Extracting Attributed Verification and Debunking Reports from Social Media: MediaEval-2015 Trust and Credibility Analysis of Image and Video
|
|
|
- Kenneth Reeves
- 6 years ago
- Views:
Transcription
1 Extracting Attributed Verification and Debunking Reports from Social Media: MediaEval-2015 Trust and Credibility Analysis of Image and Video Stuart E. Middleton University Your Name of Your Southampton Company IT @RevealEU
2 UoS-ITI Team Overview Problem Statement Approach Results Discussion Suggestions for Verification Challenge
3 Problem Statement Verification of Images and Videos for Breaking News Breaking News Timescales Minutes not hours - its old news after a couple of hours Journalists need to verify copy and get it published before their rivals do Journalistic Manual Verification Procedures for User Generated Content (UGC) Check content provenance - original post? location? timestamp? similar posts? website?... Check author / source - attributed or author? known (un)reliable? popular? reputation? post history?... Check content credibility - right image metadata? right location? right people? right weather?... Phone the author up - triangulate facts, quiz author to check genuine, get authorization to publish Automate the Simpler Verification Steps Empowering journalists Increases the volume of contextual content that can be considered Focus humans on the more complex & subjective cross-checking tasks Contact content authors via phone and ask them difficult questions Does human behaviour 'look right' in a video? Cross-reference buildings / landmarks in image backgrounds to Google StreetView / image databases... see the VerificationHandbook» 2
4 Approach Attribute evidence to trusted or untrusted sources Hypothesis The 'wisdom of the crowd' is not really wisdom at all when it comes to verifying suspicious content It is better to rank evidence according to the most trusted & credible sources like journalists do Semi-automated approach Manually create a list of trusted sources Tweets» NLP» Extract fake & genuine claims & attribution to sources» Evidence Evidence» Cross-check all content for image / video» Fake/real decision based on best evidence Trustworthiness hierarchy for tweeted claims about images & videos Claim = statement that its a fake image / video or its genuine Claim authored by trusted source Claim authored by untrusted source Claim attributed to trusted source Claim attributed to untrusted source Unattributed claim 3
5 Approach Regex patterns Named Entity (NNP NN) # (NNP NN) (NNP NN) (NNP NN) (NNP NN) Attribution Patterns <NE> *{0,3} <IMAGE>... <NE> *{0,2} <RELEASE> *{0,4} <IMAGE> <IMAGE> *{0,6} <FROM> *{0,1} <NE>... <FROM> *{0,1} <NE>... <IMAGE> *{0,1} <NE>... <RT> <SEP>{0,1} <NE> Faked Patterns... *{0,2} <FAKED> <REAL>? <NEGATIVE> *{0,1} <REAL>... Genuine Patterns... <IMAGE> *{0,2} <REAL> <REAL> *{0,2} <IMAGE> <IS> *{0,1} <REAL> <NEGATIVE> *{0,1} <FAKE>... e.g. CNN BBC e.g. FBI has released prime suspect photos pic - BBC News... image released via CNN... RT: BBC News e.g.... what a fake! is it real? thats not real... e.g.... this image is totally genuine its real... Key <NE> = named entity (e.g. trusted source) <IMAGE> = image variants(e.g. pic, image, video) <FROM> = from variants(e.g. via, from, attributed) <REAL> = real variants (e.g. real, genuine) <NEGATIVE> = negative variants (e.g. not, isn't) <RT> = RT variants (e.g. RT, MT) <SEP> = separator variants (e.g. : - = ) <IS> = is its thats 4
6 Results Fake & Real Tweet Classifier faked & genuine patterns faked & genuine & attribution patterns Fake & Real Image Classifier
7 Results Fake & Real Tweet Classifier faked & genuine patterns faked & genuine & attribution patterns No mistakes classifying fakes in testset Low false positives important for end users like journalists Fake & Real Image Classifier
8 Results Fake & Real Tweet Classifier faked & genuine patterns faked & genuine & attribution patterns Performance looks good when averaged on whole dataset Fake & Real Image Classifier Not good for all images though Better classifying real images than fake ones 7
9 Discussion Application to our journalism use case Classifying tweets in isolation (fake and real) is of limited value High precision (89%+) but low recall (1%) Cross-check tweets then ranking by trustworthiness No false positives for using testset High precision (94%+) with average recall (43%+) looking across events in devset and testset Typically viral images & videos will have 100's of tweets before journalists become aware of them so a recall of 20% is probably OK in this context Image classifiers Fake image classifier» High precision (96-100%) but low recall (4-10%) Real image classifier» High precision (62-95%) but low recall (19-23%) Classification explained in ways journalists understand & therefore trust Image X claimed verified by Tweet Y attributing to trusted entity Z We can alert journalists to trustworthy reports of verification and/or debunking Our approach does not replace manual verification techniques Someone still needs to actually verify the content! 8
10 Suggestions for Verification Challenge 2016 Focus on image classification not Tweet classification The long term aim is to classify the images & videos NOT the tweets about them Suggestion» Score image classification results as well as tweet classification results End users usually wants to know if its real, not if its fake Classifying something as fake is usually a means to an end (e.g. to allow filtering) Suggestion» Score results for & Improve the Tweet datasets to avoid bias to a single event Suggest using leave one event out cross validation when computing P/R/F1 Suggest removing tweet repetition Some events (e.g. Syrian Boy) contain many duplicate tweets with a different author A classifier might only work well on 1 or 2 text styles BUT score highly as they are repeated a lot Suggest evenly balancing number of tweets per event type to avoid bias Devset - Hurricane Sandy event has about 84% of the tweets Testset - Syrian Boy event has about 47% of the tweets 9
11 Many thanks for your attention! Any questions? Stuart E. Middleton University of Southampton IT Innovation Centre 10
PUBLIC. AI supporting content verification and analysis. Session: Automated Fact-Checking: The way to go? Stuart E. Middleton
 Floraguard AI supporting content verification and analysis Session: Automated Fact-Checking: The way to go? Stuart E. Middleton University of Southampton, Electronics and Computer Science www.ecs.soton.ac.uk/people/sem
Floraguard AI supporting content verification and analysis Session: Automated Fact-Checking: The way to go? Stuart E. Middleton University of Southampton, Electronics and Computer Science www.ecs.soton.ac.uk/people/sem
Deliverable D Visualization and analytical tools
 REVEAL FP7-610928 REVEALing hidden concepts in Social Media Deliverable D5.4.2 Visualization and analytical tools Editor(s): Responsible Partner: Stuart E. Middleton University of Southampton IT Innovation
REVEAL FP7-610928 REVEALing hidden concepts in Social Media Deliverable D5.4.2 Visualization and analytical tools Editor(s): Responsible Partner: Stuart E. Middleton University of Southampton IT Innovation
How to be a digital detective
 How to be a digital detective Online fact-checking and verification Raymond Joseph, MMX 2018, Johannesburg June 2018 But fake often trumps truth because the messenger has the loudest voice Fake come
How to be a digital detective Online fact-checking and verification Raymond Joseph, MMX 2018, Johannesburg June 2018 But fake often trumps truth because the messenger has the loudest voice Fake come
AN SEO GUIDE FOR SALONS
 AN SEO GUIDE FOR SALONS AN SEO GUIDE FOR SALONS Set Up Time 2/5 The basics of SEO are quick and easy to implement. Management Time 3/5 You ll need a continued commitment to make SEO work for you. WHAT
AN SEO GUIDE FOR SALONS AN SEO GUIDE FOR SALONS Set Up Time 2/5 The basics of SEO are quick and easy to implement. Management Time 3/5 You ll need a continued commitment to make SEO work for you. WHAT
BBC Learning English 6 Minute English Work s
 BBC Learning English 6 Minute English Work Emails NB: This is not a word for word transcript Hello and welcome to 6 Minute English from BBC Learning English. I'm Michelle. And I'm Neil. Thanks for joining
BBC Learning English 6 Minute English Work Emails NB: This is not a word for word transcript Hello and welcome to 6 Minute English from BBC Learning English. I'm Michelle. And I'm Neil. Thanks for joining
QUALITY SEO LINK BUILDING
 QUALITY SEO LINK BUILDING Developing Your Online Profile through Quality Links TABLE OF CONTENTS Introduction The Impact Links Have on Your Search Profile 02 Chapter II Evaluating Your Link Profile 03
QUALITY SEO LINK BUILDING Developing Your Online Profile through Quality Links TABLE OF CONTENTS Introduction The Impact Links Have on Your Search Profile 02 Chapter II Evaluating Your Link Profile 03
A bit of theory: Algorithms
 A bit of theory: Algorithms There are different kinds of algorithms Vector space models. e.g. support vector machines Decision trees, e.g. C45 Probabilistic models, e.g. Naive Bayes Neural networks, e.g.
A bit of theory: Algorithms There are different kinds of algorithms Vector space models. e.g. support vector machines Decision trees, e.g. C45 Probabilistic models, e.g. Naive Bayes Neural networks, e.g.
Class Sep Instructor: Bhiksha Raj
 11-755 Machine Learning for Signal Processing Boosting, face detection Class 7. 14 Sep 2010 Instructor: Bhiksha Raj 1 Administrivia: Projects Only 1 group so far Plus one individual Notify us about your
11-755 Machine Learning for Signal Processing Boosting, face detection Class 7. 14 Sep 2010 Instructor: Bhiksha Raj 1 Administrivia: Projects Only 1 group so far Plus one individual Notify us about your
The InVID Plug-in: Web Video Verification on the Browser
 The InVID Plug-in: Web Video Verification on the Browser D. Teyssou 1, J.-M. Leung 1, E. Apostolidis 2, K. Apostolidis 2, S. Papadopoulos 2, M. Zampoglou 2, O. Papadopoulou 2, V. Mezaris 2 1. AFP Medialab,
The InVID Plug-in: Web Video Verification on the Browser D. Teyssou 1, J.-M. Leung 1, E. Apostolidis 2, K. Apostolidis 2, S. Papadopoulos 2, M. Zampoglou 2, O. Papadopoulou 2, V. Mezaris 2 1. AFP Medialab,
Condition Controlled Loops. Introduction to Programming - Python
 + Condition Controlled Loops Introduction to Programming - Python + Repetition Structures n Programmers commonly find that they need to write code that performs the same task over and over again + Example:
+ Condition Controlled Loops Introduction to Programming - Python + Repetition Structures n Programmers commonly find that they need to write code that performs the same task over and over again + Example:
Social Bookmarks. Blasting their site with them during the first month of creation Only sending them directly to their site
 Hey guys, what's up? We have another, jammed packed and exciting bonus coming at you today. This one is all about the "Everyone knows Everybody" generation; where everyone is socially connected via the
Hey guys, what's up? We have another, jammed packed and exciting bonus coming at you today. This one is all about the "Everyone knows Everybody" generation; where everyone is socially connected via the
University of Sheffield, NLP. Chunking Practical Exercise
 Chunking Practical Exercise Chunking for NER Chunking, as we saw at the beginning, means finding parts of text This task is often called Named Entity Recognition (NER), in the context of finding person
Chunking Practical Exercise Chunking for NER Chunking, as we saw at the beginning, means finding parts of text This task is often called Named Entity Recognition (NER), in the context of finding person
PROTECTING YOUR BUSINESS ASSETS
 PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
Getting the most out of Reputation Management. Your How To Guide
 Getting the most out of Reputation Management Your How To Guide Getting Started Access your account at www.directwest.com using your established username and password. Getting Started Recent activity allows
Getting the most out of Reputation Management Your How To Guide Getting Started Access your account at www.directwest.com using your established username and password. Getting Started Recent activity allows
Strange Science: The Rocky Road to Modern Paleontology and Biology
 Jasroop Pannu Feb 20,13 Dinosaur Webquest Step 1 Age of the dinosaurs This website is straightforward and it s easy to find. This website was updated recently so that shows it s a trustworthy website The
Jasroop Pannu Feb 20,13 Dinosaur Webquest Step 1 Age of the dinosaurs This website is straightforward and it s easy to find. This website was updated recently so that shows it s a trustworthy website The
Launch Store. University
 Launch Store University Store Settings In this lesson, you will learn about: Completing your Store Profile Down for maintenance, physical dimensions and SEO settings Display and image settings Time zone,
Launch Store University Store Settings In this lesson, you will learn about: Completing your Store Profile Down for maintenance, physical dimensions and SEO settings Display and image settings Time zone,
Copyright 2018 Trend Micro Incorporated. All rights reserved.
 Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent
Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Definition: A data structure is a way of organizing data in a computer so that it can be used efficiently.
 The Science of Computing I Lesson 4: Introduction to Data Structures Living with Cyber Pillar: Data Structures The need for data structures The algorithms we design to solve problems rarely do so without
The Science of Computing I Lesson 4: Introduction to Data Structures Living with Cyber Pillar: Data Structures The need for data structures The algorithms we design to solve problems rarely do so without
Big Data Analytics CSCI 4030
 High dim. data Graph data Infinite data Machine learning Apps Locality sensitive hashing PageRank, SimRank Filtering data streams SVM Recommen der systems Clustering Community Detection Web advertising
High dim. data Graph data Infinite data Machine learning Apps Locality sensitive hashing PageRank, SimRank Filtering data streams SVM Recommen der systems Clustering Community Detection Web advertising
Ghent University-IBCN Participation in TAC-KBP 2015 Cold Start Slot Filling task
 Ghent University-IBCN Participation in TAC-KBP 2015 Cold Start Slot Filling task Lucas Sterckx, Thomas Demeester, Johannes Deleu, Chris Develder Ghent University - iminds Gaston Crommenlaan 8 Ghent, Belgium
Ghent University-IBCN Participation in TAC-KBP 2015 Cold Start Slot Filling task Lucas Sterckx, Thomas Demeester, Johannes Deleu, Chris Develder Ghent University - iminds Gaston Crommenlaan 8 Ghent, Belgium
Relational inductive biases, deep learning, and graph networks
 Relational inductive biases, deep learning, and graph networks Peter Battaglia et al. 2018 1 What The authors explore how we can combine relational inductive biases and DL. They introduce graph network
Relational inductive biases, deep learning, and graph networks Peter Battaglia et al. 2018 1 What The authors explore how we can combine relational inductive biases and DL. They introduce graph network
What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource.
 P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
CLIENT ONBOARDING PLAN & SCRIPT
 CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT
 CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
Website Designs Australia
 Proudly Brought To You By: Website Designs Australia Contents Disclaimer... 4 Why Your Local Business Needs Google Plus... 5 1 How Google Plus Can Improve Your Search Engine Rankings... 6 1. Google Search
Proudly Brought To You By: Website Designs Australia Contents Disclaimer... 4 Why Your Local Business Needs Google Plus... 5 1 How Google Plus Can Improve Your Search Engine Rankings... 6 1. Google Search
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
TOP RANKING FACTORS A QUICK OVERVIEW OF THE TRENDING TOP RANKING FACTORS
 TOP RANKING FACTORS A QUICK OVERVIEW OF THE TRENDING TOP RANKING FACTORS SEO is NOT Dead Plenty of New Algorithm Updates Panda, Penguin, Hummingbird, RankBrain (AI and Deep Learning) New Ranking Factors
TOP RANKING FACTORS A QUICK OVERVIEW OF THE TRENDING TOP RANKING FACTORS SEO is NOT Dead Plenty of New Algorithm Updates Panda, Penguin, Hummingbird, RankBrain (AI and Deep Learning) New Ranking Factors
Creating a Classifier for a Focused Web Crawler
 Creating a Classifier for a Focused Web Crawler Nathan Moeller December 16, 2015 1 Abstract With the increasing size of the web, it can be hard to find high quality content with traditional search engines.
Creating a Classifier for a Focused Web Crawler Nathan Moeller December 16, 2015 1 Abstract With the increasing size of the web, it can be hard to find high quality content with traditional search engines.
Large Scale Data Analysis Using Deep Learning
 Large Scale Data Analysis Using Deep Learning Machine Learning Basics - 1 U Kang Seoul National University U Kang 1 In This Lecture Overview of Machine Learning Capacity, overfitting, and underfitting
Large Scale Data Analysis Using Deep Learning Machine Learning Basics - 1 U Kang Seoul National University U Kang 1 In This Lecture Overview of Machine Learning Capacity, overfitting, and underfitting
This lesson is part 5 of 5 in a series. You can go to Invoice, Part 1: Free Shipping if you'd like to start from the beginning.
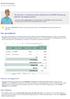 Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
Copyright
 This video will look at the different Terminology that is used with Federation Services. This will give you a good indication of what components make up a Federation Service in Active Directory Federation
This video will look at the different Terminology that is used with Federation Services. This will give you a good indication of what components make up a Federation Service in Active Directory Federation
IT Innovation Centre, University of Southampton, UK. Deutsches Geo-Forschungs-Zentrum - GFZ, Germany. Fraunhofer IOSB, Germany
 Collaborative, Complex and Critical Decision-Support in Evolving Crisis Multi-disciplinary approaches to intelligently sharing largevolumes of real-time sensor data during natural disasters Stuart E. Middleton
Collaborative, Complex and Critical Decision-Support in Evolving Crisis Multi-disciplinary approaches to intelligently sharing largevolumes of real-time sensor data during natural disasters Stuart E. Middleton
Query Phrase Expansion using Wikipedia for Patent Class Search
 Query Phrase Expansion using Wikipedia for Patent Class Search 1 Bashar Al-Shboul, Sung-Hyon Myaeng Korea Advanced Institute of Science and Technology (KAIST) December 19 th, 2011 AIRS 11, Dubai, UAE OUTLINE
Query Phrase Expansion using Wikipedia for Patent Class Search 1 Bashar Al-Shboul, Sung-Hyon Myaeng Korea Advanced Institute of Science and Technology (KAIST) December 19 th, 2011 AIRS 11, Dubai, UAE OUTLINE
Transparency report. Examining the AV-TEST January-February 2018 Results. Prepared by. Windows Defender Research team
 Transparency report Examining the AV-TEST January-February 2018 Results Prepared by Windows Defender Research team 2018 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information
Transparency report Examining the AV-TEST January-February 2018 Results Prepared by Windows Defender Research team 2018 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information
CSE 258. Web Mining and Recommender Systems. Advanced Recommender Systems
 CSE 258 Web Mining and Recommender Systems Advanced Recommender Systems This week Methodological papers Bayesian Personalized Ranking Factorizing Personalized Markov Chains Personalized Ranking Metric
CSE 258 Web Mining and Recommender Systems Advanced Recommender Systems This week Methodological papers Bayesian Personalized Ranking Factorizing Personalized Markov Chains Personalized Ranking Metric
Big Data Analytics CSCI 4030
 High dim. data Graph data Infinite data Machine learning Apps Locality sensitive hashing PageRank, SimRank Filtering data streams SVM Recommen der systems Clustering Community Detection Web advertising
High dim. data Graph data Infinite data Machine learning Apps Locality sensitive hashing PageRank, SimRank Filtering data streams SVM Recommen der systems Clustering Community Detection Web advertising
NACTA 2013 Texas A&M University
 Tweets Caroline Black @carokblack June 26 College Students perceptions of foodborne illness related tweet credibility based on features and sources #NACTA13 NACTA 2013 Texas A&M University @Background
Tweets Caroline Black @carokblack June 26 College Students perceptions of foodborne illness related tweet credibility based on features and sources #NACTA13 NACTA 2013 Texas A&M University @Background
Evaluation. David Kauchak cs160 Fall 2009 adapted from:
 Evaluation David Kauchak cs160 Fall 2009 adapted from: http://www.stanford.edu/class/cs276/handouts/lecture8-evaluation.ppt Administrative How are things going? Slides Points Zipf s law IR Evaluation For
Evaluation David Kauchak cs160 Fall 2009 adapted from: http://www.stanford.edu/class/cs276/handouts/lecture8-evaluation.ppt Administrative How are things going? Slides Points Zipf s law IR Evaluation For
Learn SEO Copywriting
 This is video 1.1 in the online course: Learn SEO Copywriting Module 1: An introduction to SEO copywriting What we ll cover in this session What is SEO? What is SEO copywriting? How does Google work Factors
This is video 1.1 in the online course: Learn SEO Copywriting Module 1: An introduction to SEO copywriting What we ll cover in this session What is SEO? What is SEO copywriting? How does Google work Factors
Creational. Structural
 Fitness for Future of Design Patterns & Architectural Styles Design patterns are difficult to teach, so we conducted a class collaboration where we all researched and reported on a variety of design patterns
Fitness for Future of Design Patterns & Architectural Styles Design patterns are difficult to teach, so we conducted a class collaboration where we all researched and reported on a variety of design patterns
Oleksandr Kuzomin, Bohdan Tkachenko
 International Journal "Information Technologies Knowledge" Volume 9, Number 2, 2015 131 INTELLECTUAL SEARCH ENGINE OF ADEQUATE INFORMATION IN INTERNET FOR CREATING DATABASES AND KNOWLEDGE BASES Oleksandr
International Journal "Information Technologies Knowledge" Volume 9, Number 2, 2015 131 INTELLECTUAL SEARCH ENGINE OF ADEQUATE INFORMATION IN INTERNET FOR CREATING DATABASES AND KNOWLEDGE BASES Oleksandr
Web Search. Lecture Objectives. Text Technologies for Data Science INFR Learn about: 11/14/2017. Instructor: Walid Magdy
 Text Technologies for Data Science INFR11145 Web Search Instructor: Walid Magdy 14-Nov-2017 Lecture Objectives Learn about: Working with Massive data Link analysis (PageRank) Anchor text 2 1 The Web Document
Text Technologies for Data Science INFR11145 Web Search Instructor: Walid Magdy 14-Nov-2017 Lecture Objectives Learn about: Working with Massive data Link analysis (PageRank) Anchor text 2 1 The Web Document
Privacy Preserving Ranked Multi-Keyword Search for Multiple Data Owners in Cloud Computing
 S.NO PROJECT CODE IEEE JAVA PROJECT TITLES DOMAIN 1 NEO1501 A Hybrid Cloud Approach for Secure Authorized Deduplication 2 NEO1502 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud
S.NO PROJECT CODE IEEE JAVA PROJECT TITLES DOMAIN 1 NEO1501 A Hybrid Cloud Approach for Secure Authorized Deduplication 2 NEO1502 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud
Setting up your Netvibes Dashboard Adding a Blog to your Dashboard
 Cr e a t i ngali s t e ni ngda s hboa r d wi t hne t vi be s Ne t v i be s Table of Contents Introduction... 1 Setting up your Netvibes Dashboard... 2 Adding a Blog to your Dashboard... 2 Adding Twitter
Cr e a t i ngali s t e ni ngda s hboa r d wi t hne t vi be s Ne t v i be s Table of Contents Introduction... 1 Setting up your Netvibes Dashboard... 2 Adding a Blog to your Dashboard... 2 Adding Twitter
University of Sheffield, NLP. Chunking Practical Exercise
 Chunking Practical Exercise Chunking for NER Chunking, as we saw at the beginning, means finding parts of text This task is often called Named Entity Recognition (NER), in the context of finding person
Chunking Practical Exercise Chunking for NER Chunking, as we saw at the beginning, means finding parts of text This task is often called Named Entity Recognition (NER), in the context of finding person
Keyword. Landing Page Audit. project management. basecamp.com. Put the important stuff above the fold. basecamp.com
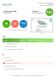 41 Good Signals 17 Issues Found Page Grade Put the important stuff above the fold. SPEED SECONDS 0.23 KILOBYTES 207.96 REQUESTS 7 This page loads fast enough This size of this page is ok The number of
41 Good Signals 17 Issues Found Page Grade Put the important stuff above the fold. SPEED SECONDS 0.23 KILOBYTES 207.96 REQUESTS 7 This page loads fast enough This size of this page is ok The number of
Creating Templates For Letterheads, Fax Cover Sheets, and More
 Creating Templates For Letterheads, Fax Cover Sheets, and More This document provides instructions for creating and using templates in Microsoft Word. Opening Comments A template is a type of document
Creating Templates For Letterheads, Fax Cover Sheets, and More This document provides instructions for creating and using templates in Microsoft Word. Opening Comments A template is a type of document
Search Engine Optimization. Presentation Overview 1/7/2014. Internet Marketing Reality Check: Discover the Techniques Proven to Increase Leads
 Internet Marketing Reality Check: Discover the Techniques Proven to Increase Leads FEBRUARY 6, 2014 10:00 11:00 AM Presenter: Chris Behan // Socius Marketing, Tampa, FL Presentation Overview Search Engine
Internet Marketing Reality Check: Discover the Techniques Proven to Increase Leads FEBRUARY 6, 2014 10:00 11:00 AM Presenter: Chris Behan // Socius Marketing, Tampa, FL Presentation Overview Search Engine
CSCI 5417 Information Retrieval Systems. Jim Martin!
 CSCI 5417 Information Retrieval Systems Jim Martin! Lecture 7 9/13/2011 Today Review Efficient scoring schemes Approximate scoring Evaluating IR systems 1 Normal Cosine Scoring Speedups... Compute the
CSCI 5417 Information Retrieval Systems Jim Martin! Lecture 7 9/13/2011 Today Review Efficient scoring schemes Approximate scoring Evaluating IR systems 1 Normal Cosine Scoring Speedups... Compute the
Embedding Intelligence through Cognitive Services
 Embedding Intelligence through Cognitive Services Dr. Latika Kharb 1, Sarabjit Kaur 2 Associate Professor 1, Student 2, Jagan Institute of Management Studies (JIMS), Delhi, India. Abstract: Cognitive Services
Embedding Intelligence through Cognitive Services Dr. Latika Kharb 1, Sarabjit Kaur 2 Associate Professor 1, Student 2, Jagan Institute of Management Studies (JIMS), Delhi, India. Abstract: Cognitive Services
CS230: Lecture 3 Various Deep Learning Topics
 CS230: Lecture 3 Various Deep Learning Topics Kian Katanforoosh, Andrew Ng Today s outline We will learn how to: - Analyse a problem from a deep learning approach - Choose an architecture - Choose a loss
CS230: Lecture 3 Various Deep Learning Topics Kian Katanforoosh, Andrew Ng Today s outline We will learn how to: - Analyse a problem from a deep learning approach - Choose an architecture - Choose a loss
Marketing & Back Office Management
 Marketing & Back Office Management Menu Management Add, Edit, Delete Menu Gallery Management Add, Edit, Delete Images Banner Management Update the banner image/background image in web ordering Online Data
Marketing & Back Office Management Menu Management Add, Edit, Delete Menu Gallery Management Add, Edit, Delete Images Banner Management Update the banner image/background image in web ordering Online Data
CONDITION CONTROLLED LOOPS. Introduction to Programming - Python
 CONDITION CONTROLLED LOOPS Introduction to Programming - Python Generating Random Numbers Generating a random integer Sometimes you need your program to generate information that isn t available when you
CONDITION CONTROLLED LOOPS Introduction to Programming - Python Generating Random Numbers Generating a random integer Sometimes you need your program to generate information that isn t available when you
Chuck Cartledge, PhD. 23 September 2017
 Introduction K-Nearest Neighbors Na ıve Bayes Hands-on Q&A Conclusion References Files Misc. Big Data: Data Analysis Boot Camp Classification with K-Nearest Neighbors and Na ıve Bayes Chuck Cartledge,
Introduction K-Nearest Neighbors Na ıve Bayes Hands-on Q&A Conclusion References Files Misc. Big Data: Data Analysis Boot Camp Classification with K-Nearest Neighbors and Na ıve Bayes Chuck Cartledge,
Anurag Sharma (IIT Bombay) 1 / 13
 0 Map Reduce Algorithm Design Anurag Sharma (IIT Bombay) 1 / 13 Relational Joins Anurag Sharma Fundamental Research Group IIT Bombay Anurag Sharma (IIT Bombay) 1 / 13 Secondary Sorting Required if we need
0 Map Reduce Algorithm Design Anurag Sharma (IIT Bombay) 1 / 13 Relational Joins Anurag Sharma Fundamental Research Group IIT Bombay Anurag Sharma (IIT Bombay) 1 / 13 Secondary Sorting Required if we need
The Data Divide. Luke Segars - Google CS10
 The Data Divide Luke Segars - Google 11/7/2012 @ CS10 Statement Google's advantage is not in writing drastically better software; it's in having more data. Question Can any problem be solved by computers
The Data Divide Luke Segars - Google 11/7/2012 @ CS10 Statement Google's advantage is not in writing drastically better software; it's in having more data. Question Can any problem be solved by computers
Part 1: Link Analysis & Page Rank
 Chapter 8: Graph Data Part 1: Link Analysis & Page Rank Based on Leskovec, Rajaraman, Ullman 214: Mining of Massive Datasets 1 Graph Data: Social Networks [Source: 4-degrees of separation, Backstrom-Boldi-Rosa-Ugander-Vigna,
Chapter 8: Graph Data Part 1: Link Analysis & Page Rank Based on Leskovec, Rajaraman, Ullman 214: Mining of Massive Datasets 1 Graph Data: Social Networks [Source: 4-degrees of separation, Backstrom-Boldi-Rosa-Ugander-Vigna,
Cross-Lingual Cross-Platform Rumor Verification Pivoting on Multimedia Content
 Cross-Lingual Cross-Platform Rumor Verification Pivoting on Multimedia Content Weiming Wen 1, Songwen Su 1, Zhou Yu 1 1 University of California, Davis wmwen@ucdavis.edu Abstract With the increasing popularity
Cross-Lingual Cross-Platform Rumor Verification Pivoting on Multimedia Content Weiming Wen 1, Songwen Su 1, Zhou Yu 1 1 University of California, Davis wmwen@ucdavis.edu Abstract With the increasing popularity
THOMAS LATOZA SWE 621 FALL 2018 DESIGN ECOSYSTEMS
 THOMAS LATOZA SWE 621 FALL 2018 DESIGN ECOSYSTEMS LOGISTICS HW5 due today Project presentation on 12/6 Review for final on 12/6 2 EXAMPLE: NPM https://twitter.com/garybernhardt/status/1067111872225136640
THOMAS LATOZA SWE 621 FALL 2018 DESIGN ECOSYSTEMS LOGISTICS HW5 due today Project presentation on 12/6 Review for final on 12/6 2 EXAMPLE: NPM https://twitter.com/garybernhardt/status/1067111872225136640
The Functional Extension Parser (FEP) A Document Understanding Platform
 The Functional Extension Parser (FEP) A Document Understanding Platform Günter Mühlberger University of Innsbruck Department for German Language and Literature Studies Introduction A book is more than
The Functional Extension Parser (FEP) A Document Understanding Platform Günter Mühlberger University of Innsbruck Department for German Language and Literature Studies Introduction A book is more than
AN EVALUATION OF THE GOOGLE CHROME EXTENSION SECURITY ARCHITECTURE
 AN EVALUATION OF THE GOOGLE CHROME EXTENSION SECURITY ARCHITECTURE Nicholas Carlini, Adrienne Porter Felt, David Wagner University of California, Berkeley CHROME EXTENSIONS CHROME EXTENSIONS servers servers
AN EVALUATION OF THE GOOGLE CHROME EXTENSION SECURITY ARCHITECTURE Nicholas Carlini, Adrienne Porter Felt, David Wagner University of California, Berkeley CHROME EXTENSIONS CHROME EXTENSIONS servers servers
Big Data - Some Words BIG DATA 8/31/2017. Introduction
 BIG DATA Introduction Big Data - Some Words Connectivity Social Medias Share information Interactivity People Business Data Data mining Text mining Business Intelligence 1 What is Big Data Big Data means
BIG DATA Introduction Big Data - Some Words Connectivity Social Medias Share information Interactivity People Business Data Data mining Text mining Business Intelligence 1 What is Big Data Big Data means
OPEN-CSAM INFORMATION AGGREGATOR AND REPORTING TOOL USING AI AND NATURAL LANGUAGE PROCESSING
 OPEN-CSAM INFORMATION AGGREGATOR AND REPORTING TOOL USING AI AND NATURAL LANGUAGE PROCESSING Georgios Chatzichristos Operational Security Unit - ENISA 6 11 2018 THE GOAL Help Decision Makers take better
OPEN-CSAM INFORMATION AGGREGATOR AND REPORTING TOOL USING AI AND NATURAL LANGUAGE PROCESSING Georgios Chatzichristos Operational Security Unit - ENISA 6 11 2018 THE GOAL Help Decision Makers take better
Fraud Detection of Mobile Apps
 Fraud Detection of Mobile Apps Urmila Aware*, Prof. Amruta Deshmuk** *(Student, Dept of Computer Engineering, Flora Institute Of Technology Pune, Maharashtra, India **( Assistant Professor, Dept of Computer
Fraud Detection of Mobile Apps Urmila Aware*, Prof. Amruta Deshmuk** *(Student, Dept of Computer Engineering, Flora Institute Of Technology Pune, Maharashtra, India **( Assistant Professor, Dept of Computer
Project 3 Q&A. Jonathan Krause
 Project 3 Q&A Jonathan Krause 1 Outline R-CNN Review Error metrics Code Overview Project 3 Report Project 3 Presentations 2 Outline R-CNN Review Error metrics Code Overview Project 3 Report Project 3 Presentations
Project 3 Q&A Jonathan Krause 1 Outline R-CNN Review Error metrics Code Overview Project 3 Report Project 3 Presentations 2 Outline R-CNN Review Error metrics Code Overview Project 3 Report Project 3 Presentations
TISA Methodology Threat Intelligence Scoring and Analysis
 TISA Methodology Threat Intelligence Scoring and Analysis Contents Introduction 2 Defining the Problem 2 The Use of Machine Learning for Intelligence Analysis 3 TISA Text Analysis and Feature Extraction
TISA Methodology Threat Intelligence Scoring and Analysis Contents Introduction 2 Defining the Problem 2 The Use of Machine Learning for Intelligence Analysis 3 TISA Text Analysis and Feature Extraction
Verizon Backup Assistant Failed To Sync Error Code 5
 Verizon Backup Assistant Failed To Sync Error Code 5 Learn how to get and use Backup Assistant for backing up contacts on a basic phone Backup Assistant is a service that saves a copy of your device's
Verizon Backup Assistant Failed To Sync Error Code 5 Learn how to get and use Backup Assistant for backing up contacts on a basic phone Backup Assistant is a service that saves a copy of your device's
Do you want to drive more traffic to your store without buying ads?
 Do you want to drive more traffic to your store without buying ads? This guide has everything you need to know! Introduction To E-Commerce SEO Did you know that organic search results are 8.5x more likely
Do you want to drive more traffic to your store without buying ads? This guide has everything you need to know! Introduction To E-Commerce SEO Did you know that organic search results are 8.5x more likely
Statistics Class 25. May 14 th 2012
 Statistics Class 25 May 14 th 2012 Quiz 20 Listed below are the overhead widths (in cm) of seals measured from photographs and the weights of the seals (in kg). The purpose of the study was to determine
Statistics Class 25 May 14 th 2012 Quiz 20 Listed below are the overhead widths (in cm) of seals measured from photographs and the weights of the seals (in kg). The purpose of the study was to determine
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
W3C Provenance Incubator Group: An Overview. Thanks to Contributing Group Members
 W3C Provenance Incubator Group: An Overview DRAFT March 10, 2010 1 Thanks to Contributing Group Members 2 Outline What is Provenance Need for
W3C Provenance Incubator Group: An Overview DRAFT March 10, 2010 1 Thanks to Contributing Group Members 2 Outline What is Provenance Need for
Social Media Reputation Management
 Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Lambton Primary School
 Lambton Primary School Advice to pupils on Cyber Bullying For pupils If you re being bullied by phone or the internet Remember, bullying is never your fault. It can be stopped, and it can usually be traced.
Lambton Primary School Advice to pupils on Cyber Bullying For pupils If you re being bullied by phone or the internet Remember, bullying is never your fault. It can be stopped, and it can usually be traced.
Deep Face Recognition. Nathan Sun
 Deep Face Recognition Nathan Sun Why Facial Recognition? Picture ID or video tracking Higher Security for Facial Recognition Software Immensely useful to police in tracking suspects Your face will be an
Deep Face Recognition Nathan Sun Why Facial Recognition? Picture ID or video tracking Higher Security for Facial Recognition Software Immensely useful to police in tracking suspects Your face will be an
Shrey Patel B.E. Computer Engineering, Gujarat Technological University, Ahmedabad, Gujarat, India
 International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2018 IJSRCSEIT Volume 3 Issue 3 ISSN : 2456-3307 Some Issues in Application of NLP to Intelligent
International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2018 IJSRCSEIT Volume 3 Issue 3 ISSN : 2456-3307 Some Issues in Application of NLP to Intelligent
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
MARKETING VOL. 1
 EMAIL MARKETING VOL. 1 TITLE: Email Promoting: What You Need To Do Author: Iris Carter-Collins Table Of Contents 1 Email Promoting: What You Need To Do 4 Building Your Business Through Successful Marketing
EMAIL MARKETING VOL. 1 TITLE: Email Promoting: What You Need To Do Author: Iris Carter-Collins Table Of Contents 1 Email Promoting: What You Need To Do 4 Building Your Business Through Successful Marketing
CS5670: Computer Vision
 CS5670: Computer Vision Noah Snavely Lecture 33: Recognition Basics Slides from Andrej Karpathy and Fei-Fei Li http://vision.stanford.edu/teaching/cs231n/ Announcements Quiz moved to Tuesday Project 4
CS5670: Computer Vision Noah Snavely Lecture 33: Recognition Basics Slides from Andrej Karpathy and Fei-Fei Li http://vision.stanford.edu/teaching/cs231n/ Announcements Quiz moved to Tuesday Project 4
InfoQ: Computational Assessment of Information Quality on the Web. Centrum voor Wiskunde en Informatica (CWI) Vrije Universiteit Amsterdam
 InfoQ: Computational Assessment of Information Quality on the Web Davide Ceolin 1 *, Chantal van Son 2, Lora Aroyo 2, Julia Noordegraaf 3, Ozkan Sener 2, Robin Sharma 2, Piek Vossen 2, Serge ter Braake
InfoQ: Computational Assessment of Information Quality on the Web Davide Ceolin 1 *, Chantal van Son 2, Lora Aroyo 2, Julia Noordegraaf 3, Ozkan Sener 2, Robin Sharma 2, Piek Vossen 2, Serge ter Braake
Aiding the Detection of Fake Accounts in Large Scale Social Online Services
 Aiding the Detection of Fake Accounts in Large Scale Social Online Services Qiang Cao Duke University Michael Sirivianos Xiaowei Yang Tiago Pregueiro Cyprus Univ. of Technology Duke University Tuenti,
Aiding the Detection of Fake Accounts in Large Scale Social Online Services Qiang Cao Duke University Michael Sirivianos Xiaowei Yang Tiago Pregueiro Cyprus Univ. of Technology Duke University Tuenti,
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE
 ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
Artificial Intelligence. Programming Styles
 Artificial Intelligence Intro to Machine Learning Programming Styles Standard CS: Explicitly program computer to do something Early AI: Derive a problem description (state) and use general algorithms to
Artificial Intelligence Intro to Machine Learning Programming Styles Standard CS: Explicitly program computer to do something Early AI: Derive a problem description (state) and use general algorithms to
Trust is the Foundations for Computer Security
 Christian Damsgaard Jensen Department of Applied Mathematics and Computer Science Technical University of Denmark Christian.Jensen@imm.dtu.dk Security and Trust Computer security is sometimes divided into:
Christian Damsgaard Jensen Department of Applied Mathematics and Computer Science Technical University of Denmark Christian.Jensen@imm.dtu.dk Security and Trust Computer security is sometimes divided into:
The Money Is in the Square Cash Lets Users Funds to Friends
 The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
Towards secure Internet. TIVIT results and business forum, Prof. Mika Rautila VTT Technical Research Centre of Finland
 Towards secure Internet TIVIT results and business forum, 12.4.2011 Prof. Mika Rautila VTT Technical Research Centre of Finland 2 Tivit Future Internet Program 2008-2013 Vision: Future Internet = a mission
Towards secure Internet TIVIT results and business forum, 12.4.2011 Prof. Mika Rautila VTT Technical Research Centre of Finland 2 Tivit Future Internet Program 2008-2013 Vision: Future Internet = a mission
Using the Force of Python and SAS Viya on Star Wars Fan Posts
 SESUG Paper BB-170-2017 Using the Force of Python and SAS Viya on Star Wars Fan Posts Grace Heyne, Zencos Consulting, LLC ABSTRACT The wealth of information available on the Internet includes useful and
SESUG Paper BB-170-2017 Using the Force of Python and SAS Viya on Star Wars Fan Posts Grace Heyne, Zencos Consulting, LLC ABSTRACT The wealth of information available on the Internet includes useful and
Total Recall: Automatic Query Expansion with a Generative Feature Model for Object Retrieval O. Chum, et al.
 Total Recall: Automatic Query Expansion with a Generative Feature Model for Object Retrieval O. Chum, et al. Presented by Brandon Smith Computer Vision Fall 2007 Objective Given a query image of an object,
Total Recall: Automatic Query Expansion with a Generative Feature Model for Object Retrieval O. Chum, et al. Presented by Brandon Smith Computer Vision Fall 2007 Objective Given a query image of an object,
Below is another example, taken from a REAL profile on one of the sites in my packet of someone abusing the sites.
 Before I show you this month's sites, I need to go over a couple of things, so that we are all on the same page. You will be shown how to leave your link on each of the sites, but abusing the sites can
Before I show you this month's sites, I need to go over a couple of things, so that we are all on the same page. You will be shown how to leave your link on each of the sites, but abusing the sites can
Trust in the Internet of Things From Personal Experience to Global Reputation. 1 Nguyen Truong PhD student, Liverpool John Moores University
 Trust in the Internet of Things From Personal Experience to Global Reputation 1 Nguyen Truong PhD student, Liverpool John Moores University 2 Outline I. Background on Trust in Computer Science II. Overview
Trust in the Internet of Things From Personal Experience to Global Reputation 1 Nguyen Truong PhD student, Liverpool John Moores University 2 Outline I. Background on Trust in Computer Science II. Overview
CS6375: Machine Learning Gautam Kunapuli. Mid-Term Review
 Gautam Kunapuli Machine Learning Data is identically and independently distributed Goal is to learn a function that maps to Data is generated using an unknown function Learn a hypothesis that minimizes
Gautam Kunapuli Machine Learning Data is identically and independently distributed Goal is to learn a function that maps to Data is generated using an unknown function Learn a hypothesis that minimizes
Program to an Interface, Not an Implementation
 Program to an Interface, Not an Implementation Early in the WeatherStation constructor: Barometer bar = new Barometer() ; Why is this problematic: WeatherStation depends on a specific implementation of
Program to an Interface, Not an Implementation Early in the WeatherStation constructor: Barometer bar = new Barometer() ; Why is this problematic: WeatherStation depends on a specific implementation of
Jeff King, Jennifer Stoll, Michael T. Hunter, Mustaque Ahamad. Georgia Tech Information Security Center (GTISC) WICOW '08
 ALPACA: A Lightweight Platform for Analyzing Claim Acceptability Jeff King, Jennifer Stoll, Michael T. Hunter, Mustaque Ahamad Georgia Tech Information Security Center (GTISC) WICOW '08 Motivation There
ALPACA: A Lightweight Platform for Analyzing Claim Acceptability Jeff King, Jennifer Stoll, Michael T. Hunter, Mustaque Ahamad Georgia Tech Information Security Center (GTISC) WICOW '08 Motivation There
Wales Council for Voluntary Action Supporting charities, volunteers and communities
 Wales Council for Voluntary Action Supporting charities, volunteers and communities 10. Promotion and marketing 10.7 Website development and maintenance How to get noticed Your potential audience should
Wales Council for Voluntary Action Supporting charities, volunteers and communities 10. Promotion and marketing 10.7 Website development and maintenance How to get noticed Your potential audience should
Structured Prediction Basics
 CS11-747 Neural Networks for NLP Structured Prediction Basics Graham Neubig Site https://phontron.com/class/nn4nlp2017/ A Prediction Problem I hate this movie I love this movie very good good neutral bad
CS11-747 Neural Networks for NLP Structured Prediction Basics Graham Neubig Site https://phontron.com/class/nn4nlp2017/ A Prediction Problem I hate this movie I love this movie very good good neutral bad
Slides 11: Verification and Validation Models
 Slides 11: Verification and Validation Models Purpose and Overview The goal of the validation process is: To produce a model that represents true behaviour closely enough for decision making purposes.
Slides 11: Verification and Validation Models Purpose and Overview The goal of the validation process is: To produce a model that represents true behaviour closely enough for decision making purposes.
A Letting agency s shop window is no longer a place on the high street, it is now online
 A Letting agency s shop window is no longer a place on the high street, it is now online 1 Let s start by breaking down the two ways in which search engines will send you more traffic: 1. Search Engine
A Letting agency s shop window is no longer a place on the high street, it is now online 1 Let s start by breaking down the two ways in which search engines will send you more traffic: 1. Search Engine
Learning Ontology-Based User Profiles: A Semantic Approach to Personalized Web Search
 1 / 33 Learning Ontology-Based User Profiles: A Semantic Approach to Personalized Web Search Bernd Wittefeld Supervisor Markus Löckelt 20. July 2012 2 / 33 Teaser - Google Web History http://www.google.com/history
1 / 33 Learning Ontology-Based User Profiles: A Semantic Approach to Personalized Web Search Bernd Wittefeld Supervisor Markus Löckelt 20. July 2012 2 / 33 Teaser - Google Web History http://www.google.com/history
/ Cloud Computing. Recitation 7 October 10, 2017
 15-319 / 15-619 Cloud Computing Recitation 7 October 10, 2017 Overview Last week s reflection Project 3.1 OLI Unit 3 - Module 10, 11, 12 Quiz 5 This week s schedule OLI Unit 3 - Module 13 Quiz 6 Project
15-319 / 15-619 Cloud Computing Recitation 7 October 10, 2017 Overview Last week s reflection Project 3.1 OLI Unit 3 - Module 10, 11, 12 Quiz 5 This week s schedule OLI Unit 3 - Module 13 Quiz 6 Project
Web & Automotive. Paris, April Dave Raggett
 Web & Automotive Paris, April 2012 Dave Raggett 1 Aims To discuss potential for Web Apps in cars Identify what kinds of Web standards are needed Discuss plans for W3C Web & Automotive Workshop
Web & Automotive Paris, April 2012 Dave Raggett 1 Aims To discuss potential for Web Apps in cars Identify what kinds of Web standards are needed Discuss plans for W3C Web & Automotive Workshop
