What s Cool About the CONNECT Command in RACF
|
|
|
- Francine Howard
- 5 years ago
- Views:
Transcription
1 What s Cool About the CONNECT Command in RACF Stu Henderson stu@stuhenderson.com 5702 Newington Road Bethesda, MD (301)
2 AGENDA 2 1. We all know the CONNECT command 2. What is in 3. Why use 4. Summary and Call to Action
3 We all know the CONNECT command 3 The CONNECT command CO USER02 GROUP(GROUPA) is used to connect a User to a Group
4 We all know the CONNECT command 4 The REMOVE command (opposite of CONNECT) RE USER02 GROUP(GROUPA) is used to remove a User from a Group
5 5 User profile has groups the user belongs to Group profile has users in the group USER02 Profile Member of: GROUPA Profile User Members:
6 6 The CONNECT command puts the group name in User Profile and the user name in Group Profile CO USER02 GROUP(GROUPA) USER02 Profile Member of: GROUPA GROUPA Profile User Members: USER02
7 7 The CONNECT command may include additional connection information about how the User relates to the Group CO USER02 GROUP(GROUPA) connection info USER02 Profile Member of: GROUPA addt l connection info GROUPA Profile User Members: USER02 addt l connection info
8 8 UserID and Group Name UACC AUTH Group Attributes, aka Connect Attributes
9 9 UACC in CONNECT INFO Safely ignored Let it default to NONE Stored in ACEE Used only for certain resource classes when creating a new profile and you forget to specify the UACC (See DSMON Class Descriptor Table under UACC)
10 10 AUTH in CONNECT INFO JOIN (can create new sub-groups under the group, and (with CLAUTH(USER) new userids in the group) CONNECT (can connect / remove others to the group) CREATE (can create dataset rule with groupname as HLQ) USE (just a member)
11 11 Group Attributes in CONNECT INFO Any of: SPECIAL, OPERATIONS, AUDIT, REVOKE, GRPACC Gives the privilege in the group And all the groups it owns And all the groups they own
12 12 Group Attributes in CONNECT INFO So in DSMON, Selected User Attribute Report, you see that USER02 has Group-SPECIAL in GROUPA You LISTUSER USER02 to see which group(s) You find those groups in DSMON, Group Tree Report
13 13 Find all the groups they own by following down the vertical lines in the Group Tree Report And the groups they own, and so on
14 14 Each group is owned by either a userid or a group. If a group, it must be the superior group, which is connected to it by a vertical line When a group has a name in parentheses to the right of the group name in the Group Tree Report, that s the name of the userid that owns the group When a group is owned by a userid, then the trickle-down stops with the group
15 15 Two Phases: 1. List all the groups which the group owns, all the groups they own, on down the tree, as long as a group owns a group owns a group 2. List every profile owned by these groups, plus dataset profiles with these as HLQs That s the scope of the group attribute
16 Why use 16 Delegation of Authority Famous Nome-Honolulu Principle AUTH gives authority just within the group Group-SPECIAL gives authority in the group, and all down the tree from there
17 Why use 17 AUTH is great for RBAC (Role Base Access Control) You permit the group where it needs and use AUTH(CONNECT) to let someone else just connect and remove for the group. He can t mess up your permit lists. To learn AUTHs greater than USE, //S1 EXEC RACFICE,REPORT=UADS
18 Group-SPECIAL 18 Is like having your userid be the owner of a profile: it lets you alter or delete it For the Help Desk, better to use FACILITY class rules named IRR.PASSWORD to delegate the ability to administer passwords and revoke/resume
19 Summary / Call to Action 19 Don t let your RACF implementation permit things you don t understand Map out your delegation of authority: who has AUTH above USE, who has group-attributes, who has CLAUTH, who has SPECIAL Then you know how to make it secure If not you, then who?
20 For More Information 20 RACF User News (back issues & subscribe) Articles on mainframe security and audit Thanks for Your Kind Attention. Questions to Stu Henderson (301)
How to Go About Setting Mainframe Security Options
 How to Go About Setting Mainframe Security Options Stu Henderson stu@stuhenderson.com 5702 Newington Road Bethesda, MD 20816 www.stuhenderson.com (301) 229-7187 ABSTRACT 2 If you don't think that checklists
How to Go About Setting Mainframe Security Options Stu Henderson stu@stuhenderson.com 5702 Newington Road Bethesda, MD 20816 www.stuhenderson.com (301) 229-7187 ABSTRACT 2 If you don't think that checklists
MANEWS Issue Number 21 the Mainframe Audit News
 This newsletter tells you stuff you need to know to audit IBM mainframe computers runinng with z/os and the MVS operating system. This issue we show you how to plan the data gathering for your audit. Table
This newsletter tells you stuff you need to know to audit IBM mainframe computers runinng with z/os and the MVS operating system. This issue we show you how to plan the data gathering for your audit. Table
Eleven Steps to Make Mainframe Security Audits More Effective and Efficient
 Eleven Steps to Make Mainframe Security Audits More Effective and Efficient These are some things I ve learned about auditing IBM mainframe computers by trying a lot of approaches, some of which worked
Eleven Steps to Make Mainframe Security Audits More Effective and Efficient These are some things I ve learned about auditing IBM mainframe computers by trying a lot of approaches, some of which worked
Tutorial: Lessons From A Real Mainframe Break-In Over the Internet
 Tutorial: Lessons From A Real Mainframe Break-In Over the Internet Stu Henderson 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 STU@STUHENDERSON.COM What You ll Hear Today Brief comments on why
Tutorial: Lessons From A Real Mainframe Break-In Over the Internet Stu Henderson 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 STU@STUHENDERSON.COM What You ll Hear Today Brief comments on why
New Security Options in DB2 for z/os Release 9 and 10
 New Security Options in DB2 for z/os Release 9 and 10 IBM has added several security improvements for DB2 (IBM s mainframe strategic database software) in these releases. Both Data Security Officers and
New Security Options in DB2 for z/os Release 9 and 10 IBM has added several security improvements for DB2 (IBM s mainframe strategic database software) in these releases. Both Data Security Officers and
Top 12 Mainframe Security Exposures and Lessons From A Real Mainframe Break-In
 Top 12 Mainframe Security Exposures and Lessons From A Real Mainframe Break-In Stu Henderson 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 STU@STUHENDERSON.COM What You ll Hear One Person s Experiences
Top 12 Mainframe Security Exposures and Lessons From A Real Mainframe Break-In Stu Henderson 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 STU@STUHENDERSON.COM What You ll Hear One Person s Experiences
Review of RACF SETROPTS
 Review of RACF SETROPTS (A Brief Tutorial) the Henderson Group 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 Abstract The SETROPTS command in RACF (mainframe computer security software) is where
Review of RACF SETROPTS (A Brief Tutorial) the Henderson Group 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 Abstract The SETROPTS command in RACF (mainframe computer security software) is where
Performing a z/os Vulnerability Assessment. Part 2 - Data Analysis. Presented by Vanguard Integrity Professionals
 Performing a z/os Vulnerability Assessment Part 2 - Data Analysis Presented by Vanguard Integrity Professionals Legal Notice Copyright 2014 Vanguard Integrity Professionals - Nevada. All Rights Reserved.
Performing a z/os Vulnerability Assessment Part 2 - Data Analysis Presented by Vanguard Integrity Professionals Legal Notice Copyright 2014 Vanguard Integrity Professionals - Nevada. All Rights Reserved.
What's Missing in Mainframe InfoSec: (What We Don't Know We Don't Know)"
 What's Missing in Mainframe InfoSec: (What We Don't Know We Don't Know)" Stu Henderson stu@stuhenderson.com 5702 Newington Road www.stuhenderson.com Bethesda, MD 20816 (301) 229-7187 ABSTRACT 2 In this
What's Missing in Mainframe InfoSec: (What We Don't Know We Don't Know)" Stu Henderson stu@stuhenderson.com 5702 Newington Road www.stuhenderson.com Bethesda, MD 20816 (301) 229-7187 ABSTRACT 2 In this
=============================================== ===============================================
 M A News Mainframe Audit News January, 2005 Issue Number 06 Table of Contents 1. Introducing the Mainframe Audit News 2. Managing Your Audit Planning Through Your View of the Mainframe 3. New Developments
M A News Mainframe Audit News January, 2005 Issue Number 06 Table of Contents 1. Introducing the Mainframe Audit News 2. Managing Your Audit Planning Through Your View of the Mainframe 3. New Developments
Performing a z/os Vulnerability Assessment. Part 3 - Remediation. Presented by Vanguard Integrity Professionals
 Performing a z/os Vulnerability Assessment Part 3 - Remediation Presented by Vanguard Integrity Professionals Legal Notice Copyright 2014 Vanguard Integrity Professionals - Nevada. All Rights Reserved.
Performing a z/os Vulnerability Assessment Part 3 - Remediation Presented by Vanguard Integrity Professionals Legal Notice Copyright 2014 Vanguard Integrity Professionals - Nevada. All Rights Reserved.
Post exploit goodness on a Mainframe
 Post exploit goodness on a Mainframe SPECIAL is the new root Ayoub ELAASSAL @ayoul3 Github.com/ayoul3 What I picture when talking about Mainframes What people picture when I talk about Mainframes In 2017
Post exploit goodness on a Mainframe SPECIAL is the new root Ayoub ELAASSAL @ayoul3 Github.com/ayoul3 What I picture when talking about Mainframes What people picture when I talk about Mainframes In 2017
The Old is New Again Engineering Security in the Age of Data Access from Anywhere
 The Old is New Again Engineering Security in the Age of Data Access from Anywhere Paul de Graaff Chief Strategy Officer Vanguard Integrity Professionals March 10, 2014 Session 14971 AGENDA History 1 This
The Old is New Again Engineering Security in the Age of Data Access from Anywhere Paul de Graaff Chief Strategy Officer Vanguard Integrity Professionals March 10, 2014 Session 14971 AGENDA History 1 This
CARLa programming how was it again? 2013 IBM Corp.
 CARLa programming how was it again? Tom Zeehandelaar zsecure enablement specialist tom.zeehandelaar@nl.ibm.com Jeroen Tiggelman Software Development/L3 Manager zsecure Jeroen.Tiggelman@nl.ibm.com Agenda
CARLa programming how was it again? Tom Zeehandelaar zsecure enablement specialist tom.zeehandelaar@nl.ibm.com Jeroen Tiggelman Software Development/L3 Manager zsecure Jeroen.Tiggelman@nl.ibm.com Agenda
RSA Ready Implementation Guide for
 RSA Ready Implementation Guide for IBM Multi-Factor Authentication for z/os V1R1 John Sammon, RSA Partner Engineering Last Modified: 4/7/16 -- 1 - Solution Summary IBM Multi-Factor Authentication for z/os,
RSA Ready Implementation Guide for IBM Multi-Factor Authentication for z/os V1R1 John Sammon, RSA Partner Engineering Last Modified: 4/7/16 -- 1 - Solution Summary IBM Multi-Factor Authentication for z/os,
MANEWS 01 ========================================== ==========================================
 ========================================== ========================================== M A News Mainframe Audit News October, 2001 Issue Number 01 Table of Contents I N T H I S I S S U E 1) Introducing
========================================== ========================================== M A News Mainframe Audit News October, 2001 Issue Number 01 Table of Contents I N T H I S I S S U E 1) Introducing
Implementation of RBAC and Data Classification
 Implementation of RBAC and Data Classification Steve Tresadern Rui Miguel Feio RSM Partners December 2014 v1.7 Agenda Introductions Data Classification & Ownership Role-Based Access Control (RBAC) Maintain
Implementation of RBAC and Data Classification Steve Tresadern Rui Miguel Feio RSM Partners December 2014 v1.7 Agenda Introductions Data Classification & Ownership Role-Based Access Control (RBAC) Maintain
RACF Grouping Class Profiles
 RACF Grouping Class Profiles RSH CONSULTING, INC. RACF SPECIALISTS 617 969 9050 WWW.RSHCONSULTING.COM RSH Consulting Robert S. Hansel RSH Consulting, Inc. is an IT security professional services firm established
RACF Grouping Class Profiles RSH CONSULTING, INC. RACF SPECIALISTS 617 969 9050 WWW.RSHCONSULTING.COM RSH Consulting Robert S. Hansel RSH Consulting, Inc. is an IT security professional services firm established
Migrating from CA Top Secret to RACF: A User Experience
 BY CHUCK CLAY Migrating from CA Top Secret to RACF: A User Experience More and more shops are deciding, for whatever reason, to migrate from Computer Associates Top Secret to IBM s RACF. However, there
BY CHUCK CLAY Migrating from CA Top Secret to RACF: A User Experience More and more shops are deciding, for whatever reason, to migrate from Computer Associates Top Secret to IBM s RACF. However, there
Security Administration Form erepository (SAFE) User s Guide. Version 3.0
 Security Administration Form erepository (SAFE) User s Guide Version 3.0 Copyright 2018, All rights reserved. Reproduction in whole or in part is prohibited without the prior written consent of the copyright
Security Administration Form erepository (SAFE) User s Guide Version 3.0 Copyright 2018, All rights reserved. Reproduction in whole or in part is prohibited without the prior written consent of the copyright
z/secure and usage of XFACILIT CLASS - A sample of ADMIN authorities -
 z/secure and the usage of XFACILIT CLASS 26 June 2013 z/secure and usage of XFACILIT CLASS - A sample of ADMIN authorities - Agenda Short briefing Who am I? - The purpose implementing z/secure ADMIN and
z/secure and the usage of XFACILIT CLASS 26 June 2013 z/secure and usage of XFACILIT CLASS - A sample of ADMIN authorities - Agenda Short briefing Who am I? - The purpose implementing z/secure ADMIN and
IBM Security zsecure. Documentation updates: 64-bit Service Stream Enhancement IBM
 IBM Security zsecure Documentation updates: 64-bit Service Stream Enhancement IBM IBM Security zsecure Documentation updates: 64-bit Service Stream Enhancement IBM ii IBM Security zsecure: Documentation
IBM Security zsecure Documentation updates: 64-bit Service Stream Enhancement IBM IBM Security zsecure Documentation updates: 64-bit Service Stream Enhancement IBM ii IBM Security zsecure: Documentation
Popping a shell on a mainframe, is that even possible?
 Popping a shell on a mainframe, is that even possible? Ayoub ELAASSAL ayoub.elaassal@wavestone.com @ayoul3 WAVESTONE 1 What people think of when I talk about mainframes WAVESTONE 2 The reality: IBM zec
Popping a shell on a mainframe, is that even possible? Ayoub ELAASSAL ayoub.elaassal@wavestone.com @ayoul3 WAVESTONE 1 What people think of when I talk about mainframes WAVESTONE 2 The reality: IBM zec
AGENDA. A New Look at Mainframe Hacking And Penetration Testing 01/11/2016. World Class z Specialists
 World Class z Specialists A New Look at Mainframe Hacking And Penetration Testing Delivering the best in z services, software, hardware and training. AGENDA What is the state of mainframe security? How
World Class z Specialists A New Look at Mainframe Hacking And Penetration Testing Delivering the best in z services, software, hardware and training. AGENDA What is the state of mainframe security? How
Vanguard Active Alerts. Jim McNeill Sr Consultant
 Vanguard Active Alerts Jim McNeill Sr Consultant Legal Notice Copyright All Rights Reserved. You have a limited license to view these materials for your organization s internal purposes. Any unauthorized
Vanguard Active Alerts Jim McNeill Sr Consultant Legal Notice Copyright All Rights Reserved. You have a limited license to view these materials for your organization s internal purposes. Any unauthorized
Guide to My DCC WHAT IS MY DCC? LOGGING IN YOUR PERSONAL HOMEPAGE
 Guide to My DCC WHAT IS MY DCC? Welcome to My DCC! My DCC is the online community of Door Creek Church. It provides an easy and effective way to communicate and connect with groups, staff and others who
Guide to My DCC WHAT IS MY DCC? Welcome to My DCC! My DCC is the online community of Door Creek Church. It provides an easy and effective way to communicate and connect with groups, staff and others who
How to Get Full Security from Security Software and Tape Management Software Together
 How to Get Full Security from Security Software and Tape Management Software Together Monday, August 22, 2005 Session 1714 1:30 Stu Henderson (stu@stuhenderson.com) Russell Witt (russell.witt@ca.com) Abstract
How to Get Full Security from Security Software and Tape Management Software Together Monday, August 22, 2005 Session 1714 1:30 Stu Henderson (stu@stuhenderson.com) Russell Witt (russell.witt@ca.com) Abstract
RACFVARS RUGONE October 2013
 Robert S. Hansel Lead RACF Consultant R.Hansel@rshconsulting.com 617 969 9050 Robert S. Hansel Robert S. Hansel is Lead RACF Specialist and founder of RSH Consulting, Inc., an IT security professional
Robert S. Hansel Lead RACF Consultant R.Hansel@rshconsulting.com 617 969 9050 Robert S. Hansel Robert S. Hansel is Lead RACF Specialist and founder of RSH Consulting, Inc., an IT security professional
Quick Guide Annual User Access Review
 Quick Guide Annual User Access Review Overview For security reasons, managers are responsible for periodically reviewing the account privileges of UPMC staff members who report to them, and validating
Quick Guide Annual User Access Review Overview For security reasons, managers are responsible for periodically reviewing the account privileges of UPMC staff members who report to them, and validating
Understanding Admin Access and RBAC Policies on ISE
 Understanding Admin Access and RBAC Policies on ISE Contents Introduction Prerequisites Requirements Components Used Configure Authentication Settings Configure Admin Groups Configure Admin Users Configure
Understanding Admin Access and RBAC Policies on ISE Contents Introduction Prerequisites Requirements Components Used Configure Authentication Settings Configure Admin Groups Configure Admin Users Configure
MANEWS 04 ========================================== ==========================================
 ========================================== ========================================== M A News Mainframe Audit News February, 2003 Issue Number 04 ========================================== ==========================================
========================================== ========================================== M A News Mainframe Audit News February, 2003 Issue Number 04 ========================================== ==========================================
Secrets of IMS Security
 Secrets of IMS Security June 20, 2014 Maida Snapper maidalee@us.ibm.com Belgium GSE June 2014 5.1 1 Disclaimer Copyright IBM Corporation [current year]. All rights reserved. U.S. Government Users Restricted
Secrets of IMS Security June 20, 2014 Maida Snapper maidalee@us.ibm.com Belgium GSE June 2014 5.1 1 Disclaimer Copyright IBM Corporation [current year]. All rights reserved. U.S. Government Users Restricted
Access Control for Windows NT
 etrust Access Control for Windows NT Administrator Guide 5.1 SP1 This documentation and related computer software program (hereinafter referred to as the Documentation ) is for the end user s informational
etrust Access Control for Windows NT Administrator Guide 5.1 SP1 This documentation and related computer software program (hereinafter referred to as the Documentation ) is for the end user s informational
CSN11111 Network Security
 CSN11111 Network Security Access Control r.ludwiniak@napier.ac.uk Learning Objectives Access Control definition Models Information access control Network based access control AAA Radius Tacacs+ ACCESS
CSN11111 Network Security Access Control r.ludwiniak@napier.ac.uk Learning Objectives Access Control definition Models Information access control Network based access control AAA Radius Tacacs+ ACCESS
Outlook Desktop Application for Windows
 Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
Technical Group Health and Health Interview Survey (HIS) Statistics
 EUROPEAN COMMISSION EUROSTAT Directorate F: Social Statistics and Information Society Unit F-5: Health and food safety statistics Technical Group Health and Health Interview Survey (HIS) Statistics Luxembourg,
EUROPEAN COMMISSION EUROSTAT Directorate F: Social Statistics and Information Society Unit F-5: Health and food safety statistics Technical Group Health and Health Interview Survey (HIS) Statistics Luxembourg,
NOTE: This process is not to be used for Grouping/ Member Classes. Those will be covered in another White Paper.
 How to use Vanguard security products to remove s greater than NONE or READ to create a more secure mainframe RACF database without risking an operational outage due to removing required access. NOTE:
How to use Vanguard security products to remove s greater than NONE or READ to create a more secure mainframe RACF database without risking an operational outage due to removing required access. NOTE:
CIS 5373 Systems Security
 CIS 5373 Systems Security Topic 3.2: OS Security Access Control Endadul Hoque Slide Acknowledgment Contents are based on slides from Ninghui Li (Purdue), John Mitchell (Stanford), Bogdan Carbunar (FIU)
CIS 5373 Systems Security Topic 3.2: OS Security Access Control Endadul Hoque Slide Acknowledgment Contents are based on slides from Ninghui Li (Purdue), John Mitchell (Stanford), Bogdan Carbunar (FIU)
RACF Power Tools Using IRRICE and Rexx on IRRADU00 and IRRDBU00 Part 1 NewEra Software - The z Exchange June 10, 2015
 RACF Power Tools Using IRRICE and Rexx on IRRADU00 and IRRDBU00 Part 1 NewEra Software - The z Exchange June 10, 2015 Thomas Conley Pinnacle Consulting Group, Inc. 59 Applewood Drive Rochester, NY 14612-3501
RACF Power Tools Using IRRICE and Rexx on IRRADU00 and IRRDBU00 Part 1 NewEra Software - The z Exchange June 10, 2015 Thomas Conley Pinnacle Consulting Group, Inc. 59 Applewood Drive Rochester, NY 14612-3501
Performing a z/os Vulnerability Assessment. Part 1 - Data Collection. Presented by Vanguard Integrity Professionals
 Performing a z/os Vulnerability Assessment Part 1 - Data Collection Presented by Vanguard Integrity Professionals Legal Notice Copyright 2014 Vanguard Integrity Professionals - Nevada. All Rights Reserved.
Performing a z/os Vulnerability Assessment Part 1 - Data Collection Presented by Vanguard Integrity Professionals Legal Notice Copyright 2014 Vanguard Integrity Professionals - Nevada. All Rights Reserved.
User Account Manager
 CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
MQ for z/os An introduction to object authorization on that other IBM queue Software manager Group Lotus software
 MQ for z/os An introduction to object authorization on that other IBM queue Software manager Group Lotus software Lyn Elkins elkinsc@us.ibm.com Mitch Johnson mitchj@us.ibm.com Agenda This session will
MQ for z/os An introduction to object authorization on that other IBM queue Software manager Group Lotus software Lyn Elkins elkinsc@us.ibm.com Mitch Johnson mitchj@us.ibm.com Agenda This session will
RACF Identity Propagation on z/os Who Are You?
 RACF Identity Propagation on z/os Who Are You? Mark Nelson SHARE Session 8352 z/os Security Server (RACF) Design and Development. IBM Poughkeepsie markan@us.ibm.com Trademarks IBM, the IBM logo, and ibm.com
RACF Identity Propagation on z/os Who Are You? Mark Nelson SHARE Session 8352 z/os Security Server (RACF) Design and Development. IBM Poughkeepsie markan@us.ibm.com Trademarks IBM, the IBM logo, and ibm.com
DLA J62D Information Operations DSS Mainframe CAC Registration Guide for (MUA) Production End-Users September 2016
 CONTROLLED UNCLASSIFIED INFORMATION DLA J62D Information Operations DSS Mainframe CAC Registration Guide for (MUA) Production End-Users September 2016 Table of Contents ABOUT THIS DOCUMENT... 3 1.0 INTRODUCTION...
CONTROLLED UNCLASSIFIED INFORMATION DLA J62D Information Operations DSS Mainframe CAC Registration Guide for (MUA) Production End-Users September 2016 Table of Contents ABOUT THIS DOCUMENT... 3 1.0 INTRODUCTION...
Oracle User Administration
 Oracle User Administration Creating user accounts User accounts consist of two components. These are: 1. User name - The name of the account. 2. Password - The password associated with the user account.
Oracle User Administration Creating user accounts User accounts consist of two components. These are: 1. User name - The name of the account. 2. Password - The password associated with the user account.
Securing JES Resource Classes
 Securing JES Resource Classes Jim McNeill NYRUG November 25, 2014 1 Session Topics Job Control Overview Controlling Job Input Controlling JOB CLASSES Controlling Printing (Output) Controlling Access to
Securing JES Resource Classes Jim McNeill NYRUG November 25, 2014 1 Session Topics Job Control Overview Controlling Job Input Controlling JOB CLASSES Controlling Printing (Output) Controlling Access to
Outline. Operating System Security CS 239 Computer Security February 23, Introduction. Server Machines Vs. General Purpose Machines
 Outline Operating System Security CS 239 Computer Security February 23, 2004 Introduction Memory protection Interprocess communications protection File protection Page 1 Page 2 Introduction Why Is OS Security
Outline Operating System Security CS 239 Computer Security February 23, 2004 Introduction Memory protection Interprocess communications protection File protection Page 1 Page 2 Introduction Why Is OS Security
Setting Access Controls on Files, Folders, Shares, and Other System Objects in Windows 2000
 Setting Access Controls on Files, Folders, Shares, and Other System Objects in Windows 2000 Define and set DAC policy (define group membership, set default DAC attributes, set DAC on files systems) Modify
Setting Access Controls on Files, Folders, Shares, and Other System Objects in Windows 2000 Define and set DAC policy (define group membership, set default DAC attributes, set DAC on files systems) Modify
RACF/VM: Protecting your z/vm system from vandals and other cyberspace miscreants
 RACF/VM: Protecting your z/vm system from vandals and other cyberspace miscreants Session 9127 Alan Altmark z/vm Development, IBM Endicott, NY Disclaimers This presentation introduces the mechanisms used
RACF/VM: Protecting your z/vm system from vandals and other cyberspace miscreants Session 9127 Alan Altmark z/vm Development, IBM Endicott, NY Disclaimers This presentation introduces the mechanisms used
LINKFM Task Manager. Client & Building Manager USER GUIDE
 Unit 7, 1 st Floor. 66-70 Railway Road Blackburn. VIC. 3130 T: 1300 872 885 F: (03) 9894 4002 E: info@statcomsystems.com.au LINKFM Task Manager Client & Building Manager USER GUIDE Contents Introduction...
Unit 7, 1 st Floor. 66-70 Railway Road Blackburn. VIC. 3130 T: 1300 872 885 F: (03) 9894 4002 E: info@statcomsystems.com.au LINKFM Task Manager Client & Building Manager USER GUIDE Contents Introduction...
Outlook - Delegate Access to Exchange Accounts (Sharing)
 Outlook - Delegate Access to Exchange Accounts (Sharing) In Outlook, someone else can be permitted to manage another's mail and calendar; this feature is termed Delegate Access. Outlook allows another
Outlook - Delegate Access to Exchange Accounts (Sharing) In Outlook, someone else can be permitted to manage another's mail and calendar; this feature is termed Delegate Access. Outlook allows another
Creating Calendar Shares in Microsoft Outlook 2016 for PC Sharing a Calendar
 University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Creating Calendar Shares in Microsoft Outlook 2016 for PC Sharing a Calendar You can share your calendars
University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Creating Calendar Shares in Microsoft Outlook 2016 for PC Sharing a Calendar You can share your calendars
Community portal User Guide OACIS
 Community portal User Guide OACIS Septembre 2015 Table des matières TELUS Health Community Portal... 3 Registering... 4 First time login... 5 If you forget your password... 5 Set up your community profile...
Community portal User Guide OACIS Septembre 2015 Table des matières TELUS Health Community Portal... 3 Registering... 4 First time login... 5 If you forget your password... 5 Set up your community profile...
Access Control. CMPSC Spring 2012 Introduction Computer and Network Security Professor Jaeger.
 Access Control CMPSC 443 - Spring 2012 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse443-s12/ Access Control Describe the permissions available to computing processes
Access Control CMPSC 443 - Spring 2012 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse443-s12/ Access Control Describe the permissions available to computing processes
Lesson 8 Transcript: Database Security
 Lesson 8 Transcript: Database Security Slide 1: Cover Welcome to Lesson 8 of the DB2 on Campus Series. Today we are going to talk about database security. My name is Raul Chong, and I am the DB2 on Campus
Lesson 8 Transcript: Database Security Slide 1: Cover Welcome to Lesson 8 of the DB2 on Campus Series. Today we are going to talk about database security. My name is Raul Chong, and I am the DB2 on Campus
Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003
 Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003 A system or combination of systems that enforces a boundary between two or more networks - NCSA
Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003 A system or combination of systems that enforces a boundary between two or more networks - NCSA
Quick Guide: Getting Started with IMS
 Quick Guide: Getting Started with IMS Quick Guide: Getting Started with IMS Subject: IMS Login and Menus. Intent: Instructions for accessing and navigating IMS. 2011 University of Pittsburgh Medical Center.
Quick Guide: Getting Started with IMS Quick Guide: Getting Started with IMS Subject: IMS Login and Menus. Intent: Instructions for accessing and navigating IMS. 2011 University of Pittsburgh Medical Center.
Division of State Fire Marshal. Florida Public School Fire Safety Report System User Manual
 Division of State Fire Marshal Florida Public School Fire Safety Report System User Manual Division of State Fire Marshal 10-1-2018 I. Inspection Agencies Definition: Inspection Agency A public school
Division of State Fire Marshal Florida Public School Fire Safety Report System User Manual Division of State Fire Marshal 10-1-2018 I. Inspection Agencies Definition: Inspection Agency A public school
Evolution Of The Need For IAM. Securing connections between people, applications, and networks
 Evolution Of The Need For IAM December 2006 Evolution Of The Need For IAM Identity issues are nothing new Who steals my purse steals trash / But he that filches from me my good name / Robs me of that which
Evolution Of The Need For IAM December 2006 Evolution Of The Need For IAM Identity issues are nothing new Who steals my purse steals trash / But he that filches from me my good name / Robs me of that which
TransUnion Direct Administrator Guide
 TransUnion Direct Administrator Guide Administrator Guide Topics Welcome to TransUnion Direct... 2 Your Role and Responsibilities... 5 Getting Started... 6 Managing Users... 8 Managing a Company... 15
TransUnion Direct Administrator Guide Administrator Guide Topics Welcome to TransUnion Direct... 2 Your Role and Responsibilities... 5 Getting Started... 6 Managing Users... 8 Managing a Company... 15
INFORMED VISIBILITY. Mail Tracking & Reporting. Applying for Access to IV
 INFORMED VISIBILITY Mail Tracking & Reporting Applying for Access to IV V2.1, September 7, 2017 Table of Contents Introduction Register for a Business Customer Gateway (BCG) Account Perform IV Business
INFORMED VISIBILITY Mail Tracking & Reporting Applying for Access to IV V2.1, September 7, 2017 Table of Contents Introduction Register for a Business Customer Gateway (BCG) Account Perform IV Business
VidyoDesktop: Quick User Guide Ver. 1.0
 Page 1 Logging In There are 3 parameters needed to log in. 1. The video portal link. (http://webvc.nic.in). 2. User Name provided by NIC. 3. Password. When you are ready to log in, enter your username
Page 1 Logging In There are 3 parameters needed to log in. 1. The video portal link. (http://webvc.nic.in). 2. User Name provided by NIC. 3. Password. When you are ready to log in, enter your username
1 SEARCHING FOR A MEMBER SEARCHING FOR A WI ADDING A NEW MEMBER HOW TO ADD A DUAL MEMBER... 9
 Contents 1 SEARCHING FOR A MEMBER... 2 2 SEARCHING FOR A WI... 4 3 ADDING A NEW MEMBER... 6 4 HOW TO ADD A DUAL MEMBER... 9 6 HOW TO CHANGE A MEMBER S WI... 19 7 HOW TO UPLOAD A DOCUMENT OR WEB LINK...
Contents 1 SEARCHING FOR A MEMBER... 2 2 SEARCHING FOR A WI... 4 3 ADDING A NEW MEMBER... 6 4 HOW TO ADD A DUAL MEMBER... 9 6 HOW TO CHANGE A MEMBER S WI... 19 7 HOW TO UPLOAD A DOCUMENT OR WEB LINK...
Challenges and Issues for RACF Systems
 Payment Card Industry (PCI) Challenges and Issues for RACF Systems Jim Yurek Vanguard Integrity Professionals February 28, 2011 Session Number 8507 The Problem: Credit Card Breaches As long as we have
Payment Card Industry (PCI) Challenges and Issues for RACF Systems Jim Yurek Vanguard Integrity Professionals February 28, 2011 Session Number 8507 The Problem: Credit Card Breaches As long as we have
Ajith s Documentum Security Notes
 1 Ajith s Documentum Security Notes Ajith s Documentum Security Notes...1 User Privileges...1 Basic privileges...2 Extended User Privileges...2 Object Level Permissions...3 Base Object- Level Permissions...3
1 Ajith s Documentum Security Notes Ajith s Documentum Security Notes...1 User Privileges...1 Basic privileges...2 Extended User Privileges...2 Object Level Permissions...3 Base Object- Level Permissions...3
Adobe Sign for Microsoft Dynamics
 Adobe Sign for Microsoft Dynamics Installation & Configuration Guide (v5) Last Updated: March 16, 2017 2017 Adobe Systems Incorporated. All rights reserved Table of Contents Overview... 3 Prerequisites...
Adobe Sign for Microsoft Dynamics Installation & Configuration Guide (v5) Last Updated: March 16, 2017 2017 Adobe Systems Incorporated. All rights reserved Table of Contents Overview... 3 Prerequisites...
HIGH-IMPACT SEO DIY IN 5 MINUTES SEO OR LESS. Digital Marketer Increase Engagement Series
 DIY SEO HIGH-IMPACT SEO IN 5 MINUTES OR LESS Digital Marketer Increase Engagement Series DIY SEO: HIGH-IMPACT SEO IN 5 MINUTES OR LESS Brought To You By: Digital Marketer PUBLISHED BY: HOW TO SEO A WORDPRESS
DIY SEO HIGH-IMPACT SEO IN 5 MINUTES OR LESS Digital Marketer Increase Engagement Series DIY SEO: HIGH-IMPACT SEO IN 5 MINUTES OR LESS Brought To You By: Digital Marketer PUBLISHED BY: HOW TO SEO A WORDPRESS
The following pages will give you a quick overview over your new XELOS intranet and help you with the first steps. 1. Overview over the user interface
 XELOS 7 First Steps Overview XELOS is a professional Enterprise.0 software that is used by companies mainly as an intranet solution to improve collaboration within teams and in the company. The brilliant
XELOS 7 First Steps Overview XELOS is a professional Enterprise.0 software that is used by companies mainly as an intranet solution to improve collaboration within teams and in the company. The brilliant
IBM Security Identity Manager Version Planning Topics IBM
 IBM Security Identity Manager Version 7.0.1 Planning Topics IBM IBM Security Identity Manager Version 7.0.1 Planning Topics IBM ii IBM Security Identity Manager Version 7.0.1: Planning Topics Table of
IBM Security Identity Manager Version 7.0.1 Planning Topics IBM IBM Security Identity Manager Version 7.0.1 Planning Topics IBM ii IBM Security Identity Manager Version 7.0.1: Planning Topics Table of
User Guide REVISION 6/6/2016
 User Guide REVISION 6/6/2016 1 Contents 1. System Overview... 3 2. Enrollment Process... 4 3. Managing Company Structure... 5 4. User List... 7 5. User Record... 8 6. Profile/Out of Office... 9 7. Company
User Guide REVISION 6/6/2016 1 Contents 1. System Overview... 3 2. Enrollment Process... 4 3. Managing Company Structure... 5 4. User List... 7 5. User Record... 8 6. Profile/Out of Office... 9 7. Company
A GUIDE FOR ADMINISTRATORS
 A GUIDE FOR ADMINISTRATORS OBJECTIVE CONNECT WORK SECURELY WITH ANYONE OBJECTIVE CONNECT A secure, private workspace, so you can work with anyone outside of your organisation. Key Features: Secure, Private
A GUIDE FOR ADMINISTRATORS OBJECTIVE CONNECT WORK SECURELY WITH ANYONE OBJECTIVE CONNECT A secure, private workspace, so you can work with anyone outside of your organisation. Key Features: Secure, Private
Chapter 7: Hybrid Policies
 Chapter 7: Hybrid Policies Overview Chinese Wall Model Clinical Information Systems Security Policy ORCON RBAC Slide #7-1 Overview Chinese Wall Model Focuses on conflict of interest CISS Policy Combines
Chapter 7: Hybrid Policies Overview Chinese Wall Model Clinical Information Systems Security Policy ORCON RBAC Slide #7-1 Overview Chinese Wall Model Focuses on conflict of interest CISS Policy Combines
Welcome to the Soholaunch Addons Affiliate Program
 Welcome to the Soholaunch Addons Affiliate Program Dear Soholaunch Partner, Thank you for your interest in the Soholaunch Addons Affiliate Program. In this presentation you ll find. An overview of the
Welcome to the Soholaunch Addons Affiliate Program Dear Soholaunch Partner, Thank you for your interest in the Soholaunch Addons Affiliate Program. In this presentation you ll find. An overview of the
Contents Office 365 Groups in Outlook 2016 on the web... 3 What are groups?... 3 Tips for getting the most out of Office 365 Groups...
 Contents Office 365 Groups in Outlook 2016 on the web... 3 What are groups?... 3 Tips for getting the most out of Office 365 Groups... 3 Create a Group in Web Outlook... 4 Group limits... 6 Group privacy...
Contents Office 365 Groups in Outlook 2016 on the web... 3 What are groups?... 3 Tips for getting the most out of Office 365 Groups... 3 Create a Group in Web Outlook... 4 Group limits... 6 Group privacy...
Software Version 5.0. Administrator Guide Release Date: 7th April, InCommon c/o Internet Oakbrook Drive, Suite 300 Ann Arbor MI, 48104
 Software Version 5.0 Administrator Guide Release Date: 7th April, 2015 InCommon c/o Internet2 1000 Oakbrook Drive, Suite 300 Ann Arbor MI, 48104 Table of Contents 1 Introduction to InCommon Certificate
Software Version 5.0 Administrator Guide Release Date: 7th April, 2015 InCommon c/o Internet2 1000 Oakbrook Drive, Suite 300 Ann Arbor MI, 48104 Table of Contents 1 Introduction to InCommon Certificate
IBM. RACF Security Guide. CICS Transaction Server for z/os Version 4 Release 2 SC
 CICS Transaction Server for z/os Version 4 Release 2 IBM RACF Security Guide SC34-7179-01 CICS Transaction Server for z/os Version 4 Release 2 IBM RACF Security Guide SC34-7179-01 Note Before using this
CICS Transaction Server for z/os Version 4 Release 2 IBM RACF Security Guide SC34-7179-01 CICS Transaction Server for z/os Version 4 Release 2 IBM RACF Security Guide SC34-7179-01 Note Before using this
Privilege Separation
 What (ideas of Provos, Friedl, Honeyman) A generic approach to limit the scope of programming bugs Basic principle: reduce the amount of code that runs with special privilege without affecting or limiting
What (ideas of Provos, Friedl, Honeyman) A generic approach to limit the scope of programming bugs Basic principle: reduce the amount of code that runs with special privilege without affecting or limiting
IBM Software Group. zsecure update IBM Corporation
 IBM Software Group zsecure update 2011 IBM Corporation Multi-system support zsecure Admin zsecure Audit zsecure Visual Release 1.12 2 Multi-system support Nodes and systems RRSF * is preferred node in
IBM Software Group zsecure update 2011 IBM Corporation Multi-system support zsecure Admin zsecure Audit zsecure Visual Release 1.12 2 Multi-system support Nodes and systems RRSF * is preferred node in
Off-Line The SC Midlands Chapter of the Information Systems Audit & Control Association
 Off-Line The SC Midlands Chapter of the Information Systems Audit & Control Association CHAPTER 54 AUGUST 2007 September Seminars: Computer Security: How to Audit Security on Any Type of Computer How to
Off-Line The SC Midlands Chapter of the Information Systems Audit & Control Association CHAPTER 54 AUGUST 2007 September Seminars: Computer Security: How to Audit Security on Any Type of Computer How to
MTAT Introduction to Databases
 MTAT.03.105 Introduction to Databases Lecture #12 DB Administration Ljubov Jaanuska (ljubov.jaanuska@ut.ee) Lecture 11. Summary Functions Procedures Lecture 11. What will you learn Users User rights Revision
MTAT.03.105 Introduction to Databases Lecture #12 DB Administration Ljubov Jaanuska (ljubov.jaanuska@ut.ee) Lecture 11. Summary Functions Procedures Lecture 11. What will you learn Users User rights Revision
Rich Powell Director, CIP Compliance JEA
 Rich Powell Director, CIP Compliance JEA Review access control requirements CIP-003 and CIP-007 Discuss compliance considerations Implementation Strategies Hints/Tips for audit presentation Account Control
Rich Powell Director, CIP Compliance JEA Review access control requirements CIP-003 and CIP-007 Discuss compliance considerations Implementation Strategies Hints/Tips for audit presentation Account Control
Database Searching (NHS)
 Database Searching (NHS) 1. Why use Databases? Databases hold bibliographic information about articles across a wide range of journal titles. You use them to search for articles within a particular subject
Database Searching (NHS) 1. Why use Databases? Databases hold bibliographic information about articles across a wide range of journal titles. You use them to search for articles within a particular subject
HUMAN RESOURCES DEPARTMENT
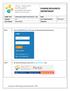 FORM TITLE MANAGING SUBSTITUTION RULES - MSS PAGE 1 Step 1 Go to the KAUST Portal link, fill in your user ID and password and click enter. Step 2 On the top of the portal, click on the Manager Self-Service
FORM TITLE MANAGING SUBSTITUTION RULES - MSS PAGE 1 Step 1 Go to the KAUST Portal link, fill in your user ID and password and click enter. Step 2 On the top of the portal, click on the Manager Self-Service
Internetwork Expert s CCNA Security Bootcamp. Securing Cisco Routers. Router Security Challenges
 Internetwork Expert s CCNA Security Bootcamp Securing Cisco Routers http:// Router Security Challenges As the system gets more complex, as do the vulnerabilities Key part of security team s job is to be
Internetwork Expert s CCNA Security Bootcamp Securing Cisco Routers http:// Router Security Challenges As the system gets more complex, as do the vulnerabilities Key part of security team s job is to be
Resource Account Instructions
 Resource Account Instructions Contents: click to skip to a section Managing a Resource Email Account in Outlook Overview of Resource Accounts for Owners... 2 Email Retention and Archives... 2 Accessing
Resource Account Instructions Contents: click to skip to a section Managing a Resource Email Account in Outlook Overview of Resource Accounts for Owners... 2 Email Retention and Archives... 2 Accessing
Is Your z/os System Secure?
 Ray Overby Key Resources, Inc. Info@kr-inc.com (312) KRI-0007 A complete z/os audit will: Evaluate your z/os system Identify vulnerabilities Generate exploits if necessary Require installation remediation
Ray Overby Key Resources, Inc. Info@kr-inc.com (312) KRI-0007 A complete z/os audit will: Evaluate your z/os system Identify vulnerabilities Generate exploits if necessary Require installation remediation
Logi Ad Hoc Reporting System Administration Guide
 Logi Ad Hoc Reporting System Administration Guide Version 12 July 2016 Page 2 Table of Contents INTRODUCTION... 4 APPLICATION ARCHITECTURE... 5 DOCUMENT OVERVIEW... 6 GENERAL USER INTERFACE... 7 CONTROLS...
Logi Ad Hoc Reporting System Administration Guide Version 12 July 2016 Page 2 Table of Contents INTRODUCTION... 4 APPLICATION ARCHITECTURE... 5 DOCUMENT OVERVIEW... 6 GENERAL USER INTERFACE... 7 CONTROLS...
If you haven t already received an invitation and started the sign-up process then start by going online and connecting to the address listed below.
 GETTING STARTED ON THE NETWORK Signing Up If you haven t already received an invitation and started the sign-up process then start by going online and connecting to the address listed below. Type the following
GETTING STARTED ON THE NETWORK Signing Up If you haven t already received an invitation and started the sign-up process then start by going online and connecting to the address listed below. Type the following
Chapter 4 Protection in General-Purpose Operating Systems
 Chapter 4 Protection in General-Purpose Operating Systems Charles P. Pfleeger & Shari Lawrence Pfleeger, Security in Computing, 4 th Ed., Pearson Education, 2007 1 An operating system has two goals: controlling
Chapter 4 Protection in General-Purpose Operating Systems Charles P. Pfleeger & Shari Lawrence Pfleeger, Security in Computing, 4 th Ed., Pearson Education, 2007 1 An operating system has two goals: controlling
Removing ID. The Solution: The Issue: The Problem:
 How to use Vanguard security products to remove ID(*) access greater than NONE or READ to create a more secure mainframe RACF database without risking an operational outage due to removing required access.
How to use Vanguard security products to remove ID(*) access greater than NONE or READ to create a more secure mainframe RACF database without risking an operational outage due to removing required access.
Manage Administrators and Admin Access Policies
 Manage Administrators and Admin Access Policies Role-Based Access Control, on page 1 Cisco ISE Administrators, on page 1 Cisco ISE Administrator Groups, on page 3 Administrative Access to Cisco ISE, on
Manage Administrators and Admin Access Policies Role-Based Access Control, on page 1 Cisco ISE Administrators, on page 1 Cisco ISE Administrator Groups, on page 3 Administrative Access to Cisco ISE, on
IBM. Security Server RACF General User's Guide. z/os. Version 2 Release 3 SA
 z/os IBM Security Server RACF General User's Guide Version 2 Release 3 SA23-2298-30 Note Before using this information and the product it supports, read the information in Notices on page 99. This edition
z/os IBM Security Server RACF General User's Guide Version 2 Release 3 SA23-2298-30 Note Before using this information and the product it supports, read the information in Notices on page 99. This edition
zsc40 Beyond Legacy Security Paul R. Robichaux NewEra Software, Inc. Thursday, May 9th at 9:00 10:15 am Session Number - zsc40 Location Melrose
 Beyond Legacy Security zsc40 Paul R. Robichaux, Inc. Thursday, May 9th at 9:00 0:5 am Session Number - zsc40 Location Melrose TCE The Control Editor Productivity and Control! Building a Safer, more Secure
Beyond Legacy Security zsc40 Paul R. Robichaux, Inc. Thursday, May 9th at 9:00 0:5 am Session Number - zsc40 Location Melrose TCE The Control Editor Productivity and Control! Building a Safer, more Secure
Protect Your Application with Secure Coding Practices. Barrie Dempster & Jason Foy JAM306 February 6, 2013
 Protect Your Application with Secure Coding Practices Barrie Dempster & Jason Foy JAM306 February 6, 2013 BlackBerry Security Team Approximately 120 people work within the BlackBerry Security Team Security
Protect Your Application with Secure Coding Practices Barrie Dempster & Jason Foy JAM306 February 6, 2013 BlackBerry Security Team Approximately 120 people work within the BlackBerry Security Team Security
CA RC/Secure for DB2 for z/os
 PRODUCT sheet: CA RC/Secure for DB2 for z/os CA RC/Secure for DB2 for z/os CA RC/Secure for DB2 for z/os (CA RC/Secure) is a comprehensive, online security administration tool for DB2 for z/os that helps
PRODUCT sheet: CA RC/Secure for DB2 for z/os CA RC/Secure for DB2 for z/os CA RC/Secure for DB2 for z/os (CA RC/Secure) is a comprehensive, online security administration tool for DB2 for z/os that helps
Banner 8 Security Enhancements Part 2
 Banner 8 Security Enhancements Part 2 Presented by: Les von Holstein SunGard Higher Education Wednesday, October 20, 2010 4:30 5:15 1 Focus Group Thank You! George Mason University Georgia State University
Banner 8 Security Enhancements Part 2 Presented by: Les von Holstein SunGard Higher Education Wednesday, October 20, 2010 4:30 5:15 1 Focus Group Thank You! George Mason University Georgia State University
Brian Marshall VP Research and Development Vanguard Integrity Professionals Session Vanguard Integrity Professionals, Inc.
 Brian Marshall VP Research and Development Vanguard Integrity Professionals Session 15992 2014 Vanguard Integrity Professionals, Inc. 1 AGENDA THE WAY IT WAS. Slides 3-5 THE WAY IT IS NOW with IRRXUTIL
Brian Marshall VP Research and Development Vanguard Integrity Professionals Session 15992 2014 Vanguard Integrity Professionals, Inc. 1 AGENDA THE WAY IT WAS. Slides 3-5 THE WAY IT IS NOW with IRRXUTIL
Mike Loos Consulting IT Specialist WebSphere on z/os
 Configuring in WebSphere Application Server V6.1 for z/os An example Configuration of fine grained security using the WSADMIN tool with Jython commands. Mike Loos Consulting IT Specialist WebSphere on
Configuring in WebSphere Application Server V6.1 for z/os An example Configuration of fine grained security using the WSADMIN tool with Jython commands. Mike Loos Consulting IT Specialist WebSphere on
1. Introduction and overview
 1. Introduction and overview 1.1 Purpose of this Document This document describes how we will test our code for robustness. It includes test cases and other methods of testing. 1.2 Scope of the Development
1. Introduction and overview 1.1 Purpose of this Document This document describes how we will test our code for robustness. It includes test cases and other methods of testing. 1.2 Scope of the Development
Configuring Role-Based Access Control
 5 CHAPTER This chapter describes how to configure role-based access control (RBAC) on the Cisco 4700 Series Application Control Engine (ACE) appliance. It describes how to create a domain and a user, and
5 CHAPTER This chapter describes how to configure role-based access control (RBAC) on the Cisco 4700 Series Application Control Engine (ACE) appliance. It describes how to create a domain and a user, and
