SGOS on AWS Deployment Guide
|
|
|
- Roy Hunter
- 5 years ago
- Views:
Transcription
1 SGOS on AWS Deployment Guide Version 6.7.x Guide Revision: 4/6/2018
2 2 SGOS on AWS Deployment Guide SGOS on AWS Deployment Guide
3 SGOS on AWS Deployment Guide 3 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks or registered trademarks of Symantec Corp. or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. SYMANTEC CORPORATION PRODUCTS, TECHNICAL SERVICES, AND ANY OTHER TECHNICAL DATA REFERENCED IN THIS DOCUMENT ARE SUBJECT TO U.S. EXPORT CONTROL AND SANCTIONS LAWS, REGULATIONS AND REQUIREMENTS, AND MAY BE SUBJECT TO EXPORT OR IMPORT REGULATIONS IN OTHER COUNTRIES. YOU AGREE TO COMPLY STRICTLY WITH THESE LAWS, REGULATIONS AND REQUIREMENTS, AND ACKNOWLEDGE THAT YOU HAVE THE RESPONSIBILITY TO OBTAIN ANY LICENSES, PERMITS OR OTHER APPROVALS THAT MAY BE REQUIRED IN ORDER TO EXPORT, RE-EXPORT, TRANSFER IN COUNTRY OR IMPORT AFTER DELIVERY TO YOU. Symantec Corporation 350 Ellis Street Mountain View, CA /6/2018
4
5 Table of Contents Table of Contents 5 About SGOS on AWS 6 Important Details about SGOS on AWS 7 Step 1: Complete Prerequisite Tasks 8 Step 2: Import and Register an AMI 11 Step 3: Deploy the Instance 15 Step 4: Verify the Instance 18 Step 5: Install the License 19 Step 6: Disassociate User Data from the Instance 20 Step 7: (Optional) Configure Load Balancing 21 Configure a Listener 21 Configure Health Checks 22 Back up and Restore an Instance of SGOS 23 Create a Snapshot to Back up Your SGOS Instance 23 Restore an Instance of SGOS from a Snapshot 23 Create an AMI from a Snapshot of an SGOS Instance 23 Deploy the Newly Registered AMI 24 Troubleshoot SGOS on AWS 25 General Troubleshooting Steps 25 Troubleshoot Licensing Errors 26 Troubleshoot Credentials Errors 27 Appendix A: Supported Configurations 28 Appendix B: Metadata and User Data Reference 29 AWS Metadata 29 AWS User Data 30 AWS User Data Security 31
6 SGOS on AWS Deployment Guide (6.7.x) About SGOS on AWS This guide provides instructions for deploying a ProxySG virtual appliance (Secure Web Gateway edition, SGOS version 6.7.x) running on Xen Hypervisor in Amazon Web Services (AWS). Because AWS is outside of the Symantec network, you must manually transfer SGOS virtual machine images into AWS, where you can configure and manage your virtual SGOS instances. SGOS on AWS permits the same features and functionality as the Secure Web Gateway Virtual Appliance (SWG VA), except it does not support transparent proxy or WCCP. This document guides you through the process of setting up SGOS on AWS. Deployment consists of the following steps: Deployment Step Prepare your environment and make sure you have the required resources and files to deploy SGOS on AWS. Use a virtual hard disk (VHD) file to create an Amazon Machine Image (AMI). This section provides instructions for EC2 CLI and AWS CLI. Import the AMI into the AWS Management Console and configure it using a user data file and manual settings. Verify that you can access the instance through SSH and the ProxySG Management Console. Install the SGOS license through the ProxySG Management Console. Disassociate the user data from the instance so that you can easily change usernames and passwords later. Configure an AWS Elastic Load Balancer (ELB) for multiple SGOS instances. This is an optional step. Create snapshots in AWS to capture the contents of an EBS volume at specific points in time. This is a recommended step. Review the known issues in this release. Document Reference "Step 1: Complete Prerequisite Tasks" on page 8 "Step 2: Import and Register an AMI" on page 11 "Step 3: Deploy the Instance " on page 15 "Step 4: Verify the Instance " on page 18 "Step 5: Install the License" on page 19 "Step 6: Disassociate User Data from the Instance" on page 20 "Step 7: (Optional) Configure Load Balancing" on page 21 "Back up and Restore an Instance of SGOS" on page 23 SGOS Release Notes at MySymantec If you encounter any issues while the SGOS on AWS instance is running, refer to "Troubleshoot SGOS on AWS" on page 25 in this guide for assistance. For details beyond the scope of SGOS documentation, refer to AWS documentation: com/documentation/ 6
7 SGOS on AWS Deployment Guide (6.7.x) Important Details about SGOS on AWS Note the following about SGOS on AWS: Version 6.7.x is supported on the SWG-V100 and SG-VA-C2S models. You have two ways to manage SGOS instances: through SSH to the CLI and the ProxySG Management Console in a web browser. You cannot access a serial or VGA console to a virtual machine. You cannot downgrade the SG-VA-C2S to SGOS 6.6.x. (You can downgrade the SWG-V100.) This release does not support AWS Marketplace for third-party AMIs. 7
8 8 SGOS on AWS Deployment Guide Step 1: Complete Prerequisite Tasks Before deploying SGOS on AWS, complete the following tasks: 1. Prepare and verify your environment, including firewall configuration, Amazon VPC configuration, and security groups for the VPC. Refer to Amazon documentation for details. 2. Allow access to the following Symantec servers: You require access to these servers in order to retrieve and install the SGOS on AWS license. 3. Verify system requirements for the virtual appliance. Refer to the following table. Depending on the AWS EC2 Instance Type and virtual appliance model you use, the ProxySG appliance's licensing health status might indicate a Warning. In addition, the Configured Memory statistic (in the Management Console, select Maintenance > Health Monitoring > Licensing) displays a notification that the appliance has under-provisioned memory. This is expected behavior and means that the configured virtual memory is lower than the 8 GB allowed by the license. Under-provisioned memory reduces the maximum number of connections, but it does not invalidate the license. Instance Type Number of Virtual CPUs Virtual Memory (GB) Number of Virtual Drives Storage Space Per Drive ProxySG Health with SWG-V100 ProxySG Health with SG-VA- C2S m4.large (recommended) GB OK OK t2.large GB OK OK t2.medium GB OK Warning c4.large GB Warning Warning Refer to "Appendix A: Supported Configurations" on page 28 for more information on instance types support. 4. Set up your preferred CLI: EC2 CLI Tools AWS CLI 5. Confirm that you are able to access the private key (PEM file) you want AWS to register with the EC2 instance. 6. Obtain or confirm your MySymantec credentials. You require these credentials to generate the instance user data file and to retrieve the SGOS on AWS license.
9 SGOS on AWS Deployment Guide 9 7. Obtain or confirm the following information: o o o o The username for the administrator account The virtual appliance serial number (which you either retrieved when you downloaded the VHD from MySymantec) The intended password for the administrator account The intended enable password for the appliance Make sure that the passwords are strong. You require these details to generate the user data file. 8. Generate the user data file: a. Go to the following URL: b. When prompted to log in, enter your MySymantec username and password. a. Enter the following: Console Username: The administrative username for accessing the SGOS Management Console. Serial Number: The appliance serial number. Console Password: The administrative password. Enable Password: The enable password. Be sure to create strong passwords. c. Click Generate User Data. The browser displays the user data. d. Click Download File to download the user data file. e. Click Finish. 9. (If necessary) Create an S3 bucket for the region from which you intend to launch EC2 instances. Using the AWS dashboard:
10 10 SGOS on AWS Deployment Guide a. Log in to the AWS dashboard. The URL is where <region_name> is the ID of the region from which you will launch EC2 instances. b. In the list of AWS services, in the Storage & Content Delivery section, select S3. c. If there are no existing S3 buckets, or if you want to use a new bucket for importing the image, click Create Bucket. Follow the prompts to create the bucket. Alternatively, you can use an existing bucket for importing the image. Using the AWS CLI: a. Issue the following command: $ aws s3 mb s3://bucket_name --region region_name where region_name is the ID of the region from which you will launch EC2 instances. Example: $ aws s3 mb s3://hq-lab-1 --region us-east-1 The following output indicates that the bucket was created: make_bucket: s3://hq-lab-1 You cannot use EC2 CLI to create a bucket because it does not have the functionality to interact with S (If you intend to use load balancing) Understand how ELBs are deployed in AWS. Refer to AWS documentation for details:
11 SGOS on AWS Deployment Guide 11 Step 2: Import and Register an AMI This section describes the CLI commands, and required parameters, you use to import and register an AMI. Refer to the instructions for your preferred CLI tools either EC2 or AWS. Complete the "Step 1: Complete Prerequisite Tasks" on page 8 before proceeding. Import and Register Using EC2 CLI 1. Import the SGOS VHD file into AWS: $ ec2-import-volume disk_image -f disk_image_format -s volume_size_in_gb -z region -b bucket_name -o owner_access_key_id -w owner_secret_key Example: $ ec2-import-volume ProxySG_SWG_AWS_ vhd -f vhd -s 8 -z us-east-1a -b proxysg-images -o access_key_id -w secret_key In the CLI output, confirm that the import was successful. Note the import volume task ID, which is in the format import-vol-alphanumeric_string. 2. Verify the status of the import: $ ec2-describe-conversion-tasks import_volume_task_id Example: $ ec2-describe-conversion-tasks import-vol-ffob6lad In the CLI output, confirm that the VHD import was successful and that the disk image properties you specified are correct. Note the VolumeId value. 3. (If necessary) For any properties that were specified incorrectly, remove the volume using the VolumeId: $ ec2-delete-volume volume_id Example: $ ec2-delete-volume vol-18d64fb Repeat step 1 to re-import the VHD. 4. Create a snapshot of the volume using the VolumeId: $ ec2-create-snapshot volume_id Example: $ ec2-create-snapshot vol-18d64fb In the CLI output, note the snapshot ID, which is in the format snap-alphanumeric_string.
12 12 SGOS on AWS Deployment Guide 5. Verify that the snapshot creation is complete using the snapshot ID: $ ec2-describe-snapshots snapshot_id Example: $ ec2-describe-snapshots snap-62af4d7b If the snapshot creation is still in progress, it shows a progress of 0%. When the snapshot is complete, the output shows a completed status and 100%. 6. Register the snapshot you created using the snapshot ID: $ ec2-register -n AMI_name -s snapshot_id -a x86_64 -d " AMI_description " -- virtualization-type hvm Example: $ ec2-register -n MyImportedSGOSVHD -s snap-62af4d7b -a x86_64 -d "CLI Imported SGOS AMI" --virtualization-type hvm Import and Register Using AWS CLI 1. Upload the SGOS VHD file to the appropriate S3 bucket: $ aws s3 cp local_path_to_vhd S3_URI Example: $ aws s3 cp C://My_VHDs/ProxySG_SWG_AWS_ vhd s3://proxysg-image 2. After the upload is complete, create a snapshot of the VHD file specifying the S3 bucket and VHD file from the previous step: $ aws ec2 import-snapshot --description "ProxySG Snapshot Import" --disk-container "{ \"Description\":\"Description\", \"UserBucket\":{ \"S3Bucket\":\"S3_bucket\", \"S3Key\":\"VHD_name\" } }" Example: $ aws ec2 import-snapshot --description "ProxySG Snapshot Import" --disk-container "{ \"Description\":\"ProxySG Snapshot Import Task\", \"UserBucket\":{ \"S3Bucket\":\"proxysg-images\", \"S3Key\":\"ProxySG_SWG_AWS_ vhd\" } }" JSON output such as the following indicates successful snapshot creation: { "SnapshotTaskDetail": { "Status": "active", "Description": "ProxySG Snapshot Import", "DiskImageSize": 0.0,
13 SGOS on AWS Deployment Guide 13 "Progress": "3", "UserBucket": { "S3Bucket": "proxysg-images", "S3Key": "ProxySG_SWG_AWS_ vhd" }, "StatusMessage": "pending" }, "Description": "ProxySG Snapshot Import", "ImportTaskId": "import-snap-fgxcnc3v" } Wait for the snapshot to be created. To view its progress, use the describe-import-snapshot-tasks command: $ aws ec2 describe-import-snapshot-tasks --import-task-ids SNAPSHOT_IMPORT_TASK_ ID where SNAPSHOT_IMPORT_TASK_ID is the identifier that AWS uses to track the snapshot creation task; look for the ImportTaskId key in the output. In this example, the identifier is import-snap-fgxcnc3v. Example: $ aws ec2 describe-import-snapshot-tasks --import-task-ids import-snap-fgxcnc3v 3. Confirm that the snapshot is created. Look for the Status key in the output; it should read "completed", as in the following example: { "ImportSnapshotTasks": [ { "SnapshotTaskDetail": { "Status": "completed", "Description": "ProxySG Snapshot Import", "Format": "VHD", "DiskImageSize": , "SnapshotId": "snap-87af1b61", "UserBucket": { "S3Bucket": "proxysg-images", "S3Key": "ProxySG_SWG_AWS_ vhd"
14 14 SGOS on AWS Deployment Guide } ] } }, } "Description": "ProxySG Snapshot Import", "ImportTaskId": "import-snap-fgxcnc3v" 4. Register the snapshot as the AMI you will use to launch EC2 instances: $ aws ec2 register-image --name "AMI_NAME" --description "VHD_NAME" --architecture x86_64 --root-device-name "/dev/sda1" --virtualization-type hvm --block-devicemappings "[{\"DeviceName\": \"/dev/sda1\",\"ebs\":{\"snapshotid\":\"snapshot_id \",\"VolumeSize\":100,\"DeleteOnTermination\":true,\"VolumeType\":\"io1\",\"Iops\" :300}}]" where AMI_NAME is the AMI name. Create user-friendly, memorable AMI names to help identify the AMI if you use the AWS web console to launch your EC2 instances. Example: $ aws ec2 register-image --name "Lab_1" --description "ProxySG_SWG_AWS_ vhd" --architecture x86_64 --root-device-name "/dev/sda1" --virtualization-type hvm -- block-device-mappings "[{\"DeviceName\": \"/dev/sda1\",\"ebs\": {\"SnapshotId\":\"snap- 87af1b61\",\"VolumeSize\":100,\"DeleteOnTermination\":true,\"VolumeType\":\"io1\", \"Iops\":300}}]" The block device mappings specify the default EBS volume to be used as the root volume. You can change the volume type when you create and launch the EC2 instance. When the snapshot is registered successfully, the CLI returns the AMI identifier: { "ImageId": "ami-8ba466e6" }
15 SGOS on AWS Deployment Guide 15 Step 3: Deploy the Instance After you import and register the AMI, deploy the instance through the AWS Management Console. To complete this step, you require the user data file. 1. Log in to the AWS Management Console: a. Open a web browser window/tab. b. Go to the following URL: The browser displays the AWS Management Console. 2. In the AWS Management Console, select Services > EC2. The browser displays the EC2 Dashboard. 3. In the Create Instance section, click Launch Instance. The browser opens a wizard to guide you through the import process. 4. On the left menu on the EC2 dashboard, select My AMIs. a. Step 1: Select the AMI and click Select. b. Step 2: Choose a supported instance type: t2.large m4.large (recommended) t2.medium c4.large Refer to"appendix A: Supported Configurations" on page 28 for more information. Click Next: Configure Instance Details. c. Step 3: (Optional) Specify networks/subnets in your AWS region and assign the instance to a placement group. (Required) Expand the Advanced Details section. Beside User data, select As file. Browse to the location where you saved the user data file that you created and select it. Do not select Input is already base64 encoded. Click Next: Add Storage. d. Step 4: Specify storage settings:
16 16 SGOS on AWS Deployment Guide For the default Root volume, specify a single EBS volume 100 GiB in size. For Volume Type, select Magnetic or Provisioned IOPS SSD (I01) for Volume Type. Symantec recommends that if you select Provisioned IOPS, set the IOPS to 300. Click Next: Tag Instance. e. Step 5: If a keypair is not already set up, add one. The wizard will prompt you to specify a keypair when you launch the instance. Click Next: Configure Security Group. f. Step 6: Create a new security group or select an existing one. Security groups allow you to control the inbound connections to, and outbound connections from, your EC2 instance. Click Review and Launch. g. Step 7: Review the instance settings. Make corrections as needed. 5. Launch the instance using your preferred method: In the Management Console: a. Click Launch to launch the instance. b. When prompted, select the appropriate keypair, accept the acknowledgment, and click Launch Instance. The browser displays the Launch Status page. Using EC2 CLI: Issue the ec2-run-instances command. For details, refer to Using AWS CLI: Issue the aws ec2 run-instances command. For details, refer to 6. In the "Your instances are now launching" message box, click the link to the instance. The browser displays the Instances page. 7. Under Instance State, look for a status icon and an indication of the number of checks passed. If the instance launched successfully, you should see a green icon and "2/2 checks passed". If fewer than two checks passed (as follows), refer to the tabs at the bottom of the page. Click Status Checks to determine which check(s) failed, and troubleshoot the problem(s) as suggested. In the following example, the Instance Status Checks report a failure and provide a link for troubleshooting.
17 SGOS on AWS Deployment Guide Repeat the previous steps as needed to set up additional instances. You might want to set up a load balancer for multiple instances. Do so after you have verified the connectivity and license validity for all instances. For ELB setup instructions, see "Step 7: (Optional) Configure Load Balancing" on page 21.
18 18 SGOS on AWS Deployment Guide Step 4: Verify the Instance After you create the instance, verify that you can access it through SSH and the ProxySG Management Console. To complete this step, you require the private key (PEM file) and/or the login credentials that you used to generate the user data file. 1. On the EC2 Dashboard, select Instances > Instances. Locate the instance. 2. Make sure that the Instance State says "running" and that Status Checks says "2/2 checks passed". If fewer than two checks passed, refer to the Status Checks tab to determine which check(s) failed, and troubleshoot the problem(s) as suggested. 3. Select the instance, right-click, and click Connect. Connect to the instance using a standalone SSH client, such as PuTTY. Follow the instructions on the dialog: 4. Access the ProxySG Management Console using the instance's AWS-assigned private IP or public IP address (depending on your security group settings) and your login credentials. With the instance selected, click the Description tab to determine the AWS-assigned network settings.
19 SGOS on AWS Deployment Guide 19 Step 5: Install the License After you verify that you can access the instance, install and verify your license. The SGOS on AWS license contains data that is used to uniquely identify the virtual appliance. 1. In the ProxySG Management Console, select Maintenance > Licensing > Install. 2. Click Retrieve. The console displays a dialog. 3. In the dialog: a. Enter your MySymantec credentials. b. Click Request License. The console displays a Confirm License Install dialog. c. Click OK to begin license retrieval. 4. (Optional) Click Show results to verify a successful retrieval. If any errors occur, verify that you are connected to the Internet. 5. Click Close. Verify that there are no license errors. If the license is invalid, select the instance in the EC2 Dashboard and look at the Description tab. If the selected instance type is not one that SGOS on AWS supports, perform step 5 of "Make sure that a supported instance type is selected." on page 26 ("Troubleshoot SGOS on AWS" on page 25, Troubleshoot Licensing Errors section). See "Appendix A: Supported Configurations" on page 28 to determine the supported instance types. After you validate the license installation, you do not have to reboot or shut down the appliance.
20 20 SGOS on AWS Deployment Guide Step 6: Disassociate User Data from the Instance After you verify that the instance boots successfully, Symantec recommends that you dissociate the user data from it. Doing so allows you to change your console username, console password, and enable password using standard methods through the SGOS Management Console and CLI commands and these changes persist after instance restarts. 1. Stop the instance. In the Instances list, select an instance and right click. On the menu, select Instance State > Stop. 2. Verify the instance state. In the Instance State column, look for a red icon and the status "stopped". 3. Select the instance again and right click. On the menu, select Instance Settings > View/Change User Data. On the dialog that appears, replace the contents of the User Data field with two sets of quotation marks, as follows: "" Deleting the contents of the User Data field does not disassociate user data from the instance; it only reverts to the user data that was associated with the instance when it was first launched. 4. Click Save to save your changes. 5. Restart the instance. Select the instance again and right click. On the menu, select Instance State > Start. For details on changing user data, refer to AWS documentation: docs.aws.amazon.com/awsec2/latest/userguide/ec2-instance-metadata.html#instancedata-add-user-data For details on changing usernames and passwords in SGOS, refer to the SGOS Administration Guide and the Command Line Interface Referenceat MySymantec:
21 SGOS on AWS Deployment Guide 21 Step 7: (Optional) Configure Load Balancing This section assumes an understanding of AWS ELBs. Refer to AWS documentation for details: To deploy an AWS ELB in front of multiple SGOS instances: 1. In the AWS Management Console, select Load Balancing > Load Balancers. 2. Click Create Load Balancer. The console displays a setup wizard. Specify the following: a. Step 1: Define Load Balancer - Enter the appropriate details. For listener configuration, see "Configure a Listener" below. b. Step 2: Assign Security Groups - This is an optional step; specify groups as required for your deployment. c. Step 3: Configure Security Settings - Skip this step; it is not applicable in this release. d. Step 4: Configure Health Check - Enter the appropriate details. See "Configure Health Checks" on the next page. e. Step 5: Add EC2 Instances - Select the instances for the load balancer. f. Step 6: Add Tags - This is an optional step; add tags as needed for your deployment. g. Step 7: Review - Review the load balancer settings. Make any required changes, and then click Create to create the load balancer. Configure a Listener You can configure an ELB to perform layer 4 load balancing and pass traffic through to the SGOS instances. Specify the protocol and port on which the instances are configured to intercept traffic. For example, if you enabled explicit interception on port 8080, use the following settings: Load Balancer Protocol: TCP Load Balancer Port: 8080 (same as instance port) Instance Protocol: TCP; this is automatically selected when you specify TCP for the load balancer protocol Instance Port: 8080
22 22 SGOS on AWS Deployment Guide Configure Health Checks For the ELB to monitor the health of the SGOS instances, configure it to TCP ping a socket to which the instances respond. The Instance Port that is configured for Load Balancer listener can serve as this listening socket. The example in "Configure a Listener" on the previous page uses TCP port 8080 for the load balancing listener; thus, in this case, use the following settings: Ping Protocol: TCP Ping Port: 8080 You do not have to change the default settings under Advanced Details.
23 SGOS on AWS Deployment Guide 23 Back up and Restore an Instance of SGOS In case you need to revert or restore your SGOS instance to an earlier state, you should create a snapshot of your SGOS instance. When you create a snapshot in an AWS environment, the AWS environment saves the snapshot to S3, which backs up the contents of your Amazon Elastic Book Store (EBS) volume. Snapshots are incremental; that is, subsequent snapshots include only contents that differ from previous snapshots. Create a Snapshot to Back up Your SGOS Instance This section provides steps for creating a snapshot of your SGOS instance using your AWS console or preferred CLI tool. To create a snapshot of your SGOS instance from your AWS console: 1. In the EC2 Dashboard, under Elastic Block Store, select Snapshots. 2. Click Create Snapshot. 3. In the Create Snapshot dialog: a. Select the volume for which you want to create the snapshot b. Enter a name and description for the snapshot. c. Click Create. To create a snapshot using your preferred CLI tool: In the EC2 CLI: ec2-create-snapshot For details, refer to In the AWS CLI: create-snapshot For details, refer to Using AWS Tools for Windows PowerShell: New-EC2Snapshot For details, refer to Cloud_cmdlets.html. Restore an Instance of SGOS from a Snapshot This section provides the steps for reverting or restoring an instance from a snapshot using your AWS console or preferred CLI tool. To revert or restore an instance: 1. Create an AMI from a snapshot of an SGOS instance. 2. Deploy the newly registered AMI. Create an AMI from a Snapshot of an SGOS Instance This section provides steps for creating an AMI from a snapshot using your AWS console or preferred CLI tool.
24 24 SGOS on AWS Deployment Guide To create an AMI from a snapshot from your AWS console: 1. In the EC2 Dashboard, under Elastic Block Store, click Snapshots. 2. In the list of snapshots, select the snapshot you want to create an AMI from. 3. Click Actions > Create Image. 4. In the Create Image from EBS Snapshot dialog, enter information in the following fields: a. Architecture: Select x86_64 for 64-bit. b. Root device name: Enter the name for the root volume. c. RAM disk ID: Use the default. d. Virtualization: Select Hardware-assisted virtualization. e. Kernel ID: Use the default. f. (Optional) Block Device Mappings: You can add new volumes or expand the size of the root volume for your AMI. 5. Click Create. To create an AMI from a snapshot using your preferred CLI tool: In the EC2 CLI: ec2-create-image For details, refer to In the AWS CLI: create-image For details, refer to Using AWS Tools for Windows PowerShell: New-EC2Image For details, refer to Deploy the Newly Registered AMI You deploy snapshots the same way that you deploy new instances. For the full steps on deploying an instance, see "Step 3: Deploy the Instance " on page 15.
25 SGOS on AWS Deployment Guide 25 Troubleshoot SGOS on AWS If you experience errors or issues using SGOS on AWS, and have already checked the SGOS Release Notes, refer to the following troubleshooting steps. General Troubleshooting Steps Possible Troubleshooting Step Monitor instance health checks. Take screenshots of the instance console. Details Look for problems under Status Checks: 1. In the EC2 Dashboard, under Instances, select Instances. The page displays all instances. 2. For the instance you are troubleshooting, under Instance State, look for a status icon and an indication of the number of checks passed. If there are no issues, you should see a green icon and "2/2 checks passed". 3. If fewer than two checks passed, refer to the tabs at the bottom of the Instances page for details. Click Status Checks to determine which check(s) failed, and troubleshoot the problem(s) as suggested. AWS does not provide serial or VGA access to instances, but it allows you to generate console screenshots. To help diagnose issues, you can take these screenshots at any time while the instance is running. 1. In the EC2 Dashboard, under Instances, select Instances. The page displays all instances. 2. Select the instance and right click. 3. On the menu, select Instance Settings > Get Instance Screenshot. The browser opens a new page with a static image of the console. 4. While troubleshooting, you can: Click Refresh to generate newer console screenshots. Right click and save screenshot images to save the information.
26 26 SGOS on AWS Deployment Guide Possible Troubleshooting Step Check the AWS security group settings and group membership for the affected instance. Details Security group settings should allow communication with Symantec servers, including the licensing server. Refer to AWS documentation for details on security groups. Change security group membership: 1. In the EC2 Dashboard, under Instances, select Instances. The page displays all instances. 2. Select the instance and right click. 3. On the menu, select Networking > Change Security Groups. 4. On the dialog that appears,select or clear security groups as needed. 5. Click Assign Security Groups. Edit security group settings: 1. In the EC2 Dashboard, under Network & Security, select Security Groups. 2. Select the security group, right click, and select Edit inbound rules or Edit outbound rules. 3. On the dialog that appears, add, remove, or configure rules as needed. 4. Click Save. Troubleshoot Licensing Errors Possible Troubleshooting Step Make sure that a supported instance type is selected. Details See "Appendix A: Supported Configurations" on page 28 to determine supported instance types. Then, verify that a supported instance type is selected: 1. In the EC2 Dashboard, under Instances, select Instances. The page displays all instances. 2. Select the instance and right click. 3. On the menu, select Instance Settings> Change Instance Type. 4. On the dialog that appears, make sure that a supported instance type is selected. 5. If the selected instance type is not one that SGOS on AWS supports: a. Stop the instance. In the Instances list, select an instance and right click. On the menu, select Instance State > Stop. b. Verify the instance state. In the Instance State column, look for a red icon and the status "stopped". c. Select the instance and right click. On the menu, select Settings > Change Instance Type. d. On the dialog, select a supported type. e. Click Apply to save your changes. f. Restart the instance. Select the instance again and right click. On the menu, select Instance State > Start.
27 SGOS on AWS Deployment Guide 27 Possible Troubleshooting Step Check the AWS security group settings and group membership for the affected instance. Details Security group settings should allow communication with Symantec servers, including the licensing server. Refer to AWS documentation for details on security groups. Change security group membership: 1. In the EC2 Dashboard, under Instances, select Instances. The page displays all instances. 2. Select the instance and right click. 3. On the menu, select Networking > Change Security Groups. 4. On the dialog that appears,select or clear security groups as needed. 5. Click Assign Security Groups. Edit security group settings: 1. In the EC2 Dashboard, under Network & Security, select Security Groups. 2. Select the security group, right click, and select Edit inbound rules or Edit outbound rules. 3. On the dialog that appears, add, remove, or configure rules as needed. 4. Click Save. Troubleshoot Credentials Errors Possible Troubleshooting Step Apply new user data. Change instance user data. Details If problems arise from lost credentials: 1. Disassociate user data. See "Step 6: Disassociate User Data from the Instance" on page While the instance is stopped, generate new user data. See step 7 in "Step 1: Complete Prerequisite Tasks" on page Select the instance again and right click. On the menu, select Instance Settings > View/Change User Data. Copy and paste the user data into the User Data field on the dialog that appears, and then click Save. 4. Restart the instance. Select the instance again and right click. On the menu, select Instance State > Start. If problems arise from compromised credentials: 1. Verify that no user data is associated with the instance. See "Step 6: Disassociate User Data from the Instance" on page Log in to the instance through SSH. 3. Issue the appropriate CLI commands to change the passwords. See the commands listed in the "AWS User Data" on page 30 section in "Appendix B: Metadata and User Data Reference" on page 29.
28 28 SGOS on AWS Deployment Guide Appendix A: Supported Configurations SGOS on AWS supports the following configurations. Configuration Settings Instance Type Supported Values SGOS on AWS supports the following instance types: t2.large m4.large (recommended) t2.medium c4.large Symantec recommends that you use the m4.large type for the best price-to-performance ratio. Using unsupported instance types is not recommended and could result in error messages and other unintended behavior. Depending on the AWS EC2 Instance Type and virtual appliance model you use, the ProxySG appliance's licensing health status might indicate a Warning. In addition, the Configured Memory statistic (in the Management Console, select Maintenance > Health Monitoring > Licensing) displays a notification that the appliance has under-provisioned memory. This is expected behavior and means that the configured virtual memory is lower than the 8 GB allowed by the license. Under-provisioned memory reduces the maximum number of connections, but it does not invalidate the license. Storage Settings Network Settings Refer to AWS documentation for more information on instance types, including virtual memory specifications: For the default Root volume, specify a single EBS volume 100 GiB in size. For Volume Type, select Magnetic or Provisioned IOPS SSD (I01) for Volume Type. Symantec recommends that if you select Provisioned IOPS, set the IOPS to 300. Refer to AWS documentation for more information on volume types: docs.aws.amazon.com/awsec2/latest/userguide/ebsvolumetypes.html You can specify multiple network interfaces if needed; however, at least one interface must have a public IP address. Symantec recommends a single network interface for both management and traffic.
29 SGOS on AWS Deployment Guide 29 Appendix B: Metadata and User Data Reference This section describes metadata and user data in AWS. AWS Metadata In AWS, each instance has access to metadata provided by the AWS infrastructure. Instance metadata is used to configure the running instance, such as some network settings. Because there is no serial console or VGA console access available for you to manually complete the initial configuration (as you would for a SWG VA, for example), the SGOS on AWS instance uses the metadata fields described in this section to configure itself. For details, see AWS documentation at Data Description Metadata Version Introduced instance-id The ID of this instance. 1.0 instance-type The type of instance public-keys/0/openssh-key Public key. Only available if supplied at instance launch time. Used to install as an authorized key for the default console username. network/interfaces/macs/mac/subnetid network/interfaces/macs/mac/vpcipv4-cidr-block The ID of the subnet in which the interface resides. Returned only for instances launched into a VPC. The subnet ID is used as a label applied to the network device. The CIDR block of the subnet in which the interface resides. Returned only for instances launched into a VPC. Used to calculate the primary DNS server of the instance
30 30 SGOS on AWS Deployment Guide Data Description Metadata Version Introduced network/interfaces/macs/mac/subnetipv4-cidr-block network/interfaces/macs/mac/localipv4s The CIDR block of the subnet in which the interface resides. Returned only for instances launched into a VPC. Used to calculate the default gateway of the instance. The private IP addresses associated with the interface. Used to apply all IP address associated to the instance This metadata is reapplied to the virtual appliance at every restart; thus, avoid making changes using the following CLI commands because any changes you make are not permanent: CLI Command #(config) dns-forwarding edit primary Do not use this command because... Primary DNS servers for the proxy have already been configured by instance metadata. Specify additional DNS servers by editing the "alternate" group. #(config) ip-default-gateway Default gateway for the proxy has already been configured by instance metadata. #(config) interface adapter_ number:interface_number #(config) wccp If required, configure additional static routes. Default settings for the network adapters have already been configured by instance metadata. AWS does not support WCCP. AWS User Data User data is required during the first boot of the SGOS instance in AWS. User data is a JSON blob that allows the instance to self-configure parameters required to initialize the instance. Generate the user data at the MySymantec website: The following is an example of the output: {"ICW_Params":{"BC_SerialNumber":" ","BC_AdminUsername":"admin","BC_ConsolePassword":"$2a$12$UjBY3DkcED02Nn96w3l0qupscB81gyLorl8NnJWL84mhRVdmkd2r6","BC_ EnablePassword":"$2a$12$8l4GTA2N59F3NM52EmGc1uPhtZEORvXjJJXqu9XS.yw2Eka0FFnLu"}} Refer to the following descriptions of the user data fields:
31 SGOS on AWS Deployment Guide 31 Field BC_SerialNumber BC_AdminUsername BC_ConsolePassword BC_EnablePassword Description The serial number associated with the VM. The user name of the console user. A bcrypt hash of the console user's password. A bcrypt hash of the enable password. This user data is reapplied to the virtual appliance at every restart. If user data is associated with the instance, avoid making changes using the following CLI commands because any changes you make are not permanent: #(config) security enable-password password #(config) security hashed-enable-password hashed_password #(config) security password password #(config) security password hashed-password hashed_password #(config) security username name AWS User Data Security Instance user data can contain sensitive information and should not be shared. To prevent accidental exposure of the data, the proxy automatically installs the following policy when detects it is running in AWS: <Proxy> url.address= FORCE_DENY This policy is designed to prevent accidental exposure of instance user data and cannot be disabled.
Blue Coat ProxySG First Steps Transparent Proxy Deployments SGOS 6.7
 Transparent Proxy Deployments SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks
Transparent Proxy Deployments SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks
Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7
 Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the
Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the
SGOS on KVM Deployment Guide
 SGOS on KVM Deployment Guide Guide Revision: 8/18/2017 2 SGOS on KVM Deployment Guide SGOS on KVM Deployment Guide 3 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec
SGOS on KVM Deployment Guide Guide Revision: 8/18/2017 2 SGOS on KVM Deployment Guide SGOS on KVM Deployment Guide 3 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec
Blue Coat Security First Steps Solution for Controlling HTTPS
 Solution for Controlling HTTPS SGOS 6.5 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks
Solution for Controlling HTTPS SGOS 6.5 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks
Migrating to a New ProxySG Appliance. ProxySG 900/9000 to ProxySG S400/500
 Migrating to a New ProxySG Appliance ProxySG 900/9000 to ProxySG S400/500 Migrating to a New Blue Coat ProxySG Appliance Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo,
Migrating to a New ProxySG Appliance ProxySG 900/9000 to ProxySG S400/500 Migrating to a New Blue Coat ProxySG Appliance Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo,
Blue Coat ProxySG First Steps Solution for Exception Pages SGOS 6.7
 Blue Coat ProxySG First Steps Solution for Exception Pages SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue
Blue Coat ProxySG First Steps Solution for Exception Pages SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue
Pulse Connect Secure Virtual Appliance on Amazon Web Services
 ` Pulse Connect Secure Virtual Appliance on Amazon Web Services Deployment Guide Release 9.0R1 Release 9.0R1 Document Revision 1.2 Published Date June 2018 Pulse Secure, LLC 2700 Zanker Road, Suite 200
` Pulse Connect Secure Virtual Appliance on Amazon Web Services Deployment Guide Release 9.0R1 Release 9.0R1 Document Revision 1.2 Published Date June 2018 Pulse Secure, LLC 2700 Zanker Road, Suite 200
Using Kerberos Authentication in a Reverse Proxy Environment
 Using Kerberos Authentication in a Reverse Proxy Environment Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat
Using Kerberos Authentication in a Reverse Proxy Environment Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat
SymantecTM Desktop and Laptop Option. Symantec DLO s Storage in Cloud (Amazon Web Services)
 SymantecTM Desktop and Laptop Option Symantec DLO s Storage in Cloud (Amazon Web Services) Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
SymantecTM Desktop and Laptop Option Symantec DLO s Storage in Cloud (Amazon Web Services) Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
SymantecTM Desktop and Laptop Option. Symantec DLO s Storage in Cloud (Amazon Web Services)
 SymantecTM Desktop and Laptop Option Symantec DLO s Storage in Cloud (Amazon Web Services) Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
SymantecTM Desktop and Laptop Option Symantec DLO s Storage in Cloud (Amazon Web Services) Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
Office 365 Best Practices: Protocols
 Office 365 Best Practices: Email Protocols VERSION 9: 08/11/17 Office 365 Integration: Email Protocols/Page 2 Skype/Lync Integration/Page 3 Copyrights Copyright 2016 Symantec Corp. All rights reserved.
Office 365 Best Practices: Email Protocols VERSION 9: 08/11/17 Office 365 Integration: Email Protocols/Page 2 Skype/Lync Integration/Page 3 Copyrights Copyright 2016 Symantec Corp. All rights reserved.
Veritas Desktop and Laptop Option 9.1 Qualification Details with Cloud Service Providers (Microsoft Azure and Amazon Web Services)
 Veritas Desktop and Laptop Option 9.1 Qualification Details with Cloud Service Providers (Microsoft Azure and Amazon Web Services) Veritas Desktop and Laptop Option: Qualification Details with Cloud Service
Veritas Desktop and Laptop Option 9.1 Qualification Details with Cloud Service Providers (Microsoft Azure and Amazon Web Services) Veritas Desktop and Laptop Option: Qualification Details with Cloud Service
F5 BIG-IQ Centralized Management and Amazon Web Services: Setup. Version 5.4
 F5 BIG-IQ Centralized Management and Amazon Web Services: Setup Version 5.4 Table of Contents Table of Contents Getting Started with BIG-IQ Virtual Edition...5 What is BIG-IQ Virtual Edition?...5 About
F5 BIG-IQ Centralized Management and Amazon Web Services: Setup Version 5.4 Table of Contents Table of Contents Getting Started with BIG-IQ Virtual Edition...5 What is BIG-IQ Virtual Edition?...5 About
IPv6 Classification. PacketShaper 11.8
 PacketShaper 11.8 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks or registered trademarks
PacketShaper 11.8 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks or registered trademarks
Multi-Tenant Policy Deployment Guide
 Multi-Tenant Policy Deployment Guide SGOS 6.6.x and later Third Party Copyright Notices Copyright 2016 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and
Multi-Tenant Policy Deployment Guide SGOS 6.6.x and later Third Party Copyright Notices Copyright 2016 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and
Symantec Protection Center Getting Started Guide. Version 2.0
 Symantec Protection Center Getting Started Guide Version 2.0 Symantec Protection Center Getting Started Guide The software described in this book is furnished under a license agreement and may be used
Symantec Protection Center Getting Started Guide Version 2.0 Symantec Protection Center Getting Started Guide The software described in this book is furnished under a license agreement and may be used
AltaVault Cloud Integrated Storage Installation and Service Guide for Cloud Appliances
 AltaVault Cloud Integrated Storage 4.4.1 Installation and Service Guide for Cloud Appliances March 2018 215-13006_A0 doccomments@netapp.com Table of Contents 3 Contents Introduction to AltaVault cloud-based
AltaVault Cloud Integrated Storage 4.4.1 Installation and Service Guide for Cloud Appliances March 2018 215-13006_A0 doccomments@netapp.com Table of Contents 3 Contents Introduction to AltaVault cloud-based
VX 9000 Virtualized Controller INSTALLATION GUIDE
 VX 9000 Virtualized Controller INSTALLATION GUIDE 2 VX 9000 Virtualized Controller Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
VX 9000 Virtualized Controller INSTALLATION GUIDE 2 VX 9000 Virtualized Controller Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
VX 9000E WiNG Express Manager INSTALLATION GUIDE
 VX 9000E WiNG Express Manager INSTALLATION GUIDE 2 VX 9000E WiNG Express Manager Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
VX 9000E WiNG Express Manager INSTALLATION GUIDE 2 VX 9000E WiNG Express Manager Service Information If you have a problem with your equipment, contact support for your region. Support and issue resolution
Deploy the Firepower Management Center Virtual On the AWS Cloud
 Deploy the Firepower Management Center Virtual On the AWS Cloud Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you define.
Deploy the Firepower Management Center Virtual On the AWS Cloud Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you define.
Symantec ediscovery Platform
 Symantec ediscovery Platform Native Viewer (ActiveX) Installation Guide 7.1.5 Symantec ediscovery Platform : Native Viewer (ActiveX) Installation Guide The software described in this book is furnished
Symantec ediscovery Platform Native Viewer (ActiveX) Installation Guide 7.1.5 Symantec ediscovery Platform : Native Viewer (ActiveX) Installation Guide The software described in this book is furnished
Filters AWS CLI syntax, 43 Get methods, 43 Where-Object command, 43
 Index Symbols AWS Architecture availability zones (AZs), 3 cloud computing, 1 regions amazon global infrastructure, 2 Govcloud, 3 list and locations, 3 services compute, 5 management, 4 monitoring, 6 network,
Index Symbols AWS Architecture availability zones (AZs), 3 cloud computing, 1 regions amazon global infrastructure, 2 Govcloud, 3 list and locations, 3 services compute, 5 management, 4 monitoring, 6 network,
Silver Peak EC-V and Microsoft Azure Deployment Guide
 Silver Peak EC-V and Microsoft Azure Deployment Guide How to deploy an EC-V in Microsoft Azure 201422-001 Rev. A September 2018 2 Table of Contents Table of Contents 3 Copyright and Trademarks 5 Support
Silver Peak EC-V and Microsoft Azure Deployment Guide How to deploy an EC-V in Microsoft Azure 201422-001 Rev. A September 2018 2 Table of Contents Table of Contents 3 Copyright and Trademarks 5 Support
EdgeConnect for Amazon Web Services (AWS)
 Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Amazon AppStream 2.0: SOLIDWORKS Deployment Guide
 2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
PCoIP Connection Manager for Amazon WorkSpaces
 PCoIP Connection Manager for Amazon WorkSpaces Version 1.0.7 Administrators' Guide TER1408002-1.0.7 Introduction Amazon WorkSpaces is a fully managed cloud-based desktop service that enables end users
PCoIP Connection Manager for Amazon WorkSpaces Version 1.0.7 Administrators' Guide TER1408002-1.0.7 Introduction Amazon WorkSpaces is a fully managed cloud-based desktop service that enables end users
SonicWall Web Application Firewall 2.0. AWS Deployment Guide
 SonicWall Web Application Firewall 2.0 AWS Deployment Guide Contents 1 Overview..........................................................................3 Before You Begin....................................................................4
SonicWall Web Application Firewall 2.0 AWS Deployment Guide Contents 1 Overview..........................................................................3 Before You Begin....................................................................4
unisys Unisys Stealth(cloud) for Amazon Web Services Deployment Guide Release 2.0 May
 unisys Unisys Stealth(cloud) for Amazon Web Services Deployment Guide Release 2.0 May 2016 8205 5658-002 NO WARRANTIES OF ANY NATURE ARE EXTENDED BY THIS DOCUMENT. Any product or related information described
unisys Unisys Stealth(cloud) for Amazon Web Services Deployment Guide Release 2.0 May 2016 8205 5658-002 NO WARRANTIES OF ANY NATURE ARE EXTENDED BY THIS DOCUMENT. Any product or related information described
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud
 How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
QUICK START: VERITAS STORAGE FOUNDATION BASIC FOR AMAZON EC2
 QUICK START: VERITAS STORAGE FOUNDATION BASIC FOR AMAZON EC2 Quick Start Guide for Using Symantec's Veritas Storage Foundation Basic for Amazon EC2 Quick Start Guide for Using Symantec's Veritas Storage
QUICK START: VERITAS STORAGE FOUNDATION BASIC FOR AMAZON EC2 Quick Start Guide for Using Symantec's Veritas Storage Foundation Basic for Amazon EC2 Quick Start Guide for Using Symantec's Veritas Storage
dbx MNT AWS Setup Guide
 dbx MNT AWS Setup Guide Rev 4.0 June 2018 XtremeData, Inc. 999 Plaza Dr., Ste. 570 Schaumburg, IL 60173 www.xtremedata.com 1. Overview... 3 1.1 Architectural Diagram... 4 1.2 Architectural Elements...
dbx MNT AWS Setup Guide Rev 4.0 June 2018 XtremeData, Inc. 999 Plaza Dr., Ste. 570 Schaumburg, IL 60173 www.xtremedata.com 1. Overview... 3 1.1 Architectural Diagram... 4 1.2 Architectural Elements...
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide. CloudLink to 4.0.3
 Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
ProxySG Virtual Appliance MACH5 Edition Initial Configuration Guide
 2015 Blue Coat Systems, Inc. All rights reserved. BLUE COAT, PROXYSG, PACKETSHAPER, CACHEFLOW, INTELLIGENCECENTER, CACHEOS, CACHEPULSE, CROSSBEAM, K9, DRTR, MACH5, PACKETWISE, POLICYCENTER, PROXYAV, PROXYCLIENT,
2015 Blue Coat Systems, Inc. All rights reserved. BLUE COAT, PROXYSG, PACKETSHAPER, CACHEFLOW, INTELLIGENCECENTER, CACHEOS, CACHEPULSE, CROSSBEAM, K9, DRTR, MACH5, PACKETWISE, POLICYCENTER, PROXYAV, PROXYCLIENT,
SonicWall Secure Mobile Access SMA 500v Virtual Appliance 8.6. Getting Started Guide
 SonicWall Secure Mobile Access SMA 500v Virtual Appliance 8.6 Getting Started Guide Copyright 2017 SonicWall Inc. All rights reserved. SonicWall is a trademark or registered trademark of SonicWall Inc.
SonicWall Secure Mobile Access SMA 500v Virtual Appliance 8.6 Getting Started Guide Copyright 2017 SonicWall Inc. All rights reserved. SonicWall is a trademark or registered trademark of SonicWall Inc.
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Partner Information. Integration Overview. Remote Access Integration Architecture
 Partner Information Partner Name Product Name Integration Overview Authentication Methods Supported Client Integration OTP Barracuda Networks Barracuda SSL VPN User Name + Security Code VIP Enterprise
Partner Information Partner Name Product Name Integration Overview Authentication Methods Supported Client Integration OTP Barracuda Networks Barracuda SSL VPN User Name + Security Code VIP Enterprise
NetApp Cloud Volumes Service for AWS
 NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
FortiMail AWS Deployment Guide
 FortiMail AWS Deployment Guide FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT https://support.fortinet.com
FortiMail AWS Deployment Guide FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT https://support.fortinet.com
QUICK START: SYMANTEC ENDPOINT PROTECTION FOR AMAZON EC2
 QUICK START: SYMANTEC ENDPOINT PROTECTION FOR AMAZON EC2 Quick Start Guide for Using Symantec Endpoint Protection for Amazon EC2 Quick Start Guide for Using Symantec Endpoint Protection for Amazon EC2
QUICK START: SYMANTEC ENDPOINT PROTECTION FOR AMAZON EC2 Quick Start Guide for Using Symantec Endpoint Protection for Amazon EC2 Quick Start Guide for Using Symantec Endpoint Protection for Amazon EC2
Veritas Desktop and Laptop Option 9.2
 1. Veritas Desktop and Laptop Option 9.2 Quick Reference Guide for DLO Installation and Configuration 24-Jan-2018 Veritas Desktop and Laptop Option: Quick Reference Guide for DLO Installation and Configuration.
1. Veritas Desktop and Laptop Option 9.2 Quick Reference Guide for DLO Installation and Configuration 24-Jan-2018 Veritas Desktop and Laptop Option: Quick Reference Guide for DLO Installation and Configuration.
Deploy and Secure an Internet Facing Application with the Barracuda Web Application Firewall in Amazon Web Services
 Deploy and Secure an Internet Facing Application with the in Amazon Web In this lab, you will deploy an unsecure web application into Amazon Web (AWS), and then secure the application using the. To create
Deploy and Secure an Internet Facing Application with the in Amazon Web In this lab, you will deploy an unsecure web application into Amazon Web (AWS), and then secure the application using the. To create
Deploying the Cisco CSR 1000v on Amazon Web Services
 Deploying the Cisco CSR 1000v on Amazon Web Services This section contains the following topics: Prerequisites, page 1 Information About Launching Cisco CSR 1000v on AWS, page 1 Launching the Cisco CSR
Deploying the Cisco CSR 1000v on Amazon Web Services This section contains the following topics: Prerequisites, page 1 Information About Launching Cisco CSR 1000v on AWS, page 1 Launching the Cisco CSR
Symantec Desktop and Laptop Option 8.0 SP2. Symantec Desktop Agent for Mac. Getting Started Guide
 Symantec Desktop and Laptop Option 8.0 SP2 Symantec Desktop Agent for Mac Getting Started Guide Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
Symantec Desktop and Laptop Option 8.0 SP2 Symantec Desktop Agent for Mac Getting Started Guide Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
Infoblox Trinzic V-x25 Series Appliances for AWS
 DEPLOYMENT GUIDE Infoblox Trinzic V-x25 Series Appliances for AWS NIOS version 8.2 Oct. 2017 2017 Infoblox Inc. All rights reserved. Infoblox Trinzic TE-Vx25 Deployment Guide October 2017 Page 1 of 29
DEPLOYMENT GUIDE Infoblox Trinzic V-x25 Series Appliances for AWS NIOS version 8.2 Oct. 2017 2017 Infoblox Inc. All rights reserved. Infoblox Trinzic TE-Vx25 Deployment Guide October 2017 Page 1 of 29
Symantec Ghost Solution Suite Web Console - Getting Started Guide
 Symantec Ghost Solution Suite Web Console - Getting Started Guide Symantec Ghost Solution Suite Web Console- Getting Started Guide Documentation version: 3.3 RU1 Legal Notice Copyright 2019 Symantec Corporation.
Symantec Ghost Solution Suite Web Console - Getting Started Guide Symantec Ghost Solution Suite Web Console- Getting Started Guide Documentation version: 3.3 RU1 Legal Notice Copyright 2019 Symantec Corporation.
CloudLink Amazon Web Services Deployment Guide
 June 2014 Notice THIS DOCUMENT CONTAINS CONFIDENTIAL AND TRADE SECRET INFORMATION OF AFORE SOLUTIONS INC AND ITS RECEIPT OR POSSESSION DOES NOT CONVEY ANY RIGHTS TO REPRODUCE OR DISCLOSE ITS CONTENTS,
June 2014 Notice THIS DOCUMENT CONTAINS CONFIDENTIAL AND TRADE SECRET INFORMATION OF AFORE SOLUTIONS INC AND ITS RECEIPT OR POSSESSION DOES NOT CONVEY ANY RIGHTS TO REPRODUCE OR DISCLOSE ITS CONTENTS,
Eucalyptus User Console Guide
 Eucalyptus 3.4.1 User Console Guide 2013-12-11 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...5 Install the Eucalyptus User Console...6 Install on Centos / RHEL 6.3...6 Configure
Eucalyptus 3.4.1 User Console Guide 2013-12-11 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...5 Install the Eucalyptus User Console...6 Install on Centos / RHEL 6.3...6 Configure
Installing the Nasuni Filer on the EC2 Platform. Version 7.9 July 2017 Last modified: July 10, Nasuni Corporation All Rights Reserved
 Installing the Nasuni Filer on the EC2 Platform Version 7.9 July 2017 Last modified: July 10, 2017 2017 Nasuni Corporation All Rights Reserved Document Information Installing the Nasuni Filer on the EC2
Installing the Nasuni Filer on the EC2 Platform Version 7.9 July 2017 Last modified: July 10, 2017 2017 Nasuni Corporation All Rights Reserved Document Information Installing the Nasuni Filer on the EC2
Quest VROOM Quick Setup Guide for Quest Rapid Recovery for Windows and Quest Foglight vapp Installers
 Quest VROOM Quick Setup Guide for Quest Rapid Recovery for Windows and Quest Foglight vapp Installers INTRODUCTION Setup of Quest VROOM requires installation of Rapid Recovery and Foglight for Virtualization
Quest VROOM Quick Setup Guide for Quest Rapid Recovery for Windows and Quest Foglight vapp Installers INTRODUCTION Setup of Quest VROOM requires installation of Rapid Recovery and Foglight for Virtualization
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
ProxySG Virtual Appliance MACH5 Edition Initial Configuration Guide
 ProxySG Virtual Appliance MACH5 Edition Initial Configuration Guide Platform: VMware ESX or ESXi Server Platform: ESX/ESXi Server Version 6.5.x and later SGOS 6.5.x and later i ProxySG Virtual Appliance
ProxySG Virtual Appliance MACH5 Edition Initial Configuration Guide Platform: VMware ESX or ESXi Server Platform: ESX/ESXi Server Version 6.5.x and later SGOS 6.5.x and later i ProxySG Virtual Appliance
PCoIP Connection Manager for Amazon WorkSpaces
 PCoIP Connection Manager for Amazon WorkSpaces Version 1.0 Administrators' TER1408002-1.0 Contents Who Should Read This 3 What's New 4 Introduction 5 Before You Begin 5 Additional Documentation 6 Network
PCoIP Connection Manager for Amazon WorkSpaces Version 1.0 Administrators' TER1408002-1.0 Contents Who Should Read This 3 What's New 4 Introduction 5 Before You Begin 5 Additional Documentation 6 Network
CPM. Quick Start Guide V2.4.0
 CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
Veritas Desktop Agent for Mac Getting Started Guide
 Veritas Desktop Agent for Mac Getting Started Guide The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation
Veritas Desktop Agent for Mac Getting Started Guide The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation
Veritas Desktop and Laptop Option Mac Getting Started Guide
 Veritas Desktop and Laptop Option 9.3.1 Mac Getting Started Guide 20-Nov-18 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms
Veritas Desktop and Laptop Option 9.3.1 Mac Getting Started Guide 20-Nov-18 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms
Configuring AWS for Zerto Virtual Replication
 Configuring AWS for Zerto Virtual Replication VERSION 1 MARCH 2018 Table of Contents 1. Prerequisites... 2 1.1. AWS Prerequisites... 2 1.2. Additional AWS Resources... 3 2. AWS Workflow... 3 3. Setting
Configuring AWS for Zerto Virtual Replication VERSION 1 MARCH 2018 Table of Contents 1. Prerequisites... 2 1.1. AWS Prerequisites... 2 1.2. Additional AWS Resources... 3 2. AWS Workflow... 3 3. Setting
Tetration Cluster Cloud Deployment Guide
 First Published: 2017-11-16 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE
First Published: 2017-11-16 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE
1.0. Quest Enterprise Reporter Discovery Manager USER GUIDE
 1.0 Quest Enterprise Reporter Discovery Manager USER GUIDE 2012 Quest Software. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
1.0 Quest Enterprise Reporter Discovery Manager USER GUIDE 2012 Quest Software. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide
 VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide The software described in this book is furnished
VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide The software described in this book is furnished
Veritas CloudPoint 1.0 Administrator's Guide
 Veritas CloudPoint 1.0 Administrator's Guide Veritas CloudPoint Administrator's Guide Last updated: 2017-09-13 Document version: 1.0 Rev 6 Legal Notice Copyright 2017 Veritas Technologies LLC. All rights
Veritas CloudPoint 1.0 Administrator's Guide Veritas CloudPoint Administrator's Guide Last updated: 2017-09-13 Document version: 1.0 Rev 6 Legal Notice Copyright 2017 Veritas Technologies LLC. All rights
Immersion Day. Getting Started with Windows Server on Amazon EC2. June Rev
 Getting Started with Windows Server on Amazon EC2 June 2017 Rev 2015-09-19 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance...
Getting Started with Windows Server on Amazon EC2 June 2017 Rev 2015-09-19 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance...
Quest VROOM Quick Setup Guide for Quest Rapid Recovery for Windows and Quest Foglight vapp Installers
 Quest VROOM Quick Setup Guide for Quest Rapid Recovery for Windows and Quest Foglight vapp Installers INTRODUCTION Setup of Quest VROOM requires installation of Rapid Recovery and Foglight for Virtualization
Quest VROOM Quick Setup Guide for Quest Rapid Recovery for Windows and Quest Foglight vapp Installers INTRODUCTION Setup of Quest VROOM requires installation of Rapid Recovery and Foglight for Virtualization
F5 iworkflow and Microsoft Hyper-V: Setup. Version 2.2.0
 F5 iworkflow and Microsoft Hyper-V: Setup Version 2.2.0 Table of Contents Table of Contents Getting Started with iworkflow Virtual Edition... 5 What is iworkflow Virtual Edition?... 5 About iworkflow
F5 iworkflow and Microsoft Hyper-V: Setup Version 2.2.0 Table of Contents Table of Contents Getting Started with iworkflow Virtual Edition... 5 What is iworkflow Virtual Edition?... 5 About iworkflow
Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide
 Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Documentation version:
Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Documentation version:
Symantec Managed PKI. Integration Guide for ActiveSync
 Symantec Managed PKI Integration Guide for ActiveSync ii Symantec Managed PKI Symantec Managed PKI Integration Guide for ActiveSync The software described in this book is furnished under a license agreement
Symantec Managed PKI Integration Guide for ActiveSync ii Symantec Managed PKI Symantec Managed PKI Integration Guide for ActiveSync The software described in this book is furnished under a license agreement
MyIGW Main. Oregon. MyVPC /16. MySecurityGroup / us-west-2b. Type Port Source SSH /0 HTTP
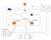 MyIGW Main Oregon MyVPC 10.0.0.0/16 10.0.1.0/24 10.0.1.0 -- us-west-2a MySecurityGroup 10.0.2.0/24 10.0.2.0 -- us-west-2b MyWebServer1 MyDBServer DMZ MyInternetRouteTable 0.0.0.0/0 IGW Type Port Source
MyIGW Main Oregon MyVPC 10.0.0.0/16 10.0.1.0/24 10.0.1.0 -- us-west-2a MySecurityGroup 10.0.2.0/24 10.0.2.0 -- us-west-2b MyWebServer1 MyDBServer DMZ MyInternetRouteTable 0.0.0.0/0 IGW Type Port Source
ElasterStack 3.2 User Administration Guide - Advanced Zone
 ElasterStack 3.2 User Administration Guide - Advanced Zone With Advance Zone Configuration TCloud Computing Inc. 6/22/2012 Copyright 2012 by TCloud Computing, Inc. All rights reserved. This document is
ElasterStack 3.2 User Administration Guide - Advanced Zone With Advance Zone Configuration TCloud Computing Inc. 6/22/2012 Copyright 2012 by TCloud Computing, Inc. All rights reserved. This document is
LB Cache Quick Start Guide v1.0
 LB Cache Quick Start Guide v1.0 Rev. 1.1.0 Copyright 2002 2017 Loadbalancer.org, Inc Table of Contents Introduction...3 About LBCache...3 Amazon Terminology...3 Getting Started...3 Deployment Concepts...4
LB Cache Quick Start Guide v1.0 Rev. 1.1.0 Copyright 2002 2017 Loadbalancer.org, Inc Table of Contents Introduction...3 About LBCache...3 Amazon Terminology...3 Getting Started...3 Deployment Concepts...4
Symantec Workflow 7.1 MP1 Release Notes
 Symantec Workflow 7.1 MP1 Release Notes Symantec Workflow 7.1 MP1 Release Notes The software described in this book is furnished under a license agreement and may be used only in accordance with the terms
Symantec Workflow 7.1 MP1 Release Notes Symantec Workflow 7.1 MP1 Release Notes The software described in this book is furnished under a license agreement and may be used only in accordance with the terms
Installation of Informatica Services on Amazon EC2
 Installation of Informatica Services on Amazon EC2 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Installation of Informatica Services on Amazon EC2 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
CloudEdge Deployment Guide
 Hillstone Networks, Inc. CloudEdge Deployment Guide Version 5.5R3P1 Copyright 2016Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice. The software
Hillstone Networks, Inc. CloudEdge Deployment Guide Version 5.5R3P1 Copyright 2016Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice. The software
Blue Coat Security First Steps Solution for Exception Pages
 Blue Coat Security First Steps Solution for Exception Pages SGOS 6.5 Third Party Copyright Notices 2014 Blue Coat Systems, Inc. All rights reserved. BLUE COAT, PROXYSG, PACKETSHAPER, CACHEFLOW, INTELLIGENCECENTER,
Blue Coat Security First Steps Solution for Exception Pages SGOS 6.5 Third Party Copyright Notices 2014 Blue Coat Systems, Inc. All rights reserved. BLUE COAT, PROXYSG, PACKETSHAPER, CACHEFLOW, INTELLIGENCECENTER,
Wave 5.0. Wave OpenVPN Server Guide for Wave 5.0
 Wave 5.0 Wave OpenVPN Server Guide for Wave 5.0 2015 by Vertical Communications, Inc. All rights reserved. Vertical Communications and the Vertical Communications logo and combinations thereof and Vertical
Wave 5.0 Wave OpenVPN Server Guide for Wave 5.0 2015 by Vertical Communications, Inc. All rights reserved. Vertical Communications and the Vertical Communications logo and combinations thereof and Vertical
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
Veritas System Recovery 18 Management Solution Administrator's Guide
 Veritas System Recovery 18 Management Solution Administrator's Guide Documentation version: 18 Legal Notice Copyright 2018 Veritas Technologies LLC. All rights reserved. Veritas and the Veritas Logo are
Veritas System Recovery 18 Management Solution Administrator's Guide Documentation version: 18 Legal Notice Copyright 2018 Veritas Technologies LLC. All rights reserved. Veritas and the Veritas Logo are
CA Agile Central Administrator Guide. CA Agile Central On-Premises
 CA Agile Central Administrator Guide CA Agile Central On-Premises 2018.1 Table of Contents Overview... 3 Server Requirements...3 Browser Requirements...3 Access Help and WSAPI...4 Time Zone...5 Architectural
CA Agile Central Administrator Guide CA Agile Central On-Premises 2018.1 Table of Contents Overview... 3 Server Requirements...3 Browser Requirements...3 Access Help and WSAPI...4 Time Zone...5 Architectural
BIG-IP Virtual Edition and Microsoft Hyper- V: Setup. Version 13.1
 BIG-IP Virtual Edition and Microsoft Hyper- V: Setup Version 13.1 Table of Contents Table of Contents Getting Started with BIG-IP Virtual Edition in Hyper-V... 5 About single NIC and multi-nic configurations...5
BIG-IP Virtual Edition and Microsoft Hyper- V: Setup Version 13.1 Table of Contents Table of Contents Getting Started with BIG-IP Virtual Edition in Hyper-V... 5 About single NIC and multi-nic configurations...5
Amazon Virtual Private Cloud. Getting Started Guide
 Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
FortiManager VM - Install Guide. Version 5.6
 FortiManager VM - Install Guide Version 5.6 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE &
FortiManager VM - Install Guide Version 5.6 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE &
Log & Event Manager UPGRADE GUIDE. Version Last Updated: Thursday, May 25, 2017
 UPGRADE GUIDE Log & Event Manager Version 6.3.1 Last Updated: Thursday, May 25, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/log_event_manager_(lem)/lem_documentation
UPGRADE GUIDE Log & Event Manager Version 6.3.1 Last Updated: Thursday, May 25, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/log_event_manager_(lem)/lem_documentation
Symantec Cloud Workload Protection on AWS Marketplace. Buyer's Guide for Getting Started
 Symantec Cloud Workload Protection on AWS Marketplace Buyer's Guide for Getting Started The software described in this book is furnished under a license agreement and may be used only in accordance with
Symantec Cloud Workload Protection on AWS Marketplace Buyer's Guide for Getting Started The software described in this book is furnished under a license agreement and may be used only in accordance with
How to Setup Total Application Security
 How to Setup Total Application Security TABLE OF CONTENTS Access Total Application Security on AWS Marketplace... 2 Configuring Total Application Security... 12 Total Application Security Portal Access...
How to Setup Total Application Security TABLE OF CONTENTS Access Total Application Security on AWS Marketplace... 2 Configuring Total Application Security... 12 Total Application Security Portal Access...
Cluster Server Generic Application Agent Configuration Guide - AIX, Linux, Solaris
 Cluster Server 7.3.1 Generic Application Agent Configuration Guide - AIX, Linux, Solaris Last updated: 2017-11-04 Legal Notice Copyright 2017 Veritas Technologies LLC. All rights reserved. Veritas and
Cluster Server 7.3.1 Generic Application Agent Configuration Guide - AIX, Linux, Solaris Last updated: 2017-11-04 Legal Notice Copyright 2017 Veritas Technologies LLC. All rights reserved. Veritas and
CIT 668: System Architecture
 CIT 668: System Architecture Amazon Web Services I Topics 1. Economics 2. Key Concepts 3. Key Services 4. Elastic Compute Cloud 5. Creating an EC2 Instance Images from AWS EC2 User Guide or Wikipedia unless
CIT 668: System Architecture Amazon Web Services I Topics 1. Economics 2. Key Concepts 3. Key Services 4. Elastic Compute Cloud 5. Creating an EC2 Instance Images from AWS EC2 User Guide or Wikipedia unless
Netwrix Auditor. Virtual Appliance and Cloud Deployment Guide. Version: /25/2017
 Netwrix Auditor Virtual Appliance and Cloud Deployment Guide Version: 9.5 10/25/2017 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Netwrix Auditor Virtual Appliance and Cloud Deployment Guide Version: 9.5 10/25/2017 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Silver Peak. AWS EC-V for Multi- Instance Inbound Load Balancing
 Silver Peak AWS EC-V for Multi- Instance Inbound Load Balancing Copyright and Trademarks Silver Peak AWS EC-V for Multi-Instance Inbound Load Balancing Guide Date: January 2017 Copyright 2017 Silver Peak
Silver Peak AWS EC-V for Multi- Instance Inbound Load Balancing Copyright and Trademarks Silver Peak AWS EC-V for Multi-Instance Inbound Load Balancing Guide Date: January 2017 Copyright 2017 Silver Peak
NetBackup Copilot for Oracle Configuration Guide. Release 2.7.1
 NetBackup Copilot for Oracle Configuration Guide Release 2.7.1 NetBackup Copilot for Oracle Configuration Guide Documentation version: 2.7.1 Legal Notice Copyright 2015 Symantec Corporation. All rights
NetBackup Copilot for Oracle Configuration Guide Release 2.7.1 NetBackup Copilot for Oracle Configuration Guide Documentation version: 2.7.1 Legal Notice Copyright 2015 Symantec Corporation. All rights
Immersion Day. Creating an Elastic Load Balancer. September Rev
 September 2016 Rev 2016-01 Table of Contents Overview... 3 Elastic Load Balancer... 3 Launch a Second Web Server... 5 Create an ELB... 7 Copyright 2015, Amazon Web Services, All Rights Reserved Page 2
September 2016 Rev 2016-01 Table of Contents Overview... 3 Elastic Load Balancer... 3 Launch a Second Web Server... 5 Create an ELB... 7 Copyright 2015, Amazon Web Services, All Rights Reserved Page 2
BIG-IP Virtual Edition and Microsoft Hyper- V: Setup. Version 12.1
 BIG-IP Virtual Edition and Microsoft Hyper- V: Setup Version 12.1 Table of Contents Table of Contents Getting Started with BIG-IP Virtual Edition on Hyper-V... 5 Steps to deploy BIG-IP VE...5 Prerequisites
BIG-IP Virtual Edition and Microsoft Hyper- V: Setup Version 12.1 Table of Contents Table of Contents Getting Started with BIG-IP Virtual Edition on Hyper-V... 5 Steps to deploy BIG-IP VE...5 Prerequisites
Immersion Day. Getting Started with Windows Server on. Amazon EC2. Rev
 Getting Started with Windows Server on Amazon EC2 Rev 2015-01-15 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance... 13
Getting Started with Windows Server on Amazon EC2 Rev 2015-01-15 Table of Contents Overview... 3 Launch a Web Server Instance... 4 Browse the Web Server... 12 Connecting To Your Windows Instance... 13
FortiManager VM - Install Guide VERSION 5.4
 FortiManager VM - Install Guide VERSION 5.4 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE &
FortiManager VM - Install Guide VERSION 5.4 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE &
Tanium IaaS Cloud Solution Deployment Guide for Microsoft Azure
 Tanium IaaS Cloud Solution Deployment Guide for Microsoft Azure Version: All December 21, 2018 The information in this document is subject to change without notice. Further, the information provided in
Tanium IaaS Cloud Solution Deployment Guide for Microsoft Azure Version: All December 21, 2018 The information in this document is subject to change without notice. Further, the information provided in
Symantec Enterprise Vault
 Symantec Enterprise Vault Guide for Microsoft Outlook 2010/2013 Users 11.0 Light Outlook Add-In Symantec Enterprise Vault: Guide for Microsoft Outlook 2010/2013 Users The software described in this book
Symantec Enterprise Vault Guide for Microsoft Outlook 2010/2013 Users 11.0 Light Outlook Add-In Symantec Enterprise Vault: Guide for Microsoft Outlook 2010/2013 Users The software described in this book
AppGate for AWS Step-by-Step Setup Guide. Last revised April 28, 2017
 AppGate for AWS Step-by-Step Setup Guide Last revised April 28, 2017 Contents Welcome & Overview... 2 Getting Started... 3 Pre-Requisites... 4 But what about Security Groups?... 5 Browser Compatibility:...
AppGate for AWS Step-by-Step Setup Guide Last revised April 28, 2017 Contents Welcome & Overview... 2 Getting Started... 3 Pre-Requisites... 4 But what about Security Groups?... 5 Browser Compatibility:...
Hands-On Lab. Windows Azure Virtual Machine Roles. Lab version: Last updated: 12/14/2010. Page 1
 Hands-On Lab Windows Azure Virtual Machine Roles Lab version: 2.0.0 Last updated: 12/14/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: CREATING AND DEPLOYING A VIRTUAL MACHINE ROLE IN WINDOWS AZURE...
Hands-On Lab Windows Azure Virtual Machine Roles Lab version: 2.0.0 Last updated: 12/14/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: CREATING AND DEPLOYING A VIRTUAL MACHINE ROLE IN WINDOWS AZURE...
Message Manager Administrator Guide
 Message Manager Administrator Guide Documentation version: 2.0 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered
Message Manager Administrator Guide Documentation version: 2.0 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered
Veritas System Recovery 16 Management Solution Administrator's Guide
 Veritas System Recovery 16 Management Solution Administrator's Guide Documentation version: 2017 Legal Notice Copyright 2017 Veritas Technologies LLC. All rights reserved. Veritas and the Veritas Logo
Veritas System Recovery 16 Management Solution Administrator's Guide Documentation version: 2017 Legal Notice Copyright 2017 Veritas Technologies LLC. All rights reserved. Veritas and the Veritas Logo
F5 iworkflow and Citrix XenServer: Setup. Version 2.0.1
 F5 iworkflow and Citrix XenServer: Setup Version 2.0.1 Table of Contents Table of Contents Getting Started with iworkflow Virtual Edition... 5 What is iworkflow Virtual Edition?... 5 About iworkflow VE
F5 iworkflow and Citrix XenServer: Setup Version 2.0.1 Table of Contents Table of Contents Getting Started with iworkflow Virtual Edition... 5 What is iworkflow Virtual Edition?... 5 About iworkflow VE
Symantec Managed PKI. Integration Guide for AirWatch MDM Solution
 Symantec Managed PKI Integration Guide for AirWatch MDM Solution ii Symantec Managed PKI Integration Guide for AirWatch MDM Solution The software described in this book is furnished under a license agreement
Symantec Managed PKI Integration Guide for AirWatch MDM Solution ii Symantec Managed PKI Integration Guide for AirWatch MDM Solution The software described in this book is furnished under a license agreement
Server Installation ZENworks Mobile Management 2.6.x January 2013
 www.novell.com/documentation Server Installation ZENworks Mobile Management 2.6.x January 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.6.x January 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
