SECURITY AND DATA REDUNDANCY. A White Paper
|
|
|
- Calvin Walton
- 6 years ago
- Views:
Transcription
1 SECURITY AND DATA REDUNDANCY A White Paper
2 Security and Data Redundancy Whitepaper 2 At MyCase, Security is Our Top Priority. Here at MyCase, we understand how important it is to keep our customer s data secure. Dealing with privileged case information isn t a responsibility that we take lightly. Everything we do is built with security in mind. It s the fundamental base that we always use as the starting point for any task. We understand that our customers may be nervous about moving their data to the cloud. It s a new and exciting field, but with that brings a fear of the unknown. Can you really trust an Internet company to protect your data? How secure is cloud based storage? What s being done to protect my data? In this whitepaper, we provide an overview of how we address the security and redundancy of your data. It s our goal to put your mind at ease. Yes, you can trust us with your data. Yes, we re as concerned about security as you are. And yes, we re on top of it - the field is always evolving, and you can be confident that we ll be evolving with it, protecting you every step of the way.
3 Security and Data Redundancy Whitepaper 3 A Brief Overview of Our Security Policies PHYSICAL SECURITY STATE OF THE ART ENCRYPTION DATA REDUNDANCY MyCase runs on Amazon EC2 cloud servers. All sensitive information is encrypted by MyCase before it s written to disk. Data is backed up using Amazon S3 storage, providing % durability. Amazon facilities are nondescript locations protected by military grade perimiters. We use 128-bit SSL encryption for data transmission and 256-bit AES encryption when storing data. The entire MyCase database is continuously backed up and can be restored to any point in time within a 5 minute window. Physical access is strictly controlled by two factor authentication and 24 hour security escorts. Unique keys are generated for every individual document, providing an additional layer of security with at rest encryption. Documents are backed up to a separate AWS region, providing additional redundancy in case of catastrophic failure. Amazon s Cloud Computing Platform MyCase is built on top of Amazon s EC2 cloud computing platform (yes, the same Amazon that you use when shopping online). They ve got over a decade of experience on running online servers and data centers, so you know you can trust them to be at the leading edge of online service technology. Amazon has strict procedures in place to protect the physical security of their servers, as well as protecting the integrity of the data they store. By building on their platform, we gain the benefit of all of their experience and knowledge. We re not just running on a server in some kid s basement - this is the best of the best when it comes to hosting your cloud-based service.
4 Security and Data Redundancy Whitepaper 4 Amazon has received a number of certifications for their servers. In addition, HIPAA compliant websites have been built on top of the Amazon cloud platform (you know if a website can pass through all of the health care regulations, there isn t much else that it couldn t handle!) Compare that to other companies that host their own servers - how reliable are their facilities? Is their data protected? Or think of trying to run your own local IT department - would you even know where to begin on building a secure storage solution? That s why we defer to the experts here. You can read more about Amazon s cloud infrastructure and security at: Experience Counts The founding engineer and current architect of MyCase has a background in securing data and servers for the US Department of Defense. He understands the importance of securing data, and has the knowledge to prevent unauthorized access and monitor compliance. With over 10 years of experience in developing commercial websites, he s worked through the evolution of the Internet from the dot-com days and has worked first hand with numerous online services. It s this experience that gives us the confidence that we ve built a secure online platform that you can trust. We re experts in our own right - top performers in our respective industry. This isn t the first time we ve been down this road, and we ve seen and learned a lot along the way. We re constantly monitoring the latest security threats, and evolving and adapting our service to address any concerns.
5 Security and Data Redundancy Whitepaper 5 State of the Art Encryption MyCase uses two forms of encryption to protect your data. When you connect to our servers, your data is encrypted before transmission using 128-bit SSL connections. This is the same type of secure connection you use when doing online banking, investments, healthcare portals, etc. Encrypting your transmission ensures that nobody can intercept your data along the way, and verifies that you re connected to our servers and not some impostor. After we receive your data, we use 256-bit AES encryption to encrypt your data before storing it to disk. This is the same level of encryption authorized for storage of top secret military information. Anything sensitive is encrypted before storage - client names and addresses, messages, appointment details, etc. This protects your data in the highly unlikely case that someone did manage to steal a physical disk drive from an Amazon facility - all they would get from us is a bunch of jumbled, useless data. In addition, we generate a unique key for every single case document that you upload to MyCase. Those keys are used to encrypt your documents on Amazon s S3 service giving you at rest encryption for your document data. Activity Streams and Audit Logs All the activity in MyCase is logged in your activity stream. You see this information on your dashboard whenever you login to your account. By monitoring your firm s activity stream, you can notice suspicious activity and take steps to prevent it. Is there a client you no longer trust? Suspend his or her MyCase account immediately and they ll no longer be able to login to the website. We also monitor every single unique page access on our server. We store the IP address, date/time, and URL of each request. These audit logs are there for your protection in the unfortunate event that you suspect your account has been compromised. We can review the audit logs and let you know the extent of what was accessed, allowing you to take preventative steps immediately.
6 Security and Data Redundancy Whitepaper 6 Server Access and Monitoring Our servers are running the open source Linux operating system. Security patches are installed as soon as they are available, making sure that we re always up to date with the latest fixes. Our servers are protected with a firewall so only the necessary information can pass through. Shell access to our servers is restricted by IP address, so remote access to the server is impossible unless you re physically present at the MyCase office. We monitor our server logs on a daily basis, allowing us to quickly resolve any issues. We also run a 24-hour monitoring service that checks the health of the server and alerts us immediately to any changes to files or problems with the website. You can rest assured that your data is safe and our servers are locked down appropriately. Two-Factor Authentication MyCase also offers Two-Factor Authentication. Two-Factor Authentication (or 2FA) is a security feature that makes it extremely difficult for unauthorized users to access your account. Even in the event of your username and password being compromised, 2FA would still prevent someone from gaining access to your confidential data.
7 Security and Data Redundancy Whitepaper 7 Logging into a web-based software system that does not implement 2FA is a simple, one-step process. All the user has to do is enter the correct username and password, then the entire database of sensitive client information is made available. Conversely, logging into a 2FA system requires an additional login step. After the user inputs a correct username and password combination, they are not immediately logged into the system where data is available. They are instead taken to a second login screen which prompts them to enter their Secure Authentication Key (or SAK). The SAK lives in an app on the user s smartphone. Once the user has been taken to the second login screen and is prompted to enter their SAK, they will take out their smartphone, open the app, and the SAK will be displayed to them. When the correct SAK has been entered, the user will be logged into the system. If the user is unable to enter the correct SAK, they will be locked out of MyCase (even though a correct username and password was entered). What You Can Do to Protect Your Data No matter how many steps we take to secure your data, the most common cause of data loss is based on the human element. It s important that you take steps to secure your own account. Use a strong password (we ll tell you how strong your password is when you change it). Don t use the same password for MyCase that you use for other websites. Don t give your MyCase password to anyone else. Change it frequently. Make sure that other people can t access your - otherwise they could reset your MyCase password and gain access to your account.
8 Security and Data Redundancy Whitepaper 8 At any time, if you feel like your account may have been compromised, just contact us immediately. We can freeze access to your firm, locking out all users immediately until we can make sure that everything is safe. Some Final Words... We know it seems like a lot to think about, and we know that security is always our customers top concern. But rest assured that we re working on it. We re always thinking about it and constantly evolving to address new security threats. Compare that to using to communicate with your client - an unencrypted, insecure platform. Anyone can read your along the way. There s no auditing and no security controls. Or think about running your own IT department and your own servers... can you really put together a team with more online experience than Amazon? We re always here to help. By working with us and keeping security at the forefront of your mind, we can make sure that your MyCase experience is protected and secure.
Information Security at Veritext Protecting Your Data
 Information Security at Veritext Protecting Your Data The Veritext Security Model Introduction Information security and privacy are built into the fabric of everything we do at Veritext. Helping to protect
Information Security at Veritext Protecting Your Data The Veritext Security Model Introduction Information security and privacy are built into the fabric of everything we do at Veritext. Helping to protect
Cloud Security Whitepaper
 Cloud Security Whitepaper Sep, 2018 1. Product Overview 3 2. Personally identifiable information (PII) 3 Using Lookback without saving any PII 3 3. Security and privacy policy 4 4. Personnel security 4
Cloud Security Whitepaper Sep, 2018 1. Product Overview 3 2. Personally identifiable information (PII) 3 Using Lookback without saving any PII 3 3. Security and privacy policy 4 4. Personnel security 4
Kenna Platform Security. A technical overview of the comprehensive security measures Kenna uses to protect your data
 Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Safeguarding Cardholder Account Data
 Safeguarding Cardholder Account Data Attachmate Safeguarding Cardholder Account Data CONTENTS The Twelve PCI Requirements... 1 How Reflection Handles Your Host-Centric Security Issues... 2 The Reflection
Safeguarding Cardholder Account Data Attachmate Safeguarding Cardholder Account Data CONTENTS The Twelve PCI Requirements... 1 How Reflection Handles Your Host-Centric Security Issues... 2 The Reflection
How Secured2 Uses Beyond Encryption Security to Protect Your Data
 Secured2 Beyond Encryption How Secured2 Uses Beyond Encryption Security to Protect Your Data Secured2 Beyond Encryption Whitepaper Document Date: 06.21.2017 Document Classification: Website Location: Document
Secured2 Beyond Encryption How Secured2 Uses Beyond Encryption Security to Protect Your Data Secured2 Beyond Encryption Whitepaper Document Date: 06.21.2017 Document Classification: Website Location: Document
The secure remote support, remote access and online meeting software that the world relies on.
 The secure remote support, remote access and online meeting software that the world relies on. TeamViewer, the market leader activated by users on 1.3 billion devices worldwide. The Right Solution for
The secure remote support, remote access and online meeting software that the world relies on. TeamViewer, the market leader activated by users on 1.3 billion devices worldwide. The Right Solution for
A company built on security
 Security How we handle security at Flywheel Flywheel was founded in 2012 on a mission to create an exceptional platform to help creatives do their best work. As the leading WordPress hosting provider for
Security How we handle security at Flywheel Flywheel was founded in 2012 on a mission to create an exceptional platform to help creatives do their best work. As the leading WordPress hosting provider for
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
The Security Behind Sticky Password
 The Security Behind Sticky Password Technical White Paper Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and personal information are often
The Security Behind Sticky Password Technical White Paper Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and personal information are often
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
Xerox FreeFlow Print Server. Security White Paper. Secure solutions. for you and your customers
 Xerox FreeFlow Print Server Security White Paper Secure solutions for you and your customers Executive Summary Why is security more important than ever? New government regulations have been implemented
Xerox FreeFlow Print Server Security White Paper Secure solutions for you and your customers Executive Summary Why is security more important than ever? New government regulations have been implemented
BEYOND CJIS: ENHANCED SECURITY, NOT JUST COMPLIANCE
 BEYOND CJIS: ENHANCED SECURITY, NOT JUST COMPLIANCE PROTECT LIFE. PROTECT TRUTH. 1 OVERVIEW Because digital evidence files are among a police agency s most sensitive assets, security is in many ways the
BEYOND CJIS: ENHANCED SECURITY, NOT JUST COMPLIANCE PROTECT LIFE. PROTECT TRUTH. 1 OVERVIEW Because digital evidence files are among a police agency s most sensitive assets, security is in many ways the
Contents. Is Rumpus Secure? 2. Use Care When Creating User Accounts 2. Managing Passwords 3. Watch Out For Symbolic Links 4. Deploy A Firewall 5
 Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
The following security and privacy-related audits and certifications are applicable to the Lime Services:
 LIME SECURITY, PRIVACY, AND ARCHITECTURE Last Updated: September 26, 2016 FinAccel s Corporate Trust Commitment FinAccel (FinAccel Pte Ltd) is committed to achieving and maintaining the trust of our customers.
LIME SECURITY, PRIVACY, AND ARCHITECTURE Last Updated: September 26, 2016 FinAccel s Corporate Trust Commitment FinAccel (FinAccel Pte Ltd) is committed to achieving and maintaining the trust of our customers.
SECURING YOUR BUSINESS INFRASTRUCTURE Today s Security Challenges & What You Can Do About Them
 BROTHER SECURITY WHITE PAPER NOVEMBER 2017 SECURING YOUR BUSINESS INFRASTRUCTURE Today s Security Challenges & What You Can Do About Them The last decade has seen many exciting advances in connectivity
BROTHER SECURITY WHITE PAPER NOVEMBER 2017 SECURING YOUR BUSINESS INFRASTRUCTURE Today s Security Challenges & What You Can Do About Them The last decade has seen many exciting advances in connectivity
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
GLOBAL PAYMENTS AND CASH MANAGEMENT. Security
 GLOBAL PAYMENTS AND CASH MANAGEMENT Security The Bank aims to provide you with a robust, reliable and secure online environment in which to do business. We seek to achieve this through the adoption of
GLOBAL PAYMENTS AND CASH MANAGEMENT Security The Bank aims to provide you with a robust, reliable and secure online environment in which to do business. We seek to achieve this through the adoption of
A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION. Establish Create Use Manage
 A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION Establish Create Use Manage SIMPLE. SECURE. SMART. ALL FROM A SINGLE SOURCE. As the ways to access your organization and its sensitive data increase,
A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION Establish Create Use Manage SIMPLE. SECURE. SMART. ALL FROM A SINGLE SOURCE. As the ways to access your organization and its sensitive data increase,
Your Data Demands More NETAPP ENABLES YOU TO LEVERAGE YOUR DATA & COMPUTE FROM ANYWHERE
 Your Data Demands More NETAPP ENABLES YOU TO LEVERAGE YOUR DATA & COMPUTE FROM ANYWHERE IN ITS EARLY DAYS, NetApp s (www.netapp.com) primary goal was to build a market for network-attached storage and
Your Data Demands More NETAPP ENABLES YOU TO LEVERAGE YOUR DATA & COMPUTE FROM ANYWHERE IN ITS EARLY DAYS, NetApp s (www.netapp.com) primary goal was to build a market for network-attached storage and
Village Software. Security Assessment Report
 Village Software Security Assessment Report Version 1.0 January 25, 2019 Prepared by Manuel Acevedo Helpful Village Security Assessment Report! 1 of! 11 Version 1.0 Table of Contents Executive Summary
Village Software Security Assessment Report Version 1.0 January 25, 2019 Prepared by Manuel Acevedo Helpful Village Security Assessment Report! 1 of! 11 Version 1.0 Table of Contents Executive Summary
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Cloud FastPath: Highly Secure Data Transfer
 Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
RADIAN6 SECURITY, PRIVACY, AND ARCHITECTURE
 ADIAN6 SECUITY, PIVACY, AND ACHITECTUE Last Updated: May 6, 2016 Salesforce s Corporate Trust Commitment Salesforce is committed to achieving and maintaining the trust of our customers. Integral to this
ADIAN6 SECUITY, PIVACY, AND ACHITECTUE Last Updated: May 6, 2016 Salesforce s Corporate Trust Commitment Salesforce is committed to achieving and maintaining the trust of our customers. Integral to this
HIPAA / HITECH Overview of Capabilities and Protected Health Information
 HIPAA / HITECH Overview of Capabilities and Protected Health Information August 2017 Rev 1.8.9 2017 DragonFly Athletics, LLC 2017, DragonFly Athletics, LLC. or its affiliates. All rights reserved. Notices
HIPAA / HITECH Overview of Capabilities and Protected Health Information August 2017 Rev 1.8.9 2017 DragonFly Athletics, LLC 2017, DragonFly Athletics, LLC. or its affiliates. All rights reserved. Notices
CTS performs nightly backups of the Church360 production databases and retains these backups for one month.
 Church360 is a cloud-based application software suite from Concordia Technology Solutions (CTS) that is used by churches of all sizes to manage their membership data, website, and financial information.
Church360 is a cloud-based application software suite from Concordia Technology Solutions (CTS) that is used by churches of all sizes to manage their membership data, website, and financial information.
Oracle Eloqua HIPAA Advanced Data Security Add-on Cloud Service
 http://docs.oracle.com Oracle Eloqua HIPAA Advanced Data Security Add-on Cloud Service Configuration Guide 2018 Oracle Corporation. All rights reserved 07-Jun-2018 Contents 1 HIPAA 3 1.0.1 What is HIPAA?
http://docs.oracle.com Oracle Eloqua HIPAA Advanced Data Security Add-on Cloud Service Configuration Guide 2018 Oracle Corporation. All rights reserved 07-Jun-2018 Contents 1 HIPAA 3 1.0.1 What is HIPAA?
AWS continually manages risk and undergoes recurring assessments to ensure compliance with industry standards.
 Security Practices Freshservice Security Practices Freshservice is online IT service desk software that allows IT teams of organizations to support their users through email, phone, website and mobile.
Security Practices Freshservice Security Practices Freshservice is online IT service desk software that allows IT teams of organizations to support their users through email, phone, website and mobile.
VSP16. Venafi Security Professional 16 Course 04 April 2016
 VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
Cloud-Based Data Security
 White Paper Cloud-Based Data Security SaaS-built Galileo collects and analyzes customized performance data efficiently, on-demand, via a secure Internet connection. About Galileo Created by the ATS Group,
White Paper Cloud-Based Data Security SaaS-built Galileo collects and analyzes customized performance data efficiently, on-demand, via a secure Internet connection. About Galileo Created by the ATS Group,
Securing Amazon Web Services (AWS) EC2 Instances with Dome9. A Whitepaper by Dome9 Security, Ltd.
 Securing Amazon Web Services (AWS) EC2 Instances with Dome9 A Whitepaper by Dome9 Security, Ltd. Amazon Web Services (AWS) provides business flexibility for your company as you move to the cloud, but new
Securing Amazon Web Services (AWS) EC2 Instances with Dome9 A Whitepaper by Dome9 Security, Ltd. Amazon Web Services (AWS) provides business flexibility for your company as you move to the cloud, but new
For Australia January 2018
 For Australia January 2018 www.sysaid.com SysAid Cloud Architecture Including Security and Disaster Recovery Plan 2 This document covers three aspects of SysAid Cloud: Datacenters Network, Hardware, and
For Australia January 2018 www.sysaid.com SysAid Cloud Architecture Including Security and Disaster Recovery Plan 2 This document covers three aspects of SysAid Cloud: Datacenters Network, Hardware, and
HIPAA COMPLIANCE AND DATA PROTECTION Page 1
 HIPAA COMPLIANCE AND DATA PROTECTION info@resultstechnology.com 877.435.8877 Page 1 CONTENTS Introduction..... 3 The HIPAA Security Rule... 4 The HIPAA Omnibus Rule... 6 HIPAA Compliance and RESULTS Cloud
HIPAA COMPLIANCE AND DATA PROTECTION info@resultstechnology.com 877.435.8877 Page 1 CONTENTS Introduction..... 3 The HIPAA Security Rule... 4 The HIPAA Omnibus Rule... 6 HIPAA Compliance and RESULTS Cloud
Administrator s Guide
 Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
SECURITY ON AWS 8/3/17. AWS Security Standards MORE. By Max Ellsberry
 SECURITY ON AWS By Max Ellsberry AWS Security Standards The IT infrastructure that AWS provides has been designed and managed in alignment with the best practices and meets a variety of standards. Below
SECURITY ON AWS By Max Ellsberry AWS Security Standards The IT infrastructure that AWS provides has been designed and managed in alignment with the best practices and meets a variety of standards. Below
5 Must-Have Magento Security Plugins
 5 Must-Have Magento Security Plugins http://beacon.by/magazine/pdf/serverguy/5-must-have-magento-security-plugins?type=print 1/16 Table of Contents 1. About ServerGuy 2. WatchLog 3. Amasty s Admin Login
5 Must-Have Magento Security Plugins http://beacon.by/magazine/pdf/serverguy/5-must-have-magento-security-plugins?type=print 1/16 Table of Contents 1. About ServerGuy 2. WatchLog 3. Amasty s Admin Login
Device Discovery for Vulnerability Assessment: Automating the Handoff
 Device Discovery for Vulnerability Assessment: Automating the Handoff O V E R V I E W While vulnerability assessment tools are widely believed to be very mature and approaching commodity status, they are
Device Discovery for Vulnerability Assessment: Automating the Handoff O V E R V I E W While vulnerability assessment tools are widely believed to be very mature and approaching commodity status, they are
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
For USA & Europe January 2018
 For USA & Europe January 2018 www.sysaid.com SysAid Cloud Architecture Including Security and Disaster Recovery Plan 2 This document covers three aspects of SysAid Cloud: Datacenters Network, Hardware,
For USA & Europe January 2018 www.sysaid.com SysAid Cloud Architecture Including Security and Disaster Recovery Plan 2 This document covers three aspects of SysAid Cloud: Datacenters Network, Hardware,
AN IPSWITCH WHITEPAPER. The Definitive Guide to Secure FTP
 AN IPSWITCH WHITEPAPER The Definitive Guide to Secure FTP The Importance of File Transfer Are you concerned with the security of file transfer processes in your company? According to a survey of IT pros
AN IPSWITCH WHITEPAPER The Definitive Guide to Secure FTP The Importance of File Transfer Are you concerned with the security of file transfer processes in your company? According to a survey of IT pros
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Duo Travel Guide. duo.com
 Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Crises Control Cloud Security Principles. Transputec provides ICT Services and Solutions to leading organisations around the globe.
 Crises Control Cloud Security Principles Transputec provides ICT Services and Solutions to leading organisations around the globe. As a provider of these services for over 30 years, we have the credibility
Crises Control Cloud Security Principles Transputec provides ICT Services and Solutions to leading organisations around the globe. As a provider of these services for over 30 years, we have the credibility
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
Security Overview. Technical Whitepaper. Secure by design. End to end security. N-tier Application Architecture. Data encryption. User authentication
 Technical Whitepaper Security Overview As a team, we have a long history of developing and delivering HR software solutions to customers worldwide, including many of the world s most-demanding organisations.
Technical Whitepaper Security Overview As a team, we have a long history of developing and delivering HR software solutions to customers worldwide, including many of the world s most-demanding organisations.
HOW SNOWFLAKE SETS THE STANDARD WHITEPAPER
 Cloud Data Warehouse Security HOW SNOWFLAKE SETS THE STANDARD The threat of a data security breach, someone gaining unauthorized access to an organization s data, is what keeps CEOs and CIOs awake at night.
Cloud Data Warehouse Security HOW SNOWFLAKE SETS THE STANDARD The threat of a data security breach, someone gaining unauthorized access to an organization s data, is what keeps CEOs and CIOs awake at night.
WHITEPAPER. MemSQL Enterprise Feature List
 WHITEPAPER MemSQL Enterprise Feature List 2017 MemSQL Enterprise Feature List DEPLOYMENT Provision and deploy MemSQL anywhere according to your desired cluster configuration. On-Premises: Maximize infrastructure
WHITEPAPER MemSQL Enterprise Feature List 2017 MemSQL Enterprise Feature List DEPLOYMENT Provision and deploy MemSQL anywhere according to your desired cluster configuration. On-Premises: Maximize infrastructure
THE TRUTH ABOUT CLOUD SECURITY. It s More Secure Than You Think
 THE TRUTH ABOUT CLOUD SECURITY It s More Secure Than You Think TABLE OF CONTENTS Cloud Security Problems Hyperbole Or Reality? It All Starts With Traversing The Internet It s Not The Cloud Itself The Major
THE TRUTH ABOUT CLOUD SECURITY It s More Secure Than You Think TABLE OF CONTENTS Cloud Security Problems Hyperbole Or Reality? It All Starts With Traversing The Internet It s Not The Cloud Itself The Major
Guide: HIPPA Compliance. Corporate HIPAA Compliance Guide. Privacy, productivity and remote access. gotomypc.com
 : HIPPA Compliance GoToMyPC Corporate HIPAA Compliance Privacy, productivity and remote access 2 The healthcare industry has benefited greatly from the ability to use remote access to view patient data
: HIPPA Compliance GoToMyPC Corporate HIPAA Compliance Privacy, productivity and remote access 2 The healthcare industry has benefited greatly from the ability to use remote access to view patient data
General Data Protection Regulation
 & General Data Protection Regulation As of May 25th 2018, the EU General Data Protection Regulation (GDPR) will become applicable with the purpose to regulate the processing of personal data of the EU
& General Data Protection Regulation As of May 25th 2018, the EU General Data Protection Regulation (GDPR) will become applicable with the purpose to regulate the processing of personal data of the EU
Xerox Audio Documents App
 Xerox Audio Documents App Additional information, if needed, on one or more lines Month 00, 0000 Information Assurance Disclosure 2018 Xerox Corporation. All rights reserved. Xerox, Xerox,
Xerox Audio Documents App Additional information, if needed, on one or more lines Month 00, 0000 Information Assurance Disclosure 2018 Xerox Corporation. All rights reserved. Xerox, Xerox,
Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3. Obtaining A Signed Certificate 4
 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 SSL/TLS Security Level 5 A Note
Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 SSL/TLS Security Level 5 A Note
SOC-2 Requirement Solution Brief. EventTracker 8815 Centre Park Drive, Columbia MD SOC-2
 Requirement Solution Brief 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized intelligence
Requirement Solution Brief 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized intelligence
Enterprise Mobile Management (EMM) Policies
 Enterprise Mobile Management (EMM) Policies Best Practices Guide Copyright 2016 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software
Enterprise Mobile Management (EMM) Policies Best Practices Guide Copyright 2016 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software
QUICK START USER S GUIDE
 QUICK START USER S GUIDE The Mount Nittany Health team is excited to bring you My Mount Nittany Health, the online tool that allows you to play a bigger part in your own healthcare journey. This Quick
QUICK START USER S GUIDE The Mount Nittany Health team is excited to bring you My Mount Nittany Health, the online tool that allows you to play a bigger part in your own healthcare journey. This Quick
InterCall Virtual Environments and Webcasting
 InterCall Virtual Environments and Webcasting Security, High Availability and Scalability Overview 1. Security 1.1. Policy and Procedures The InterCall VE ( Virtual Environments ) and Webcast Event IT
InterCall Virtual Environments and Webcasting Security, High Availability and Scalability Overview 1. Security 1.1. Policy and Procedures The InterCall VE ( Virtual Environments ) and Webcast Event IT
What can the OnBase Cloud do for you? lbmctech.com
 What can the OnBase Cloud do for you? lbmctech.com The OnBase Cloud by Hyland When it comes to cloud deployments, experience matters. With experience comes more functionality, long tracks of outstanding
What can the OnBase Cloud do for you? lbmctech.com The OnBase Cloud by Hyland When it comes to cloud deployments, experience matters. With experience comes more functionality, long tracks of outstanding
TB+ 1.5 Billion+ The OnBase Cloud by Hyland 600,000,000+ content stored. pages stored
 the onbase cloud ONBASE CLOUD // Experience Matters The OnBase Cloud by Hyland When it comes to cloud deployments, experience matters. With experience comes more functionality, an established history of
the onbase cloud ONBASE CLOUD // Experience Matters The OnBase Cloud by Hyland When it comes to cloud deployments, experience matters. With experience comes more functionality, an established history of
10 Hidden IT Risks That Might Threaten Your Business
 (Plus 1 Fast Way to Find Them) Your business depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
(Plus 1 Fast Way to Find Them) Your business depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
Your security on click Jobs
 Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
Cyber Security Hardening Guide
 Cyber Security Hardening Guide HOW FEENICS PROTECTS THE DATA AND INTEGRITY OF TRANSACTIONS FEENICS, INC. 301-2310 St. Laurent Blvd., Ottawa, Ontario K1G 5H9 (855) 333-6427 www.feenics.com Contents The
Cyber Security Hardening Guide HOW FEENICS PROTECTS THE DATA AND INTEGRITY OF TRANSACTIONS FEENICS, INC. 301-2310 St. Laurent Blvd., Ottawa, Ontario K1G 5H9 (855) 333-6427 www.feenics.com Contents The
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution
 WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
SECURE DATA EXCHANGE
 POLICY-DRIVEN SOLUTIONS FOR SECURE DATA EXCHANGE Sending and receiving data is a fundamental part of daily business for nearly every organization. Companies need to share financial transaction details,
POLICY-DRIVEN SOLUTIONS FOR SECURE DATA EXCHANGE Sending and receiving data is a fundamental part of daily business for nearly every organization. Companies need to share financial transaction details,
Data Loss Prevention Whitepaper. When Mobile Device Management Isn t Enough. Your Device Here. Good supports hundreds of devices.
 Data Loss Prevention Whitepaper When Mobile Device Management Isn t Enough Your Device Here. Good supports hundreds of devices. Contents Shifting Security Landscapes 3 Security Challenges to Enterprise
Data Loss Prevention Whitepaper When Mobile Device Management Isn t Enough Your Device Here. Good supports hundreds of devices. Contents Shifting Security Landscapes 3 Security Challenges to Enterprise
VSP18 Venafi Security Professional
 VSP18 Venafi Security Professional 13 April 2018 2018 Venafi. All Rights Reserved. 1 VSP18 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for:
VSP18 Venafi Security Professional 13 April 2018 2018 Venafi. All Rights Reserved. 1 VSP18 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for:
Pulseway Security White Paper
 Pulseway Security White Paper Table of Contents 1. Introduction 2. Encryption 2.1 Transport Encryption 2.2 Message Encryption 3. Brute-Force Protection 4. DigiCert Code Signing Certificate 5. Datacenter
Pulseway Security White Paper Table of Contents 1. Introduction 2. Encryption 2.1 Transport Encryption 2.2 Message Encryption 3. Brute-Force Protection 4. DigiCert Code Signing Certificate 5. Datacenter
Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003
 Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003 A system or combination of systems that enforces a boundary between two or more networks - NCSA
Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003 A system or combination of systems that enforces a boundary between two or more networks - NCSA
Automate sharing. Empower users. Retain control. Utilizes our purposebuilt cloud, not public shared clouds
 EXECUTIVE BRIEF SHAREBASE BY HYLAND Automate sharing. Empower users. Retain control. With ShareBase by Hyland, empower users with enterprise file sync and share (EFSS) technology and retain control over
EXECUTIVE BRIEF SHAREBASE BY HYLAND Automate sharing. Empower users. Retain control. With ShareBase by Hyland, empower users with enterprise file sync and share (EFSS) technology and retain control over
The Lighthouse Case Management System
 The Lighthouse Case Management System Get everything you need to track hotline reports from beginning to end in one easy-to-use online tool! For most organizations, keeping track of hotline reports can
The Lighthouse Case Management System Get everything you need to track hotline reports from beginning to end in one easy-to-use online tool! For most organizations, keeping track of hotline reports can
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
SIEMLESS THREAT DETECTION FOR AWS
 SOLUTION OVERVIEW: ALERT LOGIC FOR AMAZON WEB SERVICES (AWS) SIEMLESS THREAT DETECTION FOR AWS Few things are as important to your business as maintaining the security of your sensitive data. Protecting
SOLUTION OVERVIEW: ALERT LOGIC FOR AMAZON WEB SERVICES (AWS) SIEMLESS THREAT DETECTION FOR AWS Few things are as important to your business as maintaining the security of your sensitive data. Protecting
Protect Your Application with Secure Coding Practices. Barrie Dempster & Jason Foy JAM306 February 6, 2013
 Protect Your Application with Secure Coding Practices Barrie Dempster & Jason Foy JAM306 February 6, 2013 BlackBerry Security Team Approximately 120 people work within the BlackBerry Security Team Security
Protect Your Application with Secure Coding Practices Barrie Dempster & Jason Foy JAM306 February 6, 2013 BlackBerry Security Team Approximately 120 people work within the BlackBerry Security Team Security
Projectplace: A Secure Project Collaboration Solution
 Solution brief Projectplace: A Secure Project Collaboration Solution The security of your information is as critical as your business is dynamic. That s why we built Projectplace on a foundation of the
Solution brief Projectplace: A Secure Project Collaboration Solution The security of your information is as critical as your business is dynamic. That s why we built Projectplace on a foundation of the
MaintMaster Technical White Paper
 MaintMaster Technical White Paper Welcome to MaintMaster! MaintMaster is a leading tool for return on operational reliability for discrete manufacturing. This White Paper covers most of the technical aspects
MaintMaster Technical White Paper Welcome to MaintMaster! MaintMaster is a leading tool for return on operational reliability for discrete manufacturing. This White Paper covers most of the technical aspects
Keys to a more secure data environment
 Keys to a more secure data environment A holistic approach to data infrastructure security The current fraud and regulatory landscape makes it clear that every firm needs a comprehensive strategy for protecting
Keys to a more secure data environment A holistic approach to data infrastructure security The current fraud and regulatory landscape makes it clear that every firm needs a comprehensive strategy for protecting
Simple and Powerful Security for PCI DSS
 Simple and Powerful Security for PCI DSS The regulations AccessEnforcer helps check off your list. Most merchants think they are too small to be targeted by hackers. In fact, their small size makes them
Simple and Powerful Security for PCI DSS The regulations AccessEnforcer helps check off your list. Most merchants think they are too small to be targeted by hackers. In fact, their small size makes them
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
(1) Top Page. Before Using GCMS Plus. Chapter3. Top Page. Top Page is the initial screen displayed after you log in. My Menu
 Chapter Before Using GCMS Plus Cautions for Smooth (1) is the initial screen displayed after you log in. My Menu The frequently-used screens can be registered as a My Menu item by each user. Create My
Chapter Before Using GCMS Plus Cautions for Smooth (1) is the initial screen displayed after you log in. My Menu The frequently-used screens can be registered as a My Menu item by each user. Create My
WHITEPAPER. Security overview. podio.com
 WHITEPAPER Security overview Podio security White Paper 2 Podio, a cloud service brought to you by Citrix, provides a secure collaborative work platform for team and project management. Podio features
WHITEPAPER Security overview Podio security White Paper 2 Podio, a cloud service brought to you by Citrix, provides a secure collaborative work platform for team and project management. Podio features
One-Time PIN. User Guide
 One-Time PIN User Guide Table of Contents Online Banking Setting up One-Time PIN Registering your device Logging in with One-Time PIN Changing One-Time PIN Delivery Method Mobile Banking Setting up One-Time
One-Time PIN User Guide Table of Contents Online Banking Setting up One-Time PIN Registering your device Logging in with One-Time PIN Changing One-Time PIN Delivery Method Mobile Banking Setting up One-Time
SECURITY STRATEGY & POLICIES. Understanding How Swift Digital Protects Your Data
 SECURITY STRATEGY & POLICIES Understanding How Swift Digital Protects Your Data Table of Contents Introduction 1 Security Infrastructure 2 Security Strategy and Policies 2 Operational Security 3 Threat
SECURITY STRATEGY & POLICIES Understanding How Swift Digital Protects Your Data Table of Contents Introduction 1 Security Infrastructure 2 Security Strategy and Policies 2 Operational Security 3 Threat
SECURITY THAT FOLLOWS YOUR FILES ANYWHERE
 SECURITY THAT FOLLOWS YOUR FILES ANYWHERE SOLUTIONS FOR EVERY INDUSTRY VERA FOR FINANCIAL SERVICES Financial services firms are more likely to be targeted in a cyberattack than other organizations. Changes
SECURITY THAT FOLLOWS YOUR FILES ANYWHERE SOLUTIONS FOR EVERY INDUSTRY VERA FOR FINANCIAL SERVICES Financial services firms are more likely to be targeted in a cyberattack than other organizations. Changes
epldt Web Builder Security March 2017
 epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
Here is a screenshot of the log in screen you will see at the above address:
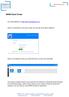 BWM Client Portal Our portal address is: https://bwm.clientspace.co.uk Here is a screenshot of the log in screen you will see at the above address: Here is an example of how your portal will look on screen
BWM Client Portal Our portal address is: https://bwm.clientspace.co.uk Here is a screenshot of the log in screen you will see at the above address: Here is an example of how your portal will look on screen
Compliant. Secure. Dependable.
 NAVIFY Cloud Security with the NAVIFY Tumor Board solution Compliant. Secure. Dependable. Trust that your oncology patients healthcare information stays protected. In the era of precision medicine, you
NAVIFY Cloud Security with the NAVIFY Tumor Board solution Compliant. Secure. Dependable. Trust that your oncology patients healthcare information stays protected. In the era of precision medicine, you
Get the most from your Health Savings Account. Your guide to your HSA and online account access
 Get the most from your Health Savings Account Your guide to your HSA and online account access 1 Health Savings Account Investments Contents Getting started... 2 Accessing the BBPadmin Online Portal...
Get the most from your Health Savings Account Your guide to your HSA and online account access 1 Health Savings Account Investments Contents Getting started... 2 Accessing the BBPadmin Online Portal...
INTRO TO AWS: SECURITY
 INTRO TO AWS: SECURITY Rob Whitmore Solutions Architect 2015, Amazon Web Services, Inc. or its affiliates. All rights reserved Security is the foundation Familiar security model Validated by security experts
INTRO TO AWS: SECURITY Rob Whitmore Solutions Architect 2015, Amazon Web Services, Inc. or its affiliates. All rights reserved Security is the foundation Familiar security model Validated by security experts
Security Specification
 Security Specification Security Specification Table of contents 1. Overview 2. Zero-knowledge cryptosystem a. The master password b. Secure user authentication c. Host-proof hosting d. Two-factor authentication
Security Specification Security Specification Table of contents 1. Overview 2. Zero-knowledge cryptosystem a. The master password b. Secure user authentication c. Host-proof hosting d. Two-factor authentication
THE DEFINITIVE GUIDE TO BACKUP FOR OFFICE 365
 THE DEFINITIVE GUIDE TO BACKUP FOR OFFICE 365 ENSURING COMPLETE AND EFFECTIVE DATA PROTECTION FOR OFFICE 365 TABLE OF CONTENTS THE TRUTH ABOUT SAAS DATA LOSS THE TOP 4 REASONS YOU NEED BACKUP FOR OFFICE
THE DEFINITIVE GUIDE TO BACKUP FOR OFFICE 365 ENSURING COMPLETE AND EFFECTIVE DATA PROTECTION FOR OFFICE 365 TABLE OF CONTENTS THE TRUTH ABOUT SAAS DATA LOSS THE TOP 4 REASONS YOU NEED BACKUP FOR OFFICE
HIPAA COMPLIANCE AND
 INTRONIS MSP SOLUTIONS BY BARRACUDA HIPAA COMPLIANCE AND DATA PROTECTION CONTENTS Introduction... 3 The HIPAA Security Rule... 4 The HIPAA Omnibus Rule... 6 HIPAA Compliance and Intronis Cloud Backup and
INTRONIS MSP SOLUTIONS BY BARRACUDA HIPAA COMPLIANCE AND DATA PROTECTION CONTENTS Introduction... 3 The HIPAA Security Rule... 4 The HIPAA Omnibus Rule... 6 HIPAA Compliance and Intronis Cloud Backup and
MD-HQ Utilizes Atlantic.Net s Private Cloud Solutions to Realize Tremendous Growth
 Success Story: MD-HQ Utilizes Atlantic.Net s Private Cloud Solutions to Realize Tremendous Growth Atlantic.Net specializes in providing security and compliance hosting solutions, most specifically in the
Success Story: MD-HQ Utilizes Atlantic.Net s Private Cloud Solutions to Realize Tremendous Growth Atlantic.Net specializes in providing security and compliance hosting solutions, most specifically in the
Google Cloud & the General Data Protection Regulation (GDPR)
 Google Cloud & the General Data Protection Regulation (GDPR) INTRODUCTION General Data Protection Regulation (GDPR) On 25 May 2018, the most significant piece of European data protection legislation to
Google Cloud & the General Data Protection Regulation (GDPR) INTRODUCTION General Data Protection Regulation (GDPR) On 25 May 2018, the most significant piece of European data protection legislation to
Guardium UI Login using a Smart card
 IBM Security Guardium Guardium UI Login using a Smart card Overview Guardium Smart card support meets the United States government mandate that all vendors must support multi-factor authentication for
IBM Security Guardium Guardium UI Login using a Smart card Overview Guardium Smart card support meets the United States government mandate that all vendors must support multi-factor authentication for
6 Tips to Find the Right Colocation Center for You
 6 Tips to Find the Right Colocation Center for You Choosing a colocation provider is one of the most important IT decisions you can make for your business. Think about it; your most valuable technology
6 Tips to Find the Right Colocation Center for You Choosing a colocation provider is one of the most important IT decisions you can make for your business. Think about it; your most valuable technology
Top. Reasons Legal Teams Select kiteworks by Accellion
 Top 10 Reasons Legal Teams Select kiteworks by Accellion Accellion Legal Customers Include: Top 10 Reasons Legal Teams Select kiteworks kiteworks by Accellion enables legal teams to manage their increasing
Top 10 Reasons Legal Teams Select kiteworks by Accellion Accellion Legal Customers Include: Top 10 Reasons Legal Teams Select kiteworks kiteworks by Accellion enables legal teams to manage their increasing
Awareness Technologies Systems Security. PHONE: (888)
 Awareness Technologies Systems Security Physical Facility Specifications At Awareness Technologies, the security of our customers data is paramount. The following information from our provider Amazon Web
Awareness Technologies Systems Security Physical Facility Specifications At Awareness Technologies, the security of our customers data is paramount. The following information from our provider Amazon Web
PCI DSS Compliance. White Paper Parallels Remote Application Server
 PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
6 Ways Office 365 Keeps Your and Business Secure
 6 Ways Office 365 Keeps Your Email and Business Secure Acora House, Albert Drive, Burgess Hill, West Sussex, RH15 9TN T: +44 (0) 844 264 2222 W: acora.com E: sales@acora.com Introduction Microsoft have
6 Ways Office 365 Keeps Your Email and Business Secure Acora House, Albert Drive, Burgess Hill, West Sussex, RH15 9TN T: +44 (0) 844 264 2222 W: acora.com E: sales@acora.com Introduction Microsoft have
Security Information & Policies
 Security Information & Policies 01 Table of Contents OVERVIEW CHAPTER 1 : CHAPTER 2: CHAPTER 3: CHAPTER 4: CHAPTER 5: CHAPTER 6: CHAPTER 7: CHAPTER 8: CHAPTER 9: CHAPTER 10: CHAPTER 11: CHAPTER 12: CHAPTER
Security Information & Policies 01 Table of Contents OVERVIEW CHAPTER 1 : CHAPTER 2: CHAPTER 3: CHAPTER 4: CHAPTER 5: CHAPTER 6: CHAPTER 7: CHAPTER 8: CHAPTER 9: CHAPTER 10: CHAPTER 11: CHAPTER 12: CHAPTER
