INTRODUCTION...2 REQUIREMENTS...2 INSTALLATION...2 DISTRIBUTION...2 SAMPLE APPLICATION...3 FUNCTION: WinsockRCP...4
|
|
|
- Betty Glenn
- 6 years ago
- Views:
Transcription
1 Copyright 2002 Denicomp Systems. All rights reserved. INTRODUCTION...2 REQUIREMENTS...2 INSTALLATION...2 DISTRIBUTION...2 SAMPLE APPLICATION...3 FUNCTION: WinsockRCP...4 Usage... 4 Parameters... 4 Source and Destination Specifications... 6 Specifying a Different Local and Remote User... 6 Using the Remote Exec Daemon... 6 Specifying a Host for Both Source and Destination... 7 Return Value... 8 Security... 9 Unix Security Example FUNCTION: WinsockRCP Usage Parameters Declaring WinsockRCP2 in Other Languages Using WinsockRCP2 in Languages with Dynamically Allocated Strings Return Value Example FUNCTION: WinsockArrRCP...14 Usage Parameters Notes Example FUNCTION: WinsockArrRCP Usage Parameters Example FUNCTION: WinsockRCPSetIntOption...18 Usage Parameters Options Available Return Value FUNCTION: WinsockRCPSetStrOption...19 Usage Parameters Options Available Return Value Example FUNCTION: WinsockRCPCancel...21 Usage RETURN VALUES FOR ERRORS...22 SUPPORT
2 INTRODUCTION is a Microsoft Win32 Dynamic Link Library (DLL) that provides a Windows Sockets compatible function that allows you to copy files over TCP/IP using the rcp protocol. You can copy files from a Windows PC to a remote host, from the remote host to your PC, or between two remote hosts. provides most of the services of the rcp command found on many Unix systems, including recursive copies. It also includes the ability to convert text files to the appropriate format for Unix or Windows. The remote host must be a system running a Remote Shell Daemon (rshd) service that supports rcp, such as a Unix system or a PC running Denicomp Systems Winsock RSHD/95 or Winsock RSHD/NT. REQUIREMENTS requires a PC running any 32-bit Windows operating system, such as Windows NT/2000/XP/2003 or Windows 95/98/ME or any other Windows operating system that supports 32-bit Windows DLL s, a connection via TCP/IP to a remote host running rshd, and any programming language that supports calls to 32-bit DLL functions, such as C and Visual Basic. INSTALLATION To install from a CD-ROM, insert the CD and wait for the installer window to appear. If you do not see it appear within several seconds, browse the CD and double click on the SETUP file. Specify the directory where you want to install the files. After installation, to develop and run applications, you will need to copy the file RCP32.DLL to a directory in your PATH environment variable, the same directory as your executable, or your Windows directory (usually \WINNT or \WINDOWS) or Windows System directory (such as \WINNT\SYSTEM32). The directory you selected will contain the file RCP32.LIB, which is the import library for RCP32.DLL. C programmers can link this file to your programs to use RCP32.DLL. You may move this file to the directory containing your other C libraries if you wish. This directory will also contain the files RCP32.H and RCPERRS.H, which are C header files containing the function declarations for and constants that define error values returned. C programmers will #include these files in programs. You may move these files to a directory your compiler searches for header files if you wish. If you are using Microsoft C++, you will need to enclose the #include of RCP32.H within an _extern C { } block. DISTRIBUTION is licensed per developer. That is, each developer (programmer) that uses it to develop applications must have a license for their system. You may distribute the RCP32.DLL file with your application that uses it royalty-free to end-users of your application if you have the appropriate developer license(s). You may distribute the RCP32.DLL file only with your application
3 Note that per the license agreement, you may not distribute RCP32.DLL royalty-free if your program is simply a command line interface to RCP32.DLL or provides the end user with an Application Programmable Interface (API) into RCP32.DLL. SAMPLE APPLICATION The distribution includes two sample programs: VRCP, which is an interactive Visual Basic sample program, and CRCP, which is an example program written using Microsoft Visual C/C++. To view the Visual Basic example, load the file VRCP.MAK with Visual Basic. The CRCP Makefile for the example C program is named CRCP.MAK. It is set up to look in the current directory for the RCP32.H and RCP32.LIB files. You must modify it if you have moved these files. To compile the example program using Microsoft Visual C/C++, type the following at a Command Prompt: NMAKE /F CRCP.MAK CRCP.EXE The executable version of this example program is also included, so you do not need to compile it if you prefer. Once compiled, the program functions as a scaled down RCP command. It is a "console" program and its command line syntax is: Where: CRCP [-r][-a][-c][-h] source dest -r Recursively copy "source" to "dest". Copies all files and subdirectories in "source" to "dest". "dest" must be a directory. -a Perform ASCII end-of-line conversions. Otherwise, contents of files are not modified. -c Preserve the case of filenames when using wildcards or recursive copies. Otherwise, names are converted to lowercase characters. When copying individual files, the case specified on the command line is used. -h When using wildcards or -r, normally hidden files are not copied. If you specify -h, hidden files will be copied. -s If a filename contains spaces, an underscore (_) will be substituted for each space in the destination filename on the remote host. Do not combine command line options; separate each with a space. For example, use "-r -c", not "-rc". The "source" and "dest" parameters either specify a file or directory on the local system or a file or directory on a remote host. At least one of these must specify a remote host. When specifying a file/directory on a remote host, the "source" and/or "dest" parameters must be in the following format: [user@]host:file or [user@]host:directory Wildcards may be used. However, only one source and one destination can be specified. That is, you cannot specify multiple source files by separating the names with spaces as you can with the standard RCP command. Licensing Note: CRCP is included as a sample only. The license does not permit royaltyfree distribution of the DLL if your program is simply a command line interface into RCP32.DLL
4 FUNCTION DESCRIPTIONS FUNCTION: WinsockRCP C: int WinsockRCP(HWND hwndparent, char *lptitle, char *lpsrc, char *lpdest, int irecurflag, int iasciiflag, int iconsoleflag, int icaseflag, int ihiddenflag, int ispacechar) Visual Basic: Declare Function WinsockRCP Lib "RCP32.DLL" (ByVal hwndparent As Long, ByVal lptitle As String, ByVal lpsrc As String, ByVal lpdest As String, ByVal irecurflag As Long, ByVal iasciiflag As Long, ByVal iconsoleflag As Long, ByVal icaseflag As Long, ByVal ihiddenflag As Long, ByVal ispacechar As Long) As Long Usage The WinsockRCP function copies the Source (lpsrc) to the Destination (lpdest). The Source and Destinations are file specifications that can include a user name, a host name, and a file name, which may include wildcard characters, such as * and?. If any errors occur during the transfer, they will be displayed in standard Windows message boxes as they occur. See the WinsockRCP2 function if you wish to handle error messages in your program. Parameters hwndparent: lptitle: The handle (HWND) of a window in your application. The WinsockRCP function may produce diagnostic error messages using the Windows MessageBox function. This is used to specify the "parent" window to the MessageBox function. It may be NULL. Note: If your program is Windows console application, you should specify NULL for this parameter and see the iconsoleflag parameter for details about displaying error messages to the Console window. The title of your application or some other title. If any error messages are displayed using the Windows MessageBox function, this will be used as the title of the message box
5 lpsrc: lpdest: irecurflag: The file or directory to copy. See below for the format. The destination of the file(s). See below for the format. Specifies how directories should be copied. The options are: 0 - Directories will not be copied. If you attempt to copy a directory, you will receive an error message. This occurs if you explicitly try to copy a directory by specifying its name or directory names are matched by the wildcard pattern you specify. If you specify a wildcard pattern that matches both files and directories, the files will be copied, but you will receive an error message for each directory matched. 1 - Directories will be recursively copied. If you explicitly copy a directory by specifying its name, all files in that directory and the files in all subdirectories of that directory will be copied. The directory structure will be recreated on the destination system. If you specify a wildcard pattern, all directories matching that pattern will be recursively copied in addition to any matching files Specifying -1 (negative one) will not recursively copy directories, but it will suppress any error messages if your wildcard pattern matches directories. That is, your wildcard pattern will match only files, not directories. This is similar to specifying 0 (zero), but you will not receive error messages if you attempt to copy directories. iasciiflag: iconsoleflag: icaseflag: Specifies whether or not the copy should convert the file to the proper text file format. If the file is being copied to a remote host, CR/NL (ASCII 13/10) combinations are replaced with one NL (ASCII 10). If the file is being copied from a remote host, NL's are replaced by CR/NL combinations. Use a value of 0 if the files are not to be converted or a value of 1 if they are to be converted. ispecifies whether or not your application is a Windows console application. If you specify a value of 0, error messages will be displayed in standard Windows message boxes. If you specify a value of 1, error messages will be displayed to the console window using the "printf" function. Specifies whether or not the case of filenames is preserved when performing recursive copies or using wildcards. This affects recursive and wildcard copies only. If you use a specific, individual filename, the case you use will be preserved. Windows filenames can be stored using mixed case characters, even though the filesystem is not case sensitive. For example, "ABC" and "abc" represent the same file. However, the directory entry is displayed in the case you used when the file was created. If you specify a value of 0, the case of filenames will not be preserved. All filenames will be converted to lower case characters as they are received from or sent to the host. ihiddenflag: If you specify a value of 1, the case of filenames is preserved. Filenames will be created on the local system in the same case as they existed on the remote host. Likewise, filenames on the local system will be created in the same case on the remote host as they appear in the directory on the local system. Specifies whether or not files with the "hidden" attribute are copied when doing recursive copies or using wildcards. A value of 0 means hidden files will not be copied; a value of 1 means hidden files will be copied
6 ispacechar: Allows you to substitute a character for space characters (ASCII 32) in filenames. If you specify a value of 0, filenames are sent to the remote host exactly as they appear on the local system. However, some systems cannot easily handle filenames with embedded spaces. If you pass a character in this parameter (as an integer value), that character will be substituted in each filename on the remote host for each space. For example, if you pass an underscore (_) in this parameter, the filename: "this is a file.txt" will be created on the remote host as: "this_is_a_file.txt" Source and Destination Specifications Both the lpsrc and lpdest parameters must be of the following format: [[User@][Host:]]{File Dir} User@ (optional) Specifies the user name to be used at the remote host. If this prefixes the Host: parameter, this user name overrides the user name obtained from the local system when it is sent to the rshd. Specifying a Different Local and Remote User The rcp transfers normally occur through the rshd protocol. The rsh protocol allows two user logins to be sent to the server: a local user and a remote user. The standard Unix rshd validates access for both users, but accesses files in the security context of the remote user. When you use the User@ construct in the file specification, it sends User as both the local and remote users. If you wish to send different users for the local and remote users for the rsh protocol, specify them in the format localuser!remoteuser@. That is, separate them with an exclamation point (!) and RCP32.DLL will send the two different users. Using the Remote Exec Daemon Normally, rcp operates through the Remote Shell Daemon (rshd) on the server. However, with some systems (most Unix systems and Denicomp s Winsock REXECD/NT), you can have the rcp operate through the Remote Exec Daemon (rexecd). The difference is that the Remote Exec Daemon requires you to specify a password for each connection. If you want to use the rexec protocol for the rcp, you can do it with function calls (explained later see the WinsockRCPSetIntOption function) or you can do it by specifying the user name in the source or destination in the format user/password@. That is, separate the user and the password with a slash (/)
7 When the RCP32.DLL functions see the slash as part of the user name, it switches to using the rexec protocol and sends the user and password as you specified them. Host Specifies the TCP/IP host name of the remote host when referring to files on the remote host. This host must be a system running the rshd service. It may be an IP address instead of a host name. NOTE: Do not use a host name when referencing files on the local system. If you do, RCP32.DLL will expect that the local system is running a Remote Shell Daemon and may have other ramifications. Even if the local system is running an rshd, referring to local files this way is much less efficient and may not even work, depending on the setup of the local system. (See the note below about specifying the host in both the source and destination). File Dir Specifies the file name of the source or destination file. You may use wildcard characters to copy multiple source files. Specifies the file name of the source or destination directory. The source may be a directory only if you are using the recursive copy option. The destination must be a directory if you are copying multiple files or copying recursively. Specifying a Host for Both Source and Destination If you specify a host name for both the source and destination filenames, the rcp standard (the Unix rcp and RCP32.DLL) is to treat it as a pass through rcp. That is, rcp simply passes through the rcp command to the source system and tells it to perform the rcp. It does this using the rsh protocol This can cause problems if the source system does not have an rcp command (or it is non-standard) or is not running a Remote Shell Daemon. For example, if you specify: Source: Destination: systema:/temp/file1.txt systemb:/temp/file2.txt Internally, RCP32.DLL executes an rsh command like this: rsh systema rcp /temp/file1.txt systemb:/temp/file2.txt The result of this is what is expected - /temp/file1.txt is copied from systema to systemb. However, if systema is not running a Remote Shell Daemon or the rcp command does not exist on SystemA or it has non-standard syntax, this may fail. It is for this reason that you should never refer to local files with a host name if you cannot guarantee that the local system is running a compatible Remote Shell Daemon. (It is also much less efficient because it generates two network connections.) - 7 -
8 Return Value If WinsockRCP successfully copies all specified files, it will return a positive value that denotes the total number of files copied. Note that this number includes only individual files copied, not directory names created through recursive copies. However, if you copy files between two remote hosts (you specify a host name in the source and destination, resulting in no files copied to or from the local PC), a success will return zero, not the number of files copied. If WinsockRCP is not successful, it will return a negative number indicating the last error that occurred. A list of these error numbers is provided later. Note that if multiple files are to be copied, it will return a negative value if an error occurs on any of the transfers. WinsockRCP may have successfully copied files prior to the error and depending on the problem, may continue to copy the remaining files. If you are copying multiple files, the RCP protocol does not stop copying files when an error occurs unless it is a network error. Notes: A Host: must be specified for either the lpsrc or lpdest parameters, or both. If a full directory path is not specified for a remote host, the path begins at the user's home directory. That is, if the file/directory name specified after the Host: parameter does not begin with a slash (/), it is assumed to reference a file/directory in the user's home directory. For example, the file "joe@remhost:file.txt" refers to the file "file.txt" in the home directory of the user "joe" on the host "remhost". The method of determining the home directory is with the Remote Shell Daemon and/or operating system at the other end of the connection. Filenames may contain either slashes (/) or backslashes (\) as directory separators, for either the host file/directory or file/directories on the PC. They will be converted to the appropriate separator. You can copy multiple files by using wildcard characters, such as * or?. The wildcard capabilities are determined by the operating system running where the source files are located. For example, if you are copying files from a Unix host, you can use any of the wildcard options available on Unix to match the filenames. If the source of the files is the PC, you are limited to the wildcard options available in Windows. The lpsrc and lpdest parameters may include only one file specification each. That is, you cannot specify multiple source files by separating them with spaces as you can with the rcp command. To copy multiple individual filenames (that cannot be specified using wildcards or using a recursive copy), you must call WinsockRCP for each file or use the WinsockArrRCP or WinsockArrRCP2 functions. If you copy multiple source files with wildcard characters, the destination the destination must be a directory. Note that a colon (:) terminates the host name. This causes a problem when filenames on the PC require a drive letter (for example, A:). If a file name specification begins with one character between A and Z and is followed by a colon (:), WinsockRCP will interpret this as a drive letter instead of a host name. This means that WinsockRCP cannot handle one character host names. The destination cannot contain only a drive specification (for example,. A:). It must also include a filename or a directory name. If the destination is the current directory on the drive, use "." (for example,. A:. ). Using the ASCII conversion option to transfer files to the remote host will slow the copy operation somewhat because it must read each file twice. It reads the file once to calculate the new translated file size, then reads it again to transfer the data. This is because the RCP protocol requires that the exact file size be transmitted before - 8 -
9 the actual data in the file is sent. Without the conversion option, the file size can be found by examining the file's directory entry, but with the conversion option, the file's contents must be examined to determine the size after CR/NL combinations are replaced with NL. The ASCII conversion option will also slow Winsock RCP when transferring files from the remote host, but only slightly, because it must examine the data and translate it before writing it to the file. If transmission speed is critical, consider using utilities to translate the text files after they are transferred. Security The local user name determines the file access privileges WinsockRCP uses at the remote host. This name also determines the ownership and access modes of the destination file or files. If you specify a user name in either the source or destination filenames using the user@host construct, that name will be used at the remote host. If no user is specified for the source or destination along with the host name, the current Windows user is used. This is the user name you used when logging in to Windows. For example, if you logged in to Windows as the user fred, WinsockRCP will use fred as the user name at the remote host. WinsockRCP will always convert this name to all lowercase characters. RCP32.DLL provides two methods for overriding the user it uses when no user is specified in the source or destination parameters, if you do not want RCP32.DLL to use the current Windows login. The first method is to use the WinsockRCPSetStrOption call to set the User option to the desired remote user. This function is described in more detail in its own section later. Your program would need to implement a method for determining the appropriate user to specify in this call. The second method is to have RCP32.DLL get the user override from the file WIN.INI in the Windows directory (e.g. \WINNT or \WINDOWS) for an alternate user name. If WIN.INI contains a section named [RCP] and contains an entry named User in that section, the name specified there will be used as the local user name. For example, WIN.INI might contain: [RCP] User=joe If this appeared in WIN.INI, the local user name would be joe and WinsockRCP would use this name at the remote host. To support multiple users, WinsockRCP will also look for a section named [RCP-user] in WIN.INI first for an alternate user name, where the "user" in the section name is the name used to log in to Windows. WinsockRCP will look at this section first; if it does not exist, it will then look at the [RCP] section. For example, if "MaryJones" and "JohnSmith" are both users on the Windows PC, but their user names at the remote host are "mary" and "joe" respectively, WIN.INI might look like this: [RCP-JohnSmith] User=john [RCP-MaryJones] User=mary - 9 -
10 When the Windows user "JohnSmith" runs a program using WinsockRCP, "john" will be used at the remote host. When the Windows user "MaryJones" runs the program, "mary" will be used instead. Unix Security If the remote host is running the Unix operating system, it allows access through WinsockRCP if one of the following conditions is satisfied:?? The Unix system can obtain a name for the IP address of the system calling WinsockRCP.?? That name is listed as an equivalent host in the /etc/hosts.equiv file on the remote host.?? If the name is not in the /etc/hosts.equiv file, the user's home directory on the remote host must contain a.rhosts file that lists the name that name.?? If the.rhosts file is used, it must be owned by either the user specified or "root", and only the owner should have read and write access. That is, it must have permissions of These rules are determined by the Remote Shell Daemon (rshd), not. If the source or destination system is not a Unix system, the rshd on that system may have other rules and requirements. Example The CRCP program included with the distribution shows a full working example of the WinsockRCP2() function call. It is similar to the WinsockRCP() function call illustrated here: // This example copies the file "system.doc" in the user tom's home // directory on the host "remhost" to the directory "\doc" on the PC int result; char *rtitle = " Sample"; char *src = "tom@remhost:system.doc" char *dest = "/doc" result = WinsockRCP(NULL,rtitle,src,dest,0,0,1,0,0,0); if (result < 0) MessageBox(NULL,"Remote Copy Was Not Successful",rtitle,MB_OK); else MessageBox(NULL,"Remote Copy Was Successful",rtitle,MB_OK);
11 FUNCTION: WinsockRCP2 C: int WinsockRCP2 (char *lpsrc, char *lpdest, int irecurflag, int iasciiflag, int icaseflag, int ihiddenflag, int ispacechar, char *lperrmsg, int ierrlen) Visual Basic: Declare Function WinsockRCP2 Lib "RCP32.DLL" (ByVal lpsrc As String, ByVal lpdest As String, ByVal irecurflag As Long, ByVal iasciiflag As Long, ByVal icaseflag As Long, ByVal ihiddenflag As Long, ByVal ispacechar As Long, ByVal lperrmsg As String, ByVal ierrlen As Long) As Long Usage The WinsockRCP2 function performs the same function as the WinsockRCP function, but does not display error messages in Windows message boxes or to a console window. Instead, it returns the error messages in the area you provide. You can then display them, ignore them, or process them as you require. Parameters lpsrc The file or directory to copy. See WinsockRCP for details. lpdest The destination of the file(s). See WinsockRCP for details. irecurflag Specifies how directories should be copied. See WinsockRCP for details. iasciiflag Specifies whether or not the copy should convert the file to the proper text file format. See WinsockRCP for details. icaseflag Specifies whether or not the case of filenames will be preserved in recursive or wildcard copies to a remote host. See WinsockRCP for details. ihiddenflag Specifies whether or not hidden files will be copied. See WinsockRCP for details. ispacechar Allows you to substitute a character for space characters in filenames. See WinsockRCP for details. lperrmsg A pointer to an area of memory where any error messages generated during the copy can be stored. It cannot be NULL. This is explained in more detail later. ierrlen The total size in bytes of ErrMsg. This must be greater than or equal to
12 This function operates in the same manner as WinsockRCP, but if any errors occur during the transfer, the error messages will be accumulated in lperrmsg. Unlike WinsockRCP, they will not be displayed in message boxes or to a Console window. When the function returns, if the return value is negative, the text of any error messages will be stored in lperrmsg. Note that multiple errors can occur, since the RCP protocol does not necessarily stop transferring files on certain errors. If multiple errors do occur, each error message will be stored in lperrmsg and they will be separated by newline characters (ASCII 10). Hence, lperrmsg will be suitable for use with the Windows MessageBox function if you desire. For example, if you are copying a number of files and you receive two Permission denied errors, lperrmsg may contain (using C notation): Permission denied\npermission denied where \n is the newline character. lperrmsg should be large enough to hold at least a few error messages. WinsockRCP2 will not exceed the size of lperrmsg as specified by the ierrlen parameter. If the area is not large enough to hold an error message, it will not be stored. It is possible that the text of all error messages will not be stored in lperrmsg if a large number of errors occur. The size of lperrmsg (and the value specified for ierrlen) must be greater than zero. If you specify a very small value for ierrlen, no error text will ever be stored in lperrmsg since no message will fit, but return values will still be negative if errors occur. Declaring WinsockRCP2 in Other Languages If you are using a language other than C and Visual Basic, please keep in mind that the area of memory pointed to by the lperrmsg parameter in the WinsockRCP2 function call is modified by the DLL. Be sure when creating declarations in your language for the RCP32.DLL functions that you keep this in mind. Some languages require that you specify which parameters passed to DLL's will be modified and should be passed as a pointer, not as a copy of the variable value in the program. You may receive errors if you do not do this. Using WinsockRCP2 in Languages with Dynamically Allocated Strings For those using languages with dynamically allocated strings, such as Visual Basic, you must allocate space in the lperrmsg parameter before calling WinsockRCP2. Your program will most likely abort if you do not. Normally, when you declare a string in one of these languages, no memory is allocated for the variable until you store data in it. If you attempt to use the string variable without filling it with some value to force the language to allocate memory for it, the pointer passed may not be valid. In Visual Basic, this is normally done with the String$ function. For example: Dim emsg As String emsg = String$(256,Chr$(0))
13 This will store 256 Chr$(0) values (the null character) in the emsg variable. This will force Visual Basic to allocate 256 bytes of memory for emsg. When you pass emsg to WinsockRCP2, there will be 256 bytes available to store error messages. In Powerbuilder, this is normally done with the Space function: String emsg emsg = Space(256) This will fill the emsg variable with 256 spaces, and therefore allocate 256 bytes for the variable. Return Value If WinsockRCP2 successfully copies all specified files, it will return a positive value that denotes the total number of files copied. Note that this number includes only individual files copied, not directory names created through recursive copies. However, if you copy files between two remote hosts (you specify a host name in the source and destination, resulting in no files copied to or from the local PC), a success will return zero, not the number of files copied. If WinsockRCP2 is not successful, it will return a negative number indicating the last error that occurred. A list of these error numbers is provided later. Note that if multiple files are to be copied, it will return a negative value if an error occurs on any of the transfers. WinsockRCP2 may have successfully copied files prior to the error and depending on the problem, may continue to copy the remaining files. If you are copying multiple files, the RCP protocol does not stop copying files when an error occurs unless it is a network error. Example For a full working example of the WinsockRCP2 function in C, see the CRCP program included in the distribution. // This example copies the file "system.doc" in the user tom's home // directory on the host "remhost" to the directory "\doc" on the PC // If any error occurs, we will display it. int result; char *src = "tom@remhost:system.doc" char *dest = "/doc" char errmsg[256]; result = WinsockRCP2(rtitle,src,dest,0,0,0,0,0,errmsg,sizeof(errmsg)); if (result < 0) MessageBox(NULL,errmsg,"RCP Error!",MB_OK);
14 FUNCTION: WinsockArrRCP C: int WinsockArrRCP (HWND hwndparent, char *lptitle, char **lpargarr, int iargcount, int irecurflag, int iasciiflag, int iconsoleflag, int icaseflag, int ihiddenflag, int ispacechar) Usage The WinsockArrRCP function is similar to the WinsockRCP function, but accepts a vector (array) of strings containing the source and destination filenames. This allows you to copy multiple source files/directories in a single call when the files cannot be named using a single wildcard pattern or recursive copy. Any errors that occur are displayed in standard Windows message boxes or to the console window. See the WinsockArrRCP2 function if you wish to handle the displaying of error messages within your program. The strings in the array should be filenames of the format: [[User@][Host:]]{File Dir} The last string in the array will be considered the destination. The array must contain at least two strings (a source and a destination). Parameters The parameters to the WinsockArrRCP function are the same as those passed to the WinsockRCP function, except for the lpsrc and lpdest parameters. WinsockArrRCP substitutes the following parameters for lpsrc and lpdest: lpargarr Pointer to an array of strings. This array must contain two or more strings. The last string in the array will be considered the destination of the copy. iargcount The number of strings in the array. This is a number greater than or equal to two (2). Notes The same rules for WinsockRCP apply to this function. Refer to that section. However, here are a few important points:
15 A Host: must be specified for either the source files/directories or the destination file/directory (or both). The destination is always the last string in the array. If you copy multiple source files, the destination the destination must be a directory. Important Note: The WinsockArrRCP2 function may modify the values in the array of strings passed to it. To avoid confusion and problems with directory separator differences between operating systems, WinsockArrRCP2 will convert all backslashes (\) that appear in the array of strings to slashes (/). After the WinsockArrRCP2 completes, the array of strings will be changed in your program if it contained any backslashes. If you require that the strings be maintained in their original form, make a copy of the array and pass the copy to WinsockArrRCP2. Example // This example copies the files "plan.xls" and "bills.xls" in the // current directory to the "/u/hold" directory on the "unix" system. int result; char *rtitle = " Sample"; char *args[] = { "plan.xls", "bills.xls", "unix:/u/hold" }; result = WinsockArrRCP(NULL,rtitle,args,3,0,0,1,0,0,0); if (result < 0) MessageBox(NULL,"Remote Copy Was Not Successful",rtitle,MB_OK); else MessageBox(NULL,"Remote Copy Was Successful",rtitle,MB_OK);
16 FUNCTION: WinsockArrRCP2 C: int WinsockArrRCP2 (char **lpargarr, int iargcount, int irecurflag, int iasciiflag, int icaseflag, int ihiddenflag, int ispacechar, char *ErrMsg, int ierrlen) Usage The WinsockArrRCP2 function is similar to the WinsockRCP2 function, but accepts an array of strings containing the source and destination filenames. This allows you to copy multiple source files/directories in a single call when the files cannot be named using a single wildcard pattern. This function is similar to the WinsockArrRCP function, but does not display error messages in Windows message boxes or to the Console window. Instead, it returns the error messages in the area you provide. You can then display them, ignore them, or process them as you require. The strings in the array should be filenames of the format: [[User@][Host:]]{File Dir} The last string in the array will be considered the destination. The array must contain at least two strings (a source and a destination). Parameters The parameters to the WinsockArrRCP2 function are the same as those passed to the WinsockRCP2 function, except for the lpsrc and lpdest parameters. WinsockArrRCP2 substitutes the following parameters for lpsrc and lpdest: lpargarr Pointer to an array of strings. This array must contain two or more strings. The last string in the array will be considered the destination of the copy. iargcount The number of strings in the array. This must be greater than or equal to two (2). Notes: The same rules for WinsockRCP2 apply to this function. Refer to that section. However, here are a few important points:
17 A Host: must be specified for either the source files/directories or the destination file/directory (or both). The destination is always the last string in the array. If you copy multiple source files, the destination the destination must be a directory. Important Note: The WinsockArrRCP2 function may modify the values in the array of strings passed to it. To avoid confusion and problems with directory separator differences between operating systems, WinsockArrRCP2 will convert all backslashes (\) that appear in the array of strings to slashes (/). After the WinsockArrRCP2 completes, the array of strings will be changed in your program if it contained any backslashes. If you require that the strings be maintained in their original form, make a copy of the array and pass the copy to WinsockArrRCP2. Example // In this example, we will simply use the standard command line arguments // (argv[]) and pass them through to the WinsockArrRCP2 function. If you // modify the CRCP example program included with this package to do this // you will be able to specify multiple source files on the command line. // If any error occurs, we will display it. main(int argc, char **argv) { int result; } char errmsg[256]; // Skip argv[0] - that's the program name! result = WinsockArrRCP2(&argv[1],argc-1,0,0,0,0,0,errmsg, sizeof(errmsg)); if (result < 0) MessageBox(NULL,errmsg,"RCP Error!",MB_OK);
18 FUNCTION: WinsockRCPSetIntOption C: int WinsockRCPSetIntOption (char *lpoptionname, int ioptionvalue) Visual Basic: Declare Function WinsockRCPSetIntOption Lib "RCP32.DLL" (ByVal lpoptionname As String, ByVal ioptionvalue As Long) As Long Usage The WinsockRCPSetIntOption function sets options that affect the operation of the functions. This function is used when setting options that take an integer value. Parameters lpoptionname ioptionvalue This is a string indicating the option to be set. This is the value to associate with the option. Options Available Debug ConnTimeout RecvTimeout SendTimeout RetryError RetryCount NoProbe Specify a non-zero value to turn on the RCP32.DLL trace and 0 to turn it off. This has no effect if you do not also set the DebugFile option using the WinsockRCPSetStrOption to specify a filename. Currently, the values available or 1, 2, 3, and 4. Each gives an increasing amount of trace detail. A value of 4 causes a byte-by-byte dump of the data received or send via rcp to be recorded in the trace file, so the file can become very large. Default value: 0 Specify the number of seconds RCP32.DLL will wait to establish a connection to the server. If the connection is not established within that amount of time, the rcp function will return with an error. Default value: 60 Specify the number of seconds RCP32.DLL will wait to receive a block of data from the server during an rcp copy. If no data is received during this time, the rcp function will return with an error. Default value: 60 Specify the number of seconds RCP32.DLL will wait for a block of data to be sent to the server. Default value: 60 Set to the value of a Windows Sockets error number. If that error occurs when connecting to the server, it will retry the connection again, up to the number of times specified by the RetryCount option. Default value: 0 Set to the number of times you want RCP32.DLL to retry connecting to the server when one of the following TCP/IP errors occur: Address in use, Connection refused, Connection shutdown, Connection timed out, or the error number specified in the RetryError option. Default value: 1 When this is set to 1, RCP32.DLL does not probe for an unused local port number to use for the connection to the Remote Shell Daemon. Instead, it records the last local port used by each call and uses the next lower port number for the next connection. This helps to solve a connection timeout error that can occur on some networks, but adds a small overhead for
19 UseRexec Port BlockSize Blocking each connection. Default value: 0 Set to 1 to use the Remote Exec Daemon (rexecd) on the server instead of the Remote Shell Daemon. When this is set to 1, it automatically sets the port number to use to 512 (the standard rexec port) and will look for the password in the source or destination specification or the Password option set using the WinsockRCPSetStrOption. The rexecd requires a password to be specified to comp lete the connection. Default value: 0 Specify the port number to be used to connect to the server. The default is 514, which is the standard port for the Remote Shell Daemon. You can set this to 512 if you wish to execute the rcp through the Remote Exec Daemon (rexecd), but you must specify a password, either in the source or destination specification or using the Password option using the WinsockRCPSetStrOption. Specifies the block size that the rcp functions will use to read and write data to files and send and receive data from the network. Deafult value: 4096 Uses Winsock blocking calls when set to 1. This will disable the ability to specify connection/send/receive timeouts. Default value: 0 Return Value The WinsockRCPSetIntOption function normally returns a value of 0. However, it will return a value of 1 if you overflow the internal table used to store options. This should never occur if you do not pass invalid option names to the function. FUNCTION: WinsockRCPSetStrOption C: int WinsockRCPSetStrOption (char *lpoptionname, char *lpoptionvalue) Visual Basic: Declare Function WinsockRCPSetStrOption Lib "RCP32.DLL" (ByVal lpoptionname As String, ByVal lpoptionvalue As String) As Long Usage The WinsockRCPSetStrOption function sets options that affect the operation of the functions. This function is used when setting options that take a string value. The string may have a length of up to 128 bytes. Parameters lpoptionname lpoptionvalue This is a string indicating the option to be set. This is the value to associate with the option
20 Options Available DebugFile User Password Specify the filename to hold trace output. This is used in conjunction with the Debug integer option. See the description of the Debug option for more details. Use this to specify the user to send to the remote host for the rcp connection. This is used when the user is not specified in the source or destination file specification, to override the current Windows user. When the integer option UseRexec is set to 1, you can use this option to specify the password to be sent to the Remote Exec Daemon server for the user s login. Return Value The WinsockRCPSetIntOption function normally returns a value of 0. However, it will return a value of 1 if you overflow the internal table used to store options. This should never occur if you do not pass invalid option names to the function. Example // This example copies the file "system.doc" in the user tom's home // directory on the host "remhost" to the directory "\doc" on the PC // If any error occurs, we will display it. // // Instead of using the Remote Shell Daemon on the server, we will use // the Remote Exec Daemon, so we must also specify a password for the // connection. We will also override the current Windows user with // the user mary. int result; char *src = "remhost:/usr/system.doc" char *dest = "/doc" char errmsg[256]; WinsockRCPSetIntOption( UseRexec,1); WinsockRCPSetStrOption( User, mary ); WinsockRCPSetStrOption( Password, HadALittleLamb ); result = WinsockRCP2(rtitle,src,dest,0,0,0,0,0,errmsg,sizeof(errmsg)); if (result < 0) MessageBox(NULL,errmsg,"RCP Error!",MB_OK);
21 FUNCTION: WinsockRCPCancel C: int WinsockRCPCancel(void) Visual Basic: Declare Function WinsockRCPSetStrOption Lib "RCP32.DLL"() As Long Usage The WinsockRCPCancel function cancels the currently executing rcp function. The WinsockRCP* function will return with an error status of 22 if it was canceled during the actual file transfer, indicating it was canceled. Important Note: The WinsockRCPCancel function must be called from the same thread that initially called the WinsockRCP* function to be canceled
22 RETURN VALUES FOR ERRORS When an error occurs during a file transfer with WinsockRCP, WinsockRCP2, WinsockArrRCP, or WinsockArrRCP2, a negative value is returned indicating the last error that occurred. Constants for these error numbers are defined for you in the files RCPERRS.H (for C) and RCPERRS.BAS (for Visual Basic). The following are the possible values: Error Number Meaning -1 No host specified for either filename. -2 Unacceptable user name sign in filename. -3 The error message was received from the remote host. -4 Lost the connection to the host prematurely (network error) -5 Cannot allocate memory. -6 Can't get user from Windows or WIN.INI. -7 Target is ambiguous. -8 Invalid file type to send (a directory was specified without recursion). -9 No match for wildcard on remote host. -10 RCP Protocol Error. -11 Can't get information about a directory on the PC. -12 Error in the wildcard pattern used. -13 Can't get information about a file to send. -14 Can't open a file to send. -15 Error reading a file while sending. -16 Cannot get the filenames in a directory. -17 Pathname is too long. -18 Cannot open a file to be received for writing. -19 Error adjusting file size after receiving. Possibly out of disk space. -20 Error writing file while receiving. Possibly out of disk space. -22 The transfer was canceled by the WinsockRCPCancel function. SUPPORT Support is available via Internet: WWW: support@denicomp.com
DENICOMP SYSTEMS Copyright? 2003 Denicomp Systems All rights reserved.
 Copyright? 2003 Denicomp Systems All rights reserved. Table of Contents INTRODUCTION TO WINSOCK RSHD/NT...1 REQUIREMENTS...1 SECURITY A WARNING...1 WINSOCK RSHD/NT INSTALLATION...2 INSTALLING FROM A CD
Copyright? 2003 Denicomp Systems All rights reserved. Table of Contents INTRODUCTION TO WINSOCK RSHD/NT...1 REQUIREMENTS...1 SECURITY A WARNING...1 WINSOCK RSHD/NT INSTALLATION...2 INSTALLING FROM A CD
Appendix A GLOSSARY. SYS-ED/ Computer Education Techniques, Inc.
 Appendix A GLOSSARY SYS-ED/ Computer Education Techniques, Inc. $# Number of arguments passed to a script. $@ Holds the arguments; unlike $* it has the capability for separating the arguments. $* Holds
Appendix A GLOSSARY SYS-ED/ Computer Education Techniques, Inc. $# Number of arguments passed to a script. $@ Holds the arguments; unlike $* it has the capability for separating the arguments. $* Holds
Computer Science 2500 Computer Organization Rensselaer Polytechnic Institute Spring Topic Notes: C and Unix Overview
 Computer Science 2500 Computer Organization Rensselaer Polytechnic Institute Spring 2009 Topic Notes: C and Unix Overview This course is about computer organization, but since most of our programming is
Computer Science 2500 Computer Organization Rensselaer Polytechnic Institute Spring 2009 Topic Notes: C and Unix Overview This course is about computer organization, but since most of our programming is
Operating Systems, Unix Files and Commands SEEM
 Operating Systems, Unix Files and Commands SEEM 3460 1 Major Components of Operating Systems (OS) Process management Resource management CPU Memory Device File system Bootstrapping SEEM 3460 2 Programs
Operating Systems, Unix Files and Commands SEEM 3460 1 Major Components of Operating Systems (OS) Process management Resource management CPU Memory Device File system Bootstrapping SEEM 3460 2 Programs
Working with the Cisco IOS File System, Configuration Files, and Software Images
 APPENDIXB Working with the Cisco IOS File System, Configuration Files, and Software Images This appendix describes how to manipulate the Catalyst 2960 switch flash file system, how to copy configuration
APPENDIXB Working with the Cisco IOS File System, Configuration Files, and Software Images This appendix describes how to manipulate the Catalyst 2960 switch flash file system, how to copy configuration
Chapter Two. Lesson A. Objectives. Exploring the UNIX File System and File Security. Understanding Files and Directories
 Chapter Two Exploring the UNIX File System and File Security Lesson A Understanding Files and Directories 2 Objectives Discuss and explain the UNIX file system Define a UNIX file system partition Use the
Chapter Two Exploring the UNIX File System and File Security Lesson A Understanding Files and Directories 2 Objectives Discuss and explain the UNIX file system Define a UNIX file system partition Use the
C How to Program, 6/e by Pearson Education, Inc. All Rights Reserved.
 C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
CS Fundamentals of Programming II Fall Very Basic UNIX
 CS 215 - Fundamentals of Programming II Fall 2012 - Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the CS (Project) Lab (KC-265)
CS 215 - Fundamentals of Programming II Fall 2012 - Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the CS (Project) Lab (KC-265)
Work relative to other classes
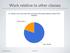 Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Command Interpreters. command-line (e.g. Unix shell) On Unix/Linux, bash has become defacto standard shell.
 Command Interpreters A command interpreter is a program that executes other programs. Aim: allow users to execute the commands provided on a computer system. Command interpreters come in two flavours:
Command Interpreters A command interpreter is a program that executes other programs. Aim: allow users to execute the commands provided on a computer system. Command interpreters come in two flavours:
Shell Programming Overview
 Overview Shell programming is a way of taking several command line instructions that you would use in a Unix command prompt and incorporating them into one program. There are many versions of Unix. Some
Overview Shell programming is a way of taking several command line instructions that you would use in a Unix command prompt and incorporating them into one program. There are many versions of Unix. Some
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Fall Programming Assignment 1 (updated 9/16/2017)
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Fall 2017 Programming Assignment 1 (updated 9/16/2017) Introduction The purpose of this programming assignment is to give you
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Fall 2017 Programming Assignment 1 (updated 9/16/2017) Introduction The purpose of this programming assignment is to give you
Introduction to Linux
 Introduction to Linux The command-line interface A command-line interface (CLI) is a type of interface, that is, a way to interact with a computer. Window systems, punched cards or a bunch of dials, buttons
Introduction to Linux The command-line interface A command-line interface (CLI) is a type of interface, that is, a way to interact with a computer. Window systems, punched cards or a bunch of dials, buttons
SE350: Operating Systems
 SE350: Operating Systems Tutorial: The Programming Interface Main Points Creating and managing processes fork, exec, wait Example: implementing a shell Shell A shell is a job control system Allows programmer
SE350: Operating Systems Tutorial: The Programming Interface Main Points Creating and managing processes fork, exec, wait Example: implementing a shell Shell A shell is a job control system Allows programmer
Features of C. Portable Procedural / Modular Structured Language Statically typed Middle level language
 1 History C is a general-purpose, high-level language that was originally developed by Dennis M. Ritchie to develop the UNIX operating system at Bell Labs. C was originally first implemented on the DEC
1 History C is a general-purpose, high-level language that was originally developed by Dennis M. Ritchie to develop the UNIX operating system at Bell Labs. C was originally first implemented on the DEC
A Fast Review of C Essentials Part I
 A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
Have examined process Creating program Have developed program Written in C Source code
 Preprocessing, Compiling, Assembling, and Linking Introduction In this lesson will examine Architecture of C program Introduce C preprocessor and preprocessor directives How to use preprocessor s directives
Preprocessing, Compiling, Assembling, and Linking Introduction In this lesson will examine Architecture of C program Introduce C preprocessor and preprocessor directives How to use preprocessor s directives
OPERATING SYSTEMS, ASSIGNMENT 4 FILE SYSTEM
 OPERATING SYSTEMS, ASSIGNMENT 4 FILE SYSTEM SUBMISSION DATE: 15/06/2014 23:59 In this assignment you are requested to extend the file system of xv6. xv6 implements a Unix-like file system, and when running
OPERATING SYSTEMS, ASSIGNMENT 4 FILE SYSTEM SUBMISSION DATE: 15/06/2014 23:59 In this assignment you are requested to extend the file system of xv6. xv6 implements a Unix-like file system, and when running
Download, Install and Setup the Linux Development Workload Create a New Linux Project Configure a Linux Project Configure a Linux CMake Project
 Table of Contents Download, Install and Setup the Linux Development Workload Create a New Linux Project Configure a Linux Project Configure a Linux CMake Project Connect to Your Remote Linux Computer Deploy,
Table of Contents Download, Install and Setup the Linux Development Workload Create a New Linux Project Configure a Linux Project Configure a Linux CMake Project Connect to Your Remote Linux Computer Deploy,
The New C Standard (Excerpted material)
 The New C Standard (Excerpted material) An Economic and Cultural Derek M. Jones derek@knosof.co.uk Copyright 2002-2008 Derek M. Jones. All rights reserved. 165 5.1.2.2.1 Program startup 5.1.2.2.1 Program
The New C Standard (Excerpted material) An Economic and Cultural Derek M. Jones derek@knosof.co.uk Copyright 2002-2008 Derek M. Jones. All rights reserved. 165 5.1.2.2.1 Program startup 5.1.2.2.1 Program
Creating a Shell or Command Interperter Program CSCI411 Lab
 Creating a Shell or Command Interperter Program CSCI411 Lab Adapted from Linux Kernel Projects by Gary Nutt and Operating Systems by Tannenbaum Exercise Goal: You will learn how to write a LINUX shell
Creating a Shell or Command Interperter Program CSCI411 Lab Adapted from Linux Kernel Projects by Gary Nutt and Operating Systems by Tannenbaum Exercise Goal: You will learn how to write a LINUX shell
Error num: 1 Meaning: Not owner Error num: 2 Meaning: No such file or directory Error num: 3 Meaning: No such process Error num: 4 Meaning:
 Error num: 1 Meaning: Not owner Error num: 2 Meaning: No such file or directory Error num: 3 Meaning: No such process Error num: 4 Meaning: Interrupted system call Error num: 5 Meaning: I/O error Error
Error num: 1 Meaning: Not owner Error num: 2 Meaning: No such file or directory Error num: 3 Meaning: No such process Error num: 4 Meaning: Interrupted system call Error num: 5 Meaning: I/O error Error
ECE Lesson Plan - Class 1 Fall, 2001
 ECE 201 - Lesson Plan - Class 1 Fall, 2001 Software Development Philosophy Matrix-based numeric computation - MATrix LABoratory High-level programming language - Programming data type specification not
ECE 201 - Lesson Plan - Class 1 Fall, 2001 Software Development Philosophy Matrix-based numeric computation - MATrix LABoratory High-level programming language - Programming data type specification not
Computer Science 322 Operating Systems Mount Holyoke College Spring Topic Notes: C and Unix Overview
 Computer Science 322 Operating Systems Mount Holyoke College Spring 2010 Topic Notes: C and Unix Overview This course is about operating systems, but since most of our upcoming programming is in C on a
Computer Science 322 Operating Systems Mount Holyoke College Spring 2010 Topic Notes: C and Unix Overview This course is about operating systems, but since most of our upcoming programming is in C on a
1 Lexical Considerations
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2013 Handout Decaf Language Thursday, Feb 7 The project for the course is to write a compiler
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2013 Handout Decaf Language Thursday, Feb 7 The project for the course is to write a compiler
Basic Tiger File System for SmartMedia. Version 1.04
 Basic Tiger File System for SmartMedia Version 1.04 Introduction...4 BTFS for SmartMedia Card...4 BTFS for SmartMedia File List...4 FS Include Files (directory File_System )...4 FS Examples (directory
Basic Tiger File System for SmartMedia Version 1.04 Introduction...4 BTFS for SmartMedia Card...4 BTFS for SmartMedia File List...4 FS Include Files (directory File_System )...4 FS Examples (directory
Should you know scanf and printf?
 C-LANGUAGE INPUT & OUTPUT C-Language Output with printf Input with scanf and gets_s and Defensive Programming Copyright 2016 Dan McElroy Should you know scanf and printf? scanf is only useful in the C-language,
C-LANGUAGE INPUT & OUTPUT C-Language Output with printf Input with scanf and gets_s and Defensive Programming Copyright 2016 Dan McElroy Should you know scanf and printf? scanf is only useful in the C-language,
ucalc Patterns Examine the following example which can be pasted into the interpreter (paste the entire block at the same time):
 [This document is far from complete but discusses some pattern essentials. Check back for more in the future; ask questions for clarity] ucalc Patterns ucalc patterns represent a key element of all current
[This document is far from complete but discusses some pattern essentials. Check back for more in the future; ask questions for clarity] ucalc Patterns ucalc patterns represent a key element of all current
Reading Assignment 4. n Chapter 4 Threads, due 2/7. 1/31/13 CSE325 - Processes 1
 Reading Assignment 4 Chapter 4 Threads, due 2/7 1/31/13 CSE325 - Processes 1 What s Next? 1. Process Concept 2. Process Manager Responsibilities 3. Operations on Processes 4. Process Scheduling 5. Cooperating
Reading Assignment 4 Chapter 4 Threads, due 2/7 1/31/13 CSE325 - Processes 1 What s Next? 1. Process Concept 2. Process Manager Responsibilities 3. Operations on Processes 4. Process Scheduling 5. Cooperating
5/20/2007. Touring Essential Programs
 Touring Essential Programs Employing fundamental utilities. Managing input and output. Using special characters in the command-line. Managing user environment. Surveying elements of a functioning system.
Touring Essential Programs Employing fundamental utilities. Managing input and output. Using special characters in the command-line. Managing user environment. Surveying elements of a functioning system.
EnableBasic. The Enable Basic language. Modified by Admin on Sep 13, Parent page: Scripting Languages
 EnableBasic Old Content - visit altium.com/documentation Modified by Admin on Sep 13, 2017 Parent page: Scripting Languages This Enable Basic Reference provides an overview of the structure of scripts
EnableBasic Old Content - visit altium.com/documentation Modified by Admin on Sep 13, 2017 Parent page: Scripting Languages This Enable Basic Reference provides an overview of the structure of scripts
CS 215 Fundamentals of Programming II Spring 2019 Very Basic UNIX
 CS 215 Fundamentals of Programming II Spring 2019 Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the EECS labs that dual boot
CS 215 Fundamentals of Programming II Spring 2019 Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the EECS labs that dual boot
Working with the Cisco IOS File System, Configuration Files, and Software Images
 CHAPTER B Working with the Cisco IOS File System, Configuration Files, and Software Images This appendix describes how to manipulate the Catalyst 3750 Metro switch flash file system, how to copy configuration
CHAPTER B Working with the Cisco IOS File System, Configuration Files, and Software Images This appendix describes how to manipulate the Catalyst 3750 Metro switch flash file system, how to copy configuration
OS lpr. www. nfsd gcc emacs ls 1/27/09. Process Management. CS 537 Lecture 3: Processes. Example OS in operation. Why Processes? Simplicity + Speed
 Process Management CS 537 Lecture 3: Processes Michael Swift This lecture begins a series of topics on processes, threads, and synchronization Today: processes and process management what are the OS units
Process Management CS 537 Lecture 3: Processes Michael Swift This lecture begins a series of topics on processes, threads, and synchronization Today: processes and process management what are the OS units
Linux & Shell Programming 2014
 Unit -1: Introduction to UNIX/LINUX Operating System Practical Practice Questions: Find errors (if any) otherwise write output or interpretation of following commands. (Consider default shell is bash shell.)
Unit -1: Introduction to UNIX/LINUX Operating System Practical Practice Questions: Find errors (if any) otherwise write output or interpretation of following commands. (Consider default shell is bash shell.)
Cisco IOS Shell. Finding Feature Information. Prerequisites for Cisco IOS.sh. Last Updated: December 14, 2012
 Cisco IOS Shell Last Updated: December 14, 2012 The Cisco IOS Shell (IOS.sh) feature provides shell scripting capability to the Cisco IOS command-lineinterface (CLI) environment. Cisco IOS.sh enhances
Cisco IOS Shell Last Updated: December 14, 2012 The Cisco IOS Shell (IOS.sh) feature provides shell scripting capability to the Cisco IOS command-lineinterface (CLI) environment. Cisco IOS.sh enhances
CS 307: UNIX PROGRAMMING ENVIRONMENT FIND COMMAND
 CS 307: UNIX PROGRAMMING ENVIRONMENT FIND COMMAND Prof. Michael J. Reale Fall 2014 Finding Files in a Directory Tree Suppose you want to find a file with a certain filename (or with a filename matching
CS 307: UNIX PROGRAMMING ENVIRONMENT FIND COMMAND Prof. Michael J. Reale Fall 2014 Finding Files in a Directory Tree Suppose you want to find a file with a certain filename (or with a filename matching
EDIABAS BEST/2 LANGUAGE DESCRIPTION. VERSION 6b. Electronic Diagnostic Basic System EDIABAS - BEST/2 LANGUAGE DESCRIPTION
 EDIABAS Electronic Diagnostic Basic System BEST/2 LANGUAGE DESCRIPTION VERSION 6b Copyright BMW AG, created by Softing AG BEST2SPC.DOC CONTENTS CONTENTS...2 1. INTRODUCTION TO BEST/2...5 2. TEXT CONVENTIONS...6
EDIABAS Electronic Diagnostic Basic System BEST/2 LANGUAGE DESCRIPTION VERSION 6b Copyright BMW AG, created by Softing AG BEST2SPC.DOC CONTENTS CONTENTS...2 1. INTRODUCTION TO BEST/2...5 2. TEXT CONVENTIONS...6
ITC213: STRUCTURED PROGRAMMING. Bhaskar Shrestha National College of Computer Studies Tribhuvan University
 ITC213: STRUCTURED PROGRAMMING Bhaskar Shrestha National College of Computer Studies Tribhuvan University Lecture 07: Data Input and Output Readings: Chapter 4 Input /Output Operations A program needs
ITC213: STRUCTURED PROGRAMMING Bhaskar Shrestha National College of Computer Studies Tribhuvan University Lecture 07: Data Input and Output Readings: Chapter 4 Input /Output Operations A program needs
Introduction to MATLAB
 Chapter 1 Introduction to MATLAB 1.1 Software Philosophy Matrix-based numeric computation MATrix LABoratory built-in support for standard matrix and vector operations High-level programming language Programming
Chapter 1 Introduction to MATLAB 1.1 Software Philosophy Matrix-based numeric computation MATrix LABoratory built-in support for standard matrix and vector operations High-level programming language Programming
Introduction to OS Processes in Unix, Linux, and Windows MOS 2.1 Mahmoud El-Gayyar
 Introduction to OS Processes in Unix, Linux, and Windows MOS 2.1 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 Processes in Unix, Linux, and Windows Unix pre-empted
Introduction to OS Processes in Unix, Linux, and Windows MOS 2.1 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 Processes in Unix, Linux, and Windows Unix pre-empted
Microprocessors & Assembly Language Lab 1 (Introduction to 8086 Programming)
 Microprocessors & Assembly Language Lab 1 (Introduction to 8086 Programming) Learning any imperative programming language involves mastering a number of common concepts: Variables: declaration/definition
Microprocessors & Assembly Language Lab 1 (Introduction to 8086 Programming) Learning any imperative programming language involves mastering a number of common concepts: Variables: declaration/definition
LPR for Windows 95/98/Me/2000 TCP/IP Printing User s Guide
 LPR for Windows 95/98/Me/2000 TCP/IP Printing User s Guide Rev. 02 (August, 2001) Copyright Statement Trademarks Copyright 1997 No part of this publication may be reproduced in any form or by any means
LPR for Windows 95/98/Me/2000 TCP/IP Printing User s Guide Rev. 02 (August, 2001) Copyright Statement Trademarks Copyright 1997 No part of this publication may be reproduced in any form or by any means
CMPT 300. Operating Systems. Brief Intro to UNIX and C
 CMPT 300 Operating Systems Brief Intro to UNIX and C Outline Welcome Review Questions UNIX basics and Vi editor Using SSH to remote access Lab2(4214) Compiling a C Program Makefile Basic C/C++ programming
CMPT 300 Operating Systems Brief Intro to UNIX and C Outline Welcome Review Questions UNIX basics and Vi editor Using SSH to remote access Lab2(4214) Compiling a C Program Makefile Basic C/C++ programming
Baan OpenWorld 2.2. Installation and Configuration Guide for Adapter
 Baan OpenWorld 2.2 Installation and Configuration Guide for Adapter A publication of: Baan Development B.V. P.O.Box 143 3770 AC Barneveld The Netherlands Printed in the Netherlands Baan Development B.V.
Baan OpenWorld 2.2 Installation and Configuration Guide for Adapter A publication of: Baan Development B.V. P.O.Box 143 3770 AC Barneveld The Netherlands Printed in the Netherlands Baan Development B.V.
UNIX files searching, and other interrogation techniques
 UNIX files searching, and other interrogation techniques Ways to examine the contents of files. How to find files when you don't know how their exact location. Ways of searching files for text patterns.
UNIX files searching, and other interrogation techniques Ways to examine the contents of files. How to find files when you don't know how their exact location. Ways of searching files for text patterns.
User Commands tar ( 1 )
 NAME tar create tape archives and add or extract files SYNOPSIS tar c [ bbeeffhiklnoppqvwx@ [0-7]] [block] [tarfile] [exclude-file] {-I include-file -C directory file file}... tar r [ bbeeffhiklnqvw@ [0-7]]
NAME tar create tape archives and add or extract files SYNOPSIS tar c [ bbeeffhiklnoppqvwx@ [0-7]] [block] [tarfile] [exclude-file] {-I include-file -C directory file file}... tar r [ bbeeffhiklnqvw@ [0-7]]
Unix Introduction to UNIX
 Unix Introduction to UNIX Get Started Introduction The UNIX operating system Set of programs that act as a link between the computer and the user. Developed in 1969 by a group of AT&T employees Various
Unix Introduction to UNIX Get Started Introduction The UNIX operating system Set of programs that act as a link between the computer and the user. Developed in 1969 by a group of AT&T employees Various
Lexical Considerations
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Fall 2005 Handout 6 Decaf Language Wednesday, September 7 The project for the course is to write a
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Fall 2005 Handout 6 Decaf Language Wednesday, September 7 The project for the course is to write a
What s in the SAS SQL Library for C?
 SAS SQL Library for C, Version 1.3 Requirements Package Contents Usage Ideas Data You Can Access SAS Concepts Usage Guide List of Functions Sample Code Error Codes & Messages Glossary What s New The SAS
SAS SQL Library for C, Version 1.3 Requirements Package Contents Usage Ideas Data You Can Access SAS Concepts Usage Guide List of Functions Sample Code Error Codes & Messages Glossary What s New The SAS
Crash Course in Unix. For more info check out the Unix man pages -orhttp://www.cs.rpi.edu/~hollingd/unix. -or- Unix in a Nutshell (an O Reilly book).
 Crash Course in Unix For more info check out the Unix man pages -orhttp://www.cs.rpi.edu/~hollingd/unix -or- Unix in a Nutshell (an O Reilly book). 1 Unix Accounts To access a Unix system you need to have
Crash Course in Unix For more info check out the Unix man pages -orhttp://www.cs.rpi.edu/~hollingd/unix -or- Unix in a Nutshell (an O Reilly book). 1 Unix Accounts To access a Unix system you need to have
5/8/2012. Creating and Changing Directories Chapter 7
 Creating and Changing Directories Chapter 7 Types of files File systems concepts Using directories to create order. Managing files in directories. Using pathnames to manage files in directories. Managing
Creating and Changing Directories Chapter 7 Types of files File systems concepts Using directories to create order. Managing files in directories. Using pathnames to manage files in directories. Managing
File Commands. Objectives
 File Commands Chapter 2 SYS-ED/Computer Education Techniques, Inc. 2: 1 Objectives You will learn: Purpose and function of file commands. Interrelated usage of commands. SYS-ED/Computer Education Techniques,
File Commands Chapter 2 SYS-ED/Computer Education Techniques, Inc. 2: 1 Objectives You will learn: Purpose and function of file commands. Interrelated usage of commands. SYS-ED/Computer Education Techniques,
Introduction to Bash Programming. Dr. Xiaolan Zhang Spring 2013 Dept. of Computer & Information Sciences Fordham University
 Introduction to Bash Programming Dr. Xiaolan Zhang Spring 2013 Dept. of Computer & Information Sciences Fordham University 1 Outline Shell command line syntax Shell builtin commands Shell variables, arguments
Introduction to Bash Programming Dr. Xiaolan Zhang Spring 2013 Dept. of Computer & Information Sciences Fordham University 1 Outline Shell command line syntax Shell builtin commands Shell variables, arguments
Fall 2015 COMP Operating Systems. Lab #3
 Fall 2015 COMP 3511 Operating Systems Lab #3 Outline n Operating System Debugging, Generation and System Boot n Review Questions n Process Control n UNIX fork() and Examples on fork() n exec family: execute
Fall 2015 COMP 3511 Operating Systems Lab #3 Outline n Operating System Debugging, Generation and System Boot n Review Questions n Process Control n UNIX fork() and Examples on fork() n exec family: execute
BLITZ I 128. A BASIC Compiler. for. Commodore 128. from. Skyles Electric Works. Instruction Manual. Bob Skyles
 Skyles Electric ~rks BLITZ I 128 A BASIC Compiler for Commodore 128 from Skyles Electric Works Instruction Manual by Bob Skyles Table of Contents Subject 1. INTRODUCTION Restrictions Special Instructions
Skyles Electric ~rks BLITZ I 128 A BASIC Compiler for Commodore 128 from Skyles Electric Works Instruction Manual by Bob Skyles Table of Contents Subject 1. INTRODUCTION Restrictions Special Instructions
commandname flags arguments
 Unix Review, additional Unix commands CS101, Mock Introduction This handout/lecture reviews some basic UNIX commands that you should know how to use. A more detailed description of this and other commands
Unix Review, additional Unix commands CS101, Mock Introduction This handout/lecture reviews some basic UNIX commands that you should know how to use. A more detailed description of this and other commands
12/22/11. Java How to Program, 9/e. public must be stored in a file that has the same name as the class and ends with the.java file-name extension.
 Java How to Program, 9/e Education, Inc. All Rights Reserved. } Covered in this chapter Classes Objects Methods Parameters double primitive type } Create a new class (GradeBook) } Use it to create an object.
Java How to Program, 9/e Education, Inc. All Rights Reserved. } Covered in this chapter Classes Objects Methods Parameters double primitive type } Create a new class (GradeBook) } Use it to create an object.
Laboratory 0 Week 0 Advanced Structured Programming An Introduction to Visual Studio and C++
 Laboratory 0 Week 0 Advanced Structured Programming An Introduction to Visual Studio and C++ 0.1 Introduction This is a session to familiarize working with the Visual Studio development environment. It
Laboratory 0 Week 0 Advanced Structured Programming An Introduction to Visual Studio and C++ 0.1 Introduction This is a session to familiarize working with the Visual Studio development environment. It
Paranoid Penguin rsync, Part I
 Paranoid Penguin rsync, Part I rsync makes efficient use of the network by only transferring the parts of files that are different from one host to the next. Here's how to use it securely. by Mick Bauer
Paranoid Penguin rsync, Part I rsync makes efficient use of the network by only transferring the parts of files that are different from one host to the next. Here's how to use it securely. by Mick Bauer
In the case of the dynamic array, the space must be deallocated when the program is finished with it. free(x);
 C Notes Relation Between Pointers and Arrays Space for static arrays in C is allocated on the stack when the function that defines them is called and is automatically deleted when the function ends, just
C Notes Relation Between Pointers and Arrays Space for static arrays in C is allocated on the stack when the function that defines them is called and is automatically deleted when the function ends, just
CSE II-Sem)
 a) Write a shell script that displays a list of all the files in the current directory to which the user has read, write and execute permissions. b) Develop an interactive script that asks for a word and
a) Write a shell script that displays a list of all the files in the current directory to which the user has read, write and execute permissions. b) Develop an interactive script that asks for a word and
printf( Please enter another number: ); scanf( %d, &num2);
 CIT 593 Intro to Computer Systems Lecture #13 (11/1/12) Now that we've looked at how an assembly language program runs on a computer, we're ready to move up a level and start working with more powerful
CIT 593 Intro to Computer Systems Lecture #13 (11/1/12) Now that we've looked at how an assembly language program runs on a computer, we're ready to move up a level and start working with more powerful
The UNIX File System
 The UNIX File System Magnus Johansson (May 2007) 1 UNIX file system A file system is created with mkfs. It defines a number of parameters for the system as depicted in figure 1. These paremeters include
The UNIX File System Magnus Johansson (May 2007) 1 UNIX file system A file system is created with mkfs. It defines a number of parameters for the system as depicted in figure 1. These paremeters include
CSC209: Software tools. Unix files and directories permissions utilities/commands Shell programming quoting wild cards files
 CSC209 Review CSC209: Software tools Unix files and directories permissions utilities/commands Shell programming quoting wild cards files ... and systems programming C basic syntax functions arrays structs
CSC209 Review CSC209: Software tools Unix files and directories permissions utilities/commands Shell programming quoting wild cards files ... and systems programming C basic syntax functions arrays structs
CSC209: Software tools. Unix files and directories permissions utilities/commands Shell programming quoting wild cards files. Compiler vs.
 CSC209 Review CSC209: Software tools Unix files and directories permissions utilities/commands Shell programming quoting wild cards files... and systems programming C basic syntax functions arrays structs
CSC209 Review CSC209: Software tools Unix files and directories permissions utilities/commands Shell programming quoting wild cards files... and systems programming C basic syntax functions arrays structs
Working with the Cisco IOS File System, Configuration Files, and Software Images
 APPENDIX B Working with the Cisco IOS File System, Configuration Files, and Software Images This appendix describes how to manipulate the switch flash file system, how to copy configuration files, and
APPENDIX B Working with the Cisco IOS File System, Configuration Files, and Software Images This appendix describes how to manipulate the switch flash file system, how to copy configuration files, and
Preview from Notesale.co.uk Page 6 of 52
 Binary System: The information, which it is stored or manipulated by the computer memory it will be done in binary mode. RAM: This is also called as real memory, physical memory or simply memory. In order
Binary System: The information, which it is stored or manipulated by the computer memory it will be done in binary mode. RAM: This is also called as real memory, physical memory or simply memory. In order
Configuring Basic File Transfer Services
 Using basic file transfer services, you can configure a router as a Trivial File Transfer Protocol (TFTP) or Reverse Address Resolution Protocol (RARP) server, configure the router to forward extended
Using basic file transfer services, you can configure a router as a Trivial File Transfer Protocol (TFTP) or Reverse Address Resolution Protocol (RARP) server, configure the router to forward extended
Armide Documentation. Release Kyle Mayes
 Armide Documentation Release 0.3.1 Kyle Mayes December 19, 2014 Contents 1 Introduction 1 1.1 Features.................................................. 1 1.2 License..................................................
Armide Documentation Release 0.3.1 Kyle Mayes December 19, 2014 Contents 1 Introduction 1 1.1 Features.................................................. 1 1.2 License..................................................
bytes per disk block (a block is usually called sector in the disk drive literature), sectors in each track, read/write heads, and cylinders (tracks).
 Understanding FAT 12 You need to address many details to solve this problem. The exercise is broken down into parts to reduce the overall complexity of the problem: Part A: Construct the command to list
Understanding FAT 12 You need to address many details to solve this problem. The exercise is broken down into parts to reduce the overall complexity of the problem: Part A: Construct the command to list
CSCI S-Q Lecture #12 7/29/98 Data Structures and I/O
 CSCI S-Q Lecture #12 7/29/98 Data Structures and I/O Introduction The WRITE and READ ADT Operations Case Studies: Arrays Strings Binary Trees Binary Search Trees Unordered Search Trees Page 1 Introduction
CSCI S-Q Lecture #12 7/29/98 Data Structures and I/O Introduction The WRITE and READ ADT Operations Case Studies: Arrays Strings Binary Trees Binary Search Trees Unordered Search Trees Page 1 Introduction
Lexical Considerations
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2010 Handout Decaf Language Tuesday, Feb 2 The project for the course is to write a compiler
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2010 Handout Decaf Language Tuesday, Feb 2 The project for the course is to write a compiler
Files (review) and Regular Expressions. Todd Kelley CST8207 Todd Kelley 1
 Files (review) and Regular Expressions Todd Kelley kelleyt@algonquincollege.com CST8207 Todd Kelley 1 midterms (Feb 11 and April 1) Files and Permissions Regular Expressions 2 Sobel, Chapter 6 160_pathnames.html
Files (review) and Regular Expressions Todd Kelley kelleyt@algonquincollege.com CST8207 Todd Kelley 1 midterms (Feb 11 and April 1) Files and Permissions Regular Expressions 2 Sobel, Chapter 6 160_pathnames.html
6Using the Install and. Licensing APIs 6CHAPTER
 6CHAPTER 6Using the Install and Chapter Licensing APIs This chapter describes how to use the functions in the InterBase Install API as part of an application install. It includes the following topics:
6CHAPTER 6Using the Install and Chapter Licensing APIs This chapter describes how to use the functions in the InterBase Install API as part of an application install. It includes the following topics:
Getting Started with UNIX
 Getting Started with UNIX What is UNIX? Boston University Information Services & Technology Course Number: 4000 Course Instructor: Kenny Burns Operating System Interface between a user and the computer
Getting Started with UNIX What is UNIX? Boston University Information Services & Technology Course Number: 4000 Course Instructor: Kenny Burns Operating System Interface between a user and the computer
BLM2031 Structured Programming. Zeyneb KURT
 BLM2031 Structured Programming Zeyneb KURT 1 Contact Contact info office : D-219 e-mail zeynebkurt@gmail.com, zeyneb@ce.yildiz.edu.tr When to contact e-mail first, take an appointment What to expect help
BLM2031 Structured Programming Zeyneb KURT 1 Contact Contact info office : D-219 e-mail zeynebkurt@gmail.com, zeyneb@ce.yildiz.edu.tr When to contact e-mail first, take an appointment What to expect help
Contents. Error Message Descriptions... 7
 2 Contents Error Message Descriptions.................................. 7 3 4 About This Manual This Unify DataServer: Error Messages manual lists the errors that can be produced by the Unify DataServer
2 Contents Error Message Descriptions.................................. 7 3 4 About This Manual This Unify DataServer: Error Messages manual lists the errors that can be produced by the Unify DataServer
Lecture 3. Introduction to Unix Systems Programming: Unix File I/O System Calls
 Lecture 3 Introduction to Unix Systems Programming: Unix File I/O System Calls 1 Unix File I/O 2 Unix System Calls System calls are low level functions the operating system makes available to applications
Lecture 3 Introduction to Unix Systems Programming: Unix File I/O System Calls 1 Unix File I/O 2 Unix System Calls System calls are low level functions the operating system makes available to applications
Gabriel Hugh Elkaim Spring CMPE 013/L: C Programming. CMPE 013/L: C Programming
 1 Literal Constants Definition A literal or a literal constant is a value, such as a number, character or string, which may be assigned to a variable or a constant. It may also be used directly as a function
1 Literal Constants Definition A literal or a literal constant is a value, such as a number, character or string, which may be assigned to a variable or a constant. It may also be used directly as a function
Configuring the Cisco IOS DHCP Server
 Cisco devices running Cisco software include Dynamic Host Configuration Protocol (DHCP) server and the relay agent software. The Cisco IOS DHCP server is a full DHCP server implementation that assigns
Cisco devices running Cisco software include Dynamic Host Configuration Protocol (DHCP) server and the relay agent software. The Cisco IOS DHCP server is a full DHCP server implementation that assigns
Language Reference Manual
 TAPE: A File Handling Language Language Reference Manual Tianhua Fang (tf2377) Alexander Sato (as4628) Priscilla Wang (pyw2102) Edwin Chan (cc3919) Programming Languages and Translators COMSW 4115 Fall
TAPE: A File Handling Language Language Reference Manual Tianhua Fang (tf2377) Alexander Sato (as4628) Priscilla Wang (pyw2102) Edwin Chan (cc3919) Programming Languages and Translators COMSW 4115 Fall
Exploring the file system. Johan Montelius HT2016
 1 Introduction Exploring the file system Johan Montelius HT2016 This is a quite easy exercise but you will learn a lot about how files are represented. We will not look to the actual content of the files
1 Introduction Exploring the file system Johan Montelius HT2016 This is a quite easy exercise but you will learn a lot about how files are represented. We will not look to the actual content of the files
www nfsd emacs lpr Process Management CS 537 Lecture 4: Processes Example OS in operation Why Processes? Simplicity + Speed
 Process Management CS 537 Lecture 4: Processes Michael Swift This lecture begins a series of topics on processes, threads, and synchronization Today: processes and process management what are the OS units
Process Management CS 537 Lecture 4: Processes Michael Swift This lecture begins a series of topics on processes, threads, and synchronization Today: processes and process management what are the OS units
In this text box, type the name of the File Watcher. By default, IntelliJ IDEA suggests the name of the selected predefined template.
 New Watcher Dialog File Settings File Watchers The dialog box opens when you click the Add or Edit button on the File Watchers page. Use the dialog box to create a project File Watcher based on a predefined
New Watcher Dialog File Settings File Watchers The dialog box opens when you click the Add or Edit button on the File Watchers page. Use the dialog box to create a project File Watcher based on a predefined
File Management. Ezio Bartocci.
 File Management Ezio Bartocci ezio.bartocci@tuwien.ac.at Cyber-Physical Systems Group Institute for Computer Engineering Faculty of Informatics, TU Wien Motivation A process can only contain a limited
File Management Ezio Bartocci ezio.bartocci@tuwien.ac.at Cyber-Physical Systems Group Institute for Computer Engineering Faculty of Informatics, TU Wien Motivation A process can only contain a limited
DAB/MOT Data Carousel Support Library Linux Server Implementation
 DAB/MOT Data Carousel Support Library Linux Server Implementation D. Knox 98-0003-003/1.0 28th Apr 1990 ENSIGMA Ltd Turing House Station Road Chepstow GWENT NP6 5PB Ensigma Ltd. Page 2 of 31 Distribution
DAB/MOT Data Carousel Support Library Linux Server Implementation D. Knox 98-0003-003/1.0 28th Apr 1990 ENSIGMA Ltd Turing House Station Road Chepstow GWENT NP6 5PB Ensigma Ltd. Page 2 of 31 Distribution
Overview of the UNIX File System
 Overview of the UNIX File System Navigating and Viewing Directories Adapted from Practical Unix and Programming Hunter College Copyright 2006 Stewart Weiss The UNIX file system The most distinguishing
Overview of the UNIX File System Navigating and Viewing Directories Adapted from Practical Unix and Programming Hunter College Copyright 2006 Stewart Weiss The UNIX file system The most distinguishing
2) clear :- It clears the terminal screen. Syntax :- clear
 1) cal :- Displays a calendar Syntax:- cal [options] [ month ] [year] cal displays a simple calendar. If arguments are not specified, the current month is displayed. In addition to cal, the ncal command
1) cal :- Displays a calendar Syntax:- cal [options] [ month ] [year] cal displays a simple calendar. If arguments are not specified, the current month is displayed. In addition to cal, the ncal command
Advanced Batch Files. Ch 11 1
 Advanced Batch Files Ch 11 1 Overview Quick review of batch file commands learned in earlier chapters. Ch 11 2 Overview Advanced features of these commands will be explained and used. Ch 11 3 Overview
Advanced Batch Files Ch 11 1 Overview Quick review of batch file commands learned in earlier chapters. Ch 11 2 Overview Advanced features of these commands will be explained and used. Ch 11 3 Overview
CS61C Machine Structures. Lecture 3 Introduction to the C Programming Language. 1/23/2006 John Wawrzynek. www-inst.eecs.berkeley.
 CS61C Machine Structures Lecture 3 Introduction to the C Programming Language 1/23/2006 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L03 Introduction to C (1) Administrivia
CS61C Machine Structures Lecture 3 Introduction to the C Programming Language 1/23/2006 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L03 Introduction to C (1) Administrivia
Table of Contents 1 FTP and SFTP Configuration TFTP Configuration 2-1
 Table of Contents 1 FTP and SFTP Configuration 1-1 Introduction to FTP and SFTP 1-1 Introduction to FTP 1-1 Introduction to SFTP 1-1 FTP Configuration 1-2 FTP Configuration: A Switch Operating as an FTP
Table of Contents 1 FTP and SFTP Configuration 1-1 Introduction to FTP and SFTP 1-1 Introduction to FTP 1-1 Introduction to SFTP 1-1 FTP Configuration 1-2 FTP Configuration: A Switch Operating as an FTP
Programming Environment Variable APIs
 System i Programming Environment Variable APIs Version 6 Release 1 System i Programming Environment Variable APIs Version 6 Release 1 Note Before using this information and the product it supports, read
System i Programming Environment Variable APIs Version 6 Release 1 System i Programming Environment Variable APIs Version 6 Release 1 Note Before using this information and the product it supports, read
CS 326 Operating Systems C Programming. Greg Benson Department of Computer Science University of San Francisco
 CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2016 Programming Assignment 1 Introduction The purpose of this
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2016 Programming Assignment 1 Introduction The purpose of this programming assignment is to give you some experience
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2016 Programming Assignment 1 Introduction The purpose of this programming assignment is to give you some experience
Converter. Dynamic Concepts' suite of conversion utilities for those migrating from. IMS to dl4
 IMS to dl4 Converter Dynamic Concepts' suite of conversion utilities for those migrating from IMS to dl4 The IMS Converter requires dl4 version 5.2.1 or higher. Contact Dynamic Concepts if a dl4 upgrade
IMS to dl4 Converter Dynamic Concepts' suite of conversion utilities for those migrating from IMS to dl4 The IMS Converter requires dl4 version 5.2.1 or higher. Contact Dynamic Concepts if a dl4 upgrade
CS102: Standard I/O. %<flag(s)><width><precision><size>conversion-code
 CS102: Standard I/O Our next topic is standard input and standard output in C. The adjective "standard" when applied to "input" or "output" could be interpreted to mean "default". Typically, standard output
CS102: Standard I/O Our next topic is standard input and standard output in C. The adjective "standard" when applied to "input" or "output" could be interpreted to mean "default". Typically, standard output
Libgdb. Version 0.3 Oct Thomas Lord
 Libgdb Version 0.3 Oct 1993 Thomas Lord Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies.
Libgdb Version 0.3 Oct 1993 Thomas Lord Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies.
Remote Watchman Device Server User Manual
 Remote Watchman Device Server User Manual Software Version 4.0 Manual P/N 071-0043 Rev 8 September 29, 2016 Copyright 2000-2016 Sensorsoft Corporation, All rights reserved. Sensorsoft, SCOM and Remote
Remote Watchman Device Server User Manual Software Version 4.0 Manual P/N 071-0043 Rev 8 September 29, 2016 Copyright 2000-2016 Sensorsoft Corporation, All rights reserved. Sensorsoft, SCOM and Remote
Introduction to Unix: Fundamental Commands
 Introduction to Unix: Fundamental Commands Ricky Patterson UVA Library Based on slides from Turgut Yilmaz Istanbul Teknik University 1 What We Will Learn The fundamental commands of the Unix operating
Introduction to Unix: Fundamental Commands Ricky Patterson UVA Library Based on slides from Turgut Yilmaz Istanbul Teknik University 1 What We Will Learn The fundamental commands of the Unix operating
