Integrating rankings: Problem statement
|
|
|
- Alan Benedict Powell
- 6 years ago
- Views:
Transcription
1 Integrating rankings: Problem statement Each object has m grades, oneforeachofm criteria. The grade of an object for field i is x i. Normally assume 0 x i 1. Typically evaluations based on different criteria The higher the value of x i, the better the object is according to the ith criterion The objects are given in m sorted lists the ith list is sorted by x i value These lists correspond to different sources or to different criteria. Goal: find the top k objects. L. Libkin 1 Data Integration and Exchange
2 Example Grade 1 (17, ) (1352,0.9916) (702,0.9826) (12, ) Grade 2 2 (235, ) (12, ) (8201, ) (17, 0.406) L. Libkin 2 Data Integration and Exchange
3 Aggregation Functions Have an aggregation function F. Let x 1,,x m be the grades of object R under the m criteria. Then F (x 1,,x m ) is the overall grade of object R. Common choices for F : min average or sum An aggregation function F is monotone if F (x 1,,x m ) F (x 1,,x m) whenever x i x i for all i. L. Libkin 3 Data Integration and Exchange
4 Other Applications Information retrieval Objects R are documents. The m criteria are search terms s 1,,s m. The grade x i : how relevant document R is for search term s i. Common to take the aggregation function F to be the sum F (x 1,,x m )=x x m. L. Libkin 4 Data Integration and Exchange
5 Modes of Access Sorted access Can obtain the next object with its grade in list L i cost c S. Random access Can obtain the grade of object R in list L i cost c R. Middleware cost: c S (# of sorted accesses) + c R (# of random accesses). L. Libkin 5 Data Integration and Exchange
6 Algorithms Want an algorithm for finding the top k objects. Naive algorithm: compute the overall grade of every object; return the top k answers. Too expensive. L. Libkin 6 Data Integration and Exchange
7 Fagin s Algorithm (FA) 1. Do sorted access in parallel to each of the m sorted lists L i. Stop when there are at least k objects, each of which have been seen in all the lists. 2. For each object R that has been seen: Retrieve all of its fields x 1,,x m by random access. Compute F (R) =F (x 1,,x m ). 3. Return the top k answers. L. Libkin 7 Data Integration and Exchange
8 Fagin s algorithm is correct Assume object R was not seen its grades are x 1,,x m. Assume object S is one of the answers returned by FA its grades are y 1,,y m. Then x i y i for each i Hence F (R) =F (x 1,,x m ) F (y 1,,y m )=F(S). L. Libkin 8 Data Integration and Exchange
9 Fagin s algorithm: performance guarantees Typically probabilistic guarantees Orderings are independent Then with high probability the middleware cost is ( k ) O N m N i.e., sublinear But may perform poorly e.g., if F is constant: ( still takes O N m k/n ) instead of a constant time algorithm L. Libkin 9 Data Integration and Exchange
10 Optimal algorithm: The Threshold Algorithm 1. Do sorted access in parallel to each of the m sorted lists L i.aseach object R is seen under sorted access: Retrieve all of its fields x 1,,x m by random access. Compute F (R) =F (x 1,,x m ). If this is one of the top k answers so far, remember it. Note: buffer of bounded size. 2. For each list L i,letˆx i be the grade of the last object seen under sorted access. 3. Define the threshold value t to be F (ˆx 1,,ˆx m ). 4. When k objects have been seen whose grade is at least t, then stop. 5. Return the top k answers. L. Libkin 10 Data Integration and Exchange
11 Threshold Algorithm: correctness and optimality The Threshold Algorithm is correct for every monotone aggregate function F. Optimal in a very strong sense: it is as good as any other algorithm on every instance any other algorithm means: except pathological algorithms as good means: within a constant factor pathological means: making wild guesses. L. Libkin 11 Data Integration and Exchange
12 Wild guesses can help An algorithm makes a wild guess if it performs random access on an object not previously encountered by sorted access. Neither FA nor TA make wild guesses, nor does any natural algorithm. Example: The aggregation function is min; k =1. LIST L 1 (1, 1) (2, 1) (3, 1) (n+1, 1) (n+2, 0) (n+3, 0) (2n+1, 0) LIST L 2 (2n+1, 1) (2n, 1) (2n-1, 1) (n+1, 1) (n, 0) (n-1, 0) (1, 0) L. Libkin 12 Data Integration and Exchange
13 Threshold Algorithm as an approximation algorithm Approximately finding top k answers. For ε>0, anε-approximation of top k answers is a collection of k objects R 1,,R k so that for each R not among them, (1 + ε) F (R i ) F (R) Turning TA into an approximation algorithm: Simply change the stopping rule into: When k objects have been seen whose grade is at least t 1+ε, then stop. L. Libkin 13 Data Integration and Exchange
Combining Fuzzy Information - Top-k Query Algorithms. Sanjay Kulhari
 Combining Fuzzy Information - Top-k Query Algorithms Sanjay Kulhari Outline Definitions Objects, Attributes and Scores Querying Fuzzy Data Top-k query algorithms Naïve Algorithm Fagin s Algorithm (FA)
Combining Fuzzy Information - Top-k Query Algorithms Sanjay Kulhari Outline Definitions Objects, Attributes and Scores Querying Fuzzy Data Top-k query algorithms Naïve Algorithm Fagin s Algorithm (FA)
modern database systems lecture 5 : top-k retrieval
 modern database systems lecture 5 : top-k retrieval Aristides Gionis Michael Mathioudakis spring 2016 announcements problem session on Monday, March 7, 2-4pm, at T2 solutions of the problems in homework
modern database systems lecture 5 : top-k retrieval Aristides Gionis Michael Mathioudakis spring 2016 announcements problem session on Monday, March 7, 2-4pm, at T2 solutions of the problems in homework
Optimal algorithms for middleware
 Optimal aggregation algorithms for middleware S856 Fall 2005 Presentation Weihan Wang w23wang@uwaterloo.ca November 23, 2005 About the paper Ronald Fagin, IBM Research Amnon Lotem, Maryland Moni Naor,
Optimal aggregation algorithms for middleware S856 Fall 2005 Presentation Weihan Wang w23wang@uwaterloo.ca November 23, 2005 About the paper Ronald Fagin, IBM Research Amnon Lotem, Maryland Moni Naor,
Combining Fuzzy Information: an Overview
 Combining Fuzzy Information: an Overview Ronald Fagin IBM Almaden Research Center 650 Harry Road San Jose, California 95120-6099 email: fagin@almaden.ibm.com http://www.almaden.ibm.com/cs/people/fagin/
Combining Fuzzy Information: an Overview Ronald Fagin IBM Almaden Research Center 650 Harry Road San Jose, California 95120-6099 email: fagin@almaden.ibm.com http://www.almaden.ibm.com/cs/people/fagin/
The interaction of theory and practice in database research
 The interaction of theory and practice in database research Ron Fagin IBM Research Almaden 1 Purpose of This Talk Encourage collaboration between theoreticians and system builders via two case studies
The interaction of theory and practice in database research Ron Fagin IBM Research Almaden 1 Purpose of This Talk Encourage collaboration between theoreticians and system builders via two case studies
Comparison of of parallel and random approach to
 Comparison of of parallel and random approach to acandidate candidatelist listininthe themultifeature multifeaturequerying Peter Gurský Peter Gurský Institute of Computer Science, Faculty of Science Institute
Comparison of of parallel and random approach to acandidate candidatelist listininthe themultifeature multifeaturequerying Peter Gurský Peter Gurský Institute of Computer Science, Faculty of Science Institute
Optimal Aggregation Algorithms for Middleware
 Optimal Aggregation Algorithms for Middleware [Extended Abstract] Ronald Fagin IBM Almaden Research Center 650 Harry Road San Jose, CA 95120 fagin@almaden.ibm.com Amnon Lotem University of Maryland College
Optimal Aggregation Algorithms for Middleware [Extended Abstract] Ronald Fagin IBM Almaden Research Center 650 Harry Road San Jose, CA 95120 fagin@almaden.ibm.com Amnon Lotem University of Maryland College
IO-Top-k at TREC 2006: Terabyte Track
 IO-Top-k at TREC 2006: Terabyte Track Holger Bast Debapriyo Majumdar Ralf Schenkel Martin Theobald Gerhard Weikum Max-Planck-Institut für Informatik, Saarbrücken, Germany {bast,deb,schenkel,mtb,weikum}@mpi-inf.mpg.de
IO-Top-k at TREC 2006: Terabyte Track Holger Bast Debapriyo Majumdar Ralf Schenkel Martin Theobald Gerhard Weikum Max-Planck-Institut für Informatik, Saarbrücken, Germany {bast,deb,schenkel,mtb,weikum}@mpi-inf.mpg.de
Information Retrieval Rank aggregation. Luca Bondi
 Rank aggregation Luca Bondi Motivations 2 Metasearch For a given query, combine the results from different search engines Combining ranking functions Text, links, anchor text, page title, etc. Comparing
Rank aggregation Luca Bondi Motivations 2 Metasearch For a given query, combine the results from different search engines Combining ranking functions Text, links, anchor text, page title, etc. Comparing
A Study on Reverse Top-K Queries Using Monochromatic and Bichromatic Methods
 A Study on Reverse Top-K Queries Using Monochromatic and Bichromatic Methods S.Anusuya 1, M.Balaganesh 2 P.G. Student, Department of Computer Science and Engineering, Sembodai Rukmani Varatharajan Engineering
A Study on Reverse Top-K Queries Using Monochromatic and Bichromatic Methods S.Anusuya 1, M.Balaganesh 2 P.G. Student, Department of Computer Science and Engineering, Sembodai Rukmani Varatharajan Engineering
Combining Fuzzy Information from Multiple Systems*
 Journal of Computer and ystem ciences 58, 8399 (1999) Article ID jcss.1998.1600, available online at http:www.idealibrary.com on Combining Fuzzy Information from Multiple ystems* Ronald Fagin - IBM Almaden
Journal of Computer and ystem ciences 58, 8399 (1999) Article ID jcss.1998.1600, available online at http:www.idealibrary.com on Combining Fuzzy Information from Multiple ystems* Ronald Fagin - IBM Almaden
Incomplete Information: Null Values
 Incomplete Information: Null Values Often ruled out: not null in SQL. Essential when one integrates/exchanges data. Perhaps the most poorly designed and the most often criticized part of SQL:... [this]
Incomplete Information: Null Values Often ruled out: not null in SQL. Essential when one integrates/exchanges data. Perhaps the most poorly designed and the most often criticized part of SQL:... [this]
CS264: Homework #1. Due by midnight on Thursday, January 19, 2017
 CS264: Homework #1 Due by midnight on Thursday, January 19, 2017 Instructions: (1) Form a group of 1-3 students. You should turn in only one write-up for your entire group. See the course site for submission
CS264: Homework #1 Due by midnight on Thursday, January 19, 2017 Instructions: (1) Form a group of 1-3 students. You should turn in only one write-up for your entire group. See the course site for submission
Peter Gurský. Institute of Computer Science, Faculty of Science.
 Towards TowardsBetter better Semantics semantics in in the the multifeature Multifeature Querying querying Peter Gurský Peter Gurský Institute of Computer Science, Faculty of Science Institute of P.J.Šafárik
Towards TowardsBetter better Semantics semantics in in the the multifeature Multifeature Querying querying Peter Gurský Peter Gurský Institute of Computer Science, Faculty of Science Institute of P.J.Šafárik
Direct Rendering of Trimmed NURBS Surfaces
 Direct Rendering of Trimmed NURBS Surfaces Hardware Graphics Pipeline 2/ 81 Hardware Graphics Pipeline GPU Video Memory CPU Vertex Processor Raster Unit Fragment Processor Render Target Screen Extended
Direct Rendering of Trimmed NURBS Surfaces Hardware Graphics Pipeline 2/ 81 Hardware Graphics Pipeline GPU Video Memory CPU Vertex Processor Raster Unit Fragment Processor Render Target Screen Extended
Lecture 23: Priority Queues, Part 2 10:00 AM, Mar 19, 2018
 CS8 Integrated Introduction to Computer Science Fisler, Nelson Lecture : Priority Queues, Part : AM, Mar 9, 8 Contents Sorting, Revisited Counting Sort Bucket Sort 4 Radix Sort 6 4. MSD Radix Sort......................................
CS8 Integrated Introduction to Computer Science Fisler, Nelson Lecture : Priority Queues, Part : AM, Mar 9, 8 Contents Sorting, Revisited Counting Sort Bucket Sort 4 Radix Sort 6 4. MSD Radix Sort......................................
Functions. Def. Let A and B be sets. A function f from A to B is an assignment of exactly one element of B to each element of A.
 Functions functions 1 Def. Let A and B be sets. A function f from A to B is an assignment of exactly one element of B to each element of A. a A! b B b is assigned to a a A! b B f ( a) = b Notation: If
Functions functions 1 Def. Let A and B be sets. A function f from A to B is an assignment of exactly one element of B to each element of A. a A! b B b is assigned to a a A! b B f ( a) = b Notation: If
A Survey of Techniques for Answering Top-k Queries
 Global Journal of Computer Science and Technology Software & Data Engineering Volume 13 Issue 2 Version 1.0 Year 2013 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
Global Journal of Computer Science and Technology Software & Data Engineering Volume 13 Issue 2 Version 1.0 Year 2013 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
Representing and Querying Imprecise Data
 Representing and Querying Imprecise Data Alberto Trombetta Università di Torino Dottorato di Ricerca in Informatica XI Ciclo Advisors: Prof. Elisa Bertino, Dr. Marenza Demarie, Prof. Antonio Di Leva, Prof.
Representing and Querying Imprecise Data Alberto Trombetta Università di Torino Dottorato di Ricerca in Informatica XI Ciclo Advisors: Prof. Elisa Bertino, Dr. Marenza Demarie, Prof. Antonio Di Leva, Prof.
Secure Multiparty Computation Multi-round protocols
 Secure Multiparty Computation Multi-round protocols Li Xiong CS573 Data Privacy and Security Secure multiparty computation General circuit based secure multiparty computation methods Specialized secure
Secure Multiparty Computation Multi-round protocols Li Xiong CS573 Data Privacy and Security Secure multiparty computation General circuit based secure multiparty computation methods Specialized secure
The complement of PATH is in NL
 340 The complement of PATH is in NL Let c be the number of nodes in graph G that are reachable from s We assume that c is provided as an input to M Given G, s, t, and c the machine M operates as follows:
340 The complement of PATH is in NL Let c be the number of nodes in graph G that are reachable from s We assume that c is provided as an input to M Given G, s, t, and c the machine M operates as follows:
Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]:
![Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]: Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]:](/thumbs/90/104324109.jpg) CSE 101 Homework 1 Background (Order and Recurrence Relations), correctness proofs, time analysis, and speeding up algorithms with restructuring, preprocessing and data structures. Due Thursday, April
CSE 101 Homework 1 Background (Order and Recurrence Relations), correctness proofs, time analysis, and speeding up algorithms with restructuring, preprocessing and data structures. Due Thursday, April
The Expected Performance Curve: a New Assessment Measure for Person Authentication
 The Expected Performance Curve: a New Assessment Measure for Person Authentication Samy Bengio Johnny Mariéthoz IDIAP CP 592, rue du Simplon4 192 Martigny, Switzerland {bengio,marietho}@idiap.ch Abstract
The Expected Performance Curve: a New Assessment Measure for Person Authentication Samy Bengio Johnny Mariéthoz IDIAP CP 592, rue du Simplon4 192 Martigny, Switzerland {bengio,marietho}@idiap.ch Abstract
SDC Platinum includes several utilities to help in creating and reusing searches and reports.
 C H A P T E R 6 Chapter 6 Helpful Utilities Chapter 6 Helpful Utilities SDC Platinum includes several utilities to help in creating and reusing searches and reports. SDC Standard Sessions There are a number
C H A P T E R 6 Chapter 6 Helpful Utilities Chapter 6 Helpful Utilities SDC Platinum includes several utilities to help in creating and reusing searches and reports. SDC Standard Sessions There are a number
Finding k-dominant Skylines in High Dimensional Space
 Finding k-dominant Skylines in High Dimensional Space Chee-Yong Chan, H.V. Jagadish 2, Kian-Lee Tan, Anthony K.H. Tung, Zhenjie Zhang School of Computing 2 Dept. of Electrical Engineering & Computer Science
Finding k-dominant Skylines in High Dimensional Space Chee-Yong Chan, H.V. Jagadish 2, Kian-Lee Tan, Anthony K.H. Tung, Zhenjie Zhang School of Computing 2 Dept. of Electrical Engineering & Computer Science
Homework #3 (Search) Out: 1/24/11 Due: 2/1/11 (at noon)
 CS121 Introduction to Artificial Intelligence Winter 2011 Homework #3 (Search) Out: 1/24/11 Due: 2/1/11 (at noon) How to complete this HW: First copy this file; then type your answers in the file immediately
CS121 Introduction to Artificial Intelligence Winter 2011 Homework #3 (Search) Out: 1/24/11 Due: 2/1/11 (at noon) How to complete this HW: First copy this file; then type your answers in the file immediately
The Expected Performance Curve: a New Assessment Measure for Person Authentication
 R E S E A R C H R E P O R T I D I A P The Expected Performance Curve: a New Assessment Measure for Person Authentication Samy Bengio 1 Johnny Mariéthoz 2 IDIAP RR 03-84 March 10, 2004 submitted for publication
R E S E A R C H R E P O R T I D I A P The Expected Performance Curve: a New Assessment Measure for Person Authentication Samy Bengio 1 Johnny Mariéthoz 2 IDIAP RR 03-84 March 10, 2004 submitted for publication
Sorting. Divide-and-Conquer 1
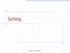 Sorting Divide-and-Conquer 1 Divide-and-Conquer 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer 2 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide:
Sorting Divide-and-Conquer 1 Divide-and-Conquer 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer 2 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide:
Rank Aggregation for Automatic Schema Matching
 Rank Aggregation for Automatic Schema Matching Carmel Domshlak Avigdor Gal Member, IEEE, Haggai Roitman Technion - Israel Institute of Technology. 2 Abstract Schema matching is a basic operation of data
Rank Aggregation for Automatic Schema Matching Carmel Domshlak Avigdor Gal Member, IEEE, Haggai Roitman Technion - Israel Institute of Technology. 2 Abstract Schema matching is a basic operation of data
Missing Value Imputation in Time Series using Top-k Case Matching
 Missing Value Imputation in Time Series using Top-k Case Matching Kevin Wellenzohn Free University of Bozen-Bolzano kevin.wellenzohn@unibz.it M. H. Böhlen University of Zurich boehlen@ifi.uzh.ch Hannes
Missing Value Imputation in Time Series using Top-k Case Matching Kevin Wellenzohn Free University of Bozen-Bolzano kevin.wellenzohn@unibz.it M. H. Böhlen University of Zurich boehlen@ifi.uzh.ch Hannes
Efficient Top-k Algorithms for Fuzzy Search in String Collections
 Efficient Top-k Algorithms for Fuzzy Search in String Collections Rares Vernica Chen Li Department of Computer Science University of California, Irvine First International Workshop on Keyword Search on
Efficient Top-k Algorithms for Fuzzy Search in String Collections Rares Vernica Chen Li Department of Computer Science University of California, Irvine First International Workshop on Keyword Search on
Chapter S:V. V. Formal Properties of A*
 Chapter S:V V. Formal Properties of A* Properties of Search Space Graphs Auxiliary Concepts Roadmap Completeness of A* Admissibility of A* Efficiency of A* Monotone Heuristic Functions S:V-1 Formal Properties
Chapter S:V V. Formal Properties of A* Properties of Search Space Graphs Auxiliary Concepts Roadmap Completeness of A* Admissibility of A* Efficiency of A* Monotone Heuristic Functions S:V-1 Formal Properties
Multi-objective Query Processing for Database Systems
 Multi-objective Query Processing for Database Systems Wolf-Tilo Balke Computer Science Department University of California Berkeley, CA, USA balke@eecs.berkeley.edu Abstract Query processing in database
Multi-objective Query Processing for Database Systems Wolf-Tilo Balke Computer Science Department University of California Berkeley, CA, USA balke@eecs.berkeley.edu Abstract Query processing in database
. A quick enumeration leads to five possible upper bounds and we are interested in the smallest of them: h(x 1, x 2, x 3) min{x 1
 large-scale search engines [14]. These intersection lists, however, take up additional space dictating a cost-benefit trade-off, and careful strategies have been proposed to select the pairs of terms for
large-scale search engines [14]. These intersection lists, however, take up additional space dictating a cost-benefit trade-off, and careful strategies have been proposed to select the pairs of terms for
Evaluating Top-k Queries Over Web-Accessible Databases
 Evaluating Top-k Queries Over Web-Accessible Databases AMÉLIE MARIAN Columbia University, New York NICOLAS BRUNO Microsoft Research, Redmond, Washington and LUIS GRAVANO Columbia University, New York A
Evaluating Top-k Queries Over Web-Accessible Databases AMÉLIE MARIAN Columbia University, New York NICOLAS BRUNO Microsoft Research, Redmond, Washington and LUIS GRAVANO Columbia University, New York A
Module 7 VIDEO CODING AND MOTION ESTIMATION
 Module 7 VIDEO CODING AND MOTION ESTIMATION Version ECE IIT, Kharagpur Lesson Block based motion estimation algorithms Version ECE IIT, Kharagpur Lesson Objectives At the end of this less, the students
Module 7 VIDEO CODING AND MOTION ESTIMATION Version ECE IIT, Kharagpur Lesson Block based motion estimation algorithms Version ECE IIT, Kharagpur Lesson Objectives At the end of this less, the students
Arnab Bhattacharya, Shrikant Awate. Dept. of Computer Science and Engineering, Indian Institute of Technology, Kanpur
 Arnab Bhattacharya, Shrikant Awate Dept. of Computer Science and Engineering, Indian Institute of Technology, Kanpur Motivation Flight from Kolkata to Los Angeles No direct flight Through Singapore or
Arnab Bhattacharya, Shrikant Awate Dept. of Computer Science and Engineering, Indian Institute of Technology, Kanpur Motivation Flight from Kolkata to Los Angeles No direct flight Through Singapore or
Exact and Approximate Generic Multi-criteria Top-k Query Processing
 Exact and Approximate Generic Multi-criteria Top-k Query Processing Mehdi Badr, Dan Vodislav To cite this version: Mehdi Badr, Dan Vodislav. Exact and Approximate Generic Multi-criteria Top-k Query Processing.
Exact and Approximate Generic Multi-criteria Top-k Query Processing Mehdi Badr, Dan Vodislav To cite this version: Mehdi Badr, Dan Vodislav. Exact and Approximate Generic Multi-criteria Top-k Query Processing.
Estimating the Quality of Databases
 Estimating the Quality of Databases Ami Motro Igor Rakov George Mason University May 1998 1 Outline: 1. Introduction 2. Simple quality estimation 3. Refined quality estimation 4. Computing the quality
Estimating the Quality of Databases Ami Motro Igor Rakov George Mason University May 1998 1 Outline: 1. Introduction 2. Simple quality estimation 3. Refined quality estimation 4. Computing the quality
Cost-aware top-k join algorithms
 Cost-aware top-k join algorithms Stefano Ceri Davide Martinenghi Marco Tagliasacchi Dipartimento di Elettronica e Informazione Politecnico di Milano Piazza Leonardo da Vinci, 32 2033 Milano, Italy {ceri,martinen,tagliasa}@elet.polimi.it
Cost-aware top-k join algorithms Stefano Ceri Davide Martinenghi Marco Tagliasacchi Dipartimento di Elettronica e Informazione Politecnico di Milano Piazza Leonardo da Vinci, 32 2033 Milano, Italy {ceri,martinen,tagliasa}@elet.polimi.it
Predictive Indexing for Fast Search
 Predictive Indexing for Fast Search Sharad Goel, John Langford and Alex Strehl Yahoo! Research, New York Modern Massive Data Sets (MMDS) June 25, 2008 Goel, Langford & Strehl (Yahoo! Research) Predictive
Predictive Indexing for Fast Search Sharad Goel, John Langford and Alex Strehl Yahoo! Research, New York Modern Massive Data Sets (MMDS) June 25, 2008 Goel, Langford & Strehl (Yahoo! Research) Predictive
A Detailed Evaluation of Threshold Algorithms for Answering Top-k queries in Peer-to-Peer Networks
 TECHNICAL REPORT: ICS-FORTH/TR-407, JULY 2010, COPYRIGHT BY INSTITUTE OF COMPUTER SCIENCE, FOUNDATION FOR RESEARCH & TECHNOLOGY - HELLAS [2010] A Detailed Evaluation of Threshold Algorithms for Answering
TECHNICAL REPORT: ICS-FORTH/TR-407, JULY 2010, COPYRIGHT BY INSTITUTE OF COMPUTER SCIENCE, FOUNDATION FOR RESEARCH & TECHNOLOGY - HELLAS [2010] A Detailed Evaluation of Threshold Algorithms for Answering
Line Arrangements. Applications
 Computational Geometry Chapter 9 Line Arrangements 1 Line Arrangements Applications On the Agenda 2 1 Complexity of a Line Arrangement Given a set L of n lines in the plane, their arrangement A(L) is the
Computational Geometry Chapter 9 Line Arrangements 1 Line Arrangements Applications On the Agenda 2 1 Complexity of a Line Arrangement Given a set L of n lines in the plane, their arrangement A(L) is the
DIRA : A FRAMEWORK OF DATA INTEGRATION USING DATA QUALITY
 DIRA : A FRAMEWORK OF DATA INTEGRATION USING DATA QUALITY Reham I. Abdel Monem 1, Ali H. El-Bastawissy 2 and Mohamed M. Elwakil 3 1 Information Systems Department, Faculty of computers and information,
DIRA : A FRAMEWORK OF DATA INTEGRATION USING DATA QUALITY Reham I. Abdel Monem 1, Ali H. El-Bastawissy 2 and Mohamed M. Elwakil 3 1 Information Systems Department, Faculty of computers and information,
Civil Engineering Systems Analysis Lecture XIV. Instructor: Prof. Naveen Eluru Department of Civil Engineering and Applied Mechanics
 Civil Engineering Systems Analysis Lecture XIV Instructor: Prof. Naveen Eluru Department of Civil Engineering and Applied Mechanics Today s Learning Objectives Dual 2 Linear Programming Dual Problem 3
Civil Engineering Systems Analysis Lecture XIV Instructor: Prof. Naveen Eluru Department of Civil Engineering and Applied Mechanics Today s Learning Objectives Dual 2 Linear Programming Dual Problem 3
Test 2 Version A. On my honor, I have neither given nor received inappropriate or unauthorized information at any time before or during this test.
 Student s Printed Name: Instructor: CUID: Section: Instructions: You are not permitted to use a calculator on any portion of this test. You are not allowed to use any textbook, notes, cell phone, laptop,
Student s Printed Name: Instructor: CUID: Section: Instructions: You are not permitted to use a calculator on any portion of this test. You are not allowed to use any textbook, notes, cell phone, laptop,
INF4820 Algorithms for AI and NLP. Evaluating Classifiers Clustering
 INF4820 Algorithms for AI and NLP Evaluating Classifiers Clustering Murhaf Fares & Stephan Oepen Language Technology Group (LTG) September 27, 2017 Today 2 Recap Evaluation of classifiers Unsupervised
INF4820 Algorithms for AI and NLP Evaluating Classifiers Clustering Murhaf Fares & Stephan Oepen Language Technology Group (LTG) September 27, 2017 Today 2 Recap Evaluation of classifiers Unsupervised
1 Overview. 2 Applications of submodular maximization. AM 221: Advanced Optimization Spring 2016
 AM : Advanced Optimization Spring 06 Prof. Yaron Singer Lecture 0 April th Overview Last time we saw the problem of Combinatorial Auctions and framed it as a submodular maximization problem under a partition
AM : Advanced Optimization Spring 06 Prof. Yaron Singer Lecture 0 April th Overview Last time we saw the problem of Combinatorial Auctions and framed it as a submodular maximization problem under a partition
COT 6936: Topics in Algorithms! Giri Narasimhan. ECS 254A / EC 2443; Phone: x3748
 COT 6936: Topics in Algorithms! Giri Narasimhan ECS 254A / EC 2443; Phone: x3748 giri@cs.fiu.edu http://www.cs.fiu.edu/~giri/teach/cot6936_s12.html https://moodle.cis.fiu.edu/v2.1/course/view.php?id=174
COT 6936: Topics in Algorithms! Giri Narasimhan ECS 254A / EC 2443; Phone: x3748 giri@cs.fiu.edu http://www.cs.fiu.edu/~giri/teach/cot6936_s12.html https://moodle.cis.fiu.edu/v2.1/course/view.php?id=174
Heuristic (Informed) Search
 Heuristic (Informed) Search (Where we try to choose smartly) R&N: Chap., Sect..1 3 1 Search Algorithm #2 SEARCH#2 1. INSERT(initial-node,Open-List) 2. Repeat: a. If empty(open-list) then return failure
Heuristic (Informed) Search (Where we try to choose smartly) R&N: Chap., Sect..1 3 1 Search Algorithm #2 SEARCH#2 1. INSERT(initial-node,Open-List) 2. Repeat: a. If empty(open-list) then return failure
6. Dicretization methods 6.1 The purpose of discretization
 6. Dicretization methods 6.1 The purpose of discretization Often data are given in the form of continuous values. If their number is huge, model building for such data can be difficult. Moreover, many
6. Dicretization methods 6.1 The purpose of discretization Often data are given in the form of continuous values. If their number is huge, model building for such data can be difficult. Moreover, many
COP 4531 Complexity & Analysis of Data Structures & Algorithms
 COP 4531 Complexity & Analysis of Data Structures & Algorithms Amortized Analysis Thanks to the text authors who contributed to these slides What is amortized analysis? Analyze a sequence of operations
COP 4531 Complexity & Analysis of Data Structures & Algorithms Amortized Analysis Thanks to the text authors who contributed to these slides What is amortized analysis? Analyze a sequence of operations
Heuris'c Search. Reading note: Chapter 4 covers heuristic search.
 Heuris'c Search Reading note: Chapter 4 covers heuristic search. Credits: Slides in this deck are drawn from or inspired by a multitude of sources including: Shaul Markovitch Jurgen Strum Sheila McIlraith
Heuris'c Search Reading note: Chapter 4 covers heuristic search. Credits: Slides in this deck are drawn from or inspired by a multitude of sources including: Shaul Markovitch Jurgen Strum Sheila McIlraith
J. Parallel Distrib. Comput.
 J. Parallel Distrib. Comput. 71 (011) 30 315 Contents lists available at ScienceDirect J. Parallel Distrib. Comput. journal homepage: www.elsevier.com/locate/jpdc Top-k vectorial aggregation queries in
J. Parallel Distrib. Comput. 71 (011) 30 315 Contents lists available at ScienceDirect J. Parallel Distrib. Comput. journal homepage: www.elsevier.com/locate/jpdc Top-k vectorial aggregation queries in
Virtual views. Incremental View Maintenance. View maintenance. Materialized views. Review of bag algebra. Bag algebra operators (slide 1)
 Virtual views Incremental View Maintenance CPS 296.1 Topics in Database Systems A view is defined by a query over base tables Example: CREATE VIEW V AS SELECT FROM R, S WHERE ; A view can be queried just
Virtual views Incremental View Maintenance CPS 296.1 Topics in Database Systems A view is defined by a query over base tables Example: CREATE VIEW V AS SELECT FROM R, S WHERE ; A view can be queried just
Lecture 10: Clocks and Time
 06-06798 Distributed Systems Lecture 10: Clocks and Time Distributed Systems 1 Time service Overview requirements and problems sources of time Clock synchronisation algorithms clock skew & drift Cristian
06-06798 Distributed Systems Lecture 10: Clocks and Time Distributed Systems 1 Time service Overview requirements and problems sources of time Clock synchronisation algorithms clock skew & drift Cristian
Optimizing Access Cost for Top-k Queries over Web Sources: A Unified Cost-based Approach
 UIUC Technical Report UIUCDCS-R-03-2324, UILU-ENG-03-1711. March 03 (Revised March 04) Optimizing Access Cost for Top-k Queries over Web Sources A Unified Cost-based Approach Seung-won Hwang and Kevin
UIUC Technical Report UIUCDCS-R-03-2324, UILU-ENG-03-1711. March 03 (Revised March 04) Optimizing Access Cost for Top-k Queries over Web Sources A Unified Cost-based Approach Seung-won Hwang and Kevin
Top of Minds Report series Removing duplicates using Informatica PowerCenter
 Top of Minds Report series Removing duplicates using Informatica PowerCenter Introduction There is more than one way to skin a cat, and there are four ways to choose one distinct row of several possibilities
Top of Minds Report series Removing duplicates using Informatica PowerCenter Introduction There is more than one way to skin a cat, and there are four ways to choose one distinct row of several possibilities
REGION BASED SEGEMENTATION
 REGION BASED SEGEMENTATION The objective of Segmentation is to partition an image into regions. The region-based segmentation techniques find the regions directly. Extract those regions in the image whose
REGION BASED SEGEMENTATION The objective of Segmentation is to partition an image into regions. The region-based segmentation techniques find the regions directly. Extract those regions in the image whose
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 7 - Jan. 17, 2018 CLRS 7.1, 7-4, 9.1, 9.3 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures 1 / 11 QuickSelect
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 7 - Jan. 17, 2018 CLRS 7.1, 7-4, 9.1, 9.3 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures 1 / 11 QuickSelect
1 Linear programming relaxation
 Cornell University, Fall 2010 CS 6820: Algorithms Lecture notes: Primal-dual min-cost bipartite matching August 27 30 1 Linear programming relaxation Recall that in the bipartite minimum-cost perfect matching
Cornell University, Fall 2010 CS 6820: Algorithms Lecture notes: Primal-dual min-cost bipartite matching August 27 30 1 Linear programming relaxation Recall that in the bipartite minimum-cost perfect matching
3. Relational Data Model 3.5 The Tuple Relational Calculus
 3. Relational Data Model 3.5 The Tuple Relational Calculus forall quantification Syntax: t R(P(t)) semantics: for all tuples t in relation R, P(t) has to be fulfilled example query: Determine all students
3. Relational Data Model 3.5 The Tuple Relational Calculus forall quantification Syntax: t R(P(t)) semantics: for all tuples t in relation R, P(t) has to be fulfilled example query: Determine all students
Process Document Creating a Query with Runtime Prompts. Creating a Query with Runtime Prompts. Concept
 Concept Adding a prompt enables you to further refine a query when you run it. For example, suppose you wanted to change a query so that you could prompt the user to enter a value for the duration of a
Concept Adding a prompt enables you to further refine a query when you run it. For example, suppose you wanted to change a query so that you could prompt the user to enter a value for the duration of a
Computing Classic Closeness Centrality, at Scale
 Computing Classic Closeness Centrality, at Scale Edith Cohen Joint with: Thomas Pajor, Daniel Delling, Renato Werneck Very Large Graphs Model relations and interactions (edges) between entities (nodes)
Computing Classic Closeness Centrality, at Scale Edith Cohen Joint with: Thomas Pajor, Daniel Delling, Renato Werneck Very Large Graphs Model relations and interactions (edges) between entities (nodes)
CS 2750 Machine Learning. Lecture 19. Clustering. CS 2750 Machine Learning. Clustering. Groups together similar instances in the data sample
 Lecture 9 Clustering Milos Hauskrecht milos@cs.pitt.edu 539 Sennott Square Clustering Groups together similar instances in the data sample Basic clustering problem: distribute data into k different groups
Lecture 9 Clustering Milos Hauskrecht milos@cs.pitt.edu 539 Sennott Square Clustering Groups together similar instances in the data sample Basic clustering problem: distribute data into k different groups
Best-First Search Minimizing Space or Time. IDA* Save space, take more time
 Best-First Search Minimizing Space or Time IDA* Save space, take more time IDA*-1 A* space complexity» What does the space complexity of A* depend upon? IDA*-2 A* space complexity 2» What does the space
Best-First Search Minimizing Space or Time IDA* Save space, take more time IDA*-1 A* space complexity» What does the space complexity of A* depend upon? IDA*-2 A* space complexity 2» What does the space
Answers to specimen paper questions. Most of the answers below go into rather more detail than is really needed. Please let me know of any mistakes.
 Answers to specimen paper questions Most of the answers below go into rather more detail than is really needed. Please let me know of any mistakes. Question 1. (a) The degree of a vertex x is the number
Answers to specimen paper questions Most of the answers below go into rather more detail than is really needed. Please let me know of any mistakes. Question 1. (a) The degree of a vertex x is the number
Rank Aggregation for Automatic Schema Matching
 Rank Aggregation for Automatic Schema Matching Carmel Domshlak Avigdor Gal Senior Member, IEEE Haggai Roitman Abstract Schema matching is a basic operation of data integration and several tools for automating
Rank Aggregation for Automatic Schema Matching Carmel Domshlak Avigdor Gal Senior Member, IEEE Haggai Roitman Abstract Schema matching is a basic operation of data integration and several tools for automating
Rank-aware Query Optimization
 Rank-aware Query Optimization Ihab F. Ilyas Rahul Shah Walid G. Aref Jeffrey Scott Vitter Ahmed K. Elmagarmid Department of Computer Sciences, Purdue University 250 N. University Street West Lafayette,
Rank-aware Query Optimization Ihab F. Ilyas Rahul Shah Walid G. Aref Jeffrey Scott Vitter Ahmed K. Elmagarmid Department of Computer Sciences, Purdue University 250 N. University Street West Lafayette,
Basic Tokenizing, Indexing, and Implementation of Vector-Space Retrieval
 Basic Tokenizing, Indexing, and Implementation of Vector-Space Retrieval 1 Naïve Implementation Convert all documents in collection D to tf-idf weighted vectors, d j, for keyword vocabulary V. Convert
Basic Tokenizing, Indexing, and Implementation of Vector-Space Retrieval 1 Naïve Implementation Convert all documents in collection D to tf-idf weighted vectors, d j, for keyword vocabulary V. Convert
Efficient Top-k Aggregation of Ranked Inputs
 Efficient Top-k Aggregation of Ranked Inputs NIKOS MAMOULIS University of Hong Kong MAN LUNG YIU Aalborg University KIT HUNG CHENG University of Hong Kong and DAVID W. CHEUNG University of Hong Kong A
Efficient Top-k Aggregation of Ranked Inputs NIKOS MAMOULIS University of Hong Kong MAN LUNG YIU Aalborg University KIT HUNG CHENG University of Hong Kong and DAVID W. CHEUNG University of Hong Kong A
Databases -Normalization I. (GF Royle, N Spadaccini ) Databases - Normalization I 1 / 24
 Databases -Normalization I (GF Royle, N Spadaccini 2006-2010) Databases - Normalization I 1 / 24 This lecture This lecture introduces normal forms, decomposition and normalization. We will explore problems
Databases -Normalization I (GF Royle, N Spadaccini 2006-2010) Databases - Normalization I 1 / 24 This lecture This lecture introduces normal forms, decomposition and normalization. We will explore problems
Finite Model Theory and Its Applications
 Erich Grädel Phokion G. Kolaitis Leonid Libkin Maarten Marx Joel Spencer Moshe Y. Vardi Yde Venema Scott Weinstein Finite Model Theory and Its Applications With 35 Figures and 2 Tables Springer Contents
Erich Grädel Phokion G. Kolaitis Leonid Libkin Maarten Marx Joel Spencer Moshe Y. Vardi Yde Venema Scott Weinstein Finite Model Theory and Its Applications With 35 Figures and 2 Tables Springer Contents
Anytime Measures for Top-k Algorithms
 Anytime Measures for Top-k Algorithms Benjamin Arai Univ. of California, Riverside barai@cs.ucr.edu Gautam Das Univ. of Texas, Arlington gdas@cse.uta.edu Nick Koudas Univ. of Toronto koudas@cs.toronto.edu
Anytime Measures for Top-k Algorithms Benjamin Arai Univ. of California, Riverside barai@cs.ucr.edu Gautam Das Univ. of Texas, Arlington gdas@cse.uta.edu Nick Koudas Univ. of Toronto koudas@cs.toronto.edu
My Query Builder Function
 My Query Builder Function The My Query Builder function is used to build custom SQL queries for reporting information out of the TEAMS system. Query results can be exported to a comma-separated value file,
My Query Builder Function The My Query Builder function is used to build custom SQL queries for reporting information out of the TEAMS system. Query results can be exported to a comma-separated value file,
Here is a recursive algorithm that solves this problem, given a pointer to the root of T : MaxWtSubtree [r]
![Here is a recursive algorithm that solves this problem, given a pointer to the root of T : MaxWtSubtree [r] Here is a recursive algorithm that solves this problem, given a pointer to the root of T : MaxWtSubtree [r]](/thumbs/79/79323586.jpg) CSE 101 Final Exam Topics: Order, Recurrence Relations, Analyzing Programs, Divide-and-Conquer, Back-tracking, Dynamic Programming, Greedy Algorithms and Correctness Proofs, Data Structures (Heap, Binary
CSE 101 Final Exam Topics: Order, Recurrence Relations, Analyzing Programs, Divide-and-Conquer, Back-tracking, Dynamic Programming, Greedy Algorithms and Correctness Proofs, Data Structures (Heap, Binary
Using the Log Viewer. Accessing the Log Viewer Window CHAPTER
 CHAPTER 6 Users with log permissions can view or delete messages generated by the various servers that make up CCNSC Subscriber Provisioning software. You can display all messages currently in the log
CHAPTER 6 Users with log permissions can view or delete messages generated by the various servers that make up CCNSC Subscriber Provisioning software. You can display all messages currently in the log
CS3DB3/SE4DB3/SE6M03 TUTORIAL
 CS3DB3/SE4DB3/SE6M03 TUTORIAL Mei Jiang Feb 13/15, 2013 Outline Relational Algebra SQL and Relational Algebra Examples Relational Algebra Basic Operators Select: C (R) where C is a list of conditions Project:
CS3DB3/SE4DB3/SE6M03 TUTORIAL Mei Jiang Feb 13/15, 2013 Outline Relational Algebra SQL and Relational Algebra Examples Relational Algebra Basic Operators Select: C (R) where C is a list of conditions Project:
Introduction to Algorithms
 Introduction to Algorithms 6.046J/8.40J/SMA5503 Lecture 4 Prof. Charles E. Leiserson How large should a hash table be? Goal: Make the table as small as possible, but large enough so that it won t overflow
Introduction to Algorithms 6.046J/8.40J/SMA5503 Lecture 4 Prof. Charles E. Leiserson How large should a hash table be? Goal: Make the table as small as possible, but large enough so that it won t overflow
Consensus Answers for Queries over Probabilistic Databases. Jian Li and Amol Deshpande University of Maryland, College Park, USA
 Consensus Answers for Queries over Probabilistic Databases Jian Li and Amol Deshpande University of Maryland, College Park, USA Probabilistic Databases Motivation: Increasing amounts of uncertain data
Consensus Answers for Queries over Probabilistic Databases Jian Li and Amol Deshpande University of Maryland, College Park, USA Probabilistic Databases Motivation: Increasing amounts of uncertain data
Database Applications (15-415)
 Database Applications (15-415) DBMS Internals- Part VII Lecture 15, March 17, 2014 Mohammad Hammoud Today Last Session: DBMS Internals- Part VI Algorithms for Relational Operations Today s Session: DBMS
Database Applications (15-415) DBMS Internals- Part VII Lecture 15, March 17, 2014 Mohammad Hammoud Today Last Session: DBMS Internals- Part VI Algorithms for Relational Operations Today s Session: DBMS
Unsupervised Sentiment Analysis Using Item Response Theory Models
 Unsupervised Sentiment Analysis Using Item Response Theory Models Nathan Danneman NLP DC March 12, 2014 Nathan Danneman IRT Models NLP DC Mar 12, 2014 1 / 24 Table of Contents 1 Introductions 2 IRT History
Unsupervised Sentiment Analysis Using Item Response Theory Models Nathan Danneman NLP DC March 12, 2014 Nathan Danneman IRT Models NLP DC Mar 12, 2014 1 / 24 Table of Contents 1 Introductions 2 IRT History
CSE 421 Applications of DFS(?) Topological sort
 CSE 421 Applications of DFS(?) Topological sort Yin Tat Lee 1 Precedence Constraints In a directed graph, an edge (i, j) means task i must occur before task j. Applications Course prerequisite: course
CSE 421 Applications of DFS(?) Topological sort Yin Tat Lee 1 Precedence Constraints In a directed graph, an edge (i, j) means task i must occur before task j. Applications Course prerequisite: course
Copyright 2000, Kevin Wayne 1
 Guessing Game: NP-Complete? 1. LONGEST-PATH: Given a graph G = (V, E), does there exists a simple path of length at least k edges? YES. SHORTEST-PATH: Given a graph G = (V, E), does there exists a simple
Guessing Game: NP-Complete? 1. LONGEST-PATH: Given a graph G = (V, E), does there exists a simple path of length at least k edges? YES. SHORTEST-PATH: Given a graph G = (V, E), does there exists a simple
On the Max Coloring Problem
 On the Max Coloring Problem Leah Epstein Asaf Levin May 22, 2010 Abstract We consider max coloring on hereditary graph classes. The problem is defined as follows. Given a graph G = (V, E) and positive
On the Max Coloring Problem Leah Epstein Asaf Levin May 22, 2010 Abstract We consider max coloring on hereditary graph classes. The problem is defined as follows. Given a graph G = (V, E) and positive
Data Structures for Range Minimum Queries in Multidimensional Arrays
 Data Structures for Range Minimum Queries in Multidimensional Arrays Hao Yuan Mikhail J. Atallah Purdue University January 17, 2010 Yuan & Atallah (PURDUE) Multidimensional RMQ January 17, 2010 1 / 28
Data Structures for Range Minimum Queries in Multidimensional Arrays Hao Yuan Mikhail J. Atallah Purdue University January 17, 2010 Yuan & Atallah (PURDUE) Multidimensional RMQ January 17, 2010 1 / 28
Math 5593 Linear Programming Lecture Notes
 Math 5593 Linear Programming Lecture Notes Unit II: Theory & Foundations (Convex Analysis) University of Colorado Denver, Fall 2013 Topics 1 Convex Sets 1 1.1 Basic Properties (Luenberger-Ye Appendix B.1).........................
Math 5593 Linear Programming Lecture Notes Unit II: Theory & Foundations (Convex Analysis) University of Colorado Denver, Fall 2013 Topics 1 Convex Sets 1 1.1 Basic Properties (Luenberger-Ye Appendix B.1).........................
Introduction to Query Processing and Query Optimization Techniques. Copyright 2011 Ramez Elmasri and Shamkant Navathe
 Introduction to Query Processing and Query Optimization Techniques Outline Translating SQL Queries into Relational Algebra Algorithms for External Sorting Algorithms for SELECT and JOIN Operations Algorithms
Introduction to Query Processing and Query Optimization Techniques Outline Translating SQL Queries into Relational Algebra Algorithms for External Sorting Algorithms for SELECT and JOIN Operations Algorithms
Multi-objective Optimization
 Some introductory figures from : Deb Kalyanmoy, Multi-Objective Optimization using Evolutionary Algorithms, Wiley 2001 Multi-objective Optimization Implementation of Constrained GA Based on NSGA-II Optimization
Some introductory figures from : Deb Kalyanmoy, Multi-Objective Optimization using Evolutionary Algorithms, Wiley 2001 Multi-objective Optimization Implementation of Constrained GA Based on NSGA-II Optimization
IS 709/809: Computational Methods in IS Research. Algorithm Analysis (Sorting)
 IS 709/809: Computational Methods in IS Research Algorithm Analysis (Sorting) Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Sorting Problem Given an
IS 709/809: Computational Methods in IS Research Algorithm Analysis (Sorting) Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Sorting Problem Given an
HOMEWORK 4 SOLUTIONS. Solution: The Petersen graph contains a cycle of odd length as a subgraph. Hence,
 HOMEWORK 4 SOLUTIONS (1) Determine the chromatic number of the Petersen graph. Solution: The Petersen graph contains a cycle of odd length as a subgraph. Hence, 3 χ(c 5 ) χ(p ). As the Petersen graph is
HOMEWORK 4 SOLUTIONS (1) Determine the chromatic number of the Petersen graph. Solution: The Petersen graph contains a cycle of odd length as a subgraph. Hence, 3 χ(c 5 ) χ(p ). As the Petersen graph is
Towards Robust Indexing for Ranked Queries
 Towards Robust Indexing for Ranked Queries Dong Xin Chen Chen Jiawei Han Department of Computer Science University of Illinois at Urbana-Champaign Urbana, IL, 61801 {dongxin, cchen37, hanj}@uiuc.edu ABSTRACT
Towards Robust Indexing for Ranked Queries Dong Xin Chen Chen Jiawei Han Department of Computer Science University of Illinois at Urbana-Champaign Urbana, IL, 61801 {dongxin, cchen37, hanj}@uiuc.edu ABSTRACT
(Refer Slide Time: 00:02:00)
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 18 Polyfill - Scan Conversion of a Polygon Today we will discuss the concepts
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 18 Polyfill - Scan Conversion of a Polygon Today we will discuss the concepts
3. Cluster analysis Overview
 Université Laval Multivariate analysis - February 2006 1 3.1. Overview 3. Cluster analysis Clustering requires the recognition of discontinuous subsets in an environment that is sometimes discrete (as
Université Laval Multivariate analysis - February 2006 1 3.1. Overview 3. Cluster analysis Clustering requires the recognition of discontinuous subsets in an environment that is sometimes discrete (as
Optimal Routing and Scheduling in Multihop Wireless Renewable Energy Networks
 Optimal Routing and Scheduling in Multihop Wireless Renewable Energy Networks ITA 11, San Diego CA, February 2011 MHR. Khouzani, Saswati Sarkar, Koushik Kar UPenn, UPenn, RPI March 23, 2011 Khouzani, Sarkar,
Optimal Routing and Scheduling in Multihop Wireless Renewable Energy Networks ITA 11, San Diego CA, February 2011 MHR. Khouzani, Saswati Sarkar, Koushik Kar UPenn, UPenn, RPI March 23, 2011 Khouzani, Sarkar,
Quick-Sort fi fi fi 7 9. Quick-Sort Goodrich, Tamassia
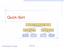 Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
Algorithms and applications for answering ranked queries using ranked views
 The VLDB Journal (24) 13: 49 7 / Digital Object Identifier (DOI) 1.17/s778-3-99-8 Algorithms and applications for answering ranked queries using ranked views Vagelis Hristidis 1, Yannis Papakonstantinou
The VLDB Journal (24) 13: 49 7 / Digital Object Identifier (DOI) 1.17/s778-3-99-8 Algorithms and applications for answering ranked queries using ranked views Vagelis Hristidis 1, Yannis Papakonstantinou
Evaluating Top-N Queries in n-dimensional Normed Spaces
 Evaluating Top-N Queries in n-dimensional Normed Spaces Liang Zhu 1, Feifei Liu 1, Weiyi Meng 2, Qin Ma 3, Yu Wang 1, Fang Yuan 4 1 Intelligent Database Laboratory, School of Computer Science and Technology,
Evaluating Top-N Queries in n-dimensional Normed Spaces Liang Zhu 1, Feifei Liu 1, Weiyi Meng 2, Qin Ma 3, Yu Wang 1, Fang Yuan 4 1 Intelligent Database Laboratory, School of Computer Science and Technology,
Advanced ARC Reporting
 COPYRIGHT & TRADEMARKS Copyright 1998, 2009, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks
COPYRIGHT & TRADEMARKS Copyright 1998, 2009, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks
Approximation Algorithms for Clustering Uncertain Data
 Approximation Algorithms for Clustering Uncertain Data Graham Cormode AT&T Labs - Research graham@research.att.com Andrew McGregor UCSD / MSR / UMass Amherst andrewm@ucsd.edu Introduction Many applications
Approximation Algorithms for Clustering Uncertain Data Graham Cormode AT&T Labs - Research graham@research.att.com Andrew McGregor UCSD / MSR / UMass Amherst andrewm@ucsd.edu Introduction Many applications
