Improving the Safety of Malwarebytes Updates
|
|
|
- Helena Pitts
- 5 years ago
- Views:
Transcription
1 Improving the Safety of Malwarebytes Updates Malwarebytes Research and Engineering January 31st, 2018
2 Purpose This document describes how Malwarebytes Research and Engineering is responding to the incident that occurred on the morning of January 27th, On this morning, a protection update was released that caused our Web Protection System to block a wide range of IP addresses, causing outages and system instability for some of our customers. This plan shows the areas that will be addressed, gives the current state of those areas, then lists the steps that are planned to improve those areas. Finally, an estimate of the timeframe to deploy those improvements are also given. The content of this document as well as the timeframes are subject to change. The following are actions have been completed or are planned by Malwarebytes Research and Engineering: Enhanced IP Syntax Checking before Publication Badly-formed IP addresses allowed onto the endpoint, causing unexpected Web Protection blocks Unintended blocking of wide ranges of IPs or top-level domains Unexpected high memory or CPU usage on the endpoint Syntax checking to verify all are correctly formatted Further limiting CIDR ranges to between 24 and 32 Expanded total count of blocked IPs are within realistic range Engineering Plan Planned Validations: o All IPs are correctly formatted o CIDR ranges between 24 and 32 only o Total count of IPs in the expanded list cannot exceed a certain range Changes are required to the build system, the workflow manager and several utility programs that handle and route the IP block lists Completed on January 30th, 2018 Enhanced Malwarebytes Web Filtering Runtime Syntax Checking Badly-formed IP addresses used by the endpoint, causing unexpected IP blocks Unintended blocking of wide ranges of IPs Unintended blocking of non-malicious IP addresses Unexpected high memory or CPU usage on the endpoint 2
3 Syntax checking to verify all are correctly formatted Validate IP address and CIDR range before usage, and reject if improperly formed To prevent excessive memory usage, do not expand the IPs into individual IPs, but keep them in a hashed CIDR format Verify no block attempts on any Malwarebytes service March 1st, 2018 Rollback Support within the Publishing System If all the other preventive measures fail to detect a harmful protection update, ensure a quick rollback of to a known-safe version would greatly reduce the number of endpoints that are affected The current technique is a process that can take from 30 minutes to 3 hours A new process where a rollback is created beforehand, tested and is made available in the chamber for immediate release If a harmful update is detected, Malwarebytes Research can release the rollback update in seconds This will roll all our customers back to a safe protection update that is >24 hours old Once the issues are fixed, a new protection update will be released that will bring all customers to a current protection state This technique will apply to all versions of Malwarebytes for Windows February 28th, 2018 Malwarebytes Endpoint Protection Agent Startup Sequence For our business customers running Malwarebytes Endpoint Protection, in the cases where a harmful detection is blocking its ability to get updates, this approach would allow our customers a route to shut off offending protection features from the management console, long enough to get the endpoint fixed. Customers must shut off protection from the console and then reboot the endpoints. Because of the non-deterministic order that the protection systems start up, this approach will work in most situations, but not all. 3
4 Or they need to access the endpoint and shut off Malwarebytes, delete the harmful update files, then restart Malwarebytes. This technique usually works, but requires the customer to visit every endpoint. On startup, if the Endpoint Protection systems cannot connect to the cloud servers for the purpose of retrieving a policy update, it will attempt a series of steps to obtain the policy, then apply any policy changes. If all attempts fail, it will fall back to its most recent last-known-good policy. March 8th, 2018 Enhanced False Positive Testing before Publishing By expanding the testing of the Web Protection System before the protection updates are published, we can prevent the Web Protection System from detecting most of the popular websites and non-routable IP addresses. Checking against a list of known-good websites Before publishing protection updates, perform the following checks: Validate that the Domain Block List does not block any of the following: Domains from a vastly-expanded list of known-good websites Domains that Malwarebytes uses for updates or telemetry Validate the IP Block List does not contain: Non-routable IP addresses (private IP address space) March 15th, 2018 Allow Endpoint Protection Customers to Control Update Timing Most customers have asked for the ability to specify longer intervals between updates, or to specify that updates occur at a certain time-of-day, for better prediction of change. Some customers have asked for the ability to select an aging period that delays the applying of protection updates until they have been in the wild for a few hours. These new features would provide our Endpoint Protection customers a policy-level setting where they could select the timing of when updates are applied, giving them finer control over changes on their endpoints. 4
5 Current Techniques Updates are released ~10x per day. The Endpoint Agent checks for updates every hour, then downloads and applies them automatically without delay. Planned Techniques Allow user to specify intervals or delays for applying protection updates, for example: o Apply all protection updates on a set interval (e.g. daily, or at a time-of-day) o Disable protection updates entirely (e.g. for emergencies or testing) o Apply protection updates only after they are aged (e.g. x hours old) Initial functionality: April 12th, 2018 Complete functionality: June 7th,
Creating Workflows. Viewing the Task Library. Creating a Workflow. This chapter contains the following sections:
 This chapter contains the following sections: Viewing the Task Library, page 1 Creating a Workflow, page 1 Example: Creating a Workflow, page 12 Resolving Workflow Validation Issues, page 15 Changing Flow
This chapter contains the following sections: Viewing the Task Library, page 1 Creating a Workflow, page 1 Example: Creating a Workflow, page 12 Resolving Workflow Validation Issues, page 15 Changing Flow
AVAYA Avaya Aura System Platform R6.2.2 Release Notes Issue 1.3
 AVAYA Avaya Aura Release Notes Issue 1.3 INTRODUCTION This document introduces the Avaya Aura and describes new features, known issues and the issues resolved in this release. WHAT S NEW IN SYSTEM PLATFORM
AVAYA Avaya Aura Release Notes Issue 1.3 INTRODUCTION This document introduces the Avaya Aura and describes new features, known issues and the issues resolved in this release. WHAT S NEW IN SYSTEM PLATFORM
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE
 ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
Creating Workflows. Viewing the Task Library. Creating a Workflow. This chapter contains the following sections:
 This chapter contains the following sections: Viewing the Task Library, page 1 Creating a Workflow, page 1 Example: Creating a Workflow, page 13 Resolving Workflow Validation Issues, page 16 Changing Flow
This chapter contains the following sections: Viewing the Task Library, page 1 Creating a Workflow, page 1 Example: Creating a Workflow, page 13 Resolving Workflow Validation Issues, page 16 Changing Flow
Information Security Guideline OPERATING SYSTEM PATCHING
 Information Security Guideline OPERATING SYSTEM PATCHING Updated - August 2017 THIS PAGE INTENTIONALLY LEFT BLANK Operating System (OS) patching refers to applying updates to operating systems. It is absolutely
Information Security Guideline OPERATING SYSTEM PATCHING Updated - August 2017 THIS PAGE INTENTIONALLY LEFT BLANK Operating System (OS) patching refers to applying updates to operating systems. It is absolutely
Avaya Aura TM System Platform R6.0.1 Service Pack Release Notes Issue 1.4
 Avaya Aura TM Service Pack Release Notes Issue 1.4 INTRODUCTION This document introduces the Avaya Aura TM System Platform Release 6.0.1 Service Pack and describes known issues and the issues resolved
Avaya Aura TM Service Pack Release Notes Issue 1.4 INTRODUCTION This document introduces the Avaya Aura TM System Platform Release 6.0.1 Service Pack and describes known issues and the issues resolved
NextGen Healthcare Success Community Frequently Asked Questions for Employees
 NextGen Healthcare Success Community Frequently NextGen Healthcare, Inc. 795 Horsham Road Horsham, PA 19044 215-657-7010 NextGen.com Updated: 2/11/2016 Table of Contents General Questions... 4 What questions
NextGen Healthcare Success Community Frequently NextGen Healthcare, Inc. 795 Horsham Road Horsham, PA 19044 215-657-7010 NextGen.com Updated: 2/11/2016 Table of Contents General Questions... 4 What questions
Websense Data Security 7.7
 Websense Data Security 7.7 New Features and Best Practices Operating system support TRITON management server Windows 2008 R2 only Supplemental Data Security servers Same as v7.6 Windows 2003 R2 (32bit)
Websense Data Security 7.7 New Features and Best Practices Operating system support TRITON management server Windows 2008 R2 only Supplemental Data Security servers Same as v7.6 Windows 2003 R2 (32bit)
How can you implement this through a script that a scheduling daemon runs daily on the application servers?
 You ve been tasked with implementing an automated data backup solution for your application servers that run on Amazon EC2 with Amazon EBS volumes. You want to use a distributed data store for your backups
You ve been tasked with implementing an automated data backup solution for your application servers that run on Amazon EC2 with Amazon EBS volumes. You want to use a distributed data store for your backups
Configuring Port-Based Traffic Control
 CHAPTER 22 This chapter describes how to configure the port-based traffic control features on the Cisco ME 3400 Ethernet Access switch. For complete syntax and usage information for the commands used in
CHAPTER 22 This chapter describes how to configure the port-based traffic control features on the Cisco ME 3400 Ethernet Access switch. For complete syntax and usage information for the commands used in
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal
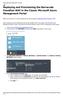 Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
December 2011 vsp-patch noarch.rpm Avaya Aura System Platform R6.0 June 2010 vsp iso
 AVAYA Avaya Aura Release Notes Issue 1.1 INTRODUCTION This document introduces the Avaya Aura and describes new features, known issues and the issues resolved in this release. WHAT S NEW IN SYSTEM PLATFORM
AVAYA Avaya Aura Release Notes Issue 1.1 INTRODUCTION This document introduces the Avaya Aura and describes new features, known issues and the issues resolved in this release. WHAT S NEW IN SYSTEM PLATFORM
AVAYA Avaya Aura System Platform Service Pack R6.2.1 Release Notes Issue 1.3
 AVAYA R6.2.1 Release Notes Issue 1.3 INTRODUCTION This document introduces the Release 6.2.1 and describes known issues and the issues resolved in this release. SOFTWARE RELEASE VERSIONS Release Date File
AVAYA R6.2.1 Release Notes Issue 1.3 INTRODUCTION This document introduces the Release 6.2.1 and describes known issues and the issues resolved in this release. SOFTWARE RELEASE VERSIONS Release Date File
LANDESK White Paper. Maintaining User Productivity through Effective Endpoint Management
 LANDESK White Paper Maintaining User Productivity through Effective Endpoint Management Contents Executive Overview... 3 Integration Increases Context... 3 Integration Drives Action... 3 Integration Provides
LANDESK White Paper Maintaining User Productivity through Effective Endpoint Management Contents Executive Overview... 3 Integration Increases Context... 3 Integration Drives Action... 3 Integration Provides
Configuring Port-Based Traffic Control
 CHAPTER 18 This chapter describes how to configure port-based traffic control features on the Catalyst 3750 Metro switch. For complete syntax and usage information for the commands used in this chapter,
CHAPTER 18 This chapter describes how to configure port-based traffic control features on the Catalyst 3750 Metro switch. For complete syntax and usage information for the commands used in this chapter,
Getting Started with ehealth for Voice Cisco Unity & Unity Bridge
 Focus on Setup Getting Started with ehealth for Voice Cisco Unity & Unity Bridge What s Inside About ehealth for Voice Cisco Unity. An overview of the product components. Requirements. Prerequisites for
Focus on Setup Getting Started with ehealth for Voice Cisco Unity & Unity Bridge What s Inside About ehealth for Voice Cisco Unity. An overview of the product components. Requirements. Prerequisites for
Managed Security Services - Endpoint Managed Security on Cloud
 Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
PureEngage Cloud Release Note. Outbound
 PureEngage Cloud Release Note Outbound 5/14/2018 Outbound Note: Not all changes listed below may pertain to your deployment. May 7, 2018 (15.5.0) April 5, 2018 (15.4.0) March 12, 2018 (15.3.0) February
PureEngage Cloud Release Note Outbound 5/14/2018 Outbound Note: Not all changes listed below may pertain to your deployment. May 7, 2018 (15.5.0) April 5, 2018 (15.4.0) March 12, 2018 (15.3.0) February
 Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
The Case for Virtualizing Your Oracle Database Deployment
 June 2012 The Case for Virtualizing Your Oracle Database Deployment Much has been written about the benefits of virtualization over the last few years. Hypervisor software promises to revolutionize the
June 2012 The Case for Virtualizing Your Oracle Database Deployment Much has been written about the benefits of virtualization over the last few years. Hypervisor software promises to revolutionize the
SOLUTION OVERVIEW. Manage your network security for up to 250 seats from a single cloud-based console
 SOLUTION OVERVIEW Manage your network security for up to 250 seats from a single cloud-based console 2 With ESET Cloud Administrator, you can manage your company network security without the need to buy,
SOLUTION OVERVIEW Manage your network security for up to 250 seats from a single cloud-based console 2 With ESET Cloud Administrator, you can manage your company network security without the need to buy,
What s New for Compute Classic
 Oracle Cloud What's New for Oracle Cloud Infrastructure Compute Classic Release 18.4 E71882-32 November 2018 What s New for Oracle Cloud Infrastructure Compute Classic This document describes what's new
Oracle Cloud What's New for Oracle Cloud Infrastructure Compute Classic Release 18.4 E71882-32 November 2018 What s New for Oracle Cloud Infrastructure Compute Classic This document describes what's new
SentinelOne Technical Brief
 SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by machine learning and intelligent automation. By rethinking
SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by machine learning and intelligent automation. By rethinking
Implementing and Supporting Windows Intune
 Implementing and Supporting Windows Intune Module 3: Computer Administration by Using Windows Intune Module Overview Understanding Groups Creating and Populating Groups The Windows Intune Update Process
Implementing and Supporting Windows Intune Module 3: Computer Administration by Using Windows Intune Module Overview Understanding Groups Creating and Populating Groups The Windows Intune Update Process
The professional IT management platform
 The professional IT management platform Total Control of Your IT Infrastructure Whether you are administrating your own IT, or providing services to your clients, with ITbrain you amaze with proactivity.
The professional IT management platform Total Control of Your IT Infrastructure Whether you are administrating your own IT, or providing services to your clients, with ITbrain you amaze with proactivity.
Oracle Java SE Advanced for ISVs
 Oracle Java SE Advanced for ISVs Oracle Java SE Advanced for ISVs is designed to enhance the Java based solutions that ISVs are providing to their enterprise customers. It brings together industry leading
Oracle Java SE Advanced for ISVs Oracle Java SE Advanced for ISVs is designed to enhance the Java based solutions that ISVs are providing to their enterprise customers. It brings together industry leading
Chrome and IE comparisons
 Last updated September 16, 2016 Copyright Copyright ezdi, Inc 2016 All Rights Reserved All rights reserved. No part of this manual may be photocopied or reproduced in any form without written permission
Last updated September 16, 2016 Copyright Copyright ezdi, Inc 2016 All Rights Reserved All rights reserved. No part of this manual may be photocopied or reproduced in any form without written permission
Multi-Machine Guide vcloud Automation Center 5.2
 Multi-Machine Guide vcloud Automation Center 5.2 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check
Multi-Machine Guide vcloud Automation Center 5.2 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check
Performance Matters Scaling Integration Processes to Meet the Needs of Your Business. James Ahlborn, Chief Software Architect, Dell Boomi
 Performance Matters Scaling Integration Processes to Meet the Needs of Your Business James Ahlborn, Chief Software Architect, Dell Boomi 1 Atoms Agenda Atoms vs. Molecules Atom Clouds Atom Workers Performance
Performance Matters Scaling Integration Processes to Meet the Needs of Your Business James Ahlborn, Chief Software Architect, Dell Boomi 1 Atoms Agenda Atoms vs. Molecules Atom Clouds Atom Workers Performance
McAfee Endpoint Security for Servers Product Guide. (McAfee epolicy Orchestrator)
 McAfee Endpoint Security for Servers 5.1.0 Product Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection,
McAfee Endpoint Security for Servers 5.1.0 Product Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection,
ITD SERVER MANAGEMENT PROCEDURE
 ITD SERVER MANAGEMENT PROCEDURE PURPOSE This procedure ensures the operation and maintenance of all ITD servers in a safe and effective fashion. This is achieved by the routine monitoring and timely update
ITD SERVER MANAGEMENT PROCEDURE PURPOSE This procedure ensures the operation and maintenance of all ITD servers in a safe and effective fashion. This is achieved by the routine monitoring and timely update
SentinelOne Technical Brief
 SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by behavior-based threat detection and intelligent automation.
SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by behavior-based threat detection and intelligent automation.
Christopher Covert. Principal Product Manager Enterprise Solutions Group. Copyright 2016 Symantec Endpoint Protection Cloud
 Christopher Covert Principal Product Manager Enterprise Solutions Group Copyright 2016 Symantec Endpoint Protection Cloud THE PROMISE OF CLOUD COMPUTING We re all moving from challenges like these Large
Christopher Covert Principal Product Manager Enterprise Solutions Group Copyright 2016 Symantec Endpoint Protection Cloud THE PROMISE OF CLOUD COMPUTING We re all moving from challenges like these Large
PureEngage Cloud Release Note. Outbound
 PureEngage Cloud Release Note Outbound 1/2/2018 Outbound Note: Not all changes listed below may pertain to your deployment. November 13, 2017 (14.15.0) October 23, 2017 (14.14.0) September 21, 2017 (14.13.0)
PureEngage Cloud Release Note Outbound 1/2/2018 Outbound Note: Not all changes listed below may pertain to your deployment. November 13, 2017 (14.15.0) October 23, 2017 (14.14.0) September 21, 2017 (14.13.0)
This option lets you reset the password that you use to log in if you do not remember it. To change the password,
 User s Guide Overview IDrive offers the most cost effective BMR functionality with onsite disk image backup for SMBs. Store entire data of hard disks including the operating system (OS) and application
User s Guide Overview IDrive offers the most cost effective BMR functionality with onsite disk image backup for SMBs. Store entire data of hard disks including the operating system (OS) and application
SIMATIC. Process Control System PCS 7 Symantec Endpoint Protection 11.0 Configuration. Using virus scanners 1. Configuration 2. Commissioning Manual
 SIMATIC Process Control System PCS 7 Using virus scanners 1 Configuration 2 SIMATIC Process Control System PCS 7 Symantec Endpoint Protection 11.0 Configuration Commissioning Manual 08/2009 A5E02634984-01
SIMATIC Process Control System PCS 7 Using virus scanners 1 Configuration 2 SIMATIC Process Control System PCS 7 Symantec Endpoint Protection 11.0 Configuration Commissioning Manual 08/2009 A5E02634984-01
GROUND FAULT CIRCUIT INTERUPTERS
 Title: GFCI Effective Date: 11/14/2014 Control Number: THG_0031 Revision Number: 1 Date: 10/21/2015 Annual Review Completed: 5/13/2015 GROUND FAULT CIRCUIT INTERUPTERS CONTENTS I. PURPOSE II. GENERAL REQUIREMENTS
Title: GFCI Effective Date: 11/14/2014 Control Number: THG_0031 Revision Number: 1 Date: 10/21/2015 Annual Review Completed: 5/13/2015 GROUND FAULT CIRCUIT INTERUPTERS CONTENTS I. PURPOSE II. GENERAL REQUIREMENTS
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
CYBER SECURITY POLICY REVISION: 12
 1. General 1.1. Purpose 1.1.1. To manage and control the risk to the reliable operation of the Bulk Electric System (BES) located within the service territory footprint of Emera Maine (hereafter referred
1. General 1.1. Purpose 1.1.1. To manage and control the risk to the reliable operation of the Bulk Electric System (BES) located within the service territory footprint of Emera Maine (hereafter referred
POWERING NETWORK RESILIENCY WITH UPS LIFECYCLE MANAGEMENT
 POWERING NETWORK RESILIENCY WITH UPS LIFECYCLE MANAGEMENT Network downtime is a business disrupter, cutting off communication between employees and customers, bringing service delivery to a halt. Yet all
POWERING NETWORK RESILIENCY WITH UPS LIFECYCLE MANAGEMENT Network downtime is a business disrupter, cutting off communication between employees and customers, bringing service delivery to a halt. Yet all
INTRODUCING CISCO SECURITY FOR AWS
 SESSION ID: SPO1-T08 INTRODUCING CISCO SECURITY FOR AWS Patrick Crowley CTO Cisco, Stealthwatch Cloud @p_crowley Who am I? I work for Cisco Systems, in the Security Business Group Founder, Observable Networks:
SESSION ID: SPO1-T08 INTRODUCING CISCO SECURITY FOR AWS Patrick Crowley CTO Cisco, Stealthwatch Cloud @p_crowley Who am I? I work for Cisco Systems, in the Security Business Group Founder, Observable Networks:
Alteryx Technical Overview
 Alteryx Technical Overview v 1.5, March 2017 2017 Alteryx, Inc. v1.5, March 2017 Page 1 Contents System Overview... 3 Alteryx Designer... 3 Alteryx Engine... 3 Alteryx Service... 5 Alteryx Scheduler...
Alteryx Technical Overview v 1.5, March 2017 2017 Alteryx, Inc. v1.5, March 2017 Page 1 Contents System Overview... 3 Alteryx Designer... 3 Alteryx Engine... 3 Alteryx Service... 5 Alteryx Scheduler...
McAfee Endpoint Security for Servers Product Guide
 McAfee Endpoint Security for Servers 5.2.0 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee epo,
McAfee Endpoint Security for Servers 5.2.0 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee epo,
Important Announcement: Substantial Upcoming Enhancement to Mirroring. Change Required for Sites Currently Using IsOtherNodeDown^ZMIRROR
 One Memorial Drive, Cambridge, MA 02142, USA Tel: +1.617.621.0600 Fax: +1.617.494.1631 http://www.intersystems.com January 30, 2014 Important Announcement: Substantial Upcoming Enhancement to Mirroring
One Memorial Drive, Cambridge, MA 02142, USA Tel: +1.617.621.0600 Fax: +1.617.494.1631 http://www.intersystems.com January 30, 2014 Important Announcement: Substantial Upcoming Enhancement to Mirroring
Ivanti Patch for Windows Servers. Quick Start Guide
 Ivanti Patch for Windows Servers Quick Start Guide Copyright and Trademarks Copyright and Trademarks This document contains the confidential information and/or proprietary property of Ivanti, Inc. and
Ivanti Patch for Windows Servers Quick Start Guide Copyright and Trademarks Copyright and Trademarks This document contains the confidential information and/or proprietary property of Ivanti, Inc. and
CAD-CARE TROUBLESHOOTING GUIDE
 CAD-CARE TROUBLESHOOTING GUIDE CAD-Care is a stable and error free system. The biggest problem encountered with CAD-Care is when something stops CAD-Care during a system sort. Windows Screen Savers have
CAD-CARE TROUBLESHOOTING GUIDE CAD-Care is a stable and error free system. The biggest problem encountered with CAD-Care is when something stops CAD-Care during a system sort. Windows Screen Savers have
VNS3 3.5 Upgrade Instructions
 VNS3 3.5 Upgrade Instructions Version 2.x/3.x to 3.5 2015 1 Agenda Introduction 3 Upgrade Steps 7 1. Create a VPN3 Snapshot of the 2.x/3.x Manager 8 2. Launch a 3.5 Controller instance 9 3. Swap the Public
VNS3 3.5 Upgrade Instructions Version 2.x/3.x to 3.5 2015 1 Agenda Introduction 3 Upgrade Steps 7 1. Create a VPN3 Snapshot of the 2.x/3.x Manager 8 2. Launch a 3.5 Controller instance 9 3. Swap the Public
Oracle9iAS Unified Messaging
 Oracle9iAS Unified Messaging Release Notes Release 9.0.2 for UNIX April 2002 Part No. A95819-01 This document summarizes the differences between Oracle9iAS Unified Messaging and its documented functionality.
Oracle9iAS Unified Messaging Release Notes Release 9.0.2 for UNIX April 2002 Part No. A95819-01 This document summarizes the differences between Oracle9iAS Unified Messaging and its documented functionality.
What s New for Oracle Java Cloud Service. On Oracle Cloud Infrastructure and Oracle Cloud Infrastructure Classic. Topics: Oracle Cloud
 Oracle Cloud What's New for Oracle Java Cloud Service Release 17.4 E64762-32 November 2017 What s New for Oracle Java Cloud Service This document describes what's new in Oracle Java Cloud Service on all
Oracle Cloud What's New for Oracle Java Cloud Service Release 17.4 E64762-32 November 2017 What s New for Oracle Java Cloud Service This document describes what's new in Oracle Java Cloud Service on all
Table of Contents HOL SLN
 Table of Contents Lab Overview - - Modernizing Your Data Center with VMware Cloud Foundation... 3 Lab Guidance... 4 Module 1 - Deploying VMware Cloud Foundation (15 Minutes)... 7 Introduction... 8 Hands-on
Table of Contents Lab Overview - - Modernizing Your Data Center with VMware Cloud Foundation... 3 Lab Guidance... 4 Module 1 - Deploying VMware Cloud Foundation (15 Minutes)... 7 Introduction... 8 Hands-on
Software Delivery Solution 6.1 SP1 HF2 for Windows Release Notes
 Software Delivery Solution 6.1 SP1 HF2 for Windows Release Notes February 17, 2006 NOTICE The content in this document represents the current view of Altiris as of the date of publication. Because Altiris
Software Delivery Solution 6.1 SP1 HF2 for Windows Release Notes February 17, 2006 NOTICE The content in this document represents the current view of Altiris as of the date of publication. Because Altiris
Kaseya 2. User Guide. Version 1.1
 Kaseya 2 Anti-Malware User Guide Version 1.1 July 11, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya 2 Anti-Malware User Guide Version 1.1 July 11, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Audit report and analyse overview. Audit report user guide v1.1
 Audit report and analyse overview Audit report user guide v1.1 Contents Service Overview... 3 Customer Agent Installation... 3 Customer Windows setup... 4 Enable SNMP... 4 Allow inbound SNMP in Windows
Audit report and analyse overview Audit report user guide v1.1 Contents Service Overview... 3 Customer Agent Installation... 3 Customer Windows setup... 4 Enable SNMP... 4 Allow inbound SNMP in Windows
USM Anywhere AlienApps Guide
 USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
MITEL PERFORMANCE ANALYTICS
 MITEL PERFORMANCE ANALYTICS RELEASE 2.3 UPGRADE GUIDE NOTICE The information contained in this document is believed to be accurate in all respects but is not warranted by Mitel Networks Corporation (MITEL
MITEL PERFORMANCE ANALYTICS RELEASE 2.3 UPGRADE GUIDE NOTICE The information contained in this document is believed to be accurate in all respects but is not warranted by Mitel Networks Corporation (MITEL
Infrastructure Insights
 72 Methods for Handling and Analyzing Monitor Alerts Regular Feature Infrastructure Insights Imagine that your database backup has surpassed its memory threshold, and as a result the backup has stalled.
72 Methods for Handling and Analyzing Monitor Alerts Regular Feature Infrastructure Insights Imagine that your database backup has surpassed its memory threshold, and as a result the backup has stalled.
Nortel Contact Center Routine Maintenance NN
 NN44400-514 Document status: Standard Document issue: 01.03 Document date: 26 February 2010 Product release: Release 7.0 Job function: Administration Type: Technical Document Language type: English Copyright
NN44400-514 Document status: Standard Document issue: 01.03 Document date: 26 February 2010 Product release: Release 7.0 Job function: Administration Type: Technical Document Language type: English Copyright
Getting over Ransomware - Plan your Strategy for more Advanced Threats
 Getting over Ransomware - Plan your Strategy for more Advanced Threats Kaspersky Lab Hong Kong Eric Kwok General Manager Lapcom Ltd. BEYOND ANTI-VIRUS: TRUE CYBERSECURITY FROM KASPERSKY LAB 20 years ago
Getting over Ransomware - Plan your Strategy for more Advanced Threats Kaspersky Lab Hong Kong Eric Kwok General Manager Lapcom Ltd. BEYOND ANTI-VIRUS: TRUE CYBERSECURITY FROM KASPERSKY LAB 20 years ago
Council, 8 February 2017 Information Technology Report Executive summary and recommendations
 Council, 8 February 2017 Information Technology Report Executive summary and recommendations Introduction This report provides the Council with an update into the work of the Information Technology Directorate
Council, 8 February 2017 Information Technology Report Executive summary and recommendations Introduction This report provides the Council with an update into the work of the Information Technology Directorate
Connected Nations Update. Spring 2018
 Connected Nations Update Spring 2018 REPORT Publication Date: 30 April 2018 About this document This is the first spring update on progress made on the coverage of broadband and mobile networks of the
Connected Nations Update Spring 2018 REPORT Publication Date: 30 April 2018 About this document This is the first spring update on progress made on the coverage of broadband and mobile networks of the
As a 3rd generation currency, not only are transactions secured, private and fast, you actually get paid for holding DigitalPrice coins.
 Introduction With the circulation of cryptocurrency becoming common, there is a need for additional information. The scope of this white paper is to provide that information. If you are under the impression
Introduction With the circulation of cryptocurrency becoming common, there is a need for additional information. The scope of this white paper is to provide that information. If you are under the impression
Standard CIP Cyber Security Critical Cyber Asset Identification
 Standard CIP 002 1 Cyber Security Critical Cyber Asset Identification Standard Development Roadmap This section is maintained by the drafting team during the development of the standard and will be removed
Standard CIP 002 1 Cyber Security Critical Cyber Asset Identification Standard Development Roadmap This section is maintained by the drafting team during the development of the standard and will be removed
What this Guide Covers. Additional Info. 1. Linux based Servers. 2. Windows Servers. 3. GoldLite and Virtual Servers. 4. Other servers. 5.
 This guide is designed to assist in shutting down the Gold Servers ensuring a clean reboot of the systems. This should be done by the System Administrators with all users logged off the system and any
This guide is designed to assist in shutting down the Gold Servers ensuring a clean reboot of the systems. This should be done by the System Administrators with all users logged off the system and any
OUR CUSTOMER TERMS CLOUD SERVICES - INFRASTRUCTURE
 CONTENTS 1 ABOUT THIS PART... 2 2 GENERAL... 2 3 CLOUD INFRASTRUCTURE (FORMERLY UTILITY HOSTING)... 2 4 TAILORED INFRASTRUCTURE (FORMERLY DEDICATED HOSTING)... 3 5 COMPUTE... 3 6 BACKUP & RECOVERY... 8
CONTENTS 1 ABOUT THIS PART... 2 2 GENERAL... 2 3 CLOUD INFRASTRUCTURE (FORMERLY UTILITY HOSTING)... 2 4 TAILORED INFRASTRUCTURE (FORMERLY DEDICATED HOSTING)... 3 5 COMPUTE... 3 6 BACKUP & RECOVERY... 8
Example. Section: PS 709 Examples of Calculations of Reduced Hours of Work Last Revised: February 2017 Last Reviewed: February 2017 Next Review:
 Following are three examples of calculations for MCP employees (undefined hours of work) and three examples for MCP office employees. Examples use the data from the table below. For your calculations use
Following are three examples of calculations for MCP employees (undefined hours of work) and three examples for MCP office employees. Examples use the data from the table below. For your calculations use
Service Portal User Guide
 FUJITSU Cloud Service K5 IaaS Service Portal User Guide Version 1.4 FUJITSU LIMITED All Rights Reserved, Copyright FUJITSU LIMITED 2015-2016 K5IA-DC-M-005-001E Preface Purpose of This Manual This manual
FUJITSU Cloud Service K5 IaaS Service Portal User Guide Version 1.4 FUJITSU LIMITED All Rights Reserved, Copyright FUJITSU LIMITED 2015-2016 K5IA-DC-M-005-001E Preface Purpose of This Manual This manual
Module 6: Deadlocks. Reading: Chapter 7
 Module 6: Deadlocks Reading: Chapter 7 Objective: To develop a description of deadlocks, which prevent sets of concurrent processes from completing their tasks To present a number of different methods
Module 6: Deadlocks Reading: Chapter 7 Objective: To develop a description of deadlocks, which prevent sets of concurrent processes from completing their tasks To present a number of different methods
VIRTUAL GPU LICENSE SERVER VERSION , , AND 5.1.0
 VIRTUAL GPU LICENSE SERVER VERSION 2018.10, 2018.06, AND 5.1.0 DU-07754-001 _v7.0 through 7.2 March 2019 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server...
VIRTUAL GPU LICENSE SERVER VERSION 2018.10, 2018.06, AND 5.1.0 DU-07754-001 _v7.0 through 7.2 March 2019 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server...
Creating Application Containers
 This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
Firmware Revision History and Upgrade Instructions
 SENSAPHONE Firmware Revision History and Upgrade Instructions Equipment Firmware: WEB600 v1.46 WEB600 with Relay Output v1.59 Release Date: July 15, 2013 The upgrade package has no prerequisites and supersedes
SENSAPHONE Firmware Revision History and Upgrade Instructions Equipment Firmware: WEB600 v1.46 WEB600 with Relay Output v1.59 Release Date: July 15, 2013 The upgrade package has no prerequisites and supersedes
SIMATIC. Process Control System PCS 7 Trend Micro OfficeScan (V8.0; V8.0 SP1) Configuration. Using virus scanners 1.
 SIMATIC Process Control System PCS 7 Using virus scanners 1 Configuration 2 SIMATIC Process Control System PCS 7 Trend Micro OfficeScan (V8.0; V8.0 SP1) Configuration Commissioning Manual 08/2009 A5E02634982-01
SIMATIC Process Control System PCS 7 Using virus scanners 1 Configuration 2 SIMATIC Process Control System PCS 7 Trend Micro OfficeScan (V8.0; V8.0 SP1) Configuration Commissioning Manual 08/2009 A5E02634982-01
Migration Extension Capabilities - Scenario: Windows 2003 Server to Cloud Migration and Upgrade. By Michael Kent :,,, rivermeadow
 Migration Extension Capabilities - Scenario: Windows 003 Server to Cloud Migration and Upgrade By Michael Kent ' :,,, rivermeadow TABLE OF CONTENTS The Problem: Windows 003 End of Life The Solution: RiverMeadow
Migration Extension Capabilities - Scenario: Windows 003 Server to Cloud Migration and Upgrade By Michael Kent ' :,,, rivermeadow TABLE OF CONTENTS The Problem: Windows 003 End of Life The Solution: RiverMeadow
Datacenter Management and The Private Cloud. Troy Sharpe Core Infrastructure Specialist Microsoft Corp, Education
 Datacenter Management and The Private Cloud Troy Sharpe Core Infrastructure Specialist Microsoft Corp, Education System Center Helps Deliver IT as a Service Configure App Controller Orchestrator Deploy
Datacenter Management and The Private Cloud Troy Sharpe Core Infrastructure Specialist Microsoft Corp, Education System Center Helps Deliver IT as a Service Configure App Controller Orchestrator Deploy
Configuring Layer 3 Interfaces
 This chapter contains the following sections: Information About Layer 3 Interfaces, page 1 Licensing Requirements for Layer 3 Interfaces, page 4 Guidelines and Limitations for Layer 3 Interfaces, page
This chapter contains the following sections: Information About Layer 3 Interfaces, page 1 Licensing Requirements for Layer 3 Interfaces, page 4 Guidelines and Limitations for Layer 3 Interfaces, page
POWER SYSTEM DATA COMMUNICATION STANDARD
 POWER SYSTEM DATA COMMUNICATION STANDARD PREPARED BY: AEMO Systems Capability VERSION: 2 EFFECTIVE DATE: 1 December 2017 STATUS: FINAL Australian Energy Market Operator Ltd ABN 94 072 010 327 www.aemo.com.au
POWER SYSTEM DATA COMMUNICATION STANDARD PREPARED BY: AEMO Systems Capability VERSION: 2 EFFECTIVE DATE: 1 December 2017 STATUS: FINAL Australian Energy Market Operator Ltd ABN 94 072 010 327 www.aemo.com.au
McAfee MVISION Endpoint 1808 Product Guide
 McAfee MVISION Endpoint 1808 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee epo, McAfee EMM,
McAfee MVISION Endpoint 1808 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee epo, McAfee EMM,
Configuring Layer 3 Interfaces
 This chapter contains the following sections: Information About Layer 3 Interfaces, page 1 Licensing Requirements for Layer 3 Interfaces, page 4 Guidelines and Limitations for Layer 3 Interfaces, page
This chapter contains the following sections: Information About Layer 3 Interfaces, page 1 Licensing Requirements for Layer 3 Interfaces, page 4 Guidelines and Limitations for Layer 3 Interfaces, page
Healthcare Database Connector
 Healthcare Database Connector Installation and Setup Guide Version: 3.0.0 Written by: Product Knowledge, R&D Date: February 2017 2015-2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark
Healthcare Database Connector Installation and Setup Guide Version: 3.0.0 Written by: Product Knowledge, R&D Date: February 2017 2015-2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark
Securing the Modern Data Center with Trend Micro Deep Security
 Advania Fall Conference Securing the Modern Data Center with Trend Micro Deep Security Okan Kalak, Senior Sales Engineer okan@trendmicro.no Infrastructure change Containers 1011 0100 0010 Serverless Public
Advania Fall Conference Securing the Modern Data Center with Trend Micro Deep Security Okan Kalak, Senior Sales Engineer okan@trendmicro.no Infrastructure change Containers 1011 0100 0010 Serverless Public
CAS Quick Deployment Guide January 2018
 CAS January 2018 Page 2 of 18 Trend Micro CAS January 2018 This document is to guide TrendMicro SE and Solution Architect team run a successful Cloud App Security POC with prospective customers. It is
CAS January 2018 Page 2 of 18 Trend Micro CAS January 2018 This document is to guide TrendMicro SE and Solution Architect team run a successful Cloud App Security POC with prospective customers. It is
Veeam Endpoint Backup
 Veeam Endpoint Backup Version 1.5 User Guide March, 2016 2016 Veeam Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced,
Veeam Endpoint Backup Version 1.5 User Guide March, 2016 2016 Veeam Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced,
Monitoring Event Logs
 13 CHAPTER This chapter describes the Monitoring module of Cisco NAC Appliance. Topics include: Overview, page 13-1 Interpreting Event Logs, page 13-4 Configuring Syslog Logging, page 13-9 Cisco NAC Appliance
13 CHAPTER This chapter describes the Monitoring module of Cisco NAC Appliance. Topics include: Overview, page 13-1 Interpreting Event Logs, page 13-4 Configuring Syslog Logging, page 13-9 Cisco NAC Appliance
Perform Manual System Restore Xp Safe Mode Not Working
 Perform Manual System Restore Xp Safe Mode Not Working If you computer has system problem, you first priority should be to make sure you Windows Advanced Options Menu Please select an option: Safe Mode
Perform Manual System Restore Xp Safe Mode Not Working If you computer has system problem, you first priority should be to make sure you Windows Advanced Options Menu Please select an option: Safe Mode
Estate Valuations & Pricing Systems, Inc. Disaster Recovery and Business Continuity
 Estate Valuations & Pricing Systems, Inc. Disaster Recovery and Business Continuity Summary Estate Valuations & Pricing Systems, Inc. maintains two active instances of its server side pricing infrastructure,
Estate Valuations & Pricing Systems, Inc. Disaster Recovery and Business Continuity Summary Estate Valuations & Pricing Systems, Inc. maintains two active instances of its server side pricing infrastructure,
Online Help StruxureWare Data Center Expert
 Online Help StruxureWare Data Center Expert Version 7.5.0 StruxureWare Data Center Expert Virtual Appliance The StruxureWare Data Center Expert 7.5.x server is available as a virtual appliance, supported
Online Help StruxureWare Data Center Expert Version 7.5.0 StruxureWare Data Center Expert Virtual Appliance The StruxureWare Data Center Expert 7.5.x server is available as a virtual appliance, supported
Product Versioning and Back Support Policy
 Effective March 18, 2016 to Feb 1, 2017 Product Versioning and Back Support Policy Definitions Semantic Versioning Date Based Versioning Standard Support Extended Support End of Life Support Critical Security
Effective March 18, 2016 to Feb 1, 2017 Product Versioning and Back Support Policy Definitions Semantic Versioning Date Based Versioning Standard Support Extended Support End of Life Support Critical Security
Online Help StruxureWare Central
 Online Help StruxureWare Central Version 7.0.0 StruxureWare Central Virtual Appliance The StruxureWare Central 7.0 server is now available as a virtual appliance, supported on VMware ESXi 4.1.0. The full-featured
Online Help StruxureWare Central Version 7.0.0 StruxureWare Central Virtual Appliance The StruxureWare Central 7.0 server is now available as a virtual appliance, supported on VMware ESXi 4.1.0. The full-featured
Best Practices for Deployment of SQL Compliance Manager
 Best Practices for Deployment of SQL Compliance Manager Table of Contents OVERVIEW/PURPOSE...2 REQUIRED LEVEL OF AUDITING...2 SQL COMPLIANCE REPOSITORY SQL SETTINGS...2 CONFIGURATION SETTINGS...3 CAPTURED
Best Practices for Deployment of SQL Compliance Manager Table of Contents OVERVIEW/PURPOSE...2 REQUIRED LEVEL OF AUDITING...2 SQL COMPLIANCE REPOSITORY SQL SETTINGS...2 CONFIGURATION SETTINGS...3 CAPTURED
Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide
 Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Documentation version:
Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Symantec Patch Management Solution for Windows 8.5 powered by Altiris technology User Guide Documentation version:
Panda Security. Corporate Presentation. Gianluca Busco Arré Country Manager
 Panda Security Corporate Presentation Gianluca Busco Arré Country Manager Great minds and Global Presence From 1990, Panda Security has become the leading European multinational developing advanced cybersecurity
Panda Security Corporate Presentation Gianluca Busco Arré Country Manager Great minds and Global Presence From 1990, Panda Security has become the leading European multinational developing advanced cybersecurity
Autonomic Web-based Simulation
 Autonomic Web-based Simulation Yingping Huang and Gregory Madey Computer Science and Engineering University of Notre Dame Autonomic Web-based Simulation p.1/38 Autonomic Web-based Simulation Autonomic
Autonomic Web-based Simulation Yingping Huang and Gregory Madey Computer Science and Engineering University of Notre Dame Autonomic Web-based Simulation p.1/38 Autonomic Web-based Simulation Autonomic
Alpha Anywhere Standard Application Server
 Alpha Anywhere Standard Application Server High Capacity Server Systems The standard Alpha Anywhere Application Server has adequate capacity for many web systems. However, Alpha Software recommends using
Alpha Anywhere Standard Application Server High Capacity Server Systems The standard Alpha Anywhere Application Server has adequate capacity for many web systems. However, Alpha Software recommends using
Integrating Juniper Sky Advanced Threat Prevention (ATP) and ForeScout CounterACT for Infected Host Remediation
 Integrating Juniper Sky Advanced Threat Prevention (ATP) and ForeScout CounterACT for Infected Host Remediation Configuration Example March 2018 2018 Juniper Networks, Inc. Juniper Networks, Inc. 1133
Integrating Juniper Sky Advanced Threat Prevention (ATP) and ForeScout CounterACT for Infected Host Remediation Configuration Example March 2018 2018 Juniper Networks, Inc. Juniper Networks, Inc. 1133
Handling Microservices with Kubernetes - Basic Info
 Handling Microservices with Kubernetes - Basic Info This course is for organizations who: you are considering expanding your DevOps skills with a future-proof platform, you want to understand Kubernetes
Handling Microservices with Kubernetes - Basic Info This course is for organizations who: you are considering expanding your DevOps skills with a future-proof platform, you want to understand Kubernetes
BEAWebLogic. Server. Automatic and Manual Service-level Migration
 BEAWebLogic Server Automatic and Manual Service-level Migration Version 10.3 Technical Preview Revised: March 2007 Service-Level Migration New in WebLogic Server 10.3: Automatic Migration of Messaging/JMS-Related
BEAWebLogic Server Automatic and Manual Service-level Migration Version 10.3 Technical Preview Revised: March 2007 Service-Level Migration New in WebLogic Server 10.3: Automatic Migration of Messaging/JMS-Related
Amazon Web Services and Feb 28 outage. Overview presented by Divya
 Amazon Web Services and Feb 28 outage Overview presented by Divya Amazon S3 Amazon S3 : store and retrieve any amount of data, at any time, from anywhere on web. Amazon S3 service: Create Buckets Create
Amazon Web Services and Feb 28 outage Overview presented by Divya Amazon S3 Amazon S3 : store and retrieve any amount of data, at any time, from anywhere on web. Amazon S3 service: Create Buckets Create
Endpoint Security. powered by HEAT Software. AntiVirus Best Practice Guide. Version 8.5 Update 2
 AntiVirus Best Practice Guide Version 8.5 Update 2 Endpoint Security powered by HEAT Software Contents Introduction 3 What Does AntiVirus Do? 3 Overview 4 Phase 1: Prepare Your Infrastructure 5 Remove
AntiVirus Best Practice Guide Version 8.5 Update 2 Endpoint Security powered by HEAT Software Contents Introduction 3 What Does AntiVirus Do? 3 Overview 4 Phase 1: Prepare Your Infrastructure 5 Remove
Protect Against Power-Related DUT Damage During Test
 Protect Against Power-Related DUT Damage During Test Our thanks to Keysight Technologies for allowing us to reprint this article. An over-voltage or over-current event can occur for a variety of reasons,
Protect Against Power-Related DUT Damage During Test Our thanks to Keysight Technologies for allowing us to reprint this article. An over-voltage or over-current event can occur for a variety of reasons,
Perceptive Content Agent
 Perceptive Content Email Agent Release Notes Version: 1.2.x Compatible with ImageNow 6.7.0, build 3740 and higher, and Perceptive Content 7.x Written by: Product Knowledge, R&D Date: May 2018 2015-2018
Perceptive Content Email Agent Release Notes Version: 1.2.x Compatible with ImageNow 6.7.0, build 3740 and higher, and Perceptive Content 7.x Written by: Product Knowledge, R&D Date: May 2018 2015-2018
Introducing KASPERSKY ENDPOINT SECURITY FOR BUSINESS
 Introducing KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 Business drivers and their impact on IT AGILITY Move fast, be nimble and flexible 66% of business owners identify business agility as a priority EFFICIENCY
Introducing KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 Business drivers and their impact on IT AGILITY Move fast, be nimble and flexible 66% of business owners identify business agility as a priority EFFICIENCY
