ECPV: EFFICIENT CERTIFICATE PATH VALIDATION IN PUBLIC-KEY INFRASTRUCTURE
|
|
|
- Alan Benson
- 5 years ago
- Views:
Transcription
1 ECPV: EFFICIENT CERTIFICATE PATH VALIDATION IN PUBLIC-KEY INFRASTRUCTURE M. Halappanavar and R. Mukkamala Department of Computer Science, Old Dominion University, Norfolk, VA, USA Abstract Keywords: In the current public-key infrastructure (PKI) schemes based on X.509, a relying party must validate a user s certificate as well as the existence of a path from its trust points to the CA of the certificate. The latter part is referred to as certificate path validation. In this paper, we suggest an efficient certificate path validation scheme (ECPV) that employs delegation with efficient computing at relying parties. In particular, in our scheme, a relying party is provided with certificate path validation trees (CPVTs) depending on its trust points and applicable trust policies. This information should enable a relying party to perform certificate path validation locally. The CPVAs can be deployed either as autonomous entities or in a federated mode. We discuss the two major components of ECPV: the data harvester and the data analyzer. Some of the concerns of security, trust, and performance are also discussed. Certificate Path Validation Authority (CPVA), certificate path validation trees (CPVT), delegated path discovery (DPD), delegated path validation (DPV), public-key Infrastructure (PKI), security and trust 1. INTRODUCTION Digital certificates have emerged as a popular tool to provide authentication, privacy, integrity, non-repudiation and other security requirements in modern day transactions [1]. PKI provides a comprehensive infrastructure for issuing and managing public keys in the form of digital certificates to a set of users [1,10]. When two users want to communicate with one another in a secure manner, they will have to authenticate each other prior to the actual communication. This stranger-to-stranger
2 216 DATA AND APPLICATIONS SECURITY XVII communication is made possible by having a trusted third-party (TTP) in the form of Certification Authority (CA) whom both the parties trust. When a user or subject submits a certificate to a relying party (RP) for a service, the relying party would like to validate the user certificate prior to offering a service. Typically, the validation of a certificate is done in three steps. In the first step, a relying party (RP) builds a chain of trust, also known as certificate chain, starting from the CA that has issued the user s certificate to the CA that RP trusts (also known as a trust point). This step is known as certificate path discovery. Generally, trust between CAs is established by issuing CA- CA cross-certificates. These certificates can also be revoked from time to time. Thus there is a need to confirm the validity of the links in the certificate chain built in step one. The second step conducts the validation, and is referred to as certificate path validation. (The logic for the validation process described above is described in RFC 2459 [9,10] and is based on various parameters specified in certificate policies.) In the third step, the validity of the issued certificate is itself verified with information provided by its CA. In this paper, we are interested in the first two steps of the validation process. Recent research trends in public-key infrastructure favor delegation of authority for certificate path validation to trusted-severs and for path discovery to untrusted-servers. DPV (Delegated Path Validation) and DPD (Delegated Path Discovery) are examples of such protocols [9]. These protocols are still evolving and are described in Internet drafts [8,9]. Simple Certificate Validation Protocol (SCVP) is another delegation protocol that is conceptually similar to DPV and DPD [6]. In this paper, we propose an efficient certificate path validation (ECPV) scheme to overcome the weaknesses in the current path validation protocols. Our scheme is based on one or more certificate path validation authorities (CPVA) that upload RPs with a certificate path validation trees (CPVT). An RP, in turn, can use this locally available tree to validate certificate paths of user certificates. The trees shall be periodically updated by the CPVA. The CPVAs can be implemented either as an autonomous entity working in isolation or organized as a federation to share information. The paper is organized as follows. In section 2, we discuss some of the issues in certificate path validation and current solutions. In section 3, we describe the proposed ECPV scheme for certificate path validation. A more detailed description of the CPVA module is provided in section 4. Two possible options for deployment are discussed in section 5. Section 6 reviews the security, trust, and performance aspects of the proposed scheme. Finally, section 7 summarizes the contributions of the paper and discusses plans for future work.
3 ECPV in Public-Key Infrastructure ISSUES IN CERTIFICATE PATH VALIDATION As explained in section 1, certificate path validation involves the task of discovering a path and then verifying its validity. The path discovery is both computation and communication intensive, since it involves discovering a network of CAs that trust each other. Several factors contribute to the complexity. First, there are many possible trust topologies [5,8,9,11]. Strict hierarchical, multi-rooted hierarchical, mesh, bilateral cross-certification, and bridge topologies are a few example topologies. However, many of the present RP implementations make simple assumptions about the trust structure and are not capable of handling these complex trust relationships [11,14]. Changes in the trust hierarchies over time also necessitate changes in the relying party software, an impractical proposition. Second is the trust policy issue. Each RP has an acceptable trust policy for the chain of CAs that it is trying to validate for a given certificate [3]. The policy would describe the minimum level of CA practices that it expects from each of the CAs on the path. Similarly, each CA also specifies, in its CA-CA certificate, the practices (policies) that it trusts other CAs to follow [1,2]. As a consequence of a wide variety of such policies, the task of RP becomes more complex during path discovery since it should only select those links that are compatible with its (RP s) own policy. Checking the policy compatibility is not a simple process [2,7,9]. Third, response time is also one of issues for certificate path validation. For example, an RP is very much interested in responding to its users as soon as possible with the service they requested. However, it cannot do so until the path validation and the subsequent certificate validation are complete. Fourth, CA and repository availability is also an important concern to an RP. All of the CAs and the relevant certificate and revocation information repositories need to be available for an RP to discover and validate a path. If a trust path is long, with several CAs, there could be a problem in data collection as some entities along the path may not be accessible during validation [9,11,14]. In other words, even though a CA-CA certificate is valid, due to the inability to access a CA s data at the validation time, an RP may not be able to validate a certificate. Finally, RP is concerned about the cost of validation. It would like to minimize this cost. When each RP undertakes the task of discovery and validation (i.e., if it is not delegated to a server), it is an expensive process. Substantial cost savings may not be realized if the entire process of validation is repeated for each certificate that the RP receives, even when delegated to a trusted validation server.
4 218 DATA AND APPLICATIONS SECURITY XVII From the above discussion, it is clear that certificate validation is a complex process involving considerable amount of communication and computational resources. 3. ECPV: PROPOSED SCHEME FOR CERTIFICATE PATH VALIDATION ECPV is based on the idea that it is much more efficient to provide a relying party with path validation information in the form of trees (CPVT) rather than to require the RP to request an external server for each certificate validation. Section 3.1 describes the CPVTs in greater detail. 3.1 Certificate Path Validation Trees (CPVT) To explain the concept of CPVT, let us consider the example in Figure 1. Figure 1 (a) describes a set of trust relationships between a set of CAs (CA1 - CA9). Here, an arrow between one CA and the other (e.g., from CA1 to CA5) indicates that one CA has issued a cross-ca certificate to the other (e.g., CA1 issued a certificate to CA5). The arrow type indicates the similarity between the trust parameters, which could be established by policy mappings (e.g., CA1 policy maps to policy for CA5). Suppose a relying party RP1 trusts CA1. In addition, it accepts input parameter set 1 for some type of requests and input parameter set 3 for other types of user requests. In this case, the intent is to build two trees for RP1 with CA1 as the root, one with IP set 1 and the other with IP set 3. Figures (1b) and (1c) are the required trees derived from Figure 1a. These are what we refer to as certificate path validation trees or CPVTs. For RP1 to accept a certificate issued by CAx under IP set 1, for example, it expects a path from CA1 to that CAx in the CPVT in Figure (1b). In this case, for example, only CA1, CA3, CA7, and CA9 meet the criteria. In fact, each directional edge in Figure 1 is associated with an expiration time (not shown in the figure), derived from the expiration time of the cross-ca certificate and the CRL (or ARL) issued by the parent CA. Thus, an edge in the network or CPVT is valid only if it has not expired at the time of its usage. The advantages of building the path from trust point, commonly referred to as building in reverse direction, are very well discussed in [7].
5 ECPV in Public-Key Infrastructure 219 Figure 1. Illustration of Certificate Path Validation Trees (CPVT) 3.2 System architecture The system architecture for ECPV is shown in Figure 2. The various components of the system are as follows: (1) CA Module: The certification authority (CA), its registration authority (RA), the repository (REP), and OCSP responder together represent the CA module. (2) CPVA module: The CPVA (Certificate Path Validation Authority) is the critical module that will perform the process of path discovery and verification. This module consists of harvester (HRV) and analyzer. CPVA is responsible for building the CPVTs and distributing them to the RP modules. (3) RP module: The relying parties (RP) service the requests from subjects for certificate validation. The relying parties provide requisite information, including trust points and validation policies, to the CPVA module, which builds relevant CPVTs based on the input and download CPVTS to the RPs. RPs are the primary users of the infrastructure for validation of certificates. (4) Subject module: Subjects or clients request service from the RPs and offer their certificates for validation. The subject s influence the system design and performance from their diversity and rate of requests.
6 220 DATA AND APPLICATIONS SECURITY XVII Figure 2. System Architecture Another important aspect of our architecture is the interactions among the modules. Among all interactions in our system, the following three are relevant with respect to this paper: (i) the RP-CPVA interactions, (ii) CPVA- CA interactions, and (iii) CPVA-CPVA interactions. We summarize these three types of interactions in the form of scenario-like description of events starting from an RP submitting a request to the uploading of CPVTs to it. 1. Each relying party (RP) submits a set of input parameters with vital information like trust point CAs, policy constraints, name constraints, maximum path length, etc. 2. The CPVA consolidates the RP information and requests its harvester component to collect data a set of <trust point, input parameter set> pairs. 3. Harvester collects all the requisite information including CA certificates, CRLs, OCSP responses, etc. (In the federated scheme, a harvester may also collect CPVTs from other CPVAs). 4. The analyzer analyzes the collected data, and builds CPVTs based on the RPs requests initially received. The analysis includes looking into the CRLs (also referred to as ARLs [1,10]) and the OCSP responses for validity of CA certificates. In addition, it needs to take a note of the validity of each response---how long is a published CRL applicable. Using this information, it builds CPVTs with trust points as the roots. 5. The CPVA uploads the appropriate trees to the respective RPs (i.e., each RP gets only the relevant CPVTs). 6. Since some edges of a CPVT may expire after the initial upload, the trees automatically get pruned at the RP while being used for certificate
7 ECPV in Public-Key Infrastructure 221 verification. In addition, the CPVA also keeps track of the expirations and updates its trees with periodic data. The updated trees may be either automatically uploaded (in a push scheme) or requested by a RP (in a pull scheme). 4. THE CERTIFICATE PATH VALIDATION AUTHORITY (CPVA ) As shown in Figure 2, CPVA has two components: harvester and analyzer. While the claimed simplicity of RP software comes from the harvester s functionality, the benefits in performance are due to both the components. We now describe these components. 4.1 The harvester The concept of harvester is adopted from the concept of data harvesting in digital libraries [14]. A harvester traverses the CA repositories and OCSP responders and collects all the requisite information like certificates, CRLs, and OCSP responses. The repositories use multiple directory protocols like DAP, LDAP, FTP and HTTP, and also have directory chaining, directory referrals. This necessitates the harvester software to be complex and capable of communicating with different protocols. The components of the harvester, as follows: Bulk Harvester: The bulk harvester is activated for gathering of information at initialization as well as occasionally to refresh data. Incremental Harvester: The incremental harvester is executed frequently to keep the data current. It can be activated on events like certificate expiry, CRL expiry, addition of new CAs, etc. The Scheduler: The Scheduler components triggers the incremental harvester and the bulk harvester at appropriate times to keep the data up-to-date. Data Normalizer: Since the collected data during the harvesting can be in different formats, the data normalizer reformats the data into single format for easy processing by the data analyzer module. 4.2 The analyzer Once the harvester has obtained all the relevant information, it is the responsibility of the analyzer to construct the CPVTs to upload to the relying
8 222 DATA AND APPLICATIONS SECURITY XVII parties. In addition, the analyzer is responsible for detecting any changes in the current CPVTs that it may have previously uploaded to RPs. For example, in a push model where the CPVA is responsible for updating the CPVTs at the RPs, the data analyzer should be able to upload the changes (or the new CPVTs) to the affected RPs. Since data analyzer is mainly responsible for constructing the CPVTs for the relying parties, the next task is to generate CPVTs from the mesh. There are several options in building the trees. The analyzer has the following four components. The Client Processor: The Client processor consolidates the data received from the various RPs that the CPVA serves. The CPVT Builder: The builder performs the primary action of building the CPVTs based on the information obtained from the Harvester and other CPVAs. The Builder builds the trees for different trust points according to particular input parameter set. Harvester Coordinator: This component interacts with the harvester to specify the information that the harvester needs to collect and feed the Scheduler with appropriate times for re-harvesting the data. Federation Coordinator: As shall be discussed in section 5, the CPVA scheme can be deployed in autonomous mode or in a federated mode. When the federated model is used, the data analyzer will collect CPVTs from other CPVAs and use them to build the CPVTs. 5. DEPLOYMENT OPTIONS WITH ECPV The ECPV scheme with CPVAs as primary components can be deployed in at least two ways: autonomous and federated. In the autonomous mode, the CPVA shall work in isolation to collect the data, to build the CPVTs, and serve only its clients. Certainly, this scheme is not highly scalable and does not offer high performance benefits in information processing. These disadvantages can be overcome by the federated mode of deployment where CPVAs would coordinate with another to build and to maintain the CPVTs in a highly scalable and distributed manner. 5.1 Autonomous harvesting When RPs handle certificates from a few domains, and the number of CAs are limited, autonomous harvesting works very well. In this method, each CPVA module is independent (of other CPVAs). Its harvester is
9 ECPV in Public-Key Infrastructure 223 responsible for contacting the individual CAs/OCSP responders/directory repositories to obtain the needed certificates, revocation lists, and certificate status responses. CPVA module is responsible for several RP s (say in its domain). It is responsible for harvesting data from CAs related to requests from its RPs. 5.2 Federated harvesting Once PKI technology becomes popular among the internet users, there would be thousands of CAs issuing certificates for their own specific domains. In other words, unlike a handful of CAs we currently have (e.g., Verisign, Entrust, etc.), there would be several autonomous ones issuing and managing certificates. In such an environment, it would not be possible for a single harvester to obtain information about all CAs, their CRLs, and the trust paths connecting them. 6. SECURITY, TRUST, AND PERFORMANCE ISSUES As stated already, the primary impetus for our work is two-fold: to simplify the task of relying parties by delegating some of the data collection and processing work to CPVAs; and to arrive at a scheme that is efficient and scalable. These objectives are to be achieved without compromising the security and trust offered by the traditional certificate path validation schemes. In this section, we briefly discuss our scheme in the context of security, trust and performance. 6.1 Security and Trust Aspects of ECPV schemes One of the primary concerns of a relying party in adopting the ECPV for path discovery and validation is of trust. In other words, why should a relying party trust that the information provided by CPVA is correct? This concern exists even with the current delegated path discovery and validation protocols [8,9]. But let us look at our schemes. Under autonomous deployment, where the CPVA collects all the needed information (e.g., CRLs, expiration times, OCSP responses, etc.) by itself and prepares customized CPVTs for each relying party, the solution is simple. A CPVA signs the provided CPVT. Thus, there is a guarantee that an impostor process has not supplied incorrect results. This also ensures non-
10 224 DATA AND APPLICATIONS SECURITY XVII repudiation. In fact, to encourage more RPs to use its service, a CPVA may offer some kind of a guarantee as is done by Digital Signature Trust ( in the case of public-key certificates. In addition, optionally, it provides all the information used to arrive at the CPVT. Since the information is itself signed by the providing entities (e.g., a CA digitally signs the CRL that it issues, and an OCSP responder signs its response), the evidence is self-explanatory and is trusted. Under federated deployment, a CPVA that provides the CPVT to a relying party is not necessarily the one that directly contacted the corresponding CAs. Instead, it may have received either the raw information or part of the trees from other CPVAs. So it appears that the trust is somewhat weakened. However, if each CPVA signs its response (e.g., partial trees) or simply forwards the CA signed raw information to its requester, then the concern is mitigated. For example, if each CPVA, when it receives a signed partial CPVT from another CPVA, checks the signature, prepares a new CPVT (if it merged several partial CPVTs into one), and digitally signs it, then there would be no problem of trust. The idea of providing guarantees (as in Digital Signature Trust discussed above) by each CPVA further enhances the trust aspects of using the CPVA servers. If the RP does not trust the CPVA, it can receive all the supporting data along with the CPVT and verify, this process is considerably faster than RP having to perform the path discovery process all by itself. 6.2 Performance aspects of CPVA schemes Let us consider CPVA and its impact on the relying parties. Clearly, a relying party is simplified due to the delegation of data collection and path construction to CPVA. This is similar to SCVP and DPD/DPV [8,9]. But CPVA significantly differs from other schemes in the information it provides to the RPs. While other schemes only provide the status information (yes/no/error/don t know) to an RP s request, CPVA empowers a relying party with validation trees that could be used by the RP to locally verify users certificates. In other words, the response time, or latency, of an RP is greatly improved due to CPVA. In addition, by providing policy-specific CPVTs, an RP is able handle requests with varied values. For example, if a request is for a low-value service, it could use a CPVT of a weaker trust assurance. On the other hand, for a high valued transaction it could use a CPVT with a strong trust assurance. In summary, by caching the CPVTs, the performance of the RPs is greatly improved. In addition, the CPVA can handle much larger number of RPs since it receives requests from RPs less frequently.
11 ECPV in Public-Key Infrastructure 225 Now let us look at the comparison between autonomous and federated schemes. Clearly, the load on CPVA is much larger in the autonomous scheme since its harvester is responsible for directly collecting data from all the required CAs. On the other hand, in federated mode, the load is distributed among several CPVAs. However, in this scheme, since the same request (and hence data) flows through several CPVAs, there is higher communication and processing overhead on the network and the intermediate CPVAs. But this scheme is highly scalable and has better performance than autonomous mode. Both schemes can greatly benefit from caching at the RPs and at the CPVAs. Since CA s certificates often have longer life and are less likely to be revoked, the CPVTs tend to have much longer validity periods. This means that a CPVT once uploaded to an RP can be used for quite some time to validate subject s certificate paths. In addition, the incremental approach of updating the trees along with the push/pull methods used to distribute the changes greatly enhances the performance of the RPs as well as the overall system Costs and benefits The performance of CPVA can best be quantified in terms of its costs and benefits when compared to traditional validation schemes. The following benefits are claimed performance advantages of CPVA over traditional schemes: Improved response time at RPs due to reduced time for certificate path validation. This implies that RP s response to user s service requests is improved. Improved system availability at RPs due to localized certificate path validation. This implies that the user requests are much more likely to be validated and serviced. Reduction in overall communication cost in the system due to harvesting at CPVA. This is due to the harvesting of CA and cross- CA certificate data ahead of time and using this information to supply validation trees to the RPs. However, these benefits are accrued at the following costs. Cost of harvesting. The harvester may collect more (bulk) information than needed. In addition, it needs to collect data to keep CPVA s validation trees up-to-date.
12 226 DATA AND APPLICATIONS SECURITY XVII Cost of analysis. The analyzer needs to analyze harvested data and build trees some of which may never be needed. In summary, while the RPs benefit by receiving the validation trees for local certificate path validations, the system of CPVAs place additional communication and computing overhead on the system. In this section, we provide a back-of-the-envelope analysis to quantify the costs and benefits Key Parameters influencing CPVA Performance While several parameters influence the performance of the proposed scheme, the following three parameters are the key factors. Validity period and revocation of CA-CA certificates: Each CA-cross certificate is valid for certain period of time. Unless its issuing CA revokes it, a cross certificate is valid until the specified expiration time. Whenever such a certificate expires or has been revoked, it results in the following costs for the CPVA: Communication cost for the harvester to collect information to update the validation data. Computation cost to select and rebuild the affected validation trees (if any). Communication cost to send updated trees to the affected RPs Rate of validation requests: Rate of validation requests of RPs determines how effectively the validation trees are being used by the RPs. For example, when the rate of requests is high, it implies that the savings due to local validation trees at RPs is high, and, hence, it may offset the cost of building, maintaining, and uploading of these trees to RPs. Maximum (trust) path length and topology: Wider adoption of PKI will necessitate greater number of CAs, probably with complex CA- CA trust relationships. For medium to low security applications, larger (5-10) values for the maximum path length can be adopted to facilitate wider acceptance of certificates.
13 ECPV in Public-Key Infrastructure CONCLUSIONS AND FUTURE WORK In this paper, we proposed an efficient certificate path validation scheme. In our scheme, a relying party receives a certificate path validation tree (CPVT) from the delegated server (CPVA). The tree is stored locally at the relying party. A relying party can now validate the path locally. The delegated server consists of a data harvester and a data analyzer. We proposed some implementation schemes for both these components. The local caching of CPVTs greatly reduces the overhead due to delegated server. At the same time, since a relying party is not responsible for collecting data from different CAs and OCSP responders on the internet, its software can still be simple. We have suggested several options for implementing the data harvester and the data analyzer. We have also shown that our scheme does not weaken the security and trust properties of delegation. We are currently looking into further design options for implementing the CPVA. One of our objectives is to improve the efficiency of harvester and analyzer. We are also looking into extending the representation structures from trees (CPVT) to other data structures. REFERENCES [1] [2] [3] [4] [5] [6] [7] [8] [9] [10] [11] C. Adams and S. Lloyd, Understanding Public-key Infrastructure: Concepts, Standards, and Deployment Considerations. Macmillan Technical Publishing, R. Housley, W. Ford, W. Polk, and D. Solo, Internet X.509 Public Key Infrastructure Certificate and CRL Profile, RFC 2459, January S. Lloyd (Editor), CA-CA Interoperability, White paper, PKI Forum, March Available at ( R. Moskowitz, An Unlikely PKI Cavalry, Network Computing, Security Watch Column, Nov A. Malpani, Bridge Validation Authority, White paper, Valicert, December 2001, Available at Malpani and R. Housley, Simple Certificate Validation Protocol (SCVP), Internet Draft, March S. Chokhani and W. Ford, Internet X.509 Public Key Infrastructure Certificate Policy and Certification Practices Framework, RFC 2527, March D. Pinkas and R. Housley, Delegated Path Validation and Delegated Path Discovery Protocol Requirements, Internet Draft, May D. Pinkas, Delegated Path Validation and Delegated Path Discovery Protocols, Internet Draft, July P. Hesse, Certification Path Development Software, Briefing to FPKITWG, April M. Branchaud and J. Linn, Extended Validation Models in PKI: Alternatives and Implications, Proc. 1st Annual PKI Research Workshop, Bethesda, Maryland, USA, April 16, 2002, pages:
14 228 DATA AND APPLICATIONS SECURITY XVII [12] [13] [14] [15] T. Cormen, C. Leiserson, and R. Rivest, Introduction to Algorithms, Prentice-Hall, December G. Coulouris, J. Dollimore, and T. Kindberg, Distributed Systems: Concepts and Design, Third Edition, Addison-Wesley, C. Bowman, P. Danzig and D. Hardy, Harvest: A Scalable. Customizable Discovery and Access System, Technical Report CU-CS , University of Colorado Boulder. G. Coulouris, J. Dollimore and T. Kindberg, Distributed Systems Concepts and Design, Addison-Wesley Publishers Limited, Third Edition 2001.
ECPV: Efficient Certificate Path Validation in Public-key Infrastructure 1
 ECPV: Efficient Certificate Path Validation in Public-key Infrastructure 1 M. Halappanavar R. Mukkamala Department of Computer Science Old Dominion University Norfolk, Virginia 23529-0162 {mhalappa, mukka}@cs.odu.edu
ECPV: Efficient Certificate Path Validation in Public-key Infrastructure 1 M. Halappanavar R. Mukkamala Department of Computer Science Old Dominion University Norfolk, Virginia 23529-0162 {mhalappa, mukka}@cs.odu.edu
Server-based Certificate Validation Protocol
 Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
Axway Validation Authority Suite
 Axway Validation Authority Suite PKI safeguards for secure applications Around the world, banks, healthcare organizations, governments, and defense agencies rely on public key infrastructures (PKIs) to
Axway Validation Authority Suite PKI safeguards for secure applications Around the world, banks, healthcare organizations, governments, and defense agencies rely on public key infrastructures (PKIs) to
PKI-An Operational Perspective. NANOG 38 ARIN XVIII October 10, 2006
 PKI-An Operational Perspective NANOG 38 ARIN XVIII October 10, 2006 Briefing Contents PKI Usage Benefits Constituency Acceptance Specific Discussion of Requirements Certificate Policy Certificate Policy
PKI-An Operational Perspective NANOG 38 ARIN XVIII October 10, 2006 Briefing Contents PKI Usage Benefits Constituency Acceptance Specific Discussion of Requirements Certificate Policy Certificate Policy
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename
 6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
X.509. CPSC 457/557 10/17/13 Jeffrey Zhu
 X.509 CPSC 457/557 10/17/13 Jeffrey Zhu 2 3 X.509 Outline X.509 Overview Certificate Lifecycle Alternative Certification Models 4 What is X.509? The most commonly used Public Key Infrastructure (PKI) on
X.509 CPSC 457/557 10/17/13 Jeffrey Zhu 2 3 X.509 Outline X.509 Overview Certificate Lifecycle Alternative Certification Models 4 What is X.509? The most commonly used Public Key Infrastructure (PKI) on
Public Key Infrastructure
 Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Internet Engineering Task Force (IETF) Request for Comments: 6490 Category: Standards Track. G. Michaelson APNIC. S. Kent BBN February 2012
 Internet Engineering Task Force (IETF) Request for Comments: 6490 Category: Standards Track ISSN: 2070-1721 G. Huston S. Weiler SPARTA, Inc. G. Michaelson S. Kent BBN February 2012 Abstract Resource Public
Internet Engineering Task Force (IETF) Request for Comments: 6490 Category: Standards Track ISSN: 2070-1721 G. Huston S. Weiler SPARTA, Inc. G. Michaelson S. Kent BBN February 2012 Abstract Resource Public
FPKIPA CPWG Antecedent, In-Person Task Group
 FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
FBCA Supplementary Antecedent, In-Person Definition This supplement provides clarification on the trust relationship between the Trusted Agent and the applicant, which is based on an in-person antecedent
PKI Services. Text PKI Definition. PKI Definition #1. Public Key Infrastructure. What Does A PKI Do? Public Key Infrastructures
 Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
ACVS: an Advanced Certificate Validation Service in Service-Oriented Architectures
 ACVS: an Advanced Certificate Validation Service in Service-Oriented Architectures Antonio Ruiz-Martínez 1, Daniel Sánchez-Martínez 1, C. Inmaculada Marín-López 1, Manuel Gil-Pérez 1, and Antonio F. Gómez-Skarmeta
ACVS: an Advanced Certificate Validation Service in Service-Oriented Architectures Antonio Ruiz-Martínez 1, Daniel Sánchez-Martínez 1, C. Inmaculada Marín-López 1, Manuel Gil-Pérez 1, and Antonio F. Gómez-Skarmeta
Next Generation Physical Access Control Systems A Smart Card Alliance Educational Institute Workshop
 Next Generation Physical Access Control Systems A Smart Card Alliance Educational Institute Workshop PACS Integration into the Identity Infrastructure Salvatore D Agostino CEO, IDmachines LLC 8 th Annual
Next Generation Physical Access Control Systems A Smart Card Alliance Educational Institute Workshop PACS Integration into the Identity Infrastructure Salvatore D Agostino CEO, IDmachines LLC 8 th Annual
DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure
 DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure Change Control Date Version Description of changes 15-December- 2016 1-December- 2016 17-March- 2016 4-February- 2016 3-February-
DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure Change Control Date Version Description of changes 15-December- 2016 1-December- 2016 17-March- 2016 4-February- 2016 3-February-
Copyright
 This video will look at the different components that make up Active Directory Certificate Services and which services you should look at installing these components on. Which components to install where?
This video will look at the different components that make up Active Directory Certificate Services and which services you should look at installing these components on. Which components to install where?
Public Key Infrastructures. Using PKC to solve network security problems
 Public Key Infrastructures Using PKC to solve network security problems Distributing public keys P keys allow parties to share secrets over unprotected channels Extremely useful in an open network: Parties
Public Key Infrastructures Using PKC to solve network security problems Distributing public keys P keys allow parties to share secrets over unprotected channels Extremely useful in an open network: Parties
Some Lessons Learned from Designing the Resource PKI
 Some Lessons Learned from Designing the Resource PKI Geoff Huston Chief Scientist, APNIC May 2007 Address and Routing Security The basic security questions that need to be answered are: Is this a valid
Some Lessons Learned from Designing the Resource PKI Geoff Huston Chief Scientist, APNIC May 2007 Address and Routing Security The basic security questions that need to be answered are: Is this a valid
Validation Policy r tra is g e R ANF AC MALTA, LTD
 Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
Certificateless Public Key Cryptography
 Certificateless Public Key Cryptography Mohsen Toorani Department of Informatics University of Bergen Norsk Kryptoseminar November 9, 2011 1 Public Key Cryptography (PKC) Also known as asymmetric cryptography.
Certificateless Public Key Cryptography Mohsen Toorani Department of Informatics University of Bergen Norsk Kryptoseminar November 9, 2011 1 Public Key Cryptography (PKC) Also known as asymmetric cryptography.
Public Key Establishment
 Public Key Establishment Bart Preneel Katholieke Universiteit Leuven February 2007 Thanks to Paul van Oorschot How to establish public keys? point-to-point on a trusted channel mail business card, phone
Public Key Establishment Bart Preneel Katholieke Universiteit Leuven February 2007 Thanks to Paul van Oorschot How to establish public keys? point-to-point on a trusted channel mail business card, phone
GLOBAL PKI TRENDS STUDY
 2018 GLOBAL PKI TRENDS STUDY Sponsored by Thales esecurity Independently conducted by Ponemon Institute LLC SEPTEMBER 2018 EXECUTIVE SUMMARY #2018GlobalPKI Mi Ponemon Institute is pleased to present the
2018 GLOBAL PKI TRENDS STUDY Sponsored by Thales esecurity Independently conducted by Ponemon Institute LLC SEPTEMBER 2018 EXECUTIVE SUMMARY #2018GlobalPKI Mi Ponemon Institute is pleased to present the
ODYSSEY. cryptic by intent. Odyssey Certrix FAQs. Odyssey Technologies Ltd
 Odyssey Certrix FAQs 1. What is Certrix? Odyssey Certrix suite of products provides a comprehensive solution that enables any organization or Trusted Third Party to run their own Certification Authority.
Odyssey Certrix FAQs 1. What is Certrix? Odyssey Certrix suite of products provides a comprehensive solution that enables any organization or Trusted Third Party to run their own Certification Authority.
Public. Atos Trustcenter. Server Certificates + Codesigning Certificates. Version 1.2
 Atos Trustcenter Server Certificates + Codesigning Certificates Version 1.2 20.11.2015 Content 1 Introduction... 3 2 The Atos Trustcenter Portfolio... 3 3 TrustedRoot PKI... 4 3.1 TrustedRoot Hierarchy...
Atos Trustcenter Server Certificates + Codesigning Certificates Version 1.2 20.11.2015 Content 1 Introduction... 3 2 The Atos Trustcenter Portfolio... 3 3 TrustedRoot PKI... 4 3.1 TrustedRoot Hierarchy...
WHITEPAPER. Vulnerability Analysis of Certificate Validation Systems
 WHITEPAPER Vulnerability Analysis of Certificate Validation Systems The US Department of Defense (DoD) has deployed one of the largest Public Key Infrastructure (PKI) in the world. It serves the Public
WHITEPAPER Vulnerability Analysis of Certificate Validation Systems The US Department of Defense (DoD) has deployed one of the largest Public Key Infrastructure (PKI) in the world. It serves the Public
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Background. Network Security - Certificates, Keys and Signatures - Digital Signatures. Digital Signatures. Dr. John Keeney 3BA33
 Background Network Security - Certificates, Keys and Signatures - Dr. John Keeney 3BA33 Slides Sources: Karl Quinn, Donal O Mahoney, Henric Johnson, Charlie Kaufman, Wikipedia, Google, Brian Raiter. Recommended
Background Network Security - Certificates, Keys and Signatures - Dr. John Keeney 3BA33 Slides Sources: Karl Quinn, Donal O Mahoney, Henric Johnson, Charlie Kaufman, Wikipedia, Google, Brian Raiter. Recommended
Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution
 Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University
Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University
Nov ember 14, Memo
 Memo Subject: Comparison of Validation Capabilities between Axway Desktop Validator and MS Windows Clients as well as Validation Authority Serv er and Windows Serv er Date: December 2016 1/5 1. Introduction
Memo Subject: Comparison of Validation Capabilities between Axway Desktop Validator and MS Windows Clients as well as Validation Authority Serv er and Windows Serv er Date: December 2016 1/5 1. Introduction
by Amy E. Smith, ShiuFun Poon, and John Wray
 Level: Intermediate Works with: Domino 6 Updated: 01-Oct-2002 by Amy E. Smith, ShiuFun Poon, and John Wray Domino 4.6 introduced the certificate authority (CA), a trusted server-based administration tool
Level: Intermediate Works with: Domino 6 Updated: 01-Oct-2002 by Amy E. Smith, ShiuFun Poon, and John Wray Domino 4.6 introduced the certificate authority (CA), a trusted server-based administration tool
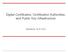
Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
![Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7. Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.](/thumbs/84/91191448.jpg) Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Issues. Separation of. Distributed system security. Security services. Security policies. Security mechanism
 Module 9 - Security Issues Separation of Security policies Precise definition of which entities in the system can take what actions Security mechanism Means of enforcing that policy Distributed system
Module 9 - Security Issues Separation of Security policies Precise definition of which entities in the system can take what actions Security mechanism Means of enforcing that policy Distributed system
SAML Metadata Signing gpolicy and Aggregation Practice Statement
 SAML Metadata Signing gpolicy and Aggregation Practice Statement Draft ftframework Presented at REFEDS, 5 th December 2008 Rodney McDuff, The University of Queensland r.mcduff@uq.edu.au Viviani Paz, AAF
SAML Metadata Signing gpolicy and Aggregation Practice Statement Draft ftframework Presented at REFEDS, 5 th December 2008 Rodney McDuff, The University of Queensland r.mcduff@uq.edu.au Viviani Paz, AAF
expires in six months October 1997 Internet Public Key Infrastructure Operational Protocols: FTP and HTTP <draft-ietf-pkix-opp-ftp-http-01.
 HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 06:26:48 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Tue, 21 Oct 1997 17:15:00 GMT ETag: "361b18-2953-344ce314" Accept-Ranges: bytes Content-Length: 10579 Connection:
HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 06:26:48 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Tue, 21 Oct 1997 17:15:00 GMT ETag: "361b18-2953-344ce314" Accept-Ranges: bytes Content-Length: 10579 Connection:
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Fourth edition 2001-08-01 Information technology Open Systems Interconnection The Directory: Public-key and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Fourth edition 2001-08-01 Information technology Open Systems Interconnection The Directory: Public-key and attribute certificate frameworks Technologies de l'information
Key Management and Distribution
 2 and Distribution : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 20 December 2015 css441y15s2l10, Steve/Courses/2015/s2/css441/lectures/key-management-and-distribution.tex,
2 and Distribution : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 20 December 2015 css441y15s2l10, Steve/Courses/2015/s2/css441/lectures/key-management-and-distribution.tex,
A CONFIDENCE MODEL BASED ROUTING PRACTICE FOR SECURE ADHOC NETWORKS
 A CONFIDENCE MODEL BASED ROUTING PRACTICE FOR SECURE ADHOC NETWORKS Ramya. S 1 and Prof. B. Sakthivel 2 ramyasiva.jothi@gmail.com and everrock17@gmail.com 1PG Student and 2 Professor & Head, Department
A CONFIDENCE MODEL BASED ROUTING PRACTICE FOR SECURE ADHOC NETWORKS Ramya. S 1 and Prof. B. Sakthivel 2 ramyasiva.jothi@gmail.com and everrock17@gmail.com 1PG Student and 2 Professor & Head, Department
Mavenir Systems Inc. SSX-3000 Security Gateway
 Secured by RSA Implementation Guide for 3rd Party PKI Applications Partner Information Last Modified: June 16, 2015 Product Information Partner Name Web Site Product Name Version & Platform Product Description
Secured by RSA Implementation Guide for 3rd Party PKI Applications Partner Information Last Modified: June 16, 2015 Product Information Partner Name Web Site Product Name Version & Platform Product Description
Scalable, Reliable Marshalling and Organization of Distributed Large Scale Data Onto Enterprise Storage Environments *
 Scalable, Reliable Marshalling and Organization of Distributed Large Scale Data Onto Enterprise Storage Environments * Joesph JaJa joseph@ Mike Smorul toaster@ Fritz McCall fmccall@ Yang Wang wpwy@ Institute
Scalable, Reliable Marshalling and Organization of Distributed Large Scale Data Onto Enterprise Storage Environments * Joesph JaJa joseph@ Mike Smorul toaster@ Fritz McCall fmccall@ Yang Wang wpwy@ Institute
Introduction to SSL. Copyright 2005 by Sericon Technology Inc.
 Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Lecture Notes 14 : Public-Key Infrastructure
 6.857 Computer and Network Security October 24, 2002 Lecture Notes 14 : Public-Key Infrastructure Lecturer: Ron Rivest Scribe: Armour/Johann-Berkel/Owsley/Quealy [These notes come from Fall 2001. These
6.857 Computer and Network Security October 24, 2002 Lecture Notes 14 : Public-Key Infrastructure Lecturer: Ron Rivest Scribe: Armour/Johann-Berkel/Owsley/Quealy [These notes come from Fall 2001. These
Network Working Group. Siemens Networks GmbH & Co KG February Online Certificate Status Protocol (OCSP) Extensions to IKEv2
 Network Working Group Request for Comments: 4806 Category: Standards Track M. Myers TraceRoute Security LLC H. Tschofenig Siemens Networks GmbH & Co KG February 2007 Online Certificate Status Protocol
Network Working Group Request for Comments: 4806 Category: Standards Track M. Myers TraceRoute Security LLC H. Tschofenig Siemens Networks GmbH & Co KG February 2007 Online Certificate Status Protocol
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Fifth edition 2005-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
Public Key Infrastructure scaling perspectives
 Public Key Infrastructure scaling perspectives Finseskolen 2012 Anders Fongen, PhD Norwegian Defence Research Establishment anders.fongen@ffi.no Outline of presentation Short intro to PKI architecture
Public Key Infrastructure scaling perspectives Finseskolen 2012 Anders Fongen, PhD Norwegian Defence Research Establishment anders.fongen@ffi.no Outline of presentation Short intro to PKI architecture
Direct, DirectTrust, and FHIR: A Value Proposition
 Direct, DirectTrust, and FHIR: A Value Proposition August 10, 2017 Authors: Grahame Grieve, HL7 Product Director for FHIR; David Kibbe, Luis Maas, Greg Meyer, and Bruce Schreiber, members of the DirectTrust
Direct, DirectTrust, and FHIR: A Value Proposition August 10, 2017 Authors: Grahame Grieve, HL7 Product Director for FHIR; David Kibbe, Luis Maas, Greg Meyer, and Bruce Schreiber, members of the DirectTrust
Category: Standards Track Microsoft May 2004
 Network Working Group Request for Comments: 3770 Category: Standards Track R. Housley Vigil Security T. Moore Microsoft May 2004 Status of this Memo Certificate Extensions and Attributes Supporting Authentication
Network Working Group Request for Comments: 3770 Category: Standards Track R. Housley Vigil Security T. Moore Microsoft May 2004 Status of this Memo Certificate Extensions and Attributes Supporting Authentication
Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure
 Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure 1.0 INTRODUCTION 1.1 Overview The Federal Reserve Banks operate a public key infrastructure (PKI) that manages
Certification Practice Statement of the Federal Reserve Banks Services Public Key Infrastructure 1.0 INTRODUCTION 1.1 Overview The Federal Reserve Banks operate a public key infrastructure (PKI) that manages
U.S. E-Authentication Interoperability Lab Engineer
 Using Digital Certificates to Establish Federated Trust chris.brown@enspier.com U.S. E-Authentication Interoperability Lab Engineer Agenda U.S. Federal E-Authentication Background Current State of PKI
Using Digital Certificates to Establish Federated Trust chris.brown@enspier.com U.S. E-Authentication Interoperability Lab Engineer Agenda U.S. Federal E-Authentication Background Current State of PKI
Certificates, Certification Authorities and Public-Key Infrastructures
 (Digital) Certificates Certificates, Certification Authorities and Public-Key Infrastructures We need to be sure that the public key used to encrypt a message indeed belongs to the destination of the message
(Digital) Certificates Certificates, Certification Authorities and Public-Key Infrastructures We need to be sure that the public key used to encrypt a message indeed belongs to the destination of the message
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
Development Authority of the North Country Governance Policies
 Development Authority of the North Country Governance Policies Subject: Electronic Signature Policy Adopted: March 28, 2018 (Annual Meeting) Resolution: 2018-03-35 Table of Contents SECTION 1.0 INTRODUCTION...
Development Authority of the North Country Governance Policies Subject: Electronic Signature Policy Adopted: March 28, 2018 (Annual Meeting) Resolution: 2018-03-35 Table of Contents SECTION 1.0 INTRODUCTION...
3GPP TR V6.0.0 ( )
 TR 33.810 V6.0.0 (2002-12) Technical Report 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; 3G Security; Network Domain Security / Authentication Framework
TR 33.810 V6.0.0 (2002-12) Technical Report 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; 3G Security; Network Domain Security / Authentication Framework
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
What is a Digital Certificate? Basic Problem. Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Bart Preneel PKI. February Public Key Establishment. PKI Overview. Keys and Lifecycle Management. How to establish public keys?
 art Preneel How to establish public keys? Public Key Establishment art Preneel Katholieke Universiteit Leuven Thanks to Paul van Oorschot point-to-point on a trusted channel mail business card, phone direct
art Preneel How to establish public keys? Public Key Establishment art Preneel Katholieke Universiteit Leuven Thanks to Paul van Oorschot point-to-point on a trusted channel mail business card, phone direct
CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University
![CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University](/thumbs/95/125142682.jpg) CS 555: DISTRIBUTED SYSTEMS [P2P SYSTEMS] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey Byzantine failures vs malicious nodes
CS 555: DISTRIBUTED SYSTEMS [P2P SYSTEMS] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey Byzantine failures vs malicious nodes
CERTIFICATE POLICY CIGNA PKI Certificates
 CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
IBM. Security Digital Certificate Manager. IBM i 7.1
 IBM IBM i Security Digital Certificate Manager 7.1 IBM IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in
IBM IBM i Security Digital Certificate Manager 7.1 IBM IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in
Digital Certificates Demystified
 Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Internet Engineering Task Force (IETF) Request for Comments: 6961 June 2013 Category: Standards Track ISSN:
 Internet Engineering Task Force (IETF) Y. Pettersen Request for Comments: 6961 June 2013 Category: Standards Track ISSN: 2070-1721 Abstract The Transport Layer Security (TLS) Multiple Certificate Status
Internet Engineering Task Force (IETF) Y. Pettersen Request for Comments: 6961 June 2013 Category: Standards Track ISSN: 2070-1721 Abstract The Transport Layer Security (TLS) Multiple Certificate Status
Federal PKI. Trust Store Management Guide
 Federal PKI Trust Store Management Guide V1.0 September 21, 2015 FINAL Disclaimer The Federal PKI Management Authority (FPKIMA) has designed and created the Trust Store Management Guide as an education
Federal PKI Trust Store Management Guide V1.0 September 21, 2015 FINAL Disclaimer The Federal PKI Management Authority (FPKIMA) has designed and created the Trust Store Management Guide as an education
Authorization and Certificates: Are We Pushing When We Should Be Pulling?
 Authorization and Certificates: Are We Pushing When We Should Be Pulling? Jason Crampton Hemanth Khambhammettu Information Security Group, Royal Holloway, University of London Egham, TW20 0EX, United Kingdom
Authorization and Certificates: Are We Pushing When We Should Be Pulling? Jason Crampton Hemanth Khambhammettu Information Security Group, Royal Holloway, University of London Egham, TW20 0EX, United Kingdom
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
Intended Category: Standards Track Expires March 2006 September 2005
 INTERNET-DRAFT S. Santesson (Microsoft) Intended Category: Standards Track Expires March 2006 September 2005 Internet X.509 Public Key Infrastructure Subject Alternative Name for expression of service
INTERNET-DRAFT S. Santesson (Microsoft) Intended Category: Standards Track Expires March 2006 September 2005 Internet X.509 Public Key Infrastructure Subject Alternative Name for expression of service
Manage Certificates. Certificates Overview
 Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
Certificate Revocation : A Survey
 Certificate Revocation : A Survey Gaurav Jain Computer Science Department University of Pennsylvania. Abstract With the increasing acceptance of digital certificates, there has been a gaining impetus for
Certificate Revocation : A Survey Gaurav Jain Computer Science Department University of Pennsylvania. Abstract With the increasing acceptance of digital certificates, there has been a gaining impetus for
PKI Interoperability Test Tool v1.2 (PITT) Usage Guide
 PKI Interoperability Test Tool v1.2 (PITT) Usage Guide Last updated: September 2010 Table of Contents 1 Introduction... 4 2 Installation... 4 3 Quick Start Guide... 8 3.1 Default settings... 8 4 Menus...
PKI Interoperability Test Tool v1.2 (PITT) Usage Guide Last updated: September 2010 Table of Contents 1 Introduction... 4 2 Installation... 4 3 Quick Start Guide... 8 3.1 Default settings... 8 4 Menus...
API Gateway Version September Validation Authority Interoperability Guide
 API Gateway Version 7.5.3 17 September 2018 Validation Authority Interoperability Guide Copyright 2018 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway
API Gateway Version 7.5.3 17 September 2018 Validation Authority Interoperability Guide Copyright 2018 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Version 3 X.509 Certificates
 Entrust Technologies White Paper Author: Ian Curry Date: July 1996 Version: 1.0 Entrust Technologies, 1997. All rights reserved. 1 1. Introduction This document provides a description of the version 3
Entrust Technologies White Paper Author: Ian Curry Date: July 1996 Version: 1.0 Entrust Technologies, 1997. All rights reserved. 1 1. Introduction This document provides a description of the version 3
there are multiple instances where two unknown parties in different branches
 Chapter 2 Literature Survey 2.1 Overview For more than two decades researchers have put much effort in developing security methodologies, models and standard definitions of security services. However,
Chapter 2 Literature Survey 2.1 Overview For more than two decades researchers have put much effort in developing security methodologies, models and standard definitions of security services. However,
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Apple Corporate Certificates Certificate Policy and Certification Practice Statement. Apple Inc.
 Apple Inc. Certificate Policy and Certification Practice Statement Version 1.0 Effective Date: March 12, 2015 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2. Table of acronyms... 4 1.3.
Apple Inc. Certificate Policy and Certification Practice Statement Version 1.0 Effective Date: March 12, 2015 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2. Table of acronyms... 4 1.3.
Helping Meet the OMB Directive
 Helping Meet the OMB 11-11 Directive March 2017 Implementing federated identity management OMB Memo 11-11 Meeting FICAM Objectives Figure 1: ICAM Conceptual Diagram FICAM Targets Figure 11: Federal Enterprise
Helping Meet the OMB 11-11 Directive March 2017 Implementing federated identity management OMB Memo 11-11 Meeting FICAM Objectives Figure 1: ICAM Conceptual Diagram FICAM Targets Figure 11: Federal Enterprise
Cristina Nita-Rotaru. CS355: Cryptography. Lecture 17: X509. PGP. Authentication protocols. Key establishment.
 CS355: Cryptography Lecture 17: X509. PGP. Authentication protocols. Key establishment. Public Keys and Trust Public Key:P A Secret key: S A Public Key:P B Secret key: S B How are public keys stored How
CS355: Cryptography Lecture 17: X509. PGP. Authentication protocols. Key establishment. Public Keys and Trust Public Key:P A Secret key: S A Public Key:P B Secret key: S B How are public keys stored How
Video Surveillance Solutions from EMC and Brocade: Scalable and Future-proof
 White Paper Video Surveillance Solutions from EMC and Brocade: Scalable and Future-proof By Dan Conde, Analyst December 2015 This ESG White Paper was commissioned by EMC and Brocade and is distributed
White Paper Video Surveillance Solutions from EMC and Brocade: Scalable and Future-proof By Dan Conde, Analyst December 2015 This ESG White Paper was commissioned by EMC and Brocade and is distributed
Reducing the Cost of Certificate Revocation for improved scalability
 NTNU NORWEGIAN UNIVERSITY OF SCIENCE AND TECHNOLOGY Reducing the of Certificate Revocation for improved scalability: A Case Study Mona Holsve Ofigsbø 10 Dec 2009 Reducing the of Certificate Revocation
NTNU NORWEGIAN UNIVERSITY OF SCIENCE AND TECHNOLOGY Reducing the of Certificate Revocation for improved scalability: A Case Study Mona Holsve Ofigsbø 10 Dec 2009 Reducing the of Certificate Revocation
A PKI For IDR Public Key Infrastructure and Number Resource Certification
 A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
Certificate Revocation: What Is It and What Should It Be
 University of the Aegean De Facto Joint Research Group Certificate Revocation: What Is It and What Should It Be John Iliadis 1,2, Stefanos Gritzalis 1 1 Department of Information and Communication Systems
University of the Aegean De Facto Joint Research Group Certificate Revocation: What Is It and What Should It Be John Iliadis 1,2, Stefanos Gritzalis 1 1 Department of Information and Communication Systems
PAA PKI Mutual Recognition Framework. Copyright PAA, All Rights Reserved 1
 PAA PKI Mutual Recognition Framework Copyright PAA, 2009. All Rights Reserved 1 Agenda Overview of the Framework Components of the Framework How It Works Other Considerations Questions and Answers Copyright
PAA PKI Mutual Recognition Framework Copyright PAA, 2009. All Rights Reserved 1 Agenda Overview of the Framework Components of the Framework How It Works Other Considerations Questions and Answers Copyright
CIP Security Pull Model from the Implementation Standpoint
 CIP Security Pull Model from the Implementation Standpoint Jack Visoky Security Architect and Sr. Project Engineer Rockwell Automation Joakim Wiberg Team Manager Technology and Platforms HMS Industrial
CIP Security Pull Model from the Implementation Standpoint Jack Visoky Security Architect and Sr. Project Engineer Rockwell Automation Joakim Wiberg Team Manager Technology and Platforms HMS Industrial
Considerations for using short-term certificates
 Considerations for using short-term certificates draft-nir-saag-star Yoav Nir Thomas Fossati Yaron Sheffer Toerless Eckert Why are we doing this? Lots of interest in short-term certificates In the standards
Considerations for using short-term certificates draft-nir-saag-star Yoav Nir Thomas Fossati Yaron Sheffer Toerless Eckert Why are we doing this? Lots of interest in short-term certificates In the standards
Guide to Deploying VMware Workspace ONE. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1
 Guide to Deploying VMware Workspace ONE DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Guide to Deploying VMware Workspace ONE DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Smart Grid Security. Selected Principles and Components. Tony Metke Distinguished Member of the Technical Staff
 Smart Grid Security Selected Principles and Components Tony Metke Distinguished Member of the Technical Staff IEEE PES Conference on Innovative Smart Grid Technologies Jan 2010 Based on a paper by: Anthony
Smart Grid Security Selected Principles and Components Tony Metke Distinguished Member of the Technical Staff IEEE PES Conference on Innovative Smart Grid Technologies Jan 2010 Based on a paper by: Anthony
NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY
 NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Standardization of Entity Authentication Assurance 5th ETSI Security Workshop 20-2222 January 2010 ETSI, Sophia Antipolis, France Erika McCallister, Esq.,
NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Standardization of Entity Authentication Assurance 5th ETSI Security Workshop 20-2222 January 2010 ETSI, Sophia Antipolis, France Erika McCallister, Esq.,
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 9594-8 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
INTERNATIONAL STANDARD ISO/IEC 9594-8 Sixth edition 2008-12-15 Information technology Open Systems Interconnection The Directory: Publickey and attribute certificate frameworks Technologies de l'information
UELMA Exploring Authentication Options Nov 4, 2011
 UELMA Exploring Authentication Options Nov 4, 2011 A U T H E N T I C A T I O N M E T H O D S P R E L I M I N A R Y R E P O R T B R A D L E E C H A N G X C E N T I A L G R O U P B R A D @ X C E N T I A
UELMA Exploring Authentication Options Nov 4, 2011 A U T H E N T I C A T I O N M E T H O D S P R E L I M I N A R Y R E P O R T B R A D L E E C H A N G X C E N T I A L G R O U P B R A D @ X C E N T I A
SERIES X: DATA NETWORKS, OPEN SYSTEM COMMUNICATIONS AND SECURITY Secure applications and services Security protocols
 I n t e r n a t i o n a l T e l e c o m m u n i c a t i o n U n i o n ITU-T X.1159 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (11/2014) SERIES X: DATA NETWORKS, OPEN SYSTEM COMMUNICATIONS AND SECURITY
I n t e r n a t i o n a l T e l e c o m m u n i c a t i o n U n i o n ITU-T X.1159 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (11/2014) SERIES X: DATA NETWORKS, OPEN SYSTEM COMMUNICATIONS AND SECURITY
Expires: 11 October April 2002
 Internet-Draft AAAarch RG Intended Category: Informational David Chadwick University of Salford Expires: 11 October 2002 11 April 2002 The PERMIS X.509 Based Privilege Management Infrastructure
Internet-Draft AAAarch RG Intended Category: Informational David Chadwick University of Salford Expires: 11 October 2002 11 April 2002 The PERMIS X.509 Based Privilege Management Infrastructure
KeyOne. Certification Authority
 Certification Description KeyOne public key infrastructure (PKI) solution component that provides certification authority (CA) functions. KeyOne CA provides: Public key infrastructure deployment for governments,
Certification Description KeyOne public key infrastructure (PKI) solution component that provides certification authority (CA) functions. KeyOne CA provides: Public key infrastructure deployment for governments,
A Survey Paper on Grid Information Systems
 B 534 DISTRIBUTED SYSTEMS A Survey Paper on Grid Information Systems Anand Hegde 800 North Smith Road Bloomington Indiana 47408 aghegde@indiana.edu ABSTRACT Grid computing combines computers from various
B 534 DISTRIBUTED SYSTEMS A Survey Paper on Grid Information Systems Anand Hegde 800 North Smith Road Bloomington Indiana 47408 aghegde@indiana.edu ABSTRACT Grid computing combines computers from various
Internet Engineering Task Force (IETF) Category: Informational ISSN: February 2012
 Internet Engineering Task Force (IETF) G. Huston Request for Comments: 6483 G. Michaelson Category: Informational APNIC ISSN: 2070-1721 February 2012 Abstract Validation of Route Origination Using the
Internet Engineering Task Force (IETF) G. Huston Request for Comments: 6483 G. Michaelson Category: Informational APNIC ISSN: 2070-1721 February 2012 Abstract Validation of Route Origination Using the
Guide to Deploying VMware Workspace ONE. VMware Identity Manager VMware AirWatch 9.1
 Guide to Deploying VMware Workspace ONE VMware Identity Manager 2.9.1 VMware AirWatch 9.1 Guide to Deploying VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware
Guide to Deploying VMware Workspace ONE VMware Identity Manager 2.9.1 VMware AirWatch 9.1 Guide to Deploying VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware
eidas Interoperability Architecture Version November 2015
 eidas Interoperability Architecture Version 1.00 6. November 2015 1 Introduction This document specifies the interoperability components of the eidas-network, i.e. the components necessary to achieve interoperability
eidas Interoperability Architecture Version 1.00 6. November 2015 1 Introduction This document specifies the interoperability components of the eidas-network, i.e. the components necessary to achieve interoperability
SSL Certificates Certificate Policy (CP)
 SSL Certificates Last Revision Date: February 26, 2015 Version 1.0 Revisions Version Date Description of changes Author s Name Draft 17 Jan 2011 Initial Release (Draft) Ivo Vitorino 1.0 26 Feb 2015 Full
SSL Certificates Last Revision Date: February 26, 2015 Version 1.0 Revisions Version Date Description of changes Author s Name Draft 17 Jan 2011 Initial Release (Draft) Ivo Vitorino 1.0 26 Feb 2015 Full
SHA-1 to SHA-2. Migration Guide
 SHA-1 to SHA-2 Migration Guide Web-application attacks represented 40 percent of breaches in 2015. Cryptographic and server-side vulnerabilities provide opportunities for cyber criminals to carry out ransomware
SHA-1 to SHA-2 Migration Guide Web-application attacks represented 40 percent of breaches in 2015. Cryptographic and server-side vulnerabilities provide opportunities for cyber criminals to carry out ransomware
A VO-friendly, Community-based Authorization Framework
 A VO-friendly, Community-based Authorization Framework Part 1: Use Cases, Requirements, and Approach Ray Plante and Bruce Loftis NCSA Version 0.1 (February 11, 2005) Abstract The era of massive surveys
A VO-friendly, Community-based Authorization Framework Part 1: Use Cases, Requirements, and Approach Ray Plante and Bruce Loftis NCSA Version 0.1 (February 11, 2005) Abstract The era of massive surveys
Online Certificate Status Protocol (OCSP) Extensions
 : Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages, standards
: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages, standards
Public Key Infrastructures
 Foundations for secure e-commerce (bmevihim219) Dr. Levente Buttyán associate professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) buttyan@hit.bme.hu,
Foundations for secure e-commerce (bmevihim219) Dr. Levente Buttyán associate professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) buttyan@hit.bme.hu,
Standard Certificate Extensions (1.)
 Standard Certificate Extensions (1.) version 3 introduces a mechanism whereby certificates can be extended, in a standardized and generic fashion, to include additional information; certificates are not
Standard Certificate Extensions (1.) version 3 introduces a mechanism whereby certificates can be extended, in a standardized and generic fashion, to include additional information; certificates are not
Better Mutual Authentication Project
 Better Mutual Authentication Project Recommendations & Requirements for Improving Web Authentication for Retail Financial Services Presented to W3C Workshop on: Transparency & Usability of Web Authentication
Better Mutual Authentication Project Recommendations & Requirements for Improving Web Authentication for Retail Financial Services Presented to W3C Workshop on: Transparency & Usability of Web Authentication
