Signal Stability based Adaptive Routing (SSA) for. Ad-Hoc Mobile Networks. Rohit Dube Cynthia D. Rais Kuang-Yeh Wang Satish K.
|
|
|
- Roy Daniels
- 6 years ago
- Views:
Transcription
1 Signal Stability based Adaptive Routing (SSA) for Ad-Hoc Mobile Networks Rohit Dube Cynthia D. Rais Kuang-Yeh Wang Satish K. Tripathi Institute for Advanced Computer Studies Mobile Computing and Multimedia Laboratory Department of Computer Science University of Maryland College Park, MD 742 CS-TR-3646, UMIACS-TR August 28, 1996 Abstract Unlike static networks, ad-hoc networks have no spatial hierarchy and suer from frequent link failures which prevent mobile hosts from using traditional routing schemes. Under these conditions, mobile hosts must nd routes to destinations without the use of designated routers and also must dynamically adapt the routes to the current link conditions. This paper proposes a distributed adaptive routing protocol for nding and maintaining stable routes based on signal strength and location stability in an ad-hoc network and presents an architecture for its implementation. 1 Introduction Ad-hoc networks consist of mobile hosts in a dynamic network bereft of base-stations and pre-designated routers. These mobile hosts can communicate directly with neighboring hosts through the shared wireless media, but communication with non-neighbor hosts requires a distributed routing algorithm. Traditional routing algorithms which depend on hierarchical addressing schemes and pass detailed routing tables between designated routers, are not eective in ad-hoc networks due to the high rate of topology change [LNT87], [RT87]. In a dynamic network, the routing tables are soon out-of-date and the propagation of the route information is too slow to be accurate. In addition, the changing topology makes looping routes a problem. Hence, new routing algorithms need be developed to support ad-hoc networks. Ad-hoc networks require a highly adaptive routing scheme to deal with the frequent host migrations. In the worst case of a highly dynamic topology, the rate of change is too fast to enable eective routing and data packets must be ooded through the network. In less dynamic cases, it is possible to take advantage of the stable parts of the network to establish routes and communicate using unicast data. This work is supported in part by NSF grant CCR and IBM equipment grants. 1
2 Not all hosts in an ad-hoc network are equally mobile at a given time. Hosts that have been stationary for a period of time are more likely to remain stationary than those currently in motion. In addition, some pairs of hosts receive stronger signals due to their physical proximity and the propagation environment. It is better to choose routes that pass through hosts which receive a stronger signal and which have been stationary for a longer period of time. We propose a routing protocol that utilizes the above observations to choose stable routes within a dynamic ad-hoc network. In this protocol, a host initiates route discovery on demand when a route is needed to send data. The source broadcasts route-search packets which will propagate to the destination, allowing the destination to choose a route and return a route-reply. Signal strength and location stability are used as the criteria for choosing between various next-hop candidates for a route. Selecting the most stable links leads to longer-lived routes and requires less route maintenance. The simulations we performed demonstrate the benets and costs of using signal strength and location stability as the route selection criteria. The results show that the use of signal strength consistently decreases the route maintenance required by providing longer-living routes. Our results also show that location stability should be used only in certain scenarios since misinformation about stability patterns is very costly and has a negative impact on the routing performance. The next section of this paper discusses the basic signal stability based adaptive routing protocol and gives an example of the use of this protocol. Section 3 presents details of the protocols and the architecture, and Section 4 discusses extensions to the protocol and the inter-operability with Mobile-IP. Section 5 presents our simulation environment and results. Section 6 discusses other ad-hoc routing proposals, and the nal section presents conclusions and some suggestions for future work. 2 Signal Stability based Adaptive Routing (SSA) Protocol The Signal Stability based Adaptive Routing protocol (SSA) performs on demand route discovery by selecting longer lived routes based on signal strength and location stability. The signal strength criteria allows the protocol to dierentiate between strong and weak channels, each channel being so characterized by the average signal strength at which packets are exchanged between the hosts at either end of the channel. The location stability criteria biases the protocol toward choosing a channel which has existed for a longer period of time. Together, these two concepts form the signal stability criteria which chooses strong channels which have been in existence for a time greater than some threshold. 2.1 Protocol Overview A source initiates a route discovery request when it has data to send to a destination which is not in the routing table. The route search is broadcast to all neighboring hosts. These hosts propagate the broadcast if (1) it is received over a strong channel and (2) the request has not been propagated previously (to avoid looping). The route search stores the address of each intermediate host in the route taken. The destination chooses the route recorded in the rst arriving request, since this route is probably shorter and/or less congested than routes for slower arriving requests. The destination returns the route reply along the selected route, and each intermediate node includes the new next hop, destination pairs in its routing table. 2
3 Host Signal Strength Last Clicks Set Y Z Table 1: The Signal Stability Table (SST) Destination Y Z Next Hop Table 2: The Routing Table (RT) Functionally, the Signal Stability based Adaptive Routing (SSA) protocol consists of two protocols, the Static Routing Protocol (SRP) and the Dynamic Routing Protocol (DRP), which utilize the extended device driver interface. This interface is responsible for making available to the routing protocols the signal strength information from the device. DRP maintains the routing table by interacting with the DRP on other hosts. SRP performs the actual routing table lookup to forward a packet onto the next hop. 2.2 Protocol Modules The Static Routing Protocol (SRP) and the Dynamic Routing Protocol (DRP) work together to route packets in the ad-hoc network. The extended device driver interface enables communication between these routing protocols and the link layer for the sending and receiving of packets and receiving wireless link quality information. Two tables are maintained to enable SSA routing: the Signal Stability Table (table 1) and the Routing Table (table 2). Each host sends out a link layer beacon 1 to its neighbors once every time quanta, denoted by a click. Every host receiving this beacon records the signal strength at which the beacon was received in the Signal Stability Table (SST). Each host also classies its neighbors as strongly connected (SC and hence belonging to the SC-set) if the host has been receiving strong beacons from the neighbor for the past few clicks. The neighbor is otherwise classied as weakly connected (WC and hence belonging to the WC-set). A host marked as SC in the SST, also has an entry in the Routing Table (RT) which stores destination and next hop pairs for each known route. The SST also has a column to indicate that a beacon was received from a host within the last click, Last, and a column to record how long beacons have been continuously received from each neighboring host. The availability and processing of signal strength information is made possible by the extended device driver interface which provides the DRP with the average signal strength at which a packet was received and the immediate sender. The DRP uses the extended interface to maintain the statistics in the SST. It then uses the SST to maintain routes to neighboring hosts in the RT and the non-neighbor routes via information provided by route- 1 Beacons are 'I am alive messages' which are exchanged between wireless devices at regular intervals to maintain connectivity. SSA does not add overhead by dening any new beacons. 3
4 search, route-reply, error, and erase messages. The SRP functions by looking up the destination in the RT and forwarding the packet on the next-hop for the destination. When there is no entry for the destination in the RT, the SRP initiates a route-search to nd a route to this destination. The route-search message has a hop-list which records the path taken by the message. Each intermediate DRP uses this list to prevent loops and adds its own address to the hop-list. Although the destination DRP may receive multiple copies of a route-search messages, it simply selects the route contained in the rst arriving route-search message and tunnels a route-reply message on the reverse path to the source. The DRP at each intermediate host installs the appropriate next-hop entry for the destination in its RT. When a route-reply message is received, the DRP at the source updates the RT and the SRP routes the data via the next hop found in the RT. A route may become unavailable due to migration of the hosts along the route's path. When a host moves out of range of its neighbors or shuts down, the neighbors will recognize that the host is unreachable since they no longer receive beacons from that host. The DRP will modify the SST and RT to reect the changes. Any routes that have this unreachable host as the next hop will become invalid. When the host receives a packet to forward along an invalid route, SRP will determine the lack of a route and will notify the source via an error message. The source SRP will initiate a new route discovery to nd an available route, and it will send a message to erase the invalid route. 2.3 An Example B D B D A F A F A C E B C E Figure 1: An Example Network Consider the example ad-hoc network shown in Figure 1. A solid edge indicates that the vertices that make up the edge are in each others' SC-sets. The dashed edges indicate that the corresponding vertices are in the WC-set. In part A of Figure 1, host a has data to send to host f and therefore wants to nd a route to destination f. The protocol starts by sending out a broadcast route-search message seeking destination f. Route-search packets that arrive at any host over WC links are dropped, such as the packet sent from a to c. The route-search packet sent to b over the SC link will be broadcast by b to its neighbors. a will drop the packet, having already forwarded it, d and c will forward the packet and mark that they have seen it. Note that c has not already marked the packet as seen since it dropped the packet over the WC from a link without processing it. Packets will arrive at the destination f via two paths: a, b, d, f and a, b, c, e, f. Assuming that the links have similar latencies and trac levels, the route-search will arrive over the shorter path rst : a, b, d, f. The destination, f, will select this route and return the route-reply along the reverse path, f, d, b, a, installing entries in the RT at each intermediate host along the path and at the source, d, b, a. Once the route is installed in the RT, a forwards the data packets via the next-hop to destination f, which is host b. 4
5 Assume now that the link b - d disappears, as shown in part B of Figure 1. When b realizes that host d is unreachable, it sends an error message to a. a then initiates another route-search and sends an erase message to erase the invalid route. f again selects the rst arriving route-search, which will be the route a, b, c, e, f. If, in the future, the link between b and c disappears, then a strong route no longer exists to the destination. In this case, no route-search packets will be propagated to the destination, since packets are not forwarded which arrive over the WC links. When a does not receive a reply after some timeout period, it must decide whether it wants to nd any route or wait and try to nd a strong route at a later time. If it wants any route, it will send a route search message specifying any route, and will nd the route a, c, e, f, which has one WC link. 3 SSA Protocol Details We present the architecture, the packet format, and the protocol details in this section. This provides a clearer understanding of the protocol and also illustrates the architecture that could be used to implement such a protocol. For clarity, the algorithm discussed below presents a synchronous processing scenario, but an implementation of the algorithm could also be asynchronous. Since ad-hoc networks exhibit no spatial hierarchy, we assume a at addressing scheme. For simplicity of exposition we use the MAC addresses of the wireless device as the address of a node. 3.1 Protocol Stack Applications and Network Layer Protocols SRP DRP SSA EXTENDED INTERFACE DEVICE DRIVER Figure 2: The Protocol Stack at each Mobile Host The SRP and DRP are located between the network layer and the link layer, as shown in Figure 2. This makes the SSA routing protocol inter-operable with Mobile-IP, as we discuss in section 4. All incoming packets pass from the device driver extended interface to DRP. The DRP updates the SST and the RT and relays the appropriate types of packets to the SRP. The SRP then either passes a packet up the stack or forwards the packet though the wireless device driver on to the next hop. All transmissions go out via SRP and all receives in through DRP. This division simplies the protocol by exporting a single interface for outgoing packets and also separating out the lter for incoming packets. 5
6 3.2 Packet Format DA SA SEQ TTL TYPE PREF LEN CRC DATA HEADER Figure 3: SSA Packet Format Figure 3 shows the packet format expected by the protocols. SA and DA refer to the source and destination addresses respectively. SEQ is a sequence number assigned by the source, which is useful for route-searches. TTL is a time-to-live eld used to eliminate erroneous packets looping in the network. TYPE distinguishes between messages and is one of the following: unicastdata, flooddata, routesearch, routereply, error or erase. PREF allows a host initiating a route-search to specify the quality of the route desired. This eld can be stronglinkonly or nopreference. LEN is the length of the entire packet and CRC is the checksum. The rest of the packet contains either data (for a packet of type unicastdata or flooddata); the recorded route hop list (for a packet of type routesearch or routereply); or the destination address of a stale route (for a packet of type error or erase). 3.3 SSA Broadcast and Flooding It is important to distinguish between MAC level broadcasting and SSA broadcasting. Every SSA packet is encapsulated in a MAC frame before transmission, and every MAC frame is de-capsulated to an SSA packet on reception. If the MAC address of the encapsulated frame is the broadcast address, then all hosts on that shared wireless media which receive the frame (immediate neighbors) will pass the packet up to the DRP for processing. On the other hand, an SSA broadcast has its DA equal to the broadcast address. This type of broadcast packet will be delivered to all hosts within this ad-hoc network and passed up to the network layer on each receiving host as well as being forwarded. To achieve this, SSA has to tell its lower layer to use MAC level broadcast, i.e. the MAC address of this packet is also the broadcast address. A ooded packet, of TYPE flooddata, must be forward by any host that receives it and is not the SSA destination. Such a packet is forwarded through a MAC level broadcast even if a route to the destination is unknown. The packet is not passed up to the network layer until it reaches the SSA destination. In summary, SSA broadcast reaches the entire ad-hoc network; ooding tries to reach a specic destination by propagating through the entire network; and MAC level broadcast only ensures that the packet reaches the SSA at all the immediate neighbors. 3.4 SRP SRP accepts packets from the DRP and from higher layer protocols. If the destination address of the packet matches that of the host, the packet is pushed up the protocol stack. SRP forwards all other packets through the device driver. Broadcasts are sent out without checking the RT, and the SRP performs a Routing Table lookup for unicast packets. If no 6
7 entry is found for the unicast destination, then a route needs to be found. If this host is the source of the packet, then a route-search is initiated. When a route is found, the DRP will receive the route-reply and install the route in the RT. The SRP then forwards the original packet to the next hop. Alternatively, if this host is not the source of the packet, then a packet of type error is sent back to the source, which will send a message of type erase to tear down the old route and will initiated a new route-search. In this case, the original packet will be dropped by the intermediate host. Table 3 shows the details of the SRP packet processing. initiateroutesearch() produces and broadcasts a route-search packet with an empty data portion, a unique sequence number in SEQ, and a TYPE eld of routesearch. The source can choose an appropriate PREF value depending on the needs of the upper layer application or protocol. We choose stronglinkonly for the rst try and nopreference for any ensuing request retry after a time-out. If after several attempts no satisfactory route is found, the data packet is broadcast and reaches the destination via ooding. An alternate approach to ooding would be be to report an exception to the application which generated the packet. The routine sendrouteerror() initiates a route-error packet, with DA equal to srcaddr and TYPE error. It sends the error packet to the original source for which forwarding was being attempted. The route maintenance packets (of TYPE error or erase) are unicast with best-eort delivery. This means that any hosts which don't have an entry for the forwarding destination will drop the packet without further action. Section 3.7 explains this further. All outgoing SSA packets are encapsulated with the current MAC address and the nexthop MAC address, or the MAC broadcast address if every neighboring host should receive the packet. In the pseudo-code, forward(pkt) is dened to be a unicast to a particular host's MAC address. broadcast(pkt) sends the packet to all reachable hosts by using the MAC broadcast address at the destination. Unicast data is processed only by the host with the matching address while broadcasts are processed by every host which receives the packet. Packets with MAC broadcast addresses may have unicast higher layer addresses, and the SRP forwards the packet and/or passes it up to the higher layers depending on the packet type and destination address. 3.5 DRP The DRP is more complex than the SRP since it processes incoming packets and maintains the RT and the SST. On receiving a packet from the device driver, the DRP deciphers the packet type, updates the tables, modies some of the header elds, and then passes it to the SRP. The DRP pseudo-code is given in Table 4. In addition to the packet, the device driver passes the signal strength (sig) at which the packet is received and the address of the host (sender) that transmitted this packet (not the original source). The updatetables() function then updates the signal strength eld in the SST according to the following formula: SScumulative = SScumulative + (1 ) SS SScumulative here is the quantity recorded in the SST and SS is the value of average signal strength for the the packet supplied by the device driver. is an experimentally determined constant. updatetables() also marks the Last eld in the SST to indicate that a beacon was received from the sending host during the current time click. 7
8 /* input : packet pkt */ destaddr = pkt->header.da; if (destaddr == myaddr isbroadcast(destaddr) == YES) /* pkt for this host */ /* pass packet to application */ enq (pkt); if (destaddr!= myaddr) { /* pkt not for this host */ if (isbroadcast(destaddr) == YES pkt->header.type == ROUTESEARCH pkt->header.type == FLOODDATA) /* pkt forwarded by DRP for broadcast */ broadcast(pkt); else { if (isinrt (destaddr) == YES) { /* if the destaddr is in the RT, forward the packet */ next = nexthop (destaddr); /* get the next hop */ forward(next, pkt); else { if (pkt->header.type!= ERASE && pkt->header.type!= ERROR) { if (srcaddr == myaddr) { /* initiate route request. At the completion of this call there will be an entry for the destaddr in the RT */ initiateroutesearch(destaddr); next = nexthop (destaddr) ; /* get the next hop */ if (next!= NULL) forward(next, pkt); else { pkt->header.type = FLOODDATA; broadcast(pkt); else { /* route fails; inform the source and drop packet */ sendrouteerror(srcaddr); discardpkt(pkt); return; else { discardpkt(pkt); return; Table 3: Pseudo-code for SRP 8
9 /* input : signal_info sig, packet pkt */ updatetables(sender, sig); /* link layer has removed the lower level header from pkt */ if (pkt!= NULL) { if (isstale(pkt) == YES) { discardpkt(pkt); return; switch (pkt->header.type) { case (ROUTESEARCH): if (isfromwc(pkt) == YES && pkt->header.pref == STRONGLINKONLY) { discardpkt(pkt); return; if (issearchforme(pkt->header) == YES) { outpkt = constructroutereply(pkt); if (outpkt == NULL) break ; /* reply not yet constructed */ else installhop(outpkt); /* update RT */ else { outpkt = constructroutesearchforward (pkt) ; seenrequest(pkt->header.sa, pkt->header.seq); SRP(outPkt); break; case (ROUTEREPLY): installhop(pkt); /* update RT */ outpkt = constructroutereplyforward(pkt); SRP(outPkt); break; case (UNICASTDATA): case (FLOODDATA): SRP(pkt); break; case (ERROR): if (pkt->header.da == myaddr) { outpkt = constructrouteerase(pkt); SRP(outPkt); deletehop(pkt); else { SRP(pkt); break; case (ERASE): SRP(pkt); deletehop(pkt); /* update RT */ break; Table 4: Pseudo-code for DRP 9
10 /* clicks assumed to be initialized to */ if (last not marked) { delete entry from SST and RT; return; unmark last; if (SS_cumulative >= SS_threshold) clicks++; else clicks = ; if (clicks == clicks_threshold) { set = SC; add host to RT; /* if clicks > clicks_threshold, then host is already in the RT */ else set = WC; Table 5: Pseudo-code updating SST When no packet is received during a certain period of time, the device driver may still pass signal information obtained through its beacon. In this case the DRP processes only the signal information. Periodically, an asynchronous process runs through the SST comparing SScumulative to an experimentally determined quantity SSthreshold. The calculation shown in Table 5 is then carried out. clicksthreshold is another experimentally determined quantity. The above piece of code ensures that a mobile host which exhibits strong signal strength for clicksthreshold consecutive clicks is included in the SC-set and is added to the RT (with itself as the next hop). The DRP processes each packet depending on its packet type. For route-search packets, isstale() determines whether the packet should be dropped. It is dropped if the packet has been previously seen by this host or if the TTL has expired. The host records route-search packets that it has seen in a table of source (SA), sequence number (SEQ) pairs. The routine seenrequest() records the pair when the host processes the route-search packet for the rst time. constructroutesearchforward() modies the route-search packet by adding the address of the resident host to the hop list to construct a new route-search packet for forwarding. When the intended destination receives a route-search packet, a route-reply is produced by constructroutereply() and sent back to the source along the reverse path of the route contained in the route-search packet. The next hop for route-reply is then installed in the RT and the reply is forwarded. Every intermediate node echoes this procedure (installhop() and constructroutereplyforward()). installhop() installs all possible routes that are implied by the route-reply. For example, Figure 4 shows a route found from a to g. When host d receives a route-reply from g, it installs routes to a and b (with a next hop of c) and installs routes to f and g (with a next hop of e). d already has routes for its neighboring hosts, c and sc e, from beaconing information. A B C D E F G Figure 4: Establishment of a Route 1
11 Once the route installation is completed, data packets starting from the source are forwarded along the next hops installed in the RTs of the intermediate nodes. In the cases where all hops are along an SC-set path, the packets would be routed quickly and eciently. If a host cannot forward a packet due to link failure, SRP sends a route-error packet back to the source. When the source receives such a route-error packet, it sends a route-erasure packet as constructed by the function constructrouteerase() with the DA equal to the destination of the stale route. The stale route is deleted from its RT (deletehop()). Any intermediate host receiving this route-erasure packet forwards it to the next hop, and deletes the stale route. If the host is unable to forward the packet, the packet is simply dropped. 3.6 Extended Interface The extended device driver interface provides the updatetable() call by which the higher layer protocols update the SST. The interface allows changes to the the time period between beacons. It also allows SSthreshold and clickthreshold to be controlled. The SSthreshold determines the extent of the host's coverage area within which the neighbor nodes have strong signals. The clickthreshold regulates the impact of location stability considerations on the protocol. It should be determined based on known mobility patterns of hosts in the ad-hoc network. In the case where it is set to one, the protocol's routing decisions are based solely on signal strength. 3.7 Route Maintenance Route maintenance is triggered when a host has data to send over a failed link. Intermediate nodes send an error message to the source when such a failure occurs. The source host sends a route search packet to nd a new route and sends an erase message to remove the old route. The erase message should reach the intermediate host which discovered the failed next hop. Error and erase messages are unicast with best-eort delivery and are dropped if a host is unable to forward the packet. This prevents a cycle of error and erase messages from wasting network resources. In cases of multiple failures, some routing messages may not reach their destinations. This may result in the existence of stale routes, but it will not cause any routing errors or loops. The stale routes will be discovered and erased by the next data packet that tries to use the invalid route. If a link failure prevents the route reply from reaching the source, the source will time out and retry the route request. The intermediate hosts between the failed link and the destination will have incorrect routes to the source. If any of these hosts use these routes, error and erase messages will be generated to correct the routes. data A B C D E F G Figure 5: Failure of route erase packet In cases where multiple link failures occur nearly simultaneously, erase and error messages may not reach their destinations. If an error packet cannot be delivered to the source, it must be due to another link failure which will also trigger an error packet closer to the source. This second error packet will inform the source of the second failure so that the source can 11
12 take appropriate action. If a data packet is between the links when they both fail, as shown in Figure 5, the resulting error message from e will not reach the source a, since it will be dropped due to the failed link at c. When a sends a data packet again, b will send the error message to inform a of the route failure. The erase message from a will erase the route at b, but the stales routes to g at c and d will only be erased if either c or d tries to send data to g. If the second link failure occurs after the error message arrives at a, then the erase message from a will be dropped at b. This creates the same situation where c and d have an invalid route to g which will be erased when either c or d sends a packet toward g. Since hosts relay route-search packets even if they already know a route to the desired destination, the algorithm works correctly in the presence of stale routes. The source is informed of the error and initiates a new route-search. SSA uses route erasure only to avoid wasting resources by forwarding data packets over routes known to be stale. The cost of this simple error and erase method is a few stale routes. Since the multiple failure cases are rare, the best-eort unicast of error and erase packets is an eective method of reducing excessive packet transmissions. 4 Other Issues 4.1 Enhanced SSA The protocol presented in the previous sections provides a basic routing function. However, there may be several enhancements to give the hosts more options to deal with varying needs. One is the route quality option (the PREF eld in the header) which the source sets when searching for a route. The host may prefer routes with more strong links but not want to exclude routes with any weak links. To accommodate this need, the hosts may implement another PREF option: strongpreferred. Any intermediate host receiving such a routesearch should forward it (by broadcast) unless its hop list contains a loop or its time-to-live has expired, even if the host has seen this request before (through a dierent path). The destination host should wait for a period of time to allow several route-search packets to arrive via dierent routes. The destination then selects the best one according to a certain criteria, such as shortest path with minimal weak links. The source host may choose this option to nd a route if it is probable that no strong route exists. Another optimization decreases route discovery latency and route-request propagation by allowing intermediate hosts to participate in route discovery. If an intermediate host receiving a route-request already has a route to the destination, it may send a route-reply immediately back to the source to decrease the latency in addition to forwarding the route-request to the destination. If this route is non-optimal or stale, it will be overwritten later by a route-reply from the destination. The source may decide whether it wants to risk losing a few packets to start transmitting data sooner. 4.2 Inter-operability Assuming that some hosts in the ad-hoc network are base-stations with both wired and wireless connectivity, SSA can be easily integrated into the global Internet through Mobile-IP ([Per96]). These base-stations serve as the home and foreign agents for Mobile-IP. 12
13 Conceptually, Mobile-IP sits on top of SSA (Figure 6). As far as SSA is concerned, Mobile-IP is just another higher layer protocol. On the other hand, Mobile-IP treats SSA as a link-layer protocol, and from the viewpoint of Mobile-IP, a base station can \directly" reach any host that resides in the same ad-hoc network. SSA will take the responsibility of delivering packets between them. The base station will take care of any encapsulation or de-capsulation required by Mobile-IP. Applications End-to-end Protocol (TCP) Mobile-IP SSA Wireless Driver Physical Layer (Wireless) Applications End-to-end Protocol (TCP) Mobile-IP SSA Wired-Link Driver Wireless Driver Physical Layer (Wireless) Physical Layer (Wired) To Internet Mobile Host Base Station Figure 6: Integration of Mobile-IP and SSA Mobile-IP on a base station may broadcast its agent advertisement, which should be heard by any potential client, in this case by any host within the ad-hoc network. In order to achieve this, all hosts in this ad-hoc network would be required to re-broadcast the agent advertisement, which takes a lot of resources. We suggest that a base station broadcast agent advertisements only rarely, or not at all, to conserve the limited bandwidth. If access to the wired network is not always available in the ad-hoc network, then occasional advertisements may be worthwhile. Otherwise, a mobile host should use agent solicitations when it desires the service of a base-station. When sending an agent solicitation, the SSA on the mobile host should send a packet addressed to the SSA broadcast address. Non-base station hosts will simply re-broadcast the packet, while any reachable base-stations will send out a reply if willing to serve as an agent. The base-station's reply would trigger SSA to nd a route to the base-station. After this handshake, the mobile host can continue with the usual registration process required by Mobile-IP and start sending and receiving datagrams to and from the Internet through the base station. If a mobile host becomes separated from its agent, it may send out a new agent solicitation to try to nd another reachable base-station. Alternatively, it may occasionally send agent solicitations to nd other base-stations while maintaining a connection with the current one. Having this list of base-stations would decrease the latency of a base-station switch in case the rst base-station becomes unreachable. 5 Simulation We performed simulations to evaluate the benets and costs of the SSA routing approach. The simulations quantify the length and longevity of the routes determined by SSA under various node densities and mobility rates. They also determine the relative ecacy of using signal strength and location stability as selection criteria for routing. 13
14 We studied a large range of cases by varying many of the input parameters, including: area, host density, transmission range, rate of topology change, pattern of individual host mobility, session length, and the routing algorithm criteria for route selection. We measured and compared the number of route reconstructions required, the average route hop length, the percentage of strong routes available, and the transmission cost of the SSA routing algorithm. We saw improved reconstruction costs for most sets of parameters. We present only a representative set of simulations in the following section. 5.1 Simulation Setup Our simulation is based on the environment of a closed unit area in which there are a number of randomly distributed mobile hosts. A signal is considered strong if it comes from a host strong-radius units or less away, and two hosts separated by more than weak-radius units are considered disconnected. Note that in a real environment, these quantities would be dependent on and controlled by the SSthreshold set through the device driver interface and the capability of the wireless device respectively. In our simulation, we assume that the signal strength depends solely on the distance between the sending and receiving hosts. If a signal is weaker than that from a host weak-radius units away, then it would be considered noise and dropped at the physical layer. SSthreshold is assumed to be equal to the strength of a signal from a host strong-radius units away. Since SSthreshold is experimentally determined, we ran simulations with strong-radius and 3 units. The weak-radius is kept constant at 4 units as it is a physical quantity dependent on the wireless device. Twenty percent of the hosts are stationary during the simulation. The other eighty percent move for a number of clicks and then stay for some number of clicks and then move again, continuing the cycle. The lengths of the moving periods are normally distributed with average 1 clicks and standard deviation 1 click. There are two classes of staying period lengths. The short-stay class is normally distributed with average 3 clicks and standard deviation 1 click, and the long-stay class with average 15 and standard deviation 1. Initially every nonstationary host is assigned a probability that determines whether it falls into the short-stay or long-stay class each time it enters a staying period. The initial staying probability is chosen from a normal distribution with standard deviation.5 and a mean that ranges from to 1 with step.1. A simulation is run for each step of the staying probability to obtain data for a range of mobility rates. If a host moves during a certain click, it moves units of distance in a randomly chosen direction. If it didn't move during the previous click, the direction is chosen from a uniformly distributed random number. Otherwise, the direction is chosen from a normally distributed random number with average equal to the previous direction and standard deviation of 1. Hence, a host is likely to continue to move in the same general direction as previous movement. If a host hits the boundary of the area, it will bounce back (mirror reection) so that the total moving distance during this time click is still units. We run simulations for networks of sizes 5, 1 and hosts with clickthreshold equal to 5 and 1. clickthreshold determines the threshold above which routes are considered stable. Note that clickthreshold equal to 1 means that location stability is not considered. When considering location stability, this threshold should be slightly greater than the mean of the short-stay period so that only hosts which have a long-stay period are considered stable. A clickthreshold of 5 is chosen since the mean of the short-stay period equals 3. During each run, we randomly generate the initial positions of the hosts and let them 14
15 move and exchange beacon signals for 1 time clicks to establish an initial state. Then we randomly choose a source and a destination and run our algorithm. After each time click, we send a data packet through the established route to trigger route maintenance actions (route erasure and re-discovery) if any of the links failed. After each session (of length 3 clicks), we observe the average number of hops in a route and the number of required route reconstructions. These quantities are averaged over several hundred runs for each combination of the input parameters. 5.2 Simulation Results We compare the results from SSA (with and without location stability) with those from an imaginary routing algorithm in which a shortest path is chosen, regardless of the strength of its links. We call the later approach the simple algorithm. The performance parameters are plotted against the average mobility rate, which is the average of all the host mobility rates. The mobility rate of a host is the number of clicks during which the host moves divided by the total number of clicks in a session. Clearly, this average mobility rate is inversely dependent on the average initial staying probability. As the mobility rate increases, the number of route reconstructions consistently increases, as shown in gures 7 to 9. The number of reconstructions also increases as the number of hosts decreases, due to the increasing sparseness of the topology. In the following graphs, we compare the simple algorithm to the SSA algorithm for the same number of hosts. Percentage of Route Reconstructions (%) Percentage of Route Reconstructions: Strong Radius = 3 SSA: SSA: hosts simple algorithm: simple algorithm: hosts Percentage of Route Reconstructions (%) Percentage of Route Reconstructions: Strong Radius = SSA: SSA: hosts simple algorithm: simple algorithm: hosts Figure 7: Number of Route Reconstructions: Stability Considered Figures 7 and 8 show that the fraction of sessions requiring route reconstructions is consistently lower for SSA both with and without stability as compared to the simple algorithm. However SSA with location stability performs worse than that without location stability. At rst glance, this is somewhat surprising. However gures 1 and 11 reveal that taking stability into account increases the probability of non-existence of strong routes considerably. This is because location stability introduces a much stronger criteria for a link to be SC. If we are unable to nds a strong route, route discovery takes long and the route likely fails sooner. The advantage of SSA arises from the buer-zone eect. If a SC link is chosen as part of a route, will become WC before breaking, and this tends to give the individual links, and therefore the entire route, a longer life. The buer-zone allows mobile hosts to roam within a certain vicinity of each other without triggering a route reconstruction. 15
16 Percentage of Route Reconstructions (%) Percentage of Route Reconstructions: Strong Radius = 3 SSA: SSA: hosts simple algorithm: simple algorithm: hosts Percentage of Route Reconstructions (%) Percentage of Route Reconstructions: Strong Radius = SSA: SSA: hosts simple algorithm: simple algorithm: hosts Figure 8: Number of Route Reconstructions: Stability Not Considered Ratio (SSA / Simple Algorithm) Number of Route Reconstructions (Ratio): Strong Radius = 3 click threshold = 5; click threshold = 5; click threshold = 5; hosts click threshold = 1; click threshold = 1; click threshold = 1; hosts Ratio (SSA / Simple Algorithm) Number of Route Reconstructions (Ratio): Strong Radius = click threshold = 5; click threshold = 5; click threshold = 5; hosts click threshold = 1; click threshold = 1; click threshold = 1; hosts.6.6 Figure 9: Improvement of SSA Over the Simple Algorithm Comparing the SSA curves for in gure 8, we see that the performance with the larger strong radius is superior to that of the smaller one. This is somewhat contrary to the buer-zone eect just described since the smaller radius allows the mobile hosts to travel a longer distance in the weak region before the link breaks. Figure 11 oers insight by showing that the percentage of non-existence of strong routes is more than 8% - 9% for a strongradius of, whereas it is only about % - 3% for a strong-radius of 3. The decreased number of strong routes more than osets any gains due to the increase in the buer-zone. Clearly, SSA performs well when there are an adequate number of strong routes. This, in turn, depends on the node density (the number of hosts in our environment), the strong radius, the mobility rate, and the criteria dening a strong link. Many combinations of these parameters result in a conguration where SSA drops the number of route reconstructions required. Figure 9 indicates that SSA reduces the route reconstructions needed by up to 4% and never performs worse than the simple algorithm. A careful comparison of the SSA curves with and without location stability considerations indicates that in most cases not taking stability into account results in better performance. Since SSA prefers routes with strong links which are likely to be between two hosts close to each other, we tend to get routes with more hops as compared to the simple algorithm. On the other hand, strong links are less vulnerable to interference and hence result in less 16
17 Percentage of Non-Existences of Strong Routes (%) Percentage of Non-Existences of Strong Routes: Strong Radius = 3 hosts Percentage of Non-Existences of Strong Routes (%) Percentage of Non-Existences of Strong Routes: Strong Radius = hosts Figure 1: Probability of No Strong Routes: Stability Considered Percentage of Non-Existences of Strong Routes (%) Percentage of Non-Existences of Strong Routes: Strong Radius = 3 hosts Percentage of Non-Existences of Strong Routes (%) Percentage of Non-Existences of Strong Routes: Strong Radius = hosts Figure 11: Probability of No Strong Routes: Stability Not Considered packet loss and corruption. As a rough weight, we count each weak link as 1.25 hops to reect its vulnerability. Figures 12 and 13 show the hop count ratio between SSA and the simple algorithm. Through the mobility rate range, the hop count ratio usually ranges between 1.1 and 1.5. Since this added hop length cost is small, SSA is benecial since it consistently reduces the route reconstruction cost. 6 Related Work For networks with static topologies, traditional routing techniques include link-state routing and distance vector routing. Routing in an ad-hoc network presents a challenge because the dynamic topology requires frequent updates and ecient routing information. If the rate of topology change is extremely dynamic then ooding becomes the only eective method for data transmission. Most routing approaches for ad-hoc networks assume a rate of change that is not so fast as to make ooding the only alternative. The requirements and diculties of ad-hoc routing are discussed in [CMB96]. One type of ad-hoc routing methods seeks to modify existing routing algorithms for use in a dynamic topology. The Destination Sequenced Distance Vector algorithm [PB94] modies the distributed Bellman-Ford algorithm to prevent looping by including sequence number to 17
18 Hop Count Ratio (SSA / Simple Algorithm) Hop Count Ratio: Strong Radius = 3 hosts Hop Count Ratio (SSA / Simple Algorithm) Hop Count Ratio: Strong Radius = hosts Figure 12: Hop Counts: Stability Considered Hop Count Ratio (SSA / Simple Algorithm) Hop Count Ratio: Strong Radius = 3 hosts Hop Count Ratio (SSA / Simple Algorithm) Hop Count Ratio: Strong Radius = hosts 1 1 Figure 13: Hop Counts: Stability Not Considered order the routing information. The Path Find algorithm in [MGLA95] is a distance vector routing protocol, which uses second-to-last hop to a destination to identify a route and prevent looping. The approach presented in [KCVP96] nds and maintains clusters in the ad-hoc network. The boundary nodes connect clusters and perform routing using a traditional routing algorithm. For all of these methods, each node, or the boundary nodes, needs to know the topology of the entire network at all times. Information is propagated through the network to achieve this goal. Another type of ad-hoc routing algorithms uses an on demand philosophy. Routes to a destination are only sought if the node has something to send to that destination. The dynamic source routing proposed in [JM96] uses broadcasts to propagate the route request. Each node which forwards the route request adds its address to the source list. When the request reaches the destination a complete route is listed in the packet. The Lightweight Mobile Routing approach proposed in [CE95] oods the network with a query broadcast when the route is desired. The nodes receiving this query broadcast either forward the broadcast or broadcast a reply to the destination with the requested route. This approach uses link status to create routes and prevent looping. Route erasure is required when the topology changes. The Associativity Based Routing approach [Toh] also uses broadcast queries to nd desired routes, but the optimal route is selected by the destination based on the stability of the route 18
19 and shortest path. The main criteria is the intermediate node stability, which is based on the idea that nodes which have been stationary for a threshold period are less likely to move. This method also uses route erasure and maintenance when topology changes cause a route failure. The main dierence between these approaches and our approach is our utilization of the information available at the link level to choose routes. The quality of the channel is used to determine whether the topology is stable or uctuating at any given time. Like the second type of algorithms, routes are determined only on demand. However, we do not limit the rate of change of the topology or suggest that all parts of the topology are equally stable. We select routes through the most stable areas of the network, using an an adaptive algorithm to ensure successful data transmission in a highly dynamic topology. 7 Conclusion and Future Work The SSA protocol proposed in this paper focuses on obtaining the most stable routes through an ad-hoc network. This approach seeks to maximize the duration of the discovered routes. Our simulations have shown signicant savings in the number of route reconstructions as a result of using signal strength to select routes. Using location stability, on the other hand, is shown to be very sensitive to the particular conguration of the ad-hoc network being considered. Since a general ad-hoc network is likely to have unpredictable and variable mobility patterns, we propose the adoption of signal strength as a criteria for routing with congurable parameters to take location stability into account where applicable. We plan to do further simulations using a packet level simulator to determine the costs and benets of this approach more accurately and to study the eect of this approach on various transport protocols, including TCP. Although it is intuitively clear that the algorithm is loop free and converges, we plan to prove these properties using theoretical constructs. We also plan to analyze convergence time and routing overhead for this algorithm. Acknowledgements We would like to thank Sambit Sahu (University of Massachusetts, Amherst) for his comments. 19
20 References [CE95] S. Corson and A. Ephremides. A Distributed Routing Algorithm for Mobile Wireless Networks. ACM/Baltzer Wireless Networks Journal, 1(1), [CMB96] [JM96] S. Corson, J. Macker, and S. Batsell. Architectural Considerations for Mobile Mesh Networking. Internet Draft RFC Version 2 work in progress, May D.B. Johnson and D.A. Maltz. Protocols for Adaptive Wireless and Mobile Networking. IEEE Personal Communications, 3(1), February [KCVP96] P. Krishna, M. Chatterjee, N.H. Vaidya, and D.K. Pradhan. A Cluster-based Approach for Routing in Ad-Hoc Networks. In USENIX Technical Conference Proceedings, January [LNT87] B.M. Leiner, D.L. Nielson, and F.A. Tobagi. Issues in Packet Radio Network Design. Proceedings of the IEEE, 75(1), January [MGLA95] S. Murthy and J.J. Garcia-Luna-Aceves. A Routing Protocol for Packet Radio Networks. In MOBICOM Conference Proceedings, November [PB94] [Per96] [RT87] [Toh] C.E. Perkins and P. Bhagwat. Highly Dynamic Destination-Sequenced Distance- Vector Routing (DSDV) for Mobile Computers. In SIGCOMM Conference Proceedings, C.E. Perkins, editor. IP Mobility Support, draft-ietf-mobileip-protocol-15.txt. Internet Engineering Task Force, February Internet draft work in progress. J. Rubin and J.D. Tarnow. The DARPA Packet Radio Network Protocols. Proceedings of the IEEE, 75(1), January C-K. Toh. Associativity-Based Routing for Ad-Hoc Mobile Networks. Personal communication.
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14
 Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET
 ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
A Routing Protocol for. Physically Hierarchical Ad Hoc Networks. (Preliminary Version) Department of Computer Science. Texas A&M University
 A Routing Protocol for Physically Hierarchical Ad Hoc Networks (Preliminary Version) Young-Bae Ko Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112, USA
A Routing Protocol for Physically Hierarchical Ad Hoc Networks (Preliminary Version) Young-Bae Ko Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112, USA
A Highly Effective and Efficient Route Discovery & Maintenance in DSR
 A Highly Effective and Efficient Route Discovery & Maintenance in DSR Shiva Prakash 1, Rajeev Kumar 2, Brijesh Nayak 3, Manindar Kumar Yadav 4 Department of Computer Science and Engineering, Madan Mohan
A Highly Effective and Efficient Route Discovery & Maintenance in DSR Shiva Prakash 1, Rajeev Kumar 2, Brijesh Nayak 3, Manindar Kumar Yadav 4 Department of Computer Science and Engineering, Madan Mohan
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
Example of TORA operations. From last time, this was the DAG that was built. A was the source and X was the destination.
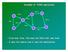 Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
forward packets do not forward packets
 Power-aware Routing in Wireless Packet Networks Javier Gomez, Andrew T. Campbell Dept. of Electrical Engineering Columbia University, N 10027, USA Mahmoud Naghshineh, Chatschik Bisdikian IBM T.J. Watson
Power-aware Routing in Wireless Packet Networks Javier Gomez, Andrew T. Campbell Dept. of Electrical Engineering Columbia University, N 10027, USA Mahmoud Naghshineh, Chatschik Bisdikian IBM T.J. Watson
ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS
 ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS Ganga S 1, Binu Chandran R 2 1, 2 Mohandas College Of Engineering And Technology Abstract: Wireless Ad-Hoc Network is a collection of wireless mobile
ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS Ganga S 1, Binu Chandran R 2 1, 2 Mohandas College Of Engineering And Technology Abstract: Wireless Ad-Hoc Network is a collection of wireless mobile
A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network
 ShriRam College of Engineering & Management 1 A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network M.Ramaiya Rohit Gupta Rachit Jain Head,Dept. Computer Science Dept. Computer
ShriRam College of Engineering & Management 1 A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network M.Ramaiya Rohit Gupta Rachit Jain Head,Dept. Computer Science Dept. Computer
A COMPARISON STUDY OF DSDV AND SEAD WIRELESS AD HOC NETWORK ROUTING PROTOCOLS
 A COMPARISON STUDY OF DSDV AND SEAD WIRELESS AD HOC NETWORK ROUTING PROTOCOLS M.S.R.S Prasad 1, S.S. Panda 2, MNM Prasad 3, S.T.V.S.Kumar 4 1 Assistant Professor (SG), Dept. of CSE., Regency Institute
A COMPARISON STUDY OF DSDV AND SEAD WIRELESS AD HOC NETWORK ROUTING PROTOCOLS M.S.R.S Prasad 1, S.S. Panda 2, MNM Prasad 3, S.T.V.S.Kumar 4 1 Assistant Professor (SG), Dept. of CSE., Regency Institute
Arvind Krishnamurthy Fall 2003
 Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
A Distributed Routing Algorithm for Supporting Connection-Oriented Service in Wireless Networks with Time-Varying Connectivity
 A Distributed Routing Algorithm for Supporting Connection-Oriented Service in Wireless Networks with Time-Varying Connectivity Anastassios Michail Department of Electrical Engineering and Institute for
A Distributed Routing Algorithm for Supporting Connection-Oriented Service in Wireless Networks with Time-Varying Connectivity Anastassios Michail Department of Electrical Engineering and Institute for
Supporting IP Multicast for Mobile Hosts. Yu Wang Weidong Chen. Southern Methodist University. May 8, 1998.
 Supporting IP Multicast for Mobile Hosts Yu Wang Weidong Chen Southern Methodist University fwy,wcheng@seas.smu.edu May 8, 1998 Abstract IP Multicast is an ecient mechanism of delivering a large amount
Supporting IP Multicast for Mobile Hosts Yu Wang Weidong Chen Southern Methodist University fwy,wcheng@seas.smu.edu May 8, 1998 Abstract IP Multicast is an ecient mechanism of delivering a large amount
AMRIS: A Multicast Protocol for Ad hoc Wireless Networks
 of AMRIS: A Multicast Protocol for Ad hoc Wireless Networks C.W. Wu, Y.C. Tay National University of Singapore wuchunwei@alum.comp.nus.edu.sg,tay@acm.org Abstract This paper introduces AMRIS, a new multicast
of AMRIS: A Multicast Protocol for Ad hoc Wireless Networks C.W. Wu, Y.C. Tay National University of Singapore wuchunwei@alum.comp.nus.edu.sg,tay@acm.org Abstract This paper introduces AMRIS, a new multicast
REVIEW ON ROUTING PROTOCOLS FOR MOBILE AD HOC NETWORKS
 REVIEW ON ROUTING PROTOCOLS FOR MOBILE AD HOC NETWORKS G. Poornima 1, Mr. M. Rajasenathipathi 2, 1 Research Scholar, Department of Computer Science, NGM College, Pollachi 2 Assistant Professor, Department
REVIEW ON ROUTING PROTOCOLS FOR MOBILE AD HOC NETWORKS G. Poornima 1, Mr. M. Rajasenathipathi 2, 1 Research Scholar, Department of Computer Science, NGM College, Pollachi 2 Assistant Professor, Department
Andrew T. Campbell, Javier Gomez. Center for Telecommunications Research, Columbia University, New York. [campbell,
 An Overview of Cellular IP Andrew T. Campbell, Javier Gomez Center for Telecommunications Research, Columbia University, New York [campbell, javierg]@comet.columbia.edu Andras G. Valko Ericsson Research
An Overview of Cellular IP Andrew T. Campbell, Javier Gomez Center for Telecommunications Research, Columbia University, New York [campbell, javierg]@comet.columbia.edu Andras G. Valko Ericsson Research
Hybrid gateway advertisement scheme for connecting mobile ad hoc networks to the Internet
 * gateway advertisement scheme for connecting mobile ad hoc networks to the Internet Jeongkeun Lee (), Dongkyun Kim (2), J.J.Garcia-Luna-Aceves (3), Yanghee Choi (), Jihyuk Choi (4), Sangwoo Nam (4) ()
* gateway advertisement scheme for connecting mobile ad hoc networks to the Internet Jeongkeun Lee (), Dongkyun Kim (2), J.J.Garcia-Luna-Aceves (3), Yanghee Choi (), Jihyuk Choi (4), Sangwoo Nam (4) ()
Performance Analysis of Three Routing Protocols for Varying MANET Size
 Proceedings of the International MultiConference of Engineers and Computer Scientists 8 Vol II IMECS 8, 9- March, 8, Hong Kong Performance Analysis of Three Routing Protocols for Varying MANET Size N Vetrivelan,
Proceedings of the International MultiConference of Engineers and Computer Scientists 8 Vol II IMECS 8, 9- March, 8, Hong Kong Performance Analysis of Three Routing Protocols for Varying MANET Size N Vetrivelan,
Extensions to RTP to support Mobile Networking: Brown, Singh 2 within the cell. In our proposed architecture [3], we add a third level to this hierarc
![Extensions to RTP to support Mobile Networking: Brown, Singh 2 within the cell. In our proposed architecture [3], we add a third level to this hierarc Extensions to RTP to support Mobile Networking: Brown, Singh 2 within the cell. In our proposed architecture [3], we add a third level to this hierarc](/thumbs/88/114904400.jpg) Extensions to RTP to support Mobile Networking Kevin Brown Suresh Singh Department of Computer Science Department of Computer Science University of South Carolina Department of South Carolina Columbia,
Extensions to RTP to support Mobile Networking Kevin Brown Suresh Singh Department of Computer Science Department of Computer Science University of South Carolina Department of South Carolina Columbia,
LECTURE 9. Ad hoc Networks and Routing
 1 LECTURE 9 Ad hoc Networks and Routing Ad hoc Networks 2 Ad Hoc Networks consist of peer to peer communicating nodes (possibly mobile) no infrastructure. Topology of the network changes dynamically links
1 LECTURE 9 Ad hoc Networks and Routing Ad hoc Networks 2 Ad Hoc Networks consist of peer to peer communicating nodes (possibly mobile) no infrastructure. Topology of the network changes dynamically links
Optimized Paging Cache Mappings for efficient location management Hyun Jun Lee, Myoung Chul Jung, and Jai Yong Lee
 Optimized Paging Cache Mappings for efficient location management Hyun Jun Lee, Myoung Chul Jung, and Jai Yong Lee Abstract Cellular IP maintains distributed cache for location management and routing purposes.
Optimized Paging Cache Mappings for efficient location management Hyun Jun Lee, Myoung Chul Jung, and Jai Yong Lee Abstract Cellular IP maintains distributed cache for location management and routing purposes.
Performance Comparison of Ad Hoc Routing Protocols over IEEE DCF and TDMA MAC Layer Protocols
 Performance Comparison of Ad Hoc Routing Protocols over IEEE 82.11 DCF and TDMA MAC Layer Protocols Govind. P. Gupta Computer Science Department R.K.G.I.T, Ghaziabad (India) er_gpgupta@yahoo.com A. K.
Performance Comparison of Ad Hoc Routing Protocols over IEEE 82.11 DCF and TDMA MAC Layer Protocols Govind. P. Gupta Computer Science Department R.K.G.I.T, Ghaziabad (India) er_gpgupta@yahoo.com A. K.
Routing Protocols in MANETs
 Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks
 Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks Jayanta Biswas and Mukti Barai and S. K. Nandy CAD Lab, Indian Institute of Science Bangalore, 56, India {jayanta@cadl, mbarai@cadl,
Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks Jayanta Biswas and Mukti Barai and S. K. Nandy CAD Lab, Indian Institute of Science Bangalore, 56, India {jayanta@cadl, mbarai@cadl,
Evaluating the Performance of Mobile Agent-Based Message Communication among Mobile Hosts in Large Ad Hoc Wireless Network
 Evaluating the Performance of Mobile Agent-Based Communication among Mobile Hosts in Large Ad Hoc Wireless Network S. Bandyopadhyay Krishna Paul PricewaterhouseCoopers Limited Techna Digital Systems Sector
Evaluating the Performance of Mobile Agent-Based Communication among Mobile Hosts in Large Ad Hoc Wireless Network S. Bandyopadhyay Krishna Paul PricewaterhouseCoopers Limited Techna Digital Systems Sector
A Study on Mobile Internet Protocol and Mobile Adhoc Network Routing Protocols
 International Journal of Computer Science & Communication Vol. 1, No. 2, July-December 2010, pp. 185-189 A Study on Mobile Internet Protocol and Mobile Adhoc Network Routing Protocols B.V. Manikyala Rao
International Journal of Computer Science & Communication Vol. 1, No. 2, July-December 2010, pp. 185-189 A Study on Mobile Internet Protocol and Mobile Adhoc Network Routing Protocols B.V. Manikyala Rao
Gateway Discovery Approaches Implementation and Performance Analysis in the Integrated Mobile Ad Hoc Network (MANET)-Internet Scenario
 Gateway Discovery Approaches Implementation and Performance Analysis in the Integrated Mobile Ad Hoc Network (MANET)-Internet Scenario K.Gautham 1, Nagajothi A 2 Student, Computer Science and Engineering,
Gateway Discovery Approaches Implementation and Performance Analysis in the Integrated Mobile Ad Hoc Network (MANET)-Internet Scenario K.Gautham 1, Nagajothi A 2 Student, Computer Science and Engineering,
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol
 1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol
 Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol Kalyan Kalepu, Shiv Mehra and Chansu Yu, Department of Electrical and Computer Engineering Cleveland State University 2121
Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol Kalyan Kalepu, Shiv Mehra and Chansu Yu, Department of Electrical and Computer Engineering Cleveland State University 2121
Outline. CS5984 Mobile Computing. Host Mobility Problem 1/2. Host Mobility Problem 2/2. Host Mobility Problem Solutions. Network Layer Solutions Model
 CS5984 Mobile Computing Outline Host Mobility problem and solutions IETF Mobile IPv4 Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Mobile IPv4 1 2 Host Mobility Problem 1/2 Host Mobility
CS5984 Mobile Computing Outline Host Mobility problem and solutions IETF Mobile IPv4 Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Mobile IPv4 1 2 Host Mobility Problem 1/2 Host Mobility
Outline. CS6504 Mobile Computing. Host Mobility Problem 1/2. Host Mobility Problem 2/2. Dr. Ayman Abdel-Hamid. Mobile IPv4.
 CS6504 Mobile Computing Outline Host Mobility problem and solutions IETF Mobile IPv4 Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Mobile IPv4 1 2 Host Mobility Problem 1/2 Host Mobility
CS6504 Mobile Computing Outline Host Mobility problem and solutions IETF Mobile IPv4 Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Mobile IPv4 1 2 Host Mobility Problem 1/2 Host Mobility
Mobile Routing : Computer Networking. Overview. How to Handle Mobile Nodes? Mobile IP Ad-hoc network routing Assigned reading
 Mobile Routing 15-744: Computer Networking L-10 Ad Hoc Networks Mobile IP Ad-hoc network routing Assigned reading Performance Comparison of Multi-Hop Wireless Ad Hoc Routing Protocols A High Throughput
Mobile Routing 15-744: Computer Networking L-10 Ad Hoc Networks Mobile IP Ad-hoc network routing Assigned reading Performance Comparison of Multi-Hop Wireless Ad Hoc Routing Protocols A High Throughput
Study of Route Reconstruction Mechanism in DSDV Based Routing Protocols
 Study of Route Reconstruction Mechanism in DSDV Based Routing Protocols Sharma Shelja, Kumar Suresh and Rathy R. K. Department of CSE, FET, MRIU, Faridabad, India Email: sharma.shelja@gmail.com, enthusk@yahoo.com,
Study of Route Reconstruction Mechanism in DSDV Based Routing Protocols Sharma Shelja, Kumar Suresh and Rathy R. K. Department of CSE, FET, MRIU, Faridabad, India Email: sharma.shelja@gmail.com, enthusk@yahoo.com,
DYNAMIC SEARCH TECHNIQUE USED FOR IMPROVING PASSIVE SOURCE ROUTING PROTOCOL IN MANET
 DYNAMIC SEARCH TECHNIQUE USED FOR IMPROVING PASSIVE SOURCE ROUTING PROTOCOL IN MANET S. J. Sultanuddin 1 and Mohammed Ali Hussain 2 1 Department of Computer Science Engineering, Sathyabama University,
DYNAMIC SEARCH TECHNIQUE USED FOR IMPROVING PASSIVE SOURCE ROUTING PROTOCOL IN MANET S. J. Sultanuddin 1 and Mohammed Ali Hussain 2 1 Department of Computer Science Engineering, Sathyabama University,
Impact of Node Velocity and Density on Probabilistic Flooding and its Effectiveness in MANET
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
CS5984 Mobile Computing
 CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET
 2011 International Conference on Information and Network Technology IPCSIT vol.4 (2011) (2011) IACSIT Press, Singapore QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET Ashwini V. Biradar
2011 International Conference on Information and Network Technology IPCSIT vol.4 (2011) (2011) IACSIT Press, Singapore QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET Ashwini V. Biradar
Unicast Routing in Mobile Ad Hoc Networks. Dr. Ashikur Rahman CSE 6811: Wireless Ad hoc Networks
 Unicast Routing in Mobile Ad Hoc Networks 1 Routing problem 2 Responsibility of a routing protocol Determining an optimal way to find optimal routes Determining a feasible path to a destination based on
Unicast Routing in Mobile Ad Hoc Networks 1 Routing problem 2 Responsibility of a routing protocol Determining an optimal way to find optimal routes Determining a feasible path to a destination based on
A Reliable Route Selection Algorithm Using Global Positioning Systems in Mobile Ad-hoc Networks
 A Reliable Route Selection Algorithm Using Global Positioning Systems in Mobile Ad-hoc Networks Won-Ik Kim Radio Performance Analysis Section Electronics & Telecommunications Research Institute 161 Kajong-dong,
A Reliable Route Selection Algorithm Using Global Positioning Systems in Mobile Ad-hoc Networks Won-Ik Kim Radio Performance Analysis Section Electronics & Telecommunications Research Institute 161 Kajong-dong,
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols. Broch et al Presented by Brian Card
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS
 A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
A System and Trac Dependent Adaptive Routing. Algorithm for Ad Hoc Networks 1. neighbor which leads to a shortest path to the destination.
 A System and Trac Dependent Adaptive Routing Algorithm for Ad Hoc Networks 1 Piyush Gupta 2 and P. R. Kumar 3 Abstract An ad hoc network consists of a number of mobile hosts who communicate with each other
A System and Trac Dependent Adaptive Routing Algorithm for Ad Hoc Networks 1 Piyush Gupta 2 and P. R. Kumar 3 Abstract An ad hoc network consists of a number of mobile hosts who communicate with each other
Dynamic Search Technique Used for Improving Passive Source Routing Protocol in Manet
 African Journal of Basic & Applied Sciences 9 (1): 27-32, 2017 ISSN 2079-2034 IDOSI Publications, 2017 DOI: 10.5829/idosi.ajbas.2017.27.32 Dynamic Search Technique Used for Improving Passive Source Routing
African Journal of Basic & Applied Sciences 9 (1): 27-32, 2017 ISSN 2079-2034 IDOSI Publications, 2017 DOI: 10.5829/idosi.ajbas.2017.27.32 Dynamic Search Technique Used for Improving Passive Source Routing
Design and Implementation of a Simulator for Ad Hoc Network Routing Protocols
 Design and Implementation of a Simulator for Ad Hoc Network Routing Protocols Mudit, Sachin Chaudhary Abstract In consideration of adaptability to the environment and flexibility in protocol construction,
Design and Implementation of a Simulator for Ad Hoc Network Routing Protocols Mudit, Sachin Chaudhary Abstract In consideration of adaptability to the environment and flexibility in protocol construction,
Mobile Communications. Ad-hoc and Mesh Networks
 Ad-hoc+mesh-net 1 Mobile Communications Ad-hoc and Mesh Networks Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto Ad-hoc+mesh-net 2 What is an ad-hoc network? What are differences between
Ad-hoc+mesh-net 1 Mobile Communications Ad-hoc and Mesh Networks Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto Ad-hoc+mesh-net 2 What is an ad-hoc network? What are differences between
Charles Perkins Nokia Research Center 2 July Mobility Support in IPv6 <draft-ietf-mobileip-ipv6-14.txt> Status of This Memo
 IETF Mobile IP Working Group INTERNET-DRAFT David B. Johnson Rice University Charles Perkins Nokia Research Center 2 July 2000 Mobility Support in IPv6 Status of This
IETF Mobile IP Working Group INTERNET-DRAFT David B. Johnson Rice University Charles Perkins Nokia Research Center 2 July 2000 Mobility Support in IPv6 Status of This
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s
 Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Handover Management for Mobile Nodes in IPv6 Networks
 TECHNOLOGY ADVANCES FOR 3G AND BEYOND Handover Management for Mobile Nodes in IPv6 Networks Nicolas Montavont and Thomas Noël LSIIT Louis Pasteur University CNRS, Strasbourg ABSTRACT In this article we
TECHNOLOGY ADVANCES FOR 3G AND BEYOND Handover Management for Mobile Nodes in IPv6 Networks Nicolas Montavont and Thomas Noël LSIIT Louis Pasteur University CNRS, Strasbourg ABSTRACT In this article we
Zone-based Proactive Source Routing Protocol for Ad-hoc Networks
 2014 IJSRSET Volume i Issue i Print ISSN : 2395-1990 Online ISSN : 2394-4099 Themed Section: Science Zone-based Proactive Source Routing Protocol for Ad-hoc Networks Dr.Sangheethaa.S 1, Dr. Arun Korath
2014 IJSRSET Volume i Issue i Print ISSN : 2395-1990 Online ISSN : 2394-4099 Themed Section: Science Zone-based Proactive Source Routing Protocol for Ad-hoc Networks Dr.Sangheethaa.S 1, Dr. Arun Korath
Performance Evaluation Of Ad-Hoc On Demand Routing Protocol (AODV) Using NS-3 Simulator
 Performance Evaluation Of Ad-Hoc On Demand Routing Protocol (AODV) Using NS-3 Simulator Dr. S. K. Singh Professor, Department of EC, India Dr. R. Gupta Asst. Prof. Department of EC, India Abstract: The
Performance Evaluation Of Ad-Hoc On Demand Routing Protocol (AODV) Using NS-3 Simulator Dr. S. K. Singh Professor, Department of EC, India Dr. R. Gupta Asst. Prof. Department of EC, India Abstract: The
Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol
 Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol V.S.Chaudhari 1, Prof.P.N.Matte 2, Prof. V.P.Bhope 3 Department of E&TC, Raisoni College of Engineering, Ahmednagar Abstract:-
Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol V.S.Chaudhari 1, Prof.P.N.Matte 2, Prof. V.P.Bhope 3 Department of E&TC, Raisoni College of Engineering, Ahmednagar Abstract:-
Reducing Router-Crossings in a Mobile Intranet. Ibrahim Korpeoglu Rohit Dube Satish K. Tripathi. University of Maryland. College Park, MD 20742
 Reducing Router-Crossings in a Mobile Intranet Ibrahim Korpeoglu Rohit Dube Satish K. Tripathi Mobile Computing and Multimedia Laboratory University of Maryland College Park, MD 20742 fkorpe,rohit,tripathig@cs.umd.edu
Reducing Router-Crossings in a Mobile Intranet Ibrahim Korpeoglu Rohit Dube Satish K. Tripathi Mobile Computing and Multimedia Laboratory University of Maryland College Park, MD 20742 fkorpe,rohit,tripathig@cs.umd.edu
Content. 1. Introduction. 2. The Ad-hoc On-Demand Distance Vector Algorithm. 3. Simulation and Results. 4. Future Work. 5.
 Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Fixed Internetworking Protocols and Networks. IP mobility. Rune Hylsberg Jacobsen Aarhus School of Engineering
 Fixed Internetworking Protocols and Networks IP mobility Rune Hylsberg Jacobsen Aarhus School of Engineering rhj@iha.dk 1 2011 ITIFN Mobile computing Vision Seamless, ubiquitous network access for mobile
Fixed Internetworking Protocols and Networks IP mobility Rune Hylsberg Jacobsen Aarhus School of Engineering rhj@iha.dk 1 2011 ITIFN Mobile computing Vision Seamless, ubiquitous network access for mobile
A Performance Comparison of MDSDV with AODV and DSDV Routing Protocols
 A Performance Comparison of MDSDV with AODV and DSDV Routing Protocols A. Etorban Peter J.B King Phil Trinder etorban@macs.hw.ac.uk pjbk@macs.hw.ac.uk P.W.Trinder@hw.ac.uk School of Mathematical and Computer
A Performance Comparison of MDSDV with AODV and DSDV Routing Protocols A. Etorban Peter J.B King Phil Trinder etorban@macs.hw.ac.uk pjbk@macs.hw.ac.uk P.W.Trinder@hw.ac.uk School of Mathematical and Computer
Contents. Configuring MSDP 1
 Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
IJMIE Volume 2, Issue 9 ISSN:
 PERFORMANCE ANALYSIS OF DSDV WITH OTHER MANET ROUTING PROTOCOL USING RANDOM WAYPOINT MOBILITY MODEL IN NS-3 Saurabh kumar soni* Prof.Prem Narayan Arya* ABSTRACT Routing protocols are a critical aspect
PERFORMANCE ANALYSIS OF DSDV WITH OTHER MANET ROUTING PROTOCOL USING RANDOM WAYPOINT MOBILITY MODEL IN NS-3 Saurabh kumar soni* Prof.Prem Narayan Arya* ABSTRACT Routing protocols are a critical aspect
An Enhancement of Mobile IP by Home Agent Handover
 An Enhancement of Mobile IP by Home Agent Handover Li-Sheng Yu and Chun-Chuan Yang Multimedia and Communications Laboratory Department of Computer Science and Information Engineering National Chi Nan University,
An Enhancement of Mobile IP by Home Agent Handover Li-Sheng Yu and Chun-Chuan Yang Multimedia and Communications Laboratory Department of Computer Science and Information Engineering National Chi Nan University,
Routing Protocols in MANET: Comparative Study
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 7, July 2014, pg.119
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 7, July 2014, pg.119
Abstract 1.1. OVERVIEW
 Operation of Dynamic Source Routing in Wireless Mobile Ad Hoc Networks Kestina Rai 1, Rubinder Kaur 2, Kanchan Aggarwal CSE/IT Department, PTU Chandigarh Engineering College, Landran(Punjab) cupids2@rediffmail.com,rubykhokhar@gmail.com
Operation of Dynamic Source Routing in Wireless Mobile Ad Hoc Networks Kestina Rai 1, Rubinder Kaur 2, Kanchan Aggarwal CSE/IT Department, PTU Chandigarh Engineering College, Landran(Punjab) cupids2@rediffmail.com,rubykhokhar@gmail.com
A Survey of Routing Protocols for Ad Hoc Wireless Home Networks
 International Journal of Electronics and Computer Science Engineering 52 Available Online at www.ijecse.org ISSN-2277-1956 A Survey of Routing Protocols for Ad Hoc Wireless Home Networks Meenakshi Chaturvedi
International Journal of Electronics and Computer Science Engineering 52 Available Online at www.ijecse.org ISSN-2277-1956 A Survey of Routing Protocols for Ad Hoc Wireless Home Networks Meenakshi Chaturvedi
Behaviour of Routing Protocols of Mobile Adhoc Netwok with Increasing Number of Groups using Group Mobility Model
 Behaviour of Routing Protocols of Mobile Adhoc Netwok with Increasing Number of Groups using Group Mobility Model Deepak Agrawal, Brajesh Patel Department of CSE Shri Ram Institute of Technology Jabalpur,
Behaviour of Routing Protocols of Mobile Adhoc Netwok with Increasing Number of Groups using Group Mobility Model Deepak Agrawal, Brajesh Patel Department of CSE Shri Ram Institute of Technology Jabalpur,
SJTU 2018 Fall Computer Networking. Wireless Communication
 SJTU 2018 Fall Computer Networking 1 Wireless Communication Internet Protocol Stack 2 Application: supporting network applications - FTP, SMTP, HTTP Transport: data transfer between processes - TCP, UDP
SJTU 2018 Fall Computer Networking 1 Wireless Communication Internet Protocol Stack 2 Application: supporting network applications - FTP, SMTP, HTTP Transport: data transfer between processes - TCP, UDP
Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8]
![Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8]](/thumbs/92/110300020.jpg) 192620010 Mobile & Wireless Networking Lecture 10: Mobile Transport Layer & Ad Hoc Networks [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Geert Heijenk Outline of Lecture 10 Mobile transport layer
192620010 Mobile & Wireless Networking Lecture 10: Mobile Transport Layer & Ad Hoc Networks [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Geert Heijenk Outline of Lecture 10 Mobile transport layer
Performance Analysis of Hierarchical Mobile IPv6 in IP-based Cellular Networks
 Performance Analysis of Hierarchical Mobile IPv6 in IP-based Cellular Networks Sangheon Pack and Yanghee Choi School of Computer Science & Engineering Seoul National University Seoul, Korea Abstract Next-generation
Performance Analysis of Hierarchical Mobile IPv6 in IP-based Cellular Networks Sangheon Pack and Yanghee Choi School of Computer Science & Engineering Seoul National University Seoul, Korea Abstract Next-generation
WSN Routing Protocols
 WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
IP Multicast Technology Overview
 IP multicast is a bandwidth-conserving technology that reduces traffic by delivering a single stream of information simultaneously to potentially thousands of businesses and homes. Applications that take
IP multicast is a bandwidth-conserving technology that reduces traffic by delivering a single stream of information simultaneously to potentially thousands of businesses and homes. Applications that take
Mr. Pradip A. Chougule 1, Mr. Rajesh A. Sanadi 2, Mr. U. H.Kamble 3
 IOSR Journal of Computer Engineering (IOSR-JCE) ISSN: 2278-0661, ISBN: 2278-8727, PP: 01-05 www.iosrjournals.org COMPARATIVE STUDY OF TABLE DRIVEN ROUTING PROTOCOLS IN AD HOC WIRELESS NETWORKS Mr. Pradip
IOSR Journal of Computer Engineering (IOSR-JCE) ISSN: 2278-0661, ISBN: 2278-8727, PP: 01-05 www.iosrjournals.org COMPARATIVE STUDY OF TABLE DRIVEN ROUTING PROTOCOLS IN AD HOC WIRELESS NETWORKS Mr. Pradip
Wireless Mesh Networks
 Wireless Mesh Networks COS 463: Wireless Networks Lecture 6 Kyle Jamieson [Parts adapted from I. F. Akyildiz, B. Karp] Wireless Mesh Networks Describes wireless networks in which each node can communicate
Wireless Mesh Networks COS 463: Wireless Networks Lecture 6 Kyle Jamieson [Parts adapted from I. F. Akyildiz, B. Karp] Wireless Mesh Networks Describes wireless networks in which each node can communicate
Analysis of Black-Hole Attack in MANET using AODV Routing Protocol
 Analysis of Black-Hole Attack in MANET using Routing Protocol Ms Neha Choudhary Electronics and Communication Truba College of Engineering, Indore India Dr Sudhir Agrawal Electronics and Communication
Analysis of Black-Hole Attack in MANET using Routing Protocol Ms Neha Choudhary Electronics and Communication Truba College of Engineering, Indore India Dr Sudhir Agrawal Electronics and Communication
II. Principles of Computer Communications Network and Transport Layer
 II. Principles of Computer Communications Network and Transport Layer A. Internet Protocol (IP) IPv4 Header An IP datagram consists of a header part and a text part. The header has a 20-byte fixed part
II. Principles of Computer Communications Network and Transport Layer A. Internet Protocol (IP) IPv4 Header An IP datagram consists of a header part and a text part. The header has a 20-byte fixed part
IP Mobility vs. Session Mobility
 IP Mobility vs. Session Mobility Securing wireless communication is a formidable task, something that many companies are rapidly learning the hard way. IP level solutions become extremely cumbersome when
IP Mobility vs. Session Mobility Securing wireless communication is a formidable task, something that many companies are rapidly learning the hard way. IP level solutions become extremely cumbersome when
DSR: The Dynamic Source Routing Protocol for Multi-Hop Wireless Ad Hoc Networks
 DSR: The Dynamic Source Routing Protocol for Multi-Hop Wireless Ad Hoc Networks David B. Johnson David A. Maltz Josh Broch Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213-3891
DSR: The Dynamic Source Routing Protocol for Multi-Hop Wireless Ad Hoc Networks David B. Johnson David A. Maltz Josh Broch Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213-3891
Active source routing for ad-hoc network: seamless integration of wireless environment
 Active source routing for ad-hoc network: seamless integration of wireless environment 1. Introduction Active networking is the emerging technology that will provide new network environment where lots
Active source routing for ad-hoc network: seamless integration of wireless environment 1. Introduction Active networking is the emerging technology that will provide new network environment where lots
Network Layer (4): ICMP
 1 Network Layer (4): ICMP Required reading: Kurose 4.4.3, 4.4.4 CSE 4213, Fall 2006 Instructor: N. Vlajic 2 1. Introduction 2. Network Service Models 3. Architecture 4. Network Layer Protocols in the Internet
1 Network Layer (4): ICMP Required reading: Kurose 4.4.3, 4.4.4 CSE 4213, Fall 2006 Instructor: N. Vlajic 2 1. Introduction 2. Network Service Models 3. Architecture 4. Network Layer Protocols in the Internet
Mobile IP Overview. Based on IP so any media that can support IP can also support Mobile IP
 Introduction: Mobile IP Overview An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet
Introduction: Mobile IP Overview An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet
STUDY ON MOBILE ADHOC NETWORK ROUTING PROTOCOLS
 International Journal of Information Technology and Knowledge Management January-June 2012, Volume 5, No. 1, pp. 155-158 STUDY ON MOBILE ADHOC NETWORK ROUTING PROTOCOLS Monika ABSTRACT: In Many wireless
International Journal of Information Technology and Knowledge Management January-June 2012, Volume 5, No. 1, pp. 155-158 STUDY ON MOBILE ADHOC NETWORK ROUTING PROTOCOLS Monika ABSTRACT: In Many wireless
G.Narasa Reddy, 2 A.Avanthi, 3 R.Prasanth Reddy 1
 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: Enhancing DSR Protocol Performance in Mobile Ad Hoc Networks
ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: Enhancing DSR Protocol Performance in Mobile Ad Hoc Networks
Subject: Adhoc Networks
 ISSUES IN AD HOC WIRELESS NETWORKS The major issues that affect the design, deployment, & performance of an ad hoc wireless network system are: Medium Access Scheme. Transport Layer Protocol. Routing.
ISSUES IN AD HOC WIRELESS NETWORKS The major issues that affect the design, deployment, & performance of an ad hoc wireless network system are: Medium Access Scheme. Transport Layer Protocol. Routing.
White Paper. Mobile Ad hoc Networking (MANET) with AODV. Revision 1.0
 White Paper Mobile Ad hoc Networking (MANET) with AODV Revision 1.0 This page is intentionally blank, or rather nearly blank. Table of Contents TABLE OF CONTENTS...3 TABLE OF FIGURES...4 WHAT IS MANET?...5
White Paper Mobile Ad hoc Networking (MANET) with AODV Revision 1.0 This page is intentionally blank, or rather nearly blank. Table of Contents TABLE OF CONTENTS...3 TABLE OF FIGURES...4 WHAT IS MANET?...5
Ad Hoc Routing. Ad-hoc Routing. Problems Using DV or LS. DSR Concepts. DSR Components. Proposed Protocols
 d oc Routing d-hoc Routing rvind Krishnamurthy all 2003 Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
d oc Routing d-hoc Routing rvind Krishnamurthy all 2003 Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
What is Multicasting? Multicasting Fundamentals. Unicast Transmission. Agenda. L70 - Multicasting Fundamentals. L70 - Multicasting Fundamentals
 What is Multicasting? Multicasting Fundamentals Unicast transmission transmitting a packet to one receiver point-to-point transmission used by most applications today Multicast transmission transmitting
What is Multicasting? Multicasting Fundamentals Unicast transmission transmitting a packet to one receiver point-to-point transmission used by most applications today Multicast transmission transmitting
Beacon Update for Greedy Perimeter Stateless Routing Protocol in MANETs
 Beacon Update for Greedy erimeter Stateless Routing rotocol in MANETs Abstract Dhanarasan 1, Gopi S 2 1 M.E/CSE Muthayammal Engineering College, getdhanarasan@gmail.com 2 Assistant rofessor / IT Muthayammal
Beacon Update for Greedy erimeter Stateless Routing rotocol in MANETs Abstract Dhanarasan 1, Gopi S 2 1 M.E/CSE Muthayammal Engineering College, getdhanarasan@gmail.com 2 Assistant rofessor / IT Muthayammal
2013, IJARCSSE All Rights Reserved Page 85
 Volume 3, Issue 12, December 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Overview of
Volume 3, Issue 12, December 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Overview of
Variable Length and Dynamic Addressing for Mobile Ad Hoc Networks
 Variable Length and Dynamic Addressing for Mobile Ad Hoc Networks Som Chandra Neema Venkata Nishanth Lolla {sneema,vlolla}@cs.ucr.edu Computer Science Department University of California, Riverside Abstract
Variable Length and Dynamic Addressing for Mobile Ad Hoc Networks Som Chandra Neema Venkata Nishanth Lolla {sneema,vlolla}@cs.ucr.edu Computer Science Department University of California, Riverside Abstract
Preemptive Multicast Routing in Mobile Ad-hoc Networks
 Preemptive Multicast Routing in Mobile Ad-hoc Networks Uyen Trang Nguyen and Xing Xiong Department of Computer Science and Engineering York University, Toronto, Ontario Canada, M3J 1P3 Email: {utn, xing}@cs.yorku.ca
Preemptive Multicast Routing in Mobile Ad-hoc Networks Uyen Trang Nguyen and Xing Xiong Department of Computer Science and Engineering York University, Toronto, Ontario Canada, M3J 1P3 Email: {utn, xing}@cs.yorku.ca
Mobile host protocols support host
 INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT Int. J. Network Mgmt 2000; 10:191 214 Location update and routing scheme for a mobile computing environment By Anna Hać Ł and Yujing Huang We present a new hierarchical
INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT Int. J. Network Mgmt 2000; 10:191 214 Location update and routing scheme for a mobile computing environment By Anna Hać Ł and Yujing Huang We present a new hierarchical
Shortcut Tree Routing using Neighbor Table in ZigBee Wireless Networks
 Shortcut Tree Routing using Neighbor Table in ZigBee Wireless Networks Salmu K.P 1, Chinchu James 2 1,2 Department of Computer Science, IIET, Nellikuzhi Abstract- ZigBee is a worldwide standard for wireless
Shortcut Tree Routing using Neighbor Table in ZigBee Wireless Networks Salmu K.P 1, Chinchu James 2 1,2 Department of Computer Science, IIET, Nellikuzhi Abstract- ZigBee is a worldwide standard for wireless
CIS 632 / EEC 687 Mobile Computing
 CIS 632 / EEC 687 Mobile Computing TCP in Mobile Networks Prof. Chansu Yu Contents Physical layer issues Communication frequency Signal propagation Modulation and Demodulation Channel access issues Multiple
CIS 632 / EEC 687 Mobile Computing TCP in Mobile Networks Prof. Chansu Yu Contents Physical layer issues Communication frequency Signal propagation Modulation and Demodulation Channel access issues Multiple
Performance Evaluation of MANET through NS2 Simulation
 International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 25-30 International Research Publication House http://www.irphouse.com Performance Evaluation
International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 25-30 International Research Publication House http://www.irphouse.com Performance Evaluation
Volume 3, Issue 6, June 2015 International Journal of Advance Research in Computer Science and Management Studies
 Volume 3, Issue 6, June 2015 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at: www.ijarcsms.com Analysis
Volume 3, Issue 6, June 2015 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at: www.ijarcsms.com Analysis
Mobile IP and Mobile Transport Protocols
 Mobile IP and Mobile Transport Protocols 1 IP routing Preliminaries Works on a hop-by-hop basis using a routing table 32 bits: 129.97.92.42 Address = subnet + host (Mobility No packet for you) Two parts»
Mobile IP and Mobile Transport Protocols 1 IP routing Preliminaries Works on a hop-by-hop basis using a routing table 32 bits: 129.97.92.42 Address = subnet + host (Mobility No packet for you) Two parts»
A Performance Comparison of Multicast Routing Protocols In Ad hoc Networks
 A Performance Comparison of Multicast Routing Protocols In Ad hoc Networks Hasnaa MOUSTAFA and Houda LABIOD ENST - INFRES Department - 46 Rue Barrault 75634 Paris cedex 3 Paris - France Tel: +33 ().45.8.74.36
A Performance Comparison of Multicast Routing Protocols In Ad hoc Networks Hasnaa MOUSTAFA and Houda LABIOD ENST - INFRES Department - 46 Rue Barrault 75634 Paris cedex 3 Paris - France Tel: +33 ().45.8.74.36
Network Layer: Routing
 Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
Current Project Work on Routing Protocols for MANET: A Literature Survey Mr. Chethan Chandra S Basavaraddi, Smt. Geetha N.B. M.Tech.
 International Journal of Scientific & Engineering Research Volume 3, Issue 5, May-2012 1 Current Project Work on Routing Protocols for MANET: A Literature Survey Mr. Chethan Chandra S Basavaraddi, Smt.
International Journal of Scientific & Engineering Research Volume 3, Issue 5, May-2012 1 Current Project Work on Routing Protocols for MANET: A Literature Survey Mr. Chethan Chandra S Basavaraddi, Smt.
ICS 351: Today's plan. distance-vector routing game link-state routing OSPF
 ICS 351: Today's plan distance-vector routing game link-state routing OSPF distance-vector routing game 1. prepare a list of all neighbors and the links to them, and the metric for each link 2. create
ICS 351: Today's plan distance-vector routing game link-state routing OSPF distance-vector routing game 1. prepare a list of all neighbors and the links to them, and the metric for each link 2. create
CS 5520/ECE 5590NA: Network Architecture I Spring Lecture 13: UDP and TCP
 CS 5520/ECE 5590NA: Network Architecture I Spring 2008 Lecture 13: UDP and TCP Most recent lectures discussed mechanisms to make better use of the IP address space, Internet control messages, and layering
CS 5520/ECE 5590NA: Network Architecture I Spring 2008 Lecture 13: UDP and TCP Most recent lectures discussed mechanisms to make better use of the IP address space, Internet control messages, and layering
Routing Protocols in Mobile Ad-Hoc Network
 International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
EFFECT OF ROUTING PROTOCOLS OVER RENOVATED CONGESTION CONTROL MECHANISMS IN SINGLE-HOP WIRELESS
 EFFECT OF ROUTING PROTOCOLS OVER RENOVATED CONGESTION CONTROL MECHANISMS IN SINGLE-HOP WIRELESS 1 TANMAYA SWAIN, 2 PRASANT KUMAR PATTNAIK School Of Computer Engineering, KIIT University, Bhubaneswar E-mail:
EFFECT OF ROUTING PROTOCOLS OVER RENOVATED CONGESTION CONTROL MECHANISMS IN SINGLE-HOP WIRELESS 1 TANMAYA SWAIN, 2 PRASANT KUMAR PATTNAIK School Of Computer Engineering, KIIT University, Bhubaneswar E-mail:
