Windows 7 Users, Groups and Security
|
|
|
- Doreen Lewis
- 5 years ago
- Views:
Transcription
1 U indows Users, Groups and ecurity P P onna arren
2 nstalling opics for this Unit Homegroups, workgroups, and domains reate user and group accounts User Account ontrol panel User authentication and authorization Malware Protection for sensitive data P P onna arren
3 User Accounts dentify users to the system and to each other Allow authentication proving they are who they say they are Allow authorization - used to grant access to resources such as iles and printers omputer systems etwork esources elegation of authority ollect information about users P P onna arren
4 Local User Accounts reated on workstations and servers that are not either members of a domain or domain controllers Provides access to the local computer through user rights and access permissions eside in the local security database called the security access manager (AM) You can logon to local machine or the domain but they are mutually exclusive P P onna arren
5 User ights versus Permissions Permissions - define what objects a user is allowed to access and what actions they can perform on an object such as modify on a file or print on a printer User rights - define what actions a user can take on the operating system such as shut down the system or take ownership of an object P P onna arren
6 Account Properties Logon is mandatory User length 20 characters max, blank allowed nvalid user characters - \ / [ ] : ;,. + *? < > User s AE case sensitive Passwords AE AE EVE Password complexity use uppercase, lowercase and numbers or symbols an enforce with group policy P P onna arren
7 Built-in Local User Accounts onfigured during setup Accounts that can log on interactively Administrator basically the computer god or goddess Guest provides limited access and is disabled by default ew User Account - Built-in accounts can be renamed but not deleted ystem Account used by the operating system has full control access and all assignable user rights by default but cannot logon interactively P P onna arren
8 ther Accounts ervice Accounts - Grant services access to system resources ervice used by the operating system Local ervice used by local services etwork ervice used by network services ncluded built-in and user-defined accounts APE used by asp.net services U_computer-name anonymous user account for the web server AM_computer-name account used to run threads for and AP.net P P onna arren
9 Managing Local Users omputer Management ontrol Panel user Accounts et.exe command P P onna arren
10 User Accounts ontrol Panel ntended for users with less experience implified interface Limited access annot create or manage groups P P onna arren
11 User Profiles Profiles are configuration files that store all of the users preferences Local user profile stored locally and applies to the local machine only oaming user profile stored on a server and applies to any machine that logs into the domain Mandatory user profile has to be used by the user when they logon P P onna arren
12 User Account ontrol (UA) ecurity measure to prevent users from always being logged on as an administrator Administrators are issued two access tokens 1 standard token 1 administrative token Best Practice is to logon as a standard user Use the runas command to perform administrative tasks P P onna arren
13 Performing Administrative asks tandard User Account - ystem displays a credential prompt where administrative account information must be entered Administrative Account - witches from standard user token to administrative token Generates an elevation prompt P P onna arren
14 onfiguring User Account ontrol P P onna arren
15 ached redentials an store domain credentials locally to allow logon when the domain controller is not available P P onna arren
16 Groups ollections of user accounts implify access to resources Members receive permissions given to the groups of which they are members Users can be members of multiple groups Groups can be members of other groups (called nested groups) an be used for security and messaging in Active irectory P P onna arren
17 Built-in Local Groups Built-in groups cannot be removed but can be renamed Administrators have all user rights and access permissions Backup perators can bypass security to backup files Power Users have limited administrative permissions and rights emote esktop Users allowed to connect to others using remote desktop Users all new account are added to users by default Guests group with very limited and usually temporary access P P onna arren
18 mplicit Groups Membership can change dynamically etermined by the user s activities Used to grant permissions based on circumstances o not appear in user administration tools nteractive all users logged on locally etwork all users who access the system over a etwork Everyone includes absolutely everyone Authenticated Users been authenticated by system s security manager reator wner the user who creates an object P P onna arren
19 Using Local Groups Valid only on the computer where you create them nly local users from the same computer can be members of local groups. hen the computer is a member of an A domain, local groups can have domain users and domain global groups as members. Local groups cannot have other local groups as members. However, they can have domain groups as members. You can only assign permissions to local groups when you are controlling access to resources on the local computer. You cannot create local groups on a indows server computer that is functioning as a domain controller. P P onna arren
20 ecurity Boundaries P P onna arren
21 Homegroup implified networking Allows users on a home network to share the contents of their libraries without creating user accounts and permissions on each of the other machines P P onna arren
22 Peer-to-peer network Each computer can function as both a server and a client Each computer has its own set of users and groups to control access to its own resources mall networks only Very little security required orkgroup P P onna arren
23 Active irectory omain ollection of computers that utilize a central directory service for authentication and authorization At least one omain ontroller is required P P onna arren
24 omain Accounts Added when a computer joins a domain omain Admins placed in administrators group by default when the computer joins a domain omain Users allows domain users to have the same access permissions as local users omain Guests member of local guest group Provide logon and resource access to local system an be placed into other local groups as well P P onna arren
25 Users Best Account Practices Place users into groups reate a standard naming convention Accounts Give administrators a limited account for non administrative use Limit the number Administrators ename or disable the Administrator account ename and leave the Guest account disabled bserve the principle of least privilege P P onna arren
26 he nternet he nternet - A global network connecting thousands of individual networks and millions of users by means of the P/P protocol nternet - a web based network connecting separate individual networks ntranet - a web based internal network used within a single company Both internet and intranets are accessed using web browsers P P onna arren
27 nternet erminology orld ide eb () - he nternet Hypertext ransport Protocol (HP) A communications protocol that obtains HML formatted documents and that works with P to transport files over the nternet supports HP through windows socket services (winsock) Hypertext Markup Language (HML) programming language used to read and enable documents and graphics images on the orld ide eb P P onna arren
28 eb Browser eb browser - oftware used to communicate with eb sites Uniform esource Locator (UL) A convention for locating an nternet site Private virtual network - An intranet that basically tunnels though the nternet to provide secure network access for individual organizations P P onna arren
29 Microsoft nternet ools nternet Assistant - orks within ord to format a document with HML tags and to save document as a text file rontpage - ull-scale eb site development tool Microsoft nternet Explorer - Microsoft's free web browser Microsoft nternet nformation erver - Microsoft's web server shipped with all versions of windows but not installed P P onna arren
30 eatures runs as a service on windows upports all HP protocol features an be administered over the internet Provides all of the operating system security features to web pages an restrict server bandwidth allocated to web services P P onna arren
31 ecurity P P onna arren
32 Authentication Authentication is the process of proving who you are here are several common methods of authentication hat you know (password or P) ho you are (retinal scan or thumb print) hat you have (smart card) ome of these methods can be used so that users no longer need to remember passwords P P onna arren
33 hould be trong Passwords At least eight characters in length ontain uppercase, lowercase letters, and numbers or symbols ifferent from other previously used passwords an be up to 12 characters in length hould EVE be Blank Your user name or real name hildren s or pet s names ompany name A complete dictionary word P P onna arren
34 Local ecurity Policy Used on individual computers to enforce restrictions P P onna arren
35 Password Policy Used to enforce good password security practices P P onna arren
36 Account Lockout Policies P P onna arren
37 redential Manager tores usernames and passwords for servers and eb sites in the indows Vault emember my credentials checkbox adds credentials to the indows Vault P P onna arren
38 mart ards Users no longer have to remember passwords ince stored on smart card, user ids and passwords are hard to steal ecurity operations such as cryptographic functions are performed on the smart card, rather than on the network server or local computer an be used from remote locations to provide authentication services Brute force attacks are usually less successful P P onna arren
39 Using Biometrics cans a physical characteristic of a user to confirm identity ingerprints humbprint etina indows Biometric ramework provides core biometric functionality and a Biometric evice control panel P P onna arren
40 ertificates Used for authentication tasks nternally n the local network n the nternet indows automatically maintains a certificate store for each Users can manage their certificate stores directly using the ertificates snap-in P P onna arren
41 ertificate Manager P P onna arren
42 Elevating Privileges Use un As Administrator context menu option Use command line runas.exe command: runas /user:dpw\administrator notepad.exe P P onna arren
43 ommon Problems Password lost or forgotten - the most common problem Passwords are encrypted which makes them unrecoverable Passwords must be reset Users can change their own password if they know their old password Administrators can reset password without supplying the old password A Password reset isk is a better option P P onna arren
44 Authorization Authorization grants the user access to resources or allows specific actions Permissions - define what objects a user is allowed to access and what actions they can perform on an object such as modify on a file or print on a printer User rights - define what actions a user can take on the operating system such as shut down the system or take ownership of an object P P onna arren
45 Malware Malicious software created specifically for the purpose of infiltrating or damaging a computer system without the user s knowledge or consent Viruses self replicating files that need an executable to spread themselves to other computers rojan horses designed to collect user ids, passwords orms self replicating program that does not need assistance to replicate pyware designed to steal private user information such as credit card numbers, etc. Adware designed to collect information on a users web surfing habits P P onna arren
46 Action enter tarts and runs automatically, to provide automatic notifications to alert the user of security vulnerabilities P P onna arren
47 ntroducing indows irewall A software program that protects a computer by opening or closing logical ports based on P addresses - pecific computers Protocol numbers - ransport layer protocol Port number - Application running on computer ules are used to filter traffic Admit all traffic, except that which applies to the rules Block all traffic, except that which applies to the rules P P onna arren
48 indows irewall P P onna arren
49 indows irewall Advanced ecurity efault profile settings can be modified nbound and outbound rules can be created P P onna arren
50 indows efender P P onna arren
51 Malicious oftware emoval ool A single user virus scanner supplied with monthly updates emoves any potentially damaging software it finds here are no controls and is not permanently installed hould install a full-featured antivirus program on indows P P onna arren
52 Encrypting ile ystem (E) E is a feature of that encrypts files on a computer he system is keyed to a specific user account. Uses public key encryption (PK). he user who creates the file is the only person who can read it. P P onna arren
53 Parental ontrols Enable parents to limit their children s access to specific nternet sites, games, and applications Based on user accounts Every family member must have their own account mpose restrictions on accounts ilter eb sites users are allowed to access Limit downloads from nternet sites Enforce time limits for computer use estrict access to games by rating, content, or title Allow or block specific applications P P onna arren
54 ummary User accounts help manage resource access User groups simplify administration. aming conventions uniquely identify users omplex passwords strengthen security ached credentials allow access when the domain is unavailable A workgroup is a collection of computers that are all peers, and can act as a client or server A domain is a collection of computers that all utilize a central directory service for authentication and authorization P P onna arren
55 ummary Built-in local groups are equipped with the permissions and rights needed to perform certain tasks. indows provides two separate interfaces for creating and managing local user accounts: the User Accounts control panel and the Local Users and Group snap-in he three profile types are local, roaming, and mandatory User Account ontrol (UA) allows an administrative user to perform regular user tasks as a standard user, and switches to an administrative token to perform administrative tasks P P onna arren
56 ummary Password Policies - enforce password security practices redential Manager - tool that stores the user names and passwords in a indows Vault. Permissions and user rights are used to authorize users access to resources and tasks Action enter - a centralized console used to configure indows security indows irewall - protects a computer by opening and closing logical ports indows efender - helps to defend against spyware he Malicious oftware emoval ool - a single user virus scanner he Encrypting ile ystem (E) encrypts files on the hard drive P P onna arren
57 EM reating Users & Groups Managing Users Assigning User ights Policies Joining a domain P P onna arren
58 Lab reate Users and Groups Join a omain Assign User right nstall nternet nformation ervice ownload and install Malware bytes ownload and install Avg antivirus program onfigure windows firewall P P onna arren
Introduction to Active Directory
 UT ntroduction to Active irectory 5-1 Topics for this Unit irectory ervices Active irectory Forests omains rganizational Units Groups A features ites Accounts 5-1 irectory ervice A directory service is
UT ntroduction to Active irectory 5-1 Topics for this Unit irectory ervices Active irectory Forests omains rganizational Units Groups A features ites Accounts 5-1 irectory ervice A directory service is
Remote Access, VPNs and Terminal Services
 U 7 emote Access, s and erminal ervices onna arren 5-1 opics for this Unit emote Administration MMs elegation of authority A (outing and emote Access) (irtual rivate etwork) erminal erver H relay agent
U 7 emote Access, s and erminal ervices onna arren 5-1 opics for this Unit emote Administration MMs elegation of authority A (outing and emote Access) (irtual rivate etwork) erminal erver H relay agent
Updating The Operating System & User Accounts
 U Updating he perating ystem & User Accounts P PAG YM UPA Update A minor revision to a software product, usually intended to address specific performance issues rather than add new features Upgrade A major
U Updating he perating ystem & User Accounts P PAG YM UPA Update A minor revision to a software product, usually intended to address specific performance issues rather than add new features Upgrade A major
C UNIT 4. Active Directory User Accounts
 UN 4 Active irectory User Accounts 2005-2010 efinitions User individual granted access to the system with the following User properties Groups associated with the user Profile path Login script Home directory
UN 4 Active irectory User Accounts 2005-2010 efinitions User individual granted access to the system with the following User properties Groups associated with the user Profile path Login script Home directory
Administering Windows Server 2003 & Data Backup
 U Administering indows erver & ata Backup P oday s opics Manage a indows erver system using MMC Access a remote computer using an MMC console Configure a server to enable emote esktop for Administration
U Administering indows erver & ata Backup P oday s opics Manage a indows erver system using MMC Access a remote computer using an MMC console Configure a server to enable emote esktop for Administration
M C I T P UNIT 9 W I N D O W S. Virtualization S E R V E R. DPW Donna Warren DPW
 U 9 irtualization onna arren 5-1 opics for this Unit erver virtualization Advantages and disadvantages of virtual servers Features and requirements of Microsoft Hyper- nstall Hyper- Guest operating systems
U 9 irtualization onna arren 5-1 opics for this Unit erver virtualization Advantages and disadvantages of virtual servers Features and requirements of Microsoft Hyper- nstall Hyper- Guest operating systems
Windows Server 2012 r2
 indows erver r P P onna arren 5- onna P. arren ducation A Accounting B lectrical ngineering M Computer cience ork xperience years as Telecommunications etwork ngineer and owner of a small T consulting
indows erver r P P onna arren 5- onna P. arren ducation A Accounting B lectrical ngineering M Computer cience ork xperience years as Telecommunications etwork ngineer and owner of a small T consulting
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
File and Print Services
 UT 5 File and Print ervices onna arren 5-1 Topics for this Unit File ervers File ystems Physical Hard isks irtual Hard disks istributed File system Printing ervices onna arren 5-1 TF File ystem onna arren
UT 5 File and Print ervices onna arren 5-1 Topics for this Unit File ervers File ystems Physical Hard isks irtual Hard disks istributed File system Printing ervices onna arren 5-1 TF File ystem onna arren
MU2a Authentication, Authorization & Accounting Questions and Answers with Explainations
 98-367 MU2a Authentication, Authorization & Accounting Questions and Answers with Explainations Which are common symptoms of a virus infection? (Lesson 5 p 135-136) Poor system performance. Unusually low
98-367 MU2a Authentication, Authorization & Accounting Questions and Answers with Explainations Which are common symptoms of a virus infection? (Lesson 5 p 135-136) Poor system performance. Unusually low
UNIT 2. Internet Information Server
 UIT 2 Internet Information erver Topics in this Unit xamine the features in II7 reate web site content Install, configure an II site ublish an II Web site onfigure web site security The Internet The Internet
UIT 2 Internet Information erver Topics in this Unit xamine the features in II7 reate web site content Install, configure an II site ublish an II Web site onfigure web site security The Internet The Internet
Configuring Windows Security Features
 04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
Lesson 3: Identifying Key Characteristics of Workgroups and Domains
 1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
Activity 1: Using Windows XP Professional Security Checklist
 Activity 1: Using Windows XP Professional Security Checklist Verify that all Disk partitions are Formatted with NTFS NTFS partitions offer access controls and protections that aren't available with the
Activity 1: Using Windows XP Professional Security Checklist Verify that all Disk partitions are Formatted with NTFS NTFS partitions offer access controls and protections that aren't available with the
C UNIT 3. Global Catalog & Flexible Single Master Operations (FSMO)
 UN 3 Global atalog & Flexible Single Master perations (FSM) PW PW onna Warren 2005-2010 opics for this Unit Functions of the Global atalog Functions of Universal Group Membership aching he Five FSM roles
UN 3 Global atalog & Flexible Single Master perations (FSM) PW PW onna Warren 2005-2010 opics for this Unit Functions of the Global atalog Functions of Universal Group Membership aching he Five FSM roles
Windows Server 2008 Security
 UT 11 indows erver ecurity 5-1 hat is Group Policy? A group of policies applied directly to Active irectory bjects Policies can be linked to: ites omains Us Policies are applied by assigning them to the
UT 11 indows erver ecurity 5-1 hat is Group Policy? A group of policies applied directly to Active irectory bjects Policies can be linked to: ites omains Us Policies are applied by assigning them to the
5 MANAGING USER ACCOUNTS AND GROUPS
 MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
Recent Operating System Class notes 04 Managing Users on Windows XP March 22, 2004
 Recent Operating System Class notes 04 Managing Users on Windows XP March 22, 2004 You log into a system to notify the system who you are. When you log off, any files you have opened are cleaned up, and
Recent Operating System Class notes 04 Managing Users on Windows XP March 22, 2004 You log into a system to notify the system who you are. When you log off, any files you have opened are cleaned up, and
SERVER HARDENING CHECKLIST
 SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
C UNIT 7. Using Group Policy
 UN 7 Using Group Policy 2005-2010 opics for this Unit Group policy security settings Audit policies in Windows Server 2008 Folder redirection Managing software using Group Policy he software life cycle
UN 7 Using Group Policy 2005-2010 opics for this Unit Group policy security settings Audit policies in Windows Server 2008 Folder redirection Managing software using Group Policy he software life cycle
ClientNet. Portal Admin Guide
 ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
8 Administering Groups
 8 Administering Groups Exam Objectives in this Chapter: Plan a security group hierarchy based on delegation requirements. Plan a security group strategy. Why This Chapter Matters As an administrator, you
8 Administering Groups Exam Objectives in this Chapter: Plan a security group hierarchy based on delegation requirements. Plan a security group strategy. Why This Chapter Matters As an administrator, you
Managing & Supporting Windows XP
 UI 9 Managing & Supporting Windows X Definitions User - individual granted access to the system roups - logical collection of users Accounts - ogical construct containing all information that defines a
UI 9 Managing & Supporting Windows X Definitions User - individual granted access to the system roups - logical collection of users Accounts - ogical construct containing all information that defines a
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003
 Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
Pass Microsoft Exam
 Pass Microsoft 98-367 Exam Number: 98-367 Passing Score: 700 Time Limit: 45 min File Version: 51.0 http://www.gratisexam.com/ Pass Microsoft 98-367 Exam Exam Name: Security Fundamentals Certdumps QUESTION
Pass Microsoft 98-367 Exam Number: 98-367 Passing Score: 700 Time Limit: 45 min File Version: 51.0 http://www.gratisexam.com/ Pass Microsoft 98-367 Exam Exam Name: Security Fundamentals Certdumps QUESTION
12 Habits of Highly Secured Magento Merchants
 12 Habits of Highly Secured Magento Merchants Jeries (Jerry) Eadeh VP of Channel Sales 5 years at Nexcess Speaker at Magento Events Small business owner @ibnwadie Have you ever left the doors unlocked?
12 Habits of Highly Secured Magento Merchants Jeries (Jerry) Eadeh VP of Channel Sales 5 years at Nexcess Speaker at Magento Events Small business owner @ibnwadie Have you ever left the doors unlocked?
Managing and Maintaining Windows 8
 Managing and Maintaining Windows 8 Number: 070-688 Passing Score: 700 Time Limit: 120 min File Version: 1.0 http://www.gratisexam.com/ All questions are taken from demo PDF files at: - Test4Actual - PassFine
Managing and Maintaining Windows 8 Number: 070-688 Passing Score: 700 Time Limit: 120 min File Version: 1.0 http://www.gratisexam.com/ All questions are taken from demo PDF files at: - Test4Actual - PassFine
Getting Started Guide. This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software.
 Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Identity & Access Management
 Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
COPYRIGHTED MATERIAL. Contents. Part I: The Basics in Depth 1. Chapter 1: Windows Attacks 3. Chapter 2: Conventional and Unconventional Defenses 51
 Acknowledgments Introduction Part I: The Basics in Depth 1 Chapter 1: Windows Attacks 3 Attack Classes 3 Automated versus Dedicated Attacker 4 Remote versus Local 7 Types of Attacks 8 Dedicated Manual
Acknowledgments Introduction Part I: The Basics in Depth 1 Chapter 1: Windows Attacks 3 Attack Classes 3 Automated versus Dedicated Attacker 4 Remote versus Local 7 Types of Attacks 8 Dedicated Manual
The Microsoft Windows. User Interface
 U 7 he icrosoft Windows User nterface he Desktop nterface Desktop tart button askbar otification and system ray area Desktop Components tart button Contains access menus to applications, data folders,
U 7 he icrosoft Windows User nterface he Desktop nterface Desktop tart button askbar otification and system ray area Desktop Components tart button Contains access menus to applications, data folders,
RSA Authentication Manager 8.0 Security Configuration Guide
 RSA Authentication Manager 8.0 Security Configuration Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
RSA Authentication Manager 8.0 Security Configuration Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
User Guide. Version R94. English
 AuthAnvil User Guide Version R94 English March 8, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated
AuthAnvil User Guide Version R94 English March 8, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated
CS 356 Operating System Security. Fall 2013
 CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
Faculty of Engineering Computer Engineering Department Islamic University of Gaza Network Lab # 5 Managing Groups
 Faculty of Engineering Computer Engineering Department Islamic University of Gaza 2012 Network Lab # 5 Managing Groups Network Lab # 5 Managing Groups Objective: Learn about groups and where to create
Faculty of Engineering Computer Engineering Department Islamic University of Gaza 2012 Network Lab # 5 Managing Groups Network Lab # 5 Managing Groups Objective: Learn about groups and where to create
Tennessee Technological University Policy No Password Management
 Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
O UNIT 5. Testing, Auditing & Monitoring
 5 esting, uditing & onitoring opics for his nit ole of an audit in effective security baselining and gap analysis mportance of monitoring systems throughout the infrastructure Penetration testing and ethical
5 esting, uditing & onitoring opics for his nit ole of an audit in effective security baselining and gap analysis mportance of monitoring systems throughout the infrastructure Penetration testing and ethical
Contents. Introduction 5. McAfee SecurityCenter 7. McAfee QuickClean 39. McAfee Shredder 45
 User Guide i Contents Introduction 5 McAfee SecurityCenter 7 Features... 8 Using SecurityCenter... 9 Header... 9 Left column... 9 Main pane... 10 Understanding SecurityCenter icons... 11 Understanding
User Guide i Contents Introduction 5 McAfee SecurityCenter 7 Features... 8 Using SecurityCenter... 9 Header... 9 Left column... 9 Main pane... 10 Understanding SecurityCenter icons... 11 Understanding
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Managing NCS User Accounts
 7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 10 Security Essentials
 : Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Security Essentials Objectives Learn why it is important to comply with established security policies Learn ways to authenticate and classify
: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Security Essentials Objectives Learn why it is important to comply with established security policies Learn ways to authenticate and classify
Authentication, Authorization, and Accounting
 Authentication, Authorization, and Accounting LESSON 2 OBJECTIVE DOMAIN MATRIX SKILLS/CONCEPTS MTA EXAM OBJECTIVE MTA EXAM OBJECTIVE NUMBER Starting Security with Understand user authentication. 2.1 Authentication
Authentication, Authorization, and Accounting LESSON 2 OBJECTIVE DOMAIN MATRIX SKILLS/CONCEPTS MTA EXAM OBJECTIVE MTA EXAM OBJECTIVE NUMBER Starting Security with Understand user authentication. 2.1 Authentication
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Introduction to Security in Laserfiche 8.3 and later. White Paper
 Introduction to Security in Laserfiche 8.3 and later White Paper November 2013 Table of Contents Authentication and Authorization... 4 Authentication... 4 Windows Accounts and LDAP... 5 Laserfiche Trustees...
Introduction to Security in Laserfiche 8.3 and later White Paper November 2013 Table of Contents Authentication and Authorization... 4 Authentication... 4 Windows Accounts and LDAP... 5 Laserfiche Trustees...
a. UTRGV owned, leased or managed computers that fall within the regular UTRGV Computer Security Standard
 Kiosk Security Standard 1. Purpose This standard was created to set minimum requirements for generally shared devices that need to be easily accessible for faculty, staff, students, and the general public,
Kiosk Security Standard 1. Purpose This standard was created to set minimum requirements for generally shared devices that need to be easily accessible for faculty, staff, students, and the general public,
Password Reset PRO INSTALLATION GUIDE
 Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. January 2009
Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. January 2009
CISNTWK-11. Microsoft Network Server. Chapter 4
 CISNTWK-11 Microsoft Network Server Chapter 4 User and Group Accounts 1 Usage Notes Throughout these slides, the term Active Directory Domain implies Domains Based on Windows Server 2008 Based on Windows
CISNTWK-11 Microsoft Network Server Chapter 4 User and Group Accounts 1 Usage Notes Throughout these slides, the term Active Directory Domain implies Domains Based on Windows Server 2008 Based on Windows
A+ Guide to Managing & Maintaining Your PC, 8th Edition. Chapter 17 Windows Resources on a Network
 Chapter 17 Windows Resources on a Network Objectives Learn how to support some client/server applications Learn how to share and secure files and folders on the network Learn how to troubleshoot network
Chapter 17 Windows Resources on a Network Objectives Learn how to support some client/server applications Learn how to share and secure files and folders on the network Learn how to troubleshoot network
How To Reset Local Group Policy Objects To Default Settings Windows 7
 How To Reset Local Group Policy Objects To Default Settings Windows 7 more information. Group policy unable to apply firewall change on Windows 7 cilent - blocked Try to reset GPO settings to default values
How To Reset Local Group Policy Objects To Default Settings Windows 7 more information. Group policy unable to apply firewall change on Windows 7 cilent - blocked Try to reset GPO settings to default values
Managing SonicWall Gateway Anti Virus Service
 Managing SonicWall Gateway Anti Virus Service SonicWall Gateway Anti-Virus (GAV) delivers real-time virus protection directly on the SonicWall security appliance by using SonicWall s IPS-Deep Packet Inspection
Managing SonicWall Gateway Anti Virus Service SonicWall Gateway Anti-Virus (GAV) delivers real-time virus protection directly on the SonicWall security appliance by using SonicWall s IPS-Deep Packet Inspection
Supporting Networked Computers
 CHAPTER 7 Supporting Networked Computers After completing this chapter, you will be able to: Define the main concepts of networking, including the roles of TCP/IP, IP addresses, and subnet masks. Set up
CHAPTER 7 Supporting Networked Computers After completing this chapter, you will be able to: Define the main concepts of networking, including the roles of TCP/IP, IP addresses, and subnet masks. Set up
Password policy settings control the complexity and lifetime for passwords. This section discusses each specific password policy setting
 Windows Security Reference This document is a checklist of the security options with reference material (provided by Microsoft) for a Windows server implementation. The options are based on Windows 2003
Windows Security Reference This document is a checklist of the security options with reference material (provided by Microsoft) for a Windows server implementation. The options are based on Windows 2003
User Guide. Version R92. English
 AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
Mission Control for the Microsoft Cloud. 5nine Cloud Security. Web Portal Version 12.o. Getting Started Guide
 Mission Control for the Microsoft Cloud 5nine Cloud Security Web Portal Version 12.o Getting Started Guide 2018 5nine Software Inc. All rights reserved. All trademarks are the property of their respective
Mission Control for the Microsoft Cloud 5nine Cloud Security Web Portal Version 12.o Getting Started Guide 2018 5nine Software Inc. All rights reserved. All trademarks are the property of their respective
Endpoint Security Client. User Guide Version R71
 Endpoint Security Client User Guide Version R71 December 24, 2008 2003-2009 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Endpoint Security Client User Guide Version R71 December 24, 2008 2003-2009 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Cyber Essentials Questionnaire Guidance
 Cyber Essentials Questionnaire Guidance Introduction This document has been produced to help companies write a response to each of the questions and therefore provide a good commentary for the controls
Cyber Essentials Questionnaire Guidance Introduction This document has been produced to help companies write a response to each of the questions and therefore provide a good commentary for the controls
Dynamic Host Configuration Protocol (DHCP)
 U 6 ynamic Host Configuration Protocol (HCP) P Advantages of HCP educes the administrative workload and eliminates clerical errors Allows administrators to easily change P configurations cales well to
U 6 ynamic Host Configuration Protocol (HCP) P Advantages of HCP educes the administrative workload and eliminates clerical errors Allows administrators to easily change P configurations cales well to
CompTIA A+ Certification ( ) Study Guide Table of Contents
 CompTIA A+ Certification (220-902) Study Guide Table of Contents Course Introduction About This Course About CompTIA Certifications Module 1 / Supporting Windows 1 Module 1 / Unit 1 Windows Operating System
CompTIA A+ Certification (220-902) Study Guide Table of Contents Course Introduction About This Course About CompTIA Certifications Module 1 / Supporting Windows 1 Module 1 / Unit 1 Windows Operating System
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Web and MAC Authentication
 3 Web and MAC Authentication Contents Overview..................................................... 3-2 Client Options.............................................. 3-3 General Features............................................
3 Web and MAC Authentication Contents Overview..................................................... 3-2 Client Options.............................................. 3-3 General Features............................................
Endpoint Protection with DigitalPersona Pro
 DigitalPersona Product Brief Endpoint Protection with DigitalPersona Pro An introductory technical overview to DigitalPersona s suite for Access Management, Data Protection and Secure Communication. April
DigitalPersona Product Brief Endpoint Protection with DigitalPersona Pro An introductory technical overview to DigitalPersona s suite for Access Management, Data Protection and Secure Communication. April
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Cyber Essentials - Requirements for IT Infrastructure Questionnaire
 Cyber Essentials - Requirements for IT Infrastructure Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a
Cyber Essentials - Requirements for IT Infrastructure Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Remote Administration
 Windows Remote Desktop, on page 1 pcanywhere, on page VNC, on page 6 Windows Remote Desktop Remote Desktop permits users to remotely execute applications on Windows Server 2012 R2 from a range of devices
Windows Remote Desktop, on page 1 pcanywhere, on page VNC, on page 6 Windows Remote Desktop Remote Desktop permits users to remotely execute applications on Windows Server 2012 R2 from a range of devices
n Learn about the Security+ exam n Learn basic terminology and the basic approaches n Implement security configuration parameters on network
 Always Remember Chapter #1: Network Device Configuration There is no 100 percent secure system, and there is nothing that is foolproof! 2 Outline Learn about the Security+ exam Learn basic terminology
Always Remember Chapter #1: Network Device Configuration There is no 100 percent secure system, and there is nothing that is foolproof! 2 Outline Learn about the Security+ exam Learn basic terminology
Trends in IT Technology
 Week 10 rends in echnology Lecture opics Virtual reality components and applications ummarize new uses of biometrics oftware as a service Virtual reality D etworking rid, utility, and cloud computing anotechnology
Week 10 rends in echnology Lecture opics Virtual reality components and applications ummarize new uses of biometrics oftware as a service Virtual reality D etworking rid, utility, and cloud computing anotechnology
Managing WCS User Accounts
 7 CHAPTER This chapter describes how to configure global email parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Viewing or Editing User Information,
7 CHAPTER This chapter describes how to configure global email parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Viewing or Editing User Information,
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, * Sources include learnfree.org, PC World, wikpedia.com, techterms.com
 INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what
INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what
ADSelfService Plus' Password Policy Enforcer. Active Directory Group Policy Object-based password policy
 Comparison Document ADSelfService Plus' Password Policy Enforcer Vs Active Directory Group Policy Object-based password policy Vs Active Directory Fine-grained password policies Passwords are the first
Comparison Document ADSelfService Plus' Password Policy Enforcer Vs Active Directory Group Policy Object-based password policy Vs Active Directory Fine-grained password policies Passwords are the first
6 Months Training Module in MS SQL SERVER 2012
 6 Months Training Module in MS SQL SERVER 2012 Module 1 Installing and Configuring Windows Server 2012 Installing and Managing Windows Server 2012 Windows Server 2012 Overview Installing Windows Server
6 Months Training Module in MS SQL SERVER 2012 Module 1 Installing and Configuring Windows Server 2012 Installing and Managing Windows Server 2012 Windows Server 2012 Overview Installing Windows Server
Lotus Domino Security NSL, Web SSO, Notes ID vault. Collin Murray Program Director, Lotus Domino Product Management
 Lotus Domino Security NSL, Web SSO, Notes ID vault Collin Murray Program Director, Lotus Domino Product Management Challenge: Reduce Cost of Ownership IBM Lotus Notes and Domino have been providing a secure
Lotus Domino Security NSL, Web SSO, Notes ID vault Collin Murray Program Director, Lotus Domino Product Management Challenge: Reduce Cost of Ownership IBM Lotus Notes and Domino have been providing a secure
KASPERSKY LAB. Kaspersky Administration Kit version 6.0. Reference Book
 KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
Module 9. Configuring IPsec. Contents:
 Configuring IPsec 9-1 Module 9 Configuring IPsec Contents: Lesson 1: Overview of IPsec 9-3 Lesson 2: Configuring Connection Security Rules 9-11 Lesson 3: Configuring IPsec NAP Enforcement 9-21 Lab: Configuring
Configuring IPsec 9-1 Module 9 Configuring IPsec Contents: Lesson 1: Overview of IPsec 9-3 Lesson 2: Configuring Connection Security Rules 9-11 Lesson 3: Configuring IPsec NAP Enforcement 9-21 Lab: Configuring
Managing the VPN Client
 Managing the VPN Client This chapter explains the tasks you can perform to manage connection entries, view and manage event reporting, and upgrade or uninstall the VPN Client software. The management features
Managing the VPN Client This chapter explains the tasks you can perform to manage connection entries, view and manage event reporting, and upgrade or uninstall the VPN Client software. The management features
x CH03 2/26/04 1:24 PM Page
 03 078973107x CH03 2/26/04 1:24 PM Page 45 3............................................. Setting Up, Managing, and Troubleshooting Security Accounts and Policies 1. You re a help desk technician for your
03 078973107x CH03 2/26/04 1:24 PM Page 45 3............................................. Setting Up, Managing, and Troubleshooting Security Accounts and Policies 1. You re a help desk technician for your
Antivirus Solution Guide for Clustered Data ONTAP: Sophos
 Technical Report Antivirus Solution Guide for Clustered Data ONTAP: Sophos Saurabh Singh and Brahmanna Chowdary Kodavali, NetApp July 2016 TR-4309 Abstract An antivirus solution is key for enterprises
Technical Report Antivirus Solution Guide for Clustered Data ONTAP: Sophos Saurabh Singh and Brahmanna Chowdary Kodavali, NetApp July 2016 TR-4309 Abstract An antivirus solution is key for enterprises
Chapter 10: Security. 2. What are the two types of general threats to computer security? Give examples of each.
 Name Date Chapter 10: Security After completion of this chapter, students should be able to: Explain why security is important and describe security threats. Explain social engineering, data wiping, hard
Name Date Chapter 10: Security After completion of this chapter, students should be able to: Explain why security is important and describe security threats. Explain social engineering, data wiping, hard
Change NETGEAR USB Control Center Settings
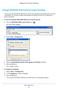 Change NETGEAR USB Control Center Settings You can stop the NETGEAR USB Control Center from starting automatically when you log in to Windows. You can also change the language and specify the time-out
Change NETGEAR USB Control Center Settings You can stop the NETGEAR USB Control Center from starting automatically when you log in to Windows. You can also change the language and specify the time-out
Security in Bomgar Remote Support
 Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
Information Technology Resource Management Council (ITRMC) ENTERPRISE GUIDELINES G950 SECURITY PROCEDURES
 Information Technology Resource Management Council (ITRMC) ENTERPRISE GUIDELINES G950 SECURITY PROCEDURES Category: G950A Server Operating System; Initial Security Requirements CONTENTS: I. Definition
Information Technology Resource Management Council (ITRMC) ENTERPRISE GUIDELINES G950 SECURITY PROCEDURES Category: G950A Server Operating System; Initial Security Requirements CONTENTS: I. Definition
Unit 1. Application Servers
 Unit 1 pplication ervers DW DW Donna. Warren ducation ccounting B lectrical ngineering M omputer cience Work xperience 8 years as etwork ngineer and owner of a small IT consulting company 7 years as networking
Unit 1 pplication ervers DW DW Donna. Warren ducation ccounting B lectrical ngineering M omputer cience Work xperience 8 years as etwork ngineer and owner of a small IT consulting company 7 years as networking
Comodo SecureBox Management Console Software Version 1.9
 6. Comodo SecureBox Management Console Software Version 1.9 Quick Start Guide Guide Version 1.9.041918 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo SecureBox Management Console
6. Comodo SecureBox Management Console Software Version 1.9 Quick Start Guide Guide Version 1.9.041918 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo SecureBox Management Console
Technical Overview of DirectAccess in Windows 7 and Windows Server 2008 R2. Microsoft Windows Family of Operating Systems
 Technical Overview of in Windows 7 and Windows Server 2008 R2 Microsoft Windows Family of Operating Systems Published: January 2009 This document supports a preliminary release of a software product that
Technical Overview of in Windows 7 and Windows Server 2008 R2 Microsoft Windows Family of Operating Systems Published: January 2009 This document supports a preliminary release of a software product that
Visitor Management Host User Guide
 Visitor Management Host User Guide Table of Contents CHAPTER 1 Introduction............................................. 5 Conventions Used in this Documentation.............................................5
Visitor Management Host User Guide Table of Contents CHAPTER 1 Introduction............................................. 5 Conventions Used in this Documentation.............................................5
Florida State University Center for Transportation and Public Safety
 FDLE Application/Service/System Audit Checklist Traffic and Criminal Software (TraCS) What is TraCS? The Traffic and Criminal Software (TraCS) is a client-server based application that uses web services
FDLE Application/Service/System Audit Checklist Traffic and Criminal Software (TraCS) What is TraCS? The Traffic and Criminal Software (TraCS) is a client-server based application that uses web services
Windows 10 and the Enterprise. Craig A. Brown Prepared for: GMIS
 Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Microsoft Exam Security fundamentals Version: 9.0 [ Total Questions: 123 ]
![Microsoft Exam Security fundamentals Version: 9.0 [ Total Questions: 123 ] Microsoft Exam Security fundamentals Version: 9.0 [ Total Questions: 123 ]](/thumbs/96/126527464.jpg) s@lm@n Microsoft Exam 98-367 Security fundamentals Version: 9.0 [ Total Questions: 123 ] Question No : 1 The Active Directory controls, enforces, and assigns security policies and access rights for all
s@lm@n Microsoft Exam 98-367 Security fundamentals Version: 9.0 [ Total Questions: 123 ] Question No : 1 The Active Directory controls, enforces, and assigns security policies and access rights for all
Endpoint Security Client
 Endpoint Security Client R80 User Guide 28 February 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
Endpoint Security Client R80 User Guide 28 February 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Practical Network Defense Labs
 Practical Network Defense Labs ABOUT This document showcases my practical hands-on engagements in the elearnsecurity HERA labs environment for the Network Defense Professional certification course. I utilized
Practical Network Defense Labs ABOUT This document showcases my practical hands-on engagements in the elearnsecurity HERA labs environment for the Network Defense Professional certification course. I utilized
Chapter 19 Security. Chapter 19 Security
 Chapter 19 Security Outline 19.1 Introduction 19.2 Cryptography 19.2.1 Secret-Key Cryptography 19.2.2 Public-Key Cryptography 19.3 Authentication 19.3.1 Basic Authentication 19.3.2 Biometrics and Smart
Chapter 19 Security Outline 19.1 Introduction 19.2 Cryptography 19.2.1 Secret-Key Cryptography 19.2.2 Public-Key Cryptography 19.3 Authentication 19.3.1 Basic Authentication 19.3.2 Biometrics and Smart
Minimum Standards for Connecting to the UCLA Network
 Minimum Standards for Connecting to the UCLA Network Last April, the CSG approved a set of minimum standards for connecting to the UCLA network that were based on a policy that had been developed by Berkeley.
Minimum Standards for Connecting to the UCLA Network Last April, the CSG approved a set of minimum standards for connecting to the UCLA network that were based on a policy that had been developed by Berkeley.
Security in the Privileged Remote Access Appliance
 Security in the Privileged Remote Access Appliance 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
Security in the Privileged Remote Access Appliance 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
System Table of Contents:
 Table of Contents: User Settings Preferences User Security Orgs / Groups / Depts Customize Database Access 2 Chapter 9 - Sadjadi et al. Introduction True automated system administration is only possible
Table of Contents: User Settings Preferences User Security Orgs / Groups / Depts Customize Database Access 2 Chapter 9 - Sadjadi et al. Introduction True automated system administration is only possible
Discount Kaspersky PURE 3.0 internet download software for windows 8 ]
![Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Discount Kaspersky PURE 3.0 internet download software for windows 8 ]](/thumbs/71/65538451.jpg) Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Description: Extended benefits Award-winning protection against all types of Internet threats Online shopping, banking and social
Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Description: Extended benefits Award-winning protection against all types of Internet threats Online shopping, banking and social
