TECHNICAL WHITE PAPER FIDO APPROACHES: NOK NOK LABS S3 SUITE VS BUILD YOUR OWN FIDO
|
|
|
- Rosanna McLaughlin
- 5 years ago
- Views:
Transcription
1 TECHNICAL WHITE PAPER FIDO APPROACHES: NOK NOK LABS S3 SUITE VS BUILD YOUR OWN FIDO
2 TABLE OF CONTENTS Executive Summary... 3 FIDO Solution Requirements... 3 FIDO UAF Client infrastructure... 4 FIDO UAF Server Infrastructure... 4 Summary... 6
3 EXECUTIVE SUMMARY The FIDO specifications provide an open approach to strong authentication. Industry leaders from across the the industry have formed an alliance to cooperate defining technical specifications that deliver strong authentication interoperability. Organizations that deploy consumer-facing applications are able to leverage these FIDO specifications and can choose to deploy the Nok Nok Labs S3 Authentication Suite or can take a do it yourself approach to building FIDO authentication infrastructure. This paper focuses on the FIDO UAF protocol and highlights the main issues that organizations should consider in making this decision. It explains why the Nok Nok Labs S3 Suite provides better value, security and a proven approach to successful FIDO-based solution deployment. FIDO SOLUTION REQUIREMENTS Keeping Up With An Evolving FIDO Specification Like any other protocol, the FIDO specifications will continue to develop over time to add new capabilities and address new use cases. An organization s ability to leverage updated FIDO capabilities that appear on new FIDO-enabled devices will be dependent on the FIDO server s support for these new features. An organization that chooses to implement its own FIDO server will need to continue to monitor the evolution of the FIDO specification, and incorporate support for updated features. Without such continued investment, the capabilities of the FIDO server will fall behind the current specifications and may result in reduced functionality and limited interoperability with newer devices featuring FIDO support. The final draft of the FIDO UAF 1.0 specification was published in December 2014, and that is expected to be superseded by FIDO UAF 1.1 in late In addition, the prospect of FIDO 2.0 (including the W3C s Web Auth proposal for integrating FIDO with modern web browsers) is on the horizon, which may entail further changes to an organization building their own FIDO deployment. The Nok Nok Labs S3 Suite allows an organization to take advantage of the feature richness of FIDO without having to dedicate considerable development resources to keeping up with FIDO updates and changes. Development Issues The FIDO protocol is a specification, not a technology. Deploying a FIDO authentication solution involves resources and costs to implement the specification. While organizations can develop their own FIDO infrastructure to support FIDO-enabled devices and applications, required resources and costs in terms of development, testing and support can quickly mount. This involves both client-side (see Figure 1) and server side (see Figure 2) development. As shown in Figure 1, organizations need to address SDKs for each target platform that interface with the target mobile application and the FIDO client on the device, in addition to the authentication server infrastructure. 3 NOK NOK LABS OCTOBER 2016
4 FIDO UAF CLIENT INFRASTRUCTURE FIDO Certified Android Device Apple ios Device Google Android 6.0+ Device Future FIDO Device Requires SDK interfacing with FIDO UAF stack preloaded by the device manufacturer. Requires SDK to leverage platform s Touch ID API to implement FIDO UAF stack. Requires SDK leveraging Android s Fingerprint APIs to implement a FIDO UAF stack. Requires SDK leveraging future FIDO authenticators and interface to future FIDO UAF protocol. SDK (Java) SDK (Objective-C) SDK (Java) SDK (OS-specific) UAF 1.0/1.1 Client UAF 1.0 Client UAF 1.x Client UAF 1.0/1.1 ASM UAF 1.0 ASM UAF 1.x ASM UAF 1.0/1.1 Authenticator UAF 1.0 Authenticator FIDO UAF 1.0/1.1 Client Touch ID API FingerprintManager API Future FIDO Authenticator Figure 1 Organization Builds FIDO UAF Interface / Data Format Device Manufacturer Builds Platform Vendor Builds FIDO UAF SERVER INFRASTRUCTURE FIDO Certified Server Infrastructure Policy and Risk Engine Data Storage Layer Policy Validation Replay Attack Protection FIDO UAF User Keys FIDO UAF Metadata Transaction Validation Attestation Verification Database Abstraction Layer Cryptographic Provider FIDO UAF Protocol Handlers FIDO UAF 1.0 Handler FIDO UAF 1.1 Handler FIDO UAF 1.x Handler Transport Interface (REST API) Application Infrastructure Session Management Business Logic Policy Selection Risk Engine Integration FIDO Certified Android Device Apple ios Device Google Android 6.0+ Device Future FIDO Device Figure 2 Organization Builds FIDO UAF Interface / Data Format 4 NOK NOK LABS OCTOBER 2016
5 The FIDO specifications include a number of nonnormative elements that are left to the FIDO developer/implementor to design and deploy. Examples include how to (i) handle replay attack prevention, (ii) track information across authentications, and (iii) represent and manage policy on the server. The developer/implementor is required to address these issues, among others, which reside outside of the FIDO protocol. The Nok Nok Labs S3 addresses these elements so the deploying organization can deploy more quickly and with lower risk. While the FIDO specifications provide a roadmap to developing an authentication server, organizations need to consider a variety of design decisions when building their own FIDO server solution. The Nok Nok Labs S3 Suite provides a proven solution for both the client and the server that accelerates deployment, lowers project risk and avoids development costs. Heterogeneous Platform & Device Support Organizations deploying FIDO solutions will want to support a broad number of devices and authenticators in order to avoid authentication silos and reduce costs. While organizations deploying their own FIDO solution can take advantage of any FIDO Certified device, the Nok Nok Labs S3 Suite also provides support for any device, not just FIDO Certified devices. For example, Nok Nok Labs App SDK supports both ios using Touch ID or Device Passcode, as well as Android 6.0 or later devices equipped with a fingerprint sensor. An organization that builds their own FIDO solution that would like to take advantage of native platform APIs such as the Google Android 6.0 Fingerprint API or Apple Touch ID API will need to develop and maintain software to enable those platform APIs in the context of FIDO. This means building a FIDO Client to embed in an organization s mobile application, as well as an Authenticator Specific Module (ASM) and the authenticator (e.g. a fingerprint sensor, etc.) that leverages the native platform APIs to perform the underlying FIDO cryptographic and user verification operations. This development is required for each target platform. The Nok Nok S3 Suite provides a complete solution to support these multiple platforms with heterogeneous devices, saving the organization time and resources. A key issue when building a FIDO server is ensuring that the implementation complies with the FIDO specifications, and is interoperable with FIDO-enabled devices provided by third parties, such as mobile device manufacturers (OEMs). An organization that chooses to build its own FIDO server will need to perform qualification against FIDO-enabled devices to ensure their implementation meets FIDO specifications and is interoperable with other FIDO enabled devices. This may require the organization create a testbed, and then purchase and test a significant inventory of devices against their own FIDO server implementation. Without such rigorous interoperability testing, an organization will not be assured their server will interoperate correctly with third-party FIDO devices. Deployment Issues Deploying a FIDO solution requires skill and planning to ensure that the server infrastructure has sufficient scalability and is tuned to deliver exceptionally low latency that optimizes the customer authentication experience. Nok Nok Labs provides a highly tuned Nok Nok Authentication Server that benefits from years of development, testing, tuning and from the lessons learned from the many customer deployments that support millions of end users at scale. Security Developing a FIDO solution requires security preparations such as penetration testing and auditability. While developing a FIDO server would require such penetration testing, the Nok Nok solution has already completed the necessary penetration testing and avoids auditing. 5 NOK NOK LABS OCTOBER 2016
6 Intellectual Property Protection The FIDO Alliance framework involves a contractual intellectual property (IP) regime that relates to the FIDO Alliance specifications. Members of the FIDO Alliance promise not to assert IP rights against other Alliance members, as related to and required by the implementation of the FIDO specifications. An implementor of the FIDO specification who is not a member of the FIDO Alliance does not benefit from this promise not to assert IP rights, and could therefore assume IP risk. Using the Nok Nok Labs S3 Suite provides certain IP protection, because Nok Nok Labs is a founding member of the Alliance, and benefits from the promise not to assert patent rights; Nok Nok Labs has also developed its own patent portfolio to protect its innovations around the implementation of its FIDO solutions. Additional Feature Requirements Out of Band (OOB) Authentication The Nok Nok Labs S3 Suite builds on top of FIDO to enable the use of a FIDO -enabled mobile device as an Out of Band method of authentication. With this feature, users can use their phone to authenticate sessions and transactions initiated on another device (such as a desktop web browser, or a kiosk). This unique functionality in the Nok Nok Labs S3 Suite is beyond the scope of FIDO specifications, and is only provided by Nok Nok Labs. Authentication Policies The Nok Nok Labs S3 Suite provides lower risk and reduces fraud through dynamic authentication policy options for flexible authentication. Such functionality requires custom code development for an organization that builds its own FIDO server. Infrastructure Integration - Nok Nok Labs S3 Suite also provides lower costs and simplicity with integration with Identity and Access Management (IAM) and federation systems. Such functionality requires custom code development for an organization building its own FIDO server. SUMMARY The Nok Nok Labs S3 Suite is a proven solution that provides simplicity, lower costs, faster deployment and optimal security. While enterprises can develop their own SDKs and authentication servers, this approach increases initial project risk and costs and also carries an ongoing burden required to support and maintain FIDO interoperability as the specifications evolve. The Nok Nok S3 approach provides functionality beyond basic FIDO support including the ability to support devices from any vendor including Apple and Touch ID. Nok Nok Labs provides the shortest route to successful FIDO-based strong authentication. 6 NOK NOK LABS OCTOBER 2016
7 ABOUT NOK NOK LABS Backed by a team of security industry veterans from PGP, Netscape, PayPal, and Phoenix Technologies, Nok Nok Labs has deep experience in building internetscale security protocols and products. Our ambition is to fundamentally transform authentication, by unifying authentication into one standard protocol, giving business the power to make the utmost of the cloud, data, mobile, and business online. Nok Nok Labs 2100 Geng Road, Suite 105 Palo Alto, CA TO LEARN MORE ABOUT NOK NOK LABS, VISIT NOKNOK.COM OR CONTACT US AT INFO@NOKNOK.COM Nok Nok Labs, Nok Nok, and NNL are all trademarks of Nok Nok Labs, Inc Nok Nok Labs, Inc. All Rights Reserved.
TECHNICAL WHITE PAPER ENABLING BIOMETRICS FOR MOBILE APPLICATION AUTHENTICATION
 TECHNICAL WHITE PAPER ENABLING BIOMETRICS FOR MOBILE APPLICATION AUTHENTICATION Comparing Nok Nok S3 Authentication Suite and Native API Approaches EXECUTIVE SUMMARY In an increasingly mobile world, relying
TECHNICAL WHITE PAPER ENABLING BIOMETRICS FOR MOBILE APPLICATION AUTHENTICATION Comparing Nok Nok S3 Authentication Suite and Native API Approaches EXECUTIVE SUMMARY In an increasingly mobile world, relying
EMERGING TRENDS AROUND AUTHENTICATION
 EMERGING TRENDS AROUND AUTHENTICATION Michelle Salway Senior Director Sales - EMEA May 2017 1 BIOMETRICS: A GIFT FROM THE DEVICE MAKERS & BIOMETRIC VENDORS DEVICES ARE RICH IN AUTHENTICATION CAPABILITIES,
EMERGING TRENDS AROUND AUTHENTICATION Michelle Salway Senior Director Sales - EMEA May 2017 1 BIOMETRICS: A GIFT FROM THE DEVICE MAKERS & BIOMETRIC VENDORS DEVICES ARE RICH IN AUTHENTICATION CAPABILITIES,
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 783 data breaches >1 billion records stolen since 2012 $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 783 data breaches >1 billion records stolen since 2012 $3.5 million average cost per breach 4 We have a PASSWORD
Who What Why
 Who What Why Board Members Sponsors Associates To Change Authentication Online by: (a) Developing unencumbered Specifications that define interoperable mechanisms that supplant reliance on passwords (b)
Who What Why Board Members Sponsors Associates To Change Authentication Online by: (a) Developing unencumbered Specifications that define interoperable mechanisms that supplant reliance on passwords (b)
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
FIDO AND PAYMENTS AUTHENTICATION. Philip Andreae Vice President Oberthur Technologies
 FIDO AND PAYMENTS AUTHENTICATION Philip Andreae Vice President Oberthur Technologies The Problem The Solution The Alliance Updates Data Breaches 781 data breaches in 2015 170 million records in 2015 (up
FIDO AND PAYMENTS AUTHENTICATION Philip Andreae Vice President Oberthur Technologies The Problem The Solution The Alliance Updates Data Breaches 781 data breaches in 2015 170 million records in 2015 (up
MODERNIZE INFRASTRUCTURE
 SOLUTION OVERVIEW MODERNIZE INFRASTRUCTURE Support Digital Evolution in the Multi-Cloud Era Agility and Innovation Are Top of Mind for IT As digital transformation gains momentum, it s making every business
SOLUTION OVERVIEW MODERNIZE INFRASTRUCTURE Support Digital Evolution in the Multi-Cloud Era Agility and Innovation Are Top of Mind for IT As digital transformation gains momentum, it s making every business
BUILDING the VIRtUAL enterprise
 BUILDING the VIRTUAL ENTERPRISE A Red Hat WHITEPAPER www.redhat.com As an IT shop or business owner, your ability to meet the fluctuating needs of your business while balancing changing priorities, schedules,
BUILDING the VIRTUAL ENTERPRISE A Red Hat WHITEPAPER www.redhat.com As an IT shop or business owner, your ability to meet the fluctuating needs of your business while balancing changing priorities, schedules,
BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE
 BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE OUR ORGANISATION AND SPECIALIST SKILLS Focused on delivery, integration and managed services around Identity and Access Management.
BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE OUR ORGANISATION AND SPECIALIST SKILLS Focused on delivery, integration and managed services around Identity and Access Management.
A NEW MODEL FOR AUTHENTICATION
 All Rights Reserved. FIDO Alliance. Copyright 2016. A NEW MODEL FOR AUTHENTICATION ENABLING MORE EFFICIENT DIGITAL SERVICE DELIVERY Jeremy Grant jeremy.grant@chertoffgroup.com Confidential 5 The world
All Rights Reserved. FIDO Alliance. Copyright 2016. A NEW MODEL FOR AUTHENTICATION ENABLING MORE EFFICIENT DIGITAL SERVICE DELIVERY Jeremy Grant jeremy.grant@chertoffgroup.com Confidential 5 The world
7 Things ISVs Must Know About Virtualization
 7 Things ISVs Must Know About Virtualization July 2010 VIRTUALIZATION BENEFITS REPORT Table of Contents Executive Summary...1 Introduction...1 1. Applications just run!...2 2. Performance is excellent...2
7 Things ISVs Must Know About Virtualization July 2010 VIRTUALIZATION BENEFITS REPORT Table of Contents Executive Summary...1 Introduction...1 1. Applications just run!...2 2. Performance is excellent...2
Easily Managing Hybrid IT with Transformation Technology
 White Paper White Paper Managing Public Cloud Computing in the Enterprise Easily Managing Hybrid IT with Transformation Technology A Quick Start Guide 1 Table of Contents Abstract... 3 Traditional Approaches
White Paper White Paper Managing Public Cloud Computing in the Enterprise Easily Managing Hybrid IT with Transformation Technology A Quick Start Guide 1 Table of Contents Abstract... 3 Traditional Approaches
THE SECURITY LEADER S GUIDE TO SSO
 THE SECURITY LEADER S TO SSO When security leaders think of single sign-on (SSO), they usually think of user convenience and experience. But SSO also plays a critical role in delivering security for data
THE SECURITY LEADER S TO SSO When security leaders think of single sign-on (SSO), they usually think of user convenience and experience. But SSO also plays a critical role in delivering security for data
Securing Office 365 with MobileIron
 Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
The CISO s Guide to Deploying True Password-less Security. by Bojan Simic and Ed Amoroso
 The CISO s Guide to Deploying True Password-less Security by Bojan Simic and Ed Amoroso TRUST ANYONE HYPR Deployment Overview for Managers HYPR is designed to eliminate credential stuffing, phishing and
The CISO s Guide to Deploying True Password-less Security by Bojan Simic and Ed Amoroso TRUST ANYONE HYPR Deployment Overview for Managers HYPR is designed to eliminate credential stuffing, phishing and
HARNESSING THE HYBRID CLOUD TO DRIVE GREATER BUSINESS AGILITY
 HARNESSING THE HYBRID CLOUD TO DRIVE GREATER BUSINESS AGILITY WHY DIGITAL TRANSFORMATION IS DRIVING ADOPTION OF MULTI-CLOUD STRATEGIES In the era of digital business, enterprises are increasingly using
HARNESSING THE HYBRID CLOUD TO DRIVE GREATER BUSINESS AGILITY WHY DIGITAL TRANSFORMATION IS DRIVING ADOPTION OF MULTI-CLOUD STRATEGIES In the era of digital business, enterprises are increasingly using
ITU-T SG 17 Q10/17. Trust Elevation Frameworks
 ITU-T SG 17 Q10/17 Trust Elevation Frameworks Abbie Barbir, Ph.D. ITU-T SG 17 Q10 Rapporteur Martin Euchner SG 17 Advisor ITU Workshop on "Future Trust and Knowledge Infrastructure July 1 2016 Contents
ITU-T SG 17 Q10/17 Trust Elevation Frameworks Abbie Barbir, Ph.D. ITU-T SG 17 Q10 Rapporteur Martin Euchner SG 17 Advisor ITU Workshop on "Future Trust and Knowledge Infrastructure July 1 2016 Contents
FIDO Alliance: Standards-based Solutions for Simpler, Strong Authentication
 FIDO Alliance: Standards-based Solutions for Simpler, Strong Authentication Jeremy Grant Managing Director, Technology Business Strategy Venable LLP jeremy.grant@venable.com @jgrantindc Digital: The Opportunity
FIDO Alliance: Standards-based Solutions for Simpler, Strong Authentication Jeremy Grant Managing Director, Technology Business Strategy Venable LLP jeremy.grant@venable.com @jgrantindc Digital: The Opportunity
Developing Enterprise Cloud Solutions with Azure
 Developing Enterprise Cloud Solutions with Azure Java Focused 5 Day Course AUDIENCE FORMAT Developers and Software Architects Instructor-led with hands-on labs LEVEL 300 COURSE DESCRIPTION This course
Developing Enterprise Cloud Solutions with Azure Java Focused 5 Day Course AUDIENCE FORMAT Developers and Software Architects Instructor-led with hands-on labs LEVEL 300 COURSE DESCRIPTION This course
Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER
 Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER Table of Contents The Digital Transformation 3 Four Must-Haves for a Modern Virtualization Platform 3
Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER Table of Contents The Digital Transformation 3 Four Must-Haves for a Modern Virtualization Platform 3
REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: VMWARE IDENTITY MANAGER ARCHITECTURE
 REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: VMWARE IDENTITY MANAGER ARCHITECTURE Table of Contents Component Design: VMware Identity Manager Architecture Design Overview VMware Identity Manager Connector
REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: VMWARE IDENTITY MANAGER ARCHITECTURE Table of Contents Component Design: VMware Identity Manager Architecture Design Overview VMware Identity Manager Connector
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
ARCHITECTURAL OVERVIEW REVISED 6 NOVEMBER 2018
 REVISED 6 NOVEMBER 2018 Table of Contents Architectural Overview Workspace ONE Logical Architecture GUIDE 2 VMware Workspace ONE Cloud-Based Reference Architecture - Architectural Overview Architectural
REVISED 6 NOVEMBER 2018 Table of Contents Architectural Overview Workspace ONE Logical Architecture GUIDE 2 VMware Workspace ONE Cloud-Based Reference Architecture - Architectural Overview Architectural
VMWARE CLOUD FOUNDATION: INTEGRATED HYBRID CLOUD PLATFORM WHITE PAPER NOVEMBER 2017
 : INTEGRATED HYBRID CLOUD PLATFORM WHITE PAPER NOVEMBER 2017 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation 4 Deploying on Premises 6
: INTEGRATED HYBRID CLOUD PLATFORM WHITE PAPER NOVEMBER 2017 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation 4 Deploying on Premises 6
Linux Automation.
 Linux Automation Using Red Hat Enterprise Linux to extract maximum value from IT infrastructure www.redhat.com Table of contents Summary statement Page 3 Background Page 4 Creating a more efficient infrastructure:
Linux Automation Using Red Hat Enterprise Linux to extract maximum value from IT infrastructure www.redhat.com Table of contents Summary statement Page 3 Background Page 4 Creating a more efficient infrastructure:
REDUCE TCO AND IMPROVE BUSINESS AND OPERATIONAL EFFICIENCY
 SOLUTION OVERVIEW REDUCE TCO AND IMPROVE BUSINESS AND OPERATIONAL EFFICIENCY Drive Up Operational Efficiency and Drive Down TCO VMware HCI with Operations Management is the foundation for modern infrastructure,
SOLUTION OVERVIEW REDUCE TCO AND IMPROVE BUSINESS AND OPERATIONAL EFFICIENCY Drive Up Operational Efficiency and Drive Down TCO VMware HCI with Operations Management is the foundation for modern infrastructure,
Delivering Business-Critical IP Multicast Applications Securely
 Delivering Business-Critical IP Multicast Applications Securely Session Number 1 Agenda Intelligent Information Network Challenges prior to Secure Multicast Secure IP Multicast Solution Benefits Summary
Delivering Business-Critical IP Multicast Applications Securely Session Number 1 Agenda Intelligent Information Network Challenges prior to Secure Multicast Secure IP Multicast Solution Benefits Summary
10 QUESTIONS, 10 ANSWERS. Get to know VMware Cloud on AWS The Best-in-Class Hybrid Cloud Service
 10 QUESTIONS, 10 ANSWERS Get to know VMware Cloud on AWS The Best-in-Class Hybrid Cloud Service GET TO KNOW VMWARE CLOUD ON AWS: THE BEST-IN-CLASS HYBRID CLOUD SERVICE IT leaders focused on finding ways
10 QUESTIONS, 10 ANSWERS Get to know VMware Cloud on AWS The Best-in-Class Hybrid Cloud Service GET TO KNOW VMWARE CLOUD ON AWS: THE BEST-IN-CLASS HYBRID CLOUD SERVICE IT leaders focused on finding ways
THREE PATHS TO CLOUD CHOICE WITHOUT COMPLEXITY. Copyright 2013 EMC Corporation. All rights reserved.
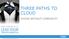 THREE PATHS TO CLOUD CHOICE WITHOUT COMPLEXITY 1 Two Fundamental Challenges 65% MAINTAIN Increase Revenue 35% INVEST Lower Operational Costs Gartner IT Key Metrics Data, December 2012 2 Cloud Transforms
THREE PATHS TO CLOUD CHOICE WITHOUT COMPLEXITY 1 Two Fundamental Challenges 65% MAINTAIN Increase Revenue 35% INVEST Lower Operational Costs Gartner IT Key Metrics Data, December 2012 2 Cloud Transforms
Modern Identity Management Patterns for Microservices and Mobile
 SESSION ID: SDS-F04 Modern Identity Management Patterns for Microservices and Mobile Mark Perry APAC CTO Ping Identity @markperryau IT S A NEW WORLD Everything s Mobile 2 IT S A NEW WORLD Agile Backend
SESSION ID: SDS-F04 Modern Identity Management Patterns for Microservices and Mobile Mark Perry APAC CTO Ping Identity @markperryau IT S A NEW WORLD Everything s Mobile 2 IT S A NEW WORLD Agile Backend
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
RCS OVERVIEW. Fábio Moraes GSMA October 2018 Future Networks Programme
 RCS OVERVIEW Fábio Moraes GSMA October 2018 Future Networks Programme RCS INDUSTRY MOMENTUM WHAT IS RCS BUSINESS MESSAGING? RCS is an upgrade to SMS on a global scale Universal Profile resolving legacy
RCS OVERVIEW Fábio Moraes GSMA October 2018 Future Networks Programme RCS INDUSTRY MOMENTUM WHAT IS RCS BUSINESS MESSAGING? RCS is an upgrade to SMS on a global scale Universal Profile resolving legacy
Kony MobileFabric. Release Notes. On-Premises. Release 6.5. Document Relevance and Accuracy
 Kony MobileFabric Release Notes On-Premises Release 6.5 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and the document version stated on
Kony MobileFabric Release Notes On-Premises Release 6.5 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and the document version stated on
BUSTED! 5 COMMON MYTHS OF MODERN INFRASTRUCTURE. These Common Misconceptions Could Be Holding You Back
 BUSTED! 5 COMMON MYTHS OF MODERN INFRASTRUCTURE These Common Misconceptions Could Be Holding You Back 2 IT Is Facing a New Set of Challenges As technology continues to evolve, IT must adjust to changing
BUSTED! 5 COMMON MYTHS OF MODERN INFRASTRUCTURE These Common Misconceptions Could Be Holding You Back 2 IT Is Facing a New Set of Challenges As technology continues to evolve, IT must adjust to changing
Fencing the Cloud. Roger Casals. Senior Director Product Management. Shared vision for the Identity: Fencing the Cloud 1
 Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
What to Look for in a Partner for Software-Defined Data Center (SDDC)
 What to Look for in a Partner for Software-Defined Data Center (SDDC) WHITE PAPER Software-defined data center (SDDC) has the potential to deliver enormous business value to organizations of any size and
What to Look for in a Partner for Software-Defined Data Center (SDDC) WHITE PAPER Software-defined data center (SDDC) has the potential to deliver enormous business value to organizations of any size and
Getting Hybrid IT Right. A Softchoice Guide to Hybrid Cloud Adoption
 Getting Hybrid IT Right A Softchoice Guide to Hybrid Cloud Adoption Your Path to an Effective Hybrid Cloud The hybrid cloud is on the radar for business and IT leaders everywhere. IDC estimates 1 that
Getting Hybrid IT Right A Softchoice Guide to Hybrid Cloud Adoption Your Path to an Effective Hybrid Cloud The hybrid cloud is on the radar for business and IT leaders everywhere. IDC estimates 1 that
THE RTOS AS THE ENGINE POWERING THE INTERNET OF THINGS
 THE RTOS AS THE ENGINE POWERING THE INTERNET OF THINGS By Bill Graham and Michael Weinstein WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Driven by the convergence of cloud technology, rapidly
THE RTOS AS THE ENGINE POWERING THE INTERNET OF THINGS By Bill Graham and Michael Weinstein WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Driven by the convergence of cloud technology, rapidly
Cloud Mobility: Meraki Wireless & EMM
 BRKEWN-2002 Cloud Mobility: Meraki Wireless & EMM Emily Sporl Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile
BRKEWN-2002 Cloud Mobility: Meraki Wireless & EMM Emily Sporl Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile
Overview. Premium Data Sheet. DigitalPersona. DigitalPersona s Composite Authentication transforms the way IT
 DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
VMWARE CLOUD FOUNDATION: THE SIMPLEST PATH TO THE HYBRID CLOUD WHITE PAPER AUGUST 2018
 VMWARE CLOUD FOUNDATION: THE SIMPLEST PATH TO THE HYBRID CLOUD WHITE PAPER AUGUST 2018 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation
VMWARE CLOUD FOUNDATION: THE SIMPLEST PATH TO THE HYBRID CLOUD WHITE PAPER AUGUST 2018 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation
VMWARE HORIZON 7. End-User Computing Today. Horizon 7: Delivering Desktops and Applications as a Service
 DATASHEET VMWARE 7 AT A GLANCE 7 delivers virtualized or hosted desktops and applications through a single platform to end users. These desktop and application services including Remote Desktop Services
DATASHEET VMWARE 7 AT A GLANCE 7 delivers virtualized or hosted desktops and applications through a single platform to end users. These desktop and application services including Remote Desktop Services
What s New in VMware vsphere 5.1 VMware vcenter Server
 What s New in VMware vsphere 5.1 VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012 Table of Contents Introduction... 3 Key Components... 3 vcenter Single Sign-On Server.... 3
What s New in VMware vsphere 5.1 VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012 Table of Contents Introduction... 3 Key Components... 3 vcenter Single Sign-On Server.... 3
HYPER-CONVERGED INFRASTRUCTURE 101: HOW TO GET STARTED. Move Your Business Forward with a Software-Defined Approach
 HYPER-CONVERGED INFRASTRUCTURE 101: HOW TO GET STARTED Move Your Business Forward with a Software-Defined Approach H Y P E R - C O N V E R G E D I N F R A S T R U C T U R E 1 0 1 : H O W T O G E T S TA
HYPER-CONVERGED INFRASTRUCTURE 101: HOW TO GET STARTED Move Your Business Forward with a Software-Defined Approach H Y P E R - C O N V E R G E D I N F R A S T R U C T U R E 1 0 1 : H O W T O G E T S TA
PULSE CONNECT SECURE APPCONNECT
 PULSE CONNECT SECURE APPCONNECT A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway Product Release 8.1 Document Revision 1.0 Published:
PULSE CONNECT SECURE APPCONNECT A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway Product Release 8.1 Document Revision 1.0 Published:
Datasheet. Only Workspaces delivers the features users want and the control that IT needs.
 Datasheet Secure SECURE Enterprise ENTERPRISE File FILE Sync, SYNC, Sharing SHARING and AND Content CONTENT Collaboration COLLABORATION BlackBerry Workspaces makes enterprises more mobile and collaborative,
Datasheet Secure SECURE Enterprise ENTERPRISE File FILE Sync, SYNC, Sharing SHARING and AND Content CONTENT Collaboration COLLABORATION BlackBerry Workspaces makes enterprises more mobile and collaborative,
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure
 Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
VMworld 2015 Track Names and Descriptions
 Software- Defined Data Center Software- Defined Data Center General VMworld 2015 Track Names and Descriptions Pioneered by VMware and recognized as groundbreaking by the industry and analysts, the VMware
Software- Defined Data Center Software- Defined Data Center General VMworld 2015 Track Names and Descriptions Pioneered by VMware and recognized as groundbreaking by the industry and analysts, the VMware
VMware Cloud Operations Management Technology Consulting Services
 VMware Cloud Operations Management Technology Consulting Services VMware Technology Consulting Services for Cloud Operations Management The biggest hurdle [that CIOs face as they move infrastructure and
VMware Cloud Operations Management Technology Consulting Services VMware Technology Consulting Services for Cloud Operations Management The biggest hurdle [that CIOs face as they move infrastructure and
Oracle Exadata Statement of Direction NOVEMBER 2017
 Oracle Exadata Statement of Direction NOVEMBER 2017 Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated
Oracle Exadata Statement of Direction NOVEMBER 2017 Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated
IBM and Juniper Networks
 IBM and Juniper Networks Transforming and simplifying your network infrastructure S O L U T I O N B R I E F Enabling strategic advantage in a changing world A less expensive energy bill, a package that
IBM and Juniper Networks Transforming and simplifying your network infrastructure S O L U T I O N B R I E F Enabling strategic advantage in a changing world A less expensive energy bill, a package that
GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS.
 GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS. Cloud computing is as much a paradigm shift in data center and IT management as it is a culmination of IT s capacity to drive business
GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS. Cloud computing is as much a paradigm shift in data center and IT management as it is a culmination of IT s capacity to drive business
Deploying VMware Workspace ONE Intelligent Hub. October 2018 VMware Workspace ONE
 Deploying VMware Workspace ONE Intelligent Hub October 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Workspace ONE Intelligent Hub October 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Convergence is accelerating the path to the New Style of Business
 Convergence is accelerating the path to the New Style of Business HP Hyper-Converged Systems Franz Weberberger Presales Consultant HP Servers Copyright 2012 Hewlett-Packard Development Company, L.P. The
Convergence is accelerating the path to the New Style of Business HP Hyper-Converged Systems Franz Weberberger Presales Consultant HP Servers Copyright 2012 Hewlett-Packard Development Company, L.P. The
905M 67% of the people who use a smartphone for work and 70% of people who use a tablet for work are choosing the devices themselves
 67% of the people who use a smartphone for work and 70% of people who use a tablet for work are choosing the devices themselves 905M tablets in use for work and home globally by 2017 Before Now 32% of
67% of the people who use a smartphone for work and 70% of people who use a tablet for work are choosing the devices themselves 905M tablets in use for work and home globally by 2017 Before Now 32% of
WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD
 WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD Imagine that you re a CISO in charge of identity and access management for a major global technology and manufacturing company. You
WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD Imagine that you re a CISO in charge of identity and access management for a major global technology and manufacturing company. You
Sentinet for Microsoft Azure SENTINET
 Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
The Modern Web Access Management Platform from on-premises to the Cloud
 The Modern Web Access Management Platform from on-premises to the Cloud Single Sign On, Access Controls, Session Management and how to use Access Management to protect applications both on premises and
The Modern Web Access Management Platform from on-premises to the Cloud Single Sign On, Access Controls, Session Management and how to use Access Management to protect applications both on premises and
Two-Factor Authentication over Mobile: Simplifying Security and Authentication
 SAP Thought Leadership Paper SAP Digital Interconnect Two-Factor Authentication over Mobile: Simplifying Security and Authentication Controlling Fraud and Validating End Users Easily and Cost-Effectively
SAP Thought Leadership Paper SAP Digital Interconnect Two-Factor Authentication over Mobile: Simplifying Security and Authentication Controlling Fraud and Validating End Users Easily and Cost-Effectively
VMWARE HORIZON CLOUD SERVICE HOSTED INFRASTRUCTURE ONBOARDING SERVICE SILVER
 DATASHEET VMWARE HORIZON CLOUD SERVICE HOSTED INFRASTRUCTURE ONBOARDING SERVICE SILVER AT A GLANCE The VMware Horizon Cloud Service Hosted Infrastructure Onboarding Service Silver provides basic assistance
DATASHEET VMWARE HORIZON CLOUD SERVICE HOSTED INFRASTRUCTURE ONBOARDING SERVICE SILVER AT A GLANCE The VMware Horizon Cloud Service Hosted Infrastructure Onboarding Service Silver provides basic assistance
EXTENDING SINGLE SIGN-ON TO AMAZON WEB SERVICES BEST PRACTICES FOR IDENTITY FEDERATION IN AWS E-BOOK
 EXTENDING SINGLE SIGN-ON TO AMAZON WEB SERVICES BEST PRACTICES FOR IDENTITY FEDERATION IN AWS 03 EXECUTIVE OVERVIEW 05 INTRODUCTION 07 MORE CLOUD DEPLOYMENTS MEANS MORE ACCESS 09 IDENTITY FEDERATION IN
EXTENDING SINGLE SIGN-ON TO AMAZON WEB SERVICES BEST PRACTICES FOR IDENTITY FEDERATION IN AWS 03 EXECUTIVE OVERVIEW 05 INTRODUCTION 07 MORE CLOUD DEPLOYMENTS MEANS MORE ACCESS 09 IDENTITY FEDERATION IN
Internet is Global. 120m. 300m 1.3bn Users. 160m. 300m. 289m
 UAF Protocol Internet is Global 120m 300m 1.3bn Users 160m 289m 300m #Users 2014 Google: 2013 Twitter: 2015 Devices without physical keyboard How Secure is Authentication? Cloud Authentication Password
UAF Protocol Internet is Global 120m 300m 1.3bn Users 160m 289m 300m #Users 2014 Google: 2013 Twitter: 2015 Devices without physical keyboard How Secure is Authentication? Cloud Authentication Password
Accelerate Your Cloud Journey
 Dubai, UAE 20th March 2013 Accelerate Your Cloud Journey James Spearman Dimension Data - Solutions Architect Cloud 2012 2011 Cisco and/or its affiliates. All rights reserved. Cisco Connect 1 Dimension
Dubai, UAE 20th March 2013 Accelerate Your Cloud Journey James Spearman Dimension Data - Solutions Architect Cloud 2012 2011 Cisco and/or its affiliates. All rights reserved. Cisco Connect 1 Dimension
Luckily, our enterprise had most of the back-end (services, middleware, business logic) already.
 2 3 4 The point here is that for real business applications, there is a connected back-end for services. The mobile part of the app is just a presentation layer that is unique for the mobile environment.
2 3 4 The point here is that for real business applications, there is a connected back-end for services. The mobile part of the app is just a presentation layer that is unique for the mobile environment.
Going cloud-native with Kubernetes and Pivotal
 Going cloud-native with Kubernetes and Pivotal A guide to Pivotal Container Service (PKS) by role Fast, low-risk enterprise-grade Kubernetes has arrived With Pivotal Container Service (PKS), organizations
Going cloud-native with Kubernetes and Pivotal A guide to Pivotal Container Service (PKS) by role Fast, low-risk enterprise-grade Kubernetes has arrived With Pivotal Container Service (PKS), organizations
The Power of Partnership
 VPN BROCHURE VPN BROCHURE / 1 Market Leading Virtualization and Cloud Computing Solutions, Award-Winning Programs, Unparalleled Value The industry is changing, the market is moving and customers are continuously
VPN BROCHURE VPN BROCHURE / 1 Market Leading Virtualization and Cloud Computing Solutions, Award-Winning Programs, Unparalleled Value The industry is changing, the market is moving and customers are continuously
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
How to Evaluate a Next Generation Mobile Platform
 How to Evaluate a Next Generation Mobile Platform appcelerator.com Introduction Enterprises know that mobility presents an unprecedented opportunity to transform businesses and build towards competitive
How to Evaluate a Next Generation Mobile Platform appcelerator.com Introduction Enterprises know that mobility presents an unprecedented opportunity to transform businesses and build towards competitive
Simplify Hybrid Cloud
 Simplify Hybrid Cloud Innovate With Cloud Agility and Economics BEST PRACTICES GUIDE Organizations Are Looking To Embrace Hybrid IT for Improved Business Agility and Lower TCO In this digital age, leaders
Simplify Hybrid Cloud Innovate With Cloud Agility and Economics BEST PRACTICES GUIDE Organizations Are Looking To Embrace Hybrid IT for Improved Business Agility and Lower TCO In this digital age, leaders
Transforming IT: From Silos To Services
 Transforming IT: From Silos To Services Chuck Hollis Global Marketing CTO EMC Corporation http://chucksblog.emc.com @chuckhollis IT is being transformed. Our world is changing fast New Technologies New
Transforming IT: From Silos To Services Chuck Hollis Global Marketing CTO EMC Corporation http://chucksblog.emc.com @chuckhollis IT is being transformed. Our world is changing fast New Technologies New
Stop sweating the password and learn to love public key cryptography. Chris Streeks Solutions Engineer, Yubico
 1 Stop sweating the password and learn to love public key cryptography Chris Streeks Solutions Engineer, Yubico Stop Sweating the Password! 2 Agenda Introduction The modern state of Phishing How to become
1 Stop sweating the password and learn to love public key cryptography Chris Streeks Solutions Engineer, Yubico Stop Sweating the Password! 2 Agenda Introduction The modern state of Phishing How to become
Liferay Security Features Overview. How Liferay Approaches Security
 Liferay Security Features Overview How Liferay Approaches Security Table of Contents Executive Summary.......................................... 1 Transport Security............................................
Liferay Security Features Overview How Liferay Approaches Security Table of Contents Executive Summary.......................................... 1 Transport Security............................................
Making hybrid IT simple with Capgemini and Microsoft Azure Stack
 Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitme
 SAAM2291BE Securing Access and Protecting Information in Office 365 with Workspace ONE Camilo Lotero Senior Technical Marketing Manager Adarsh Kesari Senior Systems Engineer #VMworld #SAAM2291BE Disclaimer
SAAM2291BE Securing Access and Protecting Information in Office 365 with Workspace ONE Camilo Lotero Senior Technical Marketing Manager Adarsh Kesari Senior Systems Engineer #VMworld #SAAM2291BE Disclaimer
AXIAD IDS CLOUD SOLUTION. Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure
 AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
Vision of the Software Defined Data Center (SDDC)
 Vision of the Software Defined Data Center (SDDC) Raj Yavatkar, VMware Fellow Vijay Ramachandran, Sr. Director, Storage Product Management Business transformation and disruption A software business that
Vision of the Software Defined Data Center (SDDC) Raj Yavatkar, VMware Fellow Vijay Ramachandran, Sr. Director, Storage Product Management Business transformation and disruption A software business that
VMware vrealize Suite and vcloud Suite
 VMware vrealize Suite and vcloud Suite Licensing, Pricing, and Packaging WHITE PAPER Table of Contents Executive Summary.... 3 vrealize Suite Licensing Overview... 3 Multiple Components under a Single
VMware vrealize Suite and vcloud Suite Licensing, Pricing, and Packaging WHITE PAPER Table of Contents Executive Summary.... 3 vrealize Suite Licensing Overview... 3 Multiple Components under a Single
OpenStack and Hadoop. Achieving near bare-metal performance for big data workloads running in a private cloud ABSTRACT
 OpenStack and Hadoop Achieving near bare-metal performance for big data workloads running in a private cloud ABSTRACT IT organizations are increasingly turning to the open source Apache Hadoop software
OpenStack and Hadoop Achieving near bare-metal performance for big data workloads running in a private cloud ABSTRACT IT organizations are increasingly turning to the open source Apache Hadoop software
How A Cloud-Based Mobile Device Lab Accelerates Time To Market And ROI
 Co-Webinar: How A Cloud-Based Mobile Device Lab Accelerates Time To Market And ROI August 2016 Speakers Guy Arieli CTO, Experitest Sai Chintala SVP & Global Head Solutions Group, Cigniti 2 AGENDA 1 2 3
Co-Webinar: How A Cloud-Based Mobile Device Lab Accelerates Time To Market And ROI August 2016 Speakers Guy Arieli CTO, Experitest Sai Chintala SVP & Global Head Solutions Group, Cigniti 2 AGENDA 1 2 3
Introduction to Big Data
 Introduction to Big Data OVERVIEW We are experiencing transformational changes in the computing arena. Data is doubling every 12 to 18 months, accelerating the pace of innovation and time-to-value. The
Introduction to Big Data OVERVIEW We are experiencing transformational changes in the computing arena. Data is doubling every 12 to 18 months, accelerating the pace of innovation and time-to-value. The
Simplify Client Virtualization
 Fact sheet Simplify Client Virtualization HPE Hyper Converged 380 and VMware Horizon Reference Architecture Ideally suited for Client Virtualization requirements, delivering architectural flexibility,
Fact sheet Simplify Client Virtualization HPE Hyper Converged 380 and VMware Horizon Reference Architecture Ideally suited for Client Virtualization requirements, delivering architectural flexibility,
Solution. Imagine... a New World of Authentication.
 A Solution Imagine... a New World of Authentication. Imagine a World Where Passwords can t be hacked People can t share credentials Users can t pretend to be someone else Where authentication is more Secure
A Solution Imagine... a New World of Authentication. Imagine a World Where Passwords can t be hacked People can t share credentials Users can t pretend to be someone else Where authentication is more Secure
SOLUTION BRIEF Enterprise WAN Agility, Simplicity and Performance with Software-Defined WAN
 S O L U T I O N O V E R V I E W SOLUTION BRIEF Enterprise WAN Agility, Simplicity and Performance with Software-Defined WAN Today s branch office users are consuming more wide area network (WAN) bandwidth
S O L U T I O N O V E R V I E W SOLUTION BRIEF Enterprise WAN Agility, Simplicity and Performance with Software-Defined WAN Today s branch office users are consuming more wide area network (WAN) bandwidth
CONFIDENTLY INTEGRATE VMWARE CLOUD ON AWS WITH INTELLIGENT OPERATIONS
 SOLUTION OVERVIEW CONFIDENTLY INTEGRATE VMWARE WITH INTELLIGENT OPERATIONS VMware Cloud TM on AWS brings VMware s enterprise class Software-Defined Data Center (SDDC) software to the AWS Cloud, with optimized
SOLUTION OVERVIEW CONFIDENTLY INTEGRATE VMWARE WITH INTELLIGENT OPERATIONS VMware Cloud TM on AWS brings VMware s enterprise class Software-Defined Data Center (SDDC) software to the AWS Cloud, with optimized
More than just being signed-in or signed-out. Parul Jain, Architect,
 More than just being signed-in or signed-out Parul Jain, Architect, Intuit @ParulJainTweety Why do we care? TRUST & SECURITY EASE OF ACCESS Can t eliminate friction? Delay it Authentication Levels to balance
More than just being signed-in or signed-out Parul Jain, Architect, Intuit @ParulJainTweety Why do we care? TRUST & SECURITY EASE OF ACCESS Can t eliminate friction? Delay it Authentication Levels to balance
SAAS: THE RDP ADVANTAGE FOR ISVS AND USERS
 SAAS: THE RDP ADVANTAGE FOR ISVS AND USERS How RDP SaaS deployment reduces costs, time to market and barriers to entry while improving security, performance and the UX Independent Software Vendors (ISVs)
SAAS: THE RDP ADVANTAGE FOR ISVS AND USERS How RDP SaaS deployment reduces costs, time to market and barriers to entry while improving security, performance and the UX Independent Software Vendors (ISVs)
BlackBerry Enterprise Identity
 Datasheet BlackBerry Enterprise Identity The Challenge: Cloud services are critical in today s enterprises, yet a reliance on the cloud comes with real and growing security risks. Enterprises want a simple,
Datasheet BlackBerry Enterprise Identity The Challenge: Cloud services are critical in today s enterprises, yet a reliance on the cloud comes with real and growing security risks. Enterprises want a simple,
SAP Forum Lausanne. Workload-optimized systems designed for speed, flexibility & unmatched scalability by HPE. June 13th, 2016
 SAP Forum Lausanne Workload-optimized systems designed for speed, flexibility & unmatched scalability by HPE June 13th, 2016 Copyright 2016 Hewlett Packard Enterprise Development LP About HPE 2 Hewlett
SAP Forum Lausanne Workload-optimized systems designed for speed, flexibility & unmatched scalability by HPE June 13th, 2016 Copyright 2016 Hewlett Packard Enterprise Development LP About HPE 2 Hewlett
GDPR Update and ENISA guidelines
 GDPR Update and ENISA guidelines 2016 [Type text] There are two topics that should be uppermost in every CISO's mind, how to address the growing demand for Unified Communications (UC) and how to ensure
GDPR Update and ENISA guidelines 2016 [Type text] There are two topics that should be uppermost in every CISO's mind, how to address the growing demand for Unified Communications (UC) and how to ensure
BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY
 SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management
 Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management June 29, 2011 1 Forward-Looking Statements This presentation
Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management June 29, 2011 1 Forward-Looking Statements This presentation
Cloud Computing Private Cloud
 Cloud Computing Private Cloud Amplifying Business Value thru IT Ivo Sladoljev, Territory Manager, Adriatic Region December, 2010. 2010 VMware Inc. All rights reserved Agenda Company Facts VMware Focus
Cloud Computing Private Cloud Amplifying Business Value thru IT Ivo Sladoljev, Territory Manager, Adriatic Region December, 2010. 2010 VMware Inc. All rights reserved Agenda Company Facts VMware Focus
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience.
 The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
Cisco HyperFlex and the F5 BIG-IP Platform Accelerate Infrastructure and Application Deployments
 OVERVIEW + Cisco and the F5 BIG-IP Platform Accelerate Infrastructure and Application Deployments KEY BENEFITS Quickly create private clouds Tested with industry-leading BIG-IP ADC platform Easily scale
OVERVIEW + Cisco and the F5 BIG-IP Platform Accelerate Infrastructure and Application Deployments KEY BENEFITS Quickly create private clouds Tested with industry-leading BIG-IP ADC platform Easily scale
FIDO & PSD2. Providing for a satisfactory customer journey. April, Copyright 2018 FIDO Alliance All Rights Reserved.
 FIDO & PSD2 Providing for a satisfactory customer journey April, 2018 Copyright 2018 FIDO Alliance All Rights Reserved. 1 Introduction When PSD2 is deployed in Europe, users will be able to take advantage
FIDO & PSD2 Providing for a satisfactory customer journey April, 2018 Copyright 2018 FIDO Alliance All Rights Reserved. 1 Introduction When PSD2 is deployed in Europe, users will be able to take advantage
2-4 April 2019 Taets Art and Event Park, Amsterdam CLICK TO KNOW MORE
 Co-Host Host 2-4 April 2019 Taets Art and Event Park, Amsterdam CLICK TO KNOW MORE Oracle Cloud Computing Strategy Han Wammes Public Sector Market Development Manager 1 Copyright 2012, Oracle and/or its
Co-Host Host 2-4 April 2019 Taets Art and Event Park, Amsterdam CLICK TO KNOW MORE Oracle Cloud Computing Strategy Han Wammes Public Sector Market Development Manager 1 Copyright 2012, Oracle and/or its
TRUSTED SUPPLY CHAIN & REMOTE PROVISIONING WITH THE TRUSTED PLATFORM MODULE
 SESSION ID: TECH-F03 TRUSTED SUPPLY CHAIN & REMOTE PROVISIONING WITH THE TRUSTED PLATFORM MODULE Tom Dodson Supply Chain Security Architect Intel Corporation/Business Client Products Monty Wiseman Security
SESSION ID: TECH-F03 TRUSTED SUPPLY CHAIN & REMOTE PROVISIONING WITH THE TRUSTED PLATFORM MODULE Tom Dodson Supply Chain Security Architect Intel Corporation/Business Client Products Monty Wiseman Security
Video Conferencing & Skype for Business: Your Need-to-Know Guide
 Video Conferencing & Skype for Business: Your Need-to-Know Guide Effective, engaging collaboration that leverages video conferencing should incorporate features like content sharing, clear participant
Video Conferencing & Skype for Business: Your Need-to-Know Guide Effective, engaging collaboration that leverages video conferencing should incorporate features like content sharing, clear participant
Single Sign-On Best Practices
 AUGUST 2018 WHITE PAPER Single Sign-On Best Practices Protecting Access in the Cloud Table of Contents Executive Summary... 3 Objectives... 3 Security Challenges... 4 Standards... 5 Conclusion... 6 Additional
AUGUST 2018 WHITE PAPER Single Sign-On Best Practices Protecting Access in the Cloud Table of Contents Executive Summary... 3 Objectives... 3 Security Challenges... 4 Standards... 5 Conclusion... 6 Additional
SIMPLIFYING THE CAR. Helix chassis. Helix chassis. Helix chassis WIND RIVER HELIX CHASSIS WIND RIVER HELIX DRIVE WIND RIVER HELIX CARSYNC
 W I N D R I V E R H E L I X C H A S S I S SIMPLIFYING THE WIND RIVER HELIX CHASSIS Helix Chassis brings together software, technologies, tools, and services to help automotive manufacturers unify, simplify,
W I N D R I V E R H E L I X C H A S S I S SIMPLIFYING THE WIND RIVER HELIX CHASSIS Helix Chassis brings together software, technologies, tools, and services to help automotive manufacturers unify, simplify,
