K2289: Using advanced tcpdump filters
|
|
|
- Ella Gilbert
- 6 years ago
- Views:
Transcription
1 K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering for packets using source or destination port Filtering for packets using specific IP addresses Filtering for packets using ICMP header properties General trace principles References Introduction When you are analyzing a captured tcpdump, it is often useful to find packets with specific properties. To assist with this process, the tcpdump utility allows the creation of filter expressions based on the following protocol types: ether fddi ip arp rarp tcp udp icmp TCP flag headers are located in the 14th byte of the header. Since numbering starts at byte 0, the TCP flag header is in byte 13. Note: For diagrams of the TCP packet structure, refer to Byte 13 can contain up to eight one-bit flags; however, TCP can use only six flags. The other two bits are reserved and should be set to zero. For TCP headers with a single flag, there is one byte per bit and byte 13 contains the following binary values in decimal: Final (Fin) = 1 Sync (Syn) = 2
2 Reset (Rst) = 4 Push = 8 Acknowledgement (ack) = 16 Urgent (Urg) = 32 Reserved = 64 and 128 (should be zero) If multiple flags are set for the TCP header, the value of byte 13 is the binary sum of the values for all the bits that are set. For example: Fin, ack = 17 (1 + 16) Syn, ack = 18 (2 + 16) Push, ack = 24 (8 + 16) Fin, Push = 9 (1 + 8) Fin, Push, ack = 25 ( ) Note: When capturing traffic to send to F5 technical support, you should not use the advanced filters unless directed to from technical support. Filtering for packets using specific TCP flags headers If you know the expected value for byte 13 of the TCP header, you can create a filter to look for that specific byte using the following syntax: header[byte #] == value For example, if you want to see only the Syn packets, you would create the following filter to report all TCP headers that contain a TCP flag byte equal to 2 flag (Syn flag set): Note: The following examples assume a byte length of 1. tcpdump -ni internal 'tcp[13] == 2' Important : You must use the half-quotes (') in all the filters to protect the filter expression from the shell so that it is passed, intact, to the tcpdump utility. The output would appear similar to the following example: tcpdump: listening on internal 23:36: > : S : (0) win :36: > : S : (0) win :36: > : S : (0) win :36: > : S : (0) win 1638 To view only the Syn and ack packets, you would create the following filter to report all TCP headers that contain a TCP flag byte equal to 18 (Syn flag set + ack flag set = = 18): tcpdump -ni internal 'tcp[13] == 18' The output would appear similar to the following example:
3 tcpdump: listening on internal 23:38: > : S : (0) ack :38: > : S : (0) ack :38: > : S : (0) ack :38: > : S : (0) ack 2196 ^C 28 packets received by filter 0 packets dropped by kernel To view the Syn packets and the Syn and ack packets, you would create the following filter that accepts either value for the flag byte: tcpdump -ni internal 'tcp[13] == 18' or 'tcp[13] == 2' You could also create a filter that looks for the set Syn bit and ignores the rest of the flags in the header. You must set the filter to perform a logic AND (&) to remove all but the value of the Syn bit and then test it. For example, if the TCP flags are and the mask for Syn is (2 in binary) then = You can then test the resulting value against the Syn flag, by setting the filter as follows: tcpdump -ni internal 'tcp[13] & 2 == 2' The output would appear similar to the following example: tcpdump: listening on internal 23:44: > : S : (0) win :44: > : S : (0) win :44: > : S : (0) win :44: > : S : (0) ack :44: > : S : (0) win :44: > : S : (0) ack :44: > : S : (0) ack :44: > : S : (0) ack 1446 ^ C28 packets received by filter 0 packets dropped by kernel You can also use the following filter for a more general setting; however, it is best to write the rule as specifically as possible so that you do not have to re-write it later in the event that further troubleshooting is required: 'tcp[13] & 2!= 0' The!= [number] construct checks if any of the flags included in [number] are set and the == [number] construct checks if all the TCP header flags in [number] are set. Following are additional examples of filters for TCP header flags: Criteria Filter View only the Fin bit set 'tcp[13] == 1'
4 View only the Push bit set 'tcp[13] == 8' View only the Syn bit set 'tcp[13] == 2' View only Syn set, ignore the others 'tcp[13] & 2 == 2' View only Syn and ack set 'tcp[13] == 18' View Syn set and ack set, ignore all others 'tcp[13] & 18 == 18' View Rst set, ignore the others 'tcp[13] & 4 == 4' View both Syn and Fin set 'tcp[13] & 3 == 3' View either Syn or Fin set 'tcp[13] & 3!= 0' View only Syn or only Fin set 'tcp[13] == 2 or tcp[13] == 1' Filtering for packets using source or destination port You can create a filter that spans several bytes of the TCP header, such as the two-byte source and destination port numbers. (In the TCP header, the source port is bytes 0 and 1 and the destination port is bytes 2 and 3.) Note: The IANA Assigned Internet Protocol Numbers list may be found on the Protocol Numbers page. As with the TCP flag example, the first entry of the filter is the offset and the second entry is the number of bytes to check. If there is no second entry, the length defaults to 1 (as do the previous examples in this article). The first two bytes of a TCP packet are the source port. If its offset is zero and the length is 2 bytes, the filters are: tcp[0:2] for the source and tcp[2:2] for the destination port. You can view traffic with the same source and destination using the following filter: 'tcp[0:2] == tcp[2:2]' For example, to view traffic destination on TCP port 80, you can use the following filter: 'tcp[2:2] == 80' Filtering for packets using specific IP addresses You can configure filters for IP header properties using the same logic as the port source and destination filter. You can view all traffic with the same source and destination IP by using the following filter: 'ip[12:4] == ip[16:4]' Note: You can combine the TCP port filter and the IP address filter to detect the LAND attack. The flags section of an IP header is only 3 bits long, and 1 bit is reserved; therefore, the only 2 bits that you can toggle in this octet are: the 1 bytes These correspond to the following two IP flags: DF (don't fragment) bit set (IP)
5 Example filter: 'ip[6] & 64!= 64' MF (more fragments) bit set (IP) Example filter: 'ip[6] & 32!= 32' Filtering for packets using ICMP header properties The first byte in an ICMP packet is the message type; the second byte is the code. You can refer to net/rfc792.txt for the numbers you need to use in the following filter, changing the two sets of numbers to the appropriate type and code as provided in RFC792. Following are type 3 Destination unreachable ICMP messages codes: Code Message 0 network unreachable 1 host unreachable 2 protocol unreachable 3 port unreachable 4 fragmentation needed but don't fragment bit set Following are type 11 Time exceeded ICMP messages codes: Code Message 0 TTL exceeded in transit (too many hops? routing loop?) 1 fragment reassembly time exceeded (frag attack? bad streaming media performance?) The IP header byte 9 is the protocol field, and the ICMP protocol is represented by a value of 1. For example: tcpdump -ni internal 'ip[9] == 1' The output would appear similar to the following example: tcpdump: listening on internal 00:06: > : icmp: echo request 00:06: > : icmp: echo reply 00:06: > : icmp: echo request
6 00:06: > : icmp: echo reply ^C Following are additional examples of filters for packets using ICMP header properties: Criteria Filter View only the ICMP Echo Requests 'icmp[0] == 8' View only the ICMP Echo Replies 'icmp[0] == 0' View all ICMP packets except ICMP Echo Requests and Replies View only the ICMP "Fragmentation needed but DF bit set" (Type 3, code 4) packets Non-header filters Following are examples of non-header filters. Match against all traffic involving a particular network: net Match against a more specific network: net mask Match against a more specific network, using CIDR notation: net /29 Match against all traffic from a specific network: src net 192 Packet length Following are examples of packet length filters: Match packets 1400 bytes long: len == 1400 Match packets greater than or equal to 1400 bytes: 'len >= 1400' 802.1q VLAN tagging Following are examples of VLAN tagging filters: Match packets with a VLAN tag of 10: vlan 10 'icmp[0]!= 8 and icmp [0]!= 0' 'icmp[0] == 3 and icmp [1] == 4'
7 To get the same result, without using the built-in keyword (such as on non-f5 modified versions of tcpdump ), use the following filter: 'ether[14:2] & 4095 == 10' This works because the Ethernet header appears as follows (per-bit): SSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD Each character in the Ethernet header is defined as follows: Character Definition Size S src 6 bytes D dst 6 bytes T type 2 bytes P priority 3 bits C canonical 1 bit Q 802.1Q vlan tag 12 bits Therefore, to ensure that you are not including the priority or canonical bits as part of the VLAN tag, perform a logic AND of 4095 against the contents of bytes 14 and 15 as follows: & = General trace principles Tracing a single session bi-directionally When tracing a single session, generally the ephemeral port is enough (the dynamic port used by the client). For example, the following stream shows two unique TCP sessions using the ephemeral ports 1039, and 1034: > : P 1:99(98) ack 1 win > : P 1:147(146) ack 99 win > :. ack 3085 win > :. 4109:4621(512) ack 529 win > :. 4621:5133(512) ack 529 win > :. ack 4109 win > :. 5133:5645(512) ack 529 win You could use this ephemeral port to isolate a single session, for example port 1039, to view only the following: > : P 1:99(98) ack 1 win > : P 1:147(146) ack 99 win 16616
8 If the ephemeral port is not specific enough to use as a unique identifier (which can be the case in very large tcpdumps), you could filter using more criteria. For example, port 1039 and host and port 443 and host Tracing a single session uni-directionally It may make more sense to filter traffic in only one direction. For example, using src port 443 to view only the following: > : P 1:147(146) ack 99 win > :. 4109:4621(512) ack 529 win > :. 4621:5133(512) ack 529 win > :. 5133:5645(512) ack 529 win Generally, however, it is more useful to filter what a client sends (uni-directionally, but in the opposite direction than the first example). For example, using src port 1039 to view the following: > : P 1:99(98) ack 1 win 8576 Or to gather everything a client sends on any port, using src host to view the following: > : P 1:99(98) ack 1 win > :. ack 3085 win > :. ack 4109 win 8576 Or lastly, to gather a single session from a client and server using the same ports for two different connections. For example: > 4354 is one connection > 4343 is another connection It is not generally done, but if you recognize those ports (the iquery protocol) you can understand the need to filter in this way. To create a filter that tracks connections where both the source and destination are the same port, you would modify a specific filter and add more detail. For example: '( src port 1039 and src host and dst host and dst port 443 )' Or: '( dst port 1039 and dst host and src host and src po
9 The output would appear similar to the following example: > : P 1:99(98) ack 1 win 8576 Note: It would not make sense to filter a TCP stream this short. If the whole packet dump is only a few hundred lines you can use grep to efficiently view it without writing complex filters. However, if you are dealing with a large tcpdump (such as 200 megabytes), filters are the only way to make it manageable. Additional Ethernet header details The Ethernet header is very short (14 bytes), with only 3 fields ( src, dst, and type). The source ( src) and destination ( dst) are the hardware (MAC) addresses for the sending and receiving units (respectively). The type field indicates the next layer protocol that is being transported. For example: Protocol Decimal HEX IP x0800 ARP x0806 VLAN x8100 Slow Protocols (for example, LACP) x8809 Note: In the case of VLANs, there are 2 additional bytes after the type field, indicating the VLAN tag. You can filter traffic based on the type field by using the filter ether proto <protocol>. Protocol can be either the decimal or hexadecimal value, as noted in the previous table. Tracing Ethernet header type LACP LACP is handled by the switch fabric, therefore packets must be captured directly on the physical interface, for example, 1.1, as opposed to the VLAN or 0.0. To capture only LACP packets, use the following syntax: tcpdump -ni <interface> -e ether proto 0x8809 Note: The -e switch prints the link-level header on each line. For example, to capture LACP packets on interface 1.1 of a Link Aggregation Group (LAG), type the following command: tcpdump -ni 1.1 -e ether proto 0x8809 The output would look similar to the following example: 15:21: :50:56:92:2a:82 > 01:80:c2:00:00:02, ethertype 802.1Q (0x8100), length 128: vlan 0, p 0, ethertype Slow Protocols, LACPv1, length: 110
10 Note: LACP sends one packet per second during its initial detection period, to a multicast MAC of 01:80:c2: 00:00:02. After the connection is either established or marked down (LACP marks the link down after three consecutive control packets with no response from the peer), LACP packets are sent either every thirty seconds, if configured for a LONG timeout, or every one second, if configured for a SHORT timeout. If the LAG is configured for a LONG timeout in ACTIVE mode, then you may only see one packet every thirty seconds. Because of this, F5 recommends that you allow the capture to run for at least one full minute. References This section contains specific examples as well as suggested reading. Miscellaneous filter examples Match all arps using either of the following two methods: arp ether[12:2] == 2054 Match all IP packets using either of the following two methods: ip ether[12:2] == 2048 Match against a specific hardware (MAC) address: ether host 0:2:b3:7:10:73 Match against src: ether src host 0:2:b3:7:10:73 Gather all traffic passing through a specific gateway (firewall, router), where 0:2:b3:7:10:73 is the gateway's MAC address and is the gateway's IP address, excluding traffic to and from the gateway itself:: ether host 0:2:b3:7:10:73 and not host Note: If you need to perform this type of task frequently, you can make the appropriate entries in the /etc /ethers and /etc/hosts files and specify your gateways by name. ASCII header diagrams Following are additional header diagrams examples. IP header (RFC791) Version IHL Type of Service Total Length
11 Identification Flags Fragment Offset Time to Live Protocol Header Checksum Source Address Destination Address Options Padding TCP header (STD7) Source Port Destination Port Sequence Number Acknowledgment Number Data U A P R S F Offset Reserved R C S S Y I Window G K H T N N Checksum Urgent Pointer Options Padding data UDP header (STD6) Source Destination Port Port Length Checksum data octets ICMP header (RFC792) ICMP ECHO / ECHO REPLY Type Code Checksum
12 Identifier Sequence Number Data Ethernet header (basically IEEE 802.3) Preamble (8) Preamble cont. Destination address (6) Destination address cont. Source address (6) Source address cont. Type (2) Pri C 802.1q tag if type!=0x8100, prev. 2 bytes are part of this field ( bytes of data)... Frame Check Sequence, FCS (4) Note: Although the previous diagram correctly shows both Preamble and Frame Check Sequence, tcpdump does not include these in the totals for header bytes (presumably because the data is fixed, so there is no reason to match against it.) As a result, if you are basing ether expressions on this chart, you must subtract 12 (as if the Preamble and FCS sections do not exist.) DNS header (RFC1035) MESSAGE FORMAT Header Question the question for the name server Answer RRs answering the question Authority RRs pointing toward an authority Additional RRs holding additional information HEADER ID QR Opcode AA TC RD RA Z RCODE
13 QDCOUNT ANCOUNT NSCOUNT ARCOUNT QUESTION / QNAME / / / QTYPE QCLASS RESOURCE RECORDS: ANSWER/ADDITIONAL/AUTHORITY / / / NAME / TYPE CLASS TTL RDLENGTH / RDATA / / / MESSAGE COMPRESSION OFFSET OFFSET refers to the byte before a preceding occurrence of a domain name. LDAP LDAP message Always 0x30 Length Always 0x02 Len of msgid msgid... Protocol Op. Operation ICMP codes
14 Type Code Definition 0 0 ECHO REPLY (ping reply) 3 DESTINATION UNREACHABLE 0 network unreachable 1 host unreachable 2 protocol unreachable 3 port unreachable 4 frag needed 5 source route failed 6 destination network unknown 7 destination host unknown 8 source host isolated 9 destination network administratively prohibited 10 destination host administratively prohibited 11 network unreachable for TOS 12 host unreachable for TOS 13 prohibited by filtering 14 host precedence violation 15 precedence cutoff 4 0 SOURCE QUENCH 5 REDIRECT 0 network 1 host 2 network & TOS 3 host & TOS 8 0 ECHO REQUEST (ping request) 9 0 ROUTER ADVERTISEMENT 10 0 ROUTER SOLICITATION 11 TIME EXCEEDED 0 TTL=0 during transmit 1 TTL=0 during reassembly 12 PARAMETER PROBLEM 13 0 TIMESTAMP REQUEST 14 0 TIMESTAMP REPLY 15 0 INFO REQUEST 16 0 INFO REPLY 17 0 ADDRESS MASK REQUEST 18 0 ADDRESS MASK REPLY
15 Supplemental Information SANS Institute TCP/IP and tcpdump primer Note: This link takes you to a resource outside of AskF5. The third party could remove the document without our knowledge. K411: Overview of packet tracing with the tcpdump utility K4714: Performing a packet trace and providing the results to F5 Technical Support K6546: Recommended methods and limitations for running tcpdump on a BIG-IP system K1893: Packet trace analysis K13637: Capturing internal TMM information with tcpdump K7227: Considerations when using the tcpdump utility with tagged VLAN traffic K13328: Troubleshooting LDAP authentication with tcpdump K13301: Overview of packet tracing a BIG-IP APM Network Access tunnel with the tcpdump utility K7823: Troubleshooting and debugging Enterprise Manager icontrol connectivity K5564: Saving large tcpdump packet traces when disk space is limited
Packet Header Formats
 A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
Chapter 6 Global CONFIG Commands
 Chapter 6 Global CONFIG Commands aaa accounting Configures RADIUS or TACACS+ accounting for recording information about user activity and system events. When you configure accounting on an HP device, information
Chapter 6 Global CONFIG Commands aaa accounting Configures RADIUS or TACACS+ accounting for recording information about user activity and system events. When you configure accounting on an HP device, information
Transport: How Applications Communicate
 Transport: How Applications Communicate Week 2 Philip Levis 1 7 Layers (or 4) 7. 6. 5. 4. 3. 2. 1. Application Presentation Session Transport Network Link Physical segments packets frames bits/bytes Application
Transport: How Applications Communicate Week 2 Philip Levis 1 7 Layers (or 4) 7. 6. 5. 4. 3. 2. 1. Application Presentation Session Transport Network Link Physical segments packets frames bits/bytes Application
CHAPTER-2 IP CONCEPTS
 CHAPTER-2 IP CONCEPTS Page: 1 IP Concepts IP is a very important protocol in modern internetworking; you can't really comprehend modern networking without a good understanding of IP. Unfortunately, IP
CHAPTER-2 IP CONCEPTS Page: 1 IP Concepts IP is a very important protocol in modern internetworking; you can't really comprehend modern networking without a good understanding of IP. Unfortunately, IP
ECE4110 Internetwork Programming. Introduction and Overview
 ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
! ' ,-. +) +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+, ) 05,-. /,*+), 01/-*+) + 01/.*+)
 ! "#! # $ %& #! '!!!( &!)'*+' '(,-. +) /,*+), 01/-*+) + 01/.*+) ) 05,-. +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+,3 4 +. 6*! ) ) ) ) 5 ) ) ) ) + 5 + + ) ) ) 5 9 + ) ) + 5 4 ) ) + ) 5, ) )
! "#! # $ %& #! '!!!( &!)'*+' '(,-. +) /,*+), 01/-*+) + 01/.*+) ) 05,-. +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+,3 4 +. 6*! ) ) ) ) 5 ) ) ) ) + 5 + + ) ) ) 5 9 + ) ) + 5 4 ) ) + ) 5, ) )
Configuring Routes on the ACE
 CHAPTER2 This chapter describes how the ACE is considered a router hop in the network when it is in routed mode. In the Admin or user contexts, the ACE supports static routes only. The ACE supports up
CHAPTER2 This chapter describes how the ACE is considered a router hop in the network when it is in routed mode. In the Admin or user contexts, the ACE supports static routes only. The ACE supports up
Dongsoo S. Kim Electrical and Computer Engineering Indiana U. Purdue U. Indianapolis
 Session 8. TCP/IP Dongsoo S. Kim (dskim@iupui.edu) Electrical and Computer Engineering Indiana U. Purdue U. Indianapolis IP Packet 0 4 8 16 19 31 Version IHL Type of Service Total Length Identification
Session 8. TCP/IP Dongsoo S. Kim (dskim@iupui.edu) Electrical and Computer Engineering Indiana U. Purdue U. Indianapolis IP Packet 0 4 8 16 19 31 Version IHL Type of Service Total Length Identification
IPv4. Christian Grothoff.
 IPv4 christian@grothoff.org http://grothoff.org/christian/ Sites need to be able to interact in one single, universal space. Tim Berners-Lee 1 The Network Layer Transports datagrams from sending to receiving
IPv4 christian@grothoff.org http://grothoff.org/christian/ Sites need to be able to interact in one single, universal space. Tim Berners-Lee 1 The Network Layer Transports datagrams from sending to receiving
TCP /IP Fundamentals Mr. Cantu
 TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
CS 356: Computer Network Architectures. Lecture 10: IP Fragmentation, ARP, and ICMP. Xiaowei Yang
 CS 356: Computer Network Architectures Lecture 10: IP Fragmentation, ARP, and ICMP Xiaowei Yang xwy@cs.duke.edu Overview Homework 2-dimension parity IP fragmentation ARP ICMP Fragmentation and Reassembly
CS 356: Computer Network Architectures Lecture 10: IP Fragmentation, ARP, and ICMP Xiaowei Yang xwy@cs.duke.edu Overview Homework 2-dimension parity IP fragmentation ARP ICMP Fragmentation and Reassembly
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
Vorlesung Kommunikationsnetze
 Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Introduction to routing in the Internet
 Introduction to routing in the Internet Internet architecture IPv4, ICMP, ARP Addressing, routing principles (Chapters 2 3 in Huitema) Internet-1 Internet Architecture Principles End-to-end principle by
Introduction to routing in the Internet Internet architecture IPv4, ICMP, ARP Addressing, routing principles (Chapters 2 3 in Huitema) Internet-1 Internet Architecture Principles End-to-end principle by
CNT5505 Programming Assignment No. 4: Internet Packet Analyzer (This is an individual assignment. It must be implemented in C++ or C)
 . CNT5505 Programming Assignment No. 4: Internet Packet Analyzer (This is an individual assignment. It must be implemented in C++ or C) PURPOSE Experience with packet analyzing and Internet packet formats.
. CNT5505 Programming Assignment No. 4: Internet Packet Analyzer (This is an individual assignment. It must be implemented in C++ or C) PURPOSE Experience with packet analyzing and Internet packet formats.
Command Manual Network Protocol. Table of Contents
 Table of Contents Table of Contents Chapter 1 IP Address Configuration Commands... 1-1 1.1 IP Address Configuration Commands... 1-1 1.1.1 display ip host... 1-1 1.1.2 display ip interface... 1-1 1.1.3
Table of Contents Table of Contents Chapter 1 IP Address Configuration Commands... 1-1 1.1 IP Address Configuration Commands... 1-1 1.1.1 display ip host... 1-1 1.1.2 display ip interface... 1-1 1.1.3
Introduction to routing in the Internet
 Introduction to routing in the Internet Internet architecture IPv4, ICMP, ARP Addressing, routing principles (Chapters 2 3 in Huitema) Internet-1 Internet Architecture Principles End-to-end principle by
Introduction to routing in the Internet Internet architecture IPv4, ICMP, ARP Addressing, routing principles (Chapters 2 3 in Huitema) Internet-1 Internet Architecture Principles End-to-end principle by
Table of Contents 1 IP Address Configuration Commands IP Performance Configuration Commands 2-1
 Table of Contents 1 IP Address Configuration Commands 1-1 IP Address Configuration Commands 1-1 display ip interface 1-1 display ip interface brief 1-2 ip address 1-4 2 IP Performance Configuration Commands
Table of Contents 1 IP Address Configuration Commands 1-1 IP Address Configuration Commands 1-1 display ip interface 1-1 display ip interface brief 1-2 ip address 1-4 2 IP Performance Configuration Commands
Table of Contents 1 IP Address Configuration Commands IP Performance Configuration Commands 2-1
 Table of Contents 1 IP Address Configuration Commands 1-1 IP Address Configuration Commands 1-1 display ip interface 1-1 display ip interface brief 1-2 ip address 1-3 2 IP Performance Configuration Commands
Table of Contents 1 IP Address Configuration Commands 1-1 IP Address Configuration Commands 1-1 display ip interface 1-1 display ip interface brief 1-2 ip address 1-3 2 IP Performance Configuration Commands
Command Manual (For Soliton) IP Address-IP Performance. Table of Contents
 Table of Contents Table of Contents Chapter 1 IP Address Configuration... 1-1 1.1 IP Address Configuration... 1-1 1.1.1 display ip interface... 1-1 1.1.2 display ip interface brief... 1-3 1.1.3 ip address...
Table of Contents Table of Contents Chapter 1 IP Address Configuration... 1-1 1.1 IP Address Configuration... 1-1 1.1.1 display ip interface... 1-1 1.1.2 display ip interface brief... 1-3 1.1.3 ip address...
EE 610 Part 2: Encapsulation and network utilities
 EE 610 Part 2: Encapsulation and network utilities Objective: After this experiment, the students should be able to: i. Understand the format of standard frames and packet headers. Overview: The Open Systems
EE 610 Part 2: Encapsulation and network utilities Objective: After this experiment, the students should be able to: i. Understand the format of standard frames and packet headers. Overview: The Open Systems
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Extended ACL Configuration Mode Commands
 Extended ACL Configuration Mode Commands To create and modify extended access lists on a WAAS device for controlling access to interfaces or applications, use the ip access-list extended global configuration
Extended ACL Configuration Mode Commands To create and modify extended access lists on a WAAS device for controlling access to interfaces or applications, use the ip access-list extended global configuration
Protocol Layers & Wireshark TDTS11:COMPUTER NETWORKS AND INTERNET PROTOCOLS
 Protocol Layers & Wireshark TDTS11:COMPUTER NETWORKS AND INTERNET PROTOCOLS Mail seban649@student.liu.se Protocol Hi Hi Got the time? 2:00 time TCP connection request TCP connection response Whats
Protocol Layers & Wireshark TDTS11:COMPUTER NETWORKS AND INTERNET PROTOCOLS Mail seban649@student.liu.se Protocol Hi Hi Got the time? 2:00 time TCP connection request TCP connection response Whats
University of Toronto Faculty of Applied Science and Engineering. Final Exam, December ECE 461: Internetworking Examiner: J.
 University of Toronto Faculty of Applied Science and Engineering Final Exam, December 2009 ECE 461: Internetworking Examiner: J. Liebeherr Exam Type: A Calculator: Type 2 There are a total of 10 problems.
University of Toronto Faculty of Applied Science and Engineering Final Exam, December 2009 ECE 461: Internetworking Examiner: J. Liebeherr Exam Type: A Calculator: Type 2 There are a total of 10 problems.
(ICMP), RFC
 Internet et Control o Message Protocol (ICMP), RFC 792 http://icourse.cuc.edu.cn/networkprogramming/ linwei@cuc.edu.cn Nov. 2009 Overview The IP (Internet Protocol) relies on several other protocols to
Internet et Control o Message Protocol (ICMP), RFC 792 http://icourse.cuc.edu.cn/networkprogramming/ linwei@cuc.edu.cn Nov. 2009 Overview The IP (Internet Protocol) relies on several other protocols to
Operational Security Capabilities for IP Network Infrastructure
 Operational Security Capabilities F. Gont for IP Network Infrastructure G. Gont (opsec) UTN/FRH Internet-Draft September 1, 2008 Intended status: Informational Expires: March 5, 2009 Status of this Memo
Operational Security Capabilities F. Gont for IP Network Infrastructure G. Gont (opsec) UTN/FRH Internet-Draft September 1, 2008 Intended status: Informational Expires: March 5, 2009 Status of this Memo
Interconnecting Networks with TCP/IP
 Chapter 8 Interconnecting s with TCP/IP 1999, Cisco Systems, Inc. 8-1 Introduction to TCP/IP Internet TCP/IP Early protocol suite Universal 1999, Cisco Systems, Inc. www.cisco.com ICND 8-2 TCP/IP Protocol
Chapter 8 Interconnecting s with TCP/IP 1999, Cisco Systems, Inc. 8-1 Introduction to TCP/IP Internet TCP/IP Early protocol suite Universal 1999, Cisco Systems, Inc. www.cisco.com ICND 8-2 TCP/IP Protocol
Network Layer (4): ICMP
 1 Network Layer (4): ICMP Required reading: Kurose 4.4.3, 4.4.4 CSE 4213, Fall 2006 Instructor: N. Vlajic 2 1. Introduction 2. Network Service Models 3. Architecture 4. Network Layer Protocols in the Internet
1 Network Layer (4): ICMP Required reading: Kurose 4.4.3, 4.4.4 CSE 4213, Fall 2006 Instructor: N. Vlajic 2 1. Introduction 2. Network Service Models 3. Architecture 4. Network Layer Protocols in the Internet
IP Services Volume Organization
 IP Services Volume Organization Manual Version 6W100-20090626 Product Version Release 1102 Organization The IP Services Volume is organized as follows: Features IP Address IP Performance Optimization ARP
IP Services Volume Organization Manual Version 6W100-20090626 Product Version Release 1102 Organization The IP Services Volume is organized as follows: Features IP Address IP Performance Optimization ARP
CPSC 826 Internetworking. The Network Layer: Routing & Addressing Outline. The Network Layer
 1 CPSC 826 Intering The Network Layer: Routing & Addressing Outline The Network Layer Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu November 10, 2004 Network layer
1 CPSC 826 Intering The Network Layer: Routing & Addressing Outline The Network Layer Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu November 10, 2004 Network layer
Internet Control Message Protocol (ICMP), RFC 792. Prof. Lin Weiguo Copyleft 2009~2017, School of Computing, CUC
 Internet Control Message Protocol (ICMP), RFC 79 Prof Lin Weiguo Copyleft 009~07, School of Computing, CUC Oct 07 Overview } The IP (Internet Protocol) relies on several other protocols to perform necessary
Internet Control Message Protocol (ICMP), RFC 79 Prof Lin Weiguo Copyleft 009~07, School of Computing, CUC Oct 07 Overview } The IP (Internet Protocol) relies on several other protocols to perform necessary
IP : Internet Protocol
 1/20 IP : Internet Protocol Surasak Sanguanpong nguan@ku.ac.th http://www.cpe.ku.ac.th/~nguan Last updated: July 30, 1999 Agenda 2/20 IP functions IP header format Routing architecture IP layer 3/20 defines
1/20 IP : Internet Protocol Surasak Sanguanpong nguan@ku.ac.th http://www.cpe.ku.ac.th/~nguan Last updated: July 30, 1999 Agenda 2/20 IP functions IP header format Routing architecture IP layer 3/20 defines
Internet Control Message Protocol (ICMP)
 Internet Control Message Protocol (ICMP) 1 Overview The IP (Internet Protocol) relies on several other protocols to perform necessary control and routing functions: Control functions (ICMP) Multicast signaling
Internet Control Message Protocol (ICMP) 1 Overview The IP (Internet Protocol) relies on several other protocols to perform necessary control and routing functions: Control functions (ICMP) Multicast signaling
IP - The Internet Protocol. Based on the slides of Dr. Jorg Liebeherr, University of Virginia
 IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
Transport Over IP. CSCI 690 Michael Hutt New York Institute of Technology
 Transport Over IP CSCI 690 Michael Hutt New York Institute of Technology Transport Over IP What is a transport protocol? Choosing to use a transport protocol Ports and Addresses Datagrams UDP What is a
Transport Over IP CSCI 690 Michael Hutt New York Institute of Technology Transport Over IP What is a transport protocol? Choosing to use a transport protocol Ports and Addresses Datagrams UDP What is a
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Detecting and Analyzing Network Threats With NetFlow
 Detecting and Analyzing Network Threats With NetFlow This document contains information about and instructions for detecting and analyzing network threats such as denial of service attacks (DoS) through
Detecting and Analyzing Network Threats With NetFlow This document contains information about and instructions for detecting and analyzing network threats such as denial of service attacks (DoS) through
IPv6. IPv4 & IPv6 Header Comparison. Types of IPv6 Addresses. IPv6 Address Scope. IPv6 Header. IPv4 Header. Link-Local
 1 v4 & v6 Header Comparison v6 Ver Time to Live v4 Header IHL Type of Service Identification Protocol Flags Source Address Destination Address Total Length Fragment Offset Header Checksum Ver Traffic Class
1 v4 & v6 Header Comparison v6 Ver Time to Live v4 Header IHL Type of Service Identification Protocol Flags Source Address Destination Address Total Length Fragment Offset Header Checksum Ver Traffic Class
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Computer Networks A Simple Network Analyzer PART A undergraduates and graduates PART B graduate students only
 Computer Networks A Simple Network Analyzer PART A undergraduates and graduates PART B graduate students only Objectives The main objective of this assignment is to gain an understanding of network activities
Computer Networks A Simple Network Analyzer PART A undergraduates and graduates PART B graduate students only Objectives The main objective of this assignment is to gain an understanding of network activities
ICS 451: Today's plan
 ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
Detecting and Analyzing Network Threats With NetFlow
 Detecting and Analyzing Network Threats With NetFlow First Published: June 19, 2006 Last Updated: October 02, 2009 This document contains information about and instructions for detecting and analyzing
Detecting and Analyzing Network Threats With NetFlow First Published: June 19, 2006 Last Updated: October 02, 2009 This document contains information about and instructions for detecting and analyzing
IPv6 Protocols and Networks Hadassah College Spring 2018 Wireless Dr. Martin Land
 IPv6 1 IPv4 & IPv6 Header Comparison IPv4 Header IPv6 Header Ver IHL Type of Service Total Length Ver Traffic Class Flow Label Identification Flags Fragment Offset Payload Length Next Header Hop Limit
IPv6 1 IPv4 & IPv6 Header Comparison IPv4 Header IPv6 Header Ver IHL Type of Service Total Length Ver Traffic Class Flow Label Identification Flags Fragment Offset Payload Length Next Header Hop Limit
The Internet Protocol. IP Addresses Address Resolution Protocol: IP datagram format and forwarding: IP fragmentation and reassembly
 The Internet Protocol IP Addresses Address Resolution Protocol: IP datagram format and forwarding: IP fragmentation and reassembly IP Addresses IP Addresses are 32 bit. Written in dotted decimal format:
The Internet Protocol IP Addresses Address Resolution Protocol: IP datagram format and forwarding: IP fragmentation and reassembly IP Addresses IP Addresses are 32 bit. Written in dotted decimal format:
Lecture 18 Overview. Last Lecture. This Lecture. Next Lecture. Internet Protocol (1) Internet Protocol (2)
 Last Lecture Internet Protocol (1) This Lecture Internet Protocol (2) Lecture 18 Overview Source: chapters 19.1, 19.2, 22,1 22.2, 26.6 Next Lecture Transport Control Protocol (1) Source: chapters 24.1,
Last Lecture Internet Protocol (1) This Lecture Internet Protocol (2) Lecture 18 Overview Source: chapters 19.1, 19.2, 22,1 22.2, 26.6 Next Lecture Transport Control Protocol (1) Source: chapters 24.1,
TCP/IP Protocol Suite
 TCP/IP Protocol Suite Computer Networks Lecture 5 http://goo.gl/pze5o8 TCP/IP Network protocols used in the Internet also used in today's intranets TCP layer 4 protocol Together with UDP IP - layer 3 protocol
TCP/IP Protocol Suite Computer Networks Lecture 5 http://goo.gl/pze5o8 TCP/IP Network protocols used in the Internet also used in today's intranets TCP layer 4 protocol Together with UDP IP - layer 3 protocol
TSIN02 - Internetworking
 Lecture 2: The Internet Protocol Literature: Forouzan: ch 4-9 and ch 27 2004 Image Coding Group, Linköpings Universitet Outline About the network layer Tasks Addressing Routing Protocols 2 Tasks of the
Lecture 2: The Internet Protocol Literature: Forouzan: ch 4-9 and ch 27 2004 Image Coding Group, Linköpings Universitet Outline About the network layer Tasks Addressing Routing Protocols 2 Tasks of the
Network Layer: Internet Protocol
 Network Layer: Internet Protocol Motivation Heterogeneity Scale Intering IP is the glue that connects heterogeneous s giving the illusion of a homogenous one. Salient Features Each host is identified by
Network Layer: Internet Protocol Motivation Heterogeneity Scale Intering IP is the glue that connects heterogeneous s giving the illusion of a homogenous one. Salient Features Each host is identified by
Network layer: Overview. Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing
 Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Introduction to TCP/IP networking
 Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
TSIN02 - Internetworking
 Lecture 2: Internet Protocol Literature: Forouzan: ch (4-6), 7-9 and ch 31 2004 Image Coding Group, Linköpings Universitet Lecture 2: IP Goals: Understand the benefits Understand the architecture IPv4
Lecture 2: Internet Protocol Literature: Forouzan: ch (4-6), 7-9 and ch 31 2004 Image Coding Group, Linköpings Universitet Lecture 2: IP Goals: Understand the benefits Understand the architecture IPv4
Network layer: Overview. Network Layer Functions
 Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Hands-On Ethical Hacking and Network Defense
 Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
WE POWER YOUR MOBILE WORLD ENUM INTEGRATION MANUAL
 ENUM INTEGRATION MANUAL 1 CONTENTS INTRODUCTION... 3 CONNECTIVITY... 3 TECHNICAL SPECIFICATION... 4 Valid format for ENUM server query... 4 ENUM server responses... 6 ENUM responses in case of error processing
ENUM INTEGRATION MANUAL 1 CONTENTS INTRODUCTION... 3 CONNECTIVITY... 3 TECHNICAL SPECIFICATION... 4 Valid format for ENUM server query... 4 ENUM server responses... 6 ENUM responses in case of error processing
SEN366 (SEN374) (Introduction to) Computer Networks
 SEN366 (SEN374) (Introduction to) Computer Networks Prof. Dr. Hasan Hüseyin BALIK (12 th Week) The Internet Protocol 12.Outline Principles of Internetworking Internet Protocol Operation Internet Protocol
SEN366 (SEN374) (Introduction to) Computer Networks Prof. Dr. Hasan Hüseyin BALIK (12 th Week) The Internet Protocol 12.Outline Principles of Internetworking Internet Protocol Operation Internet Protocol
Chapter 2 Advanced TCP/IP
 Tactical Perimeter Defense 2-1 Chapter 2 Advanced TCP/IP At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional Projects Additional
Tactical Perimeter Defense 2-1 Chapter 2 Advanced TCP/IP At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional Projects Additional
IP Protocols. ALTTC/Oct
 IP Protocols Internet or IP technology over the years has emerged as the most prominent data communication technology. TCP/IP protocol has become de-facto data comm standard throughout the world. It can
IP Protocols Internet or IP technology over the years has emerged as the most prominent data communication technology. TCP/IP protocol has become de-facto data comm standard throughout the world. It can
Configuring IPv6 for Gigabit Ethernet Interfaces
 CHAPTER 46 IP version 6 (IPv6) provides extended addressing capability beyond those provided in IP version 4 (IPv4) in Cisco MDS SAN-OS. The architecture of IPv6 has been designed to allow existing IPv4
CHAPTER 46 IP version 6 (IPv6) provides extended addressing capability beyond those provided in IP version 4 (IPv4) in Cisco MDS SAN-OS. The architecture of IPv6 has been designed to allow existing IPv4
To make a difference between logical address (IP address), which is used at the network layer, and physical address (MAC address),which is used at
 To make a difference between logical address (IP address), which is used at the network layer, and physical address (MAC address),which is used at the data link layer. To describe how the mapping of a
To make a difference between logical address (IP address), which is used at the network layer, and physical address (MAC address),which is used at the data link layer. To describe how the mapping of a
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Single Network: applications, client and server hosts, switches, access links, trunk links, frames, path. Review of TCP/IP Internetworking
 1 Review of TCP/IP working Single Network: applications, client and server hosts, switches, access links, trunk links, frames, path Frame Path Chapter 3 Client Host Trunk Link Server Host Panko, Corporate
1 Review of TCP/IP working Single Network: applications, client and server hosts, switches, access links, trunk links, frames, path Frame Path Chapter 3 Client Host Trunk Link Server Host Panko, Corporate
Network Layer. The Network Layer. Contents Connection-Oriented and Connectionless Service. Recall:
 Network Layer The Network Layer Recall: The network layer is responsible for the routing of packets The network layer is responsible for congestion control 1 2 Contents 4.1.1 Connection-Oriented and Connectionless
Network Layer The Network Layer Recall: The network layer is responsible for the routing of packets The network layer is responsible for congestion control 1 2 Contents 4.1.1 Connection-Oriented and Connectionless
Network Layer. Recall: The network layer is responsible for the routing of packets The network layer is responsible for congestion control
 The Network Layer 1 Network Layer Recall: The network layer is responsible for the routing of packets The network layer is responsible for congestion control 2 Contents Connection-Oriented (virtual circuit)
The Network Layer 1 Network Layer Recall: The network layer is responsible for the routing of packets The network layer is responsible for congestion control 2 Contents Connection-Oriented (virtual circuit)
Contents. IP addressing configuration commands 1 display ip interface 1 display ip interface brief 3 ip address 5
 Contents IP addressing configuration commands 1 display ip interface 1 display ip interface brief 3 ip address 5 i IP addressing configuration commands display ip interface Syntax View Default level Parameters
Contents IP addressing configuration commands 1 display ip interface 1 display ip interface brief 3 ip address 5 i IP addressing configuration commands display ip interface Syntax View Default level Parameters
ICMP (Internet Control Message Protocol)
 Today s Lecture ICMP (Internet Control Message Protocol) Internet Protocols CSC / C 573 I. ICMP Overview II. ICMP rror Reporting III. ICMP Query / Response Messages IV. ICMP Message Processing Fall, 2005
Today s Lecture ICMP (Internet Control Message Protocol) Internet Protocols CSC / C 573 I. ICMP Overview II. ICMP rror Reporting III. ICMP Query / Response Messages IV. ICMP Message Processing Fall, 2005
The Internetworking Problem. Internetworking. A Translation-based Solution
 Cloud Cloud Cloud 1 The Internetworking Problem Internetworking Two nodes communicating across a network of networks How to transport packets through this heterogeneous mass? A B The Internetworking Problem
Cloud Cloud Cloud 1 The Internetworking Problem Internetworking Two nodes communicating across a network of networks How to transport packets through this heterogeneous mass? A B The Internetworking Problem
TCP/IP and the OSI Model
 TCP/IP BASICS TCP/IP and the OSI Model TCP/IP BASICS The network protocol of the Internet Composed of six main protocols IP Internet Protocol UDP User Datagram Protocol TCP Transmission Control Protocol
TCP/IP BASICS TCP/IP and the OSI Model TCP/IP BASICS The network protocol of the Internet Composed of six main protocols IP Internet Protocol UDP User Datagram Protocol TCP Transmission Control Protocol
ECE 461 Internetworking Fall Quiz 1
 ECE 461 Internetworking Fall 2013 Quiz 1 Instructions (read carefully): The time for this quiz is 50 minutes. This is a closed book and closed notes in-class exam. Non-programmable (Type 2) calculators
ECE 461 Internetworking Fall 2013 Quiz 1 Instructions (read carefully): The time for this quiz is 50 minutes. This is a closed book and closed notes in-class exam. Non-programmable (Type 2) calculators
Module : ServerIron ADX Packet Capture
 Module : ServerIron ADX Packet Capture Objectives Upon completion of this module, you will be able to: Describe Brocade ServerIron ADX (ADX) Packet Capture feature Configure and verify the Packet Capture
Module : ServerIron ADX Packet Capture Objectives Upon completion of this module, you will be able to: Describe Brocade ServerIron ADX (ADX) Packet Capture feature Configure and verify the Packet Capture
RMIT University. Data Communication and Net-Centric Computing COSC 1111/2061. Lecture 2. Internetworking IPv4, IPv6
 RMIT University Data Communication and Net-Centric Computing COSC 1111/2061 Internetworking IPv4, IPv6 Technology Slide 1 Lecture Overview During this lecture, we will understand The principles of Internetworking
RMIT University Data Communication and Net-Centric Computing COSC 1111/2061 Internetworking IPv4, IPv6 Technology Slide 1 Lecture Overview During this lecture, we will understand The principles of Internetworking
Internet Protocol. Outline Introduction to Internet Protocol Header and address formats ICMP Tools CS 640 1
 Internet Protocol Outline Introduction to Internet Protocol Header and address formats ICMP Tools CS 640 1 Internet Protocol Runs on all hosts in the Internet and enables packets to be routed between systems
Internet Protocol Outline Introduction to Internet Protocol Header and address formats ICMP Tools CS 640 1 Internet Protocol Runs on all hosts in the Internet and enables packets to be routed between systems
Internet Layers. Physical Layer. Application. Application. Transport. Transport. Network. Network. Network. Network. Link. Link. Link.
 Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Computer Networks A Simple Network Analyzer Decoding Ethernet and IP headers
 Computer Networks A Simple Network Analyzer Decoding Ethernet and IP headers Objectives The main objective of this assignment is to gain an understanding of network activities and network packet formats
Computer Networks A Simple Network Analyzer Decoding Ethernet and IP headers Objectives The main objective of this assignment is to gain an understanding of network activities and network packet formats
inside: THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN
 THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 inside: SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN & The Advanced Computing Systems Association & The System Administrators
THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 inside: SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN & The Advanced Computing Systems Association & The System Administrators
Aruba 8320 Configuring ACLs and Classifier Policies Guide for ArubaOS- CX 10.00
 Aruba 8320 Configuring ACLs and Classifier Policies Guide for ArubaOS- CX 10.00 Part Number: 5200-4710a Published: April 2018 Edition: 2 Copyright 2018 Hewlett Packard Enterprise Development LP Notices
Aruba 8320 Configuring ACLs and Classifier Policies Guide for ArubaOS- CX 10.00 Part Number: 5200-4710a Published: April 2018 Edition: 2 Copyright 2018 Hewlett Packard Enterprise Development LP Notices
IPv6 Neighbor Discovery
 The IPv6 neighbor discovery process uses Internet Control Message Protocol (ICMP) messages and solicited-node multicast addresses to determine the link-layer address of a neighbor on the same network (local
The IPv6 neighbor discovery process uses Internet Control Message Protocol (ICMP) messages and solicited-node multicast addresses to determine the link-layer address of a neighbor on the same network (local
IP performance optimization
 Contents IP performance optimization 1 display icmp statistics 1 display ip socket 2 display ip statistics 6 display tcp statistics 8 display udp statistics 10 ip forward-broadcast 11 ip icmp flow-control
Contents IP performance optimization 1 display icmp statistics 1 display ip socket 2 display ip statistics 6 display tcp statistics 8 display udp statistics 10 ip forward-broadcast 11 ip icmp flow-control
Veryx ATTEST TM. Sample Test cases Overview. Conformance Test Suite. Internet Protocol version 4 (IPv4) Part Number: T / TCLS IPv /1.
 Veryx ATTEST TM Conformance Test Suite Internet Protocol version 4 (IPv4) Sample Test cases Overview Part Number: T / TCLS IPv4 1.0-1110/1.0 This page is intentionally left blank. Introduction The Veryx
Veryx ATTEST TM Conformance Test Suite Internet Protocol version 4 (IPv4) Sample Test cases Overview Part Number: T / TCLS IPv4 1.0-1110/1.0 This page is intentionally left blank. Introduction The Veryx
Internet Protocols (chapter 18)
 Internet Protocols (chapter 18) CSE 3213 Fall 2011 Internetworking Terms 1 TCP/IP Concepts Connectionless Operation Internetworking involves connectionless operation at the level of the Internet Protocol
Internet Protocols (chapter 18) CSE 3213 Fall 2011 Internetworking Terms 1 TCP/IP Concepts Connectionless Operation Internetworking involves connectionless operation at the level of the Internet Protocol
Lecture 3. The Network Layer (cont d) Network Layer 1-1
 Lecture 3 The Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router? Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets
Lecture 3 The Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router? Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets
Network Security. Introduction to networks. Radboud University, The Netherlands. Autumn 2015
 Network Security Introduction to networks Radboud University, The Netherlands Autumn 2015 What is a (computer) network Definition A computer network is two or more computers that are connected, so that
Network Security Introduction to networks Radboud University, The Netherlands Autumn 2015 What is a (computer) network Definition A computer network is two or more computers that are connected, so that
ET4254 Communications and Networking 1
 Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Outline. IP Address. IP Address. The Internet Protocol. o Hostname & IP Address. o The Address
 Outline IP The Internet Protocol o IP Address IP subnetting CIDR o ARP Protocol o IP Function o Fragmentation o NAT o IPv6 2 IP Address o Hostname & IP Address IP Address o The Address ping www.nu.ac.th
Outline IP The Internet Protocol o IP Address IP subnetting CIDR o ARP Protocol o IP Function o Fragmentation o NAT o IPv6 2 IP Address o Hostname & IP Address IP Address o The Address ping www.nu.ac.th
Lecture 11: IP routing, IP protocols
 Lecture 11: IP routing, IP protocols Contents Routing principles Local datagram delivery ICMP Protocol UDP Protocol TCP/IP Protocol Assuring requirements for streaming TPC Building and terminating TCP
Lecture 11: IP routing, IP protocols Contents Routing principles Local datagram delivery ICMP Protocol UDP Protocol TCP/IP Protocol Assuring requirements for streaming TPC Building and terminating TCP
CSE/EE 461 The Network Layer. Application Presentation Session Transport Network Data Link Physical
 CSE/EE 461 The Network Layer Application Presentation Session Transport Network Data Link Physical This Lecture Focus: What to do when one wire isn t big enough? Point to point link Broadcast link (Ethernet
CSE/EE 461 The Network Layer Application Presentation Session Transport Network Data Link Physical This Lecture Focus: What to do when one wire isn t big enough? Point to point link Broadcast link (Ethernet
Introduction to Network. Topics
 Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
4. Basic IP Support Protocols
 4. Basic IP Support Protocols There are a number of protocols that support the operation of IP. This section will only discuss the most basic three: ICMP, RARP, and ARP. Other more sophisticated protocols
4. Basic IP Support Protocols There are a number of protocols that support the operation of IP. This section will only discuss the most basic three: ICMP, RARP, and ARP. Other more sophisticated protocols
Chapter 5 TCP/IP SUITE
 Chapter 5 TCP/IP SUITE Objectives:- TCP/ IP Model Concept. Defining/functioning of different Layers of TCP / IP suite. 5.1 Introduction Addressing mechanism in the Internet An IP address is an address
Chapter 5 TCP/IP SUITE Objectives:- TCP/ IP Model Concept. Defining/functioning of different Layers of TCP / IP suite. 5.1 Introduction Addressing mechanism in the Internet An IP address is an address
Your Name: Your student ID number:
 CSC 573 / ECE 573 Internet Protocols October 11, 2005 MID-TERM EXAM Your Name: Your student ID number: Instructions Allowed o A single 8 ½ x11 (front and back) study sheet, containing any info you wish
CSC 573 / ECE 573 Internet Protocols October 11, 2005 MID-TERM EXAM Your Name: Your student ID number: Instructions Allowed o A single 8 ½ x11 (front and back) study sheet, containing any info you wish
OmniPeek Report: 21/01/ :17:00. Start: 21/01/ :16:06, Duration: 00:00:33. Total Bytes: , Total Packets: 5274
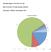 OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
Layer 4: UDP, TCP, and others. based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers
 Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
IP Services Commands. Network Protocols Command Reference, Part 1 P1R-95
 IP Services Commands Use the commands in this chapter to configure various IP services. For configuration information and examples on IP services, refer to the Configuring IP Services chapter of the Network
IP Services Commands Use the commands in this chapter to configure various IP services. For configuration information and examples on IP services, refer to the Configuring IP Services chapter of the Network
Operation Manual IP Addressing and IP Performance H3C S5500-SI Series Ethernet Switches. Table of Contents
 Table of Contents Table of Contents... 1-1 1.1 IP Addressing Overview... 1-1 1.1.1 IP Address Classes... 1-1 1.1.2 Special Case IP Addresses... 1-2 1.1.3 Subnetting and Masking... 1-2 1.2 Configuring IP
Table of Contents Table of Contents... 1-1 1.1 IP Addressing Overview... 1-1 1.1.1 IP Address Classes... 1-1 1.1.2 Special Case IP Addresses... 1-2 1.1.3 Subnetting and Masking... 1-2 1.2 Configuring IP
Each ICMP message contains three fields that define its purpose and provide a checksum. They are TYPE, CODE, and CHECKSUM fields.
 IP address ICMP Each ICMP message contains three fields that define its purpose and provide a checksum. They are TYPE, CODE, and CHECKSUM fields. The TYPE field identifies the ICMP message, the CODE field
IP address ICMP Each ICMP message contains three fields that define its purpose and provide a checksum. They are TYPE, CODE, and CHECKSUM fields. The TYPE field identifies the ICMP message, the CODE field
internet technologies and standards
 Institute of Telecommunications Warsaw University of Technology 2017 internet technologies and standards Piotr Gajowniczek Andrzej Bąk Michał Jarociński Network Layer The majority of slides presented in
Institute of Telecommunications Warsaw University of Technology 2017 internet technologies and standards Piotr Gajowniczek Andrzej Bąk Michał Jarociński Network Layer The majority of slides presented in
NetFlow Layer 2 and Security Monitoring Exports
 The feature improves your ability to detect and analyze network threats such as denial of service (DoS) attacks by increasing the number of fields from which NetFlow can capture relevant data. NetFlow
The feature improves your ability to detect and analyze network threats such as denial of service (DoS) attacks by increasing the number of fields from which NetFlow can capture relevant data. NetFlow
TCP/IP Networking. Training Details. About Training. About Training. What You'll Learn. Training Time : 9 Hours. Capacity : 12
 TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
CSCI-GA Operating Systems. Networking. Hubertus Franke
 CSCI-GA.2250-001 Operating Systems Networking Hubertus Franke frankeh@cs.nyu.edu Source: Ganesh Sittampalam NYU TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute
CSCI-GA.2250-001 Operating Systems Networking Hubertus Franke frankeh@cs.nyu.edu Source: Ganesh Sittampalam NYU TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute
ECE 358 Project 3 Encapsulation and Network Utilities
 ECE 358 Project 3 Encapsulation and Network Utilities Objective: After this project, students are expected to: i. Understand the format of standard frames and packet headers. ii. Use basic network utilities
ECE 358 Project 3 Encapsulation and Network Utilities Objective: After this project, students are expected to: i. Understand the format of standard frames and packet headers. ii. Use basic network utilities
