Analysis Range-Free Node Location Algorithm in WSN
|
|
|
- Jasmin Barrett
- 5 years ago
- Views:
Transcription
1 International Conference on Education, Management and Computer Science (ICEMC 2016) Analysis Range-Free Node Location Algorithm in WSN Xiaojun Liu1, a and Jianyu Wang1 1 School of Transportation Huanggang Normal University, Hubei Huanggang, China a whutliuxiaojun@126.com Keywords: DV-HOP; Centroid; Amorphous; APIT; Convex optimization; MDS-MAP. Abstract. This paper firstly introduced the basic concept of node location algorithm in WSN, node location technology standard of performance evaluation. Then analyzed the localization process of the six range-free localization algorithms, performance, application scope and the problems. Finally, node density including network node and beacon node, positioning error and positioning precision were compared through the form. Introduction In the practical application of WSN, the sensor node location information has become one of the essential information in the whole network, many applications once lost the position information of nodes, the network will become useless, so the sensor network node location technology has become a important hot topic in the field of many scientists. There are many algorithms in the process of the realization of the positioning; according to different standards have different classified method. The classification of the most common is: Range-Based and Range-Free localization algorithm [1]. If localization algorithm needs to know the unknown node to the reference node or Beacon nodes the absolute distance between, then to calculate the unknown node coordinate information, such as locating methods can be called a Range - -based localization algorithm. On the other hand, the other algorithm without measuring the distance between the node value localization algorithms called Range - Free. Range-based on the precision of localization algorithm is superior to the Range - Free localization algorithm, but need to measure distance, relatively large amount of calculation, to spend a lot of energy, does not apply to low power consumption, low cost, and other areas of the application[2]. Range-Free localization algorithm because do not need to accurately measure the distance between nodes information, greatly reduces the requirement for the node hardware, and it is calculated using the estimated distance between nodes, so less affected by environment, in many of the node location accuracy requirements can be extensively used in WSN is not high. The Node Location Technology Performance Evaluation Standard In the wireless sensor network (WSN) positioning technology, different localization algorithm has different influence on positioning results, usually has the following several indicators to measure [3]: Positional Accuracy: position precision is refers to the spatial location information (usually the coordinates) proximity between its true location, it is a leading indicator of measuring sensor network localization, only reach a certain position precision of localization algorithm is real and effective. Effective Range of Orientation: positioning system can locate Effective range. To satisfy most of the nodes in WSN can be positioning, only covers a wide range of node location to be meaningful. Node Density: refers to the spread of sensor Node Density in terms of network nodes. In WSN node density had a great influence on the performance of the positioning, usually Node Density high positioning precision will be higher and higher, the opposite will reduce Positional Accuracy. In view of the different localization algorithm in WSN node density is not required for the same, the performance of the sensor nodes and the price also determines the node of the seeding density The authors - Published by Atlantis Press 718
2 Density of Beacon Node: Density of Beacon Node refers to the Beacon nodes in the proportion in the WSN. Beacon node has its own positioning function, the price is more expensive, could not sow large area, its node determines the positioning precision of the high and low density. Fault Tolerance and Adaptability: refers to the so-called fault-tolerance of the presence of Fault system will not fail, the characteristics of can still work normally. Fault Tolerance is Fault how should the Fault, to be exact and not let Error. Adaptability can be thought of as a can adjust itself according to environmental changes can intelligent features of feedback control system, so that the system can work in accordance with the standards of some setting in the optimal state. Security: Security is refers to the system to legitimate users of response and to resist the illegal request, to protect themselves from the external influence and the ability to attack. WSN usually work in the area of the physical environment is more complicated, positioning system vulnerable to environmental or man-made destruction and attacks, which cannot reach the ideal wireless communication environment to achieve the positioning of the effect, therefore must have a very strong security positioning system and algorithm. Power Dissipation: refers to the Power loss of Power consumption, Power consumption in the process of WSN design has always been one of the main aspects in its application. Limited due to the energy of the sensor nodes and it is not easy to get, so we need the whole WSN can with less energy consumption and high efficiency of energy utilization to implement security positioning is the first question faced by the current research. Cost and Consideration: the cost of location algorithm includes time cost, capital cost and space cost. Under the premise of ensuring the accuracy of positioning, the positioning system should be the minimum cost, such as the amount of computation required, the amount of communication, storage space, etc. The Main Range-Free Localization Algorithm Analysis Although positioning algorithm based on distance measurement can realize accurate positioning, but also often higher requirements for hardware, hardware cost increasing, is not conducive to the use of large area, in various fields, wide Angle. Without ranging localization algorithm is simple to use, only need to use the unknown node to estimate the distance between the reference node or other location information, and then use Trilateration or Maximum Likelihood Method to calculate the unknown node coordinate information. The existing positioning algorithm based on without range mainly include: DV - HOP algorithm, Centroid algorithm, amorphous algorithm, APIT algorithm, Convex Optimization algorithm and MDS-MAP algorithm [4-5], etc. DV-HOP Algorithm. DV-HOP algorithm does not require network nodes have distance function, which USES the average of the jump distance to represent the distance between the adjacent nodes, to calculate the actual distance, the coordinates are calculated by the trilateral measurement method. Algorithm of faults is to use the jump distance between the two nodes represent the actual linear distance will cause the error, the accuracy of positioning. Therefore, DV-HOP algorithm in the high density of nodes in the network can achieve high precision positioning, positioning accuracy is not ideal in sparse network. Centroid. Centroid refers to the physical system is considered to focus on the quality of an imaginary point. In sensor networks, the center of mass is to point to the center of the polygon, the polygons each vertex coordinates of the geometric average is the bar centric coordinates. Centroid algorithm is the University of Southern California's Nirupama Bulusu etc, the algorithm is suitable for outdoor positioning under the circumstance of high node density, and it is based on the network connectivity (Connectedness) implementation of node localization. Its basic idea is: the unknown nodes according to their own set of threshold method to receive the beacon nodes around the contains the node ID and position information to determine its area, according to its beacon node ID and position information received by the calculation area in the center of mass, and the area of the center of mass as its own positioning results. This algorithm is simple, the hardware requirements is low, don't 719
3 need any additional hardware devices, but in the process of positioning requires more beacon nodes, and the algorithm are assumed in the process of locating nodes with wireless signal transmission model of the ideal, this also has the very big difference with the actual situation, thus affecting the positioning precision of the Centroid. The basic principle of centroid is shown in Fig. 1. A 1 A 6 A2 (x,y) A 3 A 5 A 4 Figure 1. Diagram centroid algorithm In this algorithm, A 1 A 2 A 3 A 6 Six vertex coordinates are: ( x1, y 1), ( x2, y 2), ( x3, y 3), ( x4, y 4), ( x5, y 5) ( x 6, y 6 ),the area of the center of mass as follows: x1 x2 x3 x4 x5 x6 y1 y2 y3 y4 y5 y6 ( xy, ) (, ) (1) 6 6 Amorphous. Amorphous is based on the connectivity of the localization algorithm; it needs to know in advance the connectivity of the network. Algorithm implementation process, the unknown node first calculated with the minimum hop count between each beacon node; And then calculate the unknown node to jump distance of each beacon node, which assumes that the network node communication radius is the same; Finally re-use Trilateration or MLE algorithm for position calculation. Amorphous is easier to implement, but the positioning precision is not high, there are two significant drawbacks: one is the need to know in advance the network connectivity, the other is to be higher in the process of positioning the node density[6]. APIT (Approximate Point-in-Triangulation Test). APIT algorithm with higher positioning accuracy is adapted to the complex geographical environment. APIT localization algorithm of unknown nodes in the process of implementation, first of all, by collecting the neighbor node identifier, the location information, the information such as the size of the transmitting power to determine whether the node is located in the different of beacon nodes within the triangle, and then statistics include the unknown node triangle area, and the intersection of the triangle area constitutes a polygon, the polygons, largely determine the unknown node area and narrow the scope of unknown node, finally calculated the center of mass of the polygon area, and the center of mass as the location of the unknown node, thus realize the unknown node location. APIT localization algorithm basic principle is shown in Fig. 2. A 2 A 3 A 4 A 1 S A 5 A n A 6 Figure 2. Diagram of APIT principle 720
4 Convex Optimization Localization Algorithm. Convex Optimization is a kind of centralized positioning algorithm, the so-called centralized localization algorithm is relative to the case of a distributed localization algorithm, centralized positioning algorithm using concentrated thought, after collected all the sensor nodes effectively information unified positioning calculation, the extensibility of centralized localization algorithm is bad, signal transmission and processing more troublesome, will not be able to use flexible. Convex programming algorithm is shown in Fig. 3: Figure 3. Diagram of convex optimization principle The basic principle of unknown nodes according to the first communication radius and can communicate with the beacon node to establish its possible location area, when the exhaustion after these areas are filtered according to certain standards in these areas and position classification, finally determine a rectangle (as shown in Fig. 3 of the rectangular area of the shaded area), to calculate the mass center of the rectangle and place it as the coordinates of the unknown node, so as to realize the node localization. MDS-MAP Localization Algorithm. MDS - MAP belongs to the centralized positioning algorithm, it is to use the node connectivity information between nodes generated by Dijkstra or Floyd algorithm distance matrix, then using Shortest Path Algorithm to get the location information between nodes. MDS to MAP the realization of the localization algorithm mainly divides into the following three steps: (1) First of all, from the global perspective, according to the given node connectivity information between network topology connected graph is generated, and then through Shortest Path Algorithm to roughly estimate the distance between each pair of nodes, node distance matrix. (2) The classic multidimensional scaling analysis technology was applied to the node distance matrix, calculated the entire network of 2 d or 3 d relative coordinate system, the coordinates of the relative coordinates. (3) According to the position of the beacon node and beacon node of the node from the density of (2) the relative coordinate transformation, make it become the absolute coordinate system. MDS - MAP algorithms assume that are connected between each pair of nodes, when the nodes density is small [7], not only the node positioning error is very big, the outside also can lead to many nodes can't locate. Only the network connectivity to a certain extent, all of the unknown node can realize positioning. Generally adopts the algorithm for node coordinates for the relative position coordinates, transformed into absolute coordinates to matrix operation, the relative coordinates of unknown nodes in the two-dimensional space into absolute coordinates generally requires at least three beacon node for auxiliary operation, in the three-dimensional space requires at least four beacon nodes, so the algorithm calculation and energy consumption are generally bigger. All Range-Free Localization Algorithm Performance Comparison. Six range-free localization algorithms are compared in Table 1 721
5 Table 1 Comparison of range-free algorithm Name DV-HO P Centroid Amorph ous APIT Convex Optimiza MDS-M AP Density of Node Density of Beacon Node Need for additional devices Beacon node localization errors Positional Accuracy greater greater no good good greater greater no good general little greater yes general general greater little no good general little little no good better greater greater yes general good Summary Various localization algorithm has different application field, things are different for different localization algorithm to choose from, what kind of algorithm has no absolute advantage, in a certain occasion is applicable, but once application environment is changed, the performance of this algorithm is probably will change. In the specific application environment to consider the characteristics of the algorithm and the actual situation, to security and positioning of the various parameters. In addition, in different application should also consider the combined use of several kinds of algorithms, division for the same kind of environment, different areas for different localization algorithm, and then combine these algorithms, it is also one of the focuses of research in the future. References [1] ESTRIN D, GOVINDAN R, HEIDEMANN J. Next century challenges: scalable coordination in sensor networks [J]. Proceedings of the Fifth Annual International Conference on Mobile Computing and Networks (Mobi COM'99),Washington, USA, 1999: [2] AGRE J, CLARE L. An integrated architecture for cooperative sensing networks [J]. IEEE Computer Magazine, 2000, 33(5): [3] SAMI M L, JAMES M C. Time synchronization in wireless sensor networks: A survey[c]. IEEE Southeast Con 2010 (Southeast Con), [4] W.A Gardner, C. K Chen. Singal selective time difference of arrival estimation for Passive location. IEEE Transaction on Signal Processing, 2012, ~1184. [5] GÜ VENC I, CHONG C C. A survey on TOA based wireless localization and NLOS mitigation techniques [J]. IEEE Communications Surveys & Tutorials, 2009, 11(3): 107~123 [6] KANG HSEO G, LEE W J. Error compensation for css-based localization system[c]. Proceedings of the World Congress on Engineering and Computer Science, [7] ANDREAS L, CHRISTIAN W. A comprehensive approach for optimizing To A-localization in harsh industrial environments[c]. Position Location and Navigation Symposium (PLANS), 2010 IEEE/ION, ~
A New Distance Independent Localization Algorithm in Wireless Sensor Network
 A New Distance Independent Localization Algorithm in Wireless Sensor Network Siwei Peng 1, Jihui Li 2, Hui Liu 3 1 School of Information Science and Engineering, Yanshan University, Qinhuangdao 2 The Key
A New Distance Independent Localization Algorithm in Wireless Sensor Network Siwei Peng 1, Jihui Li 2, Hui Liu 3 1 School of Information Science and Engineering, Yanshan University, Qinhuangdao 2 The Key
Research on Relative Coordinate Localization of Nodes Based on Topology Control
 Journal of Information Hiding and Multimedia Signal Processing c 2018 ISSN 2073-4212 Ubiquitous International Volume 9, Number 2, March 2018 Research on Relative Coordinate Localization of Nodes Based
Journal of Information Hiding and Multimedia Signal Processing c 2018 ISSN 2073-4212 Ubiquitous International Volume 9, Number 2, March 2018 Research on Relative Coordinate Localization of Nodes Based
GIS based topology for wireless sensor network modeling: Arc-Node topology approach
 GIS based topology for wireless sensor network modeling: Arc-Node topology approach S.Amin Hosseini (Author) Zanjan Branch, Islamic Azad University, Zanjan,. Iran Email: s.a.hosseini86@gmail.com Behrooz
GIS based topology for wireless sensor network modeling: Arc-Node topology approach S.Amin Hosseini (Author) Zanjan Branch, Islamic Azad University, Zanjan,. Iran Email: s.a.hosseini86@gmail.com Behrooz
Face Recognition Technology Based On Image Processing Chen Xin, Yajuan Li, Zhimin Tian
 4th International Conference on Machinery, Materials and Computing Technology (ICMMCT 2016) Face Recognition Technology Based On Image Processing Chen Xin, Yajuan Li, Zhimin Tian Hebei Engineering and
4th International Conference on Machinery, Materials and Computing Technology (ICMMCT 2016) Face Recognition Technology Based On Image Processing Chen Xin, Yajuan Li, Zhimin Tian Hebei Engineering and
Lecture 8 Wireless Sensor Networks: Overview
 Lecture 8 Wireless Sensor Networks: Overview Reading: Wireless Sensor Networks, in Ad Hoc Wireless Networks: Architectures and Protocols, Chapter 12, sections 12.1-12.2. I. Akyildiz, W. Su, Y. Sankarasubramaniam
Lecture 8 Wireless Sensor Networks: Overview Reading: Wireless Sensor Networks, in Ad Hoc Wireless Networks: Architectures and Protocols, Chapter 12, sections 12.1-12.2. I. Akyildiz, W. Su, Y. Sankarasubramaniam
Convex Polygon Generation
 Convex Polygon Generation critterai.org /projects/nmgen_study/polygen.html This page describes the forth stage in building a navigation mesh, the generation of convex polygons from the simple polygons
Convex Polygon Generation critterai.org /projects/nmgen_study/polygen.html This page describes the forth stage in building a navigation mesh, the generation of convex polygons from the simple polygons
Discussion of GPON technology application in communication engineering Zhongbo Feng
 2nd International Conference on Electronics, Network and Computer Engineering (ICENCE 2016) Discussion of GPON technology application in communication engineering Zhongbo Feng School of Physics and Electronic
2nd International Conference on Electronics, Network and Computer Engineering (ICENCE 2016) Discussion of GPON technology application in communication engineering Zhongbo Feng School of Physics and Electronic
Hole repair algorithm in hybrid sensor networks
 Advances in Engineering Research (AER), volume 116 International Conference on Communication and Electronic Information Engineering (CEIE 2016) Hole repair algorithm in hybrid sensor networks Jian Liu1,
Advances in Engineering Research (AER), volume 116 International Conference on Communication and Electronic Information Engineering (CEIE 2016) Hole repair algorithm in hybrid sensor networks Jian Liu1,
Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks
 Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks Ayad Salhieh Department of Electrical and Computer Engineering Wayne State University Detroit, MI 48202 ai4874@wayne.edu Loren
Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks Ayad Salhieh Department of Electrical and Computer Engineering Wayne State University Detroit, MI 48202 ai4874@wayne.edu Loren
Prianka.P 1, Thenral 2
 An Efficient Routing Protocol design and Optimizing Sensor Coverage Area in Wireless Sensor Networks Prianka.P 1, Thenral 2 Department of Electronics Communication and Engineering, Ganadipathy Tulsi s
An Efficient Routing Protocol design and Optimizing Sensor Coverage Area in Wireless Sensor Networks Prianka.P 1, Thenral 2 Department of Electronics Communication and Engineering, Ganadipathy Tulsi s
Design and Implementation of Dual-Mode Wireless Video Monitoring System
 Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com Design and Implementation of Dual-Mode Wireless Video Monitoring System BAO Song-Jian, YANG Shou-Liang ChongQing University
Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com Design and Implementation of Dual-Mode Wireless Video Monitoring System BAO Song-Jian, YANG Shou-Liang ChongQing University
DETECTING WORMHOLE ATTACKS IN WIRELESS SENSOR NETWORKS
 Chapter 14 DETECTING WORMHOLE ATTACKS IN WIRELESS SENSOR NETWORKS Yurong Xu, Guanling Chen, James Ford and Fillia Makedon Abstract Wormhole attacks can destabilize or disable wireless sensor networks.
Chapter 14 DETECTING WORMHOLE ATTACKS IN WIRELESS SENSOR NETWORKS Yurong Xu, Guanling Chen, James Ford and Fillia Makedon Abstract Wormhole attacks can destabilize or disable wireless sensor networks.
An Energy Efficiency Routing Algorithm of Wireless Sensor Network Based on Round Model. Zhang Ying-Hui
 Joint International Mechanical, Electronic and Information Technology Conference (JIMET 2015) An Energy Efficiency Routing Algorithm of Wireless Sensor Network Based on Round Model Zhang Ying-Hui Software
Joint International Mechanical, Electronic and Information Technology Conference (JIMET 2015) An Energy Efficiency Routing Algorithm of Wireless Sensor Network Based on Round Model Zhang Ying-Hui Software
A Fault-recovery Routing Approach for Loop-based Clustering WSN
 A Fault-recovery Routing Approach for Loop-based Clustering WSN Ming Xu 1, Shengdong Zhang 1, Jiannong Cao 2, Xiaoxing Guo 3 ( 1 School of Computer, National Univ. of Defense Technology, Changsha, China)
A Fault-recovery Routing Approach for Loop-based Clustering WSN Ming Xu 1, Shengdong Zhang 1, Jiannong Cao 2, Xiaoxing Guo 3 ( 1 School of Computer, National Univ. of Defense Technology, Changsha, China)
Excavation Balance Routing Algorithm Simulation Based on Fuzzy Ant Colony
 2018 5th International Conference on Electrical & Electronics Engineering and Computer Science (ICEEECS 2018) Excavation Balance Routing Algorithm Simulation Based on Fuzzy Ant Colony Luo Xiaojuan, Yan
2018 5th International Conference on Electrical & Electronics Engineering and Computer Science (ICEEECS 2018) Excavation Balance Routing Algorithm Simulation Based on Fuzzy Ant Colony Luo Xiaojuan, Yan
Study on Delaunay Triangulation with the Islets Constraints
 Intelligent Information Management, 2010, 2, 375-379 doi:10.4236/iim.2010.26045 Published Online June 2010 (http://www.scirp.org/journal/iim) Study on Delaunay Triangulation with the Islets Constraints
Intelligent Information Management, 2010, 2, 375-379 doi:10.4236/iim.2010.26045 Published Online June 2010 (http://www.scirp.org/journal/iim) Study on Delaunay Triangulation with the Islets Constraints
WSN Routing Protocols
 WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
ROBOT MOTION USING DELAUNAY TRIANGULATION
 ROBOT MOTION USING DELAUNAY TRIANGULATION by Ioana-Maria Ileană Abstract. Robot motion is nowadays studied from a lot of different perspectives. This paper is based on the assumption of a fully known environment,
ROBOT MOTION USING DELAUNAY TRIANGULATION by Ioana-Maria Ileană Abstract. Robot motion is nowadays studied from a lot of different perspectives. This paper is based on the assumption of a fully known environment,
Time Synchronization in Wireless Sensor Networks: CCTS
 Time Synchronization in Wireless Sensor Networks: CCTS 1 Nerin Thomas, 2 Smita C Thomas 1, 2 M.G University, Mount Zion College of Engineering, Pathanamthitta, India Abstract: A time synchronization algorithm
Time Synchronization in Wireless Sensor Networks: CCTS 1 Nerin Thomas, 2 Smita C Thomas 1, 2 M.G University, Mount Zion College of Engineering, Pathanamthitta, India Abstract: A time synchronization algorithm
Application of Redundant Backup Technology in Network Security
 2018 2nd International Conference on Systems, Computing, and Applications (SYSTCA 2018) Application of Redundant Backup Technology in Network Security Shuwen Deng1, Siping Hu*, 1, Dianhua Wang1, Limin
2018 2nd International Conference on Systems, Computing, and Applications (SYSTCA 2018) Application of Redundant Backup Technology in Network Security Shuwen Deng1, Siping Hu*, 1, Dianhua Wang1, Limin
Energy Aware Node Placement Algorithm for Wireless Sensor Network
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 4, Number 6 (2014), pp. 541-548 Research India Publications http://www.ripublication.com/aeee.htm Energy Aware Node Placement Algorithm
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 4, Number 6 (2014), pp. 541-548 Research India Publications http://www.ripublication.com/aeee.htm Energy Aware Node Placement Algorithm
CSMA based Medium Access Control for Wireless Sensor Network
 CSMA based Medium Access Control for Wireless Sensor Network H. Hoang, Halmstad University Abstract Wireless sensor networks bring many challenges on implementation of Medium Access Control protocols because
CSMA based Medium Access Control for Wireless Sensor Network H. Hoang, Halmstad University Abstract Wireless sensor networks bring many challenges on implementation of Medium Access Control protocols because
Study on Wireless Sensor Networks Challenges and Routing Protocols
 International Research Journal of Applied and Basic Sciences 2013 Available online at www.irjabs.com ISSN 2251-838X / Vol, 5 (7): 824-828 Science Explorer Publications Study on Wireless Sensor Networks
International Research Journal of Applied and Basic Sciences 2013 Available online at www.irjabs.com ISSN 2251-838X / Vol, 5 (7): 824-828 Science Explorer Publications Study on Wireless Sensor Networks
A Feedback-based Multipath Approach for Secure Data Collection in. Wireless Sensor Network.
 A Feedback-based Multipath Approach for Secure Data Collection in Wireless Sensor Networks Yuxin Mao School of Computer and Information Engineering, Zhejiang Gongshang University, Hangzhou 310018, P.R
A Feedback-based Multipath Approach for Secure Data Collection in Wireless Sensor Networks Yuxin Mao School of Computer and Information Engineering, Zhejiang Gongshang University, Hangzhou 310018, P.R
Research on Transmission Based on Collaboration Coding in WSNs
 Research on Transmission Based on Collaboration Coding in WSNs LV Xiao-xing, ZHANG Bai-hai School of Automation Beijing Institute of Technology Beijing 8, China lvxx@mail.btvu.org Journal of Digital Information
Research on Transmission Based on Collaboration Coding in WSNs LV Xiao-xing, ZHANG Bai-hai School of Automation Beijing Institute of Technology Beijing 8, China lvxx@mail.btvu.org Journal of Digital Information
Mobile Positioning System Based on the Wireless Sensor Network in Buildings
 Communications and Network, 2009, 1, 96-100 doi:10.4236/cn.2009.12015 Published Online November 2009 (http://www.scirp.org/journal/cn). Mobile Positioning System Based on the Wireless Sensor Network in
Communications and Network, 2009, 1, 96-100 doi:10.4236/cn.2009.12015 Published Online November 2009 (http://www.scirp.org/journal/cn). Mobile Positioning System Based on the Wireless Sensor Network in
A METHOD FOR DETECTING FALSE POSITIVE AND FALSE NEGATIVE ATTACKS USING SIMULATION MODELS IN STATISTICAL EN- ROUTE FILTERING BASED WSNS
 A METHOD FOR DETECTING FALSE POSITIVE AND FALSE NEGATIVE ATTACKS USING SIMULATION MODELS IN STATISTICAL EN- ROUTE FILTERING BASED WSNS Su Man Nam 1 and Tae Ho Cho 2 1 College of Information and Communication
A METHOD FOR DETECTING FALSE POSITIVE AND FALSE NEGATIVE ATTACKS USING SIMULATION MODELS IN STATISTICAL EN- ROUTE FILTERING BASED WSNS Su Man Nam 1 and Tae Ho Cho 2 1 College of Information and Communication
A Kind of Wireless Sensor Network Coverage Optimization Algorithm Based on Genetic PSO
 Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com A Kind of Wireless Sensor Network Coverage Optimization Algorithm Based on Genetic PSO Yinghui HUANG School of Electronics and Information,
Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com A Kind of Wireless Sensor Network Coverage Optimization Algorithm Based on Genetic PSO Yinghui HUANG School of Electronics and Information,
Data-Centric Routing Mechanism Using Hash-Value in Wireless Sensor Network
 Wireless Sensor Network, 2010, 2, 710-717 doi:10.4236/wsn.2010.29086 Published Online September 2010 (http://www.scirp.org/journal/wsn) Data-Centric Routing Mechanism Using Hash-Value in Wireless Sensor
Wireless Sensor Network, 2010, 2, 710-717 doi:10.4236/wsn.2010.29086 Published Online September 2010 (http://www.scirp.org/journal/wsn) Data-Centric Routing Mechanism Using Hash-Value in Wireless Sensor
A Data Classification Algorithm of Internet of Things Based on Neural Network
 A Data Classification Algorithm of Internet of Things Based on Neural Network https://doi.org/10.3991/ijoe.v13i09.7587 Zhenjun Li Hunan Radio and TV University, Hunan, China 278060389@qq.com Abstract To
A Data Classification Algorithm of Internet of Things Based on Neural Network https://doi.org/10.3991/ijoe.v13i09.7587 Zhenjun Li Hunan Radio and TV University, Hunan, China 278060389@qq.com Abstract To
Wireless Sensor Networks Localization Methods: Multidimensional Scaling vs. Semidefinite Programming Approach
 Wireless Sensor Networks Localization Methods: Multidimensional Scaling vs. Semidefinite Programming Approach Biljana Stojkoska, Ilinka Ivanoska, Danco Davcev, 1 Faculty of Electrical Engineering and Information
Wireless Sensor Networks Localization Methods: Multidimensional Scaling vs. Semidefinite Programming Approach Biljana Stojkoska, Ilinka Ivanoska, Danco Davcev, 1 Faculty of Electrical Engineering and Information
Model the P2P Attack in Computer Networks
 International Conference on Logistics Engineering, Management and Computer Science (LEMCS 2015) Model the P2P Attack in Computer Networks Wei Wang * Science and Technology on Communication Information
International Conference on Logistics Engineering, Management and Computer Science (LEMCS 2015) Model the P2P Attack in Computer Networks Wei Wang * Science and Technology on Communication Information
DIAL: A Distributed Adaptive-Learning Routing Method in VDTNs
 : A Distributed Adaptive-Learning Routing Method in VDTNs Bo Wu, Haiying Shen and Kang Chen Department of Electrical and Computer Engineering Clemson University, Clemson, South Carolina 29634 {bwu2, shenh,
: A Distributed Adaptive-Learning Routing Method in VDTNs Bo Wu, Haiying Shen and Kang Chen Department of Electrical and Computer Engineering Clemson University, Clemson, South Carolina 29634 {bwu2, shenh,
A Multipath AODV Reliable Data Transmission Routing Algorithm Based on LQI
 Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com A Multipath AODV Reliable Data Transmission Routing Algorithm Based on LQI 1 Yongxian SONG, 2 Rongbiao ZHANG and Fuhuan
Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com A Multipath AODV Reliable Data Transmission Routing Algorithm Based on LQI 1 Yongxian SONG, 2 Rongbiao ZHANG and Fuhuan
Dual and Mixture Monte Carlo Localization Algorithms for Mobile Wireless Sensor Networks
 Dual and Mixture Monte Carlo Localization Algorithms for Mobile Wireless Sensor Networks Enrique Stevens-Navarro, Vijayanth Vivekanandan, and Vincent W.S. Wong Department of Electrical and Computer Engineering
Dual and Mixture Monte Carlo Localization Algorithms for Mobile Wireless Sensor Networks Enrique Stevens-Navarro, Vijayanth Vivekanandan, and Vincent W.S. Wong Department of Electrical and Computer Engineering
FACET SHIFT ALGORITHM BASED ON MINIMAL DISTANCE IN SIMPLIFICATION OF BUILDINGS WITH PARALLEL STRUCTURE
 FACET SHIFT ALGORITHM BASED ON MINIMAL DISTANCE IN SIMPLIFICATION OF BUILDINGS WITH PARALLEL STRUCTURE GE Lei, WU Fang, QIAN Haizhong, ZHAI Renjian Institute of Surveying and Mapping Information Engineering
FACET SHIFT ALGORITHM BASED ON MINIMAL DISTANCE IN SIMPLIFICATION OF BUILDINGS WITH PARALLEL STRUCTURE GE Lei, WU Fang, QIAN Haizhong, ZHAI Renjian Institute of Surveying and Mapping Information Engineering
Yunfeng Zhang 1, Huan Wang 2, Jie Zhu 1 1 Computer Science & Engineering Department, North China Institute of Aerospace
 [Type text] [Type text] [Type text] ISSN : 0974-7435 Volume 10 Issue 20 BioTechnology 2014 An Indian Journal FULL PAPER BTAIJ, 10(20), 2014 [12526-12531] Exploration on the data mining system construction
[Type text] [Type text] [Type text] ISSN : 0974-7435 Volume 10 Issue 20 BioTechnology 2014 An Indian Journal FULL PAPER BTAIJ, 10(20), 2014 [12526-12531] Exploration on the data mining system construction
A Real-Time Directed Routing Protocol Based on Projection of Convex Holes on Underwater Acoustic Networks
 I.J. Wireless and Microwave Technologies, 01,, 65-73 Published Online April 01 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.01.0.10 Available online at http://www.mecs-press.net/ijwmt A Real-Time
I.J. Wireless and Microwave Technologies, 01,, 65-73 Published Online April 01 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.01.0.10 Available online at http://www.mecs-press.net/ijwmt A Real-Time
Nodes Energy Conserving Algorithms to prevent Partitioning in Wireless Sensor Networks
 IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.9, September 2017 139 Nodes Energy Conserving Algorithms to prevent Partitioning in Wireless Sensor Networks MINA MAHDAVI
IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.9, September 2017 139 Nodes Energy Conserving Algorithms to prevent Partitioning in Wireless Sensor Networks MINA MAHDAVI
Chongqing, China. *Corresponding author. Keywords: Wireless body area network, Privacy protection, Data aggregation.
 2016 International Conference on Computer, Mechatronics and Electronic Engineering (CMEE 2016) ISBN: 978-1-60595-406-6 The Data Aggregation Privacy Protection Algorithm of Body Area Network Based on Data
2016 International Conference on Computer, Mechatronics and Electronic Engineering (CMEE 2016) ISBN: 978-1-60595-406-6 The Data Aggregation Privacy Protection Algorithm of Body Area Network Based on Data
Study of Smart Home System based on Zigbee Wireless Sensor System. Jie Huang 1
 2nd Workshop on Advanced Research and Technology in Industry Applications (WARTIA 2016) Study of Smart Home System based on Zigbee Wireless Sensor System Jie Huang 1 1 College of Mechanical and Electronic
2nd Workshop on Advanced Research and Technology in Industry Applications (WARTIA 2016) Study of Smart Home System based on Zigbee Wireless Sensor System Jie Huang 1 1 College of Mechanical and Electronic
Enhancement of Routing in Urban Scenario using Link State Routing Protocol and Firefly Optimization
 Enhancement of Routing in Urban Scenario using Link State Routing Protocol and Firefly Optimization Dhanveer Kaur 1, Harwant Singh Arri 2 1 M.Tech, Department of Computer Science and Engineering, Lovely
Enhancement of Routing in Urban Scenario using Link State Routing Protocol and Firefly Optimization Dhanveer Kaur 1, Harwant Singh Arri 2 1 M.Tech, Department of Computer Science and Engineering, Lovely
Half-edge Collapse Simplification Algorithm Based on Angle Feature
 International Conference on Automation, Mechanical Control and Computational Engineering (AMCCE 2015) Half-edge Collapse Simplification Algorithm Based on Angle Feature 1,2 JunFeng Li, 2 YongBo Chen, 3
International Conference on Automation, Mechanical Control and Computational Engineering (AMCCE 2015) Half-edge Collapse Simplification Algorithm Based on Angle Feature 1,2 JunFeng Li, 2 YongBo Chen, 3
Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization
 Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization Maurizio Bocca, M.Sc. Control Engineering Research Group Automation and Systems Technology Department maurizio.bocca@tkk.fi
Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization Maurizio Bocca, M.Sc. Control Engineering Research Group Automation and Systems Technology Department maurizio.bocca@tkk.fi
An Optimal Method to Design Wireless Sensor Network Structures
 An Optimal Method to Design Wireless Sensor Network Structures https://doi.org/10.3991/ijoe.v14i01.8062 Ling Yang!! ", Xucan Cai, Chunlin Wu Zhongkai University of Agriculture and Engineering, Guangzhou,
An Optimal Method to Design Wireless Sensor Network Structures https://doi.org/10.3991/ijoe.v14i01.8062 Ling Yang!! ", Xucan Cai, Chunlin Wu Zhongkai University of Agriculture and Engineering, Guangzhou,
A Novel Image Super-resolution Reconstruction Algorithm based on Modified Sparse Representation
 , pp.162-167 http://dx.doi.org/10.14257/astl.2016.138.33 A Novel Image Super-resolution Reconstruction Algorithm based on Modified Sparse Representation Liqiang Hu, Chaofeng He Shijiazhuang Tiedao University,
, pp.162-167 http://dx.doi.org/10.14257/astl.2016.138.33 A Novel Image Super-resolution Reconstruction Algorithm based on Modified Sparse Representation Liqiang Hu, Chaofeng He Shijiazhuang Tiedao University,
Hole Detection and Boundary Recognition in Wireless Sensor Networks
 Hole Detection and Boundary Recognition in Wireless Sensor Networks Kun-Ying Hsieh Dept. of Computer Science and Information Engineering National Central University Jhongli, 32054, Taiwan E-mail: rocky@axp1.csie.ncu.edu.tw
Hole Detection and Boundary Recognition in Wireless Sensor Networks Kun-Ying Hsieh Dept. of Computer Science and Information Engineering National Central University Jhongli, 32054, Taiwan E-mail: rocky@axp1.csie.ncu.edu.tw
Research on Intrusion Detection Algorithm Based on Multi-Class SVM in Wireless Sensor Networks
 Communications and Network, 2013, 5, 524-528 http://dx.doi.org/10.4236/cn.2013.53b2096 Published Online September 2013 (http://www.scirp.org/journal/cn) Research on Intrusion Detection Algorithm Based
Communications and Network, 2013, 5, 524-528 http://dx.doi.org/10.4236/cn.2013.53b2096 Published Online September 2013 (http://www.scirp.org/journal/cn) Research on Intrusion Detection Algorithm Based
Research on Parallelized Stream Data Micro Clustering Algorithm Ke Ma 1, Lingjuan Li 1, Yimu Ji 1, Shengmei Luo 1, Tao Wen 2
 International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2015) Research on Parallelized Stream Data Micro Clustering Algorithm Ke Ma 1, Lingjuan Li 1, Yimu Ji 1,
International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2015) Research on Parallelized Stream Data Micro Clustering Algorithm Ke Ma 1, Lingjuan Li 1, Yimu Ji 1,
PROJECT REPORT VIRTUAL COORDINATE GENERATOR AND ROUTING SIMULATION TOOL FOR WIRELESS SENSOR NETWORKS IN 2 AND 3-DIMENSIONAL NETWORK SPACE
 PROJECT REPORT VIRTUAL COORDINATE GENERATOR AND ROUTING SIMULATION TOOL FOR WIRELESS SENSOR NETWORKS IN 2 AND 3-DIMENSIONAL NETWORK SPACE Submitted by Aravindhan Vijayaraj Department of Electrical and
PROJECT REPORT VIRTUAL COORDINATE GENERATOR AND ROUTING SIMULATION TOOL FOR WIRELESS SENSOR NETWORKS IN 2 AND 3-DIMENSIONAL NETWORK SPACE Submitted by Aravindhan Vijayaraj Department of Electrical and
Application of Theory and Technology of Wireless Sensor Network System for Soil Environmental Monitoring
 Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com Application of Theory and Technology of Wireless Sensor Network System for Soil Environmental Monitoring 1,2,3 Xu Xi, 3 Xiaoyao Xie, 4 Zhang
Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com Application of Theory and Technology of Wireless Sensor Network System for Soil Environmental Monitoring 1,2,3 Xu Xi, 3 Xiaoyao Xie, 4 Zhang
One Kind of Redundant Reliability Wireless from Network Algorithm Research Based on Advanced Version DV-HOP Route Agreement
 Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com One Kind of Redundant Reliability Wireless from Network Algorithm Research Based on Advanced Version DV-HOP Route Agreement Jiuhua ZHANG
Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com One Kind of Redundant Reliability Wireless from Network Algorithm Research Based on Advanced Version DV-HOP Route Agreement Jiuhua ZHANG
Using Consensus Estimate Technique Aimed To Reducing Energy Consumption and Coverage Improvement in Wireless Sensor Networks
 IJCSNS International Journal of Computer Science and Network Security, VOL.16 No.8, August 2016 1 Using Consensus Estimate Technique Aimed To Reducing Energy Consumption and Coverage Improvement in Wireless
IJCSNS International Journal of Computer Science and Network Security, VOL.16 No.8, August 2016 1 Using Consensus Estimate Technique Aimed To Reducing Energy Consumption and Coverage Improvement in Wireless
Multisource Remote Sensing Data Mining System Construction in Cloud Computing Environment Dong YinDi 1, Liu ChengJun 1
 4th International Conference on Computer, Mechatronics, Control and Electronic Engineering (ICCMCEE 2015) Multisource Remote Sensing Data Mining System Construction in Cloud Computing Environment Dong
4th International Conference on Computer, Mechatronics, Control and Electronic Engineering (ICCMCEE 2015) Multisource Remote Sensing Data Mining System Construction in Cloud Computing Environment Dong
Shortest Path Position Estimation between Source and Destination nodes in Wireless Sensor Networks with Low Cost.
 Shortest Path Position Estimation between Source and Destination nodes in Wireless Sensor Networks with Low Cost. N. Pushpalatha 1, Dr.B.Anuradha, 1 Assistant Professor, Department of ECE, AITS, Tirupathi
Shortest Path Position Estimation between Source and Destination nodes in Wireless Sensor Networks with Low Cost. N. Pushpalatha 1, Dr.B.Anuradha, 1 Assistant Professor, Department of ECE, AITS, Tirupathi
A Localization Scheme of Wireless Sensor Networks Based on Small
 A Localization Scheme of Wireless Sensor Networks Based on Small World Effects Nan Jiang, 2 Xiao xiang, 3 Chen Huan * East China Jiao Tong University, jiangnan8@gmail.com 2 East China Jiao Tong University,
A Localization Scheme of Wireless Sensor Networks Based on Small World Effects Nan Jiang, 2 Xiao xiang, 3 Chen Huan * East China Jiao Tong University, jiangnan8@gmail.com 2 East China Jiao Tong University,
An efficient implementation of the greedy forwarding strategy
 An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
Related Work The Concept of the Signaling. In the mobile communication system, in addition to transmit the necessary user information (usually voice
 International Conference on Information Science and Computer Applications (ISCA 2013) The Research and Design of Personalization preferences Based on Signaling analysis ZhiQiang Wei 1,a, YiYan Zhang 1,b,
International Conference on Information Science and Computer Applications (ISCA 2013) The Research and Design of Personalization preferences Based on Signaling analysis ZhiQiang Wei 1,a, YiYan Zhang 1,b,
Link-Based Wormhole Detection in Wireless Sensor Networks
 Link-Based Wormhole Detection in Wireless Sensor Networks Xiaoyuan Zhou, Lijun Chen National Key Laboratory for Novel Software Technology Nanjing University Nanjing, P.R. China, 2123 zxy@smail.nju.edu.cn,
Link-Based Wormhole Detection in Wireless Sensor Networks Xiaoyuan Zhou, Lijun Chen National Key Laboratory for Novel Software Technology Nanjing University Nanjing, P.R. China, 2123 zxy@smail.nju.edu.cn,
An Integrated Framework for Wireless Sensor Network Management
 An Integrated Framework for Wireless Sensor Network Management by Lutful Karim A Thesis presented to The University of Guelph In partial fulfilment of requirements for the degree of Doctor of Philosophy
An Integrated Framework for Wireless Sensor Network Management by Lutful Karim A Thesis presented to The University of Guelph In partial fulfilment of requirements for the degree of Doctor of Philosophy
Rumor Routing Algorithm
 Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
1 Q1. Attempt any THREE 09 1 Give the difference between Human Network and
 Sanjivani Rural Education Society s CLASS-TEST-I YEAR:- 2015-16 SANJIVANI K.B.P.POLYTECHNIC, KOPARGAON Model Answer Sub:- Computer Network Sub. Code:- 17429 Class :- Div:- A & B SYCM Dept. :- Computer
Sanjivani Rural Education Society s CLASS-TEST-I YEAR:- 2015-16 SANJIVANI K.B.P.POLYTECHNIC, KOPARGAON Model Answer Sub:- Computer Network Sub. Code:- 17429 Class :- Div:- A & B SYCM Dept. :- Computer
An Efficient Hybrid Localization Technique in Wireless Sensor Networks Deepali Virmani 1, Satbir Jain 2
 An Efficient Hybrid Localization Technique in Wireless Sensor Networks Deepali Virmani 1, Satbir Jain 2 1 Department of CSE 2 Department of CSE BPIT, GGSIPU NSIT, Dwarka Delhi, India. Delhi, India. deepalivirmani@gmail.com
An Efficient Hybrid Localization Technique in Wireless Sensor Networks Deepali Virmani 1, Satbir Jain 2 1 Department of CSE 2 Department of CSE BPIT, GGSIPU NSIT, Dwarka Delhi, India. Delhi, India. deepalivirmani@gmail.com
Dynamic Obstacle Detection Based on Background Compensation in Robot s Movement Space
 MATEC Web of Conferences 95 83 (7) DOI:.5/ matecconf/79583 ICMME 6 Dynamic Obstacle Detection Based on Background Compensation in Robot s Movement Space Tao Ni Qidong Li Le Sun and Lingtao Huang School
MATEC Web of Conferences 95 83 (7) DOI:.5/ matecconf/79583 ICMME 6 Dynamic Obstacle Detection Based on Background Compensation in Robot s Movement Space Tao Ni Qidong Li Le Sun and Lingtao Huang School
An Improved DV-Hop Algorithm for Resisting Wormhole Attack
 Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 2015, 9, 1443-1448 1443 Open Access An Improved DV-Hop Algorithm for Resisting Wormhole Attack Xiaoying
Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 2015, 9, 1443-1448 1443 Open Access An Improved DV-Hop Algorithm for Resisting Wormhole Attack Xiaoying
Application of Geometry Rectification to Deformed Characters Recognition Liqun Wang1, a * and Honghui Fan2
 6th International Conference on Electronic, Mechanical, Information and Management (EMIM 2016) Application of Geometry Rectification to Deformed Characters Liqun Wang1, a * and Honghui Fan2 1 School of
6th International Conference on Electronic, Mechanical, Information and Management (EMIM 2016) Application of Geometry Rectification to Deformed Characters Liqun Wang1, a * and Honghui Fan2 1 School of
Advanced Topics on Wireless Ad Hoc Networks. Lecture 4: Energy-aware Routing Algorithms
 Advanced Topics on Wireless Ad Hoc Networks Lecture 4: Energy-aware Routing Algorithms Sotiris Nikoletseas Professor CEID - ETY Course 2017-2018 Sotiris Nikoletseas, Professor Efficient Data propagation
Advanced Topics on Wireless Ad Hoc Networks Lecture 4: Energy-aware Routing Algorithms Sotiris Nikoletseas Professor CEID - ETY Course 2017-2018 Sotiris Nikoletseas, Professor Efficient Data propagation
M. Andrea Rodríguez-Tastets. I Semester 2008
 M. -Tastets Universidad de Concepción,Chile andrea@udec.cl I Semester 2008 Outline refers to data with a location on the Earth s surface. Examples Census data Administrative boundaries of a country, state
M. -Tastets Universidad de Concepción,Chile andrea@udec.cl I Semester 2008 Outline refers to data with a location on the Earth s surface. Examples Census data Administrative boundaries of a country, state
Mobile Agent Driven Time Synchronized Energy Efficient WSN
 Mobile Agent Driven Time Synchronized Energy Efficient WSN Sharanu 1, Padmapriya Patil 2 1 M.Tech, Department of Electronics and Communication Engineering, Poojya Doddappa Appa College of Engineering,
Mobile Agent Driven Time Synchronized Energy Efficient WSN Sharanu 1, Padmapriya Patil 2 1 M.Tech, Department of Electronics and Communication Engineering, Poojya Doddappa Appa College of Engineering,
Research on Extension of SPARQL Ontology Query Language Considering the Computation of Indoor Spatial Relations
 The International Archives of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Volume XL-4/W5, 2015 Research on Extension of SPARQL Ontology Query Language Considering the Computation
The International Archives of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Volume XL-4/W5, 2015 Research on Extension of SPARQL Ontology Query Language Considering the Computation
Improvement of SURF Feature Image Registration Algorithm Based on Cluster Analysis
 Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com Improvement of SURF Feature Image Registration Algorithm Based on Cluster Analysis 1 Xulin LONG, 1,* Qiang CHEN, 2 Xiaoya
Sensors & Transducers 2014 by IFSA Publishing, S. L. http://www.sensorsportal.com Improvement of SURF Feature Image Registration Algorithm Based on Cluster Analysis 1 Xulin LONG, 1,* Qiang CHEN, 2 Xiaoya
Design of Wireless Sensing Virtual Cloud Desktop System Based on ARM-Linux
 Design of Wireless Sensing Virtual Cloud Desktop System Based on ARM-Linux https://doi.org/10.3991/ijoe.v13i10.7743 Chunqing Han!! ", Lin Li Binzhou Tobacco Monopoly Bureau, Shandong, China hanchunqing0807@163.com
Design of Wireless Sensing Virtual Cloud Desktop System Based on ARM-Linux https://doi.org/10.3991/ijoe.v13i10.7743 Chunqing Han!! ", Lin Li Binzhou Tobacco Monopoly Bureau, Shandong, China hanchunqing0807@163.com
Open Access Algorithm of Context Inconsistency Elimination Based on Feedback Windowing and Evidence Theory for Smart Home
 Send Orders for Reprints to reprints@benthamscience.ae The Open Automation and Control Systems Journal, 2014, 6, 637-648 637 Open Access Algorithm of Context Inconsistency Elimination Based on Feedback
Send Orders for Reprints to reprints@benthamscience.ae The Open Automation and Control Systems Journal, 2014, 6, 637-648 637 Open Access Algorithm of Context Inconsistency Elimination Based on Feedback
A Logical Group Formation and Management Mechanism Using RSSI for Wireless Sensor Networks *
 A Logical Group Formation and Management Mechanism Using RSSI for Wireless Sensor Networks * Jihyuk Heo, Jin Ho Kim, and Choong Seon Hong ** Department of Computer Engineering, Kyung Hee University, Sochen-ri,
A Logical Group Formation and Management Mechanism Using RSSI for Wireless Sensor Networks * Jihyuk Heo, Jin Ho Kim, and Choong Seon Hong ** Department of Computer Engineering, Kyung Hee University, Sochen-ri,
Dijkstra's Algorithm
 Shortest Path Algorithm Dijkstra's Algorithm To find the shortest path from the origin node to the destination node No matrix calculation Floyd s Algorithm To find all the shortest paths from the nodes
Shortest Path Algorithm Dijkstra's Algorithm To find the shortest path from the origin node to the destination node No matrix calculation Floyd s Algorithm To find all the shortest paths from the nodes
Energy Optimized Routing Algorithm in Multi-sink Wireless Sensor Networks
 Appl. Math. Inf. Sci. 8, No. 1L, 349-354 (2014) 349 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.12785/amis/081l44 Energy Optimized Routing Algorithm in Multi-sink
Appl. Math. Inf. Sci. 8, No. 1L, 349-354 (2014) 349 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.12785/amis/081l44 Energy Optimized Routing Algorithm in Multi-sink
ZigBee Routing Algorithm Based on Energy Optimization
 Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com ZigBee Routing Algorithm Based on Energy Optimization Wangang Wang, Yong Peng, Yongyu Peng Chongqing City Management College, No. 151 Daxuecheng
Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com ZigBee Routing Algorithm Based on Energy Optimization Wangang Wang, Yong Peng, Yongyu Peng Chongqing City Management College, No. 151 Daxuecheng
Detection and Removal of Black Hole Attack in Mobile Ad hoc Network
 Detection and Removal of Black Hole Attack in Mobile Ad hoc Network Harmandeep Kaur, Mr. Amarvir Singh Abstract A mobile ad hoc network consists of large number of inexpensive nodes which are geographically
Detection and Removal of Black Hole Attack in Mobile Ad hoc Network Harmandeep Kaur, Mr. Amarvir Singh Abstract A mobile ad hoc network consists of large number of inexpensive nodes which are geographically
PoS(CENet2017)088. A Research on Interior Location of Improved Monte Carlo Algorithm Based on RSSI. Speaker. LiWen Liang 1.
 A Research on Interior Location of Improved Monte Carlo Algorithm Based on RSSI 1 Beijing University of Civil Engineering and Architecture Beijing,100044,China E-mail: llw_work@163.com Zhi Tan Beijing
A Research on Interior Location of Improved Monte Carlo Algorithm Based on RSSI 1 Beijing University of Civil Engineering and Architecture Beijing,100044,China E-mail: llw_work@163.com Zhi Tan Beijing
Embedded Smart Home System Based on ZigBee Song Chi
 International Conference on Intelligent Systems Research and Mechatronics Engineering (ISRME 2015) Embedded Smart Home System Based on ZigBee Song Chi Liaoning Jidian Polytechnic North Gold and Jewelry
International Conference on Intelligent Systems Research and Mechatronics Engineering (ISRME 2015) Embedded Smart Home System Based on ZigBee Song Chi Liaoning Jidian Polytechnic North Gold and Jewelry
Security of Intelligent Building Network Based on Wireless Sensor Network
 Security of Intelligent Building Network Based on Wireless Sensor Network https://doi.org/10.3991/ijoe.v14i06.8705 Shuang Xu!! ", Tong Zhou Zhengzhou Institute of Technology, Zhengzhou, China xushuangcardi@126.com
Security of Intelligent Building Network Based on Wireless Sensor Network https://doi.org/10.3991/ijoe.v14i06.8705 Shuang Xu!! ", Tong Zhou Zhengzhou Institute of Technology, Zhengzhou, China xushuangcardi@126.com
Searching Algorithm of Dormant Node in Wireless Sensor Networks
 Searching Algorithm of Dormant Node in Wireless Sensor Networks https://doi.org/10.991/ijoe.v1i05.7054 Bo Feng Shaanxi University of Science &Technologyhaanxi Xi an, China ckmtvxo44@16.com Wei Tang Shaanxi
Searching Algorithm of Dormant Node in Wireless Sensor Networks https://doi.org/10.991/ijoe.v1i05.7054 Bo Feng Shaanxi University of Science &Technologyhaanxi Xi an, China ckmtvxo44@16.com Wei Tang Shaanxi
High Resolution Remote Sensing Image Classification based on SVM and FCM Qin LI a, Wenxing BAO b, Xing LI c, Bin LI d
 2nd International Conference on Electrical, Computer Engineering and Electronics (ICECEE 2015) High Resolution Remote Sensing Image Classification based on SVM and FCM Qin LI a, Wenxing BAO b, Xing LI
2nd International Conference on Electrical, Computer Engineering and Electronics (ICECEE 2015) High Resolution Remote Sensing Image Classification based on SVM and FCM Qin LI a, Wenxing BAO b, Xing LI
An Angle Estimation to Landmarks for Autonomous Satellite Navigation
 5th International Conference on Environment, Materials, Chemistry and Power Electronics (EMCPE 2016) An Angle Estimation to Landmarks for Autonomous Satellite Navigation Qing XUE a, Hongwen YANG, Jian
5th International Conference on Environment, Materials, Chemistry and Power Electronics (EMCPE 2016) An Angle Estimation to Landmarks for Autonomous Satellite Navigation Qing XUE a, Hongwen YANG, Jian
Chapter 5 Ad Hoc Wireless Network. Jang Ping Sheu
 Chapter 5 Ad Hoc Wireless Network Jang Ping Sheu Introduction Ad Hoc Network is a multi-hop relaying network ALOHAnet developed in 1970 Ethernet developed in 1980 In 1994, Bluetooth proposed by Ericsson
Chapter 5 Ad Hoc Wireless Network Jang Ping Sheu Introduction Ad Hoc Network is a multi-hop relaying network ALOHAnet developed in 1970 Ethernet developed in 1980 In 1994, Bluetooth proposed by Ericsson
A Novel Intrusion Detection Method for WSN Sijia Wang a, Qi Li and Yanhui Guo
 International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2015) A Novel Intrusion Detection Method for WSN Sijia Wang a, Qi Li and Yanhui Guo Beijing University of
International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2015) A Novel Intrusion Detection Method for WSN Sijia Wang a, Qi Li and Yanhui Guo Beijing University of
Application of GIS best path algorithm in Harbin Roads. Sui Min, *Wang Wei-fang
 Application of GIS best path algorithm in Harbin Roads Sui Min, *Wang Wei-fang College of Forestry, Northeast Forestry University, Harbin, Heilongjiang 150040, China *Corresponding author. E-mail: weifangwang@126.com
Application of GIS best path algorithm in Harbin Roads Sui Min, *Wang Wei-fang College of Forestry, Northeast Forestry University, Harbin, Heilongjiang 150040, China *Corresponding author. E-mail: weifangwang@126.com
International Journal of Scientific & Engineering Research Volume 8, Issue 5, May ISSN
 International Journal of Scientific & Engineering Research Volume 8, Issue 5, May-2017 106 Self-organizing behavior of Wireless Ad Hoc Networks T. Raghu Trivedi, S. Giri Nath Abstract Self-organization
International Journal of Scientific & Engineering Research Volume 8, Issue 5, May-2017 106 Self-organizing behavior of Wireless Ad Hoc Networks T. Raghu Trivedi, S. Giri Nath Abstract Self-organization
Maps as Numbers: Data Models
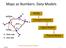 Maps as Numbers: Data Models vertices E Reality S E S arcs S E Conceptual Models nodes E Logical Models S Start node E End node S Physical Models 1 The Task An accurate, registered, digital map that can
Maps as Numbers: Data Models vertices E Reality S E S arcs S E Conceptual Models nodes E Logical Models S Start node E End node S Physical Models 1 The Task An accurate, registered, digital map that can
CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS
 International Journal of Wireless Communications and Networking 3(1), 2011, pp. 7-13 CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS Sudhanshu Pant 1, Naveen Chauhan 2 and Brij Bihari Dubey 3 Department
International Journal of Wireless Communications and Networking 3(1), 2011, pp. 7-13 CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS Sudhanshu Pant 1, Naveen Chauhan 2 and Brij Bihari Dubey 3 Department
An algorithm of lips secondary positioning and feature extraction based on YCbCr color space SHEN Xian-geng 1, WU Wei 2
 International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 015) An algorithm of lips secondary positioning and feature extraction based on YCbCr color space SHEN Xian-geng
International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 015) An algorithm of lips secondary positioning and feature extraction based on YCbCr color space SHEN Xian-geng
Recognition of Human Body Movements Trajectory Based on the Three-dimensional Depth Data
 Preprints of the 19th World Congress The International Federation of Automatic Control Recognition of Human Body s Trajectory Based on the Three-dimensional Depth Data Zheng Chang Qing Shen Xiaojuan Ban
Preprints of the 19th World Congress The International Federation of Automatic Control Recognition of Human Body s Trajectory Based on the Three-dimensional Depth Data Zheng Chang Qing Shen Xiaojuan Ban
Simulation Details for 2D
 Appendix B Simulation Details for 2D In this appendix we add some details two-dimensional simulation method. The details provided here describe the method used to obtain results reported in Chapters 3
Appendix B Simulation Details for 2D In this appendix we add some details two-dimensional simulation method. The details provided here describe the method used to obtain results reported in Chapters 3
HORIZONTAL AND VERTICAL ZONE BASED LOCATION TECHNIQUES FOR WIRELESS SENSOR NETWORKS
 HORIZONTAL AND VERTICAL ZONE BASED LOCATION TECHNIQUES FOR WIRELESS SENSOR NETWORKS M. Bala Krishna 1* and M. N. Doja 2 1* University School of Information Technology, G G S Indraprastha University, Delhi,
HORIZONTAL AND VERTICAL ZONE BASED LOCATION TECHNIQUES FOR WIRELESS SENSOR NETWORKS M. Bala Krishna 1* and M. N. Doja 2 1* University School of Information Technology, G G S Indraprastha University, Delhi,
CHAPTER 2 WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL
 WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL 2.1 Topology Control in Wireless Sensor Networks Network topology control is about management of network topology to support network-wide requirement.
WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL 2.1 Topology Control in Wireless Sensor Networks Network topology control is about management of network topology to support network-wide requirement.
Web-based Building Energy Consumption Monitoring and Conservation Service DONG Wei1, a
 4th International Conference on Mechatronics, Materials, Chemistry and Computer Engineering (ICMMCCE 2015) Web-based Building Energy Consumption Monitoring and Conservation Service DONG Wei1, a 1 Faculty
4th International Conference on Mechatronics, Materials, Chemistry and Computer Engineering (ICMMCCE 2015) Web-based Building Energy Consumption Monitoring and Conservation Service DONG Wei1, a 1 Faculty
Design of Desert Plant Monitoring System Based on SI446X Wireless Radio Frequency Communication
 4th International Conference on Sustainable Energy and Environmental Engineering (ICSEEE 2015) Design of Desert Plant Monitoring System Based on SI446X Wireless Radio Frequency Communication Hua Guo1,a,
4th International Conference on Sustainable Energy and Environmental Engineering (ICSEEE 2015) Design of Desert Plant Monitoring System Based on SI446X Wireless Radio Frequency Communication Hua Guo1,a,
Bijou Detouring - A Dynamic Node Level Routing Algorithm
 Bijou Detouring - A Dynamic Node Level Routing Algorithm G.Reshma K.Swarupa Rani D.Leela Dharani D.Anusha Abstract This paper holds a candle light on the Dijkstra algorithm and Distance Vector routing
Bijou Detouring - A Dynamic Node Level Routing Algorithm G.Reshma K.Swarupa Rani D.Leela Dharani D.Anusha Abstract This paper holds a candle light on the Dijkstra algorithm and Distance Vector routing
Analysis of Cluster-Based Energy-Dynamic Routing Protocols in WSN
 Analysis of Cluster-Based Energy-Dynamic Routing Protocols in WSN Mr. V. Narsing Rao 1, Dr.K.Bhargavi 2 1,2 Asst. Professor in CSE Dept., Sphoorthy Engineering College, Hyderabad Abstract- Wireless Sensor
Analysis of Cluster-Based Energy-Dynamic Routing Protocols in WSN Mr. V. Narsing Rao 1, Dr.K.Bhargavi 2 1,2 Asst. Professor in CSE Dept., Sphoorthy Engineering College, Hyderabad Abstract- Wireless Sensor
High Speed Data Collection in Wireless Sensor Network
 High Speed Data Collection in Wireless Sensor Network Kamal Kr. Gola a, *, Bhumika Gupta b, Zubair Iqbal c a Department of Computer Science & Engineering, Uttarakhand Technical University, Uttarakhand,
High Speed Data Collection in Wireless Sensor Network Kamal Kr. Gola a, *, Bhumika Gupta b, Zubair Iqbal c a Department of Computer Science & Engineering, Uttarakhand Technical University, Uttarakhand,
