Avira Internet Security 2012 FireWall. HowTo
|
|
|
- Jordan Chambers
- 5 years ago
- Views:
Transcription
1 Avira Internet Security 2012 FireWall HowTo
2 Table Of Contents 1. Basic knowledge about the Firewall Explanation of the terms Configuration Possibilities Security Level Block all Custom High Medium Low Configuration Adapter rules Application rules Trusted vendors Settings Pop-up settings General information about Child Protection Enable Child Protection User selection Roles Properties of the role Changing the update intervals Changing an update job Product update Restart settings Avira Internet Security Firewall (Status ) 2
3 Basic knowledge about the Firewall 1. Basic knowledge about the Firewall A firewall works with network protocols like e.g. TCP, UDP, IT, etc. A simple example for building up a connection is also called a handshake procedure. This example shows how a communication established between two computers in the Internet. Computer A sends a package with the information that it wants to build up a connection with computer B Computer B answers that it is ready Computer A confirms the answer of Computer B The connection between Computer A and B is now established and the exchange of data can begin. 2. Explanation of the terms TCP The Transmission Control Protocol (TCP) is an agreement (or protocol) about the way data is being exchanged between computers. UDP The User Datagram Protocol (UDP) is a minimal connectionless network protocol. So-called ports are used to send the data with UDP to the right program on the target computer. Therefore, the port number of the service that contains the data is sent as well. Additionally, UPD offers an integrity check by sending a check sum. This makes the detection of an incomplete transmission possible. Flooding Flooding describes the overflow in a network that is caused by packages. Flooding can paralyze the data transmission in a network (or of a single computer) as the computer or the network is overflowed by a mass of requests and cannot react anymore. You can compare that to a traffic jam on a freeway. Ports A port can be compared to a house number. The difference is that a house, in this case a computer, can have several numbers. A port is a part of an address which assigns the arriving package to an application. Avira Internet Security Firewall (Status ) 3
4 Explanation of the terms Example Port 110 is responsible for the service POP3 and guarantees the access to the server. Special applications use port numbers that are firmly assigned by the IANA and generally known. Usually the ports are numbered from 0 to 1023 and are called Well Known Ports. Producers of applications can register ports for their own protocols if necessary, similar to domain names. The registration of the ports offers the advantage that an application can be identified according to the port number, but only if the application uses the IANA registered port. The rest of the ports from port number to are so called Dynamic and/or Private Ports. For further information please click here. Port scan Port scans are executed in order to spy out free ports on the computer. If a computer provides a server service to others, it opens either a TCP/IP or UDP port or both or several ports. A web server has to open the port 80. A port scan finds out which ports are opened on the computer. IP In order to get connected to a computer the Internet Protocol (IP) identifies it with a definite IP address. In case you send a letter to a friend you have to write the street and the city on it. The IP address has the same function. Host File Sometimes the host file is used to block known web servers by entering the local host ( ), so that all requests are sent to the own system. The specialty of this method is that the blockage is valid in the whole system and is not limited to the browser as web filters are. Furthermore you can use these filters against some malware programs if they are trying to get commands from already known servers. URL Uniform Resource Locators (URL) are a kind of Uniform Resource Identifiers (URIs). URLs identify and locate a resource via the used network protocol (e.g. HTTP or FTP) and the location of the resource within the computer networks. As URLs are the first and most frequent kind of URIs the terms are often used as synonyms. In colloquial language URL is frequently used as a synonym for Internet addresses like e.g. Slide-Up A slide-up is a small window that appears slowly on the top right or down right of your screen and disappears after an interaction or after some time. Avira Internet Security Firewall (Status ) 4
5 3. Configuration Possibilities 3.1. Security Level First, you have to decide which security level you want to use. A security level that is too high might cause a malfunction of some system features. Using a security level that is to low you run the risk that not all accesses to your computer are blocked. In general it can be said: If the PC is not connected with a local network and no network-compatible device (e.g. network printer) is located near the PC, the security level can be set to High. This means the computer is invisible in the network. Furthermore, connections from outside are blocked and flooding as well as port scans are prevented. This is the default setting after the installation of the Avira Internet Security. In case the PC is located in a network environment or the PC should have access to network devices like e.g. network printer, the security level should be set on Medium. The High level might block the network printer or not recognize it as the firewall does not know that a printer is available. Please proceed as follows: Start the Avira Control Center You can start it by a left double click on the umbrella symbol. The tray icon is located in the task bar, down right next to the system time. Avira Internet Security Firewall (Status ) 5
6 Open the register FireWall The register is opened by a left mouse click on the register FireWall. The register FireWall is located on the left side of the Control Center below the menu Internet protection. Adaption of the Security Level of the Firewall By clicking and keeping hold of the security level controller you can adapt the security level. The possible levels are Low, Medium, High, Custom and Block all. You can find a description of the levels directly on the right side of the controller. Please choose the level Medium, in case any problems with network printers, removable hard disk or similar network connections should occur Block all All network connections are blocked Custom With this option you can set user defined rules High The computer is invisible in the network and the connections coming from outside are blocked. Flooding and port scan are prevented. Avira Internet Security Firewall (Status ) 6
7 Medium In comparison to the firewall setting High, the computer is visible in the network and receives TCP and UDP requests. These requests are rejected. TCP and UDP packages which are received unexpectedly will not be processed and accepted. Flooding and port scan will be prevented. Problems with the network can occur using the level Medium, too. In this case you should change the level to Low. The preset level is more distinctive in the security level Medium. This means that with Medium some TCP and UDP package requests are recognized and forwarded automatically. Others are rejected Low The level Low offers you the protection of the Avira Firewall, too. Flooding and port scan will not be prevented, only detected. These are the most frequent methods for finding vulnerabilities on your computer. In case these settings are not enough for you or you have to activate different ports for an application, you can find more configurations in chapter 3.2 Configuration Configuration Click with the right mouse button on the tray icon in the task bar and choose the item Configure Avira Internet Security You also have the possibility to start the configuration by opening the Avira Control Center. Thereafter, press F8 or click on Extras > Configuration. In the configuration on the left pane double-click on Internet protection and then on FireWall. Activate the Expert mode in order to have access to all possible settings. Here you can configure the following settings: Adapter rules Application rules Trusted vendors Settings Popup settings Avira Internet Security Firewall (Status ) 7
8 Adapter rules Each hardware entity that is simulated by a software or each hardware entity (e.g. a network interface card) is seen as an adapter (e.g. Miniport, Bridge Connection, etc.) The Avira FireWall shows the adapter rules for all adapters that exist on your computer and have a driver installed. A predefined adapter rule is dependent on the security level. You can change the security level via the Avira Control Center as it is described in chapter 3.1 or change the adapter rules as you like. After you have changed the adapter rules the controller of the firewall is set on the security level Custom. Incoming Rules Incoming rules help to control the incoming data traffic with the Avira FireWall. Example You want to add the IP address Avira Internet Security Firewall (Status ) 8
9 If you click on Add rule, a window opens with different predefined rules. There you choose Incoming IP rule and confirm it with OK. In your Incoming rules you can find the item Incoming IP rule. Select this item. You can also rename it. You can now enter the IP and its mask into the marked box below and enable or block it. You can also decide if the package should be written into the log file or not. Outgoing rules Outgoing rules help to control the outgoing data transfer by means of the Avira FireWall. You can define an outgoing rule for the following protocols: IP ICMP UDP TCP In order to enter settings for the Outgoing rules you can proceed in the same way as for the settings of the Incoming rules. Examples Peer to Peer You can use these default templates if you use e.g. exchange systems, file systems or file sharing systems. Avira Internet Security Firewall (Status ) 9
10 You can add the new rule via the following path: Internet protection > FireWall > Adapter rules > Local Area Connection 2 (Active) Press the Add button and select in the next window Allow Peer-To-Peer network. Click OK to confirm. You only have to enable the needed TCP and UDP ports. Avira Internet Security Firewall (Status ) 10
11 VMware In case the Internet access should not be possible from your VMware, you have to enable it using the following template. To change the settings of Allow VMWARE connections, do the same as in the previous rule for the Peer-To-Peer network. Avira Internet Security Firewall (Status ) 11
12 Application rules This list contains all users in the system. If you are logged on as administrator, you can choose a user and set a rule for him. If you don t have administrative rights, the list only shows you the currently logged on users. Example This way an administrator can make sure that a web browser doesn t receive Internet access or that a chat program cannot be executed. Add application If you click on the button Add application, a new window opens with the programs that are already installed on your computer. Avira Internet Security Firewall (Status ) 12
13 By a simple click the application is marked and can be added to the list with the button Add. Application settings Here you can change the mode from Filtered to Privileged. In the mode Filtered the adapter rules and the application rules are checked. The application rules are checked only in the Privileged mode. Furthermore, the action can be changed from Allow to Deny or Ask. If you choose the action Ask, you are always asked before executing a program if you really want to start the program. In case of the action Deny, the program will be blocked by the Avira Firewall. Avira Internet Security Firewall (Status ) 13
14 Trusted vendors A list of reliable software manufacturers is shown in the menu Trusted vendors. You can add or remove manufacturers on the list by using the option Always trust this vendor in the popup window of the network event. You can allow the network access of applications that are signed by the listed vendors by default. Therefore you activate the option Automatically allow applications created by trusted vendors. Trusted vendors for user This list contains all users in your system. If you are logged on as administrator, you can select a user and view as well as modify his list of trusted vendors. Avira Internet Security Firewall (Status ) 14
15 If you aren t a user with privileged rights, the list only shows you the logged in user. Automatically allow applications created by trusted vendor If this option is activated, applications with a signature of known and trusted vendors get automatically an access to the network. This option is activated by default. We recommend that you keep this option activated since we have the contact data of those vendors. Therefore, the vendors are categorized as trusted vendors. Avira Internet Security Firewall (Status ) 15
16 Vendors The list shows all vendors that have been categorized as trustworthy. Remove The marked entry is removed from the list of trusted vendors. In order to remove the marked vendor definitely from the list, press OK. Avira Internet Security Firewall (Status ) 16
17 Reload With the Reload button all changes are cancelled. The last saved list will be loaded. Note If you remove a vendor from the list and click on Apply the vendor will be removed for good. You can t reload it. But you have the possibility to add the vendor again to the list of trusted vendors using the option Always trust this vendor in the popup window of the network event. The firewall prioritizes application rules: The application rule will be used if you create an application rule and the vendor of the application is part of the list of trusted vendors Settings Automatic rule timeout Block forever A rule that has been created for a portscan is automatically kept. Remove rule after n seconds A rule that has been automatically created, e.g. for a portscan, is removed after the given time. Avira Internet Security Firewall (Status ) 17
18 This option is activated by default. Advanced options Stop Windows Firewall on startup This option deactivates the Windows Firewall on startup. This option is activated by default as the use of two firewalls at the same time might cause problems. Two desktop firewalls interfere with each other. Avira Internet Security Firewall (Status ) 18
19 Notifications Here you can define the category of events that will send a notification from the FireWall. Portscan If you activate this option you will receive a desktop notification in case a portscan has been detected by the FireWall. Portscan are not always malicious, but can be a sign of a possible attack on your system. Flooding You will receive a desktop notification in case a flooding attack has been detected by the FireWall, if you activate this option. Flooding attacks can overload your network with a high volume of data and paralyze your network. Applications blocked In case an application should try to establish an external connection which you have not allowed in the FireWall or which is not privileged, the connection is blocked by the Avira FireWall and you receive a desktop notification. This notification informs you about the application and why it has been blocked. Avira Internet Security Firewall (Status ) 19
20 IP blocked If this options is activated, you will receive a desktop notification in case the FireWall has rejected the data traffic from a certain IP address. We recommend to deactivate this option since there are a lot of unwanted IP address requests in the Internet and as a result, you would receive lots of desktop notifications. Application rules With these options you set the configurations for the application of the FireWall. Advanced settings If you activate this option, you have the possibility to manage different network accesses of an application individually. This means that you create a special application rule for an application. You can manage the traffic for an application individually or you only monitor the application. Basic settings If you activate this option, you can only set one action for different network accesses. Usually this is enough to allow or to block applications. Avira Internet Security Firewall (Status ) 20
21 Pop-up settings Pop-up settings Inspect process launch stack If this option is enabled, the process stack inspection will be more accurate. The FireWall assumes that each process in the stack being deemed as not trustworthy is the one whose child process enables the access to the network. Therefore, a popup-window is opened for each process in the stack that is deemed as untrustworthy. These options are deactivated by default. We recommend you to keep the default settings as you would receive a flow of pop-ups otherwise. Allow multiple pop-ups per process If this option is activated, a pop-up window is opened each time an application tries to build up a network connection. Alternatively, you are informed only on the first connection attempt. This option is deactivated by default. We recommend you to keep the default settings. So you receive only one pop-up window per process. Avira Internet Security Firewall (Status ) 21
22 Remember action for this application Always enabled The option Remember action for this application of the dialog box Network event ist enabled as the default setting. Always disabled The option Remember action for this application of the dialog box Network event ist disabled as the default setting. Enabled for signed applications The option Remember action for this application of the dialogue box Network event is automatically activated for the network access by signed applications of certain vendors. These vendors are: Microsoft, Mozilla, Opera, Yahoo, Google, Hewlet Packard, Sun, Skype, Adobe, Lexmark, Creative Labs, ATI, nvidia. Remember last used state The option Remember action for this application in the dialog box Network event is enabled in the same way as for the last network event. In case the option Remember action for this application has been activated for the last network event, the option will also be active for the following network event. In case the option Remember action for this application has been deactivated for the last network event, the option won t be active for the following network event. Avira Internet Security Firewall (Status ) 22
23 We recommend you to keep this option, so that all actions about the connections of the applications are saved automatically. Show details Here you can configure which detailed information in the box network event is important to you. Show details on demand The detailed information are only displayed on request in the Network event. Details are shown only after a click on the button Show details in the Network event window. Always show details The details are always shown in the Network event window. Remember last used state The display of detailed information is managed in the same way as for the previous network event. Avira Internet Security Firewall (Status ) 23
24 Child Protection 4. General information about Child Protection Avira Internet Security offers a Child protection function to filter undesired or illegal Internet offers. You can assign different roles to different users. A user role is configurable and contains forbidden or allowed URLs (Internet addresses) and forbidden content categories. Powerful URL filter lists are used to block Internet contents according to certain categories. In these URL filter lists URLs are categorized in content groups depending on the content of the websites. The URL filter lists are updated, adjusted and extended every day. They support European languages (English, German, French, Italian, Russian ). The roles child, young person, adult are preconfigured with the corresponding forbidden categories. In order to configure the parental control, you have to activate it first. If this option is enabled, all the web pages requested by the user while navigating the Internet are scanned on the basis of the role assigned to the registered user in the parental control function. In case of a forbidden website the website is blocked and a note appears in the browser. Example If a blocked page is requested, the following browser window appears. Avira Internet Security Firewall (Status ) 24
25 Child Protection 4.1. Enable Child Protection In order to activate the Child Protection, go to the Avira Control Center and activate the Expert mode via Extras > Configuration. Choose Internet Protection > Web Protection on the left side panel. You can open the windows by clicking on the plus in front of Web Protection. The Child Protection is the third item. Select it and activate it on the right pane User selection Select a user and click on Add. The user appears on the right pane with the default setting Child. You can change the role by a simple click. Avira Internet Security Firewall (Status ) 25
26 Child Protection 4.3. Roles You can add a new role or you can change the given roles. In order to add new roles, enter the role name in the free box. Please note that the name should not exceed 30 characters. Example The role child under 16 should be added. Click on Add. The new role appears in the right box. In order to configure the role Child under 16, choose the role and click on Change. Avira Internet Security Firewall (Status ) 26
27 Child Protection Properties of the role Here you can add URLs and block the access to URLs that belong to certain categories. Example and URLs of the category Pornography, Erotica/Sex and Sects should be blocked. The categories are provided by a huge data base of the enterprise Cobion. Furthermore, the web filter has access to a data base of the consumer protection office Hamburg. If you should find a website that belongs to one of those categories, you can categorize it via the Test-A-Site website and have it checked. Avira Internet Security Firewall (Status ) 27
28 Child protection Additionally, it is possible to limit the time of the Internet usage by clicking the button Allowed usage duration. Activate the category Limit time of Internet use and configure the desired maximum Internet surfing time for the current role. By clicking the button Exact usage period you ll get the opportunity to configure the maximum online time at a specified time. Enable Only allow Internet use at the specified times and then select the desired online times within the chart. The time frame for allowed online connection can be set varying from 30 minutes to 24 hours each day. Avira Internet Security Firewall (Status ) 28
29 Update 5. Changing the update intervals The update of the virus definitions are predefined in the scheduler with an interval of two hours. You can change this setting in case a different time or a more frequent update should be necessary. Start the Avira Control Center Click on Extras > Configuration and enable the Expert mode Follow the path PC protection > Update in the left menu item of the user interface. The scheduled time of the automatic update will be displayed in the main window. Preconfigured is a frequent update every two hours with an additional activated job that starts an update every time a connection with the Internet has been established. Avira Internet Security Firewall (Status ) 29
30 Update 5.1. Changing an update job In the Automatic update box you can specifiy the interval that defines when the updates should be performed. To change the interval, highlight one of the time options in the box and change the input with the arrow keys on the right side. With the enabled option Start job while connecting to the Internet (dial-up) an update will be performed every time an Internet connection has been established in addition to the specified update interval. The option Repeat job if time has expired gives the oportunity to perform past update jobs that could not be performed at the specified time Product update Whithin the menu Product update you ll find four different configuration options to run an update. Download and install product updates automatically (recommended) Updates will be downloaded and automatically installed as soon they become available. Avira Internet Security Firewall (Status ) 30
31 Update Download product updates. If a restart is necessary, install the update after the system restart, otherwise install it immediately As soon as product updates are available, they will be downloaded and auto matically installed if no restart ist necessary. Otherwise, the product installation will be executed at the next user-controlled system reboot. Notify user when new product updates are available This option sends a notification when new updates become available. Do not download product updates No automatic update or notification of available product updates are perfor - med. Note Updates to the virus definition file and search engine are performed independently of the settings within the option Product updates. Avira Internet Security Firewall (Status ) 31
32 Update 5.3. Restart settings If you have selected automatic product updates under Local protection > Update > Product update, you can choose between the different restart notification and restart cancellation options. Restart the computer after n Seconds The necessary restart after a product update is performed automatically at the specified interval. A countdown message appears with no option for canceling the computer restart. Periodic restart reminder The restart which is necessary after a product update is not performed auto matically. At the specified interval, you will receive the restart notifications wit hout cancellation options. These notifications let you confirm the computer restart or select the Remind me again option. Query whether computer should be restarted You will receive only one message that offers the option to perform a restart directly or cancel the restart routine. Restart computer without query The restart which is necessary is performed automatically. You will not receive any notification. Avira Internet Security Firewall (Status ) 32
33 Further information You find further information: In the online help of the program In the manual In our knowledge base Avira Internet Security Firewall (Status ) 33
34 This manual was created with great care. However, errors in design and contents cannot be excluded. The reproduction of this publication or parts thereof in any form is prohibited without previous written consent from Avira Operations GmbH & Co. KG. Issued Q Brand and product names are trademarks or registered trademarks of their respective owners. Protected trademarks are not marked as such in this manual. However, this does not mean that they may be used freely Avira Operations GmbH & Co. KG. All rights reserved. Errors and technical modifications are subject to change. Avira Operations GmbH & Co. KG Kaplaneiweg Tettnang Germany Telephone: Facsimile
Avira AntiVir Exchange. Installation of Avira AntiVir Exchange in a Database Availability Group. HowTo
 Avira AntiVir Exchange Installation of Avira AntiVir Exchange in a Database Availability Group HowTo Table of Contents Installation of Avira AntiVir Exchange in a DAG...3 Prerequisites... 3 Making the
Avira AntiVir Exchange Installation of Avira AntiVir Exchange in a Database Availability Group HowTo Table of Contents Installation of Avira AntiVir Exchange in a DAG...3 Prerequisites... 3 Making the
Avira Professional Security Product Updates. Best Practices
 Avira Professional Security Product Updates Best Practices Table of Contents 1. What is Avira Professional Security?... 3 2. Where else can Avira Professional Security be found?... 3 3. Product updates...
Avira Professional Security Product Updates Best Practices Table of Contents 1. What is Avira Professional Security?... 3 2. Where else can Avira Professional Security be found?... 3 3. Product updates...
Avira Free Mac Security Version HowTo
 Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Avira Endpoint Security. HowTo
 Avira Endpoint Security HowTo Table of contents 1. Introduction... 3 2. Product Information... 3 2.1 Operation mode... 3 2.2 Scope of services... 3 2.3 Optimum protection. Fast updates. Efficient administration...4
Avira Endpoint Security HowTo Table of contents 1. Introduction... 3 2. Product Information... 3 2.1 Operation mode... 3 2.2 Scope of services... 3 2.3 Optimum protection. Fast updates. Efficient administration...4
Avira Ultimate Protection Suite. Short guide
 Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Avira AntiVir Version 10 Service Pack 2
 Avira AntiVir Version 10 Service Pack 2 Update Scenarios Standalone Support 05/2011 www.avira.com Errors in design and contents cannot be excluded Avira GmbH Contents Contents... 2 1. Configuration settings...
Avira AntiVir Version 10 Service Pack 2 Update Scenarios Standalone Support 05/2011 www.avira.com Errors in design and contents cannot be excluded Avira GmbH Contents Contents... 2 1. Configuration settings...
Apptix Online Backup by Mozy User Guide
 Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Avira Premium Security Suite User Manual
 Avira Premium Security Suite User Manual Trademarks and Copyright Trademarks AntiVir is a registered trademark of Avira GmbH. Windows is a registered trademark of the Microsoft Corporation in the United
Avira Premium Security Suite User Manual Trademarks and Copyright Trademarks AntiVir is a registered trademark of Avira GmbH. Windows is a registered trademark of the Microsoft Corporation in the United
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Avira Version 2012 Service Pack 0 Release Information
 Release Information 1. Increased stability and reliability All components have been made more resilient in order to resist against targeted malware attacks which become increasingly more aggressive. The
Release Information 1. Increased stability and reliability All components have been made more resilient in order to resist against targeted malware attacks which become increasingly more aggressive. The
Internetworking Models The OSI Reference Model
 Internetworking Models When networks first came into being, computers could typically communicate only with computers from the same manufacturer. In the late 1970s, the Open Systems Interconnection (OSI)
Internetworking Models When networks first came into being, computers could typically communicate only with computers from the same manufacturer. In the late 1970s, the Open Systems Interconnection (OSI)
Telephony Toolbar Enterprise. User Guide
 Telephony Toolbar Enterprise User Guide Release 4.4 October 2009 Table of Contents 1 Summary of Changes... 7 1.1 Changes for this Release... 7 2 About This Guide... 8 2.1 Open Telephony Toolbar-Corporate...
Telephony Toolbar Enterprise User Guide Release 4.4 October 2009 Table of Contents 1 Summary of Changes... 7 1.1 Changes for this Release... 7 2 About This Guide... 8 2.1 Open Telephony Toolbar-Corporate...
Kaspersky Security for Windows Server
 Kaspersky Security for Windows Server User's Guide Application version: 10.1.0.622 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Kaspersky Security for Windows Server User's Guide Application version: 10.1.0.622 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Avira AntiVir MailGate 3.2 Migration from version 3.1.x to 3.2.x. HowTo
 Avira AntiVir MailGate 3.2 Migration from version 3.1.x to 3.2.x HowTo Table of contents 1. Manual product update via command line...3 2. Manual product update via Security Management Center (SMC)...4
Avira AntiVir MailGate 3.2 Migration from version 3.1.x to 3.2.x HowTo Table of contents 1. Manual product update via command line...3 2. Manual product update via Security Management Center (SMC)...4
Avira Antivirus Security (Version 3.1 SP1) Changelogs. Avira Antivirus Security Version 3.1 SP1 (Status Feb. 11, 2014) 1
 Avira Antivirus Security (Version 3.1 SP1) Changelogs 1 1. General Information Avira Antivirus Security Version 3.1 SP1 will be released to Google Play on 11 th February 2014. 2. Highlights This release
Avira Antivirus Security (Version 3.1 SP1) Changelogs 1 1. General Information Avira Antivirus Security Version 3.1 SP1 will be released to Google Play on 11 th February 2014. 2. Highlights This release
Configuring Windows Security Features
 04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
UbiLive Home Edition 2.0 User Guide
 UbiLive Home Edition 2.0 User Guide 1 Table of contents 1. Product Overview... 3 1.1 Language Supports... 3 2. Installation... 3 2.1 System Requirements... 3 2.2 Installation Procedure... 3 2.3 Firewall
UbiLive Home Edition 2.0 User Guide 1 Table of contents 1. Product Overview... 3 1.1 Language Supports... 3 2. Installation... 3 2.1 System Requirements... 3 2.2 Installation Procedure... 3 2.3 Firewall
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
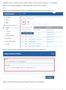 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Network Management Utility
 4343-7705-02 Network Management Utility Foreword Welcome Network Management Utility is utility software that provides central control over printers, copiers, and other devices on a network. With Network
4343-7705-02 Network Management Utility Foreword Welcome Network Management Utility is utility software that provides central control over printers, copiers, and other devices on a network. With Network
NotifySync 4.7. Notify Technology Corporation
 1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
USER GUIDE KASPERSKY MOBILE SECURITY 8.0
 USER GUIDE KASPERSKY MOBILE SECURITY 8.0 Dear User! Thank you for choosing our product. We hope that this documentation will help you in your work and will provide answers regarding this software product.
USER GUIDE KASPERSKY MOBILE SECURITY 8.0 Dear User! Thank you for choosing our product. We hope that this documentation will help you in your work and will provide answers regarding this software product.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
ForeScout Extended Module for Tenable Vulnerability Management
 ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
Exchange Security Small Business Edition. User Manual
 Exchange Security Small Business Edition User Manual Avira Exchange Security - Small Business Edition Table of contents Table of contents 1 Introduction... 3 2 System requirements... 4 3 The Avira Exchange
Exchange Security Small Business Edition User Manual Avira Exchange Security - Small Business Edition Table of contents Table of contents 1 Introduction... 3 2 System requirements... 4 3 The Avira Exchange
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
Comodo Cloud Drive Software Version 1.0
 2 Comodo Cloud Drive Software Version 1.0 User Guide Guide Version 1.0.112017 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Cloud Drive...
2 Comodo Cloud Drive Software Version 1.0 User Guide Guide Version 1.0.112017 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Cloud Drive...
Computer Security and Privacy
 CSE P 590 / CSE M 590 (Spring 2010) Computer Security and Privacy Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others for
CSE P 590 / CSE M 590 (Spring 2010) Computer Security and Privacy Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others for
Manual - TeamViewer 3.5
 Manual - TeamViewer 3.5 Revision TV3.5-3895-g Table of Contents Table of Contents 1 Introduction... 1 1.1.1 About TeamViewer... 1 1.1.2 New in version 3.5... 1 1.1.3 About this manual... 1 2 Installation...
Manual - TeamViewer 3.5 Revision TV3.5-3895-g Table of Contents Table of Contents 1 Introduction... 1 1.1.1 About TeamViewer... 1 1.1.2 New in version 3.5... 1 1.1.3 About this manual... 1 2 Installation...
Kaspersky Security for Windows Server
 Kaspersky Security for Windows Server User's Guide Application version: 10.1.1.746 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Kaspersky Security for Windows Server User's Guide Application version: 10.1.1.746 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Grandstream Networks, Inc. UCM6100 Security Manual
 Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
CityVault Client Manual
 CityVault Client Manual Contents Preface: Preface...4 Chapter 1: Overview...5 Chapter 2: Installing CityVault...6 Downloading the CityVault Client...6 Installing the CityVault Client...6 Configuring CityVault...8
CityVault Client Manual Contents Preface: Preface...4 Chapter 1: Overview...5 Chapter 2: Installing CityVault...6 Downloading the CityVault Client...6 Installing the CityVault Client...6 Configuring CityVault...8
User Manual PDUTracker
 User Manual PDUTracker Management Software for PDU Table of Contents 1. Overview... 1 1.1. Introduction... 1 1.2. Features... 1 2. Install and Uninstall... 1 2.1. System Requirement... 1 2.2. Software
User Manual PDUTracker Management Software for PDU Table of Contents 1. Overview... 1 1.1. Introduction... 1 1.2. Features... 1 2. Install and Uninstall... 1 2.1. System Requirement... 1 2.2. Software
Speed Up Windows by Disabling Startup Programs
 Speed Up Windows by Disabling Startup Programs Increase Your PC s Speed by Preventing Unnecessary Programs from Running Windows All S 630 / 1 When you look at the tray area beside the clock, do you see
Speed Up Windows by Disabling Startup Programs Increase Your PC s Speed by Preventing Unnecessary Programs from Running Windows All S 630 / 1 When you look at the tray area beside the clock, do you see
User Guide For Version 4.0
 User Guide For Version 4.0 Easy-to-use, Complete Cyber Cafe Management Software by icafe Manager User Guide Contents Chapter 1: Introduction 7 1.1 About the Manual 7 1.2 Intended Audience 7 1.3 Conventions
User Guide For Version 4.0 Easy-to-use, Complete Cyber Cafe Management Software by icafe Manager User Guide Contents Chapter 1: Introduction 7 1.1 About the Manual 7 1.2 Intended Audience 7 1.3 Conventions
Quick Start Guide. Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
OPTENET Security Suite Version (Bitdefender Engine) User Guide (rev 1.6)
 OPTENET Security Suite Version 11.01 (Bitdefender Engine) User Guide (rev 1.6) COPYRIGHT No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
OPTENET Security Suite Version 11.01 (Bitdefender Engine) User Guide (rev 1.6) COPYRIGHT No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
UCON-IP-NEO Operation Web Interface
 UCON-IP-NEO Operation Web Interface copyright G&D 25/01/2012 Web Interface version 2.30 Subject to possible errors and technical modifications License notes G&D license Copyright G&D GmbH 2003-2012: All
UCON-IP-NEO Operation Web Interface copyright G&D 25/01/2012 Web Interface version 2.30 Subject to possible errors and technical modifications License notes G&D license Copyright G&D GmbH 2003-2012: All
Quick Start Guide for Administrators and Operators Cyber Advanced Warning System
 NSS Labs Quick Start Guide for Administrators and Operators Cyber Advanced Warning System Introduction to the Cyber Advanced Warning System and RiskViewer... 1 Activating Your Account... 2 Adding a New
NSS Labs Quick Start Guide for Administrators and Operators Cyber Advanced Warning System Introduction to the Cyber Advanced Warning System and RiskViewer... 1 Activating Your Account... 2 Adding a New
I- REQUIREMENTS. A- Main
 Page 1 sur 29 Index 1 REQUIREMENTS... 3 1.1 Main... 3 1.2 Operating system / environment... 3 1.3 Privileges... 4 1.4 Starting installation... 5 1.5 Install program (InstallShield)... 5 2 GT-CENTRAL First
Page 1 sur 29 Index 1 REQUIREMENTS... 3 1.1 Main... 3 1.2 Operating system / environment... 3 1.3 Privileges... 4 1.4 Starting installation... 5 1.5 Install program (InstallShield)... 5 2 GT-CENTRAL First
MD5 FILE HASHER USER MANUAL
 User Manual Digital-Tronic Software Development MD5 FILE HASHER USER MANUAL Dated: October 2014 WELCOME MD5 File Hasher is a simple program which allows you to create and compare check sums. This allows
User Manual Digital-Tronic Software Development MD5 FILE HASHER USER MANUAL Dated: October 2014 WELCOME MD5 File Hasher is a simple program which allows you to create and compare check sums. This allows
Operation Manual Aqua M300. Version and higher
 Operation Manual Aqua M300 Version 1.0.0.4 and higher Contents 1 Functionality of the Menu... 3 1.1 File... 3 1.1.1 Opening a File... 3 1.1.2 Saving a File... 4 1.1.3 Customer s address... 4 1.1.4 Printing...
Operation Manual Aqua M300 Version 1.0.0.4 and higher Contents 1 Functionality of the Menu... 3 1.1 File... 3 1.1.1 Opening a File... 3 1.1.2 Saving a File... 4 1.1.3 Customer s address... 4 1.1.4 Printing...
Top Producer 7i Remote
 Top Producer 7i Remote Quick Setup Top Producer Systems Phone number: 1-800-830-8300 Email: support@topproducer.com www.topproducer.com Fax: 604.270.6365 Top Producer 7i Remote Quick Setup Trademarks Information
Top Producer 7i Remote Quick Setup Top Producer Systems Phone number: 1-800-830-8300 Email: support@topproducer.com www.topproducer.com Fax: 604.270.6365 Top Producer 7i Remote Quick Setup Trademarks Information
BackupVault Desktop & Laptop Edition. USER MANUAL For Microsoft Windows
 BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
Release Notes: Version March 8, Document Version:
 Release Notes: Version 10.1.459 March 8, 2012 Document Version: 110921 MindManager 2012 for Windows Version 10.1.459 -- Release Notes Page 2 Table of Contents OVERVIEW... 3 KEY HIGHLIGHTS... 3 NEW AND
Release Notes: Version 10.1.459 March 8, 2012 Document Version: 110921 MindManager 2012 for Windows Version 10.1.459 -- Release Notes Page 2 Table of Contents OVERVIEW... 3 KEY HIGHLIGHTS... 3 NEW AND
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
SecureAPlus User Guide. Version 3.4
 SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
Kerio Control. User Guide. Kerio Technologies
 Kerio Control User Guide Kerio Technologies 2017 Kerio Technologies s.r.o. Contents Viewing activity reports in Kerio Control Statistics......................... 5 Overview..................................................................
Kerio Control User Guide Kerio Technologies 2017 Kerio Technologies s.r.o. Contents Viewing activity reports in Kerio Control Statistics......................... 5 Overview..................................................................
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amcom Mobile Connect Select for BlackBerry
 User Guide for Amcom Mobile Connect Select for BlackBerry Amcom Software, Inc. Copyright Amcom Mobile Connect Select 3.2 Document Version 1.0 Last Saved Date: September 18, 2012 Copyright 2003-2012 Amcom
User Guide for Amcom Mobile Connect Select for BlackBerry Amcom Software, Inc. Copyright Amcom Mobile Connect Select 3.2 Document Version 1.0 Last Saved Date: September 18, 2012 Copyright 2003-2012 Amcom
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking
 NETWORK MANAGEMENT II Proxy Servers Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking resources from the other
NETWORK MANAGEMENT II Proxy Servers Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking resources from the other
NETWORK PRINT MONITOR User Guide
 NETWORK PRINT MONITOR User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change for improvement without notice. We
NETWORK PRINT MONITOR User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change for improvement without notice. We
KYOCERA Net Admin User Guide
 KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
Activating Intrusion Prevention Service
 Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
Zillya Internet Security User Guide
 Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
ClickCall. User Guide. Please read this manual carefully before operation. Retain it for future reference.
 ClickCall User Guide Please read this manual carefully before operation. Retain it for future reference. Copyright 2013 Ericsson-LG Enterprise Co., Ltd. All Rights Reserved. This material is copyrighted
ClickCall User Guide Please read this manual carefully before operation. Retain it for future reference. Copyright 2013 Ericsson-LG Enterprise Co., Ltd. All Rights Reserved. This material is copyrighted
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Epson Device Admin User s Guide NPD EN
 Epson Device Admin User s Guide NPD5817-00 EN About this Manual About this Manual Marks and Symbols! Caution: Instructions that must be followed carefully to avoid bodily injury. c Important: Instructions
Epson Device Admin User s Guide NPD5817-00 EN About this Manual About this Manual Marks and Symbols! Caution: Instructions that must be followed carefully to avoid bodily injury. c Important: Instructions
CounterACT Check Point Threat Prevention Module
 CounterACT Check Point Threat Prevention Module Version 1.0.0 Table of Contents About the Check Point Threat Prevention Integration... 4 Use Cases... 4 Additional Check Point Threat Prevention Documentation...
CounterACT Check Point Threat Prevention Module Version 1.0.0 Table of Contents About the Check Point Threat Prevention Integration... 4 Use Cases... 4 Additional Check Point Threat Prevention Documentation...
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
AlertMobile Configuration Guide
 MICROMEDIA INTERNATIONAL ALERT - remote alarm management ALERT: AlertMobile Configuration Guide Author: GL Update: GL Pages: 36 Date: 04/07/2018 Version: 3.7.3 AlertMobile Configuration Guide Réf. : HOWTO-Configure
MICROMEDIA INTERNATIONAL ALERT - remote alarm management ALERT: AlertMobile Configuration Guide Author: GL Update: GL Pages: 36 Date: 04/07/2018 Version: 3.7.3 AlertMobile Configuration Guide Réf. : HOWTO-Configure
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Broadband Router DC 202
 Broadband Router DC 202 Full Manual Table of Contents DC-202 xdsl/cable Broadband router REQUIREMENTS...4 INTRODUCTION...4 DC-202 Features...4 Internet Access Features...4 Advanced Internet Functions...5
Broadband Router DC 202 Full Manual Table of Contents DC-202 xdsl/cable Broadband router REQUIREMENTS...4 INTRODUCTION...4 DC-202 Features...4 Internet Access Features...4 Advanced Internet Functions...5
UTM Firewall Registration & Activation Manual DFL-260/ 860. Ver 1.00 Network Security Solution
 UTM Firewall Registration & Activation Manual DFL-260/ 860 Ver 1.00 curitycu Network Security Solution http://security.dlink.com.tw 1.Introduction...02 2.Apply for a D-Link Membership...03 3.D-Link NetDefend
UTM Firewall Registration & Activation Manual DFL-260/ 860 Ver 1.00 curitycu Network Security Solution http://security.dlink.com.tw 1.Introduction...02 2.Apply for a D-Link Membership...03 3.D-Link NetDefend
KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.3 REVIEWER S GUIDE
 KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.3 REVIEWER S GUIDE (4/20/07) WHO IS KERIO? Kerio Technologies provides Internet messaging and firewall software solutions for small to medium sized networks,
KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.3 REVIEWER S GUIDE (4/20/07) WHO IS KERIO? Kerio Technologies provides Internet messaging and firewall software solutions for small to medium sized networks,
Endpoint Security Manager
 Comodo Endpoint Security Manager Software Version 1.6 CIS Configuration Editor Version 1.6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction
Comodo Endpoint Security Manager Software Version 1.6 CIS Configuration Editor Version 1.6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction
Care360 Labs & Meds Frequently Asked Questions
 Frequently Asked Questions Table of Contents Application Interface... 4 How can I see more of on my computer?... 4 What does the message You have multiple sessions open mean?... 4 Why do I receive the
Frequently Asked Questions Table of Contents Application Interface... 4 How can I see more of on my computer?... 4 What does the message You have multiple sessions open mean?... 4 Why do I receive the
KMnet Viewer. User Guide
 KMnet Viewer User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change for improvement without notice. We cannot be
KMnet Viewer User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change for improvement without notice. We cannot be
Mobile Connect for USA Mobility Pagers for BlackBerry
 User Guide for Mobile Connect for USA Mobility Pagers for BlackBerry Amcom Software, Inc. Copyright Mobile Connect 3.5 Document Version 1.0 Last Saved Date: September 19, 2013 Copyright 2003-2013 Amcom
User Guide for Mobile Connect for USA Mobility Pagers for BlackBerry Amcom Software, Inc. Copyright Mobile Connect 3.5 Document Version 1.0 Last Saved Date: September 19, 2013 Copyright 2003-2013 Amcom
Accella Toolbar. User Guide. Release 20.0
 Accella Toolbar User Guide Release 20.0 Table of Contents 2 Introduction... 9 2.1 About Accella Toolbar... 9 2.2 About This Guide... 9 2.3 Accessing Toolbar... 9 2.4 First Time Login... 10 2.5 Subsequent
Accella Toolbar User Guide Release 20.0 Table of Contents 2 Introduction... 9 2.1 About Accella Toolbar... 9 2.2 About This Guide... 9 2.3 Accessing Toolbar... 9 2.4 First Time Login... 10 2.5 Subsequent
Quanum elabs and Quanum EHR Basic Functionality Frequently Asked Questions
 Quanum elabs and Quanum EHR Basic Functionality Frequently Asked Questions Table of Contents Application Interface... 4 How can I optimize the view of the system on my computer?... 4 What does the message
Quanum elabs and Quanum EHR Basic Functionality Frequently Asked Questions Table of Contents Application Interface... 4 How can I optimize the view of the system on my computer?... 4 What does the message
HPE Intelligent Management Center v7.3
 HPE Intelligent Management Center v7.3 Service Operation Manager Administrator Guide Abstract This guide contains comprehensive conceptual information for network administrators and other personnel who
HPE Intelligent Management Center v7.3 Service Operation Manager Administrator Guide Abstract This guide contains comprehensive conceptual information for network administrators and other personnel who
CIS 231 Windows 10 Install Lab # 3
 CIS 231 Windows 10 Install Lab # 3 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in
CIS 231 Windows 10 Install Lab # 3 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in
estos SIP Proxy
 estos SIP Proxy 6.2.3.1357 1 Welcome to estos SIP Proxy... 4 1.1 System requirements... 4 1.2 WAN Settings... 5 1.3 Network interfaces... 5 1.3.1 List of the network interfaces... 5 1.3.2 Configuration
estos SIP Proxy 6.2.3.1357 1 Welcome to estos SIP Proxy... 4 1.1 System requirements... 4 1.2 WAN Settings... 5 1.3 Network interfaces... 5 1.3.1 List of the network interfaces... 5 1.3.2 Configuration
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 ESET Smart Security Premium is all-in-one Internet security software. It keeps you safe online and offline - and includes
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 ESET Smart Security Premium is all-in-one Internet security software. It keeps you safe online and offline - and includes
Chapter 5: Configuring ServerProtect
 Chapter 5: Configuring ServerProtect Chapter Objectives After completing this chapter, you should be able to achieve the following objectives: Describe the types of ServerProtect tasks Describe which actions
Chapter 5: Configuring ServerProtect Chapter Objectives After completing this chapter, you should be able to achieve the following objectives: Describe the types of ServerProtect tasks Describe which actions
User Guide For Universal Devices Administrative Console (ISY)
 User Guide For Universal Devices Administrative Console (ISY) - 1 - Table of Contents 1. PURPOSE 6 2. THEORY OF OPERATION 6 3. INSTALLATION 7 4. CONFIGURATION 8 4.1 Prerequisites 8 4.1.1 Host Computer
User Guide For Universal Devices Administrative Console (ISY) - 1 - Table of Contents 1. PURPOSE 6 2. THEORY OF OPERATION 6 3. INSTALLATION 7 4. CONFIGURATION 8 4.1 Prerequisites 8 4.1.1 Host Computer
Protecting the Platforms. When it comes to the cost of keeping computers in good working order, Chapter10
 Chapter10 Protecting the Platforms Painting: The art of protecting flat surfaces from the weather and exposing them to the critic. Ambrose Bierce (1842 1914) When it comes to the cost of keeping computers
Chapter10 Protecting the Platforms Painting: The art of protecting flat surfaces from the weather and exposing them to the critic. Ambrose Bierce (1842 1914) When it comes to the cost of keeping computers
DKT 224/3 LAB 2 NETWORK PROTOCOL ANALYZER DATA COMMUNICATION & NETWORK SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK
 DKT 224/3 DATA COMMUNICATION & NETWORK LAB 2 NETWORK PROTOCOL ANALYZER SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK Lab #2 2 Lab #2 : Network Protocol Analyzer (Sniffing and Identify Protocol used
DKT 224/3 DATA COMMUNICATION & NETWORK LAB 2 NETWORK PROTOCOL ANALYZER SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK Lab #2 2 Lab #2 : Network Protocol Analyzer (Sniffing and Identify Protocol used
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
2018 By: RemoveVirus.net. Remove A Virus From Your PC In 5 Simple Steps
 2018 By: RemoveVirus.net Remove A Virus From Your PC In 5 Simple Steps PCs, like Macs and Mobile Devices are susceptible to different types of malware. Avoid panicking when you realize that your PC has
2018 By: RemoveVirus.net Remove A Virus From Your PC In 5 Simple Steps PCs, like Macs and Mobile Devices are susceptible to different types of malware. Avoid panicking when you realize that your PC has
Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide
 Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Documentation version:
Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Documentation version:
Amcom Mobile Connect for Android
 User Guide to Amcom Mobile Connect for Android Amcom Software, Inc. Copyright AMC 2.3 Document Version 1.5 Last Saved Date: June 30, 2011 Copyright 2003-2011 Amcom Software, Inc. All Rights Reserved. Information
User Guide to Amcom Mobile Connect for Android Amcom Software, Inc. Copyright AMC 2.3 Document Version 1.5 Last Saved Date: June 30, 2011 Copyright 2003-2011 Amcom Software, Inc. All Rights Reserved. Information
Enterprise Server Edition
 Enterprise Server Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Redstor Limited, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
Enterprise Server Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Redstor Limited, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
User Manual. MPPTracker. Management Software for Solar Charge Controller. Version: 1.2
 User Manual MPPTracker Management Software for Solar Charge Controller Version: 1.2 Table of Contents 1. MPPTracker Overview... 1 1.1. Introduction... 1 1.2. Features... 1 2. MPPTracker Install and Uninstall...
User Manual MPPTracker Management Software for Solar Charge Controller Version: 1.2 Table of Contents 1. MPPTracker Overview... 1 1.1. Introduction... 1 1.2. Features... 1 2. MPPTracker Install and Uninstall...
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Auslogics BOOSTSPEED USER MANUAL. auslogics.
 Auslogics BOOSTSPEED 10 USER MANUAL www..com TABLE OF CONTENTS: Welcome Installation Guide Registering Auslogics BoostSpeed 10 Backing up with the Rescue Center Your First Scan Navigation Panel Navigation
Auslogics BOOSTSPEED 10 USER MANUAL www..com TABLE OF CONTENTS: Welcome Installation Guide Registering Auslogics BoostSpeed 10 Backing up with the Rescue Center Your First Scan Navigation Panel Navigation
Perceptive Document Composition
 Perceptive Document Composition Client Product Guide PDC Version: 5.4 Written by: Product Documentation, R&D Date: February 2014 2014 Perceptive Software. All rights reserved Perceptive Software is a trademark
Perceptive Document Composition Client Product Guide PDC Version: 5.4 Written by: Product Documentation, R&D Date: February 2014 2014 Perceptive Software. All rights reserved Perceptive Software is a trademark
Océ Open Access. User s Guide. Version 2
 Océ Open Access User s Guide Version 2 NOTE: This document is available in multiple electronic formats on the installation CD ROM. The available formats are Portable Document Format (PDF), Microsoft Word
Océ Open Access User s Guide Version 2 NOTE: This document is available in multiple electronic formats on the installation CD ROM. The available formats are Portable Document Format (PDF), Microsoft Word
Group Administrators
 Hosted VoIP Phone System Blue Platform Admin Portal Guide for Group Administrators Table of Contents 1 About this Guide... 6 2 Accessing the Hosted VoIP Phone System Admin Portal... 7 3 Hosted VoIP Admin
Hosted VoIP Phone System Blue Platform Admin Portal Guide for Group Administrators Table of Contents 1 About this Guide... 6 2 Accessing the Hosted VoIP Phone System Admin Portal... 7 3 Hosted VoIP Admin
Total Protection Service
 User Guide McAfee Total Protection Service for Microsoft Windows Home Server COPYRIGHT Copyright 2008 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed,
User Guide McAfee Total Protection Service for Microsoft Windows Home Server COPYRIGHT Copyright 2008 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed,
Table of Contents... ii. Go Ahead Bring Your Own Device to Work... 1 Requirements... 1
 Table of Contents... ii Go Ahead Bring Your Own Device to Work... 1 Requirements... 1 1: Activate AT&T Toggle... 1 1.1: Welcome Email with ORANGE Banner... 1 1.2: Welcome Email with BLUE Banner... 2 1.3:
Table of Contents... ii Go Ahead Bring Your Own Device to Work... 1 Requirements... 1 1: Activate AT&T Toggle... 1 1.1: Welcome Email with ORANGE Banner... 1 1.2: Welcome Email with BLUE Banner... 2 1.3:
CIS 231 Windows 2012 R2 Server Install Lab #1
 CIS 231 Windows 2012 R2 Server Install Lab #1 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems
CIS 231 Windows 2012 R2 Server Install Lab #1 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems
Skill Area 209: Use Internet Technology. Software Application (SWA)
 Skill Area 209: Use Internet Technology Software Application (SWA) Skill Area 209.1 Use Browser for Research (10hrs) 209.1.1 Familiarise with the Environment of Selected Browser Internet Technology The
Skill Area 209: Use Internet Technology Software Application (SWA) Skill Area 209.1 Use Browser for Research (10hrs) 209.1.1 Familiarise with the Environment of Selected Browser Internet Technology The
FAXLAN CLIENT v3.0 USER GUIDE
 FAXLAN CLIENT v3.0 USER GUIDE Draft Version 1.2 May 15 th, 2003 2 TABLE OF CONTENTS 1. FAXLAN CLIENT OVERVIEW... 3 1.1 FAXLAN CLIENT V3.0 FEATURES... 3 1.2 FAXLAN CLIENT V3.0 SYSTEM REQUIREMENTS... 3 2.
FAXLAN CLIENT v3.0 USER GUIDE Draft Version 1.2 May 15 th, 2003 2 TABLE OF CONTENTS 1. FAXLAN CLIENT OVERVIEW... 3 1.1 FAXLAN CLIENT V3.0 FEATURES... 3 1.2 FAXLAN CLIENT V3.0 SYSTEM REQUIREMENTS... 3 2.
Integrating Microsoft Forefront Threat Management Gateway (TMG)
 Integrating Microsoft Forefront Threat Management Gateway (TMG) EventTracker v7.x Publication Date: Sep 16, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This
Integrating Microsoft Forefront Threat Management Gateway (TMG) EventTracker v7.x Publication Date: Sep 16, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This
How to Use Skype & Pamela Software to Record Your Podcast
 How to Use Skype & Pamela Software to Record Your Podcast Network 3000 Publishing 2014 1 Table of Contents Introduction...3 What is Skype?...3 The Popularity of Skype...4 What is Pamela?...4 Time to Get
How to Use Skype & Pamela Software to Record Your Podcast Network 3000 Publishing 2014 1 Table of Contents Introduction...3 What is Skype?...3 The Popularity of Skype...4 What is Pamela?...4 Time to Get
CNBK Communications and Networks Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems
 Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
