Fraude dans la Telephonie
|
|
|
- Sharon Holmes
- 6 years ago
- Views:
Transcription
1 Fraude dans la Telephonie Aurélien Francillon Merve Sahin With Monaco Telecom Also with cooperations: NYU Abu Dhabi Georgia Tech Telecom Paris Tech (Marc Relieu)
2 Telephony Fraud A long-standing problem (1870s 2010s) Early fraud mechanisms: aiming to make free calls Today: Convergence of multiple technologies Multiple actors involved Operators, VoIP providers, 3 rd party services, enterprises Touching over 7 billion people Massive volume of traffic 2
3 Telephony fraud: Some examples Small charges on your phone bill Stolen phone or SIM card Unknown international caller IDs Unwanted calls and voic s 3
4 Consequences of Telephony Fraud In 2015, estimated financial loss for operators was $38.1 billion* [*] CFCA Global Fraud Loss Survey, In the US, 400K+ spam call complaints (monthly) - In France, 574K complaints last year Effects on online security Technical support scams Telemarketing calls recording sensitive information Attacks on critical infrastructure (e.g., TDoS* on emergency lines) [*] Guri et al., DDoS: Attacks, Analysis and Mitigation, EuroS&P'17 [*] D. Cameron, Major leak exposes 400K recorded telemarketing calls, thousands of credit card numbers,
5 Problems with Telephony Fraud Multi-dimensional problem Technologies, regulations, law, historical background Multiple fraudulent actors Various skills and motivations Confusing terminology Telephony fraud and vulnerabilities are not well understood Different terms for the same problem Same term for different problems Limited public documentation, not comprehensive Without a good understanding, we cannot effectively fight fraud! 5
6 Some of your work, so far A taxonomy for telephony fraud [IEEE EuroS&P 17] Holistic view, clear terminology, a publicly available guide Detailed study of 3 fraud schemes Over-The-Top (OTT) bypass fraud [ACM CCS 16] Position it in the taxonomy Evaluate existing solutions Measure its effects with a case study International Revenue Share Fraud (coming soon...) Understand why it is difficult to address Understand the drawbacks of existing solutions Propose a way to improve detection Voice spam [Usenix SOUPS 17] Analyze a new defense approach 6
7 Example: Callback Scam 7
8 Example: Callback Scam 8
9 Example: Callback Scam 9
10 Example: Callback Scam Fraud Schemes Callback scam 10
11 Example: Callback Scam Fraud Schemes Callback scam Lead to Fraud Benefits Get a share from call revenue 11
12 Example: Callback Scam Techniques Caller ID spoofing, Auto-dialers, Social engineering Enable Fraud Schemes Callback scam Lead to Fraud Benefits Get a share from call revenue 12
13 Example: Callback Scam Weaknesses Lack of Caller ID authentication, Lack of security & fraud awareness Manipulated by Techniques Caller ID spoofing, Auto-dialers, Social engineering Enable Fraud Schemes Callback scam Lead to Fraud Benefits Get a share from call revenue 13
14 Example: Callback Scam Root Causes Result in Weaknesses Legacy/Insecure protocols, Interconnection of poorly understood technologies Lack of Caller ID authentication, Lack of security & fraud awareness Manipulated by Techniques Caller ID spoofing, Auto-dialers, Social engineering Enable Fraud Schemes Callback scam Lead to Fraud Benefits Get a share from call revenue 14
15 A definition Root Causes Result in Weaknesses Techniques Manipulated by Enable Fraud Schemes Lead to A fraud scheme is a way to obtain an illegitimate benefit using a technique. Such techniques are possible because of weaknesses in the system, which are themselves due to root causes. Fraud Benefits 15
16 Our taxonomy 16
17 Our taxonomy 17
18 Interconnect Bypass Fraud 18
19 Interconnect Bypass Frauds Bypassing International call termination fees Not going through normal routes Calls routed on VoIP Multiple well known schemes: SIM Boxes (VOIP-GSM gateways) used with stolen sim cards Compromised (IP-)PBX SIM Box with many sim cards (sim card server) OTT-Bypass: More recent, uses Smartphones voice chat applications* Cooperation with transit operators IP-PBX, voice communication server over IP * Sorry! Our lawyer does not want us to disclose which app 19
20 Regular International Call keeps 0.05$ keeps 0.05$ 20
21 OTT Bypass Call OTT Network(IP) keeps 0.05$ keeps 0.05$
22 OTT Bypass Call 0.15$ OTT Network(IP) keeps 0.05$ keeps 0.05$ 0.15$ 0.00$
23 Detecting and Measuring OTT Bypass: Challenges
24 Detecting and Measuring OTT Bypass: Challenges Outgoing bypass: No visibility on complete call route
25 Detecting and Measuring OTT Bypass: Challenges Incoming bypass: No visibility on bypassed call logs
26 Case Study: Measuring OTT bypass - on a Small European Country - with a custom TCG* platform [*]TCG: Test Call Generation 26
27 Case Study: Measuring OTT bypass - on a Small European Country - with a custom TCG* platform [*]TCG: Test Call Generation Spain Turkey United Kingdom Italy Netherlands Germany Austria Switzerland Experiment Setup Customized Android phones 4 SIM cards from victim operator Recipient phones roaming in France Calls originating from 8 countries (1 operator per country) Centralized collection of call logs test calls over 4 months France 27
28 Overall bypass OTT Network (IP) Spain 83% Turkey 72% United Kingdom 61% Italy 56% Netherlands 53% Germany 42% Austria Switzerland Results Up to 83% of calls were subjected to bypass in 6 of 8 countries OTT bypass leads to quality problems in call establishment Multiple fraud schemes may collide France 28
29 Example: Simbox and OTT Bypass UK caller ID: Mobile termination 29
30 Example: Simbox and OTT Bypass UK caller ID: Mobile - 16% Simbox bypass (over Russian mobile numbers) termination Recipient phone is online on OTT 30
31 Example: Simbox and OTT Bypass OTT Network (IP) UK caller ID: OTT - 16% Simbox bypass (over termination Russian mobile numbers) - 36% OTT bypass Recipient phone is online on OTT 31
32 Example: Simbox and OTT Bypass OTT Network (IP) UK caller ID: OTT - 16% Simbox bypass (over Russian mobile numbers) - 36% OTT bypass - 25% Simbox + OTT bypass termination ~80% fraudulent call termination Recipient phone is online on OTT 32
33 Conclusions Telephony fraud is likely to remain as a significant problem Several weaknesses (in protocols, regulations ) that are difficult to fix New technologies will bring new vulnerabilities Fraudsters are smart and have strong incentives Fighting fraud is costly? (fraud loss > cost of detection/prevention) We need industry cooperation... and data!
34 References Merve Sahin, Aurélien Francillon, Payas Gupta, Mustaque Ahamad, SoK: Fraud in Telephony Networks IEEE European Symposium on Security and Privacy (EuroS&P'17), 2017, Paris, France Merve Sahin, Aurélien Francillon, Over-The-Top Bypass: Study of a Recent Telephony Fraud ACM conference on Computer and communications security (CCS), 2016, Vienna, Austria Merve Sahin, Marc Relieu, Aurélien Francillon Using chatbots against voice spam: Analyzing Lenny's effectiveness Usenix Symposium on Usable Privacy and Security (SOUPS), 2017 emarketer. Digital content and advertising key revenue generators for messaging apps. emarketer, November New threat to mobile network operator revenues. Revector Company Blog, February B. Reaves, E. Shernan, A. Bates, H. Carter, and P. Traynor. Boxed out: Blocking cellular interconnect bypass fraud at the network edge. In USENIX Security, Vijay A. Balasubramaniyan, Aamir Poonawalla, Mustaque Ahamad, Michael T. Hunter, and Patrick Traynor PinDr0p: using single-ended audio features to determine call provenance. ACM CCS. Miramirkhani et al., Dial One for Scam: A Large-Scale Analysis of Technical Support Scams, NDSS'17. Guri et al., DDoS: Attacks, Analysis and Mitigation, EuroS&P'17. D. Cameron, Major leak exposes 400K recorded telemarketing calls, thousands of credit card numbers, Available at L. Notenboom, I got a call from Microsoft and allowed them access to my computer. What do I do now?, Available at 34
Telephony Fraud and Abuse. Merve Sahin
 Telephony Fraud and Abuse Merve Sahin sahin@eurecom.fr Background 2 Telephony Networks Quick history 1870s: Plain Old Telephone System (POTS) Enabled by transmission of voice over copper lines Used in-band
Telephony Fraud and Abuse Merve Sahin sahin@eurecom.fr Background 2 Telephony Networks Quick history 1870s: Plain Old Telephone System (POTS) Enabled by transmission of voice over copper lines Used in-band
Over-The-Top Bypass: Study of a Recent Telephony Fraud
 Over-The-Top Bypass: Study of a Recent Telephony Fraud Merve Sahin Eurecom & Monaco Digital Security Agency merve.sahin@eurecom.fr Aurélien Francillon Eurecom aurelien.francillon@eurecom.fr ABSTRACT In
Over-The-Top Bypass: Study of a Recent Telephony Fraud Merve Sahin Eurecom & Monaco Digital Security Agency merve.sahin@eurecom.fr Aurélien Francillon Eurecom aurelien.francillon@eurecom.fr ABSTRACT In
Understanding Cyber Attacks That Leverage the Telephony Channel
 SESSION ID: CCT-R04 Understanding Cyber Attacks That Leverage the Telephony Channel Payas Gupta Research Scientist CRISSP-AD, New York University Abu Dhabi payasgupta@nyu.edu In collaboration with Mustaque
SESSION ID: CCT-R04 Understanding Cyber Attacks That Leverage the Telephony Channel Payas Gupta Research Scientist CRISSP-AD, New York University Abu Dhabi payasgupta@nyu.edu In collaboration with Mustaque
Mobile Telephony Threats in Asia
 Mobile Telephony Threats in Asia Black Hat Asia 2017, Singapore Dr. Marco Balduzzi Dr. Payas Gupta Lion Gu Sr. Threat Researcher Data Scientist Sr. Threat Researcher Trend Micro Pindrop Trend Micro Joint
Mobile Telephony Threats in Asia Black Hat Asia 2017, Singapore Dr. Marco Balduzzi Dr. Payas Gupta Lion Gu Sr. Threat Researcher Data Scientist Sr. Threat Researcher Trend Micro Pindrop Trend Micro Joint
We will divide the many telecom fraud schemes into three broad categories, based on who the fraudsters are targeting. These categories are:
 Introduction to Telecom Fraud This guide will help you learn about the different types of telecom fraud and industry best practices for detection and prevention. Three Major Categories of Telecom Fraud
Introduction to Telecom Fraud This guide will help you learn about the different types of telecom fraud and industry best practices for detection and prevention. Three Major Categories of Telecom Fraud
Mobile Identity. for SmartVoice. User Guide
 Mobile Identity for SmartVoice User Guide Contact Customer Care at 877-487-8722 for additional assistance. 3/23/2017 1 OVERVIEW Mobile Identity is a simple smartphone client that enables an end-user to
Mobile Identity for SmartVoice User Guide Contact Customer Care at 877-487-8722 for additional assistance. 3/23/2017 1 OVERVIEW Mobile Identity is a simple smartphone client that enables an end-user to
Nuno Pestana, WeDo Technologies
 Nuno Pestana, WeDo Technologies SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud FRAUD THE IMPACT
Nuno Pestana, WeDo Technologies SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud FRAUD THE IMPACT
E N H A N C E D F R A U D D E T E C T I O N U S I N G S I G N A L I N G. W U G M a l a y s i a
 E N H A N C E D F R A U D D E T E C T I O N U S I N G S I G N A L I N G W U G M a l a y s i a 2 0 1 7 CONTACTS NUNO PESTANA FRAUD PROFESSIONAL SERVICES MANAGER +351 939 651 481 nuno.pestana@wedotechnol
E N H A N C E D F R A U D D E T E C T I O N U S I N G S I G N A L I N G W U G M a l a y s i a 2 0 1 7 CONTACTS NUNO PESTANA FRAUD PROFESSIONAL SERVICES MANAGER +351 939 651 481 nuno.pestana@wedotechnol
@First Anti Fraud Interconnect Roaming & Security of Transactions
 @First Anti Fraud Interconnect Roaming & Security of Transactions Pierre Paufique, Vice President Customer Service Operations & Fraud, Cost and Revenue Assurance, International Carriers, Orange agenda
@First Anti Fraud Interconnect Roaming & Security of Transactions Pierre Paufique, Vice President Customer Service Operations & Fraud, Cost and Revenue Assurance, International Carriers, Orange agenda
Mavenir Spam and Fraud Control
 SOLUTION BRIEF Assuring Operator Revenue and A2P Grey Route Monetization Operators are realizing the scale and potential of A2P (Application to Person) messaging revenues, and how advances in messaging
SOLUTION BRIEF Assuring Operator Revenue and A2P Grey Route Monetization Operators are realizing the scale and potential of A2P (Application to Person) messaging revenues, and how advances in messaging
The Spoofing/Authentication Threat
 The Spoofing/Authentication Threat An Analysis of the Spoofing/Authentication Threat in Voice Network Security A Whitepaper From SecureLogix Corporation Introduction Spoofing refers to the act of intentionally
The Spoofing/Authentication Threat An Analysis of the Spoofing/Authentication Threat in Voice Network Security A Whitepaper From SecureLogix Corporation Introduction Spoofing refers to the act of intentionally
COMMUNICATION SERVICES IN WESTERN EUROPE: TRENDS AND FORECASTS
 RESEARCH FORECAST REPORT COMMUNICATION SERVICES IN WESTERN EUROPE: TRENDS AND FORECASTS 2016 2021 STEPHEN SALE and MICHAEL LANE analysysmason.com About this report This report provides an outlook on the
RESEARCH FORECAST REPORT COMMUNICATION SERVICES IN WESTERN EUROPE: TRENDS AND FORECASTS 2016 2021 STEPHEN SALE and MICHAEL LANE analysysmason.com About this report This report provides an outlook on the
Paper on Handling Menace of International Grey Traffic
 Paper on Handling Menace of International Grey Traffic White Paper 01 of 2012 PiRRC In this paper discussion is only about the conventional international voice telephony requiring a license to bring in
Paper on Handling Menace of International Grey Traffic White Paper 01 of 2012 PiRRC In this paper discussion is only about the conventional international voice telephony requiring a license to bring in
The unbundling of international roaming
 The unbundling of international roaming There have been times that automatic international roaming did not exist. Already in the 1980 s some early type of a roaming service was available. The caller needed
The unbundling of international roaming There have been times that automatic international roaming did not exist. Already in the 1980 s some early type of a roaming service was available. The caller needed
TRUECALLER INSIGHTS SPECIAL REPORT: THE TOP 20 COUNTRIES AFFECTED BY SPAM CALLS
 TRUECALLER INSIGHTS TRUECALLER INSIGHTS SPECIAL REPORT: THE TOP 20 COUNTRIES AFFECTED BY SPAM CALLS 2017-07-13 LINDSEY LAMONT Isn t it the best feeling when Truecaller blocks a spam call or SMS? It s like
TRUECALLER INSIGHTS TRUECALLER INSIGHTS SPECIAL REPORT: THE TOP 20 COUNTRIES AFFECTED BY SPAM CALLS 2017-07-13 LINDSEY LAMONT Isn t it the best feeling when Truecaller blocks a spam call or SMS? It s like
Using your phone abroad. Enjoy happier travels with our quick roaming guide.
 Using your phone abroad Enjoy happier travels with our quick roaming guide. Hello sunshine How to use your phone abroad Whether it s a city break, a ski adventure or a week on the beach, we think you should
Using your phone abroad Enjoy happier travels with our quick roaming guide. Hello sunshine How to use your phone abroad Whether it s a city break, a ski adventure or a week on the beach, we think you should
Reducing Telecoms Fraud Losses
 Reducing Telecoms Fraud Losses A Telsis White Paper Intelligence for Your Network Introduction According to the Communication Fraud Control Association (CFCA), fraud costs the telecoms industry 1.69% of
Reducing Telecoms Fraud Losses A Telsis White Paper Intelligence for Your Network Introduction According to the Communication Fraud Control Association (CFCA), fraud costs the telecoms industry 1.69% of
Modern IP Communication bears risks
 Modern IP Communication bears risks How to protect your business telephony from cyber attacks Voice-over-IP (VoIP) provides many new features over PSTN. However, the interconnection with your IT infrastructure
Modern IP Communication bears risks How to protect your business telephony from cyber attacks Voice-over-IP (VoIP) provides many new features over PSTN. However, the interconnection with your IT infrastructure
AuthentiCall: Efficient Identity and Content Authentication for
 AuthentiCall: Efficient Identity and Content Authentication for Brad Reaves, Logan Blue, Hadi Abdullah, Luis Vargas, Patrick Traynor, and Tom Shrimpton North Carolina State University University of Florida
AuthentiCall: Efficient Identity and Content Authentication for Brad Reaves, Logan Blue, Hadi Abdullah, Luis Vargas, Patrick Traynor, and Tom Shrimpton North Carolina State University University of Florida
Course Outline Comprehensive Training on Bypass/SIM Box Fraud Detection and Termination Duration: 3 Days
 Course Outline Comprehensive Training on Bypass/SIM Box Fraud Detection and Termination Duration: 3 Days Title: Comprehensive Training on Bypass/SIM Box Fraud: Detection and Termination Duration: 3 day
Course Outline Comprehensive Training on Bypass/SIM Box Fraud Detection and Termination Duration: 3 Days Title: Comprehensive Training on Bypass/SIM Box Fraud: Detection and Termination Duration: 3 day
Analysis and Detection of Fraud in International Calls Using Decision Tree
 Analysis and Detection of Fraud in International Calls Using Decision Tree Ahmed Aljarray and Abdulla Abouda Almadar Aljadid R&D Office, Libya-Misrata Abstract. fraud is one of the most severe threats
Analysis and Detection of Fraud in International Calls Using Decision Tree Ahmed Aljarray and Abdulla Abouda Almadar Aljadid R&D Office, Libya-Misrata Abstract. fraud is one of the most severe threats
Orange Smart Cities. Smart Metering and Smart Grid : how can a telecom operator contribute? November
 Orange Smart Cities Smart Metering and Smart Grid : how can a telecom operator contribute? November 5 2012 Nathalie Leboucher Vice President Smart Cities Program Orange 1 the Orange Group in a nutshell
Orange Smart Cities Smart Metering and Smart Grid : how can a telecom operator contribute? November 5 2012 Nathalie Leboucher Vice President Smart Cities Program Orange 1 the Orange Group in a nutshell
3E. Sprint Worldwide Wireless Service
 3E. Sprint Worldwide Wireless Service Your SIM Card (page 187) Using Your Device While Traveling (page 189) Retrieving Voicemail Messages (page 192) International Data Roaming (page 193) Using Your SIM
3E. Sprint Worldwide Wireless Service Your SIM Card (page 187) Using Your Device While Traveling (page 189) Retrieving Voicemail Messages (page 192) International Data Roaming (page 193) Using Your SIM
Accelerating growth and digital adoption with seamless identity trust
 Accelerating growth and digital adoption with seamless identity trust IBM Trusteer helps organizations seamlessly establish identity trust across the omnichannel customer journey Let s get started 3 Introduction
Accelerating growth and digital adoption with seamless identity trust IBM Trusteer helps organizations seamlessly establish identity trust across the omnichannel customer journey Let s get started 3 Introduction
SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT
 DATASHEET SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT Silver level EMM Enterprise Mobility Management for Corporate-owned and BYOD devices BlackBerry Enterprise Service 10 is a powerful device,
DATASHEET SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT Silver level EMM Enterprise Mobility Management for Corporate-owned and BYOD devices BlackBerry Enterprise Service 10 is a powerful device,
Security+ Guide to Network Security Fundamentals, Fourth Edition. Chapter 1 Introduction to Security
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 1 Introduction to Security Objectives Describe the challenges of securing information Define information security and explain why
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 1 Introduction to Security Objectives Describe the challenges of securing information Define information security and explain why
Mavenir Keynote. Think Smarter Secure communication Innovate Services. By Mohamed Issa Regional Head of Africa Sales
 Mavenir Keynote Think Smarter Secure communication Innovate Services By Mohamed Issa Regional Head of Africa Sales The New Mavenir: Combining Market Leaders Combing three industry-leading companies to
Mavenir Keynote Think Smarter Secure communication Innovate Services By Mohamed Issa Regional Head of Africa Sales The New Mavenir: Combining Market Leaders Combing three industry-leading companies to
CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE
 CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE The Customer: Top 10 Airline CREDENTIAL STUFFING KILLCHAIN A Top 10 Global Airline that earns over $15 Billion in annual revenue and serves
CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE The Customer: Top 10 Airline CREDENTIAL STUFFING KILLCHAIN A Top 10 Global Airline that earns over $15 Billion in annual revenue and serves
Carrier Services. Intelligent telephony. for over COUNTRIES DID NUMBERS. All IP
 Carrier Services All IP Intelligent telephony In current times, being connected to the telephone network just isn t enough anymore; one needs to be INTERconnected with it, as it all has become IP. Along
Carrier Services All IP Intelligent telephony In current times, being connected to the telephone network just isn t enough anymore; one needs to be INTERconnected with it, as it all has become IP. Along
YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report
 YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report Fake Accounts and the Black Market There s a thriving black market for fake accounts on the internet. Fake accounts are accounts
YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report Fake Accounts and the Black Market There s a thriving black market for fake accounts on the internet. Fake accounts are accounts
Country Large Bundle Minutes Small Bundle Minutes Total Monthly Minutes United Kingdom 1, ,140
 1. What is ACN Globe Call? ACN Globe Call is a new tariff plan for the ACN Digital Phone Service (DPS) proposition. Customers now have a choice of selecting either ACN Globe Call or ACN Smart, depending
1. What is ACN Globe Call? ACN Globe Call is a new tariff plan for the ACN Digital Phone Service (DPS) proposition. Customers now have a choice of selecting either ACN Globe Call or ACN Smart, depending
Cybersecurity for Service Providers
 Cybersecurity for Service Providers Alexandro Fernandez, CISSP, CISA, CISM, CEH, ECSA, ISO 27001LA, ISO 27001 LI, ITILv3, COBIT5 Security Advanced Services February 2018 There are two types of companies:
Cybersecurity for Service Providers Alexandro Fernandez, CISSP, CISA, CISM, CEH, ECSA, ISO 27001LA, ISO 27001 LI, ITILv3, COBIT5 Security Advanced Services February 2018 There are two types of companies:
VIP TRAVELLER CHECK LIST & USER GUIDE
 VIP TRAVELLER CHECK LIST & USER GUIDE DISVENT GlobalSIM the Digital Swiss Knife 3G MOBILE BROADBAND & WIFI HOTSPOTS AROUND THE WORLD VOICE & DATA MOBILE DUAL NUMBER SIM CARD Your freedom and privacy around
VIP TRAVELLER CHECK LIST & USER GUIDE DISVENT GlobalSIM the Digital Swiss Knife 3G MOBILE BROADBAND & WIFI HOTSPOTS AROUND THE WORLD VOICE & DATA MOBILE DUAL NUMBER SIM CARD Your freedom and privacy around
MVNO Solution for Highly Profitable Global Roaming Services
 TeliSIM: MVNO Solution for Highly Profitable Global Roaming Services MVNO Solution for Highly Profitable Global Roaming Services A Guide to Help You Provide Highly Profitable Mobile Voice, Data and SMS
TeliSIM: MVNO Solution for Highly Profitable Global Roaming Services MVNO Solution for Highly Profitable Global Roaming Services A Guide to Help You Provide Highly Profitable Mobile Voice, Data and SMS
Express Monitoring 2019
 Express Monitoring 2019 WHY CHOOSE PT EXPRESS MONITORING PT Express Monitoring provides a quick evaluation of the current signaling network protection level. This service helps to discover critical vulnerabilities
Express Monitoring 2019 WHY CHOOSE PT EXPRESS MONITORING PT Express Monitoring provides a quick evaluation of the current signaling network protection level. This service helps to discover critical vulnerabilities
Dialogic PowerVille CC Cloud Centrex
 Dialogic PowerVille CC Cloud Centrex Cloud-based Feature-rich Integrated VoIP Solution for Business and Residential Customers Dialogic s PowerVille Cloud Centrex is a carrier-class solution that enables
Dialogic PowerVille CC Cloud Centrex Cloud-based Feature-rich Integrated VoIP Solution for Business and Residential Customers Dialogic s PowerVille Cloud Centrex is a carrier-class solution that enables
Digital Agenda Scoreboard 2017 Electronic communications market indicators: Definitions, methodology and footnotes on Member State data
 Digital Agenda Scoreboard 2017 Electronic communications market indicators: Definitions, methodology and footnotes on Member State data Financial indicators, fixed and mobile telephony, broadcasting and
Digital Agenda Scoreboard 2017 Electronic communications market indicators: Definitions, methodology and footnotes on Member State data Financial indicators, fixed and mobile telephony, broadcasting and
Dialogic Cloud Centrex
 Dialogic Cloud Centrex Cloud-based, feature-rich integrated VoIP solution for business and residential customers Dialogic Cloud Centrex is a carrier-class solution that enables service providers to offer
Dialogic Cloud Centrex Cloud-based, feature-rich integrated VoIP solution for business and residential customers Dialogic Cloud Centrex is a carrier-class solution that enables service providers to offer
Cloud PBX: Real world scenarios
 Cloud PBX: Real world scenarios Ralph Eckhard Ralph Eckhard IT Architect @ PeopleWare ICT Modern Workplace / M365 www.365dude.nl @ralpje Elements of Skype for Business Online Skype for Business (E1,E3,E5)
Cloud PBX: Real world scenarios Ralph Eckhard Ralph Eckhard IT Architect @ PeopleWare ICT Modern Workplace / M365 www.365dude.nl @ralpje Elements of Skype for Business Online Skype for Business (E1,E3,E5)
Interconnection and Roaming
 Interconnection and Roaming Operator Business Slide 1 Importance of Interconnection Operator s perspective Connectivity =>Network effect => Customer satisfaction =>Revenue Slide 2 Types of interconnections
Interconnection and Roaming Operator Business Slide 1 Importance of Interconnection Operator s perspective Connectivity =>Network effect => Customer satisfaction =>Revenue Slide 2 Types of interconnections
Fraud Detection in International Calls Using Fuzzy Logic
 Fraud Detection in International Calls Using Fuzzy Logic Osama Mohamed Elrajubi, Hussein Marah, Abdulla A. Abouda Abstract Telecommunications fraud is a problem that affects operators and telecommunication
Fraud Detection in International Calls Using Fuzzy Logic Osama Mohamed Elrajubi, Hussein Marah, Abdulla A. Abouda Abstract Telecommunications fraud is a problem that affects operators and telecommunication
Security in India: Enabling a New Connected Era
 White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
Fraud Detection in International Calls Using Fuzzy Logic
 Fraud Detection in International Calls Using Fuzzy Logic Hussein M. Marah Faculty of Information Technology Misurata University Misurata, Libya Osama Mohamed Elrajubi Faculty of Information Technology
Fraud Detection in International Calls Using Fuzzy Logic Hussein M. Marah Faculty of Information Technology Misurata University Misurata, Libya Osama Mohamed Elrajubi Faculty of Information Technology
PBX Fraud Information
 PBX Fraud Information Increasingly, hackers are gaining access to corporate phone and/or voice mail systems. These individuals place long distance and international calls through major telecom networks
PBX Fraud Information Increasingly, hackers are gaining access to corporate phone and/or voice mail systems. These individuals place long distance and international calls through major telecom networks
Security for SIP-based VoIP Communications Solutions
 Tomorrow Starts Today Security for SIP-based VoIP Communications Solutions Enterprises and small to medium-sized businesses (SMBs) are exposed to potentially debilitating cyber attacks and exploitation
Tomorrow Starts Today Security for SIP-based VoIP Communications Solutions Enterprises and small to medium-sized businesses (SMBs) are exposed to potentially debilitating cyber attacks and exploitation
Achieving End-to-End Security in the Internet of Things (IoT)
 Achieving End-to-End Security in the Internet of Things (IoT) Optimize Your IoT Services with Carrier-Grade Cellular IoT June 2016 Achieving End-to-End Security in the Internet of Things (IoT) Table of
Achieving End-to-End Security in the Internet of Things (IoT) Optimize Your IoT Services with Carrier-Grade Cellular IoT June 2016 Achieving End-to-End Security in the Internet of Things (IoT) Table of
NovaTec The Success Stories
 Copyright 2008 NovaTec Kommunikationstechnik GmbH NovaTec The Success Stories NovaTec Kommunikationstechnik GmbH welcomes You to this presentation Contents of this presentation 1. Overview 1.1 Our Vision
Copyright 2008 NovaTec Kommunikationstechnik GmbH NovaTec The Success Stories NovaTec Kommunikationstechnik GmbH welcomes You to this presentation Contents of this presentation 1. Overview 1.1 Our Vision
VDSL The way to Next Generation Access Networks
 WIK Conference VDSL The way to Next Generation Access Networks Patrick Dehmer, Swisscom Fixnet Ltd. Swiss Regulatory framework Telecom Act 1997 aims at lean regulation of former monopoly SUSTAINABLE COMPETITION
WIK Conference VDSL The way to Next Generation Access Networks Patrick Dehmer, Swisscom Fixnet Ltd. Swiss Regulatory framework Telecom Act 1997 aims at lean regulation of former monopoly SUSTAINABLE COMPETITION
BRIDGE TO GLOBAL MARKET FOR MVNOs. Local prices on mobile data around the world Global Mobile Data Exchange Gate to millions of underserved customers
 1 BRIDGE TO GLOBAL MARKET FOR MVNOs Local prices on mobile data around the world Global Mobile Data Exchange Gate to millions of underserved customers How to compete with big MNOs on equal terms 2 Your
1 BRIDGE TO GLOBAL MARKET FOR MVNOs Local prices on mobile data around the world Global Mobile Data Exchange Gate to millions of underserved customers How to compete with big MNOs on equal terms 2 Your
MONETIZING DATA ROAMING WITH ALEPO
 INTRODUCTION With international travel on a rise globally, mobile data subscribers are increasingly seeking out convenient and affordable ways to stay connected with family, colleagues, and travel hosts
INTRODUCTION With international travel on a rise globally, mobile data subscribers are increasingly seeking out convenient and affordable ways to stay connected with family, colleagues, and travel hosts
An Introduction to the Max PVN
 An Introduction to the Max PVN Net2Phone Overview 2 VoIP Leader Net2Phone is a leading provider of VoIP products and services throughout the world #1 worldwide for retail VoIP services Proven, scalable
An Introduction to the Max PVN Net2Phone Overview 2 VoIP Leader Net2Phone is a leading provider of VoIP products and services throughout the world #1 worldwide for retail VoIP services Proven, scalable
Notices. Third Party Project Usage. Sample Code in Documentation
 Malwarebytes for ios User Guide Version 1.2.2 12 December 2018 Notices Malwarebytes products and related documentation are provided under a license agreement containing restrictions on use and disclosure
Malwarebytes for ios User Guide Version 1.2.2 12 December 2018 Notices Malwarebytes products and related documentation are provided under a license agreement containing restrictions on use and disclosure
Mobile Security Fall 2013
 Mobile Security 14-829 Fall 2013 Patrick Tague Class #4 Telecom System Security General Vulnerabilities Service interruption vulnerabilities Due to increased capacity offered by high speed communication
Mobile Security 14-829 Fall 2013 Patrick Tague Class #4 Telecom System Security General Vulnerabilities Service interruption vulnerabilities Due to increased capacity offered by high speed communication
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
European Union Agency for Network and Information Security
 Critical Information Infrastructure Protection in the EU Evangelos Ouzounis Head of Secure Infrastructure and Services Regional Cybersecurity Forum Sofia, Bulgaria 29 th November 2016 European Union Agency
Critical Information Infrastructure Protection in the EU Evangelos Ouzounis Head of Secure Infrastructure and Services Regional Cybersecurity Forum Sofia, Bulgaria 29 th November 2016 European Union Agency
6 Significant reasons to embark and establish a mobile VoIP business
 6 Significant reasons to embark and establish a mobile VoIP business Whether you plan to enhance your current telecom infrastructure or start a completely new enterprise, enter the world of mobile VoIP
6 Significant reasons to embark and establish a mobile VoIP business Whether you plan to enhance your current telecom infrastructure or start a completely new enterprise, enter the world of mobile VoIP
BizVoice(Mobile ipn) User Guide Android
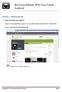 Chapter 1 : Getting Started 1. Client Download and Installation Step 1: Go to Google Play on your PC or your android device and search for < Mobile ipn >. Step 2: Download and install Mobile ipn. Note
Chapter 1 : Getting Started 1. Client Download and Installation Step 1: Go to Google Play on your PC or your android device and search for < Mobile ipn >. Step 2: Download and install Mobile ipn. Note
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Sprint International Calling Card Access Codes
 Sprint International Calling Card Access Codes Call 866-866-7509 to start service with Sprint. International support Sprint Prepaid questions & support: visit sprint.com/prepaidsupport or call 855-639-4644.
Sprint International Calling Card Access Codes Call 866-866-7509 to start service with Sprint. International support Sprint Prepaid questions & support: visit sprint.com/prepaidsupport or call 855-639-4644.
Mobile telephones/international roaming frequently asked questions (see also IP/05/161)
 MEMO/05/44 Brussels, 10 th February 2005 Mobile telephones/international roaming frequently asked questions (see also IP/05/161) What is international roaming? International roaming provides subscribers
MEMO/05/44 Brussels, 10 th February 2005 Mobile telephones/international roaming frequently asked questions (see also IP/05/161) What is international roaming? International roaming provides subscribers
ANNEX A.1 TECHNICAL SPECIFICATIONS OPEN CALL FOR TENDERS
 ANNEX A.1 TECHNICAL SPECIFICATIONS OPEN CALL FOR TENDERS Provision of Internet, Voice & Mobile Services FRA1-200 2008-2410 2410-T 01 Page 1 Table of Contents ANNEX A.1 TECHNICAL SPECIFICATIONS OPEN CALL
ANNEX A.1 TECHNICAL SPECIFICATIONS OPEN CALL FOR TENDERS Provision of Internet, Voice & Mobile Services FRA1-200 2008-2410 2410-T 01 Page 1 Table of Contents ANNEX A.1 TECHNICAL SPECIFICATIONS OPEN CALL
1 of 11 10/1/ :26 AM
 1 of 11 10/1/2010 12:26 AM About Us Careers Calculators Contact Us Search Home Your Money HQ ID Theft & Fraud FRAUD ALERT E-mail Scams ID Theft and Fraud Avoid Becoming a Victim What To Do If You Are a
1 of 11 10/1/2010 12:26 AM About Us Careers Calculators Contact Us Search Home Your Money HQ ID Theft & Fraud FRAUD ALERT E-mail Scams ID Theft and Fraud Avoid Becoming a Victim What To Do If You Are a
OTT Players. Challenges and Opportunities
 OTT Players Challenges and Opportunities Agenda 1. Introduction 2. Regulatory environment 3. Challenges The purpose of this roundtable is to initiate a discussion that would highlight key issues underlying
OTT Players Challenges and Opportunities Agenda 1. Introduction 2. Regulatory environment 3. Challenges The purpose of this roundtable is to initiate a discussion that would highlight key issues underlying
IMPORTANT SECURITY INFORMATION PHISHING
 IMPORTANT SECURITY INFORMATION PHISHING Protect Yourself and Your Accounts Important Security Information At Century Savings Bank, security and privacy of your financial information is a top priority.
IMPORTANT SECURITY INFORMATION PHISHING Protect Yourself and Your Accounts Important Security Information At Century Savings Bank, security and privacy of your financial information is a top priority.
Emerging Trends and Opportunities
 Emerging Trends and Opportunities Smart Homes & End User Engagement track_ TEF. Digital 06.11.2014 Emilio Martinez Head of Utilities & Building Energy Efficiency Telefonica M2M Global Unit 1 Wireless Connectivity
Emerging Trends and Opportunities Smart Homes & End User Engagement track_ TEF. Digital 06.11.2014 Emilio Martinez Head of Utilities & Building Energy Efficiency Telefonica M2M Global Unit 1 Wireless Connectivity
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Country Update Germany & Austria
 Country Update Germany & Austria Martin Thor Sales Unit Manager, Mobile Entertainment DIMOCO Carrier Billing Headquartered in Austria with offices in Germany, Hungary and Greece FinTech philosophy at its
Country Update Germany & Austria Martin Thor Sales Unit Manager, Mobile Entertainment DIMOCO Carrier Billing Headquartered in Austria with offices in Germany, Hungary and Greece FinTech philosophy at its
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Joining forces to fight botnets. Dan Tofan Head of the Technical Division CERT-RO 17/02/2014
 Joining forces to fight botnets Dan Tofan Head of the Technical Division CERT-RO 17/02/2014 Agenda Who are we? Benefits and collaboration opportunities ACDC European funded pilot project - 16 mil. Selected
Joining forces to fight botnets Dan Tofan Head of the Technical Division CERT-RO 17/02/2014 Agenda Who are we? Benefits and collaboration opportunities ACDC European funded pilot project - 16 mil. Selected
TERMS AND CONDITIONS FOR SIM ONLY PLANS ON EE 12 MONTH AND 30 DAY PLANS
 TERMS AND CONDITIONS FOR SIM ONLY PLANS ON EE 12 MONTH AND 30 DAY PLANS FROM 4 November 2016 Version 1.0 Date 04.11.16 To be eligible to join a SIM only plan on EE, you will need to pass our standard credit
TERMS AND CONDITIONS FOR SIM ONLY PLANS ON EE 12 MONTH AND 30 DAY PLANS FROM 4 November 2016 Version 1.0 Date 04.11.16 To be eligible to join a SIM only plan on EE, you will need to pass our standard credit
KASPERSKY ANTI-MALWARE PROTECTION SYSTEM BE READY FOR WHAT S NEXT. Kaspersky Open Space Security
 KASPERSKY ANTI-MALWARE PROTECTION SYSTEM BE READY FOR WHAT S NEXT Open Space Security Cyber-attacks are real. Today alone, Lab technology prevented nearly 3 million of them aimed at our customers worldwide.
KASPERSKY ANTI-MALWARE PROTECTION SYSTEM BE READY FOR WHAT S NEXT Open Space Security Cyber-attacks are real. Today alone, Lab technology prevented nearly 3 million of them aimed at our customers worldwide.
Robocall signaling draft-sipcore-callinfo-spam. Henning Schulzrinne IETF 98
 Robocall signaling draft-sipcore-callinfo-spam Henning Schulzrinne IETF 98 Background (for the un-stired and un-shaken) Unwanted calls are typically some are illegal, some are just unwanted (by many) example:
Robocall signaling draft-sipcore-callinfo-spam Henning Schulzrinne IETF 98 Background (for the un-stired and un-shaken) Unwanted calls are typically some are illegal, some are just unwanted (by many) example:
Hypermedia HG-4000/3U. VoIP GSM Gateway. Cost Saving Customer Premises Equipment with Carrier Grade Performance. Product Description January 2013
 Hypermedia HG-4000/3U VoIP GSM Gateway Cost Saving Customer Premises Equipment with Carrier Grade Performance Product Description January 2013 Contents Next Page Hypermedia HG-4000/3U 2 Contact Information
Hypermedia HG-4000/3U VoIP GSM Gateway Cost Saving Customer Premises Equipment with Carrier Grade Performance Product Description January 2013 Contents Next Page Hypermedia HG-4000/3U 2 Contact Information
Incubating ideas in R&D capabilities abroad
 Incubating ideas in R&D capabilities abroad European Commission - 21 October 2009 José Valerdi Tormo Head of Orange Labs R&D Spain Local markets develop break through innovations 2 inspired by innovative
Incubating ideas in R&D capabilities abroad European Commission - 21 October 2009 José Valerdi Tormo Head of Orange Labs R&D Spain Local markets develop break through innovations 2 inspired by innovative
Quad BRI GSM Gateway with 8 GSM Ports
 Quad BRI GSM Gateway with 8 GSM Ports HG-2000/3U Cost Saving Customer Premises Equipment with Carrier Grade Performance Product Description November 2009 Contents Next Page Hypermedia HG-2000/3U 3 Contents
Quad BRI GSM Gateway with 8 GSM Ports HG-2000/3U Cost Saving Customer Premises Equipment with Carrier Grade Performance Product Description November 2009 Contents Next Page Hypermedia HG-2000/3U 3 Contents
Vodafone Global FACTS
 Vodafone Global FACTS Stefanie Schmidt, Stefan Deckers July 2018 C1-Vodafone External C1-Vodafone External 2 Global FACTS Overview & Introduction Luxembourg Global Roamer Germany 23 Countries Overview
Vodafone Global FACTS Stefanie Schmidt, Stefan Deckers July 2018 C1-Vodafone External C1-Vodafone External 2 Global FACTS Overview & Introduction Luxembourg Global Roamer Germany 23 Countries Overview
Guillaume Le Mener Head of Marketing & Corporate Development Mavenir. Leonardo Hilario Planning & Project Manager Telefónica Hispanoamérica
 Guillaume Le Mener Head of Marketing & Corporate Development Mavenir Leonardo Hilario Planning & Project Manager Telefónica Hispanoamérica Securing New Revenue from Messaging Fraud Prevention Telefonica
Guillaume Le Mener Head of Marketing & Corporate Development Mavenir Leonardo Hilario Planning & Project Manager Telefónica Hispanoamérica Securing New Revenue from Messaging Fraud Prevention Telefonica
Protecting Smart Buildings
 Protecting Smart Buildings The next frontier of critical infrastructure security Suzanne Rijnbergen - MBA visibility detection control Who am I? Global Director Professional Services @SecurityMatters (ForeScout)
Protecting Smart Buildings The next frontier of critical infrastructure security Suzanne Rijnbergen - MBA visibility detection control Who am I? Global Director Professional Services @SecurityMatters (ForeScout)
NFON Whitepaper: Integrating Microsoft Lync (Skype for Business) with Telephony
 . Myths and facts - for enterprise owners, managers and buyers. Document Version: V1.0 Date: November 2015 NFON UK Ltd, 140 Wales Farm Road, London, W3 6UG, UK Page 1 of 7 1. INTRODUCTION While the business
. Myths and facts - for enterprise owners, managers and buyers. Document Version: V1.0 Date: November 2015 NFON UK Ltd, 140 Wales Farm Road, London, W3 6UG, UK Page 1 of 7 1. INTRODUCTION While the business
Trustwave SEG Cloud BEC Fraud Detection Basics
 .trust Trustwave SEG Cloud BEC Fraud Detection Basics Table of Contents About This Document 1 1 Background 2 2 Configuring Trustwave SEG Cloud for BEC Fraud Detection 5 2.1 Enable the Block Business Email
.trust Trustwave SEG Cloud BEC Fraud Detection Basics Table of Contents About This Document 1 1 Background 2 2 Configuring Trustwave SEG Cloud for BEC Fraud Detection 5 2.1 Enable the Block Business Email
The strategies for preventing telecom fraud in EACO countries
 The strategies for preventing telecom fraud in EACO countries 25 th May 2011 Protais KANYANKORE RWANDA UTILITIES REGULATORY AGENCY Table of contents 1. Overview on Grey traffic Affected areas Who is involved
The strategies for preventing telecom fraud in EACO countries 25 th May 2011 Protais KANYANKORE RWANDA UTILITIES REGULATORY AGENCY Table of contents 1. Overview on Grey traffic Affected areas Who is involved
Bringing Messaging Revenue Back to Operators Mavenir B2C Messaging Solution
 SOLUTION BRIEF B2C Messaging Solution Bringing Messaging Revenue Back to Operators Mavenir B2C Messaging Solution Consumer messaging (P2P) revenue is declining for operators, as subscribers expect free
SOLUTION BRIEF B2C Messaging Solution Bringing Messaging Revenue Back to Operators Mavenir B2C Messaging Solution Consumer messaging (P2P) revenue is declining for operators, as subscribers expect free
How DDoS Mitigation is about Corporate Social Responsibility
 How DDoS Mitigation is about Corporate Social Responsibility We see the Network, we monitor the Network and we can protect your business with automatic DDoS mitigation services from our Network core. Regardless
How DDoS Mitigation is about Corporate Social Responsibility We see the Network, we monitor the Network and we can protect your business with automatic DDoS mitigation services from our Network core. Regardless
Setera Office+ Installation and User Guide for Android devices
 Setera Office+ Installation and User Guide for Android devices Installation Welcome to use Setera Office+ Mobile! Installation of the mobile client is fast and easy. You can install Setera Office+ Android
Setera Office+ Installation and User Guide for Android devices Installation Welcome to use Setera Office+ Mobile! Installation of the mobile client is fast and easy. You can install Setera Office+ Android
January 14, Advanced Methods To Target and Eliminate Unlawful Robocalls, WC Docket No
 Amanda E. Potter AT&T Services, Inc. Assistant Vice President- 1120 20th Street, NW Senior Legal Counsel Suite 1000 Washington, DC 20036 Phone: 202.457.2103 E-mail: amanda.potter@att.com January 14, 2019
Amanda E. Potter AT&T Services, Inc. Assistant Vice President- 1120 20th Street, NW Senior Legal Counsel Suite 1000 Washington, DC 20036 Phone: 202.457.2103 E-mail: amanda.potter@att.com January 14, 2019
Ingate SIParator /Firewall SIP Security for the Enterprise
 Ingate SIParator /Firewall SIP Security for the Enterprise Ingate Systems Ingate Systems AB (publ) Tel: +46 8 600 77 50 BACKGROUND... 1 1 NETWORK SECURITY... 2 2 WHY IS VOIP SECURITY IMPORTANT?... 3 3
Ingate SIParator /Firewall SIP Security for the Enterprise Ingate Systems Ingate Systems AB (publ) Tel: +46 8 600 77 50 BACKGROUND... 1 1 NETWORK SECURITY... 2 2 WHY IS VOIP SECURITY IMPORTANT?... 3 3
HOW TO SELECT A SECURITY-BASED MESSAGING PARTNER. Six key features to consider when choosing a mission-critical messaging partner for your business.
 HOW TO SELECT A SECURITY-BASED MESSAGING PARTNER Six key features to consider when choosing a mission-critical messaging partner for your business. MESSAGING MEANS BUSINESS Text messaging (or SMS) is a
HOW TO SELECT A SECURITY-BASED MESSAGING PARTNER Six key features to consider when choosing a mission-critical messaging partner for your business. MESSAGING MEANS BUSINESS Text messaging (or SMS) is a
VoIP/SIP: Economy and Mobility
 Nowadays VoIP-services become more and more popular all over the world. VoIP stands for Voice Over Internet Protocol, a communications protocol that allows for telephonic communication via the Internet.
Nowadays VoIP-services become more and more popular all over the world. VoIP stands for Voice Over Internet Protocol, a communications protocol that allows for telephonic communication via the Internet.
Altitude Software. Data Protection Heading 2018
 Altitude Software Data Protection Heading 2018 How to prevent our Contact Centers from Data Leaks? Why is this a priority for Altitude? How does it affect the Contact Center environment? How does this
Altitude Software Data Protection Heading 2018 How to prevent our Contact Centers from Data Leaks? Why is this a priority for Altitude? How does it affect the Contact Center environment? How does this
WHITE PAPER Hybrid Approach to DDoS Mitigation
 WHITE PAPER Hybrid Approach to DDoS Mitigation FIRST LINE OF DEFENSE Executive Summary As organizations consider options for DDoS mitigation, it is important to realize that the optimal solution is a hybrid
WHITE PAPER Hybrid Approach to DDoS Mitigation FIRST LINE OF DEFENSE Executive Summary As organizations consider options for DDoS mitigation, it is important to realize that the optimal solution is a hybrid
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 7
 1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 7 ORACLE PRODUCT LOGO 20. oktober 2011 Hotel Europa Sarajevo Platform
1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 7 ORACLE PRODUCT LOGO 20. oktober 2011 Hotel Europa Sarajevo Platform
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
How to Create, Deploy, & Operate Secure IoT Applications
 How to Create, Deploy, & Operate Secure IoT Applications TELIT WHITEPAPER INTRODUCTION As IoT deployments accelerate, an area of growing concern is security. The likelihood of billions of additional connections
How to Create, Deploy, & Operate Secure IoT Applications TELIT WHITEPAPER INTRODUCTION As IoT deployments accelerate, an area of growing concern is security. The likelihood of billions of additional connections
Security Solutions. End-to-end security. Protecting your physical access control system.
 Security Solutions End-to-end security Protecting your physical access control system. www.nedapsecurity.com security common practice Bringing IT best practices to physical security Often, companies don
Security Solutions End-to-end security Protecting your physical access control system. www.nedapsecurity.com security common practice Bringing IT best practices to physical security Often, companies don
Network Access Control and VoIP. Ben Hostetler Senior Information Security Advisor
 Network Access Control and VoIP Ben Hostetler Senior Information Security Advisor Objectives/Discussion Points Network Access Control Terms & Definitions Certificate Based 802.1X MAC Authentication Bypass
Network Access Control and VoIP Ben Hostetler Senior Information Security Advisor Objectives/Discussion Points Network Access Control Terms & Definitions Certificate Based 802.1X MAC Authentication Bypass
WHITE PAPER. Session Border Controllers: Helping keep enterprise networks safe TABLE OF CONTENTS. Starting Points
 WHITE PAPER Session Border Controllers: Helping keep enterprise networks safe TABLE OF CONTENTS Starting Points...1 The Four Essentials...2 The Business Case for SIP Trunks...3 To benefit from the latest
WHITE PAPER Session Border Controllers: Helping keep enterprise networks safe TABLE OF CONTENTS Starting Points...1 The Four Essentials...2 The Business Case for SIP Trunks...3 To benefit from the latest
European Cybersecurity PPP European Cyber Security Organisation - ECSO November 2016
 European Cybersecurity PPP European Cyber Security Organisation - ECSO November 2016 Présentation Géraud Canet geraud.canet@cea.fr ABOUT THE CYBERSECURITY cppp 3 AIM 1. Foster cooperation between public
European Cybersecurity PPP European Cyber Security Organisation - ECSO November 2016 Présentation Géraud Canet geraud.canet@cea.fr ABOUT THE CYBERSECURITY cppp 3 AIM 1. Foster cooperation between public
