Push Driven Service Composition in Personal Communication Environments
|
|
|
- Samson Carroll
- 5 years ago
- Views:
Transcription
1 Push Driven Service Composition in Personal Communication Environments Justinian Oprescu, Franck Rousseau, Laurentiu-Sorin Paun, and Andrzej Duda LSR-IMAG Laboratory BP. 72, Saint Martin d Héres, France {Justinian.Oprescu,Franck.Rousseau,Laurentiu-Sorin.Paun, Andrzej.Duda}@imag.fr Abstract. Our current mode of communication is mainly based on the pull model in which the user requests information or initiates a communication stream. We believe that a personal communication environment should behave according to the push model in which a source of data or the network infrastructure takes care of preparing communications and proposing them to the user. In this proactive way of operation, the only user intervention is to choose the right communication flow. In this paper we present the service discovery and composition in Omnisphere, a personal communication environment for wireless appliances. All elements in Omnisphere are considered as services that can be dynamically discovered and composed to form complex communication applications. Based on user preferences, device capabilities, and context Omnisphere makes use of existing discovery protocols such as SLP, Jini, UPnP, or DNS-SD to discover relevant services. Service descriptors provide further information on the data types generated on output or accepted on input. All this information allows Omnisphere to configure services and user applications so that the user can benefit from complex communication applications composed on demand. 1 Introduction We present the service discovery and composition in Omnisphere [1], a personal communication environment for wireless appliances. The goal of Omnisphere is to mediate communications on behalf of the user in a proactive way. Many of our current applications are governed by the pull model in which the user requests information or initiates a communication stream (Web, etc). In this interactive mode of operation, the user is an active part and must initiate the process of information acquisition. In the push model, it is the source or the network infrastructure that proposes the information to the user in a similar way to the SIP protocol which invites the user to a communication session. Such a mode of operation is at the base of Omnisphere: it takes care of preparing communications and proposing them to the user. In this proactive way of operation, the only user intervention is to choose the right communication flow. M. Conti et al. (Eds.): PWC 2003, LNCS 2775, pp , c IFIP International Federation for Information Processing 2003
2 506 J. Oprescu et al. Fig. 1. Omnisphere architecture For common applications we transform information sources that require user intervention into sources that notify the user about some events and then the user may decide to consume the proposed information or not (e.g. a NotifyMail service checks the user mailbox for new messages and notifies the user about important messages, the user may then read a message using a standard mailer and the POP protocol). The role of Omnisphere is to mediate notification events according to the user preferences, discover required services, configure them, and compose them into complex communication applications. In the rest of the paper, we focus on the push driven service composition in Omnisphere. We consider that communication chains in a personal communication environment can be dynamically managed when all components follow the same paradigm everything-is-a-service : all basic services, sources, transcoders or filters, as well as user applications are viewed as services from the discovery point of view. Their descriptors can be found and used along with other information such as the user preferences to compose complex communication applications. Due to the space limitation we skip over the related work, obviously there are several projects related to our work. The paper is organized as follows. Section 2 presents the architecture of Omnisphere. Section 3 describes our approach to service discovery and composition. Finally, we present conclusion and future work (Section 4). 2 Architecture of Omnisphere Omnisphere is a communication and information universe surrounding wireless appliances (more detailed description can be found elsewhere [1]). It mediates various communication flows to relieve the user from any cumbersome details of finding the right service components, configuring, and composing them based on user preferences, device capabilities, and the current context. Omnisphere comprises the following elements:
3 Push Driven Service Composition in Personal Communication Environments 507 Fig. 2. Composition of basic services Ambient services. An ambient service is an abstract view of a communication component. It represents a high-level concept that allows us to construct complex services out of primitive ones by connecting them with typed data flows. An ambient service encapsulates some processing, provides a signaling interface for generating events and accepting a configuration commands, and publishes a service description. Typed data flows. A typed data flow is an abstract view of communication between ambient services. It allows to associate the type of data with a given flow. User avatar. An avatar represents the user in Omnisphere. Its role is to mediate event notifications concerning different data flows. It receives events from ambient services and acts according to the information on user preferences, the current context, and device capabilities to either notify the user or set up communications. It monitors the presence of user devices, manages services available at the given Omnisphere, and discovers services required for the user. An instance of the user avatar exists at each Omnisphere in which the user is present. Omnisphere controller. It runs on a user appliance and takes care of events sent to the user. When needed, it will configure and run applications used by the user to consume communication flows. When requested by the user, it will initiate the discovery process of available services in the present Omnisphere. Upon the arrival in a new place, it will register the device within a given Omnisphere and authenticate the user. 3 Service Discovery and Composition in Omnisphere We can compose services in two ways. The first one is pull driven a sink service looks for intermediate filter services and a source service to provide an end to end communication flow. An example of such a composition is RealPlayer that looks for a streaming source. The second way is push driven it makes the network infrastructure the active part of the communication: a source service looks for a suitable sink to deliver a flow in a proactive manner, e.g. an notifier looks for a mailer on a PDA to inform the user about s upon entering a personal communication environment. Figure 2 illustrates these approaches with
4 508 J. Oprescu et al. two chains of services: the composition of an application in the pull model starts with a sink that finds a source and places a filter (or transcoder) if needed. In the push model, the composition begins with the source that finds a suitable sink with an optional filter in between. The graph of service composition may be more complex than the simple chains shown in the figure. Although we provide both composition methods, we believe that the push model corresponds better to the requirements of Omnisphere. The user avatar is the central element in the operation of Omnisphere. It takes care of all the operations that should be performed in the network infrastructure on behalf of the user. In this way most of the operations are delegated into the network infrastructure and are automated as much as possible. When an appliance enters Omnisphere, it authenticates itself so that based on the User ID and Appliance ID, Omnisphere can retrieve the User Preferences and Device Capabilities. User Preferences define what are the most common needs of the user in terms of services and different types of data and Device Capabilities provide information about the characteristics of appliances (screen resolution, processor speed, network interface). It also uses Context that adds some location specific information such as the geographic location, available devices, type of environment public or private, and all other information related to the close neighborhood of an appliance. It then creates an avatar that discovers relevant services using a service discovery protocol. The discovered services are matched with the required characteristics provided by User Preferences, Device Capabilities, and Context. They are then configured and activated. If needed the avatar contacts the Omnisphere controller on the user appliance to run the user applications that receive data flows. To take into account state changes, for example when an appliance becomes inactive, or a new appliance enters Omnisphere, the service bindings are re-evaluated. Such a discovery process relieves appliances, which may have limited resources, from the operation that may consume scarce resources and may require the availability of different discovery protocols on the appliance. It may also save critical radio channel resources, because only selected information is provided to the appliance. 3.1 Example We present below an example of notification. Alice wants to use a mailer such as Netscape or Eudora at the office. Instead of running them all the time to periodically check her mailbox via POP, she wants the mailer to be run upon the arrival of a new mail and configured to use ssh tunnels with the company POP and SMTP servers. When she leaves the office, she wants to receive e- mail notifications as SMS messages on her cellular phone for some urgent and important messages. When attending a meeting, she wants to be notified on her PDA to decide whether it is worthwhile to read a mail. Upon arrival at home, she wants to read the mail on the home PC by using the SMTP server of her ISP. Let us start with User Preferences for Alice.
5 Push Driven Service Composition in Personal Communication Environments 509 Communication Attributs Preferred User Applications Mail domain=imag.fr laptop-netscape, pda-popup, gsm-sms transport=secure Fig. 3. Mail example This information means that Alice wants to use her mailbox in the imag.fr domain and her preferred applications are the usual Natscape mailer on her laptop, a popup dialog window for deciding whether to read a mail, or a notifier that sends a SMS message to her cell phone. Each of these applications can be configured with some additional information such as the port number or the cell phone number. The composition of ambient services is presented in Figure 3. A user mailbox exists on a server in domain=imag.fr and there is a service MailNotify able to check for a new mail of a given user. If Alice is in her office, Omnisphere looks for services that generate type /mixed/ incoming (we define a simple hierarchy of types similar to the DNS names). The query returns the addresses of incoming mail servers (POP, IMAP, HTTPS). Then, Omnisphere looks for a service that generates type /mixed/ event. In our example, the query returns the MailNotify service. A query for /mixed/ outcoming yields an outgoing local SMTP server. User applications such as Netscape register with the service discovery protocol so that Omnisphere can find them. If several applications are discovered, in the case for example when Alice is in the office with her laptop and a PDA, Netscape is chosen as the preferred user application. At this point all the ele-
6 510 J. Oprescu et al. ments are discovered and Omnisphere can configure them and compose to form the complex Mail application. When Alice goes to a meeting room, the avatar detects that she is not longer present in the office and stops the mailer. According to the preferences, it discovers a SMS notifier, configures it with the Alice s cell phone, and forwards notification events coming from the MailNotify service. In this way, Alice receives automatically an excerpt of the mail on her cell phone. Then, Omnishpere in the meeting room detects the Alice s PDA when she enters the room. It requests the migration of the avatar to the current location. The avatar stops forwarding mails to the cell phone and sends them to the Omnisphere controller on the PDA which pops up a window to ask Alice what to do with the incoming mail. She may decide to read it using a mailer on the PDA. In general, there can be multiple instances of discovered services. In this case, we need to add sufficient attributes to User Preferences in order to help resolving such ambiguities. 4 Conclusion We believe that future personal communication environments will be based on the push driven paradigm: sources of data push information towards the user and the network infrastructure takes care of mediating such communication flows. We experiment with this approach by designing and implementing Omnisphere. We have already prototyped the main elements of Omnisphere: the user avatar and the Omnisphere controller. The avatar uses the DNS-SD for service discovery we have modified the Apple Rendezvous implementation of DNS-SD to take into account our definition of data types and wildcard service queries. Our current work concerns seamless handover of the user between different places, the detection of the user movement, and implementing more complex scenarios such as follow me video the user can continuously watch a video stream presented on different appliances when moving between different places. References 1. F. Rousseau, J. Oprescu, L-S. Paun, and A. Duda. Omnisphere: a Personal Communication Environment. In Proc. Thirty-Sixth Annual Hawaii International Conference on System Sciences (HICSS-36), Big Island, Hawaii, 2003.
CS321: Computer Networks ELECTRONIC MAIL
 CS321: Computer Networks ELECTRONIC MAIL Dr. Manas Khatua Assistant Professor Dept. of CSE IIT Jodhpur E-mail: manaskhatua@iitj.ac.in Electronic mail (E-mail) It allows users to exchange messages. In HTTP
CS321: Computer Networks ELECTRONIC MAIL Dr. Manas Khatua Assistant Professor Dept. of CSE IIT Jodhpur E-mail: manaskhatua@iitj.ac.in Electronic mail (E-mail) It allows users to exchange messages. In HTTP
Electronic Mail Paradigm
 Electronic Mail Paradigm E-mail uses the client-server model. E-mail was designed as an electronic extension of the old paper office memo. - A quick and easy means of low-overhead written communication.
Electronic Mail Paradigm E-mail uses the client-server model. E-mail was designed as an electronic extension of the old paper office memo. - A quick and easy means of low-overhead written communication.
All existing accounts will be listed. 2. Click Add and select Mail to add a new account (see Figure 2). Figure 1. Figure 2
 Microsoft Outlook Express 5.x, 6.0 This section describes how to configure Outlook Express to access POP E-mail. 1. Click Tools and select Accounts from the pull-down menu (see Figure 1). Figure 1 All
Microsoft Outlook Express 5.x, 6.0 This section describes how to configure Outlook Express to access POP E-mail. 1. Click Tools and select Accounts from the pull-down menu (see Figure 1). Figure 1 All
Configure Outlook to use port 587 with authentication
 Configure Outlook 2003 email to use port 587 with authentication In order to send and receive E-mail through your website hosted with FastWebEngine, you can configure Outlook as your preferred E-mail client.
Configure Outlook 2003 email to use port 587 with authentication In order to send and receive E-mail through your website hosted with FastWebEngine, you can configure Outlook as your preferred E-mail client.
CS348: Computer Networks (SMTP, POP3, IMAP4); FTP
 CS348: Computer Networks E-MAIL (SMTP, POP3, IMAP4); FTP Dr. Manas Khatua Assistant Professor Dept. of CSE, IIT Guwahati E-mail: manaskhatua@iitg.ac.in Electronic mail (E-mail) Allows users to exchange
CS348: Computer Networks E-MAIL (SMTP, POP3, IMAP4); FTP Dr. Manas Khatua Assistant Professor Dept. of CSE, IIT Guwahati E-mail: manaskhatua@iitg.ac.in Electronic mail (E-mail) Allows users to exchange
System: Basic Functionality
 E-mail System: Basic Functionality E-mail systems support five basic functions: Composition: Creating messages Transfer: Moving messages from the originator to the recipient E-mail transfer is a connection-oriented
E-mail System: Basic Functionality E-mail systems support five basic functions: Composition: Creating messages Transfer: Moving messages from the originator to the recipient E-mail transfer is a connection-oriented
Outlook calendar guide
 Outlook 2010 - calendar guide 1 Contents Contents... 2 Purpose... 3 Document Support Boundaries... 3 Allow someone else to manage your email and calendar... 4 About Delegate Access... 4 What are the delegate
Outlook 2010 - calendar guide 1 Contents Contents... 2 Purpose... 3 Document Support Boundaries... 3 Allow someone else to manage your email and calendar... 4 About Delegate Access... 4 What are the delegate
Network Applications Principles of Network Applications
 Network Applications Principles of Network Applications A Network application is an application running on one host and provides communication to another application running on a different host. At the
Network Applications Principles of Network Applications A Network application is an application running on one host and provides communication to another application running on a different host. At the
APPLICATION LAYER APPLICATION LAYER : DNS, HTTP, , SMTP, Telnet, FTP, Security-PGP-SSH.
 APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
Application Layer: OSI and TCP/IP Models
 Application Layer Application Layer: OSI and TCP/IP Models The communication process between two communicating nodes is actually a communication process between two applications on these devices. Service
Application Layer Application Layer: OSI and TCP/IP Models The communication process between two communicating nodes is actually a communication process between two applications on these devices. Service
SETUP FOR OUTLOOK (Updated October, 2018)
 EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
IMS Client Framework for All IP-Based Communication Networks
 IMS Client Framework for All IP-Based Communication Networks D. Jayaram, S. Vijay Anand, Vamshi Raghav, Prashanth Kumar, K. Riyaz & K. Kishan Larsen & Toubro InfoTech Limited Research and Development Group,
IMS Client Framework for All IP-Based Communication Networks D. Jayaram, S. Vijay Anand, Vamshi Raghav, Prashanth Kumar, K. Riyaz & K. Kishan Larsen & Toubro InfoTech Limited Research and Development Group,
Configuring Netscape or Thunderbird Mail
 April 2004 Configuring Desktop Messaging Configuring Netscape or Thunderbird Mail Introduction This section describes how to configure Netscape Mail 6.2x or later for use with Desktop Messaging. Before
April 2004 Configuring Desktop Messaging Configuring Netscape or Thunderbird Mail Introduction This section describes how to configure Netscape Mail 6.2x or later for use with Desktop Messaging. Before
NotifySync 4.7. Notify Technology Corporation
 1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
DTV for Personalized Mobile Access and Unified Home Control
 DTV for Personalized Mobile Access and Unified Home Control Jianlin Guo, Fernando Matsubara, Johnas Cukier, Haosong Kong Mitsubishi Electric Research Labs, 558 Central Avenue, Murray Hill, NJ 07974, USA
DTV for Personalized Mobile Access and Unified Home Control Jianlin Guo, Fernando Matsubara, Johnas Cukier, Haosong Kong Mitsubishi Electric Research Labs, 558 Central Avenue, Murray Hill, NJ 07974, USA
USING EUDORA WITH ENTERGROUP EUDORA
 USING EUDORA WITH ENTERGROUP In this tutorial you will learn how to use Eudora with your EnterGroup account. You will learn how to setup an IMAP or POP account, and also how to move your emails and contacts
USING EUDORA WITH ENTERGROUP In this tutorial you will learn how to use Eudora with your EnterGroup account. You will learn how to setup an IMAP or POP account, and also how to move your emails and contacts
Sharing your calendar and setting permissions
 Sharing your calendar and setting permissions Allowing access to your calendar You can share your calendar with other users to allow them to view when you are available and to help with scheduling meetings.
Sharing your calendar and setting permissions Allowing access to your calendar You can share your calendar with other users to allow them to view when you are available and to help with scheduling meetings.
Setting Up Netscape 4.61 to read the IMAP Server
 Setting Up Netscape 4.61 to read the IMAP Server Section I 1. Open Netscape Communicator 4.61. 2. Click Edit, Preferences. 3. In the left-hand panel, if there is a plus sign (+) next to Mail and Newsgroups,
Setting Up Netscape 4.61 to read the IMAP Server Section I 1. Open Netscape Communicator 4.61. 2. Click Edit, Preferences. 3. In the left-hand panel, if there is a plus sign (+) next to Mail and Newsgroups,
Rui Campos, Carlos Pinho, Manuel Ricardo and José Ruela
 Dynamic and Automatic Interworking between Personal Area Networks using Rui Campos, Carlos Pinho, Manuel Ricardo and José Ruela Outline 1. Introduction 2. Ambient Network and Network 3. Case Study Interworking
Dynamic and Automatic Interworking between Personal Area Networks using Rui Campos, Carlos Pinho, Manuel Ricardo and José Ruela Outline 1. Introduction 2. Ambient Network and Network 3. Case Study Interworking
The Application Layer: & SMTP
 The Application Layer: email & SMTP Smith College, CSC 249 Feb 1, 2018 4-1 Chapter 2: Application layer q 2.1 Principles of network applications q 2.2 Web and HTTP q 2.3 FTP q 2.4 Electronic Mail v SMTP,
The Application Layer: email & SMTP Smith College, CSC 249 Feb 1, 2018 4-1 Chapter 2: Application layer q 2.1 Principles of network applications q 2.2 Web and HTTP q 2.3 FTP q 2.4 Electronic Mail v SMTP,
Chapter 2 Application Layer
 Chapter 2 Application Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Chapter 2 Application Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Different Layers Lecture 21
 Different Layers Lecture 21 10/17/2003 Jian Ren 1 The Transport Layer 10/17/2003 Jian Ren 2 Transport Services and Protocols Provide logical communication between app processes running on different hosts
Different Layers Lecture 21 10/17/2003 Jian Ren 1 The Transport Layer 10/17/2003 Jian Ren 2 Transport Services and Protocols Provide logical communication between app processes running on different hosts
Adapting Functionality for Mobile Terminals
 Adapting Email Functionality for Mobile Terminals Jon-Finngard Moe 1, Eivind Sivertsen 1, and Do van Thanh 2 1 Norwegian University of Science and Technology, 7491 Trondheim, Norway {jonfinng, eivindsi}@stud.ntnu.no
Adapting Email Functionality for Mobile Terminals Jon-Finngard Moe 1, Eivind Sivertsen 1, and Do van Thanh 2 1 Norwegian University of Science and Technology, 7491 Trondheim, Norway {jonfinng, eivindsi}@stud.ntnu.no
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Mobile IP. Mobile Computing. Mobility versus Portability
 Mobile IP Mobile Computing Introduction Amount of mobile/nomadic computing expected to increase dramatically in near future. By looking at the great acceptance of mobile telephony, one can foresee a similar
Mobile IP Mobile Computing Introduction Amount of mobile/nomadic computing expected to increase dramatically in near future. By looking at the great acceptance of mobile telephony, one can foresee a similar
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
Mobility Management for VoIP on Heterogeneous Networks: Evaluation of Adaptive Schemes
 Mobility Management for VoIP on Heterogeneous Networks: Evaluation of Adaptive Schemes Authors:Massimo Bernaschi, Filippo Cacace, Giulio Lannello Presented by:rukmini Sarvamangala OBJECTIVE OF THE PAPER
Mobility Management for VoIP on Heterogeneous Networks: Evaluation of Adaptive Schemes Authors:Massimo Bernaschi, Filippo Cacace, Giulio Lannello Presented by:rukmini Sarvamangala OBJECTIVE OF THE PAPER
MOBILITY MANAGEMENT FOR PROVIDING QOS IN LOCAL AREA WIRELESS NETWORKS
 MOBILITY MANAGEMENT FOR PROVIDING QOS IN LOCAL AREA WIRELESS NETWORKS J. Antonio García-Macías, Franck Rousseau, Gilles Berger-Sabbatel, Leyla Toumi, Andrzej Duda LSR-IMAG Laboratory, Grenoble, France
MOBILITY MANAGEMENT FOR PROVIDING QOS IN LOCAL AREA WIRELESS NETWORKS J. Antonio García-Macías, Franck Rousseau, Gilles Berger-Sabbatel, Leyla Toumi, Andrzej Duda LSR-IMAG Laboratory, Grenoble, France
TECHNICAL BRIEFING: MOBILE ACCESS TO THE INTERNET. Bornholm, October 2003
 Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT) TECHNICAL BRIEFING: MOBILE ACCESS TO THE INTERNET Bornholm, October 2003
Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT) TECHNICAL BRIEFING: MOBILE ACCESS TO THE INTERNET Bornholm, October 2003
CCNA Exploration Network Fundamentals. Chapter 3 Application Layer Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 3 Application Layer Functionality and Protocols Application Layer Functionality and Protocols Applications: The Interface Between the Networks Horny/Coufal
CCNA Exploration Network Fundamentals Chapter 3 Application Layer Functionality and Protocols Application Layer Functionality and Protocols Applications: The Interface Between the Networks Horny/Coufal
M+NetMail Client User Guide
 M+NetMail Client User Guide Trademarks...M+NetMail TM, MyRealBox Apple Inc....Safari Microsoft Corporation...Outlook Express Mozilla... Thunderbird Novell, Inc...GroupWise QUALCOMM... Eudora Copyright
M+NetMail Client User Guide Trademarks...M+NetMail TM, MyRealBox Apple Inc....Safari Microsoft Corporation...Outlook Express Mozilla... Thunderbird Novell, Inc...GroupWise QUALCOMM... Eudora Copyright
m-roam: A Service Invocation and Roaming Framework for Pervasive Computing
 m-roam: A Service Invocation and Roaming Framework for Pervasive Computing Alvin Chin Dept. of Computer Science University of Toronto achin@cs.toronto.edu Kostas Kontogiannis Dept. of Electrical and Computer
m-roam: A Service Invocation and Roaming Framework for Pervasive Computing Alvin Chin Dept. of Computer Science University of Toronto achin@cs.toronto.edu Kostas Kontogiannis Dept. of Electrical and Computer
A Location Model for Ambient Intelligence
 A Location Model for Ambient Intelligence National Institute of Informatics, Japan Email: ichiro@nii.ac.jp Outline 1. Motivation 2. Approach 3. Location Model 4. Design and Implementation 5. Applications
A Location Model for Ambient Intelligence National Institute of Informatics, Japan Email: ichiro@nii.ac.jp Outline 1. Motivation 2. Approach 3. Location Model 4. Design and Implementation 5. Applications
CompTIA MB CompTIA Mobility+
 CompTIA MB0-001 CompTIA Mobility+ http://killexams.com/exam-detail/mb0-001 QUESTION: 268 Users in a building report difficulty connecting and slow performance when using mobile devices. The issue is intermittent
CompTIA MB0-001 CompTIA Mobility+ http://killexams.com/exam-detail/mb0-001 QUESTION: 268 Users in a building report difficulty connecting and slow performance when using mobile devices. The issue is intermittent
Configuring Your Client: Outlook 98. Quick Reference
 Configuring Your Email Client: Outlook 98 Quick Reference Table of Contents Chapter 1. Introduction...1-1 What is an Email Client?...1-1 Who Should Read This Manual?...1-1 POP, IMAP, and SSL: Which Protocol
Configuring Your Email Client: Outlook 98 Quick Reference Table of Contents Chapter 1. Introduction...1-1 What is an Email Client?...1-1 Who Should Read This Manual?...1-1 POP, IMAP, and SSL: Which Protocol
Note: CONTENTS. 1. Outlook Express (IMAP) 2. Microsoft Outlook (IMAP) 3. Eudora (IMAP) 4. Thunderbird (IMAP) 5. Outlook Express (POP)
 CONTENTS 1. Outlook Express (IMAP) 2. Microsoft Outlook (IMAP) 3. Eudora (IMAP) 4. Thunderbird (IMAP) 5. Outlook Express (POP) Note: Prior to configuring, please ensure that your ID is enabled for POP/IMAP.
CONTENTS 1. Outlook Express (IMAP) 2. Microsoft Outlook (IMAP) 3. Eudora (IMAP) 4. Thunderbird (IMAP) 5. Outlook Express (POP) Note: Prior to configuring, please ensure that your ID is enabled for POP/IMAP.
This is the published version of a paper presented at Workshop on Innovative Mobile Applications of Context (IMAC) at MobileHCI 2006, Espoo, Finland.
 http://www.diva-portal.org This is the published version of a paper presented at Workshop on Innovative Mobile Applications of Context (IMAC) at MobileHCI 2006, Espoo, Finland. Citation for the original
http://www.diva-portal.org This is the published version of a paper presented at Workshop on Innovative Mobile Applications of Context (IMAC) at MobileHCI 2006, Espoo, Finland. Citation for the original
Change NetSet Settings on an Apple ios 12 Mobile Device using the Mail app
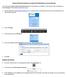 Change NetSet Email Settings on an Apple ios 12 Mobile Device using the Mail app You were issued a new random email password about a week before the migration. If you haven t done so already, you should
Change NetSet Email Settings on an Apple ios 12 Mobile Device using the Mail app You were issued a new random email password about a week before the migration. If you haven t done so already, you should
SUPERHUB OFFICE 365 OUTLOOK POP3 SETUP GUIDE
 SUPERHUB OFFICE 365 OUTLOOK POP3 SETUP GUIDE 2018 Superhub Limited. All right reserved. Table of Contents 1. Get Started... 3 2. Add New Account... 5 3. Get Help and Support... 10 The guide is to describe
SUPERHUB OFFICE 365 OUTLOOK POP3 SETUP GUIDE 2018 Superhub Limited. All right reserved. Table of Contents 1. Get Started... 3 2. Add New Account... 5 3. Get Help and Support... 10 The guide is to describe
Electronic Mail
 Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
Internet Technology 4/29/2013
 Session Initiation Protocol (SIP) Internet Technology 14. VoIP and Traversal Paul Krzyzanowski Rutgers University Spring 2013 Dominant protocol for Voice over IP (VoIP) RFC 3261 llows a call to be established
Session Initiation Protocol (SIP) Internet Technology 14. VoIP and Traversal Paul Krzyzanowski Rutgers University Spring 2013 Dominant protocol for Voice over IP (VoIP) RFC 3261 llows a call to be established
Internet Architecture
 Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
CSC 401 Data and Computer Communications Networks
 CSC 401 Data and Computer Communications Networks Application Layer: Cookies, Web Caching, SMTP Sec 2.2.4-2.4 Prof. Lina Battestilli Fall 2017 Outline Application Layer (ch 2) 2.1 principles of network
CSC 401 Data and Computer Communications Networks Application Layer: Cookies, Web Caching, SMTP Sec 2.2.4-2.4 Prof. Lina Battestilli Fall 2017 Outline Application Layer (ch 2) 2.1 principles of network
Name Resolution and Service Discovery on the Internet and in Ad Hoc Networks
 Chapter 8 Name Resolution and Service Discovery on the Internet and in Ad Hoc Networks Paal E. Engelstad and Geir Egeland CONTENTS Name Resolution... 172 An Architecture for Naming Services... 173 A Generic
Chapter 8 Name Resolution and Service Discovery on the Internet and in Ad Hoc Networks Paal E. Engelstad and Geir Egeland CONTENTS Name Resolution... 172 An Architecture for Naming Services... 173 A Generic
Innovation and Cryptoventures. Technology 101. Lee Jacobs and Campbell R. Harvey. February 22, 2017
 Innovation and Cryptoventures Technology 101 Lee Jacobs and Campbell R. Harvey February 22, 2017 What is a computer? Electronic device that has the ability to store, retrieve, and process data Hardware
Innovation and Cryptoventures Technology 101 Lee Jacobs and Campbell R. Harvey February 22, 2017 What is a computer? Electronic device that has the ability to store, retrieve, and process data Hardware
Computer Networks, Andrew Tannenbaum, Chapter 5.6. Computer Networking: A Top Down Approach Featuring the
 Mobile IP (IPv4 and IPv6) Dr. John Keeney 3BA33 Elements of a wireless Wired infrastructure wireless hosts laptop, PDA, IP phone run applications may be stationary (nonmobile) or mobile wireless does not
Mobile IP (IPv4 and IPv6) Dr. John Keeney 3BA33 Elements of a wireless Wired infrastructure wireless hosts laptop, PDA, IP phone run applications may be stationary (nonmobile) or mobile wireless does not
Quick Start Guide for Windows
 for Windows The Eudora 5.1 User Manual for Windows is on the Eudora CD included in the product box. If you prefer a printed and bound copy, you can purchase one from www.eudora.com or call 1-800-2-EUDORA
for Windows The Eudora 5.1 User Manual for Windows is on the Eudora CD included in the product box. If you prefer a printed and bound copy, you can purchase one from www.eudora.com or call 1-800-2-EUDORA
Department of Computer Science. Burapha University 6 SIP (I)
 Burapha University ก Department of Computer Science 6 SIP (I) Functionalities of SIP Network elements that might be used in the SIP network Structure of Request and Response SIP messages Other important
Burapha University ก Department of Computer Science 6 SIP (I) Functionalities of SIP Network elements that might be used in the SIP network Structure of Request and Response SIP messages Other important
An Architecture for Personal Broadband. Broadband Working Group Elisabeth Maida, MIT May 25, 2006
 An Architecture for Personal Broadband Broadband Working Group Elisabeth Maida, MIT May 25, 2006 Agenda The Vision of Personal Broadband Our Approach Define the potential business models Identify the functional
An Architecture for Personal Broadband Broadband Working Group Elisabeth Maida, MIT May 25, 2006 Agenda The Vision of Personal Broadband Our Approach Define the potential business models Identify the functional
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 Mobile IP 2 Mobile Network Layer: Problems and Concerns Entities and Terminology in Mobile IP Mobile Indirect Routing Mobile IP Agent Advertisement Registration
Mohammad Hossein Manshaei manshaei@gmail.com 1393 Mobile IP 2 Mobile Network Layer: Problems and Concerns Entities and Terminology in Mobile IP Mobile Indirect Routing Mobile IP Agent Advertisement Registration
On Accessing GSM-enabled Mobile Sensors
 On Accessing GSM-enabled Mobile Sensors Zissis K. Plitsis, # Ioannis Fudos, Evaggelia Pitoura and Apostolos Zarras Department of Computer Science, University of Ioannina, Greece {zplitsis, fudos, pitoura,
On Accessing GSM-enabled Mobile Sensors Zissis K. Plitsis, # Ioannis Fudos, Evaggelia Pitoura and Apostolos Zarras Department of Computer Science, University of Ioannina, Greece {zplitsis, fudos, pitoura,
An Overview of Cisco MobilityManager
 CHAPTER 1 An Overview of Cisco MobilityManager This chapter describes Cisco MobilityManager and includes these sections: Key Features and Benefits, page 1-4 Use Case Examples, page 1-5 Compatibility with
CHAPTER 1 An Overview of Cisco MobilityManager This chapter describes Cisco MobilityManager and includes these sections: Key Features and Benefits, page 1-4 Use Case Examples, page 1-5 Compatibility with
Homework 2 assignment for ECE374 Posted: 02/20/15 Due: 02/27/15
 ECE374: Homework 2 1 Homework 2 assignment for ECE374 Posted: 02/20/15 Due: 02/27/15 ote: In all written assignments, please show as much of your work as you can. Even if you get a wrong answer, you can
ECE374: Homework 2 1 Homework 2 assignment for ECE374 Posted: 02/20/15 Due: 02/27/15 ote: In all written assignments, please show as much of your work as you can. Even if you get a wrong answer, you can
TAXII 1.0 (DRAFT) Capabilities and Services. Charles Schmidt & Mark Davidson
 TAXII 1.0 (DRAFT) Capabilities and Services Charles Schmidt & Mark Davidson 2 About This Talk Look at the use scenarios we want to support and how we have designed TAXII to support them TAXII supports
TAXII 1.0 (DRAFT) Capabilities and Services Charles Schmidt & Mark Davidson 2 About This Talk Look at the use scenarios we want to support and how we have designed TAXII to support them TAXII supports
Set up an Account in Outlook 2003
 Set up an Email Account in Outlook 2003 This tutorial will show you how to set up an email account in Outlook 2003. The creation of standard POP3 or IMAP email accounts will be covered, but you can set
Set up an Email Account in Outlook 2003 This tutorial will show you how to set up an email account in Outlook 2003. The creation of standard POP3 or IMAP email accounts will be covered, but you can set
Panel 1 Service Platform and Network Infrastructure for Ubiquitous Services
 Panel 1 Platform and Network Infrastructure for Ubiquitous s Wolfgang Kellerer DoCoMo Euro-Labs Munich, Germany WWRF WG2 ( Architecture) Vice Chair DoCoMo Communications Landsberger Str. 312 80687 Munich
Panel 1 Platform and Network Infrastructure for Ubiquitous s Wolfgang Kellerer DoCoMo Euro-Labs Munich, Germany WWRF WG2 ( Architecture) Vice Chair DoCoMo Communications Landsberger Str. 312 80687 Munich
The Application Layer: SMTP, FTP
 The Application Layer: SMTP, FTP CS 352, Lecture 5 http://www.cs.rutgers.edu/~sn624/352-s19 Srinivas Narayana 1 Recap: Application-layer protocols DNS: lookup a (machine-readable) address using a (humanreadable)
The Application Layer: SMTP, FTP CS 352, Lecture 5 http://www.cs.rutgers.edu/~sn624/352-s19 Srinivas Narayana 1 Recap: Application-layer protocols DNS: lookup a (machine-readable) address using a (humanreadable)
Fasthosts Customer Support. Standard Mailbox Setup Guide
 Fasthosts Customer Support Standard Mailbox Setup Guide Standard Mailbox Setup Guide Setting up a Standard mailbox only takes a few minutes. You can set up any email software to receive email from your
Fasthosts Customer Support Standard Mailbox Setup Guide Standard Mailbox Setup Guide Setting up a Standard mailbox only takes a few minutes. You can set up any email software to receive email from your
Computer Networks. More on Standards & Protocols Quality of Service. Week 10. College of Information Science and Engineering Ritsumeikan University
 Computer Networks More on Standards & Protocols Quality of Service Week 10 College of Information Science and Engineering Ritsumeikan University Introduction to Protocols l A protocol is a set of rules
Computer Networks More on Standards & Protocols Quality of Service Week 10 College of Information Science and Engineering Ritsumeikan University Introduction to Protocols l A protocol is a set of rules
Computer Networking. Chapter #1. Dr. Abdulrhaman Alameer
 Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Technical Overview. Version March 2018 Author: Vittorio Bertola
 Technical Overview Version 1.2.3 26 March 2018 Author: Vittorio Bertola vittorio.bertola@open-xchange.com This document is copyrighted by its authors and is released under a CC-BY-ND-3.0 license, which
Technical Overview Version 1.2.3 26 March 2018 Author: Vittorio Bertola vittorio.bertola@open-xchange.com This document is copyrighted by its authors and is released under a CC-BY-ND-3.0 license, which
IMS signalling for multiparty services based on network level multicast
 IMS signalling for multiparty services based on network level multicast Ivan Vidal, Ignacio Soto, Francisco Valera, Jaime Garcia, Arturo Azcorra UniversityCarlosIIIofMadrid Av.Universidad,30 E-28911, Madrid,
IMS signalling for multiparty services based on network level multicast Ivan Vidal, Ignacio Soto, Francisco Valera, Jaime Garcia, Arturo Azcorra UniversityCarlosIIIofMadrid Av.Universidad,30 E-28911, Madrid,
DISTRIBUTED COMPUTER SYSTEMS
 DISTRIBUTED COMPUTER SYSTEMS Communication Fundamental REMOTE PROCEDURE CALL Dr. Jack Lange Computer Science Department University of Pittsburgh Fall 2015 Outline Communication Architecture Fundamentals
DISTRIBUTED COMPUTER SYSTEMS Communication Fundamental REMOTE PROCEDURE CALL Dr. Jack Lange Computer Science Department University of Pittsburgh Fall 2015 Outline Communication Architecture Fundamentals
Content. 1. Introduction. 2. The Ad-hoc On-Demand Distance Vector Algorithm. 3. Simulation and Results. 4. Future Work. 5.
 Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
CSC 4900 Computer Networks:
 CSC 4900 Computer Networks: Email Professor Henry Carter Fall 2017 Villanova University Department of Computing Sciences Review Last week we talked about design principles, and the application protocols
CSC 4900 Computer Networks: Email Professor Henry Carter Fall 2017 Villanova University Department of Computing Sciences Review Last week we talked about design principles, and the application protocols
TRANSMISSION CONTROL PROTOCOL. ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016
 TRANSMISSION CONTROL PROTOCOL ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016 ETI 2506 - TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember 1.
TRANSMISSION CONTROL PROTOCOL ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016 ETI 2506 - TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember 1.
 Page 1 of 6 Eudora 7.x - E-mail Client for Microsoft Windows Links for Eudora 7.x: First account Edit accounts Light Mode Mailboxes Filters Headers Anti-Spam Links on this page: SMTP Authentication Auto-dial/Auto-disconnect
Page 1 of 6 Eudora 7.x - E-mail Client for Microsoft Windows Links for Eudora 7.x: First account Edit accounts Light Mode Mailboxes Filters Headers Anti-Spam Links on this page: SMTP Authentication Auto-dial/Auto-disconnect
Network Services, Cloud Computing and Virtualization
 Network Services, Cloud Computing and Virtualization Client Side Virtualization Purpose of virtual machines Resource requirements Emulator requirements Security requirements Network requirements Hypervisor
Network Services, Cloud Computing and Virtualization Client Side Virtualization Purpose of virtual machines Resource requirements Emulator requirements Security requirements Network requirements Hypervisor
Software-Defined Access Wireless
 Introduction to, page 1 Configuring SD-Access Wireless (CLI), page 7 Enabling SD-Access Wireless (GUI), page 8 Configuring SD-Access Wireless VNID (GUI), page 9 Configuring SD-Access Wireless WLAN (GUI),
Introduction to, page 1 Configuring SD-Access Wireless (CLI), page 7 Enabling SD-Access Wireless (GUI), page 8 Configuring SD-Access Wireless VNID (GUI), page 9 Configuring SD-Access Wireless WLAN (GUI),
Chapter 10: Application Layer
 Chapter 10: Application Layer Application, Session and Presentation Presentation and Session Layers Session layer Functions, creates, and maintains dialogs between source and destination applications Handles
Chapter 10: Application Layer Application, Session and Presentation Presentation and Session Layers Session layer Functions, creates, and maintains dialogs between source and destination applications Handles
Set Up with Microsoft Outlook 2013 using POP3
 Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
OpenTouch Conversation for iphone
 OpenTouch Conversation for iphone User Manual OmniPCX Office Rich Communication Edition user OpenTouch Business Edition and Multimedia Services Conversation user OpenTouch Business Edition and Mutimedia
OpenTouch Conversation for iphone User Manual OmniPCX Office Rich Communication Edition user OpenTouch Business Edition and Multimedia Services Conversation user OpenTouch Business Edition and Mutimedia
interface Question 1. a) Applications nslookup/dig Web Application DNS SMTP HTTP layer SIP Transport layer OSPF ICMP IP Network layer
 TDTS06 Computer networks, August 23, 2008 Sketched answers to the written examination, provided by Juha Takkinen, IDA, juhta@ida.liu.se. ( Sketched means that you, in addition to the below answers, need
TDTS06 Computer networks, August 23, 2008 Sketched answers to the written examination, provided by Juha Takkinen, IDA, juhta@ida.liu.se. ( Sketched means that you, in addition to the below answers, need
Administrator Guide. Find out how to set up and use MyKerio to centralize and unify your Kerio software administration.
 Administrator Guide Find out how to set up and use MyKerio to centralize and unify your Kerio software administration. The information and content in this document is provided for informational purposes
Administrator Guide Find out how to set up and use MyKerio to centralize and unify your Kerio software administration. The information and content in this document is provided for informational purposes
Understand iwag Solution for 3G Mobile Data
 Understand iwag Solution for 3G Mobile Data Contents Introduction Prerequisites Requirements Components Used Background Information Acronyms Explanation of Terminology Used Understand Mobility Services
Understand iwag Solution for 3G Mobile Data Contents Introduction Prerequisites Requirements Components Used Background Information Acronyms Explanation of Terminology Used Understand Mobility Services
Internet Technology. 03r. Application layer protocols: . Paul Krzyzanowski. Rutgers University. Spring 2016
 Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
Service Discovery in Pervasive Computing Environments
 Service Discovery in Pervasive Computing Environments Presented by Jamal Lewis and Shruti Pathak CS 570 Computer Networks Instructor Dr. Feng Zhu Introduction What is it? Pervasive Computing Environments
Service Discovery in Pervasive Computing Environments Presented by Jamal Lewis and Shruti Pathak CS 570 Computer Networks Instructor Dr. Feng Zhu Introduction What is it? Pervasive Computing Environments
10x. Communication systems designed exclusively for small businesses. Automated Back-up /Web Server Internet Security LAN Network WAN Access
 Allworx 10x Product Specifications Communication systems designed exclusively for small businesses Phone system Full PBX & Key System Remote User Site-to-Site Access Unified Messaging Voice Over Internet
Allworx 10x Product Specifications Communication systems designed exclusively for small businesses Phone system Full PBX & Key System Remote User Site-to-Site Access Unified Messaging Voice Over Internet
CS 43: Computer Networks. 12: and SMTP September 28, 2018
 CS 43: Computer Networks 12: Email and SMTP September 28, 2018 A. HTTP Mail s communicate using B. IMAP C. POP D. SMTP Lecture 12 - Slide 2 Mail s typically A. send messages directly from the sending s
CS 43: Computer Networks 12: Email and SMTP September 28, 2018 A. HTTP Mail s communicate using B. IMAP C. POP D. SMTP Lecture 12 - Slide 2 Mail s typically A. send messages directly from the sending s
Outlook Express(POP3)
 Outlook Express(POP3) 1. Click on Tools in the menu bar and then go to Accounts 2. The Internet Accounts pop-up window appears. 3. Click on the Mail tab. If you are starting Outlook Express for the first
Outlook Express(POP3) 1. Click on Tools in the menu bar and then go to Accounts 2. The Internet Accounts pop-up window appears. 3. Click on the Mail tab. If you are starting Outlook Express for the first
Install & Configure Thunderbird E- mail
 Install & Configure Thunderbird E- mail Thunderbird is a free, open source mail client that runs on Windows, Mac, and Linux. This document will cover specific information about setting up Thunderbird 2
Install & Configure Thunderbird E- mail Thunderbird is a free, open source mail client that runs on Windows, Mac, and Linux. This document will cover specific information about setting up Thunderbird 2
The Ubiquitous Web. Dave Raggett (W3C/Volantis) CE2006, 19 September Contact:
 The Ubiquitous Web Dave Raggett (W3C/Volantis) CE2006, 19 September 2006 Contact: dsr@w3.org Web of Everything Incorporates a very wide range of devices Physical world of sensors and effectors Access to
The Ubiquitous Web Dave Raggett (W3C/Volantis) CE2006, 19 September 2006 Contact: dsr@w3.org Web of Everything Incorporates a very wide range of devices Physical world of sensors and effectors Access to
Software-Defined Access Wireless
 Introduction to, page 1 Configuring SD-Access Wireless (CLI), page 7 Introduction to The Enterprise Fabric provides end-to-end enterprise-wide segmentation, flexible subnet addressing, and controller-based
Introduction to, page 1 Configuring SD-Access Wireless (CLI), page 7 Introduction to The Enterprise Fabric provides end-to-end enterprise-wide segmentation, flexible subnet addressing, and controller-based
Setup Guide. Page 0
 Email Setup Guide Page 0 Table of Contents Mailbox Setup Guide... 2 Before you Start... 2 Desktop Mail Clients... 3 Outlook 2016 setup... 3 Outlook 2013 setup... 7 Outlook 2010 setup... 12 Windows 10 Mail
Email Setup Guide Page 0 Table of Contents Mailbox Setup Guide... 2 Before you Start... 2 Desktop Mail Clients... 3 Outlook 2016 setup... 3 Outlook 2013 setup... 7 Outlook 2010 setup... 12 Windows 10 Mail
Last time. BGP policy. Broadcast / multicast routing. Link virtualization. Spanning trees. Reverse path forwarding, pruning Tunneling
 Last time BGP policy Broadcast / multicast routing Spanning trees Source-based, group-shared, center-based Reverse path forwarding, pruning Tunneling Link virtualization Whole networks can act as an Internet
Last time BGP policy Broadcast / multicast routing Spanning trees Source-based, group-shared, center-based Reverse path forwarding, pruning Tunneling Link virtualization Whole networks can act as an Internet
E mail Setup Guide for Microsoft Outlook 2002, 2003 & 2007
 E mail Setup Guide for Microsoft Outlook 2002, 2003 & 2007 Summary of Settings Incoming mail server (POP3): mail.everythinggraphic.com Outgoing mail server (SMTP): mail.everythinggraphic.com Important:
E mail Setup Guide for Microsoft Outlook 2002, 2003 & 2007 Summary of Settings Incoming mail server (POP3): mail.everythinggraphic.com Outgoing mail server (SMTP): mail.everythinggraphic.com Important:
Introduction to Information Science and Technology 2017 Networking II. Sören Schwertfeger 师泽仁
 II Sören Schwertfeger 师泽仁 Outline Review Network Layer Routing Transport Layer Applications HTTP Demos Internet: Huge network of networks Billions of hosts (computers) Internet Structure Network Edge:
II Sören Schwertfeger 师泽仁 Outline Review Network Layer Routing Transport Layer Applications HTTP Demos Internet: Huge network of networks Billions of hosts (computers) Internet Structure Network Edge:
Simple Jabber - Divide And Conquer XMPP
 Simple Jabber - Divide And Conquer XMPP Jan Klemkow 30.08.2015 Abstract The Extensible Messaging and Presence Protocol (XMPP) 1 is like the web. It is far too complex to be implemented in one program with
Simple Jabber - Divide And Conquer XMPP Jan Klemkow 30.08.2015 Abstract The Extensible Messaging and Presence Protocol (XMPP) 1 is like the web. It is far too complex to be implemented in one program with
Making life simpler for remote and mobile workers
 : Technology GoToMyPC Technology Making life simpler for remote and mobile workers Learn why GoToMyPC is the most secure, cost-effective and easy-to-use solution for providing remote access to the desktop.
: Technology GoToMyPC Technology Making life simpler for remote and mobile workers Learn why GoToMyPC is the most secure, cost-effective and easy-to-use solution for providing remote access to the desktop.
Networking. Layered Model. DoD Model. Application Layer. ISO/OSI Model
 Networking Networking is concerned with the physical topology of two or more communicating entities and the logical topology of data transmission. Layered Model Systems communicate over a shared communication
Networking Networking is concerned with the physical topology of two or more communicating entities and the logical topology of data transmission. Layered Model Systems communicate over a shared communication
Abstract. Table of Contents. 1. License
 Your use of this Specification may be subject to other third party rights. THIS SPECIFICATION IS PROVIDED AS IS. The contributors expressly disclaim any warranties (express, implied, or otherwise), including
Your use of this Specification may be subject to other third party rights. THIS SPECIFICATION IS PROVIDED AS IS. The contributors expressly disclaim any warranties (express, implied, or otherwise), including
System Architecture Model Version 1.1 WV Tracking Number: WV-020
 System Architecture Model Version 1.1 WV Tracking Number: WV-020 Notice Copyright 2001-2002 Ericsson, Motorola and Nokia. All Rights Reserved. Implementation of all or part of any Specification may require
System Architecture Model Version 1.1 WV Tracking Number: WV-020 Notice Copyright 2001-2002 Ericsson, Motorola and Nokia. All Rights Reserved. Implementation of all or part of any Specification may require
Introduction to Networking
 Introduction to Networking The fundamental purpose of data communications is to exchange information between user's computers, terminals and applications programs. Simplified Communications System Block
Introduction to Networking The fundamental purpose of data communications is to exchange information between user's computers, terminals and applications programs. Simplified Communications System Block
IrDA INTEROPERABILITY
 Part F:2 IrDA INTEROPERABILITY The IrOBEX protocol is utilized by the Bluetooth technology. In Bluetooth, OBEX offers same features for applications as within the IrDA protocol hierarchy and enabling the
Part F:2 IrDA INTEROPERABILITY The IrOBEX protocol is utilized by the Bluetooth technology. In Bluetooth, OBEX offers same features for applications as within the IrDA protocol hierarchy and enabling the
OpenTouch Conversation for Android Smartphone
 OpenTouch Conversation for Android Smartphone User Manual OmniPCX Office Rich Communication Edition user OpenTouch Business Edition and Multimedia Services Conversation user OpenTouch Business Edition
OpenTouch Conversation for Android Smartphone User Manual OmniPCX Office Rich Communication Edition user OpenTouch Business Edition and Multimedia Services Conversation user OpenTouch Business Edition
Planning, Deploying, and Monitoring Mobility Microsoft Lync Server 2010
 Microsoft Lync Server 2010 Published: March 2012 This document is provided as-is. Information and views expressed in this document, including URL and other Internet Web site references, may change without
Microsoft Lync Server 2010 Published: March 2012 This document is provided as-is. Information and views expressed in this document, including URL and other Internet Web site references, may change without
The Undo Sent (USE) Protocol
 International Journal of Information and Computation Technology. ISSN 0974-2239 Volume 3, Number 6 (2013), pp. 593-602 International Research Publications House http://www. irphouse.com /ijict.htm The
International Journal of Information and Computation Technology. ISSN 0974-2239 Volume 3, Number 6 (2013), pp. 593-602 International Research Publications House http://www. irphouse.com /ijict.htm The
Interdomain Federation Guide for IM and Presence Service on Cisco Unified Communications Manager, Release 11.5(1)SU2
 Interdomain Federation Guide for IM and Presence Service on Cisco Unified Communications Manager, Release 11.5(1)SU2 First Published: 2017-11-29 Last Modified: 2017-12-01 Americas Headquarters Cisco Systems,
Interdomain Federation Guide for IM and Presence Service on Cisco Unified Communications Manager, Release 11.5(1)SU2 First Published: 2017-11-29 Last Modified: 2017-12-01 Americas Headquarters Cisco Systems,
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
