Troubleshooting. EAP-FAST Error Messages CHAPTER
|
|
|
- Piers Newton
- 5 years ago
- Views:
Transcription
1 CHAPTER 6 This chapter describes EAP-FAST error messages. This chapter also provides guidelines for creating strong passwords. The following topics are covered in this chapter:, page 6-1 Creating Strong Passwords, page 6-6 Automatic PAC provisioning is enabled for this profile. However, a valid PAC that matches the server to which the client adapter is connecting could not be found. Do you wish to obtain a new security credential (PAC)? Click Yes to provision a new PAC for this server using your existing credentials or click No to cancel the operation. If you click No, the client adapter will fail the authentication. Caution To prevent possible attacks from rogue access points, do not reprovision a PAC unless it is necessary. While attempting to provision your PAC during auto-provisioning, the network access device failed to authenticate itself. This condition might indicate an attack on your password by a rogue access device. Try again with your current password? Click Yes to attempt to reauthenticate with your current password. Click No to cancel the operation. Note If the authentication attempt fails again, contact your system administrator to report a rogue access device. Use strong passwords in the future to reduce the chance of your password being compromised; see the Creating Strong Passwords section on page 6-6 for tips on creating strong passwords. 6-1
2 While attempting to provision your PAC, the network access device timed out. A timeout might indicate an attack on your password by a rogue access device. However, a timeout could be caused by a server outage or a faulty connection. Try again with your current password? Click Yes to attempt to reauthenticate with your current password. Click No to cancel the operation. Note If a timeout occurs again, contact your system administrator to report a potential rogue access device. Use strong passwords in the future to reduce the chance of your password being compromised; see the Creating Strong Passwords section on page 6-6 for tips on creating strong passwords. A valid PAC was not found for your username <username>. Click OK. Re-enter your username in the credential prompt or the User Credentials tab of the EAP-FAST Properties screen. If you entered your username correctly, go to the Connection tab of the EAP-FAST Properties screen either to enable automatic PAC provisioning or Validate server certificate or import a PAC file. Re-enter your username. Click OK. Then perform one of the following: If you entered your username correctly, go to the Connection tab of the EAP-FAST Properties screen either to enable automatic PAC provisioning or to import a PAC file. The EAP-FAST authentication attempt failed because you entered the wrong username and password. Please re-enter your username and password. Click OK. Then re-enter your EAP-FAST credentials when the Enter Wireless Network Password screen appears. The EAP-FAST authentication attempt failed because you might have entered the wrong username and password. Please re-enter your username and password. Warning: If you are sure that you have typed in the right username and password, you may have connected to a rogue device. This can indicate an attack on your password. Using a strong password will reduce the chance of your password being compromised. If this failure happens again, contact your system administrator to report a potential rogue access device. Click OK. Then perform one of the following: If you entered your EAP-FAST credentials correctly, contact your system administrator to report a potential rogue access point. Use strong passwords in the future to reduce the chance of your password being compromised. See the Creating Strong Passwords section on page 6-6 for tips on creating strong passwords. If you entered your EAP-FAST credentials incorrectly, re-enter your credentials at the Enter Wireless Network Password screen. 6-2
3 If the username does not match the provisioned PAC, and automatic provisioning is enabled for this profile, click Yes at the following message: You do not appear to be registered with the authentication server. Registration requires that this device be initialized with a security credential. Do you wish to obtain a security credential? If the username does not match the provisioned PAC, and manual provisioning is enabled for this profile, go to the Connection tab of the EAP-FAST properties dialog box and either enable automatic PAC provisioning or import a PAC file. PAC provisioning has failed. This failure is not related to an issue with the username and password. This failure is commonly caused by a server configuration issue. Contact your administrator for assistance. Contact your system administrator for assistance. The PAC that you selected for this profile does not match the server to which the client is connecting. However, a matching PAC has been found in your PAC database. Would you like to use this matching credential authority and save it to the profile? Click Yes to use the matching PAC and to update the profile with this new PAC, or click No to cancel the operation and to leave the profile as it is. If you click No, the client adapter will be unable to authenticate using the existing profile. You entered different values in the New Password field and the Confirm New Password field. The passwords must be identical. Please try again. Re-enter your new password in both fields. The password that you entered in the Old Password field does not match the password that you previously used. Please try again. Re-enter your old password in the Old Password field. An error occurred when you attempted to change your EAP-FAST password. The new password might not conform to the server's password policy. Please try again. Re-enter your password in the Change Password screen. The EAP-FAST authentication process failed during initialization. Make sure that EAP-FAST and the Trusted Root Certificate Authority certificate are installed correctly. Ensure that EAP-FAST and the Trusted Root Certificate Authority certificate are installed correctly. 6-3
4 You have connected to a server with the following server name <server_name> The server certificate is signed by the following Root Certification Authority (CA): <root_ca> This Root CA does not match the specified trusted Root CA(s). Do you want to accept this connection? Warning: Connecting to a server signed with untrusted CA might compromise your security. If you want the client adapter to connect to this server even though doing so might present a security risk, click Yes. Otherwise, click No. You have connected to a server with the following server name: <server_name> This server name does not match the specified server name(s). Do you want to accept this connection? Warning: Connecting to an unsecured server might compromise your security. If you want the client adapter to connect to this server even though doing so might present a security risk, click Yes. Otherwise, click No. Your password has expired. Please enter a new password. Enter a new password to change the expired password. You entered an empty username, which is not allowed. Enter a username. You must select a PAC when using manual PAC provisioning. You clicked OK on the EAP-FAST Properties screen when automatic provisioning was disabled and no PAC authority was selected. Either enable automatic provisioning or choose a PAC authority from the drop-down list. If the list is empty, import a PAC file. Error opening or reading file: <filename>. Try to import the PAC file again. If the same message appears, obtain a new PAC file from your system administrator and import it again. 6-4
5 The file is not a valid PAC file: <filename>. Try to import the PAC file again. If the same message appears, obtain a new PAC file from your system administrator and import it again. The file does not contain a valid PAC: <filename>. Try to import the PAC file again. If the same message appears, obtain a new PAC file from your system administrator and import it using the EAP-FAST Settings screen. The file contains a PAC that will replace an existing PAC already provisioned on your system. Would you like to replace the existing PAC? Click Yes to replace the existing PAC with the new one from the imported file, or click No to cancel the operation. try again. The password you entered to import the PAC file is incorrect. Please Try entering your password again. The PAC file import operation has been aborted because of three or more attempts of incorrect passwords. Press OK to continue. An internal error occurred. the PAC again. An internal error occurred when the PAC was being imported. Try importing Insufficient memory or other system error. Close other programs and free up some more memory. You must select Validate server certificate or a PAC to use user's certificate or one-time password for authentication. One-time password or user certificate is selected as the user credential, but there is no PAC selected or Validate Server Certificate option is not checked. Change the settings. You tried to import a PAC file with the same PAC ID as a previously imported or provisioned PAC. Would you like to replace the existing PAC? Click Yes to replace the existing PAC with the new one from the imported file, or click No to cancel the operation. 6-5
6 Creating Strong Passwords Creating Strong Passwords Never write passwords down, on paper or online. Instead, create passwords that you can remember easily but no one can guess easily. One way to do this is create a password that is based on a song title, affirmation, or other phrase. For example, the phrase could be This May Be One Way To Remember and the password could be TmB1w2R! or Tmb1W>r~ or some other variation. Note Do not use either of those examples as passwords. Characteristics of Strong Passwords Strong passwords have the following characteristics: Contain both upper and lower case characters (e.g., a-z, A-Z). Contain numerals and punctuation as well as letters (e.g., 0-9,!@#$%^&*()_+ ~ =\`{}[]:";'<>?,./) Are at least five alphanumeric characters long. Are not a word in any language. Are not slang, dialect, or jargon. Are not based on personal information, such as the names of family members. Characteristics of Weak Passwords A weak password has the following characteristics: Contains fewer than eight characters. Is a word found in a dictionary (English or foreign) Is any other term that is easily guessed or found in common usage. The following are examples of terms that are easily guessed: The name of family, pet, friend, coworker, or fantasy character. A computing term or name, such as a command, site, company, model, or application. A birthday or another kind of personal information, such as an address or telephone number. A predictable letter pattern or number pattern, such as aaabbb, qwerty, zyxwvuts, or Any of the above spelled backwards. Any of the above preceded or followed by a digit. Password Security Basics Follow these basic guidelines when dealing with passwords: Never reveal a password, even to family members. Never talk about a password in front of others. Never hint at the format of a password (such as my family name ). 6-6
7 Creating Strong Passwords Never use characters from outside the standard ASCII character set. Some symbols, such the pound sterling symbol ( ), are known to cause login problems on some systems. 6-7
8 Creating Strong Passwords 6-8
Password Policy Best Practices
 Password Policy Best Practices 1.0 Overview Passwords are an important aspect of information security, and are the front line of protection for user accounts. A poorly chosen password may result in the
Password Policy Best Practices 1.0 Overview Passwords are an important aspect of information security, and are the front line of protection for user accounts. A poorly chosen password may result in the
TABLE OF CONTENTS. Lakehead University Password Maintenance Standard Operating Procedure
 TABLE OF CONTENTS 1.0 General Statement... 3 2.0 Purpose... 3 3.0 Scope... 3 4.0 Procedure... 3 4.1 General... 3 4.2 Requirements... 4 4.3 Guidelines... 4 5.0 Failure to comply... 6 2 1.0 GENERAL STATEMENT
TABLE OF CONTENTS 1.0 General Statement... 3 2.0 Purpose... 3 3.0 Scope... 3 4.0 Procedure... 3 4.1 General... 3 4.2 Requirements... 4 4.3 Guidelines... 4 5.0 Failure to comply... 6 2 1.0 GENERAL STATEMENT
PASSWORD POLICY. Policy Statement. Reason for Policy/Purpose. Who Needs to Know This Policy. Website Address for this Policy.
 Responsible University Administrator: Vice Provost for Academic Affairs Responsible Officer: Chief Information Officer Origination Date: N/A Current Revision Date: 02/19/13 Next Review Date: 02/19/17 End
Responsible University Administrator: Vice Provost for Academic Affairs Responsible Officer: Chief Information Officer Origination Date: N/A Current Revision Date: 02/19/13 Next Review Date: 02/19/17 End
COMPUTER PASSWORDS POLICY
 COMPUTER PASSWORDS POLICY 1.0 PURPOSE This policy describes the requirements for acceptable password selection and maintenance to maximize security of the password and minimize its misuse or theft. Passwords
COMPUTER PASSWORDS POLICY 1.0 PURPOSE This policy describes the requirements for acceptable password selection and maintenance to maximize security of the password and minimize its misuse or theft. Passwords
Using EAP Authentication
 CHAPTER 6 This chapter explains the sequence of events that occurs and the actions you must take when a profile that is set for EAP authentication is selected for use. The following topics are covered
CHAPTER 6 This chapter explains the sequence of events that occurs and the actions you must take when a profile that is set for EAP authentication is selected for use. The following topics are covered
Benefits of Cloud Computing
 Cloud Computing Deployment Models Public Cloud Systems and services easily accessed by the general public. Less secure. Private Cloud Systems and Services accessed within an organisation. Increased security
Cloud Computing Deployment Models Public Cloud Systems and services easily accessed by the general public. Less secure. Private Cloud Systems and Services accessed within an organisation. Increased security
Create strong passwords
 Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Securewireless Windows 7 Setup Guide
 Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Configuring EAP-FAST CHAPTER
 CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
Instructions for connecting to winthropsecure
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Hitachi High Technologies America, Inc. Password Policy
 Hitachi High Technologies America, Inc. Password Policy Revision Date: 4/17/2015 Table of Contents Table of Contents...2 Overview...3 Scope. 3 Guidelines...3 A. General Password Construction Guidelines...3
Hitachi High Technologies America, Inc. Password Policy Revision Date: 4/17/2015 Table of Contents Table of Contents...2 Overview...3 Scope. 3 Guidelines...3 A. General Password Construction Guidelines...3
ADP Security Management Service
 ADP Security Management Service Securing Administrator Accounts Updated March 2017 Welcome! Your administrators complete the security registration process to access the ADP services your organization has
ADP Security Management Service Securing Administrator Accounts Updated March 2017 Welcome! Your administrators complete the security registration process to access the ADP services your organization has
Contents About This Guide... 5 About Notifications... 5 Managing User Accounts... 6 Managing Companies Managing Password Policies...
 Cloud Services Identity Management Administration Guide Version 17 July 2017 Contents About This Guide... 5 About Notifications... 5 Managing User Accounts... 6 About the User Administration Table...
Cloud Services Identity Management Administration Guide Version 17 July 2017 Contents About This Guide... 5 About Notifications... 5 Managing User Accounts... 6 About the User Administration Table...
Manually Configuring Windows 7 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Minimum Standards for Connecting to the UCLA Network
 Minimum Standards for Connecting to the UCLA Network Last April, the CSG approved a set of minimum standards for connecting to the UCLA network that were based on a policy that had been developed by Berkeley.
Minimum Standards for Connecting to the UCLA Network Last April, the CSG approved a set of minimum standards for connecting to the UCLA network that were based on a policy that had been developed by Berkeley.
Contents. Windows 7 Instructions Windows 10 Instructions Android Instructions Mac OS Instructions ios Instructions...
 The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
Manually Configuring Windows 8 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Configuring Role-Based Access Control
 Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 3 Privileges, page 4 User
Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 3 Privileges, page 4 User
ConnectUPS-X / -BD /-E How to use and install SSL, SSH
 ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
Configuring Microsoft Outlook to Connect to Hosted Exchange Service
 Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring 802.1X Settings on the WAP351
 Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Connecting to the NJITSecure wireless network.
 Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
ADP Security Management Service
 ADP Security Management Service Securing Administrator Accounts Updated May 2018 Welcome, A New Sign in Experience Awaits You ADP is committed to continuous process improvements to reduce friction and
ADP Security Management Service Securing Administrator Accounts Updated May 2018 Welcome, A New Sign in Experience Awaits You ADP is committed to continuous process improvements to reduce friction and
Configure Wireless for Windows 7
 Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
To Activate your Wireless Account
 To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
Configuring Facebook for a More Secure Social Networking Experience
 CPF 00004-16-CID361-9H-Facebook* 8 March 2017 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Account
CPF 00004-16-CID361-9H-Facebook* 8 March 2017 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Account
How to configure SecureW2
 How to configure SecureW2 Disclaimer The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright Notice
How to configure SecureW2 Disclaimer The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright Notice
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
HCC Wireless Instructions for Windows 10 (long version)
 HCC Wireless Instructions for Windows 10 (long version) TIP: If you are having trouble connecting to the wireless network, or if just need some friendly guidance, the Library staff and Technology Help
HCC Wireless Instructions for Windows 10 (long version) TIP: If you are having trouble connecting to the wireless network, or if just need some friendly guidance, the Library staff and Technology Help
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device
 Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Cisco Extension Mobility
 CHAPTER 9 allows users to temporarily access their Cisco Unified IP Phone configuration such as line appearances, services, and speed dials from other Cisco Unified IP Phones. Extension mobility functionality
CHAPTER 9 allows users to temporarily access their Cisco Unified IP Phone configuration such as line appearances, services, and speed dials from other Cisco Unified IP Phones. Extension mobility functionality
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
Configuring 802.1X Authentication Client for Windows 8
 Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Configuring Facebook for a More Secure Social Networking Experience
 CPF 0037-14-CID361-9H-Facebook* 5 December 2014 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Settings
CPF 0037-14-CID361-9H-Facebook* 5 December 2014 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Settings
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
PASSWORD SECURITY GUIDELINE
 Section: Information Security Revised: December 2004 Guideline: Description: Password Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect
Section: Information Security Revised: December 2004 Guideline: Description: Password Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect
Digest Authentication Setup for SIP Trunks
 This chapter provides information about digest authentication setup for SIP trunks. When you configure digest authentication for SIP trunks, Cisco Unified Communications Manager challenges the identity
This chapter provides information about digest authentication setup for SIP trunks. When you configure digest authentication for SIP trunks, Cisco Unified Communications Manager challenges the identity
Consumer Banking User Guide. Getting Started
 Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Rev X 341. Table 111. Access Levels and Descriptions
 9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
Outlook 2010 Exchange Setup Guide
 Outlook 2010 Outlook Profile Configuration This section provides a quick overview of the settings needed to access Outlook client software and configure Outlook to connect to your hosted Exchange mailbox.
Outlook 2010 Outlook Profile Configuration This section provides a quick overview of the settings needed to access Outlook client software and configure Outlook to connect to your hosted Exchange mailbox.
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
um Wireless Revised 8/17/18
 um Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website Revised 8/17/18
um Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website Revised 8/17/18
Storage Security Software (Version )
 For Toshiba CANVIO series Storage Security Software (Version 1.00.6904) User s Manual Version 1.00 This document explains the installation process and basic usage of the Storage Security Software designed
For Toshiba CANVIO series Storage Security Software (Version 1.00.6904) User s Manual Version 1.00 This document explains the installation process and basic usage of the Storage Security Software designed
Octopus Online Service Safety Guide
 Octopus Online Service Safety Guide This Octopus Online Service Safety Guide is to provide you with security tips and reminders that you should be aware of when using online and mobile services provided
Octopus Online Service Safety Guide This Octopus Online Service Safety Guide is to provide you with security tips and reminders that you should be aware of when using online and mobile services provided
Manual UCSFwpa Configuration for Windows 7
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Configuring the Client Adapter through the Windows XP Operating System
 APPENDIX E through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in this appendix: Overview, page
APPENDIX E through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in this appendix: Overview, page
Part 1: Connecting to HawkNET on your Windows XP PC
 Students are NOT permitted to use any device or product that extends the HawkNET network beyond the intended personal use. These restrictions include, but are not limited to, the use of personal routers,
Students are NOT permitted to use any device or product that extends the HawkNET network beyond the intended personal use. These restrictions include, but are not limited to, the use of personal routers,
USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003)
 YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
SIX Trade Repository AG
 May 2017 Table of contents 1.0 Introduction 3 1.1 Purpose 3 1.2 Acronyms 3 1.3 Version table 3 2.0 Required credentials and roles 4 2.1 Differentiation of certificate user names 4 2.2 Optional Setup using
May 2017 Table of contents 1.0 Introduction 3 1.1 Purpose 3 1.2 Acronyms 3 1.3 Version table 3 2.0 Required credentials and roles 4 2.1 Differentiation of certificate user names 4 2.2 Optional Setup using
Guide to your CGIAR Network account Self Service tool
 Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
12d Synergy Server Installation Guide
 12d Synergy Server Installation Guide Version 3.0 April 2017 12d Solutions Pty Ltd ACN 101 351 991 PO Box 351 Narrabeen NSW Australia 2101 (02) 9970 7117 (02) 9970 7118 support@12d.com www.12d.com 12d
12d Synergy Server Installation Guide Version 3.0 April 2017 12d Solutions Pty Ltd ACN 101 351 991 PO Box 351 Narrabeen NSW Australia 2101 (02) 9970 7117 (02) 9970 7118 support@12d.com www.12d.com 12d
Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Select detnsw and click on Connect.
 1 HSHS BYOD Wireless Connection Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Windows 8.1 icon: Windows 10 icon: Select detnsw and click on Connect. or
1 HSHS BYOD Wireless Connection Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Windows 8.1 icon: Windows 10 icon: Select detnsw and click on Connect. or
How to connect to Wi-Fi
 41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
Application for Smart Card Management User manual
 Application for Smart Card Management User manual for Microsoft Windows systems (7 and newer), Mac OS Warsaw 2019-04-15 tel. + 48 22 390 59 95 email: handlowy@eurocert.pl Content 1. Installation for Windows
Application for Smart Card Management User manual for Microsoft Windows systems (7 and newer), Mac OS Warsaw 2019-04-15 tel. + 48 22 390 59 95 email: handlowy@eurocert.pl Content 1. Installation for Windows
ClientNet. Portal Admin Guide
 ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
Check Point GO R75. User Guide. 14 November Classification: [Public]
![Check Point GO R75. User Guide. 14 November Classification: [Public] Check Point GO R75. User Guide. 14 November Classification: [Public]](/thumbs/74/70104753.jpg) Check Point GO R75 User Guide 14 November 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point GO R75 User Guide 14 November 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Connecting Devices to the PSD-BYOD Network
 Connecting Devices to the PSD-BYOD Network Students and staff can use the PSD-BYOD (Bring Your Own Device) network for internet access. Below are directions for connecting different types of devices. Selecting
Connecting Devices to the PSD-BYOD Network Students and staff can use the PSD-BYOD (Bring Your Own Device) network for internet access. Below are directions for connecting different types of devices. Selecting
SP LOCKER USER MANUAL. v1.0
 SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
Configuring Remote Access using the RDS Gateway
 Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
2016 TaxSlayer Pro Desktop. Logging in to the Program Usernames/Passwords
 2016 TaxSlayer Pro Desktop Logging in to the Program Usernames/Passwords Contents Logging in to the Program... 2 First Time Logging In... 2 Forgot Username/Password Preparer... 4 Logging in as ADMIN...
2016 TaxSlayer Pro Desktop Logging in to the Program Usernames/Passwords Contents Logging in to the Program... 2 First Time Logging In... 2 Forgot Username/Password Preparer... 4 Logging in as ADMIN...
Configuring the Client Adapter through Windows CE.NET
 APPENDIX E Configuring the Client Adapter through Windows CE.NET This appendix explains how to configure and use the client adapter with Windows CE.NET. The following topics are covered in this appendix:
APPENDIX E Configuring the Client Adapter through Windows CE.NET This appendix explains how to configure and use the client adapter with Windows CE.NET. The following topics are covered in this appendix:
Websense Secure Messaging User Help
 Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Berner Fachhochschule Haute cole spcialise bernoise Berne University of Applied Sciences 2
 Table of Contents Hacking Web Sites Broken Authentication Emmanuel Benoist Spring Term 2018 Introduction Examples of Attacks Brute Force Session Spotting Replay Attack Session Fixation Attack Session Hijacking
Table of Contents Hacking Web Sites Broken Authentication Emmanuel Benoist Spring Term 2018 Introduction Examples of Attacks Brute Force Session Spotting Replay Attack Session Fixation Attack Session Hijacking
Configuring the Client Adapter through the Windows XP Operating System
 APPENDIX E Configuring the Client Adapter through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in
APPENDIX E Configuring the Client Adapter through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in
Configuring Twitter for a More Secure Social Networking Experience
 CPF 00006-18-CID361-9H 8 November 2018 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Social Media The internet s social media ecosystem is vast. To some people, social
CPF 00006-18-CID361-9H 8 November 2018 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Social Media The internet s social media ecosystem is vast. To some people, social
Installing the CGDS - Substation Workbench Server Software
 CHAPTER 2 Installing the CGDS - Substation Workbench Server Software Revised: April 15, 2013, Tips on Performing the CGDS - Substation Workbench Base Software Installation This section will cover how to
CHAPTER 2 Installing the CGDS - Substation Workbench Server Software Revised: April 15, 2013, Tips on Performing the CGDS - Substation Workbench Base Software Installation This section will cover how to
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Tennessee Technological University Policy No Password Management
 Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Web Security, Summer Term 2012
 IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 7 Broken Authentication and Session
IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 7 Broken Authentication and Session
Web Security, Summer Term 2012
 Table of Contents IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Introduction Examples of Attacks Brute Force Session
Table of Contents IIG University of Freiburg Web Security, Summer Term 2012 Brocken Authentication and Session Management Dr. E. Benoist Sommer Semester Introduction Examples of Attacks Brute Force Session
Step 3 ROS Administrator
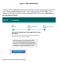 Step 3 ROS Administrator To continue the ROS registration process when you receive the system password text or email, click on the "I have my system password" button, or go to www.revenue.ie and click
Step 3 ROS Administrator To continue the ROS registration process when you receive the system password text or email, click on the "I have my system password" button, or go to www.revenue.ie and click
IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP -
 IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP - Information required for connection to the Curtin Wireless network: Wireless network names There are two wireless networks operating
IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP - Information required for connection to the Curtin Wireless network: Wireless network names There are two wireless networks operating
smartdata.gen2 Corporate Cardholder Guide February 2014
 smartdata.gen2 Corporate Cardholder Guide February 2014 Table of Contents Chapter 1 Getting Started... 1-i Introduction... 1-1 Browser Requirements... 1-1 Security... 1-2 Selecting a Language Preference...
smartdata.gen2 Corporate Cardholder Guide February 2014 Table of Contents Chapter 1 Getting Started... 1-i Introduction... 1-1 Browser Requirements... 1-1 Security... 1-2 Selecting a Language Preference...
Setting Up and Using WebDrive
 Setting Up and Using WebDrive Rutgers University has a site license for WebDrive, an SFTP program used to transfer files to and from servers such as crab and clam. Both employees and students may download
Setting Up and Using WebDrive Rutgers University has a site license for WebDrive, an SFTP program used to transfer files to and from servers such as crab and clam. Both employees and students may download
CMS Enterprise Portal User Manual
 Centers for Medicare & Medicaid Services CMS expedited Life Cycle (XLC) 11/13/2017 Document Number: Enterprise_Portal_User_Manual_v6 Table of Contents Table of Contents 1. Introduction... 1 2. Overview...
Centers for Medicare & Medicaid Services CMS expedited Life Cycle (XLC) 11/13/2017 Document Number: Enterprise_Portal_User_Manual_v6 Table of Contents Table of Contents 1. Introduction... 1 2. Overview...
Using the Certificate Authority Proxy Function
 CHAPTER 10 This chapter provides information on the following topics: Certificate Authority Proxy Function Overview, page 10-1 Cisco Unified IP Phone and CAPF Interaction, page 10-2 CAPF Interaction with
CHAPTER 10 This chapter provides information on the following topics: Certificate Authority Proxy Function Overview, page 10-1 Cisco Unified IP Phone and CAPF Interaction, page 10-2 CAPF Interaction with
Accessing COMPASS from Your Home or Office
 Accessing COMPASS from Your Home or Office IMPORTANT: Please Read! 1. We encourage you to have your office manager or IT professional establish access for you using these instructions. 2. You can establish
Accessing COMPASS from Your Home or Office IMPORTANT: Please Read! 1. We encourage you to have your office manager or IT professional establish access for you using these instructions. 2. You can establish
PowerSchool Users Guide for Parents/Guardians
 PowerSchool Users Guide for Parents/Guardians Introduction PowerSchool's Parent Portal is a tool specifically developed for parents and students that integrates into the PowerSchool Student Information
PowerSchool Users Guide for Parents/Guardians Introduction PowerSchool's Parent Portal is a tool specifically developed for parents and students that integrates into the PowerSchool Student Information
1. A broadband connection. 2. Windows Vista (for these instructions; other operating systems have other instructions).
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
WIRELESS 150N USB 2.0 ADAPTER
 WIRELESS 150N USB 2.0 ADAPTER DN-70440-1 Rev.2 DN-7042-1 Rev.3 Manual DN-70440-1 Rev.2 DN-7042-1 Rev.3 1 / 38 Chapter 1: Introduction..3 1.1 Product Features..3 1.2 Package Contents.3 1.3 Indicator Description.3
WIRELESS 150N USB 2.0 ADAPTER DN-70440-1 Rev.2 DN-7042-1 Rev.3 Manual DN-70440-1 Rev.2 DN-7042-1 Rev.3 1 / 38 Chapter 1: Introduction..3 1.1 Product Features..3 1.2 Package Contents.3 1.3 Indicator Description.3
Access ACS. Administrator s User Guide
 Access ACS Administrator s User Guide Copyright Copyright 2009 ACS Technologies Group, Inc. All rights reserved. Reproduction of any part of this publication by mechanical or electronic means, including
Access ACS Administrator s User Guide Copyright Copyright 2009 ACS Technologies Group, Inc. All rights reserved. Reproduction of any part of this publication by mechanical or electronic means, including
SafeNet Authentication Manager
 SafeNet Authentication Manager Version 8.0 Rev A User s Guide Copyright 2010 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and accurate.
SafeNet Authentication Manager Version 8.0 Rev A User s Guide Copyright 2010 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and accurate.
ipassconnect 3.65 Release Notes
 ipassconnect 3.65 Release Notes Version 1.0, October 2008 Version History Version Date Notes 1.0 October 2008 General release availability document Introduction This document contains the latest information
ipassconnect 3.65 Release Notes Version 1.0, October 2008 Version History Version Date Notes 1.0 October 2008 General release availability document Introduction This document contains the latest information
YOUR VOLUNTEER PROFILE
 YOUR VOLUNTEER PROFILE The Anti-Cruelty Society utilizes a volunteer management software called Volunteer2 to help us track everything we need to know about volunteers. Not only does this database allow
YOUR VOLUNTEER PROFILE The Anti-Cruelty Society utilizes a volunteer management software called Volunteer2 to help us track everything we need to know about volunteers. Not only does this database allow
HospiDirect Reference Guide
 HospiDirect Reference Guide Last updated: December 13, 2017 Optum and the Optum logo are registered trademarks of Optum. All other brand or product names or trademarks are registered marks of their respective
HospiDirect Reference Guide Last updated: December 13, 2017 Optum and the Optum logo are registered trademarks of Optum. All other brand or product names or trademarks are registered marks of their respective
MULTI-FACTOR AUTHENTICATION SET-UP
 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
Internet access system through the Wireless Network of the University of Bologna (last update )
 Internet access system through the Wireless Network of the University of Bologna (last update 7.03.2012) Printable service summary document: the updated version is available online at the following address
Internet access system through the Wireless Network of the University of Bologna (last update 7.03.2012) Printable service summary document: the updated version is available online at the following address
SJC Password Self-Service System FAQ 2018
 The San Jacinto College Password Self-Service System enables students to reset their password quickly and conveniently online. By utilizing this service, you can change your password and gain access to
The San Jacinto College Password Self-Service System enables students to reset their password quickly and conveniently online. By utilizing this service, you can change your password and gain access to
Passwords Overview. Set up Initial Address 2 Setup Forgotten Password/Change Your Password 4 Direct Access (DA) Self Service Password Reset 6
 Passwords Overview Introduction This guide provides the procedures for setting up an email, setting up a forgotten password function, and changing/resetting a password in Direct Access. Information Rules
Passwords Overview Introduction This guide provides the procedures for setting up an email, setting up a forgotten password function, and changing/resetting a password in Direct Access. Information Rules
Oakland University Obtaining Your 1098-T Electronically
 Accessing a student 1098-T is easy - simply go to tra.vangent.com, click on First Time Student and follow the instructions. 1. Open a web browser (such as Internet Explorer, Safari, Chrome, Firefox, etc.
Accessing a student 1098-T is easy - simply go to tra.vangent.com, click on First Time Student and follow the instructions. 1. Open a web browser (such as Internet Explorer, Safari, Chrome, Firefox, etc.
Guide Installation and User Guide - Mac
 Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
ESS Security Enhancements
 ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
UMDNJ Wireless Documentation Windows 7
 UMDNJ Wireless Documentation Windows 7 The following documentation will provide instructions for configuring the Microsoft Windows 7 native wireless client. There are wireless adapters that have 3 rd party
UMDNJ Wireless Documentation Windows 7 The following documentation will provide instructions for configuring the Microsoft Windows 7 native wireless client. There are wireless adapters that have 3 rd party
Managing Workflows. Starting Prime Network Administration CHAPTER
 CHAPTER 10 Prime Network Administration can be used to manage deployed workflow templates. Topics include: Starting Prime Network Administration, page 10-1 Viewing the List of Templates and Template Properties,
CHAPTER 10 Prime Network Administration can be used to manage deployed workflow templates. Topics include: Starting Prime Network Administration, page 10-1 Viewing the List of Templates and Template Properties,
Self Service Password Reset User Guide Canada Version 1-2 Date: 2017/05/11
 Self Service Password Reset User Guide Canada Version 1-2 Date: 2017/05/11 Contents Introduction... 3 IMPORTANT: Before you begin... 3 How to Register for Self-Service Password Reset... 4 How to Reset
Self Service Password Reset User Guide Canada Version 1-2 Date: 2017/05/11 Contents Introduction... 3 IMPORTANT: Before you begin... 3 How to Register for Self-Service Password Reset... 4 How to Reset
Registration for Online Services at Drayton Medical Practice
 Registration for Online Services at Drayton Medical Practice This user guide explains the Registration process undertaken by the patient to create an Online User Account, how to maintain it and how to
Registration for Online Services at Drayton Medical Practice This user guide explains the Registration process undertaken by the patient to create an Online User Account, how to maintain it and how to
LiveVault. Agent Guide
 LiveVault Software Version: 7.82 Agent Guide Note The guide primarily provides instruction on how to install the LiveVault agent on Windows and Linux servers. Additionally it provides information about
LiveVault Software Version: 7.82 Agent Guide Note The guide primarily provides instruction on how to install the LiveVault agent on Windows and Linux servers. Additionally it provides information about
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
