Open Source Network Monitoring Management in MANETs
|
|
|
- Patrick Gibson
- 5 years ago
- Views:
Transcription
1
2 in MANETs Rakesh Dhanalakota Student (M.Tech.) CSE Department BVRIT, Vishnupur, Narsapur. Abstract in MANETs is an open source based network monitoring tool with the advanced monitoring techniques. It s an open source based free solution for monitoring network in different communications over mobile ad hoc networks. It uses the simple monitoring and managing method to detect the network traffic activity in a single GUI console. It necessarily equates the network monitoring solution for free. The new monitoring solution method results in improving the inbound and outbound network monitoring activity by the skilled hands without any investment and without wasting time in development. It also uses the advanced network monitoring management technique with the availability of the advanced enhanced data collection with deep analysis of the advanced network monitoring platform. It also makes the use of the network usage with the wide range of varieties in monitoring with the help of network protocols with network management protocol. It s a powerful network monitoring open source tool which supports the different mobile network operating system platforms which offers the efficient network monitoring activity with unique search key. 1. Introduction in MANETs offers the easiest way to use with the mobile ad hoc network based interface with advanced monitoring support. It makes the use of network monitoring unique key for network activity detection in order to avoid network delays. Among the other mobile ad hoc networks current network monitoring tool can manage and detect the activity in depth with the unique and random network monitoring key with the advanced features which integrates with the mobile application compatibility whereas users can access the network monitoring web console over network amongst the mobile ad hoc networks. can be deployed for various mobile devices such as android phone, windows phone and the iphone. Application can be customized easily and can also be optimized with the advanced network monitoring options. It s an open source network based monitoring tool with the support of external monitoring devices and it also integrates with the advanced alert management system. It also uses the manual network monitoring and scanning modes with in the mobile ad hoc network in a given subnet address where as it integrates the advanced protection layer where other anonymous users cannot access and will not have limited access to the Open Source Network Monitoring Web Console in MANET. It also supports the multi-layouts for pointing or mapping to the network monitoring console domain. Application can be deployed on a full qualified domain. 3251
3 2. System Requirements 3. Network Monitoring Management Tool Requires a fully qualified domain with DNS support with monitoring web agent server Requires fully configured web application server with the Web Server with network tool support which can run on both Windows Operating System and the Linux Operating System Pre-requisites for the Web Server and Network Monitoring Web Agent Server Should be Supported with the Open Source Framework for advanced Network Monitoring Network Monitoring Management Console and web application deployed on a standalone web server. Network Monitoring tool with high threat Management and high security for network monitoring web application. Network Detection, monitoring and the Alert system with threat management in mobile ad hoc networks. Integrates with the high network security with the with the advanced protection service such as firewall for network monitoring web console and the integration of security tools for monitoring network console. Supported with the Quality of Service for network monitoring tool. Networking Monitoring Web Console integration for mobile devices and monitoring devices. Can be deployed in any of the above said hardware applications. Data Open Source Network Monitoring Management Tool is a standalone web application tool for managing, detecting and monitoring the network activity. Network Monitoring Management Tool is a GUI based application interface which displays the advanced network activity on the mobile ad hoc networks, it also analyses the information from the multiple sources on the mobile ad hoc network and also gathers the network activity information on differently collected mobile ad hoc networks (MANETs), It records the activities such as network event logs, network devices that are connected, network services, network traffic in mobile ad hoc network. The ad hoc network administrators can also setup the alert system and the notification system on the network. It uses the extended network search for searching the network devices, it also generates the network reports with advanced information of the connected device in the mobile ad hoc network. Monitoring Management Tool collects all the data of the devices on the network. It s an Open Source Monitoring Tool which simply points the user wireless devices on the network, Tool makes the user devices discoverable on the network with the help of advanced network services which is used in the mobile ad hoc network with unique static protocol address which is automatically assigned by the MANET router. User or administrator of the tool can gain the control access over the managed network on the GUI Web Console for 3252
4 Monitoring Management Tool which can easily detect the network activity. enterprises known as Enterprise Network Monitoring Management Tool. Administrator and User level activity report on dashboard can be easily combined with two security levels which can be managed manually. Monitoring Web can be easily installed or deployed on mobile or handheld devices. It enables the web application to use the advanced system functionality of the monitoring detection system. It runs on multi network platform for monitoring the system which can detect the various activities of the user and that provides with the user activity or user events monitoring management solution. The performance of the monitoring tool can be optimized manually or automatically which is also known as performance monitoring analysis. Network Monitoring Tool also supports the various operating system which can run with the help of the open source database engine, it also makes the use of the distributed network monitoring system with advanced detection method or advanced network discovery method. It gives the option of web console interface, GUI Interface and Mobile Console Interface. It also makes the use of impact analysis on the mobile ad hoc network with enhanced network monitoring tool. It is more than a network hub, network switch, network router, network proxy etc. It monitors the network devices and network based applications on the mobile ad hoc network. Problem can be easily troubleshooted on the Network Monitoring Management Web Console Tool. It can also be virtualized without any performance loss and workloads can be easily allocated on the network servers. It can be easily configured and performance can also be calculated with the help of the tool. It mainly focuses on the monitoring management effort system of the tool, the monitoring web application tool enables with the more number of the service oriented network monitors which can perform network monitoring request and network monitoring response system. o The network monitoring tool can detect in 2 or 3 phases of the different network layers just like a router interface with the various multiple devices on the network. Network discovery and network resolution can be solved in less time. It can also generate the activities list, events list and reporting schedule list on the MANET. This can also be used in 3253
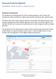
5 4. Architecture mainly useful for IT Data Centres, Organizations, Enterprises and also for the intelligence security bureau. It is a free web application and integrated with Open Source Framework. 6. References [1] AthanassiosLiakopoulos, RanganaiChaparadza, AnastasiosZafeiropoulos, AlanDavy, Monitoring within an Autonomic Network: A GANA Based Network Monitoring Framework" Published in year 2010,Vol6275. [2] GupteshwarGupta, DevendraChaphekar, BhishamSonkar, "Study of Framework of Mobile IP and MANET Integration" Vol243. [3] PhilipSamuel, G.Jisha, "Impact of Node Density on Node Connectivity in MANET Routing Protocols" Published in the year 2011, Vol.193, pp.1-8. Figure: 1 Open Source Network Monitoring Management in MANETs 5. Conclusion in MANETs is an open source based powerful network monitoring tool which supports the object detection management with built-in auto discovery and auto network device detection system. All the devices can be easily monitored in the mobile ad hoc network environment. Network Monitoring System Tool can detect and retrieve the messages from the network monitoring web console. It monitors all the activities, it notifies and alerts the administrators when the intrusion or malicious attack is detected. I hereby conclude that Open Source Network Monitoring Management in MANETS Tool is 3254
AccessEnforcer Version 4.0 Features List
 AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
MD-100: Modern Desktop Administrator Part 1
 Days: 5 Description: This five-day course is for IT professionals who deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. Students will develop
Days: 5 Description: This five-day course is for IT professionals who deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. Students will develop
ASA/PIX Security Appliance
 I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 20: Intrusion Prevention Department of Computer Science and Engineering University at Buffalo 1 Lecture Overview Firewalls purpose types locations Network perimeter
CSE 565 Computer Security Fall 2018 Lecture 20: Intrusion Prevention Department of Computer Science and Engineering University at Buffalo 1 Lecture Overview Firewalls purpose types locations Network perimeter
Course Outline Topic 1: Current State Assessment, Security Operations Centers, and Security Architecture
 About this Course This course will best position your organization to analyse threats and detect anomalies that could indicate cybercriminal behaviour. The payoff for this new proactive approach would
About this Course This course will best position your organization to analyse threats and detect anomalies that could indicate cybercriminal behaviour. The payoff for this new proactive approach would
Administration of Symantec Cyber Security Services (July 2015) Sample Exam
 Administration of Symantec Cyber Security Services (July 2015) Sample Exam Contents SAMPLE QUESTIONS... 1 ANSWERS... 6 Sample Questions 1. Which DeepSight Intelligence Datafeed can be used to create a
Administration of Symantec Cyber Security Services (July 2015) Sample Exam Contents SAMPLE QUESTIONS... 1 ANSWERS... 6 Sample Questions 1. Which DeepSight Intelligence Datafeed can be used to create a
McAfee Network Security Platform 8.3
 8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
You should not have any other MX records for your domain name (subdomain MX records are OK).
 Network Configuration In order to properly deploy ExchangeDefender, you need to make several changes on your network. First, you have to change your MX record to point all of your inbound mail to ExchangeDefender.
Network Configuration In order to properly deploy ExchangeDefender, you need to make several changes on your network. First, you have to change your MX record to point all of your inbound mail to ExchangeDefender.
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Overview: Security, Internet Access, and Communication
Trend Micro Deep Discovery Training for Certified Professionals
 Trend Micro Deep Discovery Training for Certified Professionals Length Courseware 3 days Hard or soft copy provided. Course Description Trend Micro Deep Discovery Training for Certified Professionals is
Trend Micro Deep Discovery Training for Certified Professionals Length Courseware 3 days Hard or soft copy provided. Course Description Trend Micro Deep Discovery Training for Certified Professionals is
COURSE PROJECT SEM ATTENTION ALL ADVANCED DIPLOMA & BACHELOR STUDENTS
 COURSE PROJECT SEM 2 2014 2015 ATTENTION ALL ADVANCED DIPLOMA & BACHELOR STUDENTS The students who have pre registered for Networking Course Project are required to submit your project proposal. The titles
COURSE PROJECT SEM 2 2014 2015 ATTENTION ALL ADVANCED DIPLOMA & BACHELOR STUDENTS The students who have pre registered for Networking Course Project are required to submit your project proposal. The titles
Integrating Microsoft Forefront Threat Management Gateway (TMG)
 Integrating Microsoft Forefront Threat Management Gateway (TMG) EventTracker v7.x Publication Date: Sep 16, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This
Integrating Microsoft Forefront Threat Management Gateway (TMG) EventTracker v7.x Publication Date: Sep 16, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This
VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch
 VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch Multiple AirWatch versions Have documentation feedback? Submit a Documentation Feedback
VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch Multiple AirWatch versions Have documentation feedback? Submit a Documentation Feedback
Reference Guide Revision B. McAfee Cloud Workload Security 5.0.0
 Reference Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
Reference Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
M1000, M2000, M3000. eprism Installation Guide
 M1000, M2000, M3000 eprism Installation Guide Preface 3 CHAPTER 1 Pre-Installation Tasks 5 eprism Deployment 6 Network Modifications 8 Firewall Configuration 9 DNS Configuration for Mail Routing 10 Hardware
M1000, M2000, M3000 eprism Installation Guide Preface 3 CHAPTER 1 Pre-Installation Tasks 5 eprism Deployment 6 Network Modifications 8 Firewall Configuration 9 DNS Configuration for Mail Routing 10 Hardware
Fundamentals of Windows Server 2008 Network and Applications Infrastructure
 COURSE OVERVIEW This five-day instructor-led course introduces students to network and applications infrastructure concepts and configurations provided by Window Server 2008. Students will be able to acquire
COURSE OVERVIEW This five-day instructor-led course introduces students to network and applications infrastructure concepts and configurations provided by Window Server 2008. Students will be able to acquire
20741 Networking with Windows Server 2016
 20741 Networking with Windows Server 2016 This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers
20741 Networking with Windows Server 2016 This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers
Oracle Platinum Services Platinum Configuration Worksheet Online Help E
 Oracle Platinum Services Platinum Configuration Worksheet Online Help E57997-01 Document Objectives: The Platinum Configuration Worksheet (PCW) Online Tool is a key part of planning and executing an efficient
Oracle Platinum Services Platinum Configuration Worksheet Online Help E57997-01 Document Objectives: The Platinum Configuration Worksheet (PCW) Online Tool is a key part of planning and executing an efficient
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
securing your network perimeter with SIEM
 The basics of auditing and securing your network perimeter with SIEM Introduction To thwart network attacks, you first need to be on top of critical security events occurring in your network. While monitoring
The basics of auditing and securing your network perimeter with SIEM Introduction To thwart network attacks, you first need to be on top of critical security events occurring in your network. While monitoring
Case Study emagic a Complete Datacenter Management Solution
 Case Study emagic a Complete Datacenter Solution www.esds.co.in Product Overview emagic is an all-in-one solution to manage all the aspects of data center. It is an automated system designed to make data
Case Study emagic a Complete Datacenter Solution www.esds.co.in Product Overview emagic is an all-in-one solution to manage all the aspects of data center. It is an automated system designed to make data
Product Guide Revision B. McAfee Cloud Workload Security 5.0.0
 Product Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
Product Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
Exam : Title : symantec small Business security. Version : DEMO
 Exam : 250-101 Title : symantec small Business security Version : DEMO 1. Which heuristic technology does Symantec AntiVirus use? A. Q-Factor B. Bloodhound C. pattern matching D. regular expression 2.
Exam : 250-101 Title : symantec small Business security Version : DEMO 1. Which heuristic technology does Symantec AntiVirus use? A. Q-Factor B. Bloodhound C. pattern matching D. regular expression 2.
KASPERSKY ANTI-MALWARE PROTECTION SYSTEM BE READY FOR WHAT S NEXT. Kaspersky Open Space Security
 KASPERSKY ANTI-MALWARE PROTECTION SYSTEM BE READY FOR WHAT S NEXT Open Space Security Cyber-attacks are real. Today alone, Lab technology prevented nearly 3 million of them aimed at our customers worldwide.
KASPERSKY ANTI-MALWARE PROTECTION SYSTEM BE READY FOR WHAT S NEXT Open Space Security Cyber-attacks are real. Today alone, Lab technology prevented nearly 3 million of them aimed at our customers worldwide.
VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch
 VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch Multiple AirWatch versions Have documentation feedback? Submit a Documentation Feedback
VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch Multiple AirWatch versions Have documentation feedback? Submit a Documentation Feedback
(A212) Communication Application Server (AS) Standalone Overview
 (A212) Communication Application Server (AS) Standalone Overview This course provides a technical overview of the Communication Application Server Standalone configuration. Managers, administrators and
(A212) Communication Application Server (AS) Standalone Overview This course provides a technical overview of the Communication Application Server Standalone configuration. Managers, administrators and
Cisco IOS Firewall Intrusion Detection System Commands
 Cisco IOS Firewall Intrusion Detection System Commands This chapter describes the commands used to configure the integrated Intrusion Detection System (IDS) features in Cisco IOS Firewall. Intrusion detection
Cisco IOS Firewall Intrusion Detection System Commands This chapter describes the commands used to configure the integrated Intrusion Detection System (IDS) features in Cisco IOS Firewall. Intrusion detection
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster
 AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
Network Security. Thierry Sans
 Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
"Charting the Course... MOC A Planning, Deploying and Managing Microsoft Forefront TMG Course Summary
 Description Course Summary The goal of this three-day instructor-led course is to provide students with the knowledge and skills necessary to effectively plan, deploy and manage Microsoft Forefront Threat
Description Course Summary The goal of this three-day instructor-led course is to provide students with the knowledge and skills necessary to effectively plan, deploy and manage Microsoft Forefront Threat
Vendor: McAfee. Exam Code: MA Exam Name: McAfee Certified Product Specialist - HIPs. Version: Demo
 Vendor: McAfee Exam Code: MA0-102 Exam Name: McAfee Certified Product Specialist - HIPs Version: Demo QUESTION 1 Which of the following policy categories are considered to be mufti-slot policies? (Select
Vendor: McAfee Exam Code: MA0-102 Exam Name: McAfee Certified Product Specialist - HIPs Version: Demo QUESTION 1 Which of the following policy categories are considered to be mufti-slot policies? (Select
IC32E - Pre-Instructional Survey
 Name: Date: 1. What is the primary function of a firewall? a. Block all internet traffic b. Detect network intrusions c. Filter network traffic d. Authenticate users 2. A system that monitors traffic into
Name: Date: 1. What is the primary function of a firewall? a. Block all internet traffic b. Detect network intrusions c. Filter network traffic d. Authenticate users 2. A system that monitors traffic into
Learn about the Fundamental building blocks that go into building a Windows Server infrastructure with Windows Server 2012.
 Fundamentals of a Windows Server Infrastructure Overview Learn about the Fundamental building blocks that go into building a Windows Server infrastructure with Windows Server 2012. This five day course
Fundamentals of a Windows Server Infrastructure Overview Learn about the Fundamental building blocks that go into building a Windows Server infrastructure with Windows Server 2012. This five day course
McAfee Network Security Platform
 Revision B McAfee Network Security Platform (9.2.9.3-9.2.5.34 Manager-NS3500 Release Notes) Contents About this release New Features Resolved issues Installation instructions Known issues Product documentation
Revision B McAfee Network Security Platform (9.2.9.3-9.2.5.34 Manager-NS3500 Release Notes) Contents About this release New Features Resolved issues Installation instructions Known issues Product documentation
This course incorporates a variety of hands-on lab exercises allowing participants to put the lesson content into action.
 Trend Micro Trend Micro Deep Discovery Training for Certified Professionals Course ID: TMCPDD Course Overview Course Duration: 3 Days Trend Micro Deep Discovery Training for Certified Professionals is
Trend Micro Trend Micro Deep Discovery Training for Certified Professionals Course ID: TMCPDD Course Overview Course Duration: 3 Days Trend Micro Deep Discovery Training for Certified Professionals is
McAfee Cloud Workload Security Product Guide
 Revision B McAfee Cloud Workload Security 5.1.0 Product Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection,
Revision B McAfee Cloud Workload Security 5.1.0 Product Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection,
Application Note Asterisk BE with Remote Phones - Configuration Guide
 Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
AT&T Endpoint Security
 AT&T Endpoint Security November 2016 Security Drivers Market Drivers Online business 24 x 7, Always on Globalization Virtual Enterprise Business Process / IT Alignment Financial Drivers CapEx / OpEx Reduction
AT&T Endpoint Security November 2016 Security Drivers Market Drivers Online business 24 x 7, Always on Globalization Virtual Enterprise Business Process / IT Alignment Financial Drivers CapEx / OpEx Reduction
Configuring Windows 8 Course 20687A - Five days - Instructor-led - Hands-on
 Configuring Windows 8 Course 20687A - Five days - Instructor-led - Hands-on Introduction This course provides students hands-on experience with Windows 8. It provides guidance on installing, upgrading,
Configuring Windows 8 Course 20687A - Five days - Instructor-led - Hands-on Introduction This course provides students hands-on experience with Windows 8. It provides guidance on installing, upgrading,
Transforming Security from Defense in Depth to Comprehensive Security Assurance
 Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
Certified SonicWALL Security Administrator (CSSA) Instructor-led Training
 Instructor-led Training Comprehensive Services from Your Trusted Security Partner Additional Information Recommended prerequisite for the Certified SonicWALL Security Administrator (CSSA) exam Course Description:
Instructor-led Training Comprehensive Services from Your Trusted Security Partner Additional Information Recommended prerequisite for the Certified SonicWALL Security Administrator (CSSA) exam Course Description:
Course 20741B: Networking with Windows Server 2016
 Course Duration: 5 days Course description Overview: This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations.
Course Duration: 5 days Course description Overview: This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations.
Seceon s Open Threat Management software
 Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Unified Networks Administration & Monitoring System Specifications : YM - IT. YM Unified Networks Administration & Monitoring System
 2115 YM Unified Networks Administration & Monitoring System 1. مواصفات نظام ادارة ومراقبة الشبكات الموحد: BOQ of Unified Networks Administration and Monitoring System: N 1 2 3 4 Item Main Network Monitoring
2115 YM Unified Networks Administration & Monitoring System 1. مواصفات نظام ادارة ومراقبة الشبكات الموحد: BOQ of Unified Networks Administration and Monitoring System: N 1 2 3 4 Item Main Network Monitoring
Network Deployment Guide
 WC-COA WC-COA-I Network Deployment Guide Contact Information FREE 24/7 technical support or order toll-free in the U.S. Call 877-877-BBOX (outside U.S.: call 724-746-5500) www.blackbox.com info@blackbox.com
WC-COA WC-COA-I Network Deployment Guide Contact Information FREE 24/7 technical support or order toll-free in the U.S. Call 877-877-BBOX (outside U.S.: call 724-746-5500) www.blackbox.com info@blackbox.com
Comodo Dome Shield - Admin Guide
 rat Comodo Dome Shield Software Version 1.12 Administrator Guide Guide Version 1.12.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
rat Comodo Dome Shield Software Version 1.12 Administrator Guide Guide Version 1.12.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
Experience working with Windows Server 2008 or Windows Server Experience working in a Windows Server infrastructure enterprise environment
 Networking with Windows Server 2016 va Day(s): 5 Course Code: M20741 Version: A Overview This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows
Networking with Windows Server 2016 va Day(s): 5 Course Code: M20741 Version: A Overview This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows
MONITORING WAN CONNECTIONS. How to monitor WAN connections with NetFort LANGuardian Aisling Brennan
 LANGUARDIAN MONITORING WAN CONNECTIONS How to monitor WAN connections with NetFort LANGuardian Aisling Brennan LANGuardian gives you the information you need to troubleshoot problems and monitor network
LANGUARDIAN MONITORING WAN CONNECTIONS How to monitor WAN connections with NetFort LANGuardian Aisling Brennan LANGuardian gives you the information you need to troubleshoot problems and monitor network
Administering System Center 2012 Configuration Manager (10747D)
 Administering System Center 2012 Configuration Manager (10747D) Overview This course describes how to configure and manage a System Center 2012 R2 Configuration Manager site and its associated site systems.
Administering System Center 2012 Configuration Manager (10747D) Overview This course describes how to configure and manage a System Center 2012 R2 Configuration Manager site and its associated site systems.
Scope and Sequence: CCNA Discovery
 Scope and Sequence: CCNA Discovery Last updated April 22, 2008 Target Audience CCNA Discovery is primarily designed for Cisco Networking Academy students who are looking for career-oriented, information
Scope and Sequence: CCNA Discovery Last updated April 22, 2008 Target Audience CCNA Discovery is primarily designed for Cisco Networking Academy students who are looking for career-oriented, information
Understanding Cisco Cybersecurity Fundamentals
 210-250 Understanding Cisco Cybersecurity Fundamentals NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 210-250 Exam on Understanding Cisco
210-250 Understanding Cisco Cybersecurity Fundamentals NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 210-250 Exam on Understanding Cisco
Intrusion Detection. Overview. Intrusion vs. Extrusion Detection. Concepts. Raj Jain. Washington University in St. Louis
 Intrusion Detection Overview Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: 22-1 1. Intruders 2. Intrusion
Intrusion Detection Overview Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: 22-1 1. Intruders 2. Intrusion
Copyright 2011 Trend Micro Inc.
 Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Service Description Safecom Customer Connection Version 3.5
 Service Description Safecom Customer Connection Version 3.5 2006 Telecom NZ Ltd Commercial in Confidence CONTENTS 1 INTRODUCTION...3 2 SERVICE DEFINITION...3 2.1 SERVICE OVERVIEW... 3 2.2 SERVICE FEATURES...
Service Description Safecom Customer Connection Version 3.5 2006 Telecom NZ Ltd Commercial in Confidence CONTENTS 1 INTRODUCTION...3 2 SERVICE DEFINITION...3 2.1 SERVICE OVERVIEW... 3 2.2 SERVICE FEATURES...
Christopher Covert. Principal Product Manager Enterprise Solutions Group. Copyright 2016 Symantec Endpoint Protection Cloud
 Christopher Covert Principal Product Manager Enterprise Solutions Group Copyright 2016 Symantec Endpoint Protection Cloud THE PROMISE OF CLOUD COMPUTING We re all moving from challenges like these Large
Christopher Covert Principal Product Manager Enterprise Solutions Group Copyright 2016 Symantec Endpoint Protection Cloud THE PROMISE OF CLOUD COMPUTING We re all moving from challenges like these Large
Speed Up Incident Response with Actionable Forensic Analytics
 WHITEPAPER DATA SHEET Speed Up Incident Response with Actionable Forensic Analytics Close the Gap between Threat Detection and Effective Response with Continuous Monitoring January 15, 2015 Table of Contents
WHITEPAPER DATA SHEET Speed Up Incident Response with Actionable Forensic Analytics Close the Gap between Threat Detection and Effective Response with Continuous Monitoring January 15, 2015 Table of Contents
Designing Windows Server 2008 Network and Applications Infrastructure
 Designing Windows Server 2008 Network and Applications Infrastructure Course No. 6435B - 5 Days Instructor-led, Hands-on Introduction This five-day course will provide students with an understanding of
Designing Windows Server 2008 Network and Applications Infrastructure Course No. 6435B - 5 Days Instructor-led, Hands-on Introduction This five-day course will provide students with an understanding of
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
Securing CS-MARS C H A P T E R
 C H A P T E R 4 Securing CS-MARS A Security Information Management (SIM) system can contain a tremendous amount of sensitive information. This is because it receives event logs from security systems throughout
C H A P T E R 4 Securing CS-MARS A Security Information Management (SIM) system can contain a tremendous amount of sensitive information. This is because it receives event logs from security systems throughout
Symbols. Numerics I N D E X
 I N D E X Symbols /var/log/ha-debug log, 517 /var/log/ha-log log, 517 Numerics A 3500XL Edge Layer 2 switch, configuring AD SSO, 354 355 access to resources, troubleshooting issues, 520 access VLANs, 54
I N D E X Symbols /var/log/ha-debug log, 517 /var/log/ha-log log, 517 Numerics A 3500XL Edge Layer 2 switch, configuring AD SSO, 354 355 access to resources, troubleshooting issues, 520 access VLANs, 54
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010
 Course 10135: Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Page 1 of 9 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Course 10135: 4 days; Instructor-Led
Course 10135: Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Page 1 of 9 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Course 10135: 4 days; Instructor-Led
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: Security Requirements Security Requirements, on
Security, Internet Access, and Communication Ports
 Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
Security, Internet Access, and Communication Ports The following topics provide information on system security, internet access, and communication ports: About Security, Internet Access, and Communication
Scope and Sequence: CCNA Discovery v4.0
 Scope and Sequence: CCNA Discovery v4.0 Last Updated August 30, 2007 The course objectives and outline for the final two CCNA Discovery courses, Introducing Routing and Switching in the Enterprise and
Scope and Sequence: CCNA Discovery v4.0 Last Updated August 30, 2007 The course objectives and outline for the final two CCNA Discovery courses, Introducing Routing and Switching in the Enterprise and
PSTN Security. Sougat Ghosh Security Services Leader Asia, Nortel Delhi / September 29, 2008 BUSINESS MADE SIMPLE
 PSTN Security Sougat Ghosh Security Services Leader Asia, Nortel Delhi / September 29, 2008 BUSINESS MADE SIMPLE 1 Disclaimer The slides and presentation templates are property of Nortel and must not be
PSTN Security Sougat Ghosh Security Services Leader Asia, Nortel Delhi / September 29, 2008 BUSINESS MADE SIMPLE 1 Disclaimer The slides and presentation templates are property of Nortel and must not be
Networking with Windows Server 2016
 Course 20741: Networking with Windows Server 2016 Page 1 of 7 Networking with Windows Server 2016 Course 20741: 4 days; Instructor-Led Introduction This 4-day classroom-based course provides the fundamental
Course 20741: Networking with Windows Server 2016 Page 1 of 7 Networking with Windows Server 2016 Course 20741: 4 days; Instructor-Led Introduction This 4-day classroom-based course provides the fundamental
IBM IBM Tivoli Storage Productivity Center V4.1 Implementation. Download Full Version :
 IBM 000-002 IBM Tivoli Storage Productivity Center V4.1 Implementation Download Full Version : http://killexams.com/pass4sure/exam-detail/000-002 QUESTION: 116 Which component is required if a customer
IBM 000-002 IBM Tivoli Storage Productivity Center V4.1 Implementation Download Full Version : http://killexams.com/pass4sure/exam-detail/000-002 QUESTION: 116 Which component is required if a customer
Synchronized Security
 Synchronized Security Revolutionizing Advanced Threat Protection Per Söderqvist Sales Engineer Nordics and Baltics 1 A Proven Market Leader Endpoint Encryption Leader UTM Unified Threat Management EPP
Synchronized Security Revolutionizing Advanced Threat Protection Per Söderqvist Sales Engineer Nordics and Baltics 1 A Proven Market Leader Endpoint Encryption Leader UTM Unified Threat Management EPP
Comodo Dome Shield. Administrator Guide Guide Version Software Version 2.4. Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo Dome Shield Software Version 2.4 Administrator Guide Guide Version 2.4.032019 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome Shield...3
rat Comodo Dome Shield Software Version 2.4 Administrator Guide Guide Version 2.4.032019 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome Shield...3
Course : Planning and Administering SharePoint 2016
 Course Outline Course 20339-1: Planning and Administering SharePoint 2016 Duration: 5 days About this course This five-day course will provide you with the knowledge and skills to plan and administer a
Course Outline Course 20339-1: Planning and Administering SharePoint 2016 Duration: 5 days About this course This five-day course will provide you with the knowledge and skills to plan and administer a
Installing and Configuring Windows Server 2012
 Installing and Configuring Windows Server 2012 Course 20410C - Five days - Instructor-led - Hands-on Introduction Get hands-on instruction and practice installing and configuring Windows Server 2012, including
Installing and Configuring Windows Server 2012 Course 20410C - Five days - Instructor-led - Hands-on Introduction Get hands-on instruction and practice installing and configuring Windows Server 2012, including
IT Security Training MS-500: Microsoft 365 Security Administration. Upcoming Dates. Course Description. Course Outline $2,
 IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
COURSE 20741B: NETWORKING WITH WINDOWS SERVER 2016
 ABOUT THIS COURSE This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers IP fundamentals, remote
ABOUT THIS COURSE This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers IP fundamentals, remote
NetFort LANGuardian Integration Guide. NetFort LANGuardian. NetFort LANGuardian Integration Guide 1
 NetFort LANGuardian Integration Guide NetFort LANGuardian NetFort LANGuardian Integration Guide 1 NetFort LANGuardian Integration Guide Change Log Version Date Modified By Comments 0.1 June 2018 Conor
NetFort LANGuardian Integration Guide NetFort LANGuardian NetFort LANGuardian Integration Guide 1 NetFort LANGuardian Integration Guide Change Log Version Date Modified By Comments 0.1 June 2018 Conor
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
Integrate Viper business antivirus EventTracker Enterprise
 Integrate Viper business antivirus EventTracker Enterprise Publication Date: June 2, 2016 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
Integrate Viper business antivirus EventTracker Enterprise Publication Date: June 2, 2016 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
CIH
 mitigating at host level, 23 25 at network level, 25 26 Morris worm, characteristics of, 18 Nimda worm, characteristics of, 20 22 replacement login, example of, 17 signatures. See signatures SQL Slammer
mitigating at host level, 23 25 at network level, 25 26 Morris worm, characteristics of, 18 Nimda worm, characteristics of, 20 22 replacement login, example of, 17 signatures. See signatures SQL Slammer
RSA NetWitness Logs. Airtight Management Console. Event Source Log Configuration Guide. Last Modified: Thursday, May 04, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Airtight Management Console Last Modified: Thursday, May 04, 2017 Event Source Product Information: Vendor: AirTight Event Source: Airtight Management
RSA NetWitness Logs Event Source Log Configuration Guide Airtight Management Console Last Modified: Thursday, May 04, 2017 Event Source Product Information: Vendor: AirTight Event Source: Airtight Management
Vendor: Microsoft. Exam Code: Exam Name: TS: Microsoft System Center Operations Manager 2007, Configuring. Version: Demo
 Vendor: Microsoft Exam Code: 70-400 Exam Name: TS: Microsoft System Center Operations Manager 2007, Configuring Version: Demo Question: 1 You have a System Center Operations Manager 2007 environment. You
Vendor: Microsoft Exam Code: 70-400 Exam Name: TS: Microsoft System Center Operations Manager 2007, Configuring Version: Demo Question: 1 You have a System Center Operations Manager 2007 environment. You
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
10970B: Networking with Windows Server
 10970B: Networking with Windows Server Course Details Course Code: Duration: Notes: 10970B 5 days This course syllabus should be used to determine whether the course is appropriate for the students, based
10970B: Networking with Windows Server Course Details Course Code: Duration: Notes: 10970B 5 days This course syllabus should be used to determine whether the course is appropriate for the students, based
Content for Sophos- Theory and lab session
 Content for Sophos- Theory and lab session Module 1 : Enduser Protection deployment scenarios Review of Enduser Protection features and components Factors to consider when designing solutions Single site
Content for Sophos- Theory and lab session Module 1 : Enduser Protection deployment scenarios Review of Enduser Protection features and components Factors to consider when designing solutions Single site
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, on page 1 Configure Cisco DNA Center as a Single Host Using the Wizard, on page 5 Configure Cisco DNA Center as a Multi-Host Cluster Using the Wizard,
Review Cisco DNA Center Configuration Wizard Parameters, on page 1 Configure Cisco DNA Center as a Single Host Using the Wizard, on page 5 Configure Cisco DNA Center as a Multi-Host Cluster Using the Wizard,
Networking with Windows Server 2016
 Networking with Windows Server 2016 OD20741B; On-Demand, Video-based Course Description This course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most
Networking with Windows Server 2016 OD20741B; On-Demand, Video-based Course Description This course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most
Integrate Sophos Enterprise Console. EventTracker v8.x and above
 Integrate Sophos Enterprise Console EventTracker v8.x and above Publication Date: September 22, 2017 Abstract This guide provides instructions to configure Sophos Enterprise Console to send the events
Integrate Sophos Enterprise Console EventTracker v8.x and above Publication Date: September 22, 2017 Abstract This guide provides instructions to configure Sophos Enterprise Console to send the events
Distributed Systems. 29. Firewalls. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
MAILGUARD AND MICROSOFT EXCHANGE 2013
 MAILGUARD AND MICROSOFT EXCHANGE 2013 MailGuard Secure Email Filtering MailGuard: support@mailguard.com.au Phone: 1300 30 65 10 www.mailguard.com.au TABLE OF CONTENTS Introduction 3 Document and Naming
MAILGUARD AND MICROSOFT EXCHANGE 2013 MailGuard Secure Email Filtering MailGuard: support@mailguard.com.au Phone: 1300 30 65 10 www.mailguard.com.au TABLE OF CONTENTS Introduction 3 Document and Naming
Wireless Controller DWC-1000
 Network Architecture Manage up to 6 wireless APs, upgradable to 24 APs 1 per controller Control up to 24 wireless APs, maximum 96 APs 1 per cluster Robust Network Security Wireless Instruction Detection
Network Architecture Manage up to 6 wireless APs, upgradable to 24 APs 1 per controller Control up to 24 wireless APs, maximum 96 APs 1 per cluster Robust Network Security Wireless Instruction Detection
This course prepares candidates for the CompTIA Network+ examination (2018 Objectives) N
 CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
DomainTools for Splunk
 DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
McAfee Host Intrusion Prevention Administration Course
 McAfee Host Intrusion Prevention Administration Course Education Services administration course The McAfee Host Intrusion Prevention Administration course provides attendees with indepth training on the
McAfee Host Intrusion Prevention Administration Course Education Services administration course The McAfee Host Intrusion Prevention Administration course provides attendees with indepth training on the
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Endpoint Security Manager
 Comodo Endpoint Security Manager Software Version 1.6 CIS Configuration Editor Version 1.6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction
Comodo Endpoint Security Manager Software Version 1.6 CIS Configuration Editor Version 1.6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction
Quick Heal Microsoft Exchange Protection
 Quick Heal Microsoft Exchange Protection Intuitive. Effective. Comprehensive. Feature List Web-based console makes administrative management easy and simple. Comprehensive and rapid scanning of emails
Quick Heal Microsoft Exchange Protection Intuitive. Effective. Comprehensive. Feature List Web-based console makes administrative management easy and simple. Comprehensive and rapid scanning of emails
A: PLANNING AND ADMINISTERING SHAREPOINT 2016
 ABOUT THIS COURSE This five-day course will provide you with the knowledge and skills to plan and administer a Microsoft SharePoint 2016 environment. The course teaches you how to deploy, administer, and
ABOUT THIS COURSE This five-day course will provide you with the knowledge and skills to plan and administer a Microsoft SharePoint 2016 environment. The course teaches you how to deploy, administer, and
Integrate pfsense EventTracker Enterprise
 Integrate pfsense EventTracker Enterprise Publication Date: Jul.18, 2016 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions to configure
Integrate pfsense EventTracker Enterprise Publication Date: Jul.18, 2016 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions to configure
CounterACT 7.0. Quick Installation Guide for a Single Virtual CounterACT Appliance
 CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
Sophos for Virtual Environments. startup guide -- Enterprise Console edition
 Sophos for Virtual Environments startup guide -- Enterprise Console edition Contents About this guide... 1 About Sophos for Virtual Environments...2 Key steps in installation... 5 Check the system requirements...
Sophos for Virtual Environments startup guide -- Enterprise Console edition Contents About this guide... 1 About Sophos for Virtual Environments...2 Key steps in installation... 5 Check the system requirements...
