Administrative & Operations Network Security Assessment
|
|
|
- Merry Laurel Logan
- 5 years ago
- Views:
Transcription
1 TAMPA-HILLSBOROUGH COUNTY EXPRESSWAY AUTHORITY Letter of Clarification No. 1 FOR REQUEST FOR QUALIFICATIONS (RFQ) Administrative & Operations Network Security Assessment RFQ No. O Page 1 of 15
2 Letter of Clarification No. 1 ~ Date of Letter of Clarification: June 7, 2018 To all prospective respondents: The following responds to questions received on the solicitation reference above: Question 1: Response 1: Question 2: Response 2: Question 3: Response 3: Question 4: Response 4: How long will the assessment take? Vendors are expected to discuss timeline in their response. THEA would like all work completed before 12/31/18. Once the assessment is done, if the consultant deems the network security needs an upgrade, will an RFP/RFQ be released to acquire a new system? If so, when? THEA does not anticipate any further RFP/RFQ as a result of the assessment. What is the estimated cost of a new system? This RFP is for a scope of services; not a new system. How would it be funded? This RFP is funded by THEA s operational budget. Question 5: Response 5: Question 6: Response 6: Question 7: Response 7: How many Physical locations will be evaluated in the testing? 2 = Main Building and nearby DR Site What is the function of each location? Office? Co-location facility? Branch site? Main Office and DR Testing Site How many unique subnets are in use in the entire network? There are 2 separate isolated Networks each with 1-3 internal subnets Page 2 of 15
3 Question 8: How many Internet gateways are in use in the entire network? i.e. Wide Area Network connections from ISP s. Response 8: Question 9: Response 9: Question 10: Response 10: Question 11: Response 11: Question 12: 1 per Network Will the test involve remote user policies and testing? i.e. Telecommuters, Road Warriors. Yes Roughly how many policies need to be reviewed? 2-5 Existing policies How many locations are in scope for physical penetration test? 2 Locations: TMC Main Office and East Plaza DR Site How many personnel are in scope for the social engineering penetration testing? Does this include, and phone-based attacks? Response 12: Question 13: About 25 personnel. Yes and phone based attacks. How many personnel will need to be interviewed for the assessment? Number of IT, management, and administrative, operations personnel. Response 13: Total staff is approximately 25. Question 14: How many network devices, such as firewalls, routers, switches, VPN, etc. are in scope for any external and internal testing? Response 14: 2 separate and isolated networks; Admin network has about 1 firewall, 5 access points, 6 switches; Operations Network has about 2 fires walls, 3 routers, 10 switches Question 15: How would you rate the size and complexity of the Administrative and Operations networks? Response 15: Small to medium sized simple networks Page 3 of 15
4 Question 16: How many target servers and workstations included for the penetration testing? What is the mix of physical and virtual servers? Response 16: Admin Network has about 3 host servers, 3 virtual servers, and 30 workstations; Operations Network has about 6 servers, 0 virtual servers, 15 workstations Question 17: Are there any web applications in scope for testing and how many? If yes, how many web pages can we expect for each web app? Response 17: Yes, About 1-2 ; About each Question 18: Response 18: Question 19: Response 19: Question 20: Response 20: Do you want us to test for denial of service (DoS) vulnerabilities? We don t add DoS testing by default. Yes Does the Authority have a preference how the information in the Price Proposal Form is laid out? We usually price out the phases of the engagement. Pricing out the phases of the engagement is acceptable. THEA will ask for details or clarification if needed. Number of offices (please specify approximate number of users, devices, and end-user ports at each) Approximately users, 55 devices Question 21: Outside of physical offices, what connected physical facilities does the Tampa Hillsborough Expressway Authority have? Response 21: How many users, devices and ports can be found at these facilities? 1 DR site within 15 minutes of the main office Approximately 0 users, 4 devices, 8 ports Question 22: Response 22: What technology is used to connect physical installations? Fiber and Ethernet and WiFi Page 4 of 15
5 Question 23: Number of devices (approximated if necessary): Routers, switches, firewalls, hardware appliances (e.g. load balancers, security appliances, etc.) Response 23: 2 separate and isolated networks; Admin network has about 1 firewall, 5 access points, 6 switches; Operations Network has about 2 fires walls, 3 routers, 10 switches Question 24: Response 24: Physical servers a. Virtualization environment i. Physical hosts ii. Virtual Machines iii. Containers Admin Network has about 3 host servers, 3 virtual servers, and 30 workstations Operations Network has about 6 servers, 0 virtual servers, 15 workstations a. Admin Network has about 3 virtual servers, and 30 workstations Operations Network has about 0 virtual servers, 15 workstations Question 25: Does the Expressway Authority use any Operational Technologies, such as connected sensors, toll collectors or other devices? a. What types of devices are used? b. Approximately how many are used? c. How do these devices connect back to the datacenter(s)? d. Are these devices considered in-scope for scanning and/or penetration testing? Response 25: Question 26: We will not be assessing or testing any of the Toll collecting devices. That is a separate Network. Does the Expressway Authority use any infrastructure installed on public or 3 rd -party clouds? a. Does the Expressway Authority use Microsoft Office 365, Google Documents or a similar product? i. If so, what product? ii. How does the Expressway Authority connect to the cloud? Page 5 of 15
6 Response 26: Yes. a. Yes i. Microsoft Office 365 ii. Internet Question 27: What cloud provider(s) are used to provide Infrastructure-as-a- Service? i. How many virtual machines and containers at each? ii. How does the Expressway Authority connect to the cloud? iii. What type of authentication mechanism(s) is/are used (e.g. local authentication, Active Directory Federation, etc.)? Response 27: Question 28: Response 28: None What traffic baselining tools already exist within the environment and can be made available to the consultant? Respondents should assume they are providing tools for establishing baselines Question 29: How many IP addresses total (both internal and external) will be in scope for testing? Response 29: Approximately 100 Question 30: How many web applications (websites) will be in scope for testing? Response 30: Approximately 1-2 Question 31: Are any mobile applications in scope for testing? If so: How many? Response 31: Approximately 25 Question 32: Response 32: When should penetration activities of in scope assets (scanning, exploitation) occur? (e.g. business hours, after business hours, weekends) After Hours and Weekends Page 6 of 15
7 Question 33: For internal testing, will the WWT Penetration Tester have VPN access, or need to be onsite to perform testing? Response 33: Question 34: VPN Access will be acceptable Will the WWT Penetration Tester be required to use client equipment for the test? (Please note, if WWT is required to use customer equipment, WWT will need to install a suite of penetration testing software and the machine in use will need to meet WWT specifications.) Response 34: No Question 35: How many addresses will be phished? Response 35: Approximately 50 Question 36: How many phone numbers will be in scope? Response 36: Approximately 30 Question 37: Is a physical penetration testing of one or more business location(s) or physical installation(s) in scope for the assessment? If so, how many? Response 37: Yes. 2 Question 38: Response 38 Question 39: Response 39: Question 40: Response 40: Was there a pre-bid meeting for this project? No. How many Public IP addresses? (approximate required to effectively quote) 15 but not all are used How many applications? (ie. instances of IIS, WebSphere, Oracle, Peoplesoft etc) 2 premise applications; 1 cloud application Page 7 of 15
8 Question 41: Response 41: Question 42: Response 42: Question 43: Response 43: Question 44: Response 44: Is a physical security assessment of the infrastructure in scope of the Network Assessment? Yes Is the IT organization centralized or decentralized? Centralized Has a security control framework been adopted? If yes, which one? No When was your last network security assessment performed? Internal reviews are done quarterly, but this is a special project with broader scope and purpose as stated in the RFP Question 45: Response 45: Question 46: Response 46: Question 47: Response 47: Question 48: Response 48: Question 49: Are there documented policies, procedures, standards, and guidelines in place? If so, how many? The agency intends to develop new policies and procedures because of this RFP For the external network vulnerability assessment and penetration testing, what is the approximate number of active IPs? 15 but not all are used What is the number of firewalls? Are the firewalls in HA mode? Two. No. What is the approximate number and types of switch devices? WatchGuard, Cisco and HP equipment (various models) For the internal network vulnerability assessment and penetration testing, what is the approximate number of active IPs? Page 8 of 15
9 Response 49: Question 50: Response 50: Question 51: Response 51: 3 private subnets; all Class C How many staff security training and agency policies are in scope for review? All For physical security penetration testing, how many server rooms/racks/dr sites require visitation? 1 server room and 1 communications room at main office 1 DR location approximately 10 minutes from the main office Question 52: Response 52: How many targets are in scope for user-focused penetration testing? User account testing is not part of this scope. Question 53: Response 53: Question 54: Response 54: Question 55: Response 55: Question 56: Response 56: Question 57: Is web application testing in scope for this project? If so, how many applications require assessment? Application testing is not part of this scope. Is a wireless network assessment in scope? If so, how many controllers support the wireless network? One controller (firewall) and 5 access points Will THEA accept reference letters in lieu of client contact information? Submit the most complete bid you can and it will be evaluated per the RFP. Will THEA provide its budget for this project? No, THEA is looking to the Respondent for price proposal for this project. We do have a partner who handles this work and we have worked with on numerous occasions. Will a joint proposal be permitted for the services requested? Page 9 of 15
10 Response 57: Per page 6 of the RFQ, joint proposals will not be accepted but subcontracting is acceptable. Question 58: We requests that contact info for our references only be provided should we be selected as a finalist. Is this acceptable to THEA? Response 58: Incomplete proposals will be subject to the evaluation per the RFP. Question 59: Response 59: Question 60: Response 60: Question 61: Response 61: Question 62: Response 62: Question 63: Response 63: Question 64: Is THEA seeking a fixed price or time and materials bid for this project? Responses are expected to be stated as a fixed price. How many employees total does THEA have? How many IT employees? Approximately 30 staff and 1 IT Manager. Approximately how many pages of written policies and procedures currently exist? How many documents? Less than 100 pages in multiple documents. Approximately how many staff must be interviewed for understand the organization strategy and new planned network architecture and design? Approximately 1 staff and 2-3 vendor representative. How many groups are associated with running the network (eg. Network, Security, Operations) THEA has one IT department with one IT Manager responsible for running the network(s). How many of the THEA locations have an independent Internet connection? Response 64: The Main Office has the only internet connection. Page 10 of 15
11 Question 65: Are any cloud services in use and in scope for this assessment - How many SaaS solutions? - How many PaaS solutions? - How many IaaS solutions? Response 65: Question 66: Response 66: Question 67: With the exception of Microsoft Office 365, all infrastructure is premise. How many firewalls are in the network? Two. Is rules analysis on firewalls desired to look for common issues? If so, how many firewalls, and what make, model, and software version? Response 67: Question 68: No. On about what percentage of devices is SNMP or a similar discovery protocol enabled? Response 68: Estimated 75%. Question 69: Response 69: Question 70: How much bandwidth is involved in traffic pattern analysis? How many separate locations must this be performed on? Can a network tap be inserted in these locations? Unknown. One physical location. Yes, the network can be tapped if necessary. How many physical sites are required for physical security penetration testing? Are any of these large sites, such as a distribution center? Response 70: Question 71: 2 physical locations; both small sites. Approximately how many users should phishing attempts be made on? Is phishing to be performed in both insider and outsider modes? Response 71: THEA has approximately 30 staff. Page 11 of 15
12 Question 72: Response 72: Question 73: Can testing be performed during business hours? Limited testing can be done during business hours; most testing is requested for after hours and weekends. Is 'Outsider' testing to be performed from the outside of the network, the inside of the network, or both? Response 73: Question 74: Provide your recommendation in your response. Does THEA have an estimated duration for Outsider testing? An attacker may invest significant time, which can dramatically increase the cost of a proposal without time bounds Is 'Insider' testing to be performed from the outside of the network, the inside of the network, or both? If testing is to be performed from inside the network, can remote access to a testing server be provisioned? Response 74: THEA does not have any estimates. Remote access can be provisioned. Question 75: Response 75: Question 76: Will the insider/outsider testing be performed from a perspective of assumed compromise (regular user on workstation compromised?) Provide your recommendation in your response. Is the IT service delivery organization centralized or decentralized? Response 76: Question 77: Centralized. Are there documented policies/procedures for the core IT processes? Response 77: Question 78: Some policies/procedures are documented. What centralized authentication is used (Novell, Windows AD, something else?)? o If Windows, how many Domains? Page 12 of 15
13 Response 78: Question 79: One Windows Domain structure manages authentication; it synchronizes to Office 365. Are all the operational units/divisions logically accessible on the network from a centralized location? o I.e. can the systems be tested from a central location? Response 79: Question 80: Yes. Please clarify who the client is in this objective statement. Develop physical and logical network diagrams and flow charts to compare with client s Response 80: Question 81: THEA maintains internal diagram and is the client referred to. To what level of detail are you requesting for the inventory of network equipment? Response 81: Make/Model/Serial #/ Identified Role/ Assessment Status would be considered a minimum. Question 82: As an attempt is made to execute the logical/physical penetration test, what is the goal? At some point people become suspicious with various aspects of testing being engaged (phishing, tailgating, USB, etc.) and the effort becomes an exercise in futility because word is passed around and people become suspicious. Bottom line question is What is considered success? Response 82: See RFP for the goal; all testing will be limited to reasonable efforts and it is not expected to be a major impact to THEA staff. Question 83: Is Server room in a hosted facility or on THEA premise? DR Facility? Response 83: Yes, plus a nearby DR site. Yes, within 15 minutes of the main office. Page 13 of 15
14 Question 84: A Network and/or server diagram Response 84: The development of a network diagram is a component of the scope of work and will not be provided in advance. Question 85: What is the term of the engagement? Response 85: THEA expects the scope to be completed no later than 12/31/18. Question 86: Does the THEA have to have services completed by a specific date to meet demands of an audit or some other date? Response 86: THEA expects the scope to be completed no later than 12/31/18. Respondents MUST acknowledge receipt of this Letter of Clarification by signing, dating and returning the completed Acknowledgement of Receipt of Letter of Clarification/Addendum form with Respondent s proposal. All other items, conditions, and specifications in the ITB document not specifically changed by the Addendum remain unchanged. Please send all questions to THEA s Procurement Manager, Man Le, via at Man.Le@tampa-xway.com. Page 14 of 15
15 ACKNOWLEDGEMENT OF RECEIPT OF Letter of Clarification/Addenda Were Addenda issued on this Solicitation? Yes No Were Letter of Clarification issued on this Solicitation? Yes No I (We) hereby acknowledge receipt of the following Addendum/Addenda issued in reference to this solicitation by listing the Addenda by number, date and signing the form: Addendum Date: Letter of Clarification Letter of Clarification Date: Date: PROPOSER: By: (AUTHORIZED SIGNATURE) (Printed Name of Signer) (Title of Signer) (Date Signed) Page 15 of 15
Questions Submitted Barry County Michigan Network Security Audit and Vulnerability Assessment RFP
 Questions Submitted Barry County Michigan Network Security Audit and Vulnerability Assessment RFP 1. If we cannot attend the September 27 pre-bid meeting in-person, will there be conference call capability
Questions Submitted Barry County Michigan Network Security Audit and Vulnerability Assessment RFP 1. If we cannot attend the September 27 pre-bid meeting in-person, will there be conference call capability
NOTICE TO ALL PROSPECTIVE RESPONDENTS RFP 18-ITSS/CY. Addendum No. 1 issued September 7, RFI responses are in red bold print
 DEDICATED TO THE HEALTH OF OUR COMMUNITY www.hcdpbc.org NOTICE TO ALL PROSPECTIVE RESPONDENTS RFP 18-ITSS/CY Addendum No. 1 issued September 7, 2018 RFI responses are in red bold print How many public
DEDICATED TO THE HEALTH OF OUR COMMUNITY www.hcdpbc.org NOTICE TO ALL PROSPECTIVE RESPONDENTS RFP 18-ITSS/CY Addendum No. 1 issued September 7, 2018 RFI responses are in red bold print How many public
County of El Paso Purchasing Department 800 E. Overland Room 300 El Paso, Texas (915) / Fax: (915)
 County of El Paso Purchasing Department 800 E. Overland Room 300 El Paso, Texas 79901 (915) 546-2048 / Fax: (915) 546-8180 www.epcounty.com ADDENDUM 1 To: From: All Interested Proposers Blanca Güereca,
County of El Paso Purchasing Department 800 E. Overland Room 300 El Paso, Texas 79901 (915) 546-2048 / Fax: (915) 546-8180 www.epcounty.com ADDENDUM 1 To: From: All Interested Proposers Blanca Güereca,
Request for Proposal HIPAA Security Risk and Vulnerability Assessment. May 1, First Choice Community Healthcare
 Request for Proposal HIPAA Security Risk and Vulnerability Assessment May 1, 2016 First Choice Community Healthcare Timeline The following Timeline has been defined to efficiently solicit multiple competitive
Request for Proposal HIPAA Security Risk and Vulnerability Assessment May 1, 2016 First Choice Community Healthcare Timeline The following Timeline has been defined to efficiently solicit multiple competitive
Information Technology Security Audit RFP2018-P02 - Questions and Answers
 Information Technology Security Audit RFP2018-P02 - Questions and Answers Q: Page 9 (under the Pricing section) references Perimeter Vulnerability Assessment and Internal Vulnerability Scan. For clarification,
Information Technology Security Audit RFP2018-P02 - Questions and Answers Q: Page 9 (under the Pricing section) references Perimeter Vulnerability Assessment and Internal Vulnerability Scan. For clarification,
RFQ OIT-1 Q&A. Questions and Answers, in the order received.
 Question Does the system have an existing SSP? Do they use a system like Xacta or CSAM to generate the SSP. Will they provide us the current POAM list? Will they provide scanning tools or we have to bring
Question Does the system have an existing SSP? Do they use a system like Xacta or CSAM to generate the SSP. Will they provide us the current POAM list? Will they provide scanning tools or we have to bring
RFQ OIT-1 Q&A. Questions and Answers, in the order received.
 Question Does the system have an existing SSP? Do they use a system like Xacta or CSAM to generate the SSP. Will they provide us the current POAM list? Will they provide scanning tools or we have to bring
Question Does the system have an existing SSP? Do they use a system like Xacta or CSAM to generate the SSP. Will they provide us the current POAM list? Will they provide scanning tools or we have to bring
ADDENDUM NUMBER: 1. Website Design & Development Services
 Broward County Housing Authority Solicitation Number: RFP 16-249 Website Design & Development Services DATE: June 23, 2017 TO ALL PROSPECTIVE BIDDERS PLEASE NOTE THE FOLLOWING ADDITION: Page 6, paragraph
Broward County Housing Authority Solicitation Number: RFP 16-249 Website Design & Development Services DATE: June 23, 2017 TO ALL PROSPECTIVE BIDDERS PLEASE NOTE THE FOLLOWING ADDITION: Page 6, paragraph
OVERARCHING SECURITY CONSULTING SERVICES SAWS Solicitation No. R JAM. ADDENDUM NO. 1 February 28, 2018
 To Respondent of Record: OVERARCHING SECURITY CONSULTING SERVICES SAWS Solicitation No. R-18-001-JAM ADDENDUM NO. 1 February 28, 2018 This addendum, applicable to project referenced above, is an amendment
To Respondent of Record: OVERARCHING SECURITY CONSULTING SERVICES SAWS Solicitation No. R-18-001-JAM ADDENDUM NO. 1 February 28, 2018 This addendum, applicable to project referenced above, is an amendment
Ken Agress, Senior Consultant PlanNet Consulting, LLC.
 Elements of a Vulnerability Assessment Ken Agress, Senior Consultant PlanNet Consulting, LLC. Defining a Vulnerability Assessment Agenda Types of Vulnerability Assessments Are You Ready for an Assessment?
Elements of a Vulnerability Assessment Ken Agress, Senior Consultant PlanNet Consulting, LLC. Defining a Vulnerability Assessment Agenda Types of Vulnerability Assessments Are You Ready for an Assessment?
November 1, 2018, RP Provision of Managed Security Services on an Annual Contract ADDENDUM #2
 November 1, 2018, RP029-18 Provision of Managed Security Services on an Annual Contract ADDENDUM #2 Please see the below summation of the technical questions and answers that have been received regarding
November 1, 2018, RP029-18 Provision of Managed Security Services on an Annual Contract ADDENDUM #2 Please see the below summation of the technical questions and answers that have been received regarding
Request for Proposal. I. Introduction. II. Scope of Work. IT Managed Services Support. IT Environment. Main Facility
 Request for Proposal IT Managed Services Support I. Introduction The Hoh Indian Tribe ( Tribe or Hoh Tribe ) is located in western Washington State in Jefferson County, 28 miles South of Forks, Washington.
Request for Proposal IT Managed Services Support I. Introduction The Hoh Indian Tribe ( Tribe or Hoh Tribe ) is located in western Washington State in Jefferson County, 28 miles South of Forks, Washington.
Request for Proposal (RFP)
 Request for Proposal (RFP) BOK PENETRATION TESTING Date of Issue Closing Date Place Enquiries Table of Contents 1. Project Introduction... 3 1.1 About The Bank of Khyber... 3 1.2 Critical Success Factors...
Request for Proposal (RFP) BOK PENETRATION TESTING Date of Issue Closing Date Place Enquiries Table of Contents 1. Project Introduction... 3 1.1 About The Bank of Khyber... 3 1.2 Critical Success Factors...
Great Northern Corporation Request for Proposal for Network Server Installation and Service
 Great Northern Corporation Request for Proposal for Network Server Installation and Service Background Purpose The purpose of this Request for Proposal (RFP) is to invite prospective vendors to submit
Great Northern Corporation Request for Proposal for Network Server Installation and Service Background Purpose The purpose of this Request for Proposal (RFP) is to invite prospective vendors to submit
Third Party Cloud Services Its Adoption in the New Age
 Solutions for higher performance! Third Party Cloud Services Its Adoption in the New Age 1 Introduction Cloud computing is the delivery of computing services over the Internet. Cloud services allow individuals
Solutions for higher performance! Third Party Cloud Services Its Adoption in the New Age 1 Introduction Cloud computing is the delivery of computing services over the Internet. Cloud services allow individuals
Cloud Computing. Faculty of Information Systems. Duc.NHM. nhmduc.wordpress.com
 Cloud Computing Faculty of Information Systems Duc.NHM nhmduc.wordpress.com Evaluating Cloud Security: An Information Security Framework Chapter 6 Cloud Computing Duc.NHM 2 1 Evaluating Cloud Security
Cloud Computing Faculty of Information Systems Duc.NHM nhmduc.wordpress.com Evaluating Cloud Security: An Information Security Framework Chapter 6 Cloud Computing Duc.NHM 2 1 Evaluating Cloud Security
CompTIA CAS-002. CompTIA Advanced Security Practitioner (CASP) Download Full Version :
 CompTIA CAS-002 CompTIA Advanced Security Practitioner (CASP) Download Full Version : http://killexams.com/pass4sure/exam-detail/cas-002 QUESTION: 517 A security engineer is a new member to a configuration
CompTIA CAS-002 CompTIA Advanced Security Practitioner (CASP) Download Full Version : http://killexams.com/pass4sure/exam-detail/cas-002 QUESTION: 517 A security engineer is a new member to a configuration
E-RATE YEAR Request for Proposal Wireless Access Points and Control for Monson-Sultana Joint Union Elementary School District BEN#144060
 E-RATE YEAR 2016-2017 Request for Proposal Wireless Access Points and Control for Monson-Sultana Joint Union Elementary School District BEN#144060 470 Application # 160043013 Submission Deadline: Thursday,
E-RATE YEAR 2016-2017 Request for Proposal Wireless Access Points and Control for Monson-Sultana Joint Union Elementary School District BEN#144060 470 Application # 160043013 Submission Deadline: Thursday,
Migration Services IBM Lotus Notes to MS Office 365
 City of West Palm Beach 401 Clematis Street, 3rd Floor West Palm Beach, FL 33401 TEL: (561) 822-2100 FAX: (561) 822-1564 Migration Services IBM Lotus Notes to MS Office 365 April 3, 2017 Addendum No. 1
City of West Palm Beach 401 Clematis Street, 3rd Floor West Palm Beach, FL 33401 TEL: (561) 822-2100 FAX: (561) 822-1564 Migration Services IBM Lotus Notes to MS Office 365 April 3, 2017 Addendum No. 1
The Multi Cloud Journey
 The Multi Cloud Journey GLOBAL OFFICES? WE VE GOT THE COVERAGE Presence in 69 countries 242,000 employees Offices in 42 countries regions 120 cities Largest DC provider Network coverage in 196 countries
The Multi Cloud Journey GLOBAL OFFICES? WE VE GOT THE COVERAGE Presence in 69 countries 242,000 employees Offices in 42 countries regions 120 cities Largest DC provider Network coverage in 196 countries
ADDENDUM #1 RFP # , Districtwide Network Refresh Design
 ADDENDUM #1 RFP #1718-03, Districtwide Network Refresh Design This Addendum forms a part of the Contract Documents and modifies the original Contract Documents. Acknowledge receipt of this Addendum in
ADDENDUM #1 RFP #1718-03, Districtwide Network Refresh Design This Addendum forms a part of the Contract Documents and modifies the original Contract Documents. Acknowledge receipt of this Addendum in
Service Description: CNS Federal High Touch Technical Support
 Page 1 of 1 Service Description: CNS Federal High Touch Technical Support This service description ( Service Description ) describes Cisco s Federal High Touch Technical support (CNS-HTTS), a tier 2 in
Page 1 of 1 Service Description: CNS Federal High Touch Technical Support This service description ( Service Description ) describes Cisco s Federal High Touch Technical support (CNS-HTTS), a tier 2 in
CORRIGENDUM- I. Sr. Page/Section Description Bidder s Query Clarification / Amendments. 1 Page 5 of Vol-I, and Page 15 of Vol-II
 CORRIGENDUM- I Name of work: RFP for selection of agency for creation of Digital Project Management Platform comprising OSO, Supply, Implementation and Support of 5D-BIM & ERP for the Nagpur Metro Rail
CORRIGENDUM- I Name of work: RFP for selection of agency for creation of Digital Project Management Platform comprising OSO, Supply, Implementation and Support of 5D-BIM & ERP for the Nagpur Metro Rail
Business Strategy Theatre
 Business Strategy Theatre Security posture in the age of mobile, social and new threats Steve Pao, GM Security Business 01 May 2014 In the midst of chaos, there is also opportunity. - Sun-Tzu Security:
Business Strategy Theatre Security posture in the age of mobile, social and new threats Steve Pao, GM Security Business 01 May 2014 In the midst of chaos, there is also opportunity. - Sun-Tzu Security:
Security Readiness Assessment
 Security Readiness Assessment Jackson Thomas Senior Manager, Sales Consulting Copyright 2015 Oracle and/or its affiliates. All rights reserved. Cloud Era Requires Identity-Centric Security SaaS PaaS IaaS
Security Readiness Assessment Jackson Thomas Senior Manager, Sales Consulting Copyright 2015 Oracle and/or its affiliates. All rights reserved. Cloud Era Requires Identity-Centric Security SaaS PaaS IaaS
Cyber Security Requirements for Electronic Safety and Security
 This document is to provide suggested language to address cyber security elements as they may apply to physical and electronic security projects. Security consultants and specifiers should consider this
This document is to provide suggested language to address cyber security elements as they may apply to physical and electronic security projects. Security consultants and specifiers should consider this
The Common Controls Framework BY ADOBE
 The Controls Framework BY ADOBE The following table contains the baseline security subset of control activities (derived from the Controls Framework by Adobe) that apply to Adobe s enterprise offerings.
The Controls Framework BY ADOBE The following table contains the baseline security subset of control activities (derived from the Controls Framework by Adobe) that apply to Adobe s enterprise offerings.
Campus Network Design
 Design Principles Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Design Principles Task in Network Design Plan phase
Design Principles Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Design Principles Task in Network Design Plan phase
ADDENDUM NO. 1. Kansas City Area Transportation Authority (KCATA) 1350 E. 17 th Street Kansas City, Missouri Point to Point Fiber Connection
 Issue Date: December 9, 2016 ADDENDUM NO. 1 Kansas City Area Transportation Authority (KCATA) 1350 E. 17 th Street Kansas City, Missouri 64108 Project #16-7029-25 This Addendum is hereby made a part of
Issue Date: December 9, 2016 ADDENDUM NO. 1 Kansas City Area Transportation Authority (KCATA) 1350 E. 17 th Street Kansas City, Missouri 64108 Project #16-7029-25 This Addendum is hereby made a part of
Purchasing Department Finance Group INVITATION TO BID
 Purchasing Department Finance Group September 20, 2012 INVITATION TO BID The City of Norwalk, Information Technology Department, is soliciting bids for Computer Software Microsoft Server 2008 plus SQL
Purchasing Department Finance Group September 20, 2012 INVITATION TO BID The City of Norwalk, Information Technology Department, is soliciting bids for Computer Software Microsoft Server 2008 plus SQL
ATTACHMENT A FSD WLAN PROGRAM SCOPE OF WORK IFB I NETWORK EQUIPMENT AND RELATED SERVICES
 I. EXECUTIVE SUMMARY A. The intent of this Invitation for Bid (IFB) is to solicit proposals to provide solutions for Wide Area Networking (WAN), Local Area Networking (LAN), and Wireless Local Area Networking
I. EXECUTIVE SUMMARY A. The intent of this Invitation for Bid (IFB) is to solicit proposals to provide solutions for Wide Area Networking (WAN), Local Area Networking (LAN), and Wireless Local Area Networking
CoreMax Consulting s Cyber Security Roadmap
 CoreMax Consulting s Cyber Security Roadmap What is a Cyber Security Roadmap? The CoreMax consulting cyber security unit has created a simple process to access the unique needs of each client and allows
CoreMax Consulting s Cyber Security Roadmap What is a Cyber Security Roadmap? The CoreMax consulting cyber security unit has created a simple process to access the unique needs of each client and allows
ADDENDUM #1. Manassas City Public Schools. Office of Purchasing and Contracting 8700 Centreville Rd., Suite 400 Manassas, VA 20108
 Manassas City Public Schools ADDENDUM #1 Office of Purchasing and Contracting 8700 Centreville Rd., Suite 400 Manassas, VA 20108 RFP Title: RFP Number: Proposal Due Date: MCPS Firewall Replacement 19-026-RFP
Manassas City Public Schools ADDENDUM #1 Office of Purchasing and Contracting 8700 Centreville Rd., Suite 400 Manassas, VA 20108 RFP Title: RFP Number: Proposal Due Date: MCPS Firewall Replacement 19-026-RFP
NETWORKING &SECURITY SOLUTIONSPORTFOLIO
 NETWORKING &SECURITY SOLUTIONSPORTFOLIO NETWORKING &SECURITY SOLUTIONSPORTFOLIO Acomprehensivesolutionsportfoliotohelpyougetyourbusiness securelyconnected.clickononeofoursolutionstoknowmore NETWORKING
NETWORKING &SECURITY SOLUTIONSPORTFOLIO NETWORKING &SECURITY SOLUTIONSPORTFOLIO Acomprehensivesolutionsportfoliotohelpyougetyourbusiness securelyconnected.clickononeofoursolutionstoknowmore NETWORKING
REQUEST FOR PROPOSALS FOR COMPUTER HARDWARE, SOFTWARE, PERIPHERALS, AND INSTALLATION SERVICES PROPOSAL NO.s PIT & PIT ADDENDUM #4
 PURCHASING DEPARTMENT Willowbend Road Peachtree City, GA 3069 Phone: 770-487-767 Fax: 770-63-0 www.peachtree-city.org REQUEST FOR PROPOSALS FOR COMPUTER HARDWARE, SOFTWARE, PERIPHERALS, AND INSTALLATION
PURCHASING DEPARTMENT Willowbend Road Peachtree City, GA 3069 Phone: 770-487-767 Fax: 770-63-0 www.peachtree-city.org REQUEST FOR PROPOSALS FOR COMPUTER HARDWARE, SOFTWARE, PERIPHERALS, AND INSTALLATION
REQUEST FOR PROPOSALS # DRUPAL HOSTING AND MIGRATION SERVICES RESPONSE TO CLARIFYING QUESTIONS July 10, 2017
 REQUEST FOR PROPOSALS #2017-47 DRUPAL HOSTING AND MIGRATION SERVICES RESPONSE TO CLARIFYING QUESTIONS July 10, 2017 Note that these are questions submitted by interested firms to the above referenced solicitation.
REQUEST FOR PROPOSALS #2017-47 DRUPAL HOSTING AND MIGRATION SERVICES RESPONSE TO CLARIFYING QUESTIONS July 10, 2017 Note that these are questions submitted by interested firms to the above referenced solicitation.
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
DENA BANK INFORMATION TECHNOLOGY DEPARTMENT, HO, MUMBAI.
 Replies to Queries during the Pre-bid meeting held on 12 th May, 2015 for Tender Managed Security Services [Tender Ref: HO/ITD/206/2015 Dated 06/05/2015]. Sr. No. RFP Reference No. Query Clarification/
Replies to Queries during the Pre-bid meeting held on 12 th May, 2015 for Tender Managed Security Services [Tender Ref: HO/ITD/206/2015 Dated 06/05/2015]. Sr. No. RFP Reference No. Query Clarification/
3. If so, was this taken into consideration when designing the RFP?
 9770 Culver Boulevard, Culver City, California 90232 Charles D. Herbertson, P.E., LS Public Works Director and City Engineer Mate Gaspar, P.E. Engineering Services Manager (310) 253-5600 FAX (310) 253-5626
9770 Culver Boulevard, Culver City, California 90232 Charles D. Herbertson, P.E., LS Public Works Director and City Engineer Mate Gaspar, P.E. Engineering Services Manager (310) 253-5600 FAX (310) 253-5626
Education Network Security
 Education Network Security RECOMMENDATIONS CHECKLIST Learn INSTITUTE Education Network Security Recommendations Checklist This checklist is designed to assist in a quick review of your K-12 district or
Education Network Security RECOMMENDATIONS CHECKLIST Learn INSTITUTE Education Network Security Recommendations Checklist This checklist is designed to assist in a quick review of your K-12 district or
Solution Pack. Managed Services Virtual Private Cloud Security Features Selections and Prerequisites
 Solution Pack Managed Services Virtual Private Cloud Security Features Selections and Prerequisites Subject Governing Agreement DXC Services Requirements Agreement between DXC and Customer including DXC
Solution Pack Managed Services Virtual Private Cloud Security Features Selections and Prerequisites Subject Governing Agreement DXC Services Requirements Agreement between DXC and Customer including DXC
Anna Independent School District
 Anna Independent School District 501 S. Sherley Avenue Anna Texas 75409 www.annaisd.org Phone: 972-924-1000 Fax: 972-924-1001 Request for Proposals (RFP) Spring 2015 Computer Hardware Refresh The Technology
Anna Independent School District 501 S. Sherley Avenue Anna Texas 75409 www.annaisd.org Phone: 972-924-1000 Fax: 972-924-1001 Request for Proposals (RFP) Spring 2015 Computer Hardware Refresh The Technology
Telephone System RFQ (18-WIOA-05) Bidder s Conference - Questions and Answers posted 11/14/18
 Telephone System RFQ (18-WIOA-05) Bidder s Conference - Questions and Answers posted 11/14/18 Meetings held on November 12, 2018 & November 14, 2018 @ 2pm Clemson SC Works Center, Clemson, SC 1. Internet
Telephone System RFQ (18-WIOA-05) Bidder s Conference - Questions and Answers posted 11/14/18 Meetings held on November 12, 2018 & November 14, 2018 @ 2pm Clemson SC Works Center, Clemson, SC 1. Internet
Pass4suresVCE. Pass4sures exam vce dumps for guaranteed success with high scores
 Pass4suresVCE http://www.pass4suresvce.com Pass4sures exam vce dumps for guaranteed success with high scores Exam : CS0-001 Title : CompTIA Cybersecurity Analyst (CySA+) Exam Vendor : CompTIA Version :
Pass4suresVCE http://www.pass4suresvce.com Pass4sures exam vce dumps for guaranteed success with high scores Exam : CS0-001 Title : CompTIA Cybersecurity Analyst (CySA+) Exam Vendor : CompTIA Version :
02/14/2017 ADDENDUM # 1. RFP : Managed Service Provider for IT Infrastructure. Provide answers to Managed Service Provider questions.
 02/14/2017 ADDENDUM # 1 RFP 17-031: Managed Service Provider for IT Infrastructure Addendum #1 is being issued to: Provide answers to Managed Service Provider questions. Proposers shall sign this Addendum
02/14/2017 ADDENDUM # 1 RFP 17-031: Managed Service Provider for IT Infrastructure Addendum #1 is being issued to: Provide answers to Managed Service Provider questions. Proposers shall sign this Addendum
QUESTIONS AND ANSWERS PROJECT NO Supply and Install Student System. Houston Community College System, Procurement Operations
 QUESTIONS AND ANSWERS PROJECT NO. 06-22 Supply and Install Student Email System Date: March 21, 2006 To: From: All Prospective Respondents Houston Community College System, Procurement Operations Subject:
QUESTIONS AND ANSWERS PROJECT NO. 06-22 Supply and Install Student Email System Date: March 21, 2006 To: From: All Prospective Respondents Houston Community College System, Procurement Operations Subject:
Example Azure Implementation for Government Agencies. Indirect tax-filing system. By Alok Jain Azure Customer Advisory Team (AzureCAT)
 Example Azure Implementation for Government Agencies Indirect tax-filing system By Alok Jain Azure Customer Advisory Team (AzureCAT) June 2018 Example Azure Implementation for Government Agencies Contents
Example Azure Implementation for Government Agencies Indirect tax-filing system By Alok Jain Azure Customer Advisory Team (AzureCAT) June 2018 Example Azure Implementation for Government Agencies Contents
Penetration Testing! The Nitty Gritty. Jeremy Conway Partner/CTO
 Penetration Testing! The Nitty Gritty Jeremy Conway Partner/CTO Before I Start What qualifies me to speak about this? It s all important and relevant! Brief History The Past! US Active Army DoD Contractor
Penetration Testing! The Nitty Gritty Jeremy Conway Partner/CTO Before I Start What qualifies me to speak about this? It s all important and relevant! Brief History The Past! US Active Army DoD Contractor
SOLICITATION AMENDMENT
 North Dakota University System Core Technology Services 4349 James Ray Dr. Grand Forks, ND 58202 September 29, 2014 Solicitation Number and Title: CTS-14-001 Datacenter Operations, Monitoring and Maintenance
North Dakota University System Core Technology Services 4349 James Ray Dr. Grand Forks, ND 58202 September 29, 2014 Solicitation Number and Title: CTS-14-001 Datacenter Operations, Monitoring and Maintenance
IOWA STATE UNIVERSITY OF SCIENCE AND TECHNOLOGY
 IOWA STATE UNIVERSITY OF SCIENCE AND TECHNOLOGY Procurement Services Department 1340 Administrative Services Building 2221 Wanda Daley Drive Ames, Iowa 50011-3616 515 294-4860 FAX 515 294-9606 Date: August
IOWA STATE UNIVERSITY OF SCIENCE AND TECHNOLOGY Procurement Services Department 1340 Administrative Services Building 2221 Wanda Daley Drive Ames, Iowa 50011-3616 515 294-4860 FAX 515 294-9606 Date: August
Cloud Computing. Presentation to AGA April 20, Mike Teller Steve Wilson
 Presentation to AGA April 20, 2017 Mike Teller Steve Wilson Agenda: What is cloud computing? What are the potential benefits of cloud computing? What are some of the important issues agencies need to consider
Presentation to AGA April 20, 2017 Mike Teller Steve Wilson Agenda: What is cloud computing? What are the potential benefits of cloud computing? What are some of the important issues agencies need to consider
REQUEST FOR INFORMATION (RFI) ELECTRONIC FORMS AUTOMATION DEP Solicitation Number: C
 Request for Information Electronic Forms Automation DEP RFI No.: 2016040C REQUEST FOR INFORMATION (RFI) ELECTRONIC FORMS AUTOMATION DEP Solicitation Number: 2016040C This is a Request for Information (RFI)
Request for Information Electronic Forms Automation DEP RFI No.: 2016040C REQUEST FOR INFORMATION (RFI) ELECTRONIC FORMS AUTOMATION DEP Solicitation Number: 2016040C This is a Request for Information (RFI)
Fundamentals of Information Systems Security Lesson 5 Auditing, Testing, and Monitoring
 Fundamentals of Information Systems Security Lesson 5 Auditing, Testing, and Monitoring Learning Objective Explain the importance of security audits, testing, and monitoring to effective security policy.
Fundamentals of Information Systems Security Lesson 5 Auditing, Testing, and Monitoring Learning Objective Explain the importance of security audits, testing, and monitoring to effective security policy.
A Measurement Companion to the CIS Critical Security Controls (Version 6) October
 A Measurement Companion to the CIS Critical Security Controls (Version 6) October 2015 1 A Measurement Companion to the CIS Critical Security Controls (Version 6) Introduction... 3 Description... 4 CIS
A Measurement Companion to the CIS Critical Security Controls (Version 6) October 2015 1 A Measurement Companion to the CIS Critical Security Controls (Version 6) Introduction... 3 Description... 4 CIS
REQUEST FOR PROPOSALS
 REQUEST FOR PROPOSALS ADDENDUM # 1 Questions and Clarifications Website Redesign RFP #NF2018-01 TO: Prospective Proposers FROM: Martha Howarter, Director of Federal Programs DATE: March 16, 2018 SUBJECT:
REQUEST FOR PROPOSALS ADDENDUM # 1 Questions and Clarifications Website Redesign RFP #NF2018-01 TO: Prospective Proposers FROM: Martha Howarter, Director of Federal Programs DATE: March 16, 2018 SUBJECT:
An Operational Cyber Security Perspective on Emerging Challenges. Michael Misumi CIO Johns Hopkins University Applied Physics Lab (JHU/APL)
 An Operational Cyber Security Perspective on Emerging Challenges Michael Misumi CIO Johns Hopkins University Applied Physics Lab (JHU/APL) Johns Hopkins University Applied Physics Lab (JHU/APL) University
An Operational Cyber Security Perspective on Emerging Challenges Michael Misumi CIO Johns Hopkins University Applied Physics Lab (JHU/APL) Johns Hopkins University Applied Physics Lab (JHU/APL) University
ADDENDUM B 02/23/2018. Due to an administrative oversite, the following questions were not included in Addendum A.
 Finance Department Purchasing Division REQUEST FOR PROPOSALS (RFP) Specification No. 17-11152-C FOR OFFICE 365 EXCHANGE MIGRATION AND ONE DRIVE IMPLEMENTATION PROPOSALS WILL NOT BE OPENED AND READ PUBLICLY
Finance Department Purchasing Division REQUEST FOR PROPOSALS (RFP) Specification No. 17-11152-C FOR OFFICE 365 EXCHANGE MIGRATION AND ONE DRIVE IMPLEMENTATION PROPOSALS WILL NOT BE OPENED AND READ PUBLICLY
OFFICE OF PROCUREMENT AND CONTRACTING 301 LARGO ROAD, LARGO MARYLAND PHONE: 301/
 OFFICE OF PROCUREMENT AND CONTRACTING 301 LARGO ROAD, LARGO MARYLAND 20774-2199 PHONE: 301/546-0641 REQUEST FOR PROPOSAL #16-11 LEASE FOR NEW COPIERS/MFDS AND PRINT MANAGEMENT SOFTWARE Addendum No. 2 Issued:
OFFICE OF PROCUREMENT AND CONTRACTING 301 LARGO ROAD, LARGO MARYLAND 20774-2199 PHONE: 301/546-0641 REQUEST FOR PROPOSAL #16-11 LEASE FOR NEW COPIERS/MFDS AND PRINT MANAGEMENT SOFTWARE Addendum No. 2 Issued:
Cloud Computing Standard 1.1 INTRODUCTION 2.1 PURPOSE. Effective Date: July 28, 2015
 Cloud Computing Standard Effective Date: July 28, 2015 1.1 INTRODUCTION Cloud computing services are application and infrastructure resources that users access via the Internet. These services, contractually
Cloud Computing Standard Effective Date: July 28, 2015 1.1 INTRODUCTION Cloud computing services are application and infrastructure resources that users access via the Internet. These services, contractually
Surprisingly Successful: What Really Works in Cyber Defense. John Pescatore, SANS
 Surprisingly Successful: What Really Works in Cyber Defense John Pescatore, SANS 1 Largest Breach Ever 2 The Business Impact Equation All CEOs know stuff happens in business and in security The goal is
Surprisingly Successful: What Really Works in Cyber Defense John Pescatore, SANS 1 Largest Breach Ever 2 The Business Impact Equation All CEOs know stuff happens in business and in security The goal is
CISCO NETWORKS BORDERLESS Cisco Systems, Inc. All rights reserved. 1
 CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
Questions and Answers for Request for Proposal #03588
 1. Is 10GB a requirement? Questions and Answers for Request for Proposal #03588 Vendors are welcome to quote on both 10GB and 1GB options. 2. The RFP indicates that you would like to replace the 5 2 nd
1. Is 10GB a requirement? Questions and Answers for Request for Proposal #03588 Vendors are welcome to quote on both 10GB and 1GB options. 2. The RFP indicates that you would like to replace the 5 2 nd
Addendum 1 Emerald Coast Convention & Visitor Bureau Website Development RFP TDD 87-17
 Addendum 1 Emerald Coast Convention & Visitor Bureau Website Development RFP TDD 87-17 This addendum is to answer the following questions: 1. Whether companies from Outside USA can apply for this? There
Addendum 1 Emerald Coast Convention & Visitor Bureau Website Development RFP TDD 87-17 This addendum is to answer the following questions: 1. Whether companies from Outside USA can apply for this? There
Cisco Cloud Architecture with Microsoft Cloud Platform Peter Lackey Technical Solutions Architect PSOSPG-1002
 Cisco Cloud Architecture with Microsoft Cloud Platform Peter Lackey Technical Solutions Architect PSOSPG-1002 Agenda Joint Cisco and Microsoft Integration Efforts Introduction to CCA-MCP What is a Pattern?
Cisco Cloud Architecture with Microsoft Cloud Platform Peter Lackey Technical Solutions Architect PSOSPG-1002 Agenda Joint Cisco and Microsoft Integration Efforts Introduction to CCA-MCP What is a Pattern?
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
ADDENDUM I REQUEST FOR PROPOSAL FOR WEBSITE ACCESSIBILITY COMPLIANCE October 12, 2018
 ADDENDUM I REQUEST FOR PROPOSAL FOR WEBSITE ACCESSIBILITY COMPLIANCE October 12, 2018 This addendum is separated into two sessions: (I) Questions received and answered, and (II) Questions that will be
ADDENDUM I REQUEST FOR PROPOSAL FOR WEBSITE ACCESSIBILITY COMPLIANCE October 12, 2018 This addendum is separated into two sessions: (I) Questions received and answered, and (II) Questions that will be
Verizon Software Defined Perimeter (SDP).
 Verizon Software Defined Perimeter (). 1 Introduction. For the past decade, perimeter security was built on a foundation of Firewall, network access control (NAC) and virtual private network (VPN) appliances.
Verizon Software Defined Perimeter (). 1 Introduction. For the past decade, perimeter security was built on a foundation of Firewall, network access control (NAC) and virtual private network (VPN) appliances.
OWASP RFP CRITERIA v 1.1
 OWASP RFP CRITERIA v 1.1 Project Sponsored by : ProactiveRisk. Table of Contents. 1. Introduction.3 2. Recommended Information the Client should provide to Service Providers/Vendors.4 2.1 Lines of Code..4
OWASP RFP CRITERIA v 1.1 Project Sponsored by : ProactiveRisk. Table of Contents. 1. Introduction.3 2. Recommended Information the Client should provide to Service Providers/Vendors.4 2.1 Lines of Code..4
Pre Bid Query Response. Request for Proposal for Procurement of Cloud Services
 S No Section Existing Clause Revised Clause 1 Section 4 Calendar of Last Date & Time for Bid Submission : 5 th May Last Date & Time for Bid Submission : events 2018 : 3:30 pm or before 30 th April : 4:00
S No Section Existing Clause Revised Clause 1 Section 4 Calendar of Last Date & Time for Bid Submission : 5 th May Last Date & Time for Bid Submission : events 2018 : 3:30 pm or before 30 th April : 4:00
ICBA Migration to IaaS Cloud Platform REQUEST FOR PROPOSAL
 INTERNATIONAL CENTER FOR BIOSALINE AGRICULTURE ICBA Migration to IaaS Cloud Platform REQUEST FOR PROPOSAL Imane Boujidane Procurement Officer +971 4 336 1100 ext. 201 i.boujidane@biosaline.org.ae International
INTERNATIONAL CENTER FOR BIOSALINE AGRICULTURE ICBA Migration to IaaS Cloud Platform REQUEST FOR PROPOSAL Imane Boujidane Procurement Officer +971 4 336 1100 ext. 201 i.boujidane@biosaline.org.ae International
MIS5206-Section Protecting Information Assets-Exam 1
 Your Name Date 1. Which of the following contains general approaches that also provide the necessary flexibility in the event of unforeseen circumstances? a. Policies b. Standards c. Procedures d. Guidelines
Your Name Date 1. Which of the following contains general approaches that also provide the necessary flexibility in the event of unforeseen circumstances? a. Policies b. Standards c. Procedures d. Guidelines
RFP No , Security Incident Event Monitoring (SIEM) Management Services
 BOARD OF EDUCATION Linda P. Bryant, President Linda McCain, Vice President Julia C. Bernath Gail Dean Kimberly Dove Katie Reeves Katha Stuart Jeff Rose, Ed. D., Superintendent DATE: March 6, 2018 TO: FROM:
BOARD OF EDUCATION Linda P. Bryant, President Linda McCain, Vice President Julia C. Bernath Gail Dean Kimberly Dove Katie Reeves Katha Stuart Jeff Rose, Ed. D., Superintendent DATE: March 6, 2018 TO: FROM:
Request for Qualifications for Audit Services March 25, 2015
 Request for Qualifications for Audit Services March 25, 2015 I. GENERAL INFORMATION A. Purpose This Request for Qualifications (RFQ) is to solicit a CPA firm with which to contract for a financial and
Request for Qualifications for Audit Services March 25, 2015 I. GENERAL INFORMATION A. Purpose This Request for Qualifications (RFQ) is to solicit a CPA firm with which to contract for a financial and
REQUEST FOR PROPOSALS FOR WEBSITE REDESIGN
 REQUEST FOR PROPOSALS FOR WEBSITE REDESIGN Issued: May 3, 2012 Proposals Due: May 31, 2012, 3:00 pm Monica Devincenzi RethinkWaste Recycling Outreach & Sustainability Manager 610 Elm Street, Suite 202
REQUEST FOR PROPOSALS FOR WEBSITE REDESIGN Issued: May 3, 2012 Proposals Due: May 31, 2012, 3:00 pm Monica Devincenzi RethinkWaste Recycling Outreach & Sustainability Manager 610 Elm Street, Suite 202
REQUEST FOR PROPOSALS
 REQUEST FOR PROPOSALS January 15, 2015 Electronic Catalog Management System Project 2014-2015 Due 2:00 PM CST/CDT Friday, February 6, 2015 Company Name: Contact Information: Printed Name & Title E-mail
REQUEST FOR PROPOSALS January 15, 2015 Electronic Catalog Management System Project 2014-2015 Due 2:00 PM CST/CDT Friday, February 6, 2015 Company Name: Contact Information: Printed Name & Title E-mail
Metropolitan Washington Airports Authority PROCUREMENT AND CONTRACTS DEPT. AMENDMENT OF SOLICITATION
 Metropolitan Washington Airports Authority PROCUREMENT AND CONTRACTS DEPT. AMENDMENT OF SOLICITATION Metropolitan Washington Airports Authority Procurement and Contracts Dept., MA-29 2733 Crystal Drive
Metropolitan Washington Airports Authority PROCUREMENT AND CONTRACTS DEPT. AMENDMENT OF SOLICITATION Metropolitan Washington Airports Authority Procurement and Contracts Dept., MA-29 2733 Crystal Drive
ADDENDUM NO. 1 TO THE BID DOCUMENTS FOR VOICE OVER IP SYSTEM September 16, 2014
 ADDENDUM NO. 1 TO THE BID DOCUMENTS FOR VOICE OVER IP SYSTEM September 16, 2014 This Addendum No. 1 is issued in connection with the above described Bid Documents. The Louisville Regional Airport Authority,
ADDENDUM NO. 1 TO THE BID DOCUMENTS FOR VOICE OVER IP SYSTEM September 16, 2014 This Addendum No. 1 is issued in connection with the above described Bid Documents. The Louisville Regional Airport Authority,
Managed Security Services RFP 2019 Q&A
 Managed Security Services RFP 2019 Q&A 1. EPS count. 150 EPS seems low (our minimum deal size is for 1,000 EPS). If we can get a detailed list of the equipment in scope for the SIEM, we can determine if
Managed Security Services RFP 2019 Q&A 1. EPS count. 150 EPS seems low (our minimum deal size is for 1,000 EPS). If we can get a detailed list of the equipment in scope for the SIEM, we can determine if
ArcGIS in the Cloud. Andrew Sakowicz & Alec Walker
 ArcGIS in the Cloud Andrew Sakowicz & Alec Walker Key Takeaways How to Identify Organizational Strategy & Priorities Esri s Cloud Offerings A Broad Spectrum Successfully Executing Your Strategy The Cloud
ArcGIS in the Cloud Andrew Sakowicz & Alec Walker Key Takeaways How to Identify Organizational Strategy & Priorities Esri s Cloud Offerings A Broad Spectrum Successfully Executing Your Strategy The Cloud
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
NERC CIP VERSION 6 BACKGROUND COMPLIANCE HIGHLIGHTS
 NERC CIP VERSION 6 COMPLIANCE BACKGROUND The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Reliability Standards define a comprehensive set of requirements
NERC CIP VERSION 6 COMPLIANCE BACKGROUND The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Reliability Standards define a comprehensive set of requirements
Level 3 Certificate in Cloud Services (for the Level 3 Infrastructure Technician Apprenticeship) Cloud Services
 9628-08 Level 3 Certificate in Cloud Services (for the Level 3 Infrastructure Technician Apprenticeship) 9628-808 Cloud Services Sample question paper Duration: 60 minutes Candidate s name: Candidate s
9628-08 Level 3 Certificate in Cloud Services (for the Level 3 Infrastructure Technician Apprenticeship) 9628-808 Cloud Services Sample question paper Duration: 60 minutes Candidate s name: Candidate s
How Cyber-Criminals Steal and Profit from your Data
 How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
Table of Contents Table of Contents...2 Introduction...3 Mission of IT...3 Primary Service Delivery Objectives...3 Availability of Systems...
 Table of Contents Table of Contents...2 Introduction...3 Mission of IT...3 Primary Service Delivery Objectives...3 Availability of Systems...3 Improve Processes...4 Innovation...4 IT Planning & Alignment
Table of Contents Table of Contents...2 Introduction...3 Mission of IT...3 Primary Service Delivery Objectives...3 Availability of Systems...3 Improve Processes...4 Innovation...4 IT Planning & Alignment
Regulation P & GLBA Training
 Regulation P & GLBA Training Overview Regulation P governs the treatment of nonpublic personal information about consumers by the financial institution. (Gramm-Leach-Bliley Act of 1999) The GLBA is composed
Regulation P & GLBA Training Overview Regulation P governs the treatment of nonpublic personal information about consumers by the financial institution. (Gramm-Leach-Bliley Act of 1999) The GLBA is composed
AppPulse Point of Presence (POP)
 AppPulse Point of Presence Micro Focus AppPulse POP service is a remotely delivered solution that provides a managed environment of Application Performance Management. AppPulse POP service supplies real-time
AppPulse Point of Presence Micro Focus AppPulse POP service is a remotely delivered solution that provides a managed environment of Application Performance Management. AppPulse POP service supplies real-time
Solicitation NUES Next Generation Firewall RFP. Bid designation: Public
 Solicitation 2014-1 NUES Next Generation Firewall RFP Bid designation: Public Northeastern Utah 4/17/2014 2:07 PM p. 1 Bid Number 2014-1 Bid Title NUES Next Generation Firewall RFP NUES Next Generation
Solicitation 2014-1 NUES Next Generation Firewall RFP Bid designation: Public Northeastern Utah 4/17/2014 2:07 PM p. 1 Bid Number 2014-1 Bid Title NUES Next Generation Firewall RFP NUES Next Generation
Telecommunications RFP 02. for. North Country Telemedicine Project (NCTP) Network
 Telecommunications RFP 02 for North Country Telemedicine Project (NCTP) Network TABLE OF CONTENTS 1. PROJECT OVERVIEW 2. PROJECT ADMINISTRATION 3. TECHNICAL REQUIREMENTS 4. PROJECT MANAGEMENT REQUIREMENTS
Telecommunications RFP 02 for North Country Telemedicine Project (NCTP) Network TABLE OF CONTENTS 1. PROJECT OVERVIEW 2. PROJECT ADMINISTRATION 3. TECHNICAL REQUIREMENTS 4. PROJECT MANAGEMENT REQUIREMENTS
Contents. 1 General Terms. Page 1 of 8
 Page 1 of 8 Service Description: Advanced Services --- Fixed Price Secure Agile Exchange Advise and Implement (Quick Start) (ASF-CORE-SAI-QS) This document describes Cisco s Secure Agile Exchange Advise
Page 1 of 8 Service Description: Advanced Services --- Fixed Price Secure Agile Exchange Advise and Implement (Quick Start) (ASF-CORE-SAI-QS) This document describes Cisco s Secure Agile Exchange Advise
Digital Advisory Services Professional Service Description SIP SBC with Field Trial Endpoint Deployment Model
 Digital Advisory Services Professional Service Description SIP SBC with Field Trial Endpoint Deployment Model 1. Description of Services. 1.1 SIP SBC with Field Trial Endpoint Deployment Verizon will assist
Digital Advisory Services Professional Service Description SIP SBC with Field Trial Endpoint Deployment Model 1. Description of Services. 1.1 SIP SBC with Field Trial Endpoint Deployment Verizon will assist
12,000+ Associates. Worldwide. Worldwide. 36 Countries. Customer Base 230+ Infra Supported Data Centers. 300,000+ End Users.
 Tech Mahindra IT Infrastructure Management Services (IMS) offers a suite of reliable, responsive, flexible and proven Infrastructure services and solutions that deliver differentiated value to our customers
Tech Mahindra IT Infrastructure Management Services (IMS) offers a suite of reliable, responsive, flexible and proven Infrastructure services and solutions that deliver differentiated value to our customers
PISMO BEACH COUNCIL AGENDA REPORT
 PISMO BEACH COUNCIL AGENDA REPORT SUBJECT/TITLE: REVIEW OF INFORMATION TECHNOLOGY (IT) STATUS AND IT STRATEGIC PLAN IMPLEMENTATION UPDATE. RECOMMENDATION: 1. Receive the IT Status and Implementation Update.
PISMO BEACH COUNCIL AGENDA REPORT SUBJECT/TITLE: REVIEW OF INFORMATION TECHNOLOGY (IT) STATUS AND IT STRATEGIC PLAN IMPLEMENTATION UPDATE. RECOMMENDATION: 1. Receive the IT Status and Implementation Update.
ADDENDUM 1 April 13, 2018 Request for Proposals: Professional Services for Server Backup Solution
 Following are the questions submitted on or before April 6, 2018, in accordance with RFP specifications. All questions are published verbatim as received, without regard to errors in spelling, punctuation,
Following are the questions submitted on or before April 6, 2018, in accordance with RFP specifications. All questions are published verbatim as received, without regard to errors in spelling, punctuation,
Grant Parish School Board 512 Main Street P.O. Box 208 Colfax, LA 71417
 Grant Parish School Board 512 Main Street P.O. Box 208 Colfax, LA 71417 Request for Proposals Wireless Network Upgrade and Expansion Grant Parish School Board (GPSB) is soliciting proposals for the products/services
Grant Parish School Board 512 Main Street P.O. Box 208 Colfax, LA 71417 Request for Proposals Wireless Network Upgrade and Expansion Grant Parish School Board (GPSB) is soliciting proposals for the products/services
Request for Proposal for Technical Consulting Services
 Request for Proposal for Technical Consulting Services The Node.js Foundation is requesting proposals from highly qualified consultants with demonstrated expertise in providing Node.js technical consultation
Request for Proposal for Technical Consulting Services The Node.js Foundation is requesting proposals from highly qualified consultants with demonstrated expertise in providing Node.js technical consultation
REQUEST FOR BID August 3, 2013
 REQUEST FOR BID August 3, 2013 Fluke OneTouch AT 1T-3000 Bundle Project 2013-2014 Due 10:00 AM CDT/CST Monday, August 19, 2013 Company Name: Contact Information: Printed Name & Title Phone Number *Please
REQUEST FOR BID August 3, 2013 Fluke OneTouch AT 1T-3000 Bundle Project 2013-2014 Due 10:00 AM CDT/CST Monday, August 19, 2013 Company Name: Contact Information: Printed Name & Title Phone Number *Please
Securing Privileged Access Securing High Value Assets Datacenter Security Information Protection Information Worker and Device Protection
 Securing Privileged Access Securing High Value Assets Datacenter Security Information Protection Information Worker and Device Protection Azure Active Directory 3 rd Party IaaS IaaS Rights Management Services
Securing Privileged Access Securing High Value Assets Datacenter Security Information Protection Information Worker and Device Protection Azure Active Directory 3 rd Party IaaS IaaS Rights Management Services
1. Click on "IaaS" to advance to the Windows Azure Scenario. 2. Click to configure the "CloudNet" Virtual Network
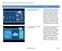 Introduction to the Virtual Network Lab Scenario Steps Description 1. Click on "IaaS" to advance to the Windows Azure Scenario Windows Azure Infrastructure Services ( IaaS ) provides us with the capability
Introduction to the Virtual Network Lab Scenario Steps Description 1. Click on "IaaS" to advance to the Windows Azure Scenario Windows Azure Infrastructure Services ( IaaS ) provides us with the capability
Lincoln County, Georgia. Office 365 & Antivirus
 Lincoln County, Georgia November 16, 2018 Office 365 & Antivirus Invitation for Bid RFP 18-006 The Lincoln County Board of Commissioners is requesting bids for migration to, and implementation of, the
Lincoln County, Georgia November 16, 2018 Office 365 & Antivirus Invitation for Bid RFP 18-006 The Lincoln County Board of Commissioners is requesting bids for migration to, and implementation of, the
10 Cloud Myths Demystified
 10 Cloud s Demystified The Realities for Digital Healthcare Transformation It s a challenging time for the healthcare industry, with changing regulations, consolidation and the consumerization of healthcare
10 Cloud s Demystified The Realities for Digital Healthcare Transformation It s a challenging time for the healthcare industry, with changing regulations, consolidation and the consumerization of healthcare
