Lecture 13: MySQL and PHP. Monday, March 26, 2018
|
|
|
- Hortense Flynn
- 5 years ago
- Views:
Transcription
1 Lecture 13: MySQL and PHP Monday, March 26, 2018
2 MySQL The Old Way In older versions of PHP, we typically used functions that started with mysql_ that did not belong to a class For example: o o o o mysql_connect() to create a connection mysql_select_db() to choose the database mysql_query() to execute a query (and so on ) However, as of PHP 5, these functions are deprecated, will likely be removed from PHP some point down the road The newer mysqli class should be used instead DO NOT USE THESE OLD FUNCTIONS IN THIS COURSE 1
3 mysqli: Connecting <?php $conn = new mysqli($host, $user, $pw, $db); if($conn->connect_error) die($conn->connect_error);?> 2
4 mysqli: Querying <?php $conn = new mysqli($host, $user, $pw, $db); if($conn->connect_error) die($conn->connect_error); $results = $conn->query($query_goes_here); if(!$results) die($conn->error);?> 3
5 mysqli: Querying The result of query method for queries that return data (such as SELECT queries not UPDATE, INSERT, or DELETE) is an object that contains the following attributes: o current_field o field_count o lengths o num_rows 4
6 mysqli: Viewing Results You can use the fetch_assoc method to advance the pointer (current_field) to each row 5
7 mysqli: Querying <?php $conn = new mysqli($host, $user, $pw, $db); if($conn->connect_error) die($conn->connect_error); $results = $conn->query("select * FROM foo"); if(!$results) die($conn->error); while($row = $results->fetch_assoc()) { // do whatever you want with records // access using using $row->fieldname }?> 6
8 Security for Storing Passwords Your first lab will deal with authenticating off of an existing database with usernames/passwords in it The obvious way to set up a database is to create a users table and include a field called username and a field called password, and store both as entered However, storing passwords in plain text is not secure 7
9 Security for Storing Passwords Most services use the MD5 encryption algorithm to encrypt passwords There are MD5 functions available in BOTH MySQL and PHP The result of an MD5 encryption is a 32-character string containing hexadecimal characters (0-9 and a-f) 8
10 Security for Storing Passwords MD5 is not reversible once something is encrypted, there is no way to decrypt it There are 32^16 (1,208,925,819,614,629,174,706,176) different values that can result from MD5 encryption thus, it s not quick to brute force This is why most services don t let you retrieve your old password, and only reset it there is no way to retrieve it However, to verify an MD5 value, you can encrypt the other item and compare them 9
11 Security for Storing Passwords So when a user registers and creates a password, that password should be run through MD5 to be stored for the database: INSERT INTO users (username, password) VALUES ('$username', MD5('$password')); 10
12 Security for Storing Passwords To verify logins: SELECT * FROM users WHERE username = '$username' AND password = MD5('$password'); If there is 1 result from this query, the login is valid 11
13 Changing Your Password To change your MySQL password to something more memorable, login to dilbert, and login to mysql: dilbert> mysql p Then, run the following command mysql> SET PASSWORD = PASSWORD('YOURNEWPASSWORD'); 12
14 Hiding Your Password After you ve changed your password more memorable, you probably don t want me to see it Solution: Put the login information in a separate file (such as mysql_login.php), and then include it in your lab files I have access to your MySQL databases for this course, so I can substitute in my own MySQL login information to check your programs 13
15 Hiding Your Password mysql_login.php: <?php $username = "wagnerja"; $password = "password123";?> lab.php: <?php require_once('mysql_login.php'); $conn = new mysqli("localhost", $username, $password, "cs383"); // rest of program...?> 14
16 Closing a MySQL Connection One thing I forgot to cover last week you should close your MySQL connections when you are finished with them: <?php $conn = new mysqli("localhost", "wagnerja", "password123", "cs383"); // rest of program... $conn->close();?> 15
17 Code Injection Last week, we talked about creating a form with a user s login and validating it on the next page We talked about the security of storing passwords, but not the security of validating input 16
18 Code Injection 17
19 Code Injection Remember the query that we ended last week s lecture with: SELECT * FROM users WHERE username = '$username' AND password = MD5('$password'); What happens if someone enters the following on the login form in the username field: '; TRUNCATE TABLE users; 18
20 Code Injection When username is substituted in, the following is run as the query: SELECT * FROM users WHERE username = ''; TRUNCATE TABLE users; ' AND password = MD5('$password'); What happens? o A SELECT statement, looking for the username of an empty string, is parsed until it reaches the semicolon, telling it that this first query has ended an to execute it o As long as that first query does not produce an error, it will move on to the next query o It executes the query through the next semicolon truncating (deleting all records from) the users table o Although the remainder of the query is not valid, it does not matter the second one is executed before the third one is parsed 19
21 Code Injection There are other things code injection can do Suppose someone enters for the username: '; UPDATE users SET password = MD5('password12'); Now all passwords in the system (including potentially admin users) has been set to password12 20
22 Code Injection For code injection to work in databases, users would need to know the structure of your tables But is it really that hard to figure out? o What are you going to name a table that contains data about your users? o What about open source software if the source code is out there, anybody can read it to see what the tables and field names should be 21
23 Code Injection Some ways to protect from code injection: o o Search the input for symbols that don t match what the field is asking for Why would somebody be putting a semicolon in for a username or first name? Escape out characters If the single quote gets preceded by an escape character (backslash), it will not end the string for the field in the WHERE clause Your book suggests the using the following function to pass all input through: <?php function mysql_fix_string($conn, $string) { if(get_magic_quotes_gpc()) $string = stripslashes($string); } return $conn->real_escape_string($string);?> 22
24 Code Injection get_magic_quotes_gpc() returns an environment variable which is set to false on dilbert, so really, you can just do the following in this class: $query = "SELECT * FROM users WHERE username = '". $conn->real_escape_string($username). "'"; 23
25 Prepared Statements Prepared statements (when not retrieving records more on this at a later time) allow you to repeat the same SQL statements more efficiently This is not more efficient when you are only executing a statement a couple times 24
26 Prepared Statements <?php $conn = new mysqli("localhost", "wagnerja", "password123", "cs383"); // provide query with?s in place of variables $stmt = $conn->prepare("insert INTO lab8users (username, password, firstname, lastname) VALUES (?,?,?,?)"); // bind parameters // the first argument contains one character per // variable: s = str, i = int, d = dbl, b = blob $stmt->bindparam("ssss", $u, $p, $f, $l);... 25
27 Prepared Statements... $u = "ally.apple"; $p = md5("password1"); $f = "Ally"; $l = "Apple"; $stmt->execute(); $u = "bill.bear"; $p = md5("password2"); $f = "Bill"; $l = "Bear"; $stmt->execute(); // more $stmt->close(); $conn->close();?> 26
Development Technologies. Agenda: phpmyadmin 2/20/2016. phpmyadmin MySQLi. Before you can put your data into a table, that table should exist.
 CIT 736: Internet and Web Development Technologies Lecture 10 Dr. Lupiana, DM FCIM, Institute of Finance Management Semester 1, 2016 Agenda: phpmyadmin MySQLi phpmyadmin Before you can put your data into
CIT 736: Internet and Web Development Technologies Lecture 10 Dr. Lupiana, DM FCIM, Institute of Finance Management Semester 1, 2016 Agenda: phpmyadmin MySQLi phpmyadmin Before you can put your data into
Networks and Web for Health Informatics (HINF 6220) Tutorial 13 : PHP 29 Oct 2015
 Networks and Web for Health Informatics (HINF 6220) Tutorial 13 : PHP 29 Oct 2015 PHP Arrays o Arrays are single variables that store multiple values at the same time! o Consider having a list of values
Networks and Web for Health Informatics (HINF 6220) Tutorial 13 : PHP 29 Oct 2015 PHP Arrays o Arrays are single variables that store multiple values at the same time! o Consider having a list of values
PHP Development - Introduction
 PHP Development - Introduction Php Hypertext Processor PHP stands for PHP: Hypertext Preprocessor PHP is a server-side scripting language, like ASP PHP scripts are executed on the server PHP supports many
PHP Development - Introduction Php Hypertext Processor PHP stands for PHP: Hypertext Preprocessor PHP is a server-side scripting language, like ASP PHP scripts are executed on the server PHP supports many
Lecture 5. Monday, September 15, 2014
 Lecture 5 Monday, September 15, 2014 The MySQL Command So far, we ve learned some parts of the MySQL command: mysql [database] [-u username] p [-- local-infile]! Now let s go further 1 mysqldump mysqldump
Lecture 5 Monday, September 15, 2014 The MySQL Command So far, we ve learned some parts of the MySQL command: mysql [database] [-u username] p [-- local-infile]! Now let s go further 1 mysqldump mysqldump
Chapters 10 & 11 PHP AND MYSQL
 Chapters 10 & 11 PHP AND MYSQL Getting Started The database for a Web app would be created before accessing it from the web. Complete the design and create the tables independently. Use phpmyadmin, for
Chapters 10 & 11 PHP AND MYSQL Getting Started The database for a Web app would be created before accessing it from the web. Complete the design and create the tables independently. Use phpmyadmin, for
MySQL: Access Via PHP
 MySQL: Access Via PHP CISC 282 November 15, 2017 phpmyadmin: Login http://cisc282.caslab. queensu.ca/phpmyadmin/ Use your NetID and CISC 282 password to log in 2 phpmyadmin: Select DB Clicking on this
MySQL: Access Via PHP CISC 282 November 15, 2017 phpmyadmin: Login http://cisc282.caslab. queensu.ca/phpmyadmin/ Use your NetID and CISC 282 password to log in 2 phpmyadmin: Select DB Clicking on this
MySQL: Querying and Using Form Data
 MySQL: Querying and Using Form Data CISC 282 November 15, 2017 Preparing Data $mysqli >real_escape_string($datavalue); Requires a $mysqli object Functional version mysqli_real_escape_string( ) does not
MySQL: Querying and Using Form Data CISC 282 November 15, 2017 Preparing Data $mysqli >real_escape_string($datavalue); Requires a $mysqli object Functional version mysqli_real_escape_string( ) does not
Lecture 3: Web Servers / PHP and Apache. CS 383 Web Development II Monday, January 29, 2018
 Lecture 3: Web Servers / PHP and Apache CS 383 Web Development II Monday, January 29, 2018 Server Configuration One of the most common configurations of servers meant for web development is called a LAMP
Lecture 3: Web Servers / PHP and Apache CS 383 Web Development II Monday, January 29, 2018 Server Configuration One of the most common configurations of servers meant for web development is called a LAMP
Database Connectivity using PHP Some Points to Remember:
 Database Connectivity using PHP Some Points to Remember: 1. PHP has a boolean datatype which can have 2 values: true or false. However, in PHP, the number 0 (zero) is also considered as equivalent to False.
Database Connectivity using PHP Some Points to Remember: 1. PHP has a boolean datatype which can have 2 values: true or false. However, in PHP, the number 0 (zero) is also considered as equivalent to False.
CHAPTER 10. Connecting to Databases within PHP
 CHAPTER 10 Connecting to Databases within PHP CHAPTER OBJECTIVES Get a connection to a MySQL database from within PHP Use a particular database Send a query to the database Parse the query results Check
CHAPTER 10 Connecting to Databases within PHP CHAPTER OBJECTIVES Get a connection to a MySQL database from within PHP Use a particular database Send a query to the database Parse the query results Check
PHP: Cookies, Sessions, Databases. CS174. Chris Pollett. Sep 24, 2008.
 PHP: Cookies, Sessions, Databases. CS174. Chris Pollett. Sep 24, 2008. Outline. How cookies work. Cookies in PHP. Sessions. Databases. Cookies. Sometimes it is useful to remember a client when it comes
PHP: Cookies, Sessions, Databases. CS174. Chris Pollett. Sep 24, 2008. Outline. How cookies work. Cookies in PHP. Sessions. Databases. Cookies. Sometimes it is useful to remember a client when it comes
More loops. Control structures / flow control. while loops. Loops / Iteration / doing things over and over and over and over...
 Control structures / flow control More loops while loops if... else Switch for loops while... do.. do... while... Much of this material is explained in PHP programming 2nd Ed. Chap 2 Control structures
Control structures / flow control More loops while loops if... else Switch for loops while... do.. do... while... Much of this material is explained in PHP programming 2nd Ed. Chap 2 Control structures
A1 (Part 2): Injection SQL Injection
 A1 (Part 2): Injection SQL Injection SQL injection is prevalent SQL injection is impactful Why a password manager is a good idea! SQL injection is ironic SQL injection is funny Firewall Firewall Accounts
A1 (Part 2): Injection SQL Injection SQL injection is prevalent SQL injection is impactful Why a password manager is a good idea! SQL injection is ironic SQL injection is funny Firewall Firewall Accounts
PHP Querying. Lecture 21. Robb T. Koether. Hampden-Sydney College. Fri, Mar 2, 2018
 PHP Querying Lecture 21 Robb T. Koether Hampden-Sydney College Fri, Mar 2, 2018 Robb T. Koether (Hampden-Sydney College) PHP Querying Fri, Mar 2, 2018 1 / 32 1 Connect to the Database 2 Querying the Database
PHP Querying Lecture 21 Robb T. Koether Hampden-Sydney College Fri, Mar 2, 2018 Robb T. Koether (Hampden-Sydney College) PHP Querying Fri, Mar 2, 2018 1 / 32 1 Connect to the Database 2 Querying the Database
Daniel Pittman October 17, 2011
 Daniel Pittman October 17, 2011 SELECT target-list FROM relation-list WHERE qualification target-list A list of attributes of relations in relation-list relation-list A list of relation names qualification
Daniel Pittman October 17, 2011 SELECT target-list FROM relation-list WHERE qualification target-list A list of attributes of relations in relation-list relation-list A list of relation names qualification
School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University
 School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University ITS331 Information Technology Laboratory I Laboratory #8: PHP & Form Processing II Objective:
School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University ITS331 Information Technology Laboratory I Laboratory #8: PHP & Form Processing II Objective:
Mount Saint Mary College, Newburgh, NY Internet Programming III - CIT310
 Warm up mini-lab Lab 1 - Functions Type in the following function definition and calls to the function. Test it and understand it. function myprint($str= No String Supplied ) // the argument is optional
Warm up mini-lab Lab 1 - Functions Type in the following function definition and calls to the function. Test it and understand it. function myprint($str= No String Supplied ) // the argument is optional
PHP. How Web Applications interact with server side databases CRUD. Connecting and using mysql from PHP PHP provides many mysql specific functions
 PHP How Web Applications interact with server side databases CRUD Connecting and using mysql from PHP PHP provides many mysql specific functions mysql_connect mysql_select_db mysql_query mysql_fetch_array
PHP How Web Applications interact with server side databases CRUD Connecting and using mysql from PHP PHP provides many mysql specific functions mysql_connect mysql_select_db mysql_query mysql_fetch_array
Chapter 10: MySQL & PHP. PHP and MySQL CIS 86 Mission College
 Chapter 10: MySQL & PHP PHP and MySQL CIS 86 Mission College Tonight s agenda Drop the class? Login file Connecting to a MySQL database Object-oriented PHP Executing a query Fetching a result Fetching
Chapter 10: MySQL & PHP PHP and MySQL CIS 86 Mission College Tonight s agenda Drop the class? Login file Connecting to a MySQL database Object-oriented PHP Executing a query Fetching a result Fetching
Welcome to VFW WebMail. We hope you enjoy your new mailbox. For those users who had been using the old VFW WebMail system, a couple of items:
 VFW WebMail Help Help for VFW WebMail Users Getting Started Welcome to VFW WebMail. We hope you enjoy your new mailbox. For those users who had been using the old VFW WebMail system, a couple of items:
VFW WebMail Help Help for VFW WebMail Users Getting Started Welcome to VFW WebMail. We hope you enjoy your new mailbox. For those users who had been using the old VFW WebMail system, a couple of items:
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks
 A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
Lecture 5. Monday, February 1, 2016
 Lecture 5 Monday, February 1, 2016 === and!== In an example last week, we talked about how PHP does not check type when doing comparisons (so 1.0 == "1.0" is true) PHP calls this type juggling it juggles
Lecture 5 Monday, February 1, 2016 === and!== In an example last week, we talked about how PHP does not check type when doing comparisons (so 1.0 == "1.0" is true) PHP calls this type juggling it juggles
Quick Guide to Installing and Setting Up MySQL Workbench
 Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Comp 519: Web Programming Autumn 2015
 Comp 519: Web Programming Autumn 2015 Advanced SQL and PHP Advanced queries Querying more than one table Searching tables to find information Aliasing tables PHP functions for using query results Using
Comp 519: Web Programming Autumn 2015 Advanced SQL and PHP Advanced queries Querying more than one table Searching tables to find information Aliasing tables PHP functions for using query results Using
Server side scripting and databases
 Example table Server side scripting and databases student How Web Applications interact with server side databases - part 2 student kuid lastname money char char int student table Connecting and using
Example table Server side scripting and databases student How Web Applications interact with server side databases - part 2 student kuid lastname money char char int student table Connecting and using
Web Security. Attacks on Servers 11/6/2017 1
 Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
Real Web Development. yeah, for real.
 Real Web Development yeah, for real. 1 who am i? i m still cyle i m a systems developer and architect every day i m developin i like this kind of stuff 2 real? kind of ranty, sorry web development is more
Real Web Development yeah, for real. 1 who am i? i m still cyle i m a systems developer and architect every day i m developin i like this kind of stuff 2 real? kind of ranty, sorry web development is more
ITS331 IT Laboratory I: (Laboratory #11) Session Handling
 School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University ITS331 Information Technology Laboratory I Laboratory #11: Session Handling Creating
School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University ITS331 Information Technology Laboratory I Laboratory #11: Session Handling Creating
This lab will introduce you to MySQL. Begin by logging into the class web server via SSH Secure Shell Client
 Lab 2.0 - MySQL CISC3140, Fall 2011 DUE: Oct. 6th (Part 1 only) Part 1 1. Getting started This lab will introduce you to MySQL. Begin by logging into the class web server via SSH Secure Shell Client host
Lab 2.0 - MySQL CISC3140, Fall 2011 DUE: Oct. 6th (Part 1 only) Part 1 1. Getting started This lab will introduce you to MySQL. Begin by logging into the class web server via SSH Secure Shell Client host
Secure Web-Based Systems Fall Test 1
 Secure Web-Based Systems Fall 2016 CS 4339 Professor L. Longpré Name: Directions: Test 1 This test is closed book and closed notes. However, you may consult the special cheat sheet provided to you with
Secure Web-Based Systems Fall 2016 CS 4339 Professor L. Longpré Name: Directions: Test 1 This test is closed book and closed notes. However, you may consult the special cheat sheet provided to you with
Server-side web security (part 2 - attacks and defences)
 Server-side web security (part 2 - attacks and defences) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Basic injections $query = "SELECT name, lastname,
Server-side web security (part 2 - attacks and defences) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Basic injections $query = "SELECT name, lastname,
PHP: Databases and Classes. CS174. Chris Pollett. Sep 29, 2008.
 PHP: Databases and Classes. CS174. Chris Pollett. Sep 29, 2008. Outline. Databases. Classes. Connecting to MySQL from PHP. To start a connect to a MySQL database one can issue the command: $db = mysql_connect();
PHP: Databases and Classes. CS174. Chris Pollett. Sep 29, 2008. Outline. Databases. Classes. Connecting to MySQL from PHP. To start a connect to a MySQL database one can issue the command: $db = mysql_connect();
In this exercise you will practice some more SQL queries. First let s practice queries on a single table.
 More SQL queries In this exercise you will practice some more SQL queries. First let s practice queries on a single table. 1. Download SQL_practice.accdb to your I: drive. Launch Access 2016 and open the
More SQL queries In this exercise you will practice some more SQL queries. First let s practice queries on a single table. 1. Download SQL_practice.accdb to your I: drive. Launch Access 2016 and open the
Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion
 IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
I n p u t. This time. Security. Software. sanitization ); drop table slides. Continuing with. Getting insane with. New attacks and countermeasures:
 This time Continuing with Software Security Getting insane with I n p u t sanitization ); drop table slides New attacks and countermeasures: SQL injection Background on web architectures A very basic web
This time Continuing with Software Security Getting insane with I n p u t sanitization ); drop table slides New attacks and countermeasures: SQL injection Background on web architectures A very basic web
WEB SECURITY: SQL INJECTION
 WEB SECURITY: SQL INJECTION CMSC 414 FEB 15 2018 A very basic web architecture Client Server A very basic web architecture Client Server A very basic web architecture Client Server A very basic web architecture
WEB SECURITY: SQL INJECTION CMSC 414 FEB 15 2018 A very basic web architecture Client Server A very basic web architecture Client Server A very basic web architecture Client Server A very basic web architecture
Overview of MySQL Structure and Syntax [2]
![Overview of MySQL Structure and Syntax [2] Overview of MySQL Structure and Syntax [2]](/thumbs/81/84702958.jpg) PHP PHP MySQL Database Overview of MySQL Structure and Syntax [2] MySQL is a relational database system, which basically means that it can store bits of information in separate areas and link those areas
PHP PHP MySQL Database Overview of MySQL Structure and Syntax [2] MySQL is a relational database system, which basically means that it can store bits of information in separate areas and link those areas
LAMP Apps. Overview. Learning Outcomes: At the completion of the lab you should be able to:
 LAMP Apps Overview This lab walks you through using Linux, Apache, MySQL and PHP (LAMP) to create simple, yet very powerful PHP applications connected to a MySQL database. For developers using Windows,
LAMP Apps Overview This lab walks you through using Linux, Apache, MySQL and PHP (LAMP) to create simple, yet very powerful PHP applications connected to a MySQL database. For developers using Windows,
You can use Dreamweaver to build master and detail Web pages, which
 Chapter 1: Building Master and Detail Pages In This Chapter Developing master and detail pages at the same time Building your master and detail pages separately Putting together master and detail pages
Chapter 1: Building Master and Detail Pages In This Chapter Developing master and detail pages at the same time Building your master and detail pages separately Putting together master and detail pages
Database-Connection Libraries. Java Database Connectivity PHP
 Database-Connection Libraries Call-Level Interface Java Database Connectivity PHP 1 An Aside: SQL Injection SQL queries are often constructed by programs. These queries may take constants from user input.
Database-Connection Libraries Call-Level Interface Java Database Connectivity PHP 1 An Aside: SQL Injection SQL queries are often constructed by programs. These queries may take constants from user input.
IELM 511 Information Systems Design Labs 5 and 6. DB creation and Population
 IELM 511 Information Systems Design Labs 5 and 6. DB creation and Population In this lab, your objective is to learn the basics of creating and managing a DB system. One way to interact with the DBMS (MySQL)
IELM 511 Information Systems Design Labs 5 and 6. DB creation and Population In this lab, your objective is to learn the basics of creating and managing a DB system. One way to interact with the DBMS (MySQL)
SQL Data Definition Language: Create and Change the Database Ray Lockwood
 Introductory SQL SQL Data Definition Language: Create and Change the Database Pg 1 SQL Data Definition Language: Create and Change the Database Ray Lockwood Points: DDL statements create and alter the
Introductory SQL SQL Data Definition Language: Create and Change the Database Pg 1 SQL Data Definition Language: Create and Change the Database Ray Lockwood Points: DDL statements create and alter the
Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary Attack
 P3 - Explain the security risks and protection mechanisms involved in website performance Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary
P3 - Explain the security risks and protection mechanisms involved in website performance Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary
COMP284 Scripting Languages Lecture 13: PHP (Part 5) Handouts
 COMP284 Scripting Languages Lecture 13: PHP (Part 5) Handouts Ullrich Hustadt Department of Computer Science School of Electrical Engineering, Electronics, and Computer Science University of Liverpool
COMP284 Scripting Languages Lecture 13: PHP (Part 5) Handouts Ullrich Hustadt Department of Computer Science School of Electrical Engineering, Electronics, and Computer Science University of Liverpool
SQL stands for Structured Query Language. SQL lets you access and manipulate databases
 CMPSC 117: WEB DEVELOPMENT SQL stands for Structured Query Language SQL lets you access and manipulate databases SQL is an ANSI (American National Standards Institute) standard 1 SQL can execute queries
CMPSC 117: WEB DEVELOPMENT SQL stands for Structured Query Language SQL lets you access and manipulate databases SQL is an ANSI (American National Standards Institute) standard 1 SQL can execute queries
Database-Connection Libraries
 Database-Connection Libraries CALL-LEVEL INTERFACE JAVA DATABASE CONNECTIVITY PHP PEAR/DB 1 An Aside: SQL Injection SQL queries are often constructed by programs. These queries may take constants from
Database-Connection Libraries CALL-LEVEL INTERFACE JAVA DATABASE CONNECTIVITY PHP PEAR/DB 1 An Aside: SQL Injection SQL queries are often constructed by programs. These queries may take constants from
Web Programming. Dr Walid M. Aly. Lecture 10 PHP. lec10. Web Programming CS433/CS614 22:32. Dr Walid M. Aly
 Web Programming Lecture 10 PHP 1 Purpose of Server-Side Scripting database access Web page can serve as front-end to a database Ømake requests from browser, Øpassed on to Web server, Øcalls a program to
Web Programming Lecture 10 PHP 1 Purpose of Server-Side Scripting database access Web page can serve as front-end to a database Ømake requests from browser, Øpassed on to Web server, Øcalls a program to
APLIKACJE INTERNETOWE 8 PHP WYKORZYSTANIE BAZY DANYCH MYSQL
 APLIKACJE INTERNETOWE 8 PHP WYKORZYSTANIE BAZY DANYCH MYSQL PLAN PREZENTACJI Bazy danych w PHP Połączenie z bazą danych Zamknięcie połączenie Tworzenie bazy danych Tworzenie tabeli Operacje na tabelach
APLIKACJE INTERNETOWE 8 PHP WYKORZYSTANIE BAZY DANYCH MYSQL PLAN PREZENTACJI Bazy danych w PHP Połączenie z bazą danych Zamknięcie połączenie Tworzenie bazy danych Tworzenie tabeli Operacje na tabelach
Book IX. Developing Applications Rapidly
 Book IX Developing Applications Rapidly Contents at a Glance Chapter 1: Building Master and Detail Pages Chapter 2: Creating Search and Results Pages Chapter 3: Building Record Insert Pages Chapter 4:
Book IX Developing Applications Rapidly Contents at a Glance Chapter 1: Building Master and Detail Pages Chapter 2: Creating Search and Results Pages Chapter 3: Building Record Insert Pages Chapter 4:
This lecture. PHP tags
 This lecture Databases I This covers the (absolute) basics of and how to connect to a database using MDB2. (GF Royle 2006-8, N Spadaccini 2008) I 1 / 24 (GF Royle 2006-8, N Spadaccini 2008) I 2 / 24 What
This lecture Databases I This covers the (absolute) basics of and how to connect to a database using MDB2. (GF Royle 2006-8, N Spadaccini 2008) I 1 / 24 (GF Royle 2006-8, N Spadaccini 2008) I 2 / 24 What
Lecture 17. Monday, November 17, 2014
 Lecture 17 Monday, November 17, 2014 DELIMITER So far this semester, we ve used ; to send all of our SQL statements However, when we define routines that use SQL statements in them, it can make distinguishing
Lecture 17 Monday, November 17, 2014 DELIMITER So far this semester, we ve used ; to send all of our SQL statements However, when we define routines that use SQL statements in them, it can make distinguishing
Simple sets of data can be expressed in a simple table, much like a
 Chapter 1: Building Master and Detail Pages In This Chapter Developing master and detail pages at the same time Building your master and detail pages separately Putting together master and detail pages
Chapter 1: Building Master and Detail Pages In This Chapter Developing master and detail pages at the same time Building your master and detail pages separately Putting together master and detail pages
Databases PHP I. (GF Royle, N Spadaccini ) PHP I 1 / 24
 Databases PHP I (GF Royle, N Spadaccini 2006-2010) PHP I 1 / 24 This lecture This covers the (absolute) basics of PHP and how to connect to a database using MDB2. (GF Royle, N Spadaccini 2006-2010) PHP
Databases PHP I (GF Royle, N Spadaccini 2006-2010) PHP I 1 / 24 This lecture This covers the (absolute) basics of PHP and how to connect to a database using MDB2. (GF Royle, N Spadaccini 2006-2010) PHP
SQL Injection Attack Lab
 SEED Labs SQL Injection Attack Lab 1 SQL Injection Attack Lab Copyright 2006-2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation
SEED Labs SQL Injection Attack Lab 1 SQL Injection Attack Lab Copyright 2006-2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation
Go to SQA Academy the website address is
 Joining a course on the SQA Academy You may find it useful to print out this document for reference. There are two steps to joining an SQA Academy course. First you need an account with the SQA Academy,
Joining a course on the SQA Academy You may find it useful to print out this document for reference. There are two steps to joining an SQA Academy course. First you need an account with the SQA Academy,
Professional PHP for working with MySQL
 Chapter 19 Professional PHP for working with MySQL PDO (PHP Data Objects) Pros Is included with PHP 5.1 and later and available for 5.0. Provides an object-oriented interface. Provides a consistent interface
Chapter 19 Professional PHP for working with MySQL PDO (PHP Data Objects) Pros Is included with PHP 5.1 and later and available for 5.0. Provides an object-oriented interface. Provides a consistent interface
COMP 250. Lecture 27. hashing. Nov. 10, 2017
 COMP 250 Lecture 27 hashing Nov. 10, 2017 1 RECALL Map keys (type K) values (type V) Each (key, value) pairs is an entry. For each key, there is at most one value. 2 RECALL Special Case keys are unique
COMP 250 Lecture 27 hashing Nov. 10, 2017 1 RECALL Map keys (type K) values (type V) Each (key, value) pairs is an entry. For each key, there is at most one value. 2 RECALL Special Case keys are unique
COMP519: Web Programming Autumn 2015
 COMP519: Web Programming Autumn 2015 In the next lectures you will learn What is SQL How to access mysql database How to create a basic mysql database How to use some basic queries How to use PHP and mysql
COMP519: Web Programming Autumn 2015 In the next lectures you will learn What is SQL How to access mysql database How to create a basic mysql database How to use some basic queries How to use PHP and mysql
CS 112 Project Assignment: Visual Password
 CS 112 Project Assignment: Visual Password Instructor: Dan Fleck Overview In this project you will use Python to implement a visual password system. In the industry today there is ongoing research about
CS 112 Project Assignment: Visual Password Instructor: Dan Fleck Overview In this project you will use Python to implement a visual password system. In the industry today there is ongoing research about
Eat (we provide) link. Eater. Goal: Eater(Self) == Self()
 15-251: Great Theoretical Ideas Guru: Yinmeng Zhang Assignment 12 Due: December 6, 2005 1 Reading Comprehension (0 points) Read the accompanying handout containing Ken Thompson s Turing Award Lecture,
15-251: Great Theoretical Ideas Guru: Yinmeng Zhang Assignment 12 Due: December 6, 2005 1 Reading Comprehension (0 points) Read the accompanying handout containing Ken Thompson s Turing Award Lecture,
Mysql Tutorial Create Database Username Password Through Phpmyadmin
 Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
IERG 4210 Tutorial 07. Securing web page (I): login page and admin user authentication Shizhan Zhu
 IERG 4210 Tutorial 07 Securing web page (I): login page and admin user authentication Shizhan Zhu Content for today Phase 4 preview From now please pay attention to the security issue of your website This
IERG 4210 Tutorial 07 Securing web page (I): login page and admin user authentication Shizhan Zhu Content for today Phase 4 preview From now please pay attention to the security issue of your website This
Lecture 05 I/O statements Printf, Scanf Simple statements, Compound statements
 Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 05 I/O statements Printf, Scanf Simple
Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 05 I/O statements Printf, Scanf Simple
SchoolBooking LDAP Integration Guide
 SchoolBooking LDAP Integration Guide Before you start This guide has been written to help you configure SchoolBooking to connect to your LDAP server. Please treat this document as a reference guide, your
SchoolBooking LDAP Integration Guide Before you start This guide has been written to help you configure SchoolBooking to connect to your LDAP server. Please treat this document as a reference guide, your
CSCE 548 Building Secure Software SQL Injection Attack
 CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
Chapter 6 Part2: Manipulating MySQL Databases with PHP
 IT215 Web Programming 1 Chapter 6 Part2: Manipulating MySQL Databases with PHP Jakkrit TeCho, Ph.D. Business Information Technology (BIT), Maejo University Phrae Campus Objectives In this chapter, you
IT215 Web Programming 1 Chapter 6 Part2: Manipulating MySQL Databases with PHP Jakkrit TeCho, Ph.D. Business Information Technology (BIT), Maejo University Phrae Campus Objectives In this chapter, you
CSE361 Web Security. Attacks against the server-side of web applications. Nick Nikiforakis
 CSE361 Web Security Attacks against the server-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Threat model In these scenarios: The server is benign The client is malicious The client
CSE361 Web Security Attacks against the server-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Threat model In these scenarios: The server is benign The client is malicious The client
Perl Dbi Insert Hash Into Table >>>CLICK HERE<<<
 Perl Dbi Insert Hash Into Table How to insert values in PostgreSQL faster than insert() value() functions? At the moment I am using DBI in Perl to connect to IQ(Sybase) then load the values into a hash,
Perl Dbi Insert Hash Into Table How to insert values in PostgreSQL faster than insert() value() functions? At the moment I am using DBI in Perl to connect to IQ(Sybase) then load the values into a hash,
Using PHP with MYSQL
 Using PHP with MYSQL PHP & MYSQL So far you've learned the theory behind relational databases and worked directly with MySQL through the mysql command-line tool. Now it's time to get your PHP scripts talking
Using PHP with MYSQL PHP & MYSQL So far you've learned the theory behind relational databases and worked directly with MySQL through the mysql command-line tool. Now it's time to get your PHP scripts talking
Please write your name and username here legibly: C212/A592 6W2 Summer 2017 Early Evaluation Exam: Fundamental Programming Structures in Java
 Please write your name and username here legibly: C212/A592 6W2 Summer 2017 Early Evaluation Exam: Fundamental Programming Structures in Java Use BigDecimal (a class defined in package java.math) to write
Please write your name and username here legibly: C212/A592 6W2 Summer 2017 Early Evaluation Exam: Fundamental Programming Structures in Java Use BigDecimal (a class defined in package java.math) to write
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur
 Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 15 Branching : IF ELSE Statement We are looking
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 15 Branching : IF ELSE Statement We are looking
2017 Accenture. All Rights Reserved. PWM USER GUIDE
 PWM USER GUIDE There are three operations that can be performed through PWM. These are: Operations Change Password Forgot Password First Time User Usage When the user remembers their password but still
PWM USER GUIDE There are three operations that can be performed through PWM. These are: Operations Change Password Forgot Password First Time User Usage When the user remembers their password but still
Chapter. Accessing MySQL Databases Using PHP
 Chapter 12 Accessing MySQL Databases Using PHP 150 Essential PHP fast Introduction In the previous chapter we considered how to create databases using MySQL. While this is useful, it does not enable us
Chapter 12 Accessing MySQL Databases Using PHP 150 Essential PHP fast Introduction In the previous chapter we considered how to create databases using MySQL. While this is useful, it does not enable us
Your (printed!) Name: CS 1803 Exam 3. Grading TA / Section: Monday, Nov. 22th, 2010
 Your (printed!) Name: CS 1803 Exam 3 Grading TA / Section: Monday, Nov. 22th, 2010 INTEGRITY: By taking this exam, you pledge that this is your work and you have neither given nor received inappropriate
Your (printed!) Name: CS 1803 Exam 3 Grading TA / Section: Monday, Nov. 22th, 2010 INTEGRITY: By taking this exam, you pledge that this is your work and you have neither given nor received inappropriate
COM1004 Web and Internet Technology
 COM1004 Web and Internet Technology When a user submits a web form, how do we save the information to a database? How do we retrieve that data later? ID NAME EMAIL MESSAGE TIMESTAMP 1 Mike mike@dcs Hi
COM1004 Web and Internet Technology When a user submits a web form, how do we save the information to a database? How do we retrieve that data later? ID NAME EMAIL MESSAGE TIMESTAMP 1 Mike mike@dcs Hi
COMP102: Introduction to Databases, 23
 COMP102: Introduction to Databases, 23 Dr Muhammad Sulaiman Khan Department of Computer Science University of Liverpool U.K. 04 April, 2011 Programming with SQL Specific topics for today: Client/Server
COMP102: Introduction to Databases, 23 Dr Muhammad Sulaiman Khan Department of Computer Science University of Liverpool U.K. 04 April, 2011 Programming with SQL Specific topics for today: Client/Server
Lecture 6: More Arrays & HTML Forms. CS 383 Web Development II Monday, February 12, 2018
 Lecture 6: More Arrays & HTML Forms CS 383 Web Development II Monday, February 12, 2018 Lambdas You may have encountered a lambda (sometimes called anonymous functions) in other programming languages The
Lecture 6: More Arrays & HTML Forms CS 383 Web Development II Monday, February 12, 2018 Lambdas You may have encountered a lambda (sometimes called anonymous functions) in other programming languages The
Options. Real SQL Programming 1. Stored Procedures. Embedded SQL
 Real 1 Options We have seen only how SQL is used at the generic query interface an environment where we sit at a terminal and ask queries of a database. Reality is almost always different: conventional
Real 1 Options We have seen only how SQL is used at the generic query interface an environment where we sit at a terminal and ask queries of a database. Reality is almost always different: conventional
Quick Start Manual for Mechanical TA
 Quick Start Manual for Mechanical TA Chris Thornton cwthornt@cs.ubc.ca August 18, 2013 Contents 1 Quick Install 1 2 Creating Courses 2 3 User Management 2 4 Assignment Management 3 4.1 Peer Review Assignment
Quick Start Manual for Mechanical TA Chris Thornton cwthornt@cs.ubc.ca August 18, 2013 Contents 1 Quick Install 1 2 Creating Courses 2 3 User Management 2 4 Assignment Management 3 4.1 Peer Review Assignment
Discuss setting up JDBC connectivity. Demonstrate a JDBC program Discuss and demonstrate methods associated with JDBC connectivity
 Objectives Discuss setting up JDBC connectivity. Demonstrate a JDBC program Discuss and demonstrate methods associated with JDBC connectivity Setting Up JDBC Before you can begin to utilize JDBC, you must
Objectives Discuss setting up JDBC connectivity. Demonstrate a JDBC program Discuss and demonstrate methods associated with JDBC connectivity Setting Up JDBC Before you can begin to utilize JDBC, you must
SQL. Often times, in order for us to build the most functional website we can, we depend on a database to store information.
 Often times, in order for us to build the most functional website we can, we depend on a database to store information. If you ve ever used Microsoft Excel or Google Spreadsheets (among others), odds are
Often times, in order for us to build the most functional website we can, we depend on a database to store information. If you ve ever used Microsoft Excel or Google Spreadsheets (among others), odds are
CS352 Lecture - Introduction to SQL
 CS352 Lecture - Introduction to SQL Objectives: last revised September 12, 2002 1. To introduce the SQL language 2. To introduce basic SQL DML operations (select, insert, update, delete, commit, rollback)
CS352 Lecture - Introduction to SQL Objectives: last revised September 12, 2002 1. To introduce the SQL language 2. To introduce basic SQL DML operations (select, insert, update, delete, commit, rollback)
Lecture 4. Wednesday, January 27, 2016
 Lecture 4 Wednesday, January 27, 2016 PHP through Apache Last week, we talked about building command line scripts This week, we will transition to building scripts that will run through the web server,
Lecture 4 Wednesday, January 27, 2016 PHP through Apache Last week, we talked about building command line scripts This week, we will transition to building scripts that will run through the web server,
Lecture 2: Variables & Assignments
 http://www.cs.cornell.edu/courses/cs1110/2018sp Lecture 2: Variables & Assignments (Sections 2.1-2.3,2.5) CS 1110 Introduction to Computing Using Python [E. Andersen, A. Bracy, D. Gries, L. Lee, S. Marschner,
http://www.cs.cornell.edu/courses/cs1110/2018sp Lecture 2: Variables & Assignments (Sections 2.1-2.3,2.5) CS 1110 Introduction to Computing Using Python [E. Andersen, A. Bracy, D. Gries, L. Lee, S. Marschner,
web.py Tutorial Tom Kelliher, CS 317 This tutorial is the tutorial from the web.py web site, with a few revisions for our local environment.
 web.py Tutorial Tom Kelliher, CS 317 1 Acknowledgment This tutorial is the tutorial from the web.py web site, with a few revisions for our local environment. 2 Starting So you know Python and want to make
web.py Tutorial Tom Kelliher, CS 317 1 Acknowledgment This tutorial is the tutorial from the web.py web site, with a few revisions for our local environment. 2 Starting So you know Python and want to make
PHP: Hypertext Preprocessor. A tutorial Introduction
 PHP: Hypertext Preprocessor A tutorial Introduction Introduction PHP is a server side scripting language Primarily used for generating dynamic web pages and providing rich web services PHP5 is also evolving
PHP: Hypertext Preprocessor A tutorial Introduction Introduction PHP is a server side scripting language Primarily used for generating dynamic web pages and providing rich web services PHP5 is also evolving
Today s Goals. CSCI 2910 Client/Server-Side Programming. More on Querying Records. Conditions. Conditions (continued) Conditions (continued)
 CSCI 2910 Client/Server-Side Programming Topic: More on SQL Reading: PHP and MySQL, pp. 152 168 Today s Goals Today s lecture will improve our use of the SQL query "SELECT" by using: WHERE, BETWEEN, IN,
CSCI 2910 Client/Server-Side Programming Topic: More on SQL Reading: PHP and MySQL, pp. 152 168 Today s Goals Today s lecture will improve our use of the SQL query "SELECT" by using: WHERE, BETWEEN, IN,
CSC 405 Computer Security. Web Security
 CSC 405 Computer Security Web Security Alexandros Kapravelos akaprav@ncsu.edu (Derived from slides by Giovanni Vigna and Adam Doupe) 1 source: https://xkcd.com/327/ 2 source: https://xkcd.com/327/ 3 source:
CSC 405 Computer Security Web Security Alexandros Kapravelos akaprav@ncsu.edu (Derived from slides by Giovanni Vigna and Adam Doupe) 1 source: https://xkcd.com/327/ 2 source: https://xkcd.com/327/ 3 source:
ATMS ACTION TRACKING MANAGEMENT SYSTEM. Quick Start Guide. The ATMS dev team
 ATMS ACTION TRACKING MANAGEMENT SYSTEM Quick Start Guide The ATMS dev team Contents What is ATMS?... 2 How does ATMS work?... 2 I get it, now where can I find more info?... 2 What s next?... 2 Welcome
ATMS ACTION TRACKING MANAGEMENT SYSTEM Quick Start Guide The ATMS dev team Contents What is ATMS?... 2 How does ATMS work?... 2 I get it, now where can I find more info?... 2 What s next?... 2 Welcome
Enterprise Reporting -- APEX
 Quick Reference Enterprise Reporting -- APEX This Quick Reference Guide documents Oracle Application Express (APEX) as it relates to Enterprise Reporting (ER). This is not an exhaustive APEX documentation
Quick Reference Enterprise Reporting -- APEX This Quick Reference Guide documents Oracle Application Express (APEX) as it relates to Enterprise Reporting (ER). This is not an exhaustive APEX documentation
Vanguard Secure Service (VSES) User Guide
 Vanguard Secure Email Service (VSES) User Guide Enterprise Security and Fraud October 20, 2017 Contents Guide for Users of Secure Email From Vanguard 1 View Secure Email 1 New Registration 3 Compose a
Vanguard Secure Email Service (VSES) User Guide Enterprise Security and Fraud October 20, 2017 Contents Guide for Users of Secure Email From Vanguard 1 View Secure Email 1 New Registration 3 Compose a
Installing Joomla
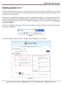 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
How to set up your wireless network
 How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
ONLINE BULK SEED SALE CERTIFICATE INSTRUCTIONS. Welcome to Seed Hub! (SM)
 ONLINE BULK SEED SALE CERTIFICATE INSTRUCTIONS 1. SET UP PUREHARVEST ACCOUNT Contact the MCIA office to set up a user name and password for the Pureharvest database. It is best to do this a couple of days
ONLINE BULK SEED SALE CERTIFICATE INSTRUCTIONS 1. SET UP PUREHARVEST ACCOUNT Contact the MCIA office to set up a user name and password for the Pureharvest database. It is best to do this a couple of days
Locate your Advanced Tools and Applications
 MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
Lab 6. Out: Wednesday 9 March 2005
 CS034 Intro to Systems Programming Doeppner & Van Hentenryck What you ll learn. Lab 6 Out: Wednesday 9 March 2005 Modern C++ comes with a powerful template library, the Standard Template Library, or STL.
CS034 Intro to Systems Programming Doeppner & Van Hentenryck What you ll learn. Lab 6 Out: Wednesday 9 March 2005 Modern C++ comes with a powerful template library, the Standard Template Library, or STL.
Creating the Data Layer
 Creating the Data Layer When interacting with any system it is always useful if it remembers all the settings and changes between visits. For example, Facebook has the details of your login and any conversations
Creating the Data Layer When interacting with any system it is always useful if it remembers all the settings and changes between visits. For example, Facebook has the details of your login and any conversations
Quick Start. for Users. Online Banking
 Quick Start for Users Online Banking Table of Contents Getting Started... 1 Multifactor Authentication.... 2 Log In.... 3 Reset Your Password.... 4 Reset Your Security Question... 6 Change Your Phone Number....
Quick Start for Users Online Banking Table of Contents Getting Started... 1 Multifactor Authentication.... 2 Log In.... 3 Reset Your Password.... 4 Reset Your Security Question... 6 Change Your Phone Number....
Chapter 7 PHP Files & MySQL Databases
 Chapter 7 PHP Files & MySQL Databases At the end of the previous chapter, a simple calendar was displayed with an appointment. This demonstrated again how forms can be used to pass data from one page to
Chapter 7 PHP Files & MySQL Databases At the end of the previous chapter, a simple calendar was displayed with an appointment. This demonstrated again how forms can be used to pass data from one page to
Side-channel attacks (and blind SQL injections)
 Side-channel attacks (and blind SQL injections) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction It is often the case that applications have
Side-channel attacks (and blind SQL injections) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction It is often the case that applications have
