Certificates and Certification
|
|
|
- Melinda Johnson
- 6 years ago
- Views:
Transcription
1 ch06.fm Page 69 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification As we discussed in Chapter 2, public-key cryptography involves the use of public/private-key pairs to facilitate digital signature and key management services. The fundamental principle that enables public-key technology to scale is the fact that the public component of the public/private-key pair may be distributed freely among the entities that need the public component to use the underlying security services. (See Chapters 4 and 5 for more information regarding security services enabled through the use of a PKI.) However, distribution of the public component without some form of integrity protection would defeat the very foundation for these security services. Thus, the public-key component must be protected in such a way that it will not impact the overall scalability that public-key cryptography techniques offer. Further, we need to bind certain attributes with the public key. Thus, a data integrity mechanism is required to ensure that the public key (and any other information associated with that public key) is not modified without detection. However, a data integrity mechanism alone is not sufficient to guarantee that the public key belongs to the claimed owner. A mechanism that binds the public key to the claimed owner in a trustworthy manner is also required. In the end, the goal is to provide a single mechanism by which a relying party (that is, the user of the key and associated data, as defined in [RFC2527]) is assured that The integrity of the public key (and any other associated information) is sound. The public key (and any other associated information) has been bound to the claimed owner in a trusted manner. Our purpose in this chapter is to explain how the use of public-key certificates accomplishes these goals. In particular, we will focus on the syntax and semantics of the X.509 Version 3
2 ch06.fm Page 70 Thursday, September 26, :55 PM 70 Understanding PKI public-key certificate, and we will explain how the integrity of these certificates is established and maintained. Certificates Kohnfelder first introduced the concept of using a signed data structure or certificate to convey the public key to a relying party in his 1978 bachelor s thesis entitled Towards a Practical Public-Key Cryptosystem [Kohn78]. Thus, over two decades ago, it was recognized that a scalable and secure method (from an integrity perspective) would be required to convey the public keys to the parties that needed them. Simply stated, public-key certificates are used to bind an entity s name (and possibly additional attributes associated with that entity) with the corresponding public key. When discussing the concept of a certificate, it is important to recognize that a number of different types of certificates exist, including X.509 public-key certificates Simple Public Key Infrastructure (SPKI) certificates Pretty Good Privacy (PGP) certificates Attribute certificates The certificate types listed here have separate and distinct formats. In some cases, one type of certificate may be defined in several different versions, and a single version may be instantiated in a number of different ways. For example, there are three versions of an X.509 public-key certificate. Version 1 is a subset of Version 2, and Version 2 is a subset of Version 3. Because a Version 3 public-key certificate includes numerous optional extensions (as discussed later), it can be instantiated in a number of application-specific ways; for example, Secure Electronic Transaction (SET) certificates are X.509 Version 3 public-key certificates with specific extensions defined solely for SET exchanges. To complicate matters further, multiple terms commonly denote the same thing. For example, in many environments the terms certificate and digital certificate are synonymous with an X.509 public-key certificate. For the purposes of this book, a certificate is synonymous only with a Version 3 public-key certificate as defined in the X.509 Recommendation [X509 00]. (See Box 6.1.) Any other type of certificate will be further qualified to avoid any confusion with this usage. In this chapter, we discuss the structure and content of a certificate. As we describe the structure of a certificate in the next section, you will notice that certificates can be issued to Certification Authorities
3 ch06.fm Page 71 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 71 Box 6.1 Versions 1 3 of X.509 Three versions of an X.509 public-key certificate are defined. The original Version 1 publickey certificate, defined in the 1988 X.509 Recommendation, suffers from inherent inflexibility because this version cannot be extended to support additional attributes. The Version 2 public-key certificate did little to correct this shortcoming because it simply augments Version 1 with the addition of two optional fields. Because the demand for these fields was (and continues to be) negligible and the same inability to support extensions also applies, the Version 2 public-key certificate has failed to gain widespread acceptance. Not surprisingly, Version 3 public-key certificates, as specified in the 1997 X.509 Recommendation [X509 97], were introduced to correct the deficiencies associated with the Version 1 and Version 2 definitions. Specifically, Version 3 offers significant improvements over Version 1 and Version 2 through the addition of optional extensions. More recently (circa June 2000), the 2000 X.509 Recommendation [X509 00] was completed. The 2000 version includes numerous changes from the previous version, including the definition of two additional extensions to the Version 3 public-key certificate. In the enterprise domain, it is fair to say that Version 3 public-key certificates are the preferred choice as they are the most flexible, and many of the extensions are required to fully support the requirements of the enterprise. (CAs) and to end entities (for example, end users or devices). These are referred to as CA certificates and end-entity certificates, respectively. Digital Certificate The term digital certificate is sometimes used to denote a certificate in electronic form. However, this term can be somewhat confusing in some circumstances because a number of quite different certificates (for example, an X.509 public-key certificate, an attribute certificate, a PGP certificate, and so on) are digital. For that matter, a digitized birth certificate might be considered to be a digital certificate. Thus, unless the term is either explicitly defined or further qualified, it is not precise enough to convey any intended meaning. The use of this term has also introduced confusion when describing the relationship between digital certificates and digital signatures. In particular, a common mistake is to assume that Alice can authenticate herself by simply supplying a digital certificate without the corresponding digital signature. Further, although a digital signature is meaningful in itself (that is, a digital signature is distinguished from a handwritten or a generic electronic signature), digital
4 ch06.fm Page 72 Thursday, September 26, :55 PM 72 Understanding PKI certificate does not offer the same connotation especially when referring solely to a publickey certificate. To be perfectly precise, any reference to a certificate should be fully qualified to avoid unnecessary confusion. However, in accordance with common practice in the PKI industry, we will simply use the term certificate as a shorthand notation for an X.509 Version 3 public-key certificate. We will explicitly identify all other types of certificates where appropriate even the generic use of certificate will be qualified wherever any doubt may arise. Certificate Structure and Semantics Although X.509 defines certain requirements associated with the standard fields and extensions of a certificate, other issues still must be further refined in specific profiles to fully address interoperability considerations. The Internet Engineering Task Force (IETF) Public Key Infrastructure X.509 (PKIX) Working Group introduced such a profile in January 1999 with the publication of RFC2459. In April 2002, RFC2459 was replaced with RFC3280. Although RFC3280 is targeted for the Internet community, a number of its recommendations could equally apply in the enterprise environment, and consistency should be maintained wherever possible. Therefore, we will provide references to some of the recommendations made in RFC3280 where appropriate. Figure 6.1 shows the generic structure of a Version 3 certificate. The following list defines the fields represented in Figure 6.1: Figure 6.1 Version 3 certificate structure. Signed by Authorized CA (issuer) Serial Subject Public Issuer Subject Version Signature Issuer Validity Subject Extensions Number Key Info Unique ID Unique ID Digital Signature Identifies the Version of the Certificate (e.g., V3) Optional Extensions Unique Integer Identifier for the Certificate Algorithm ID Used to Sign the Certificate Unique Name of the Certificate Issuer Not Before and Not After Validity Times Unique Name of the Owner Public Key (and Algorithm ID) of the Owner Optional Unique ID of the Issuing CA Optional Unique ID of the Subject Algorithm Id and Digital Signature
5 ch06.fm Page 73 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 73 Version indicates the version of the certificate (either 1, 2, or 3). Serial Number is the unique identifier for this certificate relative to the certificate issuer. Signature indicates the algorithm identifier (that is, the Object Identifier, or OID, plus any associated parameters) of the algorithm used to calculate the digital signature on the certificate. 1 For example, the OID for SHA-1 with RSA might be present, indicating that the digital signature is an SHA-1 hash encrypted using RSA. Issuer is the Distinguished Name (DN) of the CA that issued the certificate and must always be present. 2 Validity indicates the window of time that this certificate should be considered valid unless otherwise revoked (refer to Chapter 8 for more information on revocation). This field is composed of Not Valid Before and Not Valid After dates/times that may be represented in UTC Time or in Generalized Time (however, RFC3280 has specific rules associated with the use of these time representations). Subject indicates the DN of the certificate owner and must be non-null unless an alternate name form is used (refer to the Extensions field later). Subject Public Key Info is the public key (and algorithm identifier) associated with the subject and must always be present. Issuer Unique ID is an optional unique identifier of the certificate issuer present in Version 2 and Version 3 only; this field is rarely used in implementation practice, and it is not recommended for use by RFC An OID is simply a unique representation for a given object. When expressed verbally or in writing among human beings, an OID is represented as a sequence of integers that are separated by decimal points or dots (much the same as an Internet Protocol (IP) address is expressed in the familiar dotted decimal notation). OIDs are hierarchical in nature, and they are registered with international, national, or organizational registration authorities in order to ensure that the allocated OID for a given object is unique. As an example, the OID for SHA-1 with RSA (which might be present in the Signature field of a certificate) is A DN is a hierarchical naming convention defined in the X.500 Recommendations. DNs are designed to help ensure entity names are unique. Without getting into too much detail regarding Directories and Directory Information Trees, DNs are expressed as a concatenation of Relative Distinguished Names (RDNs) from the top- or root-level node down to the last node of the DN. For example, C = CA, O = ADGA, OU = AEPOS Technologies, CN = Steve Lloyd is an example of a DN. Note that each RDN (C = CA is an RDN, O = ADGA is an RDN, and so on) must be unique at each level, otherwise the uniqueness of the DN as a whole would not be guaranteed.
6 ch06.fm Page 74 Thursday, September 26, :55 PM 74 Understanding PKI Subject Unique ID is an optional unique identifier of the certificate owner present in Version 2 and Version 3 only; this field is rarely used in implementation practice, and it is not recommended for use by RFC3280. Each certificate extension described next is associated with a criticality flag. In general, extensions can be marked critical or noncritical, although the standards often recommend or even mandate the criticality associated with certain extensions. An extension that has been marked critical must be processed and understood, or the certificate is not to be used. A noncritical extension is to be processed if possible, but it may be gracefully ignored if it is not recognized. Extensions are optional standard and private extensions (present in Version 3 only) and include the following: Authority Key Identifier is a unique identifier of the key that should be used to verify the digital signature calculated over the certificate; it distinguishes between multiple keys that apply to the same certificate issuer. RFC3280 mandates the inclusion of this field for all but self-signed certificates. (Chapter 9 discusses self-signed certificates.) Subject Key Identifier is a unique identifier associated with the public key contained in this certificate; it distinguishes between multiple keys that apply to the same certificate owner. RFC3280 mandates this field for CA certificates, and it is recommended for end-entity certificates. Key Usage is a bit string used to identify (or restrict) the functions or services that can be supported by using the public key in this certificate; it can be used to indicate support for digital signature, non-repudiation, key encipherment, data encipherment, key agreement, certificate signature, Certification Revocation List (CRL) signature, encipher only, and decipher only. A profile typically specifies allowable combinations (for example, the U.S. Federal PKI (FPKI) profile [FPKIpro] explicitly identifies permitted key usage combinations). Extended Key Usage is a sequence of one or more OIDs that identify specific usage of the public key in the certificate. Although X.509 does not explicitly define identifiers for this purpose, RFC3280 identifies several OIDs associated with this extension, including Transport Layer Security (TLS) server authentication, TLS client authentication, code signing, protection, time stamping, and Online Certificate Status Protocol (OCSP) signing. (OCSP is discussed in more detail in Chapter 8.) The list of OIDs will likely be augmented over time as needs dictate, so this should not be considered an exhaustive list. RFC3280 also points out that this extension is typically used with end-entity certificates. CRL Distribution Point indicates the location of the CRL partition where revocation information associated with this certificate resides. (Refer to Chapter 8 for more informa-
7 ch06.fm Page 75 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 75 tion regarding revocation techniques and CRL Distribution Points.) RFC3280 provides additional guidance with respect to which attributes within the CRL Distribution Point extension should be populated and what it means when multiple distribution points are present. Private Key Usage Period indicates the time window that the private key associated with the public key in this certificate can be used; it is intended for use with digital signature keys/ certificates. Like the certificate validity period, this window is specified in terms of Not Valid Before and Not Valid After dates/times (although only Generalized Time is permitted here). Judicious use of this extension can establish a buffer between the time the signing private key expires and the time the corresponding public key used to verify the digital signatures created with that private key expires. This should help eliminate many instances where perfectly valid digital signatures needlessly come into question because the key lifetimes of both the private and public key were too close together (or even identical). Note that when this extension is absent, the validity periods of the public key and the private key are identical. As Chapter 7 discusses, a new key pair should be issued before the private key expires in order to avoid any unnecessary downtime. It is interesting to note that RFC3280 recommends against the use of this extension. One reason for this is that the interpretation of this field is not universally agreed upon, which could give rise to inconsistent implementations. Certificate Policies indicates a sequence of one or more policy OIDs and optional qualifiers associated with the issuance and subsequent use of the certificate. If this extension is marked critical, the processing application must adhere to at least one of the policies indicated, or the certificate is not to be used. Although RFC3280 recommends that policy qualifiers should not be used (in order to promote interoperability), it does define two possible qualifiers: the Certification Practice Statement (CPS) qualifier and the User Notice qualifier. The CPS qualifier is a Uniform Resource Identifier (URI) at which one can find the CPS that applies to this certificate. A notice reference, an explicit notice (up to 200 characters), or both, can comprise the User Notice qualifier. Policy Mappings indicates one or more policy OID equivalencies between two CA domains and are present only in CA certificates. The Certificate Policies section in this chapter provides additional information related to policy mappings. Subject Alternative Name indicates alternative name forms associated with the owner of the certificate (for example, address, IP address, URI, and so on). Alternative name forms are to be considered just as binding as the subject DN, if present. RFC3280 further specifies that if the subject DN is null, one or more alternative name forms must be present, and this extension must be marked critical.
8 ch06.fm Page 76 Thursday, September 26, :55 PM 76 Understanding PKI Issuer Alternative Name indicates alternative name forms associated with the issuer of the certificate (for example, address, IP address, URI, and so on). RFC3280 specifies the same processing rules as specified under the Subject Alternate Name extension with the exception that the issuer s DN must always be present in the Issuer field. One reason for this requirement is to maintain compatibility with the S/MIME specification. Subject Directory Attributes indicates a sequence of attributes associated with the owner of the certificate. Although this extension is not currently in widespread use, several known applications exist where this extension conveys access control information. However, we recommend exercising caution when using a certificate to convey privilege-related information, because any change in those privileges would force the revocation of the existing certificate and a new certificate would have to be issued. (See Box 6.2.) Basic Constraints indicates whether this is a CA certificate. Typically, this field is absent in end-entity certificates. If it is present in an end-entity certificate, the value of the CA attribute in the Basic Constraints field must be false. For CA certificates, the Basic Constraints field should always be present, and the CA attribute in the Basic Constraints field must be set to a value of true. Note that X.509 [X509 00] recommends (but doesn t mandate) that this extension be marked critical. RFC3280 mandates that this extension be present and marked critical if the associated public key is to be used to verify digital signatures on certificates. However, RFC3280 makes a distinction between public keys used to verify digital signatures on certificates and those that might be used to verify digital signatures on CRLs only or those that are used in conjunction with certificate management protocols. In these cases, the extension may be marked critical or noncritical. For CA certificates, the Basic Constraints extension can also include a Path Length Constraint. In accordance with X.509 [X509 00], the Path Length Constraint indicates the maximum number of CA certificates that may follow this certificate in a certification path. (Chapter 9 describes certification paths and certification path processing.) A value of zero indicates that the CA can issue only end-entity certificates. The absence of the Box 6.2 Certificate Perishability Any change to the information contained within a given certificate before it naturally expires necessarily means that the existing certificate must be revoked and a new certificate must be issued. Therefore, exercise care to ensure that the attributes placed within the certificate are fairly static in order to avoid wasteful certificate revocation and (re)issuance. Attributes associated with an end entity that will tend to be fairly dynamic in nature should be conveyed through some other means (for example, via attribute certificates, which are briefly discussed later in this chapter and in Chapter 5).
9 ch06.fm Page 77 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 77 Path Length Constraint in a CA certificate indicates that no restriction is placed on the length of the certification path (that is, the length of the certification path is unbounded). Note that the Path Length Constraint should not be present in an end-entity certificate and is meaningless therein; it should be ignored if it is present. Name Constraints, an extension present only in CA certificates, indicates required and/or excluded subtree names through the use of the Permitted Subtrees and/or Excluded Subtrees attributes, respectively. The specified names can take the form of a DN, a URI, an address, or any other name form that lends itself to a hierarchical structure. The idea is to qualify the name space that applies to the subject names that follow the CA certificate in which the restrictions took effect. If present, this extension should be marked critical [X509 00]. RFC3280 mandates that this extension be marked critical and points out that Name Constraints should not be applied to certificates where the Issuer and Subject fields are the same unless the certificate is the last one in the certification path. (Chapter 9 provides additional information regarding Name Constraints in relation to certification path validation.) Policy Constraints, an extension present only in CA certificates, indicates required policy identifiers and/or prohibited policy mappings through the use of the Require Explicit Policy and/or Inhibit Policy Mapping attributes, respectively. It is important to note that if the Require Explicit Policy comes into effect anywhere in a given certification path, it applies to the entire certification path. This is not the case with the Inhibit Policy Mapping attribute that applies only to subsequent certificates in the certification path. A value of zero for either attribute indicates that the restrictions apply immediately. A nonzero value for either attribute indicates where the restrictions might apply; that is, the value is an offset in the certification path, and the nominated CA certificate may or may not be encountered. If present, this extension should be marked critical [X509 00]. RFC3280 states that this extension may be critical or noncritical. Inhibit Any Policy, an extension present only in CA certificates, indicates that the anypolicy identifier (OID value ) should not be considered a legitimate match for other policy identifiers. A value of zero indicates that this restriction applies from this point forward. A nonzero value indicates where the restriction might apply; that is, the value is an offset in the certification path, and the nominated CA certificate may or may not be encountered. This extension was first standardized in the 2000 version of X.509 [X509 00]. In accordance with X.509, this extension may be marked critical or noncritical, but it is recommended that it be marked critical. RFC3280 states that this extension must be marked critical. Freshest CRL Pointer, an extension present in end-entity and CA certificates, provides a pointer to the freshest CRL information. In practice, this is likely to be a pointer to a Delta CRL. (Refer to Chapter 8 for more information on Delta CRLs.) The syntax is the
10 ch06.fm Page 78 Thursday, September 26, :55 PM 78 Understanding PKI same as is used with CRL Distribution Points. This extension was first standardized in the 2000 version of X.509 [X509 00]. The extension may be marked critical or noncritical, but if it is marked critical, the relying party must retrieve and use this information. RFC3280 states that this extension should be marked noncritical. Private extensions can also be defined in accordance with X.509. Private extensions are typically defined for domain-specific use. For example, RFC3280 defines two private extensions for Internet use as follows: Authority Information Access, a private extension present in end-entity and CA certificates, indicates how information or services offered by the issuer of the certificate can be obtained. The type of information and services include on-line validation services and policy information but do not include CRL location information. (The CRL Distribution Point discussed earlier is used for that purpose.) The extension syntax is composed of a sequence of an access method OID that describes the type and format of the service/information and the associated location of the service/information in the form of a General Name (for example, a URI, Directory Name, or RFC822 Name). Two access method OIDs have been defined. One access method, referred to as CA Issuers, retrieves information about CAs that are superior to the issuer of the certificate. This information can be used to help build certification paths. The other defined access method is for on-line validation services based on OCSP. (Refer to Chapter 8 for more information on OCSP.) Other access methods may be defined in the future. RFC3280 states that this extension must be marked noncritical. Subject Information Access, a private extension present in end-entity and CA certificates, indicates how information and services offered by the subject in the certificate can be obtained. Like the Authority Information Access private extension, the extension syntax is composed of a sequence of an access method OID and the associated location of the service/information in the form of a General Name. One access method OID has been defined for CAs (CA Repository), and one access method OID has been defined for end entities (time stamping). The CA Repository access method identifies the location of the repository where the CA publishes certificate and CRL information. The Time-Stamping access method indicates that the subject identified in the certificate offers a time stamping service. Other access methods may be defined in the future. RFC3280 states that this extension must be marked noncritical. Alternative Certificate Formats As discussed previously in this chapter, certificate types other than the X.509 Version 3 publickey certificate are available. We discuss these further in the next few pages.
11 ch06.fm Page 79 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 79 SPKI In contrast to the IETF PKIX Working Group that focused on X.509 issues for the Internet (see Chapter 18), a separate IETF working group was formed to address a (potentially) simpler public-key infrastructure, referred to as the Simple Public Key Infrastructure (SPKI), for the Internet. Specifically, the charter of the IETF SPKI Working Group 3 was to develop Internet standards for an IETF sponsored public-key certificate format, associated signature and other formats, and key acquisition protocols. The key certificate format and associated protocols are to be simple to understand, implement, and use. The IETF SPKI Working Group produced a number of technical and informational documents, including SPKI certificate format SPKI certificate theory SPKI requirements SPKI examples You can retrieve the relevant SPKI documents from _charters/spki-charter.html. Because the focus of the SPKI work was on authorization rather than on identity, the SPKI certificate is referred to as an authorization certificate. The primary purpose of the SPKI authorization certificate is to convey permissions. It also includes the ability to delegate permissions to others. Although the SPKI authorization certificate has some things in common with an X.509 publickey certificate (for example, Issuer and Validity), the syntax and, in many cases, the semantics of these fields are not the same. Further, a number of fields are defined for one type of certificate that does not correspond to an equivalent mapping in the other. In addition, the naming conventions (and assumptions) are completely different because the SPKI work adopted the naming conventions as defined in SDSI. The IETF work on SPKI has concluded. However, the extent to which this work will be used in practice still remains to be seen. There is currently very little demand for SPKI-based certificates, and in the absence of market demand, CA and PKI vendors are not likely to implement a completely different certificate syntax in addition to X.509 Version 3 public-key certificates. 3 See
12 ch06.fm Page 80 Thursday, September 26, :55 PM 80 Understanding PKI Chapter 18 provides additional information regarding the role and status of the SPKI work. PGP Essentially, Pretty Good Privacy (PGP) is a method for encrypting and digitally signing messages and files. Phil Zimmermann introduced the first version of PGP in the early 1990s [Zimm95]. Version 2.x of PGP was published a number of years later as an IETF standardstrack specification entitled PGP Message Exchange Formats [RFC1991]. The latest version of PGP, referred to as OpenPGP, has been published as an IETF standards-track specification entitled OpenPGP Message Format [RFC2440]. A document on the Internet standards track also incorporates MIME with PGP and is entitled MIME Security with Pretty Good Privacy [RFC2015]. PGP specifies packet formats that convey messages and files from one entity to another. PGP also includes packet formats that convey PGP keys (sometimes referred to as PGP certificates) from one entity to another. Significant differences exist between PGP keys (or certificates) and X.509 Version 3 public-key certificates, and the trust models they embody are also completely different. (Chapter 9 discusses the PGP trust model further.) The significant differences between PGP keys and the X.509 Version 3 public-key certificate have created interoperability barriers between the PGPuser community and other communities that base their certificate formats on X.509 (for example, the S/MIME-user community). This is much more than a protocol incompatibility issue because the very foundation for the underlying public-key-enabled security services is different and incompatible. One possible solution is for PGP (or OpenPGP) to adopt X.509 Version 3 public-key certificates in addition to (or perhaps in lieu of) the PGP certificate. In fact, Version 6.5 of OpenPGP has pursued this direction and is now capable of supporting X.509 certificates. Although allowing OpenPGP users to tap into X.509-based PKIs, this still does not solve the basic protocol incompatibilities between OpenPGP and S/MIME. Another possibility might be for PKI vendors to offer products that support both PGP and X.509 Version 3 public-key certificates, but this can lead to other difficulties due to the significant differences in the trust models. (For example, it would introduce significant administrative and control issues.) Although PGP enjoys a significant amount of use over the Internet, it does not make a good candidate for the corporate intranet (that is, the enterprise domain) because all trust decisions rest with individuals rather than with the enterprise. Because many CA and PKI vendors seem to have concentrated their product development efforts on the enterprise domain, it is unclear that they have any motivation to offer PGP-compatible (or OpenPGP-compatible) products. Chapter 18 provides additional information regarding the role and status of the PGP/Open- PGP work.
13 ch06.fm Page 81 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 81 SET The Secure Electronic Transaction (SET) specifications [SET1; SET2; SET3] define a standard to support credit card payment transactions over distributed communications networks such as the Internet. Essentially, SET defines a standard payment protocol and specifies requirements that the supporting PKI is expected to meet. SET adopts the X.509 Version 3 public-key certificate format, and it defines specific private extensions that have meaning only in a SET context. SET also levies certain profile requirements on the standard extensions. Figure 6.2 illustrates a SET certificate. Note that Figure 6.2 does not represent all the possible extensions. (For example, it does not represent the Hashed Root Key extension present in a SET root CA certificate.) Because non-set applications will not understand the private extensions SET defines, one cannot expect a non-set application (for example, S/MIME-based ) to accept a SET certificate for use. This is true even though the SET certificate format is compliant with an X.509 Version 3 public-key certificate. Although one might suggest that a non-set application could ignore the SET extensions, the Certificate Type extension is critical; therefore, by definition a non-set application must reject a SET certificate. Note that it is accepted practice to intentionally mark certain extensions critical so that a particular type of certificate can be used only in the context of a specific application to minimize liability concerns. Figure 6.2 SET certificate structure. Signed by Authorized CA Serial Subject Public Issuer Subject Version Signature Issuer Validity Subject Extensions Number Key Info Unique ID Unique ID Authority Key Identifier Key Usage Certificate Type Merchant Data (M) Card Certificate Required (G) Tunneling (G) SET Qualifier Standard Extensions SET Specific Extensions (G) - Payment Gateway Only (M) - Merchant Only
14 ch06.fm Page 82 Thursday, September 26, :55 PM 82 Understanding PKI Although it is not necessarily the case that end users will require a separate certificate for each application, this example helps illustrate that multiple certificates per end entity will be required. (Chapter 10 provides additional discussion regarding the requirements for multiple certificates.) Attribute Certificates Attribute certificates were first standardized in the 1997 version of X.509 when the basic ASN.1 constructs for an attribute certificate were defined. The 2000 version of X.509 expands on the definition and use of attribute certificates significantly and even describes an attribute certificate framework that can be used as a foundation for building Privilege Management Infrastructures (PMIs). The subject of PMI is rather extensive and could very well be the topic of another book. For the purpose of this book, it is sufficient to say that although attribute certificates are defined in the X.509 Recommendation attribute certificates are not publickey certificates. Attribute certificates are designed to convey (potentially short-lived) attributes about a given subject to facilitate flexible and scalable privilege management. The attribute certificate may point to a public-key certificate that can be used to authenticate the identity of the attribute certificate holder. (Chapter 5 provides additional information regarding privilege management.) Certificate Policies As indicated earlier, a number of policy-related extensions may be present in a given certificate. The policy-related extensions are extremely important in the sense that they help govern the acceptable use of the certificate in terms of policy compliance, potentially across multiple PKI domains. The policy-related extensions refer either directly or indirectly to a certificate policy. The X.509 Recommendation [X ] defines a Certificate Policy as a named set of rules that indicates the applicability of a certificate to a particular community and/or class of application with common security requirements. For example, a particular certificate policy might indicate applicability of a type of certificate to the authentication of electronic data interchange transactions for the trading of goods within a given price range. The Internet X.509 Public Key Infrastructure Certificate Policy and Certification Practices Framework [RFC2527] also adopts this definition. This can be contrasted with the definition of a Certification Practice Statement (CPS): a statement of the practices which a certification authority employs in issuing certificates [ABA].
15 ch06.fm Page 83 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 83 In general, it is agreed that (1) a Certificate Policy is a high-level statement of requirements and restrictions associated with the intended use of the certificates issued under that policy and (2) a CPS is an extremely detailed (and potentially extremely sensitive) document that describes the internal operating procedures of the CA and/or PKI that issues those certificates. What is not universally accepted is the role that these documents have with respect to end-user notice and multidomain cross-certification arrangements. Interesting sources of information related to Certificate Policies and CPSs include the following: The Internet X.509 Public Key Infrastructure: Certificate Policy and Certification Practices Framework [RFC2527] CARAT Guidelines [CARAT] sponsored by the National Automated Clearing House Association (NACHA) The American Bar Association (ABA), Digital Signature Guidelines: Legal Infrastructure for Certification Authorities and Electronic Commerce [ABA] The Automotive Network exchange (ANX) Certificate Policy [ANX] The Government of Canada Certificate Policy [GOCCP] The U.S. Federal PKI Model Certificate Policy [MCP] From a high-level perspective, most of this documentation reflects the common theme noted earlier. In particular, a Certificate Policy is expected to be a higher-level document than a CPS, and it is typically concerned with what will be supported rather than how it will be supported. (See Box 6.3.) Conversely, a CPS is expected to be a fairly detailed and comprehensive technical and procedural document regarding the operation of the supporting infrastructure. For example RFC2527 points out that CPSs may be quite comprehensive, robust documents providing a description of the precise service offerings, detailed procedures of the life-cycle management of certificates, and more a level of detail which weds the CPS to a particular (proprietary) implementation of a service offering. Object Identifiers To easily distinguish one Certificate Policy from another, each Certificate Policy is assigned a globally unique OID. One or more OIDs can be specified in the Certificate Policies certificate extension, which can be further qualified as appropriate. For example, RFC3280 defines two optional Certificate Policy qualifiers: a User Notice and a pointer to a CPS. Certificate Policies can be placed in end-entity certificates as well as CA certificates. Cross-certificates (as described in Chapter 9) may also contain the Policy Mappings extension, which permits a policy OID in
16 ch06.fm Page 84 Thursday, September 26, :55 PM 84 Understanding PKI Box 6.3 The Role of Certificate Policies and CPSs The role that Certificate Policies and CPSs may have is not universally agreed upon and, to a large extent, depends on the type of PKI domain in question. For example, the model we see in the Web environment demonstrates that suppliers of Web server and end-user certificates (such as Verisign) publish their CPS on their Web site, and the certificates that they issue point to their on-line CPS. The CPS contains a great deal of information, including warranties and obligations meant to be conveyed to the end user. Thus, the CPS is a public-domain document, subject to the scrutiny of many. On the other hand, an enterprise PKI domain typically considers the CPS to be extremely sensitive, usually reserved for internal audit purposes. The CPS is rarely a public-domain document in these cases, nor is it used to convey information to the end users in the enterprise domain. The role these documents have in forging cross-certification arrangements (cross-certification is described in Chapter 9) can also vary. One school of thought suggests that the CPS of one domain should be scrutinized against the CPS of another. On the other hand, the CPS may not form a suitable basis for establishing cross-certification (or more generally, interoperability arrangements) for a number of reasons. First, as noted earlier, the CPS tends to be an extremely detailed and voluminous document, which would make CPS comparisons tedious and labor intensive (barring standardized markup languages and automated tools, of course). Second, terminology variations from one CPS to another that make equivalency comparisons problematic may be present [PAG]. Third, a given organization may consider their CPS to be too sensitive to be released externally, even for the purposes of establishing a cross-certification agreement with another enterprise. It can therefore be argued that Certificate Policies form a much more suitable basis for establishing cross-certification agreements. In the future, we may even see the use of PKI Disclosure Statements for establishing interoperability agreements between enterprise domains. See for an example of a PKI Disclosure Statement. Given the above, some would suggest that only a CPS is required for a CA service provider and only a Certificate Policy is required for an organization. However, it has been our experience that a CPS is typically used in an enterprise context to document the internal operating procedures of the organization s PKI and that the CPS is often used for internal audit purposes. It is also possible for an organization to adopt the CPS of a thirdparty service provider when that third party supplies some or all of that organization s PKI services.
17 ch06.fm Page 85 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 85 one domain to be designated equivalent to a policy OID in another domain. Thus, if two PKI domains have each defined a Certificate Policy for the exchange of their own internal and the two policies are deemed to be equivalent by each domain, defining yet a third policy OID to allow exchanges between the two domains is not needed. Policy Authorities Policy authorities (sometimes referred to as policy management authorities) establish Certificate Policies. The policy authority itself may vary from one organization to another. For example, each organization may establish its own policies under the authority of the internal Information Technology Security (ITS) department or equivalent. Alternatively, this authority may emanate from a policy advisory board made up of members from each major department in an organization. In concert with the internal authority (or perhaps in lieu of such an authority), an external policy authority may establish the Certificate Policies for a number of PKI domains that belong to the same community of interest. In any event, the applicable policy authority is responsible for registering Certificate Policies with the appropriate registration authority (for example, a national registration authority) so that the Certificate Policy OIDs can be assigned appropriately. Certification Authority In the context of a PKI, certification is the act of binding a subject name (and potentially other attributes) with a public key. As discussed previously in this chapter, this binding occurs in the form of a signed data structure referred to as a public-key certificate. A Certification Authority (CA) is responsible for issuing these public-key certificates. (See Box 6.4.) These certificates are digitally signed with the private key of the issuing CA. Box 6.4 Certificate Authority versus Certification Authority A CA is sometimes referred to as a certificate authority rather than a Certification Authority in much of today s literature. Although it may be too late to stop the growing use of this term, we would like to point out that using this term to denote a CA is technically (and logically) incorrect. There is no such thing as a certificate authority in X.509, and the implication that a CA is an authority on certificates is somewhat misleading. Specifically, a policy authority (or policy management authority) is the authority on certificates; the CA is simply an instrument that issues certificates in accordance with the Certificate Policy dictated by the policy authority. The term Certification Authority is used throughout this book because a CA is an authority on the process of certification.
18 ch06.fm Page 86 Thursday, September 26, :55 PM 86 Understanding PKI Because the issuing CA digitally signs certificates, they are self-protected from an integrity perspective. Thus, the certificates can be freely disseminated, assuming that they do not contain any sensitive information. (In Chapter 11, we discuss the difficulties associated with the dissemination of certificates that might be considered sensitive in nature.) The CA can take on a number of different representations, depending on the trust model embodied by that CA. For example, in an enterprise domain, one can expect one or more CAs to be responsible for issuing certificates to the employees of the enterprise. The employees essentially place their trust in the enterprise CA(s). 4 A completely different architecture is reflected in the PGP web of trust model where individuals can act as their own CA, and all trust decisions lie with the individual rather than a remote CA. (Chapter 9 provides a more detailed discussion regarding trust models and the role a CA plays in relation to those trust models.) Registration Authority Although the registration function can be implemented directly with the CA component, it sometimes makes sense to off-load the registration function to a separate component referred to as a Registration Authority (RA). For example, as the number of end entities in a given PKI domain increases and/or the end entities are widely dispersed geographically, the notion of centralized registration becomes problematic. Judicious deployment of multiple RAs (sometimes referred to as Local Registration Authorities, or LRAs) helps solve this problem. The primary purpose of the RA is to off-load certain functions from the CA to enhance scalability and decrease operational costs. Although the functions implemented by the RA may vary, it can be designed to support one or more of the following: Establish and confirm the identity of an individual as part of the initialization process. (For example, the RA might verify the identify of an individual through a combination of physical presence and associated identification such as a driver s license, employee badge with picture, or a passport.) Distribute shared secrets to end users for subsequent authentication during an on-line initialization process. Initiate the certification process with a CA on behalf of individual end-users (including the registration of certain attributes to be associated with the end user). 4 We recognize that the interpretation of the word trust is often the subject of lively debate. Chapter 9 provides the definition of trust as it applies in the context of this book.
19 ch06.fm Page 87 Thursday, September 26, :55 PM CHAPTER 6 Certificates and Certification 87 Generate keying material on behalf of an end user. Perform certain key/certificate life-cycle management functions, such as to initiate a revocation request or a key recovery operation on behalf of an end entity. Regardless of the set of functions implemented in the RA, it should be noted that a RA is never allowed to issue certificates or CRLs. These functions rest solely with the CA. End-entity registration requirements may vary significantly from one domain to another, between distinct applications in a given domain, or between distinct contexts in a given application in a given domain. (Chapter 7 discusses specific registration issues and procedures further.) 5 Summary The primary focus of this chapter has been the structure and semantics of the X.509 Version 3 public-key certificate and the need for certification in order to maintain the integrity and trustworthiness of the certificate itself. The Version 3 X.509 public-key certificate is by far the preferred choice for the enterprise domain, and it is quickly becoming widely accepted in other environments such as the Internet. This chapter also introduced a number of other certificate types (which may or may not be encountered in wide-scale implementation practice). We also addressed the importance and role of the CA and RA components. A CA is responsible for issuing certificates in accordance with one or more Certificate Policies. The CA may also be responsible for end-entity registration, although one or more RAs can implement this function separately. Deploying one or more RAs reduces cost and enhances the overall scalability of a large-scale PKI. A full understanding of certificates and certification requires familiarity with two related topics: the details regarding key/certificate life-cycle management (see Chapter 7) and the concepts associated with trust models and certification path processing. (See Chapter 9.) 5 Chapter 7 presents in detail all aspects associated with key/certificate life-cycle management (for example, registration and initialization, revocation, key recovery, and so on).
PKI Services. Text PKI Definition. PKI Definition #1. Public Key Infrastructure. What Does A PKI Do? Public Key Infrastructures
 Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
PKI-An Operational Perspective. NANOG 38 ARIN XVIII October 10, 2006
 PKI-An Operational Perspective NANOG 38 ARIN XVIII October 10, 2006 Briefing Contents PKI Usage Benefits Constituency Acceptance Specific Discussion of Requirements Certificate Policy Certificate Policy
PKI-An Operational Perspective NANOG 38 ARIN XVIII October 10, 2006 Briefing Contents PKI Usage Benefits Constituency Acceptance Specific Discussion of Requirements Certificate Policy Certificate Policy
Apple Inc. Certification Authority Certification Practice Statement
 Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.2 Effective
Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.2 Effective
Apple Inc. Certification Authority Certification Practice Statement
 Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.3 Effective
Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.3 Effective
Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure
 Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure 1.0 INTRODUCTION 1.1 Overview The Federal Reserve Banks operate a public key infrastructure (PKI) that manages
Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure 1.0 INTRODUCTION 1.1 Overview The Federal Reserve Banks operate a public key infrastructure (PKI) that manages
Apple Corporate Certificates Certificate Policy and Certification Practice Statement. Apple Inc.
 Apple Inc. Certificate Policy and Certification Practice Statement Version 1.0 Effective Date: March 12, 2015 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2. Table of acronyms... 4 1.3.
Apple Inc. Certificate Policy and Certification Practice Statement Version 1.0 Effective Date: March 12, 2015 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2. Table of acronyms... 4 1.3.
SSL Certificates Certificate Policy (CP)
 SSL Certificates Last Revision Date: February 26, 2015 Version 1.0 Revisions Version Date Description of changes Author s Name Draft 17 Jan 2011 Initial Release (Draft) Ivo Vitorino 1.0 26 Feb 2015 Full
SSL Certificates Last Revision Date: February 26, 2015 Version 1.0 Revisions Version Date Description of changes Author s Name Draft 17 Jan 2011 Initial Release (Draft) Ivo Vitorino 1.0 26 Feb 2015 Full
X.509. CPSC 457/557 10/17/13 Jeffrey Zhu
 X.509 CPSC 457/557 10/17/13 Jeffrey Zhu 2 3 X.509 Outline X.509 Overview Certificate Lifecycle Alternative Certification Models 4 What is X.509? The most commonly used Public Key Infrastructure (PKI) on
X.509 CPSC 457/557 10/17/13 Jeffrey Zhu 2 3 X.509 Outline X.509 Overview Certificate Lifecycle Alternative Certification Models 4 What is X.509? The most commonly used Public Key Infrastructure (PKI) on
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 11: Public Key Infrastructure Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Public key infrastructure Certificates Trust
CSE 565 Computer Security Fall 2018 Lecture 11: Public Key Infrastructure Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Public key infrastructure Certificates Trust
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Security Digital Certificate Manager
 System i Security Digital Certificate Manager Version 6 Release 1 System i Security Digital Certificate Manager Version 6 Release 1 Note Before using this information and the product it supports, be sure
System i Security Digital Certificate Manager Version 6 Release 1 System i Security Digital Certificate Manager Version 6 Release 1 Note Before using this information and the product it supports, be sure
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations
 Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.18 Effective Date: August 16, 2017 Table of Contents 1. Introduction... 5 1.1. Trademarks...
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.18 Effective Date: August 16, 2017 Table of Contents 1. Introduction... 5 1.1. Trademarks...
IBM. Security Digital Certificate Manager. IBM i 7.1
 IBM IBM i Security Digital Certificate Manager 7.1 IBM IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in
IBM IBM i Security Digital Certificate Manager 7.1 IBM IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in
Public Key Infrastructures. Using PKC to solve network security problems
 Public Key Infrastructures Using PKC to solve network security problems Distributing public keys P keys allow parties to share secrets over unprotected channels Extremely useful in an open network: Parties
Public Key Infrastructures Using PKC to solve network security problems Distributing public keys P keys allow parties to share secrets over unprotected channels Extremely useful in an open network: Parties
IBM i Version 7.2. Security Digital Certificate Manager IBM
 IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
CERTIFICATE POLICY CIGNA PKI Certificates
 CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
Some Lessons Learned from Designing the Resource PKI
 Some Lessons Learned from Designing the Resource PKI Geoff Huston Chief Scientist, APNIC May 2007 Address and Routing Security The basic security questions that need to be answered are: Is this a valid
Some Lessons Learned from Designing the Resource PKI Geoff Huston Chief Scientist, APNIC May 2007 Address and Routing Security The basic security questions that need to be answered are: Is this a valid
A PKI For IDR Public Key Infrastructure and Number Resource Certification
 A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
Version 3 X.509 Certificates
 Entrust Technologies White Paper Author: Ian Curry Date: July 1996 Version: 1.0 Entrust Technologies, 1997. All rights reserved. 1 1. Introduction This document provides a description of the version 3
Entrust Technologies White Paper Author: Ian Curry Date: July 1996 Version: 1.0 Entrust Technologies, 1997. All rights reserved. 1 1. Introduction This document provides a description of the version 3
Apple Inc. Certification Authority Certification Practice Statement. Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA
 Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Version 4.0 Effective Date: September 18, 2013 Table of Contents
Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Version 4.0 Effective Date: September 18, 2013 Table of Contents
R. Sabett Cooley Godward LLP C. Merrill McCarter & English, LLP S. Wu Infoliance, Inc. November 2003
 Network Working Group Request for Comments: 3647 Obsoletes: 2527 Category: Informational S. Chokhani Orion Security Solutions, Inc. W. Ford VeriSign, Inc. R. Sabett Cooley Godward LLP C. Merrill McCarter
Network Working Group Request for Comments: 3647 Obsoletes: 2527 Category: Informational S. Chokhani Orion Security Solutions, Inc. W. Ford VeriSign, Inc. R. Sabett Cooley Godward LLP C. Merrill McCarter
Public Key Infrastructures
 Foundations for secure e-commerce (bmevihim219) Dr. Levente Buttyán associate professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) buttyan@hit.bme.hu,
Foundations for secure e-commerce (bmevihim219) Dr. Levente Buttyán associate professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) buttyan@hit.bme.hu,
Internet Engineering Task Force (IETF) Request for Comments: 6403 Category: Informational ISSN: M. Peck November 2011
 Internet Engineering Task Force (IETF) Request for Comments: 6403 Category: Informational ISSN: 2070-1721 L. Zieglar NSA S. Turner IECA M. Peck November 2011 Suite B Profile of Certificate Management over
Internet Engineering Task Force (IETF) Request for Comments: 6403 Category: Informational ISSN: 2070-1721 L. Zieglar NSA S. Turner IECA M. Peck November 2011 Suite B Profile of Certificate Management over
Certification Authority
 Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
TELIA MOBILE ID CERTIFICATE
 Telia Mobile ID Certificate CPS v2.3 1 (56) TELIA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.3 Valid from June 30, 2017 Telia Mobile ID
Telia Mobile ID Certificate CPS v2.3 1 (56) TELIA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.3 Valid from June 30, 2017 Telia Mobile ID
Chapter 9: Key Management
 Chapter 9: Key Management Session and Interchange Keys Key Exchange Cryptographic Key Infrastructure Storing and Revoking Keys Digital Signatures Slide #9-1 Overview Key exchange Session vs. interchange
Chapter 9: Key Management Session and Interchange Keys Key Exchange Cryptographic Key Infrastructure Storing and Revoking Keys Digital Signatures Slide #9-1 Overview Key exchange Session vs. interchange
Lecture Notes 14 : Public-Key Infrastructure
 6.857 Computer and Network Security October 24, 2002 Lecture Notes 14 : Public-Key Infrastructure Lecturer: Ron Rivest Scribe: Armour/Johann-Berkel/Owsley/Quealy [These notes come from Fall 2001. These
6.857 Computer and Network Security October 24, 2002 Lecture Notes 14 : Public-Key Infrastructure Lecturer: Ron Rivest Scribe: Armour/Johann-Berkel/Owsley/Quealy [These notes come from Fall 2001. These
OpenADR Alliance Certificate Policy. OpenADR-CP-I
 Notice This document is a cooperative effort undertaken at the direction of the OpenADR Alliance and NetworkFX, Inc. for the benefit of the OpenADR Alliance. Neither party is responsible for any liability
Notice This document is a cooperative effort undertaken at the direction of the OpenADR Alliance and NetworkFX, Inc. for the benefit of the OpenADR Alliance. Neither party is responsible for any liability
Public Key Establishment
 Public Key Establishment Bart Preneel Katholieke Universiteit Leuven February 2007 Thanks to Paul van Oorschot How to establish public keys? point-to-point on a trusted channel mail business card, phone
Public Key Establishment Bart Preneel Katholieke Universiteit Leuven February 2007 Thanks to Paul van Oorschot How to establish public keys? point-to-point on a trusted channel mail business card, phone
Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
![Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7. Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.](/thumbs/84/91191448.jpg) Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
ICS 180 May 4th, Guest Lecturer: Einar Mykletun
 ICS 180 May 4th, 2004 Guest Lecturer: Einar Mykletun 1 Symmetric Key Crypto 2 Symmetric Key Two users who wish to communicate share a secret key Properties High encryption speed Limited applications: encryption
ICS 180 May 4th, 2004 Guest Lecturer: Einar Mykletun 1 Symmetric Key Crypto 2 Symmetric Key Two users who wish to communicate share a secret key Properties High encryption speed Limited applications: encryption
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.10 Effective Date: June 10, 2013
 Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.10 Effective Date: June 10, 2013 Table of Contents 1. Introduction... 5 1.1. Trademarks... 5
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.10 Effective Date: June 10, 2013 Table of Contents 1. Introduction... 5 1.1. Trademarks... 5
Lecture 15 Public Key Distribution (certification)
 0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
Public Key Infrastructure
 Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Introduction to SSL. Copyright 2005 by Sericon Technology Inc.
 Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Server-based Certificate Validation Protocol
 Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
Security Protocols and Infrastructures. Winter Term 2015/2016
 Security Protocols and Infrastructures Winter Term 2015/2016 Nicolas Buchmann (Harald Baier) Chapter 5: Standards for Security Infrastructures Contents Introduction and naming scheme X.509 and its core
Security Protocols and Infrastructures Winter Term 2015/2016 Nicolas Buchmann (Harald Baier) Chapter 5: Standards for Security Infrastructures Contents Introduction and naming scheme X.509 and its core
by Amy E. Smith, ShiuFun Poon, and John Wray
 Level: Intermediate Works with: Domino 6 Updated: 01-Oct-2002 by Amy E. Smith, ShiuFun Poon, and John Wray Domino 4.6 introduced the certificate authority (CA), a trusted server-based administration tool
Level: Intermediate Works with: Domino 6 Updated: 01-Oct-2002 by Amy E. Smith, ShiuFun Poon, and John Wray Domino 4.6 introduced the certificate authority (CA), a trusted server-based administration tool
Key Management. Digital signatures: classical and public key Classic and Public Key exchange. Handwritten Signature
 Key Management Digital signatures: classical and public key Classic and Public Key exchange 1 Handwritten Signature Used everyday in a letter, on a check, sign a contract A signature on a signed paper
Key Management Digital signatures: classical and public key Classic and Public Key exchange 1 Handwritten Signature Used everyday in a letter, on a check, sign a contract A signature on a signed paper
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
Cristina Nita-Rotaru. CS355: Cryptography. Lecture 17: X509. PGP. Authentication protocols. Key establishment.
 CS355: Cryptography Lecture 17: X509. PGP. Authentication protocols. Key establishment. Public Keys and Trust Public Key:P A Secret key: S A Public Key:P B Secret key: S B How are public keys stored How
CS355: Cryptography Lecture 17: X509. PGP. Authentication protocols. Key establishment. Public Keys and Trust Public Key:P A Secret key: S A Public Key:P B Secret key: S B How are public keys stored How
Certification Practice Statement
 SWIFT SWIFT Qualified Certificates Certification Practice Statement This document applies to SWIFT Qualified Certificates issued by SWIFT. This document is effective from 1 July 2016. 17 June 2016 SWIFT
SWIFT SWIFT Qualified Certificates Certification Practice Statement This document applies to SWIFT Qualified Certificates issued by SWIFT. This document is effective from 1 July 2016. 17 June 2016 SWIFT
The Information Technology (Certifying Authority) Regulations, 2001
 The Information Technology (Certifying Authority) Regulations, 2001 The Information Technology (Certifying Authority) Regulations, 2001 Appendix XXXIV Notification, New Delhi, the 9th July, 2001, G.S.R.
The Information Technology (Certifying Authority) Regulations, 2001 The Information Technology (Certifying Authority) Regulations, 2001 Appendix XXXIV Notification, New Delhi, the 9th July, 2001, G.S.R.
Network Security Essentials
 Network Security Essentials Fifth Edition by William Stallings Chapter 4 Key Distribution and User Authentication No Singhalese, whether man or woman, would venture out of the house without a bunch of
Network Security Essentials Fifth Edition by William Stallings Chapter 4 Key Distribution and User Authentication No Singhalese, whether man or woman, would venture out of the house without a bunch of
SONERA MOBILE ID CERTIFICATE
 Sonera Mobile ID Certificate CPS v2.1 1 (56) SONERA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.1 Valid from, domicile: Helsinki, Teollisuuskatu
Sonera Mobile ID Certificate CPS v2.1 1 (56) SONERA MOBILE ID CERTIFICATE CERTIFICATION PRACTICE STATEMENT (Translation from official Finnish version) Version 2.1 Valid from, domicile: Helsinki, Teollisuuskatu
FPKIPA CPWG Antecedent, In-Person Task Group
 FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
Digital Certificates Demystified
 Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Category: Standards Track W. Ford VeriSign D. Solo Citigroup April 2002
 Network Working Group Request for Comments: 3280 Obsoletes: 2459 Category: Standards Track R. Housley RSA Laboratories W. Polk NIST W. Ford VeriSign D. Solo Citigroup April 2002 Internet X.509 Public Key
Network Working Group Request for Comments: 3280 Obsoletes: 2459 Category: Standards Track R. Housley RSA Laboratories W. Polk NIST W. Ford VeriSign D. Solo Citigroup April 2002 Internet X.509 Public Key
Public-Key Infrastructure NETS E2008
 Public-Key Infrastructure NETS E2008 Many slides from Vitaly Shmatikov, UT Austin slide 1 Authenticity of Public Keys? private key Alice Bob public key Problem: How does Alice know that the public key
Public-Key Infrastructure NETS E2008 Many slides from Vitaly Shmatikov, UT Austin slide 1 Authenticity of Public Keys? private key Alice Bob public key Problem: How does Alice know that the public key
Smart Meters Programme Schedule 2.1
 Smart Meters Programme Schedule 2.1 (DCC Requirements) (SMKI version) V1.2 1 Schedule 2.1 (DCC Requirements) This Schedule 2.1 (DCC Requirements) is formed of the following parts: Part A Introduction...3
Smart Meters Programme Schedule 2.1 (DCC Requirements) (SMKI version) V1.2 1 Schedule 2.1 (DCC Requirements) This Schedule 2.1 (DCC Requirements) is formed of the following parts: Part A Introduction...3
ING Corporate PKI G3 Internal Certificate Policy
 ING Corporate PKI G3 Internal Certificate Policy Version 1.0 March 2018 ING Corporate PKI Service Centre Final Version 1.0 Document information Commissioned by Additional copies of this document ING Corporate
ING Corporate PKI G3 Internal Certificate Policy Version 1.0 March 2018 ING Corporate PKI Service Centre Final Version 1.0 Document information Commissioned by Additional copies of this document ING Corporate
SOME TYPES AND USES OF DATA MODELS
 3 SOME TYPES AND USES OF DATA MODELS CHAPTER OUTLINE 3.1 Different Types of Data Models 23 3.1.1 Physical Data Model 24 3.1.2 Logical Data Model 24 3.1.3 Conceptual Data Model 25 3.1.4 Canonical Data Model
3 SOME TYPES AND USES OF DATA MODELS CHAPTER OUTLINE 3.1 Different Types of Data Models 23 3.1.1 Physical Data Model 24 3.1.2 Logical Data Model 24 3.1.3 Conceptual Data Model 25 3.1.4 Canonical Data Model
Conformance Requirements Guideline Version 0.1
 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 Editors: Conformance Requirements Guideline Version 0.1 Aug 22, 2001 Lynne Rosenthal (lynne.rosenthal@nist.gov)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 Editors: Conformance Requirements Guideline Version 0.1 Aug 22, 2001 Lynne Rosenthal (lynne.rosenthal@nist.gov)
X.509 Certificate Policy For The Virginia Polytechnic Institute and State University Certification Authorities
 X.509 Certificate Policy For The Virginia Polytechnic Institute and State University Certification Authorities May 13, 2004 Amended March 16, 2011 OBJECT IDENTIFIER 1.3.6.1.4.1.6760.5.2.1.1.1 Release 1.0
X.509 Certificate Policy For The Virginia Polytechnic Institute and State University Certification Authorities May 13, 2004 Amended March 16, 2011 OBJECT IDENTIFIER 1.3.6.1.4.1.6760.5.2.1.1.1 Release 1.0
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
ECA Trusted Agent Handbook
 Revision 8.0 September 4, 2015 Introduction This Trusted Agent Handbook provides instructions for individuals authorized to perform personal presence identity verification of subscribers enrolling for
Revision 8.0 September 4, 2015 Introduction This Trusted Agent Handbook provides instructions for individuals authorized to perform personal presence identity verification of subscribers enrolling for
Disclosure text - PDS (PKI Disclosure Statement) for electronic signature and authentication certificates
 Disclosure text - PDS (PKI Disclosure Statement) for electronic signature and authentication certificates Index INDEX... 2 1. DISCLOSURE TEXT APPLICABLE TO NATURAL PERSON CERTIFICATES ISSUED ON QSCD...
Disclosure text - PDS (PKI Disclosure Statement) for electronic signature and authentication certificates Index INDEX... 2 1. DISCLOSURE TEXT APPLICABLE TO NATURAL PERSON CERTIFICATES ISSUED ON QSCD...
TeliaSonera Gateway Certificate Policy and Certification Practice Statement
 TeliaSonera Gateway Certificate Policy and Certification Practice Statement v. 1.2 TeliaSonera Gateway Certificate Policy and Certification Practice Statement TeliaSonera Gateway CA v1 OID 1.3.6.1.4.1.271.2.3.1.1.16
TeliaSonera Gateway Certificate Policy and Certification Practice Statement v. 1.2 TeliaSonera Gateway Certificate Policy and Certification Practice Statement TeliaSonera Gateway CA v1 OID 1.3.6.1.4.1.271.2.3.1.1.16
APNIC Trial of Certification of IP Addresses and ASes
 APNIC Trial of Certification of IP Addresses and ASes ARIN XVII Open Policy Meeting George Michaelson Geoff Huston Motivation: Address and Routing Security What we have today is a relatively insecure system
APNIC Trial of Certification of IP Addresses and ASes ARIN XVII Open Policy Meeting George Michaelson Geoff Huston Motivation: Address and Routing Security What we have today is a relatively insecure system
Security Protocols and Infrastructures
 Security Protocols and Infrastructures Dr. Michael Schneider michael.schneider@h-da.de Chapter 5: Standards for Security Infrastructures November 13, 2017 h_da WS2017/18 Dr. Michael Schneider 1 1 Introduction
Security Protocols and Infrastructures Dr. Michael Schneider michael.schneider@h-da.de Chapter 5: Standards for Security Infrastructures November 13, 2017 h_da WS2017/18 Dr. Michael Schneider 1 1 Introduction
OISTE-WISeKey Global Trust Model
 OISTE-WISeKey Global Trust Model Certification Practices Statement (CPS) Date: 18/04/2018 Version: 2.10 Status: FINAL No. of Pages: 103 OID: 2.16.756.5.14.7.1 Classification: PUBLIC File: WKPKI.DE001 -
OISTE-WISeKey Global Trust Model Certification Practices Statement (CPS) Date: 18/04/2018 Version: 2.10 Status: FINAL No. of Pages: 103 OID: 2.16.756.5.14.7.1 Classification: PUBLIC File: WKPKI.DE001 -
Public Key Infrastructures
 Public Key Infrastructures How to authenticate public keys? Chapter 4 Certificates Cryptography and Computeralgebra Johannes Buchmann 1 2 Authenticated by digital signature 3 4 Click on icon Click on view
Public Key Infrastructures How to authenticate public keys? Chapter 4 Certificates Cryptography and Computeralgebra Johannes Buchmann 1 2 Authenticated by digital signature 3 4 Click on icon Click on view
Smart Grid Security. Selected Principles and Components. Tony Metke Distinguished Member of the Technical Staff
 Smart Grid Security Selected Principles and Components Tony Metke Distinguished Member of the Technical Staff IEEE PES Conference on Innovative Smart Grid Technologies Jan 2010 Based on a paper by: Anthony
Smart Grid Security Selected Principles and Components Tony Metke Distinguished Member of the Technical Staff IEEE PES Conference on Innovative Smart Grid Technologies Jan 2010 Based on a paper by: Anthony
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename
 6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
APNIC Trial of Certification of IP Addresses and ASes
 APNIC Trial of Certification of IP Addresses and ASes RIPE 52 Plenary George Michaelson Geoff Huston Motivation: Address and Routing Security What we have today is a relatively insecure system that is
APNIC Trial of Certification of IP Addresses and ASes RIPE 52 Plenary George Michaelson Geoff Huston Motivation: Address and Routing Security What we have today is a relatively insecure system that is
CHEVRON U.S.A. INC. PUBLIC KEY INFRASTRUCTURE Root Certificate Authority Set of Provisions Version 2
 CHEVRON U.S.A. INC. PUBLIC KEY INFRASTRUCTURE Root Certificate Authority Set of Provisions Version 2 Approved by the Chevron Policy Management Authority on December 20, 2012 LEGAL DISCLAIMER No portion
CHEVRON U.S.A. INC. PUBLIC KEY INFRASTRUCTURE Root Certificate Authority Set of Provisions Version 2 Approved by the Chevron Policy Management Authority on December 20, 2012 LEGAL DISCLAIMER No portion
Issues in Assessing Commercial Certification Service Trust
 The Open Group Security Program Group Building Trust on the Net ---- San Diego -- April 30, 1998 Issues in Assessing Commercial Certification Service Trust Michael S. Baum, J.D., M.B.A. VP, Practices &
The Open Group Security Program Group Building Trust on the Net ---- San Diego -- April 30, 1998 Issues in Assessing Commercial Certification Service Trust Michael S. Baum, J.D., M.B.A. VP, Practices &
Digi-CPS. Certificate Practice Statement v3.6. Certificate Practice Statement from Digi-Sign Limited.
 Certificate Practice Statement v3.6 Certificate Practice Statement from Digi-Sign Limited. Digi-CPS Version 3.6. Produced by the Legal & Technical Departments For further information, please contact: CONTACT:
Certificate Practice Statement v3.6 Certificate Practice Statement from Digi-Sign Limited. Digi-CPS Version 3.6. Produced by the Legal & Technical Departments For further information, please contact: CONTACT:
Machine Readable Travel Documents
 Machine Readable Travel Documents GUIDANCE DOCUMENT PKI for Machine Readable Travel Documents Version -1.0 Date - 22 June, 2011 Pg. 1 of 24 Table of Contents 1 Introduction... 5 2 Structure of the document...
Machine Readable Travel Documents GUIDANCE DOCUMENT PKI for Machine Readable Travel Documents Version -1.0 Date - 22 June, 2011 Pg. 1 of 24 Table of Contents 1 Introduction... 5 2 Structure of the document...
PUBLIC-KEY CERTIFICATES
 INFS 766 Internet Security Protocols Lecture 6 Digital Certificates Prof. Ravi Sandhu PUBLIC-KEY CERTIFICATES reliable distribution of public-keys public-key encryption sender needs public key of receiver
INFS 766 Internet Security Protocols Lecture 6 Digital Certificates Prof. Ravi Sandhu PUBLIC-KEY CERTIFICATES reliable distribution of public-keys public-key encryption sender needs public key of receiver
DECISION OF THE EUROPEAN CENTRAL BANK
 L 74/30 Official Journal of the European Union 16.3.2013 DECISIONS DECISION OF THE EUROPEAN CENTRAL BANK of 11 January 2013 laying down the framework for a public key infrastructure for the European System
L 74/30 Official Journal of the European Union 16.3.2013 DECISIONS DECISION OF THE EUROPEAN CENTRAL BANK of 11 January 2013 laying down the framework for a public key infrastructure for the European System
EXBO e-signing Automated for scanned invoices
 EXBO e-signing Automated for scanned invoices Signature Policy Document OID: 0.3.2062.7.2.1.12.1.0 Approval Status: Approved Version: 1.0 Page #: 1 of 13 1. Introduction 1.1. Scope This document covers
EXBO e-signing Automated for scanned invoices Signature Policy Document OID: 0.3.2062.7.2.1.12.1.0 Approval Status: Approved Version: 1.0 Page #: 1 of 13 1. Introduction 1.1. Scope This document covers
National Identity Exchange Federation. Trustmark Signing Certificate Policy. Version 1.0. Published October 3, 2014 Revised March 30, 2016
 National Identity Exchange Federation Trustmark Signing Certificate Policy Version 1.0 Published October 3, 2014 Revised March 30, 2016 Copyright 2016, Georgia Tech Research Institute Table of Contents
National Identity Exchange Federation Trustmark Signing Certificate Policy Version 1.0 Published October 3, 2014 Revised March 30, 2016 Copyright 2016, Georgia Tech Research Institute Table of Contents
DIGITALSIGN - CERTIFICADORA DIGITAL, SA.
 DIGITALSIGN - CERTIFICADORA DIGITAL, SA. TIMESTAMP POLICY VERSION 1.1 21/12/2017 Page 1 / 18 VERSION HISTORY Date Edition n.º Content 10/04/2013 1.0 Initial drafting 21/12/2017 1.1 Revision AUTHORIZATIONS
DIGITALSIGN - CERTIFICADORA DIGITAL, SA. TIMESTAMP POLICY VERSION 1.1 21/12/2017 Page 1 / 18 VERSION HISTORY Date Edition n.º Content 10/04/2013 1.0 Initial drafting 21/12/2017 1.1 Revision AUTHORIZATIONS
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 15945 First edition 2002-02-01 Information technology Security techniques Specification of TTP services to support the application of digital signatures Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 15945 First edition 2002-02-01 Information technology Security techniques Specification of TTP services to support the application of digital signatures Technologies de l'information
INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD This is a preview - click here to buy the full publication ISO/IEC 9594-8 Eighth edition 2017-05 Information technology Open Systems Interconnection The Directory Part 8: frameworks
INTERNATIONAL STANDARD This is a preview - click here to buy the full publication ISO/IEC 9594-8 Eighth edition 2017-05 Information technology Open Systems Interconnection The Directory Part 8: frameworks
ING Public Key Infrastructure Technical Certificate Policy
 ING Public Key Infrastructure Technical Certificate Policy Version 5.4 - November 2015 Commissioned by ING PKI Policy Approval Authority (PAA) Additional copies Document version General Of this document
ING Public Key Infrastructure Technical Certificate Policy Version 5.4 - November 2015 Commissioned by ING PKI Policy Approval Authority (PAA) Additional copies Document version General Of this document
Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile draft-ietf-pkix-rfc3280bis-04.
 Network Working Group Internet-Draft Obsoletes: 3280, 4325 (if approved) Expires: December 2006 D. Cooper NIST S. Santesson Microsoft S. Farrell Trinity College Dublin S. Boeyen Entrust R. Housley Vigil
Network Working Group Internet-Draft Obsoletes: 3280, 4325 (if approved) Expires: December 2006 D. Cooper NIST S. Santesson Microsoft S. Farrell Trinity College Dublin S. Boeyen Entrust R. Housley Vigil
X.509 CERTIFICATE X.509 CERTIFICATE PUBLIC-KEY CERTIFICATES THE CERTIFICATE TRIANGLE CERTIFICATE TRUST. INFS 766 Internet Security Protocols
 INFS 766 Internet Security Protocols X.509 CERTIFICATE Lecture 6 Digital Certificates VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER VALIDITY Prof. Ravi SUBJECT SUBJECT PUBLIC KEY INFO SIGNATURE 4 PUBLIC-KEY
INFS 766 Internet Security Protocols X.509 CERTIFICATE Lecture 6 Digital Certificates VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER VALIDITY Prof. Ravi SUBJECT SUBJECT PUBLIC KEY INFO SIGNATURE 4 PUBLIC-KEY
Key management. Pretty Good Privacy
 ECE 646 - Lecture 4 Key management Pretty Good Privacy Using the same key for multiple messages M 1 M 2 M 3 M 4 M 5 time E K time C 1 C 2 C 3 C 4 C 5 1 Using Session Keys & Key Encryption Keys K 1 K 2
ECE 646 - Lecture 4 Key management Pretty Good Privacy Using the same key for multiple messages M 1 M 2 M 3 M 4 M 5 time E K time C 1 C 2 C 3 C 4 C 5 1 Using Session Keys & Key Encryption Keys K 1 K 2
National Identity Exchange Federation. Certificate Policy. Version 1.1
 National Identity Exchange Federation Certificate Policy Version 1.1 September 9, 2014 Table of Contents 1 Introduction...4 1.1 Overview... 6 1.1.1 Certificate Policy...6 1.1.2 References...6 1.2 Document
National Identity Exchange Federation Certificate Policy Version 1.1 September 9, 2014 Table of Contents 1 Introduction...4 1.1 Overview... 6 1.1.1 Certificate Policy...6 1.1.2 References...6 1.2 Document
thawte Certification Practice Statement Version 3.4
 thawte Certification Practice Statement Version 3.4 Effective Date: July, 2007 thawte Certification Practice Statement 2006 thawte, Inc. All rights reserved. Printed in the United States of America. Revision
thawte Certification Practice Statement Version 3.4 Effective Date: July, 2007 thawte Certification Practice Statement 2006 thawte, Inc. All rights reserved. Printed in the United States of America. Revision
What is a Digital Certificate? Basic Problem. Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
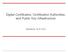 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
THE WALT DISNEY COMPANY PUBLIC KEY INFRASTRUCTURE CERTIFICATE POLICY. November 2015 Version 4.0. Copyright , The Walt Disney Company
 THE WALT DISNEY COMPANY PUBLIC KEY INFRASTRUCTURE CERTIFICATE POLICY November 2015 Version 4.0 Copyright 2006-2015, The Walt Disney Company Version Control Version Revision Date Revision Description Revised
THE WALT DISNEY COMPANY PUBLIC KEY INFRASTRUCTURE CERTIFICATE POLICY November 2015 Version 4.0 Copyright 2006-2015, The Walt Disney Company Version Control Version Revision Date Revision Description Revised
LET S ENCRYPT SUBSCRIBER AGREEMENT
 Page 1 of 7 LET S ENCRYPT SUBSCRIBER AGREEMENT This Subscriber Agreement ( Agreement ) is a legally binding contract between you and, if applicable, the company, organization or other entity on behalf
Page 1 of 7 LET S ENCRYPT SUBSCRIBER AGREEMENT This Subscriber Agreement ( Agreement ) is a legally binding contract between you and, if applicable, the company, organization or other entity on behalf
United States Department of Defense External Certification Authority X.509 Certificate Policy
 United States Department of Defense External Certification Authority X.509 Certificate Policy Version 4.3 4 January 2012 THIS PAGE INTENTIONALLY LEFT BLANK ii TABLE OF CONTENTS 1 Introduction...1 1.1 Overview...1
United States Department of Defense External Certification Authority X.509 Certificate Policy Version 4.3 4 January 2012 THIS PAGE INTENTIONALLY LEFT BLANK ii TABLE OF CONTENTS 1 Introduction...1 1.1 Overview...1
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Fourth edition 2001-08-01 Information technology Open Systems Interconnection The Directory: Public-key and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Fourth edition 2001-08-01 Information technology Open Systems Interconnection The Directory: Public-key and attribute certificate frameworks Technologies de l'information
Background. Network Security - Certificates, Keys and Signatures - Digital Signatures. Digital Signatures. Dr. John Keeney 3BA33
 Background Network Security - Certificates, Keys and Signatures - Dr. John Keeney 3BA33 Slides Sources: Karl Quinn, Donal O Mahoney, Henric Johnson, Charlie Kaufman, Wikipedia, Google, Brian Raiter. Recommended
Background Network Security - Certificates, Keys and Signatures - Dr. John Keeney 3BA33 Slides Sources: Karl Quinn, Donal O Mahoney, Henric Johnson, Charlie Kaufman, Wikipedia, Google, Brian Raiter. Recommended
AlphaSSL Certification Practice Statement
 AlphaSSL Certification Practice Statement Date: December 16th 2008 Version: v1.2 Table of Contents DOCUMENT HISTORY... 3 ACKNOWLEDGMENTS... 3 1.0 INTRODUCTION... 4 1.1 OVERVIEW... 4 1.2 ALPHASSL CERTIFICATE
AlphaSSL Certification Practice Statement Date: December 16th 2008 Version: v1.2 Table of Contents DOCUMENT HISTORY... 3 ACKNOWLEDGMENTS... 3 1.0 INTRODUCTION... 4 1.1 OVERVIEW... 4 1.2 ALPHASSL CERTIFICATE
X.509 Certificate Policy for the New Zealand Government PKI RSA Individual - Software Certificates (Medium Assurance)
 X.509 Certificate Policy for the New Zealand Government PKI RSA Individual - Software Certificates (Medium Assurance) Version 0.7 Mar-17 Notice to all parties seeking to rely Reliance on a Certificate
X.509 Certificate Policy for the New Zealand Government PKI RSA Individual - Software Certificates (Medium Assurance) Version 0.7 Mar-17 Notice to all parties seeking to rely Reliance on a Certificate
(1) Jisc (Company Registration Number ) whose registered office is at One Castlepark, Tower Hill, Bristol, BS2 0JA ( JISC ); and
 SUB-LRA AGREEMENT BETWEEN: (1) Jisc (Company Registration Number 05747339) whose registered office is at One Castlepark, Tower Hill, Bristol, BS2 0JA ( JISC ); and (2) You, the Organisation using the Jisc
SUB-LRA AGREEMENT BETWEEN: (1) Jisc (Company Registration Number 05747339) whose registered office is at One Castlepark, Tower Hill, Bristol, BS2 0JA ( JISC ); and (2) You, the Organisation using the Jisc
Avira Certification Authority Policy
 Avira Certification Authority Policy Version: 1.0 Status: Draft Updated: 2010-03-09 Copyright: Avira GmbH Author: omas Merkel Introduction is document describes the Certification Policy (CP) of Avira Certification
Avira Certification Authority Policy Version: 1.0 Status: Draft Updated: 2010-03-09 Copyright: Avira GmbH Author: omas Merkel Introduction is document describes the Certification Policy (CP) of Avira Certification
Entrust SSL Web Server Certificate Subscription Agreement
 Entrust SSL Web Server Certificate Subscription Agreement ATTENTION - READ CAREFULLY: THIS SUBSCRIPTION AGREEMENT (THIS "AGREEMENT") IS A LEGAL CONTRACT BETWEEN THE PERSON, ENTITY, OR ORGANIZATION NAMED
Entrust SSL Web Server Certificate Subscription Agreement ATTENTION - READ CAREFULLY: THIS SUBSCRIPTION AGREEMENT (THIS "AGREEMENT") IS A LEGAL CONTRACT BETWEEN THE PERSON, ENTITY, OR ORGANIZATION NAMED
Symantec Managed PKI Overview. v8.15
 Symantec Managed PKI Overview v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered trademarks of
Symantec Managed PKI Overview v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered trademarks of
Strong Customer Authentication and common and secure communication under PSD2. PSD2 in a nutshell
 Strong Customer Authentication and common and secure communication under PSD2 PSD2 in a nutshell Summary On August 12, the EBA has issued the long-awaited draft of the Regulatory Technical Standards (RTS)
Strong Customer Authentication and common and secure communication under PSD2 PSD2 in a nutshell Summary On August 12, the EBA has issued the long-awaited draft of the Regulatory Technical Standards (RTS)
Bart Preneel PKI. February Public Key Establishment. PKI Overview. Keys and Lifecycle Management. How to establish public keys?
 art Preneel How to establish public keys? Public Key Establishment art Preneel Katholieke Universiteit Leuven Thanks to Paul van Oorschot point-to-point on a trusted channel mail business card, phone direct
art Preneel How to establish public keys? Public Key Establishment art Preneel Katholieke Universiteit Leuven Thanks to Paul van Oorschot point-to-point on a trusted channel mail business card, phone direct
September 1997 Expires March Storing Certificates in the Domain Name System
 September 1997 Expires March 1998 Storing Certificates in the Domain Name System ------- ------------ -- --- ------ ---- ------ Donald E. Eastlake 3rd Olafur Gudmundsson Status of This Document This draft,
September 1997 Expires March 1998 Storing Certificates in the Domain Name System ------- ------------ -- --- ------ ---- ------ Donald E. Eastlake 3rd Olafur Gudmundsson Status of This Document This draft,
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
