Steganos Security Suite 2006 released to increase privacy protection for UK PC users
|
|
|
- Morgan French
- 5 years ago
- Views:
Transcription
1 1 Steganos Security Suite 2006 released to increase privacy protection for UK PC users The latest version of the leading encryption software offers stronger encryption and more user-friendly decryption, defence against 100,000 malware programs, secure deletion of data and user behaviour traces, AntiTheft-technology that can help to recover stolen computers, a password manager and password-protected browser favourites. 11 October Steganos, European leader in providing security and privacy software for consumers and SMEs, has launched Steganos Security Suite This latest version of the leading privacy protection suite includes the latest releases of Steganos Safe 8 and Steganos AntiSpyware 2006, as well as a raft of features exclusive to this suite. Highlights of the new software include: Support for 256 bit encryption using the never-cracked AES algorithm USB-sticks, mobile phones or digital cameras can be used to unlock encrypted drives USB sticks can be used as rewriteable encrypted safes Steganos AntiTheft: gives a PC owner data on where their PC is being used so stolen machines can more easily be recovered Password-protection for browser favourites Integrated Internet Trace Destructor and Shredder Password Manager can now automatically enter passwords as well as storing them Automatic Crash Protection Free updates for a generation of the software Steganos Security Suite 2006 in detail Steganos Safe 8 With Steganos Safe 8, also available as standalone product, users can create an unlimited number of secure, encrypted virtual drives, each containing up to 64GB of data. The drives can be accessed directly from within applications, through Windows Explorer and through any internet browser. Safe 8 uses the long-established but never cracked international encryption standard AES (Advanced Encryption Standard). Previous versions of Steganos Safe employed 128-bit AES. Now using 256 bit keys, Safe 8 provides a level of encryption that is considered by the US National Security Agency to be of a high enough standard to protect its data classified as top secret.
2 2 Drives can be unlocked using USB keys, storage cards, digital cameras or even wirelessly using ActiveSync-compatible mobile telephones and Bluetooth. The secure data is automatically unlocked when the device is connected and is automatically locked when the device is removed again. USB keys can now be used as rewritable mobile safes: Data can be added from any PC when the key is removed all data is securely encrypted. Encrypted archives can be burned to CD, DVD, and the 8.5GB capacity DVD-DL disks. The content of the encrypted storage can be opened on any PC without additional software. Steganos File Manager and encryption Steganos Security Suite 2006 encrypts and hides sensitive data invisibly in image and sound files so that they don t attract attention. Users can encrypt individual files or whole drives and even s can be encrypted for sending. The self-decrypting s can be opened on receipt without any additional software. Steganos AntiSpyware 2006 Steganos AntiSpyware, also available as standalone product, is included in the Steganos Security Suite for the first time. Steganos AntiSpyware erects a defence against identity theft and will help computer users to protect their hardware, software and data from malicious programs and hackers. Steganos AntiSpyware 2006 now destroys over 100,000 malware programs and has been optimised to run up to 400% faster than the previous version. The software offers realtime protection and prevents personal data being sent over the internet, browser favourites being manipulated, the start page being hijacked and search requests being diverted. The application comes with a year of fully automated free updates. The programs identified and fully destroyed by AntiSpyware include: Keyloggers - which monitor keypresses and help hackers to steal passwords; Remote access trojans which hackers can use to control computers remotely; Denial of service agents which can be used to initiate attacks against websites and internet connections, thereby damaging the user s connection availability. Steganos AntiSpyware complements firewalls and antivirus programs which do not seek out these threats. Steganos Shredder
3 3 To ensure data is securely deleted, Steganos Security Suite includes Steganos Shredder. This provides three methods of destroying unwanted data: simple overwriting, the technology of the US Department of Defense DoD M/NISPOM and the Gutmann method with 35 rounds of overwriting. The deep cleaning shredder can eliminate any remains from files previously deleted using other means, ensuring that there is no data on the disk s free space which can be reconstituted. This is especially important if a computer is being sold on the second hand market. Internet Trace Destructor The integrated Steganos Internet Trace Destructor 2006 now destroys over 200 surf and work traces. With a mouse click, users can delete history traces from browsers (now including Firefox), AIM and other messengers, Google Toolbar and Desktop Search, Media Player, and search requests on peer to peer networks. Data can be deleted on request or automatically after surfing. In the latest version it is also possible for traces to be discreetly deleted in the background without on-screen notifications. With a click, users can select different trace groups, such as Windows or browser traces. This enables files that consume excessive space or threaten the user s privacy to be chosen for removal. Users can store their trace deletion preferences. Steganos Password Manager Steganos Password Manager enables users to store and manage their passwords, including automated entry of user name and password at password-protected websites: the user only has to remember the password for the Password Manager. It can also create secure passwords automatically by extrapolating random codes from mouse movements. The user just chooses how many characters the password should have and whether numbers or special characters should be used. Private Favorites The user s favourite Web sites remain private: The list of favorites is password-protected. Steganos AntiTheft By using Steganos AntiTheft, computer owners can increase the likelihood of recovering their computer should it be stolen. When the program is activated, the computer is given
4 4 an ID and regularly communicates with the Steganos Server. Should a computer be stolen, the owner can log in at the Steganos website to see the IP addresses of that computer s connections to the internet in the last 30 days. With the assistance of the appropriate internet service providers, this data can be used to identify where the computer was connected to the internet and whose internet access account was used to connect it. System requirements Windows 2000, Windows XP Home Edition, Windows XP Professional Internet access 27MB free disk space for installation Minimum screen resolution of 800x600; at least high colour (16 Bit) At least 40MB free memory, 60MB free memory recommended At least Pentium or comparable processor Mouse or other pointing device Requirements for Steganos Safe8: Additional hard disk space is required for secure storage. The NFTS file system is required for the full use of 64GB secure drives. With the FAT32 file system, drives have a maximum possible size of 4GB. For the portable safe, a CD or DVD burner with corresponding software is required. Up to 8.5GB is required as temporary storage space for optimal use. The use of Steganos Portable Safes on computers without Steganos Safe8 installed requires administrator rights. Supported devices: ActiveSync-compatible devices (eg phones, PDAs); all devices that Windows recognises as a writeable storage device (eg USB keys, storage cards, digital cameras). Bluetooth must be supported by the computer and mobile phone for wireless unlocking to be supported. Storage devices and key devices are not supplied by Steganos. Availability Steganos Security Suite 2006 is available online at now and the boxed version will be available 7 October 2005.
5 5 Price Download and boxed versions are Users can upgrade from the previous version of Steganos Security Suite for Review software If you would like to request review copies of the software, please call Kate Boulby on or her at About Steganos About Steganos: Founded in 1996 in Germany, Steganos offers a complete portfolio of user-friendly security and privacy products, including encryption/steganography, antivirus protection, personal firewall and internet anonymity software. Steganos has more than two million users throughout Europe, North America and Latin America. The company markets and sells its products through its website and through its growing network of global resellers, retailers and electronic software distributors. Steganos is a privately held company. For more information on Steganos, see:
Steganos Safe Professional th June 2007
 Steganos Safe Professional 2007 26 th June 2007 Contents Page Introduction 4 Installation and Deployment 5 Managing and Policies 6 Recovery Using EDK 8 Setting Up Network Shares 8 Creating A Key Pair 8
Steganos Safe Professional 2007 26 th June 2007 Contents Page Introduction 4 Installation and Deployment 5 Managing and Policies 6 Recovery Using EDK 8 Setting Up Network Shares 8 Creating A Key Pair 8
Data Security Double Package Sexy & Fresh: The new Steganos Safe 11 and Steganos Privacy Suite 11 are out!
 PRESS RELEASE APPROVED FOR RELEASE Data Security Double Package Sexy & Fresh: The new Steganos Safe 11 and Steganos Privacy Suite 11 are out! Steganos, the Frankfurt based expert on encryption and anonymization
PRESS RELEASE APPROVED FOR RELEASE Data Security Double Package Sexy & Fresh: The new Steganos Safe 11 and Steganos Privacy Suite 11 are out! Steganos, the Frankfurt based expert on encryption and anonymization
Seqrite Antivirus for Server
 Best server security with optimum performance. Product Highlights Easy installation, optimized antivirus scanning, and minimum resource utilization. Robust and interoperable technology makes it one of
Best server security with optimum performance. Product Highlights Easy installation, optimized antivirus scanning, and minimum resource utilization. Robust and interoperable technology makes it one of
Quick Heal AntiVirus Pro. Tough on malware, light on your PC.
 Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
Discount Kaspersky PURE 3.0 internet download software for windows 8 ]
![Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Discount Kaspersky PURE 3.0 internet download software for windows 8 ]](/thumbs/71/65538451.jpg) Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Description: Extended benefits Award-winning protection against all types of Internet threats Online shopping, banking and social
Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Description: Extended benefits Award-winning protection against all types of Internet threats Online shopping, banking and social
Quick Heal AntiVirus for Server. Optimized Antivirus Scanning. Low on Resources. Strong on Technology.
 Optimized Antivirus Scanning. Low on Resources. Strong on Technology. Product Highlights Quick Heal» Easy installation, optimized antivirus scanning, and minimum resource utilization.» Robust and interoperable
Optimized Antivirus Scanning. Low on Resources. Strong on Technology. Product Highlights Quick Heal» Easy installation, optimized antivirus scanning, and minimum resource utilization.» Robust and interoperable
CleanMyPC User Guide
 CleanMyPC User Guide Copyright 2017 MacPaw Inc. All rights reserved. macpaw.com CONTENTS Overview 3 About CleanMyPC... 3 System requirements... 3 Download and installation 4 Activation and license reset
CleanMyPC User Guide Copyright 2017 MacPaw Inc. All rights reserved. macpaw.com CONTENTS Overview 3 About CleanMyPC... 3 System requirements... 3 Download and installation 4 Activation and license reset
Quick Heal Total Security
 For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
ACRONIS TRUE IMAGE 11 HOME REVIEWER S GUIDE
 ACRONIS TRUE IMAGE 11 HOME REVIEWER S GUIDE Acronis True Image 11.0 Home provides the maximum flexibility to ensure you are adequately protected and can recover from unforeseen events such as viruses,
ACRONIS TRUE IMAGE 11 HOME REVIEWER S GUIDE Acronis True Image 11.0 Home provides the maximum flexibility to ensure you are adequately protected and can recover from unforeseen events such as viruses,
User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Review Kaspersky Internet Security - multi-device 2015 online software downloader ]
![Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Review Kaspersky Internet Security - multi-device 2015 online software downloader ]](/thumbs/72/67088147.jpg) Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Description: Benefits Protecting all your connected devices the one-licence, easy-touse solution Kaspersky Internet Security
Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Description: Benefits Protecting all your connected devices the one-licence, easy-touse solution Kaspersky Internet Security
Ethical Hacking and Countermeasures: Secure Network Operating Systems and Infrastructures, Second Edition
 Ethical Hacking and Countermeasures: Secure Network Operating Systems and Infrastructures, Second Edition Chapter 7 Hacking Mobile Phones, PDAs, and Handheld Devices Objectives After completing this chapter,
Ethical Hacking and Countermeasures: Secure Network Operating Systems and Infrastructures, Second Edition Chapter 7 Hacking Mobile Phones, PDAs, and Handheld Devices Objectives After completing this chapter,
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
What Storage Security Will Users Tolerate and What do they Need?
 What Storage Security Will Users Tolerate and What do they Need? Tom Coughlin Coughlin Associates www.tomcoughlin.com 2006 Coughlin Associates 1 Outline Security definition Data security trends and customer
What Storage Security Will Users Tolerate and What do they Need? Tom Coughlin Coughlin Associates www.tomcoughlin.com 2006 Coughlin Associates 1 Outline Security definition Data security trends and customer
ABOUT LAVASOFT. Contact. Lavasoft Product Sheet: Ad-Aware Free Antivirus+
 ABOUT LAVASOFT Company Overview Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available
ABOUT LAVASOFT Company Overview Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available
PGP NetShare Quick Start Guide Version 10.2
 PGP NetShare Quick Start Guide Version 10.2 What is PGP NetShare? The PGP NetShare product is a software tool that provides multiple ways to protect and share your data. Use PGP NetShare to: Let authorized
PGP NetShare Quick Start Guide Version 10.2 What is PGP NetShare? The PGP NetShare product is a software tool that provides multiple ways to protect and share your data. Use PGP NetShare to: Let authorized
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Help & User Manual. Table of Contents. 1 Introduction of Safe-All. 2 Safe-All Installation. 3 Safe-All Login. 4 Safe-All Functions & Features
 Help & User Manual Table of Contents No. Chapter 1 Introduction of Safe-All 2 Safe-All Installation 3 Safe-All Login 4 Safe-All Functions & Features 4.1 Virtual Drive 4.2 Shredder 4.3 Disk-Wipe 5 Tools
Help & User Manual Table of Contents No. Chapter 1 Introduction of Safe-All 2 Safe-All Installation 3 Safe-All Login 4 Safe-All Functions & Features 4.1 Virtual Drive 4.2 Shredder 4.3 Disk-Wipe 5 Tools
The best for everyday PC users
 The best for everyday PC users 2019 ESET Internet Security delivers rock-solid protection for everyday web users, built on ESET s trademark best mix of detection, speed and usability. Legendary antivirus
The best for everyday PC users 2019 ESET Internet Security delivers rock-solid protection for everyday web users, built on ESET s trademark best mix of detection, speed and usability. Legendary antivirus
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 ESET SMART SECURITY PREMIUM IS ALL-IN-ONE INTERNET SECURITY SOFTWARE. IT KEEPS YOU SAFE ONLINE AND OFFLINE - AND INCLUDES
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 ESET SMART SECURITY PREMIUM IS ALL-IN-ONE INTERNET SECURITY SOFTWARE. IT KEEPS YOU SAFE ONLINE AND OFFLINE - AND INCLUDES
Quick Heal Mobile Security. Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
ESET NOD32 ANTIVIRUS 8
 ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 7
 ESET NOD32 ANTIVIRUS 7 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 7 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Seqrite Endpoint Security
 Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Lenovo Europe, Middle East, and Africa Hardware Announcement ZG , dated January 27, 2009
 Hardware Announcement ZG09-0077, dated January 27, 2009 Utimaco SafeGuard Enterprise suite of offerings for ThinkVantage Technologies offers hard drive encryption and additional modules for complete PC
Hardware Announcement ZG09-0077, dated January 27, 2009 Utimaco SafeGuard Enterprise suite of offerings for ThinkVantage Technologies offers hard drive encryption and additional modules for complete PC
Built without compromise for users who want it all
 Built without compromise for users who want it all 2019 Enjoy your digital life, secured by ESET s ultimate multilayered antimalware protection for all internet users, built on ESET s trademark best mix
Built without compromise for users who want it all 2019 Enjoy your digital life, secured by ESET s ultimate multilayered antimalware protection for all internet users, built on ESET s trademark best mix
Table of Contents. User Guide
 Table of Contents Locate Laptop Laptop Tracking & Data Security 2 Feature: 2 Port Locker Stop Information & File Leaks 3 Feature 3 BitDefender Internet Security Secure Your Every Bit 3 Feature: 3 PROTEGENT
Table of Contents Locate Laptop Laptop Tracking & Data Security 2 Feature: 2 Port Locker Stop Information & File Leaks 3 Feature 3 BitDefender Internet Security Secure Your Every Bit 3 Feature: 3 PROTEGENT
The process by which a user can associate specific permissions to each username.
 Jargon Buster A Antispyware A program that detects and removes malicious programs on your computer called spyware. Once it is installed can collect information without the users consent, that can be almost
Jargon Buster A Antispyware A program that detects and removes malicious programs on your computer called spyware. Once it is installed can collect information without the users consent, that can be almost
Microsoft Questions $ Answers
 Microsoft 98-375 Questions $ Answers Number: 98-375 Passing Score: 700 Time Limit: 45 min File Version: 35.4 http://www.gratisexam.com/ Microsoft 98-375 Questions $ Answers Exam Name: HTML5 Application
Microsoft 98-375 Questions $ Answers Number: 98-375 Passing Score: 700 Time Limit: 45 min File Version: 35.4 http://www.gratisexam.com/ Microsoft 98-375 Questions $ Answers Exam Name: HTML5 Application
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server Click here to download the most recent version of this document
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET INTERNET SECURITY IS ALL-IN-ONE INTERNET SECURITY SOFTWARE.
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET INTERNET SECURITY IS ALL-IN-ONE INTERNET SECURITY SOFTWARE.
ESET SMART SECURITY 10
 ESET SMART SECURITY 10 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security software.
ESET SMART SECURITY 10 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security software.
About Lavasoft. Contact. Key Facts:
 About Lavasoft Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available to everybody,
About Lavasoft Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available to everybody,
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
FOR macos. Quick Start Guide. Click here to download the most recent version of this document
 FOR macos Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based
FOR macos Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based
Sophos Mobile Security
 Help Product Version: 8.5 Contents About Sophos Mobile Security...1 Dashboard... 2 Scanner... 3 Web Filtering... 4 App Protection...5 Call Blocking...6 Loss & Theft...7 Configure Loss & Theft... 8 Wi-Fi
Help Product Version: 8.5 Contents About Sophos Mobile Security...1 Dashboard... 2 Scanner... 3 Web Filtering... 4 App Protection...5 Call Blocking...6 Loss & Theft...7 Configure Loss & Theft... 8 Wi-Fi
Free Utilities for Your Computer September 20, 2007
 Free Utilities for Your Computer September 20, 2007 Frank Crua Phil Goff Dean Steichen 1 Free Software Programs Avast! 4 Home Edition AntiVirus www.avast.com ZoneAlarm Firewall www.zonelabs.com WinPatrol
Free Utilities for Your Computer September 20, 2007 Frank Crua Phil Goff Dean Steichen 1 Free Software Programs Avast! 4 Home Edition AntiVirus www.avast.com ZoneAlarm Firewall www.zonelabs.com WinPatrol
Security Awareness. Presented by OSU Institute of Technology
 Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Mobile Computing Policy
 Mobile Computing Policy Overview and Scope 1. The purpose of this policy is to ensure that effective measures are in place to protect against the risks of using mobile computing and communication facilities..
Mobile Computing Policy Overview and Scope 1. The purpose of this policy is to ensure that effective measures are in place to protect against the risks of using mobile computing and communication facilities..
Chapter 1: Introduction About the User Manual Intended Audience Conventions Used Revision History 4
 CLINCK Speed Manager User Manual Contents Chapter 1: Introduction 3 1.1 About the User Manual 3 1.2 Intended Audience 3 1.3 Conventions Used 3 1.4 Revision History 4 1.5 Overview of the CLINCK Speed Manager
CLINCK Speed Manager User Manual Contents Chapter 1: Introduction 3 1.1 About the User Manual 3 1.2 Intended Audience 3 1.3 Conventions Used 3 1.4 Revision History 4 1.5 Overview of the CLINCK Speed Manager
Table of Contents. A. Introduction...2. B. General Description...2. C. Features...3. D. Before Using the Security Application Program LOCK...
 v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Enterprise Cybersecurity Best Practices Part Number MAN Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
F-Secure Mobile Security
 F-Secure Mobile Security for S60 User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or
F-Secure Mobile Security for S60 User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 ESET Smart Security Premium is all-in-one Internet security software. It keeps you safe online and offline - and includes
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 ESET Smart Security Premium is all-in-one Internet security software. It keeps you safe online and offline - and includes
F-Secure Mobile Security
 F-Secure Mobile Security for Windows Mobile User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks
F-Secure Mobile Security for Windows Mobile User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks
Lockngo Professional
 Lockngo Professional User Manual Rev. 26-04.15 Updated for Version 7 Page 1 Table of contents 1. System Requirements...3 2. Using Lockngo...3 2.1. The Lockngo user interface...3 2.2. Locking your portable
Lockngo Professional User Manual Rev. 26-04.15 Updated for Version 7 Page 1 Table of contents 1. System Requirements...3 2. Using Lockngo...3 2.1. The Lockngo user interface...3 2.2. Locking your portable
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Technology in Action 12/11/2014. Cybercrime and Identity Theft (cont.) Cybercrime and Identity Theft (cont.) Chapter Topics
 Technology in Action Alan Evans Kendall Martin Mary Anne Poatsy Eleventh Edition Technology in Action Chapter 9 Securing Your System: Protecting Your Digital Data and Devices Copyright 2015 Pearson Education,
Technology in Action Alan Evans Kendall Martin Mary Anne Poatsy Eleventh Edition Technology in Action Chapter 9 Securing Your System: Protecting Your Digital Data and Devices Copyright 2015 Pearson Education,
Microsoft Questions $ Answers
 Microsoft 98-375 Questions $ Answers Number: 98-375 Passing Score: 700 Time Limit: 45 min File Version: 35.4 http://www.gratisexam.com/ Microsoft 98-375 Questions $ Answers Exam Name: HTML5 Application
Microsoft 98-375 Questions $ Answers Number: 98-375 Passing Score: 700 Time Limit: 45 min File Version: 35.4 http://www.gratisexam.com/ Microsoft 98-375 Questions $ Answers Exam Name: HTML5 Application
Features. Product Highlights. Not just an app, but a friend for your phone. Optimization. Speed. Battery. Storage. Data Usage
 PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
Contents. Introduction 5. McAfee SecurityCenter 7. McAfee QuickClean 39. McAfee Shredder 45
 User Guide i Contents Introduction 5 McAfee SecurityCenter 7 Features... 8 Using SecurityCenter... 9 Header... 9 Left column... 9 Main pane... 10 Understanding SecurityCenter icons... 11 Understanding
User Guide i Contents Introduction 5 McAfee SecurityCenter 7 Features... 8 Using SecurityCenter... 9 Header... 9 Left column... 9 Main pane... 10 Understanding SecurityCenter icons... 11 Understanding
User Guide. Quick Heal Technologies Ltd.
 User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
PCI Compliance Updates
 PCI Compliance Updates PCI Mobile Payment Acceptance Security Guidelines Adam Goslin, Chief Operations Officer AGoslin@HighBitSecurity.com Direct: 248.388.4328 PCI Guidance February, 2013 - PCI Mobile
PCI Compliance Updates PCI Mobile Payment Acceptance Security Guidelines Adam Goslin, Chief Operations Officer AGoslin@HighBitSecurity.com Direct: 248.388.4328 PCI Guidance February, 2013 - PCI Mobile
Defining Computers. Defining Computers. Understanding Essential Computer Concepts
 Understanding Essential Computer Concepts Defining Computers A high-speed idiot must be told exactly what to do by humans and programs step-by-step instructions An electronic device that accepts input,
Understanding Essential Computer Concepts Defining Computers A high-speed idiot must be told exactly what to do by humans and programs step-by-step instructions An electronic device that accepts input,
Install and setup TrueCrypt
 Install and setup TrueCrypt Install and setup TrueCrypt This guide is for organisations and individuals who wish to use TrueCrypt to secure their computer(s) and/or portable USB drives. It explains how
Install and setup TrueCrypt Install and setup TrueCrypt This guide is for organisations and individuals who wish to use TrueCrypt to secure their computer(s) and/or portable USB drives. It explains how
i-vault User Guide Comodo i- Vault User Guide Comodo
 Comodo i- Vault User Guide 1998-2006 Comodo Introduction... 3 Unique features:... 3 Major features:... 3 Hardware and software system requirements... 4 Getting Started... 5 Three easy steps to begin work
Comodo i- Vault User Guide 1998-2006 Comodo Introduction... 3 Unique features:... 3 Major features:... 3 Hardware and software system requirements... 4 Getting Started... 5 Three easy steps to begin work
Online Threats. This include human using them!
 Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
Use of this product is subject to acceptance of the Panda End User License Agreement enclosed. Panda Security TM. TruPrevent: registered in U.S.A. Pat
 Important! Please read the Service activation section of this guide carefully. The information in this section is essential to keep your PC protected. MEGA DETECTION Quick installation guide Windows Vista,
Important! Please read the Service activation section of this guide carefully. The information in this section is essential to keep your PC protected. MEGA DETECTION Quick installation guide Windows Vista,
LabSim Mapping Matrix
 LabSim Mapping Matrix (220-601) Mapping: Chapters to LabSims Chapter Page Number LabSim Chapter 1 Pages 2-3 Pages 2-3 Pages 4-6 Pages 4-6 Pages 3-6 Pages 7-25 1.3.1 Computing Basics 1.3.2 Computing Facts
LabSim Mapping Matrix (220-601) Mapping: Chapters to LabSims Chapter Page Number LabSim Chapter 1 Pages 2-3 Pages 2-3 Pages 4-6 Pages 4-6 Pages 3-6 Pages 7-25 1.3.1 Computing Basics 1.3.2 Computing Facts
Manually Remove Of Xp Internet Security Protect Virus Manually
 Manually Remove Of Xp Internet Security Protect Virus Manually We show you how to remove malware from a PC or laptop. You may also wish to read: Windows users: how to protect your PC from Check now: do
Manually Remove Of Xp Internet Security Protect Virus Manually We show you how to remove malware from a PC or laptop. You may also wish to read: Windows users: how to protect your PC from Check now: do
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Codebook. Codebook for OS X Introduction and Usage
 Codebook Codebook for OS X Introduction and Usage What is Codebook Encrypted Data Vault Guards passwords and private data Keeps sensitive information organized Enables quick recall of secrets Syncs data
Codebook Codebook for OS X Introduction and Usage What is Codebook Encrypted Data Vault Guards passwords and private data Keeps sensitive information organized Enables quick recall of secrets Syncs data
Introduction to Information Security Dr. Rick Jerz
 Introduction to Information Security Dr. Rick Jerz 1 Goals Explain the various types of threats to the security of information Discuss the different categorizations of security technologies and solutions
Introduction to Information Security Dr. Rick Jerz 1 Goals Explain the various types of threats to the security of information Discuss the different categorizations of security technologies and solutions
For this class we are going to create a file in Microsoft Word. Open Word on the desktop.
 File Management Windows 10 What is File Management? As you use your computer and create files you may need some help in storing and retrieving those files. File management shows you how to create, move,
File Management Windows 10 What is File Management? As you use your computer and create files you may need some help in storing and retrieving those files. File management shows you how to create, move,
Kerio Cloud. Adam Bielawski. Cloud Hosted Enterprise-Class , Calendars, Contacts, Tasks, and Instant Messaging. Twitter LinkedIn Facebook
 Kerio Cloud Cloud Hosted Enterprise-Class Email, Calendars, Contacts, Tasks, and Instant Messaging Twitter LinkedIn Facebook Presented by Adam Bielawski June 15, 2016 Why Kerio? Kerio provides safe, simple,
Kerio Cloud Cloud Hosted Enterprise-Class Email, Calendars, Contacts, Tasks, and Instant Messaging Twitter LinkedIn Facebook Presented by Adam Bielawski June 15, 2016 Why Kerio? Kerio provides safe, simple,
MEMORY AND BEHAVIORAL PROTECTION ENDPOINT SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY
 MEMORY AND BEHAVIORAL PROTECTION ENDPOINT SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY FACT: COMPUTERS AND SERVERS ARE STILL AT RISK CONVENTIONAL TOOLS NO LONGER MEASURE UP Despite pouring
MEMORY AND BEHAVIORAL PROTECTION ENDPOINT SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY FACT: COMPUTERS AND SERVERS ARE STILL AT RISK CONVENTIONAL TOOLS NO LONGER MEASURE UP Despite pouring
stickapp anti-virus password manager vpn client free Security & Productivity Apps for SafeStick stickapps.co.uk
 Security & Productivity Apps for SafeStick StickApps are a collection of Security and Productivity apps - some free and some licenced - which have been selected, designed and tested to work on SafeStick
Security & Productivity Apps for SafeStick StickApps are a collection of Security and Productivity apps - some free and some licenced - which have been selected, designed and tested to work on SafeStick
Product Brief. Circles of Trust.
 Product Brief Circles of Trust www.cryptomill.com product overview Circles of Trust is an enterprise security software system that eliminates the risks associated with data breaches from a hacker attack
Product Brief Circles of Trust www.cryptomill.com product overview Circles of Trust is an enterprise security software system that eliminates the risks associated with data breaches from a hacker attack
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
PcZealous [Professional] User Manual
![PcZealous [Professional] User Manual PcZealous [Professional] User Manual](/thumbs/82/86438296.jpg) STEPS TO INSTALL PcZEALOUS [Professional]: Double Click on the PcZealous [Professional] Setup.exe file. In the welcome screen as shown below, Click the Next button Read the Software License Agreement,
STEPS TO INSTALL PcZEALOUS [Professional]: Double Click on the PcZealous [Professional] Setup.exe file. In the welcome screen as shown below, Click the Next button Read the Software License Agreement,
2018 By: RemoveVirus.net. Remove A Virus From Your PC In 5 Simple Steps
 2018 By: RemoveVirus.net Remove A Virus From Your PC In 5 Simple Steps PCs, like Macs and Mobile Devices are susceptible to different types of malware. Avoid panicking when you realize that your PC has
2018 By: RemoveVirus.net Remove A Virus From Your PC In 5 Simple Steps PCs, like Macs and Mobile Devices are susceptible to different types of malware. Avoid panicking when you realize that your PC has
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Cyber Security Basics. Presented by Darrel Karbginsky
 Cyber Security Basics Presented by Darrel Karbginsky What s to come In the following slides I am going to discuss amongst other things and in no particular order things to enlighten, frighten, educate,
Cyber Security Basics Presented by Darrel Karbginsky What s to come In the following slides I am going to discuss amongst other things and in no particular order things to enlighten, frighten, educate,
Reporting for Contact Center Setup and Operations Guide. BCM Contact Center
 Reporting for Contact Center Setup and Operations Guide BCM Contact Center Document Number: Document Status: Standard Document Version: 05.01 Date: September 2006 Copyright 2005 2006 Nortel Networks, All
Reporting for Contact Center Setup and Operations Guide BCM Contact Center Document Number: Document Status: Standard Document Version: 05.01 Date: September 2006 Copyright 2005 2006 Nortel Networks, All
A practical guide to IT security
 Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
An Agency Under MOSTI SECURITY ASSURANCE. Securing Our Cyberspace. Copyright 2008 CyberSecurity Malaysia
 An Agency Under MOSTI Understanding Mobile Phone Threat Vectors 4 th th ETSI Mobile Security Workshop Sophia Antipolis, France SECURITY ASSURANCE Creating Trust & Confidence Mohamad Nizam Kassim, GAWN
An Agency Under MOSTI Understanding Mobile Phone Threat Vectors 4 th th ETSI Mobile Security Workshop Sophia Antipolis, France SECURITY ASSURANCE Creating Trust & Confidence Mohamad Nizam Kassim, GAWN
How To Remove Personal Antivirus Security Pro Virus Windows 8
 How To Remove Personal Antivirus Security Pro Virus Windows 8 When hackers break into government servers to steal your personal data, there's As for just relying on the antivirus built into Windows 8.x,
How To Remove Personal Antivirus Security Pro Virus Windows 8 When hackers break into government servers to steal your personal data, there's As for just relying on the antivirus built into Windows 8.x,
Endpoint Protection. ESET Endpoint Antivirus with award winning ESET NOD32 technology delivers superior detection power for your business.
 Endpoint Protection Antivirus and Antispyware Eliminates all types of threats, including viruses, rootkits, worms and spyware. ESET Endpoint Antivirus with award winning ESET NOD32 technology delivers
Endpoint Protection Antivirus and Antispyware Eliminates all types of threats, including viruses, rootkits, worms and spyware. ESET Endpoint Antivirus with award winning ESET NOD32 technology delivers
Systems and Principles Unit Syllabus
 Systems and Principles Unit Syllabus Level 2 7540-011 www.cityandguilds.com January 2011 Version 1.0 About City & Guilds City & Guilds is the UK s leading provider of vocational qualifications, offering
Systems and Principles Unit Syllabus Level 2 7540-011 www.cityandguilds.com January 2011 Version 1.0 About City & Guilds City & Guilds is the UK s leading provider of vocational qualifications, offering
<Criminal Justice Agency Name> Personally Owned Device Policy. Allowed Personally Owned Device Policy
 Policy Title: Effective Date: Revision Date: Approval(s): LASO: CSO: Agency Head: Allowed Personally Owned Device Policy Every 2 years or as needed Purpose: A personally owned information system or device
Policy Title: Effective Date: Revision Date: Approval(s): LASO: CSO: Agency Head: Allowed Personally Owned Device Policy Every 2 years or as needed Purpose: A personally owned information system or device
A Review Paper on Network Security Attacks and Defences
 EUROPEAN ACADEMIC RESEARCH Vol. IV, Issue 12/ March 2017 ISSN 2286-4822 www.euacademic.org Impact Factor: 3.4546 (UIF) DRJI Value: 5.9 (B+) A Review Paper on Network Security Attacks and ALLYSA ASHLEY
EUROPEAN ACADEMIC RESEARCH Vol. IV, Issue 12/ March 2017 ISSN 2286-4822 www.euacademic.org Impact Factor: 3.4546 (UIF) DRJI Value: 5.9 (B+) A Review Paper on Network Security Attacks and ALLYSA ASHLEY
CHAPTER 8 SECURING INFORMATION SYSTEMS
 CHAPTER 8 SECURING INFORMATION SYSTEMS BY: S. SABRAZ NAWAZ SENIOR LECTURER IN MANAGEMENT & IT SEUSL Learning Objectives Why are information systems vulnerable to destruction, error, and abuse? What is
CHAPTER 8 SECURING INFORMATION SYSTEMS BY: S. SABRAZ NAWAZ SENIOR LECTURER IN MANAGEMENT & IT SEUSL Learning Objectives Why are information systems vulnerable to destruction, error, and abuse? What is
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from
Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from
ESET NOD32 Antivirus 4. Product Briefing
 ESET NOD32 Antivirus 4 Product Briefing Company Profile Global security software company, est. 1992 Headquarters in Bratislava, Slovakia Offices in San Diego, Prague, Buenos Aires, and Krakow Servicing
ESET NOD32 Antivirus 4 Product Briefing Company Profile Global security software company, est. 1992 Headquarters in Bratislava, Slovakia Offices in San Diego, Prague, Buenos Aires, and Krakow Servicing
Author: Tonny Rabjerg Version: Company Presentation WSF 4.0 WSF 4.0
 Author: Tonny Rabjerg Version: 20150730 Company Presentation WSF 4.0 WSF 4.0 Cybercrime is a growth industry. The returns are great, and the risks are low. We estimate that the likely annual cost to the
Author: Tonny Rabjerg Version: 20150730 Company Presentation WSF 4.0 WSF 4.0 Cybercrime is a growth industry. The returns are great, and the risks are low. We estimate that the likely annual cost to the
Microsoft Questions $ Answers
 Microsoft 98-375 Questions $ Answers Number: 98-375 Passing Score: 700 Time Limit: 45 min File Version: 35.4 http://www.gratisexam.com/ Microsoft 98-375 Questions $ Answers Exam Name: HTML5 Application
Microsoft 98-375 Questions $ Answers Number: 98-375 Passing Score: 700 Time Limit: 45 min File Version: 35.4 http://www.gratisexam.com/ Microsoft 98-375 Questions $ Answers Exam Name: HTML5 Application
19 - This PC Inside This PC
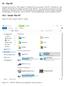 19 - This PC Computer (also known as My Computer in Windows XP) was renamed to This PC in Windows 8.1, and Windows 10 keeps this new naming convention. From This PC, you can get access or browse to all
19 - This PC Computer (also known as My Computer in Windows XP) was renamed to This PC in Windows 8.1, and Windows 10 keeps this new naming convention. From This PC, you can get access or browse to all
MIGRATING FROM WINDOWS XP
 MIGRATING FROM WINDOWS XP WHAT S THE PROBLEM WITH XP? Microsoft is no longer providing security updates for XP after April 8, 2014 After this date, Microsoft Security Essentials (MSE) for XP will no longer
MIGRATING FROM WINDOWS XP WHAT S THE PROBLEM WITH XP? Microsoft is no longer providing security updates for XP after April 8, 2014 After this date, Microsoft Security Essentials (MSE) for XP will no longer
Antivirus: Proactively detects and disables more known and even unknown new malware threats than any other security product.
 Quick Start Guide ESET Cybersecurity provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine first introduced in the award-winning NOD32
Quick Start Guide ESET Cybersecurity provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine first introduced in the award-winning NOD32
Kaspersky Mobile Security 9. Reviewer s Guide
 Kaspersky Mobile Security 9 Reviewer s Guide The purpose of this document is to provide an introduction to Kaspersky Mobile Security 9 (KMS 9). KMS 9 is a product that has been designed to protect the
Kaspersky Mobile Security 9 Reviewer s Guide The purpose of this document is to provide an introduction to Kaspersky Mobile Security 9 (KMS 9). KMS 9 is a product that has been designed to protect the
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
