Agenda. Simple precursor to Sessions. Sessions via Cookies in Hapi
|
|
|
- Bridget Patrick
- 5 years ago
- Views:
Transcription
1 Sessions in Hapi
2 Agenda Simple precursor to Sessions Sessions via Cookies in Hapi
3 Sharing Information across an App Before server launches, bind an array of donations to the server object. Most commonly used to share database connection information index.js server.bind({ donations: [], });
4 Sharing Information across an App This donations array can subsequently be accessed in all handlers. Each handler can read/ write to this shared data structure All users donations held in effectively a global array in memory index.js server.bind({ donations: [], }); exports.donate = { handler: function (request, reply) { const data = request.payload; this.donations.push(data); reply.redirect('/report'); }, }; donations.js
5 Separating out User Donations Try to keep track of all users, the current user all donations. index.js server.bind({ currentuser: {}, users: {}, donations: [], });
6 Registering & Authenticating Users exports.register = { handler: function (request, reply) { const user = request.payload; this.users[user. ] = user; reply.redirect('/login'); }, }; exports.authenticate = { handler: function (request, reply) { const user = request.payload; if ((user. in this.users) && (user.password === this.users[user. ].password)) { this.currentuser = this.users[user. ]; reply.redirect('/home'); } else { reply.redirect('/signup'); } }, }; Record user object at registration Record current user at login accounts.js
7 Creating & Listing Donations exports.donate = { handler: function (request, reply) { let data = request.payload; data.donor = this.currentuser; this.donations.push(data); reply.redirect('/report'); }, }; Record donation + donor when creating donation donations.js
8 exports.report = { handler: function (request, reply) { reply.view('report', { title: 'Donations to Date', donations: this.donations, }); }, }; donations.js Send all donations to the view <tbody> {{#each donations}} <tr> <td> {{amount}} </td> <td> {{method}} </td> <td> {{donor.firstname}} {{donor.lastname}} </td> </tr> {{/each}} </tbody> donationlist.hbs
9 Summary Current approach - brittle and not scalable Server.bind to maintain global data Store user + donation data structures Revised Approach Migrate to more robust, cookie based session management Introduce proper persistence capability (a database)
10 Sessions HTTP is described as a stateless protocol - every new request is just as anonymous as the last. This sounds very unhelpful for a protocol that powers websites, where users expect to be remembered as they go to page to page. Cookies to the Rescue: A request comes to a web application with a cookie using the cookie the server can look up information about the user, either from the cookie itself or from server-side storage. It can then forget all about them for a while, until the next request and the same process continues over for every request.
11 hapi-auth-cookie A Hapi Plugin to manage cookie access and management. Must be downloaded, installed and registered (like all plugins)
12 hapi-auth-cookie Installation & Registration npm install command package.json updated Register in index.js
13 hapi-auth-cookie Configuration Set an auth strategy before application starts Specifies range or parameters, including: password for securing cookie cookie name time to live (expiry) server.auth.strategy('standard', 'cookie', { password: 'secretpasswordnotrevealedtoanyone', cookie: 'donation-cookie', ttl: 24 * 60 * 60 * 1000, });
14 hapi-auth-cookie Configuration By default hapi-auth-cookie will only allow the cookie to be transferred over a secure TLS/ SSLconnection. This may not be convenient during development so you can set the issecure option to false. Set standard as the default strategy for all routes server.auth.strategy('standard', 'cookie', { password: 'secretpasswordnotrevealedtoanyone', cookie: 'donation-cookie', issecure: false, ttl: 24 * 60 * 60 * 1000, }); server.auth.default({ strategy: 'standard', });
15 Annotating Routes All routes are now guarded by default, cookie based authentication mechanism Any attempt to visit a route will be rejected unless valid cookie detected. Some routes need to be available (to signup or login for instance) These routes must specifically disable auth mechanism server.auth.default({ strategy: 'standard', }); exports.signup = { auth: false, handler: function (request, reply) { reply.view('signup', { title: 'Sign up for Donations' }); }, }; exports.login = { auth: false, handler: function (request, reply) { reply.view('login', { title: 'Login to Donations' }); }, };
16 Setting the Cookie Set the cookie if correct user credentials presented. request.cookieauth.set({ loggedin: true, loggedinuser: user. , }); exports.authenticate = { auth: false, handler: function (request, reply) { const user = request.payload; if ((user. in this.users) && (user.password === this.users[user. ].password)) { request.cookieauth.set({ loggedin: true, loggedinuser: user. , }); reply.redirect('/home'); } else { reply.redirect('/signup'); } }, };
17 Reading the Cookie If cookie set, it can be read back in any handler We are storing logged in users in this example Use this to look up user details in some storage infrastructure (database). request.cookieauth.set({ loggedin: true, loggedinuser: user. , }); const donor = request.auth.credentials.loggedinuser; exports.donate = { handler: function (request, reply) { let data = request.payload; const donor = request.auth.credentials.loggedinuser; data.donor = this.users[donor ]; this.donations.push(data); reply.redirect('/report'); }, };
18 Clearing the Cookie Cookie deleted Any attempt to access protected routes rejected exports.logout = { auth: false, handler: function (request, reply) { request.cookieauth.clear(); reply.redirect('/'); }, };
19 Redirects If route protected, and cookie deleted/ timeout Redirect to login server.auth.strategy('standard', 'cookie', { password: 'secretpasswordnotrevealedtoanyone', cookie: 'donation-cookie', issecure: false, ttl: 24 * 60 * 60 * 1000, redirectto: '/login', });
20 Cookies can be Inspected in Browser
Agenda. JWT Node Libraries. Encoding & Decoding the Tokens. The Authenticate Route. Securing the API with a JWT Strategy. Testing the Secured API
 Secure Donation API Agenda JWT Node Libraries Encoding & Decoding the Tokens The Authenticate Route Securing the API with a JWT Strategy Testing the Secured API hapi-auth-jwt2 jwt.sign(payload, secretorprivatekey,
Secure Donation API Agenda JWT Node Libraries Encoding & Decoding the Tokens The Authenticate Route Securing the API with a JWT Strategy Testing the Secured API hapi-auth-jwt2 jwt.sign(payload, secretorprivatekey,
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How do I sign up for a Canvas account as a parent?
 How do I sign up for a Canvas account as a parent? Parents (Observers) can link their Canvas account to their student's account so they can see assignment dues dates, announcements, and other course content.
How do I sign up for a Canvas account as a parent? Parents (Observers) can link their Canvas account to their student's account so they can see assignment dues dates, announcements, and other course content.
Revised: 08/02/ Click the Start button at bottom left, enter Server Manager in the search box, and select it in the list to open it.
 Mobile App Windows Authentication & SSL Config Revised: 08/02/2017 Job Aid This Job Aid is intended for agency IT staff and explains how to enable Windows Authentication and SSL for your mobile applications
Mobile App Windows Authentication & SSL Config Revised: 08/02/2017 Job Aid This Job Aid is intended for agency IT staff and explains how to enable Windows Authentication and SSL for your mobile applications
Topic 15: Authentication
 Topic 15: Authentication CITS3403 Agile Web Development Getting MEAN with Mongo, Express, Angular and Node, Chapter 11 Semester 1, 2018 Secure web apps Security is a primary concern for anyone developing
Topic 15: Authentication CITS3403 Agile Web Development Getting MEAN with Mongo, Express, Angular and Node, Chapter 11 Semester 1, 2018 Secure web apps Security is a primary concern for anyone developing
BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents
 BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents Definitions... 2 Summary... 2 BIDMC Multi-Factor Authentication Enrollment... 3 Common Multi-Factor Authentication Enrollment Issues...
BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents Definitions... 2 Summary... 2 BIDMC Multi-Factor Authentication Enrollment... 3 Common Multi-Factor Authentication Enrollment Issues...
CA SSO Cloud-Enabled with SSO/Rest
 CA SSO Cloud-Enabled with SSO/Rest SSO/Rest Solves Many Challenges Applications in the Cloud AJAX / Mobile / Thick Client Application Integration "Agent-less" Infrastructure Server-side Application Integration
CA SSO Cloud-Enabled with SSO/Rest SSO/Rest Solves Many Challenges Applications in the Cloud AJAX / Mobile / Thick Client Application Integration "Agent-less" Infrastructure Server-side Application Integration
Using Microsoft Azure Active Directory MFA as SAML IdP with Pulse Connect Secure. Deployment Guide
 Using Microsoft Azure Active Directory MFA as SAML IdP with Pulse Connect Secure Deployment Guide v1.0 May 2018 Introduction This document describes how to set up Pulse Connect Secure for SP-initiated
Using Microsoft Azure Active Directory MFA as SAML IdP with Pulse Connect Secure Deployment Guide v1.0 May 2018 Introduction This document describes how to set up Pulse Connect Secure for SP-initiated
COMP 2406: Fundamentals of Web Applications. Fall 2013 Mid-Term Exam Solutions
 COMP 2406: Fundamentals of Web Applications Fall 2013 Mid-Term Exam Solutions 1. ( false ) HTTP cookies are only sent to a web server when explicitly requested. 2. ( false ) Cookies are normally parsed
COMP 2406: Fundamentals of Web Applications Fall 2013 Mid-Term Exam Solutions 1. ( false ) HTTP cookies are only sent to a web server when explicitly requested. 2. ( false ) Cookies are normally parsed
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
Xerox Connect App for Blackboard
 Xerox Connect App for Blackboard Information Assurance Disclosure Additional information, if needed, on one or more lines Month 00, 0000 2018 Xerox Corporation. All rights reserved. Xerox,
Xerox Connect App for Blackboard Information Assurance Disclosure Additional information, if needed, on one or more lines Month 00, 0000 2018 Xerox Corporation. All rights reserved. Xerox,
The Modern Web Access Management Platform from on-premises to the Cloud
 The Modern Web Access Management Platform from on-premises to the Cloud Single Sign On, Access Controls, Session Management and how to use Access Management to protect applications both on premises and
The Modern Web Access Management Platform from on-premises to the Cloud Single Sign On, Access Controls, Session Management and how to use Access Management to protect applications both on premises and
Serverless Microservices Are The New Black. Lorna Mitchell, IBM
 Serverless Microservices Are The New Black Lorna Mitchell, IBM Serverless FaaS: Functions as a Service write a function (many languages supported) deploy it to the cloud (Lambda, Cloud Functions, etc)
Serverless Microservices Are The New Black Lorna Mitchell, IBM Serverless FaaS: Functions as a Service write a function (many languages supported) deploy it to the cloud (Lambda, Cloud Functions, etc)
qrlogin Developer s Guide Version 1.2
 qrlogin Developer s Guide Version 1.2 Table of contents qrlogin. System description 2 How to Embed System on Your Web Source 2 Main Functions 2 Strategy to Embed qrlogin System on Web Source 2 Mode of
qrlogin Developer s Guide Version 1.2 Table of contents qrlogin. System description 2 How to Embed System on Your Web Source 2 Main Functions 2 Strategy to Embed qrlogin System on Web Source 2 Mode of
SPOOFING. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
Client 2. Authentication 5
 Pipeline Pilot Web Port Support Guide April 2011 Contents Requirements 2 Requirements 2 Server 2 Client 2 Web Port Access 3 Authentication 5 Introduction Pipeline Pilot Web Port is a web-based application
Pipeline Pilot Web Port Support Guide April 2011 Contents Requirements 2 Requirements 2 Server 2 Client 2 Web Port Access 3 Authentication 5 Introduction Pipeline Pilot Web Port is a web-based application
OAuth 2 and Native Apps
 OAuth 2 and Native Apps Flows While all OAuth 2 flows can be used by native apps, only the user delegation flows will be considered in this document: Web Server, User-Agent and Device flows. The Web Server
OAuth 2 and Native Apps Flows While all OAuth 2 flows can be used by native apps, only the user delegation flows will be considered in this document: Web Server, User-Agent and Device flows. The Web Server
TopGlobal MB8000 Hotspots Solution
 MB8000 s MB8000 is a mobile/portable wireless communication gateway. It combines the best of Wi-Fi technology and 2.5G/3G mobile communication technology. WISP can deploy their wireless hotspots with MB8000
MB8000 s MB8000 is a mobile/portable wireless communication gateway. It combines the best of Wi-Fi technology and 2.5G/3G mobile communication technology. WISP can deploy their wireless hotspots with MB8000
Guide to your CGIAR Network account Self Service tool
 Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
TireCheck Mobile: Creating a Service Request. This document describes the creation of a service request using the TireCheck Mobile Application.
 TireCheck Mobile: Creating a Service Request This document describes the creation of a service request using the TireCheck Mobile Application. Logging in and Accessing the Service Request Module The Service
TireCheck Mobile: Creating a Service Request This document describes the creation of a service request using the TireCheck Mobile Application. Logging in and Accessing the Service Request Module The Service
etrac ATOM Android App Setup Guide
 etrac ATOM Android App Setup Guide Version: 1.0.0 Published: 10/22/2014 Global DMS, 1555 Bustard Road, Suite 300, Lansdale, PA 19446 2014, All Rights Reserved. Table of Contents Initial Setup... 3 Settings...
etrac ATOM Android App Setup Guide Version: 1.0.0 Published: 10/22/2014 Global DMS, 1555 Bustard Road, Suite 300, Lansdale, PA 19446 2014, All Rights Reserved. Table of Contents Initial Setup... 3 Settings...
Job Aid: Citrix Receiver Upgrade
 January 3, 2018 Job Aid: Citrix Receiver Upgrade Overview We have upgraded the Citrix infrastructure that securely delivers your Citrix applications and desktops. While your applications and desktops are
January 3, 2018 Job Aid: Citrix Receiver Upgrade Overview We have upgraded the Citrix infrastructure that securely delivers your Citrix applications and desktops. While your applications and desktops are
BI Office. Web Authentication Model Guide Version 6
 Web Authentication Model Guide Version 6 Copyright Pyramid Analytics 2010-2016 Contents 1. Web Authentication Model Overview... 3 A. Basic Authentication Models... 3 B. Windows Authentication Models...
Web Authentication Model Guide Version 6 Copyright Pyramid Analytics 2010-2016 Contents 1. Web Authentication Model Overview... 3 A. Basic Authentication Models... 3 B. Windows Authentication Models...
Accessing Your Payroll Stubs via
 Accessing Your Payroll Stubs via Email Logging On to a Computer within the District: (does not apply to your computer at home) 1) Turn on the computer, if it is not already on. At this screen, press the
Accessing Your Payroll Stubs via Email Logging On to a Computer within the District: (does not apply to your computer at home) 1) Turn on the computer, if it is not already on. At this screen, press the
Automation with Meraki Provisioning API
 DEVNET-2120 Automation with Meraki Provisioning API Courtney M. Batiste, Solutions Architect- Cisco Meraki Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1.
DEVNET-2120 Automation with Meraki Provisioning API Courtney M. Batiste, Solutions Architect- Cisco Meraki Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1.
Checklist for Testing of Web Application
 Checklist for Testing of Web Application Web Testing in simple terms is checking your web application for potential bugs before its made live or before code is moved into the production environment. During
Checklist for Testing of Web Application Web Testing in simple terms is checking your web application for potential bugs before its made live or before code is moved into the production environment. During
All about SAML End-to-end Tableau and OKTA integration
 Welcome # T C 1 8 All about SAML End-to-end Tableau and OKTA integration Abhishek Singh Senior Manager, Regional Delivery Tableau Abhishek Singh Senior Manager Regional Delivery asingh@tableau.com Agenda
Welcome # T C 1 8 All about SAML End-to-end Tableau and OKTA integration Abhishek Singh Senior Manager, Regional Delivery Tableau Abhishek Singh Senior Manager Regional Delivery asingh@tableau.com Agenda
Cookies, sessions and authentication
 Cookies, sessions and authentication TI1506: Web and Database Technology Claudia Hauff! Lecture 7 [Web], 2014/15 1 Course overview [Web] 1. http: the language of Web communication 2. Web (app) design &
Cookies, sessions and authentication TI1506: Web and Database Technology Claudia Hauff! Lecture 7 [Web], 2014/15 1 Course overview [Web] 1. http: the language of Web communication 2. Web (app) design &
FIRST TIME USER GUIDE- 2016
 FIRST TIME USER GUIDE- 2016 COMMODITY TRACKING SYSTEM (CTS) Table of Contents Introduction... 2 Contacts... 2 Steps required Prior To Re-Registering Online With The National Energy Board (NEB):... 3 Become
FIRST TIME USER GUIDE- 2016 COMMODITY TRACKING SYSTEM (CTS) Table of Contents Introduction... 2 Contacts... 2 Steps required Prior To Re-Registering Online With The National Energy Board (NEB):... 3 Become
Authentication in Rails
 Authentication in Rails Aaron Mulder CTO Chariot Solutions Philly on Rails, October 2007 1 Agenda The problem Plugins in Rails, and the (many) solutions acts_as_authenticated Generated Code Custom Code
Authentication in Rails Aaron Mulder CTO Chariot Solutions Philly on Rails, October 2007 1 Agenda The problem Plugins in Rails, and the (many) solutions acts_as_authenticated Generated Code Custom Code
Architecture Assessment Case Study. Single Sign on Approach Document PROBLEM: Technology for a Changing World
 Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
Accessing Insurance Portal/PAS Job Aid Single Sign-On
 Accessing Insurance Portal/PAS Job Aid Single Sign-On Getting Started with Insurance Portal and PAS - Create Desktop Shortcut and Single Sign-On Password Getting Started To Get Started with Insurance Portal
Accessing Insurance Portal/PAS Job Aid Single Sign-On Getting Started with Insurance Portal and PAS - Create Desktop Shortcut and Single Sign-On Password Getting Started To Get Started with Insurance Portal
Oracle Access Manager Administration Interview Questions. Edition.
 Oracle Access Manager Administration Interview Questions Edition contact@k21academy.com 1 Oracle Access Manager Interview Questions Author Oracle ACE, Atul Kumar For any training/consulting requirements
Oracle Access Manager Administration Interview Questions Edition contact@k21academy.com 1 Oracle Access Manager Interview Questions Author Oracle ACE, Atul Kumar For any training/consulting requirements
13241 Woodland Park Road, Suite 400 Herndon, VA USA A U T H O R : E X O S T A R D ATE: M A R C H V E R S I O N : 3.
 SECURE ACCESS MAN AG E R FIRST TIME LOGIN GUIDE A U T H O R : E X O S T A R D ATE: M A R C H 2 0 1 5 V E R S I O N : 3.0 1 S E C U R E A CCESS M A N A G E R SECURE ACCESS MANAGER OVERVIEW... 3 SUMMARY...
SECURE ACCESS MAN AG E R FIRST TIME LOGIN GUIDE A U T H O R : E X O S T A R D ATE: M A R C H 2 0 1 5 V E R S I O N : 3.0 1 S E C U R E A CCESS M A N A G E R SECURE ACCESS MANAGER OVERVIEW... 3 SUMMARY...
Infoblox Authenticated DHCP
 Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Aurelia comes with 2 http client libraries:
 Aurelia Http Http Clients Aurelia comes with 2 http client libraries: aurelia-http-client - A basic HttpClient based on XMLHttpRequest. It supports all HTTP verbs, JSONP and request cancellation. aurelia-fetch-client
Aurelia Http Http Clients Aurelia comes with 2 http client libraries: aurelia-http-client - A basic HttpClient based on XMLHttpRequest. It supports all HTTP verbs, JSONP and request cancellation. aurelia-fetch-client
SSL VPN Web Portal User Guide
 The SSL VPN web portal provides easy access to your organization s web resources via the web browser on your desktop or mobile device. The SSL VPN web portal's responsive interface automatically detects
The SSL VPN web portal provides easy access to your organization s web resources via the web browser on your desktop or mobile device. The SSL VPN web portal's responsive interface automatically detects
Guide for Windows users with Internet Explorer and Firefox
 Velocity@ocbc Guide for Windows users with Internet Explorer and Firefox Version 2.0 070513 1 of 18 Check the Java version 1. Launch a browser and go to http://www.java.com/en/download/installed.jsp?detect=jre
Velocity@ocbc Guide for Windows users with Internet Explorer and Firefox Version 2.0 070513 1 of 18 Check the Java version 1. Launch a browser and go to http://www.java.com/en/download/installed.jsp?detect=jre
GUIDE TO REGISTRATION
 GUIDE TO REGISTRATION May 17, 2011 Revision 1.1 BINGHAM ICT webmaster@binghamuni.edu.ng systemadmin@binghamuni.edu.ng Table of Contents Table of Contents----------------------------------------------------------------------
GUIDE TO REGISTRATION May 17, 2011 Revision 1.1 BINGHAM ICT webmaster@binghamuni.edu.ng systemadmin@binghamuni.edu.ng Table of Contents Table of Contents----------------------------------------------------------------------
Getting Started with Outlook Web App (OWA)
 Getting Started with Outlook Web App (OWA) Office 365 User Guide When first accessing your new Office 365 account, or if you are having any issues with your regular email client, use the below directions
Getting Started with Outlook Web App (OWA) Office 365 User Guide When first accessing your new Office 365 account, or if you are having any issues with your regular email client, use the below directions
I. How to Purchase Cryptfunder CFND Tokens
 I. How to Purchase Cryptfunder CFND Tokens You can participate in the Cryptfunder (CFND) Token Sale by following the steps in this document. Once you have completed the steps, the CFND tokens will automatically
I. How to Purchase Cryptfunder CFND Tokens You can participate in the Cryptfunder (CFND) Token Sale by following the steps in this document. Once you have completed the steps, the CFND tokens will automatically
Guide to Deploying NetScaler as an Active Directory Federation Services Proxy
 Deployment Guide Guide to Deploying NetScaler as an Active Directory Federation Services Proxy Enabling seamless authentication for Office 365 use cases Table of Contents Introduction 3 ADFS proxy deployment
Deployment Guide Guide to Deploying NetScaler as an Active Directory Federation Services Proxy Enabling seamless authentication for Office 365 use cases Table of Contents Introduction 3 ADFS proxy deployment
MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017
 MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017 General Contents General... 3 1 Requirements... 4 1.1 Citrix client... 4 1.2 Citrix NetScaler (Access Gateway) plugin... 4 1.3 SMS Passcode...
MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017 General Contents General... 3 1 Requirements... 4 1.1 Citrix client... 4 1.2 Citrix NetScaler (Access Gateway) plugin... 4 1.3 SMS Passcode...
DATACENTER MANAGEMENT Goodbye ADFS, Hello Modern Authentication! Osman Akagunduz
 Goodbye ADFS, Hello Modern Authentication! Osman Akagunduz Osman Akagunduz Consultant @ InSpark Microsoft Country Partner Of The Year Twitter: @Osman_Akagunduz What s in this session The role of Azure
Goodbye ADFS, Hello Modern Authentication! Osman Akagunduz Osman Akagunduz Consultant @ InSpark Microsoft Country Partner Of The Year Twitter: @Osman_Akagunduz What s in this session The role of Azure
Table of Contents. Single Sign On 1
 Table of Contents Table of Contents Single Sign On SAML Authentication Using SAML SSO Authentication Setting up SAML SSO Authentication Configuring OneLogin as an Identity Provider LDAP Authentication
Table of Contents Table of Contents Single Sign On SAML Authentication Using SAML SSO Authentication Setting up SAML SSO Authentication Configuring OneLogin as an Identity Provider LDAP Authentication
Qualys SAML 2.0 Single Sign-On (SSO) Technical Brief
 Qualys SAML 2.0 Single Sign-On (SSO) Technical Brief Qualys provides its customers the option to use SAML 2.0 Single SignOn (SSO) authentication with their Qualys subscription. When implemented, Qualys
Qualys SAML 2.0 Single Sign-On (SSO) Technical Brief Qualys provides its customers the option to use SAML 2.0 Single SignOn (SSO) authentication with their Qualys subscription. When implemented, Qualys
Guide for Windows users with Internet Explorer and Firefox
 Velocity@ocbc Guide for Windows users with Internet Explorer and Firefox Version 5.0 171013 1 of 14 Uninstall prior Java versions 1. Log in to an administrator account. Go to Start > Control Panel 2. Click
Velocity@ocbc Guide for Windows users with Internet Explorer and Firefox Version 5.0 171013 1 of 14 Uninstall prior Java versions 1. Log in to an administrator account. Go to Start > Control Panel 2. Click
OWIZA 1.0 U S E R ' S G U I D E. Owiza 1.0. User s Guide. Copyright Ositcom LTD. All rights reserved.
 Owiza 1.0 User s Guide Copyright 2006-2014 Ositcom LTD. All rights reserved. Owiza 1.0: User s Guide Copyright 2006 2013 OSITCOM LTD. http://www.ositcom.net/ Copyright 2006-2014 Ositcom LTD. All rights
Owiza 1.0 User s Guide Copyright 2006-2014 Ositcom LTD. All rights reserved. Owiza 1.0: User s Guide Copyright 2006 2013 OSITCOM LTD. http://www.ositcom.net/ Copyright 2006-2014 Ositcom LTD. All rights
Local. Responsive. Reliable.
 Local. Responsive. Reliable. FAQs WHAT IS myvrb? myvrb is the new name of your online and mobile banking experience at Valley Republic Bank. While you will continue to access online and mobile banking
Local. Responsive. Reliable. FAQs WHAT IS myvrb? myvrb is the new name of your online and mobile banking experience at Valley Republic Bank. While you will continue to access online and mobile banking
The Wifidog project is an open source captive portal solution It consists of two components:
 Captive Portal System typically used by business centers, airports, hotel lobbies, coffee shops, and other venues which offer Wi-Fi hot spots for Internet users It permits to authenticate a client by username
Captive Portal System typically used by business centers, airports, hotel lobbies, coffee shops, and other venues which offer Wi-Fi hot spots for Internet users It permits to authenticate a client by username
CIS 6930/4930 Computer and Network Security. Topic 7. Trusted Intermediaries
 CIS 6930/4930 Computer and Network Security Topic 7. Trusted Intermediaries 1 Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC) Representative
CIS 6930/4930 Computer and Network Security Topic 7. Trusted Intermediaries 1 Trusted Intermediaries Problem: authentication for large networks Solution #1 Key Distribution Center (KDC) Representative
Heart Walk Mobile App Training
 Heart Walk Mobile App Training New Users App Welcome Welcome screens for new app users to guide them as to how to use the app and what they can do 2 Login Users can login using their same credentials as
Heart Walk Mobile App Training New Users App Welcome Welcome screens for new app users to guide them as to how to use the app and what they can do 2 Login Users can login using their same credentials as
DB2 Web Query (REST based) Application Extension. Usage Instructions
 DB2 Web Query (REST based) Application Extension Usage Instructions Updated March 29, 2016 Page 1 1 Overview... 4 2 Initial Setup... 5 3 Using the Extension... 6 3.1 Modes of use... 6 3.1.1 Browse Mode...
DB2 Web Query (REST based) Application Extension Usage Instructions Updated March 29, 2016 Page 1 1 Overview... 4 2 Initial Setup... 5 3 Using the Extension... 6 3.1 Modes of use... 6 3.1.1 Browse Mode...
INTRODUCTION TO THE GLOBAL ENVIRONMENT FACILITY e-course
 INTRODUCTION TO THE GLOBAL ENVIRONMENT FACILITY e-course New User Sign-up & login Existing user Login Troubleshooting Login Issues INTRODUCTION TO THE GLOBAL ENVIRONMENT FACILITY (GEF) e-course To access
INTRODUCTION TO THE GLOBAL ENVIRONMENT FACILITY e-course New User Sign-up & login Existing user Login Troubleshooting Login Issues INTRODUCTION TO THE GLOBAL ENVIRONMENT FACILITY (GEF) e-course To access
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
Readme for ios 7 WebAuth on Cisco Wireless LAN Controller, Release 7.4 MR 2
 Readme for ios 7 WebAuth on Cisco Wireless LAN Controller, Release 7.4 MR 2 September, 2013 1 Contents This document includes the following sections: 1 Contents 1 2 Background 1 2.1 Captive Bypassing on
Readme for ios 7 WebAuth on Cisco Wireless LAN Controller, Release 7.4 MR 2 September, 2013 1 Contents This document includes the following sections: 1 Contents 1 2 Background 1 2.1 Captive Bypassing on
The 12-Factor app and IBM Bluemix IBM Corporation
 The 12-Factor app and IBM Bluemix After you complete this section, you should understand: The characteristics of a 12-Factor app Examples of following 12-Factor App methodology in Bluemix 2 What are the
The 12-Factor app and IBM Bluemix After you complete this section, you should understand: The characteristics of a 12-Factor app Examples of following 12-Factor App methodology in Bluemix 2 What are the
CSE 154 LECTURE 13: SESSIONS
 CSE 154 LECTURE 13: SESSIONS Expiration / persistent cookies setcookie("name", "value", expiration); $expiretime = time() + 60*60*24*7; # 1 week from now setcookie("couponnumber", "389752", $expiretime);
CSE 154 LECTURE 13: SESSIONS Expiration / persistent cookies setcookie("name", "value", expiration); $expiretime = time() + 60*60*24*7; # 1 week from now setcookie("couponnumber", "389752", $expiretime);
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
maxecurity Product Suite
 maxecurity Product Suite Domain Administrator s Manual Firmware v2.2 ii Table of Contents BASICS... 1 Understanding how maxecurity products work in your company... 1 Getting started as a Domain Administrator...
maxecurity Product Suite Domain Administrator s Manual Firmware v2.2 ii Table of Contents BASICS... 1 Understanding how maxecurity products work in your company... 1 Getting started as a Domain Administrator...
Deltek Touch T&E Startup Guide
 Deltek Touch T&E Startup Guide https://dte.unisys.com 2015 Unisys Corporation. All rights reserved. FOR INTERNAL USE ONLY. 1 Mobile Device Pre-requisites Make sure your mobile browser allows cookies from
Deltek Touch T&E Startup Guide https://dte.unisys.com 2015 Unisys Corporation. All rights reserved. FOR INTERNAL USE ONLY. 1 Mobile Device Pre-requisites Make sure your mobile browser allows cookies from
Trusted Login Connector (Hosted SSO)
 Trusted Login Connector (Hosted SSO) Table of Contents Summary... 3 Frequently Asked Questions... 3 Architecture... 5 Installation/configuration... 5 2 Summary New functionality allows SelectHR users to
Trusted Login Connector (Hosted SSO) Table of Contents Summary... 3 Frequently Asked Questions... 3 Architecture... 5 Installation/configuration... 5 2 Summary New functionality allows SelectHR users to
MICROSOFT OFFICE Desktop Applications. Student User Guide Overview
 Student User Guide Overview This document provides detailed instructions to students of Baldivis Secondary College on how-to download and install a free copy of Microsoft Office 2016 Desktop applications
Student User Guide Overview This document provides detailed instructions to students of Baldivis Secondary College on how-to download and install a free copy of Microsoft Office 2016 Desktop applications
Programming for the Web with PHP
 Aptech Ltd Version 1.0 Page 1 of 11 Table of Contents Aptech Ltd Version 1.0 Page 2 of 11 Abstraction Anonymous Class Apache Arithmetic Operators Array Array Identifier arsort Function Assignment Operators
Aptech Ltd Version 1.0 Page 1 of 11 Table of Contents Aptech Ltd Version 1.0 Page 2 of 11 Abstraction Anonymous Class Apache Arithmetic Operators Array Array Identifier arsort Function Assignment Operators
ArcGIS Server and Portal for ArcGIS An Introduction to Security
 ArcGIS Server and Portal for ArcGIS An Introduction to Security Jeff Smith & Derek Law July 21, 2015 Agenda Strongly Recommend: Knowledge of ArcGIS Server and Portal for ArcGIS Security in the context
ArcGIS Server and Portal for ArcGIS An Introduction to Security Jeff Smith & Derek Law July 21, 2015 Agenda Strongly Recommend: Knowledge of ArcGIS Server and Portal for ArcGIS Security in the context
Computer Networks. HTTP and more. Jianping Pan Spring /20/17 CSC361 1
 Computer Networks HTTP and more Jianping Pan Spring 2017 1/20/17 CSC361 1 First things first W1 due next Monday (Jan 23) submit a single PDF file through connex Noah posted a docx for for questions on
Computer Networks HTTP and more Jianping Pan Spring 2017 1/20/17 CSC361 1 First things first W1 due next Monday (Jan 23) submit a single PDF file through connex Noah posted a docx for for questions on
Contents Upgrading BFInventory iii
 Upgrading ii Upgrading Contents Upgrading.............. 1 Upgrading to IBM Tivoli Endpoint Manager for Software Use Analysis version 2.0....... 1 Planning and preparing for the upgrade.... 2 Installing
Upgrading ii Upgrading Contents Upgrading.............. 1 Upgrading to IBM Tivoli Endpoint Manager for Software Use Analysis version 2.0....... 1 Planning and preparing for the upgrade.... 2 Installing
Introduction to Voltage Secur
 Introduction to Voltage SecureMail: JPMorgan Chase values your privacy. In order to protect sensitive email conversations and private documents, we are now using Voltage SecureMail, a data privacy tool
Introduction to Voltage SecureMail: JPMorgan Chase values your privacy. In order to protect sensitive email conversations and private documents, we are now using Voltage SecureMail, a data privacy tool
Migrating Enterprise Applications to the Azure Platform
 Migrating Enterprise Applications to the Azure Platform Agenda Announcements Silverlight Migration ASP.NET Migration Web Service Migration Database Migration Announcements Microsoft Shutting Down Northwest
Migrating Enterprise Applications to the Azure Platform Agenda Announcements Silverlight Migration ASP.NET Migration Web Service Migration Database Migration Announcements Microsoft Shutting Down Northwest
Administering Jive Mobile Apps for ios and Android
 Administering Jive Mobile Apps for ios and Android TOC 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios...3 Custom App Wrapping for ios...3 Authentication with Mobile
Administering Jive Mobile Apps for ios and Android TOC 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios...3 Custom App Wrapping for ios...3 Authentication with Mobile
Configuration Note. RADIUS for Secure Device Access. Multi-Service Business Routers. Enterprise Session Border Controllers. VoIP Media Gateways
 Multi-Service Business Routers Enterprise Session Border Controllers VoIP Media Gateways Configuration Note RADIUS for Secure Device Access December 2012 Document # LTRT-34201 Configuration Note Contents
Multi-Service Business Routers Enterprise Session Border Controllers VoIP Media Gateways Configuration Note RADIUS for Secure Device Access December 2012 Document # LTRT-34201 Configuration Note Contents
Pulse Secure Desktop Client Release Notes
 Pulse Secure Desktop Client Release Notes Pulse5.1 R3.2 Build 56743 May 2015 Revision 00 Contents Introduction... 2 Interoperability and Supported Platforms... 2 Problems Resolved in Pulse5.1R3.2... 2
Pulse Secure Desktop Client Release Notes Pulse5.1 R3.2 Build 56743 May 2015 Revision 00 Contents Introduction... 2 Interoperability and Supported Platforms... 2 Problems Resolved in Pulse5.1R3.2... 2
Lecture 8. Validations & Sessions 1 / 41
 Lecture 8 Validations & Sessions 1 / 41 Advanced Active Record 2 / 41 More Complex Queries Arel provides us with a number of methods to query our database tables So far, we've only used find which limits
Lecture 8 Validations & Sessions 1 / 41 Advanced Active Record 2 / 41 More Complex Queries Arel provides us with a number of methods to query our database tables So far, we've only used find which limits
SecurEnvoy Microsoft Server Agent
 SecurEnvoy Microsoft Server Agent SecurEnvoy Global HQ Merlin House, Brunel Road, Theale, Reading. RG7 4TY Tel: 0845 2600010 Fax: 0845 260014 www.securenvoy.com SecurEnvoy Microsoft Server Agent Installation
SecurEnvoy Microsoft Server Agent SecurEnvoy Global HQ Merlin House, Brunel Road, Theale, Reading. RG7 4TY Tel: 0845 2600010 Fax: 0845 260014 www.securenvoy.com SecurEnvoy Microsoft Server Agent Installation
LogMeIn Rescue Getting Started with Two-Step Verification. User Guide
 LogMeIn Rescue Getting Started with Two-Step Verification User Guide Contents Two-Step Verification at a Glance...3 How to Enforce Two-Step Verification...4 How to Reset Two-Step Verification...4 How to
LogMeIn Rescue Getting Started with Two-Step Verification User Guide Contents Two-Step Verification at a Glance...3 How to Enforce Two-Step Verification...4 How to Reset Two-Step Verification...4 How to
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Configuring Caching Services
 CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
The ecampus User Guide
 Click to edit Master title style The ecampus User Guide https://ecampus.amref.org February 2019 Click Table to of edit Content Master title style GETTING STARTED Accessing the Platform Operating Modes
Click to edit Master title style The ecampus User Guide https://ecampus.amref.org February 2019 Click Table to of edit Content Master title style GETTING STARTED Accessing the Platform Operating Modes
ISA 767, Secure Electronic Commerce Xinwen Zhang, George Mason University
 Identity Management and Federated ID (Liberty Alliance) ISA 767, Secure Electronic Commerce Xinwen Zhang, xzhang6@gmu.edu George Mason University Identity Identity is the fundamental concept of uniquely
Identity Management and Federated ID (Liberty Alliance) ISA 767, Secure Electronic Commerce Xinwen Zhang, xzhang6@gmu.edu George Mason University Identity Identity is the fundamental concept of uniquely
Please post bugs on our forum on or us on
 Login One! authentication and user plug-in for Joomla! 3.x Trial Edition 2011-2018 INNATO BV - www.innato.nl - All rights reserved **************************************************************************
Login One! authentication and user plug-in for Joomla! 3.x Trial Edition 2011-2018 INNATO BV - www.innato.nl - All rights reserved **************************************************************************
Configuring Actinic with ISA Server 2000
 Configuring Actinic with ISA Server 2000 Actinic Software Ltd. Author: Gordon Camley Date: 26 January 2004 Revision: 1.0 Introduction As of release 6.1.4, Actinic can be configured to work with an ISA
Configuring Actinic with ISA Server 2000 Actinic Software Ltd. Author: Gordon Camley Date: 26 January 2004 Revision: 1.0 Introduction As of release 6.1.4, Actinic can be configured to work with an ISA
Wireless LAN Controller Web Authentication Configuration Example
 Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Okta Integration Guide for Web Access Management with F5 BIG-IP
 Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
OAuth securing the insecure
 Black Hat US 2011 khash kiani khash@thinksec.com OAuth securing the insecure roadmap OAuth flow malicious sample applications mobile OAuth google app web-based OAuth facebook app insecure implementation
Black Hat US 2011 khash kiani khash@thinksec.com OAuth securing the insecure roadmap OAuth flow malicious sample applications mobile OAuth google app web-based OAuth facebook app insecure implementation
HOW TO SET UP YOUR FUNDRAISING WEBPAGE
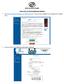 HOW TO SET UP YOUR FUNDRAISING WEBPAGE 1. Go to http://wakebgc.donorpages.com/backtoschool15. Once you have navigated to the webpage click Register Here. 2. Proceed to fill out the registration information
HOW TO SET UP YOUR FUNDRAISING WEBPAGE 1. Go to http://wakebgc.donorpages.com/backtoschool15. Once you have navigated to the webpage click Register Here. 2. Proceed to fill out the registration information
CN Assignment I. 1. With an example explain how cookies are used in e-commerce application to improve the performance.
 CN Assignment I 1. With an example explain how cookies are used in e-commerce application to improve the performance. In an e-commerce application, when the user sends a login form to the server, the server
CN Assignment I 1. With an example explain how cookies are used in e-commerce application to improve the performance. In an e-commerce application, when the user sends a login form to the server, the server
SAML-Based SSO Solution
 About SAML SSO Solution, page 1 Single Sign on Single Service Provider Agreement, page 2 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 3 Cisco Unified Communications Applications
About SAML SSO Solution, page 1 Single Sign on Single Service Provider Agreement, page 2 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 3 Cisco Unified Communications Applications
REMOTE ACCESS OUTLOOK WEB ACCESS
 Introduction REMOTE ACCESS OUTLOOK WEB ACCESS Outlook Web Access (Outlook Web) offers basic email, calendar and contact access. You will not be able to access any of your documents or launch any applications,
Introduction REMOTE ACCESS OUTLOOK WEB ACCESS Outlook Web Access (Outlook Web) offers basic email, calendar and contact access. You will not be able to access any of your documents or launch any applications,
CMX Connected Experiences- Social, SMS and Custom Portal Registration Configuration Example
 CMX Connected Experiences- Social, SMS and Custom Portal Registration Configuration Example Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Authentication
CMX Connected Experiences- Social, SMS and Custom Portal Registration Configuration Example Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Authentication
Bambu API Documentation
 Bambu API Documentation Release 2.0.1 Steadman Sep 27, 2017 Contents 1 About Bambu API 3 2 About Bambu Tools 2.0 5 3 Installation 7 4 Basic usage 9 5 Questions or suggestions? 11 6 Contents 13 6.1 Defining
Bambu API Documentation Release 2.0.1 Steadman Sep 27, 2017 Contents 1 About Bambu API 3 2 About Bambu Tools 2.0 5 3 Installation 7 4 Basic usage 9 5 Questions or suggestions? 11 6 Contents 13 6.1 Defining
USER MANUAL. SalesPort Salesforce Customer Portal for WordPress (Lightning Mode) TABLE OF CONTENTS. Version: 3.1.0
 USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
Leaving the State: Sessionless (Stateless) Authentication in D8 with Whole Foods Market. BADCamp 2017
 Leaving the State: Sessionless (Stateless) Authentication in D8 with Whole Foods Market BADCamp 2017 These Guys Dr J Daverth Technical Lead, Whole Foods Market D.O.: dr-jay BitBucket: drjdaverth LinkedIn:
Leaving the State: Sessionless (Stateless) Authentication in D8 with Whole Foods Market BADCamp 2017 These Guys Dr J Daverth Technical Lead, Whole Foods Market D.O.: dr-jay BitBucket: drjdaverth LinkedIn:
The MSU Department of Mathematics "Account Manager" can be used for the following:
 MSU Department of Mathematics Account Manager Tutorial Overview The MSU Department of Mathematics "Account Manager" can be used for the following: Change your Math account password Reset a forgotten password
MSU Department of Mathematics Account Manager Tutorial Overview The MSU Department of Mathematics "Account Manager" can be used for the following: Change your Math account password Reset a forgotten password
SCHEDULE AN APPOINTMENT
 SCHEDULE AN APPOINTMENT 1. Go to https://www.donorpoint.org/. You will be directed to this page. 2. Enter your login information. Enter your username and password. 3. From the login page, you will be directed
SCHEDULE AN APPOINTMENT 1. Go to https://www.donorpoint.org/. You will be directed to this page. 2. Enter your login information. Enter your username and password. 3. From the login page, you will be directed
Atlantic Capital Exchange ACE Secure Browser MAC Quick Start Guide
 Atlantic Capital Exchange ACE Secure Browser MAC Quick Start Guide ACE Secure Browser is a user friendly, secure application that protects your company while accessing bank information and services. Early
Atlantic Capital Exchange ACE Secure Browser MAC Quick Start Guide ACE Secure Browser is a user friendly, secure application that protects your company while accessing bank information and services. Early
SAML-Based SSO Solution
 About SAML SSO Solution, page 1 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 2 SAML SSO Web Browsers, page 3 Cisco Unified Communications Applications that Support SAML SSO,
About SAML SSO Solution, page 1 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 2 SAML SSO Web Browsers, page 3 Cisco Unified Communications Applications that Support SAML SSO,
Table of Contents Chapter 1: Upgrading to Observer v Index...8
 Upgrading to 17.5.2.0 User Guide 29 Mar 2019 Table of Contents Chapter 1: Upgrading to v17... 3 Before upgrading to v17...3 What is new in v17...3 What is needed for upgrading...4 Installing and licensing...5
Upgrading to 17.5.2.0 User Guide 29 Mar 2019 Table of Contents Chapter 1: Upgrading to v17... 3 Before upgrading to v17...3 What is new in v17...3 What is needed for upgrading...4 Installing and licensing...5
Identity Provider for SAP Single Sign-On and SAP Identity Management
 Implementation Guide Document Version: 1.0 2017-05-15 PUBLIC Identity Provider for SAP Single Sign-On and SAP Identity Management Content 1....4 1.1 What is SAML 2.0.... 5 SSO with SAML 2.0.... 6 SLO with
Implementation Guide Document Version: 1.0 2017-05-15 PUBLIC Identity Provider for SAP Single Sign-On and SAP Identity Management Content 1....4 1.1 What is SAML 2.0.... 5 SSO with SAML 2.0.... 6 SLO with
IBM LOT-911. IBM WebSphere Portal 8.0 Solution Development.
 IBM LOT-911 IBM WebSphere Portal 8.0 Solution Development http://killexams.com/exam-detail/lot-911 QUESTION: 105 Bill is developing a mail portlet. One of the requirements of the mail portlet is that it
IBM LOT-911 IBM WebSphere Portal 8.0 Solution Development http://killexams.com/exam-detail/lot-911 QUESTION: 105 Bill is developing a mail portlet. One of the requirements of the mail portlet is that it
Manual Html A Href Onclick Submit Form
 Manual Html A Href Onclick Submit Form JS HTML DOM. DOM Intro DOM Methods HTML form validation can be done by a JavaScript. If a form field _input type="submit" value="submit" /form_. As shown in a previous
Manual Html A Href Onclick Submit Form JS HTML DOM. DOM Intro DOM Methods HTML form validation can be done by a JavaScript. If a form field _input type="submit" value="submit" /form_. As shown in a previous
