User Guide. Application Security for Workspace Environment Management - Preview V2/ September 2017
|
|
|
- Loreen Hamilton
- 5 years ago
- Views:
Transcription
1 User Guide Application Security for Workspace Environment Management - Preview V2/ September 2017
2 Software version: Release date: September 2017 Document revision: 2 Copyright 2017 Citrix Systems, Inc. All rights reserved. Citrix, Inc 851 West Cypress Creek Road Fort Lauderdale, FL United States of America This document provides installation, configuration, and usage instructions for using application security in Workspace Environment Management. Citrix.com 2
3 Introduction This preview allows you to test the application security functionality added to the administration console Security pane. It is not intended for use in production environments. The application security functionality allows you to control the applications end users are permitted to run by defining rules in Workspace Environment Management. This functionality is similar to Windows AppLocker but gives you the additional ability to: define rules without assigning them, bulk-assign rules to users, import rules from Windows AppLocker. Citrix.com 3
4 Known issues In addition to the Known Issues documented in this Preview release contains the following issues: When you examine the properties of rules in the Microsoft Security Policy Editor (secpol.msc), script rules set to "Audit" mode in the Workspace Environment Management Security tab are incorrectly shown as not configured. (PowerShell can be used to confirm that these rules are actually in audit mode.) [#WEM-352] In the WEM Infrastructure Server Configuration wizard Advanced tab, if you select the option Use cache even if online, it is not saved when you close the wizard. A workaround is to set the registry key BrokerUseCacheEvenIfOnline = 1 in HKLM\System\CurrentControlSet\Control\Norskale\Infrastructure Services. [#WEM-396] While in the Security Tab and switching between Configuration Sets, the side panel may incorrectly display its state, either enabled/disabled. Switching to another tab and back resolves this issue. [#WEM-405] When you select multiple rules and click Edit, any changes to rule assignments you make are applied to all users and user groups you select. In other words, both new and existing rule assignments are merged across those rules. If you do not change rule assignments, existing rule assignments are unchanged. To fine tune rule assignments, select one rule at a time and and click Edit. [#WEM-420] When you select multiple rules and then use Edit, the Permissions option defaults to "Allow", even if some or all of the selected rules are set to deny. In the rule list, permissions are correctly reported in the Action column. [#WEM-421] In the Security tab, when you clear the option Process DLL Rules, the rule count reported next to the "DLL Rules" collection is set to zero, regardless of the actual number in the WEM database. [#WEM-425] System requirements This preview has the same requirements as Workspace Environment Management. See Citrix.com 4
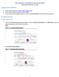
5 Install and configure Note: The preview build is for testing and evaluation purposes only. It is not intended for production environments. None of the preview components are compatible with any production release of Workspace Environment Management, and vice versa. Updates to or from the preview build are not supported. Therefore:" Do not deploy the preview in production environments. Do not use the preview with a production Workspace Environment Management database. Do not install any preview components in the same environment as a production Workspace Environment Management installation. Download the preview from the download page, and then follow the usual installation and configuration steps in Enable logging in the administration console (Ribbon > About > Options > Enable debug mode) so that mismatched rule assignments are recorded for export during restore of security settings. Using application security Overview To control which applications end users can run, you can use either the Windows AppLocker interface, or Workspace Environment Management to manage Windows AppLocker rules. You can switch between these approaches at any time but we recommend that you do not use both approaches at the same time. When you already have AppLocker rules which you want to manage in Workspace Environment Management, you can import them into the current Workspace Environment Management configuration set. When you use Workspace Environment Management to manage Windows AppLocker rules, the agent processes (converts) Application Security tab rules into Windows AppLocker rules on the agent host. If you stop the agent processing rules, they are preserved in the configuration set and AppLocker continues running by using the last set of instructions processed by the agent. Application Security tab The Application Security tab is inside the Security section: Citrix.com 5
6 This tab lists the application security rules in the current Workspace Environment Management configuration set. You can use Find to filter the list according to a text string. When you select the top-level item "Application Security," the following options become available to enable or disable rule processing: Process Application Security Rules. When selected, the Application Security tab controls are enabled and the agent processes rules in the current configuration set, converting them into AppLocker rules on the agent host. When not selected, the Application Security tab controls are disabled and the agent does not process rules into AppLocker rules. (In this case AppLocker rules are not updated.) Process DLL Rules. When selected, the agent processes DLL rules in the current configuration set into AppLocker DLL rules on the agent host. This option is only available when you select Process Application Security Rules. Important: If you use DLL rules, you must create a DLL rule with "Allow" permission for each DLL that is used by all of the allowed apps. Caution: If you use DLL rules, end users may experience a reduction in performance. This is because, when you use DLL rules, AppLocker checks each DLL that an app loads before it is allowed to run. Rule collections Rules belong to AppLocker rule collections. Each collection name indicates how many rules it contains, for example (12). Click a collection name to filter the rule list to one of the following collections: Executable Rules. Rules which include files with the.exe and.com extensions that Citrix.com 6
7 are associated with an application. Windows Rules. Rules which include installer file formats (.msi,.msp,.mst) which control the installation of files on client computers and servers. Script Rules. Rules which include files of the following formats:.ps1,.bat,.cmd,.vbs,.js. Packaged Rules. Rules which include packaged apps, also known as Universal Windows apps. In packaged apps, all files within the app package share the same identity. Therefore, one rule can control the entire app. Workspace Environment Management supports only publisher rules for packaged apps. DLL Rules. Rules which include files of the following formats:.dll,.ocx. Important: If you use DLL rules, you must create a DLL rule with "Allow" permission for each DLL that is used by all of the allowed apps. Caution: If you use DLL rules, end users may experience a reduction in performance. This is because, when you use DLL rules, AppLocker checks each DLL that an app loads before it is allowed to run. When you filter the rule list to a collection, the Rule enforcement option is available to control how AppLocker enforces all rules in that collection on the agent host. The following rule enforcement values are possible: Icon Value Behavior Off (default) On Audit Rules are created and set to "off," which means they are not applied. Rules are created and set to "enforce," which means they are active on the agent host. Rules are created and set to "audit," which means they are on the agent host in an inactive state. Windows logs when things are started that would violate these rules were they enforced. Citrix.com 7
8 To import AppLocker rules You can import rules already exported from AppLocker into Workspace Environment Management. Imported Windows AppLocker settings are added to any existing rules in the Security tab. Any invalid application security rules are automatically deleted and listed in a report dialog, which you can export. 1. In the ribbon click Import AppLocker Rules. 2. Browse to the XML file exported from AppLocker containing your AppLocker rules. 3. Click Import. The rules are added to the Application Security rules list. To add a rule 1. Click a rule collection name in the sidebar. For example, to add an executable rule click the Executable Rules collection. 2. Click Add Rule. 3. In the Display section, enter the following details: Name. The display name of the rule as it displays in the rule list. Description. Additional information about the resource (optional). 4. In the Type section select an option: Path. The rule matches a file path or folder path Publisher. The rule matches a selected publisher. Hash. The rule matches a specific hash code. Citrix.com 8
9 5. In the Permissions section select whether this rule will Allow or Deny applications from running: 6. To assign this rule to users or user groups, in Assignments pane, select users or groups, to assign this rule to. The "Assigned" column shows a "check" icon for assigned users or groups. Tip: You can use the usual Windows selection modifier keys to make multiple selections, or use Select All to select all rows. Tip: Users must already be in the Workspace Environment Management Users list. Tip: You can assign rules after the rule is created. 7. Click Next. 8. Specify the criteria the rule matches, depending on the rule type you select: Path. Specify a file path or folder path the rule to match. If you select a folder, the rule matches all files inside and below that folder. Publisher. Specify a signed reference file, and then use the Publisher Info slider to tune the level of property matching. Hash. Specify a file. The rule matches the hash code of the file. 9. Click Next. 10. Add any exceptions you require (optional). In Add exception, select an exception type then click Add. (You can Edit and Remove exceptions as required.) 11. To save the rule, click Create. Citrix.com 9
10 To assign rules to users Select one or more rules in the list, then click Edit in the toolbar or context menu. In the editor, select the rows containing the users and user groups you want to assign the rule to, then click OK. You can also unassign the selected rules from everyone using Select All to clear all selections. Note: When you select multiple rules and click Edit, any rule assignment changes for those rules are applied to all users and user groups you select. In other words, existing rule assignments are merged across those rules. To add default rules Click Add Default Rules. A set of AppLocker default rules are added to the list. To edit rules Select one or more rules in the list, then click Edit in the toolbar or context menu. The editor opens allowing you to adjust settings which apply to the selection you made. To delete rules Select one or more rules in the list, then click Delete in the toolbar or context menu. To back up application security rules You can back up all application security rules in your current configuration set. Rules are all exported as a single XML file. You can use Restore to restore the rules to any configuration set. In the ribbon, click Backup then select Security Settings. To restore application security rules You can restore application security rules from XML files created by the Workspace Environment Management Backup command. The restore process replaces the rules in the current configuration set with those in the backup. When you switch to or refresh the Security tab, any invalid application security rules are detected. Invalid rules are automatically deleted and listed in a report dialog, which you can export. During the restore process, you can choose whether you want to restore rule assignments to users and user groups in your current configuration set. Reassignment will only succeed if the backed up users/groups are present in your current configuration set/active directory. Any mismatched rules are restored but remain unassigned. After restore, they are listed in a report dialog which you can export in CSV format. 1. In the ribbon, click Restore to start the restore wizard. 2. Select Security settings, then click Next twice. 3. In Restore from folder, browse to the folder containing the backup file. Citrix.com 10
11 4. Select AppLocker Rule Settings, then click Next. 5. Confirm whether you want to restore rule assignments or not: Yes. Restore rules and reassign them to the same users and user groups in your current configuration set. No. Restore rules and leave them unassigned. 6. To start restoring, click Restore Settings. Citrix.com 11
Workspace Environment Management
 Workspace Environment Management Dec 08, 2017 Workspace Environment Management 4.5 is the current release. For documentation about earlier releases, see the following sections: Workspace Environment Management
Workspace Environment Management Dec 08, 2017 Workspace Environment Management 4.5 is the current release. For documentation about earlier releases, see the following sections: Workspace Environment Management
Self-Service Password Reset
 Citrix Product Documentation docs.citrix.com September 21, 2018 Contents Self-Service Password Reset 1.1.x 3 What s new 3 What s new in version 1.1.20................................... 3 What s new in
Citrix Product Documentation docs.citrix.com September 21, 2018 Contents Self-Service Password Reset 1.1.x 3 What s new 3 What s new in version 1.1.20................................... 3 What s new in
Package Manager. Managing Cisco VXC Manager Packages CHAPTER
 CHAPTER 3 This chapter describes how to perform routine Cisco VXC Manager package management tasks using the Administrator Console. It provides information on managing the Cisco VXC Manager packages (software,
CHAPTER 3 This chapter describes how to perform routine Cisco VXC Manager package management tasks using the Administrator Console. It provides information on managing the Cisco VXC Manager packages (software,
VMware Mirage Web Manager Guide
 Mirage 5.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
Mirage 5.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
Tutorial 1. Creating a Database
 Tutorial 1 Creating a Database Microsoft Access 2010 Objectives Learn basic database concepts and terms Explore the Microsoft Access window and Backstage view Create a blank database Create and save a
Tutorial 1 Creating a Database Microsoft Access 2010 Objectives Learn basic database concepts and terms Explore the Microsoft Access window and Backstage view Create a blank database Create and save a
VMware Mirage Web Management Guide. VMware Mirage 5.9.1
 VMware Mirage Web Management Guide VMware Mirage 5.9.1 VMware Mirage Web Management Guide You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
VMware Mirage Web Management Guide VMware Mirage 5.9.1 VMware Mirage Web Management Guide You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
DocAve 6 SQL Server Data Manager
 DocAve 6 SQL Server Data Manager User Guide Service Pack 4, Cumulative Update 2 Revision G Issued July 2014 Table of Contents About DocAve SQL Server Data Manager... 4 Complementary Products... 5 Submitting
DocAve 6 SQL Server Data Manager User Guide Service Pack 4, Cumulative Update 2 Revision G Issued July 2014 Table of Contents About DocAve SQL Server Data Manager... 4 Complementary Products... 5 Submitting
Sophos Mobile as a Service
 startup guide Product Version: 8 Contents About this guide... 1 What are the key steps?... 2 Change your password... 3 Change your login name... 4 Activate Mobile Advanced licenses...5 Check your licenses...6
startup guide Product Version: 8 Contents About this guide... 1 What are the key steps?... 2 Change your password... 3 Change your login name... 4 Activate Mobile Advanced licenses...5 Check your licenses...6
Deploying Virtual Apps and Desktops with Citrix Provisioning using Oracle Cloud Infrastructure
 Deploying Virtual Apps and Desktops with Citrix Provisioning using Oracle Cloud Infrastructure Citrix Virtual Apps and Desktops (formerly XenApp and XenDesktop) on Oracle Cloud (also known as Oracle Cloud
Deploying Virtual Apps and Desktops with Citrix Provisioning using Oracle Cloud Infrastructure Citrix Virtual Apps and Desktops (formerly XenApp and XenDesktop) on Oracle Cloud (also known as Oracle Cloud
End User Manual. December 2014 V1.0
 End User Manual December 2014 V1.0 Contents Getting Started... 4 How to Log into the Web Portal... 5 How to Manage Account Settings... 6 The Web Portal... 8 How to Upload Files in the Web Portal... 9 How
End User Manual December 2014 V1.0 Contents Getting Started... 4 How to Log into the Web Portal... 5 How to Manage Account Settings... 6 The Web Portal... 8 How to Upload Files in the Web Portal... 9 How
ProfileUnity with FlexApp Technology
 ProfileUnity with FlexApp Technology Best Practices for Highly Secured Desktop Environments Introduction This guide has been authored by experts at Liquidware in order to provide information and guidance
ProfileUnity with FlexApp Technology Best Practices for Highly Secured Desktop Environments Introduction This guide has been authored by experts at Liquidware in order to provide information and guidance
ImageNow eforms. Getting Started Guide. ImageNow Version: 6.7. x
 ImageNow eforms Getting Started Guide ImageNow Version: 6.7. x Written by: Product Documentation, R&D Date: September 2016 2014 Perceptive Software. All rights reserved CaptureNow, ImageNow, Interact,
ImageNow eforms Getting Started Guide ImageNow Version: 6.7. x Written by: Product Documentation, R&D Date: September 2016 2014 Perceptive Software. All rights reserved CaptureNow, ImageNow, Interact,
Manually Configuring IIS
 Manually Configuring IIS This application note describes how to manually configure Microsoft's Internet Information Server (IIS) and the ProHelp EPM Web Reporting option. This configuration is typically
Manually Configuring IIS This application note describes how to manually configure Microsoft's Internet Information Server (IIS) and the ProHelp EPM Web Reporting option. This configuration is typically
ControlPoint. Managing ControlPoint Users, Permissions, and Menus. February 05,
 Managing Users, Permissions, and Menus February 05, 2018 www.metalogix.com info@metalogix.com 202.609.9100 Copyright International GmbH., 2008-2018 All rights reserved. No part or section of the contents
Managing Users, Permissions, and Menus February 05, 2018 www.metalogix.com info@metalogix.com 202.609.9100 Copyright International GmbH., 2008-2018 All rights reserved. No part or section of the contents
VMware Mirage Web Management Guide
 VMware Mirage Web Management Guide Mirage 5.7 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for
VMware Mirage Web Management Guide Mirage 5.7 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for
Sophos Mobile SaaS startup guide. Product version: 7.1
 Sophos Mobile SaaS startup guide Product version: 7.1 Contents 1 About this guide...4 2 What are the key steps?...5 3 Change your password...6 4 Change your login name...7 5 Activate SMC Advanced licenses...8
Sophos Mobile SaaS startup guide Product version: 7.1 Contents 1 About this guide...4 2 What are the key steps?...5 3 Change your password...6 4 Change your login name...7 5 Activate SMC Advanced licenses...8
LiteSpeed for SQL Server 6.1. Configure Log Shipping
 LiteSpeed for SQL Server 6.1 Configure Log Shipping 2010 Quest Software, Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
LiteSpeed for SQL Server 6.1 Configure Log Shipping 2010 Quest Software, Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
KASPERSKY LAB. Kaspersky Administration Kit version 6.0. Reference Book
 KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
KYOCERA Net Admin User Guide
 KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
Source Control: Subversion
 USER GUIDE MADCAP LINGO 10.1 Source Control: Subversion Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in
USER GUIDE MADCAP LINGO 10.1 Source Control: Subversion Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in
Customizing Wizards with Cisco Prime Network Activation Wizard Builder
 CHAPTER 3 Customizing Wizards with Cisco Prime Network Activation Wizard Builder The following topics provide detailed information about customizing Network Activation wizard metadata files using the Cisco
CHAPTER 3 Customizing Wizards with Cisco Prime Network Activation Wizard Builder The following topics provide detailed information about customizing Network Activation wizard metadata files using the Cisco
Source Control: Perforce
 USER GUIDE MADCAP LINGO 10.1 Source Control: Perforce Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
USER GUIDE MADCAP LINGO 10.1 Source Control: Perforce Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
BDM Hyperion Workspace Basics
 BDM Hyperion Workspace Basics Contents of this Guide - Toolbars & Buttons Workspace User Interface 1 Standard Toolbar 3 Explore Toolbar 3 File extensions and icons 4 Folders 4 Browsing Folders 4 Root folder
BDM Hyperion Workspace Basics Contents of this Guide - Toolbars & Buttons Workspace User Interface 1 Standard Toolbar 3 Explore Toolbar 3 File extensions and icons 4 Folders 4 Browsing Folders 4 Root folder
Contents. Add a Form Element to a Group Box Add a Field to a Form... 22
 Workflow Design Guide Version 17 November 2017 Contents About This Guide... 7 Workflows and Forms Overview... 7 Security Permissions for Workflows and Forms... 8 Search for a Workflow Design, Workflow
Workflow Design Guide Version 17 November 2017 Contents About This Guide... 7 Workflows and Forms Overview... 7 Security Permissions for Workflows and Forms... 8 Search for a Workflow Design, Workflow
CREATING CUSTOMER MAILING LABELS
 CREATING CUSTOMER MAILING LABELS agrē has a built-in exports to make it easy to create a data file of customer address information, but how do you turn a list of names and addresses into mailing labels?
CREATING CUSTOMER MAILING LABELS agrē has a built-in exports to make it easy to create a data file of customer address information, but how do you turn a list of names and addresses into mailing labels?
Configuring and Managing Zones
 Send documentation comments to mdsfeedback-doc@cisco.com CHAPTER 30 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric,
Send documentation comments to mdsfeedback-doc@cisco.com CHAPTER 30 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric,
Polycom RealPresence Resource Manager System
 [Type the document title] Upgrade Guide 8.0.1 October 2013 3725-72106-001C Polycom RealPresence Resource Manager System Polycom Document Title 1 Contents Contents Prepare for Polycom RealPresence Resource
[Type the document title] Upgrade Guide 8.0.1 October 2013 3725-72106-001C Polycom RealPresence Resource Manager System Polycom Document Title 1 Contents Contents Prepare for Polycom RealPresence Resource
How to Use the Job Merge Wizard
 How to Use the Job Merge Wizard Print Audit 5 includes a tool called the Job Merge Wizard. This tool is intended for companies that have multiple locations and want to consolidate the data for reporting
How to Use the Job Merge Wizard Print Audit 5 includes a tool called the Job Merge Wizard. This tool is intended for companies that have multiple locations and want to consolidate the data for reporting
Attix5 Pro Storage Platform Console
 Attix5 Pro Storage Platform Console V7.0.1 User Manual for Microsoft Windows Your guide to managing the Attix5 Pro backup environment using the Storage Platform Console. 0 Copyright notice and proprietary
Attix5 Pro Storage Platform Console V7.0.1 User Manual for Microsoft Windows Your guide to managing the Attix5 Pro backup environment using the Storage Platform Console. 0 Copyright notice and proprietary
Explore commands on the ribbon Each ribbon tab has groups, and each group has a set of related commands.
 Quick Start Guide Microsoft Excel 2013 looks different from previous versions, so we created this guide to help you minimize the learning curve. Add commands to the Quick Access Toolbar Keep favorite commands
Quick Start Guide Microsoft Excel 2013 looks different from previous versions, so we created this guide to help you minimize the learning curve. Add commands to the Quick Access Toolbar Keep favorite commands
Release Notes. PREEvision. Version 6.5 SP11 English
 Release Notes PREEvision Version 6.5 SP11 English Imprint Vector Informatik GmbH Ingersheimer Straße 24 70499 Stuttgart, Germany Vector reserves the right to modify any information and/or data in this
Release Notes PREEvision Version 6.5 SP11 English Imprint Vector Informatik GmbH Ingersheimer Straße 24 70499 Stuttgart, Germany Vector reserves the right to modify any information and/or data in this
User Management Tool
 Citrix Product Documentation docs.citrix.com September 21, 2018 Contents What s new 3 What s new in User Management Tool 1.8.1........................... 3 What s new in User Management Tool 1.8............................
Citrix Product Documentation docs.citrix.com September 21, 2018 Contents What s new 3 What s new in User Management Tool 1.8.1........................... 3 What s new in User Management Tool 1.8............................
Contents. Properties: Field Area Fields Add a Table to a Form... 23
 Workflow Design Guide Version 18 February 2018 Contents About This Guide... 7 Workflows and Forms Overview... 7 Security Permissions for Workflows and Forms... 8 Search for a Workflow Design, Workflow
Workflow Design Guide Version 18 February 2018 Contents About This Guide... 7 Workflows and Forms Overview... 7 Security Permissions for Workflows and Forms... 8 Search for a Workflow Design, Workflow
Citrix SCOM Management Pack for StoreFront
 Citrix SCOM Management Pack for StoreFront Aug 14, 2017 Citrix SCOM Management Pack 1.12 for StoreFront Citrix SCOM Management Pack 1.11 for StoreFront Citrix SCOM Management Pack 1.9 for StoreFront Citrix
Citrix SCOM Management Pack for StoreFront Aug 14, 2017 Citrix SCOM Management Pack 1.12 for StoreFront Citrix SCOM Management Pack 1.11 for StoreFront Citrix SCOM Management Pack 1.9 for StoreFront Citrix
Security Explorer 9.1. User Guide
 Security Explorer 9.1 User Guide Security Explorer 9.1 User Guide Explorer 8 Installation Guide ii 2013 by Quest Software All rights reserved. This guide contains proprietary information protected by copyright.
Security Explorer 9.1 User Guide Security Explorer 9.1 User Guide Explorer 8 Installation Guide ii 2013 by Quest Software All rights reserved. This guide contains proprietary information protected by copyright.
Administration. Training Guide. Infinite Visions Enterprise Edition phone toll free fax
 Administration Training Guide Infinite Visions Enterprise Edition 406.252.4357 phone 1.800.247.1161 toll free 406.252.7705 fax www.csavisions.com Copyright 2005 2011 Windsor Management Group, LLC Revised:
Administration Training Guide Infinite Visions Enterprise Edition 406.252.4357 phone 1.800.247.1161 toll free 406.252.7705 fax www.csavisions.com Copyright 2005 2011 Windsor Management Group, LLC Revised:
vrealize Operations Manager Customization and Administration Guide vrealize Operations Manager 6.4
 vrealize Operations Manager Customization and Administration Guide vrealize Operations Manager 6.4 vrealize Operations Manager Customization and Administration Guide You can find the most up-to-date technical
vrealize Operations Manager Customization and Administration Guide vrealize Operations Manager 6.4 vrealize Operations Manager Customization and Administration Guide You can find the most up-to-date technical
Copyright 2017 Trend Micro Incorporated. All rights reserved.
 Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent
Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent
Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface
 Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface Document ID: 13-603114 Release 2.2 July 2008 Issue No.1 2008 Avaya Inc. All Rights Reserved. Notice While reasonable
Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface Document ID: 13-603114 Release 2.2 July 2008 Issue No.1 2008 Avaya Inc. All Rights Reserved. Notice While reasonable
Workspace Environment Management 4.6 Current Release
 Workspace Environment Management 4.6 Current Release Mar 27, 2018 Workspace Environment Management 4.6 is the current release. For documentation about earlier releases, see the following sections: Workspace
Workspace Environment Management 4.6 Current Release Mar 27, 2018 Workspace Environment Management 4.6 is the current release. For documentation about earlier releases, see the following sections: Workspace
Microsoft User Experience Virtualization Deployment Guide
 Microsoft User Experience Virtualization Deployment Guide Microsoft User Experience Virtualization (UE-V) is an enterprise-scalable user state virtualization solution that can provide users a consistent
Microsoft User Experience Virtualization Deployment Guide Microsoft User Experience Virtualization (UE-V) is an enterprise-scalable user state virtualization solution that can provide users a consistent
McAfee Management for Optimized Virtual Environments AntiVirus 4.5.0
 Migration Guide McAfee Management for Optimized Virtual Environments AntiVirus 4.5.0 For use with McAfee epolicy Orchestrator COPYRIGHT 2016 Intel Corporation TRADEMARK ATTRIBUTIONS Intel and the Intel
Migration Guide McAfee Management for Optimized Virtual Environments AntiVirus 4.5.0 For use with McAfee epolicy Orchestrator COPYRIGHT 2016 Intel Corporation TRADEMARK ATTRIBUTIONS Intel and the Intel
USER GUIDE MADCAP LINGO Source Control: Git
 USER GUIDE MADCAP LINGO 10.1 Source Control: Git Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document
USER GUIDE MADCAP LINGO 10.1 Source Control: Git Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
Export Metadata. Learning Objectives. In this Job Aid, you will learn how to export metadata: 1 For a location 3 2 From search results 7
 Export Metadata Learning Objectives In this Job Aid, you will learn how to export metadata: 1 For a location 3 2 From search results 7 Last updated: July 8, 2013 Overview You can export content metadata
Export Metadata Learning Objectives In this Job Aid, you will learn how to export metadata: 1 For a location 3 2 From search results 7 Last updated: July 8, 2013 Overview You can export content metadata
Configuring and Managing Zones
 CHAPTER 5 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric, you can create zones to increase network security and
CHAPTER 5 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric, you can create zones to increase network security and
Introduction to Qualtrics Research Suite Wednesday, September 19, 2012
 Logging in to Qualtrics Introduction to Qualtrics Research Suite Wednesday, September 19, 2012 1. Open a browser and go to http://www.qualtrics.com 2. If you have a Qualtrics account, use it to login.
Logging in to Qualtrics Introduction to Qualtrics Research Suite Wednesday, September 19, 2012 1. Open a browser and go to http://www.qualtrics.com 2. If you have a Qualtrics account, use it to login.
ShareFile Account Admin Guide
 ShareFile ShareFile Account Admin Guide A quick guide to get you started with managing your ShareFile account! Intended for: Master Admins, Employees with Admin-level permissions Admin Guide 1 Contents
ShareFile ShareFile Account Admin Guide A quick guide to get you started with managing your ShareFile account! Intended for: Master Admins, Employees with Admin-level permissions Admin Guide 1 Contents
Deploying Windows 7 Using MDT UDI
 The Microsoft Deployment Toolkit (MDT) supports three types of deployments Zero Touch Installation (ZTI), Lite Touch Installation (LTI), and User Driven Installation (UDI). However each deployment type
The Microsoft Deployment Toolkit (MDT) supports three types of deployments Zero Touch Installation (ZTI), Lite Touch Installation (LTI), and User Driven Installation (UDI). However each deployment type
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
Veritas Enterprise Vault PST Migration 12.2
 Veritas Enterprise Vault PST Migration 12.2 Veritas Enterprise Vault: PST Migration Last updated: 2017-08-10. Legal Notice Copyright 2017 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas
Veritas Enterprise Vault PST Migration 12.2 Veritas Enterprise Vault: PST Migration Last updated: 2017-08-10. Legal Notice Copyright 2017 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas
ProjectWise Explorer Basic Users Guide
 ProjectWise Explorer Basic Users Guide (Revision Date: 09/05/17) Index: 1. Introduction... 2 2. Getting Started... 2 3. Login to ProjectWise Explorer... 3 4. Working Directory... 3 5. Inside the ProjectWise
ProjectWise Explorer Basic Users Guide (Revision Date: 09/05/17) Index: 1. Introduction... 2 2. Getting Started... 2 3. Login to ProjectWise Explorer... 3 4. Working Directory... 3 5. Inside the ProjectWise
Citrix ADC Web App Firewall Service
 Citrix ADC Web App Firewall Service Citrix Product Documentation docs.citrix.com October 15, 2018 Contents Getting started 3 Step 1: Sign Up for Citrix Cloud.................................. 3 Step 2:
Citrix ADC Web App Firewall Service Citrix Product Documentation docs.citrix.com October 15, 2018 Contents Getting started 3 Step 1: Sign Up for Citrix Cloud.................................. 3 Step 2:
Welcome to your Citrix User Adoption Kit
 Guide Welcome to your Citrix User Adoption Kit Thank you for choosing Citrix as your cloud and virtualization partner. We put together this kit of promotional materials to help you prepare and onboard
Guide Welcome to your Citrix User Adoption Kit Thank you for choosing Citrix as your cloud and virtualization partner. We put together this kit of promotional materials to help you prepare and onboard
Microsoft Word - Starting the Mail Merge Wizard
 Microsoft Word - Starting the Mail Merge Wizard Starting the Mail Merge Wizard. 1. Select the Mailings tab. 2. Click the Start Mail Merge button 3. Select Step by step Mil Merge Wizard. 4. Select the type
Microsoft Word - Starting the Mail Merge Wizard Starting the Mail Merge Wizard. 1. Select the Mailings tab. 2. Click the Start Mail Merge button 3. Select Step by step Mil Merge Wizard. 4. Select the type
Sophos Mobile in Central
 startup guide Product Version: 8.1 Contents About this guide... 1 What are the key steps?... 2 Activate Mobile Advanced licenses... 3 Configure settings... 4 Configure personal settings...4 Configure technical
startup guide Product Version: 8.1 Contents About this guide... 1 What are the key steps?... 2 Activate Mobile Advanced licenses... 3 Configure settings... 4 Configure personal settings...4 Configure technical
Source Control Guide: Microsoft Team Foundation Server
 MadCap Software Source Control Guide: Microsoft Team Foundation Server Lingo 10.1 Copyright 2017 MadCap Software. All rights reserved. Information in this document is subject to change without notice.
MadCap Software Source Control Guide: Microsoft Team Foundation Server Lingo 10.1 Copyright 2017 MadCap Software. All rights reserved. Information in this document is subject to change without notice.
Section 508 Conformance Audit Voluntary Product Accessibility Template
 10/27/2017 Section 508 Conformance Audit Voluntary Product Accessibility Template Citrix Workspace Environment Management: Agent Log Parser Citrix Systems, Inc. 851 West Cypress Creek Road Fort Lauderdale,
10/27/2017 Section 508 Conformance Audit Voluntary Product Accessibility Template Citrix Workspace Environment Management: Agent Log Parser Citrix Systems, Inc. 851 West Cypress Creek Road Fort Lauderdale,
ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA. Technical Setup and User Guide
 ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA Technical Setup and User Guide ESET REMOTE ADMINISTRATOR PLUG-INFOR KASEYA Copyright 2014 by ESET, spol. s r.o. ESET REMOTE ADMINISTRATOR Plug-in FOR KASEYA
ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA Technical Setup and User Guide ESET REMOTE ADMINISTRATOR PLUG-INFOR KASEYA Copyright 2014 by ESET, spol. s r.o. ESET REMOTE ADMINISTRATOR Plug-in FOR KASEYA
SQL Server Course Administering a SQL 2016 Database Infrastructure. Length. Prerequisites. Audience. Course Outline.
 SQL Server Course - 20764 Administering a SQL 2016 Database Infrastructure Length 5 days Prerequisites Basic knowledge of the Microsoft Windows operating system and its core functionality. Working knowledge
SQL Server Course - 20764 Administering a SQL 2016 Database Infrastructure Length 5 days Prerequisites Basic knowledge of the Microsoft Windows operating system and its core functionality. Working knowledge
Welcome to your Citrix Endpoint Management (formerly XenMobile) User Adoption Kit
 Guide Download your kit https://citrite.sharefile.com/d-s1dde6c97b9b470d8 Welcome to your Citrix Endpoint Management (formerly XenMobile) User Adoption Kit Thank you for choosing Citrix as your mobility
Guide Download your kit https://citrite.sharefile.com/d-s1dde6c97b9b470d8 Welcome to your Citrix Endpoint Management (formerly XenMobile) User Adoption Kit Thank you for choosing Citrix as your mobility
DocAve 6 Lotus Notes Migrator
 DocAve 6 Lotus Notes Migrator User Guide Service Pack 4, Cumulative Update 2 Revision B Issued July 2014 Table of Contents About Lotus Notes Migrator... 5 Complementary Products... 5 Submitting Documentation
DocAve 6 Lotus Notes Migrator User Guide Service Pack 4, Cumulative Update 2 Revision B Issued July 2014 Table of Contents About Lotus Notes Migrator... 5 Complementary Products... 5 Submitting Documentation
AppSense Environment Manager. Personalization Product Guide Version 10.0
 AppSense Environment Manager Personalization Product Guide Version 10.0 AppSense Limited, 2016 All rights reserved. No part of this document may be produced in any form (including photocopying or storing
AppSense Environment Manager Personalization Product Guide Version 10.0 AppSense Limited, 2016 All rights reserved. No part of this document may be produced in any form (including photocopying or storing
Cloud Attached Storage
 Using CTERA Appliances in Replicated Configuration Cloud Attached Storage June 2013 Version 3.2 1 Introduction This document explains how to use CTERA C series appliances in replicated configuration. In
Using CTERA Appliances in Replicated Configuration Cloud Attached Storage June 2013 Version 3.2 1 Introduction This document explains how to use CTERA C series appliances in replicated configuration. In
COMOS. Lifecycle 3D Integration Operation. COMOS PDMS Integration 1. Material management 2. COMOS 3D viewing 3. References 4.
 1 Material management 2 COMOS Lifecycle COMOS 3D viewing 3 References 4 Operating Manual 03/2017 V 10.2.1 A5E37098336-AB Legal information Warning notice system This manual contains notices you have to
1 Material management 2 COMOS Lifecycle COMOS 3D viewing 3 References 4 Operating Manual 03/2017 V 10.2.1 A5E37098336-AB Legal information Warning notice system This manual contains notices you have to
Resource Manager System Upgrade Guide
 [Type the document title] 7.1.0 December 2012 3725-72106-001A Polycom RealPresence Resource Manager System Upgrade Guide Polycom Document Title 1 Trademark Information POLYCOM and the names and marks associated
[Type the document title] 7.1.0 December 2012 3725-72106-001A Polycom RealPresence Resource Manager System Upgrade Guide Polycom Document Title 1 Trademark Information POLYCOM and the names and marks associated
Microsoft Access 2013
 Microsoft Access 2013 Chapter 1 Databases and Database Objects: An Introduction Objectives Describe the features of the Access window Create a database Create tables in Datasheet and Design views Add records
Microsoft Access 2013 Chapter 1 Databases and Database Objects: An Introduction Objectives Describe the features of the Access window Create a database Create tables in Datasheet and Design views Add records
EMCO Remote Installer Professional 5. Copyright EMCO. All rights reserved.
 EMCO Remote Installer Professional 5 Copyright 2001-2017 EMCO. All rights reserved. Company web site: emcosoftware.com Support e-mail: support@emcosoftware.com Table of Contents Chapter... 1: Introduction
EMCO Remote Installer Professional 5 Copyright 2001-2017 EMCO. All rights reserved. Company web site: emcosoftware.com Support e-mail: support@emcosoftware.com Table of Contents Chapter... 1: Introduction
Getting Started. Version 2.1
 Getting Started Version 2.1 September 2015 Table of Contents About this Release...2 About the Citrix DesktopPlayer for Mac Solution...3 About system memory usage...3 DesktopPlayer Components...3 About
Getting Started Version 2.1 September 2015 Table of Contents About this Release...2 About the Citrix DesktopPlayer for Mac Solution...3 About system memory usage...3 DesktopPlayer Components...3 About
The Quick Access Toolbar can be either just below the Title Bar or, as in this case, just above the ruler.
 Table of Contents Ribbon... 3 Customizing the Ribbon and Quick Access Toolbars... 3 File Tab... 5 Print and Print Preview... 7 Working in Protected Mode... 8 Accessibility Checker... 9 Compatibility Changes
Table of Contents Ribbon... 3 Customizing the Ribbon and Quick Access Toolbars... 3 File Tab... 5 Print and Print Preview... 7 Working in Protected Mode... 8 Accessibility Checker... 9 Compatibility Changes
IMPORTING AVALANCHE MANAGER 3.6 BACKUP FILES TO AVALANCHE MC OR SE
 This document provides instructions for migrating to Avalanche SE or MC. OVERVIEW This document contains the following sections: Overview Backing Up the Avalanche Agent Installing Avalanche Importing Backup
This document provides instructions for migrating to Avalanche SE or MC. OVERVIEW This document contains the following sections: Overview Backing Up the Avalanche Agent Installing Avalanche Importing Backup
Polycom RealPresence Resource Manager System
 Upgrade Guide 8.2.0 July 2014 3725-72106-001E Polycom RealPresence Resource Manager System Copyright 2014, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into
Upgrade Guide 8.2.0 July 2014 3725-72106-001E Polycom RealPresence Resource Manager System Copyright 2014, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into
Module 2: Managing Your Resources Lesson 5: Configuring System Settings and Properties Learn
 Module 2: Managing Your Resources Lesson 5: Configuring System Settings and Properties Learn Welcome to Module 2, Lesson 5. In this lesson, you will learn how to use the Administration Console to configure
Module 2: Managing Your Resources Lesson 5: Configuring System Settings and Properties Learn Welcome to Module 2, Lesson 5. In this lesson, you will learn how to use the Administration Console to configure
XenApp 7.x on Oracle Cloud Infrastructure
 2018-032 XenApp 7.x on Oracle Cloud Infrastructure OUT OF BAND DEPLOYMENT GUIDE CITRIX SYSTEMS, INC. Citrix.com 1 Deploying Citrix Cloud XenApp and XenDesktop Service with Oracle Cloud Infrastructure Deploying
2018-032 XenApp 7.x on Oracle Cloud Infrastructure OUT OF BAND DEPLOYMENT GUIDE CITRIX SYSTEMS, INC. Citrix.com 1 Deploying Citrix Cloud XenApp and XenDesktop Service with Oracle Cloud Infrastructure Deploying
Equitrac Embedded for Ricoh Basic. Setup Guide Equitrac Corporation
 Equitrac Embedded for Ricoh Basic 1.1 Setup Guide 2012 Equitrac Corporation Equitrac Embedded for Ricoh Basic Setup Guide Document History Revision Date Revision List November 2, 2012 Update for Equitrac
Equitrac Embedded for Ricoh Basic 1.1 Setup Guide 2012 Equitrac Corporation Equitrac Embedded for Ricoh Basic Setup Guide Document History Revision Date Revision List November 2, 2012 Update for Equitrac
ECM-VNA Convergence Connector
 ECM-VNA Convergence Connector Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: September 2016 2016 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International
ECM-VNA Convergence Connector Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: September 2016 2016 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International
McAfee File and Removable Media Protection Product Guide
 McAfee File and Removable Media Protection 5.0.8 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
McAfee File and Removable Media Protection 5.0.8 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
Azure MFA Integration with NetScaler
 Azure MFA Integration with NetScaler This guide focuses on describing the configuration required for integrating Azure MFA (Multi-Factor Authentication) with NetScaler. Citrix.com 1 NetScaler is a world-class
Azure MFA Integration with NetScaler This guide focuses on describing the configuration required for integrating Azure MFA (Multi-Factor Authentication) with NetScaler. Citrix.com 1 NetScaler is a world-class
Discovering Computers & Microsoft Office Office 2010 and Windows 7: Essential Concepts and Skills
 Discovering Computers & Microsoft Office 2010 Office 2010 and Windows 7: Essential Concepts and Skills Objectives Perform basic mouse operations Start Windows and log on to the computer Identify the objects
Discovering Computers & Microsoft Office 2010 Office 2010 and Windows 7: Essential Concepts and Skills Objectives Perform basic mouse operations Start Windows and log on to the computer Identify the objects
Sophos Mobile Control SaaS startup guide. Product version: 6.1
 Sophos Mobile Control SaaS startup guide Product version: 6.1 Document date: September 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your
Sophos Mobile Control SaaS startup guide Product version: 6.1 Document date: September 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your
Sophos Mobile as a Service
 startup guide product version: 8.6 Contents About this guide... 1 What are the key steps?... 2 Change your password... 3 Change your login name... 4 Activate Mobile Advanced licenses... 5 Check your licenses...6
startup guide product version: 8.6 Contents About this guide... 1 What are the key steps?... 2 Change your password... 3 Change your login name... 4 Activate Mobile Advanced licenses... 5 Check your licenses...6
SAP BusinessObjects Live Office User Guide SAP BusinessObjects Business Intelligence platform 4.1 Support Package 2
 SAP BusinessObjects Live Office User Guide SAP BusinessObjects Business Intelligence platform 4.1 Support Package 2 Copyright 2013 SAP AG or an SAP affiliate company. All rights reserved. No part of this
SAP BusinessObjects Live Office User Guide SAP BusinessObjects Business Intelligence platform 4.1 Support Package 2 Copyright 2013 SAP AG or an SAP affiliate company. All rights reserved. No part of this
AvePoint Governance Automation 2. Release Notes
 AvePoint Governance Automation 2 Release Notes Service Pack 2, Cumulative Update 1 Release Date: June 2018 New Features and Improvements In the Create Office 365 Group/Team service > Governance Automation
AvePoint Governance Automation 2 Release Notes Service Pack 2, Cumulative Update 1 Release Date: June 2018 New Features and Improvements In the Create Office 365 Group/Team service > Governance Automation
User Guide. BlackBerry Workspaces for Windows. Version 5.5
 User Guide BlackBerry Workspaces for Windows Version 5.5 Published: 2017-03-30 SWD-20170330110027321 Contents Introducing BlackBerry Workspaces for Windows... 6 Getting Started... 7 Setting up and installing
User Guide BlackBerry Workspaces for Windows Version 5.5 Published: 2017-03-30 SWD-20170330110027321 Contents Introducing BlackBerry Workspaces for Windows... 6 Getting Started... 7 Setting up and installing
S/MIME on Good for Enterprise MS Online Certificate Status Protocol. Installation and Configuration Notes. Updated: November 10, 2011
 S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
Using the VMware vrealize Orchestrator Client
 Using the VMware vrealize Orchestrator Client vrealize Orchestrator 7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Using the VMware vrealize Orchestrator Client vrealize Orchestrator 7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
MetaManager 3.3 New Features Guide METAMANAGER AN IBM GLOBAL SOLUTIONS DIRECTORY OFFERING BSP Software LLC 1/5
 METAMANAGER AN IBM GLOBAL SOLUTIONS DIRECTORY OFFERING Version 3.3 New Features Guide 2008 2009 BSP Software LLC 1/5 Product Information This document applies to MetaManager TM Series 3 version 3 and may
METAMANAGER AN IBM GLOBAL SOLUTIONS DIRECTORY OFFERING Version 3.3 New Features Guide 2008 2009 BSP Software LLC 1/5 Product Information This document applies to MetaManager TM Series 3 version 3 and may
USER GUIDE. MADCAP FLARE 2017 r3. Source Control: Git
 USER GUIDE MADCAP FLARE 2017 r3 Source Control: Git Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
USER GUIDE MADCAP FLARE 2017 r3 Source Control: Git Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
LiveNX Upgrade Guide from v5.1.2 to v Windows
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
IBM. Database Database overview. IBM i 7.1
 IBM IBM i Database Database overview 7.1 IBM IBM i Database Database overview 7.1 Note Before using this information and the product it supports, read the information in Notices, on page 39. This edition
IBM IBM i Database Database overview 7.1 IBM IBM i Database Database overview 7.1 Note Before using this information and the product it supports, read the information in Notices, on page 39. This edition
Versions. Overview. OU Campus Versions Page 1 of 6
 Versions Overview A unique version of a page is saved through the automatic version control system every time a page is published. A backup version of a page can also be created at will with the use of
Versions Overview A unique version of a page is saved through the automatic version control system every time a page is published. A backup version of a page can also be created at will with the use of
User Manual. Admin Report Kit for IIS (ARKIIS)
 User Manual Admin Report Kit for IIS (ARKIIS) Table of Contents 1 Admin Report Kit for Internet Information Server-(ARKIIS)... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements...
User Manual Admin Report Kit for IIS (ARKIIS) Table of Contents 1 Admin Report Kit for Internet Information Server-(ARKIIS)... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements...
Software Restriction for Zero Client Users (AppLocker Group Policy)
 Software Restriction for Zero Client Users (AppLocker Group Policy) Software Restriction for Zero Client Users by Using AppLocker Group Policy AppLocker Group policy Description: AppLocker Group Policy
Software Restriction for Zero Client Users (AppLocker Group Policy) Software Restriction for Zero Client Users by Using AppLocker Group Policy AppLocker Group policy Description: AppLocker Group Policy
PC Agent Quick Start. Opening the Agent. Logging in to the Agent. Connected Backup. Version 8.6. Revision 0
 T E C H N I C A L N O T E Version 8.6 PC Agent Quick Start Revision 0 Use this document as a quick reference for common Connected Backup PC Agent tasks. If the Agent is not on your computer, contact your
T E C H N I C A L N O T E Version 8.6 PC Agent Quick Start Revision 0 Use this document as a quick reference for common Connected Backup PC Agent tasks. If the Agent is not on your computer, contact your
Using the Subscriber Manager GUI Tool
 CHAPTER 11 Using the Subscriber Manager GUI Tool Published: December 23, 2013, Introduction This chapter describes how to use the Subscriber Manager (SM) graphical user interface (GUI) tool to configure
CHAPTER 11 Using the Subscriber Manager GUI Tool Published: December 23, 2013, Introduction This chapter describes how to use the Subscriber Manager (SM) graphical user interface (GUI) tool to configure
Area Access Manager User Guide
 Area Access Manager User Guide Area Access Manager User Guide Table of Contents Chapter 1: Introduction...9 Conventions Used in this Documentation... 9 Getting Started... 10 Licensing Requirements...
Area Access Manager User Guide Area Access Manager User Guide Table of Contents Chapter 1: Introduction...9 Conventions Used in this Documentation... 9 Getting Started... 10 Licensing Requirements...
Main Window. Overview. Do this Click the New Report link. Create a New Report.
 Overview Main Window Create a new report from a table or existing view Create a new report by defining a custom join Work with your custom reports Open a recently accessed custom report Work with reports
Overview Main Window Create a new report from a table or existing view Create a new report by defining a custom join Work with your custom reports Open a recently accessed custom report Work with reports
ImageNow Interact for Microsoft Office Installation and Setup Guide
 ImageNow Interact for Microsoft Office Installation and Setup Guide Version: 6.6.x Written by: Product Documentation, R&D Date: February 2011 ImageNow and CaptureNow are registered trademarks of Perceptive
ImageNow Interact for Microsoft Office Installation and Setup Guide Version: 6.6.x Written by: Product Documentation, R&D Date: February 2011 ImageNow and CaptureNow are registered trademarks of Perceptive
Attix5 Pro SE Backup Operator Mode
 Attix5 Pro SE Backup Operator Mode User Manual for Windows Your guide to using the SE Backup Client in Backup Operator mode. Includes a list of limitations. Introduction From V7.0.3, the Attix5 Pro Server
Attix5 Pro SE Backup Operator Mode User Manual for Windows Your guide to using the SE Backup Client in Backup Operator mode. Includes a list of limitations. Introduction From V7.0.3, the Attix5 Pro Server
