PIX/ASA: Upgrade a Software Image using ASDM or CLI Configuration Example
|
|
|
- Darlene Holmes
- 6 years ago
- Views:
Transcription
1 PIX/ASA: Upgrade a Software Image using ASDM or CLI Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Download Software Upgrade a Software Image using ASDM 5.x Upgrade an ASDM Image using ASDM 5.x Upgrade a Software Image with ASDM 6.x Upgrade an ASDM Image with ASDM 6.x Upgrade a Software Image and ASDM Image using CLI Verify Troubleshoot Related Information Introduction This document describes how to upgrade a software image on the Cisco ASA 5500 Series Adaptive Security Appliances using the Cisco Adaptive Security Device Manager (ASDM). ASDM does not work if you upgrade (or downgrade) the security appliance software from 7.0 to 7.2 directly or upgrade (or downgrade) the ASDM software from 5.0 to 5.2 directly. You need to do it in incremental order. Example: In order to perform the ASDM software upgrade from 5.0 to 5.2, first upgrade from 5.0 to 5.1 and then upgrade from 5.1 to 5.2. Likewise, for the security appliance, first upgrade from 7.0 to 7.1 and then upgrade from 7.1 to 7.2. Note: If you want to upgrade or downgrade from version 7.1.(x) to 7.2(x) and vice versa, you must follow the steps in this procedure since older versions of the security appliance images do not recognize new ASDM images and new security appliance images do not recognize old ASDM images. Refer to the Upgrading to a New Software Version section of Cisco PIX Security Appliance Release Notes, Version 7.2(2) in order to learn more about the upgrade procedures. Note: You cannot downgrade the ASA 5550 to a software version earlier than 7.1(2). Similarly, you cannot downgrade the ASA 5505 to a software version earlier than 7.2. Refer to Cisco ASA 5500 Series and PIX 500 Series Security Appliance Hardware and Software Compatibility for more information.
2 Note: In Multicontext mode, you cannot use the copy tftp flash command to upgrade or downgrade the PIX/ASA image in all contexts; it is supported only in the System Exec mode. Prerequisites Requirements There are no specific requirements for this document. Components Used The information in this document is based on these software and hardware versions: Cisco ASA and later Cisco ASDM 5.0 and later The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Related Products This configuration can also be used with Cisco PIX 500 Series Security Appliance Software Version 7.0 and later. Conventions Refer to the Cisco Technical Tips Conventions for more information on document conventions. Download Software You can download your required release version of ASA Software images and ASDM Software images using these links: Cisco ASA Software Release Download (registered customers only) Cisco ASDM Software Release Download (registered customers only) Note: You need to have valid Cisco user credentials in order to download this software from Cisco.com. Upgrade a Software Image using ASDM 5.x Complete these steps to upgrade a software image on the ASA 5500 using ASDM. 1. Select Tools > Upgrade Software... from the Home window of the ASDM.
3 2. Select the type of image to upload from the drop-down menu. 3. Click Browse Local Files... or type the path in the Local File Path field to specify the location of the software image on your PC. 4. Click Browse Flash...A Browse Flash Dialog window appears with the file name entered automatically. If the file name does not appear, enter it manually in the File Name field. Click OK when you are done.
4 5. Once both the local and remote file names are specified, click Upload Image. A Status window appears while ASDM writes the image to Flash.
5 Once completed, an Information window appears that indicates a successful upload. 6. Click OK in the Information window and then Close in the Upload Image from Local PC window. 7. Choose Configuration > Properties > Device Administration > Boot Image/Configuration > Edit in order to change the boot image location.
6 Click Browse Flash in order to choose or specify the ASA image file. Then click OK. 8. Choose File > Save Running Configuration to Flash in order to store the configuration to Flash memory.
7 9. Choose Tools > System Reload from the Home window to reload the device. 10. A new window appears that asks you to verify the details of the reload. Select Save the running configuration at the time of reload and then choose a time to reload.now Reboot the device immediately.delay By Specify in how many minutes or hours from now to reload the device.schedule at Specify a time and date to reload the
8 device.you can also specify whether or not the device should force a reload immediately if a scheduled reload fails. Check On Reload failure, force an immediate reload after and then specify a maximum hold time. This is the amount of time that the security appliance waits to notify other subsystems before a shutdown or reboot. After this time elapses, a quick (forced) shutdown/reboot occurs. Click Schedule Reload. 11. Once the reload is in progress, a Reload Status window appears that indicates that a reload is being performed. An option to exit ASDM is also provided.note: Start ASDM again after the ASA reloads.
9 Upgrade an ASDM Image using ASDM 5.x Complete these steps to upgrade an ASDM image on the ASA 5500 using ASDM. 1. Choose Tools > Upgrade Software... from the Home window of the ASDM.
10 2. Select the type of image to upload from the drop-down menu. 3. Click Browse Local... or type the path in the Local File Path field to specify the location of the ASDM image on your PC. 4. Click Browse Flash...A Browse Flash Dialog window appears with the file name entered automatically. If the file name does not appear, enter it manually in the File Name field. Click OK when you are
11 done. 5. Once both the local and remote file names are specified, click Upload Image. A Status window appears while ASDM writes the image to Flash.
12 Once completed, an Information window appears that indicates a successful upload. 6. Click OK in the Information window and then Close in the Upload Image from Local PC window. 7. Choose Configuration > Properties > Device Administration > Boot Image/Configuration in order to change the ASDM image file name in the configuration.
13 Click Browse Flash in order to choose or specify the ASDM image file. Then click OK. 8. Choose File > Save Running Configuration to Flash in order to store the configuration to Flash memory.
14 9. Choose Tools > System Reload from the Home window to reload the device. 10. A new window appears that asks you to verify the details of the reload. Click Save the running configuration at the time of reload and then choose a time to reload.now Reboot the device immediately.delay By Specify in how many minutes or hours from now to reload the device.schedule at Specify a time and date to reload the
15 device.you can also specify whether or not the device should force a reload immediately if a scheduled reload fails. Check On Reload failure, force an immediate reload after and then specify a maximum hold time. This is the amount of time that the security appliance waits to notify other subsystems before a shutdown or reboot. After this time elapses, a quick (forced) shutdown/reboot occurs. Click Schedule Reload. 11. Once the reload is in progress, a Reload Status window appears that indicates that a reload is being performed. An option to exit ASDM is also provided.note: Start ASDM again after the ASA reloads.
16 Upgrade a Software Image with ASDM 6.x Note: ASDM 6.x is supported only on ASA software image 8.x and later. Complete these steps to upgrade a software image on the ASA 5500 with ASDM: 1. Choose Tools > Upgrade Software from Local computer... from the Home window of the ASDM.
17 2. Choose the type of image to upload from the drop-down menu. 3. Click Browse Local Files... or type the path in the Local File Path field to specify the location of the software image on your PC. The file path in Flash File System is automatically determined and shown. If the file path in Flash File System is not shown, you can type it manually or click Browse Flash and choose the path.
18 4. Once both of the file paths are specified, click Upload Image. A Status window appears while ASDM writes the image to Flash. 5. Once completed, an Information window appears that indicates a successful upload and asks to set this image as boot image. Click Yes if you want the new image to be set as boot image; otherwise click No. 6. If you click Yes, it sets the new image as the boot image, and a Information box appears. Click OK.
19 7. Choose Tools > System Reload from the Home window to reload the device. 8. A new window appears that asks you to verify the details of the reload. Choose Save the running configuration at the time of reload, and then choose a time to reload.now Reboot the device immediately.delay By Specify in how many minutes or hours from now to reload the device.schedule at Specify a time and date to reload the device.you can also specify whether or not the device must force a reload immediately if a scheduled reload fails. Check On Reload failure, force an immediate reload after, and then specify a maximum hold time. This is the amount of time that the security appliance waits to notify other subsystems before a shutdown or reboot. After this time elapses, a quick (forced) shutdown/reboot occurs. Click Schedule Reload.
20 9. Once the reload is in progress, a Reload Status window appears that indicates that a reload is being performed. An option to exit ASDM is also provided. Click Exit ASDM, and restart ASDM after the device reloads.
21 Upgrade an ASDM Image with ASDM 6.x Note: ASDM 6.x is supported only on ASA software image 8.x and later. Complete these steps to upgrade an ASDM image on the ASA 5500 with ASDM: 1. Choose Tools > Upgrade Software from Local Computer... from the Home window of the ASDM.
22 2. Choose the type of image to upload from the drop-down menu. 3. Click Browse Local Files... or type the path in the Local File Path field to specify the location of the ASDM image on your PC. The file path in Flash File System is automatically determined and shown. If the file path in Flash File System is not shown, you can type it manually or click Browse Flash and choose the path.
23 4. Once both of the file paths are specified, click Upload Image. A Status window appears while ASDM writes the image to Flash. 5. Once completed, an Information window appears that indicates a successful upload and asks to set this image as the default an ASDM image. Click Yes if you want the new image to be set as the ASDM image; otherwise click No. 6. If you chose Yes to use the new image as the ASDM image, an Information box appears. Click OK.
24 7. Click Save on top of the window to save the running configuration to Flash. 8. A dialog box appears for your confirmation. Click Apply. 9. Click File on top of window, and choose Exit to close ASDM.
25 10. A dialog box can appear that asks for your confirmation. Click Yes. 11. Run ASDM again to load the new ASDM image.refer to this video for more information: How to upgrade the software image on a Cisco Adaptive Security Appliance(ASA) using Cisco Adaptive Security Device Manager (ASDM) This video posted to the Cisco Support Community describes how to upgrade the software image on Cisco ASA using ASDM: How to upgrade the software image on a Cisco Adaptive Security Appliance(ASA) using Cisco Adaptive Security Device Manager(ASDM)
26 Upgrade a Software Image and ASDM Image using CLI A TFTP server is required to upgrade or downgrade a software image as well as an ASDM image for a PIX/ASA. Refer to TFTP Server Selection and Use in order to learn more about TFTP server selection. The copy tftp flash command enables you to download a software image into the Flash memory of the firewall via TFTP. You can use the copy tftp flash command with any security appliance model. The image you download is made available to the security appliance on the next reload (reboot). This is the output from the copy tftp flash command: copy tftp[:[[//location] [/tftp_pathname]]] [[flash/disk0][:[image asdm]]] Note: For ASA, keyword disk0 replaces flash in the copy command. If the command is used without the location or pathname optional parameters, then the location and filename are obtained from the user interactively via a series of questions similar to those presented by Cisco IOS software. If you only enter a colon, parameters are taken from the tftpserver command settings. If other optional parameters are supplied, then these values are used in place of the corresponding tftp-server command setting. If any of the optional parameters, such as a colon and anything after it are supplied, the command runs without a prompt for user input. The location is either an IP address or a name that resolves to an IP address via the security appliance naming resolution mechanism, which is currently static mappings via the name and names commands. The security appliance must know how to reach this location via its routing table information. This information is determined by the IP address, the route, or the RIP
27 commands. This depends on your configuration. The pathname can include any directory names besides the actual last component of the path to the file on the server. The pathname cannot contain spaces. If a directory name has spaces set to the directory in the TFTP server instead of in the copy tftp flash command, and if your TFTP server is configured to point to a directory on the system from which you download the image, you only need to use the IP address of the system and the image filename. The TFTP server receives the command and determines the actual file location from its root directory information. The server then downloads the TFTP image to the security appliance. These commands are needed to upgrade the software image as well as the ASDM image and make it as a boot image at the next reload. Example: ASA#copy tftp [[flash:/disk0:][software image name/asdm image name]]!--- Command to set an image as bootup or specify the!--- ASDM image file. ASA(config)#boot system [flash:/disk0:]/[software image name]!--- Save active configuration to the Flash. ASA#write memory!--- Reboot the security appliance and load!--- with the new boot image as per the configuration file. ASA#reload ASA5510#copy tftp disk0: Address or name of remote host []? Source filename []? asa722-k8.bin Destination filename [asa722-k8.bin]? Accessing tftp:// /asa722-k8.bin...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Writing file disk0:/asa722-k8.bin...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! bytes copied in secs (50998 bytes/sec) ASA5510#show disk0: -#- --length date/time path Jan :06:22 asa702-k8.bin Feb :23:48 asdm-522.bin Feb :14:18 asdm-521.bin Dec :47:20 asa k8.bin Dec :58:30 asdm bin Feb :46:30 asa722-k8.bin bytes available ( bytes used)!--- Command to set "asa722-k8.bin" as the boot image. ASA5510(config)# boot system disk0:/asa722-k8.bin!--- Command to set "asdm-522.bin" as the ASDM image. ASA5510(config)# asdm image disk0:/asdm-522.bin ASA5510# write memory ASA5510# reload Note: When you try to upgrade the image on the ASA from an FTP server, you can use the copy ftp flash command. This command allows you to specify parameters, such as remote IP address and source file name. This procedure is similar to TFTP. However, one limitation with is that you can not modify the remote IP/source interface (like you can with TFTP). In TFTP mode, options specified with the tftp-server command can be pulled and executed. But with FTP, there is no such option. The source interface should always be the outside by default, which cannot be modified. That is, the FTP server should be reachable from the outside interface. Verify Use this section to confirm that your software upgrade was successful. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output. After the ASA reloads and you have successfully logged into ASDM again, you can verify the
28 version of the image that runs on the device. See the General tab on the Home window for this information. These CLI commands are used in order to verify the upgrade: 1. Show version This shows the current image with which the ASA is booted. 2. Show bootvar This shows the priority of the image to be used after reload. 3. Show asdm image This shows the current asdm image used by ASA. Troubleshoot There is currently no specific troubleshooting information available for this configuration. Related Information Downloading Software or Configuration Files to Flash Memory, Cisco Security Appliance Command Line Configuration Guide Cisco ASA 5500 Series Adaptive Security Appliances Product Support Cisco Adaptive Security Device Manager Product Support Cisco PIX Firewall Software Cisco Secure PIX Firewall Command References Security Product Field Notices (including PIX) TFTP Server Selection and Use Backup and Restore PIX Configuration Files Requests for Comments (RFCs)
29 ASA 8.3 Upgrade - What You Need to Know Technical Support & Documentation - Cisco Systems
PIX/ASA 7.x to 7.x Upgrade a Software Image using ASDM or CLI Configuration Example
 PIX/ASA 7.x to 7.x Upgrade a Software Image using ASDM or CLI Configuration Example Document ID: 69984 Introduction Prerequisites Requirements Components Used Related Products Conventions Upgrade a Software
PIX/ASA 7.x to 7.x Upgrade a Software Image using ASDM or CLI Configuration Example Document ID: 69984 Introduction Prerequisites Requirements Components Used Related Products Conventions Upgrade a Software
Upgrade ASA and ASDM Cisco ASA Firewall
 Upgrade ASA and ASDM Cisco ASA Firewall Complete these steps to upgrade a software image on the ASA 5500 using ASDM. 1. Select Tools > Upgrade Software... from the Home window of the ASDM. 2. Select the
Upgrade ASA and ASDM Cisco ASA Firewall Complete these steps to upgrade a software image on the ASA 5500 using ASDM. 1. Select Tools > Upgrade Software... from the Home window of the ASDM. 2. Select the
Deploying Cisco ASA Firewall Features (FIREWALL) v1.0. Global Knowledge European Remote Labs Instructor Guide
 Deploying Cisco ASA Firewall Features (FIREWALL) v1.0 Global Knowledge European Remote Labs Instructor Guide Revision Draft 0.2 11/03/2011 1. Contents 1. Contents.2 2. Introduction.3 3. Remote Labs Topology,
Deploying Cisco ASA Firewall Features (FIREWALL) v1.0 Global Knowledge European Remote Labs Instructor Guide Revision Draft 0.2 11/03/2011 1. Contents 1. Contents.2 2. Introduction.3 3. Remote Labs Topology,
Table of Contents. Cisco WebVPN Capture Tool on the Cisco ASA 5500 Series Adaptive Security Appliance
 Table of Contents WebVPN Capture Tool on the Cisco ASA 5500 Series Adaptive Security Appliance...1 Document ID: 65096...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2
Table of Contents WebVPN Capture Tool on the Cisco ASA 5500 Series Adaptive Security Appliance...1 Document ID: 65096...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2
Upgrading Software and Firmware
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
PIX/ASA: PPPoE Client Configuration Example
 PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
Password Recovery Procedure for the PIX
 Password Recovery Procedure for the PIX Document ID: 8529 Introduction Prerequisites Requirements Components Used Conventions Step by Step Procedure PIX With a Floppy Drive PIX Without a Floppy Drive Sample
Password Recovery Procedure for the PIX Document ID: 8529 Introduction Prerequisites Requirements Components Used Conventions Step by Step Procedure PIX With a Floppy Drive PIX Without a Floppy Drive Sample
Lab 3.4.6a Configure the PIX Security Appliance using Setup Mode and ASDM Startup Wizard
 Lab 3.4.6a Configure the PIX Security Appliance using Setup Mode and ASDM Startup Wizard Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Verify that the
Lab 3.4.6a Configure the PIX Security Appliance using Setup Mode and ASDM Startup Wizard Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Verify that the
Getting Started. Getting Started with Your Platform Model. Factory Default Configurations CHAPTER
 CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Using Cisco Unity Express Software
 Using Cisco Unity Express Software Last Updated: May 1, 2006 This chapter provides helpful tips for understanding and configuring Cisco Unity Express software using the command-line interface (CLI). It
Using Cisco Unity Express Software Last Updated: May 1, 2006 This chapter provides helpful tips for understanding and configuring Cisco Unity Express software using the command-line interface (CLI). It
Upgrading the Cisco IOS XE Software
 Prerequisites for the Software Upgrade Process, page 1 Saving Backup Copies of Your Old System Image and Configuration, page 2 Using TFTP or Remote Copy Protocol to Copy the System Image into Boot Flash
Prerequisites for the Software Upgrade Process, page 1 Saving Backup Copies of Your Old System Image and Configuration, page 2 Using TFTP or Remote Copy Protocol to Copy the System Image into Boot Flash
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example
 ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
Configuration Replace and Configuration Rollback
 Configuration Replace and Configuration Rollback Prerequisites for Configuration Replace and Configuration Rollback, page 1 Restrictions for Configuration Replace and Configuration Rollback, page 2 Information
Configuration Replace and Configuration Rollback Prerequisites for Configuration Replace and Configuration Rollback, page 1 Restrictions for Configuration Replace and Configuration Rollback, page 2 Information
Configurations for the Layer 3 Switch Router
 CHAPTER 3 This chapter describes the initial configuration of the Layer 3 switch router and contains the following major sections: Starting Up the Layer 3 Switch Router, page 3-1 Using the Console and
CHAPTER 3 This chapter describes the initial configuration of the Layer 3 switch router and contains the following major sections: Starting Up the Layer 3 Switch Router, page 3-1 Using the Console and
Firmware Management. Overview of Firmware. This chapter includes the following sections:
 This chapter includes the following sections: Overview of Firmware, page 1 Options for Upgrading Firmware, page 2 Obtaining Software from Cisco Systems, page 2 Installing CIMC Firmware from a Remote Server,
This chapter includes the following sections: Overview of Firmware, page 1 Options for Upgrading Firmware, page 2 Obtaining Software from Cisco Systems, page 2 Installing CIMC Firmware from a Remote Server,
Upgrading the Server Software
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.5.0, page B-2 Obtaining
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.5.0, page B-2 Obtaining
Release Notes for the Cisco ASA Services Module, Version 8.5(x)
 Release s for the Cisco ASA Services Module, Version 8.5(x) Released: July 7, 2011 Updated: September 4, 2012 This document contains release information for the Cisco ASA Services Module (ASASM) Version
Release s for the Cisco ASA Services Module, Version 8.5(x) Released: July 7, 2011 Updated: September 4, 2012 This document contains release information for the Cisco ASA Services Module (ASASM) Version
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
 ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Background
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Background
Lab 6.2.7a Managing Switch Operating System Files
 Lab 6.2.7a Managing Switch Operating System Files Objective Create and verify a basic switch configuration. Backup the switch IOS to a TFTP server and then restore it. Background/Preparation Cable a network
Lab 6.2.7a Managing Switch Operating System Files Objective Create and verify a basic switch configuration. Backup the switch IOS to a TFTP server and then restore it. Background/Preparation Cable a network
Configuring the SMA 500v Virtual Appliance
 Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts.
 Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Transferring Files Using HTTP or HTTPS
 Cisco IOS Release 12.4 provides the ability to transfer files between your Cisco IOS software-based device and a remote HTTP server using the HTTP or HTTP Secure (HTTPS) protocol. HTTP and HTTPS can now
Cisco IOS Release 12.4 provides the ability to transfer files between your Cisco IOS software-based device and a remote HTTP server using the HTTP or HTTP Secure (HTTPS) protocol. HTTP and HTTPS can now
Configuring Administrative Operations
 This section includes the following topics: Administrative Operation Conventions, page 1 Managing Backup Operations, page 1 Restoring a Backup Configuration, page 6 Managing Export Operations, page 10
This section includes the following topics: Administrative Operation Conventions, page 1 Managing Backup Operations, page 1 Restoring a Backup Configuration, page 6 Managing Export Operations, page 10
MOP for upgrading StoneOS
 MOP for upgrading StoneOS Make a backup of current configurations A. WebUI: Refer to the image below, click tab System menu Configuration File Management, check the box before the Startup configuration
MOP for upgrading StoneOS Make a backup of current configurations A. WebUI: Refer to the image below, click tab System menu Configuration File Management, check the box before the Startup configuration
Configuring the Cisco VPN 3000 Concentrator 4.7.x to Get a Digital Certificate and a SSL Certificate
 Configuring the Cisco VPN 3000 Concentrator 4.7.x to Get a Digital Certificate and a SSL Certificate Document ID: 4123 Contents Introduction Prerequisites Requirements Components Used Conventions Install
Configuring the Cisco VPN 3000 Concentrator 4.7.x to Get a Digital Certificate and a SSL Certificate Document ID: 4123 Contents Introduction Prerequisites Requirements Components Used Conventions Install
How to Configure ASA 5500-X Series Firewall to send logs to EventTracker. EventTracker
 How to Configure ASA 5500-X Series Firewall to send logs to EventTracker EventTracker Publication Date: September 14, 2018 Abstract This guide helps you in configuring ASA 5500-X Series Firewall to send
How to Configure ASA 5500-X Series Firewall to send logs to EventTracker EventTracker Publication Date: September 14, 2018 Abstract This guide helps you in configuring ASA 5500-X Series Firewall to send
Managing Controller Software and Configurations
 CHAPTER 8 Managing Controller Software and Configurations This chapter describes how to manage configurations and software versions on the controllers. This chapter contains these sections: Transferring
CHAPTER 8 Managing Controller Software and Configurations This chapter describes how to manage configurations and software versions on the controllers. This chapter contains these sections: Transferring
Working with Cisco IOS XE Software Bundles
 About Software Bundles and Packages, page 1 Bundle and Package File Location on the Switch, page 1 Upgrading Cisco IOS XE Software, page 2 Additional References, page 10 About Software Bundles and Packages
About Software Bundles and Packages, page 1 Bundle and Package File Location on the Switch, page 1 Upgrading Cisco IOS XE Software, page 2 Additional References, page 10 About Software Bundles and Packages
Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on a router.
 Lab 5.2.5 Managing IOS Images with TFTP Objective Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on a router. Background/Preparation
Lab 5.2.5 Managing IOS Images with TFTP Objective Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on a router. Background/Preparation
Performing Software Maintenance Upgrades (SMUs)
 Performing Software Maintenance Upgrades (SMUs) This chapter describes how to perform software maintenance upgrades (SMUs) on Cisco Nexus 3000 Series switches. This chapter includes the following sections:
Performing Software Maintenance Upgrades (SMUs) This chapter describes how to perform software maintenance upgrades (SMUs) on Cisco Nexus 3000 Series switches. This chapter includes the following sections:
Configuring Administrative Operations
 Configuring Administrative Operations This section includes the following topics: Administrative Operation Conventions, page 1 Configuring Backup Operations, page 1 Restoring a Backup Configuration, page
Configuring Administrative Operations This section includes the following topics: Administrative Operation Conventions, page 1 Configuring Backup Operations, page 1 Restoring a Backup Configuration, page
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example
 ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
Sybex CCENT Chapter 8: Cisco IOS. Instructor & Todd Lammle
 Sybex CCENT Chapter 8: Cisco IOS Instructor & Todd Lammle Chapter 8 Objectives The ICND1 Topics Covered in this chapter include: 5.0 Infrastructure Management 5.2 Configure and verify device management.
Sybex CCENT Chapter 8: Cisco IOS Instructor & Todd Lammle Chapter 8 Objectives The ICND1 Topics Covered in this chapter include: 5.0 Infrastructure Management 5.2 Configure and verify device management.
Troubleshooting. Testing Your Configuration CHAPTER
 82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
Initial Configuration on ML-Series Card
 CHAPTER 3 This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
CHAPTER 3 This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
Catalyst 6500 FWSM Replacement of Failover Unit after a Hardware Failure
 Catalyst 6500 FWSM Replacement of Failover Unit after a Hardware Failure Document ID: 65604 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Upgrade the FWSM Code Enable
Catalyst 6500 FWSM Replacement of Failover Unit after a Hardware Failure Document ID: 65604 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Upgrade the FWSM Code Enable
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Maintaining Your WAAS System
 14 CHAPTER This chapter describes the tasks you may need to perform to maintain your WAAS system. Throughout this chapter, the term WAAS device is used to refer collectively to the WAAS Central Managers
14 CHAPTER This chapter describes the tasks you may need to perform to maintain your WAAS system. Throughout this chapter, the term WAAS device is used to refer collectively to the WAAS Central Managers
Table of Contents. 1 TFTP Configuration Commands 1-1 TFTP Client Configuration Commands 1-1 tftp-server acl 1-1 tftp 1-2 tftp ipv6 1-3
 Table of Contents 1 TFTP Configuration Commands 1-1 TFTP Client Configuration Commands 1-1 tftp-server acl 1-1 tftp 1-2 tftp ipv6 1-3 i 1 TFTP Configuration Commands TFTP Client Configuration Commands
Table of Contents 1 TFTP Configuration Commands 1-1 TFTP Client Configuration Commands 1-1 tftp-server acl 1-1 tftp 1-2 tftp ipv6 1-3 i 1 TFTP Configuration Commands TFTP Client Configuration Commands
Cisco RF Switch Firmware Command Reference Guide
 Cisco RF Switch Firmware Command Reference Guide March 31, 2011 Cisco RF Switch Firmware Version 4.0 OL-15733-03 This document describes the cable-specific RF Switch Firmware and supporting command-line
Cisco RF Switch Firmware Command Reference Guide March 31, 2011 Cisco RF Switch Firmware Version 4.0 OL-15733-03 This document describes the cable-specific RF Switch Firmware and supporting command-line
Symptom Condition / Workaround Issue Full domain name is not resolved by the RDP- ActiveX Client.
 Secure Remote Access Contents Platform Compatibility...1 Known Issues...1 Resolved Issues...3 Upgrading SonicOS SSL VPN Firmware Procedures...4 Related Technical Documentation...6 Platform Compatibility
Secure Remote Access Contents Platform Compatibility...1 Known Issues...1 Resolved Issues...3 Upgrading SonicOS SSL VPN Firmware Procedures...4 Related Technical Documentation...6 Platform Compatibility
Managing ACE Software Licenses
 CHAPTER 4 Note The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. This chapter describes how to manage the software licenses for your ACE. It contains
CHAPTER 4 Note The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. This chapter describes how to manage the software licenses for your ACE. It contains
Configuring Virtual Blades
 CHAPTER 14 This chapter describes how to configure virtual blades, which are computer emulators that reside in a WAE or WAVE device. A virtual blade allows you to allocate WAE system resources for use
CHAPTER 14 This chapter describes how to configure virtual blades, which are computer emulators that reside in a WAE or WAVE device. A virtual blade allows you to allocate WAE system resources for use
Lab Managing IOS Images with TFTP Instructor Version 2500
 Lab 5.2.5 Managing IOS Images with TFTP Instructor Version 2500 Objective Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on
Lab 5.2.5 Managing IOS Images with TFTP Instructor Version 2500 Objective Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on
Configuration Replace and Configuration Rollback
 Configuration Replace and Configuration Rollback The Configuration Replace and Configuration Rollback feature provides the capability to replace the current running configuration with any saved Cisco IOS
Configuration Replace and Configuration Rollback The Configuration Replace and Configuration Rollback feature provides the capability to replace the current running configuration with any saved Cisco IOS
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Lab Using the Boot System Command. Objective. Background/Preparation
 Lab 5.1.3 Using the Boot System Command Objective Display information about the Cisco IOS Image (software) that is currently running. Determine where the IOS is booting from. Check the amount of RAM, Flash
Lab 5.1.3 Using the Boot System Command Objective Display information about the Cisco IOS Image (software) that is currently running. Determine where the IOS is booting from. Check the amount of RAM, Flash
ASA 8.x/ASDM 6.x: Add New VPN Peer Information in an Existing Site-to-Site VPN using ASDM
 ASA 8.x/ASDM 6.x: Add New VPN Peer Information in an Existing Site-to-Site VPN using ASDM Contents Introduction Prerequisites Requirements Components Used Conventions Backround information ASDM Configuration
ASA 8.x/ASDM 6.x: Add New VPN Peer Information in an Existing Site-to-Site VPN using ASDM Contents Introduction Prerequisites Requirements Components Used Conventions Backround information ASDM Configuration
LifeSize Gatekeeper Installation Guide
 LifeSize Gatekeeper Installation Guide July 2008 Copyright Notice 2008 LifeSize Communications Inc, and its licensors. All rights reserved. LifeSize Communications has made every effort to ensure that
LifeSize Gatekeeper Installation Guide July 2008 Copyright Notice 2008 LifeSize Communications Inc, and its licensors. All rights reserved. LifeSize Communications has made every effort to ensure that
Using Cisco Unified SIP Proxy Software
 Using Cisco Unified SIP Proxy Software First Published: February 6, 2009 Last Updated: June 1, 2010 This chapter provides helpful tips for understanding and configuring Cisco Unified SIP Proxy software
Using Cisco Unified SIP Proxy Software First Published: February 6, 2009 Last Updated: June 1, 2010 This chapter provides helpful tips for understanding and configuring Cisco Unified SIP Proxy software
Troubleshooting. Understanding POST Results CHAPTER
 CHAPTER 4 Troubleshooting This chapter provides the following information for troubleshooting problems. Understanding POST Results Recovering from Corrupted Software Recovering from a Lost or Forgotten
CHAPTER 4 Troubleshooting This chapter provides the following information for troubleshooting problems. Understanding POST Results Recovering from Corrupted Software Recovering from a Lost or Forgotten
Managing Software. Upgrading the Controller Software. Considerations for Upgrading Controller Software
 Upgrading the Controller Software, on page 1 Considerations for Upgrading Controller Software, on page 1 Upgrading Controller Software (GUI), on page 2 Upgrading Controller Software (CLI), on page 5 Predownloading
Upgrading the Controller Software, on page 1 Considerations for Upgrading Controller Software, on page 1 Upgrading Controller Software (GUI), on page 2 Upgrading Controller Software (CLI), on page 5 Predownloading
CIMC Firmware Management
 CIMC Firmware Management This chapter includes the following sections: Overview of Firmware, page 1 Obtaining Firmware from Cisco, page 2 Installing CIMC Firmware from a TFTP Server, page 3 Activating
CIMC Firmware Management This chapter includes the following sections: Overview of Firmware, page 1 Obtaining Firmware from Cisco, page 2 Installing CIMC Firmware from a TFTP Server, page 3 Activating
WLM1200-RMTS User s Guide
 WLM1200-RMTS User s Guide Copyright 2011, Juniper Networks, Inc. 1 WLM1200-RMTS User Guide Contents WLM1200-RMTS Publication Suite........................................ 2 WLM1200-RMTS Hardware Description....................................
WLM1200-RMTS User s Guide Copyright 2011, Juniper Networks, Inc. 1 WLM1200-RMTS User Guide Contents WLM1200-RMTS Publication Suite........................................ 2 WLM1200-RMTS Hardware Description....................................
Virtual Services Container
 Prerequisites for a, page 1 Information about, page 2 How to Configure a, page 2 Configuration Examples for Installation, page 10 Upgrading a, page 11 Additional References for the, page 11 Prerequisites
Prerequisites for a, page 1 Information about, page 2 How to Configure a, page 2 Configuration Examples for Installation, page 10 Upgrading a, page 11 Additional References for the, page 11 Prerequisites
FWSM: Multiple Context Configuration Example
 FWSM: Multiple Context Configuration Example Document ID: 107524 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported
FWSM: Multiple Context Configuration Example Document ID: 107524 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported
Cisco Firepower Troubleshoot File Generation Procedures
 Cisco Firepower Troubleshoot File Generation Procedures Contents Introduction Prerequisites Using the Web Interface of FMC Generate a Troubleshoot File Download a Troubleshoot File Using the Command Line
Cisco Firepower Troubleshoot File Generation Procedures Contents Introduction Prerequisites Using the Web Interface of FMC Generate a Troubleshoot File Download a Troubleshoot File Using the Command Line
Migration of Cisco Physical Access Manager to the Identiv Connected Physical Access Manager
 Migration of Cisco Physical Access Manager to the Identiv Connected Physical Access Manager The following upgrade path from Cisco Physical Access Manager (CPAM) to Identiv Connected Physical Access Manager
Migration of Cisco Physical Access Manager to the Identiv Connected Physical Access Manager The following upgrade path from Cisco Physical Access Manager (CPAM) to Identiv Connected Physical Access Manager
Lab 3: Basic Device Configuration
 Lab 3: Basic Device Configuration University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 2 Lab 3: Basic Device Configuration **Given
Lab 3: Basic Device Configuration University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 2 Lab 3: Basic Device Configuration **Given
Password Recovery Procedure for the Cisco 3600 and 3800 Series Routers
 Password Recovery Procedure for the Cisco 3600 and 3800 Series Routers Document ID: 22189 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Step by Step Procedure
Password Recovery Procedure for the Cisco 3600 and 3800 Series Routers Document ID: 22189 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Step by Step Procedure
Upgrade Guide for Cisco Digital Media System Release 5.0
 Upgrade Guide for Cisco Digital Media System Release 5.0 Revised: December 12, 2008, This guide provides information about and instructions for upgrading your Cisco DMS appliances and Cisco Digital Media
Upgrade Guide for Cisco Digital Media System Release 5.0 Revised: December 12, 2008, This guide provides information about and instructions for upgrading your Cisco DMS appliances and Cisco Digital Media
Using the TUI Upgrade Utility to Update an Existing Release 2.4 Server
 Using the TUI Upgrade Utility to Update an Existing Release 2.4 Server First Published: November 4, 2011 Revised: June 12, 2012 Do not use the information in this module to perform an upgrade from Cisco
Using the TUI Upgrade Utility to Update an Existing Release 2.4 Server First Published: November 4, 2011 Revised: June 12, 2012 Do not use the information in this module to perform an upgrade from Cisco
Managing Services Modules
 CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
Avaya Distributed Office Release 1.2.x Job Aid: Upgrading to Avaya Aura Communication Manager Branch 2.0
 Avaya Distributed Office Release 1.2.x Job Aid: Upgrading to Avaya Aura Communication Manager Branch 2.0 03-602863 May 2009 Issue 3 Introduction This Job Aid describes the upgrade procedure for Distributed
Avaya Distributed Office Release 1.2.x Job Aid: Upgrading to Avaya Aura Communication Manager Branch 2.0 03-602863 May 2009 Issue 3 Introduction This Job Aid describes the upgrade procedure for Distributed
Upgrading the Software
 APPENDIX B Upgrading the Software You can upgrade your software in the following ways: From the Cisco IOS command-line interface (CLI) From the ROM monitor Cisco recommends upgrading your software from
APPENDIX B Upgrading the Software You can upgrade your software in the following ways: From the Cisco IOS command-line interface (CLI) From the ROM monitor Cisco recommends upgrading your software from
The Lab. The lab (cont ) 5 (6) routers ETSF05 + ETSF The routing lab. Jens A Andersson. Many links (vlans) Front-end server
 ETSF05 + ETSF10 2011 The routing lab Jens A Andersson The Lab 2 The lab (cont ) 5 (6) routers Cisco 1841 IOS vers 15 Many links (vlans) Front-end server Access to router lab tftp and ftp server for the
ETSF05 + ETSF10 2011 The routing lab Jens A Andersson The Lab 2 The lab (cont ) 5 (6) routers Cisco 1841 IOS vers 15 Many links (vlans) Front-end server Access to router lab tftp and ftp server for the
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
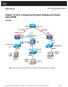 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example
 ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Nortel Network Resource Manager Fundamentals. Release: NRM 2.1 Document Revision: NN
 Release: NRM 21 Document Revision: 0301 wwwnortelcom NN48020-300 Release: NRM 21 Publication: NN48020-300 Document status: Standard Document release date: All Rights Reserved Printed in Canada, India,
Release: NRM 21 Document Revision: 0301 wwwnortelcom NN48020-300 Release: NRM 21 Publication: NN48020-300 Document status: Standard Document release date: All Rights Reserved Printed in Canada, India,
PXM45 Backup Boot Procedures
 APPENDIX B 2 When a PXM45 card starts up, it first loads the boot software on the card. If the PXM45 cannot load the runtime firmware, the card continues to run the boot software in what is called backup
APPENDIX B 2 When a PXM45 card starts up, it first loads the boot software on the card. If the PXM45 cannot load the runtime firmware, the card continues to run the boot software in what is called backup
User can upgrade the firmware directly using the Web or Console.
 17. Firmware Upgrade User can upgrade the firmware directly using the Web or Console. Firmware name (current) and applied model: V3K31257_en.all:Vigor 3300B+ 2.5.7 English version. V3K31257_cn.all:Vigor
17. Firmware Upgrade User can upgrade the firmware directly using the Web or Console. Firmware name (current) and applied model: V3K31257_en.all:Vigor 3300B+ 2.5.7 English version. V3K31257_cn.all:Vigor
Symptom Condition / Workaround Issue No validation is provided for name and IP address fields when creating bookmarks.
 Secure Remote Access Contents Platform Compatibility...1 Known Issues...1 Resolved Issues...2 Upgrading SonicOS SSL VPN Firmware Procedures...3 Related Technical Documentation...5 Platform Compatibility
Secure Remote Access Contents Platform Compatibility...1 Known Issues...1 Resolved Issues...2 Upgrading SonicOS SSL VPN Firmware Procedures...3 Related Technical Documentation...5 Platform Compatibility
Initial Configuration
 3 CHAPTER This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
3 CHAPTER This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
Software Images. About Software Images. Dependent Factors. Send documentation comments to CHAPTER
 CHAPTER 10 This chapter describes how to install and upgrade software images, and introduces the file system. It includes the following sections: About, page 10-1 Essential Upgrade Prerequisites, page
CHAPTER 10 This chapter describes how to install and upgrade software images, and introduces the file system. It includes the following sections: About, page 10-1 Essential Upgrade Prerequisites, page
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2
 Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
RAID Controller Firmware Upgrade Instructions for the Cisco WAVE-7541, 7571, and 8541
 RAID Controller Firmware Upgrade Instructions for the Cisco WAVE-7541, 7571, and 8541 March 1, 2012, This document describes how to upgrade the RAID controller firmware in Cisco Wide Area Virtualization
RAID Controller Firmware Upgrade Instructions for the Cisco WAVE-7541, 7571, and 8541 March 1, 2012, This document describes how to upgrade the RAID controller firmware in Cisco Wide Area Virtualization
About Backup and Restore, on page 1 Supported Backup and Restore Procedures, on page 3
 About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
Performing Software Maintenance Upgrades
 This chapter describes how to perform software maintenance upgrades (SMUs) on Cisco NX-OS devices. This chapter includes the following sections: About SMUs, page 1 Prerequisites for SMUs, page 3 Guidelines
This chapter describes how to perform software maintenance upgrades (SMUs) on Cisco NX-OS devices. This chapter includes the following sections: About SMUs, page 1 Prerequisites for SMUs, page 3 Guidelines
Consolidated Packages and SubPackages Management
 Consolidated Packages and SubPackages Management This chapter discusses how consolidated packages and software subpackages (individual and optional) are managed and are used to run the Cisco ASR 1000 Series
Consolidated Packages and SubPackages Management This chapter discusses how consolidated packages and software subpackages (individual and optional) are managed and are used to run the Cisco ASR 1000 Series
Before Contacting Technical Support
 APPENDIXA This appendix describes the steps to perform before calling for technical support for any Cisco MDS 9000 Family multilayer director and fabric switch. This appendix includes the following sections:
APPENDIXA This appendix describes the steps to perform before calling for technical support for any Cisco MDS 9000 Family multilayer director and fabric switch. This appendix includes the following sections:
Converting Autonomous Access Points to Lightweight Mode
 Converting Autonomous Access Points to Lightweight Mode Finding Feature Information, on page 1 Prerequisites for, on page 1 Information About Autonomous Access Points Converted to Lightweight Mode, on
Converting Autonomous Access Points to Lightweight Mode Finding Feature Information, on page 1 Prerequisites for, on page 1 Information About Autonomous Access Points Converted to Lightweight Mode, on
INDEX. Cisco Unity Express CLI Administrator Guide for Cisco CallManage, Release Cisco Unity Express Release 1.1
 INDEX A active calls backup 105 restore 107 administration CLI 28 differences 29 GU and CLI 39 GUI 27 administrative privileges 84 administrator Cisco CallManager 29 Cisco Unity Express 29 password 35
INDEX A active calls backup 105 restore 107 administration CLI 28 differences 29 GU and CLI 39 GUI 27 administrative privileges 84 administrator Cisco CallManager 29 Cisco Unity Express 29 password 35
Converting Autonomous Access Points to Lightweight Mode
 Converting Autonomous Access Points to Lightweight Mode Finding Feature Information, page 1 Prerequisites for Converting Autonomous Access Points to Lightweight Mode, page 1 Information About Autonomous
Converting Autonomous Access Points to Lightweight Mode Finding Feature Information, page 1 Prerequisites for Converting Autonomous Access Points to Lightweight Mode, page 1 Information About Autonomous
Troubleshooting the Security Appliance
 CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
Configuration Guide. Upgrading AOS Firmware L1-29.1D July 2011
 61200990L1-29.1D July 2011 Configuration Guide This configuration guide explains how to update your ADTRAN Operating System (AOS) firmware using the AOS Web-based graphical user interface (GUI) with Trivial
61200990L1-29.1D July 2011 Configuration Guide This configuration guide explains how to update your ADTRAN Operating System (AOS) firmware using the AOS Web-based graphical user interface (GUI) with Trivial
Configuration File Management Commands
 This chapter provides detailed descriptions of commands used to manage configuration files in Cisco IOS Release 12.2. Configuration files contain the set of commands used to customize the function of the
This chapter provides detailed descriptions of commands used to manage configuration files in Cisco IOS Release 12.2. Configuration files contain the set of commands used to customize the function of the
Release Notes. Dell SonicWALL SRA Release Notes
 Secure Remote Access Contents Release Purpose... 1 Platform Compatibility... 1 Licensing on the Dell SonicWALL SRA Appliances and Virtual Appliance... 1 Important Differences Between the SRA Appliances...
Secure Remote Access Contents Release Purpose... 1 Platform Compatibility... 1 Licensing on the Dell SonicWALL SRA Appliances and Virtual Appliance... 1 Important Differences Between the SRA Appliances...
Lab assignment #2 IPSec and VPN Tunnels
 University of Pittsburgh School of Information Science IS2820/TEL2813 - Security Management Lab assignment #2 IPSec and VPN Tunnels Lab GSA: Carlos Caicedo Page I. Lab resources for this assignment...
University of Pittsburgh School of Information Science IS2820/TEL2813 - Security Management Lab assignment #2 IPSec and VPN Tunnels Lab GSA: Carlos Caicedo Page I. Lab resources for this assignment...
No Service Password-Recovery
 No Service Password-Recovery Last Updated: January 18, 2012 The No Service Password-Recovery feature is a security enhancement that prevents anyone with console access from accessing the router configuration
No Service Password-Recovery Last Updated: January 18, 2012 The No Service Password-Recovery feature is a security enhancement that prevents anyone with console access from accessing the router configuration
Upgrade the ASA FirePOWER Module
 This document describes how to upgrade the ASA FirePOWER module using ASDM or the Firepower Management Center, depending on your management choice. Refer to Upgrade the ASA Appliance or ASAv to determine
This document describes how to upgrade the ASA FirePOWER module using ASDM or the Firepower Management Center, depending on your management choice. Refer to Upgrade the ASA Appliance or ASAv to determine
Replace Supervisor Module in Cisco Catalyst 6500 Virtual Switching System 1440
 Replace Supervisor Module in Cisco Catalyst 6500 Virtual Switching System 1440 Document ID: 109334 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
Replace Supervisor Module in Cisco Catalyst 6500 Virtual Switching System 1440 Document ID: 109334 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
Software and Configurations
 This chapter describes how to manage the Cisco ASA software and configurations. Upgrade the Software, page 1 Use the ROMMON to Load an Image, page 1 Upgrade the ROMMON Image (ASA 5506-X, 5508-X, and 5516-X),
This chapter describes how to manage the Cisco ASA software and configurations. Upgrade the Software, page 1 Use the ROMMON to Load an Image, page 1 Upgrade the ROMMON Image (ASA 5506-X, 5508-X, and 5516-X),
ACS Shell Command Authorization Sets on IOS and ASA/PIX/FWSM Configuration Example
 ACS Shell Command Authorization Sets on IOS and ASA/PIX/FWSM Configuration Example Document ID: 99361 Contents Introduction Prerequisites Requirements Components Used Conventions Command Authorization
ACS Shell Command Authorization Sets on IOS and ASA/PIX/FWSM Configuration Example Document ID: 99361 Contents Introduction Prerequisites Requirements Components Used Conventions Command Authorization
System Administration
 Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Performing Maintenance Operations
 This chapter describes how to back up and restore Cisco Mobility Services Engine (MSE) data and how to update the MSE software. It also describes other maintenance operations. Guidelines and Limitations,
This chapter describes how to back up and restore Cisco Mobility Services Engine (MSE) data and how to update the MSE software. It also describes other maintenance operations. Guidelines and Limitations,
Installation of Cisco Business Edition 6000H/M
 Installation Overview, page 1 Installation Task Flow of Cisco Business Edition 6000H/M, page 2 Installation Overview This chapter describes the tasks that you must perform to install software on your Business
Installation Overview, page 1 Installation Task Flow of Cisco Business Edition 6000H/M, page 2 Installation Overview This chapter describes the tasks that you must perform to install software on your Business
Deferred Deployments of Service Profile Updates
 Service Profile Deferred Deployments, page 1 Maintenance Policy, page 3 Pending Activities for Deferred Deployments, page 7 Service Profile Deferred Deployments Some modifications to a service profile
Service Profile Deferred Deployments, page 1 Maintenance Policy, page 3 Pending Activities for Deferred Deployments, page 7 Service Profile Deferred Deployments Some modifications to a service profile
Cisco CTL Client setup
 Cisco CTL Client setup This chapter provides information about Cisco CTL client setup. About Cisco CTL Client setup, page 2 Remove etoken Run Time Environment 3.00 for CTL Client 5.0 plug-in, page 2 Cisco
Cisco CTL Client setup This chapter provides information about Cisco CTL client setup. About Cisco CTL Client setup, page 2 Remove etoken Run Time Environment 3.00 for CTL Client 5.0 plug-in, page 2 Cisco
