Gotcha! Network Analytics to augment Fraud Detection Big Data in the Food Chain: the un(der)explored goldmine?
|
|
|
- June Edwards
- 5 years ago
- Views:
Transcription
1 Gotcha! Network Analytics to augment Fraud Detection Big Data in the Food Chain: the un(der)explored goldmine? December 4th, 2018 Author: Véronique Van Vlasselaer SAS Pre-Sales Analytical Consultant
2 Introduction Fraud Analytics Using Descriptive, Predictive and Social Network Techniques: A Guide to Data Science for Fraud Detection
3 Network Analytics! Say what?! Main analytical question in fraud: Given the current network, who shall be the next one that commits fraud?
4 Network Analytics! Say what?! Traditional approach in an fraud context: Finding descriptive patterns(e.g. multivariate outliers) or predictive patterns (e.g. predictive analytics) in massive amounts of structured data
5 Network Analytics! Say what?! Traditional approach in an fraud context: Finding descriptive patterns(e.g. multivariate outliers) or predictive patterns (e.g. predictive analytics) in massive amounts of structured data Multivariate Outlier Detection Predictive Analytics
6 Network Analytics! Say what?! State-of-the-art insights grounded in social sciences: Fraud is socially contagious. - If Bart and Peter are both fraudsters, and Véronique is friends of Bart and Peter, what would you expect of Véronique s behavior? Extension of traditional detection approaches by including social interactions among fraudsters (and other people). Data issue: networked data is unstructured.
7 Network Analytics! Say what?! Credit Card Transaction Fraud
8 Network Analytics! Say what?! Social Security Fraud
9 Network Analytics! Say what?! Networked data? Where to find? Much more than data on social media channels. Call behavior data Review data Transactional data Employee data Financial data Sales data (e.g. Ebay)...
10 Network Analytics! Say what?! Networked data? Where to find? International agro-food trade network - Network of food suppliers and nations - Detection of faulty food production - Impact of food contamination - How to quickly shortcut a potential safety breach? Food supply network - Network of raw material suppliers, food processors and retail Chemical networks - Network of OTU s
11 Network Analytics! Say what?! Main analytical question in fraud: Given the current network, who shall be the next one that commits fraud? Main analytical solutions Featurization of the network Collective inference algorithms (incl. behavioral propagation)
12 Featurization
13 Network Analysis Featurization Featurizationis the process in which the unstructured network is transformed to a structured form unstructured data structured data predictive model
14 Network Analysis Featurization Featurizationis the process in which the unstructured network is transformed to a structured form FEATURIZATION unstructured data structured data predictive model
15 Sociogram: Network Analytics Network Representation Matrix representation:
16 Network featurization processbased on the first-order neighborhood or egonet of each entity - How many churners/fraudsters/adopters are connected to node (i.e., degree)? - Density of the egonet? - Number of suppliers/addresses/customers from a black list in the egonet? - Velocity of the network (time-based network analysis)? - Network Analytics Feature Engineering the n-order neighborhood - Betweenness, closeness, community detection
17 Network featurization process examples: the n-order neighborhood Network Analytics Feature Engineering Betweenness Closeness
18 Network Analysis Featurization
19 Collective Inference Algorithms
20 Collective Inference Algorithms Collective inference algorithms The label of a node is said to dependent on the labels of the neighboring nodes. Chicken-egg problem: - The label of node A depends on the label of node B, and - The label of node B depends on the label of node A. In general: iterative procedure with random ordering
21 Collective Inference Algorithms RULE: IF MORE THAN HALF OF NEIGHBORS IS FRAUDULENT, NODE IS FRAUDULENT
22 Collective Inference Algorithms Influence propagation through the network E.g. Gotcha!, based on Google s famous PageRank algorithm
23 Collective Inference Algorithms Influence propagation through the network E.g. Gotcha!, based on Google s famous PageRank algorithm
24 Conclusion: Fraud Detection A Hybrid Approach
25 Hybrid Approach for Detection HYBRID ANALYTICAL METHODS Predictive Models Fraud Network Analysis Anomaly Detection Value Rules Manual Detection Capability
26 Questions? Feedback? Comments?
Fraud Mobility: Exploitation Patterns and Insights
 WHITEPAPER Fraud Mobility: Exploitation Patterns and Insights September 2015 2 Table of Contents Introduction 3 Study Methodology 4 Once a SSN has been Compromised, it Remains at Risk 4 Victims Remain
WHITEPAPER Fraud Mobility: Exploitation Patterns and Insights September 2015 2 Table of Contents Introduction 3 Study Methodology 4 Once a SSN has been Compromised, it Remains at Risk 4 Victims Remain
Introduction to Data Mining and Data Analytics
 1/28/2016 MIST.7060 Data Analytics 1 Introduction to Data Mining and Data Analytics What Are Data Mining and Data Analytics? Data mining is the process of discovering hidden patterns in data, where Patterns
1/28/2016 MIST.7060 Data Analytics 1 Introduction to Data Mining and Data Analytics What Are Data Mining and Data Analytics? Data mining is the process of discovering hidden patterns in data, where Patterns
A Layered Approach to Fraud Mitigation. Nick White Product Manager, FIS Payments Integrated Financial Services
 A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
Detect Fraud & Financial Crime
 IBM i2 Intelligence Analysis Detect Fraud & Financial Crime Acquire Discover Action! Urs Christen Security Sales Government urs.christen@ch.ibm.com 1 IBM Security 2014 IBM Corporation Build an integrated
IBM i2 Intelligence Analysis Detect Fraud & Financial Crime Acquire Discover Action! Urs Christen Security Sales Government urs.christen@ch.ibm.com 1 IBM Security 2014 IBM Corporation Build an integrated
Nuno Pestana, WeDo Technologies
 Nuno Pestana, WeDo Technologies SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud FRAUD THE IMPACT
Nuno Pestana, WeDo Technologies SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud SUBSCRIPTION FRAUD SUBSCRIPTION FRAUD In Raid FMS REAL-TIME Subscription Fraud FRAUD THE IMPACT
Copyright 2013 EMC Corporation. All rights reserved. BIG DATA AND SECURITY JOINING FORCES
 1 BIG DATA AND SECURITY JOINING FORCES 2 Agenda Security for Big Data Big Data for Security Conclusions Structured + Unstructured Data = Big Telemetry, Location-Based, etc. Structured in Relational Databases
1 BIG DATA AND SECURITY JOINING FORCES 2 Agenda Security for Big Data Big Data for Security Conclusions Structured + Unstructured Data = Big Telemetry, Location-Based, etc. Structured in Relational Databases
ADVANCED ANALYTICS USING SAS ENTERPRISE MINER RENS FEENSTRA
 INSIGHTS@SAS: ADVANCED ANALYTICS USING SAS ENTERPRISE MINER RENS FEENSTRA AGENDA 09.00 09.15 Intro 09.15 10.30 Analytics using SAS Enterprise Guide Ellen Lokollo 10.45 12.00 Advanced Analytics using SAS
INSIGHTS@SAS: ADVANCED ANALYTICS USING SAS ENTERPRISE MINER RENS FEENSTRA AGENDA 09.00 09.15 Intro 09.15 10.30 Analytics using SAS Enterprise Guide Ellen Lokollo 10.45 12.00 Advanced Analytics using SAS
Business Data Analytics
 MTAT.03.319 Business Data Analytics Lecture 9 The slides are available under creative common license. The original owner of these slides is the University of Tartu Fraud Detection Wrongful act for financial
MTAT.03.319 Business Data Analytics Lecture 9 The slides are available under creative common license. The original owner of these slides is the University of Tartu Fraud Detection Wrongful act for financial
Lecture 27: Learning from relational data
 Lecture 27: Learning from relational data STATS 202: Data mining and analysis December 2, 2017 1 / 12 Announcements Kaggle deadline is this Thursday (Dec 7) at 4pm. If you haven t already, make a submission
Lecture 27: Learning from relational data STATS 202: Data mining and analysis December 2, 2017 1 / 12 Announcements Kaggle deadline is this Thursday (Dec 7) at 4pm. If you haven t already, make a submission
EYWA: a Distributed Graph Engine in the Huawei MIND Platform. Yinglong Xia Huawei Research America 02/09/2017
 EYWA: a Distributed Graph Engine in the Huawei MIND Platform Yinglong Xia Huawei Research America 02/09/2017 About Huawei employees countries revenue 2012 Labs regional HQ R&D centers YoY growth 2 ICT
EYWA: a Distributed Graph Engine in the Huawei MIND Platform Yinglong Xia Huawei Research America 02/09/2017 About Huawei employees countries revenue 2012 Labs regional HQ R&D centers YoY growth 2 ICT
Identity Theft Prevention Program. Effective beginning August 1, 2009
 Identity Theft Prevention Program Effective beginning August 1, 2009 I. PROGRAM ADOPTION Christian Brothers University developed this Identity Theft Prevention Program pursuant to the Federal Trade Commission's
Identity Theft Prevention Program Effective beginning August 1, 2009 I. PROGRAM ADOPTION Christian Brothers University developed this Identity Theft Prevention Program pursuant to the Federal Trade Commission's
Data Mining. Jeff M. Phillips. January 7, 2019 CS 5140 / CS 6140
 Data Mining CS 5140 / CS 6140 Jeff M. Phillips January 7, 2019 What is Data Mining? What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational
Data Mining CS 5140 / CS 6140 Jeff M. Phillips January 7, 2019 What is Data Mining? What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational
Last updated 31 March 2016 This document is publically available at
 PRIVACY POLICY Last updated 31 March 2016 This document is publically available at http://www.conexusfinancial.com.au/privacy 1. INTRODUCTION This Privacy Policy sets out our commitment to protecting the
PRIVACY POLICY Last updated 31 March 2016 This document is publically available at http://www.conexusfinancial.com.au/privacy 1. INTRODUCTION This Privacy Policy sets out our commitment to protecting the
Input to ORMS TC Definitions and reference model proposals, Use cases. Daniela Bourges Waldegg
 Input to ORMS TC Definitions and reference model proposals, Use cases Daniela Bourges Waldegg dbw@zurich.ibm.com Reputation definitions Reputation definitions Reputation is a collective evaluation of an
Input to ORMS TC Definitions and reference model proposals, Use cases Daniela Bourges Waldegg dbw@zurich.ibm.com Reputation definitions Reputation definitions Reputation is a collective evaluation of an
CSE 316: SOCIAL NETWORK ANALYSIS INTRODUCTION. Fall 2017 Marion Neumann
 CSE 316: SOCIAL NETWORK ANALYSIS Fall 2017 Marion Neumann INTRODUCTION Contents in these slides may be subject to copyright. Some materials are adopted from: http://www.cs.cornell.edu/home /kleinber/ networks-book,
CSE 316: SOCIAL NETWORK ANALYSIS Fall 2017 Marion Neumann INTRODUCTION Contents in these slides may be subject to copyright. Some materials are adopted from: http://www.cs.cornell.edu/home /kleinber/ networks-book,
A Smart New Cofely Dutch Data Summit Roland Schneiders
 A Smart New Cofely Dutch Data Summit 2014 Roland Schneiders 16 december 2014 2 How the world has changed: Stock Exchange 16 december 2014 3 A Smart New Cofely - Dutch Data Summit 2014 Big Data @ Stock
A Smart New Cofely Dutch Data Summit 2014 Roland Schneiders 16 december 2014 2 How the world has changed: Stock Exchange 16 december 2014 3 A Smart New Cofely - Dutch Data Summit 2014 Big Data @ Stock
Analytical model A structure and process for analyzing a dataset. For example, a decision tree is a model for the classification of a dataset.
 Glossary of data mining terms: Accuracy Accuracy is an important factor in assessing the success of data mining. When applied to data, accuracy refers to the rate of correct values in the data. When applied
Glossary of data mining terms: Accuracy Accuracy is an important factor in assessing the success of data mining. When applied to data, accuracy refers to the rate of correct values in the data. When applied
How Real Time Are Your Analytics?
 How Real Time Are Your Analytics? Min Xiao Solutions Architect, VoltDB Table of Contents Your Big Data Analytics.... 1 Turning Analytics into Real Time Decisions....2 Bridging the Gap...3 How VoltDB Helps....4
How Real Time Are Your Analytics? Min Xiao Solutions Architect, VoltDB Table of Contents Your Big Data Analytics.... 1 Turning Analytics into Real Time Decisions....2 Bridging the Gap...3 How VoltDB Helps....4
Big Data - Some Words BIG DATA 8/31/2017. Introduction
 BIG DATA Introduction Big Data - Some Words Connectivity Social Medias Share information Interactivity People Business Data Data mining Text mining Business Intelligence 1 What is Big Data Big Data means
BIG DATA Introduction Big Data - Some Words Connectivity Social Medias Share information Interactivity People Business Data Data mining Text mining Business Intelligence 1 What is Big Data Big Data means
From Data Challenge to Data Opportunity
 From Data Challenge to Data Opportunity Jason Hunter, CTO Asia-Pacific, MarkLogic A Big Data Challenge: Pushing the Limits of What's Possible The Art of the Possible Multiple Government Agencies Data Hub
From Data Challenge to Data Opportunity Jason Hunter, CTO Asia-Pacific, MarkLogic A Big Data Challenge: Pushing the Limits of What's Possible The Art of the Possible Multiple Government Agencies Data Hub
DSCI 575: Advanced Machine Learning. PageRank Winter 2018
 DSCI 575: Advanced Machine Learning PageRank Winter 2018 http://ilpubs.stanford.edu:8090/422/1/1999-66.pdf Web Search before Google Unsupervised Graph-Based Ranking We want to rank importance based on
DSCI 575: Advanced Machine Learning PageRank Winter 2018 http://ilpubs.stanford.edu:8090/422/1/1999-66.pdf Web Search before Google Unsupervised Graph-Based Ranking We want to rank importance based on
[Utility Name] Identity Theft Prevention Program
![[Utility Name] Identity Theft Prevention Program [Utility Name] Identity Theft Prevention Program](/thumbs/77/75712648.jpg) [Utility Name] Identity Theft Prevention Program Effective beginning, 2008 Minnesota Municipal Utilities Association Sample Red Flag policy I. PROGRAM ADOPTION The [Utility Name] ("Utility") developed
[Utility Name] Identity Theft Prevention Program Effective beginning, 2008 Minnesota Municipal Utilities Association Sample Red Flag policy I. PROGRAM ADOPTION The [Utility Name] ("Utility") developed
Credit Union Cyber Crisis: Gaining Awareness and Combatting Cyber Threats Without Breaking the Bank
 Credit Union Cyber Crisis: Gaining Awareness and Combatting Cyber Threats Without Breaking the Bank Introduction The 6,331 credit unions in the United States face a unique challenge when it comes to cybersecurity.
Credit Union Cyber Crisis: Gaining Awareness and Combatting Cyber Threats Without Breaking the Bank Introduction The 6,331 credit unions in the United States face a unique challenge when it comes to cybersecurity.
E X E C U T I V E B R I E F
 Create a Better Way to Work: OpenText Suite 16 & OpenText Cloud 16 Over the next five years, executives expect digital disruption to displace four out of 10 incumbents or 40 percent of established market
Create a Better Way to Work: OpenText Suite 16 & OpenText Cloud 16 Over the next five years, executives expect digital disruption to displace four out of 10 incumbents or 40 percent of established market
Data Mining. Jeff M. Phillips. January 9, 2013
 Data Mining Jeff M. Phillips January 9, 2013 Data Mining What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational statistics? Data
Data Mining Jeff M. Phillips January 9, 2013 Data Mining What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational statistics? Data
Sales Intelligence The Secret Weapon for 2014
 Sales Intelligence The Secret Weapon for 2014 Jeff Ramminger Senior Vice President, Field Marketing & Client Consulting Justin Hoskins Vice President, Product Architecture & Innovation #TTGTSummit www.techtarget.com/formarketers
Sales Intelligence The Secret Weapon for 2014 Jeff Ramminger Senior Vice President, Field Marketing & Client Consulting Justin Hoskins Vice President, Product Architecture & Innovation #TTGTSummit www.techtarget.com/formarketers
MATH36032 Problem Solving by Computer. Data Science
 MATH36032 Problem Solving by Computer Data Science NO. of jobs on jobsite 1 10000 NO. of Jobs 8000 6000 4000 2000 MATLAB Data Data Science 0 Jan 2016 Jul 2016 Jan 2017 1 http://www.jobsite.co.uk/ What
MATH36032 Problem Solving by Computer Data Science NO. of jobs on jobsite 1 10000 NO. of Jobs 8000 6000 4000 2000 MATLAB Data Data Science 0 Jan 2016 Jul 2016 Jan 2017 1 http://www.jobsite.co.uk/ What
Understanding the SAP HANA Difference. Amit Satoor, SAP Data Management
 Understanding the SAP HANA Difference Amit Satoor, SAP Data Management Webinar Logistics Got Flash? http://get.adobe.com/flashplayer to download. The future holds many transformational opportunities Capitalize
Understanding the SAP HANA Difference Amit Satoor, SAP Data Management Webinar Logistics Got Flash? http://get.adobe.com/flashplayer to download. The future holds many transformational opportunities Capitalize
Chapter 6. Foundations of Business Intelligence: Databases and Information Management VIDEO CASES
 Chapter 6 Foundations of Business Intelligence: Databases and Information Management VIDEO CASES Case 1a: City of Dubuque Uses Cloud Computing and Sensors to Build a Smarter, Sustainable City Case 1b:
Chapter 6 Foundations of Business Intelligence: Databases and Information Management VIDEO CASES Case 1a: City of Dubuque Uses Cloud Computing and Sensors to Build a Smarter, Sustainable City Case 1b:
2017 INVESTMENT MANAGEMENT CONFERENCE NEW YORK Big Data: Risks and Rewards for Investment Management
 2017 INVESTMENT MANAGEMENT CONFERENCE NEW YORK Big Data: Risks and Rewards for Investment Management Derek N. Steingarten, New York Julia B. Jacobson, Boston Barbara Bridges, VP of Legal & Compliance,
2017 INVESTMENT MANAGEMENT CONFERENCE NEW YORK Big Data: Risks and Rewards for Investment Management Derek N. Steingarten, New York Julia B. Jacobson, Boston Barbara Bridges, VP of Legal & Compliance,
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
Holiday Season Cyberattacks on Pace to Increase by Nearly 60%
 Holiday Season Cyberattacks on Pace to Increase by Nearly 60% NOVEMBER 2018 1 Tis the season for cyberattacks. According to the Carbon Black Threat Analysis Unit (TAU), organizations should expect to see
Holiday Season Cyberattacks on Pace to Increase by Nearly 60% NOVEMBER 2018 1 Tis the season for cyberattacks. According to the Carbon Black Threat Analysis Unit (TAU), organizations should expect to see
Do Social Networks Improve e-commerce? A Study on Social Marketplaces
 Do Social Networks Improve e-commerce? A Study on Social Marketplaces 1 GAYATRI SWAMYNATHAN, CHRISTO WILSON, BRYCE BOE, KEVIN ALMEROTH AND BEN Y. ZHAO UC SANTA BARBARA Leveraging Online Social Networks
Do Social Networks Improve e-commerce? A Study on Social Marketplaces 1 GAYATRI SWAMYNATHAN, CHRISTO WILSON, BRYCE BOE, KEVIN ALMEROTH AND BEN Y. ZHAO UC SANTA BARBARA Leveraging Online Social Networks
Applying SnapVX to Real-World Problems
 Applying SnapVX to Real-World Problems David Hallac Stanford University Goal Other resources (MLOSS Paper, website, documentation,...) describe the math/software side of SnapVX This presentation is meant
Applying SnapVX to Real-World Problems David Hallac Stanford University Goal Other resources (MLOSS Paper, website, documentation,...) describe the math/software side of SnapVX This presentation is meant
Graph Data Management Systems in New Applications Domains. Mikko Halin
 Graph Data Management Systems in New Applications Domains Mikko Halin Introduction Presentation is based on two papers Graph Data Management Systems for New Application Domains - Philippe Cudré-Mauroux,
Graph Data Management Systems in New Applications Domains Mikko Halin Introduction Presentation is based on two papers Graph Data Management Systems for New Application Domains - Philippe Cudré-Mauroux,
Evaluating Cloud Databases for ecommerce Applications. What you need to grow your ecommerce business
 Evaluating Cloud Databases for ecommerce Applications What you need to grow your ecommerce business EXECUTIVE SUMMARY ecommerce is the future of not just retail but myriad industries from telecommunications
Evaluating Cloud Databases for ecommerce Applications What you need to grow your ecommerce business EXECUTIVE SUMMARY ecommerce is the future of not just retail but myriad industries from telecommunications
Data Mining. Jeff M. Phillips. January 12, 2015 CS 5140 / CS 6140
 Data Mining CS 5140 / CS 6140 Jeff M. Phillips January 12, 2015 Data Mining What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational
Data Mining CS 5140 / CS 6140 Jeff M. Phillips January 12, 2015 Data Mining What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational
Deep Learning & Accelerating the NLP Journey in the Unstructured World
 Deep Learning & Accelerating the NLP Journey in the Unstructured World Jenny Chong, Global Head of ecommunications Surveillance Shahzad Chohan, Global Head of Machine Intelligence and Accelerated Computing
Deep Learning & Accelerating the NLP Journey in the Unstructured World Jenny Chong, Global Head of ecommunications Surveillance Shahzad Chohan, Global Head of Machine Intelligence and Accelerated Computing
Advanced Threat Intelligence to Detect Advanced Malware Jim Deerman
 Advanced Threat Intelligence to Detect Advanced Malware Jim Deerman jdeerman@isc8.com Safe Harbor Statement All statements included or incorporated by reference in these slides, other than statements or
Advanced Threat Intelligence to Detect Advanced Malware Jim Deerman jdeerman@isc8.com Safe Harbor Statement All statements included or incorporated by reference in these slides, other than statements or
Fall 2017 ECEN Special Topics in Data Mining and Analysis
 Fall 2017 ECEN 689-600 Special Topics in Data Mining and Analysis Nick Duffield Department of Electrical & Computer Engineering Teas A&M University Organization Organization Instructor: Nick Duffield,
Fall 2017 ECEN 689-600 Special Topics in Data Mining and Analysis Nick Duffield Department of Electrical & Computer Engineering Teas A&M University Organization Organization Instructor: Nick Duffield,
THE TERMS OF THIS PRIVACY & DATA USE POLICY ( POLICY ) ARE LEGALLY BINDING.
 Privacy Policy THE TERMS OF THIS PRIVACY & DATA USE POLICY ( POLICY ) ARE LEGALLY BINDING. IF YOU USE OUR SERVICE (AS DEFINED BELOW), YOU AGREE TO BE BOUND TO ALL OF THE TERMS AND CONDITIONS OF THIS POLICY.
Privacy Policy THE TERMS OF THIS PRIVACY & DATA USE POLICY ( POLICY ) ARE LEGALLY BINDING. IF YOU USE OUR SERVICE (AS DEFINED BELOW), YOU AGREE TO BE BOUND TO ALL OF THE TERMS AND CONDITIONS OF THIS POLICY.
Data Mining. Jeff M. Phillips. January 8, 2014
 Data Mining Jeff M. Phillips January 8, 2014 Data Mining What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational statistics? Data
Data Mining Jeff M. Phillips January 8, 2014 Data Mining What is Data Mining? Finding structure in data? Machine learning on large data? Unsupervised learning? Large scale computational statistics? Data
STOCKTON UNIVERSITY PROCEDURE DEFINITIONS
 STOCKTON UNIVERSITY PROCEDURE Identity Theft Prevention Program Procedure Administrator: Director of Risk Management and Environmental/Health/Safety Authority: Fair and Accurate Credit Transactions Act
STOCKTON UNIVERSITY PROCEDURE Identity Theft Prevention Program Procedure Administrator: Director of Risk Management and Environmental/Health/Safety Authority: Fair and Accurate Credit Transactions Act
Big Data Analytics: What is Big Data? Stony Brook University CSE545, Fall 2016 the inaugural edition
 Big Data Analytics: What is Big Data? Stony Brook University CSE545, Fall 2016 the inaugural edition What s the BIG deal?! 2011 2011 2008 2010 2012 What s the BIG deal?! (Gartner Hype Cycle) What s the
Big Data Analytics: What is Big Data? Stony Brook University CSE545, Fall 2016 the inaugural edition What s the BIG deal?! 2011 2011 2008 2010 2012 What s the BIG deal?! (Gartner Hype Cycle) What s the
Data Mining Concepts & Tasks
 Data Mining Concepts & Tasks Duen Horng (Polo) Chau Georgia Tech CSE6242 / CX4242 Sept 9, 2014 Partly based on materials by Professors Guy Lebanon, Jeffrey Heer, John Stasko, Christos Faloutsos Last Time
Data Mining Concepts & Tasks Duen Horng (Polo) Chau Georgia Tech CSE6242 / CX4242 Sept 9, 2014 Partly based on materials by Professors Guy Lebanon, Jeffrey Heer, John Stasko, Christos Faloutsos Last Time
International Journal of Data Mining & Knowledge Management Process (IJDKP) Vol.7, No.3, May Dr.Zakea Il-Agure and Mr.Hicham Noureddine Itani
 LINK MINING PROCESS Dr.Zakea Il-Agure and Mr.Hicham Noureddine Itani Higher Colleges of Technology, United Arab Emirates ABSTRACT Many data mining and knowledge discovery methodologies and process models
LINK MINING PROCESS Dr.Zakea Il-Agure and Mr.Hicham Noureddine Itani Higher Colleges of Technology, United Arab Emirates ABSTRACT Many data mining and knowledge discovery methodologies and process models
Maximise your return in search. Mark Lilley
 Maximise your return in search Mark Lilley 19.10.2017 Hello Mark Lilley Co- Founder & Director Groundswell groundswellgrowth.com Head of Ecommerce Chain Reaction Cycles 5 years Who are Groundswell? Ecommerce
Maximise your return in search Mark Lilley 19.10.2017 Hello Mark Lilley Co- Founder & Director Groundswell groundswellgrowth.com Head of Ecommerce Chain Reaction Cycles 5 years Who are Groundswell? Ecommerce
IMAGE ACQUISTION AND PROCESSING FOR FINANCIAL ANALYSIS
 Technical Disclosure Commons Defensive Publications Series August 24, 2016 IMAGE ACQUISTION AND PROCESSING FOR FINANCIAL ANALYSIS Matthew Wood Patrick Dunagan John Clark Kristina Bohl Follow this and additional
Technical Disclosure Commons Defensive Publications Series August 24, 2016 IMAGE ACQUISTION AND PROCESSING FOR FINANCIAL ANALYSIS Matthew Wood Patrick Dunagan John Clark Kristina Bohl Follow this and additional
Data Mining. Introduction. Hamid Beigy. Sharif University of Technology. Fall 1395
 Data Mining Introduction Hamid Beigy Sharif University of Technology Fall 1395 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1395 1 / 21 Table of contents 1 Introduction 2 Data mining
Data Mining Introduction Hamid Beigy Sharif University of Technology Fall 1395 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1395 1 / 21 Table of contents 1 Introduction 2 Data mining
ma recycle GDPR Privacy Policy .com Rely and Comply... Policy Date: 24 May 2018
 ma recycle.com Rely and Comply... GDPR Privacy Policy Policy Date: 24 May 2018 Max Recycle Hawthorne House Blackthorn Way Sedgeletch Industrial Estate Fencehouses Tyne & Wear DH4 6JN T: 0845 026 0026 F:
ma recycle.com Rely and Comply... GDPR Privacy Policy Policy Date: 24 May 2018 Max Recycle Hawthorne House Blackthorn Way Sedgeletch Industrial Estate Fencehouses Tyne & Wear DH4 6JN T: 0845 026 0026 F:
Chapter 9: Outlier Analysis
 Chapter 9: Outlier Analysis Jilles Vreeken 8 Dec 2015 IRDM Chapter 9, overview 1. Basics & Motivation 2. Extreme Value Analysis 3. Probabilistic Methods 4. Cluster-based Methods 5. Distance-based Methods
Chapter 9: Outlier Analysis Jilles Vreeken 8 Dec 2015 IRDM Chapter 9, overview 1. Basics & Motivation 2. Extreme Value Analysis 3. Probabilistic Methods 4. Cluster-based Methods 5. Distance-based Methods
Know your neighbours: Machine Learning on Graphs
 Know your neighbours: Machine Learning on Graphs Andrew Docherty Senior Research Engineer andrew.docherty@data61.csiro.au www.data61.csiro.au 2 Graphs are Everywhere Online Social Networks Transportation
Know your neighbours: Machine Learning on Graphs Andrew Docherty Senior Research Engineer andrew.docherty@data61.csiro.au www.data61.csiro.au 2 Graphs are Everywhere Online Social Networks Transportation
Mining Web Data. Lijun Zhang
 Mining Web Data Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Web Crawling and Resource Discovery Search Engine Indexing and Query Processing Ranking Algorithms Recommender Systems
Mining Web Data Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Web Crawling and Resource Discovery Search Engine Indexing and Query Processing Ranking Algorithms Recommender Systems
Graphs III. CSE 6242 A / CS 4803 DVA Feb 26, Duen Horng (Polo) Chau Georgia Tech. (Interactive) Applications
 CSE 6242 A / CS 4803 DVA Feb 26, 2013 Graphs III (Interactive) Applications Duen Horng (Polo) Chau Georgia Tech Partly based on materials by Professors Guy Lebanon, Jeffrey Heer, John Stasko, Christos
CSE 6242 A / CS 4803 DVA Feb 26, 2013 Graphs III (Interactive) Applications Duen Horng (Polo) Chau Georgia Tech Partly based on materials by Professors Guy Lebanon, Jeffrey Heer, John Stasko, Christos
Unit 10 Databases. Computer Concepts Unit Contents. 10 Operational and Analytical Databases. 10 Section A: Database Basics
 Unit 10 Databases Computer Concepts 2016 ENHANCED EDITION 10 Unit Contents Section A: Database Basics Section B: Database Tools Section C: Database Design Section D: SQL Section E: Big Data Unit 10: Databases
Unit 10 Databases Computer Concepts 2016 ENHANCED EDITION 10 Unit Contents Section A: Database Basics Section B: Database Tools Section C: Database Design Section D: SQL Section E: Big Data Unit 10: Databases
Learn SEO Copywriting
 This is video 1.1 in the online course: Learn SEO Copywriting Module 1: An introduction to SEO copywriting What we ll cover in this session What is SEO? What is SEO copywriting? How does Google work Factors
This is video 1.1 in the online course: Learn SEO Copywriting Module 1: An introduction to SEO copywriting What we ll cover in this session What is SEO? What is SEO copywriting? How does Google work Factors
Data Science Tutorial
 Eliezer Kanal Technical Manager, CERT Daniel DeCapria Data Scientist, ETC Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 2017 SEI SEI Data Science in in Cybersecurity Symposium
Eliezer Kanal Technical Manager, CERT Daniel DeCapria Data Scientist, ETC Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 2017 SEI SEI Data Science in in Cybersecurity Symposium
Whitepaper on AuthShield Two Factor Authentication with SAP
 Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
The French WEEE system. Cécile des Abbayes Research Manager Eco-systèmes
 The French WEEE system Research Manager Eco-systèmes I. The French WEEE system 1. Focus on two specific strengths of the organisation Collaboration between collective schemes and local authorities The
The French WEEE system Research Manager Eco-systèmes I. The French WEEE system 1. Focus on two specific strengths of the organisation Collaboration between collective schemes and local authorities The
Prevention of Identity Theft in Student Financial Transactions AP 5800
 Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name.
 security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name. Security for Your Business Mitigating risk is a daily reality for business owners, but you don t have
security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name. Security for Your Business Mitigating risk is a daily reality for business owners, but you don t have
Data Mining. Introduction. Hamid Beigy. Sharif University of Technology. Fall 1394
 Data Mining Introduction Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1394 1 / 20 Table of contents 1 Introduction 2 Data mining
Data Mining Introduction Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Data Mining Fall 1394 1 / 20 Table of contents 1 Introduction 2 Data mining
Executive brief Create a Better Way to Work: OpenText Release 16
 Executive brief Create a Better Way to Work: OpenText Release 16 Over the next five years, executives expect digital disruption to displace four out of 10 incumbents or 40 percent of established market
Executive brief Create a Better Way to Work: OpenText Release 16 Over the next five years, executives expect digital disruption to displace four out of 10 incumbents or 40 percent of established market
When Graph Meets Big Data: Opportunities and Challenges
 High Performance Graph Data Management and Processing (HPGDM 2016) When Graph Meets Big Data: Opportunities and Challenges Yinglong Xia Huawei Research America 11/13/2016 The International Conference for
High Performance Graph Data Management and Processing (HPGDM 2016) When Graph Meets Big Data: Opportunities and Challenges Yinglong Xia Huawei Research America 11/13/2016 The International Conference for
Seattle University Identity Theft Prevention Program. Purpose. Definitions
 Seattle University Identity Theft Prevention Program Purpose The purpose of the program is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection
Seattle University Identity Theft Prevention Program Purpose The purpose of the program is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection
Unsupervised Learning Partitioning Methods
 Unsupervised Learning Partitioning Methods Road Map 1. Basic Concepts 2. K-Means 3. K-Medoids 4. CLARA & CLARANS Cluster Analysis Unsupervised learning (i.e., Class label is unknown) Group data to form
Unsupervised Learning Partitioning Methods Road Map 1. Basic Concepts 2. K-Means 3. K-Medoids 4. CLARA & CLARANS Cluster Analysis Unsupervised learning (i.e., Class label is unknown) Group data to form
How technology changed fraud investigations. Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011
 How technology changed fraud investigations Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011 The Changing Cyberfraud Landscape Underground Economy Malware Authors Organized
How technology changed fraud investigations Jean-François Legault Senior Manager Analytic & Forensic Technology June 13, 2011 The Changing Cyberfraud Landscape Underground Economy Malware Authors Organized
Answer: A Reference:http://www.vertica.com/wpcontent/uploads/2012/05/MicroStrategy_Vertica_12.p df(page 1, first para)
 1 HP - HP2-N44 Selling HP Vertical Big Data Solutions QUESTION: 1 When is Vertica a better choice than SAP HANA? A. The customer wants a closed ecosystem for BI and analytics, and is unconcerned with support
1 HP - HP2-N44 Selling HP Vertical Big Data Solutions QUESTION: 1 When is Vertica a better choice than SAP HANA? A. The customer wants a closed ecosystem for BI and analytics, and is unconcerned with support
Super-convergence for Real Time Analytics at the Edge Flashmatrix 1000 Series. storage.toshiba.com/flashmatrix/
 Super-convergence for Real Time Analytics at the Edge Flashmatrix 1000 Series About the Flashmatrix 1000 Series Edge computing represents the next significant wave in computing. The IoT is ushering in
Super-convergence for Real Time Analytics at the Edge Flashmatrix 1000 Series About the Flashmatrix 1000 Series Edge computing represents the next significant wave in computing. The IoT is ushering in
Introduction to NoSQL by William McKnight
 Introduction to NoSQL by William McKnight All rights reserved. Reproduction in whole or part prohibited except by written permission. Product and company names mentioned herein may be trademarks of their
Introduction to NoSQL by William McKnight All rights reserved. Reproduction in whole or part prohibited except by written permission. Product and company names mentioned herein may be trademarks of their
Oliver Engels & Tillmann Eitelberg. Big Data! Big Quality?
 Oliver Engels & Tillmann Eitelberg Big Data! Big Quality? Like to visit Germany? PASS Camp 2017 Main Camp 5.12 7.12.2017 (4.12 Kick Off Evening) Lufthansa Training & Conference Center, Seeheim SQL Konferenz
Oliver Engels & Tillmann Eitelberg Big Data! Big Quality? Like to visit Germany? PASS Camp 2017 Main Camp 5.12 7.12.2017 (4.12 Kick Off Evening) Lufthansa Training & Conference Center, Seeheim SQL Konferenz
Managing Data at Scale: Microservices and Events. Randy linkedin.com/in/randyshoup
 Managing Data at Scale: Microservices and Events Randy Shoup @randyshoup linkedin.com/in/randyshoup Background VP Engineering at Stitch Fix o Combining Art and Science to revolutionize apparel retail Consulting
Managing Data at Scale: Microservices and Events Randy Shoup @randyshoup linkedin.com/in/randyshoup Background VP Engineering at Stitch Fix o Combining Art and Science to revolutionize apparel retail Consulting
Session 7: Oracle R Enterprise OAAgraph Package
 Session 7: Oracle R Enterprise 1.5.1 OAAgraph Package Oracle Spatial and Graph PGX Graph Algorithms Oracle R Technologies Mark Hornick Director, Oracle Advanced Analytics and Machine Learning July 2017
Session 7: Oracle R Enterprise 1.5.1 OAAgraph Package Oracle Spatial and Graph PGX Graph Algorithms Oracle R Technologies Mark Hornick Director, Oracle Advanced Analytics and Machine Learning July 2017
Intel & Cisco Relationship. Nikos Botinis Regional Sales Manager Cisco Systems
 Intel & Cisco Relationship Nikos Botinis Regional Sales Manager Cisco Systems 1 Long History of Collaboration Unified Computing System UCS E Series Router Module Routers, Switches, Security Appliances,
Intel & Cisco Relationship Nikos Botinis Regional Sales Manager Cisco Systems 1 Long History of Collaboration Unified Computing System UCS E Series Router Module Routers, Switches, Security Appliances,
Introduction Types of Social Network Analysis Social Networks in the Online Age Data Mining for Social Network Analysis Applications Conclusion
 Introduction Types of Social Network Analysis Social Networks in the Online Age Data Mining for Social Network Analysis Applications Conclusion References Social Network Social Network Analysis Sociocentric
Introduction Types of Social Network Analysis Social Networks in the Online Age Data Mining for Social Network Analysis Applications Conclusion References Social Network Social Network Analysis Sociocentric
Keep the Door Open for Users and Closed to Hackers
 Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Webinar Series TMIP VISION
 Webinar Series TMIP VISION TMIP provides technical support and promotes knowledge and information exchange in the transportation planning and modeling community. Today s Goals To Consider: Parallel Processing
Webinar Series TMIP VISION TMIP provides technical support and promotes knowledge and information exchange in the transportation planning and modeling community. Today s Goals To Consider: Parallel Processing
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
STREAMLINED CERTIFICATION PATHS
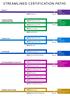 STREAMLINED CERTIFICATION PATHS MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2016 Cloud Platform & Infrastructure Linux on Azure Cloud Platform PRODUCTIVITY Server 2016 Productivity Office
STREAMLINED CERTIFICATION PATHS MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2016 Cloud Platform & Infrastructure Linux on Azure Cloud Platform PRODUCTIVITY Server 2016 Productivity Office
Big data. Professor Dan Ariely, Duke University.
 Big data BIG DATA is like teenage sex: everyone talks about it, nobody really knows how to do it, everyone thinks everyone else is doing it, so everyone claims they are doing it... Professor Dan Ariely,
Big data BIG DATA is like teenage sex: everyone talks about it, nobody really knows how to do it, everyone thinks everyone else is doing it, so everyone claims they are doing it... Professor Dan Ariely,
Fusion de données: l'union fait la force
 Fusion de données: l'union fait la force Philippe Cudré-Mauroux exascale Infolab, University of Fribourg Switzerland Swiss Data Forum November 28, 2017 On the Menu Today 1. XI, Big Data, Data Integration
Fusion de données: l'union fait la force Philippe Cudré-Mauroux exascale Infolab, University of Fribourg Switzerland Swiss Data Forum November 28, 2017 On the Menu Today 1. XI, Big Data, Data Integration
Rockwell Automation ODVA Annual Meeting
 Rockwell Automation ODVA Annual Meeting Copyright 2011 Rockwell Automation, Inc. All rights reserved. Topics Industrial Energy Management: Industrial GreenPrint Business Drivers Enabling Solutions Copyright
Rockwell Automation ODVA Annual Meeting Copyright 2011 Rockwell Automation, Inc. All rights reserved. Topics Industrial Energy Management: Industrial GreenPrint Business Drivers Enabling Solutions Copyright
WHAT IS GRAPH ANALYTICS? AND WHEN DO YOU USE IT?
 INNOVATION PLATFORM WHITE PAPER 1 Technica s Independent Research and Development (IR&D) team is focused on engineering innovative Big Data offerings that make use of Graphics Process Units (GPUs). The
INNOVATION PLATFORM WHITE PAPER 1 Technica s Independent Research and Development (IR&D) team is focused on engineering innovative Big Data offerings that make use of Graphics Process Units (GPUs). The
Mining Web Data. Lijun Zhang
 Mining Web Data Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Web Crawling and Resource Discovery Search Engine Indexing and Query Processing Ranking Algorithms Recommender Systems
Mining Web Data Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Web Crawling and Resource Discovery Search Engine Indexing and Query Processing Ranking Algorithms Recommender Systems
Acceptance. Changes to this Policy
 Privacy Policy Last Updated: January 3, 2019 Thank you for visiting Etalia Foods! We work hard to provide you unforgettable and naturally gluten-free pizzas. We know that by choosing Etalia Foods for your
Privacy Policy Last Updated: January 3, 2019 Thank you for visiting Etalia Foods! We work hard to provide you unforgettable and naturally gluten-free pizzas. We know that by choosing Etalia Foods for your
REDUCING THE RISK OF CARD NOT PRESENT FRAUD
 www.globalpaymentsinc.co.uk REDUCING THE RISK OF CARD NOT PRESENT FRAUD 02 03 REDUCING THE RISK OF CARD NOT PRESENT FRAUD INTRODUCTION Many businesses accept Card Not Present (CNP) transactions on a daily
www.globalpaymentsinc.co.uk REDUCING THE RISK OF CARD NOT PRESENT FRAUD 02 03 REDUCING THE RISK OF CARD NOT PRESENT FRAUD INTRODUCTION Many businesses accept Card Not Present (CNP) transactions on a daily
2010 Web Analytics Progress and Plans in BtoB Organizations: Survey Report
 2010 Web Analytics Progress and Plans in BtoB Organizations: Survey Report page 1 Web Analytics Association 2010 Web Analytics Progress and Plans in BtoB Organizations: Survey Report Prepared by the Web
2010 Web Analytics Progress and Plans in BtoB Organizations: Survey Report page 1 Web Analytics Association 2010 Web Analytics Progress and Plans in BtoB Organizations: Survey Report Prepared by the Web
User-to-Data-Center Access Control Using TrustSec Design Guide
 CISCO VALIDATED DESIGN User-to-Data-Center Access Control Using TrustSec Design Guide October 2015 REFERENCE NETWORK ARCHITECTURE Table of Contents About This Document... 1 Cisco TrustSec Overview... 2
CISCO VALIDATED DESIGN User-to-Data-Center Access Control Using TrustSec Design Guide October 2015 REFERENCE NETWORK ARCHITECTURE Table of Contents About This Document... 1 Cisco TrustSec Overview... 2
Food Protection and Defense Institute
 Food Protection and Defense Institute Updates in Education and IT for AFDO 2017 FPDI Product Lines RESEARCH Research organized and led by internal and external PIs according to themes Exploratory, Basic,
Food Protection and Defense Institute Updates in Education and IT for AFDO 2017 FPDI Product Lines RESEARCH Research organized and led by internal and external PIs according to themes Exploratory, Basic,
WYNN SOCIAL CASINO PRIVACY POLICY
 WYNN SOCIAL CASINO PRIVACY POLICY This privacy policy for the Wynn Slots App ( App ), made available by Wynn Social Gaming, LLC ( Wynn Social, Us, We, or Our ), describes our privacy practices (the "Privacy
WYNN SOCIAL CASINO PRIVACY POLICY This privacy policy for the Wynn Slots App ( App ), made available by Wynn Social Gaming, LLC ( Wynn Social, Us, We, or Our ), describes our privacy practices (the "Privacy
Seminars and modules offered in a foreign language at FH Münster
 Seminars and modules offered in a foreign language at FH Münster Faculty Module Degree course ECTS WS SS Advanced Inorganic Chemistry Master Chemical Engineering 8 x Advanced Organic Chemistry Master Chemical
Seminars and modules offered in a foreign language at FH Münster Faculty Module Degree course ECTS WS SS Advanced Inorganic Chemistry Master Chemical Engineering 8 x Advanced Organic Chemistry Master Chemical
Applications of the k-nearest neighbor method for regression and resampling
 Applications of the k-nearest neighbor method for regression and resampling Objectives Provide a structured approach to exploring a regression data set. Introduce and demonstrate the k-nearest neighbor
Applications of the k-nearest neighbor method for regression and resampling Objectives Provide a structured approach to exploring a regression data set. Introduce and demonstrate the k-nearest neighbor
NExT++: Center for Extreme Search
 NExT++: Center for Extreme Search A Joint Center between NUS, Tsinghua and Southampton University CHUA Tat-Seng National University of Singapore OUTLINE Welcome Key Research Focuses Summary Users at Center
NExT++: Center for Extreme Search A Joint Center between NUS, Tsinghua and Southampton University CHUA Tat-Seng National University of Singapore OUTLINE Welcome Key Research Focuses Summary Users at Center
Powering Knowledge Discovery. Insights from big data with Linguamatics I2E
 Powering Knowledge Discovery Insights from big data with Linguamatics I2E Gain actionable insights from unstructured data The world now generates an overwhelming amount of data, most of it written in natural
Powering Knowledge Discovery Insights from big data with Linguamatics I2E Gain actionable insights from unstructured data The world now generates an overwhelming amount of data, most of it written in natural
NOVEMBER 2017 Leading Digital Transformation Driving innovation at scale Marc Leroux Executive Evangelist/Digital ABB
 NOVEMBER 2017 Leading Digital Transformation Driving innovation at scale Marc Leroux Executive Evangelist/Digital ABB Discussion topics Introductions The digital transformation Innovating at scale How
NOVEMBER 2017 Leading Digital Transformation Driving innovation at scale Marc Leroux Executive Evangelist/Digital ABB Discussion topics Introductions The digital transformation Innovating at scale How
The Emerging Data Lake IT Strategy
 The Emerging Data Lake IT Strategy An Evolving Approach for Dealing with Big Data & Changing Environments bit.ly/datalake SPEAKERS: Thomas Kelly, Practice Director Cognizant Technology Solutions Sean Martin,
The Emerging Data Lake IT Strategy An Evolving Approach for Dealing with Big Data & Changing Environments bit.ly/datalake SPEAKERS: Thomas Kelly, Practice Director Cognizant Technology Solutions Sean Martin,
Real-time Fraud Detection with Innovative Big Graph Feature. Gaurav Deshpande, VP Marketing, TigerGraph; Mingxi Wu, VP Engineering, TigerGraph
 Real-time Fraud Detection with Innovative Big Graph Feature Gaurav Deshpande, VP Marketing, TigerGraph; Mingxi Wu, VP Engineering, TigerGraph Speaking Today Gaurav Deshpande VP Marketing, TigerGraph gaurav@tigergraph.com
Real-time Fraud Detection with Innovative Big Graph Feature Gaurav Deshpande, VP Marketing, TigerGraph; Mingxi Wu, VP Engineering, TigerGraph Speaking Today Gaurav Deshpande VP Marketing, TigerGraph gaurav@tigergraph.com
Identifying Fraudulently Promoted Online Videos
 Identifying Fraudulently Promoted Online Videos Vlad Bulakh, Christopher W. Dunn, Minaxi Gupta April 7, 2014 April 7, 2014 Vlad Bulakh 2 Motivation Online video sharing websites are visited by millions
Identifying Fraudulently Promoted Online Videos Vlad Bulakh, Christopher W. Dunn, Minaxi Gupta April 7, 2014 April 7, 2014 Vlad Bulakh 2 Motivation Online video sharing websites are visited by millions
1. Muscat & Co Mortgage Solutions Ltd - Privacy Notice
 1. This Muscat & Co Mortgage Solutions Ltd privacy notice provides information on how we and any of our subsidiaries, and any 3 rd party providers collect, use, secure, transfer and share your information.
1. This Muscat & Co Mortgage Solutions Ltd privacy notice provides information on how we and any of our subsidiaries, and any 3 rd party providers collect, use, secure, transfer and share your information.
