30th March 2019 People Over Pixels
|
|
|
- Geraldine Roberts
- 5 years ago
- Views:
Transcription
1 30th March 2019 People Over Pixels
2 Finding BountyCon CTF flags Kishan Bagaria
3 $ whoami # " indie software engineer by trade # security enthusiast # first hack: probably the time I bypassed the BIOS password my father set when I was 6 &
4 $ whoami # found 30 flags (18 FB, 12 Google) in the BountyCon CTF between Jan 10th and 29th # my rank: # that's not an error code. it's the total number of participants :)
5
6 also found these flags which weren't accepted
7 FB: Challenge # flag present in submit flag endpoint # initially didn't expect the form to have any vulnerabilities since it was crafted by security engineers # after finding other flags in security/whitehat related pages, I realized this was a good place to hide a flag
8 FB: Challenge # let's inspect the form using developer tools # unusual `user_id` param # can you submit a flag for another user?
9 FB: IDOR Challenge # set the user_id param to a valid user ID # you can set it to 4 the smallest valid user ID belonging to this guy # pretty sure he wasn't playing in the CTF so even if there was a legit IDOR here, you wouldn't have increased his flags count meaningfully # jk. don't test possible vulnerabilities with accounts that you don't control
10 FB: IDOR Challenge # after changing the param, submit the form # popup appears with the flag:
11 FB: IDOR Challenge 88 points
12 Google: # lots of storage buckets around the web have directory listing set to public causing data breaches # what if there's a bucket named "bountycon"? # let's open in a browser
13 Google: Public Cloudstore Bucket
14 Google: Public Cloudstore Bucket file named dec-5-data.csv exists in the bucket and it's huge 1.55GiB! you have to download it to find the flag. use wget/curl and download on a server to download faster
15 Google: Public Cloudstore Bucket grep the file to find the flag:
16 Google: Public Cloudstore Bucket 99 points
17 Google: Bug Hunter University Steganography # most of the Google flags were in security related pages # the Bug Hunter University site has a flag hidden in the "BountyCon.ics" file that you could find by searching for "BountyCon":
18 Google: Bug Hunter University Steganography # after finding the ICS file, I tried to list all other files that might been added/updated on the site # Google Sites exposes an endpoint for getting the RSS feed: # the RSS feed gave away that: # the home page was updated around the time ( ) the ICS file was added ( ) # on , bug200_new.jpg and bug200_new (1).jpg were uploaded # only the latter image was linked on the home page, the other is simply a dud that nobody deleted # bug200_new (1).jpg seemed like a suspicious file name because of "_new" and "(1)"
19 Google: Bug Hunter University Steganography # if you're a CTF player and you see an interesting image, the first thing that will come to your mind is steganography # lots of different steganography tools # use steghide to extract data from the image # a file named flag.txt will be extracted with the flag:
20 Google: Bug Hunter University Steganography steghide not installed? you can instead use an online wrapper of steghide:
21 Google: Bug Hunter University Steganography 100 points
22 Google: TLS Certificate # what if there's a secret site where you can find more BountyCon challenges? # you can make up a bunch of possible links and try accessing them: # bountycon.google.com, bountycon.facebook.com, bountycon.fb.com # goo.gl/bountycon, fb.com/bountycon # you can also search certificate transparency logs if any certificate was issued for a domain matching "bountycon"
23 Google: TLS Certificate crt.sh is one of the sites you can use to search certificate transparency logs:
24 Google: TLS Certificate # there's a match: bountycon.corp.google.com # *.corp.google.com addresses are only accessible over Google's internal networks # there are no public DNS records for that domain # it's entirely possible that the site is for Google employees to assist them with something BountyCon related
25 Google: TLS Certificate # let's inspect the certificate # you'll notice the cert has been issued for two extra domains with random seeming subdomains:
26 Google: TLS Certificate # `ijxxk3tupfbw63t3mu2dkzdemfstkyrzgm4tim3bg` and `y4tqylbmjrtqm3fmvqwmn3fmi3dszlegbstkylbpu` look like encoded strings or link fragments # base64 obviously requires upper case characters and DNS names cannot have them # so it must be in base32!
27 Google: TLS Certificate base32 decode both subdomains together to get the flag:
28 Google: TLS Certificate 100 points
29 random tips # ask yourself, "where would I hide a flag if I had to hide one?" # note down good ideas of what you tried but didn't work, because it might in the future # look for patterns # most of the BountyCon flags were in security/whitehat related pages # both Google and Facebook had a flag hidden in their respective vulnerability submission pages # put your computer to use. use automated tools to notify you when a potential flag is found # like Burp Suite or any proxy that constantly searches network traffic for string matches
30 $ exit full writeup of all 30 on KishanBagaria.com
31 $ exit # reach out on # twitter: # hi@kishan.info # official BountyCon Slack # IRL I don't bite
32 $ exit thanks for listening!
CTF Workshop. Crim Synopsys, Inc. 1
 CTF Workshop Crim2018 31.10.2018 2018 Synopsys, Inc. 1 CTF (Capture the Flag) Capture the Flag (CTF) is a computer security competition. CTF are usually designed test and teach computer security skills.
CTF Workshop Crim2018 31.10.2018 2018 Synopsys, Inc. 1 CTF (Capture the Flag) Capture the Flag (CTF) is a computer security competition. CTF are usually designed test and teach computer security skills.
Supplemental Use of the Master Shorty Software Locustware.com 2016 This tutorial has been provided for you by: Gary Affron
 Supplemental Use of the Master Shorty Software Locustware.com 2016 This tutorial has been provided for you by: Gary Affron The Master Shorty is an extremely Effective Tool that at First Glance hides its
Supplemental Use of the Master Shorty Software Locustware.com 2016 This tutorial has been provided for you by: Gary Affron The Master Shorty is an extremely Effective Tool that at First Glance hides its
TOP 7 UPDATES IN LOCAL SEARCH FOR JANUARY 2015 YAHOO DIRECTORY NOW OFFICALLY CLOSED GOOGLE INTRODUCES NEWADWORDS TOOL AD CUSTOMIZERS
 Changes In Google And Bing Local Results Penguin Update Continues To Affect Local Rankings How To Add A sticky Post on Google+ page TOP 7 UPDATES IN LOCAL SEARCH FOR JANUARY 2015 0 Facebook Allows Calls-To-Action
Changes In Google And Bing Local Results Penguin Update Continues To Affect Local Rankings How To Add A sticky Post on Google+ page TOP 7 UPDATES IN LOCAL SEARCH FOR JANUARY 2015 0 Facebook Allows Calls-To-Action
High Quality Inbound Links For Your Website Success
 Axandra How To Get ö Benefit from tested linking strategies and get more targeted visitors. High Quality Inbound Links For Your Website Success How to: ü Ü Build high quality inbound links from related
Axandra How To Get ö Benefit from tested linking strategies and get more targeted visitors. High Quality Inbound Links For Your Website Success How to: ü Ü Build high quality inbound links from related
Can't Add Songs To Iphone From Itunes 11 >>>CLICK HERE<<<
 Can't Add Songs To Iphone From Itunes 11 Plug in your iphone or ipad running ios 8 or higher and launch itunes. Even for my ipod touch, for which I have a 64GB, I have to add genres one by Make sure you
Can't Add Songs To Iphone From Itunes 11 Plug in your iphone or ipad running ios 8 or higher and launch itunes. Even for my ipod touch, for which I have a 64GB, I have to add genres one by Make sure you
Main area: Security Additional areas: Digital Access, Information Literacy, Privacy and Reputation
 Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
Configure Unsanctioned Device Access Control
 Configure Unsanctioned Device Access Control paloaltonetworks.com/documentation Contact Information Corporate Headquarters: Palo Alto Networks 3000 Tannery Way Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-support
Configure Unsanctioned Device Access Control paloaltonetworks.com/documentation Contact Information Corporate Headquarters: Palo Alto Networks 3000 Tannery Way Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-support
FileWave 10 Webinar Q&A
 FileWave 10 Webinar Q&A When will 10 be released? October 14 th, but you can sign up today to get into the beta program. Link: www.filewave.com/beta-program How stable is the beta? Should we use it for
FileWave 10 Webinar Q&A When will 10 be released? October 14 th, but you can sign up today to get into the beta program. Link: www.filewave.com/beta-program How stable is the beta? Should we use it for
H1-212 Capture the Flag Solution Author: Corben Douglas
 H1-212 Capture the Flag Solution Author: Corben Douglas (@sxcurity) Description: An engineer of acme.org launched a new server for a new admin panel at http://104.236.20.43/. He is completely confident
H1-212 Capture the Flag Solution Author: Corben Douglas (@sxcurity) Description: An engineer of acme.org launched a new server for a new admin panel at http://104.236.20.43/. He is completely confident
Gmail Error Code 21 Itunes Fix >>>CLICK HERE<<<
 Gmail Error Code 21 Itunes Fix Video How to fix error 21 on Itunes!!!! sorry for the AVS thing in the How to Fix Error code 3194,1600, 21, 1 on Itunes and Restore / Update to New IOS 7 / 8 (HD) i accept
Gmail Error Code 21 Itunes Fix Video How to fix error 21 on Itunes!!!! sorry for the AVS thing in the How to Fix Error code 3194,1600, 21, 1 on Itunes and Restore / Update to New IOS 7 / 8 (HD) i accept
Getting Started. Opening TM Control Panel. TM Control Panel User Guide Getting Started 1
 TM Control Panel User Guide Getting Started 1 Getting Started Opening TM Control Panel To open TM Control Panel (CP), perform the following steps: 1 In the browser address field, type https://cp.netmyne.net.
TM Control Panel User Guide Getting Started 1 Getting Started Opening TM Control Panel To open TM Control Panel (CP), perform the following steps: 1 In the browser address field, type https://cp.netmyne.net.
I always recommend diversifying and testing more than one source, but make sure it is as targeted as possible.
 With traffic there are two real kinds - free and paid. I always recommend diversifying and testing more than one source, but make sure it is as targeted as possible. More often than not, I've had people
With traffic there are two real kinds - free and paid. I always recommend diversifying and testing more than one source, but make sure it is as targeted as possible. More often than not, I've had people
The Way of the Bounty. by David Sopas
 The Way of the Bounty by David Sopas (@dsopas) ./whoami Security Consultant for Checkmarx Security Team Leader for Char49 Disclosed more than 50 security advisories Founder of WebSegura.net Love to hack
The Way of the Bounty by David Sopas (@dsopas) ./whoami Security Consultant for Checkmarx Security Team Leader for Char49 Disclosed more than 50 security advisories Founder of WebSegura.net Love to hack
MSI Sakib - Blogger, SEO Researcher and Internet Marketer
 About Author: MSI Sakib - Blogger, SEO Researcher and Internet Marketer Hi there, I am the Founder of Techmasi.com blog and CEO of Droid Digger (droiddigger.com) android app development team. I love to
About Author: MSI Sakib - Blogger, SEO Researcher and Internet Marketer Hi there, I am the Founder of Techmasi.com blog and CEO of Droid Digger (droiddigger.com) android app development team. I love to
How To Update My Iphone 4 To Ios 7 Without
 How To Update My Iphone 4 To Ios 7 Without Itunes Aug 25, 2014. IPhone, ipod Touch, and ipad ios Compatibility Chart If you are still using ios 4 Updating your device to ios 5 or later. a version of ios
How To Update My Iphone 4 To Ios 7 Without Itunes Aug 25, 2014. IPhone, ipod Touch, and ipad ios Compatibility Chart If you are still using ios 4 Updating your device to ios 5 or later. a version of ios
CNIT 129S: Securing Web Applications. Ch 12: Attacking Users: Cross-Site Scripting (XSS) Part 2
 CNIT 129S: Securing Web Applications Ch 12: Attacking Users: Cross-Site Scripting (XSS) Part 2 Finding and Exploiting XSS Vunerabilities Basic Approach Inject this string into every parameter on every
CNIT 129S: Securing Web Applications Ch 12: Attacking Users: Cross-Site Scripting (XSS) Part 2 Finding and Exploiting XSS Vunerabilities Basic Approach Inject this string into every parameter on every
Hunting Bugs in Web App. By Suleman Malik
 Hunting Bugs in Web App By Suleman Malik About Me About Me Suleman Malik is an independent security researcher and author specializing in web application security, IOS and Android application security.
Hunting Bugs in Web App By Suleman Malik About Me About Me Suleman Malik is an independent security researcher and author specializing in web application security, IOS and Android application security.
Text transcript of show #280. August 18, Microsoft Research: Trinity is a Graph Database and a Distributed Parallel Platform for Graph Data
 Hanselminutes is a weekly audio talk show with noted web developer and technologist Scott Hanselman and hosted by Carl Franklin. Scott discusses utilities and tools, gives practical how-to advice, and
Hanselminutes is a weekly audio talk show with noted web developer and technologist Scott Hanselman and hosted by Carl Franklin. Scott discusses utilities and tools, gives practical how-to advice, and
6 TIPS FOR IMPROVING YOUR WEB PRESENCE
 6 TIPS FOR IMPROVING YOUR WEB PRESENCE 6 TIPS FOR IMPROVING YOUR WEB PRESENCE We all want to get noticed on the web. If you are running a business you want to be on the first page in Google via organic
6 TIPS FOR IMPROVING YOUR WEB PRESENCE 6 TIPS FOR IMPROVING YOUR WEB PRESENCE We all want to get noticed on the web. If you are running a business you want to be on the first page in Google via organic
How To Remove Internet Explorer 7 And Install 6
 How To Remove Internet Explorer 7 And Install 6 Do I have to uninstall Internet Explorer 11 prior to installing 8 or 7? IE9, IE8, IE7 IE 6 and IE5.5 on Windows 8 desktop, Windows 7, Vista and XP, as well.
How To Remove Internet Explorer 7 And Install 6 Do I have to uninstall Internet Explorer 11 prior to installing 8 or 7? IE9, IE8, IE7 IE 6 and IE5.5 on Windows 8 desktop, Windows 7, Vista and XP, as well.
CS144 Final Review. Dec 4th, 2009 Tom Wiltzius
 CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
The following topics provide more information on user identity. Establishing User Identity Through Passive Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Qualys Indication of Compromise
 18 QUALYS SECURITY CONFERENCE 2018 Qualys Indication of Compromise Bringing IOC to the Next Level Chris Carlson VP, Product Management, Qualys, Inc. Adversary TTPs are Changing Early 2010s Zero-day Vulnerabilities
18 QUALYS SECURITY CONFERENCE 2018 Qualys Indication of Compromise Bringing IOC to the Next Level Chris Carlson VP, Product Management, Qualys, Inc. Adversary TTPs are Changing Early 2010s Zero-day Vulnerabilities
Helping the Compiler Help You. Thomas Dy
 Helping the Compiler Help You Thomas Dy Programming do { programmer.write_code(); if(lazy) { sleep(); } compile_code(); } while(compiler.has_errors()); Compiler: Me no speaky English Programmer: Compiler,
Helping the Compiler Help You Thomas Dy Programming do { programmer.write_code(); if(lazy) { sleep(); } compile_code(); } while(compiler.has_errors()); Compiler: Me no speaky English Programmer: Compiler,
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
Security For The People End-User Authentication Security On The Internet. Mark Stanislav
 Security For The People End-User Authentication Security On The Internet Mark Stanislav mstanislav@duosecurity.com A Few Notes on Research Methodology Worked backwards by establishing a list of services
Security For The People End-User Authentication Security On The Internet Mark Stanislav mstanislav@duosecurity.com A Few Notes on Research Methodology Worked backwards by establishing a list of services
FB Image Contest. Users Manual
 FB Image Contest Users Manual Table of contents Description.. 3 Step by step installation... 5 The administration interface.. 10 Creating a new contest... 13 Creating a Facebook Application.. 19 Adding
FB Image Contest Users Manual Table of contents Description.. 3 Step by step installation... 5 The administration interface.. 10 Creating a new contest... 13 Creating a Facebook Application.. 19 Adding
SAKAI.WFU.EDU. What is Sakai?
 SAKAI.WFU.EDU What is Sakai? Sakai is a free and open source online Collaboration and Learning Environment. Many users of Sakai deploy it to support teaching and learning, ad hoc group collaboration, support
SAKAI.WFU.EDU What is Sakai? Sakai is a free and open source online Collaboration and Learning Environment. Many users of Sakai deploy it to support teaching and learning, ad hoc group collaboration, support
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Uploading and Embedding Your Digital Story (YouTube/Wordpress Version)
 Uploading and Embedding Your Digital Story (YouTube/Wordpress Version) If you were using digital stories in your classroom, you wouldn't even need to upload the videos to the Internet; you could just watch
Uploading and Embedding Your Digital Story (YouTube/Wordpress Version) If you were using digital stories in your classroom, you wouldn't even need to upload the videos to the Internet; you could just watch
5/10/2009. Introduction. The light-saber is a Jedi s weapon not as clumsy or random as a blaster.
 The Hacking Protocols and The Hackers Sword The light-saber is a Jedi s weapon not as clumsy or random as a blaster. Obi-Wan Kenobi, Star Wars: Episode IV Slide 2 Introduction Why are firewalls basically
The Hacking Protocols and The Hackers Sword The light-saber is a Jedi s weapon not as clumsy or random as a blaster. Obi-Wan Kenobi, Star Wars: Episode IV Slide 2 Introduction Why are firewalls basically
Using Canvas: A Student Quickstart Guide SWOSU Center for Distance and elearning
 To log in, click on the Canvas button on the homepage or go to swosu.instructure.com Passwords have been reset for Canvas. Students will need to use their Dawgtag and their default password to log in.
To log in, click on the Canvas button on the homepage or go to swosu.instructure.com Passwords have been reset for Canvas. Students will need to use their Dawgtag and their default password to log in.
Identity Policies. Identity Policy Overview. Establishing User Identity through Active Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Pinterest. What is Pinterest?
 Pinterest What is Pinterest? Pinterest is like an electronic bulletin board that allows users to save and share photos they find on the internet. Usually when a user pins a photo it is linked to a blog
Pinterest What is Pinterest? Pinterest is like an electronic bulletin board that allows users to save and share photos they find on the internet. Usually when a user pins a photo it is linked to a blog
FREEWAY SIGNAGE series 9. user manual
 FREEWAY SIGNAGE series 9 user manual FREEWAY SIGNAGE series 9 Page 2 Table of Contents Overview...3 What is Digital Signage?...3 So what is FREEWAY SIGNAGE Series 9?...4 What can I display through my channel?...4
FREEWAY SIGNAGE series 9 user manual FREEWAY SIGNAGE series 9 Page 2 Table of Contents Overview...3 What is Digital Signage?...3 So what is FREEWAY SIGNAGE Series 9?...4 What can I display through my channel?...4
Security Course. WebGoat Lab sessions
 Security Course WebGoat Lab sessions WebGoat Lab sessions overview Initial Setup Tamper Data Web Goat Lab Session 4 Access Control, session information stealing Lab Session 2 HTTP Basics Sniffing Parameter
Security Course WebGoat Lab sessions WebGoat Lab sessions overview Initial Setup Tamper Data Web Goat Lab Session 4 Access Control, session information stealing Lab Session 2 HTTP Basics Sniffing Parameter
Configuring OpenVPN on pfsense
 Configuring OpenVPN on pfsense Configuring OpenVPN on pfsense Posted by Glenn on Dec 29, 2013 in Networking 0 comments In this article I will go through the configuration of OpenVPN on the pfsense platform.
Configuring OpenVPN on pfsense Configuring OpenVPN on pfsense Posted by Glenn on Dec 29, 2013 in Networking 0 comments In this article I will go through the configuration of OpenVPN on the pfsense platform.
Typing Software For Macbook Pro Facebook Application
 Typing Software For Macbook Pro Facebook Application Because MacBook Pro already comes with apps you need and want, you can The all-new Photos app for Mac makes it simpler than ever to manage a And post
Typing Software For Macbook Pro Facebook Application Because MacBook Pro already comes with apps you need and want, you can The all-new Photos app for Mac makes it simpler than ever to manage a And post
F-Secure Antivirus & Internet Security Discover Top 10 Best Most Effective Antivirus Internet Secur
 F-Secure Internet Security offers what many other antivirus programs do not--a complete family protection package. Its revolutionary system combines firewall and antivirus and browsing protection while
F-Secure Internet Security offers what many other antivirus programs do not--a complete family protection package. Its revolutionary system combines firewall and antivirus and browsing protection while
In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features.
 CentovaCast 3 - Shoutcast2 Overview In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features. Details Once you purchase
CentovaCast 3 - Shoutcast2 Overview In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features. Details Once you purchase
Lecture Overview. IN5290 Ethical Hacking. Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing
 Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Don t blink or how to create secure software. Bozhidar Bozhanov, LogSentinel
 Don t blink or how to create secure software Bozhidar Bozhanov, CEO @ LogSentinel About me Senior software engineer and architect Founder & CEO @ LogSentinel Former IT and e-gov advisor to the deputy prime
Don t blink or how to create secure software Bozhidar Bozhanov, CEO @ LogSentinel About me Senior software engineer and architect Founder & CEO @ LogSentinel Former IT and e-gov advisor to the deputy prime
Placester Quick Start Guide
 Placester Quick Start Guide Congratulations! You re on your way to building a strong online presence for your real estate business. This Quick Start Guide will walk you through all of the basics for getting
Placester Quick Start Guide Congratulations! You re on your way to building a strong online presence for your real estate business. This Quick Start Guide will walk you through all of the basics for getting
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
DECENTRALIZED SOCIAL NETWORKING WITH WORDPRESS. November 7, 2018 WordPress Meetup Vienna Alex Kirk
 DECENTRALIZED SOCIAL NETWORKING WITH WORDPRESS DECENTRALIZED? Centralized = control is with a single entity If you use Facebook, the servers are all controlled by Facebook Inc. Facebook can draw conclusions
DECENTRALIZED SOCIAL NETWORKING WITH WORDPRESS DECENTRALIZED? Centralized = control is with a single entity If you use Facebook, the servers are all controlled by Facebook Inc. Facebook can draw conclusions
eportfolio Support Guide
 eportfolio Support Guide D2L Services West Chester University of Pennsylvania www.wcupa.edu/d2l 610-436-3350, option 2 Anderson Hall, room 20 d2l@wcupa.edu v10.3 September 2014 1 CONTENTS EPortfolio Basics
eportfolio Support Guide D2L Services West Chester University of Pennsylvania www.wcupa.edu/d2l 610-436-3350, option 2 Anderson Hall, room 20 d2l@wcupa.edu v10.3 September 2014 1 CONTENTS EPortfolio Basics
Hi everyone. Starting this week I'm going to make a couple tweaks to how section is run. The first thing is that I'm going to go over all the slides
 Hi everyone. Starting this week I'm going to make a couple tweaks to how section is run. The first thing is that I'm going to go over all the slides for both problems first, and let you guys code them
Hi everyone. Starting this week I'm going to make a couple tweaks to how section is run. The first thing is that I'm going to go over all the slides for both problems first, and let you guys code them
Contents Release Notes System Requirements Using Jive for Office
 Jive for Office TOC 2 Contents Release Notes...3 System Requirements... 4 Using Jive for Office... 5 What is Jive for Office?...5 Working with Shared Office Documents... 5 Get set up...6 Get connected
Jive for Office TOC 2 Contents Release Notes...3 System Requirements... 4 Using Jive for Office... 5 What is Jive for Office?...5 Working with Shared Office Documents... 5 Get set up...6 Get connected
Manual Restart Iphone 4s Apple Id Password >>>CLICK HERE<<<
 Manual Restart Iphone 4s Apple Id Password Keeps Popping Up Type in your password to disable Find My iphone if you're prompted and tap Turn Off. Once you are signed out of icloud, reboot your iphone or
Manual Restart Iphone 4s Apple Id Password Keeps Popping Up Type in your password to disable Find My iphone if you're prompted and tap Turn Off. Once you are signed out of icloud, reboot your iphone or
Moving Targets: Assessing the Security of Mobile Devices. March 3 rd, 2016 Kevin Johnson, CEO Secure Ideas
 Moving Targets: Assessing the Security of Mobile Devices March 3 rd, 2016 Kevin Johnson, CEO Secure Ideas Conflict of Interest Kevin Johnson Has no real or apparent conflicts of interest to report. Kevin
Moving Targets: Assessing the Security of Mobile Devices March 3 rd, 2016 Kevin Johnson, CEO Secure Ideas Conflict of Interest Kevin Johnson Has no real or apparent conflicts of interest to report. Kevin
Your Auth is open! Oversharing with OpenAuth & SAML
 Your Auth is open! Oversharing with OpenAuth & SAML Andrew Pollack Northern Collaborative Technologies 2013 by the individual speaker Sponsors 2013 by the individual speaker Who Am I? Andrew Pollack President
Your Auth is open! Oversharing with OpenAuth & SAML Andrew Pollack Northern Collaborative Technologies 2013 by the individual speaker Sponsors 2013 by the individual speaker Who Am I? Andrew Pollack President
Remobjects for Webservices
 Remobjects for Webservices Michaël Van Canneyt December 6, 2008 Abstract The RemObjects SDK is a versatile tool which is likely to provide a solution for all your remoting needs: it implements a complete
Remobjects for Webservices Michaël Van Canneyt December 6, 2008 Abstract The RemObjects SDK is a versatile tool which is likely to provide a solution for all your remoting needs: it implements a complete
Content Author's Reference and Cookbook
 Sitecore CMS 7.0 Content Author's Reference and Cookbook Rev. 130425 Sitecore CMS 7.0 Content Author's Reference and Cookbook A Conceptual Overview and Practical Guide to Using Sitecore Table of Contents
Sitecore CMS 7.0 Content Author's Reference and Cookbook Rev. 130425 Sitecore CMS 7.0 Content Author's Reference and Cookbook A Conceptual Overview and Practical Guide to Using Sitecore Table of Contents
Version 14 Supplemental Manual
 Version 14 Supplemental Manual This is a reference to the features that will be released from July 1, 2013 through July 1, 2014. Click the name of the feature to jump to that section. New Features: Version
Version 14 Supplemental Manual This is a reference to the features that will be released from July 1, 2013 through July 1, 2014. Click the name of the feature to jump to that section. New Features: Version
Are You Avoiding These Top 10 File Transfer Risks?
 Are You Avoiding These Top 10 File Transfer Risks? 1. 2. 3. 4. Today s Agenda Introduction 10 Common File Transfer Risks Brief GoAnywhere MFT Overview Question & Answer HelpSystems Corporate Overview.
Are You Avoiding These Top 10 File Transfer Risks? 1. 2. 3. 4. Today s Agenda Introduction 10 Common File Transfer Risks Brief GoAnywhere MFT Overview Question & Answer HelpSystems Corporate Overview.
MITOCW ocw f99-lec07_300k
 MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
Introduction to Ethical Hacking
 Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Agile Project Management: A Quick Start Beginner's Guide To Mastering Agile Project Management PDF
 Agile Project Management: A Quick Start Beginner's Guide To Mastering Agile Project Management PDF Discover Agile Project Management *** 3rd Edition *** DO YOU WANT TO ACHIEVE THE BEST AT EVERY STAGE OF
Agile Project Management: A Quick Start Beginner's Guide To Mastering Agile Project Management PDF Discover Agile Project Management *** 3rd Edition *** DO YOU WANT TO ACHIEVE THE BEST AT EVERY STAGE OF
Introduction! 2. Why You NEED This Guide 2. Step One: Research! 3. What Are Your Customers Searching For? 3. Step Two: Title Tag!
 Table of Contents Introduction! 2 Why You NEED This Guide 2 Step One: Research! 3 What Are Your Customers Searching For? 3 Step Two: Title Tag! 4 The First Thing Google Sees 4 How Do I Change It 4 Step
Table of Contents Introduction! 2 Why You NEED This Guide 2 Step One: Research! 3 What Are Your Customers Searching For? 3 Step Two: Title Tag! 4 The First Thing Google Sees 4 How Do I Change It 4 Step
LiveText via Group Member User Guide
 March 2017 LiveText via Group Member User Guide Who is this Guide for?... 4 Accessing Via... 4 In Progress Tab... 4 Group Details Page... 4 The Homepage Tab... 5 Activities... 5 The Activity Tab... 5 To
March 2017 LiveText via Group Member User Guide Who is this Guide for?... 4 Accessing Via... 4 In Progress Tab... 4 Group Details Page... 4 The Homepage Tab... 5 Activities... 5 The Activity Tab... 5 To
Manually Setup Yahoo Mail Iphone 5 Can't >>>CLICK HERE<<<
 Manually Setup Yahoo Mail Iphone 5 Can't Comes up with 'The IMAP server "apple.imap.mail.yahoo.com" is not responding. If it doesn't allow you to change it, add the account manually by going to Settings
Manually Setup Yahoo Mail Iphone 5 Can't Comes up with 'The IMAP server "apple.imap.mail.yahoo.com" is not responding. If it doesn't allow you to change it, add the account manually by going to Settings
User Help
 ginlo @work User Help 19 June 2018 Contents Get started... 5 System requirements for the ginlo @work app... 5 Recommended browsers for ginlo websites... 6 Supported languages... 6 Navigation in ginlo @work...
ginlo @work User Help 19 June 2018 Contents Get started... 5 System requirements for the ginlo @work app... 5 Recommended browsers for ginlo websites... 6 Supported languages... 6 Navigation in ginlo @work...
MEMBERSHIP & PARTICIPATION
 MEMBERSHIP & PARTICIPATION What types of activities can I expect to participate in? There are a variety of activities for you to participate in such as discussion boards, idea exchanges, contests, surveys,
MEMBERSHIP & PARTICIPATION What types of activities can I expect to participate in? There are a variety of activities for you to participate in such as discussion boards, idea exchanges, contests, surveys,
The Definitive Guide to Office 365 External Sharing. An ebook by Sharegate
 The Definitive Guide to Office 365 External Sharing An ebook by Sharegate The Definitive Guide to External Sharing In any organization, whether large or small, sharing content with external users is an
The Definitive Guide to Office 365 External Sharing An ebook by Sharegate The Definitive Guide to External Sharing In any organization, whether large or small, sharing content with external users is an
Cyber Security Stress Test SUMMARY REPORT
 Cyber Security Stress Test SUMMARY REPORT predict prevent respond detect FINAL SCORE PREDICT: PREVENT: Final score: RESPOND: DETECT: BRILLIANT! You got a 100/100. That's as good as it gets. So take a second
Cyber Security Stress Test SUMMARY REPORT predict prevent respond detect FINAL SCORE PREDICT: PREVENT: Final score: RESPOND: DETECT: BRILLIANT! You got a 100/100. That's as good as it gets. So take a second
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE
 GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
Security. https://outflux.net/slides/2015/osu-devops.pdf. DevOps Bootcamp, OSU, Feb 2015 Kees Cook (pronounced Case )
 https://outflux.net/slides/2015/osu-devops.pdf, Feb 2015 Kees Cook (pronounced Case ) Who is this guy? Fun: DefCon CTF team won in 2006 & 2007 Debian Ubuntu Jobs: OSDL (proto Linux Foundation)
https://outflux.net/slides/2015/osu-devops.pdf, Feb 2015 Kees Cook (pronounced Case ) Who is this guy? Fun: DefCon CTF team won in 2006 & 2007 Debian Ubuntu Jobs: OSDL (proto Linux Foundation)
CS Paul Krzyzanowski
 Computer Security 17. Tor & Anonymous Connectivity Anonymous Connectivity Paul Krzyzanowski Rutgers University Spring 2018 1 2 Anonymity on the Internet Often considered bad Only criminals need to hide
Computer Security 17. Tor & Anonymous Connectivity Anonymous Connectivity Paul Krzyzanowski Rutgers University Spring 2018 1 2 Anonymity on the Internet Often considered bad Only criminals need to hide
Career Center Job Aid
 Career Center Job Aid The Career Center allows candidates to search for and apply for jobs posted at UH. This job aid assists you in using the Career Center to search, apply, review, match, and share jobs.
Career Center Job Aid The Career Center allows candidates to search for and apply for jobs posted at UH. This job aid assists you in using the Career Center to search, apply, review, match, and share jobs.
The IBM I A Different Roadmap
 The IBM I A Different Roadmap Not long ago I was reading an article about a session Steve Will gave on how to make the IBM i "sexy". Those who know me know that that would immediately start me thinking
The IBM I A Different Roadmap Not long ago I was reading an article about a session Steve Will gave on how to make the IBM i "sexy". Those who know me know that that would immediately start me thinking
Manual Update Java 7 Version 11 Not Work In
 Manual Update Java 7 Version 11 Not Work In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in version 17.0.0 installed after applying the Chrome update and restarting (the
Manual Update Java 7 Version 11 Not Work In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in version 17.0.0 installed after applying the Chrome update and restarting (the
Want to make $50+/day
 Want to make $50+/day from CPALead? In first of all what CPALead is? The Company. CPALead, LLC is a performance-based, online advertising network that develops technologies to promote incentive-based advertisements
Want to make $50+/day from CPALead? In first of all what CPALead is? The Company. CPALead, LLC is a performance-based, online advertising network that develops technologies to promote incentive-based advertisements
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
Set up the Outlook mobile app on an Android device
 Set up the Outlook mobile app on an Android device You can set up the Outlook mobile app on your Android device to access your email, calendar, and contacts. The instructions below will show you how to
Set up the Outlook mobile app on an Android device You can set up the Outlook mobile app on your Android device to access your email, calendar, and contacts. The instructions below will show you how to
Q1 How often do you visit the MACTA website?
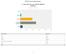 Q1 How often do you visit the MACTA website? Answ ered: 26 Skipped: 8 Daily Weekly Monthly Less than once per month/rarely Nev er 2 4 6 8 10 Answ er Choices Daily Weekly Monthly Less than once per month/rarely
Q1 How often do you visit the MACTA website? Answ ered: 26 Skipped: 8 Daily Weekly Monthly Less than once per month/rarely Nev er 2 4 6 8 10 Answ er Choices Daily Weekly Monthly Less than once per month/rarely
CSC 352, Fall 2015 Assignment 5 Due: Wednesday, September 30 at 23:59:59
 CSC 352, Fall 2015 Assignment 5 Due: Wednesday, September 30 at 23:59:59 Introduction The a2 write-up started with 3+ pages of various information about assignments. None of that is repeated here, but
CSC 352, Fall 2015 Assignment 5 Due: Wednesday, September 30 at 23:59:59 Introduction The a2 write-up started with 3+ pages of various information about assignments. None of that is repeated here, but
Azon Master Class. By Ryan Stevenson Guidebook #9 Amazon Advertising
 Azon Master Class By Ryan Stevenson https://ryanstevensonplugins.com/ Guidebook #9 Amazon Advertising Table of Contents 1. Joining Amazon Associates Program 2. Product Style Joining Amazon Associates Program
Azon Master Class By Ryan Stevenson https://ryanstevensonplugins.com/ Guidebook #9 Amazon Advertising Table of Contents 1. Joining Amazon Associates Program 2. Product Style Joining Amazon Associates Program
Who am I? I m a python developer who has been working on OpenStack since I currently work for Aptira, who do OpenStack, SDN, and orchestration
 Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
EasyChair Instructions for Authors
 EasyChair Instructions for Authors The submission and review of papers for SIGUCCS 2017 will be managed through an online conference paper management system called EasyChair. This system gives you, the
EasyChair Instructions for Authors The submission and review of papers for SIGUCCS 2017 will be managed through an online conference paper management system called EasyChair. This system gives you, the
Corner The Local Search Engine Market Four Steps to Ensure your Business will Capitalize from Local Google Search Exposure by Eric Rosen
 Corner The Local Search Engine Market Four Steps to Ensure your Business will Capitalize from Local Google Search Exposure by Eric Rosen 2011 www.marketingoutthebox.com Table of Contents Introduction
Corner The Local Search Engine Market Four Steps to Ensure your Business will Capitalize from Local Google Search Exposure by Eric Rosen 2011 www.marketingoutthebox.com Table of Contents Introduction
BEGINNER PHP Table of Contents
 Table of Contents 4 5 6 7 8 9 0 Introduction Getting Setup Your first PHP webpage Working with text Talking to the user Comparison & If statements If & Else Cleaning up the game Remembering values Finishing
Table of Contents 4 5 6 7 8 9 0 Introduction Getting Setup Your first PHP webpage Working with text Talking to the user Comparison & If statements If & Else Cleaning up the game Remembering values Finishing
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make
MITOCW Recitation 4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make
Register by completing the form, or connecting via your GitHub or Google account.
 SDL Developer Portal Registration Guide In order to register an application on the SDL developer portal, you must first create both a developer and company profile. Developer Profile Registration To create
SDL Developer Portal Registration Guide In order to register an application on the SDL developer portal, you must first create both a developer and company profile. Developer Profile Registration To create
Ad Muncher's New Interface Layout
 Ad Muncher's New Interface Layout We are currently working on a new layout for Ad Muncher's configuration window. This page will document the new layout. Interface Layout Objectives The ability to modify
Ad Muncher's New Interface Layout We are currently working on a new layout for Ad Muncher's configuration window. This page will document the new layout. Interface Layout Objectives The ability to modify
OLLI Online. Users Guide
 OLLI Online Users Guide Version 1 / December 3, 2014 Table of Contents LOGIN... 3 EDIT MEMBER SETTINGS... 4 Settings Overview... 4 Community Profile... 4 Member Info... 5 Photo... 6 Notifications... 7
OLLI Online Users Guide Version 1 / December 3, 2014 Table of Contents LOGIN... 3 EDIT MEMBER SETTINGS... 4 Settings Overview... 4 Community Profile... 4 Member Info... 5 Photo... 6 Notifications... 7
Before You Lose Your iphone
 iphones are lost and stolen every day, but luckily Apple has robust tools built into ios that will keep your data safe and your device unusable if it's misplaced or snatched by a thief. With Find My iphone,
iphones are lost and stolen every day, but luckily Apple has robust tools built into ios that will keep your data safe and your device unusable if it's misplaced or snatched by a thief. With Find My iphone,
SalonVision Configuration Guide
 SalonVision Configuration Guide A Guide For SalonVision Live Data Integration I SalonVision Online Booking Configurations Table of Contents Part I Introduction 1 Part II Envision Setup 2 1 Setup Program
SalonVision Configuration Guide A Guide For SalonVision Live Data Integration I SalonVision Online Booking Configurations Table of Contents Part I Introduction 1 Part II Envision Setup 2 1 Setup Program
P1_L3 Operating Systems Security Page 1
 P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
App Configuration. Version 6.0 August All rights reserved
 App Configuration Version 6.0 August 2016 2015 systems@work. All rights reserved Contents CONTENTS... 1 INTRODUCTION... 2 LIMITATIONS... 3 FORM TYPES... 4 SYSTEM PARAMETERS... 8 ICONS... 10 IMAGE FOLDERS...
App Configuration Version 6.0 August 2016 2015 systems@work. All rights reserved Contents CONTENTS... 1 INTRODUCTION... 2 LIMITATIONS... 3 FORM TYPES... 4 SYSTEM PARAMETERS... 8 ICONS... 10 IMAGE FOLDERS...
Visual Presenter Visual Webcaster
 ) Visual Presenter Visual Webcaster Last Revised 8/3/11 Powered by Table of Contents Overview 3 System Requirements 4-5 Login 6 Main Menu 7 Preparing for the Event Presenter 8-12 Slides 13-20 URL s 21-23
) Visual Presenter Visual Webcaster Last Revised 8/3/11 Powered by Table of Contents Overview 3 System Requirements 4-5 Login 6 Main Menu 7 Preparing for the Event Presenter 8-12 Slides 13-20 URL s 21-23
Lesson 11: WordPress SEO, Statistics, and Analysis
 Lesson 11: WordPress SEO, Statistics, and Analysis Chapter 1: Introduction Welcome to Lesson 11! We're in the home stretch now. So you've been spending lots of time learning how to build and optimize WordPress
Lesson 11: WordPress SEO, Statistics, and Analysis Chapter 1: Introduction Welcome to Lesson 11! We're in the home stretch now. So you've been spending lots of time learning how to build and optimize WordPress
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
San Luis Obispo CUPA Public Portal. On-Line Hazardous Materials Business Plan Submittals Instructions for Use
 Document Prepared by County of San Luis Obispo Environmental Health Services 1/4/2010 The Portal is being implemented to allow for easy submittal of HazMat Business Plans. A business can submit their information
Document Prepared by County of San Luis Obispo Environmental Health Services 1/4/2010 The Portal is being implemented to allow for easy submittal of HazMat Business Plans. A business can submit their information
Digital Signage The perfect solution from one source.
 Digital Signage The perfect solution from one source. Our new service movebox is a cloud-based software platform that empowers you to manage the contents of digital signage screens and interactive kiosks
Digital Signage The perfect solution from one source. Our new service movebox is a cloud-based software platform that empowers you to manage the contents of digital signage screens and interactive kiosks
Containers: Exploits, Surprises, And Security
 Containers: Exploits, Surprises, And Security with Elissa Shevinsky COO at SoHo Token Labs Editor of Lean Out #RVASec @ElissaBeth on twitter @Elissa_is_offmessage on Instagram this was Silicon Valley in
Containers: Exploits, Surprises, And Security with Elissa Shevinsky COO at SoHo Token Labs Editor of Lean Out #RVASec @ElissaBeth on twitter @Elissa_is_offmessage on Instagram this was Silicon Valley in
68 Insider Threat Red Flags
 68 Insider Threat Red Flags Are you prepared to stop the insider threat? Enterprises of all shapes and sizes are taking a fresh look at their insider threat programs. As a company that s been in the insider
68 Insider Threat Red Flags Are you prepared to stop the insider threat? Enterprises of all shapes and sizes are taking a fresh look at their insider threat programs. As a company that s been in the insider
EU Login Version 1 7 March 2017
 EU Login Version 1 7 March 2017 EUROPEAN COMMISSION EU Login Version 1 7 March 2017 Directorate-General for Education, Youth, Sport and Culture 2017 EN Table of Contents Table of Contents... 4 1. What
EU Login Version 1 7 March 2017 EUROPEAN COMMISSION EU Login Version 1 7 March 2017 Directorate-General for Education, Youth, Sport and Culture 2017 EN Table of Contents Table of Contents... 4 1. What
Account Settings. Private Messages. Reporting Abuse. Create a Ladder. Ladder Admin Guide. Ladd Admin Guide - Quick Challenge / Result
 User Manual 1 2 3 General 1.1 Sign Up 5 1.2 Set HomePage 11 1.3 Profile 15 1.4 Account Settings 21 1.5 Private Messages 26 1.6 Reporting Abuse 31 1.7 Privacy 33 Ladders 2.1 Create a Ladder 36 2.2 Ladder
User Manual 1 2 3 General 1.1 Sign Up 5 1.2 Set HomePage 11 1.3 Profile 15 1.4 Account Settings 21 1.5 Private Messages 26 1.6 Reporting Abuse 31 1.7 Privacy 33 Ladders 2.1 Create a Ladder 36 2.2 Ladder
SPOOFING. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
