Ns2 SetDest Acceleration Enhancement EEC 787 Final Project Mid Report. Brian Krupp and Limei Hou
|
|
|
- Roderick Pierce
- 6 years ago
- Views:
Transcription
1 2011 Ns2 SetDest Acceleration Enhancement EEC 787 Final Project Mid Report Brian Krupp and Limei Hou
2 Ns2 SetDest Acceleration Enhancement Abstract The introduction of the NS2 simulator has allowed students and researches to experiment existing and modifications of network protocols to help support their understanding and research. With the increasing presence of wireless networks and mobile nodes communicating within these networks, the simulation of these nodes is of greater focus. NS2 supports the capability of movement of mobile nodes via setdest commands in the simulator however these don t represent ideal movement scenarios, for example acceleration. Our goal is to implement this capability such that simulation models provide a more true representation of movement of a mobile node. Introduction and Background The NS2 simulator is a very powerful network simulation program that allows us to test network simulation of both wired and wireless networks. With the increasing presence of wireless network devices, often these devices are not stationary and we need to have a mechanism to test movement of these mobile nodes. The NS2 simulator provides the simulation capability of having an object move at a certain time to a specific coordinate from its current location at a specific constant speed. For example, the following code would move anode named WT(1) once the simulation reached five seconds to the coordinate 50,50 at a speed of 10 meters per second: $ns_ at 5.0 $WT(1) setdest The important piece of the code above being the setdest command. This code doesn t have any awareness of where the node is currently located at, only where it is going. By using setdest, we are able to simulate movement within the ns2 simulator, but the entering the simulated movements for a set of particular nodes can become quite a task, especially if you have to do it for a simulation that contains a large set of nodes. Also if these commands were to be manually entered into a simulation script or sourced in, although the results would be consistent the movement is not random and may not provide a true simulation. To help address this problem, a Random Waypoint (RWP) mobility model was introduced into NS2. Random Waypoint mobility is the most popular in simulation studies, where each mobile node will follow the process of pausing at a location, selecting a waypoint randomly, and then move towards it with a randomly chosen speed between two numbers, then repeat this cycle until the end of simulation. The diagram below demonstrates this where the node starts off at coordinate 0,0, picks a random destination of 15,0 and moves there at a speed of 10 meters per second. The next coordinate it picks is 15,10, and picks a speed of 20 meters per second, and this cycle would then repeat until the end of the simulation.
3 To implement the above model in a simulation, two commands are needed for both movements. If you had twenty nodes, with each node moving five times during the simulation, you would have one hundred commands to put in the simulation. To address this problem, a utility called setdest was developed in c++. The utility has two versions. The first version had an issue where when it picked a random speed, it would be so small that a node may never reach its destination and not provide a true simulation. Setdest version 2 fixed this problem by providing the capability of adding a minimum speed along with some other features. Below is an example of a setdest version 2 command that sets the version to 2, the nodes as 6, the speed type as 1, the minimum speed as 1, the maximum speed of 10, the maximum time of 200, pause type of 1, and the coordinates of our simulation graph. In the command below, we use a standard unix redirect to store the output from STDOUT to the mob file: setdest -v2 -n 6 -s 1 -m 1 -M t 200 -P 1 -p 2.0 -x y 1000 > mob This mob file can them be sourced into a tcl script for NS simulation via the following commands: set opt(sc)./mob source $opt(sc) The sourcing of the mob file should be after the nodes are defined. There is a problem within the setdest program that we found that needs to be modified in order to get this to work. GOD shouldn t be declared as a variable in setdest, rather it should be referenced as a TCL class[1] so the below modifications had to be made: Original: #define GOD_FORMAT "$ns_ at %.12f \"$god_ set-dist %d %d %d\"\n" #define GOD_FORMAT2 "$god_ set-dist %d %d %d\n" Modified: #define GOD_FORMAT "$ns_ at %.12f \"God set-dist %d %d %d\"\n" #define GOD_FORMAT2 "God set-dist %d %d %d\n"
4 After these modifications were made, importing into the tcl script for NS2 simulation worked. However, even with the convenience that the setdest utility brings, the movement is rigid with the mobile nodes. One of the features we will add is an acceleration feature that shows a node accelerating from its current location to its waypoint and decelerating as it reaches its destination. An example of where this feature can be useful is if you have wireless sensors attached to ground vehicles that move around and take measurements of their environment, this simulation would show the acceleration and deceleration of those vehicles and simulate real movement. There are many other examples where this can be used. By default, NS2 doesn t inherently support acceleration and deceleration of nodes as they move with its sedest command. Our approach to implement this capability is to break a movement that is configured using setdest into several setdest commands so that we would get the behavior of as a node moves away from its origin, it does so at a slower speed, and once it hits a certain point in its path to its destination, that speed becomes constant, and as it approaches its destination, the speed decreases. For the increase and decrease, we will need to implement an approach where each setdest command that makes up each component slowly increases or decreases the speed. Experiment Setup and Plan To setup our experiment we will build from the lab 6 that we performed in our class. Our host machine will be an Ubuntu Virtual Machine running in VMware Player that has ns2 already installed on it and the source code for setdest. The host machine will be a Windows 7 machine. We will first observe the simulations without our modifications, and then start to implement our acceleration into the mobile node. The first step will be to manually input the commands into the mobility file for a given node before it is automated into the setdest utility. We will then run the network simulation and see if the node that we modified moves as expected. For this experiment, we will use a low number of network nodes. If we are pleased with the movement, we will then begin to automate it within setdest by creating an acceleration and deceleration formula. Subsequent tests will check the movement of the node and then tune the algorithm so that the movement is fluid and more realistic. Once we have the algorithm set, we will then parameterize the options into the algorithm by adding addition capabilities into setdest and allow a version 3. This will give the acceleration capability and other enhancements we may want to add in the future. Expected Results and Comments We expect that we can get acceleration and deceleration to work, however the primary concern is if the movement will appear to not be fluid in simulation since we are defining multiple setdest commands that may interfere with the fluidity of the movement from the origin to the destination. If this is something that other researches and students will find useful in ns2, the next step would be to allow it to be a core component within the ns2 where a setdest command would be modified so that an acceleration component can be modified into the simulation.
5 We also expect of getting the right formula for acceleration and deceleration to be a challenge as well. Some things to consider are the distance length, the top speed of the node, and how long it takes to accelerate and decelerate from the origin and to the destination. With this, we understand that depending on future enhancements, an acceleration/deceleration model may need to be imported into the network simulation as our acceleration/deceleration model will be very broad and can t be applied to each scenario. References [1] [ns] Setdest problem with $god_ (NS-2 v2.26) December/ html
Obstacle Avoidance Project: Final Report
 ERTS: Embedded & Real Time System Version: 0.0.1 Date: December 19, 2008 Purpose: A report on P545 project: Obstacle Avoidance. This document serves as report for P545 class project on obstacle avoidance
ERTS: Embedded & Real Time System Version: 0.0.1 Date: December 19, 2008 Purpose: A report on P545 project: Obstacle Avoidance. This document serves as report for P545 class project on obstacle avoidance
APPENDIX 1 SIMULATORS
 113 APPENDIX 1 SIMULATORS The Network Simulator-2 (NS-2) and Opportunistic Network Environment (ONE) Simulators are used for simulation purpose. Movement report of ONE generates suitable movement data
113 APPENDIX 1 SIMULATORS The Network Simulator-2 (NS-2) and Opportunistic Network Environment (ONE) Simulators are used for simulation purpose. Movement report of ONE generates suitable movement data
A NEW APPROACH FOR MOBILITY ENHANCEMENT OF OLSR PROTOCOL
 A NEW APPROACH FOR MOBILITY ENHANCEMENT OF OLSR PROTOCOL N. Lakki 1, A. Ouacha 1, A. Habbani 1, 2, M. AJANA EL KHADDAR 2, M. El Koutbi 2, J. El Abbadi 2 1 LEC Lab, MIS Team, EMI, University of Mohammed
A NEW APPROACH FOR MOBILITY ENHANCEMENT OF OLSR PROTOCOL N. Lakki 1, A. Ouacha 1, A. Habbani 1, 2, M. AJANA EL KHADDAR 2, M. El Koutbi 2, J. El Abbadi 2 1 LEC Lab, MIS Team, EMI, University of Mohammed
CHAPTER 5. Simulation Tools. be reconfigured and experimented with, usually this is impossible and too expensive or
 CHAPTER 5 Simulation Tools 5.1 Introduction A simulation of a system is the operation of a model of the system. The model can be reconfigured and experimented with, usually this is impossible and too expensive
CHAPTER 5 Simulation Tools 5.1 Introduction A simulation of a system is the operation of a model of the system. The model can be reconfigured and experimented with, usually this is impossible and too expensive
CHAPTER 4 SIMULATION MODEL AND PERFORMANCE METRICS
 59 CHAPTER 4 SIMULATION MODEL AND PERFORMANCE METRICS 4.1 OVERVIEW OF SIMULATION MODEL The performance of a MANET routing protocol under varying network conditions is to be evaluated in order to understand
59 CHAPTER 4 SIMULATION MODEL AND PERFORMANCE METRICS 4.1 OVERVIEW OF SIMULATION MODEL The performance of a MANET routing protocol under varying network conditions is to be evaluated in order to understand
STRAW - An integrated mobility & traffic model for vehicular ad-hoc networks
 STRAW - An integrated mobility & traffic model for vehicular ad-hoc networks David R. Choffnes & Fabián E. Bustamante Department of Computer Science, Northwestern University www.aqualab.cs.northwestern.edu
STRAW - An integrated mobility & traffic model for vehicular ad-hoc networks David R. Choffnes & Fabián E. Bustamante Department of Computer Science, Northwestern University www.aqualab.cs.northwestern.edu
Motion Detector. Lab Pro. Fig Lab Pro Interface. Motion Detector. Power Supply Basketball Ramp and Block Cart
 Experiment 2 Motion: Uniform and Non-Uniform Motion Detector Lab Pro Fig. 2-1 Equipment Lab Pro Interface Motion Detector Power Supply Basketball Ramp and Block Cart Advance Reading: Halliday, Resnick
Experiment 2 Motion: Uniform and Non-Uniform Motion Detector Lab Pro Fig. 2-1 Equipment Lab Pro Interface Motion Detector Power Supply Basketball Ramp and Block Cart Advance Reading: Halliday, Resnick
iracing Camera Tool Introduction Positioning the camera with Position Type
 iracing Camera Tool Introduction This is a brief introduction to the new camera tool built into the iracing simulator. You can enter the camera tool when in replay mode by hitting Ctrl-F12 at any time,
iracing Camera Tool Introduction This is a brief introduction to the new camera tool built into the iracing simulator. You can enter the camera tool when in replay mode by hitting Ctrl-F12 at any time,
Motorized Linear Slides. EZS Series SPF Series SPR Series SPV Series. EZS Series Without Electromagnetic Brake Stroke 300 mm
 Motorized Linear Slides EZS Series SPF Series SPR Series SPV Series EZS Series Without Electromagnetic Brake Stroke 0 mm 2 Overview Selection EZS Series SPF Series SPR Series SPV Series EZS/SPF/SPR/SPV
Motorized Linear Slides EZS Series SPF Series SPR Series SPV Series EZS Series Without Electromagnetic Brake Stroke 0 mm 2 Overview Selection EZS Series SPF Series SPR Series SPV Series EZS/SPF/SPR/SPV
Comparing ad-hoc wireless to wiredwireless
 TNK092: Network Simulation/Nätverkssimulering Network Simulation---ns2 Lecture 6 wired-wireless simulation Comparing ad-hoc wireless to wiredwireless We are going to make modifications to the tcl script
TNK092: Network Simulation/Nätverkssimulering Network Simulation---ns2 Lecture 6 wired-wireless simulation Comparing ad-hoc wireless to wiredwireless We are going to make modifications to the tcl script
An Analysis of Simulators for Vehicular Ad hoc Networks
 World Applied Sciences Journal 23 (8): 1044-1048, 2013 ISSN 1818-4952 IDOSI Publications, 2013 DOI: 10.5829/idosi.wasj.2013.23.08.584 An Analysis of Simulators for Vehicular Ad hoc Networks Syed A. Hussain
World Applied Sciences Journal 23 (8): 1044-1048, 2013 ISSN 1818-4952 IDOSI Publications, 2013 DOI: 10.5829/idosi.wasj.2013.23.08.584 An Analysis of Simulators for Vehicular Ad hoc Networks Syed A. Hussain
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
Installing VMware Player to Run Ubuntu Linux on a Windows Machine
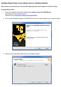 Installing VMware Player to Run Ubuntu Linux on a Windows Machine Check that you are connected to the internet before beginning (open Internet Explorer or Firefox or similar). Installing VMware Player
Installing VMware Player to Run Ubuntu Linux on a Windows Machine Check that you are connected to the internet before beginning (open Internet Explorer or Firefox or similar). Installing VMware Player
Routing Protocols in MANETs
 Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Study on Indoor and Outdoor environment for Mobile Ad Hoc Network: Random Way point Mobility Model and Manhattan Mobility Model
 Study on and Outdoor for Mobile Ad Hoc Network: Random Way point Mobility Model and Manhattan Mobility Model Ibrahim khider,prof.wangfurong.prof.yinweihua,sacko Ibrahim khider, Communication Software and
Study on and Outdoor for Mobile Ad Hoc Network: Random Way point Mobility Model and Manhattan Mobility Model Ibrahim khider,prof.wangfurong.prof.yinweihua,sacko Ibrahim khider, Communication Software and
SUMMERY, CONCLUSIONS AND FUTURE WORK
 Chapter - 6 SUMMERY, CONCLUSIONS AND FUTURE WORK The entire Research Work on On-Demand Routing in Multi-Hop Wireless Mobile Ad hoc Networks has been presented in simplified and easy-to-read form in six
Chapter - 6 SUMMERY, CONCLUSIONS AND FUTURE WORK The entire Research Work on On-Demand Routing in Multi-Hop Wireless Mobile Ad hoc Networks has been presented in simplified and easy-to-read form in six
Since a projectile moves in 2-dimensions, it therefore has 2 components just like a resultant vector: Horizontal Vertical
 Since a projectile moves in 2-dimensions, it therefore has 2 components just like a resultant vector: Horizontal Vertical With no gravity the projectile would follow the straight-line path (dashed line).
Since a projectile moves in 2-dimensions, it therefore has 2 components just like a resultant vector: Horizontal Vertical With no gravity the projectile would follow the straight-line path (dashed line).
LECTURE 11. Memory Hierarchy
 LECTURE 11 Memory Hierarchy MEMORY HIERARCHY When it comes to memory, there are two universally desirable properties: Large Size: ideally, we want to never have to worry about running out of memory. Speed
LECTURE 11 Memory Hierarchy MEMORY HIERARCHY When it comes to memory, there are two universally desirable properties: Large Size: ideally, we want to never have to worry about running out of memory. Speed
Math Learning Center Boise State 2010, Quadratic Modeling STEM 10
 Quadratic Modeling STEM 10 Today we are going to put together an understanding of the two physics equations we have been using. Distance: Height : Recall the variables: o acceleration o gravitation force
Quadratic Modeling STEM 10 Today we are going to put together an understanding of the two physics equations we have been using. Distance: Height : Recall the variables: o acceleration o gravitation force
9/10/2016. Time for Some Detailed Examples. ECE 120: Introduction to Computing. Let s See How This Loop Works. One Statement/Step at a Time
 University of Illinois at Urbana-Champaign Dept. of Electrical and Computer Engineering ECE 120: Introduction to Computing Examples of C Programs with Loops Time for Some Detailed Examples Let s do some
University of Illinois at Urbana-Champaign Dept. of Electrical and Computer Engineering ECE 120: Introduction to Computing Examples of C Programs with Loops Time for Some Detailed Examples Let s do some
6.3 Creating and Comparing Quadratics
 6.3 Creating and Comparing Quadratics Just like with exponentials and linear functions, to be able to compare quadratics, we ll need to be able to create equation forms of the quadratic functions. Let
6.3 Creating and Comparing Quadratics Just like with exponentials and linear functions, to be able to compare quadratics, we ll need to be able to create equation forms of the quadratic functions. Let
CSCI 1100L: Topics in Computing Lab Lab 11: Programming with Scratch
 CSCI 1100L: Topics in Computing Lab Lab 11: Programming with Scratch Purpose: We will take a look at programming this week using a language called Scratch. Scratch is a programming language that was developed
CSCI 1100L: Topics in Computing Lab Lab 11: Programming with Scratch Purpose: We will take a look at programming this week using a language called Scratch. Scratch is a programming language that was developed
Peer-To-Peer Network!
 Computer Networks! Introduction. I've been asked to create a PowerPoint on two different kinds of computer networks to be able to discuss the strengths and weaknesses of both. In this PowerPoint I will
Computer Networks! Introduction. I've been asked to create a PowerPoint on two different kinds of computer networks to be able to discuss the strengths and weaknesses of both. In this PowerPoint I will
Adaptive Cruise Control
 Teacher Notes & Answers 7 8 9 10 11 12 TI-Nspire Investigation Student 50 min Introduction Basic cruise control is where the car s computer automatically adjusts the throttle so that the car maintains
Teacher Notes & Answers 7 8 9 10 11 12 TI-Nspire Investigation Student 50 min Introduction Basic cruise control is where the car s computer automatically adjusts the throttle so that the car maintains
Effects of Sensor Nodes Mobility on Routing Energy Consumption Level and Performance of Wireless Sensor Networks
 Effects of Sensor Nodes Mobility on Routing Energy Consumption Level and Performance of Wireless Sensor Networks Mina Malekzadeh Golestan University Zohre Fereidooni Golestan University M.H. Shahrokh Abadi
Effects of Sensor Nodes Mobility on Routing Energy Consumption Level and Performance of Wireless Sensor Networks Mina Malekzadeh Golestan University Zohre Fereidooni Golestan University M.H. Shahrokh Abadi
Exercise Effect of Fractures on Groundwater Flow Patterns Context: Goal:
 Exercise Effect of Fractures on Groundwater Flow Patterns Maureen Muldoon UW-Oshkosh Dept of Geology 800 Algoma Blvd. Oshkosh, WI 54901 920-424-4461 muldoon@uwosh.edu Context: This activity was developed
Exercise Effect of Fractures on Groundwater Flow Patterns Maureen Muldoon UW-Oshkosh Dept of Geology 800 Algoma Blvd. Oshkosh, WI 54901 920-424-4461 muldoon@uwosh.edu Context: This activity was developed
Bash Programming. Student Workbook
 Student Workbook Bash Programming Published by ITCourseware, LLC, 7245 South Havana Street, Suite 100, Englewood, CO 80112 Contributing Authors: Julie Johnson, Rob Roselius Editor: Jeff Howell Special
Student Workbook Bash Programming Published by ITCourseware, LLC, 7245 South Havana Street, Suite 100, Englewood, CO 80112 Contributing Authors: Julie Johnson, Rob Roselius Editor: Jeff Howell Special
AN INTRODUCTION TO SCRATCH (2) PROGRAMMING
 AN INTRODUCTION TO SCRATCH (2) PROGRAMMING Document Version 2 (04/10/2014) INTRODUCTION SCRATCH is a visual programming environment and language. It was launched by the MIT Media Lab in 2007 in an effort
AN INTRODUCTION TO SCRATCH (2) PROGRAMMING Document Version 2 (04/10/2014) INTRODUCTION SCRATCH is a visual programming environment and language. It was launched by the MIT Media Lab in 2007 in an effort
Analysis of Routing Protocols in MANETs
 Analysis of Routing Protocols in MANETs Musica Supriya, Rashmi, Nishchitha, Ashwini C Shetty, Sharath Kumar Student, Dept. of CSE, SMVITM Bantakal, Karnataka, India Student, Dept. of CSE, SMVITM Bantakal,
Analysis of Routing Protocols in MANETs Musica Supriya, Rashmi, Nishchitha, Ashwini C Shetty, Sharath Kumar Student, Dept. of CSE, SMVITM Bantakal, Karnataka, India Student, Dept. of CSE, SMVITM Bantakal,
Amir Herzberg and Ronen Margulies Dept. of Computer Science Bar Ilan University
 Amir Herzberg and Ronen Margulies Dept. of Computer Science Bar Ilan University 1 Agenda Conflicts in usable security studies Introducing the Experiment, or: how to balance the risk level Ethical Attacks
Amir Herzberg and Ronen Margulies Dept. of Computer Science Bar Ilan University 1 Agenda Conflicts in usable security studies Introducing the Experiment, or: how to balance the risk level Ethical Attacks
Redundancy for Corporate Broadband WHITE PAPER
 Redundancy for Corporate Broadband WHITE PAPER Introduction Over the past twenty years, broadband service providers have been using different mediums to deliver their services. From wireless to wired (fiber,
Redundancy for Corporate Broadband WHITE PAPER Introduction Over the past twenty years, broadband service providers have been using different mediums to deliver their services. From wireless to wired (fiber,
Conveyor Belt Instructions
 Conveyor Belt Instructions AN01010101 V1.11 Date: 2017/08/09 Shenzhen Yuejiang Technology Co.,Ltd Revised History Version Date Reason V1.10 2017/05/16 Create a document V1.11 2017/08/09 Update the information
Conveyor Belt Instructions AN01010101 V1.11 Date: 2017/08/09 Shenzhen Yuejiang Technology Co.,Ltd Revised History Version Date Reason V1.10 2017/05/16 Create a document V1.11 2017/08/09 Update the information
Performance Evaluation of Routing Protocols for Mobile Ad Hoc Networks
 2013, TextRoad Publication ISSN 2090-4304 Journal of Basic and Applied Scientific Research www.textroad.com Performance Evaluation of Routing Protocols for Mobile Ad Hoc Networks Hina Tariq 1, Urfa Suhaib
2013, TextRoad Publication ISSN 2090-4304 Journal of Basic and Applied Scientific Research www.textroad.com Performance Evaluation of Routing Protocols for Mobile Ad Hoc Networks Hina Tariq 1, Urfa Suhaib
Definition: A data structure is a way of organizing data in a computer so that it can be used efficiently.
 The Science of Computing I Lesson 4: Introduction to Data Structures Living with Cyber Pillar: Data Structures The need for data structures The algorithms we design to solve problems rarely do so without
The Science of Computing I Lesson 4: Introduction to Data Structures Living with Cyber Pillar: Data Structures The need for data structures The algorithms we design to solve problems rarely do so without
ARTIFICIAL INTELLIGENCE: SITUATIONAL AWARENESS
 ARTIFICIAL INTELLIGENCE: SITUATIONAL AWARENESS So first of all before we start, we have to ask our self: What s is situational awareness exactly. A Quick google search reveals that: WHAT IS SITUATIONAL
ARTIFICIAL INTELLIGENCE: SITUATIONAL AWARENESS So first of all before we start, we have to ask our self: What s is situational awareness exactly. A Quick google search reveals that: WHAT IS SITUATIONAL
IHE NA Connectathon 2018: Network
 1 IHE NA Connectathon 2018: Network Revisions 2017-11-30: First release Network Sharing Rules Below are what I hope are simple rules that will allow our group to share the wired and wireless networks.
1 IHE NA Connectathon 2018: Network Revisions 2017-11-30: First release Network Sharing Rules Below are what I hope are simple rules that will allow our group to share the wired and wireless networks.
Aircraft Smooth Motion Controls with Intel Perceptual Computing SDK. Cédric Andreolli - Intel
 Aircraft Smooth Motion Controls with Intel Perceptual Computing SDK Cédric Andreolli - Intel 1 Contents 1 Introduction... 3 2 Playing with the aircraft orientation... 4 2.1 The forces in our game... 4
Aircraft Smooth Motion Controls with Intel Perceptual Computing SDK Cédric Andreolli - Intel 1 Contents 1 Introduction... 3 2 Playing with the aircraft orientation... 4 2.1 The forces in our game... 4
Chapter-4. Simulation Design and Implementation
 Chapter-4 Simulation Design and Implementation In this chapter, the design parameters of system and the various metrics measured for performance evaluation of the routing protocols are presented. An overview
Chapter-4 Simulation Design and Implementation In this chapter, the design parameters of system and the various metrics measured for performance evaluation of the routing protocols are presented. An overview
!! What is virtual memory and when is it useful? !! What is demand paging? !! When should pages in memory be replaced?
 Chapter 10: Virtual Memory Questions? CSCI [4 6] 730 Operating Systems Virtual Memory!! What is virtual memory and when is it useful?!! What is demand paging?!! When should pages in memory be replaced?!!
Chapter 10: Virtual Memory Questions? CSCI [4 6] 730 Operating Systems Virtual Memory!! What is virtual memory and when is it useful?!! What is demand paging?!! When should pages in memory be replaced?!!
Xkitz.com. 8 Channel Capacitive Touch Switch Model XCTS-8M. Operators Manual. Invisible Touch Switch:
 8 Channel Capacitive Touch Switch Model XCTS-8M Operators Manual Xkitz.com Invisible Touch Switch: The XCTS-8M allows you to install up to 8 capacitive touch switches nearly anywhere. It detects any sudden
8 Channel Capacitive Touch Switch Model XCTS-8M Operators Manual Xkitz.com Invisible Touch Switch: The XCTS-8M allows you to install up to 8 capacitive touch switches nearly anywhere. It detects any sudden
Topic 7 Machine learning
 CSE 103: Probability and statistics Winter 2010 Topic 7 Machine learning 7.1 Nearest neighbor classification 7.1.1 Digit recognition Countless pieces of mail pass through the postal service daily. A key
CSE 103: Probability and statistics Winter 2010 Topic 7 Machine learning 7.1 Nearest neighbor classification 7.1.1 Digit recognition Countless pieces of mail pass through the postal service daily. A key
Analyzing Systems. Steven M. Bellovin November 26,
 Analyzing Systems When presented with a system, how do you know it s secure? Often, you re called upon to analyze a system you didn t design application architects and programmers build it; security people
Analyzing Systems When presented with a system, how do you know it s secure? Often, you re called upon to analyze a system you didn t design application architects and programmers build it; security people
Ordering through Gateway for MCDB Labs
 Ordering through Gateway for MCDB Labs Gateway is the purchasing application used for ordering at UCSB. It is rather complex, and aspects of it can be confusing and mystifying. This document is an attempt
Ordering through Gateway for MCDB Labs Gateway is the purchasing application used for ordering at UCSB. It is rather complex, and aspects of it can be confusing and mystifying. This document is an attempt
Performance Analysis of Wireless Mobile ad Hoc Network with Varying Transmission Power
 , pp.1-6 http://dx.doi.org/10.14257/ijsacs.2015.3.1.01 Performance Analysis of Wireless Mobile ad Hoc Network with Varying Transmission Power Surabhi Shrivastava, Laxmi Shrivastava and Sarita Singh Bhadauria
, pp.1-6 http://dx.doi.org/10.14257/ijsacs.2015.3.1.01 Performance Analysis of Wireless Mobile ad Hoc Network with Varying Transmission Power Surabhi Shrivastava, Laxmi Shrivastava and Sarita Singh Bhadauria
Administrivia. Added 20 more so far. Software Process. Only one TA so far. CS169 Lecture 2. Start thinking about project proposal
 Administrivia Software Process CS169 Lecture 2 Added 20 more so far Will limit enrollment to ~65 students Only one TA so far Start thinking about project proposal Bonus points for proposals that will be
Administrivia Software Process CS169 Lecture 2 Added 20 more so far Will limit enrollment to ~65 students Only one TA so far Start thinking about project proposal Bonus points for proposals that will be
State of the Art Sensing: 132 AD
 Sensors in Design 2012: Sensor Communications in Harsh Environments Class Number SID-401 Mike Fahrion B&B Electronics State of the Art Sensing: 132 AD And today Image sensor Capacitive touch screen GPS
Sensors in Design 2012: Sensor Communications in Harsh Environments Class Number SID-401 Mike Fahrion B&B Electronics State of the Art Sensing: 132 AD And today Image sensor Capacitive touch screen GPS
Impact of Node Velocity and Density on Probabilistic Flooding and its Effectiveness in MANET
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Goal: Conduct simple numerical experiments to gain a better understanding of the effect of fractures on groundwater flow patterns.
 Exercise Effect of Fractures on Groundwater Flow Patterns Maureen Muldoon UW-Oshkosh Dept of Geology 800 Algoma Blvd. Oshkosh, WI 54901 920-424-4461 muldoon@uwosh.edu Context: This activity was developed
Exercise Effect of Fractures on Groundwater Flow Patterns Maureen Muldoon UW-Oshkosh Dept of Geology 800 Algoma Blvd. Oshkosh, WI 54901 920-424-4461 muldoon@uwosh.edu Context: This activity was developed
WT1800 PRECISION POWER ANALYZER
 PRECISION POWER ANALYZER Page 1 Page 2 PRODUCT TUTORIAL Table of Contents: A.) Overview & Objectives... B.) Power Meter Connections.. C.) Basic Setup for Power Measurement Initialize Settings Setting Wiring
PRECISION POWER ANALYZER Page 1 Page 2 PRODUCT TUTORIAL Table of Contents: A.) Overview & Objectives... B.) Power Meter Connections.. C.) Basic Setup for Power Measurement Initialize Settings Setting Wiring
CS 31: Intro to Systems Caching. Martin Gagne Swarthmore College March 23, 2017
 CS 1: Intro to Systems Caching Martin Gagne Swarthmore College March 2, 2017 Recall A cache is a smaller, faster memory, that holds a subset of a larger (slower) memory We take advantage of locality to
CS 1: Intro to Systems Caching Martin Gagne Swarthmore College March 2, 2017 Recall A cache is a smaller, faster memory, that holds a subset of a larger (slower) memory We take advantage of locality to
Graph Matching. walk back and forth in front of Motion Detector
 Graph Matching Experiment 1 One of the most effective methods of describing motion is to plot graphs of distance, velocity, and acceleration vs. time. From such a graphical representation, it is possible
Graph Matching Experiment 1 One of the most effective methods of describing motion is to plot graphs of distance, velocity, and acceleration vs. time. From such a graphical representation, it is possible
Wireless sensor networks simulators computer simulation tools
 International Conference on Applied Internet and Information Technologies, 2016 DOI:10.20544/AIIT2016.24 Wireless sensor networks simulators computer simulation tools Igor Georgioski and Hristina Trenchevska
International Conference on Applied Internet and Information Technologies, 2016 DOI:10.20544/AIIT2016.24 Wireless sensor networks simulators computer simulation tools Igor Georgioski and Hristina Trenchevska
One Dimensional Motion (Part I and Part II)
 One Dimensional Motion (Part I and Part II) Purpose:To understand the relationship between displacement (position), motion (velocity), and change in motion (acceleration). Topics of PART I and PART II:
One Dimensional Motion (Part I and Part II) Purpose:To understand the relationship between displacement (position), motion (velocity), and change in motion (acceleration). Topics of PART I and PART II:
POLITECNICO DI TORINO Repository ISTITUZIONALE
 POLITECNICO DI TORINO Repository ISTITUZIONALE Comparative Performance Simulation of DSDV, AODV and DSR MANET Protocols in NS2 Original Comparative Performance Simulation of DSDV, AODV and DSR MANET Protocols
POLITECNICO DI TORINO Repository ISTITUZIONALE Comparative Performance Simulation of DSDV, AODV and DSR MANET Protocols in NS2 Original Comparative Performance Simulation of DSDV, AODV and DSR MANET Protocols
Lecture 1: January 23
 CMPSCI 677 Distributed and Operating Systems Spring 2019 Lecture 1: January 23 Lecturer: Prashant Shenoy Scribe: Jonathan Westin (2019), Bin Wang (2018) 1.1 Introduction to the course The lecture started
CMPSCI 677 Distributed and Operating Systems Spring 2019 Lecture 1: January 23 Lecturer: Prashant Shenoy Scribe: Jonathan Westin (2019), Bin Wang (2018) 1.1 Introduction to the course The lecture started
CS 378: Computer Game Technology
 CS 378: Computer Game Technology Dynamic Path Planning, Flocking Spring 2012 University of Texas at Austin CS 378 Game Technology Don Fussell Dynamic Path Planning! What happens when the environment changes
CS 378: Computer Game Technology Dynamic Path Planning, Flocking Spring 2012 University of Texas at Austin CS 378 Game Technology Don Fussell Dynamic Path Planning! What happens when the environment changes
OpenStack Havana All-in-One lab on VMware Workstation
 OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
µtasker Document CodeWarrior 10
 Embedding it better... µtasker Document CodeWarrior 10 utasker_codewarrior10.doc/0.0 Copyright 2012 M.J.Butcher Consulting Table of Contents 1. Introduction...3 2. Importing the Project into a Workspace...4
Embedding it better... µtasker Document CodeWarrior 10 utasker_codewarrior10.doc/0.0 Copyright 2012 M.J.Butcher Consulting Table of Contents 1. Introduction...3 2. Importing the Project into a Workspace...4
Simulation and Analysis of Opportunistic Routing Protocols
 Simulation and Analysis of Opportunistic Routing Protocols 1 The Purpose The purpose of this assignment is to gain familiarity with a network simulation tool and to get experience in basic data analysis.
Simulation and Analysis of Opportunistic Routing Protocols 1 The Purpose The purpose of this assignment is to gain familiarity with a network simulation tool and to get experience in basic data analysis.
Wireshark Lab: Getting Started v7.0
 Wireshark Lab: Getting Started v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Wireshark Lab: Getting Started v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
OPERATIONS MANUAL ACL 350 DIGITAL STATIC LOCATOR
 OPERATIONS MANUAL ACL 350 DIGITAL STATIC LOCATOR ACL 350 DIGITAL STATIC LOCATOR OPERATIONS MANUAL TABLE OF CONTENTS Title Page No. BEFORE USING THE INSTRUMENT... ACL 350 Page 2 SAFETY... ACL 350 Page 2
OPERATIONS MANUAL ACL 350 DIGITAL STATIC LOCATOR ACL 350 DIGITAL STATIC LOCATOR OPERATIONS MANUAL TABLE OF CONTENTS Title Page No. BEFORE USING THE INSTRUMENT... ACL 350 Page 2 SAFETY... ACL 350 Page 2
Getting to know your Cronus device
 Getting to know your Cronus device 1. INPUT (USB Receptacle Type A) Connector for wired game controllers or wireless receivers. 2. OUTPUT (USB Plug Type A) To connect the Cronus device on game consoles
Getting to know your Cronus device 1. INPUT (USB Receptacle Type A) Connector for wired game controllers or wireless receivers. 2. OUTPUT (USB Plug Type A) To connect the Cronus device on game consoles
COURSE PLAN COMPUTER INFORMATION TECHNOLOGY
 COURSE PLAN COMPUTER INFORMATION TECHNOLOGY CIT132: LINUX / UNIX OPERATING SYSTEM CONTENT INSTRUCTOR S DETAILS 1 COURSE SCHEDULE 1 SYNOPSIS 2 LEARNING OUTCOMES 2 COURSE OUTLINE 2 WEEKLY PLAN 3 ASSESSMENT
COURSE PLAN COMPUTER INFORMATION TECHNOLOGY CIT132: LINUX / UNIX OPERATING SYSTEM CONTENT INSTRUCTOR S DETAILS 1 COURSE SCHEDULE 1 SYNOPSIS 2 LEARNING OUTCOMES 2 COURSE OUTLINE 2 WEEKLY PLAN 3 ASSESSMENT
State of the Art Sensing: 132 A.D.
 State of the Art Sensing: 132 A.D. And today Image sensor Capacitive touch screen GPS Compass Proximity sensor Light sensor 3 axis accelerometer Gyroscopic sensor GPIO WWAN WLAN WPAN The Point? The ways
State of the Art Sensing: 132 A.D. And today Image sensor Capacitive touch screen GPS Compass Proximity sensor Light sensor 3 axis accelerometer Gyroscopic sensor GPIO WWAN WLAN WPAN The Point? The ways
Synthesis and APR Tools Tutorial
 Synthesis and APR Tools Tutorial (Last updated: Oct. 26, 2008) Introduction This tutorial will get you familiarized with the design flow of synthesizing and place and routing a Verilog module. All the
Synthesis and APR Tools Tutorial (Last updated: Oct. 26, 2008) Introduction This tutorial will get you familiarized with the design flow of synthesizing and place and routing a Verilog module. All the
EEN118 LAB FOUR. h = v t ½ g t 2
 EEN118 LAB FOUR In this lab you will be performing a simulation of a physical system, shooting a projectile from a cannon and working out where it will land. Although this is not a very complicated physical
EEN118 LAB FOUR In this lab you will be performing a simulation of a physical system, shooting a projectile from a cannon and working out where it will land. Although this is not a very complicated physical
22-Sep CSCI 2132 Software Development Lecture 8: Shells, Processes, and Job Control. Faculty of Computer Science, Dalhousie University
 Lecture 8 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lecture 8: Shells, Processes, and Job Control 22-Sep-2017 Location: Goldberg CS 127 Time: 14:35 15:25 Instructor:
Lecture 8 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lecture 8: Shells, Processes, and Job Control 22-Sep-2017 Location: Goldberg CS 127 Time: 14:35 15:25 Instructor:
Fill er Up: Winners and Losers for Filling an Ordered Container
 Fill er Up: Winners and Losers for Filling an Ordered Container David Kieras & Steve Plaza, EECS Department, University of Michigan A handy and common component is an ordered container, one that contains
Fill er Up: Winners and Losers for Filling an Ordered Container David Kieras & Steve Plaza, EECS Department, University of Michigan A handy and common component is an ordered container, one that contains
Fireplace Mantel in Google SketchUp
 Creating the fireplace itself is quite easy: it s just a box with a hole. But creating the mantel around the top requires the fun-to-use Follow Me tool. This project was created in SketchUp 8, but will
Creating the fireplace itself is quite easy: it s just a box with a hole. But creating the mantel around the top requires the fun-to-use Follow Me tool. This project was created in SketchUp 8, but will
Robotics II. Module 1: Introduction to Data & Advanced Programming Blocks
 Robotics II Module 1: Introduction to Data & Advanced Programming Blocks PREPARED BY Academic Services Unit December 2011 Applied Technology High Schools, 2011 Module 1: Introduction to Data & Advanced
Robotics II Module 1: Introduction to Data & Advanced Programming Blocks PREPARED BY Academic Services Unit December 2011 Applied Technology High Schools, 2011 Module 1: Introduction to Data & Advanced
Enabling Apple AirPrint with Your Xerox AltaLink Multifunction Printer. White Paper
 Enabling Apple AirPrint with Your Xerox AltaLink Multifunction Printer White Paper Contents 3 Background 3 AirPrint Basics Step 1: Device Discovery Apple Bonjour 3 Step 2: Device Information and Status
Enabling Apple AirPrint with Your Xerox AltaLink Multifunction Printer White Paper Contents 3 Background 3 AirPrint Basics Step 1: Device Discovery Apple Bonjour 3 Step 2: Device Information and Status
CS 31: Intro to Systems Caching. Kevin Webb Swarthmore College March 24, 2015
 CS 3: Intro to Systems Caching Kevin Webb Swarthmore College March 24, 205 Reading Quiz Abstraction Goal Reality: There is no one type of memory to rule them all! Abstraction: hide the complex/undesirable
CS 3: Intro to Systems Caching Kevin Webb Swarthmore College March 24, 205 Reading Quiz Abstraction Goal Reality: There is no one type of memory to rule them all! Abstraction: hide the complex/undesirable
User Manual for the Time-variant Community Mobility Model
 User Manual for the Time-variant Community Mobility Model Release Version: TVCM-1.1-beta Release Date: May 31, 2007 Authors: Wei-jen Hsu, Dept. of Computer and Information Science and Engineering, U. of
User Manual for the Time-variant Community Mobility Model Release Version: TVCM-1.1-beta Release Date: May 31, 2007 Authors: Wei-jen Hsu, Dept. of Computer and Information Science and Engineering, U. of
Study Guide Processes & Job Control
 Study Guide Processes & Job Control Q1 - PID What does PID stand for? Q2 - Shell PID What shell command would I issue to display the PID of the shell I'm using? Q3 - Process vs. executable file Explain,
Study Guide Processes & Job Control Q1 - PID What does PID stand for? Q2 - Shell PID What shell command would I issue to display the PID of the shell I'm using? Q3 - Process vs. executable file Explain,
My Mediasite Guide (V7.2) Create and Share Videos from Your Desktop
 My Mediasite Guide (V7.2) Create and Share Videos from Your Desktop Introduction: Your My Mediasite Portal provides instructors access to the Mediasite desktop Recorder (MDR) for creation of presentations
My Mediasite Guide (V7.2) Create and Share Videos from Your Desktop Introduction: Your My Mediasite Portal provides instructors access to the Mediasite desktop Recorder (MDR) for creation of presentations
Installing and Configuring
 Installing and Configuring Advanced Hardware Setups Introduction For most community wireless networks, installing a few rooftop and window nodes will fit the needs of the neighborhood or town. For others,
Installing and Configuring Advanced Hardware Setups Introduction For most community wireless networks, installing a few rooftop and window nodes will fit the needs of the neighborhood or town. For others,
Last time. Security Policies and Models. Trusted Operating System Design. Bell La-Padula and Biba Security Models Information Flow Control
 Last time Security Policies and Models Bell La-Padula and Biba Security Models Information Flow Control Trusted Operating System Design Design Elements Security Features 10-1 This time Trusted Operating
Last time Security Policies and Models Bell La-Padula and Biba Security Models Information Flow Control Trusted Operating System Design Design Elements Security Features 10-1 This time Trusted Operating
Support reference for common LogicalLABs questions and issues.
 Support reference for common LogicalLABs questions and issues. Ensure all systems meet minimum technical specifications: Microsoft Windows 7 or higher. Microsoft Internet Explorer 11.0 or higher. Monitor:
Support reference for common LogicalLABs questions and issues. Ensure all systems meet minimum technical specifications: Microsoft Windows 7 or higher. Microsoft Internet Explorer 11.0 or higher. Monitor:
Random Walks and Cover Times. Project Report. Aravind Ranganathan. ECES 728 Internet Studies and Web Algorithms
 Random Walks and Cover Times Project Report Aravind Ranganathan ECES 728 Internet Studies and Web Algorithms 1. Objectives: We consider random walk based broadcast-like operation in random networks. First,
Random Walks and Cover Times Project Report Aravind Ranganathan ECES 728 Internet Studies and Web Algorithms 1. Objectives: We consider random walk based broadcast-like operation in random networks. First,
Robotics II. Module 5: Creating Custom Made Blocks (My Blocks)
 Robotics II Module 5: Creating Custom Made Blocks (My Blocks) PREPARED BY Academic Services Unit December 2011 Applied Technology High Schools, 2011 Module 5: Creating Custom Made Blocks (My Blocks) Module
Robotics II Module 5: Creating Custom Made Blocks (My Blocks) PREPARED BY Academic Services Unit December 2011 Applied Technology High Schools, 2011 Module 5: Creating Custom Made Blocks (My Blocks) Module
ECE 463/521: Fall 2002 Project #1: Data-Cache System Design Due: Monday, Sept. 30, 11:00 PM
 ECE 463/521: Fall 2002 Project #1: Data-Cache System Design Due: Monday, Sept. 30, 11:00 PM Project rules 1. All students are encouraged to work in teams of two, using pair programming. Pair programming
ECE 463/521: Fall 2002 Project #1: Data-Cache System Design Due: Monday, Sept. 30, 11:00 PM Project rules 1. All students are encouraged to work in teams of two, using pair programming. Pair programming
Data Acquisition Instructions
 Page 1 of 26 Form DAQ2_A 01/23/2007 Superchips Inc. Superchips flashpaq Data Acquisition Instructions Visit Flashpaq.com for downloadable updates & upgrades to your existing tuner. Page 2 of 26 Form DAQ2_A
Page 1 of 26 Form DAQ2_A 01/23/2007 Superchips Inc. Superchips flashpaq Data Acquisition Instructions Visit Flashpaq.com for downloadable updates & upgrades to your existing tuner. Page 2 of 26 Form DAQ2_A
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades Q2
 Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
On the Scalability of Hierarchical Ad Hoc Wireless Networks
 On the Scalability of Hierarchical Ad Hoc Wireless Networks Suli Zhao and Dipankar Raychaudhuri Fall 2006 IAB 11/15/2006 Outline Motivation Ad hoc wireless network architecture Three-tier hierarchical
On the Scalability of Hierarchical Ad Hoc Wireless Networks Suli Zhao and Dipankar Raychaudhuri Fall 2006 IAB 11/15/2006 Outline Motivation Ad hoc wireless network architecture Three-tier hierarchical
Add in a new balloon sprite, and a suitable stage backdrop.
 Balloons Introduction You are going to make a balloon-popping game! Step 1: Animating a balloon Activity Checklist Start a new Scratch project, and delete the cat sprite so that your project is empty.
Balloons Introduction You are going to make a balloon-popping game! Step 1: Animating a balloon Activity Checklist Start a new Scratch project, and delete the cat sprite so that your project is empty.
Micro Focus Desktop Containers
 White Paper Security Micro Focus Desktop Containers Whether it s extending the life of your legacy applications, making applications more accessible, or simplifying your application deployment and management,
White Paper Security Micro Focus Desktop Containers Whether it s extending the life of your legacy applications, making applications more accessible, or simplifying your application deployment and management,
Virtualization. Q&A with an industry leader. Virtualization is rapidly becoming a fact of life for agency executives,
 Virtualization Q&A with an industry leader Virtualization is rapidly becoming a fact of life for agency executives, as the basis for data center consolidation and cloud computing and, increasingly, as
Virtualization Q&A with an industry leader Virtualization is rapidly becoming a fact of life for agency executives, as the basis for data center consolidation and cloud computing and, increasingly, as
Animator Friendly Rigging Part 1
 Animator Friendly Rigging Part 1 Creating animation rigs which solve problems, are fun to use, and don t cause nervous breakdowns. - http://jasonschleifer.com/ - 1- CONTENTS I. INTRODUCTION... 4 What is
Animator Friendly Rigging Part 1 Creating animation rigs which solve problems, are fun to use, and don t cause nervous breakdowns. - http://jasonschleifer.com/ - 1- CONTENTS I. INTRODUCTION... 4 What is
Wireless Network Capacity. Nitin Vaidya
 Wireless Network Capacity Nitin Vaidya 2009 1 Wireless Networks Why use multi-hop routes to delivery data? Is this optimal? What s the best performance achievable? Capacity analysis can help answer such
Wireless Network Capacity Nitin Vaidya 2009 1 Wireless Networks Why use multi-hop routes to delivery data? Is this optimal? What s the best performance achievable? Capacity analysis can help answer such
Using Handbrake to Reformat DVD Clips
 While copying or ripping DVDs has negative connotations, academics engaged in the critique of media often reformat portions of DVD video to an easily editable format they then use this footage to highlight
While copying or ripping DVDs has negative connotations, academics engaged in the critique of media often reformat portions of DVD video to an easily editable format they then use this footage to highlight
CSE 461: Bridging LANs. Last Topic
 CSE 461: Bridging LANs Last Topic Medium Access Control (MAC) protocols Part of the Link Layer At the heart of Local Area Networks (LANs) How do multiple parties share a wire or the air? Random access
CSE 461: Bridging LANs Last Topic Medium Access Control (MAC) protocols Part of the Link Layer At the heart of Local Area Networks (LANs) How do multiple parties share a wire or the air? Random access
Simulation and Analysis of AODV and DSDV Routing Protocols in Vehicular Adhoc Networks using Random Waypoint Mobility Model
 Simulation and Analysis of AODV and DSDV Routing Protocols in Vehicular Adhoc Networks using Random Waypoint Mobility Model 1 R. Jeevitha, 2 M. Chandra Kumar 1 Research Scholar, Department of Computer
Simulation and Analysis of AODV and DSDV Routing Protocols in Vehicular Adhoc Networks using Random Waypoint Mobility Model 1 R. Jeevitha, 2 M. Chandra Kumar 1 Research Scholar, Department of Computer
NETWORK SECURITY. Ch. 3: Network Attacks
 NETWORK SECURITY Ch. 3: Network Attacks Contents 3.1 Network Vulnerabilities 3.1.1 Media-Based 3.1.2 Network Device 3.2 Categories of Attacks 3.3 Methods of Network Attacks 03 NETWORK ATTACKS 2 3.1 Network
NETWORK SECURITY Ch. 3: Network Attacks Contents 3.1 Network Vulnerabilities 3.1.1 Media-Based 3.1.2 Network Device 3.2 Categories of Attacks 3.3 Methods of Network Attacks 03 NETWORK ATTACKS 2 3.1 Network
When the player powers up you will first see a CeeNee loading screen followed by the Orchid screen seen below.
 How to setup the CeeNee Orchid Player using a wired Ethernet connection? 1) Carefully insert the supplied SD card into the front of the CeeNee player. It will go in around a 1/2 inch and stop. 2) Connect
How to setup the CeeNee Orchid Player using a wired Ethernet connection? 1) Carefully insert the supplied SD card into the front of the CeeNee player. It will go in around a 1/2 inch and stop. 2) Connect
Basic editing of a recording with Audacity
 Basic editing of a recording with Audacity To edit a recording in Audacity you can use same type of actions that you can use in most computer applications, such as selecting, copying, pasting and deleting.
Basic editing of a recording with Audacity To edit a recording in Audacity you can use same type of actions that you can use in most computer applications, such as selecting, copying, pasting and deleting.
Page Replacement. (and other virtual memory policies) Kevin Webb Swarthmore College March 27, 2018
 Page Replacement (and other virtual memory policies) Kevin Webb Swarthmore College March 27, 2018 Today s Goals Making virtual memory virtual : incorporating disk backing. Explore page replacement policies
Page Replacement (and other virtual memory policies) Kevin Webb Swarthmore College March 27, 2018 Today s Goals Making virtual memory virtual : incorporating disk backing. Explore page replacement policies
#44. Accelerate Skype Using Your Keyboard Make Skype fly, by speeding up common tasks with key sequences and hotkeys.
 Accelerate Skype Using Your Keyboard #44 H A C K #44 Hack Accelerate Skype Using Your Keyboard Make Skype fly, by speeding up common tasks with key sequences and hotkeys. #44 Works with: Windows version
Accelerate Skype Using Your Keyboard #44 H A C K #44 Hack Accelerate Skype Using Your Keyboard Make Skype fly, by speeding up common tasks with key sequences and hotkeys. #44 Works with: Windows version
Full file at
 Guide to Networking Essentials, Sixth Edition 2-1 Chapter 2 Network Hardware Essentials At a Glance Instructor s Manual Table of Contents Overview Objectives Tips Quick Quizzes Class Discussion Topics
Guide to Networking Essentials, Sixth Edition 2-1 Chapter 2 Network Hardware Essentials At a Glance Instructor s Manual Table of Contents Overview Objectives Tips Quick Quizzes Class Discussion Topics
lab A.3: introduction to RoboLab vocabulary materials cc30.03 Brooklyn College, CUNY c 2006 Name: RoboLab communication tower canvas icon
 cc30.03 Brooklyn College, CUNY c 2006 lab A.3: introduction to RoboLab Name: vocabulary RoboLab communication tower canvas icon drag-and-drop function palette tools palette program algorithm syntax error
cc30.03 Brooklyn College, CUNY c 2006 lab A.3: introduction to RoboLab Name: vocabulary RoboLab communication tower canvas icon drag-and-drop function palette tools palette program algorithm syntax error
Computer Architecture Review. ICS332 - Spring 2016 Operating Systems
 Computer Architecture Review ICS332 - Spring 2016 Operating Systems ENIAC (1946) Electronic Numerical Integrator and Calculator Stored-Program Computer (instead of Fixed-Program) Vacuum tubes, punch cards
Computer Architecture Review ICS332 - Spring 2016 Operating Systems ENIAC (1946) Electronic Numerical Integrator and Calculator Stored-Program Computer (instead of Fixed-Program) Vacuum tubes, punch cards
