). Selecting
Managing User Account Passwords August 2013 Image 9: Confirming Security Preference Updates Selecting Yes will direct the user to the User Settings editor where preferences can be set (see Image 10). Selecting
SBI Mingle User Manual
 SBI Mingle User Manual 1. Facebook banking for State Bank of India: Registration 1.1 Registration Mode 1: Debit Card 2. Open the SBI Mingle application User visits SBI Official Page, clicks on SBI Mingle
SBI Mingle User Manual 1. Facebook banking for State Bank of India: Registration 1.1 Registration Mode 1: Debit Card 2. Open the SBI Mingle application User visits SBI Official Page, clicks on SBI Mingle
User manual For 1. Obtaining GST provisional user id and password from the Department portal or from unit offices.
 User manual For 1. Obtaining GST provisional user id and password from the Department portal or from unit offices. 2. GST enrollment process at the gst.gov.in portal 1.a Process for obtaining GST provisional
User manual For 1. Obtaining GST provisional user id and password from the Department portal or from unit offices. 2. GST enrollment process at the gst.gov.in portal 1.a Process for obtaining GST provisional
FortiAuthenticator - Two-Factor Authentication for Web Applications Solution Guide VERSION 1.0
 FortiAuthenticator - Two-Factor Authentication for Web Applications Solution Guide VERSION 1.0 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET
FortiAuthenticator - Two-Factor Authentication for Web Applications Solution Guide VERSION 1.0 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET
Report HQ. Quick Start Guide. Report HQ Quick Start Guide - Version 1.2
 Report HQ Quick Start Guide STEP 1 Requesting An Account 1) Request an account via the Report HQ Request Form 2) Nasdaq will verify your account 3) Once your account is verified and provisioned, you will
Report HQ Quick Start Guide STEP 1 Requesting An Account 1) Request an account via the Report HQ Request Form 2) Nasdaq will verify your account 3) Once your account is verified and provisioned, you will
Berner Fachhochschule Haute cole spcialise bernoise Berne University of Applied Sciences 2
 Table of Contents Hacking Web Sites Broken Authentication Emmanuel Benoist Spring Term 2018 Introduction Examples of Attacks Brute Force Session Spotting Replay Attack Session Fixation Attack Session Hijacking
Table of Contents Hacking Web Sites Broken Authentication Emmanuel Benoist Spring Term 2018 Introduction Examples of Attacks Brute Force Session Spotting Replay Attack Session Fixation Attack Session Hijacking
Authentication Technology for a Smart eid Infrastructure.
 Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Beaufort Asset Clearing Services Limited (in special administration) Client Claim Portal. User Guide
 Beaufort Asset Clearing Services Limited (in special administration) Client Claim Portal User Guide Contents 1. System Overview 2. User Access 3. Logging In 4. Confirming your client details 5. Reviewing
Beaufort Asset Clearing Services Limited (in special administration) Client Claim Portal User Guide Contents 1. System Overview 2. User Access 3. Logging In 4. Confirming your client details 5. Reviewing
Nemesis: Preventing Web Authentication & Access Control Vulnerabilities. Michael Dalton, Christos Kozyrakis Stanford University
 Nemesis: Preventing Web Authentication & Access Control Vulnerabilities Michael Dalton, Christos Kozyrakis Stanford University Nickolai Zeldovich Massachusetts Institute of Technology Web Application Overview
Nemesis: Preventing Web Authentication & Access Control Vulnerabilities Michael Dalton, Christos Kozyrakis Stanford University Nickolai Zeldovich Massachusetts Institute of Technology Web Application Overview
Stop sweating the password and learn to love public key cryptography. Chris Streeks Solutions Engineer, Yubico
 1 Stop sweating the password and learn to love public key cryptography Chris Streeks Solutions Engineer, Yubico Stop Sweating the Password! 2 Agenda Introduction The modern state of Phishing How to become
1 Stop sweating the password and learn to love public key cryptography Chris Streeks Solutions Engineer, Yubico Stop Sweating the Password! 2 Agenda Introduction The modern state of Phishing How to become
Personal account manual A ME
 Personal account manual A.005.34.01-01.ME 05.07.2018 Table of Contents 1. Logging in... 4 2. Main page... 6 3. Orders monitor... 6 3.1. Orders search... 7 3.2. Search results... 8 3.3. Saving data to file...
Personal account manual A.005.34.01-01.ME 05.07.2018 Table of Contents 1. Logging in... 4 2. Main page... 6 3. Orders monitor... 6 3.1. Orders search... 7 3.2. Search results... 8 3.3. Saving data to file...
Web Security. Thierry Sans
 Web Security Thierry Sans 1991 Sir Tim Berners-Lee Web Portals 2014 Customer Resources Managemen Accounting and Billing E-Health E-Learning Collaboration Content Management Social Networks Publishing Web
Web Security Thierry Sans 1991 Sir Tim Berners-Lee Web Portals 2014 Customer Resources Managemen Accounting and Billing E-Health E-Learning Collaboration Content Management Social Networks Publishing Web
Release note Tornaborate
 Release note 1.2.6 Tornaborate 2015-09-10 Contents 1 Summary 4 2 Additional important information about this release 5 3 Upgrade 6 3.1 Prerequisites................................... 6 3.2 How to apply
Release note 1.2.6 Tornaborate 2015-09-10 Contents 1 Summary 4 2 Additional important information about this release 5 3 Upgrade 6 3.1 Prerequisites................................... 6 3.2 How to apply
Combating Common Web App Authentication Threats
 Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Go to SQA Academy the website address is
 Joining a course on the SQA Academy You may find it useful to print out this document for reference. There are two steps to joining an SQA Academy course. First you need an account with the SQA Academy,
Joining a course on the SQA Academy You may find it useful to print out this document for reference. There are two steps to joining an SQA Academy course. First you need an account with the SQA Academy,
APG8205 OTP Generator
 APG8205 OTP Generator User Manual V1.00 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Supported Card Type... 3 1.2. Supported Language... 3 2.0. APG8205 Illustration...
APG8205 OTP Generator User Manual V1.00 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Supported Card Type... 3 1.2. Supported Language... 3 2.0. APG8205 Illustration...
Web Attacks Lab. 35 Points Group Lab Due Date: Lesson 16
 CS482 SQL and XSS Attack Lab AY172 1 Web Attacks Lab 35 Points Group Lab Due Date: Lesson 16 Derived from c 2006-2014 Wenliang Du, Syracuse University. Do not redistribute with explicit consent from MAJ
CS482 SQL and XSS Attack Lab AY172 1 Web Attacks Lab 35 Points Group Lab Due Date: Lesson 16 Derived from c 2006-2014 Wenliang Du, Syracuse University. Do not redistribute with explicit consent from MAJ
Slides adopted from Laurie Williams. OWASP Top Ten. John Slankas
 Slides adopted from Laurie Williams OWASP Top Ten John Slankas jbslanka@ncsu.edu Agenda Overview of the Top 10 A1 Injection A2 Broken Authentication and Session Management A3 Cross-Site Scripting A4 Broken
Slides adopted from Laurie Williams OWASP Top Ten John Slankas jbslanka@ncsu.edu Agenda Overview of the Top 10 A1 Injection A2 Broken Authentication and Session Management A3 Cross-Site Scripting A4 Broken
PHP Wrap Up. Thomas Beebe Advanced DataTools Corp
 PHP Wrap Up June 17 2014 Thomas Beebe Advanced DataTools Corp (tom@advancedatatools.com) Tom Beebe Tom is a Senior Database Consultant and has been with Advanced DataTools for over 10 years. He has been
PHP Wrap Up June 17 2014 Thomas Beebe Advanced DataTools Corp (tom@advancedatatools.com) Tom Beebe Tom is a Senior Database Consultant and has been with Advanced DataTools for over 10 years. He has been
Why bother? Default configurations Buffer overflows Authentication mechanisms Reverse engineering Questions?
 Jeroen van Beek 1 Why bother? Default configurations Buffer overflows Authentication mechanisms Reverse engineering Questions? 2 Inadequate OS and application security: Data abuse Stolen information Bandwidth
Jeroen van Beek 1 Why bother? Default configurations Buffer overflows Authentication mechanisms Reverse engineering Questions? 2 Inadequate OS and application security: Data abuse Stolen information Bandwidth
Maximizing the speed of time based SQL injection data retrieval
 Maximizing the speed of time based SQL injection data retrieval 30c3, Hamburg, 29.12.2013 Arnim' ; DROP TABLE students;-- ) Introduction SQL injection SQLi is #1 of OWASP Top 10 Web vulnerabilities Sample
Maximizing the speed of time based SQL injection data retrieval 30c3, Hamburg, 29.12.2013 Arnim' ; DROP TABLE students;-- ) Introduction SQL injection SQLi is #1 of OWASP Top 10 Web vulnerabilities Sample
jk0-022 Exam Questions Demo CompTIA Exam Questions jk0-022
 CompTIA Exam Questions jk0-022 CompTIA Academic/E2C Security+ Certification Exam Voucher Only Version:Demo 1.An attacker used an undocumented and unknown application exploit to gain access to a file server.
CompTIA Exam Questions jk0-022 CompTIA Academic/E2C Security+ Certification Exam Voucher Only Version:Demo 1.An attacker used an undocumented and unknown application exploit to gain access to a file server.
Web Security, Summer Term 2012
 IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 7 Broken Authentication and Session
IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 7 Broken Authentication and Session
Web Security, Summer Term 2012
 Table of Contents IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Introduction Examples of Attacks Brute Force Session
Table of Contents IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Introduction Examples of Attacks Brute Force Session
HUB International: Citrix Troubleshooting. July 2016
 HUB International: Citrix Troubleshooting July 2016 Agenda 1 Logging into the new HUB Citrix Desktop (a.k.a. VDI or Xen) 2 CITRIX Receiver RESET 3 Issues with Citrix6 4 Common Issues 2 Logging into the
HUB International: Citrix Troubleshooting July 2016 Agenda 1 Logging into the new HUB Citrix Desktop (a.k.a. VDI or Xen) 2 CITRIX Receiver RESET 3 Issues with Citrix6 4 Common Issues 2 Logging into the
Administrative Guide
 Administrative Guide Admin Home: Wiley Digital Archives (WDA) Admin pages. Please login using the admin name and password assigned to the institution 1. The first screen shows information about the institution,
Administrative Guide Admin Home: Wiley Digital Archives (WDA) Admin pages. Please login using the admin name and password assigned to the institution 1. The first screen shows information about the institution,
User Guidelines Phase 2
 2.11 Existing User Perform Change Passphrase Image And Slogan Existing user login to IDSS and change passphrase image and slogan 2.11.1 Event Handling Success Case NO STEPS 1. Go to IDSS via URL https://idss.tm.com.my/
2.11 Existing User Perform Change Passphrase Image And Slogan Existing user login to IDSS and change passphrase image and slogan 2.11.1 Event Handling Success Case NO STEPS 1. Go to IDSS via URL https://idss.tm.com.my/
Personal account manual A ME
 Personal account manual A.005.34.01-01.ME 08.04.2019 Table of Contents 1. Logging in... 4 2. Main page... 6 3. Orders monitor... 6 3.1. Orders search... 7 3.2. Search results... 9 3.3. Saving data to file...
Personal account manual A.005.34.01-01.ME 08.04.2019 Table of Contents 1. Logging in... 4 2. Main page... 6 3. Orders monitor... 6 3.1. Orders search... 7 3.2. Search results... 9 3.3. Saving data to file...
