Audit report and analyse overview. Audit report user guide v1.1
|
|
|
- Anis Caldwell
- 5 years ago
- Views:
Transcription
1 Audit report and analyse overview Audit report user guide v1.1
2 Contents Service Overview... 3 Customer Agent Installation... 3 Customer Windows setup... 4 Enable SNMP... 4 Allow inbound SNMP in Windows Firewall... 6 Ensure outbound HTTPS is allowed... 6 Analysing the Audit Report... 7 Audit report user guide v1.1
3 Service Overview An audit of your current infrastructure can be carried out to ensure we match the cloud infrastructure to the actual usage of your environment (as opposed to its allocated physical resources). This is important to ensure the most performant and efficient service offering is provided, whilst identifying any cost savings. The audit requires a low impact collector application to be loaded onto any server to monitor the infrastructure and usage over the internal network. All data is stored for the continuous 7 days of the audit in a highly secure location before being deleted after the audit report is completed. The instructions show what is required in a Windows 2012 R2 Server environment. Other versions of Windows may require slightly different steps, but the requirements are the same. Customer Agent Installation 1. Download the agent software from Note: The software is for Windows only, but the agent can poll any SNMP-enabled host, including Windows and Linux 2. Extract the file Highlight.Agent.Bundle.Setup.exe from the zip and run it 3. Agree to the terms & conditions and click Install 4. When prompted, enter the Activation code. This will have been previously ed to you and will be in the format: XXXX-XXXX-XXXX-XXXX-XXXX. Fill in the Service URL in with Click Next and complete the installation 5. You should now have the following icon on the desktop. Double-click on it 6. After a few minutes, the Agent should show the following status
4 The important field is Connection Status. Once this says Connected, it shows that connectivity is in place between the Agent and the Highlight platform. This then allows Gamma to configure the endpoints for monitoring. Customer Windows setup Enable SNMP 1. Go to Turn Windows features on or off and tick the Simple Network Monitoring Protocol (SNMP) box, then OK 2. Run services.msc and double-click on the SNMP Service
5 3. Click on the Security tab, then click Add to add a new community called highlightro. This should be a Read only community 4. Click on the Accept SNMP packets from any host radio box and then OK
6 Allow inbound SNMP in Windows Firewall 1. Open Windows Firewall 2. Click on Advanced Settings 3. Click on Inbound Rules, then New Rule 4. Choose Port then Next 5. Choose UDP and enter 161 in the Specific local Ports field, then Next 6. Choose Allow the Connection then Next 7. Ensure Domain, Private and Public are all ticked and click Next 8. Give the rule a name (e.g. Inbound SNMP) and click Finish Ensure outbound HTTPS is allowed By default, outbound https is allowed from Windows hosts. You should ensure this server is allowed outbound https to any destination. This is required for the Agent to send its collected information to the Highlight platform via a secure, encrypted HTTPS connection.
7 Analysing the Audit Report The report will contain the key elements being created in the Cloud Compute environment over a 7-day period i.e. Memory, CPU and Storage. An introductory summary page will illustrate the servers with their current specifications and the suggested specification. Each of the following sections will illustrate each server and their 7-day utilisation results. The Audit report will show the results and recommendations based on minimising the server size requirements while meeting the usage found during the auditing survey. The goal is to ensure a performant solution without over specifying the server to ensure costs are Finally, the amount of storage will be suggested based on current usage and predicted growth. It is very simple to expand the size of the storage volume so the recommendation will be close to the current usage with some head room.
Amazon Virtual Private Cloud. Getting Started Guide
 Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Open Ports on a SQL. August 22, Copyright 2013 by World Class CAD, LLC. All Rights Reserved.
 Open Ports on a SQL August 22, 2013 Copyright 2013 by World Class CAD, LLC. All Rights Reserved. Open Ports on SQL Server 2012 We will want to open the following TCP inbound and outbound ports on the SQL
Open Ports on a SQL August 22, 2013 Copyright 2013 by World Class CAD, LLC. All Rights Reserved. Open Ports on SQL Server 2012 We will want to open the following TCP inbound and outbound ports on the SQL
sflow Agent Contents 14-1
 14 sflow Agent Contents Overview..................................................... 14-2 Flow Sampling by the sflow Agent........................... 14-2 Counter Polling by the sflow Agent...........................
14 sflow Agent Contents Overview..................................................... 14-2 Flow Sampling by the sflow Agent........................... 14-2 Counter Polling by the sflow Agent...........................
Use of the TCP/IP Protocols and the OSI Model in Packet Tracer
 Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
C L O U D V O I C E Y E A L I N K S I P - C P 8 6 0
 C L O U D V O I C E Y E A L I N K S I P - C P 8 6 0 I P P H O N E C O N F I G U R A T I ON G U I D E V E R S I O N 2. 0 Contents Introduction... 3 Overview... 3 Audience... 3 Supported Devices... 4 Network,
C L O U D V O I C E Y E A L I N K S I P - C P 8 6 0 I P P H O N E C O N F I G U R A T I ON G U I D E V E R S I O N 2. 0 Contents Introduction... 3 Overview... 3 Audience... 3 Supported Devices... 4 Network,
Cloud Compute. Backup Portal User Guide
 Cloud Compute Backup Portal User Guide Contents Service Overview... 4 Gaining Access... 5 Operational Guide... 6 Landing Page... 6 Profile View... 6 Detailed View... 8 Overview... 8 Cloud Backup... 8
Cloud Compute Backup Portal User Guide Contents Service Overview... 4 Gaining Access... 5 Operational Guide... 6 Landing Page... 6 Profile View... 6 Detailed View... 8 Overview... 8 Cloud Backup... 8
H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5)
 H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5) Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual
H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5) Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual
Advanced Application Reporting USER GUIDE
 Advanced Application Reporting USER GUIDE CONTENTS 1.0 Preface: About This Document 5 2.0 Conventions 5 3.0 Chapter 1: Introducing Advanced Application Reporting 6 4.0 Features and Benefits 7 5.0 Product
Advanced Application Reporting USER GUIDE CONTENTS 1.0 Preface: About This Document 5 2.0 Conventions 5 3.0 Chapter 1: Introducing Advanced Application Reporting 6 4.0 Features and Benefits 7 5.0 Product
SYNTHESYS MANAGEMENT
 SYNTHESYS MANAGEMENT Teams User Management Synthesys.Net Management Basics 1 SYNTHESYS.NET MANAGEMENT Introduction... 3 Synthesys Management Features... 4 User Login... 5 Synthesys Management Main Screen...
SYNTHESYS MANAGEMENT Teams User Management Synthesys.Net Management Basics 1 SYNTHESYS.NET MANAGEMENT Introduction... 3 Synthesys Management Features... 4 User Login... 5 Synthesys Management Main Screen...
Securing Containers Using a PNSC and a Cisco VSG
 Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 4 About
Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 4 About
Securing Containers Using a PNSC and a Cisco VSG
 Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 3 About
Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 3 About
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Packet Tracer - Explore a Network
 Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
FUJITSU Cloud Service S5 Setup and Configuration of the FTP Service under Windows 2008/2012 Server
 FUJITSU Cloud Service S5 Setup and Configuration of the FTP Service under Windows 2008/2012 Server This guide details steps required to install and configure a basic FTP server on a Windows 2008/2012 VM
FUJITSU Cloud Service S5 Setup and Configuration of the FTP Service under Windows 2008/2012 Server This guide details steps required to install and configure a basic FTP server on a Windows 2008/2012 VM
Q: How do I connect to my wireless network?
 TEW-421PC/ TEW-423PI/ TEW-424UB F.A.Q. Q: How do I connect to my wireless network? A: Open the utility by right clicking on the icon at the bottom right hand side of the screen. Click on the Network tab.
TEW-421PC/ TEW-423PI/ TEW-424UB F.A.Q. Q: How do I connect to my wireless network? A: Open the utility by right clicking on the icon at the bottom right hand side of the screen. Click on the Network tab.
F.A.Q s for TEW-421PC, TEW-423PI, and TEW-424UB(version 2)
 F.A.Q s for TEW-421PC, TEW-423PI, and TEW-424UB(version 2) Q: How do I connect to my wireless network? A: Open the utility by double clicking on the icon at the bottom right hand side of the screen. Click
F.A.Q s for TEW-421PC, TEW-423PI, and TEW-424UB(version 2) Q: How do I connect to my wireless network? A: Open the utility by double clicking on the icon at the bottom right hand side of the screen. Click
Version June 2016
 HOSTING GUIDE Version 3.2.3 June 2016 This guide is sold in conjunction with the VETtrak Hosting Serv ice and is current at the time of purchase. Later v ersions are av ailable for download from www.v
HOSTING GUIDE Version 3.2.3 June 2016 This guide is sold in conjunction with the VETtrak Hosting Serv ice and is current at the time of purchase. Later v ersions are av ailable for download from www.v
KASPERSKY SECURITY CENTER 10 & KASPERSKY SECURITY FOR SERVER
 KASPERSKY SECURITY CENTER 10 & KASPERSKY SECURITY FOR SERVER Testing of Installation base on the AWS server Abstract This document create to present the result of testing installation of KSC 10 and the
KASPERSKY SECURITY CENTER 10 & KASPERSKY SECURITY FOR SERVER Testing of Installation base on the AWS server Abstract This document create to present the result of testing installation of KSC 10 and the
Integrating Entuity Network Management with BMC TrueSight Operations Management. For use with Entuity 16.5 downwards June 2017
 Integrating Entuity Network Management with BMC TrueSight Operations Management For use with Entuity 16.5 downwards June 2017 1 Document Overview 3 Installing the Entuity Network Component 3 Example 4
Integrating Entuity Network Management with BMC TrueSight Operations Management For use with Entuity 16.5 downwards June 2017 1 Document Overview 3 Installing the Entuity Network Component 3 Example 4
FUJITSU Cloud Service S5
 FUJITSU Cloud Service S5 Basic System Setup Windows 2008 and 2012 VMs This guide documents the basic configuration that should be performed to a vsys and VM in order to configure the standard London East
FUJITSU Cloud Service S5 Basic System Setup Windows 2008 and 2012 VMs This guide documents the basic configuration that should be performed to a vsys and VM in order to configure the standard London East
Business Intelligence & Financial Performance. PROFITstar and PROFITability. Configuring the Window s Firewall
 Business Intelligence & Financial Performance ... 3 Summary... 3 How to Allow Communication through Windows Firewall... 4 Firewall Exclusions for SQL Servers... 8 Inbound Rules... 8 Outbound Rules...10
Business Intelligence & Financial Performance ... 3 Summary... 3 How to Allow Communication through Windows Firewall... 4 Firewall Exclusions for SQL Servers... 8 Inbound Rules... 8 Outbound Rules...10
Virtual Private Cloud. User Guide. Issue 03 Date
 Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
FUJITSU Cloud Service S5 Modifying Virtual Resources
 FUJITSU Cloud Service S5 Modifying Virtual Resources This guide describes the process for modifying virtual resources on the FUJITSU Cloud Service S5 platform How to Modify a Virtual System A Virtual System
FUJITSU Cloud Service S5 Modifying Virtual Resources This guide describes the process for modifying virtual resources on the FUJITSU Cloud Service S5 platform How to Modify a Virtual System A Virtual System
Monitoring Windows Systems with WMI
 Monitoring Windows Systems with WMI ScienceLogic version 8.8.1 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is WMI? 5 PowerPacks 5 Configuring
Monitoring Windows Systems with WMI ScienceLogic version 8.8.1 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is WMI? 5 PowerPacks 5 Configuring
WEB ANALYTICS HOW-TO GUIDE
 WEB ANALYTICS HOW-TO GUIDE MOTOROLA, MOTO, MOTOROLA SOLUTIONS and the Stylized M logo are trademarks or registered trademarks of Motorola Trademark Holdings, LLC and are used under license. All other trademarks
WEB ANALYTICS HOW-TO GUIDE MOTOROLA, MOTO, MOTOROLA SOLUTIONS and the Stylized M logo are trademarks or registered trademarks of Motorola Trademark Holdings, LLC and are used under license. All other trademarks
Integration Guide. Auvik
 Integration Guide Auvik Revised: 27 February 2017 About This Guide Guide Type Documented Integration WatchGuard or a Technology Partner has provided documentation demonstrating integration. Guide Details
Integration Guide Auvik Revised: 27 February 2017 About This Guide Guide Type Documented Integration WatchGuard or a Technology Partner has provided documentation demonstrating integration. Guide Details
Installation Guide. 3CX CRM Plugin for ConnectWise. Single Tenant Version
 Installation Guide 3CX CRM Plugin for ConnectWise Single Tenant Version "Copyright VoIPTools, LLC 2011-2016" Information in this document is subject to change without notice. No part of this document may
Installation Guide 3CX CRM Plugin for ConnectWise Single Tenant Version "Copyright VoIPTools, LLC 2011-2016" Information in this document is subject to change without notice. No part of this document may
Basic Steps for Autotask Endpoint Management. Updated Wednesday, January 31, Autotask Corporation
 Basic Steps for Autotask Endpoint Management Updated Wednesday, January 31, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 Basic Steps 3 Step 1 - Log in 4 Step 2 - Create a New Site
Basic Steps for Autotask Endpoint Management Updated Wednesday, January 31, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 Basic Steps 3 Step 1 - Log in 4 Step 2 - Create a New Site
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
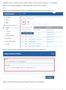 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Cloud Services. Introduction
 Introduction adi Digital have developed a resilient, secure, flexible, high availability Software as a Service (SaaS) cloud platform. This Platform provides a simple to use, cost effective and convenient
Introduction adi Digital have developed a resilient, secure, flexible, high availability Software as a Service (SaaS) cloud platform. This Platform provides a simple to use, cost effective and convenient
Sonicwall NSA240 / TZ210 Configuration Guide (Firmware: SonicOS Enhanced o & up)
 Sonicwall Configuration Guide v1.0 Sonicwall NSA240 / TZ210 Configuration Guide (Firmware: SonicOS Enhanced 5.8.1.1-35o & up) 169 Saxony Road, Suite 212 Encinitas, CA 92024 Phone & Fax: (800) 477-1477
Sonicwall Configuration Guide v1.0 Sonicwall NSA240 / TZ210 Configuration Guide (Firmware: SonicOS Enhanced 5.8.1.1-35o & up) 169 Saxony Road, Suite 212 Encinitas, CA 92024 Phone & Fax: (800) 477-1477
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Firewall Policy. Edit Firewall Policy/ACL CHAPTER7. Configure a Firewall Before Using the Firewall Policy Feature
 CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
Configuring SNMP. Understanding SNMP CHAPTER
 9 CHAPTER To have the sensor send SNMP traps, you must also choose Request SNMP Trap as the event action when you configure signatures. For more information, see Assigning Actions to Signatures, page 5-23.
9 CHAPTER To have the sensor send SNMP traps, you must also choose Request SNMP Trap as the event action when you configure signatures. For more information, see Assigning Actions to Signatures, page 5-23.
Packet Tracer - Investigating the TCP/IP and OSI Models in Action (Instructor Version Optional Packet Tracer)
 (Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
(Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
VMware Workspace ONE UEM VMware AirWatch Cloud Connector
 VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
Requirements. Cisco VPN Client setup file. Cisco VPN Client software installation
 Cisco VPN Client installation 1. Requirements 2. Cisco VPN Client setup file 3. Cisco VPN Client software installation 4. New connection setup 5. Authorization 6. Troubleshooting 7. Contacts Requirements
Cisco VPN Client installation 1. Requirements 2. Cisco VPN Client setup file 3. Cisco VPN Client software installation 4. New connection setup 5. Authorization 6. Troubleshooting 7. Contacts Requirements
VMware AirWatch Cloud Connector Guide ACC Installation and Integration
 VMware AirWatch Cloud Connector Guide ACC Installation and Integration Workspace ONE UEM v1810 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Cloud Connector Guide ACC Installation and Integration Workspace ONE UEM v1810 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
KYOCERA Device Manager Installation and Upgrade Guide
 KYOCERA Device Manager Installation and Upgrade Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice.
KYOCERA Device Manager Installation and Upgrade Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice.
ISA Management Set-up
 Windows 2000 Server - ISA management set-up Microsoft s Internet Security & Acceleration Server is an extensible enterprise firewall and Web cache server. This is an example of how to establish the proxy
Windows 2000 Server - ISA management set-up Microsoft s Internet Security & Acceleration Server is an extensible enterprise firewall and Web cache server. This is an example of how to establish the proxy
KYOCERA Device Manager Installation and Upgrade Guide
 KYOCERA Device Manager Installation and Upgrade Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice.
KYOCERA Device Manager Installation and Upgrade Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice.
while the LAN interface is in the DMZ. You can control access to the WAN port using either ACLs on the upstream router, or the built-in netfilter
 When the LAN interface is in a private IP DMZ, you can write the firewall rule-set to restrict the number of hosts the VBP can communicate with to only those devices. This enhances security. You can also
When the LAN interface is in a private IP DMZ, you can write the firewall rule-set to restrict the number of hosts the VBP can communicate with to only those devices. This enhances security. You can also
OneSecure VPN Remote User Installation & Configuration Guide
 OneSecure VPN Remote User Installation & Configuration Guide 3/11/2015 CONTENTS Download Client Software 02 Install Client Software 03 Enable Client Software 07 Configure the Connection 08 WELCOME Welcome
OneSecure VPN Remote User Installation & Configuration Guide 3/11/2015 CONTENTS Download Client Software 02 Install Client Software 03 Enable Client Software 07 Configure the Connection 08 WELCOME Welcome
Overlay Engine. VNS3 Plugins Guide 2018
 Overlay Engine VNS3 Plugins Guide 2018 Table of Contents Introduction 3 Overlay Engine Detail 7 Running the Overlay Engine Plugin 12 Overlay Engine Best Practices 20 Restrictions/Limitations 22 Resources
Overlay Engine VNS3 Plugins Guide 2018 Table of Contents Introduction 3 Overlay Engine Detail 7 Running the Overlay Engine Plugin 12 Overlay Engine Best Practices 20 Restrictions/Limitations 22 Resources
Lab - Configure the Firewall in Windows 7 and Vista
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected on a network Windows installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected on a network Windows installed
A 2012 RD Gateway server uses port 443 (HTTPS), which provides a secure connection using a Secure Sockets Layer (SSL) tunnel.
 Deploying Remote Desktop Gateway RDS 2012 What is a Remote Desktop Gateway A Remote Desktop Gateway Server enables users to connect to remote computers on a corporate network from any external computer.
Deploying Remote Desktop Gateway RDS 2012 What is a Remote Desktop Gateway A Remote Desktop Gateway Server enables users to connect to remote computers on a corporate network from any external computer.
Avaya Solution & Interoperability Test Lab Application Notes for configuring Datatal AB Flexi with Avaya IP Office 500 V2 Standalone R Issue 1.
 Avaya Solution & Interoperability Test Lab Application Notes for configuring Datatal AB Flexi with Avaya IP Office 500 V2 Standalone R10.0 - Issue 1.0 Abstract These Application Notes describe the configuration
Avaya Solution & Interoperability Test Lab Application Notes for configuring Datatal AB Flexi with Avaya IP Office 500 V2 Standalone R10.0 - Issue 1.0 Abstract These Application Notes describe the configuration
Step by Step SQL Server Alerts and Operator Notifications
 Step by Step SQL Server Alerts and Email Operator Notifications Hussain Shakir LinkedIn: https://www.linkedin.com/in/mrhussain Twitter: https://twitter.com/hshakir_ms Blog: http://mstechguru.blogspot.ae/
Step by Step SQL Server Alerts and Email Operator Notifications Hussain Shakir LinkedIn: https://www.linkedin.com/in/mrhussain Twitter: https://twitter.com/hshakir_ms Blog: http://mstechguru.blogspot.ae/
Sophos Transparent Authentication Suite Quick Start Guide. Product version: 2.0 Document date: Wednesday, July 05, 2017
 Sophos Transparent Authentication Suite Quick Start Guide Product version: 2.0 Document date: Wednesday, July 05, 2017 The specifications and information in this document are subject to change without
Sophos Transparent Authentication Suite Quick Start Guide Product version: 2.0 Document date: Wednesday, July 05, 2017 The specifications and information in this document are subject to change without
Installation Guide for Windows
 Installation Guide for Windows Advanced Research Computing V1.1 FINAL OPEN Document History This document relates to the BEAR DataShare service which is based on the product PowerFolder, version 11.5.625
Installation Guide for Windows Advanced Research Computing V1.1 FINAL OPEN Document History This document relates to the BEAR DataShare service which is based on the product PowerFolder, version 11.5.625
AWS VPC Cloud Environment Setup
 AWS VPC Cloud Environment Setup Table of Contents Introduction 3 Requirements 5 Step 1: VPC Deployment Setup 10 Step 2: Launching a VNS3 Controller 15 Instance VNS3 Configuration Document Links 19 2 Introduction
AWS VPC Cloud Environment Setup Table of Contents Introduction 3 Requirements 5 Step 1: VPC Deployment Setup 10 Step 2: Launching a VNS3 Controller 15 Instance VNS3 Configuration Document Links 19 2 Introduction
Application Notes for Virsae Service Management for Unified Communications with Avaya Aura Session Manager - Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Virsae Service Management for Unified Communications with Avaya Aura Session Manager - Issue 1.0 Abstract These Application Notes describe
Avaya Solution & Interoperability Test Lab Application Notes for Virsae Service Management for Unified Communications with Avaya Aura Session Manager - Issue 1.0 Abstract These Application Notes describe
BIZPRAC 12 GUIDE RE-INSTALLATION
 BIZPRAC 12 GUIDE RE-INSTALLATION BEFORE YOU START 1. Please ensure that your computer/s meets the Minimum System Requirements: http://www.bizprac.com/wp-content/uploads/bizprac- Minimum-System-Requirements.pdf.
BIZPRAC 12 GUIDE RE-INSTALLATION BEFORE YOU START 1. Please ensure that your computer/s meets the Minimum System Requirements: http://www.bizprac.com/wp-content/uploads/bizprac- Minimum-System-Requirements.pdf.
sflow (http://www.sflow.org) Agent Software Description
 sflow (http://www.sflow.org) sflow Agent Software Description This slide set is intended as a guide to InMon s example sflow agent software. The concepts and design choices are illustrated. The intention
sflow (http://www.sflow.org) sflow Agent Software Description This slide set is intended as a guide to InMon s example sflow agent software. The concepts and design choices are illustrated. The intention
Setting the firewall for LAN and DMZ
 Setting the firewall for LAN and DMZ Dokument-ID Version 2.0 Status Date of publication Setting the firewall for LAN and DMZ Final Version 01.2017 1 Contents 1.1 Need 3 1.2 Description 3 1.3 Requirements/limitations
Setting the firewall for LAN and DMZ Dokument-ID Version 2.0 Status Date of publication Setting the firewall for LAN and DMZ Final Version 01.2017 1 Contents 1.1 Need 3 1.2 Description 3 1.3 Requirements/limitations
Configuring MSDTC for Windows 2003 SP1
 Configuring MSDTC for Windows 2003 SP1 MSDTC for Windows 2003 SP1 has changed Configuration of the Microsoft Distributed Transaction Coordinator (MSDTC) in Microsoft Windows 2003 SP1 is slightly different
Configuring MSDTC for Windows 2003 SP1 MSDTC for Windows 2003 SP1 has changed Configuration of the Microsoft Distributed Transaction Coordinator (MSDTC) in Microsoft Windows 2003 SP1 is slightly different
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic. Topology. Objectives. Background / Scenario
 BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
H3C SecBlade NetStream Card Configuration Examples
 H3C SecBlade NetStream Card Configuration Examples Copyright 2012 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual may be reproduced or transmitted in any form or by any
H3C SecBlade NetStream Card Configuration Examples Copyright 2012 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual may be reproduced or transmitted in any form or by any
VISION. Network Assessment Tool User Guide
 VISION Network Assessment Tool User Guide Vision Network Assessment Tool - Presentation Ensuring our customers a reliable service is our first priority. ArkadinVision is designed to guarantee they will
VISION Network Assessment Tool User Guide Vision Network Assessment Tool - Presentation Ensuring our customers a reliable service is our first priority. ArkadinVision is designed to guarantee they will
Deploying VMware Identity Manager in the DMZ. JULY 2018 VMware Identity Manager 3.2
 Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Russian Cyber Attack Warning and Impact on AccessEnforcer UTM Firewall
 Russian Cyber Attack Warning and Impact on AccessEnforcer UTM Firewall 1 U.S. and U.K. authorities last week alerted the public to an on-going effort to exploit network infrastructure devices including
Russian Cyber Attack Warning and Impact on AccessEnforcer UTM Firewall 1 U.S. and U.K. authorities last week alerted the public to an on-going effort to exploit network infrastructure devices including
Palo Alto Networks Integration with LiveNX
 LIVEACTION, INC. Palo Alto Networks Integration with LiveNX LiveAction, Inc. Copyright 2008-2016 LiveAction, Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the 3500 LiveAction WEST BAYSHORE Logo
LIVEACTION, INC. Palo Alto Networks Integration with LiveNX LiveAction, Inc. Copyright 2008-2016 LiveAction, Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the 3500 LiveAction WEST BAYSHORE Logo
APSCN VPN Settings for Windows 7 2. APSCN VPN Settings for Windows XP 8. APSCN VPN Settings for MAC OS 15
 APSCN VPN Settings for Windows 7 2 1. Creating a VPN Connection 2 2. Disconnecting the VPN 6 3. Connecting to an existing VPN Connection 7 APSCN VPN Settings for Windows XP 8 1. Creating a VPN Connection
APSCN VPN Settings for Windows 7 2 1. Creating a VPN Connection 2 2. Disconnecting the VPN 6 3. Connecting to an existing VPN Connection 7 APSCN VPN Settings for Windows XP 8 1. Creating a VPN Connection
Integrate Palo Alto Traps. EventTracker v8.x and above
 EventTracker v8.x and above Publication Date: August 16, 2018 Abstract This guide provides instructions to configure Palo Alto Traps to send its syslog to EventTracker Enterprise. Scope The configurations
EventTracker v8.x and above Publication Date: August 16, 2018 Abstract This guide provides instructions to configure Palo Alto Traps to send its syslog to EventTracker Enterprise. Scope The configurations
A guide to configure agents for log collection in Log360
 A guide to configure agents for log collection in Log360 Contents Introduction... 2 Agent-based log collection... 2 When can you go for agent-based log collection?... 2 Architecture of agent-based log
A guide to configure agents for log collection in Log360 Contents Introduction... 2 Agent-based log collection... 2 When can you go for agent-based log collection?... 2 Architecture of agent-based log
User Guide. Setup and Installation guide
 User Guide Setup and Installation guide Contents 1. Getting Help... 2 2. System Requirements... 2 3. Loki Architecture and Installation Types... 3 4. Installation... 4 5. First Run... 7 6. Licencing...
User Guide Setup and Installation guide Contents 1. Getting Help... 2 2. System Requirements... 2 3. Loki Architecture and Installation Types... 3 4. Installation... 4 5. First Run... 7 6. Licencing...
SurePassID Local Agent Guide SurePassID Authentication Server 2016
 SurePassID Local Agent Guide SurePassID Authentication Server 2016 SurePassID Local Agent Guide Revision: 03 10 2016 You can find the most up-to-date technical documentation at: http://www.surepassid.com
SurePassID Local Agent Guide SurePassID Authentication Server 2016 SurePassID Local Agent Guide Revision: 03 10 2016 You can find the most up-to-date technical documentation at: http://www.surepassid.com
Unified Communications in RealPresence Access Director System Environments
 [Type the document title] 2.1.0 March 2013 3725-78704-001A Deploying Polycom Unified Communications in RealPresence Access Director System Environments Polycom Document Title 1 Trademark Information POLYCOM
[Type the document title] 2.1.0 March 2013 3725-78704-001A Deploying Polycom Unified Communications in RealPresence Access Director System Environments Polycom Document Title 1 Trademark Information POLYCOM
All rights reserved. All trademarks are the property of their respective owners.
 2017 5nine Software Inc. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
2017 5nine Software Inc. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Transport Gateway Installation / Registration / Configuration
 CHAPTER 4 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
CHAPTER 4 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
Lab IP Addresses and Network Communication
 Lab 3.5.2 IP Addresses and Network Communication Objectives Build a simple peer-to-peer network and verify physical connectivity. Assign various IP addresses to hosts and observe the effects on network
Lab 3.5.2 IP Addresses and Network Communication Objectives Build a simple peer-to-peer network and verify physical connectivity. Assign various IP addresses to hosts and observe the effects on network
Transport Gateway Installation / Registration / Configuration
 CHAPTER 2 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
CHAPTER 2 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
KLAS v7 Workstation Installation Self-Hosted Progress Version 10.2B / Windows 7
 KLAS Technical Notes Technical Notes 2012-1014 Doc Name: v7.5installation-selfhosted.docx KLAS v7 Workstation Installation Self-Hosted Progress Version 10.2B / Windows 7 Keystone has developed a means
KLAS Technical Notes Technical Notes 2012-1014 Doc Name: v7.5installation-selfhosted.docx KLAS v7 Workstation Installation Self-Hosted Progress Version 10.2B / Windows 7 Keystone has developed a means
DS2 Support. DS2 / inet System Installation Scenario 2. Scenario 1: - Windows 2003 Server - Utilizing an External SQL Server
 DS2 Support DS2 / inet System Installation Scenario 2 Scenario 1: - Windows 2003 Server - Utilizing an External SQL Server Author: Jason May Revision 8.0 Revision Date 03/2009 Overview The purpose of this
DS2 Support DS2 / inet System Installation Scenario 2 Scenario 1: - Windows 2003 Server - Utilizing an External SQL Server Author: Jason May Revision 8.0 Revision Date 03/2009 Overview The purpose of this
Dell SupportAssist Version 2.1 for Dell OpenManage Essentials Quick Setup Guide
 Dell SupportAssist Version 2.1 for Dell OpenManage Essentials Quick Setup Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer.
Dell SupportAssist Version 2.1 for Dell OpenManage Essentials Quick Setup Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer.
Horizon DaaS Platform 6.1 Service Provider Installation - vcloud
 Horizon DaaS Platform 6.1 Service Provider Installation - vcloud This guide provides information on how to install and configure the DaaS platform Service Provider appliances using vcloud discovery of
Horizon DaaS Platform 6.1 Service Provider Installation - vcloud This guide provides information on how to install and configure the DaaS platform Service Provider appliances using vcloud discovery of
Immotec Systems, Inc. SQL Server 2008 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
Blackpipe User Document
 This document describes Blackpipe, Dresser Wayne s secure alternative to the Netbios-based directory sharing that was implemented as the back-office system (BOS) interaction mechanism for Nucleus (POS)
This document describes Blackpipe, Dresser Wayne s secure alternative to the Netbios-based directory sharing that was implemented as the back-office system (BOS) interaction mechanism for Nucleus (POS)
Using Trend Reports. Understanding Reporting Options CHAPTER
 CHAPTER 10 To learn about supported services and platforms, see Supported Services and Platforms for Monitoring and Reports, page 1-5. The following topics describe the reporting features available in
CHAPTER 10 To learn about supported services and platforms, see Supported Services and Platforms for Monitoring and Reports, page 1-5. The following topics describe the reporting features available in
VNS3 Configuration. Google Compute Engine
 VNS3 Configuration Google Compute Engine Table of Contents Requirements 3 Step 1: GCE VNS3 Image Delivery 9 Step 2: GCE Network Setup 16 Step 3: Launching a VNS3 Controller 19 VNS3 Configuration Document
VNS3 Configuration Google Compute Engine Table of Contents Requirements 3 Step 1: GCE VNS3 Image Delivery 9 Step 2: GCE Network Setup 16 Step 3: Launching a VNS3 Controller 19 VNS3 Configuration Document
Creating Application Containers
 This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
Agent and Agent Browser. Updated Friday, January 26, Autotask Corporation
 Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
N-central 6.7 Express Essentials. Cisco Partner Guide for Deployment and Best Practices
 N-central 6.7 Express Essentials Cisco Partner Guide for Deployment and Best Practices Table of Contents Introduction...3 The N-central Express Trial...3 Preparing a Network for N-central Express...4 Outbound
N-central 6.7 Express Essentials Cisco Partner Guide for Deployment and Best Practices Table of Contents Introduction...3 The N-central Express Trial...3 Preparing a Network for N-central Express...4 Outbound
Client Installation Guide
 Client Installation Guide Version 2.3 April 2014 Purpose of this document This document is designed to assist you in installing the RMS client onto your workstations. The RMS client needs to be installed
Client Installation Guide Version 2.3 April 2014 Purpose of this document This document is designed to assist you in installing the RMS client onto your workstations. The RMS client needs to be installed
Freshservice Discovery Probe User Guide
 Freshservice Discovery Probe User Guide 1. What is Freshservice Discovery Probe? 1.1 What details does Probe fetch? 1.2 How does Probe fetch the information? 2. What are the minimum system requirements
Freshservice Discovery Probe User Guide 1. What is Freshservice Discovery Probe? 1.1 What details does Probe fetch? 1.2 How does Probe fetch the information? 2. What are the minimum system requirements
Using Templates. 5.4 Using Templates
 5.4 Using Templates Templates are used to create master files for control panel programming data to speed up programming of a new account. A template gives you a very quick and easy way to add a customer
5.4 Using Templates Templates are used to create master files for control panel programming data to speed up programming of a new account. A template gives you a very quick and easy way to add a customer
SET UP VPN FOR WINDOWS 10
 SET UP VPN FOR WINDOWS 10 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure
SET UP VPN FOR WINDOWS 10 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure
Wireless-G Router User s Guide
 Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Installing PERRY protech Automated Meter Collection Software
 Onsite Installation Instructions: 1) Verify and note the.net Framework, Microsoft OS Version and Administrative rights. i) Should any of these items be incorrect STOP THE INSTALLATION and notify the Customer
Onsite Installation Instructions: 1) Verify and note the.net Framework, Microsoft OS Version and Administrative rights. i) Should any of these items be incorrect STOP THE INSTALLATION and notify the Customer
Device Protocol Ports Source or Destination Required / Optional. Inbound TCP 1935, (see Purpose)
 27-Oct-2017 Device Protocol Ports Source or Destination / LU-2000 (MMH) Inbound UDP 8601-8608 Anywhere Incoming video and audio from any LiveU device. Note: if these ports are not available, the LiveU
27-Oct-2017 Device Protocol Ports Source or Destination / LU-2000 (MMH) Inbound UDP 8601-8608 Anywhere Incoming video and audio from any LiveU device. Note: if these ports are not available, the LiveU
Deploying VMware Identity Manager in the DMZ. SEPT 2018 VMware Identity Manager 3.3
 Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
AuditConfigurationArchiveandSoftwareManagementChanges (Network Audit)
 This section contains the following topics: Audit Configuration Archive and Software Management Changes (Network Audit), on page 1 Audit Changes Made By Users (Change Audit), on page 1 Audit Actions Executed
This section contains the following topics: Audit Configuration Archive and Software Management Changes (Network Audit), on page 1 Audit Changes Made By Users (Change Audit), on page 1 Audit Actions Executed
3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings 4. Select the check box for SPoE as default.
 Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Installation Guide. Research Computing Team V2.0 RESTRICTED
 Installation Guide Research Computing Team V2.0 RESTRICTED Document History This document relates to the BEAR DataShare service which is based on the product Power Folder, version 10.3.232 ( some screenshots
Installation Guide Research Computing Team V2.0 RESTRICTED Document History This document relates to the BEAR DataShare service which is based on the product Power Folder, version 10.3.232 ( some screenshots
Using Google Drive Some Basics
 Using Google Drive Some Basics Contents LOGIN 2 PURPOSE OF GOOGLE DRIVE 2 CREATE A FOLDER ON GOOGLE DRIVE 3 SHARE A FOLDER ON GOOGLE DRIVE 4 DOWNLOADING FROM GOOGLE DRIVE 5 UPLOADING TO GOOGLE DRIVE 6
Using Google Drive Some Basics Contents LOGIN 2 PURPOSE OF GOOGLE DRIVE 2 CREATE A FOLDER ON GOOGLE DRIVE 3 SHARE A FOLDER ON GOOGLE DRIVE 4 DOWNLOADING FROM GOOGLE DRIVE 5 UPLOADING TO GOOGLE DRIVE 6
Recording Agent User Guide
 Recording Agent User Guide Developed by New Rock Technologies, Inc., recording agent runs on Windows OS. It collects and manages, through Web GUI, recording files generated by the OM/WROC/MX series devices
Recording Agent User Guide Developed by New Rock Technologies, Inc., recording agent runs on Windows OS. It collects and manages, through Web GUI, recording files generated by the OM/WROC/MX series devices
Product Guide Revision B. McAfee Cloud Workload Security 5.0.0
 Product Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
Product Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
Module Overview. works Identify NAP enforcement options Identify scenarios for NAP usage
 Module 6: Network Policies and Access Protection Module Overview Describe how Network Policies Access Protection (NAP) works Identify NAP enforcement options Identify scenarios for NAP usage Describe Routing
Module 6: Network Policies and Access Protection Module Overview Describe how Network Policies Access Protection (NAP) works Identify NAP enforcement options Identify scenarios for NAP usage Describe Routing
Intelligent GP Reporting. Docman10 Import Process
 Intelligent GP Reporting Docman10 Import Process 1 Contents Import Required Notification... 3 Stage 1 Docman10 Export Process... 4 Stage 2 - Import Docman documents into igpr... 7 2 Import Required Notification
Intelligent GP Reporting Docman10 Import Process 1 Contents Import Required Notification... 3 Stage 1 Docman10 Export Process... 4 Stage 2 - Import Docman documents into igpr... 7 2 Import Required Notification
