Topic 1: Analyzing Mobile Devices
|
|
|
- Earl Patrick
- 5 years ago
- Views:
Transcription
1 Topic 1: Analyzing Mobile Devices One aspect of forensics procedure is to secure and analyze mobile devices. What types of tools can be selected for use in mobile device investigations and how are they used during the investigation? What types of evidence can be retrieved from mobile devices and where are they physically located? Edward Jackson 6/13/2015 3:44:19 PM So many mobile devices When we talk about mobile devices, what we really mean is any device that a person can carry with them. However, often times the word mobile means a phone, specifically a cellular or smart phone. It is important to note, forensic investigators should learn how to retrieve evidence from all mobile-type devices, not just phones. Thus, to better understand the complex methods and techniques associated with the evidence collection in mobile devices, research was done to find tools that would assist the forensic investigator. But first, what is meant by evidence in mobile devices? Many modern digital devices are very much like computers, as they have data storage, RAM, CPUs, and applications. For example, today s smartphones have games, calendars, contact storage, , office applications, and other personal and professional software. Tablets, slate computers, e-readers, ultrabooks, laptops, netbooks, and proprietary devices such as Chromebooks, all are mobile, and all have the potential of containing data that would be considered evidence. The numerous digital devices on the market make the forensic investigator s job just that much more difficult. To help the investigator with the evidence collection process, many tools exist. These tools have different features and functions, but all aim to collect evidence. In my research, I came across an excellent article from Detective Cynthia A. Murphy, Developing Process for Mobile Device Forensics. Murphy explores the concepts of digital forensics as they relate to mobile technologies. For instance, she explains what ESN, MEID, MIN, and MDN are. ESN is the electronic serial number; MEID is the mobile equipment ID; a MIN is a mobile identification number; and a MDN is a mobile directory number (Murphy, 2013). Two important items that should be examined when collecting evidence are the SIM and SD storage. A SIM card contains mobile information---which is unique---that allows the customer to make phone calls.
2 Because this card contains private information which can be used to identify the customer, the phone number, and the mobile carrier, obtaining the SIM will become critical to case. Likewise, many mobile devices have SD cards. SD cards are types of storage devices which extend the mobile device's storage capacity. These storage cards can contain applications, personal and company information, as well as logs and usage reports that may be used as evidence in a court of law (Ware, n.d.). Additionally, mobile devices use RAM to store and run applications. Thus, learning how to properly obtain SIM cards, SD cards, and the contents of RAM will be essential in the evidence collection process. It is important to note, mobile devices found at a crime scene should be treated just like any other piece of evidence, and processed using digital forensics best practices that are safe and secure. When it comes to specific tools, I found four tools which basically are Swiss Army tools (they have features that address mobile evidence collection). The tools are Cellebrite, CellDEK, Oxygen Forensic Suite, and XRY/XACT (Murphy, 2013). What exactly do these tools do? All four of these mobile forensic tools have the ability to do six things; they are examining CDMA, GSM, iden, and the SIM card, as well as performing a logical dump and a physical dump. What is meant by a logical dump is the extraction of the mobile device s entire operating system. A physical dump is taking the flash memory of the device and moving it into a static file. This means, if the forensic investigator uses any one of these tools, they will have access to the mobile device s unique information, SD cards, flash memory, and operating system---all of which contain evidence, and which can ultimately become admissible as evidence in a court of law. References Easttom, Chuck. (2013). System forensics, investigation and response, 2nd Edition. Jones & Bartlett. Murphy. (2013). Developing process for mobile device forensics. Retrieved from
3 Ware. (n.d.). What is a SIM card? And why do we need one? Retrieved from One.htm Topic 2: Network Traffic Analysis What are some of the tools for network traffic analysis? Discuss at least two tools for network traffic analysis along with their key capabilities. What is the importance of log files in digital forensics? Edward Jackson Uncommon Free Analyzers 6/13/2015 6:17:58 PM As a forensic investigator, there will be the need to not only learn evidence collection processes, but to also know how to use network analyzers. Network analyzers are just how they sound; they are used to analyze network traffic. Why are network analyzers important? These analyzers can be used to troubleshoot problems on networks (such as dropped packets, switching, and routing issues), they can peer into packets to view packet content, and can be used to increase network performance. When it comes to a forensic investigation, network analyzers (and their reporting) can be used to identify a suspect, as well as detect machines and network gear that have become the target of a crime. After reading several of the posts here, I realize I could not choose some of the most popular network analyzers, i.e. Wireshark, Nmap, TCPDump. So, I went after a special niche, free analyzers. Some of the best free network analyzers out there are NetXMS and Xymon (Tabona, 2015). NetXMS is a network analyzer/monitoring tool which can be used on small and large networks. The software has nine main features. They include (NetXMS, 2015): Has enterprise management and monitoring features
4 High-performing and scalable Has distributed monitoring capability Automated discovery of networks Event processing which is easy to use Built-in business impact tools Easy to deploy Integrates well with other products Built-in support for many operating systems When viewing the software, I noticed there were tabs for object details, alarm browser, event monitor, event configuration, and event processing policy. See the picture below to view more details of the software.
5 Next, I reviewed Xymon. Xymon is web-based network analyzer utility, rather than a standalone software application. It has basic features such as performance and real-statistics, reporting capability, and network monitoring. A couple great features of the analyzer include historical data and graphical performance graphs. Examining the software, I noticed you had to add each host into the interface, and then you could drill down and view things like that host s IP addresses, online/offline status, CPU cycles being used, memory utilization, and storage device information. I like the idea of a web-based console, because the software can be accessed and used anywhere on the network, as long as the person is authorized to run it. For other details of the software, take a look at the picture below.
6 I would like to point out, both NetXMS and Xymon can be administered from Linux/Unix computers, but only NetXMS has been ported to run on Windows-based machines. NetXMS and Wireshark The main difference between NetXMS and Wireshark is, Wireshark is more of just a packet recorder/packet analyzer, whereas NetXMS is more robust and offers desktop management features. For example, NetXMS can restart processes and send reboots to host machines. NetXMS also has a built-in script engine, which allows an admin to send out scripts and packages in an automated fashion. Of course, this isn't to say Wireshark doesn't serve it's purpose. Wireshark specializes in packet capture, and as such, has a ton of features and functions just meant to record packets. For instance, Wireshark has decryption support for IPsec, ISAKMAP, Kerberos, SNMPv3, etc., which aids in packet analysis. References NetXMS. (2015). NetXMS features. Retrieved from Tabona. (2015). The top twenty free network monitoring and analysis tools for sys admins. Retrieved from Internet and Network Forensics and Intrusion Detection Mobile devices of all types are used by almost everyone and these include smartphones and tablets. A forensic case is likely to involve a mobile device. This unit explains the evidence that you can get from a mobile device, as well as tools and techniques for getting evidence from a cell phone. You will also learn about network forensics including an understanding of network packets and examining routers and firewalls for forensic evidence.
7 Outcomes After completing this unit, you should be able to: Evaluate tools and techniques for mobile device forensics. Examine network device logs for evidence in a forensic case. Course outcome(s) practiced in this unit IT550-3: Select forensic analysis tools for securing digital evidence and investigations. What do you have to do in this unit? Complete assigned Reading. Participate in Discussion. Complete unit Assignment. Participate in Seminar or complete Alternative Assignment. Complete the optional Learning Activity. Textbook Reading: Read Chapters 11 and 12 in System Forensics, Investigation, and Response.
8 Attending live Seminars is important to your academic success, and attendance is highly recommended. The Seminar allows you to review the important concepts presented in each unit, discuss work issues in your lives that pertain to these concepts, ask your instructor questions, and allows you to come together in real time with your fellow classmates. There will be a graded Seminar in Units 1 through 5 in this course. You must either attend the live Seminar, or you must complete the Seminar alternative assignment in order to earn points for this part of the class. Option 1: Attend Seminar: The Seminar will look into Unit 5 topics along with the Assignment. Remember, if you do not participate in the weekly Seminar, you need to complete the alternative assignment. Unit 5 Assignment Outcomes addressed in this activity: Unit Outcomes:
9 Evaluate tools and techniques for mobile device forensics. Examine network device logs for evidence in a forensic case. Course Outcome: IT550-3: Select forensic analysis tools for securing digital evidence and investigations. View the Rubric below for more information
10
11
You will discuss topics related to ethical hacking, information risks, and security techniques which hackers will seek to circumvent.
 IDPS Effectiveness and Primary Takeaways You will discuss topics related to ethical hacking, information risks, and security techniques which hackers will seek to circumvent. IDPS Effectiveness and Primary
IDPS Effectiveness and Primary Takeaways You will discuss topics related to ethical hacking, information risks, and security techniques which hackers will seek to circumvent. IDPS Effectiveness and Primary
Cellebrite Digital Forensics for Legal Professionals (CDFL)
 Global forensic training Course description Level Intermediate Length Two days (14 hours) Training Track Investigative The two-day Cellebrite Digital Forensics for Legal Professionals course is designed
Global forensic training Course description Level Intermediate Length Two days (14 hours) Training Track Investigative The two-day Cellebrite Digital Forensics for Legal Professionals course is designed
AccessData offers a broad array of training options.
 Forensics Training AccessData offers a broad array of training options. Our trainers have more than two centuries of cumulative experience in their respective fields. Take Advantage of the All Access Pass
Forensics Training AccessData offers a broad array of training options. Our trainers have more than two centuries of cumulative experience in their respective fields. Take Advantage of the All Access Pass
A good example of entities and relationships can be seen below.
 Unit 2: Unit 2: Conceptual Design: Data Modeling and the Entity Relationship Model - Discussion 1 Scroll down and click "Respond" to post your reply to the Discussion questions. Please review the Discussion
Unit 2: Unit 2: Conceptual Design: Data Modeling and the Entity Relationship Model - Discussion 1 Scroll down and click "Respond" to post your reply to the Discussion questions. Please review the Discussion
Steady stream of bits 9/6/2014 5:02:53 PM. Edward Jackson
 DB1 As noted in this unit's reading, there are three main categories of streaming video systems. Name the three categories, give a brief comparison of the categories, then state (and support) your own
DB1 As noted in this unit's reading, there are three main categories of streaming video systems. Name the three categories, give a brief comparison of the categories, then state (and support) your own
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Topic 1: Obstacles to Successful Implementation
 Topic 1: Obstacles to Successful Implementation Implementing a developed computer network security policy is oftentimes difficult to accomplish. What are some of the obstacles to computer network security
Topic 1: Obstacles to Successful Implementation Implementing a developed computer network security policy is oftentimes difficult to accomplish. What are some of the obstacles to computer network security
NMS300 Network Management System Application
 NMS300 Network Management System Application Quick Start Guide October 2013 202-11288-02 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing
NMS300 Network Management System Application Quick Start Guide October 2013 202-11288-02 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing
Course Title: Network+/Networking Fundamentals. Course Section: CNS-101-I1. FORMAT: Online
 Course Title: Network+/Networking Fundamentals Course Section: CNS-101-I1 FORMAT: Online TIME FRAME: Start Date: 15 January 2018 End Date: 06 May 2018 CREDITS: 4 INSTRUCTOR: Carlos J. Garcia Office Hours:
Course Title: Network+/Networking Fundamentals Course Section: CNS-101-I1 FORMAT: Online TIME FRAME: Start Date: 15 January 2018 End Date: 06 May 2018 CREDITS: 4 INSTRUCTOR: Carlos J. Garcia Office Hours:
Course Title: Computer Networking 2. Course Section: CNS (Winter 2018) FORMAT: Face to Face
 Course Title: Computer Networking 2 Course Section: CNS-106-50 (Winter 2018) FORMAT: Face to Face TIME FRAME: Start Date: 15 January 2018 End Date: 28 February 2018 Monday & Wednesday 1:00pm 5:00pm CREDITS:
Course Title: Computer Networking 2 Course Section: CNS-106-50 (Winter 2018) FORMAT: Face to Face TIME FRAME: Start Date: 15 January 2018 End Date: 28 February 2018 Monday & Wednesday 1:00pm 5:00pm CREDITS:
ehealth SPECTRUM Integration
 User Guide May 2006 ehealth SPECTRUM Integration Whether you are a large enterprise or a service provider, your operations team faces a significant challenge maintaining critical service levels across
User Guide May 2006 ehealth SPECTRUM Integration Whether you are a large enterprise or a service provider, your operations team faces a significant challenge maintaining critical service levels across
NEW BRUNSWICK. IT Systems Administrator
 NEW BRUNSWICK *Please scroll to see other provinces. IT Systems Administrator PROGRAM OBJECTIVES The IT Systems Administrator program will provide students with the skills and knowledge to pursue certifications
NEW BRUNSWICK *Please scroll to see other provinces. IT Systems Administrator PROGRAM OBJECTIVES The IT Systems Administrator program will provide students with the skills and knowledge to pursue certifications
COMPUTER FORENSICS (CFRS)
 Computer Forensics (CFRS) 1 COMPUTER FORENSICS (CFRS) 500 Level Courses CFRS 500: Introduction to Forensic Technology and Analysis. 3 credits. Presents an overview of technologies of interest to forensics
Computer Forensics (CFRS) 1 COMPUTER FORENSICS (CFRS) 500 Level Courses CFRS 500: Introduction to Forensic Technology and Analysis. 3 credits. Presents an overview of technologies of interest to forensics
Section Title. Body content goes here! Guidebook. Edverum
 Section Title Body content goes here! Edverum Section Title Body content goes here! Section Title Body content goes here! Table of Contents Technical Requirements... Getting Started... Navigating Edverum
Section Title Body content goes here! Edverum Section Title Body content goes here! Section Title Body content goes here! Table of Contents Technical Requirements... Getting Started... Navigating Edverum
SAULT COLLEGE OF APPLIED ARTS AND TECHNOLOGY SAULT STE. MARIE, ONTARIO COURSE OUTLINE
 SAULT COLLEGE OF APPLIED ARTS AND TECHNOLOGY SAULT STE. MARIE, ONTARIO COURSE OUTLINE COURSE TITLE: CODE NO. : SEMESTER: Fall 2011 PROGRAM: AUTHOR: Computer Engineering Technologist - Networking Dan Kachur
SAULT COLLEGE OF APPLIED ARTS AND TECHNOLOGY SAULT STE. MARIE, ONTARIO COURSE OUTLINE COURSE TITLE: CODE NO. : SEMESTER: Fall 2011 PROGRAM: AUTHOR: Computer Engineering Technologist - Networking Dan Kachur
Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014
 Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014 INTRODUCTION The field of computer forensics has long been centered on traditional media like hard drives.
Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014 INTRODUCTION The field of computer forensics has long been centered on traditional media like hard drives.
TECHNOLOGY Introduction The Difference Protection at the End Points Security made Simple
 APPGATE TECHNOLOGY UNIFIED TECHNOLOGY Introduction The AppGate solution truly delivers holistic security and access control where other approaches fall short. It is designed to address the security and
APPGATE TECHNOLOGY UNIFIED TECHNOLOGY Introduction The AppGate solution truly delivers holistic security and access control where other approaches fall short. It is designed to address the security and
ehealth SPECTRUM Integration
 User Guide March 2007 ehealth SPECTRUM Integration Whether you are a large enterprise or a service provider, your operations team faces a significant challenge maintaining critical service levels across
User Guide March 2007 ehealth SPECTRUM Integration Whether you are a large enterprise or a service provider, your operations team faces a significant challenge maintaining critical service levels across
Topic 1: Physical Security Measures for HGA
 Topic 1: Physical Security Measures for HGA Return to HGA s mainframe (depicted within Figure B-1 located in Doc Sharing). Suggest appropriate physical security measures as requited in PCI specification
Topic 1: Physical Security Measures for HGA Return to HGA s mainframe (depicted within Figure B-1 located in Doc Sharing). Suggest appropriate physical security measures as requited in PCI specification
University of San Francisco Course Syllabus and Outline
 College of Professional Studies BSIS 340 Business Data Networks and Telecommunications University of San Francisco Fall Semester 2008 Robert C. Hughes, M.S. Email: rchughes3@usfca.edu Enrolled Student
College of Professional Studies BSIS 340 Business Data Networks and Telecommunications University of San Francisco Fall Semester 2008 Robert C. Hughes, M.S. Email: rchughes3@usfca.edu Enrolled Student
REQUIRED TEXT: Mobile Phone Examiner Training Manual. Various articles and white papers. as assigned by instructor
 Course: CJ 4750 Small Devices Forensics Credit Hours: 3 credit hours Instructor: Joan Runs Through Office Phone: (435) 879-4420 Office Hours: TBA PREREQUISITES: CJ 2700 (CJ 3900 is highly recommended)
Course: CJ 4750 Small Devices Forensics Credit Hours: 3 credit hours Instructor: Joan Runs Through Office Phone: (435) 879-4420 Office Hours: TBA PREREQUISITES: CJ 2700 (CJ 3900 is highly recommended)
MPE+ Frequently Asked Questions & Troubleshooting
 MPE+ Frequently Asked Questions & Troubleshooting Version 7 (4.5.0.45078) 2011 AccessData Group, LLC Table of Contents Mobile Forensics Background Knowledge... 4 Q. What is the difference between Computer
MPE+ Frequently Asked Questions & Troubleshooting Version 7 (4.5.0.45078) 2011 AccessData Group, LLC Table of Contents Mobile Forensics Background Knowledge... 4 Q. What is the difference between Computer
Microsoft Excel Starter 2010 Cannot Be Opened
 Microsoft Excel Starter 2010 Cannot Be Opene Check Your Internet Error message when clicking hyperlink in Office: "Cannot locate the Internet server or proxy server firewall that does not allow HTTP requests
Microsoft Excel Starter 2010 Cannot Be Opene Check Your Internet Error message when clicking hyperlink in Office: "Cannot locate the Internet server or proxy server firewall that does not allow HTTP requests
Thread in Commercial Backgrounder
 Thread in Commercial Backgrounder September 2018 An introduction to Thread, its Network Topology and Application Support 1 What is Thread Thread is an open standard for wireless communication providing
Thread in Commercial Backgrounder September 2018 An introduction to Thread, its Network Topology and Application Support 1 What is Thread Thread is an open standard for wireless communication providing
Trends in Mobile Forensics from Cellebrite
 Trends in Mobile Forensics from Cellebrite EBOOK 1 Cellebrite Survey Cellebrite is a well-known name in the field of computer forensics, and they recently conducted a survey as well as interviews with
Trends in Mobile Forensics from Cellebrite EBOOK 1 Cellebrite Survey Cellebrite is a well-known name in the field of computer forensics, and they recently conducted a survey as well as interviews with
COWLEY COLLEGE & Area Vocational Technical School
 COWLEY COLLEGE & Area Vocational Technical School COURSE PROCEDURE FOR Student Level: This course is open to students on the college level in either the freshman or sophomore year. Catalog Description:
COWLEY COLLEGE & Area Vocational Technical School COURSE PROCEDURE FOR Student Level: This course is open to students on the college level in either the freshman or sophomore year. Catalog Description:
Syllabus. Course Title: Cyber Forensics Course Number: CIT 435. Course Description: Prerequisite Courses: Course Overview
 Syllabus Course Title: Cyber Course Number: CIT 435 Course Description: Introduces the principles and practices of digital forensics including digital investigations, data and file recovery methods, and
Syllabus Course Title: Cyber Course Number: CIT 435 Course Description: Introduces the principles and practices of digital forensics including digital investigations, data and file recovery methods, and
IT Systems Administrator
 IT Systems Administrator PROGRAM OBJECTIVES The IT Systems Administrator program will provide students with the skills and knowledge to pursue certifications and careers in computer and networkrelated
IT Systems Administrator PROGRAM OBJECTIVES The IT Systems Administrator program will provide students with the skills and knowledge to pursue certifications and careers in computer and networkrelated
OXYGEN SOFTWARE OXYGEN FORENSIC KIT
 OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
ONLINE LEARNING MOODLE INSTRUCTIONS FOR STUDENTS TAFENSW.EDU.AU
 ONLINE LEARNING MOODLE INSTRUCTIONS FOR STUDENTS TAFENSW.EDU.AU welcome CONTENTS TECHNICAL REQUIREMENTS FOR USING MOODLE 4 LOGGING INTO YOUR MOODLE COURSE 5 WELCOME TO YOUR STUDY EDITING YOUR MOODLE PROFILE
ONLINE LEARNING MOODLE INSTRUCTIONS FOR STUDENTS TAFENSW.EDU.AU welcome CONTENTS TECHNICAL REQUIREMENTS FOR USING MOODLE 4 LOGGING INTO YOUR MOODLE COURSE 5 WELCOME TO YOUR STUDY EDITING YOUR MOODLE PROFILE
XLink Kai Raspberry Pi Beginners Tutorial
 XLink-Kai-Raspberry-Pi-Beginners-Tutorial.md XLink Kai Raspberry Pi Beginners Tutorial Hi! This tutorial will guide you through setting up XLink Kai on a Raspberry Pi to play multiplayer system link Xbox
XLink-Kai-Raspberry-Pi-Beginners-Tutorial.md XLink Kai Raspberry Pi Beginners Tutorial Hi! This tutorial will guide you through setting up XLink Kai on a Raspberry Pi to play multiplayer system link Xbox
A Cry for Help: Persuading Cell phone Developers to Get Involved with Digital Forensics
 A Cry for Help: Persuading Cell phone Developers to Get Involved with Digital Forensics Kendra Carr 1 Abstract Computer Forensics predominantly concentrates on the accessibility of retrievable information
A Cry for Help: Persuading Cell phone Developers to Get Involved with Digital Forensics Kendra Carr 1 Abstract Computer Forensics predominantly concentrates on the accessibility of retrievable information
Administering System Center Configuration Manager
 Administering System Center Configuration Manager Course 20703-1A 5 Days Instructor-led, Hands on Course Information This five-day course describes how to use Configuration Manager and its associated site
Administering System Center Configuration Manager Course 20703-1A 5 Days Instructor-led, Hands on Course Information This five-day course describes how to use Configuration Manager and its associated site
FIRST YOU LEARN. THEN YOU LAB.
 FIRST YOU LEARN. THEN YOU LAB. Real equipment. Real applications. Really cool live interactions. Nothing complements your IT learning like KnowledgeNet Live Labs. With access to real hardware and software,
FIRST YOU LEARN. THEN YOU LAB. Real equipment. Real applications. Really cool live interactions. Nothing complements your IT learning like KnowledgeNet Live Labs. With access to real hardware and software,
Interactive PDFs Start
 Interactive PDFs Introduction Generally, we use the term interactive PDF when we re talking about a PDF file that is meant to be viewed on screen. The interactive PDF features are the parts of a PDF that
Interactive PDFs Introduction Generally, we use the term interactive PDF when we re talking about a PDF file that is meant to be viewed on screen. The interactive PDF features are the parts of a PDF that
Fundamentals of Windows Server 2008 Network and Applications Infrastructure
 COURSE OVERVIEW This five-day instructor-led course introduces students to network and applications infrastructure concepts and configurations provided by Window Server 2008. Students will be able to acquire
COURSE OVERVIEW This five-day instructor-led course introduces students to network and applications infrastructure concepts and configurations provided by Window Server 2008. Students will be able to acquire
Administering System Center Configuration Manager
 Administering System Center Configuration Manager 20703-1; 5 Days; Instructor-led Course Description This five-day course describes how to use Configuration Manager and its associated site systems to efficiently
Administering System Center Configuration Manager 20703-1; 5 Days; Instructor-led Course Description This five-day course describes how to use Configuration Manager and its associated site systems to efficiently
WHAT S NEW IN SECURITY+ SY0-401?
 WHAT S NEW IN SECURITY+ SY0-401? PRESENTED BY NETCOM LEARNING PRESENTER BRAD PARKER, MCT WHY SHOULD I TAKE SYO-401? CompTIA has increased the coverage of the Security+ exam Demonstrates a better understanding
WHAT S NEW IN SECURITY+ SY0-401? PRESENTED BY NETCOM LEARNING PRESENTER BRAD PARKER, MCT WHY SHOULD I TAKE SYO-401? CompTIA has increased the coverage of the Security+ exam Demonstrates a better understanding
Understanding Routers, Switches, and Network Hardware
 Understanding Routers, Switches, and Network Hardware Rather than start off with a glossary of networking terms and in the process slam you with a technical terms with no easy point of reference let s
Understanding Routers, Switches, and Network Hardware Rather than start off with a glossary of networking terms and in the process slam you with a technical terms with no easy point of reference let s
10/21/2013. The ubiquity of social media has lead inevitably to the involvement of digital evidence in nearly every segment of Criminal Practice
 Adam Zion Director of Information Technology Office of the Kings County District Attorney The ubiquity of social media has lead inevitably to the involvement of digital evidence in nearly every segment
Adam Zion Director of Information Technology Office of the Kings County District Attorney The ubiquity of social media has lead inevitably to the involvement of digital evidence in nearly every segment
The Use of Technology to Enhance Investigation
 The Use of Technology to Enhance Investigation Of High Profile Corruption Cases. Centre for Socio-Legal Studies Objectives By the end of this keynote, participants will be knowledgeable on: 1. Open Source
The Use of Technology to Enhance Investigation Of High Profile Corruption Cases. Centre for Socio-Legal Studies Objectives By the end of this keynote, participants will be knowledgeable on: 1. Open Source
Gateway 2.0 Cellular (P/N )
 Lumewave by Echelon Gateway 2.0 Cellular (P/N 100141) End User Cellular Activation Manual Rev. B 8-17-2017 Revision Date Notes A 3-14-2016 Initial Draft B 08-17-2017 Updated password to align what was
Lumewave by Echelon Gateway 2.0 Cellular (P/N 100141) End User Cellular Activation Manual Rev. B 8-17-2017 Revision Date Notes A 3-14-2016 Initial Draft B 08-17-2017 Updated password to align what was
Intro. This program can retrieve messages, call logs, pictures, contacts, apps, calendar events, s, passwords, deleted data, and much more.
 FAQ Intro Thank you for purchasing MOBILedit Forensic Express. This tool preforms mobile phone content extractions and is used by professionals in law enforcement, military as well as the corporate and
FAQ Intro Thank you for purchasing MOBILedit Forensic Express. This tool preforms mobile phone content extractions and is used by professionals in law enforcement, military as well as the corporate and
Course 10324A: Implementing and Managing Microsoft Desktop Virtualization
 Course 10324A: Implementing and Managing Microsoft Desktop Virtualization Length: 5 days Audience: IT Professionals OVERVIEW This five-day, instructor-led course provides you with the knowledge and skills
Course 10324A: Implementing and Managing Microsoft Desktop Virtualization Length: 5 days Audience: IT Professionals OVERVIEW This five-day, instructor-led course provides you with the knowledge and skills
Security Enhancements
 OVERVIEW Security Enhancements February 9, 2009 Abstract This paper provides an introduction to the security enhancements in Microsoft Windows 7. Built upon the security foundations of Windows Vista, Windows
OVERVIEW Security Enhancements February 9, 2009 Abstract This paper provides an introduction to the security enhancements in Microsoft Windows 7. Built upon the security foundations of Windows Vista, Windows
Student User s Guide
 Student User s Guide Topics Introduction... 2 Registration... 2 Registration with 1Pass... 6 Start an Assignment... 7 Viewing your Grades... 8 Communication Tool... 9 The English 21 Tools... 10 Interactive
Student User s Guide Topics Introduction... 2 Registration... 2 Registration with 1Pass... 6 Start an Assignment... 7 Viewing your Grades... 8 Communication Tool... 9 The English 21 Tools... 10 Interactive
Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003
 SecurityFocus HOME Infocus: Forensics on the Windows Platform, Part Two 2003-02-17 12:56:05-0900 SFOnline Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003 Introduction
SecurityFocus HOME Infocus: Forensics on the Windows Platform, Part Two 2003-02-17 12:56:05-0900 SFOnline Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003 Introduction
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition. Chapter 2 Investigating Network Traffic
 Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
CCRI Networking Technology I CSCO-1850 Spring 2014
 CCRI Networking Technology I CSCO-1850 Spring 2014 Instructor John Mowry Telephone 401-825-2138 E-mail jmowry@ccri.edu Office Hours Room 2126 Class Sections 102 Monday & Wednesday 6:00PM-9:50PM, starts
CCRI Networking Technology I CSCO-1850 Spring 2014 Instructor John Mowry Telephone 401-825-2138 E-mail jmowry@ccri.edu Office Hours Room 2126 Class Sections 102 Monday & Wednesday 6:00PM-9:50PM, starts
ONLINE TRAINING REFERENCE GUIDE
 ONLINE TRAINING REFERENCE GUIDE Updated February 2018 Maine Roads to Quality Professional Development Network PO Box 9300, 34 Bedford Street, Portland, ME 04104 1-888-900-055 www.muskie.usm.maine.edu/maineroads
ONLINE TRAINING REFERENCE GUIDE Updated February 2018 Maine Roads to Quality Professional Development Network PO Box 9300, 34 Bedford Street, Portland, ME 04104 1-888-900-055 www.muskie.usm.maine.edu/maineroads
Course Outline. MCSA: Windows 8.1 Complete Study Guide Exam & (Course & Labs)
 Course Outline MCSA: Windows 8.1 Complete Study Guide Exam 70-687 & 70-688 (Course & Labs) 31 Dec 2018 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number
Course Outline MCSA: Windows 8.1 Complete Study Guide Exam 70-687 & 70-688 (Course & Labs) 31 Dec 2018 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number
Starting from. An Introduction to Computing Science by Jeremy Scott LEARNER NOTES
 Starting from An to Computing Science by Jeremy Scott LEARNER NOTES You have probably already used several computers today without realising it. If you have sent a text, been driven in a car, or checked
Starting from An to Computing Science by Jeremy Scott LEARNER NOTES You have probably already used several computers today without realising it. If you have sent a text, been driven in a car, or checked
1. The first true 32-bit operating system developed by Microsoft was Windows 3.1.
 Chapter 02 TRUE/FALSE 1. The first true 32-bit operating system developed by Microsoft was Windows 3.1. F PTS: 1 REF: 58 2. Windows 95 used cooperative multitasking for 16-bit applications and preemptive
Chapter 02 TRUE/FALSE 1. The first true 32-bit operating system developed by Microsoft was Windows 3.1. F PTS: 1 REF: 58 2. Windows 95 used cooperative multitasking for 16-bit applications and preemptive
Course Syllabus: Linux Essentials
 Course Syllabus: Linux Essentials Instructor: Roger Elliott Email: rlelliott@c-tec.edu Phone: Office: (740) 364-2299 Cell: (740) 814-7504 Course text Course #: Hours: Meeting Days & Times: Location Linux
Course Syllabus: Linux Essentials Instructor: Roger Elliott Email: rlelliott@c-tec.edu Phone: Office: (740) 364-2299 Cell: (740) 814-7504 Course text Course #: Hours: Meeting Days & Times: Location Linux
A: Administering System Center Configuration Manager
 20703-1A: Administering System Center Configuration Manager Duration: 5 days; Instructor-led WHAT YOU WILL LEARN This five-day course describes how to use Configuration Manager and its associated site
20703-1A: Administering System Center Configuration Manager Duration: 5 days; Instructor-led WHAT YOU WILL LEARN This five-day course describes how to use Configuration Manager and its associated site
PATCtech. Cellular Records Review and Analysis Part 2: Verizon
 Cellular Records Review and Analysis Part 2: Verizon PATCtech Glenn K Bard, Chief Technology Officer Scott Lucas, Instructor and Examiner Steve Dempsey, Instructor Kathy Enriquez, Instructor Brian Sprinkle,
Cellular Records Review and Analysis Part 2: Verizon PATCtech Glenn K Bard, Chief Technology Officer Scott Lucas, Instructor and Examiner Steve Dempsey, Instructor Kathy Enriquez, Instructor Brian Sprinkle,
About Advanced Access Control Settings for Network Analysis and Intrusion Policies
 Advanced Access Control Settings for Network Analysis and Intrusion Policies The following topics describe how to configure advanced settings for network analysis and intrusion policies: About Advanced
Advanced Access Control Settings for Network Analysis and Intrusion Policies The following topics describe how to configure advanced settings for network analysis and intrusion policies: About Advanced
ITSY 2330 Intrusion Detection Course Syllabus
 ITSY 2330 Intrusion Detection Course Syllabus Instructor Course Reference Number (CRN) Course Description: Course Prerequisite(s) Course Semester Credit Hours (SCH) (Lecture, Lab) Name: Hung Le Tel: Office:
ITSY 2330 Intrusion Detection Course Syllabus Instructor Course Reference Number (CRN) Course Description: Course Prerequisite(s) Course Semester Credit Hours (SCH) (Lecture, Lab) Name: Hung Le Tel: Office:
Audience(s) : IT Professionals Level : 300 Technology : Microsoft System Center Configuration Manager Delivery Method : Instructor-led (Classroom)
 [MS10748]: Planning and Deploying System Center 2012 Configuration Length : 3 Days Audience(s) : IT Professionals Level : 300 Technology : System Center Configuration Delivery Method : Instructor-led (Classroom)
[MS10748]: Planning and Deploying System Center 2012 Configuration Length : 3 Days Audience(s) : IT Professionals Level : 300 Technology : System Center Configuration Delivery Method : Instructor-led (Classroom)
CHAPTER 03: MULTIMEDIA & OPERATING SYSTEM. :: Operating System :: ~ What is OS?~ ~ OS Functions~ ~ OS Characteristics ~ ~ Type of OS~
 CHAPTER 03: MULTIMEDIA & OPERATING SYSTEM :: Operating System :: ~ What is OS?~ ~ OS Functions~ ~ OS Characteristics ~ ~ Type of OS~ 1 Operating System and Software Computer Operating System An operating
CHAPTER 03: MULTIMEDIA & OPERATING SYSTEM :: Operating System :: ~ What is OS?~ ~ OS Functions~ ~ OS Characteristics ~ ~ Type of OS~ 1 Operating System and Software Computer Operating System An operating
AT&T SD-WAN Network Based service quick start guide
 AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
Creating a Cell Phone Investigation Toolkit: Basic Hardware and Software Specifications
 Creating a Cell Phone Investigation Toolkit: Basic Hardware and Software Specifications SEARCH Training Services May 2006 SEARCH The National Consortium for Justice Information and Statistics 7311 Greenhaven
Creating a Cell Phone Investigation Toolkit: Basic Hardware and Software Specifications SEARCH Training Services May 2006 SEARCH The National Consortium for Justice Information and Statistics 7311 Greenhaven
Instructor: Eric Rettke Phone: (every few days)
 Instructor: Eric Rettke Phone: 818 364-7775 email: rettkeeg@lamission.edu (every few days) Fall 2016 Computer Science 411 - Principles of Cyber Security 1 Please keep a copy of the syllabus handy for the
Instructor: Eric Rettke Phone: 818 364-7775 email: rettkeeg@lamission.edu (every few days) Fall 2016 Computer Science 411 - Principles of Cyber Security 1 Please keep a copy of the syllabus handy for the
SYSTEM FORENSICS, INVESTIGATION, AND RESPONSE (INFORMATION SYSTEMS SECURITY & ASSURANCE) BY JOHN R. VACCA, K RUDOLPH
 SYSTEM FORENSICS, INVESTIGATION, AND RESPONSE (INFORMATION SYSTEMS SECURITY & ASSURANCE) BY JOHN R. VACCA, K RUDOLPH DOWNLOAD EBOOK : SYSTEM FORENSICS, INVESTIGATION, AND RESPONSE JOHN R. VACCA, K RUDOLPH
SYSTEM FORENSICS, INVESTIGATION, AND RESPONSE (INFORMATION SYSTEMS SECURITY & ASSURANCE) BY JOHN R. VACCA, K RUDOLPH DOWNLOAD EBOOK : SYSTEM FORENSICS, INVESTIGATION, AND RESPONSE JOHN R. VACCA, K RUDOLPH
HOW TO USE MOODLE. Welcome to BFI Wien! QUICK GUIDE
 Welcome to BFI Wien! In order to provide our customers with the possibility to learn independently of time and place, some of our courses are supported by our learning management system Moodle. There,
Welcome to BFI Wien! In order to provide our customers with the possibility to learn independently of time and place, some of our courses are supported by our learning management system Moodle. There,
DISTRICT TECHNOLOGY COORDINATOR WEBINAR. Spring 2018 South Carolina Alternate Assessments
 DISTRICT TECHNOLOGY COORDINATOR WEBINAR Spring 2018 South Carolina Alternate Assessments Topics 2 SC Alternate Assessment Portal TIDE Site Readiness Network Requirements Hardware and Software Requirements
DISTRICT TECHNOLOGY COORDINATOR WEBINAR Spring 2018 South Carolina Alternate Assessments Topics 2 SC Alternate Assessment Portal TIDE Site Readiness Network Requirements Hardware and Software Requirements
OXYGEN SOFTWARE OXYGEN FORENSIC KIT
 OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
CompTIA CAS-003. CompTIA Advanced Security Practitioner (CASP)
 CompTIA CAS-003 CompTIA Advanced Security Practitioner (CASP) http://killexams.com/pass4sure/exam-detail/cas-003 DEMO Find some pages taken from full version Killexams CAS-003 questions and answers are
CompTIA CAS-003 CompTIA Advanced Security Practitioner (CASP) http://killexams.com/pass4sure/exam-detail/cas-003 DEMO Find some pages taken from full version Killexams CAS-003 questions and answers are
Information Systems and Tech (IST)
 Information Systems and Tech (IST) 1 Information Systems and Tech (IST) Courses IST 101. Introduction to Information Technology. 4 Introduction to information technology concepts and skills. Survey of
Information Systems and Tech (IST) 1 Information Systems and Tech (IST) Courses IST 101. Introduction to Information Technology. 4 Introduction to information technology concepts and skills. Survey of
COURSE OUTLINE: Supporting and Troubleshooting Windows 10
 Course Name 10982-Supporting and Troubleshooting Course Duration 5 Days Course Structure Instructor-Led Course Overview This course is designed to provide students with the knowledge and skills required
Course Name 10982-Supporting and Troubleshooting Course Duration 5 Days Course Structure Instructor-Led Course Overview This course is designed to provide students with the knowledge and skills required
IT JARGON BUSTERS NETWORKING TERMS
 IT JARGON BUSTERS NETWORKING TERMS WAN Wide Area The WAN is associated with connections over a large area. In most circumstances this is referred to as the Internet connection you will have at home or
IT JARGON BUSTERS NETWORKING TERMS WAN Wide Area The WAN is associated with connections over a large area. In most circumstances this is referred to as the Internet connection you will have at home or
"Charting the Course... MOC A: Administering System Center Configuration Manager. Course Summary
 MOC 20703-1A: Administering System Center Configuration Manager Course Summary Description This five-day course describes how to use Configuration Manager and its associated site systems to efficiently
MOC 20703-1A: Administering System Center Configuration Manager Course Summary Description This five-day course describes how to use Configuration Manager and its associated site systems to efficiently
Setup Google Analytics
 Setup Google Analytics 1.1 Sign Up Google Analytics 1. Once you have a Google account, you can go to Google Analytics (https://analytics.google.com) and click the Sign into Google Analytics button. You
Setup Google Analytics 1.1 Sign Up Google Analytics 1. Once you have a Google account, you can go to Google Analytics (https://analytics.google.com) and click the Sign into Google Analytics button. You
COWLEY COLLEGE & Area Vocational Technical School
 COWLEY COLLEGE & Area Vocational Technical School COURSE PROCEDURE FOR COMPTIA A+ ESSENTIALS CIS1756 3 Credit Hours Student Level: This course is open to students on the college level in either the Freshman
COWLEY COLLEGE & Area Vocational Technical School COURSE PROCEDURE FOR COMPTIA A+ ESSENTIALS CIS1756 3 Credit Hours Student Level: This course is open to students on the college level in either the Freshman
SERVANT KEEPER 7. Upgrade today! You will feel right at home
 SERVANT KEEPER 7 Upgrade today! You will feel right at home with the familiar look and feel which have been updated to provide more functionality and even faster access to your information. Expanded platforms
SERVANT KEEPER 7 Upgrade today! You will feel right at home with the familiar look and feel which have been updated to provide more functionality and even faster access to your information. Expanded platforms
ADOBE CONNECT GUIDE FOR INSTRUCTORS
 Setting up a Class ADOBE CONNECT GUIDE FOR INSTRUCTORS When you set up your Acrobat Connect account, Adobe sends you an e-mail message that includes your meeting URL along with other information about
Setting up a Class ADOBE CONNECT GUIDE FOR INSTRUCTORS When you set up your Acrobat Connect account, Adobe sends you an e-mail message that includes your meeting URL along with other information about
Digital Cameras. An evaluation of the collection, preservation and evaluation of data collected from digital
 Ronald Prine CSC 589 - Digital Forensics New Mexico Institute of Mining and Technology October 17, 2006 Digital Cameras Executive Summary An evaluation of the collection, preservation and evaluation of
Ronald Prine CSC 589 - Digital Forensics New Mexico Institute of Mining and Technology October 17, 2006 Digital Cameras Executive Summary An evaluation of the collection, preservation and evaluation of
Networking Technology
 Associate in Applied Science Networking Fundamentals Diploma Cisco Networking Certificate Network Security Certificate Networking Technology IT Support Certificate Advanced IT Support Certificate Information
Associate in Applied Science Networking Fundamentals Diploma Cisco Networking Certificate Network Security Certificate Networking Technology IT Support Certificate Advanced IT Support Certificate Information
Course Outline. Networking Essentials, Fifth Edition Pearson ucertify Labs.
 Course Outline Networking Essentials, Fifth Edition Pearson ucertify 22 Apr 2019 Contents 1. Course Objective 2. Expert Instructor-Led Training 3. ADA Compliant & JAWS Compatible Platform 4. State of the
Course Outline Networking Essentials, Fifth Edition Pearson ucertify 22 Apr 2019 Contents 1. Course Objective 2. Expert Instructor-Led Training 3. ADA Compliant & JAWS Compatible Platform 4. State of the
Course Outline Topic 1: Current State Assessment, Security Operations Centers, and Security Architecture
 About this Course This course will best position your organization to analyse threats and detect anomalies that could indicate cybercriminal behaviour. The payoff for this new proactive approach would
About this Course This course will best position your organization to analyse threats and detect anomalies that could indicate cybercriminal behaviour. The payoff for this new proactive approach would
HANDOUT: COMPUTER PARTS
 HANDOUT: COMPUTER PARTS Because computers are so important to our lives, there is a constant need to design and develop new hardware, software, and systems. Have you used a computer before? I m sure you
HANDOUT: COMPUTER PARTS Because computers are so important to our lives, there is a constant need to design and develop new hardware, software, and systems. Have you used a computer before? I m sure you
ADMINISTERING SYSTEM CENTER CONFIGURATION MANAGER
 ADMINISTERING SYSTEM CENTER CONFIGURATION MANAGER Course Code: 20703-1a Duration 5 days Introduction This five-day course describes how to use Configuration and its associated site systems to efficiently
ADMINISTERING SYSTEM CENTER CONFIGURATION MANAGER Course Code: 20703-1a Duration 5 days Introduction This five-day course describes how to use Configuration and its associated site systems to efficiently
CASPER COLLEGE COURSE SYLLABUS MSFT 1600 Managing Microsoft Exchange Server 2003 Semester/Year: Fall 2007
 CASPER COLLEGE COURSE SYLLABUS MSFT 1600 Managing Microsoft Exchange Server 2003 Semester/Year: Fall 2007 Lecture Hours: 2 Lab Hours: 2 Credit Hours: 3 Class Time: Saturday 8:30 AM - 12:00 PM Room: BU
CASPER COLLEGE COURSE SYLLABUS MSFT 1600 Managing Microsoft Exchange Server 2003 Semester/Year: Fall 2007 Lecture Hours: 2 Lab Hours: 2 Credit Hours: 3 Class Time: Saturday 8:30 AM - 12:00 PM Room: BU
Billing PracticeMaster Financial. Tabs3 Connect Quick Guide
 Billing PracticeMaster Financial Tabs3 Connect Quick Guide Tabs3 Connect Quick Guide Copyright 2012-2018 Software Technology, LLC 1621 Cushman Drive Lincoln, NE 68512 (402) 423-1440 Tabs3.com Tabs3, PracticeMaster,
Billing PracticeMaster Financial Tabs3 Connect Quick Guide Tabs3 Connect Quick Guide Copyright 2012-2018 Software Technology, LLC 1621 Cushman Drive Lincoln, NE 68512 (402) 423-1440 Tabs3.com Tabs3, PracticeMaster,
CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE
 UDC 343.3/.7:340.6 Pregledni rad CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE American University in Bosnia & Herzegovina, BOSNIA & HERZEGOVINA, e-mail: edita.bajramovic@gmail.com
UDC 343.3/.7:340.6 Pregledni rad CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE American University in Bosnia & Herzegovina, BOSNIA & HERZEGOVINA, e-mail: edita.bajramovic@gmail.com
Developing a Network:
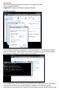 Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
20698 Installing and Configuring Windows 10
 Course Overview This five-day instructor-led course provides IT professionals with the knowledge and skills required to install and configure Windows 10 desktops in a Windows Server small to mediumsized
Course Overview This five-day instructor-led course provides IT professionals with the knowledge and skills required to install and configure Windows 10 desktops in a Windows Server small to mediumsized
Wake Technical Community College Computer Technologies Division Syllabus
 Wake Technical Community College Computer Technologies Division Syllabus Course Number: NOS-220 Course Title: Linux/UNIX Admin I Textbook Information (Opens in Barnes & Noble Search window) http://waketech.bncollege.com/webapp/wcs/stores/servlet/tbwizardview?catalogid=10001&langid=-
Wake Technical Community College Computer Technologies Division Syllabus Course Number: NOS-220 Course Title: Linux/UNIX Admin I Textbook Information (Opens in Barnes & Noble Search window) http://waketech.bncollege.com/webapp/wcs/stores/servlet/tbwizardview?catalogid=10001&langid=-
What equipment do I need?
 GETTING STARTED GUIDE: FOR CLIENTS Telehealth by This guide includes basic tips and instructions on how to join a video session, as well as some FAQs to make your first video call a success. To prepare,
GETTING STARTED GUIDE: FOR CLIENTS Telehealth by This guide includes basic tips and instructions on how to join a video session, as well as some FAQs to make your first video call a success. To prepare,
Dynatrace Data Center RUM Professional Certification. Exam Blueprint
 Dynatrace Data Center RUM Professional Certification Exam Blueprint Introduction The Data Center Real User Monitoring (DC RUM) Professional Certification covers Dynatrace APM and NPM technologies. It validates
Dynatrace Data Center RUM Professional Certification Exam Blueprint Introduction The Data Center Real User Monitoring (DC RUM) Professional Certification covers Dynatrace APM and NPM technologies. It validates
Independent Solution Review AppEnsure for Citrix Monitoring
 Independent Solution Review AppEnsure for Citrix Monitoring Pawel Serwan, organizer of Polish Citrix Users Group Monitoring is always one of the most important topics that you have to define during implementation
Independent Solution Review AppEnsure for Citrix Monitoring Pawel Serwan, organizer of Polish Citrix Users Group Monitoring is always one of the most important topics that you have to define during implementation
Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access)
 Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access) Published June 2015 Why do certain web-based applications have issues through the rewrite engine compared to accessing the resource
Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access) Published June 2015 Why do certain web-based applications have issues through the rewrite engine compared to accessing the resource
LEARN READ ON TO MORE ABOUT:
 For a complete picture of what s going on in your network, look beyond the network itself to correlate events in applications, databases, and middleware. READ ON TO LEARN MORE ABOUT: The larger and more
For a complete picture of what s going on in your network, look beyond the network itself to correlate events in applications, databases, and middleware. READ ON TO LEARN MORE ABOUT: The larger and more
Welcome to PDQ Inventory
 Getting Started Contents Welcome to PDQ Inventory........ 1 Licensing.................... 2 PDQ Inventory Licensing Mode Comparison.................. 2 PDQ Inventory Product Feature Comparison..................
Getting Started Contents Welcome to PDQ Inventory........ 1 Licensing.................... 2 PDQ Inventory Licensing Mode Comparison.................. 2 PDQ Inventory Product Feature Comparison..................
Software System For Automatic Reaction To Network Anomalies And In Real Time Data Capturing Necessary For Investigation Of Digital Forensics
 Software System For Automatic Reaction To Network Anomalies And In Real Time Data Capturing Necessary For Investigation Of Digital Forensics Mladen Vukašinović Faculty of Information Technology Mediterranean
Software System For Automatic Reaction To Network Anomalies And In Real Time Data Capturing Necessary For Investigation Of Digital Forensics Mladen Vukašinović Faculty of Information Technology Mediterranean
A Software System for automatic reaction to network anomalies and in Real Time Data Capturing necessary for investigation of digital Forensics
 A Software System for automatic reaction to network anomalies and in Real Time Data Capturing necessary for investigation of digital Forensics Mladen Vukašinović Abstract Digital forensics has a technical
A Software System for automatic reaction to network anomalies and in Real Time Data Capturing necessary for investigation of digital Forensics Mladen Vukašinović Abstract Digital forensics has a technical
Iphone 3g Factory Reset
 Iphone 3g Factory Reset Thank you very much for reading. As you may know, people have search numerous times for their chosen books like this, but end up in harmful downloads. Rather than reading a good
Iphone 3g Factory Reset Thank you very much for reading. As you may know, people have search numerous times for their chosen books like this, but end up in harmful downloads. Rather than reading a good
Administering System Center Configuration Manager ( A)
 Administering System Center Configuration Manager (20703-1A) Duration: 5 Days Price: $895 Delivery Option: Attend via MOC On-Demand Students Will Learn Describing the features Configuration Manager and
Administering System Center Configuration Manager (20703-1A) Duration: 5 Days Price: $895 Delivery Option: Attend via MOC On-Demand Students Will Learn Describing the features Configuration Manager and
Appendix F Course codes, descriptions, units, lecture/lab
 Appendix F Course codes, descriptions, units, lecture/lab CIS 003 Introduction to Microsoft Word Units: 1 Students will learn the basics of Windows and Microsoft Word. Specific topics covered include:
Appendix F Course codes, descriptions, units, lecture/lab CIS 003 Introduction to Microsoft Word Units: 1 Students will learn the basics of Windows and Microsoft Word. Specific topics covered include:
