A Model of Salient Region Detection
|
|
|
- Ira Wilkerson
- 5 years ago
- Views:
Transcription
1 5 Chapter 2 A Model of alient Region Detection 2.1 Introduction Attention as a selective gating mechanism is often compared to a spotlight (osner 1980; Treisman and Gelade 1980), enhancing visual processing in the attended ( illuminated ) region of a few degrees of visual angle (agi and Julesz 1986). In a modification to the spotlight metaphor, the size of the attended region can be adjusted depending on the task, making attention similar to a zoom lens (Eriksen and t. James 1986; hulman and Wilson 1987). Neither of these theories considers the shape and extent of the attended object for determining the attended area. This may seem natural, since commonly attention is believed to act before objects are recognized. However, experimental evidence suggests that attention can be tied to objects, object parts, or groups of objects (Duncan 1984; Roelfsema et al. 1998). How can we attend to objects before we recognize them? everal computational models of visual attention have been suggested. Tsotsos et al. (1995) use local winner-take-all networks and top-down mechanisms to selectively tune model neurons at the attended location. Deco and chürmann (2000) modulate the spatial resolution of the image based on a top-down attentional control signal. Itti et al. (1998) introduced a model for bottomup selective attention based on serially scanning a saliency map, which is computed from local feature contrasts, for salient locations in the order of decreasing saliency. resented with a manually preprocessed input image, their model replicates human viewing behavior for artificial and natural scenes. Making extensive use of feedback and long-range cortical connections, Hamker (2005b,a) models the interactions of several brain areas involved in processing visual attention, which enables him to fit both physiological and behavioral data in the literature. Closely following and extending Duncan s Integrated Competition Hypothesis (Duncan 1997), un and Fisher (2003) developed and implemented a common framework for object-based and location-based visual attention using groupings.
2 6 Attended location Input image Figure 2.1: (1998). Architecture of the model of saliency-based visual attention, adapted from Itti et al. However, none of these models provides a satisfactory solution to the problem of attending to objects even before they are recognized. To solve this chicken-and-egg problem in first approximation, we have developed a model for estimating the extent of salient objects in a bottom-up fashion solely based on low-level image features. In chapters 3, 5, and 6 we demonstrate the use of the model as an initial step for object detection. Our attention system is based on the Itti et al. (1998) implementation of the saliency-based model of bottom-up attention by Koch and Ullman (1985). For a color input image, the model computes a saliency map from maps for color, luminance, and orientation contrasts at different scales (figure 2.1). A winner-take-all (WTA) neural network scans the saliency map for the most salient location and returns the location s coordinates. Finally, inhibition of return (IOR) is applied to a disc-shaped region of fixed radius around the attended location in the saliency map, and further iterations of the WTA network lead to successive direction of attention to several locations in order of decreasing saliency. The model has been verified in human psychophysical experiments (eters et al. 2005; Itti 2005), and it has been applied to object recognition (Miau et al. 2001; Walther et al. 2002a, 2005a) and robot navigation (Chung et al. 2002). We briefly review the details of the model in section 2.2 in order to explain our extensions in the same formal framework. In section 2.3 we describe our method of selecting salient regions instead of just salient locations by using feedback connections in the existing processing hierarchy of the original saliency model.
3 2.2 aliency-based Bottom-up Attention 7 The input image I is sub-sampled into a dyadic Gaussian pyramid by convolution with a linearly separable Gaussian filter and decimation by a factor of two (see appendix A.1 for details). This process is repeated to obtain the next levels σ = [0,.., 8] of the pyramid (Burt and Adelson 1983). Resolution of level σ is 1/2 σ times the original image resolution, i.e., the 8 th level has a resolution of 1/256 th of the input image s I and (1/256) 2 of the total number of pixels. If r, g, and b are the red, green, and blue values of the color image, then the intensity map is computed as M I = r + g + b. (2.1) 3 This operation is repeated for each level of the input pyramid to obtain an intensity pyramid with levels M I (σ). Each level of the image pyramid is furthermore decomposed into maps for red-green (RG) and blue-yellow (BY ) opponencies: r g M RG = max (r, g, b) b min (r, g) M BY = max (r, g, b). (2.2a) (2.2b) To avoid large fluctuations of the color opponency values at low luminance, M RG and M BY are set to zero at locations with max(r, g, b) < 1/10, assuming a dynamic range of [0, 1]. Note that the definitions in eq. 2.2 deviate from the original model by Itti et al. (1998). For a discussion of the definition of color opponencies see appendix A.2. Local orientation maps M θ are obtained by applying steerable filters to the intensity pyramid levels M I (σ) (imoncelli and Freeman 1995; Manduchi et al. 1998). In subsection we show how lateral inhibition between units with different θ can aid in detecting faint elongated objects. Motion is another highly salient feature. In appendix A.3 we describe our implementation of a set of motion detectors for saliency due to motion. Center-surround receptive fields are simulated by across-scale subtraction between two maps at the center (c) and the surround (s) levels in these pyramids, yielding feature maps : F l,c,s = N ( M l (c) M l (s) ) l L = L I L C L O (2.3) with L I = {I}, L C = {RG, BY }, L O = {0, 45, 90, 135 }. (2.4) N ( ) is an iterative, nonlinear normalization operator, simulating local competition between neigh-
4 8 boring salient locations (Itti and Koch 2001b). Each iteration step consists of self-excitation and neighbor-induced inhibition, implemented by convolution with a difference of Gaussians filter, followed by rectification. For the simulations in this thesis, between one and five iterations are used. For more details see Itti (2000) and Itti and Koch (2001b). The feature maps are summed over the center-surround combinations using across-scale addition, and the sums are normalized again: F l = N ( 4 c+4 c=2 s=c+3 F l,c,s ) l L. (2.5) For the general features color and orientation, the contributions of the sub-features are summed and normalized once more to yield conspicuity maps. For intensity, the conspicuity map is the same as F I obtained in eq. 2.5: ( ) ( ) C I = F I, C C = N Fl, C O = N Fl. (2.6) l L C l L O All conspicuity maps are combined into one saliency map: = 1 C k. (2.7) 3 k {I,C,O} The locations in the saliency map compete for the highest saliency value by means of a winner-takeall (WTA) network of integrate-and-fire neurons. The parameters of the model neurons are chosen such that they are physiologically realistic, and such that the ensuing time course of the competition for saliency results in shifts of attention in approximately ms simulated time (aarinen and Julesz 1991). The winning location (x w, y w ) of this process is attended to, and the saliency map is inhibited within a given radius of (x w, y w ). Continuing WTA competition produces the second most salient location, which is attended to subsequently and then inhibited, thus allowing the model to simulate a scan path over the image in the order of decreasing saliency of the attended locations. In the next section we demonstrate a mechanism for extracting an image region around the focus of attention (FOA) that corresponds to the approximate extent of an object at that location. Aside from its use to facilitate further visual processing of the attended object, this enables object-based inhibition of return (IOR), thereby eliminating the need for a fixed-radius disc as an IOR template.
5 9 Multiscale Feature Extraction of Colors (RG and BY), Intensities, and Orientations (4 orientations) Input image Center-surround differences and spatial competition Color Feature Maps BY Intensity Feature Maps Orientation Feature Maps 0 o 45 o Winning Feature Map RG 90 o 135 o argmax After egmentation Color Conspicuity Map Intensity Conspicuity Map Orientation Conspicuity Map argmax Feature Combination caled-up and smoothed Contrast-modulated image Inhibition of return Winnertake-all aliency Map Computation of saliency Region selection Compared locations Across-scale addition Figure 2.2: Illustration of the processing steps for obtaining the attended region. The input image is processed for low-level features at multiple scales, and center-surround differences are computed (eq. 2.3). The resulting feature maps are combined into conspicuity maps (eq. 2.6) and, finally, into a saliency map (eq. 2.7). A winner-take-all neural network determines the most salient location, which is then traced back through the various maps to identify the feature map that contributes most to the saliency of that location (eqs. 2.8 and 2.9). After segmentation around the most salient location (eqs and 2.11), this winning feature map is used for obtaining a smooth object mask at image resolution and for object-based inhibition of return.
6 Attending roto-object Regions While Itti et al. s model successfully identifies the most salient location in the image, it has no notion of the extent of the attended object or object part at this location. We introduce a method of estimating this region based on the maps and salient locations computed so far, using feedback connections in the saliency computation hierarchy (figure 2.2). Looking back at the conspicuity maps, we find the one map that contributes the most to the activity at the most salient location: k w = argmax C k (x w, y w ). (2.8) k {I,C,O} The argmax function, which is critical to this step, could be implemented in a neural network of linear threshold units (LTUs), as shown in figure 2.3. efficient generic argmax function because of its higher efficiency. For practical applications we use a more Examining the feature maps that gave rise to the conspicuity map C kw, we find the one that contributes most to its activity at the winning location: (l w, c w, s w ) = argmax F l,c,s (x w, y w ), (2.9) l L kw,c {2,3,4},s {c+3,c+4} with L kw as defined in eqs The winning feature map F lw,c w,s w (figure 2.2) is segmented around (x w, y w ). For this operation, a binary version of the map (B) is obtained by thesholding F lw,c w,s w with 1/10 of its value at the attended location: 1 if F lw,c w,s w (x, y) 0.1 F lw,c w,s w (x w, y w ) B(x, y) =. (2.10) 0 otherwise The 4-connected neighborhood of active pixels in B is used as the template to estimate the spatial extent of the attended object: ˆF w = label (B, (x w, y w )). (2.11) For the label function, we use the classical algorithm by Rosenfeld and faltz (1966) as implemented in the Matlab bwlabel function. After a first pass over the binary map for assigning temporary labels, the algorithm resolves equivalence classes and replaces the temporary labels with equivalence class labels in a second pass. In figure 2.4 we show an implementation of the segmentation operation with a network of LTUs to demonstrate feasibility of our procedure in a neural network. The segmented feature map ˆF w is used as a template to trigger object-based inhibition of return (IOR) in the WTA network and to deploy spatial attention to subsequent processing stages such as object detection. We have implemented our model of salient region selection as part of the aliencytoolbox for
7 11 patial WTA for saliency winner selection feed-forward feed-back local processing inhibitory synapse excitatory synapse b M f M aliency map b Col c Col f Col b Int c Int f Int b Ori c Ori f Ori Conspicuity maps inhibitory interneurons Color FMs Intensity FMs Orientation FMs Feature maps Figure 2.3: A network of linear threshold units (LTUs) for computing the argmax function in eq. 2.8 for one image location. Feed-forward (blue) units f Col, f Int, and f Ori compute conspicuity maps for color, intensity, and orientation by pooling activity from the respective sets of feature maps as described in eqs. 2.5 and 2.6, omitting the normalization step N here for clarity. The saliency map is computed in a similar fashion in f M (eq. 2.7), and f M participates in the spatial WTA competition for the most salient location. The feed-back (red) unit b M receives a signal from the WTA only when this location is attended to, and it relays the signal to the b units in the conspicuity maps. Competition units (c) together with a pool of inhibitory interneurons (black) form an across-feature WTA network with input from the f units of the respective conspicuity maps. Only the most active c unit will remain active due to WTA dynamics, allowing it to unblock the respective b unit. As a result, the activity pattern of the b units represents the result of the argmax function in eq This signal is relayed further to the constituent feature maps, where a similar network selects the feature map with the largest contribution to the saliency of this location (eq. 2.9).
8 12 inhibitory synapse excitatory synapse out select map input Figure 2.4: An LTU network implementation of the segmentation operation in eqs and Each pixel consists of two excitatory neurons and an inhibitory interneuron. The thresholding operation in eq is performed by the inhibitory interneuron, which only unblocks the segmentation unit if input from the winning feature map F lw,c w,s w (blue) exceeds its firing threshold. can be excited by a select signal (red) or by input from the pooling unit. Originating from the feedback units b in figure 2.3, the select signal is only active at the winning location (x w, y w ). ooling the signals from the unit in its 4-connected neighborhood, excites its own unit when it receives at least one input. Correspondingly, the unit projects to the units of the pixels in the 4-connected neighborhood. In their combination, the reciprocal connections between the and units form a localized implementation of the labeling algorithm (Rosenfeld and faltz 1966). preading of activation to adjacent pixels stops where the inbound map activity is not large enough to unblock the unit. The activity pattern of the units (green) represents the segmented feature map ˆF w. Matlab, described in appendix B, and as part of the ilab Neuromorphic Vision (invt) C++ toolkit. In the Matlab toolbox we provide both versions of the segmentation operation, the fast image processing implementation, and the LTU network version. They are functionally equivalent, but the LTU network simulation runs much slower than the fast image processing version. Figure 2.5 shows examples of applying region selection to three natural images as well as an artificial display of bent paper clips as used for the simulations in chapter 3. These examples and the results in chapters 3 and 5 were obtained using invt toolkit; for chapter 6 we used a modified version that was derived from the invt toolkit; and for chapter 4 we used the aliencytoolbox. 2.4 Discussion As part of their selective tuning model of visual attention, Tsotsos et al. (1995) introduced a mechanism for tracing back activations through a hierarchical network of WTA circuits to identify contiguous image regions with similarly high saliency values within a given feature domain. Our method is
9 13 Figure 2.5: Four examples for salient region extraction as described in section 2.3. For each example the following steps are shown (from left to right): the original image I; the saliency map ; the original image contrast-modulated with a cumulative superposition of F w for the locations attended to during the first 700 ms of simulated time of the WTA network, with the scan path overlayed; and the inverse of this cumulative mask, covering all salient parts of the image. It is apparent from this figure that our salient region extraction approach does indeed cover the salient parts of the images, leaving the non-salient parts unattended. similar in spirit but extends across feature domains. By tracing back the activity from the attended location in the saliency map through the hierarchy of conspicuity and feature maps, we identify the feature that contributes most to the activity of the currently fixated location. We identify a contiguous region around this location with high activity in the feature map that codes for this most active feature. This procedure is motivated by the observation that between-object variability of visual information is significantly higher than within-object variability (Ruderman 1997). Hence, even if two salient objects are close to each other or occluding each other, it is not very likely that they are salient for the same reason. This means that they can be distinguished in the feature maps that code for their respective most active features. Note, however, that attended regions may not necessarily have a one-to-one correspondence to objects. Groups of similar objects, e.g., a bowl of fruits, may be segmented as one region, as may object parts that are dissimilar from the rest of the object, e.g., a skin-colored hand appearing to terminate at a dark shirt sleeve. We call these regions proto-objects because they can lead
10 14 to the detection of the actual objects in further iterative interactions between the attention and recognition systems. ee the work by Rybak et al. (1998), for instance, for a model that uses the vector of saccades to code for the spatial relations between object parts. The additional computational cost for region selection is minimal because the feature and conspicuity maps have already been computed during the processing for saliency. Note that although ultimately only the winning feature map is used to segment the attended image region, the interaction of WTA and IOR operating on the saliency map provides the mechanism for sequentially attending several salient locations. There is no guarantee that the region selection algorithm will find objects. It is purely bottomup, stimulus driven and has no prior notion of what constitutes an object. Also note that we are not attempting an exhaustive segmentation of the image, such as done by hi and Malik (2000) or Martin et al. (2004). Our algorithm provides us with a first rough guess of the extent of a salient region. As we will see in the remainder of this thesis, in particular in chapter 5, it works well for localizing objects in cluttered environments. In some respects, our method of extracting the approximate extent of an object bridges spatial attention with object-based attention. Egly et al. (1994), for instance, report spreading of attention over an object. In their experiments, subjects detected invalidly cued targets faster if they appeared on the same object than if they appeared on a different object than the cue, although the distance between cue and target was the same in both cases. In our method, attention spreads over the extent of a proto-object as well, guided by the feature with the largest contribution to saliency at the attended location. Finding this most active feature is somewhat similar to the idea of flipping through an object file, a metaphor for a collection of properties that comprise an object (Kahneman and Treisman 1984). However, while Kahneman and Treisman (1984) consider spatial location of an object as another entry in the object file, in our implementation spatial location has a central role as an index for binding together the features belonging to a proto-object. Our method should be seen as an initial step toward a location invariant object representation, providing initial detection of proto-object that allow for subsequent tracking or recognition operations. In fact, in chapter 6, we demonstrate the suitability of our approach as a detection step for multi-target tracking in a machine vision application. 2.5 Outlook In this chapter we have introduced our model of bottom-up salient region selection based on the model of saliency-based bottom-up attention by Itti et al. (1998). The attended region, which is given by the segmented feature map ˆF w from eq. 2.11, serves as a means of deploying selective visual attention for:
11 15 (i) modulation of neural activity at specific levels of the visual processing hierarchy (chapter 3); (ii) preferential processing of image regions for learning and recognizing objects (chapter 5); (iii) initiating object tracking and simplifying the assignment problem in multi-target tracking (chapter 6).
12 16
Selective visual attention enables learning and recognition of multiple objects in cluttered scenes
 Selective visual attention enables learning and recognition of multiple objects in cluttered scenes Dirk Walther, 1 Ueli Rutishauser, 1 Christof Koch, and Pietro Perona Computation and Neural Systems,
Selective visual attention enables learning and recognition of multiple objects in cluttered scenes Dirk Walther, 1 Ueli Rutishauser, 1 Christof Koch, and Pietro Perona Computation and Neural Systems,
A Model of Dynamic Visual Attention for Object Tracking in Natural Image Sequences
 Published in Computational Methods in Neural Modeling. (In: Lecture Notes in Computer Science) 2686, vol. 1, 702-709, 2003 which should be used for any reference to this work 1 A Model of Dynamic Visual
Published in Computational Methods in Neural Modeling. (In: Lecture Notes in Computer Science) 2686, vol. 1, 702-709, 2003 which should be used for any reference to this work 1 A Model of Dynamic Visual
Modeling Attention to Salient Proto-objects
 Modeling Attention to Salient Proto-objects Dirk Bernhardt-Walther Collaborators: Laurent Itti Christof Koch Pietro Perona Tommy Poggio Maximilian Riesenhuber Ueli Rutishauser Beckman Institute, University
Modeling Attention to Salient Proto-objects Dirk Bernhardt-Walther Collaborators: Laurent Itti Christof Koch Pietro Perona Tommy Poggio Maximilian Riesenhuber Ueli Rutishauser Beckman Institute, University
CMPUT 616 Implementation of a Visual Attention Model
 CMPUT 616 Implementation of a Visual Attention Model Nathan Funk April 14, 2004 1 Introduction This project implements the visual attention model described by Itti, Koch and Niebur in their 1998 paper
CMPUT 616 Implementation of a Visual Attention Model Nathan Funk April 14, 2004 1 Introduction This project implements the visual attention model described by Itti, Koch and Niebur in their 1998 paper
Dynamic visual attention: competitive versus motion priority scheme
 Dynamic visual attention: competitive versus motion priority scheme Bur A. 1, Wurtz P. 2, Müri R.M. 2 and Hügli H. 1 1 Institute of Microtechnology, University of Neuchâtel, Neuchâtel, Switzerland 2 Perception
Dynamic visual attention: competitive versus motion priority scheme Bur A. 1, Wurtz P. 2, Müri R.M. 2 and Hügli H. 1 1 Institute of Microtechnology, University of Neuchâtel, Neuchâtel, Switzerland 2 Perception
A Modified Approach to Biologically Motivated Saliency Mapping
 A Modified Approach to Biologically Motivated Saliency Mapping Shane Grant Department of Computer Science University of California, San Diego La Jolla, CA 9093 wgrant@ucsd.edu Kevin A Heins Department
A Modified Approach to Biologically Motivated Saliency Mapping Shane Grant Department of Computer Science University of California, San Diego La Jolla, CA 9093 wgrant@ucsd.edu Kevin A Heins Department
Selective visual attention enables learning and recognition of multiple objects in cluttered scenes
 Computer Vision and Image Understanding 100 (2005) 41 63 www.elsevier.com/locate/cviu Selective visual attention enables learning and recognition of multiple objects in cluttered scenes Dirk Walther a,
Computer Vision and Image Understanding 100 (2005) 41 63 www.elsevier.com/locate/cviu Selective visual attention enables learning and recognition of multiple objects in cluttered scenes Dirk Walther a,
The Use of Attention and Spatial Information for Rapid Facial Recognition in Video
 * Manuscript The Use of Attention and Spatial Information for Rapid Facial Recognition in Video J. Bonaiuto & L. Itti Neuroscience Department University of Southern California Los Angeles, CA, 90089 Abstract
* Manuscript The Use of Attention and Spatial Information for Rapid Facial Recognition in Video J. Bonaiuto & L. Itti Neuroscience Department University of Southern California Los Angeles, CA, 90089 Abstract
Evaluation of regions-of-interest based attention algorithms using a probabilistic measure
 Evaluation of regions-of-interest based attention algorithms using a probabilistic measure Martin Clauss, Pierre Bayerl and Heiko Neumann University of Ulm, Dept. of Neural Information Processing, 89081
Evaluation of regions-of-interest based attention algorithms using a probabilistic measure Martin Clauss, Pierre Bayerl and Heiko Neumann University of Ulm, Dept. of Neural Information Processing, 89081
Neurally Inspired Mechanisms for the Dynamic Visual Attention Map Generation Task
 Neurally Inspired Mechanisms for the Dynamic Visual Attention Map Generation Task Maria T. López 1, Miguel A. Fernández 1, Antonio Fernández-Caballero 1, and Ana E. Delgado 2 1 Departamento de Informática
Neurally Inspired Mechanisms for the Dynamic Visual Attention Map Generation Task Maria T. López 1, Miguel A. Fernández 1, Antonio Fernández-Caballero 1, and Ana E. Delgado 2 1 Departamento de Informática
Is bottom-up attention useful for object recognition?
 Is bottom-up attention useful for object recognition? Ueli Rutishauser Λ, Dirk Walther Λ, Christof Koch, and Pietro Perona Computation and Neural Systems, California Institute of Technology, Pasadena,
Is bottom-up attention useful for object recognition? Ueli Rutishauser Λ, Dirk Walther Λ, Christof Koch, and Pietro Perona Computation and Neural Systems, California Institute of Technology, Pasadena,
A SYNOPTIC ACCOUNT FOR TEXTURE SEGMENTATION: FROM EDGE- TO REGION-BASED MECHANISMS
 A SYNOPTIC ACCOUNT FOR TEXTURE SEGMENTATION: FROM EDGE- TO REGION-BASED MECHANISMS Enrico Giora and Clara Casco Department of General Psychology, University of Padua, Italy Abstract Edge-based energy models
A SYNOPTIC ACCOUNT FOR TEXTURE SEGMENTATION: FROM EDGE- TO REGION-BASED MECHANISMS Enrico Giora and Clara Casco Department of General Psychology, University of Padua, Italy Abstract Edge-based energy models
An Object-based Visual Attention Model for Robots
 An Object-based Visual Attention Model for Robots Yuanlong Yu, George K. I. Mann, and Raymond G. Gosine Faculty of Engineering Memorial University of Newfoundland St. John s, Newfoundland, A1B 3X5, Canada
An Object-based Visual Attention Model for Robots Yuanlong Yu, George K. I. Mann, and Raymond G. Gosine Faculty of Engineering Memorial University of Newfoundland St. John s, Newfoundland, A1B 3X5, Canada
A Novel Approach for Saliency Detection based on Multiscale Phase Spectrum
 A Novel Approach for Saliency Detection based on Multiscale Phase Spectrum Deepak Singh Department of Electronics & Communication National Institute of Technology Rourkela 769008, Odisha, India Email:
A Novel Approach for Saliency Detection based on Multiscale Phase Spectrum Deepak Singh Department of Electronics & Communication National Institute of Technology Rourkela 769008, Odisha, India Email:
Confidence Based updation of Motion Conspicuity in Dynamic Scenes
 Confidence Based updation of Motion Conspicuity in Dynamic Scenes Vivek Kumar Singh, Subhransu Maji and Amitabha Mukerjee, Dept of Computer Science and Engineering, Indian Institute of Technology Kanpur,
Confidence Based updation of Motion Conspicuity in Dynamic Scenes Vivek Kumar Singh, Subhransu Maji and Amitabha Mukerjee, Dept of Computer Science and Engineering, Indian Institute of Technology Kanpur,
Object-Based Saliency Maps Harry Marr Computing BSc 2009/2010
 Object-Based Saliency Maps Harry Marr Computing BSc 2009/2010 The candidate confirms that the work submitted is their own and the appropriate credit has been given where reference has been made to the
Object-Based Saliency Maps Harry Marr Computing BSc 2009/2010 The candidate confirms that the work submitted is their own and the appropriate credit has been given where reference has been made to the
A SPATIOTEMPORAL SALIENCY MODEL OF VISUAL ATTENTION BASED ON MAXIMUM ENTROPY
 A SPATIOTEMPORAL SALIENCY MODEL OF VISUAL ATTENTION BASED ON MAXIMUM ENTROPY Longsheng Wei, Nong Sang and Yuehuan Wang Institute for Pattern Recognition and Artificial Intelligence National Key Laboratory
A SPATIOTEMPORAL SALIENCY MODEL OF VISUAL ATTENTION BASED ON MAXIMUM ENTROPY Longsheng Wei, Nong Sang and Yuehuan Wang Institute for Pattern Recognition and Artificial Intelligence National Key Laboratory
APPENDIX A THE NEURO BIOLOGY OF VISION AND ATTENTION
 APPENDIX A THE NEURO BIOLOGY OF VISION AND ATTENTION A.1 Introduction To understand the concept to human attention, it is worth to regard the processing involved in human visual system as discussed in
APPENDIX A THE NEURO BIOLOGY OF VISION AND ATTENTION A.1 Introduction To understand the concept to human attention, it is worth to regard the processing involved in human visual system as discussed in
Spatio-temporal Saliency Detection Using Phase Spectrum of Quaternion Fourier Transform
 Spatio-temporal Saliency Detection Using Phase Spectrum of Quaternion Fourier Transform Chenlei Guo, Qi Ma and Liming Zhang Department of Electronic Engineering, Fudan University No.220, Handan Road, Shanghai,
Spatio-temporal Saliency Detection Using Phase Spectrum of Quaternion Fourier Transform Chenlei Guo, Qi Ma and Liming Zhang Department of Electronic Engineering, Fudan University No.220, Handan Road, Shanghai,
A Hierarchical Visual Saliency Model for Character Detection in Natural Scenes
 A Hierarchical Visual Saliency Model for Character Detection in Natural Scenes Renwu Gao 1, Faisal Shafait 2, Seiichi Uchida 3, and Yaokai Feng 3 1 Information Sciene and Electrical Engineering, Kyushu
A Hierarchical Visual Saliency Model for Character Detection in Natural Scenes Renwu Gao 1, Faisal Shafait 2, Seiichi Uchida 3, and Yaokai Feng 3 1 Information Sciene and Electrical Engineering, Kyushu
AUTONOMOUS IMAGE EXTRACTION AND SEGMENTATION OF IMAGE USING UAV S
 AUTONOMOUS IMAGE EXTRACTION AND SEGMENTATION OF IMAGE USING UAV S Radha Krishna Rambola, Associate Professor, NMIMS University, India Akash Agrawal, Student at NMIMS University, India ABSTRACT Due to the
AUTONOMOUS IMAGE EXTRACTION AND SEGMENTATION OF IMAGE USING UAV S Radha Krishna Rambola, Associate Professor, NMIMS University, India Akash Agrawal, Student at NMIMS University, India ABSTRACT Due to the
Detecting Salient Contours Using Orientation Energy Distribution. Part I: Thresholding Based on. Response Distribution
 Detecting Salient Contours Using Orientation Energy Distribution The Problem: How Does the Visual System Detect Salient Contours? CPSC 636 Slide12, Spring 212 Yoonsuck Choe Co-work with S. Sarma and H.-C.
Detecting Salient Contours Using Orientation Energy Distribution The Problem: How Does the Visual System Detect Salient Contours? CPSC 636 Slide12, Spring 212 Yoonsuck Choe Co-work with S. Sarma and H.-C.
A Visual Attention-based Approach for Automatic Landmark Selection and Recognition
 WAPCV 04, in Lecture Notes in Computer Science, Springer Verlag, LNCS 3368, pp. 183-195, 2005 A Visual Attention-based Approach for Automatic Landmark Selection and Recognition Nabil Ouerhani 1, Heinz
WAPCV 04, in Lecture Notes in Computer Science, Springer Verlag, LNCS 3368, pp. 183-195, 2005 A Visual Attention-based Approach for Automatic Landmark Selection and Recognition Nabil Ouerhani 1, Heinz
Image Similarity based on Animate Vision: Information-Path Matching
 Image Similarity based on Animate Vision: Information-Path Matching G. Boccignone Università di Salerno and INFM boccig@unisa.it A. Picariello Università di Napoli picus@unina.it V. Moscato Università
Image Similarity based on Animate Vision: Information-Path Matching G. Boccignone Università di Salerno and INFM boccig@unisa.it A. Picariello Università di Napoli picus@unina.it V. Moscato Università
Published in Pattern Recognition (In: Lecture Notes in Computer Science) 2449, , 2002 which should be used for any reference to this work
 Published in Pattern Recognition (In: Lecture Notes in Computer Science) 29, 282-289, 2002 which should be used for any reference to this work 1 A Real Time Implementation of the Saliency-Based Model of
Published in Pattern Recognition (In: Lecture Notes in Computer Science) 29, 282-289, 2002 which should be used for any reference to this work 1 A Real Time Implementation of the Saliency-Based Model of
Salient Region Detection and Segmentation
 Salient Region Detection and Segmentation Radhakrishna Achanta, Francisco Estrada, Patricia Wils, and Sabine Süsstrunk School of Computer and Communication Sciences (I&C), Ecole Polytechnique Fédérale
Salient Region Detection and Segmentation Radhakrishna Achanta, Francisco Estrada, Patricia Wils, and Sabine Süsstrunk School of Computer and Communication Sciences (I&C), Ecole Polytechnique Fédérale
Saliency Detection in Aerial Imagery
 Saliency Detection in Aerial Imagery using Multi-scale SLIC Segmentation Samir Sahli 1, Daniel A. Lavigne 2 and Yunlong Sheng 1 1- COPL, Image Science group, Laval University, Quebec, Canada 2- Defence
Saliency Detection in Aerial Imagery using Multi-scale SLIC Segmentation Samir Sahli 1, Daniel A. Lavigne 2 and Yunlong Sheng 1 1- COPL, Image Science group, Laval University, Quebec, Canada 2- Defence
CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS
 CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS This chapter presents a computational model for perceptual organization. A figure-ground segregation network is proposed based on a novel boundary
CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS This chapter presents a computational model for perceptual organization. A figure-ground segregation network is proposed based on a novel boundary
The Vehicle Logo Location System based on saliency model
 ISSN 746-7659, England, UK Journal of Information and Computing Science Vol. 0, No. 3, 205, pp. 73-77 The Vehicle Logo Location System based on saliency model Shangbing Gao,2, Liangliang Wang, Hongyang
ISSN 746-7659, England, UK Journal of Information and Computing Science Vol. 0, No. 3, 205, pp. 73-77 The Vehicle Logo Location System based on saliency model Shangbing Gao,2, Liangliang Wang, Hongyang
Computer security experts often tell us not to choose an easy to guess word as a password. For example, the user name or date of birth.
 Graphical Passwords: Computer security experts often tell us not to choose an easy to guess word as a password. For example, the user name or date of birth. The Graphical Passwords team have been working
Graphical Passwords: Computer security experts often tell us not to choose an easy to guess word as a password. For example, the user name or date of birth. The Graphical Passwords team have been working
Chapter 3 Image Registration. Chapter 3 Image Registration
 Chapter 3 Image Registration Distributed Algorithms for Introduction (1) Definition: Image Registration Input: 2 images of the same scene but taken from different perspectives Goal: Identify transformation
Chapter 3 Image Registration Distributed Algorithms for Introduction (1) Definition: Image Registration Input: 2 images of the same scene but taken from different perspectives Goal: Identify transformation
Analysis and Modeling of Fixation Point Selection for Visual Search in Cluttered Backgrounds
 Presented at Targets and Backgrounds VI, AeroSense, Orlando, FL, April 2000. Proceedings of SPIE, Vol. 4029 Analysis and Modeling of Fixation Point Selection for Visual Search in Cluttered Backgrounds
Presented at Targets and Backgrounds VI, AeroSense, Orlando, FL, April 2000. Proceedings of SPIE, Vol. 4029 Analysis and Modeling of Fixation Point Selection for Visual Search in Cluttered Backgrounds
The SIFT (Scale Invariant Feature
 The SIFT (Scale Invariant Feature Transform) Detector and Descriptor developed by David Lowe University of British Columbia Initial paper ICCV 1999 Newer journal paper IJCV 2004 Review: Matt Brown s Canonical
The SIFT (Scale Invariant Feature Transform) Detector and Descriptor developed by David Lowe University of British Columbia Initial paper ICCV 1999 Newer journal paper IJCV 2004 Review: Matt Brown s Canonical
Saliency Extraction for Gaze-Contingent Displays
 In: Workshop on Organic Computing, P. Dadam, M. Reichert (eds.), Proceedings of the 34th GI-Jahrestagung, Vol. 2, 646 650, Ulm, September 2004. Saliency Extraction for Gaze-Contingent Displays Martin Böhme,
In: Workshop on Organic Computing, P. Dadam, M. Reichert (eds.), Proceedings of the 34th GI-Jahrestagung, Vol. 2, 646 650, Ulm, September 2004. Saliency Extraction for Gaze-Contingent Displays Martin Böhme,
Saliency Maps of High Dynamic Range Images
 Saliency Maps of High Dynamic Range Images Roland Brémond and Josselin Petit and Jean-Philippe Tarel Universié Paris Est, LEPSiS, INRETS-LCPC {bremond,petit,tarel}@lcpc.fr Abstract. A number of computational
Saliency Maps of High Dynamic Range Images Roland Brémond and Josselin Petit and Jean-Philippe Tarel Universié Paris Est, LEPSiS, INRETS-LCPC {bremond,petit,tarel}@lcpc.fr Abstract. A number of computational
EE795: Computer Vision and Intelligent Systems
 EE795: Computer Vision and Intelligent Systems Spring 2012 TTh 17:30-18:45 WRI C225 Lecture 04 130131 http://www.ee.unlv.edu/~b1morris/ecg795/ 2 Outline Review Histogram Equalization Image Filtering Linear
EE795: Computer Vision and Intelligent Systems Spring 2012 TTh 17:30-18:45 WRI C225 Lecture 04 130131 http://www.ee.unlv.edu/~b1morris/ecg795/ 2 Outline Review Histogram Equalization Image Filtering Linear
Experimenting a Visual Attention Model in the Context of CBIR systems
 Experimenting a Visual Attention Model in the Context of CBIR systems Franco Alberto Cardillo, Giuseppe Amato, and Fabrizio Falchi Istituto di Scienza e Tecnologie dell Informazione Consiglio Nazionale
Experimenting a Visual Attention Model in the Context of CBIR systems Franco Alberto Cardillo, Giuseppe Amato, and Fabrizio Falchi Istituto di Scienza e Tecnologie dell Informazione Consiglio Nazionale
SUMMARY: DISTINCTIVE IMAGE FEATURES FROM SCALE- INVARIANT KEYPOINTS
 SUMMARY: DISTINCTIVE IMAGE FEATURES FROM SCALE- INVARIANT KEYPOINTS Cognitive Robotics Original: David G. Lowe, 004 Summary: Coen van Leeuwen, s1460919 Abstract: This article presents a method to extract
SUMMARY: DISTINCTIVE IMAGE FEATURES FROM SCALE- INVARIANT KEYPOINTS Cognitive Robotics Original: David G. Lowe, 004 Summary: Coen van Leeuwen, s1460919 Abstract: This article presents a method to extract
Sequential Maximum Entropy Coding as Efficient Indexing for Rapid Navigation through Large Image Repositories
 Sequential Maximum Entropy Coding as Efficient Indexing for Rapid Navigation through Large Image Repositories Guoping Qiu, Jeremy Morris and Xunli Fan School of Computer Science, The University of Nottingham
Sequential Maximum Entropy Coding as Efficient Indexing for Rapid Navigation through Large Image Repositories Guoping Qiu, Jeremy Morris and Xunli Fan School of Computer Science, The University of Nottingham
3D Object Recognition: A Model of View-Tuned Neurons
 3D Object Recognition: A Model of View-Tuned Neurons Emanuela Bricolo Tomaso Poggio Department of Brain and Cognitive Sciences Massachusetts Institute of Technology Cambridge, MA 02139 {emanuela,tp}gai.mit.edu
3D Object Recognition: A Model of View-Tuned Neurons Emanuela Bricolo Tomaso Poggio Department of Brain and Cognitive Sciences Massachusetts Institute of Technology Cambridge, MA 02139 {emanuela,tp}gai.mit.edu
A Real-time Visual Attention System Using Integral Images
 A Real-time Visual Attention System Using Integral Images Simone Frintrop 1, Maria Klodt 2, and Erich Rome 2 1 Institute of Computer Science III, Rheinische Friedrich-Wilhems-Universität, 53111 Bonn, Germany
A Real-time Visual Attention System Using Integral Images Simone Frintrop 1, Maria Klodt 2, and Erich Rome 2 1 Institute of Computer Science III, Rheinische Friedrich-Wilhems-Universität, 53111 Bonn, Germany
Computational Models of V1 cells. Gabor and CORF
 1 Computational Models of V1 cells Gabor and CORF George Azzopardi Nicolai Petkov 2 Primary visual cortex (striate cortex or V1) 3 Types of V1 Cells Hubel and Wiesel, Nobel Prize winners Three main types
1 Computational Models of V1 cells Gabor and CORF George Azzopardi Nicolai Petkov 2 Primary visual cortex (striate cortex or V1) 3 Types of V1 Cells Hubel and Wiesel, Nobel Prize winners Three main types
Improvement of optic flow estimation from an event-based sensor with recurrently connected processing layers
 Improvement of optic flow estimation from an event-based sensor with recurrently connected processing layers Vilim Štih 31st March 2014 1 Introduction The Dynamic Vision Sensor (DVS) is a visual sensor
Improvement of optic flow estimation from an event-based sensor with recurrently connected processing layers Vilim Štih 31st March 2014 1 Introduction The Dynamic Vision Sensor (DVS) is a visual sensor
Evaluation of Selective Attention under Similarity Transforms
 Evaluation of Selective Attention under Similarity Transforms Bruce A. Draper and Albert Lionelle Department of Computer Science Colorado State University Fort Collins, CO, 80523, U.S.A. draper,lionelle@cs.colostate.edu
Evaluation of Selective Attention under Similarity Transforms Bruce A. Draper and Albert Lionelle Department of Computer Science Colorado State University Fort Collins, CO, 80523, U.S.A. draper,lionelle@cs.colostate.edu
Lecture 28 Intro to Tracking
 Lecture 28 Intro to Tracking Some overlap with T&V Section 8.4.2 and Appendix A.8 Recall: Blob Merge/Split merge occlusion occlusion split When two objects pass close to each other, they are detected as
Lecture 28 Intro to Tracking Some overlap with T&V Section 8.4.2 and Appendix A.8 Recall: Blob Merge/Split merge occlusion occlusion split When two objects pass close to each other, they are detected as
Asymmetry as a Measure of Visual Saliency
 Asymmetry as a Measure of Visual Saliency Ali Alsam, Puneet Sharma, and Anette Wrålsen Department of Informatics & e-learning (AITeL), Sør-Trøndelag University College (HiST), Trondheim, Norway er.puneetsharma@gmail.com
Asymmetry as a Measure of Visual Saliency Ali Alsam, Puneet Sharma, and Anette Wrålsen Department of Informatics & e-learning (AITeL), Sør-Trøndelag University College (HiST), Trondheim, Norway er.puneetsharma@gmail.com
Recall: Blob Merge/Split Lecture 28
 Recall: Blob Merge/Split Lecture 28 merge occlusion Intro to Tracking Some overlap with T&V Section 8.4.2 and Appendix A.8 occlusion split When two objects pass close to each other, they are detected as
Recall: Blob Merge/Split Lecture 28 merge occlusion Intro to Tracking Some overlap with T&V Section 8.4.2 and Appendix A.8 occlusion split When two objects pass close to each other, they are detected as
An Oscillatory Correlation Model of Object-based Attention
 Proceedings of International Joint Conference on Neural Networks, Atlanta, Georgia, USA, June 14-19, 2009 An Oscillatory Correlation Model of Object-based Attention Marcos G. Quiles, DeLiang Wang, Liang
Proceedings of International Joint Conference on Neural Networks, Atlanta, Georgia, USA, June 14-19, 2009 An Oscillatory Correlation Model of Object-based Attention Marcos G. Quiles, DeLiang Wang, Liang
Salient Region Detection using Weighted Feature Maps based on the Human Visual Attention Model
 Salient Region Detection using Weighted Feature Maps based on the Human Visual Attention Model Yiqun Hu 2, Xing Xie 1, Wei-Ying Ma 1, Liang-Tien Chia 2 and Deepu Rajan 2 1 Microsoft Research Asia 5/F Sigma
Salient Region Detection using Weighted Feature Maps based on the Human Visual Attention Model Yiqun Hu 2, Xing Xie 1, Wei-Ying Ma 1, Liang-Tien Chia 2 and Deepu Rajan 2 1 Microsoft Research Asia 5/F Sigma
CS 664 Segmentation. Daniel Huttenlocher
 CS 664 Segmentation Daniel Huttenlocher Grouping Perceptual Organization Structural relationships between tokens Parallelism, symmetry, alignment Similarity of token properties Often strong psychophysical
CS 664 Segmentation Daniel Huttenlocher Grouping Perceptual Organization Structural relationships between tokens Parallelism, symmetry, alignment Similarity of token properties Often strong psychophysical
Machine Learning 13. week
 Machine Learning 13. week Deep Learning Convolutional Neural Network Recurrent Neural Network 1 Why Deep Learning is so Popular? 1. Increase in the amount of data Thanks to the Internet, huge amount of
Machine Learning 13. week Deep Learning Convolutional Neural Network Recurrent Neural Network 1 Why Deep Learning is so Popular? 1. Increase in the amount of data Thanks to the Internet, huge amount of
CS231A Course Project Final Report Sign Language Recognition with Unsupervised Feature Learning
 CS231A Course Project Final Report Sign Language Recognition with Unsupervised Feature Learning Justin Chen Stanford University justinkchen@stanford.edu Abstract This paper focuses on experimenting with
CS231A Course Project Final Report Sign Language Recognition with Unsupervised Feature Learning Justin Chen Stanford University justinkchen@stanford.edu Abstract This paper focuses on experimenting with
Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science
 2D Gabor functions and filters for image processing and computer vision Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science 2 Most of the images in this presentation
2D Gabor functions and filters for image processing and computer vision Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science 2 Most of the images in this presentation
Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science
 V1-inspired orientation selective filters for image processing and computer vision Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science 2 Most of the images in this
V1-inspired orientation selective filters for image processing and computer vision Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science 2 Most of the images in this
TRANSPARENT OBJECT DETECTION USING REGIONS WITH CONVOLUTIONAL NEURAL NETWORK
 TRANSPARENT OBJECT DETECTION USING REGIONS WITH CONVOLUTIONAL NEURAL NETWORK 1 Po-Jen Lai ( 賴柏任 ), 2 Chiou-Shann Fuh ( 傅楸善 ) 1 Dept. of Electrical Engineering, National Taiwan University, Taiwan 2 Dept.
TRANSPARENT OBJECT DETECTION USING REGIONS WITH CONVOLUTIONAL NEURAL NETWORK 1 Po-Jen Lai ( 賴柏任 ), 2 Chiou-Shann Fuh ( 傅楸善 ) 1 Dept. of Electrical Engineering, National Taiwan University, Taiwan 2 Dept.
Predicting Visual Saliency of Building using Top down Approach
 Predicting Visual Saliency of Building using Top down Approach Sugam Anand,CSE Sampath Kumar,CSE Mentor : Dr. Amitabha Mukerjee Indian Institute of Technology, Kanpur Outline Motivation Previous Work Our
Predicting Visual Saliency of Building using Top down Approach Sugam Anand,CSE Sampath Kumar,CSE Mentor : Dr. Amitabha Mukerjee Indian Institute of Technology, Kanpur Outline Motivation Previous Work Our
A Keypoint Descriptor Inspired by Retinal Computation
 A Keypoint Descriptor Inspired by Retinal Computation Bongsoo Suh, Sungjoon Choi, Han Lee Stanford University {bssuh,sungjoonchoi,hanlee}@stanford.edu Abstract. The main goal of our project is to implement
A Keypoint Descriptor Inspired by Retinal Computation Bongsoo Suh, Sungjoon Choi, Han Lee Stanford University {bssuh,sungjoonchoi,hanlee}@stanford.edu Abstract. The main goal of our project is to implement
Introduction to visual computation and the primate visual system
 Introduction to visual computation and the primate visual system Problems in vision Basic facts about the visual system Mathematical models for early vision Marr s computational philosophy and proposal
Introduction to visual computation and the primate visual system Problems in vision Basic facts about the visual system Mathematical models for early vision Marr s computational philosophy and proposal
Satellite Image Processing with Biologically-Inspired Computational Methods and Visual Attention
 Satellite Image Processing with Biologically-Inspired Computational Methods and Visual Attention Md Ibne Sina Thesis submitted to the Faculty of Graduate and Postdoctoral Studies in partial fulfillment
Satellite Image Processing with Biologically-Inspired Computational Methods and Visual Attention Md Ibne Sina Thesis submitted to the Faculty of Graduate and Postdoctoral Studies in partial fulfillment
11/14/2010 Intelligent Systems and Soft Computing 1
 Lecture 8 Artificial neural networks: Unsupervised learning Introduction Hebbian learning Generalised Hebbian learning algorithm Competitive learning Self-organising computational map: Kohonen network
Lecture 8 Artificial neural networks: Unsupervised learning Introduction Hebbian learning Generalised Hebbian learning algorithm Competitive learning Self-organising computational map: Kohonen network
EECS150 - Digital Design Lecture 14 FIFO 2 and SIFT. Recap and Outline
 EECS150 - Digital Design Lecture 14 FIFO 2 and SIFT Oct. 15, 2013 Prof. Ronald Fearing Electrical Engineering and Computer Sciences University of California, Berkeley (slides courtesy of Prof. John Wawrzynek)
EECS150 - Digital Design Lecture 14 FIFO 2 and SIFT Oct. 15, 2013 Prof. Ronald Fearing Electrical Engineering and Computer Sciences University of California, Berkeley (slides courtesy of Prof. John Wawrzynek)
BSB663 Image Processing Pinar Duygulu. Slides are adapted from Selim Aksoy
 BSB663 Image Processing Pinar Duygulu Slides are adapted from Selim Aksoy Image matching Image matching is a fundamental aspect of many problems in computer vision. Object or scene recognition Solving
BSB663 Image Processing Pinar Duygulu Slides are adapted from Selim Aksoy Image matching Image matching is a fundamental aspect of many problems in computer vision. Object or scene recognition Solving
2. LITERATURE REVIEW
 2. LITERATURE REVIEW CBIR has come long way before 1990 and very little papers have been published at that time, however the number of papers published since 1997 is increasing. There are many CBIR algorithms
2. LITERATURE REVIEW CBIR has come long way before 1990 and very little papers have been published at that time, however the number of papers published since 1997 is increasing. There are many CBIR algorithms
EE368 Project Report CD Cover Recognition Using Modified SIFT Algorithm
 EE368 Project Report CD Cover Recognition Using Modified SIFT Algorithm Group 1: Mina A. Makar Stanford University mamakar@stanford.edu Abstract In this report, we investigate the application of the Scale-Invariant
EE368 Project Report CD Cover Recognition Using Modified SIFT Algorithm Group 1: Mina A. Makar Stanford University mamakar@stanford.edu Abstract In this report, we investigate the application of the Scale-Invariant
Probabilistic Models of Attention based on Iconic Representations and Predictive Coding
 To appear in: Neurobiology of Attention, L. Itti, G. Rees, and J. Tsotsos (editors), Academic Press, 2004. Probabilistic Models of Attention based on Iconic Representations and Predictive Coding Rajesh
To appear in: Neurobiology of Attention, L. Itti, G. Rees, and J. Tsotsos (editors), Academic Press, 2004. Probabilistic Models of Attention based on Iconic Representations and Predictive Coding Rajesh
Color Local Texture Features Based Face Recognition
 Color Local Texture Features Based Face Recognition Priyanka V. Bankar Department of Electronics and Communication Engineering SKN Sinhgad College of Engineering, Korti, Pandharpur, Maharashtra, India
Color Local Texture Features Based Face Recognition Priyanka V. Bankar Department of Electronics and Communication Engineering SKN Sinhgad College of Engineering, Korti, Pandharpur, Maharashtra, India
cse 252c Fall 2004 Project Report: A Model of Perpendicular Texture for Determining Surface Geometry
 cse 252c Fall 2004 Project Report: A Model of Perpendicular Texture for Determining Surface Geometry Steven Scher December 2, 2004 Steven Scher SteveScher@alumni.princeton.edu Abstract Three-dimensional
cse 252c Fall 2004 Project Report: A Model of Perpendicular Texture for Determining Surface Geometry Steven Scher December 2, 2004 Steven Scher SteveScher@alumni.princeton.edu Abstract Three-dimensional
82 REGISTRATION OF RETINOGRAPHIES
 82 REGISTRATION OF RETINOGRAPHIES 3.3 Our method Our method resembles the human approach to image matching in the sense that we also employ as guidelines features common to both images. It seems natural
82 REGISTRATION OF RETINOGRAPHIES 3.3 Our method Our method resembles the human approach to image matching in the sense that we also employ as guidelines features common to both images. It seems natural
Motion Detection Algorithm
 Volume 1, No. 12, February 2013 ISSN 2278-1080 The International Journal of Computer Science & Applications (TIJCSA) RESEARCH PAPER Available Online at http://www.journalofcomputerscience.com/ Motion Detection
Volume 1, No. 12, February 2013 ISSN 2278-1080 The International Journal of Computer Science & Applications (TIJCSA) RESEARCH PAPER Available Online at http://www.journalofcomputerscience.com/ Motion Detection
Sobel Edge Detection Algorithm
 Sobel Edge Detection Algorithm Samta Gupta 1, Susmita Ghosh Mazumdar 2 1 M. Tech Student, Department of Electronics & Telecom, RCET, CSVTU Bhilai, India 2 Reader, Department of Electronics & Telecom, RCET,
Sobel Edge Detection Algorithm Samta Gupta 1, Susmita Ghosh Mazumdar 2 1 M. Tech Student, Department of Electronics & Telecom, RCET, CSVTU Bhilai, India 2 Reader, Department of Electronics & Telecom, RCET,
Function approximation using RBF network. 10 basis functions and 25 data points.
 1 Function approximation using RBF network F (x j ) = m 1 w i ϕ( x j t i ) i=1 j = 1... N, m 1 = 10, N = 25 10 basis functions and 25 data points. Basis function centers are plotted with circles and data
1 Function approximation using RBF network F (x j ) = m 1 w i ϕ( x j t i ) i=1 j = 1... N, m 1 = 10, N = 25 10 basis functions and 25 data points. Basis function centers are plotted with circles and data
Research Article A Computing Model of Selective Attention for Service Robot Based on Spatial Data Fusion
 Journal of Robotics Volume 2018, Article ID 5368624, 9 pages https://doi.org/10.1155/2018/5368624 Research Article A Computing Model of Selective Attention for Service Robot Based on Spatial Data Fusion
Journal of Robotics Volume 2018, Article ID 5368624, 9 pages https://doi.org/10.1155/2018/5368624 Research Article A Computing Model of Selective Attention for Service Robot Based on Spatial Data Fusion
CS4442/9542b Artificial Intelligence II prof. Olga Veksler
 CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 8 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 8 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
Neurophysical Model by Barten and Its Development
 Chapter 14 Neurophysical Model by Barten and Its Development According to the Barten model, the perceived foveal image is corrupted by internal noise caused by statistical fluctuations, both in the number
Chapter 14 Neurophysical Model by Barten and Its Development According to the Barten model, the perceived foveal image is corrupted by internal noise caused by statistical fluctuations, both in the number
STEREO-DISPARITY ESTIMATION USING A SUPERVISED NEURAL NETWORK
 2004 IEEE Workshop on Machine Learning for Signal Processing STEREO-DISPARITY ESTIMATION USING A SUPERVISED NEURAL NETWORK Y. V. Venkatesh, B. S. Venhtesh and A. Jaya Kumar Department of Electrical Engineering
2004 IEEE Workshop on Machine Learning for Signal Processing STEREO-DISPARITY ESTIMATION USING A SUPERVISED NEURAL NETWORK Y. V. Venkatesh, B. S. Venhtesh and A. Jaya Kumar Department of Electrical Engineering
CS4442/9542b Artificial Intelligence II prof. Olga Veksler
 CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 2 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 2 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
Biometrics Technology: Image Processing & Pattern Recognition (by Dr. Dickson Tong)
 Biometrics Technology: Image Processing & Pattern Recognition (by Dr. Dickson Tong) References: [1] http://homepages.inf.ed.ac.uk/rbf/hipr2/index.htm [2] http://www.cs.wisc.edu/~dyer/cs540/notes/vision.html
Biometrics Technology: Image Processing & Pattern Recognition (by Dr. Dickson Tong) References: [1] http://homepages.inf.ed.ac.uk/rbf/hipr2/index.htm [2] http://www.cs.wisc.edu/~dyer/cs540/notes/vision.html
Exercise: Simulating spatial processing in the visual pathway with convolution
 Exercise: Simulating spatial processing in the visual pathway with convolution This problem uses convolution to simulate the spatial filtering performed by neurons in the early stages of the visual pathway,
Exercise: Simulating spatial processing in the visual pathway with convolution This problem uses convolution to simulate the spatial filtering performed by neurons in the early stages of the visual pathway,
Digital image processing
 Digital image processing Image enhancement algorithms: grey scale transformations Any digital image can be represented mathematically in matrix form. The number of lines in the matrix is the number of
Digital image processing Image enhancement algorithms: grey scale transformations Any digital image can be represented mathematically in matrix form. The number of lines in the matrix is the number of
Connected Component Analysis and Change Detection for Images
 Connected Component Analysis and Change Detection for Images Prasad S.Halgaonkar Department of Computer Engg, MITCOE Pune University, India Abstract Detection of the region of change in images of a particular
Connected Component Analysis and Change Detection for Images Prasad S.Halgaonkar Department of Computer Engg, MITCOE Pune University, India Abstract Detection of the region of change in images of a particular
Disguised Face Identification (DFI) with Facial KeyPoints using Spatial Fusion Convolutional Network. Nathan Sun CIS601
 Disguised Face Identification (DFI) with Facial KeyPoints using Spatial Fusion Convolutional Network Nathan Sun CIS601 Introduction Face ID is complicated by alterations to an individual s appearance Beard,
Disguised Face Identification (DFI) with Facial KeyPoints using Spatial Fusion Convolutional Network Nathan Sun CIS601 Introduction Face ID is complicated by alterations to an individual s appearance Beard,
A Novel Approach to Image Segmentation for Traffic Sign Recognition Jon Jay Hack and Sidd Jagadish
 A Novel Approach to Image Segmentation for Traffic Sign Recognition Jon Jay Hack and Sidd Jagadish Introduction/Motivation: As autonomous vehicles, such as Google s self-driving car, have recently become
A Novel Approach to Image Segmentation for Traffic Sign Recognition Jon Jay Hack and Sidd Jagadish Introduction/Motivation: As autonomous vehicles, such as Google s self-driving car, have recently become
Solution: filter the image, then subsample F 1 F 2. subsample blur subsample. blur
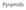 Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Image Mining: frameworks and techniques
 Image Mining: frameworks and techniques Madhumathi.k 1, Dr.Antony Selvadoss Thanamani 2 M.Phil, Department of computer science, NGM College, Pollachi, Coimbatore, India 1 HOD Department of Computer Science,
Image Mining: frameworks and techniques Madhumathi.k 1, Dr.Antony Selvadoss Thanamani 2 M.Phil, Department of computer science, NGM College, Pollachi, Coimbatore, India 1 HOD Department of Computer Science,
Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science
 2D Gabor functions and filters for image processing and computer vision Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science 2 Most of the images in this presentation
2D Gabor functions and filters for image processing and computer vision Nicolai Petkov Intelligent Systems group Institute for Mathematics and Computing Science 2 Most of the images in this presentation
CSE 252B: Computer Vision II
 CSE 252B: Computer Vision II Lecturer: Serge Belongie Scribes: Jeremy Pollock and Neil Alldrin LECTURE 14 Robust Feature Matching 14.1. Introduction Last lecture we learned how to find interest points
CSE 252B: Computer Vision II Lecturer: Serge Belongie Scribes: Jeremy Pollock and Neil Alldrin LECTURE 14 Robust Feature Matching 14.1. Introduction Last lecture we learned how to find interest points
4 Tracking Object Features Using Dynamically Defined Spatial Context Implementation Results... 27
 Contents 1 Statement of the Problem Studied 5 2 Detection of Moving and Still Vehicles from Real-Time Videos 6 2.1 Introduction......................................... 6 2.2 Segmentation, Grouping and
Contents 1 Statement of the Problem Studied 5 2 Detection of Moving and Still Vehicles from Real-Time Videos 6 2.1 Introduction......................................... 6 2.2 Segmentation, Grouping and
Suitability Analysis Based on Multi-Feature Fusion Visual Saliency Model in Vision Navigation
 Suitability Analysis Based on Multi-Feature Fusion Visual Saliency Model in Vision Navigation Zhen-lu Jin, Quan Pan, Chun-hui Zhao, Yong Liu School of Automation Northwestern Polytechnical University Xi
Suitability Analysis Based on Multi-Feature Fusion Visual Saliency Model in Vision Navigation Zhen-lu Jin, Quan Pan, Chun-hui Zhao, Yong Liu School of Automation Northwestern Polytechnical University Xi
Robust contour extraction and junction detection by a neural model utilizing recurrent long-range interactions
 Robust contour extraction and junction detection by a neural model utilizing recurrent long-range interactions Thorsten Hansen 1, 2 & Heiko Neumann 2 1 Abteilung Allgemeine Psychologie, Justus-Liebig-Universität
Robust contour extraction and junction detection by a neural model utilizing recurrent long-range interactions Thorsten Hansen 1, 2 & Heiko Neumann 2 1 Abteilung Allgemeine Psychologie, Justus-Liebig-Universität
Face Detection Using Convolutional Neural Networks and Gabor Filters
 Face Detection Using Convolutional Neural Networks and Gabor Filters Bogdan Kwolek Rzeszów University of Technology W. Pola 2, 35-959 Rzeszów, Poland bkwolek@prz.rzeszow.pl Abstract. This paper proposes
Face Detection Using Convolutional Neural Networks and Gabor Filters Bogdan Kwolek Rzeszów University of Technology W. Pola 2, 35-959 Rzeszów, Poland bkwolek@prz.rzeszow.pl Abstract. This paper proposes
FPGA IMPLEMENTATION FOR REAL TIME SOBEL EDGE DETECTOR BLOCK USING 3-LINE BUFFERS
 FPGA IMPLEMENTATION FOR REAL TIME SOBEL EDGE DETECTOR BLOCK USING 3-LINE BUFFERS 1 RONNIE O. SERFA JUAN, 2 CHAN SU PARK, 3 HI SEOK KIM, 4 HYEONG WOO CHA 1,2,3,4 CheongJu University E-maul: 1 engr_serfs@yahoo.com,
FPGA IMPLEMENTATION FOR REAL TIME SOBEL EDGE DETECTOR BLOCK USING 3-LINE BUFFERS 1 RONNIE O. SERFA JUAN, 2 CHAN SU PARK, 3 HI SEOK KIM, 4 HYEONG WOO CHA 1,2,3,4 CheongJu University E-maul: 1 engr_serfs@yahoo.com,
Saliency Detection: A Spectral Residual Approach
 Saliency Detection: A Spectral Residual Approach Xiaodi Hou and Liqing Zhang Department of Computer Science, Shanghai Jiao Tong University No.8, Dongchuan Road, Shanghai http://bcmi.sjtu.edu.cn/ houxiaodi,
Saliency Detection: A Spectral Residual Approach Xiaodi Hou and Liqing Zhang Department of Computer Science, Shanghai Jiao Tong University No.8, Dongchuan Road, Shanghai http://bcmi.sjtu.edu.cn/ houxiaodi,
SIFT: SCALE INVARIANT FEATURE TRANSFORM SURF: SPEEDED UP ROBUST FEATURES BASHAR ALSADIK EOS DEPT. TOPMAP M13 3D GEOINFORMATION FROM IMAGES 2014
 SIFT: SCALE INVARIANT FEATURE TRANSFORM SURF: SPEEDED UP ROBUST FEATURES BASHAR ALSADIK EOS DEPT. TOPMAP M13 3D GEOINFORMATION FROM IMAGES 2014 SIFT SIFT: Scale Invariant Feature Transform; transform image
SIFT: SCALE INVARIANT FEATURE TRANSFORM SURF: SPEEDED UP ROBUST FEATURES BASHAR ALSADIK EOS DEPT. TOPMAP M13 3D GEOINFORMATION FROM IMAGES 2014 SIFT SIFT: Scale Invariant Feature Transform; transform image
All Rights Reserved 2014 IJARECE
 SALIENCY BASED ADAPTIVE IMAGE SIGNATURE USING BINARY HOLISTIC IMAGE DESCRIPTOR RAJESH MATE1, PRAVIN DERE2 & SANJAY M. HUNDIWALE3 1M.E Student, Department of EXTC, ARMIET College of Engineering, Sapgaon,
SALIENCY BASED ADAPTIVE IMAGE SIGNATURE USING BINARY HOLISTIC IMAGE DESCRIPTOR RAJESH MATE1, PRAVIN DERE2 & SANJAY M. HUNDIWALE3 1M.E Student, Department of EXTC, ARMIET College of Engineering, Sapgaon,
Image Enhancement. Digital Image Processing, Pratt Chapter 10 (pages ) Part 1: pixel-based operations
 Image Enhancement Digital Image Processing, Pratt Chapter 10 (pages 243-261) Part 1: pixel-based operations Image Processing Algorithms Spatial domain Operations are performed in the image domain Image
Image Enhancement Digital Image Processing, Pratt Chapter 10 (pages 243-261) Part 1: pixel-based operations Image Processing Algorithms Spatial domain Operations are performed in the image domain Image
INVARIANT CORNER DETECTION USING STEERABLE FILTERS AND HARRIS ALGORITHM
 INVARIANT CORNER DETECTION USING STEERABLE FILTERS AND HARRIS ALGORITHM ABSTRACT Mahesh 1 and Dr.M.V.Subramanyam 2 1 Research scholar, Department of ECE, MITS, Madanapalle, AP, India vka4mahesh@gmail.com
INVARIANT CORNER DETECTION USING STEERABLE FILTERS AND HARRIS ALGORITHM ABSTRACT Mahesh 1 and Dr.M.V.Subramanyam 2 1 Research scholar, Department of ECE, MITS, Madanapalle, AP, India vka4mahesh@gmail.com
Robotics Programming Laboratory
 Chair of Software Engineering Robotics Programming Laboratory Bertrand Meyer Jiwon Shin Lecture 8: Robot Perception Perception http://pascallin.ecs.soton.ac.uk/challenges/voc/databases.html#caltech car
Chair of Software Engineering Robotics Programming Laboratory Bertrand Meyer Jiwon Shin Lecture 8: Robot Perception Perception http://pascallin.ecs.soton.ac.uk/challenges/voc/databases.html#caltech car
Region-based Segmentation
 Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
MULTIRESOLUTION SHAPE FROM SHADING*
 MULTIRESOLUTION SHAPE FROM SHADING* Gad Ron Shmuel Peleg Dept. of Computer Science The Hebrew University of Jerusalem 91904 Jerusalem, Israel Abstract Multiresolution approaches are often used in computer
MULTIRESOLUTION SHAPE FROM SHADING* Gad Ron Shmuel Peleg Dept. of Computer Science The Hebrew University of Jerusalem 91904 Jerusalem, Israel Abstract Multiresolution approaches are often used in computer
International Conference on Information Sciences, Machinery, Materials and Energy (ICISMME 2015)
 International Conference on Information Sciences, Machinery, Materials and Energy (ICISMME 2015) Brief Analysis on Typical Image Saliency Detection Methods Wenwen Pan, Xiaofei Sun, Xia Wang, Wei Zhang
International Conference on Information Sciences, Machinery, Materials and Energy (ICISMME 2015) Brief Analysis on Typical Image Saliency Detection Methods Wenwen Pan, Xiaofei Sun, Xia Wang, Wei Zhang
