ActiveTrust Platform Dossier & TIDE
|
|
|
- Erick Bryant
- 5 years ago
- Views:
Transcription
1 ActiveTrust Platform Dossier & TIDE Quick Start Guide 2018 Infoblox Inc. All rights reserved. Page 1 of Infoblox Inc. All rights reserved.
2 Overview ActiveTrust Platform TIDE and Dossier Quick Start Guide ActiveTrust uses highly accurate machine-readable threat intelligence data via a flexible Threat Intelligence Data Exchange (TIDE) to aggregate, curate, and enable distribution of data across a broad range of infrastructure. TIDE enables organizations to ease consumption of threat intelligence from various internal and external sources, and to effectively defend against and quickly respond to cyberthreats. TIDE is backed by the Infoblox threat intelligence team that normalizes and refines high-quality threat intelligence data feeds. Infoblox Threat Intelligence Data Exchange (TIDE) collects and manages curated threat intelligence from internal and external sources in a single platform. It enables security operations to remediate threats more rapidly by sharing normalized TIDE data in real time with third-party security systems such as Palo Alto Networks, SIEM, etc. By leveraging highly accurate machine-readable threat intelligence (MRTI) data to aggregate and selectively distribute data across a broad range of security infrastructure, the end result is a highly refined feed with a very low historical false-positive rate. Infoblox Dossier is a threat investigation tool providing immediate contextual information on threats from a dozen sources (including TIDE) simultaneously. This allows threat analysts to save precious time in taking action against any identified threats. By using Dossier, accurate decisions may be made more quickly and with greater confidence, thereby shortening the threat s attack window. Infoblox Dossier threat indicator investigation provides rich threat context to prioritize incidents and respond quickly. Prerequisites Prerequisites ActiveTrust Dossier and TIDE are subscription-based services provided in Infoblox Cloud. There are no specific requirements for the software to access the services except a relevant subscription. Recent versions of Google Chrome are recommended to access ActiveTrust portal Infoblox Inc. All rights reserved. Page 2 of 41
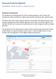
3 The ActiveTrust TIDE and Dossier User Interface Access to ActiveTrust TIDE and Dossier Dossier can be accessed from CSP at under the Analyze section. Dossier may also be accessed from the CSP dashboard by clicking on the Dossier shortcut on the left sidebar. The Portal is not integrated with CSP and separate credentials are required. Your credentials are provided in a welcome when your account is created. Home Dashboard and Navigation Menu Home Dashboard and Navigation Menu On the home dashboard you can find: Dossier Keyword Search widget a shortcut to start an Infoblox Dossier keyword search. Indicator Search widget a shortcut to perform an Infoblox Threat Indicator search. Active Indicator Filters search widget a shortcut to perform an Infoblox active indicator filter search. Daily Threat Types and Weekly Data Types widgets provide information about daily and weekly Infoblox published IOC s discovered/added by our Cyber Threat Intelligence team. Resources widget providing shortcuts to popular resource links. Partners widgets provide overview information about premium partner data feeds which are part of the TIDE marketplace and can be purchased a la carte. By selecting ActiveTrust in the upper left corner you can return to the start page/dashboard. The navigation menu is located on the top of the screen and provides an access to all functions of the portal. It consists of Data Management, Search, Resources and user s profile sub-menus Infoblox Inc. All rights reserved. Page 3 of 41
4 Data Management provides access to data governance and submission tools, link to the dashboard and Alexa Top domains. Search provides access to conducting Dossier and Indicator searches. Resources contains API guides, Threat Classification Guide, default threat indicators TTLs and description of the subscription levels. Your username : sub-menu with metric reports and user settings. User Settings and Metric Reports User Settings and Metric Reports Metric Reports Subscriptions include a limited number of Dossier and partners searches. Statistics per user, organization, partners, and dossier transactions are provided in Metric Reports. The menu is available only to an organization s administrators. User Settings On the User Management page, you can change your password and manage your API Keys. The passwords must satisfy the requirements described on the Change Password page. API keys are required to access Dossier and TIDE via the REST API. A user can create multiple API keys. There are no specific permissions associated with an API key. Only the key name and description can be edited. A key may be deactivated or deleted. In order to copy, please follow this simple procedure: Click on the API key. An info window Copying the key to the clipboard was successful will be displayed. To edit an API key, click on Active, Edit, or Remove as appropriate. To add an API key, click on the Create New Key link. Please refer to the RESOURCES section for examples of API key usage. User Management User Management 2018 Infoblox Inc. All rights reserved. Page 4 of 41
5 An Organization Administrator (OrgAdmin) user management role is available to organizations in ActiveTrust TIDE. This role is provisioned at the time the account is created, or upon request for organizations previously created without the organization admin role implemented. Please note, An OrgAdmin can only update or edit user accounts within their own organization. As an OrgAdmin, you can manage users within your own organization. The org administrator can perform the following tasks: View a list of all users in the organization along with their account information. Invite a new user. Update or change user information. Update or change a user s role. Reset a user s password. Activate or deactivate all other users within the organization. Can grant other users within the organization the role of OrgAdmin. Managing Users using the UI To manage an organization s users using the UI, do the following: From the ActiveTrust TIDE dashboard, navigate to the User Management page (your user name > Admin > User Management). A listing of the organization s current users will be displayed in the Users panel located on the left-hand side of the page. Inviting a New User 1. Click on the Add New User The Invite A New User panel will be displayed. 2. Select which role(s) the new user will be assigned. Multiple roles may be assigned by holding down the Shift key on your keyboard while selecting more than one user role. 3. Fill out the First Name, Last Name, and 4. Click the Invite button to invite the new user. When the pop-up window appears confirming your intent to create a new user, click on the Submit button to continue. 5. From the New User Credentials pop-up window, copy and paste the new user s logon credentials into an addressed to the user, before clicking on the OK 6. Verify in the Users panel that the new user s account has been created as intended. Updating the Account of a Current User 1. Click on the user s name in the Users The View User panel will be displayed. 2. Click on the Edit button in the View User panel to open the Edit User panel. 3. Select the types of edits you wish to make to the user s account. The types of edits that can be made include edits in the user s role, changes to the user s account information, resetting the user s password, and activating/deactivating the user s account Infoblox Inc. All rights reserved. Page 5 of 41
6 4. Once the desired edits/changes have been made to the user s account, click on the Update button to apply changes to the user s account. 5. In the Update User pop-up window, click OK to confirm you want to update the user s account. 6. Verify in the Users panel that the user s account has been updated as intended. Managing Users using the API To manage an organization s users using the API, do the following: Adding a New User This API call adds a new user to the caller s organization. The person making the call must be assigned the role of OrgAdmin to make the call. Request Request endpoint POST /api/admin/accounts/org/users Request Body Field Type Description firstname lastname password roles string string string string Array of strings User , chars, required User first name, chars, required User last name, chars, required User password, 8 72 chars, optional. Mix of upper and lowercase characters, numbers and non-alphanumerics List of user roles available: DataAdmin, DataUser, DataWriter, Reports, OrgAdmin Response 2018 Infoblox Inc. All rights reserved. Page 6 of 41
7 If the submission is successful, the HTTP code 200 (OK) will be returned, along with a JSON object that includes the api key generated for the user. Example Using curl to add user to the caller s organization. curl -H "Content-Type":"application/json" -u [YOUR_API_KEY]: -X POST " -d '{" ":"djfrosh@bankorg.net","firstname":"dj", "lastname":"frosh", "password":"djfr#shl1te", "roles":["dataadmin", "DataUser", "DataWriter","Reports"]}' Response: { } "code": 0, "status": "success", "data": { "httpcode": 201, "data": { "code": 0, "status": "success", "data": { " ": "djfrosh@bankorg.net", "uid": "djfrosh@bankorg.net", "oid": "BankOrg", "apikey": "a7d8ab2a43b6406bbd8c4f3d33698e9f6087e81fc34c4e4199d5c4ecbbc0f502" } } } Updating a User s Information This API call allows the editing of a current user to the caller s organization. The person making the call must possess the role of OrgAdmin to make the call. Request 2018 Infoblox Inc. All rights reserved. Page 7 of 41
8 Request endpoint PUT /api/admin/accounts/org/user/{user_id} It is required to have at least one of the below fields: Request Body Field Type Description firstname string User first name, chars lastname string User last name, chars Path Parameters Field Type Description user_id string User , targeted user to be updated Response If the submission is successful, the HTTP code 200 (OK) will be returned, along with a JSON object. Example Using curl to update firstname and lastname for user djfrosh@bankorg.net curl -H "Content-Type":"application/json" -u [YOUR_API_KEY]: -X POST " -d '{" ":"djfrosh@bankorg.net","firstname":"dj", "lastname":"frosh", "password":"djfr#shl1te", "roles":["dataadmin", "DataUser", "DataWriter","Reports"]}' 2018 Infoblox Inc. All rights reserved. Page 8 of 41
9 Response: { } "code": 200, "status": "success" Updating a User s Role This API call allows the updating of a current user s role within the caller s organization. The person making the call must possess the role of OrgAdmin to make the call. Request Request endpoint PUT /api/admin/accounts/org/user/{user_id}/roles Request Body Request Body Field Type Description roles Array of string List of user roles available: DataAdmin, DataUser, DataWriter, Reports, OrgAdmin Path Parameters Path Parameters Field Type Description user_id string User , targeted user to be updated Response If the submission is successful, the HTTP code 200 (OK) will be returned with a JSON response object Infoblox Inc. All rights reserved. Page 9 of 41
10 Example Using curl to update roles for user curl -H "Content-Type":"application/json" -u [YOUR_API_KEY]: -X PUT g.net/roles" -d '{"roles":["dataadmin", "DataUser"]}' Response: { } "code": 200, "status": "success" Activating/Deactivating a User s Account Using this API call a user s account within the caller s organization can be activated or deactivated. The person making the call must possess the role of OrgAdmin to make the call. Request Request endpoint PUT /api/admin/accounts/org/user/{user_id}/active/{is_active} Payload N/A 2018 Infoblox Inc. All rights reserved. Page 10 of 41
11 Path Parameters Field Type Description user_id string User , targeted user to be updated is_active boolean User status, true to activate user, false to deactivate user Response If the submission is successful, the HTTP code 200 (OK) will be returned, along with a JSON object. Example curl -u [YOUR_API_KEY]: -X PUT " korg.net/active/true" Response: { "code": 0, "status": "success", "data": { "auth": { "httpcode": 200, "data": { 2018 Infoblox Inc. All rights reserved. Page 11 of 41
12 } } "code": 0, "status": "success" } }, "admin": { "httpcode": 200, "data": { "code": 200, "status": "success" } } Resetting a User s Password Using this API call a user s password can be reset within the caller s organization. The person making the call must possess the role of OrgAdmin to make the call. Request Request endpoint POST /api/auth/credentials/password/reset/{user_id} Payload Request Body Field Type Description new_password string New password. Required chars. At least one uppercase. At least one lowercase. At least one number. At least one special character (specified below) or space:! #$%&'()*+,-./:;<= 2018 Infoblox Inc. All rights reserved. Page 12 of 41
13 Path Parameters Field Type Description user_id string User , targeted user to be updated Response If the submission is successful, the HTTP code 200 (OK) will be returned, along with a JSON object. Example curl -H Content-Type : application/json -u [YOUR_API_KEY]: -X POST -d { new_password : Test.Pass.1 } Response: { "code": 200, "status": "success" } Get User list Using this API call a list of all the users within the caller s organization may be obtained. The person making the call must possess the role of OrgAdmin to make the call. Request Request endpoint GET /api/admin/accounts/org/users Response 2018 Infoblox Inc. All rights reserved. Page 13 of 41
14 If the submission is successful, the HTTP code 200 (OK) will be returned, along with a JSON object. The root key of the object is data. The value of the root object is an array of user objects containing user profile, roles, and active status. Example curl -X GET -u [YOUR_API_KEY]: Response: { } "code": 0, "status": "success", "data": [ { "id": "j.j@bankorg.net", "status": "inactive", "profile": { " ": "j.j@bankorg.net", "fullname": "John Jones", "firstname": "John", "lastname": "Jones", "rolestring": "DataAdmin DataUser DataWriter Reports" }, "roles": [ "DataAdmin", "DataUser", "DataWriter", "Reports" ] }, { "id": "j.joans@bankorg.net", "status": "inactive", "profile": { " ": "j.joans@bankorg.net", "fullname": "Jon joans", "firstname": "Jon", "lastname": "joans", "rolestring": "DataAdmin DataUser DataWriter Reports" }, "roles": [ "DataAdmin", "DataUser", "DataWriter", "Reports" ] 2018 Infoblox Inc. All rights reserved. Page 14 of 41
15 } } ] Get Available Roles for an Organization Using this API call all available user roles within the caller s organization may be obtained. The person making the call must possess the role of OrgAdmin to make the call. Request Request endpoint GET /api/admin/accounts/org/roles Response If the submission is successful, the HTTP code 200 (OK) will be returned, along with a JSON object. Example Request using curl to return available roles for the caller s organization. curl GET -u [YOUR_API_KEY]: Response: { "code": 200, "status": "success", "data": [ { "name": "DataAdmin", "description": "Data sharing administrators", "org": "TEST_ORG" }, { "name": "DataUser", "description": "Organization data users", "org": "TEST_ORG" }, { "name": "DataWriter", 2018 Infoblox Inc. All rights reserved. Page 15 of 41
16 } ] "description": "Organization data users", "org": "TEST_ORG" }, { "name": "OrgAdmin", "description": "Organization administrators", "org": "TEST_ORG" }, { "name": "Reports", "description": "Access to organization reports", "org": "TEST_ORG" }, { "name": "User", "description": "Organization users", "org": "TEST_ORG" } Dossier Dossier Dossier search is available through the web-interface and via the REST API. The portal uses the same API so there is no difference in available filters and search results when using either the Web or the API searches. Dossier Threat Indicators Dossier Threat Indicators The Dossier threat indicator research tool offers the following features. Using the Dossier toolset, users may make accurate decisions more quickly and with greater confidence based on the contextual information obtained from a dozen sources simultaneously. Dossier source descriptions are as follows: Alexa Alexa is a global pioneer in the world of analytical insight. Their vast experience means they have developed the most robust and accurate web analytics service. Search results from Alexa provide a ranking from the global Top 1,000,000 Sites list Infoblox Inc. All rights reserved. Page 16 of 41
17 ActiveTrust ActiveTrust is Infoblox s flagship data collection. Queries are executed against all data within ActiveTrust and data provider subscriptions. Current DNS Search results from Current DNS provide all the available information about a given hostname from DNS nameservers. Google Custom Search Google Custom Search, or GCS, searches anti-virus analysis pages, malware analysis blogs and other related malware/rce websites. Google Custom Search is a platform provided by Google that allows web developers to feature specialized information in web searches, refine and categorize queries and create customized search engines. Geolocation The geolocation tool plots the identified coordinates on a map, providing city-level accuracy. Other information including ISP, city, region, lat/long, and country are also included. Google Safe Browsing Google Safe Browsing, or GSB, is a Google service that enables applications to check URLs against Google s constantly updated lists of suspected phishing, malware, and unwanted software pages. isight isight Partners is the leading provider of global cyber threat intelligence, delivering unparalleled insight into your cyber adversaries, their motives and methods. isight provides instant reporting on threat actors targeting organizations, plus related Indicators of Compromise (IOCs) to help prioritize relevant threats, speed detection of advanced attacks and bolster responses to minimize further risk. isight is available as a separate subscription and is not automatically included with Dossier. Passive DNS Passive DNS is the historical DNS record for hostnames. When searching a hostname, Passive DNS will return all IPs that hostname has resolved to and were caught by the Passive DNS sensors in the previous 12 months. When searching an IP, Passive DNS will return all hostnames that have pointed to that IP. Note: Not every DNS change is caught, so there will be missing information. Reverse DNS The Reverse DNS tool performs a reverse DNS lookup of an IP address by searching domain name registry and registrar tables. Reverse Whois DomainTools Reverse Whois lookup API allows a lookup in Whois records that contain a string. This is typically used for identifying information like an address or name. The results can reveal related, registered domains Infoblox Inc. All rights reserved. Page 17 of 41
18 Secure Domain Foundation Secure Domain Foundation, or SDF, is a Canadian incorporated not-for-profit organization whose primary mission is to provide Domain Name Registrars, registries (cctld & gtld), hosting providers, DNS operators, and other Internet infrastructure providers with the tools they need to combat abuse of their services and a forum for sharing intelligence on bad actors. This version of SDF s API is designed specifically to assist domain registries, registrars, and hosting providers to easily obtain validation and reputation information on certain account or Whois related data points. Malware Analysis Data collection of malicious content detected by aggregation of antivirus engines and website scanners. Whois DomainTools Whois lookup API provides the ownership record for a domain name or IP address with basic registration details, all in well-structured format that groups together important data. Dossier Search Dossier Search The indicator search returns data only from the ActiveTrust database but the search is not limited to a specific indicator (e.g. a hostname). The search interface currently returns a maximum of 25,000 records. It is recommended to use API for larger data sets. Because of size of the available data, it is recommended to apply filters to limit the resulting dataset. When a keyword is used to search data, other filters are not applied even if they were specified. The result dataset can be exported in XML, CSV or JSON format. It is also possible to limit the number of returns by inputting a value in the Records Returned field. Indicator Search Indicator Search The indicator search returns data only from the ActiveTrust database but the search is not limited to a specific indicator (e.g. a hostname). The search interface currently returns a maximum of 25,000 records. It is recommended to use API for larger data sets. Because of size of the available data, it is recommended to apply filters to limit the resulting dataset. When a keyword is used to search data, other filters are not applied even if they were specified. The result dataset can be exported in XML, CSV or JSON format. It is also possible to limit the number of returns by inputting a value in the Records Returned field Infoblox Inc. All rights reserved. Page 18 of 41
19 BRIC Score BRIC Score The Business Risk Impact Calculation score (BRIC) identifies the likely business impact of blocking a hostname to the average company with no insight into their network practices. The score for a hostname is based on a combination of factors; the domain s popularity, the robustness of the domain s resources, the domain s history, and the domain s order of separation from known threats. The factors making up the BRIC score can be assessed and assigned an integer value of 0-100, to match an enterprise defender s preferences. A low BRIC score value is indicative of a lesser likelihood of impacting a company when blocking a hostname, while a high BRIC score indicative of a greater likelihood of companies of impacted a company by blocking a hostname. Viewing the BRIC Score in the UI The BRIC Score for hostnames may be viewed in the search results pane after an indicator search has been performed. please note, BRIC Score data is only available for the IID feed. For each hostname in the IID feed, the hostname will have an associated BRIC Score ranging from BRIC Score API Calls The following API calls may be used to retrieve BRIC Score data: /api/data/threat/<type>?<ip,host,url>=<indicator>&bric_score=<0-100> /api/data/threat/<type>?bric_score_from=<0-100>&bric_score_to=<0-100> /api/data/threat/state/<type>?<ip,host,url>=<indicator>&bric_score=<0-100> /api/data/threat/state/<type>?bric_score_from=<0-100>&bric_score_to=<0-100> /api/data/threat?type=<ip,host,url>&<ip,host,url>=<indicator>&bric_score=<0-100> /api/data/threat/state?type=<ip.host,url>&bric_score_from=<0-100>&bric_score_to=<0-100> When performing an API call to retrieve the BRIC score for hostnames in the IID partner feed, the following information will be displayed in the report body. An example API report body is displayed below Infoblox Inc. All rights reserved. Page 19 of 41
20 { "id": "c fa7-11e8-91b6-e9a8dd7a1bc9", "type": "IP", "ip": " ", "profile": "IID", "property": "MalwareC2_Generic", "class": "MalwareC2", "threat_level": 100, "expiration": " T21:02:53.000Z", "detected": " T21:02:53.000Z", "received": " T23:11:20.819Z", "imported": " T23:11:20.819Z", "up": "true", "batch_id": "c516c127-5fa7-11e8-91b6-e9a8dd7a1bc9", "bric_score": 10 } BRIC Score API call examples Several example API calls for retrieving BRIC Score information are provided: Running an API call for a specific BRIC Score When performing a threat query using the API, records may be requested based on a specific BRIC score by amending the API query. For example: /api/data/threats?text_search= &bric_score=10 Running an API call for a specified range of BRIC scores When performing a threat query using the API, records may be requested based on a range of BRIC scores. For example: /api/data/threats?text_search= &bric_score_from=10&bric_score_to=50 Batch Submissions BRIC Scores may also be retrieved when searching batch submissions. In this case, bric_score can be appended to a query to return hostname BRIC scores in the IID partner feed Infoblox Inc. All rights reserved. Page 20 of 41
21 Search for Lookalike Domains Search for Lookalike Domains Lookalike domains are domains that are found to be visually similar (look-alike) with other domains. These domains are composed using methods such as replacing letters with visually confusion ones (e.g. o to 0, l to 1, w to vv), switching to different top level domains (e.g..com to.cc), among others. These domains are often found in cyber attacks seeking brandjacking, traffic redirection, and phishing. TIDE supports searching for lookalike domains through the UI and through the API. To retrieve records through the TIDE UI, the Indicator Search is used. To retrieve records through API, two methods are supported: 1. Running an API call using the Swagger page. 2. Running an API call through Terminal Searching for Lookalike Domains via the TIDE UI You can use the Indicator Search in the TIDE UI to search for lookalike domains. Note that Indicator Search is limited to a maximum of 25,000 records. The default number of search returns is limited to 1,000 records. To search for lookalike domains using Indicator Search, follow these steps: 1. Select Hostnames for data type. 2. For Threat Class, deselect All and select Policy. 3. From the Data Provider options, deselect All and select IID. 4. Click the Search button to run the search query. 5. From the returned search results, in the Property column, apply a sort to classify the different policies according to type. 6. Scroll through the returned search results until the lookalike domains are located (Policy_LookalikeDomains). From the returned indicator search results, you can perform a Dossier search against a selected lookalike domain to discover additional details on the indicator. You can download the search results as an XML, CSV, or JSON file. Searching for Lookalike Domains using an API call on the Swagger page To run a search for a lookalike domain in TIDE using Swagger, follow these steps: 2018 Infoblox Inc. All rights reserved. Page 21 of 41
22 1. Navigate to the Manage API Keys page (user name > User Settings > User Management Manage API Keys). 2. Select an active API key and copy it. 3. Navigate to the Data API Guide (Resources > API guides > Data API Guide). 4. Paste the copied API key into the api key text field. 5. Click the Enter API key button. A modal window will appear acknowledging that your API key has been accepted. 6. From the list of ActiveTrust Platform Data Service REST APIs, click threat: Threat APIs to reveal all available API GET calls. 7. From the list of GET calls, click State Table API (/data/threats/state/(type)) to display all available search parameters. Note that while running any of the threat API calls, TIDE will return data on lookalike domains. The recommended GET call to run when querying the system for lookalike domains is the State Table. 8. For the type parameter, select host. 9. For the property parameter, input Policy_LookalikeDomains. 10. Click the Try it out button to run the call. Once you execute the API call, the Response Body of the returned search will yield the requested lookalike domain data. By default, TIDE returns 100 lookalike domain records. However, by adjusting the rlimit parameter of the query, you may request fewer or more records (as few as one record and as many as 500 records). A lookalike domain query returns data as shown in the following example: { } "id": "dc396246y e6-91e8-77e31fb69hcv", "type": "HOST", "host": "whatsapp.qxowgqhtny.site", "domain": "lookalikedomain.site", "tld": "site", "profile": "IID", "property": "Policy_LookalikeDomains", "class": "Policy", "threat_level": 100, "detected": " T02:15:07.473Z", "received": " T15:37:24.173Z", "imported": " T15:37:24.173Z", "expiration": " T02:15:07.473Z", "dga": false, "up": true, "batch_id": "dc396246y e6-91e8-77e31fb69hcve", "extended": { "extended": "301a337ecd3490a61bc54e4dfd2bcg610ded2" } 2018 Infoblox Inc. All rights reserved. Page 22 of 41
23 Searching for Lookalike Domains using an API Call in Terminal To run a search for a lookalike domain in TIDE using Terminal, use the following API call. When using an API call in Terminal, all records within the system can be obtained. curl -u [YOUR_API_KEY]: ' omains&rlimit=100' The resulting response will retrieve the requested number of records. Resources Resources Under the Resources menu are located the API guides and the Threat Classification guides. The API guides are tool kits which can be used to build API calls and review retrieved data. The Threat Classification guide defines the common threat intelligence data classification groups in the TIDE platform, as well as the specific properties that each group encompasses. Data Management Data Management ATP-TIDE allows the user to effectively and efficiently manage data with many useful tools including Alexa Top, data submission, and the associated governance system. It also includes the ability to run robust API calls within the TIDE ecosystem. ActiveTrust Threat Classifications Guide TIDE Threat Classifications The TIDE Threat Classification Guide defines the common threat intelligence data classification groups in the TIDE platform as well as the specific properties that these groups encompass Infoblox Inc. All rights reserved. Page 23 of 41
24 When using the Threat Classification Guide, the threat indicators returned by a search contain Class and Property fields e.g. class Bot and property Bot_Bankpatch. The Threat Classification Guide contains descriptions of all classes and properties supported by Dossier and TIDE. Each threat indicator belongs to a specific class and has a default expiration time (TTL). The default expiration times for all threat classes are provided on the Default TTLs page. To search for a specific threat type, search by threat class or property using the search box to narrow down the results. Expired threat indicators are still available in the database and returned by a search, but they are not included in the ActiveTrust/DNS Firewall feeds. The Cyber Threat Intelligence team periodically checks the indicators for validity and accuracy. Alexa Top Alexa Top Alexa top is a ranking of the most popular sites in the Internet. This tool provides access to Alexa Top sites. Default Threat Time-To-Live (TTL) Default TTLs The default TTL (time-to-live) list displays each threat class s default time-to- live value within TIDE. Please note, the TTL values may vary. Default TTLs Class Property TTL APT Bot CompromisedHost DDoS ExploitKit IllegalContent InternetInfrastructure 20 years 7 days 30 days 12 hours 20 days 3 days 1 year 2018 Infoblox Inc. All rights reserved. Page 24 of 41
25 MaliciousNameserver MalwareC2 Malware C2DGA MalwareDownload Phishing Policy Proxy Scam Scanner Sinkhole Spambot UncategorizedThreat Undefined UnwantedContent Whitelist 90 days 60 days 15 days 30 days 30 days 3 days 3 days 14 days 7 days 1 year 5 days 30 days 1 day 14 days 1 year Infoblox Threat Intelligence Data Exchange (TIDE) Infoblox Threat Intelligence Data Exchange Infoblox Threat Intelligence Data Exchange provides an access to highly curated threat indicators and data governance tools to share indicators inside the organization and/or between the organizations Infoblox Inc. All rights reserved. Page 25 of 41
26 Infoblox TIDE and Dossier API Guides Infoblox ActiveTrust and Dossier API Guides The following ActiveTrust-TIDE and Dossier guides are accessible only through the UI. Swagger Rest API Guides Data API Guide Dossier API Guide Basic Admin API Guide (this guide is available to admin only) Dossier API Guide Advanced (this guide is available to admin only) Web-based API Guides API FAQ Default TTLs Threat Classification Guide PDF API Guides TIDE API Getting Started Guide Dossier API Reference Guide TIDE API Guide TIDE API TIDE API consist of a Data API and an Admin API. The Data API is used to submit and retrieve threat indicators. The Admin API provides access to governance policies, data profiles, and information about available sources and targets for data sharing. The TIDE platform provides API Guides, which describe all filters and options available by using an API call. Before using the API guides, an API Key must be entered into the api_key field. The API keys are configured in the Manage API Keys section of the User Settings page. The TIDE platform leverages the Basic Auth method in HTTP/HTTPS to transport the API key. The API key is passed in the username field. The password field should be set to an empty string. All data fields (including filter) represented in ISO 8601 format Infoblox Inc. All rights reserved. Page 26 of 41
27 Dossier API Dossier API Customers commonly use Dossier API Basic. It provides access to all information available on the portal. The Dossier API Basic Guide describes all available filters and options. Before using the Dossier API Guide, you need to enter an API Key in api_key field. The API keys are configured on the User Settings page under Manage API Keys. The ActiveTrust platform leverages the Basic Auth method in HTTP/HTTPS to transport the API key. The API key is passed in the username field. The password field should be set to an empty string. When a test query is executed, the API Guide returns: a CURL command to request the data, response body and response code. The listing below contains a sample CURL command which retrieves information about eicar.top domain in JSON format, which is the only supported export format for API based indicator search. curl -H Content-Type : application/json -X POST -u <User_API_Key>: -d { target :{ one :{ type : host, target : eicar.top, sources : [ alexa, atp, dns, gcs, gsb, malware_analysis, pdns, ptr, rwhois, sdf, whois ]}}} Depending on the amount of data being requested, it may take some time to retrieve the data. In the case where the data is not required immediately, a search can be executed with the wait parameter set to false and retrieved later using the Dossier API Advanced call. In this case the first search (Basic API call) will return the job_id. The status of the job and results can be retrieved using the Advanced API lookup_jobs_management calls. The URL below retrieves results of a job using the job_id parameter: The Dossier Advanced API provides these API calls: Lookup Jobs APIs (lookup_jobs_management) API calls return status and results of the lookup jobs. Lookup Job Index (lookup_jobs_index) API calls return list of the performed searches per user or organization Infoblox Inc. All rights reserved. Page 27 of 41
28 Worker Status (worker_stats) API calls provide statistics per source, e.g. alexa, atp, dns etc. Service Metadata (service_metadata) API calls return information about supported sources, targets, supported sources by targets and targets descriptions. Data API Data API ActiveTrust Data API consist of: Threat Batch APIs (batch) used to submit own threat indicators and retrieve details about uploaded batches. Dashboard APIs (dashboard) used to retrieve daily, weekly and monthly statistics by threats. This information is available on the dashboard. Threat Feed APIs (feed) used to create feeds and retrieve threat indicators using the feeds. Property APIs (property) used to retrieve threat properties registered on ActiveTrust platform. Threat Search APIs (search) allow to save predefined searches of threat indicators and evoke them later by a name. Threat APIs (threat) search threat indicators on ActiveTrust platform. Threat Class APIs (threat_class) used to retrieve threat classes registered on ActiveTrust platform. Whitelist Host APIs (whitelist_host) used to check if a hostname is whitelisted. If the call was evoked without the parameter, it returns all whitelisted hostnames. Whitelist IP APIs (whitelist_ip) used to check if an IP address is whitelisted. If the call was evoked without the parameter, it returns all whitelisted IP ranges and IPaddresses Infoblox Inc. All rights reserved. Page 28 of 41
29 Admin API Admin API ActiveTrust Admin API consist of: Sharing Info APIs (sharing) provide information about organizations and groups which provide thereat indicators or can be shared with. Resource Info APIs (resources) manage data profiles. GET requests retrieve information, POST create a profile. API FAQ contains information how to create a profile. Governance Policy APIs (governance) manage governance policies. GET requests retrieve information, POST create a policy. API FAQ contains information how to create a policy. CURL Command Requests Request Description curl net:8000/api/data/threats/h ost?profile=iid&dga=false& from_date= T00:00:00Z&data_format =csv&rlimit=100 -u [YOUR_API_KEY]: 1000 threat indicators in CSV format which were added after GMT (Date/Time is in ISO 8601 format) by Infoblox and are not DGA. curl et:8000/api/data/threats/stat e/host?profile=iid&data_for mat=json -u [YOUR_API_KEY]: All currently active hostname threats detected by Infoblox (IID) 2018 Infoblox Inc. All rights reserved. Page 29 of 41
30 curl type=host&profile=iid& period=30min&data_forma t=json -u [YOUR_API_KEY]: Infoblox-sourced hostnames for the past 30 minutes. curl profile=ais- FEDGOV,iSIGHTPARTNE RS& period=1w&data_format=c sv -u [YOUR_API_KEY]: isight Partners and DHS AIS IPs for the past week, in CSV format. Governance Policies and Data Submission Governance Policies and Data Submissions Customers can submit/upload their own threat indicators and share them with other organizations or groups that they have the rights to do so. Submitted data is available via Dossier and Indicator searches on the portal and through the Data API. Data Governance Policies allow organizations to control how their submitted data is shared with other organizations or groups on the platform. Infoblox can enable accessing and data sharing between organizations upon request. Policies can be used for multiple data submissions and are only visible within your organization. Data profiles are used to identify data in the platform from one or many data submissions. A data profile must be specified when data is submitted. Data profiles are associated with governance policies, which control who can access the data. When a data profile is created it must be associated with a governance policy Infoblox Inc. All rights reserved. Page 30 of 41
31 Users can submit threat indicators on the portal or via Data API. In order to submit data, the following is required: 1. A governance policy defines how data is shared. 2. A data profile defines if standard TTL should be used and a governance policy. Users can submit data using the following formats: JSON, CSV, XML, TSV (tab separated values). For all data formats the submitted data must identify the data/record type in addition to the list of data records. For CSV and TSV the record type must be provided as one of the columns. For JSON and XML the record type is defined in a separate top level field. The record type field can be one of the following values: host, ip, or url. It is not possible to upload data using different profiles or different record types in the same file. Threat data consists of file-level fields and record-level fields. The table below contains descriptions of all available fields. Threat Data Fields Field Name Description File-level fields profile data profile id or name record_type host, ip, or url external_id string indicating an external ID to assign to the batch 2018 Infoblox Inc. All rights reserved. Page 31 of 41
32 record surrounds the individual record(s) in the XML and JSON formats Record-level fields host threat hostname ip threat IP address url threat URL property threat type target target of threat detected date/time threat was detected, in ISO 8601 format duration duration of this threat in XyXmXwXdXh format, expiration date will be set to the detected date + this duration 2018 Infoblox Inc. All rights reserved. Page 32 of 41
33 The listing below contains a sample data submission in XML format. <feed> <profile>sampleprofile</profile> <record_type>ip</record_type> <record> <ip> </ip> <property>phishing_phish</property> <detected> t154742z</detected> </record> <record> <ip> </ip> <property>scanner_generic</property> <detected> t154242z</detected> <duration>42y0m0w0d42h</duration> </record> </feed> The listing below contains a sample data submission in JSON format. { } "feed": { "profile": "SampleProfile", "record_type": "host", "record": [ {"host": " "property": "Scanner_Generic", "detected": " T154242Z", "duration":"42y0m0w0d42h"}, {"host": " "property": "Phishing_Phish", "detected": " T154742Z"} ] } The listing below contains a sample data submission in CSV format. record_type,url,profile,detected,property url," "UnwantedContent_Parasite" url," "Scam_FakeGiftCard" 2018 Infoblox Inc. All rights reserved. Page 33 of 41
34 The recommended limit for the number of records in a given data submission is 50,000. The maximum number of records should be no more than 60,000 at this point in time. Submitting Threat Indicators Submitting Threat indicators ActiveTrust Admin API consist of: The listing below contains a sample curl command to submit threat indicators in JSON format to TIDE. curl -X POST -H "Content-Type: application/json" -u [YOUR_API_KEY]: The system determines the format of the input data based on the Content-Type HTTP header (application/xml, text/xml, application/json, text/plain, text/csv, text/tab-separatedvalues, text/tsv, text/psv). If the Content-Type is not match with predefined types, or is not specified, it tries to determine the format dynamically by reading the first part of the data. It s safest to specify the format in the Content-Type. The file format is described in Governance policies and data submission chapter. Searching for Threat Indicators Searching for Threat indicators Data Threat API calls are used to search threat indicators. Submitted threat indicators are also available for the search. The resulting dataset can be formatted in JSON, XML, STIX, CSV, TSV, PSV, CEF. The threat indicators can be used by 3rd party solutions, e.g. with Palo Alto NGFW (please check Implementing Infoblox TIDE feeds into Palo Alto Networks Firewalls deployment guide for details) after a simple post processing. It is highly recommended to limit amount of retrieving data by applying filters. The table below contains sample requests using CURL command Infoblox Inc. All rights reserved. Page 34 of 41
35 CURL Command Requests Request Description curl t:8000/api/data/threats/host?p rofile=iid&dga=false&from_d ate= T00:00:00Z&data_format= csv&rlimit=100 -u [YOUR_API_KEY]: 1000 threat indicators in CSV format which were added after GMT (Date/Time is in ISO 8601 format) by Infoblox and are not DGA. curl :8000/api/data/threats/state/ho st?profile=iid&data_format=js on -u [YOUR_API_KEY]: All currently active hostname threats detected by Infoblox (IID) curl et:8000/api/data/threats?typ e=host&profile=iid& period=30min&data_format=j son -u [YOUR_API_KEY]:period=30 min&data_format=json -u [YOUR_API_KEY]: Infoblox-sourced hostnames for the past 30 minutes Infoblox Inc. All rights reserved. Page 35 of 41
36 curl et:8000/api/data/threats?prof ile=ais- FEDGOV,iSIGHTPARTNER S& period=1w&data_format=csv -u [YOUR_API_KEY]: isight Partners and DHS AIS IPs for the past week, in CSV format. Export of Threat Indicators for 3rd Party Solutions Exporting Threat indicators TIDE s threat indicators can be used by 3rd party solutions, e.g. with Palo Alto NGFW (please check Implementing Infoblox TIDE feeds into Palo Alto Networks Firewalls deployment guide for details) after a simple post-processing. It is highly recommended to limit amount of retrieving data by applying filters. The table below contains sample requests using CURL command. CURL Command Requests Request Description curl 00/api/data/threats/host?profile=II D&dga=false&from_date= threat indicators in CSV format which were added after GMT (Date/Time is in ISO 8601 format) by Infoblox and are not DGA Infoblox Inc. All rights reserved. Page 36 of 41
37 04T00:00:00Z&data_format=csv&r limit=100 -u [YOUR_API_KEY]: curl 0/api/data/threats/state/host?Profile =IID&data_format=json -u [YOUR_API_KEY]: All currently active hostname threats detected by Infoblox (IID) curl 00/api/data/threats?type=host&pr ofile=iid& period=30min&data_format=json -u [YOUR_API_KEY]: Infoblox-sourced hostnames for the past 30 minutes. curl 00/api/data/threats?profile=AIS- FEDGOV,iSIGHTPARTNERS& period=1w&data_format=csv -u [YOUR_API_KEY]: isight Partners and DHS AIS IPs for the past week, in CSV format. DHS Automated Information Sharing (AIS) Program Infoblox AIS Program Overview and Deployment Guide DHS Automated Information Sharing (AIS) Program 2018 Infoblox Inc. All rights reserved. Page 37 of 41
38 Introduction to AIS Introduction This document provides an overview of the DHS Automated Indicator Sharing (AIS) Program Threat Indicator Feeds and preliminary steps on how to deploy and utilize this data in the protection of your network. As this program evolves, Infoblox will enhance our applicable customer offerings in a continuous effort to deliver timely, accurate, and comprehensive threat intelligence in ways that customers can efficiently consume. AIS: A Cybersecurity Block Watch AIS: A Cybersecurity Block Watch As stated on the DHS website, The Department of Homeland Security s (DHS) free Automated Indicator Sharing (AIS) capability enables the exchange of cyber threat indicators between the Federal Government and the private sector at machine speed. Threat indicators are pieces of information like malicious IP addresses or the sender address of a phishing (although they can also be much more complicated). AIS is a part of the Department s effort to create an ecosystem where as soon as a company or federal agency observes an attempted compromise, the indicator will be shared in real time with all our partners, protecting them from that threat. That means adversaries can only use an attack once, which increases their costs and ultimately reduces the prevalence of cyber attacks. While AIS won t eliminate sophisticated cyber threats, it will allow companies and federal agencies to concentrate more on them by clearing away less sophisticated attacks. Ultimately, the goal is to commoditize cyber threat indicators through AIS so that tactical indicators are shared broadly among the public and private sector, enabling everyone to be better protected against cyber attacks. Infoblox s Role as a Commercial Capability for AIS Infoblox s Role as a Commercial Capability for AIS Infoblox supports leveraging collective threat intelligence to broaden our customers viewpoints into the external threat space. In many cases, indicators that start out as suspicious broken infrastructure from one organization s perspective quickly become threat 2018 Infoblox Inc. All rights reserved. Page 38 of 41
39 attack components for another organization. As the market leader in core network services, and by actively participating in and enhancing programs like AIS, Infoblox can function as an effective distribution mechanism where our customers can realize the outsized impact of Threat Intelligence Exchange Programs like AIS. Utilize AIS Data Today with Infoblox ActiveTrust Utilize AIS Data Today with Infoblox ActiveTrust As a qualified commercial capability provider, Infoblox has completed the technical and operational integrations necessary to distribute AIS threat data to our private sector customers. In addition, we have completed the terms of use and interconnectivity agreements on behalf of our customers who wish to deploy this data in their network protection mechanisms immediately. No additional agreements are required. Infoblox presents the AIS Threat Indicators in a variety of ways within our ActiveTrust Solutions: Threat Intelligence Data Exchange (TIDE): o For bulk download use cases, customers can pull the historical and updated AIS indicator sets both manually and via the TIDE API in a variety of formats. o For correlation use cases, customers can search the AIS data set for evidence of specific hostnames or IP addresses. Dossier: o For customers who have access to AIS Commercial threat indicators, Dossier will be automatically enabled and search against this data set. For those AIS indicators where additional context is needed, Dossier query results offer a broad set of information for better threat response and triage. RPZ Feeds: o Infoblox offers curated sets of threat indicators for native inclusion in Infoblox DNS Firewall implementations. o This allows you to leverage your DNS Resolver as the AIS integration engine, then block or alert on outbound traffic that intersects with the most recent AIS Threat Data Infoblox Inc. All rights reserved. Page 39 of 41
Infoblox TIDE User Guide
 Infoblox TIDE User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 Overview of TIDE Overview TIDE uses highly accurate machine-readable threat
Infoblox TIDE User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 Overview of TIDE Overview TIDE uses highly accurate machine-readable threat
Infoblox Dossier User Guide
 Infoblox Dossier User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 1. Overview of Dossier... 3 2. Prerequisites... 3 3. Access to the Dossier
Infoblox Dossier User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 1. Overview of Dossier... 3 2. Prerequisites... 3 3. Access to the Dossier
DHS Automated Information Sharing (AIS) Program
 DHS Automated Information Sharing (AIS) Program 2018 Infoblox Inc. All rights reserved. Page 1 of 5 2018 Infoblox Inc. All rights reserved. DHS Automated Information Sharing (AIS) Program Infoblox AIS
DHS Automated Information Sharing (AIS) Program 2018 Infoblox Inc. All rights reserved. Page 1 of 5 2018 Infoblox Inc. All rights reserved. DHS Automated Information Sharing (AIS) Program Infoblox AIS
Threat Containment and Operations. Yong Kwang Kek, Director of Presales SE, APJ
 Threat Containment and Operations Yong Kwang Kek, Director of Presales SE, APJ 2018-07-19 1 1 2017 Infoblox Inc. All Rights 2013 Infoblox Inc. All Reserved. Rights Reserved. Three Aspects of Security #1
Threat Containment and Operations Yong Kwang Kek, Director of Presales SE, APJ 2018-07-19 1 1 2017 Infoblox Inc. All Rights 2013 Infoblox Inc. All Reserved. Rights Reserved. Three Aspects of Security #1
CYBER ANALYTICS. Architecture Overview. Technical Brief. May 2016 novetta.com 2016, Novetta
 CYBER ANALYTICS Architecture Overview Technical Brief May 2016 novetta.com 2016, Novetta Novetta Cyber Analytics: Technical Architecture Overview 1 INTRODUCTION 2 CAPTURE AND PROCESS ALL NETWORK TRAFFIC
CYBER ANALYTICS Architecture Overview Technical Brief May 2016 novetta.com 2016, Novetta Novetta Cyber Analytics: Technical Architecture Overview 1 INTRODUCTION 2 CAPTURE AND PROCESS ALL NETWORK TRAFFIC
Infoblox as Part of the Ecosystem
 Infoblox Core Exchange Infoblox Core Exchange is a highly-interconnected set of ecosystem integrations that extend security, increase agility, and provide situational awareness for more efficient operations,
Infoblox Core Exchange Infoblox Core Exchange is a highly-interconnected set of ecosystem integrations that extend security, increase agility, and provide situational awareness for more efficient operations,
Comodo Unknown File Hunter Software Version 2.1
 rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
Automated Response in Cyber Security SOC with Actionable Threat Intelligence
 Automated Response in Cyber Security SOC with Actionable Threat Intelligence while its biggest weakness is lack of visibility: SOCs still can t detect previously unknown threats, which is a consistent
Automated Response in Cyber Security SOC with Actionable Threat Intelligence while its biggest weakness is lack of visibility: SOCs still can t detect previously unknown threats, which is a consistent
Forescout. eyeextend for Palo Alto Networks Wildfire. Configuration Guide. Version 2.2
 Forescout Version 2.2 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 2.2 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science
 Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS
 PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
Security. Made Smarter.
 Security. Made Smarter. Your job is to keep your organization safe from cyberattacks. To do so, your team has to review a monumental amount of data that is growing exponentially by the minute. Your team
Security. Made Smarter. Your job is to keep your organization safe from cyberattacks. To do so, your team has to review a monumental amount of data that is growing exponentially by the minute. Your team
Comodo Unknown File Hunter Software Version 5.0
 rat Comodo Unknown File Hunter Software Version 5.0 Administrator Guide Guide Version 5.0.073118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo Unknown File Hunter Software Version 5.0 Administrator Guide Guide Version 5.0.073118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness
 Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness Introduction Drowning in data but starving for information. It s a sentiment that resonates with most security analysts. For
Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness Introduction Drowning in data but starving for information. It s a sentiment that resonates with most security analysts. For
Seceon s Open Threat Management software
 Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
DomainTools for Splunk
 DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
10x Increase Your Team s Effectiveness by Automating the Boring Stuff
 SESSION ID: TTA-R02 10x Increase Your Team s Effectiveness by Automating the Boring Stuff Jonathan Trull Chief Cybersecurity Advisor Microsoft @jonathantrull Vidhi Agarwal Senior Program Manager Microsoft
SESSION ID: TTA-R02 10x Increase Your Team s Effectiveness by Automating the Boring Stuff Jonathan Trull Chief Cybersecurity Advisor Microsoft @jonathantrull Vidhi Agarwal Senior Program Manager Microsoft
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
PALANTIR CYBERMESH INTRODUCTION
 100 Hamilton Avenue Palo Alto, California 94301 PALANTIR CYBERMESH INTRODUCTION Cyber attacks expose organizations to significant security, regulatory, and reputational risks, including the potential for
100 Hamilton Avenue Palo Alto, California 94301 PALANTIR CYBERMESH INTRODUCTION Cyber attacks expose organizations to significant security, regulatory, and reputational risks, including the potential for
ThreatConnect Learning Exercises
 ThreatConnect Learning Exercises The following exercises will teach you some of the important features within the ThreatConnect platform. You will learn various ways of adding intelligence data into ThreatConnect,
ThreatConnect Learning Exercises The following exercises will teach you some of the important features within the ThreatConnect platform. You will learn various ways of adding intelligence data into ThreatConnect,
ClientNet Admin Guide. Boundary Defense for
 ClientNet Admin Guide Boundary Defense for Email DOCUMENT REVISION DATE: Feb 2012 ClientNet Admin Guide / Table of Contents Page 2 of 36 Table of Contents OVERVIEW... 3 1 INTRODUCTION... 3 1.1. AUDIENCE
ClientNet Admin Guide Boundary Defense for Email DOCUMENT REVISION DATE: Feb 2012 ClientNet Admin Guide / Table of Contents Page 2 of 36 Table of Contents OVERVIEW... 3 1 INTRODUCTION... 3 1.1. AUDIENCE
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
ForeScout Extended Module for Carbon Black
 ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
ForeScout Extended Module for MobileIron
 Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
NetWitness Overview. Copyright 2011 EMC Corporation. All rights reserved.
 NetWitness Overview 1 The Current Scenario APT Network Security Today Network-layer / perimeter-based Dependent on signatures, statistical methods, foreknowledge of adversary attacks High failure rate
NetWitness Overview 1 The Current Scenario APT Network Security Today Network-layer / perimeter-based Dependent on signatures, statistical methods, foreknowledge of adversary attacks High failure rate
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Comodo APT Assessment Tool
 rat Comodo APT Assessment Tool Software Version 1.1 Administrator Guide Guide Version 1.1.102815 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo APT Assessment Tool Software Version 1.1 Administrator Guide Guide Version 1.1.102815 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
McAfee Advanced Threat Defense
 Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
How-to Guide: Tenable.io for Microsoft Azure. Last Updated: November 16, 2018
 How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
McAfee MVISION Mobile epo Extension Product Guide
 McAfee MVISION Mobile epo Extension 1809 Product Guide September 11, 2018 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator,
McAfee MVISION Mobile epo Extension 1809 Product Guide September 11, 2018 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator,
Novetta Cyber Analytics
 Know your network. Arm your analysts. Introduction Novetta Cyber Analytics is an advanced network traffic analytics solution that empowers analysts with comprehensive, near real time cyber security visibility
Know your network. Arm your analysts. Introduction Novetta Cyber Analytics is an advanced network traffic analytics solution that empowers analysts with comprehensive, near real time cyber security visibility
AvePoint Online Services for Partners 2
 AvePoint Online Services for Partners 2 User Guide Service Pack 1 Issued June 2017 Table of Contents What s New in this Guide...4 About...5 Submitting Documentation Feedback to AvePoint...6 Browser Support
AvePoint Online Services for Partners 2 User Guide Service Pack 1 Issued June 2017 Table of Contents What s New in this Guide...4 About...5 Submitting Documentation Feedback to AvePoint...6 Browser Support
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
SOLUTION BRIEF RSA NETWITNESS EVOLVED SIEM
 RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version 1.1.122415 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie...
rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version 1.1.122415 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie...
Enhanced Threat Detection, Investigation, and Response
 Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
THREAT INTEL AND CONTENT CURATION: ORGANIZING THE PATH TO SUCCESSFUL DETECTION
 SESSION ID: AIR-W12 THREAT INTEL AND CONTENT CURATION: ORGANIZING THE PATH TO SUCCESSFUL DETECTION Justin Monti CTO MKACyber Mischel Kwon CEO MKACyber @MKACyber What is Cyber Threat Intelligence Data collected,
SESSION ID: AIR-W12 THREAT INTEL AND CONTENT CURATION: ORGANIZING THE PATH TO SUCCESSFUL DETECTION Justin Monti CTO MKACyber Mischel Kwon CEO MKACyber @MKACyber What is Cyber Threat Intelligence Data collected,
How-to Guide: Tenable Nessus for Microsoft Azure. Last Updated: April 03, 2018
 How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
DomainTools App for QRadar
 DomainTools App for QRadar App Startup Guide for Version 1.0.480 Updated November 1, 2017 Table of Contents DomainTools App for QRadar... 1 App Features... 2 Prerequisites... 3 Data Source Identification...
DomainTools App for QRadar App Startup Guide for Version 1.0.480 Updated November 1, 2017 Table of Contents DomainTools App for QRadar... 1 App Features... 2 Prerequisites... 3 Data Source Identification...
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
Avanan for G Suite. Technical Overview. Copyright 2017 Avanan. All rights reserved.
 Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
ForeScout Extended Module for VMware AirWatch MDM
 ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
Sandboxing and the SOC
 Sandboxing and the SOC Place McAfee Advanced Threat Defense at the center of your investigation workflow As you strive to further enable your security operations center (SOC), you want your analysts and
Sandboxing and the SOC Place McAfee Advanced Threat Defense at the center of your investigation workflow As you strive to further enable your security operations center (SOC), you want your analysts and
ActiveTrust Cloud Threats API
 QUICK START GUIDE ActiveTrust Cloud Threats API March 2018 2018 Infoblox Inc. All rights reserved. ActiveTrust Cloud Threats API Quick Start Guide March 2018 Page 1 of 19 Contents Overview... 3 Prerequisites...
QUICK START GUIDE ActiveTrust Cloud Threats API March 2018 2018 Infoblox Inc. All rights reserved. ActiveTrust Cloud Threats API Quick Start Guide March 2018 Page 1 of 19 Contents Overview... 3 Prerequisites...
Hi rat. Comodo Valkyrie. Software Version User Guide Guide Version Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 Hi rat Comodo Valkyrie Software Version 1.19 User Guide Guide Version 1.19.091217 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie... 3
Hi rat Comodo Valkyrie Software Version 1.19 User Guide Guide Version 1.19.091217 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie... 3
ClientNet. Portal Admin Guide
 ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
Quick Start Guide for Administrators and Operators Cyber Advanced Warning System
 NSS Labs Quick Start Guide for Administrators and Operators Cyber Advanced Warning System Introduction to the Cyber Advanced Warning System and RiskViewer... 1 Activating Your Account... 2 Adding a New
NSS Labs Quick Start Guide for Administrators and Operators Cyber Advanced Warning System Introduction to the Cyber Advanced Warning System and RiskViewer... 1 Activating Your Account... 2 Adding a New
Integration Service. Admin Console User Guide. On-Premises
 Kony MobileFabric TM Integration Service Admin Console User Guide On-Premises Release 7.3 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and
Kony MobileFabric TM Integration Service Admin Console User Guide On-Premises Release 7.3 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and
McAfee Endpoint Threat Defense and Response Family
 Defense and Family Detect zero-day malware, secure patient-zero, and combat advanced attacks The escalating sophistication of cyberthreats requires a new generation of protection for endpoints. Advancing
Defense and Family Detect zero-day malware, secure patient-zero, and combat advanced attacks The escalating sophistication of cyberthreats requires a new generation of protection for endpoints. Advancing
Building Resilience in a Digital Enterprise
 Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
ISO COMPLIANCE GUIDE. How Rapid7 Can Help You Achieve Compliance with ISO 27002
 ISO 27002 COMPLIANCE GUIDE How Rapid7 Can Help You Achieve Compliance with ISO 27002 A CONTENTS Introduction 2 Detailed Controls Mapping 3 About Rapid7 8 rapid7.com ISO 27002 Compliance Guide 1 INTRODUCTION
ISO 27002 COMPLIANCE GUIDE How Rapid7 Can Help You Achieve Compliance with ISO 27002 A CONTENTS Introduction 2 Detailed Controls Mapping 3 About Rapid7 8 rapid7.com ISO 27002 Compliance Guide 1 INTRODUCTION
Juniper Sky Advanced Threat Prevention
 Juniper Sky Advanced Threat Prevention Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX Series Services
Juniper Sky Advanced Threat Prevention Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX Series Services
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Reducing the Cost of Incident Response
 Reducing the Cost of Incident Response Introduction Cb Response is the most complete endpoint detection and response solution available to security teams who want a single platform for hunting threats,
Reducing the Cost of Incident Response Introduction Cb Response is the most complete endpoint detection and response solution available to security teams who want a single platform for hunting threats,
CounterACT Check Point Threat Prevention Module
 CounterACT Check Point Threat Prevention Module Version 1.0.0 Table of Contents About the Check Point Threat Prevention Integration... 4 Use Cases... 4 Additional Check Point Threat Prevention Documentation...
CounterACT Check Point Threat Prevention Module Version 1.0.0 Table of Contents About the Check Point Threat Prevention Integration... 4 Use Cases... 4 Additional Check Point Threat Prevention Documentation...
THE RSA SUITE NETWITNESS REINVENT YOUR SIEM. Presented by: Walter Abeson
 THE RSA NETWITNESS SUITE REINVENT YOUR SIEM Presented by: Walter Abeson 1 Reality Goals GOALS VERSUS REALITY OF SIEM 1.0 Single compliance & security interface Analyze & prioritize alerts across various
THE RSA NETWITNESS SUITE REINVENT YOUR SIEM Presented by: Walter Abeson 1 Reality Goals GOALS VERSUS REALITY OF SIEM 1.0 Single compliance & security interface Analyze & prioritize alerts across various
Symantec & Blue Coat Technical Update Webinar 29. Juni 2017
 Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
NetBackup Collection Quick Start Guide
 NetBackup Collection Quick Start Guide This whitepaper is intended for IT professionals, IT managers, and IT personnel responsible for the planning, setup, and/or administration of Veritas Information
NetBackup Collection Quick Start Guide This whitepaper is intended for IT professionals, IT managers, and IT personnel responsible for the planning, setup, and/or administration of Veritas Information
Comodo cwatch Web Security Software Version 2.10
 rat Comodo cwatch Web Security Software Version 2.10 Website Administrator Guide Guide Version 2.10.042018 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction
rat Comodo cwatch Web Security Software Version 2.10 Website Administrator Guide Guide Version 2.10.042018 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction
Comodo Dome Shield - Admin Guide
 rat Comodo Dome Shield Software Version 1.12 Administrator Guide Guide Version 1.12.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
rat Comodo Dome Shield Software Version 1.12 Administrator Guide Guide Version 1.12.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
Comodo cwatch Web Security Software Version 1.6
 rat Comodo cwatch Web Security Software Version 1.6 Quick Start Guide Guide Version 1.6.010918 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo cwatch Web Security - Quick Start Guide
rat Comodo cwatch Web Security Software Version 1.6 Quick Start Guide Guide Version 1.6.010918 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo cwatch Web Security - Quick Start Guide
ForeScout Extended Module for Qualys VM
 ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
JUNIPER SKY ADVANCED THREAT PREVENTION
 Data Sheet JUNIPER SKY ADVANCED THREAT PREVENTION Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX
Data Sheet JUNIPER SKY ADVANCED THREAT PREVENTION Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX
Tenable for Google Cloud Platform
 How-To Guide Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
How-To Guide Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppDefense Cb Defense Configuration Guide. AppDefense Appendix Cb Defense Integration Configuration Guide
 AppDefense Appendix Cb Defense Integration Configuration Guide Table of Contents Overview 3 Requirements 3 Provision API Key for Cb Defense Integration 3 Figure 1 Integration Type 4 Figure 2 API Key Provisioning
AppDefense Appendix Cb Defense Integration Configuration Guide Table of Contents Overview 3 Requirements 3 Provision API Key for Cb Defense Integration 3 Figure 1 Integration Type 4 Figure 2 API Key Provisioning
WHITE PAPER. Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale
 WHITE PAPER Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale One key number that is generally
WHITE PAPER Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale One key number that is generally
Detect Cyber Threats with Securonix Proxy Traffic Analyzer
 Detect Cyber Threats with Securonix Proxy Traffic Analyzer Introduction Many organizations encounter an extremely high volume of proxy data on a daily basis. The volume of proxy data can range from 100
Detect Cyber Threats with Securonix Proxy Traffic Analyzer Introduction Many organizations encounter an extremely high volume of proxy data on a daily basis. The volume of proxy data can range from 100
Introduction. Deployment Models. IBM Watson on the IBM Cloud Security Overview
 IBM Watson on the IBM Cloud Security Overview Introduction IBM Watson on the IBM Cloud helps to transform businesses, enhancing competitive advantage and disrupting industries by unlocking the potential
IBM Watson on the IBM Cloud Security Overview Introduction IBM Watson on the IBM Cloud helps to transform businesses, enhancing competitive advantage and disrupting industries by unlocking the potential
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS
 Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
<Partner Name> RSA NETWITNESS Intel Feeds Implementation Guide. Kaspersky Threat Feed Service. <Partner Product>
 RSA NETWITNESS Intel Feeds Implementation Guide Kaspersky Jeffrey Carlson, RSA Partner Engineering Last Modified: December 19 th, 2017 Solution Summary Kaspersky Lab offers
RSA NETWITNESS Intel Feeds Implementation Guide Kaspersky Jeffrey Carlson, RSA Partner Engineering Last Modified: December 19 th, 2017 Solution Summary Kaspersky Lab offers
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
USM Anywhere AlienApps Guide
 USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
DATA SHEET RSA NETWITNESS PLATFORM PERVASIVE VISIBILITY. ACTIONABLE INSIGHTS.
 DATA SHEET RSA NETWITNESS PLATFORM PERVASIVE VISIBILITY. ACTIONABLE INSIGHTS. KEY ANALYSTS BENEFITS: Gain complete visibility across your network Alleviate pressures from security staff shortages with
DATA SHEET RSA NETWITNESS PLATFORM PERVASIVE VISIBILITY. ACTIONABLE INSIGHTS. KEY ANALYSTS BENEFITS: Gain complete visibility across your network Alleviate pressures from security staff shortages with
Kaspersky Security Network
 The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM
 THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM Modern threats demand analytics-driven security and continuous monitoring Legacy SIEMs are Stuck in the Past Finding a mechanism to collect, store
THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM Modern threats demand analytics-driven security and continuous monitoring Legacy SIEMs are Stuck in the Past Finding a mechanism to collect, store
McAfee Investigator Product Guide
 McAfee Investigator Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee epo, McAfee EMM, Foundstone,
McAfee Investigator Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee epo, McAfee EMM, Foundstone,
ForeScout Extended Module for Symantec Endpoint Protection
 ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
Symantec Advanced Threat Protection: Endpoint
 Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Incident Play Book: Phishing
 Incident Play Book: Phishing Issue: 1.0 Issue Date: September 12, 2017 Copyright 2017 Independent Electricity System Operator. Some Rights Reserved. The following work is licensed under the Creative Commons
Incident Play Book: Phishing Issue: 1.0 Issue Date: September 12, 2017 Copyright 2017 Independent Electricity System Operator. Some Rights Reserved. The following work is licensed under the Creative Commons
Forescout. eyeextend for Carbon Black. Configuration Guide. Version 1.1
 Forescout Version 1.1 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 1.1 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
White Paper. View cyber and mission-critical data in one dashboard
 View cyber and mission-critical data in one dashboard Table of contents Rising cyber events 2 Mitigating threats 2 Heighten awareness 3 Evolving the solution 5 One of the direct benefits of the Homeland
View cyber and mission-critical data in one dashboard Table of contents Rising cyber events 2 Mitigating threats 2 Heighten awareness 3 Evolving the solution 5 One of the direct benefits of the Homeland
Battle between hackers and machine learning. Alexey Lukatsky Cybersecurity Business Consultant April 03, 2019
 Battle between hackers and machine learning Alexey Lukatsky Cybersecurity Business Consultant April 03, 2019 Google: facts and numbers Real Cisco Big Data for Security Training Set Why is Machine Learning
Battle between hackers and machine learning Alexey Lukatsky Cybersecurity Business Consultant April 03, 2019 Google: facts and numbers Real Cisco Big Data for Security Training Set Why is Machine Learning
Integration Service. Admin Console User Guide. On-Premises
 Kony Fabric Integration Service Admin Console User Guide On-Premises Release V8 SP1 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and the
Kony Fabric Integration Service Admin Console User Guide On-Premises Release V8 SP1 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and the
RSA NetWitness Suite Respond in Minutes, Not Months
 RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
ForeScout Extended Module for MaaS360
 Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Security by Default: Enabling Transformation Through Cyber Resilience
 Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
esendpoint Next-gen endpoint threat detection and response
 DATA SHEET esendpoint Next-gen endpoint threat detection and response esendpoint powered by Carbon Black eliminates endpoint blind-spots that traditional technologies miss. Operating on a philosophy that
DATA SHEET esendpoint Next-gen endpoint threat detection and response esendpoint powered by Carbon Black eliminates endpoint blind-spots that traditional technologies miss. Operating on a philosophy that
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
Integration with Tenable Security Center
 DEPLOYMENT GUIDE Integration with Tenable Security Center Outbound API 2017 Infoblox Inc. All rights reserved. Integration with Tenable Security Center August 2017 Page 1 of 10 Contents Introduction...
DEPLOYMENT GUIDE Integration with Tenable Security Center Outbound API 2017 Infoblox Inc. All rights reserved. Integration with Tenable Security Center August 2017 Page 1 of 10 Contents Introduction...
SOLUTION BRIEF. RiskSense Platform. RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk.
 RiskSense Platform RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 27 RiskSense, Inc. Executive Summary The RiskSense Platform is a Software-as-a-Service
RiskSense Platform RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 27 RiskSense, Inc. Executive Summary The RiskSense Platform is a Software-as-a-Service
Integrating Okta and Preempt Detecting and Preventing Threats With Greater Visibility and Proactive Enforcement
 Integrating Okta and Preempt Detecting and Preventing Threats With Greater Visibility and Proactive Enforcement The Challenge: Smarter Attackers and Dissolving Perimeters Modern enterprises are simultaneously
Integrating Okta and Preempt Detecting and Preventing Threats With Greater Visibility and Proactive Enforcement The Challenge: Smarter Attackers and Dissolving Perimeters Modern enterprises are simultaneously
Managed Security Services - Endpoint Managed Security on Cloud
 Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Service Cloud Using Service Cloud Configuration Assistant Release 17D
 Oracle Service Cloud Using Service Cloud Configuration Assistant Release 17D Part Number: E89541-02 Copyright 2017, Oracle and/or its affiliates. All rights reserved Authors: The Service Cloud Information
Oracle Service Cloud Using Service Cloud Configuration Assistant Release 17D Part Number: E89541-02 Copyright 2017, Oracle and/or its affiliates. All rights reserved Authors: The Service Cloud Information
Deploying Lookout with IBM MaaS360
 Lookout Mobile Endpoint Security Deploying Lookout with IBM MaaS360 February 2018 2 Copyright and disclaimer Copyright 2018, Lookout, Inc. and/or its affiliates. All rights reserved. Lookout, Inc., Lookout,
Lookout Mobile Endpoint Security Deploying Lookout with IBM MaaS360 February 2018 2 Copyright and disclaimer Copyright 2018, Lookout, Inc. and/or its affiliates. All rights reserved. Lookout, Inc., Lookout,
Integration with McAfee DXL
 DEPLOYMENT GUIDE Integration with McAfee DXL Visibility into Network Changes and Faster Threat Containment Using Outbound APIs 2017 Infoblox Inc. All rights reserved. Integration with McAfee DXL November
DEPLOYMENT GUIDE Integration with McAfee DXL Visibility into Network Changes and Faster Threat Containment Using Outbound APIs 2017 Infoblox Inc. All rights reserved. Integration with McAfee DXL November
