Computer security experts often tell us not to choose an easy to guess word as a password. For example, the user name or date of birth.
|
|
|
- Ambrose Perkins
- 5 years ago
- Views:
Transcription
1 Graphical Passwords: Computer security experts often tell us not to choose an easy to guess word as a password. For example, the user name or date of birth. The Graphical Passwords team have been working on a new password system that is more secure. Their tests suggest that the Background Draw A Secret (BDAS) graphical password are up to 40 percent stronger than a typical eight. Character password made up of letters, numbers and symbols. Just a simple smiley face password, can have a strength of 55 bits. For example, traditional passwords such as C4hjy!89 would have a strength of about 53bits. The very simple smiley face would have a similar strength. But a slightly morecomplex picture would be much stronger. In earlier time where secure communication and code-breaking were vitally important. An American electrical engineer and mathematician called Claude Shannon published a groundbreaking book. The Mathematical theory of Communication established a new branch of applied mathematics now known as information theory which enabled mathematicians to quantify information. In particular, he came up with a way of measuring how much information there is in a message, called information entropy. Information entropy can measure how much redundancy there is in a message or conversely, how much information it carries. A high entropy means there is a lot of uncertainty, so the message carries a lot of new information. So the higher the entropy, the more difficult a password is to guess. For example, a message telling You are at the 2008 Royal Society Summer Exhibition doesn t tell you anything you don t know. You knew that would happen when you set out this morning. But telling you You are at the Graphical Passwords stand does give you new information. The overall entropy of an event X is calculated as the sum of each possible outcome x within X. Let s write the probability of a particular outcome as p(x). So if p(x) = 1, then we know that that particular outcome will definitely happen in information terms, this means a content of 0.Putting in some other conditions, it turns out that taking the logarithm - i.e. log(p(x)) is the best way to handle this measure of information. Logarithms can be calculated in any base but if the chosen base is 2 then we say that the information is in bits, ideal when you are talking about computer information. So the information entropy is computed mathematically as: H(X) = - Ó p(x)log2 p(x) all possible x Now consider another situation where two events are equally likely to happen, such as tossing a fair coin. So if we consider tossing a coin, the entropy is -(½ log2(1/2) + ½ log2(1/2)) = 1 bit In general, the more equally likely events n there are, log(n) increases and the entropy goes up as the amount of information is greater. The practical strength of commonly used 8-character passwords is far less than 53 bits since people often choose memorable words and names. A modern desktop computer can search through about 240 (around 1,000 billion) passwords in 24 hours, and the speed of computers is fast increasing. So passwords with a bit-strength of less than 40 bits can be easily guessed, when hackers are able to make repeated tries to verify their guess.
2 In the BDAS system, it isn t just different characters that make up passwords and affect their strength. BDAS password strength comprises: - number of strokes (a stroke is complete when the pen is lifted up) - length or number of grid cells a drawing cuts through - size of the grid and the grid size - order of strokes. The team found that the average strength of the BDAS passwords created by participants in their experiments could be as high as bits, and 95% users were able to recreate their passwords within three attempts one week later. Reference: Purely Automated Attacks on Pass Points-Style Graphical Passwords Graphical passwords are an alternative to text passwords, where by a user is asked to remember an image(or parts of an image) instead of a word. They are motivated in part by the well-known fact that people have superior memorability for images and the promise of their suitability for small devices such as smart phones. Graphical passwords have become an active topic of research with many new proposals. One proposal of interest, Pass Points involves a user creating a 5-point click sequence on a background image. Usability studies have indicated that these graphical passwords have reasonable login and creation times, acceptable error rates, decent general perception, and less interference between multiple passwords when compared to text passwords. This research improves the understanding of the security of Pass Points-style graphical passwords, i.e., schemes closely resembling Pass Points, where in a user creates a click sequence Of r points (e.g., r = 5) on a single background image. Pass Points-style graphical passwords have been shown to be susceptible to hot-spots, which can be exploited in human-seeded attack where by human-computed data (harvesting click-points from a small set of users) is used to facilitate efficient attacks. These attacks require that the attacker collect sufficient humancomputed" data for the target image, which is more costly for systems with multiple images. This leads us to ask whether more scalable attacks exist, and in particular, effective fully-automated attacks. In the present work we introduce and evaluate a set of purely automated attacks against Pass Points-style graphical passwords. This attack method is based on the hypothesis that users are more likely to choose click-points relating to predictable preferences, e.g., logically grouping the click-points through a click-order pattern (such as five points in a straight line), and/or choosing click-points in the areas of the image that their attention is naturally drawn towards. To find parts of the image that users are more likely to attend to (salient parts of the image), we use model of visual attention. We also examine click-order patterns both alone and in combination with these more salient parts of the image. Pass Points allows users to click a sequence of r points anywhere on an image while allowing error tolerance. Studies using r = 5 suggest promising usability. A related commercial
3 system designed for the Pocket PC, called VisKey, allows the user to choose the number of click-points and to set the error tolerance. One way that an attacker could predict hot-spots is by using image processing tools to locate areas of interest. Using an image processing tool for guessing Pass Points passwords to guess single-session user passwords for two images, one being a particularly simple image. For the other image, their method guessed 8% of passwords using an attack dictionary with 232 entries where the full space was 240 entries. On examining an automated method (based on a variation of model of visual attention), using 1% and 0.9% of passwords on two images, using an attack dictionary with 235 entries compared to a full password space of 243 passwords. The method focused only on a variation of stage 1 of the model ordering an attack dictionary based on the raw values of the resulting saliency map, whereas the present paper uses the entire model including stage 2 of the model. In a preliminary version of the present work guess 8-15% of passwords for two representative images using dictionaries of less than entries, and about 16% of passwords on each of these images using dictionaries of less than entries, where the full space is 243.Basic click-order patterns were first introduced and evaluated in combination with humanseeded attacks the only pattern in common with the present work is regular IAG (i.e., without any laziness" relaxation). Chiasson analyze a set of patterns for three click-based graphical password schemes: pass points and two variants named Cued Click-Points (CCP) and Persuasive Cued Click-Points (PCCP). In CCP and PCCP, a user clicks on a single point on each of five images, where each image (except the first image) is dependent on the previous click-point. They show that the design of the interface impacts whether users select click-points in some predictable patterns, and implied that such patterns in user choice might reduce the effective password space. The present paper mathematically models click-order patterns and uses them to mount purely automated attacks, demonstrating and experimentally quantifying the degree to which certain patterns can be used to efficiently search the password space. Human-computed data sets (harvesting click-points from a small set of users) were used in two human-seeded attacks against passwords from a field study on two different images: one based on a first-order Markov model another based on an independent probability model. Using their human-computed data sets (harvested from a single-session lab study), a dictionary based on independent probabilities contained entries and found 20-36% of field study passwords, and a dictionary based on the first-order Markov model found 4-10% of field study passwords within 100 guesses. These attacks require the attacker to collect sufficient click-points for each image, and are image dependent, thus requiring per-image costs for systems with multiple images. Models of Visual Attention Computational models of bottom-up visual attention are normally defined by features of a digital image, such as intensity, color, and orientation.feature maps are then created and used to generate a saliency map, which is a grayscale image where higher-intensity locations define more conspicuous areas.
4 Computational models of top-down visual attention can be defined by training.the difficulty of these models is that the top-down task must be pre-defined (e.g., find all people in image), and then a corpus of images that are tagged with the areas containing the subject to find (e.g., people) must be used for training. We discuss an alternate method to create a top-down model, based on guided search, which weighs visual feature maps according to the top down task. For example, with a task of locating a red object, a red-sensitive feature map would gain more weight, giving it a higher value in the resulting saliency map. In both cases assumptions regarding what sort of objects people are looking for are required to create such a model. In this work, we focus on bottom-up visual attention, using the computational model of visual attention. We chose this model as it is well-known, and there is empirical evidence that it captures people s bottom-up visual attention. The general idea is that areas of an image will be salient (or visually stand out") when they differ from their surroundings. Given an input image, the model outputs a focus-of-attention scan-path to model the locations and the order in which a human might automatically and unconsciously attend these parts of the image. The model first constructs a saliency map based on visual features. Then it uses a winner-take-all neural network with inhibition of return to define a specific focus-ofattention scan-path, intended to represent the order in which a user would scan the image. In stage 1, the saliency map is created by decomposing the original image into a set of 50 multi-level feature maps", which extract spatial discontinuities based on color opponency (either red-green or blue-yellow), intensity, or orientation. Each level defines a different size of the center and its surround, in order to account for conspicuous locations of various sizes. All feature maps are then combined into a single saliency map. In stage 2, the neural network detects the point of highest salience (as indicated by the intensity value of the saliency map), and draws the focus of attention towards this location. Once an area has been attended to, inhibition of return will prevent the area from being the focus again for a period of time. Together, the neural network with inhibition of return produces output in the form of spatio-temporal attentional scan-paths, which follow the order of decreasing saliency as defined by stage 1. Two different normalization types (producing different scan-paths) can be used with the model : LocalMax and Iterative. In LocalMax normalization,the neural network will have a bias towards those areas that are closer to the previously attended location.
5 LocalMax normalization Iterative normalization In Iterative normalization, the neural network will find the next most salient area that has not been inhibited. Corner Detection: A corner is defined as the intersection of two edges, where an edge is defined by the points in a digital image where there are sharp changes in intensity. We use Harris corner detection as implemented by Kovesi.This first identifies the edges. Those edges are then blurred to reduce the effect of any noise. Next, based on the edges, an energy map is generated, containing local maxima and minima. We also create a binary corners map (a specialized type of binary map or one-to-one mapping from its pixels of value 0 or 1 to the pixels of the original image): when a pixel is a corner in the original image, its corresponding value is 1;otherwise 0. Centroid Detection:
6 To find the centers of objects, we first partition the digital image into segments using image segmentation, by the mean-shift segmentation algorithm,which takes a feature (range) bandwidth, spatial bandwidth, and a minimum region area (in pixels) as input. We set these parameters to 7, 9, and 50 respectively, which we found empirically to provide an acceptable segmentation with the smallest resulting number of segments. These results suggest that automated attacks provide an effective alternative to a humanseeded attack against PassPoints-style graphical passwords. Furthermore, they allow continuation of an attack using click-order patterns, guessing more passwords overall than human-seeded methods. Finally, purely automated attacks are arguably much easier for an attacker to launch (removing the requirement of humans to index the images), especially if large image datasets are used. We emphasize that a number of our attack dictionaries, do not rely on visual attention techniques or any image-specific precomputation, implying that the actual dictionaries are the same for all images, though the attack results (i.e., their effectiveness) are image-dependent and of course depend also on the actual passwords chosen by any users in question. We do not expect that these attacks can be effectively applied to multi-image clickbased schemes. These findings might be used to help background image selection, although precise details of an exact method remain unclear. As one possibility, corners and centroids of images might be extracted, and used to build a click-order heuristic graph (as in our dictionary generation algorithm); the images that generate a larger resulting dictionary might indicate a more attack-resistant image. Another possibility might be to measure the amount of structure an image has, assuming that such image structure would encourage click-order patterns. Reference: df
GRAPHICAL passwords are an alternative to text passwords, Purely Automated Attacks on PassPoints-Style Graphical Passwords
 1 Purely Automated Attacks on PassPoints-Style Graphical Passwords P.C. van Oorschot, Amirali Salehi-Abari, Julie Thorpe Abstract We introduce and evaluate various methods for purely automated attacks
1 Purely Automated Attacks on PassPoints-Style Graphical Passwords P.C. van Oorschot, Amirali Salehi-Abari, Julie Thorpe Abstract We introduce and evaluate various methods for purely automated attacks
Purely Automated Attacks on PassPoints-Style Graphical Passwords
 1 Purely Automated Attacks on PassPoints-Style Graphical Passwords P.C. van Oorschot, Amirali Salehi-Abari, Julie Thorpe School of Computer Science, Carleton University Abstract We introduce and evaluate
1 Purely Automated Attacks on PassPoints-Style Graphical Passwords P.C. van Oorschot, Amirali Salehi-Abari, Julie Thorpe School of Computer Science, Carleton University Abstract We introduce and evaluate
On Purely Automated Attacks and Click-Based Graphical Passwords
 On Purely Automated Attacks and Click-Based Graphical Passwords Amirali Salehi-Abari, Julie Thorpe, and P.C. van Oorschot School of Computer Science, Carleton University, Canada {asabari, jthorpe, paulv}@scs.carleton.ca
On Purely Automated Attacks and Click-Based Graphical Passwords Amirali Salehi-Abari, Julie Thorpe, and P.C. van Oorschot School of Computer Science, Carleton University, Canada {asabari, jthorpe, paulv}@scs.carleton.ca
ISSN: (Online) Volume 2, Issue 10, October 2014 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 2, Issue 10, October 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
ISSN: 2321-7782 (Online) Volume 2, Issue 10, October 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
Character Recognition
 Character Recognition 5.1 INTRODUCTION Recognition is one of the important steps in image processing. There are different methods such as Histogram method, Hough transformation, Neural computing approaches
Character Recognition 5.1 INTRODUCTION Recognition is one of the important steps in image processing. There are different methods such as Histogram method, Hough transformation, Neural computing approaches
Defenses against Large Scale Online Password Guessing by Using Persuasive Cued Click Points
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Cued Click Point Technique for Graphical Password Authentication
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS
 http:// KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS G Anil Kumar 1, K Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor (CSE), Nalanda Institute of Engineering
http:// KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS G Anil Kumar 1, K Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor (CSE), Nalanda Institute of Engineering
DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS
 http:// DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS Chalichima Harshitha 1, Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor
http:// DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS Chalichima Harshitha 1, Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor
KNOWLEDGE BASED AUTHENTICATION MECHANISM FOR SECURED DATA TRANSFER
 KNOWLEDGE BASED AUTHENTICATION MECHANISM FOR SECURED DATA TRANSFER R.T.Narmadha1, R.T.Nivetha2, M.Roobia Fathima 2, P.Vijayalakshmi 2 1 Department of Information Technology, Info Institute of Engineering,
KNOWLEDGE BASED AUTHENTICATION MECHANISM FOR SECURED DATA TRANSFER R.T.Narmadha1, R.T.Nivetha2, M.Roobia Fathima 2, P.Vijayalakshmi 2 1 Department of Information Technology, Info Institute of Engineering,
International Journal of Emerging Technology in Computer Science & Electronics (IJETCSE) ISSN: Volume 14 Issue 2 APRIL 2015
 Persuasive Cued Click Point Authentication Mechanism with Sound Signature MOUNESHWAR KANAMADI 1,AMIT SAWANT 2,JAMDADE MARUTI 3,4 MEGHARANI BAMBUGADE, 5 ROKADE KOMAL 1 Department of CSE, Ashokrao Mane Group
Persuasive Cued Click Point Authentication Mechanism with Sound Signature MOUNESHWAR KANAMADI 1,AMIT SAWANT 2,JAMDADE MARUTI 3,4 MEGHARANI BAMBUGADE, 5 ROKADE KOMAL 1 Department of CSE, Ashokrao Mane Group
6.871 Expert System: WDS Web Design Assistant System
 6.871 Expert System: WDS Web Design Assistant System Timur Tokmouline May 11, 2005 1 Introduction Today, despite the emergence of WYSIWYG software, web design is a difficult and a necessary component of
6.871 Expert System: WDS Web Design Assistant System Timur Tokmouline May 11, 2005 1 Introduction Today, despite the emergence of WYSIWYG software, web design is a difficult and a necessary component of
7. Decision or classification trees
 7. Decision or classification trees Next we are going to consider a rather different approach from those presented so far to machine learning that use one of the most common and important data structure,
7. Decision or classification trees Next we are going to consider a rather different approach from those presented so far to machine learning that use one of the most common and important data structure,
(Refer Slide Time: 00:02:00)
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 18 Polyfill - Scan Conversion of a Polygon Today we will discuss the concepts
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 18 Polyfill - Scan Conversion of a Polygon Today we will discuss the concepts
3LAS (Three Level Authentication Scheme)
 3LAS (Three Level Authentication Scheme) Kunal Mulwani 1, Saurabh Naik 2, Navinkumar Gurnani 3, Dr. Nupur Giri 4, Prof. Sharmila Sengupta 5 1, 2,3,4,5 Vivekanand Education Society's Institute of Technology,
3LAS (Three Level Authentication Scheme) Kunal Mulwani 1, Saurabh Naik 2, Navinkumar Gurnani 3, Dr. Nupur Giri 4, Prof. Sharmila Sengupta 5 1, 2,3,4,5 Vivekanand Education Society's Institute of Technology,
To become familiar with array manipulation, searching, and sorting.
 ELECTRICAL AND COMPUTER ENGINEERING 06-88-211: COMPUTER AIDED ANALYSIS LABORATORY EXPERIMENT #2: INTRODUCTION TO ARRAYS SID: OBJECTIVE: SECTIONS: Total Mark (out of 20): To become familiar with array manipulation,
ELECTRICAL AND COMPUTER ENGINEERING 06-88-211: COMPUTER AIDED ANALYSIS LABORATORY EXPERIMENT #2: INTRODUCTION TO ARRAYS SID: OBJECTIVE: SECTIONS: Total Mark (out of 20): To become familiar with array manipulation,
5-899 / Usable Privacy and Security Text Passwords Lecture by Sasha Romanosky Scribe notes by Ponnurangam K March 30, 2006
 5-899 / 17-500 Usable Privacy and Security Text Passwords Lecture by Sasha Romanosky Scribe notes by Ponnurangam K March 30, 2006 1 Topics covered Authentication and authorization Pass-sentences, pass-phrases
5-899 / 17-500 Usable Privacy and Security Text Passwords Lecture by Sasha Romanosky Scribe notes by Ponnurangam K March 30, 2006 1 Topics covered Authentication and authorization Pass-sentences, pass-phrases
Authentication Using Grid-Based Authentication Scheme and Graphical Password
 Authentication Using Grid-Based Authentication Scheme and Graphical Password Vijayshri D. Vaidya 1 Department of Computer engineering SND COE & RC Yeola, India Imaran R. Shaikh 2 Department of Computer
Authentication Using Grid-Based Authentication Scheme and Graphical Password Vijayshri D. Vaidya 1 Department of Computer engineering SND COE & RC Yeola, India Imaran R. Shaikh 2 Department of Computer
Computer Exercise #3 (due March 7, but most useful if completed before class, Friday March 3) Adding Waves
 Physics 212E Chowdary Classical and Modern Physics Name: Computer Exercise #3 (due March 7, but most useful if completed before class, Friday March 3) Adding Waves This exercise can be broken up into two
Physics 212E Chowdary Classical and Modern Physics Name: Computer Exercise #3 (due March 7, but most useful if completed before class, Friday March 3) Adding Waves This exercise can be broken up into two
Decision Tree CE-717 : Machine Learning Sharif University of Technology
 Decision Tree CE-717 : Machine Learning Sharif University of Technology M. Soleymani Fall 2012 Some slides have been adapted from: Prof. Tom Mitchell Decision tree Approximating functions of usually discrete
Decision Tree CE-717 : Machine Learning Sharif University of Technology M. Soleymani Fall 2012 Some slides have been adapted from: Prof. Tom Mitchell Decision tree Approximating functions of usually discrete
Chapter 10 Working with Graphs and Charts
 Chapter 10: Working with Graphs and Charts 163 Chapter 10 Working with Graphs and Charts Most people understand information better when presented as a graph or chart than when they look at the raw data.
Chapter 10: Working with Graphs and Charts 163 Chapter 10 Working with Graphs and Charts Most people understand information better when presented as a graph or chart than when they look at the raw data.
Unit 1, Lesson 1: Moving in the Plane
 Unit 1, Lesson 1: Moving in the Plane Let s describe ways figures can move in the plane. 1.1: Which One Doesn t Belong: Diagrams Which one doesn t belong? 1.2: Triangle Square Dance m.openup.org/1/8-1-1-2
Unit 1, Lesson 1: Moving in the Plane Let s describe ways figures can move in the plane. 1.1: Which One Doesn t Belong: Diagrams Which one doesn t belong? 1.2: Triangle Square Dance m.openup.org/1/8-1-1-2
ENHANCEMENT OF SECURITY FEATURE IN GRAPHICAL PASSWORD AUTHENTICATION
 International Journal of Computer Science Engineering and Information Technology Research (IJCSEITR) ISSN 2249-6831 Vol. 3, Issue 2, Jun 2013, 395-402 TJPRC Pvt. Ltd. ENHANCEMENT OF SECURITY FEATURE IN
International Journal of Computer Science Engineering and Information Technology Research (IJCSEITR) ISSN 2249-6831 Vol. 3, Issue 2, Jun 2013, 395-402 TJPRC Pvt. Ltd. ENHANCEMENT OF SECURITY FEATURE IN
Outline Key Management CS 239 Computer Security February 9, 2004
 Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
Confidence Intervals. Dennis Sun Data 301
 Dennis Sun Data 301 Statistical Inference probability Population / Box Sample / Data statistics The goal of statistics is to infer the unknown population from the sample. We ve already seen one mode of
Dennis Sun Data 301 Statistical Inference probability Population / Box Sample / Data statistics The goal of statistics is to infer the unknown population from the sample. We ve already seen one mode of
Authentication schemes for session password using color and special characters
 Authentication schemes for session password using color and special characters Rohit Jagtap1, a, Vaibhav Ahirrao2,b Vinayak Kadam3,c Nilesh Aher4 1.Department of Computer Engineering, 2 Department of Computer
Authentication schemes for session password using color and special characters Rohit Jagtap1, a, Vaibhav Ahirrao2,b Vinayak Kadam3,c Nilesh Aher4 1.Department of Computer Engineering, 2 Department of Computer
How to Tell a Human apart from a Computer. The Turing Test. (and Computer Literacy) Spring 2013 ITS B 1. Are Computers like Human Brains?
 How to Tell a Human apart from a Computer The Turing Test (and Computer Literacy) Spring 2013 ITS102.23 - B 1 Are Computers like Human Brains? The impressive contributions of computers during World War
How to Tell a Human apart from a Computer The Turing Test (and Computer Literacy) Spring 2013 ITS102.23 - B 1 Are Computers like Human Brains? The impressive contributions of computers during World War
User Authentication. Daniel Halperin Tadayoshi Kohno
 CSE 484 / CSE M 584 (Autumn 2011) User Authentication Daniel Halperin Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others
CSE 484 / CSE M 584 (Autumn 2011) User Authentication Daniel Halperin Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others
NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION
 NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION P.Kiruthika R.Tamilarasi Department of Computer Applications, Dr.Mahalingam College Of Engineering and Technology,
NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION P.Kiruthika R.Tamilarasi Department of Computer Applications, Dr.Mahalingam College Of Engineering and Technology,
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14 Scan Converting Lines, Circles and Ellipses Hello everybody, welcome again
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14 Scan Converting Lines, Circles and Ellipses Hello everybody, welcome again
Fundamentals of Operations Research. Prof. G. Srinivasan. Department of Management Studies. Indian Institute of Technology, Madras. Lecture No.
 Fundamentals of Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras Lecture No. # 13 Transportation Problem, Methods for Initial Basic Feasible
Fundamentals of Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras Lecture No. # 13 Transportation Problem, Methods for Initial Basic Feasible
Coarse-to-fine image registration
 Today we will look at a few important topics in scale space in computer vision, in particular, coarseto-fine approaches, and the SIFT feature descriptor. I will present only the main ideas here to give
Today we will look at a few important topics in scale space in computer vision, in particular, coarseto-fine approaches, and the SIFT feature descriptor. I will present only the main ideas here to give
Ryan Parsons Chad Price Jia Reese Alex Vassallo
 Ryan Parsons - Paper Prototype, Writing Chad Price - Paper Prototype, Digital Mockup Jia Reese - Paper Prototype, Usability Testing Alex Vassallo - Usability Testing, Writing All we have to decide is what
Ryan Parsons - Paper Prototype, Writing Chad Price - Paper Prototype, Digital Mockup Jia Reese - Paper Prototype, Usability Testing Alex Vassallo - Usability Testing, Writing All we have to decide is what
Developing a Network:
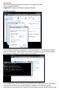 Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
FACE DETECTION AND RECOGNITION OF DRAWN CHARACTERS HERMAN CHAU
 FACE DETECTION AND RECOGNITION OF DRAWN CHARACTERS HERMAN CHAU 1. Introduction Face detection of human beings has garnered a lot of interest and research in recent years. There are quite a few relatively
FACE DETECTION AND RECOGNITION OF DRAWN CHARACTERS HERMAN CHAU 1. Introduction Face detection of human beings has garnered a lot of interest and research in recent years. There are quite a few relatively
HumanAUT Secure Human Identification Protocols
 HumanAUT Secure Human Identification Protocols Adam Bender Manuel Blum Nick Hopper The ALADDIN Center Carnegie Mellon University What is HumanAUT?! HumanAUT stands for Human AUThentication " Authentication:
HumanAUT Secure Human Identification Protocols Adam Bender Manuel Blum Nick Hopper The ALADDIN Center Carnegie Mellon University What is HumanAUT?! HumanAUT stands for Human AUThentication " Authentication:
Clustering algorithms and autoencoders for anomaly detection
 Clustering algorithms and autoencoders for anomaly detection Alessia Saggio Lunch Seminars and Journal Clubs Université catholique de Louvain, Belgium 3rd March 2017 a Outline Introduction Clustering algorithms
Clustering algorithms and autoencoders for anomaly detection Alessia Saggio Lunch Seminars and Journal Clubs Université catholique de Louvain, Belgium 3rd March 2017 a Outline Introduction Clustering algorithms
A Novel Approach to Image Segmentation for Traffic Sign Recognition Jon Jay Hack and Sidd Jagadish
 A Novel Approach to Image Segmentation for Traffic Sign Recognition Jon Jay Hack and Sidd Jagadish Introduction/Motivation: As autonomous vehicles, such as Google s self-driving car, have recently become
A Novel Approach to Image Segmentation for Traffic Sign Recognition Jon Jay Hack and Sidd Jagadish Introduction/Motivation: As autonomous vehicles, such as Google s self-driving car, have recently become
Graphical Passwords: Learning from the First Twelve Years
 Graphical Passwords: Learning from the First Twelve Years Robert Biddle, Sonia Chiasson, P.C. van Oorschot School of Computer Science Carleton University, Ottawa, Canada robert_biddle@carleton.ca, chiasson@scs.carleton.ca,
Graphical Passwords: Learning from the First Twelve Years Robert Biddle, Sonia Chiasson, P.C. van Oorschot School of Computer Science Carleton University, Ottawa, Canada robert_biddle@carleton.ca, chiasson@scs.carleton.ca,
Highly Secure Authentication Scheme: A Review
 e-issn: 2349-9745 p-issn: 2393-8161 Scientific Journal Impact Factor (SJIF): 1.711 International Journal of Modern Trends in Engineering and Research www.ijmter.com Highly Secure Authentication Scheme:
e-issn: 2349-9745 p-issn: 2393-8161 Scientific Journal Impact Factor (SJIF): 1.711 International Journal of Modern Trends in Engineering and Research www.ijmter.com Highly Secure Authentication Scheme:
Get Started in Web Conference Classes: During the Semester
 Get Started in Web Conference Classes: During the Semester Online classroom etiquette Log in to your WebEx class Change views, go full-screen Chat tool Class presentations Need help? 1-877-348-6503 or
Get Started in Web Conference Classes: During the Semester Online classroom etiquette Log in to your WebEx class Change views, go full-screen Chat tool Class presentations Need help? 1-877-348-6503 or
Cryptanalysis. Ed Crowley
 Cryptanalysis Ed Crowley 1 Topics Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types 2 Cryptanalysis Science of cracking ciphers and codes, decoding secrets,
Cryptanalysis Ed Crowley 1 Topics Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types 2 Cryptanalysis Science of cracking ciphers and codes, decoding secrets,
Graphical Authentication System
 Graphical Authentication System A Sivasankar Reddy 1, M Kusuma 2 1 Student, Dept. of MCA, EAIMS 2 Professor, Dept. of MCA, EAIMS, Tirupati, A.P. Abstract- This evolution brings great convenience but also
Graphical Authentication System A Sivasankar Reddy 1, M Kusuma 2 1 Student, Dept. of MCA, EAIMS 2 Professor, Dept. of MCA, EAIMS, Tirupati, A.P. Abstract- This evolution brings great convenience but also
Direct Variations DIRECT AND INVERSE VARIATIONS 19. Name
 DIRECT AND INVERSE VARIATIONS 19 Direct Variations Name Of the many relationships that two variables can have, one category is called a direct variation. Use the description and example of direct variation
DIRECT AND INVERSE VARIATIONS 19 Direct Variations Name Of the many relationships that two variables can have, one category is called a direct variation. Use the description and example of direct variation
Usable Privacy and Security Introduction to HCI Methods January 19, 2006 Jason Hong Notes By: Kami Vaniea
 Usable Privacy and Security Introduction to HCI Methods January 19, 2006 Jason Hong Notes By: Kami Vaniea Due Today: List of preferred lectures to present Due Next Week: IRB training completion certificate
Usable Privacy and Security Introduction to HCI Methods January 19, 2006 Jason Hong Notes By: Kami Vaniea Due Today: List of preferred lectures to present Due Next Week: IRB training completion certificate
Artificial Intelligence Introduction Handwriting Recognition Kadir Eren Unal ( ), Jakob Heyder ( )
 Structure: 1. Introduction 2. Problem 3. Neural network approach a. Architecture b. Phases of CNN c. Results 4. HTM approach a. Architecture b. Setup c. Results 5. Conclusion 1.) Introduction Artificial
Structure: 1. Introduction 2. Problem 3. Neural network approach a. Architecture b. Phases of CNN c. Results 4. HTM approach a. Architecture b. Setup c. Results 5. Conclusion 1.) Introduction Artificial
Final Review CMSC 733 Fall 2014
 Final Review CMSC 733 Fall 2014 We have covered a lot of material in this course. One way to organize this material is around a set of key equations and algorithms. You should be familiar with all of these,
Final Review CMSC 733 Fall 2014 We have covered a lot of material in this course. One way to organize this material is around a set of key equations and algorithms. You should be familiar with all of these,
The SD-WAN security guide
 The SD-WAN security guide How a flexible, software-defined WAN can help protect your network, people and data SD-WAN security: Separating fact from fiction For many companies, the benefits of SD-WAN are
The SD-WAN security guide How a flexible, software-defined WAN can help protect your network, people and data SD-WAN security: Separating fact from fiction For many companies, the benefits of SD-WAN are
Unit 21 - Creating a Navigation Bar in Macromedia Fireworks
 Unit 21 - Creating a Navigation Bar in Macromedia Fireworks Items needed to complete the Navigation Bar: Unit 21 - House Style Unit 21 - Graphics Sketch Diagrams Document ------------------------------------------------------------------------------------------------
Unit 21 - Creating a Navigation Bar in Macromedia Fireworks Items needed to complete the Navigation Bar: Unit 21 - House Style Unit 21 - Graphics Sketch Diagrams Document ------------------------------------------------------------------------------------------------
CSc 545 Lecture topic: The Criss-Cross method of Linear Programming
 CSc 545 Lecture topic: The Criss-Cross method of Linear Programming Wanda B. Boyer University of Victoria November 21, 2012 Presentation Outline 1 Outline 2 3 4 Please note: I would be extremely grateful
CSc 545 Lecture topic: The Criss-Cross method of Linear Programming Wanda B. Boyer University of Victoria November 21, 2012 Presentation Outline 1 Outline 2 3 4 Please note: I would be extremely grateful
Robust line segmentation for handwritten documents
 Robust line segmentation for handwritten documents Kamal Kuzhinjedathu, Harish Srinivasan and Sargur Srihari Center of Excellence for Document Analysis and Recognition (CEDAR) University at Buffalo, State
Robust line segmentation for handwritten documents Kamal Kuzhinjedathu, Harish Srinivasan and Sargur Srihari Center of Excellence for Document Analysis and Recognition (CEDAR) University at Buffalo, State
Crypto-systems all around us ATM machines Remote logins using SSH Web browsers (https invokes Secure Socket Layer (SSL))
 Introduction (Mihir Bellare Text/Notes: http://cseweb.ucsd.edu/users/mihir/cse207/) Cryptography provides: Data Privacy Data Integrity and Authenticity Crypto-systems all around us ATM machines Remote
Introduction (Mihir Bellare Text/Notes: http://cseweb.ucsd.edu/users/mihir/cse207/) Cryptography provides: Data Privacy Data Integrity and Authenticity Crypto-systems all around us ATM machines Remote
Digital Communication Prof. Bikash Kumar Dey Department of Electrical Engineering Indian Institute of Technology, Bombay
 Digital Communication Prof. Bikash Kumar Dey Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 26 Source Coding (Part 1) Hello everyone, we will start a new module today
Digital Communication Prof. Bikash Kumar Dey Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 26 Source Coding (Part 1) Hello everyone, we will start a new module today
An object in 3D space
 An object in 3D space An object's viewpoint Every Alice object has a viewpoint. The viewpoint of an object is determined by: The position of the object in 3D space. The orientation of the object relative
An object in 3D space An object's viewpoint Every Alice object has a viewpoint. The viewpoint of an object is determined by: The position of the object in 3D space. The orientation of the object relative
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
Graphical Password to Increase the Capacity of Alphanumeric Password
 Graphical Password to Increase the Capacity of Alphanumeric Password Gaddam Ramu Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer Science
Graphical Password to Increase the Capacity of Alphanumeric Password Gaddam Ramu Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer Science
1 Achieving IND-CPA security
 ISA 562: Information Security, Theory and Practice Lecture 2 1 Achieving IND-CPA security 1.1 Pseudorandom numbers, and stateful encryption As we saw last time, the OTP is perfectly secure, but it forces
ISA 562: Information Security, Theory and Practice Lecture 2 1 Achieving IND-CPA security 1.1 Pseudorandom numbers, and stateful encryption As we saw last time, the OTP is perfectly secure, but it forces
Making Tables and Figures
 Making Tables and Figures Don Quick Colorado State University Tables and figures are used in most fields of study to provide a visual presentation of important information to the reader. They are used
Making Tables and Figures Don Quick Colorado State University Tables and figures are used in most fields of study to provide a visual presentation of important information to the reader. They are used
Adobe Graphics Software
 Adobe Graphics Software Untitled-1.indd 1 20.11.2015 13:05:28 Untitled-1.indd 2 20.11.2015 13:05:28 3 Recent versions have brought in functionality for working with 3D designs, though the program still
Adobe Graphics Software Untitled-1.indd 1 20.11.2015 13:05:28 Untitled-1.indd 2 20.11.2015 13:05:28 3 Recent versions have brought in functionality for working with 3D designs, though the program still
Fundamentals of Operations Research. Prof. G. Srinivasan. Department of Management Studies. Indian Institute of Technology Madras.
 Fundamentals of Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology Madras Lecture No # 06 Simplex Algorithm Initialization and Iteration (Refer Slide
Fundamentals of Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology Madras Lecture No # 06 Simplex Algorithm Initialization and Iteration (Refer Slide
Exploring Fractals through Geometry and Algebra. Kelly Deckelman Ben Eggleston Laura Mckenzie Patricia Parker-Davis Deanna Voss
 Exploring Fractals through Geometry and Algebra Kelly Deckelman Ben Eggleston Laura Mckenzie Patricia Parker-Davis Deanna Voss Learning Objective and skills practiced Students will: Learn the three criteria
Exploring Fractals through Geometry and Algebra Kelly Deckelman Ben Eggleston Laura Mckenzie Patricia Parker-Davis Deanna Voss Learning Objective and skills practiced Students will: Learn the three criteria
Text and Lists Use Styles. What Are Styles?
 Creating Accessible Word Documents Using Microsoft Word 2003 Cassandra Tex, MBA Assistive Technology Specialist Student Disability Resource Center Humboldt State University Word documents are inherently
Creating Accessible Word Documents Using Microsoft Word 2003 Cassandra Tex, MBA Assistive Technology Specialist Student Disability Resource Center Humboldt State University Word documents are inherently
Admin. How's the project coming? After these slides, read chapter 13 in your book. Quizzes will return
 Recursion CS 1 Admin How's the project coming? After these slides, read chapter 13 in your book Yes that is out of order, but we can read it stand alone Quizzes will return Tuesday Nov 29 th see calendar
Recursion CS 1 Admin How's the project coming? After these slides, read chapter 13 in your book Yes that is out of order, but we can read it stand alone Quizzes will return Tuesday Nov 29 th see calendar
Graphical Password or Graphical User Authentication as Effective Password Provider
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 9 September 2013 Page No. 2765-2769 Graphical Password or Graphical User Authentication as Effective
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 9 September 2013 Page No. 2765-2769 Graphical Password or Graphical User Authentication as Effective
Innovative Graphical Passwords using Sequencing and Shuffling Together
 Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
How to use the Sales Based Availability Dashboard
 How to use the Sales Based Availability Dashboard Supplier Guide Sept 2017 v1 1 Contents What is Sales Based Availability and why is it important?... 3 How is Sales Based Availability calculated and how
How to use the Sales Based Availability Dashboard Supplier Guide Sept 2017 v1 1 Contents What is Sales Based Availability and why is it important?... 3 How is Sales Based Availability calculated and how
L E S S O N 2 Background
 Flight, Naperville Central High School, Naperville, Ill. No hard hat needed in the InDesign work area Once you learn the concepts of good page design, and you learn how to use InDesign, you are limited
Flight, Naperville Central High School, Naperville, Ill. No hard hat needed in the InDesign work area Once you learn the concepts of good page design, and you learn how to use InDesign, you are limited
Word: Print Address Labels Using Mail Merge
 Word: Print Address Labels Using Mail Merge No Typing! The Quick and Easy Way to Print Sheets of Address Labels Here at PC Knowledge for Seniors we re often asked how to print sticky address labels in
Word: Print Address Labels Using Mail Merge No Typing! The Quick and Easy Way to Print Sheets of Address Labels Here at PC Knowledge for Seniors we re often asked how to print sticky address labels in
Banking in QuickBooks Online
 QuickBooks Online Student Guide Chapter 6 Banking in QuickBooks Online Chapter 2 Chapter 6 The Banking page is where you connect your accounts and download transactions. This is sometimes known as bank
QuickBooks Online Student Guide Chapter 6 Banking in QuickBooks Online Chapter 2 Chapter 6 The Banking page is where you connect your accounts and download transactions. This is sometimes known as bank
Section 4 General Factorial Tutorials
 Section 4 General Factorial Tutorials General Factorial Part One: Categorical Introduction Design-Ease software version 6 offers a General Factorial option on the Factorial tab. If you completed the One
Section 4 General Factorial Tutorials General Factorial Part One: Categorical Introduction Design-Ease software version 6 offers a General Factorial option on the Factorial tab. If you completed the One
Tactile and Advanced Computer Graphics Module 7. Introduction to Illustrator
 Tactile and Advanced Computer Graphics Module 7 Introduction to Illustrator Module #7 Introduction to Illustrator Tactile and Advanced Computer Graphics Module 7 Introduction to Illustrator Summary Goal(s):
Tactile and Advanced Computer Graphics Module 7 Introduction to Illustrator Module #7 Introduction to Illustrator Tactile and Advanced Computer Graphics Module 7 Introduction to Illustrator Summary Goal(s):
Administrivia. Next Monday is Thanksgiving holiday. Tuesday and Wednesday the lab will be open for make-up labs. Lecture as usual on Thursday.
 Administrivia Next Monday is Thanksgiving holiday. Tuesday and Wednesday the lab will be open for make-up labs. Lecture as usual on Thursday. Lab notebooks will be due the week after Thanksgiving, when
Administrivia Next Monday is Thanksgiving holiday. Tuesday and Wednesday the lab will be open for make-up labs. Lecture as usual on Thursday. Lab notebooks will be due the week after Thanksgiving, when
CHAOS Chaos Chaos Iterate
 CHAOS Chaos is a program that explores data analysis. A sequence of points is created which can be analyzed via one of the following five modes: 1. Time Series Mode, which plots a time series graph, that
CHAOS Chaos is a program that explores data analysis. A sequence of points is created which can be analyzed via one of the following five modes: 1. Time Series Mode, which plots a time series graph, that
A Modified Approach to Biologically Motivated Saliency Mapping
 A Modified Approach to Biologically Motivated Saliency Mapping Shane Grant Department of Computer Science University of California, San Diego La Jolla, CA 9093 wgrant@ucsd.edu Kevin A Heins Department
A Modified Approach to Biologically Motivated Saliency Mapping Shane Grant Department of Computer Science University of California, San Diego La Jolla, CA 9093 wgrant@ucsd.edu Kevin A Heins Department
Outline 7/2/201011/6/
 Outline Pattern recognition in computer vision Background on the development of SIFT SIFT algorithm and some of its variations Computational considerations (SURF) Potential improvement Summary 01 2 Pattern
Outline Pattern recognition in computer vision Background on the development of SIFT SIFT algorithm and some of its variations Computational considerations (SURF) Potential improvement Summary 01 2 Pattern
Navigation and Metric Path Planning
 Navigation and Metric Path Planning October 4, 2011 Minerva tour guide robot (CMU): Gave tours in Smithsonian s National Museum of History Example of Minerva s occupancy map used for navigation Objectives
Navigation and Metric Path Planning October 4, 2011 Minerva tour guide robot (CMU): Gave tours in Smithsonian s National Museum of History Example of Minerva s occupancy map used for navigation Objectives
Adapted from: The Human Factor: Designing Computer Systems for People, Rubinstein & Hersh (1984) Designers make myths. Users make conceptual models.
 User Interface Guidelines UI Guidelines 1 Adapted from: The Human Factor: Designing Computer Systems for People, Rubinstein & Hersh (1984) Know your users - they are not you Designers make myths. Users
User Interface Guidelines UI Guidelines 1 Adapted from: The Human Factor: Designing Computer Systems for People, Rubinstein & Hersh (1984) Know your users - they are not you Designers make myths. Users
Evaluation of regions-of-interest based attention algorithms using a probabilistic measure
 Evaluation of regions-of-interest based attention algorithms using a probabilistic measure Martin Clauss, Pierre Bayerl and Heiko Neumann University of Ulm, Dept. of Neural Information Processing, 89081
Evaluation of regions-of-interest based attention algorithms using a probabilistic measure Martin Clauss, Pierre Bayerl and Heiko Neumann University of Ulm, Dept. of Neural Information Processing, 89081
Fundamentals of Website Development
 Fundamentals of Website Development CSC 2320, Fall 2015 The Department of Computer Science Chapter 4: Creating a Simple Page An introduction to (X)HTML elements and attributes A step-by-step demo for simple
Fundamentals of Website Development CSC 2320, Fall 2015 The Department of Computer Science Chapter 4: Creating a Simple Page An introduction to (X)HTML elements and attributes A step-by-step demo for simple
A Prehistory of Arithmetic
 A Prehistory of Arithmetic History and Philosophy of Mathematics MathFest August 8, 2015 Patricia Baggett Andrzej Ehrenfeucht Dept. of Math Sci. Computer Science Dept. New Mexico State Univ. University
A Prehistory of Arithmetic History and Philosophy of Mathematics MathFest August 8, 2015 Patricia Baggett Andrzej Ehrenfeucht Dept. of Math Sci. Computer Science Dept. New Mexico State Univ. University
A New Hybrid Graphical User Authentication Technique based on Drag and Drop Method
 A New Hybrid Graphical User Authentication Technique based on Drag and Drop Method Salim Istyaq, Khalid Saifullah Assistant Professor, Dept. of Computer Engineering, EES, University Polytechnic, Faculty
A New Hybrid Graphical User Authentication Technique based on Drag and Drop Method Salim Istyaq, Khalid Saifullah Assistant Professor, Dept. of Computer Engineering, EES, University Polytechnic, Faculty
Colin Paul Updated 14 November Preparation of publication-quality videos using ImageJ
 Preparation of publication-quality videos using ImageJ Statements made in scientific papers are often much easier to understand if they are supplemented by representative videos. In the best case, these
Preparation of publication-quality videos using ImageJ Statements made in scientific papers are often much easier to understand if they are supplemented by representative videos. In the best case, these
Advantage Plus QUICK START GUIDE
 Advantage Plus QUICK START GUIDE INSTALLATION and SETUP 1. Install Advantage Plus on your computer. By default it should install to c:\gh folder. Here is a direct link to that file on our web site. You
Advantage Plus QUICK START GUIDE INSTALLATION and SETUP 1. Install Advantage Plus on your computer. By default it should install to c:\gh folder. Here is a direct link to that file on our web site. You
Math 4. Class work 2. Algebra. Sets.
 Math 4. Class work 2. Algebra. Sets. I put a skirt, a book, a toothbrush, a coffee mug, and an apple into a bag. Can we call this collection of items a set? Do all these objects have something in common?
Math 4. Class work 2. Algebra. Sets. I put a skirt, a book, a toothbrush, a coffee mug, and an apple into a bag. Can we call this collection of items a set? Do all these objects have something in common?
What to come. There will be a few more topics we will cover on supervised learning
 Summary so far Supervised learning learn to predict Continuous target regression; Categorical target classification Linear Regression Classification Discriminative models Perceptron (linear) Logistic regression
Summary so far Supervised learning learn to predict Continuous target regression; Categorical target classification Linear Regression Classification Discriminative models Perceptron (linear) Logistic regression
(Refer Slide Time: 01.26)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture # 22 Why Sorting? Today we are going to be looking at sorting.
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture # 22 Why Sorting? Today we are going to be looking at sorting.
Three Types of Probability
 CHAPTER Three Types of Probability This article is not so much about particular problems or problem solving tactics as it is about labels. If you think about it, labels are a big key to the way we organize
CHAPTER Three Types of Probability This article is not so much about particular problems or problem solving tactics as it is about labels. If you think about it, labels are a big key to the way we organize
AP COMPUTER SCIENCE PRINCIPLES SCORING COMMENTARY: 2017 STUDENT SAMPLES ALIGNED TO THE 2018 SCORING GUIDELINES
 Sample: A Create Performance Task Row 3: 1 Row 6: 1 Row 7: 1 The video demonstrates how to log in, review, and add entries to the personal diary. The response indicates that keeping a personal diary is
Sample: A Create Performance Task Row 3: 1 Row 6: 1 Row 7: 1 The video demonstrates how to log in, review, and add entries to the personal diary. The response indicates that keeping a personal diary is
Cryptography ThreeB. Ed Crowley. Fall 08
 Cryptography ThreeB Ed Crowley Fall 08 Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types Cryptanalysis. Science of cracking ciphers and codes, decoding secrets,
Cryptography ThreeB Ed Crowley Fall 08 Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types Cryptanalysis. Science of cracking ciphers and codes, decoding secrets,
Edge Detection (with a sidelight introduction to linear, associative operators). Images
 Images (we will, eventually, come back to imaging geometry. But, now that we know how images come from the world, we will examine operations on images). Edge Detection (with a sidelight introduction to
Images (we will, eventually, come back to imaging geometry. But, now that we know how images come from the world, we will examine operations on images). Edge Detection (with a sidelight introduction to
Cache Timing Attacks on estream Finalists
 Cache Timing Attacks on estream Finalists Erik Zenner Technical University Denmark (DTU) Institute for Mathematics e.zenner@mat.dtu.dk Echternach, Jan. 9, 2008 Erik Zenner (DTU-MAT) Cache Timing Attacks
Cache Timing Attacks on estream Finalists Erik Zenner Technical University Denmark (DTU) Institute for Mathematics e.zenner@mat.dtu.dk Echternach, Jan. 9, 2008 Erik Zenner (DTU-MAT) Cache Timing Attacks
Deep Learning for Visual Computing Prof. Debdoot Sheet Department of Electrical Engineering Indian Institute of Technology, Kharagpur
 Deep Learning for Visual Computing Prof. Debdoot Sheet Department of Electrical Engineering Indian Institute of Technology, Kharagpur Lecture - 05 Classification with Perceptron Model So, welcome to today
Deep Learning for Visual Computing Prof. Debdoot Sheet Department of Electrical Engineering Indian Institute of Technology, Kharagpur Lecture - 05 Classification with Perceptron Model So, welcome to today
15 Data Compression 2014/9/21. Objectives After studying this chapter, the student should be able to: 15-1 LOSSLESS COMPRESSION
 15 Data Compression Data compression implies sending or storing a smaller number of bits. Although many methods are used for this purpose, in general these methods can be divided into two broad categories:
15 Data Compression Data compression implies sending or storing a smaller number of bits. Although many methods are used for this purpose, in general these methods can be divided into two broad categories:
Word Found Meaning Innovation
 AP CSP Quarter 1 Study Guide Vocabulary from Unit 1 & 3 Word Found Meaning Innovation A novel or improved idea, device, product, etc, or the development 1.1 thereof Binary 1.2 A way of representing information
AP CSP Quarter 1 Study Guide Vocabulary from Unit 1 & 3 Word Found Meaning Innovation A novel or improved idea, device, product, etc, or the development 1.1 thereof Binary 1.2 A way of representing information
Image Compression With Haar Discrete Wavelet Transform
 Image Compression With Haar Discrete Wavelet Transform Cory Cox ME 535: Computational Techniques in Mech. Eng. Figure 1 : An example of the 2D discrete wavelet transform that is used in JPEG2000. Source:
Image Compression With Haar Discrete Wavelet Transform Cory Cox ME 535: Computational Techniques in Mech. Eng. Figure 1 : An example of the 2D discrete wavelet transform that is used in JPEG2000. Source:
SFU CMPT week 11
 SFU CMPT-363 2004-2 week 11 Manuel Zahariev E-mail: manuelz@cs.sfu.ca Based on course material from Arthur Kirkpatrick, Alissa Antle and Paul Hibbits July 21, 2004 1 Analytic Methods Advantages can be
SFU CMPT-363 2004-2 week 11 Manuel Zahariev E-mail: manuelz@cs.sfu.ca Based on course material from Arthur Kirkpatrick, Alissa Antle and Paul Hibbits July 21, 2004 1 Analytic Methods Advantages can be
A Virtual Laboratory for Study of Algorithms
 A Virtual Laboratory for Study of Algorithms Thomas E. O'Neil and Scott Kerlin Computer Science Department University of North Dakota Grand Forks, ND 58202-9015 oneil@cs.und.edu Abstract Empirical studies
A Virtual Laboratory for Study of Algorithms Thomas E. O'Neil and Scott Kerlin Computer Science Department University of North Dakota Grand Forks, ND 58202-9015 oneil@cs.und.edu Abstract Empirical studies
Cursor Design Considerations For the Pointer-based Television
 Hillcrest Labs Design Note Cursor Design Considerations For the Pointer-based Television Designing the cursor for a pointing-based television must consider factors that differ from the implementation of
Hillcrest Labs Design Note Cursor Design Considerations For the Pointer-based Television Designing the cursor for a pointing-based television must consider factors that differ from the implementation of
Compressing Data. Konstantin Tretyakov
 Compressing Data Konstantin Tretyakov (kt@ut.ee) MTAT.03.238 Advanced April 26, 2012 Claude Elwood Shannon (1916-2001) C. E. Shannon. A mathematical theory of communication. 1948 C. E. Shannon. The mathematical
Compressing Data Konstantin Tretyakov (kt@ut.ee) MTAT.03.238 Advanced April 26, 2012 Claude Elwood Shannon (1916-2001) C. E. Shannon. A mathematical theory of communication. 1948 C. E. Shannon. The mathematical
Business Club. Decision Trees
 Business Club Decision Trees Business Club Analytics Team December 2017 Index 1. Motivation- A Case Study 2. The Trees a. What is a decision tree b. Representation 3. Regression v/s Classification 4. Building
Business Club Decision Trees Business Club Analytics Team December 2017 Index 1. Motivation- A Case Study 2. The Trees a. What is a decision tree b. Representation 3. Regression v/s Classification 4. Building
